Victoria’s Secret Angels Erin Heatherton, Adriana Lima, Candice Swanepoel, Lindsay Ellingson, Doutzen Kroes and Lily Aldridge let you in on their resolutions and a sexy little New Year’s tradition.
Month: December 2011
VIDEO – Bollywood Stars wish ‘Happy New Year 2012’ – EXCLUSIVE
POLITICAL MURDER TODAY – Syria man records his own death
FEMEN Protes in Kiev – Uncensored
Study – Open Source Center Chinese Premier Promotes Cyberspace Agenda

Authoritative PRC media reports of Chinese Premier Wen Jiabao’s live online appearances illustrate authorities’ expanding use of the Internet to set and control policy discourse in Chinese-language virtual space. They also suggest ongoing efforts to manage leaders’ images and portray them as accessible and soliciting online public opinion. While some apparent missteps suggest a cautious, evolving approach to interactive Internet media in relation to top leaders, reported leadership statements indicate sustained attention to the goal of incorporating new technologies into the propaganda system.
Recent online appearances by Chinese Premier Wen Jiabao on authoritative PRC media platforms indicate that Beijing continues to expand its use of Internet media to broadcast unique programs communicating the government’s view and signaling its policy preferences as part of its overall media strategy.
- On Saturday 27 February, in the run-up to the annual meeting of China’s National People’s Congress (NPC), Wen appeared in a live “web chat” — his second — jointly hosted by Xinhua Wang, the internet portal of PRC official news agency Xinhua, and by Zhongguo Zhengfu Wang (www.gov.cn), the PRC central government website. The two sites also posted feature pages with reports, video, and transcripts of the chat. Xinhua billed the event in advance as Wen’s “annual dialogue with netizens” (27 December 2009).
- Wen’s 27 February 2010 online appearance followed his first live “web chat” (zaixian fangtan), held by Zhongguo Zhengfu Wang on 28 February 2009. Xinhua later described that chat as the first of the “top ten events” of 2009 (29 December 2009).
- On 27 December 2009, Xinhua Wang broadcast an exclusive online interview of Wen held inside the Zhongnanhai central leadership compound, in which — like the web chats — Wen presented the Chinese leadership’s views by “answering netizens’ questions.”
Suggesting an attempt to portray Wen as accessible and soliciting public opinion, in his live online appearances Wen answered selected questions ostensibly submitted by Internet users. Reports portrayed the live online events as direct and sincere communication between Wen and the public as represented by Internet users, who are sometimes referred to in PRC media as “netizens” (wang min) or “net friends” (wang you).
- The moderator of Wen’s 27 February web chat claimed to have selected questions from among 190,000 submitted online by Internet users and 70,000 submitted via cell phone instant message (SMS) by users of the joint Xinhua Wang — China Mobile online newspaper, according to the chat transcript (Xinhua Wang). The moderator described “net friends” worldwide as “eagerly looking forward” to “meeting” Wen based on the “deep, positive impression” created by the 2009 web chat, in which Wen was said to have answered Internet users’ questions in a “frank and honest way.”
- Wen and the moderator worked to create personal emotional appeal throughout the chat, starting with the language of Wen’s opening remarks emphasizing his sense of duty to “the people” and his desire to have a sincere “heart-to-heart” exchange (Xinhua Wang). Wen claimed that he “follows the various issues raised by netizens on the Internet very closely.”
- Similarly, a Xinhua report on the February 2009 web chat quoted Wen as saying that the government needs to solicit “questions about governance from the people” (28 February 2009).
- Jiefangjun Bao Online, website of the daily newspaper of the Central Military Commission, touted “zero distance” between netizens and the PRC leadership and described Wen as a “super net friend” in a report on the 2009 web chat (10 March 2009).
DOWNLAOD ORIGINAL DOCUMENT HERE
FBI – Former Chief Executive Officer of Construction Supply Company Convicted in Bank Fraud Scheme
BROOKLYN, NY—Following three weeks of trial, a federal jury in Brooklyn today returned guilty verdicts against Courtney Dupree, the former chief executive officer at GDC Acquisitions, on charges of bank fraud, false statements, and conspiracy to commit bank fraud. These charges arose out of the defendant’s scheme to defraud Amalgamated Bank, GDC’s asset-based lender, of $21 million in fraudulent loans. When sentenced by U.S. District Judge Kiyo Matsumoto, the defendant faces a maximum sentence of 30 years in prison on the most serious charge. The jury also acquitted Thomas Foley, GDC’s former chief operating officer.
The verdicts were announced by Loretta E. Lynch, U.S. Attorney for the Eastern District of New York.
GDC, based in Long Island City, Queens, is a holding company that owns various subsidiaries, including JDC Lighting, a lighting distributor; Unalite Electric and Lighting, a lighting maintenance company; and Hudson Bay Environments Group, a furniture distributor. The evidence included the testimony of GDC’s former chief financial officer and two GDC accountants, all three of whom had previously pleaded guilty to fraud charges arising from the scheme. At trial, the government proved Dupree and others gave Amalgamated Bank false financial information for GDC in which they had fraudulently inflated the company’s accounts receivables in order to obtain initially, and then maintain, credit lines totaling approximately $21 million. For example, the defendant represented to Amalgamated Bank in writing in November 2009 that GDC had $25.2 million in accounts receivables when, in fact, it had only $9 million. The evidence proved that the conspirators inflated the accounts receivables by a variety of means, including by recording fake sales that had never taken place in the corporate books. According to the trial testimony, the scheme unraveled when one of the accountants turned himself into the FBI and cooperated in the government’s investigation in an undercover capacity for approximately two months.
“The defendant Courtney Dupree defrauded an FDIC insured bank out of millions of dollars by lying about his company’s financial condition,” stated U.S. Attorney Lynch. “Executives who abuse positions of influence and trust should expect to be investigated and prosecuted to the full extent of the law.”
U.S. Attorney Lynch extended her grateful appreciation to the FBI and the U.S. Postal Inspection Service, the agencies responsible for leading the government’s criminal investigation.
The government’s case is being prosecuted by Assistant U.S. Attorneys David C. Woll and Michael L. Yaeger, and Special Assistant U.S. Attorney Brian Morris.
This case was brought in coordination with President Barack Obama’s Financial Fraud Enforcement Task Force. President Obama established the interagency Financial Fraud Enforcement Task Force to wage an aggressive, coordinated and proactive effort to investigate and prosecute financial crimes. The task force includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general, and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch, and with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes. For more information about the task force, visit http://www.stopfraud.gov.
FRAUD – Confidential People’s Bank of China Report on Billions in Theft by Government Officials



DOWNLOAD ORIGINAL DOCUMENT HERE
This report was originally released by the Chinese central bank before later being removed. For more explanation of the report and its contents, see:

China’s rulers say corrupt cadres are the nation’s worst enemy. Now, according to a report that was given widespread coverage this week in local media, Beijing says that enemy resides overseas, particularly in the U.S.
The 67-page report from China’s central bank looks at where corrupt officials go and how they get their money out. A favored method is to squirrel cash away with the help of loved ones emigrating abroad, schemes that often depend on fake documents.
News of the study got prominent notice this week in Chinese media. A sample headline from page one of the Shanghai Daily on Thursday: “Destination America For China’s Corrupt Officials.”
The reports said the study was posted to the website of China’s central bank. While the document remains widely available in Chinese cyberspace, the report – dated June 2008 and identified as “confidential” – no longer appears on the People’s Bank of China website.
The central bank didn’t respond to requests for comment.
Though the report reads like an academic study, it doesn’t cite a clear conclusion.
Instead, it is broken into two main sections, the first starting with estimates that up to 18,000 corrupt officials and employees of state-owned enterprises have fled abroad or gone into hiding since the mid-1990s. They are suspected of pilfering coffers to the tune of 800 billion yuan, or $123 billion — a sum that works out to 2% of last year’s gross domestic product.
Destination America for China’s corrupt officials:
America is the destination most favored by high-ranking corrupt Chinese officials fleeing the country with large sums of money, according to a report by China’s central bank.
Other popular destinations include Australia and the Netherlands.
Those unable to get visas for Western countries opt for temporary stays in small countries in Africa, Latin America and eastern Europe while they wait for a chance to move to more developed countries, the People’s Bank of China report said.
Low-ranking officials usually escape to neighboring countries such as Thailand, Myanmar, Malaysia, Mongolia and Russia, it said.
The report cited research by the Chinese Academy of Social Sciences which revealed that about 16,000 to 18,000 government employees, police officers, judicial officers, senior managers of government institutions and state-owned companies, as well as employees of Chinese organizations in foreign countries, had escaped abroad or gone missing since the middle of the 1990s.
The money they carried with them is said to add up to 800 billion yuan (US$123 billion).
SECRET – U.S. Pacific Command China Pandemic Influenza Readiness Review

The United States (U.S.) Pacific Command (PACOM) and the Hawaii National Guard (HING) have entered into an Inter-Service Support Agreement (ISSA) to execute two (2) USPACOM J07, Command Surgeon, Pandemic Influenza (PI) led activities in support of the U.S. Agency for International Development (USAID): A Comprehensive Nation Review/Disparity Analysis and a PI Healthcare System Surge Demand and Intervention Workshop. These USAID approved and resourced training and education activities support military-to-military engagement for a World Health Organization (WHO) PI Phase 6 event in six (6) USAID focus countries; a WHO PI Phase 6 event is defined as sustained human-to-human transmission in at least two (2) WHO regions with at least two (2) countries involved in one of the regions. The six (6) USAID focus countries for this project are Bangladesh, Cambodia, China, Indonesia, Nepal, and Vietnam. This report will focus specifically on China.
The People’s Republic of China is one of the global leaders in vaccine research and production, and an active participant in international PI initiatives, but despite steps to improve influenza surveillance and ministerial coordination, major challenges remain to Chinese PI response preparedness. Substantial global concern has emerged in recent years regarding China’s ability to effectively monitor, prevent, and contain infectious disease threats within its borders. Factors including potential Avian Influenza (AI) outbreaks in poultry, China’s immense size and population, a largely underdeveloped health care infrastructure, and a sizable poultry industry all contribute to make China a global PI hotspot and an important area of focus for the potential emergence of human influenza pandemics that threaten the rest of the world.
A PI Review Team from PACOM will use the results of this report as a starting point to complete an in-country review of China’s military capabilities (People’s Liberation Army) to prepare for and respond to this threat. The team will use an interactive Review Tool, standardized and scalable to the needs of China, to aid the team members in identifying capability disparities. Analysis of the information collected in this Review Report and through the use of the Review Tool will provide PACOM and USAID with the data needed to develop a three (3) to five (5) year strategic plan for future PI preparedness efforts in China.
DOWNLOAD ORIGINAL DOCUMENT HERE
CONFIDENTIAL – The Majority of U.S. Foreign Aid is Now Military Aid

A new bill approved by Congress last week would again make the Defense Department the premier funder of security assistance to foreign countries, giving it more than double the comparable budget of the agency popularly associated with America’s foreign aid, the State Department.
The $17 billion Pentagon aid budget for the 2012 fiscal year is the second in a row to exceed the State Department’s by $10 billion, a disparity that has begun to provoke debate among foreign policy experts in Washington. Seven years ago, circumstances were reversed, with the State Department spending triple the amount the Pentagon spent on such aid.
Some foreign aid experts have complained that, as a result of the shifting responsibilities, U.S. aid priorities have shifted from trying to establish good governance to supporting stronger foreign military partners.
Defense-funded security assistance programs, like those funded directly by the State Department, include military and police training, counter-drug assistance, counterterrorism activities, and infrastructure projects. These programs, detailed in the 2012 National Defense Authorization Act, have been steadily expanding, according to a March 2011 report by the Stimson Center, a nonprofit research group in Washington.
The expansion has largely come at the expense of the authority of the State Department, which was long chiefly responsible for the planning, budgeting and oversight of security assistance – including military training – with the Department of Defense responsible for implementation. After 9/11, the Pentagon has assumed more authority in foreign aid budgeting and planning.
…
The Pentagon has argued that supporting foreign forces reduces the chance that U.S. troops will be deployed overseas. The Pentagon has also long complained that State Department-run aid programs are too slow and inflexible. Its combatant commanders now frequently tap funds that can be distributed almost at will, known in aid parlance as “walking around money” and formally as the Combatant Commander Initiative Fund and the Commander Emergency Response Fund.
The 2012 budget bill authorizes spending of more than $415 million for these funds, or around $100 million less than in 2011.
NEO-STASI 2011 – WIE DIE NEO-STASI HEUTE AKTIV IST – 2011 – Retrospective-Retrospektive
Dear Readers,
the year 2011 has shown which damage the “Nazi underground” and their terrorist cell could do.
Much more damage, much meaner and more dangerous is going on with the Neo-Stasi.
They have a strong netwerk of politicians, lawyers, attorneys, bankers, media, hackers, SEO specialists, informers, experts and cyber-infiltration killers, but continues to be of professional killers.
Because these people were still not detected and punished.
They still use a lot of money missing from the DDR-money and their fellows even sit in the German parliament!
The peak of the iceberg is “GoMoPa”.
They could even prevent an impeccable Berlin justice Senator by infiltrating the media before he could be dangerous for them.
2011 was the year of the unmasking of Neo- Stasi and their supporters in the media and the judiciary by our strength and dedication.
Sincerely yours,
Bernd Pulch, Master of Arts in Journalism, Germanic and Comparative Literature
Liebe Leser,
das Jahr 2011 hat gezeigt, welche Schäden der “Nationalsozialistische Untergrund” und deren Terror-Zelle angerichtet hat.
Viel mehr Schäden, viel gefährlicher und viel gemeiner geht die Neo-Stasi vor.
Sie verfügt über ein starkes Netwerk von Politkern, Anwälten, Bankiers, Medien, Hackern, SEO-Spezialisten, Unterwanderungsexperten und Cyber-Killern, aber auch weiterhin von professionellen Mördern.
Denn diese Leute wurden bis heute nicht enttarnt und bestraft. Gehen die etwa aufs Arbeitsamt oder schulen die sogar um ?
Wohl kaum, denn sie werden weiter gefragt, die alten Stasi-Seilschaften funktionieren und viel Geld aus den verschwundenen DD-Geldern ist da und die Genossen sitzen sogar im Bundestag !
Die Spitze des Eisberg ist die enttarnte Stasi-Seilschaft “GoMOPa”.
Sie konnten sogar einen untadeligen Berliner Justiz-Senator durch willfährige Medien verhindern bevor er ihnen gefährlich werden konnte.
2011 war auch das Jahr der Enttarnung dieser Stasi-Bande ud ihrer Helfer in den Medien und in der Justiz.
Herzlichst Ihr
Brnd Pulch, Magister Artium der Publizistik, Germanistik und Komparatistik
TOP-SECRET-Libyan Intelligence Service CIA-MI6 Extraordinary Rendition Documents




These documents concerning CIA rendition of terrorism suspects, with the help of the UK, were recovered from the offices of Libyan intelligence.
DOWNLOAD FULL DOCUMENTS HERE
CONFIDENTIAL -STRATFOR Hacked Update
30 December 2011. A writes that five Pastebin posts of recovered STRATFOR passwords have been removed as indicated below. In addition, four files from sources have been removed from Rapid Share (1) and Wikisend (3).
29 December 2011.
Lulzxmas Dumps 860,000 STRATFOR Accounts:
http://www.megaupload.com/?d=O5P03RXK
28 December 2011.
Prepping for the Stratfor 5M Email Release
27 December 2011.
http://pastebin.com/78MUAaeZ [Now removed]
These are 28517 of 53281 (54%) passwords from the list of STRATFOR customer accounts cracked.
Part 1/3: http://pastebin.com/CdD92fJG [Now removed]
Part 2/3: http://pastebin.com/AcwQgHmF [Now removed]
Part 3/3: http://pastebin.com/78MUAaeZ [Now removed]
26 December 2011. Firms and personal first names beginning with “D” through “My” (~ 30,000).
https://rapidshare.com/#!download|44tl6|2444489251|STRATFOR_full_d_m.txt.gz|3255|
R~7B8842ED6343CEAE67A23C094E131679|0|0 [Now removed]
And 25,000 IT work tickets:
http://www.verzend.be/s8v8ccig12hp/it.tar.gz.html
26 December 2011. Sample Stratfor.com email:
“just a small preview of the mayhem to come. 1 out of 2.7 million”
26 December 2011. STRATFOR leaked accounts (10257 passwords recovered)
http://pastebin.com/CdD92fJG [Now removed]
25 December 2011. Firms and personal miscellaneous names not in alphabetical order (~13,000):
http://pastebin.com/8v3768Bw [Now removed]
http://wikisend.com/download/132838/stratfor_full_misc.txt.gz [Now removed]
25 December 2011. Firms and personal first names beginning with “B-By” through “C-Cz” (~4,000) :
http://wikisend.com/download/597646/stratfor_full_b.txt.gz [Now removed]
25 December 2011. Firms and personal first names beginning with “A” through “Az” (~ 4,000).
http://wikisend.com/download/601776/stratfor_full_a.txt.gz [Now removed]
25 December 2011. A message allegedly to subscribers from George Friedman, Stratfor, was posted to Facebook and Pastebin (below).
25 December 2011. A paste today denying Anonymous role:
And, Stratfor’s A client list of passwords:
24 December 2011
STRATFOR Hacked
Related:
A sends:
Subject: Important Announcement from STRATFOR
Date: Sat, 24 Dec 2011 19:49:58 -0500
From: STRATFOR <mail[at]response.stratfor.com>
Dear Stratfor Member,
We have learned that Stratfor’s web site was hacked by an unauthorized party. As a result of this incident the operation of Stratfor’s servers and email have been suspended.
We have reason to believe that the names of our corporate subscribers have been posed [sic] on other web sites. We are diligently investigating the extent to which subscriber information may have been obtained.
Stratfor and I take this incident very seriously. Stratfor’s relationship with its members and, in particular, the confidentiality of their subscriber information, are very important to Stratfor and me. We are working closely with law enforcement in their investigation and will assist them with the identification of the individual(s) who are responsible.
Although we are still learning more and the law enforcement investigation is active and ongoing, we wanted to provide you with notice of this incident as quickly as possible. We will keep you updated regarding these matters.
Sincerely,
George Friedman
STRATFOR
221 W. 6th Street, Suite 400
Austin, TX 78701 US
http://www.stratfor.com
http://www.facebook.com/stratfor
Dec 25th, 2011
On December 24th an unauthorized party disclosed personally identifiable information and related credit card data of some of our members. We have reason to believe that your personal and credit card data could have been included in the information that was illegally obtained and disclosed.
Also publicly released was a list of our members which the unauthorized party claimed to be Stratfor’s “private clients.” Contrary to this assertion the disclosure was merely a list of some of the members that have purchased our publications and does not comprise a list of individuals or entities that have a relationship with Stratfor beyond their purchase of our subscription-based publications.
We have also retained the services of a leading identity theft protection and monitoring service on behalf of the Stratfor members that have been impacted by these events. Details regarding the services to be provided will be forwarded in a subsequent email that is to be delivered to the impacted members no later than Wednesday, December 28th.
In the interim, precautions that can be taken by you to minimize and prevent the misuse of information which may have been disclosed include the following:
– contact your financial institution and inform them of this incident;
– if you see any unauthorized activity on your accounts promptly notify your financial institution;
– submit a complaint with the Federal Trade Commission (“FTC”) by calling 1-877-ID-THEFT (1-877- 438-4338) or online at https://www.ftccomplaintassistant.gov/; and
– contact the three U.S. credit reporting agencies: Equifax (http://www.equifax.com/ or (800) 685-1111), Experian (http://www.experian.com/ or (888) 397-3742), and TransUnion (http://www.transunion.com/ or (800) 888-4213), to obtain a free credit report from each.
Even if you do not find any suspicious activity on your initial credit reports, the FTC recommends that you check your credit reports periodically. Checking your credit reports can help you spot problems and address them quickly.
To ease any concerns you may have about your personal information going forward, we have also retained an experienced outside consultant that specializes in such security matters to bolster our existing efforts on these issues as we work to better serve you. We are on top of the situation and will continue to be vigilant in our implementation of the latest, and most comprehensive, data security measures.
We are also working to restore access to our website and continuing to work closely with law enforcement regarding these matters. We will continue to update you regarding the status of these matters.
Again, my sincerest apologies for this unfortunate incident.
Sincerely,
George Friedman
SECRET – (SBU) State Department Uganda Lord’s Resistance Army Disarmament Report to Congress

The Lord’s Resistance Army Disarmament and Northern Uganda Recovery Act, Public Law 111-172, requires the Secretary of State to submit a report to Congress on implementation of the President’s strategy to support disarmament of the Lord’s Resistance Army (LRA) and assistance provided toward a lasting solution to the conflict in northern Uganda.
The United States has worked over the last year with our bilateral and multilateral partners to advance the President’s strategy. With our encouragement, the African Union (AU) and United Nations (UN) are working to enhance regional coordination toward addressing the LRA threat. We have also continued to support regional efforts to increase diplomatic and military pressure on the LRA. We have deployed U.S. military personnel to the region to serve as advisors to regional militaries pursuing the LRA. Meanwhile, we continue work with partners in the region to increase civilian protection, facilitate LRA defections, and address humanitarian needs, while also supporting the recovery of northern Uganda.
The United States remains committed to pursuing the multi-year, comprehensive strategy submitted to Congress last year. Any reduction in regional cooperation or military pressure could enable the LRA to regroup and rebuild its forces. However, the extent of U.S. efforts to implement the strategy remains a function of available and consistent resources. Given our budget constraints, we continue to encourage other members of the international community to join this effort and help fill funding gaps. We co-chair the International Working Group on the LRA, a mechanism established to enhance coordination among all donors.
Enhancing Regional Efforts to Apprehend LRA Top Commanders
Over the last year, the United States has worked with regional governments to enhance their military operations to apprehend or remove top LRA commanders from the battlefield. We continue to provide critical logistical support and nonlethal equipment to assist the Ugandan military’s counter-LRA operations. With our encouragement, the government of the Democratic Republic of the Congo (DRC) has deployed a U.S. trained and equipped battalion to participate in counter-LRA efforts in the LRA’s area of operations in the DRC. As the Central African Republic (CAR) and South Sudan increase their efforts to counter the LRA, we are engaging with and supporting their militaries. We have provided some equipment to the CAR forces deployed to the LRA-affected area.
Although regional militaries have reduced the LRA’s numbers to an estimated 200 core fighters and an unknown number of accompanying children and abductees, the LRA will remain a serious regional threat as long as Joseph Kony and the LRA’s top leaders remain in place. Over the last year, sustained military pressure has limited the LRA’s opportunities to regroup and rearm. Abductees and low-level fighters have continued to escape and reintegrate into their communities. Nonetheless, the LRA is still terrorizing communities and undermining regional security across a broad swath of central Africa. According to the UN, there have been over 250 attacks attributed to the LRA this year alone.
In line with the President’s strategy, we have reviewed how we can improve our support to the coalition of LRA-affected countries to increase the likelihood of successful operations to apprehend or remove LRA top commanders from the battlefield and bring them to justice. On October 14, the President reported to Congress that he had authorized a small number of U.S. forces to deploy to the LRA-affected region, in consultation with the regional governments, to act as advisors to the regional militaries that are pursuing the LRA. These advisors will enhance the capacity of regional militaries to coordinate and fuse intelligence with effective operational planning. The U.S. forces will not themselves engage directly against LRA forces unless necessary to defend themselves.
This is a short-term deployment with clear goals and objectives. We believe the U.S. advisors can address critical capabilities gaps to help the regional forces succeed. Additionally, our advisors are sensitive to civilian protection considerations and will work closely with our embassies to ensure they remain cognizant of local and regional political dynamics. The State Department has deployed a Civilian Response Corps officer to the region to work with the advisors in this regard. We will regularly review and assess whether the advisory effort is sufficiently enhancing the regional effort to justify continued deployment. Our embassies will also continue to consult with the regional governments and ensure their consent as we move forward. Continued deployment is conditional on regional governments’ sustained commitment and cooperation to bring an eventual end to the LRA threat.
…
Supporting Post-Conflict Recovery and Reconciliation in Northern Uganda Finally, the United States remains committed to supporting efforts to promote comprehensive reconstruction, transitional justice, and reconciliation in northern Uganda, where the LRA carried out its brutal campaign for nearly two decades. In Fiscal Year 2011, USAID provided approximately $102 million in assistance to northern Uganda, including:
• $2 million to assist internally-displaced persons (IDPs) and returnees to secure durable return solutions;
• $2.1 million to enhance accountability and administrative competence of local governance institutions, including the civilian police and judiciary;
• $4.2 million to help former LRA combatants with vocational education and employment opportunities; and
• $15 million to promote rural rehabilitation and food security.Northern Uganda has undergone a visible transformation since the LRA’s departure from Uganda in 2005, especially in terms of infrastructure and social services. The population is able to move freely, stores are open, and fields are being cultivated. According to UNHCR, an estimated 95 percent of people once living in IDP camps have moved from camps to transit sites or returned home.
According to the Ugandan Bureau of Statistics, poverty in northern Uganda declined from 60.7 percent to 46.2 percent between 2005/6 and 2009/10, representing the largest decline in poverty of all regions in Uganda during that period. Yet, even with this impressive decline, the north remains the poorest region in the country. Furthermore, land issues, tensions between tribes and subtribes in the region, and widespread psycho-social trauma, among other issues, need to be addressed to ensure the sustainability of peace in northern Uganda.
From 2009 to 2011, the Government of Uganda (GoU) contributed approximately $ 110 million to its Peace, Recovery and Development Plan for Northern Uganda (PRDP). This is less than the government’s original pledge to provide 30 percent of the PRDP’s total budget, but GoU officials state that they will continue to earmark funds for northern Uganda’s recovery. During this period, non-USG donors have provided significant funding in support of the PRDP.
DOWNLOAD FULL DOCUMENT HERE
MEDIA – White House Refuses to Inform Lawmakers About Drone Operations

Tensions Rising Over Drone Secrecy:
Tensions are quietly increasing between the White House and some congressional leaders over access to sensitive information about the government’s use of drones in Pakistan and Yemen, officials said.The White House has brushed aside requests for information from lawmakers, who argue that the strikes, carried out secretly by the Central Intelligence Agency and the military’s Joint Special Operations Command, have broad implications for U.S. policy but don’t receive adequate oversight.Some current and former administration, military and congressional officials point to what they see as significant oversight gaps, in part because few lawmakers have full access to information about the drone strikes.Lawmakers on Congress’s intelligence committees are privy to information about all CIA and military-intelligence operations, but members of at least two other panels want insight on the drone program. Compounding the dispute: Lawmakers who are briefed on classified information are legally constrained from raising their concerns publicly. Current and former officials say the White House wants to keep a tight hold on classified information to avoid unauthorized disclosures.
The demand for lawmakers outside the intelligence committees to have access to details on the covert drone program, said one U.S. official, “just doesn’t hold water.”
…
After the CIA launches a drone strike, the intelligence committees receive a notification telephone call almost immediately, which is followed by a secure fax with the details of the strike, according to government officials. There are also monthly meetings at the CIA’s Langley, Va. headquarters with congressional staff to review the program and classified briefings or hearings on Capitol Hill at least every three months.
Administration officials say the drone programs run by the CIA and Joint Special Operations Command are carefully monitored by top officials at both agencies and by the White House National Security Council.
Secrecy defines Obama’s drone war:
Since September, at least 60 people have died in 14 reported CIA drone strikes in Pakistan’s tribal regions. The Obama administration has named only one of the dead, hailing the elimination of Janbaz Zadran, a top official in the Haqqani insurgent network, as a counterterrorism victory.The identities of the rest remain classified, as does the existence of the drone program itself. Because the names of the dead and the threat they were believed to pose are secret, it is impossible for anyone without access to U.S. intelligence to assess whether the deaths were justified.The administration has said that its covert, targeted killings with remote-controlled aircraft in Pakistan, Yemen, Somalia and potentially beyond are proper under both domestic and international law. It has said that the targets are chosen under strict criteria, with rigorous internal oversight.It has parried reports of collateral damage and the alleged killing of innocents by saying that drones, with their surveillance capabilities and precision missiles, result in far fewer mistakes than less sophisticated weapons. Yet in carrying out hundreds of strikes over three years — resulting in an estimated 1,350 to 2,250 deaths in Pakistan — it has provided virtually no details to support those assertions.
Exposed and Uncensored – Nudity Protests
|
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict3.jpg) ** EDS NOTE NUDITY ** Brazilian carnival queen Viviane Castro parades with an image depicting President Barack Obama painted on her left leg during carnival celebrations in Sao Paulo, Brazil, Saturday, Feb. 21, 2009. Castro’s stomach reads in Portuguese “for sale,” a message she said represented the sale of Brazil’s Amazon to the U.S. (Folha Imagem, Lalo de Almeida) ** EDS NOTE NUDITY ** Brazilian carnival queen Viviane Castro parades with an image depicting President Barack Obama painted on her left leg during carnival celebrations in Sao Paulo, Brazil, Saturday, Feb. 21, 2009. Castro’s stomach reads in Portuguese “for sale,” a message she said represented the sale of Brazil’s Amazon to the U.S. (Folha Imagem, Lalo de Almeida) |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict18.jpg) (EDITORS NOTE: Image contains nudity. The indignants have come from across the country to protest high levels of unemployment, the austerity measures and what they consider a stagnant and corrupt political system. Getty (EDITORS NOTE: Image contains nudity. The indignants have come from across the country to protest high levels of unemployment, the austerity measures and what they consider a stagnant and corrupt political system. Getty
|
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict9.jpg) ** EDS NOTE NUDITY ** A model walks her bicycle during a protest against worldwide pollution in Bogota, Wednesday, April 1, 2009. (Fernando Vergara) ** EDS NOTE NUDITY ** A model walks her bicycle during a protest against worldwide pollution in Bogota, Wednesday, April 1, 2009. (Fernando Vergara) |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict22.jpg) EDS NOTE NUDITY – South Korean prostitutes in their underwear and covered in body and face paint, and some others wearing mourning clothes, rush to police line after a rally in Seoul, South Korea, Tuesday, May 17, 2011. Hundreds of prostitutes and pimps rallied Tuesday near a red-light district in Seoul to protest a police crackdown on brothels, with some unsuccessfully attempting to set themselves on fire. AP EDS NOTE NUDITY – South Korean prostitutes in their underwear and covered in body and face paint, and some others wearing mourning clothes, rush to police line after a rally in Seoul, South Korea, Tuesday, May 17, 2011. Hundreds of prostitutes and pimps rallied Tuesday near a red-light district in Seoul to protest a police crackdown on brothels, with some unsuccessfully attempting to set themselves on fire. AP |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict14.jpg) ** EDS NOTE NUDITY ** A woman holds up her bike during the World Naked Bike Ride in Sao Paulo, Saturday, June 14, 2008. Although total nudity is prohibited in public areas in Brazil, the woman was not detained. Of about 200 bikers, police detained only one man after he denied to wear his clothes. (Andre Penner) ** EDS NOTE NUDITY ** A woman holds up her bike during the World Naked Bike Ride in Sao Paulo, Saturday, June 14, 2008. Although total nudity is prohibited in public areas in Brazil, the woman was not detained. Of about 200 bikers, police detained only one man after he denied to wear his clothes. (Andre Penner) |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict12.jpg) ** EDS NOTE NUDITY ** A policemen kicks a man during the World Naked Bike Ride in Sao Paulo, Saturday, June 14, 2008.(Andre Penner) ** EDS NOTE NUDITY ** A policemen kicks a man during the World Naked Bike Ride in Sao Paulo, Saturday, June 14, 2008.(Andre Penner) |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict23.jpg) (EDITORS NOTE: THIS IMAGE CONTAINS PARTIAL NUDITY) Protesters perfom during demonstrations against the influence of bankers and financiers in front of the Reichstagsgebaeude on October 15, 2011 in Berlin, Germany. Thousands of people took to the streets today in cities across Germany in demonstrations inspired by the Occupy Wall Street protests in the United States. Activists are demanding an end to the free-wheeling ways of global financial players whom they see as responsible for the current European and American economic woes. (EDITORS NOTE: THIS IMAGE CONTAINS PARTIAL NUDITY) Protesters perfom during demonstrations against the influence of bankers and financiers in front of the Reichstagsgebaeude on October 15, 2011 in Berlin, Germany. Thousands of people took to the streets today in cities across Germany in demonstrations inspired by the Occupy Wall Street protests in the United States. Activists are demanding an end to the free-wheeling ways of global financial players whom they see as responsible for the current European and American economic woes.
|
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict20.jpg) AUGUST 13: (EDITORS NOTE: Image contains nudity. Several thousand men and women turned out to protest against rape and a woman’s right to her body. AUGUST 13: (EDITORS NOTE: Image contains nudity. Several thousand men and women turned out to protest against rape and a woman’s right to her body. |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict7.jpg) EDS NOTE NUDITY Semi naked activists from the Ukrainian female rights group Femen protest in front of the Saudi Arabian embassy against a ban on driving cars for women in Kiev, Ukraine, Thursday, June 16, 2011. (Sergei Chuzavkov) EDS NOTE NUDITY Semi naked activists from the Ukrainian female rights group Femen protest in front of the Saudi Arabian embassy against a ban on driving cars for women in Kiev, Ukraine, Thursday, June 16, 2011. (Sergei Chuzavkov) |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict8.jpg) ** EDS NOTE NUDITY ** A nude demonstrator gestures towards the police in Malmo, Sweden, Friday Sept. 19, 2008. A street occupation by activists on the fringes of the European Social Forum turned into stone throwing and fighting. (Drago Prvulovic) ** EDS NOTE NUDITY ** A nude demonstrator gestures towards the police in Malmo, Sweden, Friday Sept. 19, 2008. A street occupation by activists on the fringes of the European Social Forum turned into stone throwing and fighting. (Drago Prvulovic) |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict1.jpg) ** EDS NOTE NUDITY ** A protester performs during a march to mark the 1968 Tlatelolco plaza “massacre”‘ in Mexico City, Thursday, Oct. 2, 2008. Hundreds of student demonstrators were killed by men with guns and soldiers on October 2, 1968, ten days before the 1968 Summer Olympics celebrations in Mexico City. (AP Photo/Alexandre Meneghini) ** EDS NOTE NUDITY ** A protester performs during a march to mark the 1968 Tlatelolco plaza “massacre”‘ in Mexico City, Thursday, Oct. 2, 2008. Hundreds of student demonstrators were killed by men with guns and soldiers on October 2, 1968, ten days before the 1968 Summer Olympics celebrations in Mexico City. (AP Photo/Alexandre Meneghini) |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict0.jpg) ** EDS NOTE NUDITY ** Employees of LUSH Fresh Handmade Cosmetics lead a protest outside of the LUSH Walnut Street shop, wearing nothing but aprons to urge shoppers to buy products that are free of packaging, in Philadelphia, Wednesday, Aug. 27, 2008. (Justin Maxon) ** EDS NOTE NUDITY ** Employees of LUSH Fresh Handmade Cosmetics lead a protest outside of the LUSH Walnut Street shop, wearing nothing but aprons to urge shoppers to buy products that are free of packaging, in Philadelphia, Wednesday, Aug. 27, 2008. (Justin Maxon) |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict16.jpg) ** EDS NOTE: NUDITY ** Animal rights activist wearing banderillas, barbed darts which are stabbed into the bull’s neck during bullfights, are seen during a protest prior to start the nine day San Fermin Festival on Sunday in Pamplona northern Spain, Saturday, July 5, 2008. (Alvaro Barrientos) ** EDS NOTE: NUDITY ** Animal rights activist wearing banderillas, barbed darts which are stabbed into the bull’s neck during bullfights, are seen during a protest prior to start the nine day San Fermin Festival on Sunday in Pamplona northern Spain, Saturday, July 5, 2008. (Alvaro Barrientos) |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict13.jpg) ** EDS NOTE NUDITY ** A policeman sprays pepper gas as he detains a man during the World Naked Bike Ride in Sao Paulo, Saturday, June 14, 2008.(Andre Penner) ** EDS NOTE NUDITY ** A policeman sprays pepper gas as he detains a man during the World Naked Bike Ride in Sao Paulo, Saturday, June 14, 2008.(Andre Penner) |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict4.jpg) ** EDS NOTE NUDITY ** Two models wearing gas masks ride bicycles during a protest against worldwide pollution as a man takes their picture in Bogota, Wednesday, April 1, 2009. (Fernando Vergara) ** EDS NOTE NUDITY ** Two models wearing gas masks ride bicycles during a protest against worldwide pollution as a man takes their picture in Bogota, Wednesday, April 1, 2009. (Fernando Vergara) |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict15.jpg) ** EDS NOTE NUDITY ** Five models wearing gas masks pose for a photo as they protest worldwide pollution in Bogota, Wednesday, April 1, 2009. (Fernando Vergara) ** EDS NOTE NUDITY ** Five models wearing gas masks pose for a photo as they protest worldwide pollution in Bogota, Wednesday, April 1, 2009. (Fernando Vergara) |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict5.jpg) **EDS NOTE NUDITY** A group of women with their bodies painted march during the International Day of the Elimination of Violence Against Women in Bogota, Wednesday, Nov. 25, 2009. (Fernando Vergara) **EDS NOTE NUDITY** A group of women with their bodies painted march during the International Day of the Elimination of Violence Against Women in Bogota, Wednesday, Nov. 25, 2009. (Fernando Vergara) |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict6.jpg) **EDS NOTE NUDITY** Women with painted bodies perform during a march against violence against women in San Salvador, Wednesday , Nov. 25 , 2009. Hundreds of people marched Wednesday in honor of International Day for Elimination of Violence against Women. (Luis Romero) **EDS NOTE NUDITY** Women with painted bodies perform during a march against violence against women in San Salvador, Wednesday , Nov. 25 , 2009. Hundreds of people marched Wednesday in honor of International Day for Elimination of Violence against Women. (Luis Romero) |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict17.jpg) EDS NOTE NUDITY – Women protest against the high cost of living during a rally marking May Day in the streets of San Salvador, El Salvador, Sunday May 1, 2011. Activists filled the streets marking International Workers’ Day with skits and marchers that brought attention to the rising cost of living and growing disparities between the rich and poor. AP EDS NOTE NUDITY – Women protest against the high cost of living during a rally marking May Day in the streets of San Salvador, El Salvador, Sunday May 1, 2011. Activists filled the streets marking International Workers’ Day with skits and marchers that brought attention to the rising cost of living and growing disparities between the rich and poor. AP |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict21.jpg) EDS NOTE NUDITY – Students, one with her body painted, march to protest a government law project to increase private investments in public universities in Medellin, Colombia, Thursday, April 7, 2011. EDS NOTE NUDITY – Students, one with her body painted, march to protest a government law project to increase private investments in public universities in Medellin, Colombia, Thursday, April 7, 2011. |
Nudity Celebration |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict2.jpg) ** EDS NOTE NUDITY ** Dancers perform on a Vila Isabel samba school float at the Sambodrome in Rio de Janeiro, Monday, Feb. 23, 2009. (Natacha Pisarenko) ** EDS NOTE NUDITY ** Dancers perform on a Vila Isabel samba school float at the Sambodrome in Rio de Janeiro, Monday, Feb. 23, 2009. (Natacha Pisarenko) |
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict11.jpg) **EDS NOTE NUDITY** A dancer performs during the parade of the Gavioes da Fiel samba school in Sao Paulo, Sunday, Feb. 22, 2009. (Andre Penner) **EDS NOTE NUDITY** A dancer performs during the parade of the Gavioes da Fiel samba school in Sao Paulo, Sunday, Feb. 22, 2009. (Andre Penner) |
TOP-SECRET – U.S. Army Guerrilla Hunter Killer Smartbook Version 9.5

To effectively defeat an enemy, one must first understand the enemy. Intelligence professionals have forgotten the basic principles on which intelligence analysis is conducted, instead they sub-scribe to the paradigm that the enemy faced in this Global War on Terror has no structure or doctrine. Any organization, military or civilian, must have a structure and a way of doing business if they are to have any chance of being successful. As previously stated, understanding an enemy is critical to defeating him, but how much do we really understand the Taliban? We know that the Taliban fights in small groups using unconventional tactics that usually manifest themselves in the form of Improvised Explosive Device (IED), Direct Fire (DF), and Indirect Fire (IDF) attacks against Coalition Forces (CF) vehicles, patrols, and operating bases. The Taliban uses fear and intimidation against the Afghan people, collecting taxes, establishing court systems based on Shari’a law and doling out justice when these laws are broken. We also know that the Taliban enjoys sanctuary in regions bordering Afghanistan, such as Pakistan, with most of their senior leadership issuing decrees and orders just across the border. All of these “knowns” about the Taliban are not new to warfare of this nature, instead many of these same factors have been observed all over the world and throughout time. The military leader and fighter Ernesto “Che” Guevara waged guerrilla campaigns in multiple countries almost forty years ago using many of the same tactics the Taliban em-ploy today. Che’s successful war in Cuba and his failed guerrilla movements in the Congo and Bolivia are not the only historical examples of low intensity conflict that resemble our current fight in Afghanistan. Mao Tse Tung, Carlos Marighella and Alberto Bayo are just a few other Guerrilla leaders whose writings were examined and captured in the Guerrilla Hunter Killer Template. Volumes of source documents exist that can be referenced to help understand and define the enemy. Interestingly, the Guerrilla Hunter Killer Template was written using these source documents almost exclusively, but as you will see the parallels to the Taliban are frightening and therefore applicable to the war in Afghanistan. Truly understanding and defining the enemy as a collective group, not as individuals, is key to defeating him. The GH/K template blends historical writings of Guerrilla Leaders in conjunction with current and past United States Army doctrine to form the “melting pot” that is The Guerrilla Hunter Killer.
Once a base line understanding of the enemy was established, we understood the need to use common graphics and terms to accurately describe the enemy formations and tactical tasks. Sim-ply using U.S. Army operational terms and graphics does a severe disservice to all involved. The enemy we face is not the U.S. Army, and we should not attempt to “make them fit” into our own maneuver doctrine. While some tactical terms and graphics may fit what the enemy is trying to accomplish and how he organizes himself a majority do not, and at the end of the day this method is simply shoe horning the enemy into doctrine meant for ourselves. The enemy deserves his own graphics and tactical terms, for his structure and tasks are unique to what he is attempting to accomplish.

DOWNLOAD ORIGINAL DOCUMENT HERE
Confidential from the FBI – A Year in Review 2011 – Bulger, Mafia, Cybercrime, Terrorism, Fraud – Part 1

As the year comes to a close, here is a look at some of the most significant cases the Bureau investigated with the help of our domestic and international law enforcement and intelligence community partners.
Part 1 focuses on our top investigative priority: protecting the nation from terrorist attack. The death of Osama bin Laden in May was a milestone, but al Qaeda remains committed to high-profile attacks against the U.S. And on the home front, lone offenders radicalized on the Internet continue to pose a serious threat to national security.
Here are some of the top terror cases of 2011, in reverse chronological order:
Murder of U.S. soldiers in Iraq: A 38-year-old Canadian citizen was indicted this month by a New York grand jury for his role in the murder of five American soldiers in a suicide-bomb attack in Iraq in 2009. The individual was arrested last January in Canada, and the U.S. is seeking his extradition.
Senior citizens indicted in ricin plot: Four Georgia men in their 60s and 70s were arrested last month for planning to manufacture the biological toxin ricin and purchasing explosives for use in attacks against American citizens. The defendants are alleged to be part of a fringe militia group.
Plot against Saudi ambassador: Two individuals were charged in October for their participation in a plot directed by elements of the Iranian government to murder the Saudi ambassador to the U.S. with explosives while the ambassador was on U.S. soil. One of the individuals is in custody; the other is still at large.
Attack planned on U.S. Capitol: A 26-year-old Massachusetts man was arrested in September and charged with plotting to bomb the Pentagon and U.S. Capitol using remote-controlled aircraft filled with explosives.
Material support to terrorists: An Albanian citizen living in New York was charged in September with providing material support to terrorists for planning travel to Pakistan to join a radical jihadist fighting group. He was arrested while trying to catch a flight out of the country.
Texas bomb plot: A 21-year-old soldier who was absent without leave was charged in July with planning to detonate a bomb inside a restaurant frequented by soldiers from Fort Hood. When he was arrested, the individual was in possession of a variety of bomb-making components. In November he was charged with additional crimes including attempted murder.
Plot to attack Seattle military installation: Two men were indicted in July for conspiring to use a weapon of mass destruction to attack a military installation in Seattle with the intention of killing U.S. citizens. Law enforcement first became aware of the plot when an individual alerted them that he had been approached about participating in the attack.
Conduit to terror organizations: A Somali national in his mid-20s was indicted in July for providing material support to foreign terror organizations al Shabaab and al Qaeda in the Arabian Peninsula (AQAP). He was captured in the Gulf region by the U.S. military in April 2011 and was allegedly a conduit between al Shabaab and AQAP.
Iraq bomb attacks: An Iraqi citizen who allegedly carried out numerous improvised explosive device (IED) attacks against U.S. troops in Iraq and another Iraqi national alleged to have participated in the Iraq insurgency were indicted in May on terrorism charges in Kentucky, where both were residents.
Jihadist indicted: A 20-year-old Saudi Arabia citizen and Texas resident was arrested in February and charged with attempted use of a weapon of mass destruction in connection with the purchase of chemicals and equipment used to make an IED and his research of potential U.S. targets. The individual came to the U.S. in 2008 on a student visa.
Confidential from the FBI – A Year in Review 2011 – Bulger, Mafia, Cybercrime, Terrorism, Fraud – Part 2

Part 1 focused on terrorism. This segment highlights some of the year’s top cases from the FBI’s other investigative priorities:
Martin Luther King Jr. Day attempted bombing: A Washington state man was sentenced to 32 years in prison last week for attempting to bomb a Martin Luther King Jr. Day parade last January in Spokane.
International cyber takedown: Six Estonian nationals were arrested last month for running a sophisticated Internet fraud ring that infected millions of computers worldwide with a virus and enabled the thieves to manipulate the multi-billion-dollar Internet advertising industry.
Operation Delta Blues: After a two-year investigation dubbed Operation Delta Blues, 70 individuals—including five law enforcement officers—were charged in Arkansas in October with crimes including public corruption, drug trafficking, money laundering, and firearms offenses.
Corporate fraud scheme: The former chairman and owner of Taylor, Bean & Whitaker (TBW), a privately held mortgage lending company, was sentenced in June to 30 years in prison for his role in a more than $2.9 billion fraud scheme that contributed to the failure of TBW and Colonial Bank, one of the 25 largest banks in the U.S.
James “Whitey” Bulger arrested: Top Ten fugitive James “Whitey” Bulger was arrested in June thanks to a tip from the public—just days after a new FBI media campaign was launched to help locate the Boston gangster who had been on the run for 16 years.
Cyber fraud organization disrupted: In an unprecedented move in the fight against cyber crime, the FBI disrupted an international cyber fraud operation in April by seizing the servers that had infected as many as two million computers with malicious software.
Southwest border gang arrests: Thirty-five members and associates of the Barrio Azteca gang were charged in March with various counts of racketeering, murder, drug offenses, and money laundering. Ten of the defendants were Mexican nationals and were also charged in connection with the 2010 murders in Juarez, Mexico of a U.S. Consulate employee, her husband, and the husband of a U.S. Consulate employee.
Health care fraud takedown: Twenty individuals, including three doctors, were charged in South Florida in February for their participation in a fraud scheme involving $200 million in Medicare billing for mental health services. The charges coincided with a national federal health care fraud takedown involving 111 defendants in nine cities.
Selling secrets for profit: A 66-year-old resident of Hawaii was sentenced in January to 32 years in prison for communicating classified national defense information about U.S. military planes to the People’s Republic of China, along with illegally exporting military technical data and other offenses.
Massive Mafia takedown: Nearly 130 members of the Mafia in New York City and other East Coast cities were arrested in January in the largest nationally coordinated organized crime takedown in FBI history. Charges included murder, drug trafficking, arson, loan sharking, illegal gambling, witness tampering, labor racketeering, and extortion
CONFIDENTIAL – U.S. Forces – Iraq Private Security Contractors (PSC) Registration Requirements

(U) FRAGO 0309 REGISTRATION REQUIREMENTS FOR PRIVATE SECURITY CONTRACTORS
(PSC) TO USF-I OPERATIONS ORDER 10-01.
(U) TIME ZONE USED THROUGHOUT THIS PUBLICATION: CHARLIE (C).
1. (U) SITUATION: USF-I, DEPARTMENT OF STATE AND NUMEROUS OTHER ENTITIES IN
IRAQ HAVE CONTRACTED SECURITY OPERATIONS FOR FORWARD OPERATING BASES (FOB)
AND PERSONAL SECURITY DETAILS (PSD) TO PRIVATE SECURITY CONTRACTORS (PSC).
GOVERNMENT OF IRAQ, MINISTRY OF INTERIOR (MOI) HAS IN RECENT MONTHS INDICATED
THAT CONTRACTED SECURITY COMPANIES ARE NOT OPERATING WITH THE THE PURVIEW OF
ESTABLISHED LAW. AS A RESULT, MANY PRIVATE SECURITY COMPANIES HAVE BEEN
STOPPED AT SNAP CHECK POINTS AND ENTRY CONTROL POINTS TO VERIFY THEIR
CREDINTIALS. THOSE COMPANIES OUT OF COMPLAINCE HAVE HAD PERSONNEL ARRESTED
AND WEAPONS AND VEHICLES CONFISCATED. GOVERNMENT OF IRAQ, IN COORDINATION
WITH USF-I, HAS GRANTED A 30 GRACE PERIOD FOR ALL PRIVATE SECURITY
CONTRACTORS TO COMPLY WITH IRAQ LAW STARTING 14 JAN 2010 AND ENDING 12 FEB
2010.2. (U) MISSION: EFFECTIVE UPON PUBLICATION, USF-I UNITS WITH PRIVATE
SECURITY CONTRACTORS AND ARMED CONTRACT CIVILIANS WILL ENSURE THAT ALL ARE IN
FULL COMPLIANCE WITH PUBLISHED USF-I POLICY AND GOVERNMENT OF IRAQ LAW PRIOR
TO 12 FEB 2010.3. (U) EXECUTION:
3.A. (U) CONCEPT OF THE OPERATION:
3.A.1 (U) UPON RECIEPT OF THIS FRAGO, MSC’S IDENTIFY THE NUMBER OF PRIVATE
SECURITY CONTRACTORS (PSC) AND ARMED CIVILIAN CONTRACTORS WITNIN THEIR
COMMAND AND VERIFY THEIR LEVEL OF COMPLIANCE WITH USF-I POLICY DIRECTIVES AND
GOVERNMENT OF IRAQ LAW. DIRECT ALL CONTRACT OFFICER REPRESENTATIVES(COR)TO
TRACK SUBMISSION OF REQUIRED INFORMATION TO GOI BY EACH COMPANY UNTIL COMPLETE. ADDITIONALLY SUBMIT A STATUS REPORT TO JCC-I/A AND ACOB WEEKLY INDICATING COMPLETE DOCUMENT SUBMISSION AND THE PERCENTAGE OF MOI EMPLOYEE
ID AND WEAPON CARDS RECEIVED FROM GOI. AFTER REACHING 100% CONTINUE TO SUBMIT
UPDATES WITH A MONTHLY COR REPORT TO JCC-I/A.3.B. (U) TASKS TO UNITS:
3.B.1. (U) ALL MSC’S AND SEPARATES.
3.B.1.A (U) ALL UNITS WITH CIVILIAN ARMING AUTHORIZATIONS FROM THE DEPUTY
CHIEF OF STAFF (DCOS), USF-I WILL NOMINATE AND JCC-I/A WILL APPOINT OF A
CONTRACTING OFFICER REPRESENTATIVE (COR) WHO IS PROPERLY TRAINED, QUALIFIED,
AND ASSIGNED COR DUTIES AS A PRIMARY TASK IAW DCMA COR TRAINING AND
REQUIREMENTS.3.B.1.B (U)CONTRACT OFFICER REPRESENTATIVE (COR) VERIFIES THAT EACH COMPANY
WITH A DOD CONTRACT FOR ARMED PERSONNEL WITHIN THEIR COMMAND IS IN COMPLIANCE
WITH ALL USF-I POLICY DIRECTIVES AND GOVERNMENT OF IRAQ LAW. SUBMIT A WEEKLY
STATUS REPORT TO JCC-I/A AND ACOB UNTIL ALL UNITS ARE IN COMPLIANCE AND THEN
MONTHLY THERE AFTER WITH THE MONTHLY COR REPORT TO JCC-I/A.3.B.2. (U) JCC-I/A
3.B.2.A (U) RECEIVE AND CONSOLIDATE COR WEEKLY AND MONTHLY REPORTS. PROVIDE
AN AGGREGATE STATUS REPORT OF ALL APPLICABLE CONTRACTS AND ISSUES RELATED TO
NON-COMPLAINCE TO USF-I ARMED CONTRACTOR OVERSIGHT BRANCH (ACOB).3.B.2.B (U) ENSURE ALL CONTRACTS WITH ARMED CONTRACTORS HAVE TRAINED CONTRACT
OFFICER REPRESENTAIVES (COR) APPOINTED, MONTHLY CONTRACTOR STATUS REPORTS
SUBMITTED AND STRICT MONITORING BY CONTRACTING OFFICERS (KO).
…
3.D. (U) TASKS TO STAFF:
3.D.1. (U) USF-I J34 PROTECTION
3.D.1.A (U)UPON PUBLISHING OF THIS FRAGO, ENSURE ARMED CONTRACTOR OVERSIGHT
BRANCH (ACOB) PROVIDES OVERSIGHT OF ALL DOD ARMED CONTRACTORS SUPPORTING USFI
OPERATIONS.3.D.1.B (U) REVIEW THE CONSOLIDATED ARMED CONTRACTOR COMPLIANCE RESULTS FROM
JCC-I/A, AND FORWARD TO J3 AND COMMAND GROUP WITH ANALYSIS OF ANY ISSUES.3.D.1.C (U) COORDINATE WITH GOI TO MAINTAIN A STATUS ON THE NUMBER OF DOD
PRIVATE SECURITY CONTRATORS WHO HAVE SUBMITTED THE REQUIRED DOCUMENTS.
FURTHER ASSESS STATUS OF GOI PROCESSING MOI EMPLOYEE ID AND WEAPONS CARDS.
BASES.3.E. (U) COORDINATING INSTRUCTIONS:
3.E.1. (U) ALL PRIVATE SECURITY CONTRACTORS ARE REQUIRED TO COMPLY WITH ALL
USF-I POLICY DIRECTIVES, ORDERS AND GOVERNMENT OF IRAQ LAW. FOR A LIST OF
REQUIRMENTS ON GOVERNMENT OF IRAQ REQUIRMENTS VISIT WEBSITE
WWW.IRAQIINTERIOR.COM/PSCD/PSCD_INDEX.HTM.3.E.2. (U) PER THE GUIDANCE ISSUED AT THE PRIVATE SECURITY MEETING ON 17 JAN
10 CORS WILL RECEIVE REPORTS ON THE STATUS OF PERSONNEL, WEAPONS AND VEHICLES
EVERY TUESDAY FROM PRIVATE SECURITY CONTRACTORS. SEE ENCLOSURE 1, PSC
LICENSE AND REGISTRATION STATUS REPORT FORM. AFTER THE CRISIS PERIOD CEASES,
REPORT THE INFORMATION MONTHLY TO COR WHO WILL SUBMIT CONSOLIDATE REPORT TO
JCC-I/A.3.E.3. (U) ALL REQUESTS FOR 30 DAY GRACE PERIOD WAIVERS CAN BE REQUESTED FROM
GOI AT THE OFFICE OF THE DIRECTOR REGISTRATION AND ASSESSMENT OF PRIVATE
SECURITY CONTRACTORS.
DOWNLOAD ORGINAL DOCUMENT HERE
SECRET – Photos of U.S. “Kill Team” Posing with Murdered Afghan Civilians
The following photos depict soldiers from the 5th Stryker Brigade, 2nd Infantry Division, posing next to the corpse of Gul Mudin, an unarmed Afghan civilian killed by their unit on January 15, 2010, as well as the corpses of two other unnamed Afghan civilians. The photos were published today by Der Spiegel in their German-language print release. However, they are blocked behind a paywall that restricts their dissemination. The U.S. Army responded to the release by saying that the photos depict “actions repugnant to us as human beings and contrary to the standards and values of the United States.” There are reportedly more than four thousand photos of the “kill team”.
UNCENSORED – Femen protest in Kiev
TOP-SECRET – Restricted U.S. Military Multi-Service Kill Box Employment Manual

The Kill Box MTTP reinforces kill boxes as three-dimensional areas used to facilitate the integration of joint fires while also being a permissive fire support coordination measure (FSCM) in accordance with JP 3-09, Joint Fire Support. The publication offers a detailed explanation of kill box employment and provides information to effectively organize, plan, and execute kill box procedures.
The purpose of this publication is to provide planners and operators with a single source MTTP manual that focuses on employment of kill boxes at the operational and tactical levels of warfighting to facilitate the expeditious air-to-surface lethal attack of targets which may be augmented by or integrated with surface-to-surface indirect fires. The target audience includes commanders, operations and intelligence sections of Service components, and their counterparts on the JFC’s staff.
…
1. Definition and Purpose
a. Definition: A kill box is a three-dimensional area used to facilitate the integration of joint fires. It is a permissive FSCM as described in JP 3-09, Joint Fire Support.
b. Purpose: When established, the primary purpose of a kill box is to allow lethal attack against surface targets without further coordination with the establishing commander and without terminal attack control. When used to integrate air-to-surface and surface-to-surface indirect fires, the kill box will have appropriate restrictions. The goal is to reduce the coordination required to fulfill support requirements with maximum flexibility while preventing fratricide.
Note: All aircrew conducting air interdiction within the confines of a kill box will execute their mission in accordance with rules of engagement (ROE) and special instructions (SPINS) applicable to air interdiction.
2. Establishment
a. Supported component commanders, acting on JFC authority, establish and adjust kill boxes in consultation with superior, subordinate, supporting, and affected commanders. Requirements for kill boxes and other control measures are determined using normal component targeting and planning processes and are established and approved by commanders or their designated staff (e.g., G-3, fire support coordinator [FSCOORD]). Information about the type, effective time, duration, and other attributes will be published and disseminated using existing voice and digital command and control (C2) systems. Kill boxes should be canceled when no longer needed.
b. There are two types of kill boxes: blue and purple. Chapter 3 provides further details.
(1) Blue Kill Box. A blue kill box permits air interdiction in the kill box without further coordination from the establishing headquarters (HQ).
(2) Purple Kill Box. A purple kill box permits air interdiction in the kill box without further coordination from the establishing HQ while allowing land and maritime component commanders to employ surface-to-surface indirect fires. The end state is maximum use of joint fires within the kill box to create synergistic effects with maximum potential for engaging targets.
c. Kill box characteristics:
(1) Target Area. The location and size of the kill box are determined by the expected or known location of targets in a specified area. The dimensions of a kill box are normally defined using an area reference system (i.e., Global Area Reference System [GARS]) but could follow well defined terrain features or be located by grid coordinates or by a radius from a center point. The standard dimensions using GARS would be a cell (30 minute (min) by 30 min [approximately (approx) 44 kilometer (km) by 44km] area), quadrant (15 min by 15 min [approx 22km by 22km] area), or keypad (5 min by 5 min [approx 7.5km by 7.5km] area). Reference JP 2-03, Geospatial Intelligence Support to Joint Operations, for further information concerning GARS.
(2) Airspace. The airspace block located above the kill box target area is protected and extends from the surface (or coordinating altitude if established) up to a ceiling established by the airspace control authority. The airspace for a purple kill box includes a floor and a ceiling to enable separation between aircraft delivering air-to-surface fires, trajectories of surface-to-surface indirect fires, surface-to-air fires, and other aircraft. The height of the ceiling should be established in the Airspace Control Plan (ACP), Airspace Control Order (ACO), or SPINS to permit standardized planning for other airspace uses. These parameters are developed by coordination between fire support and airspace organizations.

DOWNLOAD ORIGINAL DOCUMENT HERE
WARUM DIE STASI-LISTE HEUTE NOCH SINNVOLL IST
Liebe Leser,
warum ist diese Liste und deren Publikation heute noch sinnvoll ?
Zum Einen für die Millionen der Opfer der traditionellen STASI.
Aber auch für die Opfer der Neo-STASI ! Und zu denen gehören auch Sie !
Die alten Netzwerke existieren weiter in der Finanz, Wirtschaft, den Medien, der Justiz, der Polizei und der Politik.
Ich will Sie hier nicht mit meinem persönlichen Schicksal und den aus oben genannten Verflechtungen entstanden lebens- und existenzbedrohlichen Folgen für mein Umfeld und mich langweilen.
Das ist sekundär.
PRIMÄR IST , WIE IST SO ETWAS HEUTE NOCH MÖGLICH ?
In diesem Zusammenhang sage ich, mich wundert in Deutschland nichts mehr.
Die staatlichen Stellen haben versagt und versagen weiter und verstecken sich hinter Formalien ! In Sachen STASI ebenso wie in Sachen Wirtschaftskrise !
Das kann die Realität nicht stoppen.
Mit dem Staat versagen die deutschen Medien- unfähig und korrupt !
Aus diesen Gründen ist die Publikation der STASI-Liste und der damit verbundenen auch und besonders heute noch tätigen Genossen sinnvoller denn je.
Denn die Neo-STASI ist den Neo-Nazis an Finanzkraft, Organsiationskraft, Agenten, IM etc weit überlegen und sitzt sogar im Bundestag.
Die wenigen Mahner, die es dagegen gab, wurden systematisch ruiniert oder getötet !
Die 3 Affen – stumm, taub und blind sind das Wahrzeichen der deutschen Justiz und Exekutive !
Wohin das führt ?
Na, schauen Sie sich doch einmal um !
Herzlichst Ihr
Bernd Pulch, Magister Artium der Publizistik, Germanistik und Komparatistik
CONFIDENTIAL- Raytheon Non-Lethal Acoustic Pressure Riot Shield Patent

A man-portable non-lethal pressure shield provides both a physical as well as pressure shield. The pressure shield addresses the concerns of military, police and human rights organizations and international law as regards effectiveness, efficiency and safety and efficiency. A folded acoustic horn is incorporated into the physical shell of the shield. The horn couples acoustic pulses from a sonic pulse generator to an acoustic aperture to output a pulsed pressure beam that approximates a plane wave to produce a pressure barrier. The operator may specify a desired effect on its human target that is maintained as range-to-target changes or a desired effect at a specified perimeter range. The shields may be networked to facilitate coordinated action among multiple pressure shields as a force multiplier or to provide a more sophisticated pressure
barrier.

DOWNLOAD ORIGINAL DOCUMENT HERE
CONFIDENTIAL from the CIA – Stories of Sacrifice and Dedication Civil Air Transport, Air America, and the CIA

Booklet featuring two specific stories that exemplify
the themes of sacrifice and dedication: Lima Site 85 and a CIA mission
utilizing CAT flight support to recover an
agent inside Communist China.
DOWNLOAD HERE THE ORIGINAL E-BOOK
DER BEWEIS – WARUM DIE STASI-LISTE ECHT IST UND WIE SIE FRÜHER DURCH EINSCHÜCHTERUNG VERHINDERT WURDE
Liebe Leser,
Neo-STASI versucht die Echtheit der STASI-Listen zu diskreditieren, um ihren Einfluss zu zementieren.
Dies nachdem ihre Morddrohungen und Verleumdungen mich nicht gestoppt haben und nicht stoppen werden.
Die STASI-Liste wurde bereits früher hier publiziert:
http://stasiopfer.de/component/option,com_simpleboard/Itemid,/func,view/id,993815828/catid,4/
Vom “Stasiopfer”-Angebot führt ein Link zu einer Website in den USA (www.jya.com), die sich auch mit den Praktiken von Geheimdiensten beschäftigt. Dort findet sich die “Fipro-Liste”, das detaillierte “Finanzprojekt” der Stasi, angefertigt in den letzten Tagen der DDR, um die Rentenansprüche der rund 100 000 hauptamtlichen Mitarbeiter des MfS auch nach dem Zusammenbruch des Systems belegen zu können. Die “Fipro-Liste” ist seit langem bekannt und diente Anfang der neunziger Jahre etwa zur Identifizierung der so genannten OibE – Offiziere im besonderen Einsatz. Diese Liste „Offiziere im besonderen Einsatz“im Jahre 1991 erschien in der “taz. Die Echtheit kann beim BStU überprüft werden.
Siehe u.a. http://www.spiegel.de/spiegel/print/d-22539439.html
Auf Druck ehemaliger STASI-Leute und Ihrer Genossen wurde die Liste aus dem Verkehr gezogen.
Durch dieses pseudo-juristische Machwerk, dass niemals ausserhalb von Deutschland Bestand hat !
Mein Kommentar: Pseudo-juristische, formale Spitzfindigkeiten ersetzen Hirn und Herz- nur deshalb konnte es mit Deutschland im 20. Jahrhrundert soweit kommen und dieses Denken ist weiterhin überall vorhanden und wird sich bitter rächen – wieder einmal – denn Querdenken und/oder besser selbst denken ist nicht angesagt in diesen Formal-Strukturen. Und die Main-Stream-Presse ist völlig anzeigenhörig und duckmäuserisch. Ein Fiasko !
Die Geschichte zeigt, wohin diese groteske Wirklichkeits-Verleugnung führt. Armes Deutschland ! Wieder einmal !
Ich habe meinen Beitrag geliefert, um diese Fehlentwicklungen zu vermeiden. Viele andere auch… Und Sie ?
Herzlichst Ihr
Bernd Pulch
Magister Artium der Publizistik, Germanistik und Komaparatistik
TOP – SECRET – DoD Non-Lethal Weapons Reference Book 2011

PURPOSE: The purpose of the NLW Reference Book is to provide a single source document that contains key information about NLW descriptions, effects, characteristics, concepts of employment, and associated operational parameters and considerations to enhance NLW education and training.
EXPLANATION OF TERMS: The NLW described in this book are at various acquisition stages and of varied Service interest. Service-unique systems meet specific Service needs, often meet Joint needs, and are provided to ensure Joint visibility and consideration. Systems are grouped as follows:
- FIELDED: NLW currently in use.
- PROTOYPE: NLW which have completed development, produced in limited quantities and no fielding decision has been made.
- DEVELOPMENTAL: NLW requiring technological or other improvements prior to production approval. Typically denotes a Service-led program of record with a technical readiness level (TRL) of 5 or higher. Anticipated fielding dates are provided, but are subject to change and should not be used for acquisition or resource planning.
- CONCEPTUAL: Ideas or concepts that can support exercises and modeling &simulations. Typically denotes a pre-acquisition science and technology project with a TRL of 4 or less. Conceptual capabilities do not currently exist, but are potential technologies that could be developed to satisfy a non-lethal requirement in the near future.




DOWNLOAD ORIGINAL DOCUMENT HERE
Amercia vs iran – Iran Says American Could Face Death Penalty
STUDY – Study Finds 40% of South Asians Have Paid a Bribe in the Past Year
 A chart from the Transparency International study found that police are the largest recipient of public service bribes in South Asia.More than one in three south Asians say they were forced to bribe officials in the last year, mainly for services they were legally entitled to, an international anti-graft watchdog said on Thursday.
A chart from the Transparency International study found that police are the largest recipient of public service bribes in South Asia.More than one in three south Asians say they were forced to bribe officials in the last year, mainly for services they were legally entitled to, an international anti-graft watchdog said on Thursday.
A survey released by Berlin-based Transparency International in the Nepalese capital Kathmandu showed bribery has become so endemic that the region is second only to sub-Saharan Africa as the corruption hotspot of the world.
The watchdog surveyed 7,800 people in India, Pakistan, Bangladesh, Nepal, Sri Lanka and the Maldives, finding 40 percent had paid backhanders over the last 12 months to public servants, with police being the largest recipients.
Two thirds of Indians, Bangladeshis and Pakistanis who had dealt with the police said they had paid bribes to corrupt officers in the last 12 months.
“With bribery such a big part of life for south Asians, you can see why so many people are angry at their governments for not tackling corruption,” said Rukshana Nanayakkara, senior programme coordinator for the watchdog’s south Asia region.
“People are sick of paying bribes to get on with their daily lives, and they are sick of the sleaze and undue influence of public servants.”
Who Do Indians Bribe Most?
If the Lokpal Bill ever gets cleared by the Indian Parliament, episodes of everyday corruption, widely perceived as endemic, may finally start to decline.
At the moment, the figures are not encouraging, according to a new study by the Berlin-based anticorruption group Transparency International.
The report, “Daily Lives and Corruption,” offers fresh data on bribery in South Asia based on a survey of 7,500 people taken over the past two years. The results are alarming: they suggests that 39% of South Asians who had to deal with public services in the previous year admitted to paying a bribe.
In India, more than half of the people surveyed, or 54% of respondents, said they’ve paid a bribe. This was only worse in Bangladesh, where the figure is 66%, or two out of every three people. In Pakistan, the figure was around 50%, in Nepal 32%, in Sri Lanka 32% and in the Maldives 6%.
…
Take a look at how frequently Indians pay bribes when dealing with the following public services:
Police: 64%
Land services (buying, selling, renting and inheriting property): 63%
Registry and permit services: 62%
Tax revenue: 51%
Utilities (including water, telephone, electricity services): 47%
Judiciary: 45%
Customs: 41%
Medical services: 26%
Education: 23%
DOWNLOAD ORGINAL STUDY HERE
CONFIDENTIAL – FBI – Man Pleads Guilty in $74 Million Ponzi Scheme
ALBUQUERQUE—Douglas F. Vaughan, 64, of Albuquerque, pled guilty to wire and mail fraud charges that involved his operation of a Ponzi scheme in which he fraudulently obtained more than $74 million from approximately 600 investors who were promised extraordinary returns, announced U.S. Attorney Kenneth J. Gonzales. Carol K.O. Lee, Special Agent in Charge of the Albuquerque Division of the FBI, and Daniel S. Tanaka, Director of the New Mexico Regulation and Licensing Department’s Securities Division, joined the U.S. Attorney in making the announcement.
Vaughan entered guilty pleas to count one and four of a 30-count indictment charging him with wire fraud and mail fraud, respectively, before Chief Judge Bruce D. Black in federal court in Santa Fe, N.M., this afternoon. Under the terms of his plea agreement, Vaughan will be sentenced to a term of imprisonment between 10 and 12 years. Chief Judge Black will determine Vaughan’s specific sentence within that range, with Vaughan retaining the right to request a sentence at the lowest end of the range and the U.S. Attorney’s Office retaining the right to request a sentence at the highest end.
Vaughan also faces up to five years of supervised release following imprisonment, a fine of up to $250,000, or twice the gross gain or gross loss resulting from his offenses, whichever is greater, as well as any restitution ordered by the court. The plea agreement also requires that Vaughan immediately forfeit to the United States previously seized funds in the amount of $38,298.24 and real property located in Spring Valley, Nevada, and that Vaughan agree to the imposition of a money judgment against him in the amount of $74,745,723.93, which represents a portion of the gross proceeds that he derived from the offenses charged in the indictment.
The plea agreement also requires that Vaughan resolve two other pending cases: a civil case filed against Vaughan by the Securities and Exchange Commission (SEC) in federal court, and a bankruptcy case initiated by Vaughan in federal bankruptcy court. In the SEC case, Vaughan will consent to the entry of a judgment that permanently enjoins him from violating the federal securities laws. Vaughan also is required to consent to an order by the SEC in an administrative proceeding that bars him from associating with any broker, dealer or investment advisor, and from participating in any stock offerings. In the bankruptcy case, Vaughan is required to enter into a stipulated judgment that denies him a discharge from bankruptcy.
Under the terms of the plea agreement, the U.S. Attorney’s Office will move to dismiss the remaining 28 counts of the indictment after sentence has been imposed on Vaughan. Vaughan remains on conditions of release under pretrial supervision pending his sentencing hearing, which has yet to be scheduled.
Vaughan was charged on February 24, 2011, in an indictment alleging that, between 2005 and 2010, Vaughan operated a promissory note investment program, which he marketed as a means of generating revenue to grow his real estate business, as a Ponzi scheme. It alleged that Vaughan owed more than $74 million in unpaid principal and interest payments to approximately 600 investors when the fraudulent scheme collapsed in early 2010. Vaughan’s plea agreement includes a 16-page addendum.
According to the addendum, Vaughan was the chairman, chief executive officer, president and majority shareholder of Vaughan Company, Realtors (VCR), a business that operated primarily as a residential real estate brokerage and was at one time the largest independent residential brokerage in New Mexico. In 1993, Vaughan began an investment program in which he accepted money on behalf of VCR in exchange for interest-bearing promissory notes. The typical note had a three-year term, an interest rate ranging from 8 percent to 40 percent per year, and provided for interest to be paid in monthly installments. At the end of the note’s term, Vaughan either paid off the principal or offered the investor the opportunity to “roll over” the principal into a new note. Vaughan signed each promissory note on behalf of VCR.
Vaughan led investors to believe that their investments in the promissory note program were actually or virtually risk-free because they were guaranteed by VCR, Vaughan’s personal guarantee, and a $2.5 million deed of trust on certain real estate. Vaughan marketed his promissory note program by representing that the invested funds would be used to purchase real estate and to acquire smaller real estate companies. Instead, Vaughan used the promissory note program funds primarily for three undisclosed purposes: (i) to pay the interest and principal on promissory notes taken out by earlier investors; (ii) to pay himself, under the guise of salary, bonuses, or some other personal transfers; and (iii) to subsidize the operation of VCR, which was generating insufficient “legitimate” revenues to sustain itself.
The addendum states that, by 2005, the promissory note program was an important source of funding for VCR and, without the infusion of capital generated by new promissory note program investors, VCR was insolvent. Despite this, Vaughan continued to distribute the same marketing materials for the promissory note program, sign the same promissory notes, and make the same corporate and personal guarantees. Although Vaughan represented to investors that he would not extend more than $2,500,000.00 in promissory notes, end-of-year financial records reflect that the aggregate principal balance owed to note holders far exceeded this amount:
2004—$24,351,605.00;
2005—$32,299,363.37;
2006—$39,969,110.68;
2007—$49,984,845.80;
2008—$62,844,445.57; and
2009—$74,386,623.38.
From at least 2005 through February 2010, Vaughan used funds from new promissory note program investors to make interest payments to existing note holders and thus lulled existing investors into believing that they were being paid returns from VCR’s legitimate business revenues. However, VCR’s corporate tax returns reflected the following annual losses:
2004—$4,041,048.00;
2005—$5,595,285.00;
2006—$7,461,409.00;
2007—$9,913,893.00;
2008—$13,313,323.00; and
2009—$13,907,738.00.
In announcing Vaughan’s guilty plea, U.S. Attorney Gonzales said, “Today Doug Vaughan stood up in court and admitted that he deceived hundreds of investors into handing over tens of millions of dollars with promises of guaranteed high rates of return and the safety of their investments. Instead, people who trusted Vaughan ended up losing a lot of money, in some cases, their life savings. The United States’ plea agreement with Doug Vaughan brings about a fair and certain resolution of this case. The 10- to 12-year federal prison sentence included in the plea agreement holds Vaughan accountable for the massive Ponzi scheme in which he defrauded hundreds of investors, and is a very significant sentence in a financial fraud case. It is an appropriate resolution for the victims of Doug Vaughan’s crimes who have suffered financially and emotionally as a result of Vaughan’s scam and for the United States’ ensuing efforts to bring Vaughan to justice. Today’s guilty plea helps bring finality to what could have been a protracted criminal case. Although the victims of Vaughan’s crimes will not be compensated for their financial loss, I hope they will find a measure of solace and closure in knowing that Vaughan will be held accountable for his actions by spending substantially the rest of his productive life behind bars.”
Special Agent in Charge Lee added, “Mr. Vaughan’s plea today is the result of the hard work and dedication of the FBI special agents and U.S. Attorney’s Office prosecutors who worked together to bring to justice the individual responsible for the largest Ponzi scheme in New Mexico history. This multi-million-dollar fraud scheme wreaked havoc on the lives of hundreds of hard-working people and demonstrates the immense impact white-collar criminals can have on a community. Today’s fraud schemes are more sophisticated than ever, and we at the Albuquerque FBI, along with our law enforcement and community partners, are dedicated to the pursuit of those who choose to violate the investors’ trust and the law for personal gain.”
“Mr. Vaughan has accepted responsibility for his actions but it is cold comfort for the hundreds of New Mexicans that he victimized,” said Director Tanaka of the New Mexico Regulation and Licensing Department’s Securities Division. “We are proud of all the team members who demonstrated such commitment to investigating and prosecuting New Mexico’s largest Ponzi scheme. Financial crime is an insidious threat, therefore we will take the fight to those who would exploit the citizens of New Mexico.”
The case against Vaughan was the result of a joint federal-state investigation by the FBI, the Securities Division of the New Mexico Regulation and Licensing Department, U.S. Postal Inspection Service, U.S. Secret Service and the New Mexico Attorney General’s Office. The case is being prosecuted by Assistant U.S. Attorneys Gregory J. Fouratt and John C. Anderson.
This case was brought in coordination with the President’s Financial Fraud Enforcement Task Force, which includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general, and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch, and with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets and recover proceeds for victims of financial crimes. The task force is also making the public aware of resources available to protect against these types of fraud and how to report fraud when it occurs. To learn more about investment scams, how to take steps to protect yourself from scams or how to report investment fraud if you believe you have been victimized, the task force recommends that you visit its website, http://www.StopFraud.gov.
Secret from the FBI – Murder of ICE Special Agent Jaime Zapata and the Attempted Murder of ICE Special Agent Victor Avila
WASHINGTON—Julian Zapata Espinoza, also known as “Piolin,” has been extradited from Mexico to the United States to face charges for his alleged participation in the murder of U.S. Immigration and Customs Enforcement (ICE) Special Agent Jaime Zapata and the attempted murder of ICE Special Agent Victor Avila on Feb. 15, 2011, in Mexico.
The charges and extradition were announced today by Assistant Attorney General Lanny A. Breuer of the Justice Department’s Criminal Division; U.S. Attorney Ronald C. Machen Jr. for the District of Columbia; Kevin Perkins, Assistant Director for the FBI Criminal Investigative Division; and ICE Director John Morton.
On April 19, 2011, a federal grand jury in the District of Columbia returned a four-count indictment against Zapata Espinoza, charging him with one count of murder of an officer or employee of the United States, for the murder of ICE Special Agent Zapata; one count of attempted murder of an officer or employee of the United States and one count of attempted murder of an internationally protected person, both for the attempted murder of ICE Special Agent Avila; and one count of using, carrying, brandishing and discharging a firearm during and in relation to a crime of violence causing death.
“Julian Zapata Espinoza (“Piolin”) allegedly participated in the murder of ICE Special Agent Jaime Zapata and the attempted murder of ICE Special Agent Victor Avila,” said Assistant Attorney General Breuer. “The indictment unsealed today, and the successful extradition of Piolin to the United States, reflect the Justice Department’s vigorous and determined efforts to seek justice for Agents Zapata and Avila. We will continue to work closely with our law enforcement partners in Mexico to hold violent criminals accountable.”
“This prosecution exemplifies our unwavering effort to prosecute those who committed this heinous offense against U.S. law enforcement agents,” said U.S. Attorney Machen. “We will not rest until those responsible for the murder of Agent Zapata and the wounding of Agent Avila are brought to justice.”
“The extradition of Julian Zapata Espinoza to face charges in the U.S. is a significant development in the ongoing investigation into the murder of Special Agent Jaime Zapata and attack on Special Agent Victor Avila,” said Kevin Perkins, Assistant Director for the FBI Criminal Investigative Division. “This extradition would not have been possible without the dedicated efforts of all involved in this case. The FBI, DHS and the Department of Justice will continue its pursuit of justice for the Zapata family.”
“The extradition and charges filed against Zapata Espinoza is an important step in bringing Jaime and Victor’s alleged shooters to justice,” said ICE Director Morton. “All of us at ICE are encouraged by today’s action and appreciate the unwavering work and support of all our law enforcement partners in this case. Our hearts and prayers continue to go out to Jaime’s family and his close colleagues within the ICE community. ICE will continue to see that Jaime and Victor’s work is done by continuing our efforts with all involved in working on this case.”
The indictment was unsealed today, when Zapata Espinoza made his initial appearance before U.S. District Chief Judge Royce Lamberth of the District of Columbia. Zapata Espinoza was ordered detained without bail. His next appearance in court is scheduled for Jan. 25, 2012.
The case is being investigated by the FBI, with substantial assistance from ICE, the Bureau of Alcohol, Tobacco, Firearms and Explosives, the Drug Enforcement Administration, the U.S. Customs and Border Patrol, the Diplomatic Security Service and the U.S. Marshals Service. The investigation was also coordinated with the assistance of the Government of Mexico.
The case is being prosecuted by the Organized Crime and Gang Section and the Narcotic and Dangerous Drugs Section of the Justice Department’s Criminal Division and the U.S. Attorney’s Office for the District of Columbia. The Office of International Affairs of the Justice Department’s Criminal Division provided substantial assistance.
An indictment is a formal charging document and defendants are presumed innocent until proven guilty.
TOP-SECRET from the CIA – Penetrating the Iron Curtain

In the mid-1950s the US faced the first real challenge since World War II to its strategic superiority over any nation on earth. The attempt to collect intelligence on the Soviets began with an initial period of poor collection capabilities and consequent limited analysis. With few well-placed human sources inside the Soviet Union, it was only with the CIA’s development of, what can only be called, timely technological wizardry—the U-2 aircraft and Corona Satellite reconnaissance program—that breakthroughs occurred in gaining valuable, game-changing intelligence. Coupled with the innovative use of aerial and satellite photography and other technical collection programs, the efforts began to produce solid, national intelligence.
DOWNLOAD ORIGINAL PDF HERE
CONFIDENTIAL – U.S. House of Representatives Report: Warlords Provide Security for U.S. Supply Chain in Afghanistan

Specifically, the Subcommittee on National Security and Foreign Affairs Majority staff makes the following findings:
1. Security for the U.S. Supply Chain Is Principally Provided by Warlords. The principal private security subcontractors on the HNT contract are warlords, strongmen, commanders, and militia leaders who compete with the Afghan central government for power and authority. Providing “protection” services for the U.S. supply chain empowers these warlords with money, legitimacy, and a raison d’etre for their private armies. Although many of these warlords nominally operate under private security companies licensed by the Afghan Ministry of Interior, they thrive in a vacuum of government authority and their interests are in fundamental conflict with U.S. aims to build a strong Afghan government.
2. The Highway Warlords Run a Protection Racket. The HNT contractors and their trucking subcontractors in Afghanistan pay tens of millions of dollars annually to local warlords across Afghanistan in exchange for “protection” for HNT supply convoys to support U.S. troops. Although the warlords do provide guards and coordinate security, the contractors have little choice but to use them in what amounts to a vast protection racket. The consequences are clear: trucking companies that pay the highway warlords for security are provided protection; trucking companies that do not pay believe they are more likely to find themselves under attack. As a result, almost everyone pays. In interviews and documents, the HNT contractors frequently referred to such payments as “extortion,” “bribes,” “special security,” and/or “protection payments.”
3. Protection Payments for Safe Passage Are a Significant Potential Source of Funding for the Taliban. Within the HNT contractor community, many believe that the highway warlords who provide security in turn make protection payments to insurgents to coordinate safe passage. This belief is evidenced in numerous documents, incident reports, and e-mails that refer to attempts at Taliban extortion along the road. The Subcommittee staff has not uncovered any direct evidence of such payments and a number of witnesses, including Ahmed Wali Karzai, all adamantly deny that any convoy security commanders pay insurgents. According to experts and public reporting, however, the Taliban regularly extort rents from a variety of licit and illicit industries, and it is plausible that the Taliban would try to extort protection payments from the coalition supply chain that runs through territory in which they freely operate.
4. Unaccountable Supply Chain Security Contractors Fuel Corruption. HNT contractors and their private security providers report widespread corruption by Afghan officials and frequent government extortion along the road. The largest private security provider for HNT trucks complained that it had to pay $1,000 to $10,000 in monthly bribes to nearly every Afghan governor, police chief, and local military unit whose territory the company passed. HNT contractors themselves reported similar corruption at a smaller scale, including significant numbers of Afghan National Police checkpoints. U.S. military officials confirmed that they were aware of these problems.
5. Unaccountable Supply Chain Security Contractors Undermine U.S. Counterinsurgency Strategy. While outsourcing principal responsibility for the supply chain in Afghanistan to local truckers and unknown security commanders has allowed the Department of Defense to devote a greater percentage of its force structure to priority operations, these logistics arrangements have significant unintended consequences for the overall counterinsurgency strategy. By fueling government corruption and funding parallel power structures, these logistics arrangements undercut efforts to establish popular confidence in a credible and sustainable Afghan government.
…
The following companies are prime contractors under the HNT contract:
NCL Holdings (NCL) – NCL was founded in May 2005 by Hamed Wardak, the son of the Afghan Defense Minister, Abdul Rahim Wardak. The company is based in Northern Virginia. Prior to receiving the HNT contract in 2009, NCL performed security operations in Afghanistan for Department of Defense contractors. NCL subcontracts out all of its trucking operations under HNT, and had no direct experience with managing trucking before this contract.
The Sandi Group – The Sandi Group is based in Washington, D.C. and has worked in private sector development in both Iraq and Afghanistan. To perform HNT missions, the Sandi Group has subcontracted out all trucking to local Afghan subcontractors.
Mesopotamia Group and EMA, Joint Venture – Mesopotamia Group, a Delaware-based company and EMA, an Afghan company, received an HNT contract as a joint venture after having worked on the BPA contract in a contractor-subcontractor relationship, with EMA as the local subcontractor. EMA owns many of its own trucks and also brokers with owner-operators from local tribes. Mesopotamia Group provides management and capital to the joint venture.
HEB International Logistics – HEB is an international logistics and transportation company based in Dubai. HEB owns some of its own trucks but principally relies on local Afghan subcontractors. HEB performed trucking operations under the BPA prior to receiving the HNT contract.
Anham, LLC – Anham is a partnership that was formed in 2004 by a Virginia-based investment group (HII-Finance), a Saudi conglomerate, and a Jordanian investment group. It is based in Dubai. Anham owns its own trucks and does not subcontract to local companies, but it performs far fewer missions than the leading HNT contractors.
The Four Horsemen International (Four Horsemen) and Three Bullets Incorporated (Three Bullets), Joint Venture – Four Horsemen is a New Jersey-based security company with principal operations in Afghanistan managed by Western military expatriates; Three Bullets is an Afghan-based transportation company that owns some of its own trucks and brokers with local owner-operators. Four Horsemen provides the security force for the joint venture. Four Horsemen had previously performed security operations under the BPA with other companies, and Three Bullets performed trucking operations on the BPA.
Afghan American Army Services (AAA) – AAA is Afghan-owned and was added to the HNT contract in November 2009 following a bid protest before the U.S. Government Accountability Office. AAA had previously worked under the BPA and had performed trucking operations since July 2006. Under HNT, AAA subcontracts out trucking operations to several local companies.
Guzar Mir Bacha Kot Transportation (GMT) – GMT is an Afghan-owned company that was added to the HNT contract in November 2009 in order to increase trucking capacity. GMT was a prime contractor on the BPA and the company has provided trucking services in Afghanistan for more than 15 years. GMT provides its own trucks and, before receiving the HNT contract, worked as a subcontractor for other HNT prime contractors.
DOWNLOAD THE ORIGINAL DOCUMENT HERE
SECRET – Afghan National Army Base and Incentive Pay Chart


TOP-SECRET -U.S. Army Afghanistan Route Clearance Handbook

Route clearance (RC) operations for Operation Enduring Freedom in Afghanistan are much different from RC operations for Operation Iraqi Freedom in terms of the terrain, seasonal weather, level of infrastructure, volume of insurgent threats, sources of improvised explosive device (IED) components, and motivation for IED emplacement. The purpose of this supplement is to focus on RC in Afghanistan.
Overview of Afghanistan
Afghanistan is composed of 34 provinces and is operationally divided into five regional commands: Regional Command Capital, Regional Command East, Regional Command North, Regional Command South, and Regional Command West. Regional Command Capital is completely surrounded by Regional Command East but is independent of the Regional Command East command. Regional Command Capital is composed of Kabul Province alone. The provinces in Regional Command East are Paktika, Paktya, Khwost (P2K); Ghazni, Wardak, Logar; Nangarhar, Nuristan, Konar, Laghman (N2KL); Bamyan; Parwan; Kapisa; and Panjshir. The provinces in Regional Command North are Faryab, Jawzjan, Sari Pul, Balkh, Samangan, Kunduz, Baghlan, Takhar, and Badakhshan. The provinces in Regional Command South are Nimroz, Helmand, Day Kundi, Oruzgan, and Zabul. The provinces in Regional Command West are Badghis, Herat, Ghowr, and Farah.
U.S. forces are focused primarily on Regional Command East. Regional Command East is further divided into five areas of operations (AOs). The five AOs for Regional Command East are Currahee in the southeast, Duke in the northeast, Warrior in the north-northwest, Ghazni in the west, and Spartan in the center. The provinces in AO Currahee are Paktika, Paktya, and Khwost (P2K). The provinces in AO Duke are Nangarhar, Nuristan, Konar, and Laghman (N2KL). The provinces in AO Warrior are Bamyan, Parwan, Kapisa, and Panjshir. AO Ghazni is composed of the Ghazni Province alone. The provinces in AO Spartan are Wardak and Logar.
Some AOs are further subdivided into minor AOs; however, the minor AOs do not necessarily correspond to the provincial boundaries. AO Currahee is composed of Team (TM) Paktya, TM Khowst, TM Eagle, and TM White Eagle. AO Duke is composed of AO Raptor, AO Pacesetter, AO King, AO Rock, and AO Saber. AO Warrior, AO Ghazni, and AO Spartan are not broken down into minor AOs.
In AO Currahee, the minor AO boundaries generally align with the provinces; however, there are a few exceptions. TM Paktya contains only Paktya Province. TM Khowst contains only Khowst Province. TM Eagle contains the east half of Paktika Province, while TM White Eagle contains the west half of Paktika Province.
In AO Duke, the minor AO boundaries generally do not align with the provinces; however, there are a few exceptions. AO Raptor contains Nangarhar Province. AO Pacesetter contains Laghman Province. AO King contains the westernmost third of Nuristan Province; AO Rock contains the middle third of Nuristan Province and the westernmost three-quarters of Konar Province. AO Saber contains the easternmost third of Nuristan Province and the easternmost quarter of Konar Province.
Terrain and Weather
In Afghanistan, the terrain varies drastically from one area to the next. The country is divided into three major geographic zones: the northern steppe, the southern desert plateau, and the spine of the Hindu Kush mountain range. The northern steppe runs across the northern border from Badghis in Regional Command West to Takhar in Regional Command North. The southern desert plateau runs across the western and southern border from Herat in Regional Command West to Kandahar in Regional Command South. The Hindu Kush mountain range and its offshoots run generally from northeast to southwest and cover the rest of the country.
The provinces that contain the northern steppe include Badghis, the northern half of Faryab, Jawzjan, the northern half of Sari Pul, the northern two-thirds of Balkh, Konduz, and the northeast quarter of Takhar. The provinces that contain the southern desert plateau include the western half of Herat, the western two-thirds of Farah, Nimroz, the southern three-quarters of Helmand, and the southwestern three-quarters of Kandahar. The provinces that contain the Hindu Kush mountain range and its offshoots include Badakhshan, Takhar, Baghlan, Samangan, Balkh, Sari Pul, Faryab, Herat, Ghowr, Farah, Helmand, Day Kundi, Oruzgan, Kandahar, Zabul, Paktika, Paktya, Khowst, Ghazni, Wardak, Logar, Bamyan, Parwan, Kapisa, Panjshir, Nuristan, Laghman, Konar, Nangarhar, and Kabul.
Some areas are extremely mountainous, and the so-called roads are nothing more than narrow goat trails, which offer insurgent forces excellent cover and concealment from approaching maneuver forces. There are many ideal spots for ambush near to the roads, and several IED events in these areas have coordinated small arms fire incorporated into the attacks. In other areas of the country, the terrain is wide open desert and without many hiding spots near the roads. The methods of attack in these areas are drastically different.
Fighting Season
The weather in Afghanistan plays a major role in the way units conduct operations. The seasonal nature of the mountainous regions lends itself to a “survival season” and a “fighting season.” The survival season is primarily the winter months. Harsh winters offer extremely cold temperatures and large snow accumulations. In many areas, the snowfall makes the roads completely impassible and shuts off ground maneuvers completely in some parts of the country. The fighting season begins with the spring thaw and allows for movement in areas that were previously impassible due to the harsh winter conditions. This fighting season usually ramps up from the early spring to the beginning of summer. The summer weather can also be harsh. Hot, dusty, dry conditions will often limit the movement of forces not properly protected from the heat. In the fall, when the extreme heat has passed, IED activity sparks up again; however, it is usually not as intense as the spring fighting. Most people are focusing on preparing for the coming winter months and not on fighting.
Infrastructure
Infrastructure or, more to the point, a lack of infrastructure is a major issue in Afghanistan. The vast majority of the roads in Afghanistan are unimproved and not well defined. Often the location of the road changes from season to season and from year to year. Flooding, washouts, rockslides, lack of infrastructure, discovery of a better/safer/faster/more direct path, and many other factors all contribute to the ever-changing network of trails and paths used for vehicular traffic. In some areas, drivers use dry riverbeds as primary roads during the dry season. These wide open “roads” can quickly become raging rivers during the spring thaw. In some areas, the roads are paved; however, many years of damage from tracked vehicles and explosions from previous wars have greatly degraded their serviceability. These paved roads are often limited to the main ring road and a few off shoots from that road.
The sources of IED components in Afghanistan are drastically different from those in Iraq. In Afghanistan, there are fewer components for making IEDs. A cache in Afghanistan usually does not meet the minimum requirements of a cache in Iraq. The enemy uses homemade explosives in IEDs in Afghanistan, which bring additional complications to the RC mission. Additionally, there are many existing minefields that are mistaken for IEDs. RC units should deal with these areas as minefields rather than IEDs. Sometimes the enemy transplants mines from the minefields to a roadway. In these situations, it is difficult to determine if the area is a part of a larger minefield and should be dealt with as such, or if the area is more like an IED and should be dealt with accordingly.
The motivations for using IEDs in Iraq and Afghanistan are similar in some areas and different in others. In the lowlands, which are primarily in the south and west, the enemy uses IEDs as an initiator for an attack and then again when targeting first responders or reactionary forces. In the highlands, which are primarily in the north and east, the enemy uses IEDs to shape an attack and limit mobility.
Culture, People, and Religion
Culture
Afghan culture is a rich mix influenced by different ethnicities and languages. It is extremely difficult to generalize about an entire population; however, Afghans are typically friendly and hospitable. Their lives have been rife with conflict, and they can be stern. The Afghan’s belief that Allah controls all matters greatly influences his perceptions. This belief helps Afghans tolerate extreme physical hardship.
Approximately 44 percent of Afghans are Pashtun, about half of whom are of the Durrani tribal group and the other half of the Ghilzai group. Tajiks are the second largest ethnic group with 25 percent of the population, followed by Hazaras at 10 percent and Uzbeks at 8 percent. Other smaller groups, including Turkmen, Qizilbash, Kazakhs, Aimaq, Wakhis, Nuristanis, Baluchis, Kyrgyz, Sikhs, Hindus, and Jews, constitute the remaining 13 percent of the total population.
People
The Afghans’ primary loyalty is to their families, kin groups, clans, or tribes; they express their identities through these groups. Their moral attitudes are often strict and inflexible, and they stress honor and individual responsibility to fulfill expected roles. Personal disputes are not resolved easily because of the need to protect one’s honor. Personal behavior affects family honor, so Afghans consider it essential to live according to these rigid rules. Piety and stoicism are admired traits.
Afghan society is mostly rural. The rural populations are mostly concentrated along the rivers. Villages in Afghanistan encircle larger towns that act as commercial, communication, and administrative centers. The most heavily populated and urban part of the country is between the cities of Kabul and Charikar. Other population concentrations can be found east of Kabul near Jalalabad, in the Heart oasis and the valley of the Harirud River in the northwest, and in the Valley of Kunduz River in the northeast. Most urban settlements have grown along the ring road that runs from Kabul southwest to Kandahar, then northwest to Herat, northeast to Mazar-e Sharif, and southeast to Kabul. Cities have formed where major routes intersect.
Thirty-two languages and dialects are spoken in Afghanistan. Dari (a form of Persian) is spoken widely and has several dialects. It is similar to the Farsi spoken in Iran and Tajik spoken in Tajikistan. Pashtu has two major variants and many dialects.
Religion
Afghanistan is an Islamic society; 84 percent of the population follows the Sunni tradition, 15 percent of the population follows the Shi’a tradition, and 1 percent of the population follows other traditions. However, Islam has not been a unifying force that has overcome ethnic differences. Local religious leaders are often not well educated. The level of religious observation varies, but most Afghans profess a strong adherence to the Islamic faith.
DWONLOAD ORIGINAL DOCUMENT HERE
TOP-SECRET from the CIA – Berlin – A city torn apart

From the end of World War II in 1945, the question of Berlin’s status 90 miles within the Deutsche Demokratische Republik (East Germany) and the Soviet Union’s zone of occupation, along with the status of Germany among the community of nations, remained a source of tension between the East and West. Premier Khrushchev continued to push President Eisenhower and the other Western leaders for resolution of the issue.
DOWNLOAD ORIGINAL DOCUMENT HERE
CONFRIDENTIAL – ATF American/Canadian Northern Border Extremists like Ku Klux Klan

According to information obtained via the Southern Poverty Law Center (SPLC), the number of hate groups operating with the United States has risen and continues to rise. In 2006, law enforcement intelligence and SPLC information counted 844 organizations in 2007; this number has risen to 888, an increase of approximately 4.7 percent. This number may seem small; however, during an 8-year time period, this has translated into a 48-percent jump in the number
of groups since 2000, when there were 602 hate groups operating in the United States, according to research by the intelligence project of the SPLC. Much of the expansion has been driven by hate groups’ exploitation of the issue of illegal immigration, which most Americans see as a pressing concern. This overview addresses the issue of American and Canadian extremism in Canada and in those States that fall along the American-Canadian border.
Federal law enforcement officials believe White supremacists and other hate groups consist of some of the most violent and dangerous domestic organizations because of their willingness to act on their hatred. While traditional targets of hate groups have been African Americans and Jews, White supremacists have enhanced their focus in recent years to include homosexuals, prochoice advocates, Hispanics, and Asians.
America, unfortunately, has no shortage of extremists. Some come from the far right, in the
form of racist and anti-Semitic hate groups or anti-government extremists. Others come from the
far left, which include environmental and animal rights extremists.
At the same time as the United States enacted its Hate Crimes Statistics Act of 1990, which
lobbied to recognize the impact of crimes motivated by hatred, hate crimes commenced in
Canada. Although the term hate crime is commonly used today, little consensus exists as to its
exact meaning. Although most definitions list a number of identifiable traits based on race,
religion, and ethnicity, differences remain.
To date, more than 40 States have enacted hate crime legislation. Of these, 21 States and the
District of Columbia also include sexual orientation as a protected status.
In Canada, some of these definitional issues are currently being addressed. To date, Canada has
no centralized system for collecting national police-reported statistics relating to hate-motivated
crimes. Offenders of hate crimes have been associated with organizations such as Neo Nazis,
Skinheads, and the Ku Klux Klan. At the root of extremism are radical ideologies and religious
beliefs, held in anger and frustration, which can lead to violent acts ranging from hate crimes to
terrorism.
Hate and extremist activity are also flourishing through new electronic avenues such as the
Internet. Monitoring this activity at both the national and international levels remains difficult at
best in both Canada and the United States.
…
Rightwing Extremists
Rightwing extremists reject Federal Authority and are in favor of State or local government.
They are concerned with preserving the Constitution, including their right to liberty and privacy.
These extremists are nationalistic and may embrace racist views or multiple belief systems. This
group consists of the following:
• Militias – Origins mid to late 1993
The militia movement is a relatively new rightwing extremist movement consisting of armed
paramilitary groups, both formal and informal, with an anti-government, conspiracy-oriented
ideology. Militia groups began to form shortly after the deadly standoff at Waco, Texas, in
1993. By the spring of 1995, they had spread to almost every State. Many members of militia
groups have since been arrested, usually on weapons, explosives, and conspiracy charges.
Although the militia movement has declined in strength from its peak in early 1996, it remains
an active movement, especially in the Midwest, and continues to cause a number of problems for
law enforcement.
• White Supremacists
Groups or individuals that believe Caucasians/Aryans are intellectually and morally superior to
other races and use their racist ideology to commit crimes, acts of violence, and terrorism are
called White supremacists. Most advocate racial separation and segregation. White
supremacists are broken down generally into six types: Neo-Nazi, Ku Klux Klan, Christian
Identity, Skinhead, Odinist, or Racist Prison Gangs. The largest two are briefly described below.
…
To effectively combat the growing violence of the White racist, law enforcement agencies must
continue to cooperate and communicate. Supremacists are transient in nature, and it is not
uncommon for members to travel from city to city committing crimes. Skinheads in particular
have a belief that a crime committed in a locality other than their own is likely to go unnoticed
by law enforcement. Typically their criminal activity is often centered around a major event,
such as a march, rally, or skinhead concert.
Although there was deterioration in the formal structure of these groups in the last few years,
evidence suggests hate group organization is definitely on the rise in Canada. The Canadian
White supremacist community has been scattered and without formal leadership for the last few
years, but Internet recruitment has allowed individuals to align themselves with pre-established
hate groups in urban areas in both Canada and the United States.
It seems as though small arms and improvised explosive devices (IEDs) are the weapons of
choice for supremacists/extremists because they are widely available and easy to construct and
use. Some groups have shown an increased interest since September 11, 2001, in using
chemical, biological, and radiological weapons, raising law enforcement concerns that these
groups may pursue different methods of attack in the future.
The animal and environmental extremists believe companies are responsible for the destruction
of animal habitats and natural resources. In the last couple of years arson has become the tool
most widely used by animal rights and eco-terrorist groups. Law enforcement can become
proactive by identifying and locating logical targets (i.e. construction sites causing
environmental controversies or facilities that use animals for testing) and consider initiating
liaisons with these targets. Law enforcement has made strides prosecuting cells, but has been
unable to end the arsons directed toward housing developments in the United States and Canada.
The abortion issue will continue to be a political topic in the years to come. ATF will continue
to monitor violent (i.e. arsons/bombing) incidents directed toward reproductive healthcare
centers.
In conclusion, there appears to be a significant number of domestic extremist groups operating in
Pennsylvania, New York, Ohio, Michigan, and Washington. The main ideology of these groups
is the supremacy of the White race with disrespect toward the U.S. Government. To date, there
are estimated to be more than 600 members of the neo-Nazi skinhead movement in Canada.
While their numbers declined in the late 1980s, the trend was reversed in the 1990s. With
immigration an issue of the upcoming U.S. Presidential election, law enforcement could expect
to see even more of an increase in hate crimes. It should also be noted that mergers of Canadian
and U.S. groups may possibly take place between racist groups operating along the border as the
United States will have its first African-American President taking office in January 2009.

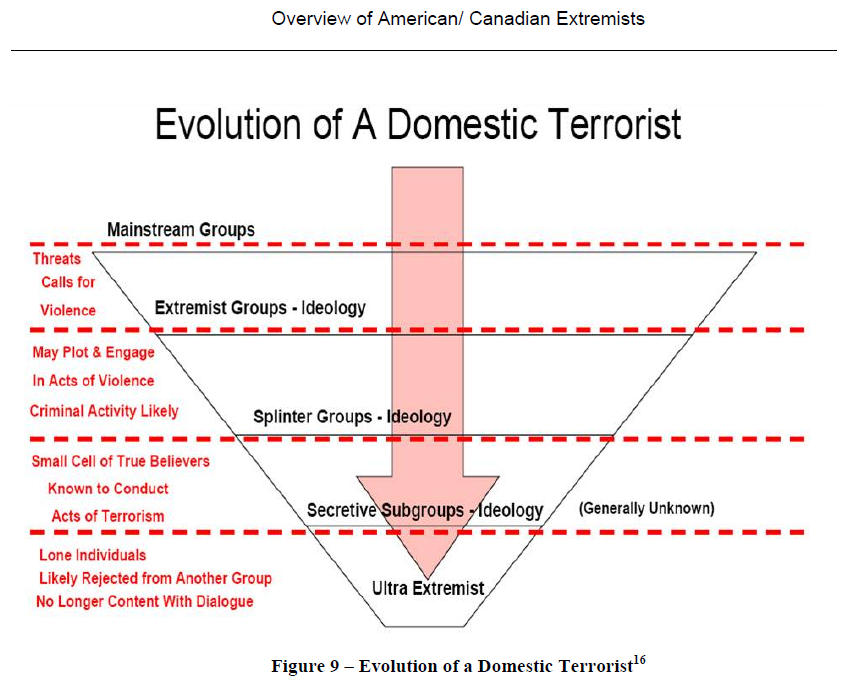
DOWNLOAD THE ORIGINAL DOCUMENT HERE
ANONYMOUS and Stratfor’s “private client list
Could this be Stratfor’s “private client list”? And what kind of info do you think we have on them?
anonymous targets – one in a series of targets they say will last all week – a private security firm called STRATFOR. from news site RT:
Anonymous hacks and discredits STRATFOR intelligence company
The global intelligence company Strategic Forecasting, Inc has been hacked by Anonymous group. Anonymous claim to have dumped a heap of information from the server, including internal correspondence and credit card data. AnonymouSabu tweeted “Over 90,000 Credit cards from LEA, journalists, intelligence community and whitehats leaked and used for over a million dollars in donations.” Hackers also defaced Stratfor’s website, forcing the administrators to shut down the web server for some 40 minutes. Stratfor has released a statement to its clients about the security breach, saying that they are “diligently investigating the extent to which the subscriber information may have been obtained.” A number of large corporations and government agencies are among the clients of Strategic Forecasting, which provides strategic intelligence on global business, economic, security and geopolitical affairs. Anonymous have not released the complete list of Stratfor’s clients yet, but mentioned that the United States Air Force, Goldman Sachs investment bank, and financial broker MF Global were on the list.
#antisec #lulzxmas
Company: Homeland Security Bureau of Miami Dade Police Dept
Company: 17 Concepts
Company: 1707 Corp
Company: 2 Years / $349 – Academic acct
Company: 2-377 PFAR
Company: 21st Century Technologies
Company: 23 Shillings LTD.
Company: 230th ALT, TNARNG
Company: 3 month $59 academic memberships
Company: 3 months and The Next Decade / $16
Company: 303-279-0773
Company: 308-792-4109
Company: 312-719-1711 cell
Company: 3157313 nova scotia ltd.
Company: 334-857-3857
Company: 360∞ MEDIZIN
Company: 3M
Company: 403-263-7052
Company: 4M Firearms Import Service,LLC
Company: 5096829056
Company: 51486655
Company: 646-295-4481
Company: 7Q Financial Services Ltd
Company: 805-402-9964 Cell
Company: 817-837-1901
Company: 937-255-3529
Company: 954-562-8425
Company: 972-729-7879
Company: A G Edwards
Company: A Montag & Assoc
Company: A Place for Us Foundation
Company: A. G. Edwards
Company: A. J. Kirshen, Medicine Professional Corporation
Company: a.g. edwards.com
Company: A.R. Consultants
Company: A.T.&T.
Company: A/S/M Communications
Company: A&E Computer Services
Company: AAA Motors, Inc.
Company: AarhusKarlshamn Mexico SA de CV
Company: Abacus, Inc.
Company: Abaxon
Company: ABB
Company: ABB
Company: abeedle.com, incorporated
Company: Abilene Christian University
Company: ABSA Capital
Company: Abt Inc
Company: Abu Dhabi University
Company: Academic / 003607603@coyote.csusb.edu
Company: Academic $19.95 for 1 month
Company: Academic 2 years for $349
Company: Academic Computing Services
Company: Acadia Asset Management
Company: Accendor Research, Inc.
Company: Accendx Management, LLC
Company: Accent Capital
Company: Accenture
Company: Access Insurance Holdings, Inc.
Company: ACCTS
Company: Acero Group International, Inc.
Company: ACMR
Company: ACN
Company: ACS Industries.
Company: Actagon AB
Company: Acton Framers
Company: Acuitas (London) Ltd
Company: Adair Capital, LLC
Company: Adelante Consulting
Company: Adeline Companies
Company: Adelphi University
Company: Adexta, Inc.
Company: ADK Wealth Management
Company: Admins
Company: Admiral Security Services, Inc.
Company: Admn Staff College of India
Company: Advisor
Company: AECOM
Company: AEG Partners LLC
Company: Aegis Defence Services
Company: AEGON Asset Management
Company: Aegon USA
Company: Aero Spares Int’l
Company: Aeroquest Airborne
Company: Aerospace Defence Italy s.r.l.
Company: AES Corporation
Company: AES Corporation
Company: Aetos Capital
Company: AF
Company: AF Group
Company: Affiliated Capital Resources
Company: AFIO
Company: AFL Private Limited
Company: AfricaSearcher Inc.
Company: AFROTC
Company: afs
Company: AG Edwards
Company: AG Edwards
Company: Agate Holdings, Inc.
Company: Aggreko, LLC
Company: AHPC Inc
Company: AIG – American General
Company: AIG American General
Company: AIG Financial Products
Company: AIM Group
Company: Air & Marine Travel
Company: Air Canada Pilots Association
Company: Air Force Office of Scientific Research
Company: Air National Guard
Company: Air New Zealand
Company: Air Products & Chemicals, Inc.
Company: Air Serv International
Company: Air Serv International
Company: AirBattleForce.com
Company: AJC
Company: Al Amin
Company: Al Jazeera English
Company: Al Morrell Development
Company: Al Thuraya Consultancy Inc
Company: ALANSA International, LLC
Company: Alaric Advisres
Company: Alcatel-Lucent
Company: ALCOA
Company: ALCOA
Company: Aleagent, Inc.
Company: alecorp inc
Company: Alexander Capital
Company: ALEXIS International Ltd.
Company: Alfa
Company: Alinpa AG
Company: All-Chemie Ltd.
Company: Allbritton Capital Management Assoc.
Company: Alleghany Consulting
Company: Alleghany Corp
Company: Allegheny Medical Systems
Company: Allen & Company LLC
Company: Allergy and Asthma Assoc. PA
Company: Alliant Techsystems Inc.
Company: Alliant Techsystems, Inc.
Company: allied beverage group
Company: Allied Machined Products Corp
Company: Allocation Sciences Corp
Company: ALM First
Company: ALPA
Company: Alpha Baking Company
Company: Alpha Omega Global
Company: ALPHA PLATFORM SDN BHD
Company: Alpha Scout Capital Management
Company: Alphamax Advisors LLC
Company: Alpi Viajes
Company: ALSO Holding AG
Company: Altair Advisers LLC
Company: Altova, Inc.
Company: Amansa Capital Pte Ltd
Company: Amaranth
Company: AMB Minerals & Energy Inc
Company: Ambac Assurance Corporation
Company: AMCHAMDR
Company: Amco International
Company: AMD
Company: Amdahl
Company: American Airlines
Company: American Express
Company: American Express
Company: American Funds
Company: American Investment Services, Inc.
Company: American Military University
Company: AMERICAN NATIONAL BANK
Company: American Safe Room, Inc.
Company: American Shipping & Logistics Group
Company: American Textile, LLC.
Company: American University’s Brussels Center
Company: Ameriprise Financial
Company: AMETEK, Inc.
Company: AMI International
Company: Aminoff & Co.
Company: AMLA Consulting
Company: AMP Capital Brookfield
Company: AMR Consulting, Inc.
Company: AMTEC Corporation
Company: AMUNDI SINGAPORE LIMITED
Company: Anadarko Petroleum
Company: Anadarko Petroleum
Company: Anadarko Petroleum
Company: Anadarko Petroleum
Company: Anadarko Petroleum Company
Company: Anadarko Petroleum Corporation
Company: Analytica Asia
Company: Andean Development Bank
Company: Andean Development Bank
Company: Andean Development Bank
Company: Andean Development Bank
Company: Anderson & Strudwick, Inc.
Company: Anderson Valuation
Company: Andrews Capital Mgmt
Company: Andrews International Inc.
Company: Anesthesia Care Ltd.
Company: Angel Alert Network Inc.
Company: Angus Taverner Ltd
Company: Annuitas
Company: ANSER
Company: Anson Consulting Inc
Company: ansr audio
Company: Antarctica Asset Management LLP
Company: Antares Defense LLC
Company: ANTHONY ISLAND PROTECTIVE SERVICES Ltd
Company: Antipodean Capital Management P/L
Company: ANZ Bank
Company: ANZ Bank
Company: Aon
Company: Aon, Inc.
Company: AOPA
Company: Apache Corporation
Company: Apache Corporation
Company: Apollo Capital Management
Company: Apollo Company
Company: Apollos Software, Inc.
Company: Apple
Company: Applegate Investment Mgmt
Company: Appletiser
Company: Applied Financial Planning Inc
Company: APS Consultores Gerenciales, S.A.
Company: AQMI Strategy Corporation
Company: Aquamarine Fund
Company: ARA Strategic Capital
Company: Arab World Ministries
Company: Aramco
Company: ARCADIS
Company: ArcelorMittal
Company: Arch Insurance Co.
Company: ARCH Venture Partners
Company: Archangel Emergency Management Group
Company: Archer Financial Group, LLC
Company: Archstone Consulting
Company: arcon partners
Company: Argyll Investment Services Limited
Company: ariely commodities, inc
Company: ARINC
Company: Armaris Group
Company: Army
Company: Army
Company: Arque Advisors, LLC
Company: ArvinMeritor, Inc.
Company: ARX Investment Management
Company: ARX Investment Management
Company: AsAsalam Party
Company: ASCG Incorporated
Company: ASFT
Company: Ashland Inc.
Company: Ashley Investment
Company: ASIA CALLING
Company: Asia Mezzanine
Company: ASIANZ Holdings Ltd
Company: Asociace pro mezinarodni otazky
Company: ASPI
Company: Assembly of Western European Union
Company: Asset Management Advisors
Company: AssetMark
Company: Associated Pathology Laboratories, Inc.
Company: ASTEK Ltd.
Company: Astrakhan Consulting
Company: ASV Shipping LLC
Company: ASWS
Company: AT&T
Company: AT&T Government Solutions
Company: AT&T, Inc.
Company: Atlantic
Company: Atlantic Advisors
Company: Atlantik AD
Company: Atomic Energy of Canada Ltd
Company: ATP
Company: ATP Investments
Company: Attn: Gabriele Hysong Library – Rolls Royce – S. 05
Company: ATTrite Corp.
Company: Attwell Interests, Inc.
Company: ATWEL International,s.r.o.
Company: AUB-FEA
Company: Auchan
Company: Auctor Savjetovanja d.o.o.
Company: AUMS Ltd
Company: Aurora Disaster Strategies
Company: Austin Capital Management
Company: Austin Energy
Company: Austin Investment Management
Company: Australian National University
Company: Austria Tabak GmbH
Company: Austrian Armed Forces
Company: AutoAlaska LLC
Company: Aventis (Personal Account)
Company: Aviation Consultants Ltd.
Company: Avion Solutions Inc.
Company: Aviva Investors Australia
Company: Avondale Partners
Company: AVOW
Company: Avra Software Lab Inc.
Company: Avra Software Lab Inc.
Company: AW Investor
Company: AWG
Company: AXA Financial
Company: Axel Chemicals
Company: axiom capital management
Company: Axis Capital
Company: Azteca Gold
Company: Azumia
Company: B & K International
Company: B.A. Systems, Inc.
Company: b’huth
Company: B&B Tax Service
Company: B&G Risk Strategies LLC
Company: B&K International
Company: Babcock & Wilcox
Company: BAE Systems
Company: BAE Systems Inc.
Company: BAE Systems Inc.
Company: BAE Systems Inc.
Company: BAE Systems Information Technology
Company: bahiapulp
Company: bailey sign
Company: Bailey Tool & Mfg. Co.
Company: bain
Company: Bain & Company Middle East
Company: Bainco International Investors
Company: Baker McKenzie Krzyzowski i Wspolnicy
Company: Baker & Hostetler
Company: baker & mckenzie
Company: Baker Brown Dixon
Company: Baker Exploration Co.
Company: Baker Hughes
Company: BAKER HUGHES
Company: Baker Hughes Incorporated
Company: Baker Hughes Incorporated
Company: Baker Managers
Company: Balboa City School
Company: Balestra Capital, Ltd.
Company: Balfour Beatty Construction
Company: Ball Aerospace & Technologies Corp.
Company: Ballwin Police Department
Company: Bami World Sdn. Bhd.
Company: BAML
Company: Banco de Mexico
Company: Banco Ita˙ S.A.
Company: Bank Audi sal/Audi Saradar Group
Company: Bank Julius B‰r
Company: bank of america
Company: Bank of America
Company: Bank of America
Company: Bank of America
Company: Bank of America
Company: Bank of America
Company: Bank of America
Company: Bank of America
Company: Bank of America
Company: Bank of New York
Company: Bank of New Zealand
Company: Bank of New Zealand
Company: Bank of Tokyo-Mitrsubishi UFJ
Company: Banner Good Samaritan Hospital
Company: Banyan Tree Advisors Pvt Ltd
Company: Barbay Consulting
Company: Barbnet Investment Company
Company: Barclays Bank
Company: Barclays Capital c/o Prenax
Company: Barg Capital
Company: Barkto Zankiel Attn: John Bartko
Company: barloworld
Company: Barnebee Trading Group, Inc
Company: Barnett Financial, Inc.
Company: Barnett Waddingham Investments LLP
Company: Barrantagh Investment Management
Company: Barrantagh Investment Management Inc.
Company: Barrick Gold
Company: Barrick Gold Corp. Pueblo Viejo Project
Company: Barrow, Hanley, Mewhinney and Strauss, Inc.
Company: Bartlett & Co
Company: Bartner Group LLC
Company: BASE INDUSTRIES GROUP
Company: Baseball Historians, Inc.
Company: BASF
Company: BASF Corporation
Company: BasicsProject.org
Company: BASIL Networks
Company: Bauhaus Construction Corp.
Company: Bausch and Lomb
Company: Baxter
Company: Bay Area Medical Consulting
Company: bay city capital
Company: Baycraft Asset Management
Company: BayPort Financial Services
Company: BB&T Commercial Finance
Company: BCR ASIGURARI DE VIATA
Company: Bear Mountain Science & Photography
Company: Bear Stearns
Company: Bear Stearns
Company: Bearing Point
Company: Bechtel
Company: Bechtel Corporation
Company: Bechtel Corporation
Company: BedRock Ventures
Company: Bee-Sting Ventures
Company: Behr & Associates
Company: Belier Group, LLC
Company: Bellevue Baptist Church
Company: Bellocchi & Co LLC
Company: Belmont Properties
Company: Belux
Company: Benchmark Asset Managers
Company: benjamin investments
Company: BENS
Company: Benson Inc
Company: Benton Rutledge Properties
Company: Berkshire Securities Inc.
Company: BertFilm
Company: Bessemer Trust
Company: Best Buy
Company: Best Buy
Company: Bettinger Financial Advisors, Inc.
Company: Bevmor Mgmt
Company: BG Group
Company: BHP Billiton
Company: BHP Billiton
Company: BHP Billiton
Company: BILBROinc.
Company: Bill Owens, LLC
Company: BIN S.A.
Company: BioCompsoite Solutions
Company: BioHorizons
Company: BIONDO INVESTMENT ADVISORS
Company: Birkmere Associates LLC
Company: Birmingham International Air
Company: BJ Services Company
Company: Black & Veatch
Company: Black and Veatch
Company: Black Star
Company: Blackbird Technologies
Company: Blackfriars Capital Management AS
Company: BlackRock
Company: Blackwater Security Consulting
Company: BLACKWELL CONSULTING, LLC
Company: Blankinship & Foster, LLC
Company: BLB
Company: Blessing Petroleum Group, LLC
Company: Blinn College
Company: Blizzard Enterprises
Company: BLOCK 4 CONSULTING
Company: Blue Altarus, Inc
Company: Blue Diamond CT
Company: Blue Fox Management
Company: Blue Mountain, Ltd.
Company: Blue Planet Services LLC
Company: Blue Shield of California
Company: Blue Sky Apeiron Pty Ltd
Company: Blue Water Intl
Company: Blue, Johnson & Associates, Inc.
Company: Bluebonnet Consulting, Inc.
Company: blueshift tech
Company: Blum Capital Partners
Company: blurgl Inc.
Company: BMI
Company: BMO Capital Markets
Company: BMO Nesbitt Burns
Company: BMO Nesbitt Burns
Company: BMS
Company: BNC National Bank
Company: BNMM & Associates Engineering, LLC
Company: BNP Paribas
Company: BNS
Company: BNY Mellon
Company: Bob Haden, Broker
Company: Bob Lunday Consulting
Company: bobfloran@aol.com
Company: Boeing
Company: Boeing
Company: Boeing
Company: Boeing
Company: Boeing
Company: Boeing Company
Company: Boeing Company
Company: Boeing Company
Company: Boeing Company
Company: Boeing Corporation – BD Int
Company: Boenning
Company: Bold Marketing Partners
Company: Bongo Woodley Consultants
Company: Booz Allen Hamilton
Company: Booz Allen Hamilton
Company: Booz Allen Hamilton
Company: Booz Allen Hamilton Inc.
Company: Booz Allen Hamilton Inc.
Company: Booz Allen Hamilton Inc.
Company: Booz Allen Hamilton Inc.
Company: Booz Allen Hamilton Inc.
Company: Borger Financial Service
Company: Bose Corporation
Company: Boston College
Company: Boston Partners
Company: Boulder Capital
Company: Bowditch Consulting, LLC
Company: Box Appliance Service Co.
Company: Boyden
Company: BP
Company: BP
Company: BP
Company: BP
Company: BP
Company: BP
Company: Bp Exploration (Caspian Sea) Limited
Company: BP Plc
Company: BP Plc
Company: BPI Gestao de Activos
Company: Br. Gen USAF
Company: Bradford & Associates Ltd
Company: Bravado Appraisal Group
Company: Brazile and Associates, LLC
Company: Brazillian Army Commisison
Company: Brechnitz Group
Company: Brencourt Advisors
Company: Bresnahan & Associates, Inc.
Company: Brett M. Poston, P.C.
Company: Brian C Jensen, CPA
Company: Brian Stableford
Company: BriarPatch Opportunities
Company: Brickell Motors
Company: Brickell Motors
Company: Bridges Family Petroleum, Inc.
Company: Bridgespan
Company: brinkmann roofing co
Company: Brisbois Capital Mgmt, LLC
Company: Bristol Myers Squibb
Company: Brookstreet Securities
Company: brown advirory
Company: Brown Technical Service
Company: Browning, Randall, Pasteur & Assoc LLC
Company: Brownsville OEM / HS
Company: Brummer & Partners
Company: Bsrclays Capital
Company: BT Ireland
Company: Budway Enterprises
Company: Buffalo State College (SUNY)
Company: Bugg Properties, Inc.
Company: bulk bag express, inc
Company: Bull Dog Trading
Company: Bullard, McLeod & Associates, Inc.
Company: Burns, Taylor, et al
Company: Burrows Paper Corporation
Company: BUSARA
Company: Business Health Plus
Company: Business Technology Associates LLC
Company: BV
Company: BybeePower
Company: BYC co.ltd.
Company: Bytheway Limited
Company: C R Parr & Associates, PC
Company: C.A.P. Enterprises, Inc
Company: C.C.I.
Company: C.S. Crosby & Associates
Company: C/ HQJOC
Company: c/o Al Witzell
Company: C/o Johns Byrne
Company: C2I – CI/HUMINT TEAM
Company: CA Stromberg AB
Company: CACI
Company: Cadent Energy Partners
Company: CAI
Company: Calamos Holdings
Company: Calamos Holdings LLC.
Company: Caldera Resources Inc.
Company: Cales Investments, Inc.
Company: Calgas Exploration Ltd
Company: Calhoun High school
Company: CALIBRE Systems, Inc.
Company: California State University San Bernardiono Graduate Student
Company: calpian
Company: Caltex Australia Limited
Company: Calvary Baptist Church
Company: Calyon Corporate and Investment Bank
Company: Calyon Financial Inc.
Company: CAM International
Company: Camber
Company: Cambium Group
Company: Cambria Investment Management
Company: Campbell Fittings Inc
Company: Campbell Soup
Company: Canaccord Capital
Company: Canada Pension Plan Investment Board
Company: Canada-Israel Committee
Company: Canadian Air Transport Security (CATSA)
Company: Canadian Defence & Foreign Affairs Institute
Company: Canadian Forces College
Company: Canadian Forces College
Company: Cancel
Company: canceled account 01/04/2008 via call to customer service
Company: Candlestick LLC
Company: Canonbury Group
Company: CAPE Legacy Fund
Company: Capital Alpha Partners, LLC
Company: Capital Group Companies
Company: Capital Group Companies
Company: Capital Group Companies
Company: Capital Group Companies
Company: Capital Group Companies
Company: Capital Group Companies
Company: Capital Growth Management
Company: Capital Ideas, Inc.
Company: Capital One
Company: Capital Plan, Inc
Company: CapitalRock Advisors
Company: Capral
Company: CapRock Oil Tools, Inc.
Company: Cardframer
Company: Cardinal Gas Partners,LLC
Company: CARE International
Company: Cargill
Company: Cargill Inc & Subsid
Company: caritas
Company: Carlsen & Co.
Company: Carnegie Capital
Company: Carobu Engineering
Company: carpeteers carpet cleaning service
Company: Carrelton Asset Management
Company: Carrollton
Company: Carrow Companies, LLC
Company: Cart-Away Concrete Systems
Company: Cartel Consulting
Company: Carter Concepts, Inc
Company: Carthage College
Company: Casablanca Infrastructure Pvt. Ltd.
Company: Casals & Associates, Inc
Company: Cascadian Enterprises LLC
Company: Casey Financial
Company: Caspian Steppes
Company: Castleman Group
Company: Catalent
Company: Catalyst
Company: Catalyst Investment Group Limited
Company: Caxton Associates LLC
Company: CB Richard Ellis
Company: CBR
Company: CBS
Company: CC Riders
Company: CCG
Company: CCM (Pty) Ltd
Company: CCOliphant&Son,Inc.
Company: CCS International
Company: CDW
Company: CECO Associates
Company: Cedar Road Capital
Company: CEFAM
Company: CEL & Associates, Inc.
Company: cell 502 905 1842
Company: CEMEX
Company: Center for Environmental Diplomacy
Company: Center for European Policy Analysis
Company: Center for Global Strategies
Company: Center for International Security and Strategic Studies
Company: Center of Doctrine and Strategic Development (CDSD), RTA
Company: Central Florida Community College
Company: Central Trust & Investment Co
Company: Centurion
Company: CEO, MVmax
Company: Cerberus Capital Management
Company: Cervantes and Associates
Company: CESCE, S.A. – VAT: ESA28264034
Company: CG Maton Agency, Inc.
Company: CH&I Technologies
Company: CH2M HILL
Company: CH2M HILL
Company: Chairman & CEO / Belvoir Media Group LLC
Company: Chamber of Deputies
Company: Chaminade College Preparatory
Company: Chaminade University
Company: Chandlas Enterprises Ltd
Company: Changsha Huir Biological-tech Co.,ltd
Company: Chapman Consulting
Company: Charles D. Haines, LLC
Company: Charles F. Day & Assoc. LLC
Company: Charles Schwab
Company: Charles Schwab
Company: Charles Schwab & Co, Inc
Company: Charles Sturt University
Company: Charlotte Pipe
Company: Chaswil Ltd
Company: Chemonics International
Company: Chen and Partners
Company: ChengChi University
Company: ChengChi University
Company: Chesney & Company
Company: Chevron
Company: Chevron
Company: Chevron Corporation
Company: Chevron Corporation
Company: Chevron Corporation
Company: Chevron Corporation
Company: Chevron Corporation
Company: Chevron Global Gas
Company: Chevron Phillips Chemical Company
Company: Chevron Phillips Chemical Company
Company: Chevron Phillips Chemical Company
Company: Chickasaw Capital Management
Company: Chile Company
Company: Chinese Embassy
Company: Choate, Hall & Stewart
Company: Chosunilbo
Company: CHP
Company: Christian Science Monitor
Company: CHRISTUS Health
Company: CHS, Inc
Company: Chubb & Son
Company: Church of the Great God
Company: CI Investments
Company: CI Investments
Company: Cia. Colombiana de Inversiones S.A.
Company: CIBC
Company: CIBC Wood Gundy
Company: cibc world markets
Company: CIBC World Markets
Company: circle financial group
Company: Cisco
Company: Cisco
Company: Cisco
Company: Cisco Systems
Company: Cisco Systems
Company: Citadel International
Company: Citgo
Company: CITGO Petroleum Corporation
Company: Citi
Company: Citi Investment Research
Company: Citi Smith Barney
Company: Citigroup
Company: Citigroup
Company: Citigroup
Company: Citigroup
Company: CITIGROUP
Company: Citigroup Corporate & Investment Bank
Company: Citigroup Smith Barney
Company: Citigroup Smith Barney
Company: Citigroup/Smith Barney
Company: Citizens & Northern Bank
Company: citizens natl bank
Company: City Center Security
Company: City Center Security
Company: City of Miami Police Department
Company: City of Weslaco
Company: Cityteam
Company: ck locke & partners
Company: Claire Orthopaedics PA
Company: Claren Road
Company: Clarium Capital Management
Company: clarkson and company
Company: Clarsen & Associates
Company: Clayton Consultants, Inc.
Company: Clemens Capital
Company: Clemson University
Company: Cloverdale Investments Pte Ltd
Company: Clovis Point Solutions, LLC
Company: CMC
Company: CMS Energy
Company: CMSU, LLC
Company: CNR HOLDING AS
Company: Co / TD Waterhouse
Company: Co-Mar Management Services
Company: Coca-Cola
Company: Cognitive Assets
Company: Cognitive Investments LLC
Company: Cogsdill Tool Prod.
Company: Cole Papers, Inc.
Company: Colgate Palmolive
Company: Colgate Palmolive
Company: Colgate Palmolive
Company: Colgate Palmolive
Company: Colliers International
Company: Colliers International
Company: Colliers International
Company: Collins Development Co
Company: Colorado Army National Guard
Company: colorado player consultans
Company: COLSA Corporation
Company: Colton & Associates, P.C.
Company: Columbia University
Company: Combat Support Associates
Company: ComitÈ Internacional de la Cruz Roja
Company: Commonwealth North
Company: comp
Company: Company:
Company: Compass Asset Management
Company: Compass Capital AG
Company: compass financial advisors,llc
Company: Compass Foundation
Company: Compensation Resource Group
Company: Compliance Associates
Company: Comprehensive Computer Services
Company: ComPro Realty
Company: Computer Sciences Corp.
Company: Comunicaciones Nextel de Mexico SA de CV
Company: CONCERT Advisor Services
Company: Condortech Services, Inc.
Company: Conductix, Inc
Company: Conflex Consulting
Company: Conflict Resolution, Inc.
Company: Confluence Investment Management
Company: Congress of Racial Equality
Company: Connect Consulting, Inc.
Company: Conning & Company
Company: ConocoPhillips
Company: ConocoPhillips
Company: ConocoPhillips
Company: ConocoPhillips
Company: ConocoPhillips Russia
Company: Consejo Mexicano de Asuntos Internacionales, A.C.
Company: Consilium
Company: Consolidated Water Power Co
Company: Constellation Investment Group
Company: Constellation Wealth Advisors
Company: Consulant/Adjunct Professor Utah State University
Company: consultant
Company: consultco
Company: Consultiera
Company: Consultora Demison
Company: Consultoria Estrategica Primer Circulo, S.C.
Company: Contact name is Debbie McCoy
Company: Contingent Macro Advisors LLC
Company: Convio Inc
Company: Cook Management, LLC.
Company: Coolescence, LLC
Company: Cooperative Consultants, Inc.
Company: Copernio Corporation
Company: Copymaven, Inc
Company: Corbin Capital Partners
Company: Corestates Capital, LLC
Company: Coril Holdings Ltd.
Company: Cormark
Company: Corn Products International
Company: Cornell University
Company: Cornish & Co.
Company: Cornwall Capital, Inc.
Company: Corona Investments, LP
Company: Corporacion REY S.A.
Company: Corporate Intelligence Analyst Network, Pty. Ltd.
Company: Corriente Partners
Company: Coss Consulting Int. BDA
Company: Cottage Realty LLC
Company: Cottonfield Family Office AG
Company: Cougar Global Investment
Company: Council on Foreign Relations (CFR)
Company: Council on Foreign Relations (CFR)
Company: COUNTRY Trust Bank
Company: Covenant
Company: Covenant International
Company: Covenant International
Company: Coventry Realty
Company: Covepoint Capital Advisors
Company: Coyote Oilfield Consulting Ltd.
Company: CR
Company: Crain’s Detroit Business
Company: CRANE CURRENCY
Company: Crane Realty
Company: Credit Libanais SAL
Company: Credit Suisse
Company: Credit Suisse
Company: Credit Suisse
Company: Credit Suisse
Company: Credit Suisse
Company: Credit Suisse
Company: Creighton University
Company: CRI
Company: Crisis Management Initiative
Company: Criswell Financial, Inc.
Company: Crossinvest (Asia) Pte Ltd
Company: crosswind partners,llc
Company: Crown Flour Mills
Company: Crown Point Solutions
Company: Crown Productions
Company: Crown Productions
Company: Crown Productions
Company: CRP
Company: CS INVEST CONSULTING
Company: CSA Wealth Management
Company: CSC
Company: CSC
Company: csx transportation
Company: CTV
Company: Cubic
Company: Cubic Applications
Company: CUF QI
Company: Cumberland Advisors
Company: Cure International
Company: Currie Partners, Inc.
Company: Cushman & Wakefield
Company: Cushman & Wakefield
Company: Cushman & Wakefield
Company: Custom Concrete Co
Company: Custom Direct LLC
Company: Cyrte Investments
Company: Cyrte Investments
Company: d elliott
Company: D-8 Organization
Company: D-Link Corporation
Company: D. J. Hall & Co
Company: D.B. Root & Company, Inc.
Company: D&D Securities Inc.
Company: Dallas Federal Reserve Bank
Company: Dan Aridor Holdings Ltd
Company: Dandelion Digital
Company: Daniel Defense International
Company: Daniel I Shapiro, M.D.,P.C.
Company: Danneberg Oil Ltd
Company: Das Kapital Capital
Company: DataSphere, LLC
Company: DataView LLC
Company: DataViz, Inc
Company: David Anderson Financial Planning, LLC
Company: David B. Dunbar & Associates
Company: David F Palmer
Company: David G. Major Associates, Inc.
Company: Davis LLP
Company: Davis-Ross Investment Advisers LLC
Company: Davutoglu Avukatlik Burosu Attorneys at Law
Company: Dawnhouse Ltd.
Company: DCF Capital
Company: De Lage Landen Financial Services, Inc.
Company: DE Shaw
Company: De Stefano Wealth Management
Company: DEALGLOBAL SERVICIOS S.A.
Company: Deane Retirement Strategies
Company: Debt Settlement Associates, LLC
Company: Decipher Securities
Company: Deere & Company
Company: Defense $ Security , Consulting/Training
Company: Defense Intelligence Agency
Company: DEFINE CREATIONS
Company: DEIK
Company: Del Campo
Company: Del Oil
Company: Dell
Company: Dell Inc
Company: Deloitte
Company: Deloitte
Company: Deloitte
Company: Deloitte and Touche
Company: Deloitte Consultanta SRL
Company: Delta Air Lines
Company: Delta Airlines
Company: Delta Corporation Limited
Company: Demand Lending
Company: Demographic Wave, LLC
Company: Dentist
Company: Denton Record-Chronicle
Company: Denton Record-Chronicle
Company: DEP, PC
Company: Department of Army
Company: Department of Defense
Company: Department of Defense
Company: Department of Defense & Homeland Securtity Group
Company: Department of Energy
Company: Department of Justice
Company: Department Of National Defense
Company: Department of the Air Force
Company: Deployment Support Command, USAR
Company: DEPLU
Company: Dept. of Treasury
Company: DER SPIEGEL
Company: Desert Palms Golf and RV Resort
Company: DeShurko Investment Services, Inc.
Company: deutsche bank
Company: Deutsche bank
Company: Deutsche Bank
Company: Deutsche Bank
Company: Deutsche Bank
Company: Deutsche Bank
Company: DEUTSCHE BANK
Company: Deutsche Bank AG
Company: Deutsche Bank AG Hong Kong Branch
Company: Development Plus
Company: Development Research Associates
Company: Development Solutions, Inc.
Company: Devonshire Investors
Company: Dexter Oilfield Inc.
Company: DFI
Company: DGAM
Company: DHL
Company: DHR International
Company: DHRC
Company: DHS International Advisors LLC
Company: DHS/TSA
Company: Diablo Health Company
Company: DIAM U.S.A., Inc.
Company: Diamond Hill Investment Group, Inc.
Company: DIARIO PANORAMA
Company: Dickson Financial Group
Company: DigiscanUSA LLC
Company: Digital Analysis & Graphics, Inc.
Company: Digital Bear Consulting
Company: Digital Solutions & Video Inc
Company: Dillon Aero Inc.
Company: Dimension Capital Management
Company: DINACIE
Company: Dipartimento di Matematica
Company: direct action medical network
Company: direct resources
Company: Discere Docendo, Inc
Company: Discovery Institute for Public Policy
Company: Diversified Mortgage
Company: DML Associates, LLC
Company: DO NOT RENEW
Company: DO NOT RENEW SUBSCRIPTION
Company: Doctors Without Borders
Company: Doctors Without Borders
Company: Doctors Without Borders
Company: DoD
Company: DOD
Company: Domaine Clarence Dillon S.A.
Company: Dominion Resources
Company: Dominion Resources
Company: dominion securities
Company: Domus Enterprises
Company: Don Kuykendalls Comp Accounts
Company: Don Kuykendalls Comp Accounts
Company: Don Kuykendalls Comp Accounts
Company: Donald Martin Enterprises, Inc.
Company: Dora French Designs
Company: Doraville Police Dept
Company: Doug Bell & Associates
Company: Doug Whitehead Comp Accounts
Company: Dover Consulting
Company: Dow Chemical
Company: Dow Corning
Company: Downeast Rover, Inc.
Company: Downer Grove South ISD
Company: Doxsee Sea Clam Co,Inc
Company: Dr. John Templeton
Company: Dr. John Templeton
Company: Dr. John Templeton
Company: Dr. Wayne Peace Inc.
Company: DRD Laboratory, LLC
Company: Dresdner Kleinwort
Company: DRS Defense Solutions, LLC
Company: DRS Technologies
Company: DRW Trading Group
Company: DSS Engineering
Company: DTC Communications
Company: dte energy
Company: DTE Energy Trading
Company: DTI
Company: Du Pont China Ltd.
Company: Du Pont China Ltd.
Company: Duarte Design, Inc.
Company: Dudobi Limited
Company: Duke Energy
Company: Duke Energy
Company: Duke Energy
Company: Duke Energy Corporation
Company: Duke Management Company
Company: Duke University
Company: Duke University
Company: Dumas Bay Properties
Company: Dunross & Co AB
Company: DUOMENTIS
Company: Dutko Worldwide
Company: Dutko WorldWide
Company: Duty Tire & Service Center
Company: Dwight Asset Management
Company: Dynamatic Technologies Limited
Company: Dynamic Capital Holdings, LLC
Company: Dynamic IT Solutions
Company: Dynamiq Pty Ltd
Company: E-B Advertising & Display
Company: e-Ventus Corporation
Company: E.I. du Pont de Nemours & Company
Company: eads
Company: Ealby & Jake Group, LLC
Company: East Asia Strategic Centre
Company: Eastman Chemical Company
Company: Eastman Dillon Oil & Gas Associates
Company: easyDNS Technologies Inc.
Company: Eaton
Company: Eaton Vance
Company: Eaton Vance
Company: EBERVEIN FINANCIAL GROUP, INC.
Company: Echostar Purchasing
Company: Ecocem
Company: ECONOMETRIX TREASURY MANAGEMENT
Company: eCreate
Company: Ed Kenley Investments
Company: EDARE sprl
Company: Edatis
Company: Eddington Capital Management
Company: Edengate Estate
Company: Editora Abril
Company: EDITORIAL CLIO, LIBROS Y VIDEOS SA DE CV
Company: EDS
Company: EESS
Company: EGS
Company: Ehanced Investment Partners LLC
Company: EHC Global
Company: Eidactics
Company: Eldred Rock Associates
Company: Electoral Office of Jamaica
Company: Eli Lilly
Company: Eli Lilly
Company: Elk Creek Trading Company
Company: Elkem AS
Company: Elliott Cove Capital Management
Company: Elm Income Group, Inc
Company: ELS Riska and Security Consulting, LLC
Company: Embassy of Angola
Company: Embassy of Argentina
Company: EMBASSY OF BRUNEI DARUSSALAM
Company: Embassy of India
Company: Embassy of India
Company: Embassy of Italy
Company: Embassy of Japan
Company: Embassy of Lithuania Defence Attache Office
Company: Embassy of Peru, Belgium
Company: Embassy of Romania
Company: Embassy of Sweden
Company: Embassy of Vietnam
Company: Embassy Republic of Uzbekistan
Company: Embry-Riddle Aeronautical University
Company: Emerald Touch Inc
Company: Emerson
Company: Emertia
Company: Emirates Investment Services (EIS)
Company: EMO Trans Inc.
Company: Empire Homes
Company: Empire Royalty Co.
Company: EN McCully Trading
Company: Enbridge Inc.
Company: EnCana
Company: Endeavor Real Estate Group
Company: Endeavour Group
Company: Endurance
Company: Energy & Precious Metals Capital
Company: Energy Developments and Investments Corporation
Company: ENERGY STRATEGY CONSULTANTS
Company: Engel, McCarney and Kenny LLP
Company: EnTEC
Company: Entergy
Company: Entergy Operations, Inc.
Company: Enterra Solutions
Company: Entheos Consulting
Company: ENTRIX, Inc.
Company: Envestnet
Company: Environmental Chemical Corporation
Company: EPCINT International, Inc.
Company: EPCINT International, Inc.
Company: EPCINT International, Inc.
Company: EPCINT International, Inc.
Company: Episcopal Church
Company: EPRS Energy Co
Company: Epson America, Inc.
Company: EQM Inc
Company: Equinox Partners
Company: Equity Research Associates
Company: ERA Coastal Properties
Company: Ergon Refining, Inc.
Company: Eric Haupt General Const.
Company: Ericsson
Company: ESCOC MoFA
Company: Escuela de Graduados en AdministraciÛn P˙blica y PolÌtica P˙blic
Company: ESRI
Company: ESRI
Company: ESRI
Company: ESRI
Company: ESRI
Company: ESRI
Company: ESRI
Company: ESRI
Company: ESRI
Company: ESRI
Company: Essential Financial Planning
Company: Essex County Prosecutor’s Office
Company: Eto Investmenrs Limited
Company: EURISC Foundation
Company: Eurizon Capital
Company: Euro Guild
Company: eurocology
Company: Europacific Marketing, Inc.
Company: EUROPEAN COMMISSION
Company: European Commission – League of Arab States Liaison Office
Company: European Commission ECHO Amman
Company: European Parliament
Company: Europol
Company: euurfid
Company: Evans Consultants
Company: Everett Advisory Partners
Company: Everglades Capital Management
Company: EvoCapital Limited
Company: EWA/IIT
Company: Ex Cathedra
Company: Ex3, Inc.
Company: ExACT Mixing
Company: Excalibur Consulting
Company: Excel Risk Consultancy
Company: EXECAIRE
Company: executive insurance
Company: Executive Search International
Company: Exel Inc.
Company: Exelon Nuclear
Company: Exeter Group
Company: Expat Money Management, Inc.
Company: ext 113
Company: Extek Pacific
Company: ExxonMobil
Company: ExxonMobil
Company: ExxonMobil Corporation
Company: ExxonMobil Corporation
Company: ExxonMobil Russia Inc
Company: F & F Conseil
Company: F & G Ventures
Company: F. Clark Sauls, MD
Company: F.J. Westcott Company
Company: F&D Advisors
Company: Faherty Property Co. Ltd.
Company: Fahnestock Asset Management
Company: Fairmont State University
Company: FAITH BAPTIST CHURCH
Company: Falcon Private Bank Ltd
Company: Falcon Security Group Iraq
Company: Fallon-Countrywide Ltd
Company: Farm Field Defense, Inc.
Company: Farm Field Defense, Inc.
Company: Farm Field Defense, Inc.
Company: Faron Comps
Company: Fat Prophets
Company: Fayez Sarofim & Co.
Company: Fazzari + Partners LLP
Company: FCC
Company: FDH Asset Mgt. Inc.
Company: fdlnz
Company: Fed Reserve
Company: Federal Express
Company: Federal Express
Company: Federal Express / U.S. Navy
Company: Federal Way AFJROTC
Company: Federated Financial Corporation of America
Company: Federated Investors
Company: Fedoroff Associates
Company: Ferrell Capital Management
Company: Ferrington Vineyards
Company: FFM
Company: FGV
Company: FH International
Company: FIB Management AG
Company: Fick & May Law Firm
Company: Ficogrande Pty Ltd
Company: Fidelity
Company: Fidelity
Company: Fidelity International
Company: Fidelity Investments
Company: Fidelity Investments
Company: Fidelity Management & Research Company
Company: Fidelity Management & Research Company
Company: Fidelity Management & Research Company
Company: Fidelity State Bank and Trust Co
Company: FIDUCIARY REVIEW SERVICES
Company: Fifth Street Capital, LLC
Company: FIG Partners LLC
Company: Finacial Design Associates
Company: Financial Achievement Services Inc
Company: Financial Advisory Corporation
Company: Financial Advisory Services
Company: Financial Leadership Group, LLC
Company: Financial Management Advisors
Company: Financial Stocks, Inc
Company: Financial Strategies & Solutions Group
Company: Financial Technologies
Company: Financial Times
Company: FINARC
Company: Finch
Company: Fine Gardens
Company: FINTRAC
Company: First Austin
Company: First Baptist Concord
Company: First Capitol Ag
Company: First Financial Advisors
Company: First Industries Corp
Company: FIRVA Capital Management, LLC
Company: FIT Group
Company: Five Corners Consulting
Company: Flick Confreres & Associates Pty Ltd
Company: FlightSafety International Inc.
Company: Flint Financial Group
Company: Flint Hills Resources
Company: Florida Engineering & Design Inc.
Company: Fluent Wealth Partners
Company: Fluid Communications
Company: Fluor Corporation
Company: Fluor Corporation
Company: Fluor Corporation
Company: fmc
Company: Focus Financial
Company: Focus LLC
Company: Focus Strategies Merchant Banking, LLC
Company: Focustar Consulting
Company: Foliage Software Systems
Company: Fondazione CDF
Company: FondElec Capital ADvisors, LLC
Company: FONINSA
Company: Force 10 Consulting, LLC
Company: Ford Commercial
Company: Ford Foundation
Company: Fore Research and Management, LP
Company: Forecast International
Company: Foreign Affairs
Company: Foreign Policy Research Institute
Company: Forensic Analytics LLC
Company: foreseeable risk analysis center
Company: Formula Capital
Company: Forticom UAB
Company: Fortis
Company: FortisMeespierson
Company: Forum for Comparative Correction
Company: Forward Pass Inc
Company: Fory Group LLC
Company: Foster Dykema Cabot
Company: Foster Tire Co.
Company: Foundation for Environmental Security and Sustainability (FESS)
Company: Fountain cosmetics pty ltd
Company: Fourells Business Development Group
Company: Fox Consulting
Company: Fox News Channel
Company: Foxhall Capital
Company: Framestore
Company: Frank Wilson
Company: Franklin Templeton
Company: Fraumann Associates LLC
Company: freedom foundation inc
Company: Freestyle Marketing
Company: Fremont Group
Company: Friday, Friday & Kazen
Company: Fried Asset Management Inc.
Company: Friesland Campina Middle East
Company: Frist Capital, LLC
Company: Frontline Systems Inc.
Company: Ft. Richardson
Company: Fuel For Truth
Company: Fujisanke communications international
Company: Fulcrumnet
Company: Full Court Fundamentals
Company: Full Spectrum Technologies, Inc.
Company: FundaciÛn TelefÛnica G 8208680
Company: Funding Blueprint, LLC
Company: Fusion Enterprises
Company: Future Escape Ltd
Company: Future Pipe Industries
Company: FX Concepts, Inc.
Company: G3
Company: Gaia Capital Management Inc
Company: Gaines & Co
Company: Galo Properties
Company: GAM LLC
Company: Gamma Capital LLC
Company: Gamma Knife Center of the Pacific
Company: Garanti Bankas?
Company: Gardner-Webb University
Company: Gartner Group
Company: Gateway Consulting Group, Inc.
Company: Gauteng Discount Consultants
Company: gavekal
Company: gavel capital group inc.
Company: GBB
Company: GCM Analys
Company: GCResourses
Company: GDT
Company: GE Real Estate
Company: Gelker Gear
Company: Gemini Financial Services Corporation
Company: Gemini industries
Company: Gemmer Asset Management LLC
Company: General Atlantic
Company: General Dynamics
Company: General Dynamics
Company: General Dynamics
Company: General Dynamics AIS
Company: General Dynamics Land Systems
Company: General Dynamics Land Systems
Company: General Dynamics Land Systems
Company: General Dynamics Land Systems
Company: General Electric
Company: General Electric
Company: General Electric
Company: General Electric
Company: General Electric Company
Company: General Electric Company
Company: General Growth Properties
Company: General Maritime Corporation
Company: General Mills
Company: General Steamship Corporation
Company: Generation Investments
Company: Geohazards Consultant
Company: GeoPetra
Company: George Mason U.
Company: George Mason University
Company: George Washington Univ
Company: George Weiss Associates
Company: Georgetown University
Company: Georgetown University
Company: Georgetown University
Company: Georgia of Technology
Company: Georgian Library Association
Company: Geotechnologies
Company: Gevo Inc
Company: GFA
Company: Ghent University
Company: GIFT MEMBERSHIP
Company: Gillespie Air Services Inc
Company: GIPL
Company: glencrest investment advisors
Company: Glenmede Trust Company
Company: Glennel Associates
Company: Global Capital Investments, Inc.
Company: Global Criterion Solutions Limited
Company: Global Crop Diversity Trust
Company: Global Exchange Trading
Company: Global Geophysical.com
Company: Global Group Solutions
Company: Global Impact Inc.
Company: Global Industries
Company: Global Project srl
Company: Global Prospect
Company: Global Security Services, LLC
Company: Global SourceNet
Company: Global Technonlogy Applicatons, Ltd.
Company: Global Terrorism Consulting
Company: GlobalAffairs.org
Company: GlobalBusiness Initiatives
Company: GlobaLogix, Inc
Company: GlobalSecur Consulting Services
Company: GlobalView Capital, LLC
Company: Globepharm
Company: GMAC Financial Services
Company: GMI Solutions
Company: Gnomon Security
Company: Gobal Executive Protection
Company: Godandi & Sons, Inc.
Company: Gold Coast Futures Group
Company: Golden Dome Data
Company: Golden Hills Brokers/SG
Company: Golden Key Investments, Ltd.
Company: Golder Investment Management
Company: goldi inc
Company: Goldman Sachs
Company: Goldman Sachs
Company: Goldman Sachs
Company: Goldman Sachs
Company: Goldman Sachs
Company: Goldman Sachs
Company: Goldman Sachs
Company: Goldman Sachs
Company: Goldman Sachs
Company: Goldman Sachs
Company: Golfregistrations.com LLC
Company: goodkin consulting
Company: Goodwood Investments
Company: Google, Inc
Company: Gordon Asset Management, LLC
Company: GorGrp Inc.
Company: GORGRP, Inc.
Company: Gornal Consulting
Company: Gov
Company: goverment
Company: government
Company: Government of Alberta
Company: Government of Canada
Company: Government of Macedonia
Company: Government of Ontario
Company: GP Investimentos
Company: GPLP
Company: Grace Fellowship
Company: Grace Outdoors
Company: Graf Financial Advisors, LLC
Company: GRANBERG AS
Company: Grand-Jean Capital
Company: Granite Investment Advisors
Company: Grant Aviation
Company: Grant Thornton LLP
Company: Grasshopper Creek Associates, Inc.
Company: Graver Capital Management
Company: Great Northern Sentry Co.
Company: Greater Good Global Support Services
Company: Green Valley company
Company: Greenberg Traurig
Company: Greensfelder, Hemker & Gale, P.C.
Company: greenville hosp system
Company: Gregory & Cook inc
Company: Gresham Ventures
Company: GreyBridge Solutions
Company: Griffith University
Company: Grossmann Jet Service
Company: Grupo Atenea
Company: Gryphus d.o.o.
Company: GSCG
Company: Guardian Western Inc.
Company: Guardian-gbs
Company: Guerin & Guerin Inc.
Company: Guermantes Inc
Company: guilford county emergency services
Company: Gulf Strategic Advisors
Company: Gulf Strategies, LLC
Company: Gutierrez Law Firm
Company: Guy N Molinari, LP
Company: Gygi Capital Management
Company: H-E-B
Company: H.I.S. Security Consulting, LLC
Company: H.J. Heinz
Company: H.M. Payson & Co.
Company: H&H Investment Advisors
Company: H&S Engineering
Company: HABERTURK TV
Company: Halbert Mill
Company: Haliburton
Company: Hall Wilson, LLC
Company: Halliburton
Company: Halliburton
Company: Hallwood Investments Limited
Company: Hamilton Jackson Consulting
Company: hamilton robinson llc
Company: Hammarskjold & Co.
Company: Hammond Law Firm
Company: Hampton Consulting
Company: Hampton-Newport News Community Services Board
Company: Hancock Bank
Company: Hancock Holding Company
Company: Hands On Centering
Company: Harding University
Company: Harley-Davidson, Inc.
Company: Harley-Mohawk Inc.
Company: Harris Investment Mgmt
Company: Harris Investments
Company: Harrison Cardiology Clininc
Company: HARRY B. SANDS, LOBOSKY & CO
Company: harston consulting
Company: Hart Security
Company: Harvard University
Company: Harvest Investment Consultants
Company: Haven
Company: HAWAII HOLDINGS, LLC
Company: Hawkesbury Advisors
Company: Hayden Capital Preservation, LLC
Company: Hazelett Strip-Casting Corp
Company: HB Technologies, Inc.
Company: HBA CONSULTORIA
Company: HBK Capital Management
Company: HBS Financial Planning Ltd
Company: HeadCase Humanufacturing, Inc.
Company: Health Plus Inc
Company: healy mattos
Company: Hefren-Tillotson
Company: Heineken USA
Company: Heldenfels Enterprises
Company: helen yunker realty
Company: Hellenic Center for Chinese Studies (EKKIM)
Company: Helmerich & Payne
Company: Herbert (3) Limited
Company: Hercules Offshore
Company: Heritage Plastics Inc
Company: Heritage West Financial
Company: Hermening Financial Group LLC
Company: Heron Capital Management Inc
Company: Herzstein Charitable Foundation
Company: Heska Corp
Company: Hess Corp
Company: Hess Corporation
Company: Hewlett Packard Centro de Servicios Globales S de RL de CV
Company: Hewlett-Packard Company
Company: Heximer Investment Mgmt
Company: hff
Company: hgkhg
Company: HHC, 20th EN BN
Company: HHC, 5th BDE, 75th DIV (BCTD)
Company: Hickory Ground Solutions
Company: Hidden Advantage, Inc.
Company: Higdon Law Firm
Company: Highfields
Company: Highfields Capital
Company: Highschool Software&Media
Company: Highview Capital Management, LLC
Company: Hill Musuem & Manuscript Library
Company: hillsboro journal
Company: hillsboro journal inc
Company: Hillwood Energy
Company: Hilton Hotels Corp
Company: Hinds Banner
Company: Hines
Company: Hirshfield Law
Company: Hitachi-GE Nuclear Energy, Ltd.
Company: Hits Magazine
Company: HL Cap Inc
Company: HMZ Law
Company: Hoff & Leigh
Company: Hoisington Management
Company: Holland Investment Management
Company: Holonym
Company: Holowesko Partners Ltd
Company: home
Company: Home
Company: Home
Company: Home & Family
Company: Home Network News, Inc.
Company: Homeland Security
Company: Homeopathic Trends, Inc.
Company: HOMEWORTH
Company: Honeywell
Company: Honeywell International
Company: Honeywell International
Company: Hoover Institution
Company: Hoover Investment Mgt
Company: Horizon
Company: Horst & Associates Consulting
Company: Hortgrow Services
Company: Hoshen-Eliav
Company: Hospital
Company: Hotel Diplomat AB
Company: HouseMaster
Company: houston insurance
Company: Houston Police Department
Company: how 2 pty ltd
Company: Howrey, LLP
Company: HR Financial Services, Inc.
Company: HREF Tools Corp.
Company: HSBC
Company: HSBC
Company: HSBC
Company: HSBC Bank Australia
Company: HSBC Markets (Asia) Limited
Company: HSBC Securities Japan Limited. Tokyo Branch
Company: HTC Security
Company: Hubbell Incorporated
Company: Huber Companies, Inc.
Company: Hueter Engineering
Company: Hughes Financial Services
Company: Human Intelligence Enterprise
Company: Humint Services Group
Company: Hungarian Mission to NATO
Company: hungerpiller capitla managment
Company: Hunt Oil
Company: Hunt Oil
Company: Hunt Oil
Company: Hunter Douglas
Company: Hunton & Williams LLP
Company: Hurst-Euless-Bedford ISD
Company: Husky Energy
Company: Hyatt Hotels
Company: Hyatt International (Europe Africa Middle East) LLC
Company: HYPATIA I & S
Company: HyperCompany
Company: Hyperion Resources
Company: I agree with the author.
Company: Ian A Schapkaitz
Company: IASG, Inc.
Company: IB Russia Trading Ltd Oy
Company: IBCONTACTS
Company: IBM
Company: IBM
Company: ICA FLUOR
Company: ICANN
Company: ICAP
Company: ICC
Company: ICC
Company: ICCO
Company: Iceline Investments Inc.
Company: iCONOS
Company: ICRC
Company: icrier
Company: Idea Transfer Inc
Company: Ideal Aerosmith, Inc.
Company: IDSS Co.
Company: IFSC Ireland
Company: IIIT
Company: IISD
Company: Image Enhancement Center
Company: Imara SP Reid
Company: IMM Swiss AG
Company: Immediate Response Group LLC
Company: Immunity Incorporated
Company: Immunity Incorporated
Company: impact outdoor advertising co
Company: Incoe corporation
Company: Independent
Company: Independent
Company: Independent Contractor
Company: index ventures
Company: Indian Military Review
Company: Individual
Company: Individual
Company: Individual
Company: Individual
Company: Individual
Company: Individual
Company: Industrial Supply
Company: Infinium Capital Mgt
Company: Inflection Energy LLC
Company: Informatica
Company: ING Group
Company: ING Investment
Company: ING Life Insurance Japan Ltd
Company: Innovation Capital
Company: Innovative Solutions
Company: Innovative Title Services, LLC
Company: Innoven
Company: Institute of International Politics and Economics
Company: Institute of South East Asian Studies
Company: Institute of the Legislation and Comparative Law under the Russ/
Company: Intact Investment Management Inc.
Company: Integration consulting
Company: Intel
Company: Intel
Company: Intel Corp
Company: Intel Corporation
Company: Intel Corporation
Company: Intel Corporation
Company: Intel Corporation
Company: Intel Corporation
Company: Intel Corporation
Company: INTELLMD
Company: Intelsec Corporation
Company: Inter-Pochta.ru
Company: Interacciones casa de Bolsa C.A
Company: Intereal Corp. / Bressie & Co.
Company: Intergraph
Company: Interlogic, Inc.
Company: International Association of Chiefs of Police
Company: International Atomic Energy Agency
Company: International Committee of the Red Cross
Company: International Consultant
Company: International Criminal Court
Company: International Equity Sales
Company: International Iron Works, Inc.
Company: International Medical Corps
Company: International Mission Board
Company: International Mission Board
Company: International Mission Board
Company: International Mission Board
Company: International Mission Board
Company: International Monetary Fund
Company: International Paper
Company: International Pathfinder Solutions Ltd
Company: International Rescue Committee
Company: International Science Exchange
Company: INTERNATIONAL SERVICE CONSULTANTS LTD.
Company: International SOS
Company: International Test Solutions
Company: Interpochta.ru
Company: INTERPOL
Company: INTERPOL
Company: Interventional Pain Management
Company: Intl Crescent Ltd.
Company: Intrepid Group Limited
Company: Invatamant Superior
Company: Invemed
Company: Inveniam
Company: Invensys Plc
Company: Inversiones, Inc.
Company: Invesco AIM
Company: Investment Science Asset Management Pty Ltd
Company: Investure
Company: Invus Financial Advisors
Company: IOM
Company: Iowa Division of Criminal Investigation
Company: IPKeys Technologies, LLC
Company: IPM AB
Company: IPMServ
Company: IPS Advisory, Inc.
Company: IR Sources, Inc.
Company: IR Weinbraub
Company: Iron Point Capital Management
Company: IronBridge Capital Management
Company: Ironwood Investment Counsel, LLC
Company: Ironworks Capital
Company: IS Corporate
Company: IS Corporate
Company: IS Corporate
Company: IS Corporate
Company: IS Corporate
Company: IS Corporate
Company: IS Corporate
Company: IS Corporate
Company: ISBC
Company: Islamabad Policy Research Institute
Company: Island Capital Management, LLC
Company: ISPSW
Company: Israel Aerospace Industries
Company: Israel Aerospace Industries Ltd
Company: Isurus Capital Management LLP
Company: IT army
Company: ITT Aerospace and Communications
Company: ITT Corporation
Company: Ivy Tech State College
Company: Izzle Networks
Company: J & B Ventures, Inc.
Company: J RANDALL FARRAR MD
Company: J WOODWARD NELSON & ASSOCIATES, CONSULTANTS
Company: J. L. Benacci Ventures
Company: J. Wood Television Production
Company: J.O. Alvarez Inc.
Company: J.T. Parker Associates, Inc.
Company: JAARS Inc.
Company: jack chivers realty
Company: Jacobs
Company: Jacobs Consultancy Inc.
Company: JAH Consulting
Company: JAH Consulting
Company: Jalapeno Corporation
Company: james alexander fine gardens llc
Company: James Raymond
Company: JANA Partners, LLC
Company: Janus Executive Services
Company: Janus Solutions
Company: Janusian Security Risk Management Ltd
Company: Japan Center for International Finance
Company: JAPCC
Company: Japs-Olson Company
Company: Jarin Ltd
Company: JAS Global Investments LLC
Company: JAS Global Investments, LLC
Company: JAYFEL Associates
Company: Jaypee Capital Services
Company: JB Drax
Company: Jebsen Management AS
Company: Jefferies
Company: Jefferies & Company
Company: Jeffers Ltd
Company: Jefferson Institute
Company: Jefferson Waterman International
Company: Jennifer Richmond Comps
Company: Jennings Capital
Company: Jensen Construction, Inc.
Company: Jera servcices
Company: Jerry Brown’s Boat Service
Company: JETRO London
Company: JETRO London
Company: Jewish Community Association of Austin
Company: Jewish Institute for National Security Affairs
Company: JFH-MS ANG
Company: JGC Corporation
Company: JGC Corporation
Company: JHL Capital Group LLC
Company: JLG Industries
Company: JM Advisors, LLC
Company: JMP Consulting
Company: john c eklof LLC
Company: John C. Lincoln Health Network
Company: John D. Svirsky Inc.
Company: John Pavel, DDS-INTEGRATIVE ORAL&MAXILLOFACIAL SRGY
Company: John S. Appel and Associates, Inc.
Company: John S. Landrum Interests
Company: John W. Brooker & Co.
Company: Johns Hopkins University Applied Physics Lab
Company: Johnson Management Group, Inc.
Company: Johnson Rice & Co
Company: JOHTAN
Company: JOHTAN
Company: Jones Day
Company: jonescarroll
Company: JonesTrading
Company: Joy Productions
Company: JP Consulting
Company: JP Morgan
Company: JP Morgan
Company: JP Morgan
Company: JP MORGAN
Company: JP Morgan Chase & Co.
Company: JP Oglesby & Associates, Inc.
Company: JPayne Mortgage
Company: JRG Law
Company: judicial recovery systems
Company: Jumbert
Company: Junipero group LLC
Company: Jupiter Asset Management
Company: K&A Shardlow Pty Ltd
Company: Ka mgt and Mkt consultants
Company: Kaisere
Company: kaizen capital
Company: Kalbian Hagerty LLP
Company: Kaleb Resources LLC
Company: Kallpa Asset Management
Company: KAM
Company: Kanaanlawfirm
Company: Kanos Capital Management, LLC
Company: Kardiologicke centrum MUDr. Janky Skrobakove s.r.o.
Company: KASHMERE VENTURES, LLC
Company: kathy@kenngeorge.com
Company: Kay Investments Inc.
Company: KBR
Company: KBR
Company: KBR
Company: KBR
Company: KBR
Company: KBR
Company: KBR
Company: KBR
Company: KBR
Company: KBR
Company: KBR
Company: KBR – 65203
Company: kcbox
Company: keiser & Associates
Company: Kelford Capital
Company: Kellbgg Brown and Root
Company: Keller Group
Company: Kelly Services
Company: Kemnay Advisory Services
Company: Kenfield Capital Strategies
Company: Kenneth A. Ziskin Law Corp
Company: Kenneth Frenke & Co.
Company: KenPeek Enterprises
Company: Kensington Investment Group
Company: Kent School
Company: kentwood associates
Company: KERRY J. BLAIN, INC.
Company: Kesar Terminals & Infrastructure Ltd
Company: Ketchum
Company: Key Private Bank KUI
Company: KFPC(Pty)Ltd
Company: KG Solutions, Inc.
Company: KHennesseyAssociates
Company: Kiawah Development Partners
Company: KIDA
Company: KIERS & CO
Company: Killer Admins, Inc.
Company: Kinder Family LImited Partnership
Company: Kinder Morgan
Company: Kinetic Concepts, Inc. (KCI)
Company: KING INVESTMENT ADVISORS
Company: King’s College London
Company: Kinnett Capital
Company: Kinross Gold
Company: KIO
Company: Kiraca Group
Company: Kirton & McConkie
Company: Kite Lake Capital Management (UK) LLP
Company: Kitt McCord Associates
Company: KJS P/L
Company: Knight Advisors
Company: Knight Equity Markets
Company: Knights of Columbus
Company: Knights of Columbus
Company: Knights of Columbus
Company: Knights of Columbus
Company: KNO
Company: Knoll Capital Management
Company: Knowledge Trading Pty Ltd
Company: Koch Asset Management
Company: Kola Science Center Norway/Mira Consulting
Company: Korea IT Times
Company: Korean Mission to the UN
Company: korti
Company: kp partners
Company: KPMG
Company: Kroger Pharmacy
Company: Kroll, Inc.
Company: Kronos
Company: Kruck Consulting, LLC
Company: Krueger Asset Management, Ltd
Company: KS DANISMANLIK VE GUVENLIK LTD
Company: KTF
Company: Kurke & Associates, inc.
Company: L A Motley LLC
Company: L A R Enterprises
Company: L T Mlcoch, Inc.
Company: L-3 Communications
Company: L-3 Communications
Company: L-3 Communications
Company: L-3 Communications MPRI
Company: L. G. Sucsy & Co. Inc.
Company: L3 Com/MPRI
Company: La Follette Associates
Company: LA Times
Company: LABOVITZ
Company: Labrador Capital. LLC
Company: LAC Consultants Corp
Company: Lake Cook Investment Corp.
Company: Lake Forest (IL) Police Department
Company: Lancaster Capital Management
Company: landspitali-university hospital of iceland
Company: Lanham O’Dell & Company
Company: LanRunner
Company: Lansdowne Partners
Company: Lansdownepartners.com
Company: Lantern Security
Company: Lap Dance Diet, LLC
Company: LaPacifica Publications
Company: Lapin & Davis, LLP
Company: LARRY HUSTON STUDIO
Company: Larry T. Lanning Services Company
Company: Las Vegas Chamber of Commerce
Company: Las Vegas Development Associates., LLC
Company: Lasercom
Company: Latent S.E.A. LLC
Company: Lattice Semiconductor Corp
Company: Laurel Knoll Farm, LLC
Company: Laurel Lodge Enterprises, Inc.
Company: Law Firm
Company: Law Office of Patrick J. Massari
Company: Law Offices of Jane A. Clark
Company: LAW OFFICES OF JIM BLAIR
Company: Law Offices of Wendy L. Rome
Company: LB Trailer Sales
Company: LDB & Assoc.
Company: Lee Ault & Company
Company: Lee Financial
Company: LEEDS HOLDINGS S/E, INC
Company: Leeds University
Company: Leeston Medical
Company: Leeway Transportation Inc.
Company: Lefebure Brothers
Company: Legion Lighting Co., Inc.
Company: Lehigh Univesity – Investment Office
Company: Lehman Brothers
Company: Let Freedom Ring
Company: Letaw Associates
Company: Lewis-Pipgras, Inc.
Company: Lexmark Internacional S de R.L. de C.V.
Company: Lexmark International, Inc.
Company: Lextek International
Company: LGT Investment Management (Asia) Ltd.
Company: LHC llc
Company: Libre Consturction
Company: lider and fogarty
Company: Lifechangers, Inc.
Company: Lighthouse for the Blind
Company: Lighthouse Information Systems, Inc.
Company: Lighthouse Investment Group LLC
Company: Limitless LLC
Company: Lincoln Group
Company: LIONCLAD
Company: Lionscrest Capital Ltd
Company: Lisa Chakrabarti, Fine Artist
Company: Litigation Research
Company: Live Oak Systems
Company: LJT Inc
Company: LL
Company: Locke Financial Services, Inc.
Company: Lockheed Martin
Company: Lockheed Martin
Company: Lockheed Martin
Company: Lockheed Martin
Company: Lockheed Martin
Company: Lockheed Martin
Company: Lockheed Martin
Company: Lockheed Martin
Company: Lockheed Martin
Company: Lockheed Martin
Company: Lockheed Martin
Company: Lockheed Martin – ISO
Company: Lockheed Martin Corporation
Company: Lockheed Martin Investment Company
Company: Locus Pharmaceuticals, Inc.
Company: Logic Fund Management Limited
Company: Lohengrin Group
Company: Loma Linda University
Company: Lone Star Ventures
Company: Lone Star Ventures
Company: Lonely Planet Publications
Company: Long Investment Advisory, Inc.
Company: Longhorn Capital Partners LP
Company: loop capital
Company: Loqtus Enterprises
Company: Lord, Abbett & Co. LLC
Company: Lorence & Vander Zwart
Company: Lorimax Investigations
Company: Los Alamos National Laboratory
Company: Los Alamos National Laboratory
Company: Los Angeles Times
Company: LostChord.Org
Company: Louis Berger Group, Inc
Company: Lourido Capital, S.L.
Company: Love Services Pty Ltd
Company: Lowell International Company
Company: Lowry Hill
Company: LPL
Company: LRQA Ltd
Company: LST Prudential Limited.
Company: LTAstrology
Company: Luanne InfoSearcy
Company: Lubrizol
Company: Lucas Capital Advisors, LLC
Company: Lundin Sudan Limited
Company: Lusman Capital Management
Company: Lustig & Associates, P.A.
Company: Lux Capital
Company: LVM Capital Management, Ltd.
Company: Lyman Ward Military Academy
Company: lynchris holdings inc.
Company: Lynn Clough Portraits
Company: LyondellBasell – Houston Refining
Company: Lyric Opera of Chicago
Company: M. Lukic & Associates Insurance Brokers LTD.
Company: m.glosser&sons inc
Company: M2 Solids LC
Company: M3G Capital
Company: M6 Concrete Accessories
Company: MacDougall, MacDougall, MacTier
Company: MacKenzie Financial
Company: MacLeod International
Company: Macquarie
Company: macquarie bank
Company: Madacovi Ltd
Company: Madden Asset Management
Company: Maersk Line, Limited
Company: Magnitude Capital
Company: Magog Holdings Limited
Company: Mainichi Shimbun
Company: Mainsail Asset Mgmt
Company: Maitland-Carter Properties, Co.
Company: Makena Capital Management
Company: maliban sal
Company: Malmgren Global
Company: management services
Company: Manas Publications
Company: Manitowoc
Company: manley asset managemeny
Company: Manning Navcomp, Inc.
Company: Manro Haydan Trading
Company: Manulife Financial
Company: Maranatha Group LLC
Company: MAREX Financial Limited
Company: Marine Corps
Company: Marinette Marine Corporation
Company: Market-Tek Enterprises, Inc.
Company: Markit
Company: Marsh USA Inc.
Company: Marsh, Inc.
Company: Marshfield Associates
Company: Martin Capital
Company: Martingale Systems
Company: Martronics Corporation
Company: Marvin & Palmer Associates, Inc.
Company: MAS
Company: Mason County Fire District # 2
Company: Mass. Trial Court
Company: master asset management
Company: MasterCard
Company: Matt Management Co.
Company: Matteson-Hudson Construction Company
Company: Mawarid Holding Company
Company: Max Recovery
Company: Mc Guinness & assoc.
Company: McCaffrey and Company International
Company: McCormick & Company, Inc.
Company: McCormick Tribune Foundation
Company: McDep LLC
Company: MCG
Company: McGlinchey Stafford
Company: McGrew Enteprises
Company: McIntosh Enterprises
Company: McKinsey
Company: McQuilling Services, LLC
Company: McSafetySolutions, LLC
Company: MD
Company: MDA
Company: MDOG
Company: MDRI
Company: MDW Investments
Company: Mead OBrien Inc.
Company: MeadWestvaco
Company: Med-Link Staffing, Inc.
Company: MedExpress Companies
Company: Mediabiz International Inc.
Company: Medical Graphics Corporation
Company: Medway Capital
Company: Melberg Marketing
Company: mercuria
Company: Mercyhurst College
Company: Merrill Lynch
Company: Merrill Lynch
Company: Merrill Lynch
Company: Merrill Lynch
Company: Merrill Lynch
Company: Merrill Lynch
Company: Merrill Lynch
Company: Merrill Lynch
Company: Merrill Lynch
Company: Merrill Lynch
Company: Merrill Lynch
Company: Mesa Police Department
Company: mesirow financial
Company: MetaCarta
Company: metis consulting
Company: METKA
Company: Metro-North Railroad
Company: Mexican Navy
Company: Meximerica Media Inc
Company: MF Global
Company: MF Global
Company: MF Publishing
Company: MFC Global Investment Management
Company: MFK Bank
Company: MGS Group
Company: Miami University
Company: Miami-Dade College
Company: Michael J. Poff lcsw pa
Company: Michael V. Fewell & Assoc., Inc.
Company: Michigan State University
Company: Mick Geary Production
Company: Microsoft
Company: Microsoft
Company: Microsoft
Company: Microsoft
Company: Microsoft
Company: Microsoft
Company: Microsoft
Company: Microsoft
Company: Microsoft Corporation
Company: Microsoft Corporation
Company: Middle East Access
Company: Middle East Facilitations Executive
Company: Middle East Observatory
Company: MIGROS TICARET AS
Company: MilePro LLC
Company: Military
Company: Military Personnel
Company: Millardair
Company: Miller Investment Management
Company: MILNEWS.ca – Military News for Canadians
Company: Min Pin Rescue
Company: Minining Interactive Corp.
Company: Ministry of Defence – Singapore (Library)
Company: Ministry of Defense
Company: Ministry of Economic Affairs
Company: Ministry of External Relations
Company: Ministry of Foreign Affairs & International Trade
Company: Ministry of Foreign Affairs and Emigrants, BOUSTROS Palace
Company: Ministry of the Economy & Foreign Trade
Company: mintzlaff design, inc.
Company: Mipod Nuclear
Company: MIR Corporation
Company: Miracle of the Rosary Mission, Inc.
Company: Miravisa S.A.
Company: Mission Advisors
Company: Mission Leader
Company: Mission of Lithuania to UN
Company: Missouri State Employees’s Retirement System
Company: MitonOptimal Limited
Company: Mitsubishi UFJ Securities
Company: MJWW
Company: MJWW
Company: Mliven
Company: MLSK Associates LLC
Company: MLTDesign
Company: Mobile Reasoning, Inc.
Company: MoD
Company: Modern Transport Systems Corp.
Company: Mody Pumps Inc.
Company: MOHAMMED JALAL & SONS
Company: Molinos Azteca SA de CV
Company: Monarch Machinery, Inc.
Company: Monitor Group
Company: Monroe & Associates
Company: Monsanto
Company: Monsanto Company
Company: Montesino
Company: montgomery goodwin investments
Company: montgomery goodwin investments
Company: Monthly $19.95
Company: Monthly $19.95
Company: Moody’s Corporation
Company: Moog Inc.
Company: Moore Consultant
Company: MoPress
Company: Moray Holdings Ltd
Company: morgan keegan
Company: Morgan Keegan
Company: Morgan Stanely
Company: morgan stanley
Company: Morgan Stanley
Company: Morgan Stanley
Company: Morgan Stanley
Company: Morgan Stanley
Company: Morgan Stanley
Company: Morgan Stanley
Company: Morgan Stanley
Company: Morgan Stanley
Company: Morgan Stanley
Company: Morgan Stanley
Company: Morgan Stanley
Company: Morgan Stanley
Company: Morgan Stanley
Company: MORGAN STANLEY
Company: morganstanley
Company: Morningstar
Company: Morris Communications
Company: Morrison Company
Company: Morrison Cohen LLC
Company: Morse Wealth Management, LLC
Company: Mortgage Loan Specialists
Company: Morty\’s Cabin Inc
Company: Moscow State University Science Park
Company: Moseley Law
Company: Moss
Company: Mostly, Inc.
Company: Mota Motors
Company: Motorola, Inc.
Company: Motorola, Inc.
Company: Mott Corporation
Company: Mount Lucas Management
Company: Mount Pleasant Baptist Church
Company: Mountain Dreams
Company: Mountain Pacific Group, LLC
Company: Mountain Travel Sobek
Company: Mountain Vines Cellars LLC
Company: Mountaire, Inc
Company: Mowery @ Schoenfeld
Company: Mowery Capital Management
Company: mp4 Aviation Security LLC
Company: MPRI
Company: MQP
Company: MRM Capital
Company: MS Designs
Company: MSA
Company: MSF – OCG
Company: MSIA
Company: msnbc
Company: Mueller Water
Company: Mulberry Street Family Dentistry
Company: Murphy Companies
Company: My Test Company
Company: Myers Center for the Eye
Company: N W Altemus & Co.
Company: n. d. pitman & company, inc.
Company: n/a
Company: n/a
Company: n/a
Company: n/a
Company: N/A
Company: N/A
Company: N/A
Company: N/A
Company: N/A
Company: N/A
Company: N/A
Company: N/A
Company: na
Company: na
Company: NA
Company: NA
Company: NA
Company: NA
Company: NAFTA GAS CONSULTING AUSTRALIA Pty. Ltd.
Company: Nagant Communications
Company: Nancy A. Socha & Associates, LLC
Company: Naples Council on World Affairs
Company: NARF
Company: NAS
Company: NASA
Company: Nathan Lane Associates
Company: National Assembly of Republic of Korea
Company: National Australia Bank
Company: National Bank of Romania
Company: National Bank of Romania
Company: National Center for Intelligence & Counter-Terrorism
Company: national chengchi university
Company: National City Corporation
Company: National Commercial Bank
Company: National Democratic Institute
Company: National Instruments
Company: National Journal
Company: National Oilwell varco
Company: National Oilwell Varco
Company: National Oilwell Varco
Company: National Oilwell Varco
Company: National Oilwell Varco
Company: National Security Corresponden
Company: National War College
Company: Natixis Alternative Investments (US), Inc.
Company: natl. bond &trust
Company: NATO
Company: Naval Criminal Investigative Service
Company: Naval History & Heritage Command
Company: Navigators
Company: Navy
Company: NBC News
Company: nbcnews
Company: NCH Corp.
Company: NCMC
Company: NCMEC
Company: Neat Communications
Company: Nelson Associates
Company: Neo Dimension
Company: nestle
Company: Net Results Group
Company: NetCom Solutions
Company: Netherlands Armed Forces
Company: NetJets International
Company: NetJets, Inc.
Company: Neuberger Berman
Company: Neuberger Berman
Company: Neuberger Berman
Company: Neumeier Consulting, Inc
Company: New Dominion LC
Company: New England Financial
Company: New Hope Partners, LLC
Company: New Mountain Capitol
Company: New Orleans Private Patrol
Company: New Tribes Mission
Company: New Tribes Mission
Company: New West Investment Management, Inc.
Company: New York Marriott Marquis
Company: New York State Police
Company: New Zealand Dept of the Prime Minister & Cabinet
Company: New Zealand Fire Service
Company: New Zealand Fire Service
Company: New Zealand Police, Wellington District
Company: Newmont Mining Corporation
Company: Newmont Mining Corporation
Company: Newmont South America
Company: Nexant Inc.
Company: nexen petroleum usa
Company: Nexstore Investments
Company: NextChem PTY LTD
Company: NF Wealth Management
Company: ng
Company: NI
Company: NIELSEN WURSTER GROUP
Company: Nigerian Agip Oil Company
Company: Nigerian Airforce
Company: Nike, Inc.
Company: nil
Company: NIL
Company: NJ-TF1 / EAOEM
Company: NMHG
Company: NMKK Holdings
Company: NMU
Company: No Company Name
Company: Noble Rogue Consulting
Company: Noblegene Development
Company: Nomads Aus Pty Ltd
Company: Nomura
Company: Nomura
Company: Nomura International
Company: Non profit Orgnization
Company: none
Company: none
Company: none
Company: none
Company: none
Company: none
Company: none
Company: none
Company: none
Company: none
Company: None
Company: None
Company: None
Company: None
Company: None
Company: None
Company: None
Company: None
Company: NONE
Company: Noonan Trading LLC
Company: Noram Management
Company: Nordic American Group
Company: Nordile Holdings Ltd.
Company: Nordstrom
Company: Norm Portner Consulting
Company: North American Energy Credit and Clearing Corp
Company: north phoenix anesthesiologists, ltd
Company: Northern Forum
Company: Northern Gulf institute
Company: Northern Leasing Systems, Inc.
Company: Northern Trust
Company: Northern Trust, NA
Company: Northfield Glass Group Ltd.
Company: Northrop Grumman
Company: Northrop Grumman
Company: Northrop Grumman
Company: Northrop Grumman Coroporation, Aerospace Sector
Company: Northrop Grumman Intl.
Company: Northrop Grumman IT
Company: NorthStar Nuclear Medicine, LLC
Company: Northwest Airlines
Company: Northwestern University
Company: Norvest,Inc
Company: not applicable
Company: Not Applicable
Company: Not Applicable
Company: notify gptaylor20@gmail.com for renewal 512-966-0299
Company: Novero County / HIDTA
Company: NPR
Company: NRCan
Company: NS Fields
Company: NTAsset
Company: NTMA
Company: NTX Resources
Company: Nucleus Global Investors
Company: Null Pointer Solutions
Company: Nustar Energy LP
Company: NVS
Company: NYCHESSKIDS
Company: Nye Lubricants, Inc.
Company: NYPD
Company: NYPD
Company: NYPSC
Company: NYSP
Company: O’Brien’s Response Management Inc
Company: O’Melveny & Myers LLP
Company: Oak Ridge Strategy Group
Company: Oak Springs Partners
Company: Oakhurst Consulting
Company: OAM
Company: Oasis Petroleum
Company: Oasis Security Solutions
Company: Oberrauch Advisory
Company: Objective Consulting, Inc.
Company: OBS24 Security Services Ltd
Company: OC International
Company: OC International
Company: OC International
Company: Occidental Oil and Gas Corporation
Company: Occidental Oil and Gas Corporation
Company: Occidental Petroleum
Company: Ocean Park Advisors
Company: Ocelot Developments Pty Ltd
Company: Ochoco Armory
Company: OCI
Company: octcs
Company: Odentrading llc
Company: OER, Inc.
Company: OETA – The Oklahoma Network
Company: Off Road Equipment Parts Inc
Company: Office of Hon Joel Fitzgibbon MP, Minister for Defence
Company: Office of the Asia Pacific Advisor
Company: Ogden Asset Management
Company: Ogilvy & Mather Advertising
Company: OI Ventures
Company: Old Saw Mill Investments Inc
Company: Olive International
Company: Oliver Wyman – Delta Organization & Leadership
Company: Omaha Public Power District
Company: OMICRON electronics GmbH
Company: Omniplan
Company: Omniture
Company: on24, Inc.
Company: One Stone Productions, Ltd.
Company: OneBeacon Insurance
Company: ontourgroup
Company: ONUG Communications, Inc.
Company: Onyx Capital
Company: Operadora de Personal Tecnico, SA de CV
Company: Operations and Safety Solutions, LLC
Company: Oppenheimer & Co, Inc
Company: oppenheimer and co
Company: oppenheimer&co.inc.
Company: OppenheimerFunds
Company: OpTech
Company: Optimal Wealth & Investments, Inc.
Company: Optiver Holding BV
Company: Oracle
Company: Orange Light
Company: Orbis Capital Inc.
Company: Orbital Research Inc.
Company: Oregon Custom Homes
Company: Oregon HIDTA Fusion Center
Company: Orkla ASA
Company: Oryx
Company: OSET GREGOR – DETEKTIV
Company: Ostend Tennis Club
Company: Ottawa International Airport
Company: Out of Office Films
Company: Ove Arup and Partners, P.C.
Company: Oxberr Risk Strategies
Company: Oxford
Company: Oyu Tolgoi LLC (Rio Tinto)
Company: PACES,LLC
Company: pacific real properties
Company: Pacific Wealth Creators Ltd
Company: Palacio y Asociados
Company: Paladin Associates
Company: paladin strategy partners LLC
Company: PALL
Company: palm beach family physicians
Company: Palo Verde Group
Company: Palos capital corp.
Company: Pan Optic
Company: Paper Fibers International, Inc.
Company: Pappas Consulting, LLC
Company: Paracelsus Clinic of Washington
Company: Paramount Strategic Advocacy, Inc
Company: Parker Hannifin
Company: Parliament
Company: Parmi les retraitÈs
Company: Parr Johnston Consultants
Company: Parsons Corporation
Company: Parthenon Futures Management, LLC
Company: Pat Flynn for U. S. Senate
Company: Pathmark
Company: Patriot Tours, Inc.
Company: Patronus Analytical
Company: Paul Comstock Partners
Company: Paul Davis Restoration
Company: Paul E. Morris, M.D.
Company: Pauling Advisors Limited
Company: Pave & Bogaards
Company: Pay By Touch
Company: Payden & Rygel
Company: PDF Solutions, Inc.
Company: peak financial advisors
Company: Pecks Management Partners Ltd
Company: Pellerin Milnor
Company: Peninsula Goldfields Pty Ltd
Company: Penn Davis McFarland, Inc.
Company: Pennsylvania Trust Co.
Company: Pentarch Forest Products
Company: Performance Capital Services, LLC.
Company: Perimeter Capital Management
Company: Periodico Reforma
Company: Perkins Coie LLP
Company: Perot Systems
Company: Perot Systems Corporation
Company: Personal
Company: Personal Financial Advisors, Inc.
Company: Personal Safety Training Group
Company: Personal Use
Company: Personal Use
Company: Peruvian Defence Ministry
Company: Peter Payne Limited
Company: Peter R. Mack & Co., Inc.
Company: PETERCAM
Company: PetMol Development
Company: Petro Summit Investments UK Ltd
Company: Petro-Canada
Company: Petrobras
Company: Petrobras EnergÌa
Company: Petroleum Advisory Forum
Company: Petroleum Database Services
Company: PetroStar Associates
Company: Pfizer Venezuela, S.A.
Company: Pfizer, Inc
Company: Pfizer, Inc.
Company: PFPA
Company: PGR
Company: Phado BVBA
Company: Phibro LLC
Company: PHIDIPPIDES CAPITAL
Company: PhilanthroCorp
Company: Philippine Daily Inquirer
Company: Philips
Company: Phillips & Associates, Inc.
Company: Phillips Security Consulting
Company: PIFHelp
Company: Pinkerton Consulting & Investigations
Company: Pinnacle Northwest Financial, LLC
Company: Pinon PC Support
Company: Pioneer Investments Austria
Company: Pioneer Natural Resources
Company: Pioneer Natural Resources
Company: Piper Jaffray
Company: Piper Jaffray
Company: Pivot International
Company: PJ
Company: PJTV
Company: PK Enterprises
Company: Placements Gilles Landry Inc.
Company: plainfield financial group
Company: Plano ISD
Company: Plansmith
Company: Plaskolite
Company: Platinum Asset Management
Company: Playboy Enterprises
Company: Pletcher Consulting LLC
Company: Plum Cor
Company: Plumb Performance Portfolio
Company: Plus Capital Ltd.
Company: PMF
Company: PMP Solutions
Company: PNM
Company: Polar Capital Partners
Company: Polaris Management Assistance Consultancy
Company: POLESTAR MGT
Company: Polio Eradication Initiative, WHO
Company: Porter Capital Management
Company: Porter Orlin LLC
Company: Portola Valley Consulting Group
Company: Portuguese Navy
Company: Post Advisory Group
Company: Post Road Capital Management, LLC
Company: Potomac Associates
Company: Potomac Fusion, Inc.
Company: Potomac Institute for Policy Studies
Company: Poudre Schools
Company: PQI Netherlands
Company: Practical Management
Company: Praemittias Group, Inc.
Company: Praesidium Security Group
Company: Prairie Pacific Corp
Company: pras tecnica edilizia srl
Company: Pratt Foundation
Company: Prediction Company
Company: Premier BPO Inc
Company: premium team Handel & Marketing e.U.
Company: premium team Handel & Marketing e.U.
Company: Prenax
Company: Presbyterian Church USA
Company: Presbyterian Record Inc.
Company: Presidio Group
Company: Pressnet ( Aust ) Pty Ltd
Company: Pretty Good Consulting
Company: Prevail Health Consultancy
Company: Price
Company: Price Resources LLC
Company: PricewaterhouseCoopers, LLP
Company: Primary Action Inc
Company: Prime International Trading
Company: PrimeSolutions Investment Advisors
Company: Primet Precision Materials Inc.
Company: Primm Investment Inc.
Company: Primrose Drilling Ventures.com
Company: Prince George’s Community College
Company: Princeton American Corp
Company: Principal Financial Group
Company: Pripol Pty Ltd
Company: private
Company: private
Company: Private
Company: Private
Company: Privy Council Office Canada
Company: Privy Council Office Canada
Company: Priwer & Company
Company: PRO Intelligence
Company: Production Intercom IOnc.
Company: Professional Insight
Company: Profitable Company
Company: ProfitScore Capital Management, Inc.
Company: Project Services Intl LLC
Company: Prometheus Asset Management
Company: Promineon, Inc
Company: Promontory Interfinancial
Company: Property Council of Australia
Company: Property Tax Experts, Inc.
Company: Prophecy Consulting Group
Company: Proskauer Rose LLP
Company: Prototek Corp
Company: Prtichard Capital
Company: Prudential
Company: PSAM LLC
Company: PSI
Company: PSK Management, Inc.
Company: Pubco Corporation
Company: Public gas Corporation of Greece
Company: Public Sector Pension Investment Board
Company: PUC Minas
Company: puc-rio
Company: Pull-A-Part
Company: Pumpkin Patch
Company: Purdue University CERIAS
Company: Putnam Lieb
Company: PWC Logisitics
Company: PYPE, INC.
Company: Qatar Financial Centre Authority
Company: Qintar Technologies, Inc.
Company: Qualcomm
Company: QUALITY PLUS INC
Company: Quantum Capital Management, LLC
Company: Quantum North Inc.
Company: Quest
Company: QuintilesTransnational Corp
Company: Quivus Systems
Company: R D Grant Investments
Company: R.S. Precision Ind’s Inc.
Company: Rafael A. Perez, P.A.
Company: Ragen MacKenzie Incorporated
Company: rail logistics
Company: RAINSTONE
Company: RAMMA Consulting, Inc.
Company: RAN Science & Technology, LLC
Company: Rand Merchant Bank
Company: rarer enterprises
Company: Raven Global Security, Inc.
Company: Ray Wave Investments Inc
Company: RAYA Spa
Company: raymond james
Company: Raymond James
Company: Raymond James
Company: Raymond James
Company: raymond james & associates
Company: Raymond James & Associates
Company: Raymond James & Associates
Company: Raymond James & Associates
Company: Raymond James & Associates, Inc.
Company: Raymond James 416-7774983
Company: Raytheon
Company: Raytheon
Company: Raytheon
Company: Raytheon
Company: Raytheon Company
Company: Raytheon Company
Company: Raytheon Company
Company: Raytheon Company
Company: Raytheon Company
Company: Raytheon Company
Company: Raytheon Company
Company: Raytheon Company
Company: Raytheon Company
Company: Raytheon Company
Company: RBC
Company: RBC Attn Doug Vicic
Company: RBC Capital Markets
Company: RBC Dain Rauscher, Inc.
Company: rbc dominion securities
Company: RBC Dominion Securities
Company: RBC Dominion Securities
Company: RBC Dominion Securities
Company: RBC Dominion Securities
Company: RBC Dominion Securities
Company: RBC Dominion Securities
Company: RBC Dominion Securities
Company: RBC Dominion Securities
Company: RBC Dominion Securities
Company: rbc wealth management
Company: RBC wealth Management
Company: RBC Wealth Management
Company: RBC Wealth Management
Company: RBS
Company: RC CONTRACTORS
Company: RCMP
Company: RCMP
Company: REAL ESTATE ASSOC.
Company: Real Estats
Company: Recreational Holdings
Company: Red Flag Investigations
Company: RED MTG CAP INC
Company: Redondo & Asociados Public Affairs FIrm
Company: Redwood Day School
Company: Redwood Trust
Company: redzone athletics
Company: Reel Boss Enterprises
Company: Reflex Response Management
Company: REFLEXIONS, Inc.
Company: Refratechnik Cement GmbH
Company: Refresh Waters Queensland Pty Ltd.
Company: Refugee Review Tribunal
Company: REHAB ORTHO
Company: Remgro Ltd
Company: Renaissance Capital
Company: Renaissance Insurance
Company: renaissance media group, inc.
Company: Reperi LLC
Company: Resort Masters International
Company: Resource America, Inc.
Company: Resource Consultants S.A.
Company: Restricted Access Ltd
Company: Result Group GmbH
Company: retired
Company: retired
Company: retired
Company: retired
Company: retired
Company: retired
Company: retired
Company: retired
Company: retired
Company: retired
Company: retired
Company: retired
Company: retired
Company: retired
Company: retired
Company: retired
Company: retired
Company: retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: Retired
Company: RETIRED
Company: Retired — US Navy
Company: Retired Govt Official
Company: Retired military
Company: Retired Teacher
Company: Retired USAF
Company: retired/CIA
Company: Retirement Counselors, Inc.
Company: Rezidor Hotel Group
Company: RFE-RL, Inc.
Company: RFG
Company: RFK Consultants Ltd
Company: RHL
Company: RHP Consultants to Management
Company: Rice Medical Associates
Company: RICE University
Company: Rich Guard & Associates
Company: Richeberg International
Company: Rim Rock Capital
Company: Rimrock Capital Management, LLC
Company: Rimrock Capital Management, LLC
Company: Rimrock Capital Management, LLC
Company: Rio Tinto London Ltd
Company: riskmat futures ltd
Company: Rivanna Capital, LLC
Company: Rivendel Consultants
Company: Riverford Partners LLC
Company: Riverside Realty Inc.
Company: Riviera Pools & Spas
Company: RKZ Mgmt.
Company: RLR Resources
Company: RMG
Company: RMI Consultants Inc.
Company: Robert Adams, CPA
Company: Robert Bosch Mexico
Company: Robert E. Greenstein Attorney at Law
Company: Robert Fox
Company: Robert Justich Bear.com
Company: Robert Justich Bear.com
Company: Robert R. Anthony M.D. PC
Company: Robert Schuman Foundation
Company: Robert W. Baird
Company: Roberts Group
Company: Robinson Financial
Company: Robinson Koerner International, Inc
Company: Roby Solutions
Company: Rockefeller & Co., Inc.
Company: Rockefeller Foundation
Company: Rockingham Capital Advisors LLC
Company: Rockwell Automation
Company: Rockwell Automation, Inc.
Company: Rockwell Collins
Company: ROCKY MOUNT PSYCHOLOGICAL SERVICES
Company: Rocky Mountain College – President’s Office
Company: Rogue Expeditions, Inc.
Company: Rohan LLP
Company: Rohm and Haas Company
Company: Rolls-Royce Corporation
Company: Roosevelt Institute
Company: Rose Super Fund
Company: Rosendin Electric, Inc.
Company: Rosewood Corporation
Company: Ross Group, Inc.
Company: Rothbuilt Ltd. Co
Company: Roundtree Automotive Group
Company: Royal Bank of Scotland
Company: Royal LePage
Company: Royal Ministry of Foreign Affairs
Company: Royal Ministry of Foreign Affairs
Company: Royal Ministry of Foreign Affairs
Company: Royal Ministry of Foreign Affairs
Company: Royal Ministry of Foreign Affairs
Company: RPM Energy
Company: RPSA
Company: RPX Corporation
Company: RREEF
Company: RTG & Associates, Inc.
Company: RTI International
Company: RTW LONDON LTD
Company: Rub Music
Company: Russell
Company: Russell Investments
Company: Russian Insight Ltd
Company: rvcintl
Company: RWTH Aachen University
Company: Rx2000 Institute
Company: Ryerson, Inc.
Company: S & P Financial Services Inc.
Company: S. T. Crone, Ltd
Company: S.A.Baker & Associates
Company: S.O.C.-S.M.G.
Company: s.s.corporation
Company: S„o Paulo School of Politics and Sociology
Company: S&R Consulting Grioup
Company: S2A Security Group
Company: S3
Company: S4 Inc
Company: Saab North America
Company: saachnoff & weaver.ltd.
Company: Saber Ops
Company: SABIS Educational Systems Inc.
Company: Sabre International
Company: SACHEM
Company: Safecastle LLC
Company: Sage Advisory Services
Company: Sage Financial Advisors Inc.
Company: SAHE
Company: SAIC
Company: SAIC
Company: SAIC
Company: SAIC, Inc.
Company: SAIC, Inc.
Company: Saieco International Corp.
Company: SAIL
Company: Sailfish Capital Partners
Company: SAIMANI
Company: Saint Leo University
Company: Saito Consulting
Company: SAJBD
Company: Salget Solutions LLC
Company: salida capital
Company: SALOV North America Corp.
Company: SAM Capital Management LLC
Company: SAMCO
Company: Samson International Ltd.
Company: samsung electronics italia spa
Company: Samwoo Communications
Company: San Diego ADVenture
Company: San Jose
Company: San Juan Safe Communities Initiative, Inc.
Company: Sands Capital Mgmt
Company: Sandwell Engineering
Company: SANE Management LLC
Company: sanpalo investments corporation
Company: Santiam Ballistics
Company: Sapere Wealth Management
Company: Sapiens Movement Inc
Company: Sarasota County Fire Department
Company: Sardonyx International Ltd
Company: SAS
Company: Sasfin Bank
Company: SATORone
Company: Saturna Capital
Company: Satyam
Company: Saudi Arabia Embassy
Company: Saudi Aramco
Company: Saudi Defense Office
Company: Saunders Norval Nichols & Atkins
Company: Save the Children – Indonesia
Company: Sawinsky, Inc.
Company: Saxo Bank Schweiz AG
Company: Saye Capital Mgmt
Company: SBL
Company: SC JOHNSON & SON, INCE
Company: scanlan associates
Company: SCCI
Company: Schafer Resources, Inc.
Company: Schellenberg & Evers PC
Company: Schlindwein Associates, LLC
Company: schlumberger
Company: Schlumberger
Company: Schlumberger
Company: Schneider Electric
Company: schnitzius & vaughan
Company: Schroders
Company: Science Applications Int’l Corporation
Company: Sciens Capital
Company: SCMC
Company: Scotch College
Company: ScotiaMcLeod
Company: Scott & Stringfellow, Inc.
Company: Scott&Stringfellow, inc.
Company: Scottish Enterprise
Company: scottsdale
Company: SCTY INC
Company: Seabreeze Books & Charts
Company: seabulk tankers inc
Company: Seacor Marine (International) Ltd
Company: SEACORP Holdings
Company: SEALORD HOLDINGS
Company: Seant Pty Ltd
Company: SECO Manufacturing Company, Inc.
Company: Second Wind Inc
Company: Secure Ocean Service LLC
Company: Secured Perimeters, Inc.
Company: SecureGroup.org
Company: Securewest International
Company: Security Consulting Investigations, LLC
Company: Security Global Investors
Company: Security Konsultants Inc. of Nevada
Company: Security Solutions, Inc
Company: SecurityWorks
Company: sef
Company: SELEX Galileo Ltd
Company: self
Company: self
Company: self
Company: self
Company: self
Company: self
Company: self
Company: self
Company: self
Company: self
Company: self
Company: Self
Company: Self
Company: Self
Company: Self -employed
Company: self employed
Company: self employed
Company: self employed
Company: self employed
Company: self employed
Company: Self employed
Company: Self employed
Company: Self employed
Company: Self Employed
Company: Self Employed
Company: self-emp
Company: self-employed
Company: Seligman & Associates LLC
Company: SEMAR
Company: Senate of Canada
Company: Senda Inc
Company: Seneca Shore Wine Cellars
Company: Senior Resource Group, LLC
Company: Sentek Global
Company: Senter for Strategiske Studier as
Company: Sentinel Risk Management
Company: Septa Energy US Limited
Company: Sequoia North America
Company: serge wibaut sprl
Company: Serjical Strike Inc.
Company: Servicios Administrativos Penoles, SA de CV
Company: sesac, inc
Company: Seven Seas Trading, Inc.
Company: Sewell Realty Services
Company: SFA Inc.
Company: SFERS
Company: SG Hiscock and Co
Company: SGH Holdings, Inc.
Company: Sgtgrit.inc
Company: shaker’s
Company: Sharp Auto Parts
Company: Shea Ear Clinic
Company: Shell
Company: Shell
Company: Shell Chemical
Company: Shell Chemical Co.
Company: Shell International E&P
Company: Sherwin Alumina L.P.
Company: Shilpa Offshore, Inc
Company: Shodan Security
Company: Short Side Trading, LLC
Company: Shultz Investigations
Company: SICKLE CORP
Company: SIDERSA
Company: Siemens
Company: SIEVERT ELECTRIC SERVICE AND SALES
Company: SIG
Company: Sigillum GmbH
Company: Signature Consultants
Company: SignatureFD, LLC
Company: SIL International
Company: SIL International
Company: SIL International
Company: SIL International
Company: Silver Eagle Consulting, Inc.
Company: Silver Group, L.L.C.
Company: Simo Energy LLC
Company: Simon Hunt Strategic Services Ltd
Company: Simon International, LLC
Company: Singapore Press Holdings Library
Company: Singapore Press Holdings Library
Company: Singleton Electric, Inc.
Company: sip enterprise
Company: Sitrick and Company Inc.
Company: SJM
Company: SK Communications
Company: Skadden Arp
Company: Skoll Global Threats Fund
Company: skram cmr
Company: Slavic Gospel Association
Company: SLi
Company: SM&A
Company: Smadja & Associates
Company: Smardt Inc
Company: SMART BUCHAREST PARTNERS SRL
Company: SMB Media Group
Company: SMDudin Architects & Engineers
Company: SMEC International Ltd.
Company: smersh, inc
Company: smi
Company: Smith & Sawyer
Company: Smith Barney
Company: Smith Barney
Company: Smith Barney
Company: Smith Barney
Company: Smith Barney
Company: Smith Barney
Company: SNM Research, LLC
Company: Snodgrass plc
Company: Snohomish Dept of Emergency Mgt
Company: SOC
Company: SoftPath, Inc.
Company: SOG
Company: sole prop. rancher
Company: Solios Asset Management
Company: Solon Mack Capital
Company: SOLUCIONES INTERACTIVAS EN MM SA
Company: Soludrex Inc.
Company: SON Systems
Company: SONY
Company: Sony Music / BMG
Company: Sony Pictures Entertainment
Company: Soos Global Capital Advisors, LLC
Company: Sopher Consulting
Company: SOS Security Incorporated
Company: SOSi, Ltd.
Company: SOTT-I LLC
Company: Sound Carpentry
Company: South Texas Corpus Christi
Company: Southwest Aerotrekking Academy
Company: Southwest Airlines
Company: SouthWest Gas
Company: Southwest Properties
Company: Southwest Torque Tools, Inc.
Company: Span-O-Matic Inc.
Company: Sparkhill Global, LLC
Company: SparkPeople
Company: Spartacus Security
Company: Spectrum Asset Management, Inc.
Company: Spectrum Design West
Company: Spectrum Management Group, Inc.
Company: Spengler Trading, LLC
Company: Spot Trading L.L.C.
Company: Springbanc
Company: Squire, Sanders & Dempsey (US) LLP
Company: SRA International
Company: SRA International, Inc.
Company: SRC
Company: SRD Associates
Company: SRO Development LLC
Company: Sronehenge
Company: SRS Inc.
Company: SSgA
Company: SSI
Company: St Jude Medical
Company: St Jude Productions
Company: St. Andrews University (undergraduate student)
Company: St. Francis Hospital
Company: St. George Marketing, L.L.C.
Company: St. Mary’s University, School of Law
Company: Stallion Oilfield Services
Company: Stallion Oilfield Services
Company: Stand Up South Pacific
Company: Standard Bank
Company: Standard Chartered Bank
Company: Standish
Company: STANLEY H. FLORANCE CONSULTING
Company: STANLIB Asset Management
Company: Stanton Marketing Ltd.
Company: Staples Advantage Canada
Company: Star Point Star
Company: Star Quality
Company: Starbucks
Company: Starr Marine Agency, Inc.
Company: Starside Security & Investigation, Inc
Company: State Bar of California
Company: State of New Jersey
Company: STATOIL
Company: Statoil ASA
Company: STAVE Worldwide, LLC
Company: Stealth Forex Systems
Company: Stein Roe Investment Counsel
Company: Steketee
Company: STEP Artillery House (South)
Company: Stephen M. Robinson LLC
Company: Sterling Energy International
Company: Sterling Sound
Company: Stern Fisher Edwards Inc
Company: Sterne, Agee
Company: Steven M Brooks
Company: Stewart & Stevenson LLC
Company: Stifel, Nicolaus
Company: Stockman’s Casino
Company: Stoltenberg & Associates
Company: Stone Works LLP
Company: Stonehage Limited
Company: Stonehaven Development, Inc.
Company: StoneRidge Capital
Company: Stralem & Company, Inc.
Company: Strategic Investment Solutions
Company: Strategic Organization Design, Inc.
Company: Strategic Underwriters Int’l
Company: Strategic Workforce
Company: Strategy 2100
Company: Strategy Garden
Company: Stratex Networks
Company: Stratex Networks Inc
Company: Stratfor
Company: Stratfor Customer Service
Company: Stratfor Customer Service
Company: Stratfor Employee Accounts
Company: Stratfor Interns
Company: STRATIX LTD.
Company: Streettalk Advisors
Company: Streettalk Advisors, LLC
Company: Stubborn Facts
Company: Subrosa Consulting
Company: sudan
Company: Suez Energy Marketing NA
Company: Suez Energy Marketing NA
Company: Suez-Tractebel NV/SA
Company: Sullivan Haave Associates, Inc.
Company: SullivanSites LLC
Company: Summit Creek Capital LLC
Company: Sun Microsystem
Company: Suncor Energy
Company: Suncor Energy Inc.
Company: SuNova Capital
Company: Sunray Energy LLP
Company: SunTrust Bank
Company: SunTrust Bank
Company: SUNY-Brockport
Company: superDimension
Company: Superior Court of New Jersey
Company: Superior Graphite Company
Company: SUPERSONIC MOTOR OIL CO., INC
Company: Surface Treatment Technologies Inc.
Company: Survival Educators
Company: Surya Capital
Company: Sushi Zushi of Texas, Inc
Company: Sustainable Forest Systems LLC
Company: Suttle Bros
Company: SWF
Company: Swift
Company: Swift Freight Int’l
Company: Swiss & Global Asset Management
Company: Swiss Agency for Development and Cooperation
Company: Swiss Agency for Development and Cooperation
Company: Swiss Agency for Development and Cooperation
Company: Swiss Federal Chancellery
Company: Swiss Reinsurance Company Ltd
Company: SWORD International
Company: SWR Consulting
Company: Sycamore Bank
Company: Sylvan Research Inc.
Company: Symphony Asset
Company: Symphony Capital Partners
Company: Synergia
Company: Syngenta International AG
Company: Synthesys
Company: Systems Planning and Analysis, Inc.
Company: T. Rowe Price
Company: T.H. Fitzgerald & Co.
Company: TA&MT MURRAY-PRIOR
Company: TableTop Game & Hobby, Inc.
Company: Taconic Capital Advisors LP
Company: TAG Aviation
Company: Tahoe Partners LLC
Company: Talas es Tarsa Bt.
Company: Talisman Energy
Company: Talon Executive Services, Inc
Company: Tangent Networks LLC
Company: Tappenden Holdings Ltd
Company: TAR Enterprises
Company: Target Corporation
Company: Target Corporation
Company: Tarnbrae Distributing
Company: Tarrier Steel
Company: Tartan controls
Company: Tasman Technology
Company: TAX ADVISORS, LLC
Company: Taylor Fresh Foods
Company: Taylor Investment Associates
Company: Taylor Woods Capital
Company: TBS Shipping Services Inc
Company: TCCM, s.r.o.
Company: TCE Kids Inc
Company: TCOM, LP
Company: TD Bank
Company: TD Bank Group
Company: TD Securities
Company: TD Securities
Company: TD Securities
Company: TD Securities
Company: TD Securities
Company: TD waterhouse
Company: TD Waterhouse
Company: tdt, inc
Company: TE4 Capital Management, LLC
Company: Teachers Retirements System of Texas
Company: TECC sal
Company: Technology Research Corp.
Company: Technosoft, LLC
Company: TechVerity LLC
Company: Tecnologico de Monterrey
Company: Tecolote Research
Company: Tekno Books
Company: TeleAtlas Africa
Company: Telegraf
Company: telekom deutschland gmbh
Company: Terminus Global Services, Inc.
Company: TerraConcepts, LLC
Company: Terry McDaniel & Company
Company: Tesco HSC
Company: Tesoro Corporation
Company: Tesoro Corporation
Company: Teton Capital Management
Company: Texas A&M University
Company: Texas Army National Guard
Company: texas back institute
Company: Texas Children’s Hospital
Company: Texas Department of Banking
Company: Texas Permanent School Fund
Company: Texas Realty Capital
Company: Texas State Auditor’s Office
Company: Texas Tech University
Company: Texas Treasury Safekeeping Trust Company
Company: Texas Woman’s University
Company: Textron Systems
Company: The 4th Branch
Company: The Advocatus Group
Company: The Alchemind Group
Company: the alden group
Company: The Ambient Branding Company Ltd
Company: The Andarrios Fund
Company: The Asahi Shimbun
Company: The Associated Press (AP)
Company: The Atlantic Council of the United States
Company: The Bayliss Wealth Managment Group of Wells Fargo Advisors
Company: The Boeing Company
Company: The Boeing Company – Long Beach
Company: The Bollard Group, LLC
Company: The Bright Light Group, LLC
Company: The Bush School, Texas A&M University
Company: The CAPROCK Group
Company: The CAPROCK Group
Company: The Central Group
Company: The Chemical Company
Company: The Church in Tacoma
Company: The Coca-Cola Company
Company: The Coca-Cola Company
Company: The Concordia Electric Wire and Cable Company Ltd
Company: The Craig Group, Inc
Company: The Cromwell Group
Company: The Devon Group
Company: The Dilenschneider Group
Company: The Dow Chemical Company
Company: The Embassy of the Hashemite Kingdom of Jordan
Company: The Embassy of the Hashemite Kingdom of Jordan
Company: The Endowment Office
Company: The F. L. Emmert Company
Company: The Fairman Group
Company: The Farwell Group
Company: The fedder Company
Company: The Flexitallic Group, Inc.
Company: The Galaxy Organization
Company: The Glenview Trust Company
Company: The Hamilton Group Inc
Company: The Happiness Realization Party
Company: The Helix Group, Inc.
Company: The Humphreys Group
Company: The Inkerman Group
Company: The Karis Group
Company: The Kayser Group, Inc.
Company: The Laredo National Bank
Company: The Law Offices of Terrance W. Stone
Company: The League Corp
Company: The Leuthold Group
Company: The LifeBoat Group
Company: The Macerich Company
Company: The Mainichi Newspapers Co.
Company: The Mauer Group Consultancy
Company: The McMillen Group
Company: The McMillen Group, LLC
Company: The Muse Company
Company: The National Alliance For Insurance Education & Research
Company: THE NATIONAL COMMERCIAL BANK
Company: The Navigators
Company: The New York Mortgage Company
Company: The Ostrom Company
Company: THE PEGASUS GROUP, INC.
Company: The Ramaro Group, Ltd.
Company: The Rapidan Group
Company: The Sandi Group
Company: The Scotts Company
Company: The Scowcroft Group
Company: The Seed Company
Company: The Seng Company
Company: The Show Me Group
Company: The SIGMA Centre Ltd
Company: The South Financial Group
Company: The Steele Agency, Inc.
Company: The Steelman Group, Inc.
Company: The Stratford Company
Company: The Stream Companies
Company: The Thacher School
Company: The Times
Company: The Treadstone Group
Company: The Turing Studio
Company: The Walt Disney Company
Company: The Walt Disney Company
Company: The Warren Group
Company: The Washington Times
Company: The Wealth Conservancy
Company: The Whitewind Co
Company: The Wilhelm Group, Inc.
Company: The Witcoff Group LLC
Company: the womens center pllc
Company: The Workthreat Group, LLC
Company: The Yzaguirre Group, L.L.C.
Company: Thermo King Calgary
Company: Think Equitly llc
Company: Thinkwell Development
Company: Thinkwerk.com
Company: thint
Company: Third Hemisphere
Company: Thomas H Lee Capital LLC
Company: Thomas M. Smith, Ph.D.
Company: Thomas Publishing Company
Company: Thompson, Siegel & Walmsley
Company: thomson reuters
Company: Thomson Reuters
Company: Thoughts of Faith, Inc.
Company: three
Company: Thrive Engineering Corporation
Company: Thrivent Financial
Company: Thunder Exploration, Inc.
Company: TIAA-CREF
Company: Ticaboo
Company: Tierra Capital
Company: Tilleke & Gibbins
Company: Tillman and Co
Company: TIMA International GmbH
Company: Time Warner Cable
Company: Timken Company
Company: tinker
Company: TIOUW.com BV
Company: Titan
Company: Tiverton Trading
Company: TML Information Services, Inc
Company: TML Solutions
Company: TNCO Inc.
Company: TNE Capital Management
Company: TNK-BP
Company: tns
Company: To Every Tribe
Company: To Office / 303.410.2827
Company: Todd Hanna Biz Dev Comps
Company: Todd Hanna Biz Dev Comps
Company: Todd Hanna Biz Dev Comps
Company: Toll Holdings
Company: Tomkin Estates Limited
Company: Tomoco LP
Company: Tooley Investment Company
Company: torah academy
Company: Tortoise Capital
Company: Total
Company: Total
Company: Total Defense Logistics (HKG) Ltd.
Company: TOTSA Total Oil Trading SA
Company: Touch Poll of Georgia
Company: Towers Watson
Company: Town of Corte Madera
Company: Town Shoes
Company: TPH Assetmanagement
Company: Trabon
Company: Trademark Financial Management
Company: Tradesur
Company: Tradewinds International
Company: Tradewinds Investment Management
Company: Tradition Ltd
Company: Trans-Expedite Inc.
Company: trans-resources inc
Company: TRC
Company: Treasury
Company: Treasury Board Secretariat
Company: Trellus Management Co., LLC
Company: Trend Capture LLC
Company: TREVOC WORLDWIDE
Company: Tribalco, LLC
Company: tribecca properties
Company: Trident Partners
Company: Trident Response Group
Company: TRIM Broker
Company: Trimmier Law Firm
Company: Tritium Networks Consulting AB
Company: Triune Capital Advisors
Company: Trivandrum Capital
Company: Tropicana Entertainment LLC
Company: Troutman Fire and Rescue
Company: Truffle Hound Capital, LLC
Company: Truluck’s Restaurant Group
Company: TRUST COMPANY OF THE WEST (TCW)
Company: Tuatara Management
Company: Tudor Pickering
Company: Turtle Creek Management, LLC
Company: tuscany advisors
Company: Tutor Pickering
Company: TVS & Associates
Company: TWIN FEATHERS Enterprises
Company: Two Sigma Investments, LLC
Company: Tyco International
Company: Tyrannet, Inc.
Company: U of Notre Dame
Company: U S Army
Company: U. of Pennsylvania
Company: U.C. San Diego
Company: U.S Army
Company: U.S. Air Force
Company: u.s. army
Company: U.S. Army
Company: U.S. Army
Company: U.S. Army
Company: U.S. Army, (Ret.)
Company: U.S. Bank
Company: U.S. Government
Company: U.S. House of Representatives
Company: U.S. Navy
Company: U.S. Navy
Company: U.S. Office of Personnel Management
Company: U.S. Oil Co., Inc.
Company: U.S.-Ukraine Business Council
Company: UAB Soft Artis
Company: UAL Corporation
Company: UAL Corporation
Company: UBS
Company: UBS
Company: UBS
Company: UBS
Company: UBS
Company: UBS
Company: UBS
Company: UBS Capital
Company: UBS Financial Services
Company: UBS Financial Services
Company: UBS Financial Services, Inc
Company: UBS Investment Bank
Company: UBS OConnor Limited
Company: UFRGS
Company: UJA Federation of Greater Toronto
Company: UKATCO
Company: ULTRAM2 Sa de CV
Company: umc trauma and burn center
Company: UN
Company: Unda Mexico, S.A. de C.V.
Company: UNDP
Company: UNDSS
Company: UNDSS
Company: Unicom Capital
Company: Unicom Capital
Company: UNIFIL – United Nations Interim Forces in Lebanon
Company: Union Bancaire Privee
Company: Unipharm,Inc.
Company: Unisports Sports Medicine
Company: Unisys Corp.
Company: Unit International
Company: United Aerospace Co., Ltd.
Company: United Capital Partners
Company: United Church of God
Company: United Group Consultants SA
Company: United Hi-tech Preventive Systems
Company: United Launch Alliance
Company: United Nations
Company: United Nations
Company: United Nations
Company: United Nations
Company: UNITED NATIONS
Company: United Nations Foundation
Company: United Nations Relief Works Agency
Company: United Nations, Department of Safety and Security
Company: United Parcel Service
Company: United Space Alliance Attn: USK-011
Company: United States Air Force
Company: United States Coast Guard Auxiliary
Company: Unity Resources Group
Company: Univ of Arizona
Company: Universal Lighting Technologies
Company: Universal Risks
Company: Universidad AutÛnoma metropolitana
Company: universidad autÛnoma metropolitana, unidad iztapalapa
Company: Universidade Federal Fluminense
Company: Universidade Federal Fluminense
Company: university
Company: University
Company: university of arizona
Company: University of Canberra
Company: University of Chicago – Student Sub
Company: University of Colorado at Boulder
Company: University of Colorado Denver
Company: University of Florida Investment Corporation
Company: University of Fribourg
Company: University of Hawaii-Maui College
Company: University of Houston Public Policy
Company: University Of Illinois
Company: University of Mich
Company: University of Michigan
Company: University of Michigan
Company: University of Missouri
Company: University of Missouri
Company: University of Missouri
Company: University of Missouri
Company: University of Missouri
Company: University of Missouri
Company: University of Missouri
Company: University of Missouri
Company: University of Missouri
Company: University of Notre Dame
Company: University of Oklahoma
Company: University of Ottawa
Company: University of Rhode Island
Company: University Of South Florida
Company: University of Toronto
Company: University of Winnipeg
Company: University of Wisconsin
Company: University of Wisconsin School of Medicine
Company: University of Wyoming
Company: UNOG
Company: UNTSO
Company: UNX Inc.
Company: UPS
Company: UPS
Company: Ur Energy USA
Company: URBAN CONTRACTORS, LLC
Company: URS Corp.
Company: Urso Ltd.
Company: US – Azerbaijan Chamber of Commerce
Company: US African Development Foundation and American University
Company: US Air Force
Company: us army
Company: us army
Company: US Army
Company: US Army
Company: US Army
Company: US Army
Company: US Army
Company: US Army
Company: US Army
Company: US Army
Company: US Army
Company: US Army – ARMY NORTH
Company: US Army Corps of Engineers
Company: US ARMY MARS TEXAS
Company: US Army Reserve Command
Company: US Army Retired
Company: US Army Spec Ops Command
Company: US Army, Retired
Company: US Army, TRADOC, ARCIC, Joint & Army Concepts Development
Company: US Civil Service
Company: US Coast Guard
Company: US Dept of State
Company: US Dept of State
Company: US Forest Service
Company: US Government
Company: US Govt
Company: US GOVT/DOT
Company: US Marine Corps
Company: US Navy
Company: US Navy
Company: US Navy
Company: US Navy
Company: US Navy
Company: US of A
Company: US Property Valuation, LLC
Company: USACE-GRD
Company: USAF
Company: USAF
Company: USAF
Company: USAF
Company: USAF
Company: USAF
Company: usaf (ret)
Company: USAID
Company: USAID
Company: USDOJ
Company: USFI
Company: USG
Company: usmc
Company: USMC
Company: USMC
Company: USMC
Company: USMC
Company: USMC
Company: USNR
Company: usp
Company: USSTRATCOM/J722
Company: UT International Office
Company: UTC
Company: Utley Interests Inc
Company: VA hospital
Company: Valero
Company: Valero
Company: Valero
Company: Valero
Company: Valhalla Capital Advisors
Company: Valor Security Services
Company: Value Line Publishing
Company: Value Logic
Company: van dent pty limited
Company: Van Norman LLC
Company: Vanadium Capital
Company: Vanco Exploration Company
Company: Vanderbilt
Company: Vanguard
Company: vantage consulting group
Company: Vaultit, Inc.
Company: VC Experts
Company: VCU Qatar
Company: VDB BioMed LLC
Company: Vector Asset Management LLC
Company: Vedanta Energy Fund
Company: Vedette Asset Management, LLC
Company: Venable LLP
Company: VenArete Growth Advisors (VGA)
Company: venisys
Company: Verboven Immigration
Company: Verdant Strategies, Inc.
Company: Verger Corp
Company: Veritas
Company: Veritas Targeting
Company: Verity Investments Inc.
Company: Verizon Investment Mgmt.
Company: Verna
Company: Vertebrae DA
Company: Vertical Information Systems
Company: VIA Consulting
Company: VIACK Corp
Company: VIAP
Company: VICCON GmbH
Company: Vickers Appraisals
Company: Victory Packaging
Company: Vietnam Embassy
Company: VietNamNet Media Company
Company: Vikstrˆm & Andersson Asset Management AB
Company: Vindice Consult SRL
Company: ViP Innovative Solutions, Inc.
Company: Virchow Krause Wealth Management, LLC
Company: Virginia Commonwealth University
Company: Virginia Commonwealth University
Company: Virginia Peninsula Real Estate
Company: Viriya Holding BV
Company: Virtuality Inc.
Company: Visa International
Company: Vision Centric, Inc
Company: Vision Investments
Company: Vision Space Partners
Company: Vistage International
Company: VitalSpark Beheer BV
Company: VLSI Research
Company: VMS Ventures Inc.
Company: Volens Et Potens, LLC
Company: Volunteer America – 1776
Company: Volunteer Intelligence
Company: Volusia County Sheriff’s Office
Company: Volvo Bus Corporation
Company: Vostok Nafta Investment Ltd.
Company: VT Group
Company: VTS, Inc
Company: Vulcan Inc
Company: W. R. Theuer, Company
Company: W.D. Warth & Associates
Company: W.T.W.E.
Company: Wachovia Sec LLC
Company: Wachovia Securities
Company: Wachovia Securities
Company: Wachovia Securities
Company: Wachovia Securities
Company: Wachovia Securities
Company: Walden Media
Company: Walker Talent Group
Company: WallStreetWindow
Company: Walpole Police and LESC, INC
Company: Walt Disney
Company: Walter & Haverfield
Company: Washington Defence Co, LLC
Company: Washington Group International
Company: Wasser Financial
Company: Water Asset Management LLC
Company: Watlow
Company: Watson Holdings
Company: wavecount247
Company: Wavecrest Asset Management
Company: WBB Consulting
Company: WD Music Products. Inc.
Company: Wealth Management LLC
Company: Wealth Resources, Inc.
Company: Weatherhaven
Company: WEB Aruba NV
Company: Web Communication Wizards
Company: WEB Sales Inc.
Company: Webb Systems LLC
Company: Weber Shandwick
Company: Weber-Aries, Inc.
Company: Weiss & Partner
Company: Welch Cap
Company: Welhausen Foundation
Company: Wells Capital Management
Company: Wells Fargo
Company: Wells Fargo
Company: Wells Fargo Investments
Company: WER Global Services, LLC
Company: Werlinich Asset Management
Company: Wesley Capitol CO Barclays Cap
Company: West Africa Transport Corporation
Company: West Central Cooperative
Company: West Ellis Investment Management
Company: West End Avenue Advisors LLC
Company: West Point Grey Academy
Company: Western Mutual Ins. Grp
Company: Western Union
Company: Western Union
Company: Westfall Surgery Center
Company: Westford Asset Management LLC
Company: WestLB
Company: WESTLB AG LONDON BRANCH
Company: Weston Capital Management
Company: Weston County
Company: WestPac Banking Corp
Company: WestPan Associates
Company: Westport Petroleum, Inc
Company: Wetherby Asset Management
Company: WGFleming, LLC
Company: Whatcom County, WA
Company: White & Case LLP
Company: White Oak Investment
Company: White Pines Group
Company: White Rock, Inc.
Company: Whitney, Wetzel & Kuether, LLC
Company: WiJo Capital LLP
Company: Wild Cat Ranch
Company: Wilkison Investment Services
Company: William Blair & Company
Company: William Fell Consultants
Company: Williams & Co
Company: Williams and Williams
Company: Williamson Research & Solutions
Company: Willkie Farr & Gallagher
Company: Willowbend Software
Company: Willowbridge Associates
Company: Wilpon Investors
Company: wilson & associates
Company: Wilson Financial Group LLC
Company: Wimco
Company: Winning Writers
Company: Winton duPont Films
Company: Wintonbury Risk Management
Company: Wipfli, LLP
Company: Wisconsin University
Company: Wisuschil & Partner – Rechtsanw‰lte
Company: WitmarkEnteprises
Company: WJS Business Consulting Inter
Company: WMundell Consultores
Company: woodgundy
Company: Woodside Capital
Company: Woodside Energy Ltd
Company: Woori Investment & Securities
Company: Woosh Wireless Ltd
Company: Worcester & Associates
Company: World Affairs Council of South Texas
Company: World Airways, Inc.
Company: World Bank
Company: World Economic Forum
Company: World Food Programme of United Nations in Colombia
Company: World Health Organization
Company: World Vision
Company: World Vision
Company: worldview
Company: Wright Asset Management
Company: WSI
Company: WSI Group
Company: WSP
Company: WTCI
Company: WTF
Company: Wuethrich, Henz & Co.
Company: WVM & Associates
Company: WW Grainger
Company: http://www.addingvalue4u.com Ltd
Company: http://www.wooty.com
Company: Wyeth
Company: Wysard Inc
Company: x
Company: x
Company: x
Company: x
Company: x
Company: x
Company: x
Company: X
Company: X-RingTrades LLC
Company: Xanadoo Company
Company: xecos capital llc
Company: XTO Energy
Company: Yale
Company: Yale – SOM
Company: Yale University
Company: Yamotech Inc.
Company: Yavapai College
Company: Yellow House Associates, LLC
Company: yenitan.com.tr
Company: YENRAB Investing
Company: Yukon Wealth Mgt.
Company: Yum! Brand
Company: Yum! Brand
Company: Z.S.S. CORP.
Company: Zad Investment Company
Company: ZFS
Company: Ziff Brothers Investments
Company: Ziff Brothers Investments
Company: Ziff Brothers Investments
Company: Zinndevco,Inc.
Company: Zumtobel Lighting Ltd.
Company: Zurich State Police
TOP-SECRET – (U//FOUO) LulzSec Release: DHS National Socialist Movement NAZI Reference Aid

(U) Overview
(U//FOUO) The National Socialist Movement (NSM) USPER is the most active neo-Nazi group operating in the United States. It has grown from a small organization with a limited following confined to the mid-western United States to the preeminent National Socialist group in the nation. Despite having recently suffered a defection of several regional leaders, NSM remains an influential force within white supremacist circles and the only major racist group that eschews all attempts to distance its methods and objectives from those of the Third Reich. NSM has a reputation for conducting numerous public rallies that have triggered a violent response, including a riot in Toledo, Ohio, in October 2005.
(U) Description
(U//FOUO) The National Socialist Movement (NSM) is the largest neo-Nazi organization in the United States. Founded in 1974 by two former members of the American Nazi PartyUSPER, NSM claims that it is the only “legitimate” Nazi party operating in the United States. Although active since 1974, NSM only became a major player in the white supremacist movement in the late 1990s and has had its greatest period of growth over the past three years. This growth likely resulted from the collapse of other prominent neo-Nazi groups such as the National AllianceUSPER and Aryan NationsUSPER.
(U) Ideology and Objectives
(U//FOUO) NSM promotes the ideology of traditional National Socialism, which is a mix of racism, anti-Semitism, xenophobia, rabid anti-communism, and white supremacy. NSM seeks to transform the United States into a National Socialist state that would deny all rights to Jews, nonwhites, and gays. NSM also advocates the mass deportation of all illegal immigrants, the militarization of the Mexican border, the end of all foreign aid, and the severing of all ties with Israel.
(U) Symbology
(U//FOUO) NSM patterns its uniforms after those of the Third Reich’s Wehrmacht and the Waffen SS. The armbands, shoulder boards, and collar insignia used by NSM are replicas of those worn by the military units and political officers of Nazi Germany. NSM also uses many forms of Nazi symbols and imagery in its propaganda.
…
(U) Active Membership
(U//FOUO) Although NSM has small chapters operating throughout the country, over half of its estimated active membership is based in the Midwest, primarily in Illinois, Michigan, Minnesota, Missouri, Ohio, and Wisconsin. Another large concentration of NSM members operates in the Southwestern United States, centered mainly in Arizona and Nevada. There are an estimated 300 active NSM members along with a similar number of associates that are active on NSM’s various Internet forums. Online members have little direct involvement with the group.
(U) Financial Support
(U//FOUO) All active NSM members as well as new recruits are required to contribute monthly dues to help sustain the organization. NSM also generates a great deal of its revenue from sponsoring white power rock concerts and from the sale of racist music CDs, DVDs, video games, and other white power paraphernalia. NSM conducts much of their sales through its own music distributor, NSM88Records. The group uses funding to further their political ambitions, propaganda mechanisms, and various commercial enterprises that sell Nazi regalia and memorabilia.
…
(U) Targets of Actions
(U//FOUO) To date, NSM confines its activities primarily to conducting a series of high profile public rallies and marches targeting minority neighborhoods, illegal immigrants, and U.S. support to Israel. In several instances, these activities have triggered violent confrontations between protestors opposing NSM and law enforcement attempting to preserve public order. During an October 2005 march in Toledo, Ohio, police were unable to prevent local residents from rioting for several hours following the NSM rally. The disturbances resulted in the arrest of 120 rioters and the destruction of several local businesses. Toledo’s mayor was forced to restore order by imposing a curfew.
(U) Criminal Activity
(U//FOUO) There is little or no evidence that NSM, as an organization, is engaged in any organized criminal activity. A large number of current and former members of NSM, however, have engaged in sporadic criminal acts that are unrelated to their involvement with the group. NSM members have committed a wide range of crimes to include: murder, kidnapping, rape, domestic violence, pedophilia, burglary, trespassing, and narcotics possession.
DOWNLOAD FULL DOCUMENT HERE
CONFIDENTIAL -Nazi Victims Call for Investigation into Vatican Laundering of Stolen Assets
 In this file photo a nun walks past a branch of Credito Artigiano’s bank in Rome. Italian prosecutors contest claims by the Vatican bank that it is trying to comply with international rules to fight money laundering, saying an investigation that led to the seizure of euros 23 million ($30 million) from a Vatican bank account shows “exactly the opposite,” according to a court document obtained. An Italian court on Wednesday rejected a Vatican request to lift the seizure, leading the Vatican to express “astonishment” at the court’s ruling and indicating the case will not be cleared up quickly, as the Vatican originally predicted. Under the investigation, financial police seized the money Sept. 21 from a Vatican bank account at the Rome branch of Credito Artigiano Spa, after the bank informed the Bank of Italy about possible violations of anti-money laundering norms. (AP Photo/Angelo Carconi/Files)
In this file photo a nun walks past a branch of Credito Artigiano’s bank in Rome. Italian prosecutors contest claims by the Vatican bank that it is trying to comply with international rules to fight money laundering, saying an investigation that led to the seizure of euros 23 million ($30 million) from a Vatican bank account shows “exactly the opposite,” according to a court document obtained. An Italian court on Wednesday rejected a Vatican request to lift the seizure, leading the Vatican to express “astonishment” at the court’s ruling and indicating the case will not be cleared up quickly, as the Vatican originally predicted. Under the investigation, financial police seized the money Sept. 21 from a Vatican bank account at the Rome branch of Credito Artigiano Spa, after the bank informed the Bank of Italy about possible violations of anti-money laundering norms. (AP Photo/Angelo Carconi/Files)
Nazi Victims Ask EU to Probe Vatican on Looted Assets:
Holocaust survivors from the former Yugoslavia accused the Vatican of helping Nazi allies launder their stolen valuables and have asked the European Commission to investigate their claims.
“We are requesting the commission open an inquiry into allegations of money laundering of Holocaust victim assets by financial organs associated with or which are agencies of the Vatican City State,” Jonathan Levy, a Washington-based attorney for the survivors and their heirs, wrote in a letter to Olli Rehn, the European Union’s economic and monetary affairs commissioner. Levy provided the letter to Bloomberg.
The request follows a decade-long lawsuit in U.S. courts on behalf of Holocaust survivors and their heirs from the former Yugoslavia and Ukraine. That case, basing its claims on a U.S. State Department report on the fate of Nazi plunder, alleged that the Vatican Bank laundered assets stolen from thousands of Jews, gypsies and Serbs killed or captured by the Ustasha, the Nazi-backed regime of wartime Croatia. The Vatican repeatedly denied the charges and the findings of the 1998 U.S. report.
Amadeu Altafaj, Rehn’s spokesman, said in Brussels today that the commission had received Levy’s letter and contacted Vatican authorities about it. Vatican spokesman Father Federico Lombardi declined to comment on Levy’s request to the commission.
Vatican Immunity
The U.S. case, which sought as much as $2 billion in restitution, was dismissed last December by a U.S. appeals court in San Francisco on grounds that the Vatican Bank enjoyed immunity under the 1976 Foreign Service Immunities Act, which may prevent foreign governments from facing lawsuits in the U.S.
The commission should have the authority to probe the Institute for Religious Works, or IOR, as the Vatican Bank is called, according to Levy’s letter. It cites a monetary accord signed on Dec. 17 of last year. Under the agreement the Vatican, which uses the euro and issues euro coins, pledged to implement EU laws against money laundering, counterfeiting and fraud.
Rome prosecutors have also sought to show that the Vatican bank is covered under European law. Last month they seized 23 million euros ($32 million) from an Italian account registered to the IOR as they opened a probe into alleged violations of money-laundering laws by the Vatican Bank.
“We looked at all the places where the Vatican may have surrendered sovereignty,” Levy said in a telephone interview. “The only place we could find was with the euro, where they placed themselves under the jurisdiction of either the European Central Bank or the European Commission.”
Swiss Payout
Levy initially contacted the legal office of the Frankfurt- based ECB and was told to take the claim to the commission, he said. An ECB spokeswoman confirmed that after being contacted by Levy, the central bank advised him to go directly to the EU’s executive arm.
The U.S. lawsuit was first filed in 1999, one year after an official Swiss commission concluded that Switzerland received three times more gold taken from Nazi victims than previously estimated by the U.S. government. The same year, UBS AG and Credit Suisse AG, the biggest Swiss banks, agreed to pay $1.25 billion in compensation to Holocaust survivors and their heirs.
In his letter, Levy said “gold and other valuables” stolen in the “genocidal” murder of 500,000 Serbs, Jews and gypsies “were deposited at the Vatican in 1946,” according to “contemporaneous documents authored by Allied investigators” and “the sworn testimony of former U.S. Special Agent William Gowen.” He interviewed and investigated the Ustasha involved in transferring the loot while stationed in Rome after the war.
UNCENSORED – Topless protest in Ukraine FEMEN euronews 2011 against sex tourism
SECRET – Neo-Nazi Fantasy Border Patrol Pictures
The following photos are taken from the Flickr feed of the U.S. Border Guard, a group with an official-sounding name that is, in reality, comprised of volunteers who patrol the border in Arizona. The group’s patrols are led by J.T. Ready, who has openly defended his views as a neo-Nazi. All titles and captions are taken, unaltered, from the group’s Flickr feed. Some people believe that J.T. Ready is an FBI informant.
The following photos are taken from the Flickr feed of the U.S. Border Guard, a group with an official-sounding name that is, in reality, comprised of volunteers who patrol the border in Arizona. The group’s patrols are led by J.T. Ready, who has openly defended his views as a neo-Nazi. All titles and captions are taken, unaltered, from the group’s Flickr feed. Some people believe that J.T. Ready is an FBI informant.
CONFIDENTIAL – Purported List of Israeli War Criminals Names and Information
The following information was anonymously published on a website (http://israeliwarcriminals.zzl.org) that is no longer accessible. It was accompanied by the following message:
All took an active and direct role in the offensive.
In underlining them we are purposefully directing attention to individuals rather than the static structures through which they operate. We are aligning people with actions. It is to these persons and others, Like them, to which we must object and bring our plaints to
bear upon.
This information was pirated. We encourage people to seek out other such similar information, it is readily available in the public sphere and
inside public officials’ locked cabinets. This is a form of resistance that can be effectively sustained for a long while.
This project for one, has only just begun, do your bit so that this virtual list may come to bear upon the physical.
Disseminate widely.
| Picture
תמונה |
Name
שם |
Rank
דרגה |
Position
תפקיד |
Date of Birth תאריך |
ID מספר |
Address
כתובת |
|
 |
Agai Yehezkel אגאי יחזקאל |
Brigadier General תא”ל
|
Head of the Armored Corps קצין שריון |
19/04/66 |
22380406
|
26 Caesarea 30889 ענבר קיסריה 30889 |
|
|
Aharon אהרן חליוה |
Colonel אל”מ |
Head of “Bahad 1″ (officer training academy) מפקד |
12/10/67 |
23050578 |
|||
|
|
Alex Shakliar אלכס שקליאר |
Second Lieutenant סג”מ |
Nesher Field Inteligence Battalion, Squad Commander גדוד |
12/12/87 |
304074636 |
||
 |
Amir Ulo אמיר אולו |
Lieutenant Colonel סא”ל |
Yahalom Engineering Battalion Commander מפקד גדוד |
09/05/71 |
28542900 |
62 Hagai st. Har Adar 90836 הגיא הר אדר 90836
|
|
 |
Amir Abstein אמיר אבשטיין |
Lieutenant Colonel סא”ל |
7th Regiment, 75 Romach Battalion Commander חטיבה |
28/03/73 | 16436917 |
21 Modi’in-Maccabim-Re’ut 71725 יהלום מודיעין– 71725 |
|
 |
Amir אמיר שמעון
|
Major General אלוף |
Head of the Planning Directorate ראש אגף התכנון |
04/04/59 |
55652846 |
# 78
Kidron 70795 קידרון 70795 |
|
 |
Amos Yadlin עמוס ידלין |
Major General אלוף |
Head of Intelligence Directorate ראש אמ“ן |
20/11/51 | 51112027 |
11 Smadar st. Karmei 99797 סמדר 11 כרמי יוסף 99797
|
|
 |
Anna Strelski אנה סטרלסקי |
Sergeant
סמלת |
Bislmach Infantry Training Academy, Mortar Commander ביסלמ“ח |
22/09/88 |
309313674
|
||
 |
Anton Siomin אנטון סיומין |
L:ieutenant (Reserve) סגן |
Paratroopers צנחנים |
22/12/84
|
324417930 |
חיפה Haifa |
|
|
|
Aram ארם זהבי |
Captain סרן |
601 |
03/09′/81 | 43249036
|
||
 |
Ariel אריאל בריקמן |
Colonel
אל”מ |
“Hazor” Air Force Base Commander מפקד בסיס חיל |
01/01/64 |
58497306 |
Machane Mizpe 80600 מחנה טלי מצפה רמון 80600 |
|
 |
Ariel Karo אריאל קארו |
Brigadier General תא”ל |
Head of Field Intelligence Corps קצין מודיעין |
01/01/65
|
22136576 |
73 Kefar 44213 הרצל כפר סבא 44213 |
|
 |
Ariel Rifkin אריאל ריפקין |
Sergeant Major רס“ל |
601 Assaf engineering Battalion, Heavy Engineering Team Work manager (D-9 operators) גדוד |
19/07/79 | 37287497 | ||
| Ariel Yochanan אריאל יוחנן
|
Lieutenant Colonel סא”ל |
Paratroopers 101 Peten Batallion Commander (as replacement) צנחנים, |
22/09/73 | 25244492 |
# (Nevatim) 8554 מחנה (נבטים 85540 |
||
| Arnon Avital ארנון אביטל |
Lieutenant
סגן |
401 Regiment 9 Eshet, Deputy Company Commander חטיבה |
27/08/85 |
37079779 |
|||
 |
Assaf Bryt אסף בריט |
Captain (Reserve) סרן |
Golani Reconnaissance Battalion, Squad Commander גדס“ר |
07/11/1979 | 37414240 |
||
|
|
Avi Balut אבי בלוט
|
Lieutenant Colonel סא”ל |
Paratroopers 101 Peten Battalion Commander צנחנים, |
12/09/74 | 31795750 | 66 Yisaschar st. Modi’in-Maccabim-Re’ut 71724
יששכר מודיעין– 71724
|
|
 |
Avi Bnayahu אבי בניהו |
Brigadier general תא”ל |
Military Spokesperson דובר |
11/07/77 |
33809724
|
Lehavot 38835 להבות 38835 |
|
 |
Avi Mizrakhi אבי מזרחי |
Major General אלוף |
Commander of the Ground Forces מפקד זרוע |
26/12/57 |
55006639 |
14 Zikhron 30900 ששת זכרון יעקוב 30900 |
|
 |
Avi Peled אבי
|
Colonel
אל”מ
|
Golani Regiment Commander מפקד
|
01/11/69 |
24638306
|
24 Shivtei Israel st. Modi’in-Maccabim-Re’ut 71700
שבטי מודיעין–מכבים–רעות
71700
|
|
|
|
Aviad אביעד |
Lieutenant סגן |
401 Rregiment 71 Reshef, Platoon Commander חטיבה401 |
27/04/87 | 300409752 | ||
 |
Aviel Siman-Tov אביאל |
Captain
סרן |
Givati 424 Shaked, Company Commander גבעתי |
19/12/84 | 36541704 | 49 Shlomo Hamelech st. Tel Aviv 64386 שלמה תל אביב 64386 |
|
 |
Avihay אביחי ויזמן |
Captain
סרן |
Golani 12 Barak, Company Commander גולני |
27/04/85 | 21544416 | ||
 |
Avihu Ben Zahar אביהו בן זכר |
Lieutenant
סגן |
Givaati 432 Tsabar, Platoon Commander גבעתי |
14/04/87 | 300751518 | ||
 |
Avishay Levi אבישי לוי |
Brigadier General תא”ל |
Head of Air Force Intelligence ראש להק מודיעין |
02/12/63 | 58430992 |
27 Modi’in 71799
גבעת מודיעין– 71799 |
|
 |
Avishay Shasha אבישי שאשא |
Lieutenant סגן
|
“Nurit” סוללת |
15/10/87 |
301178984
|
||
| Aviv Edri אביב עודרי |
Captain
סרן |
Paratroopers Reconnaissance Battalion, Squad Commander גדס“ר |
20/07/84 | 66444779 |
1180 Merhavim st. Dimona 86176 מרחבים דימונה 86176 |
||
 |
Aviv אביב כוכבי
|
Brigadier תא”ל |
Head of the Operations Division ראש חטיבת |
23/04/64 |
58741323 |
# 249
Adi 17940 עדי 17940 |
|
 |
Aviv Mendelowitz אביב מנדלוביץ |
Major
רס”ן |
Gaza Division, Deputy Commander of Artillery אוגדת |
17/01/81 |
40882888 |
# 2 Shaked neighborhood Yerucham 80500 שכונת ירוחם 80500 |
|
|
|
Baruch (Barry) Berlinsky ברוך
|
Second Lieutenant סג“מ |
Golani Reconnossaince Batallion, Squad Commander גדס“ר |
16/08/86 |
300046588 | ||
 |
Basam Alian בסאם עליאן |
Lieutenant Colonel סא”ל |
Deputy
סגן
|
26/11/73 | 26458588 | Shfaram
20200 שפרעם 20200 |
|
 |
Ben-Zion (Benzi) Gruver בן–ציון |
Colonel (reserve) אל”מ |
Deputy Commander of a Reserve Division סגן מפקד אוגדת |
02/10/58 |
55486237 |
44 Efrata 90435 הגפן אפרתה 90435 |
|
|
|
Bnaya Sarel בניה שראל |
Second Lieutenant סג”מ |
Givaati 424 Shaked, Platoon Commander גבעתי |
24/08/87 |
301071320
|
66 Bne Beitcha st.
Givaat
Kiryat 90100 בנה גבעת קרית
90100 |
|
| Boaz Dabush בועז דבוש |
Staff Sergeant Major רס”מ |
601 Assaf engineering Battalion, Heavy Engineering Team Work manager (D-9 operators) גדוד |
02/08/71
|
28804276 |
# 10
Zeitan
71915
זיתן
71915 |
||
| Boaz Rubin בועז רובין |
Captain סרן |
Hanegev Reserve Regiment, Deputy Company Commnader חטיבת |
11/09/77 |
34233114 | 4 Stefen Zweig st. Tel-Aviv 69642 סטפן תל אביב 69642 |
||
 |
Boris Schuster בוריס שוסטר |
Major
רס“ן |
Commander of a “Dabur” Navy Flotilla מפקד שייטת |
12/02/81 | 309209070 | Ashkelon אשקלון
|
|
| Dado Bar-Kalifa דדו |
Lieutenant Colonel סא”ל |
Givati 424 Shaked Battalion Commander גבעתי, |
20/08/76 | 33193061 | 114 Sderot Hagalil st. Bat-Hefer 42842 שדרות בת–חפר 42842 |
||
 |
Dan Dolberg דן דולברג |
Second Lieutenant סג“מ |
401 חטיבה |
15/04/89
|
300257755
|
Yavne
יבנה |
|
 |
Dan Harel דן הראל |
Major general אלוף |
Deputy Chief of Staff סגן |
17/02/55
|
53312690 |
13 Erez st. Modi’in-Maccabim-Re’ut 71908 ארז מודיעין–מכבים–רעות 71908
|
|
|
|
Daniel Kotler דניאל קוטלר |
Second Lieutenant סג”מ |
Givaati 424 Shaked, Operations Officer גבעתי
|
10/08/88 |
301894911 |
||
 |
David Shapira דוד שפירא |
Major
רס“ן |
Paratroopers צנחנים |
14/11/78 | 35716711 | 6 Shoshana Poliakov st. Jerusalem 96106 שושנה ירושלים 96106
|
|
 |
David Slovozkoi דוד סלובוצקוי |
Captain
סרן |
Givati 424 Shaked, Company Commander גבעתי
|
07/06/85 | 304511173 | ||
| David Zini דוד |
Lieutenant Colonel סא”ל |
Golani, Commander of Egoz Unit גולני, |
09/01/74 | 25627266 | |||
| Dvir Diamond דביר דיאמונד |
Lieutenant
סגן |
Paratroopers 101 Peten, Platoon Commander צנחנים |
16/06/86
|
29986791
|
ראס אל עמוד Ras- El- |
||
 |
Eden Atias עדן אטיאס |
Colonel
אל“מ |
Commander of Nevatim Air Force Base מפקד בסיס חיל |
09/10/66 | 22665954 |
Machane Adi (Nevatim) 80700 מחנה עדי (נבטים) 80700 |
|
|
|
Efraim Aviad Tehila אפרים |
Lieutenant סגן
|
Golani גולני
|
31/12/84 |
39764287 | #37
Moshav 60932
צפריה , 60932 |
|
 |
Efraim Avni אפרים אבני |
Captain
סרן |
Paratroopers צנחנים |
06/10/81 |
43239698 | ||
| Eitan Ben-Gad איתן |
Major
רס”ן |
Paratroopers, Operations Officer צנחנים, |
02/03/75 |
32273542 |
29 Aliyat Hanoar st. Jerusalem 97234 עליית ירושלים 97234 |
||
 |
Elad Chachkis אלעד |
Major
רס“ן |
Commander of the “Hetz” Navy Vessel מפקד אח“י |
20/07/80 | 40288151
|
||
| Elad Itzik אלעד |
Second Lieutenant סג”מ |
Paratroopers 101 Peten, Communications Officer צנחנים |
27/11/86 | 29991338 | |||
| Elad Shoshan אלעד שושן |
Captain
סרן |
Paratroopers גדס“ר |
14/10/81 |
46222980 |
|||
 |
Elad Yakobson אלעד יעקובסון |
Captain (reserve) סרן |
Paratroopers 202 Zefa, Company Commander צנחנים |
25/03/80 | 37263308 | ||
 |
Eli Fadida אלי פדידה |
Staf Sergeant סמ“ר |
402 Reshef Artillery Battalion, Squad Commander גדוד
|
23/04/88 | 200661783 | ||
 |
Eli Yafe אלי יפה |
Brigadier General תא”ל |
Head of the Operations Division רח”ט מבצעים |
11/01/57 | 54649173 | 4 Ela st. Kokhav 44864 אלה כוכב יאיר 44864 |
|
 |
Eliezer אליעזר |
Major General אלוף |
Navy Commander מפקד חיל הים |
13/11/55 |
53227492
|
1 Zikhron 30900 עורבנית זכרון יעקוב 30900 |
|
 |
Eliezer Shkedi אליעזר שקדי |
Major General אלוף |
Former Air force Commander, Co-Authored the Operation לשעבר |
10/08/57 |
54898903
|
2 Seora st. Yehud 56475 שעורה יהוד 56475 |
|
 |
Elik אליק סרור |
Captain
סרן
|
Givaati גבעתי |
19/07/83 | 37747391 | ||
|
|
Eran ערן קריסי |
Lietenant Colonel סא“ל |
Lahav 603 Engineering Battalion Commander מפקדגדוד |
08/02/75 | 32264731 | ||
|
Erez |
Lietenant Colonel סא“ל |
401 Regiment, 52 Habokim Battalion Commander חטיבה |
21/11/1975 | 32347890 | |||
 |
Eyal Ben Haim אייל בן חיים |
Major (Reserve) רס“ן |
500 Regiment, Deputy Company Commander חטיבה |
05/02/71 | 27963461 |
# Bizron 60946 ביצרון 60946 |
|
 |
Eyal Eizenberg אייל אייזנברג |
Brigadier General תא”ל |
Gaza Division Commander מפקד אוגדת |
19/04/63 | 58018532 | # 152
Ben 73115 בן 73115 |
|
|
|
Eyal אייל הנדלמן |
Captain
סרן |
3rd Flotilla, Ordnance Officer שייטת
|
20/08/84 |
66629999
|
||
 |
Eyal Zukowsky אייל |
Captain סרן |
Golani 51 Habokim, Company Commander גולני |
27/11/83 | 65922197 | ||
 |
Gaby Ashkenazi גבי אשכנזי |
Leutenant General רב–אלוף |
Chief of Staff ראש המטה הכללי |
25/02/54 | 52228764
|
44 Hakarmel st. Kefar 44205 הכרמל כפר סבא 44205 |
|
| Gil Shen גיל שן |
Lieutenant Colonel סא”ל |
Commander מפקד |
12/10/69 | 24524589 | 12 Weizmann av. Ramat- 47211 שדרות רמת השרון 47211 |
||
| Gur Rozenblat גור רוזנבלט |
Captain
סרן |
Givaati 435 Rotem, Company Commander גבעתי |
05/07/73 | 25343484 |
# 335
Revava 44839 רבבה 44839 |
||
| Gur Schreibmann גור |
Lieutenant Colonel סא”ל |
Givaati, Reconnaissance Battalion Commander מפקד
|
11/09/75 | 32394348 |
1
Kefat
44627
עמק עירון 1
כפר סבא 44627
|
||
|
|
Guy Givoni גיא גבעוני
|
Lieutenant (reserve) סגן |
Golani 13 Gideon, Artillery Coordination officer גולני |
05/03/85 | 36834521 |
||
|
|
Guy Hazut גיא חזות
|
Lieutenant סא”ל |
Deputy Commander of the Paratroopers Regiment סגן |
03/05/71
|
28454650 |
||
|
|
Haggai חגי עמר |
Lietenant Colonel סא“ל |
401 Regiment, 71 Reshef Battalion Commander חטיבה |
16/05/75 |
31926819
|
#
Halamish
71945
חלמיש
71945 |
|
 |
Hanan (Yochanan) Schwartz חנן |
Captain
סרן |
Givati 432 Zabar, Company Commander גבעתי |
18/11/84 | 66363664 | ||
 |
Harel Knafo הראל קנפו |
Brigadier
תא”ל |
Southern Command, Chief of Staff ראש מטה פיקוד |
31/03/65 |
59206961 |
40 Modi’in-Maccabim- 71724 יהודה מודיעין– 71724 |
|
|
|
Harel Naaman הראל |
Lieutenant סגן |
Golani גולני
|
07/08/86 | 37991189
|
||
|
|
Herzel (Herzi) Halevi הרצל |
Colonel
אל”מ |
Paratroopers Regiment Commander מח“ט |
17/12/67 |
57207771
|
||
 |
Hila Yafe הילה יפה |
Major
רס”ן |
Drone Company Commander מפקדת פלוגת |
24/03/82 |
43547967
|
||
|
Idan עידן חמו |
Captain סרן |
188 Regiment 71 Reshef, Company Commander חטיבה |
04/03/83 | 39098843 | |||
 |
Ido Ender עדו אנדר |
Lieutenant
סגן |
Paratroopers 101 Peten, Deputy Company Commander צנחנים |
22/06/86 | 21965363 | ||
 |
Ido Nechushtan עדו נחושתן |
Major General אלוף |
Air Force Commander מפקד חיל האוויר |
18/04/57 |
54744297 |
1 Yavne 81501 יקינטון יבנה 81501 |
|
 |
Ilan אילן בוגר |
Colonel
אל“מ |
Commander of Ramat David Air-Force Base
מפקד |
09/12/66 | 22807341 |
49 Lehi st. Ramat לח“י רמת השרון |
|
|
Ilan אילן דיקשטיין |
Lieutenant Colonel סא”ל |
Kfir חרוב |
11/01/73 |
25093089 |
# 45
Eli 44828 עלי 44828
|
||
 |
Ilan Malka אילן |
Colonel
אל“מ |
Givaati Regiment Commander מפקדחטיבת |
21/12/67 | 23582752 | ||
| Itamar Ben Haim איתמר
|
Major
רס”ן |
Paratroopers 101 Peten Deputy Commander צנחנים, |
15/07/78 | 34386045 | |||
 |
Itamar Cohen איתמר כהן |
Lieutenant סגן |
Givaati 435 Rotem, Deputy Company Commander גבעתי |
15/07/85 | 34592295
|
||
| Itamar Eitam איתמר |
Captain
סרן |
Golani 51 Habokim, Company Commander גולני51 |
18/03/81
|
40558439 |
# 38
Nov 12921 נוב38 12921 |
||
 |
Itamar איתמר פרנקל |
Sergeant
סמל |
Kfir כפיר |
29/09/88 |
200756377
|
||
 |
Itay איתי רייס |
Bigadier General תא”ל |
Commander of Palmachim Air Force Base מפקד בסיס |
03/12/63 |
58495755 |
25 Ramat- 47212
התקוה רמת השרון 47212 |
|
 |
Itay Virob איתי וירוב |
Colonel אל”מ |
Kfir Regiment Commander מח“ט |
14/04/66 |
22376974 |
# 71
Ma’ale 19145 מעלה .19145
|
|
|
|
Johnny |
Lieutenant Colonel סא”ל |
401 חטיבה |
Ovda Military Camp מחנה עובדה |
|||
 |
Lior Algai ליאור אלגאי |
Captain
סרן |
Paratrooper 890 Efee, Company Commander צנחנים |
20/01/76 | 21510813 |
||
|
|
Lior Bialik ליאור ביאליק |
Sergeant
סמל |
Nesher Field Intelligence Batallion, Squad Commander גדוד |
08/02/88 |
301535316 |
||
 |
Lior Dadon ליאור דדון |
Sergeant סמל |
Paratroopers 101 Peten, Squad Commander צנחנים
|
13/02/87 |
300468188 |
||
 |
Lior Shushan ליאור שושן |
Captain
סרן |
Kfir 93 Haruv, Operations Officer כפיר 93 |
17/01/82
|
49845423 |
||
 |
Liran Luzon לירן לוזון |
Lieutenant סגן |
Givaati 432 Tsabar, Platoon Commander גבעתי |
21/08/87 | 301092011 | ||
|
|
Liran Nachman לירן נחמן |
Lieutenant סגן |
Givaati 432 Tsabar, Deputy Company Commander גבעתי
|
03/08/85 |
36729234 | ||
 |
Liron Padlad לירון
|
Second Lieutenant סג”מ |
Paratroopers צנחנים |
31/12/88 |
302243134
|
||
 |
Meir Kalifi מאיר כליפי |
Major General אלוף |
Prime Minister’s Military Secretary המזכיר הצבאי
|
30/04/59 |
55659486 |
2 Tarshish st. Caesarea 30889
תרשיש קיסריה 30889 |
|
 |
Michael מיכאל היימן |
Captain
סרן |
605 Hamachatz, Company Commander גדוד |
07/10/81 | 310666037 | Tel Aviv
תל אביב |
|
 |
Michael Taksyak מיכאל טקסיאק
|
Lieutenant (reserve) סגן |
46 Reserve Battalion, Platoon Commander גדוד |
26/05/80 |
306131269 |
||
 |
Michaor Israeli מיכאור ישראלי |
Second Lieutenant סג“מ |
Paratrooperts 101 Peten, Platoon Commander צנחנים |
02/03/87 | 300712387 | ||
| Michelle Ben-Baruch מישל |
Brigadier General תא”ל |
Head of the Artillery Corps קצין תותחנים |
20/11/63
|
69111672 |
10 Alon st. Rosh 48560 אלון ראש העין 48560 |
||
 |
Miki Ohayon מיקי אוחיון |
Lieutenant
סגן |
Paratroopers 202 Zefa , Deputy Company Commander צנחנים |
03/12/86 | 300181906 | ||
 |
Mordechai Kahana מרדכי כהנא |
Colonel
אל”מ |
Gaza Division, Southern Regiment Commander מפקד החטיבה |
04/10/70 | 28059632 | 14 Livne st. Ma’alot 21521 לבנה מעלות תרשיחא 21521 |
|
|
Moshe משה אלרט |
Lietenant Colonel סא“ל |
Shuali Marom Reserve Regiment, Battalion Commander מג“ד |
06/03/88 |
23605132 |
|||
|
|
Moshe (Chico) Tamir משה
|
Brigadier General תא“ל |
Former Commander of the Gaza Division (co-authored the operation) מפקד |
12/08/64
|
58845686 |
Kfar Giladi 12210 כפר 12210 |
|
|
Moshe משה צופי |
Lietenant Colonel סא“ל |
Hanegev Reserve Regiment, Battalion Commander מג“ד |
06/09/72 |
29585635 |
101 Be’er-Sheva 84747 הצבי באר שבע 84747 |
||
 |
Nadav Hajbi נדב
|
Colonel
אל”מ |
Gaza Division Deputy Commander סגן מפקד אוגדת |
10/01/64
|
58455007 |
||
|
|
Nadav Musa נדב
|
Lieutenant סגן
|
Givati 424 Shaked, Deputy Company Commander גבעתי |
01/01/86 |
38031506 | ||
| Nathan Be’eri נתן בארי |
Staff Sergeant סמ“ר |
Golani 12 Barak, Squad Commander גולני |
28/05/89 |
200691061 | |||
 |
Nezah Rubin נצח רובין |
Lieutenant colonel סא”ל
|
Head of Imprisonment Branch of Military Police ראש ענף כליאה |
04/06/68 | 23690159 | ||
 |
Nimrod Schefer נמרוד שפר |
Brigadier General תא”ל |
Head of the Air Division in the Air Force ראש להק אוויר בחיל |
16/03/61 | 56539208 |
# 46
Nataf 90804 נטף 90804 |
|
 |
Nir Ben-David ניר בן דוד |
Lietenant Colonel סא“ל |
188 Regiment 74 Saar Battalion Commander חטיבה |
17/09/73 | 25243403 |
Nofit
36001
נופית 36001 |
|
| Nir Dupet ניר דופט
|
Captain
סרן
|
Paratroopers 202 Zefa, Company Commander צנחנים |
03/10/82 |
66238429
|
# Nov 12921 נוב 12921 |
||
 |
Nir Ohayon ניר אוחיון |
Second Lieutenant סג”מ |
Givaati 432 Tsabar, Platoon Commander גבעתי |
19/08/87 | 301073862 | ||
 |
Niv Samban ניב סאמבן |
Staff Sergeant סמ”ר |
Paratroopers 101 Peten, Platoon Sergeant צנחנים |
14/06/88 | 200345320 |
||
 |
Noam Keshwisky נועם קשיביצקי |
Lieutenant סגן |
401 Reconnaissance Unit, Deputy Company Commander פלס“ר |
23/10/85 |
21663604
|
||
 |
Ofek Gal
אופק גל |
Sergeant
סמלת |
Northern Regiment of the Gaza Division, Field Intelligence Commander אוגדת |
03/07/87 | 300934890 | ||
 |
Ofer Lahad עופר להד |
Staf Sergeant סמ“ר |
402 Reshef Artillery Battalion, Squad Commander גדוד |
08/10/88 |
200494623 | ||
 |
Ofer Levi עופר לוי |
Lieutenant Colonel סא”ל |
Givati Regiment, Deputy Commander סגן מפקד חטיבת |
31/03/72 | 28880656 | ||
 |
Ofer Winter עופר וינטר |
Colonel
אל”מ |
Commander of “Duvdevan” Unit מפקד |
03/02/71 | 27998632 | # 107
Mizpe 15295 מצפה 15295 |
|
 |
Ofer Zafrir עופר צפריר |
Colonel
אל”מ |
401 Regiment Commander מפקד |
29/01/66 |
22280283 |
||
 |
Ofir Edri אופיר אדרי |
Lieutenant
סגן |
Kfir 93 Haruv, Deputy Company Commander כפיר |
30/09/87 | 301168548 | ||
 |
Ohad Dabush אוהד דבוש |
Second Lieutenant סג“מ |
Givaati 432 Tsabar, Platoon Commander גבעתי |
25/10/87 | 301105052 | ||
 |
Ohad Girhish אוהד גירחיש |
Second Lieutenant סג“מ |
Golani 51 Habokim, Platoon Commander גולני 51 |
02/03/87 | 300397445 | ||
 |
Ohad אוהד |
Lieutenant Colonel סא”ל |
401 Regiment, 9 Eshet Battalion Commander חטיבה |
16/03/76 |
38616751 |
||
|
|
Omer Dori
עומר |
Second Lieutenant
סג”מ |
Paratroopers 101 Peten, Platoon Commander
צנחנים101
|
05/12/86 |
300070612 |
||
| Omri Dover עמרי דובר |
Lieutenant סגן
|
401 Regiment 71 Reshef, Deputy Company Commander חטיבה401 |
28/04/86 |
32573214
|
Zur Hadasa 349 99875 צור 99875
|
||
|
|
Or Nelkenbaum אור נלקנבאום |
Second Lieutenant סג”מ |
Nesher Field Intelligence Battalion, Squad Commander גדוד |
11/11/87 |
301062170 |
||
|
|
Oren Bersano אורן ברסאנו
|
Major
רס”ן |
Paratroopers 101 Peten, Company commander צנחנים |
09/05/81 |
42834044 | ||
 |
Oren Cohen אורן כהן |
Lieutenant Colonel סא”ל
|
Golani 13 Gideon Battalion Commander גולני, |
14/01/73 | 25092362 | 7 Agas st. Rosh 48570 אגס ראש העין 48570 |
|
|
|
Oren Kupitz אורן קופיץ
|
Lieutenant סגן
|
Paratroopers 101 Peten, Company Commander צנחנים |
12/02/87 |
300374139
|
||
 |
Oren Zini אורן זיני |
Lieutenant Colonel סא”ל |
Givaati, 432 Tsabar Battalion Commander גבעת |
30/08/74 | 27310176 | 21 Menachem Usishkin st. Ashdod 77513 מנחם אשדוד 77513 |
|
 |
Pinkhas Buchris פנחס בוכריס |
Brigadier General (reserve) תא”ל |
Director General of the Defense Ministry מנכ“ל |
11/04/56 | 53305868 | 7 Maanit st. Kefar 44288 מענית 7 כפר–סבא 44288 |
|
|
|
Ghasan Alian ע‘סאן
|
Lieutenant Colonel סא”ל
|
Golani Reconnossaince Battalion Commander מפקד |
21/03/72 |
29151529 |
Shfaram 20200
שפרעם
20200 |
|
 |
Raz Sarig רז שריג |
Major
רס”ן |
Kfir חטיבת |
22/07/76 |
33069170 |
33 Hamigdal st. Givataim 53447 המגדל גבעתיים 53447
|
|
 |
Ron Asherov רון אשרוב |
Colonel
אל”מ |
Gaza Division, Northern Regiment Commander אוגדת |
26/05/69 |
24417248 |
11 Ufter Ya’akov Tel-Aviv 69362 אפטר תל–אביב 69362
|
|
 |
Ron Levinger רון לוינגר |
Captain
סרן |
Paratroopers 202 Zefa, Company Commander צנחנים |
09/05/83 | 39975230 | ||
| Ron Shirto רון שירטו |
Captain (reserve) סרן
|
Paratroopers, Coordination Officer צנחנים, |
28/05/78 |
32970220 |
|||

|
Ronen Dan רונן דן |
Brigadier General תא”ל |
Commander of Tel-Nof Air-Force Base מפקד |
25/04/61 |
57220790 |
57 Keshet st. Modi’in-Maccabim-Re’ut 71908 קשת מודיעין–מכבים–רעות 71908 |
|
| Ronen Dogmi רונן דגמי |
Lieutenant Colonel סא”ל |
401 Regiment Deputy Commander סגן |
11/01/73 | 29608882 | Sde Yoav 79351 שדה יואב 79351
|
||
|
|
Roi Elkabetz רועי אלקבץ |
Colonel
אל”מ |
7th Regiment Commander מפקד |
02/08/68 |
23668767 | ||
|
Roi רועי אופנהיימר |
Major
רס”ן |
401 Regiment, 71 Reshef Deputy Commander חטיבה
|
10/07/77 |
33802018
|
|||
|
|
Roi Weinberger רועי ויינברגר |
Lieutenant סגן
|
Givaati 435 Rotem, Platoon Commander גבעתי |
26/09/88 |
301818043 | ||
| Sahar Abargel סהר |
Lieutenant Colonel סא”ל |
601 Assaf Battalion Commander מפקד |
17/07/75 |
32433062 |
16 Yeshaia Hanavi Modi’in- 71723
ישעיהו מודיעין– 71723 |
||
 |
Shai Belaich שי בלאיש |
Lieutenant Colonel סא”ל |
Commander of the Shachar Rescue Battalion מפקד גדוד שחר |
07/10/74 | 31938244 |
16 Ashkelon 78360 הסנונית אשקלון 78360 |
|
 |
Shai Fargian שי |
Captain
סרן |
Givati
גבעתי |
06/01/85 | 66658964 | ||
| Shaked Galin שקד גלעין |
Lieutenant סגן |
Navy Vessel Commander מפקד ספינה של |
14/10/85 |
34716712 |
|||
 |
Sharon Itach שרון איטח |
Captain
סרן |
Sachar Rescue Battalion, Company Commander גדוד |
20/03/82 | 60125119 | 58 Ben Gurion st. Sderot 87070 בן–גוריון שדרות 87070 |
|
|
|
Shaul שאול בדוסה |
Lieutenant סגן |
Kfir 93 Haruv, Platoon Commander כפיר |
03/10/86 | 300168200 | ||
| Shay Unger שי אונגר |
Major
רס“ן |
605 Mahaz Engineering Battalion, Deputy Commander סגן
|
31/12/77
|
34488403
|
Tel Aviv
תל אביב |
||
 |
Shimon Siso שמעון סיסו
|
Lieutenant
סגן |
Golani 51 Habokim, Deputy Company Commander גולני |
19/02/86 | 38140091 | … | |
|
|
Shiran שירן מוסא |
Captain סרן |
Nesher Field Intelligence Battalion, Company Commander גדוד |
11/11/84 | 36625655 | ||
 |
Shlomit Tako |
Captain סרן |
“Ein Hasea’ara” Artillery Battery Commander מפקדת
|
23/04/84 |
39821459 | ||
 |
Tal Alkobi טל אלקובי |
Lieutenant
סגן |
188 Regiment 71 Reshef, Company Commander חטיבה |
10/04/87 | 300690435 | ||
| Tal Bendel טל בנדל |
Sergeant סמל |
Paratroopers 101 Peten Squad Commander צנחנים |
10/11/88 |
301723102 |
|||
|
|
Tal Kommemi טל קוממי |
Sergeant סמל |
Paratroopers 101 Peten, Squad Commander צנחנים |
03/01/88 |
200375541 |
||
 |
Tal Ruso טל רוסו |
Major General אלוף |
Head of the Operations Directorate ראש אגף המבצעים |
27/09/59
|
56046295 |
Tel תל אביב |
|
 |
Tamir Oren תמיר אורן |
Lieutenant
סגן |
Paratroopers 202 Zefa, Platoon Commander צנחנים
|
13/11/87 |
200210961 |
||
|
|
Tamir תמיר |
Brigadier General תא“ל |
Replaced the Golani Regiment Commander מילא |
16/12/69 | 24840340
|
59 Kefar 44351 ויצמן כפר סבא 44351 |
|
 |
Tom תום כהן |
Second Lieutenant סג“מ
|
188 Regiment, 74 Sa’ar, Platoon Commander חטיבה |
20/11/87 | 301355517 | ||
| Tomer Meltzmann תומר מלצמן |
Captain
סרן |
Golani 12 Barak, Company Commander גולני |
23/11/81 | 52670791 |
|||
|
|
Geva גבע ראפ |
Colonel אל“מ |
Reserve מפקד חטיבת |
15/01/57 |
54958723 |
||
 |
Tslil Birbir צליל בירביר
|
Second Lieutenant סג”מ |
Golani 52 Habokim, Logistics Officer גולני 52 |
11/07/88 |
200394310 |
||
|
|
Udi אודי שגיא |
Lietenant Colonel סא“ל |
Paratroopers 202 Zefa Commander צנחנים |
Even אבן יהודה |
|||
 |
Uri Ron
אורי רון |
Captain
סרן |
601 Assaf Engineering Battalion, Company Commander גדוד |
29/10/84 | 66348392 |
||
| Yair Keinan יאיר קינן |
Lieutenant
סגן |
7th Regiment Reconnaissance Unit, Squad Commander פלס“ר |
12/12/85 | 38029062 |
|||
|
|
Yair Palay יאיר |
Captain
סרן |
Golani Egoz, Company Commander גולני |
23/02/80 |
40045981 |
Keshet Moshav 12410
מושב קשת
12410
|
|
|
|
Ya’akov (Yaki) Dolf יעקב |
Lietenant Colonel סא“ל |
Paratroopers 890 Efee Battalion Commander צנחנים, |
07/01/76 |
38374211
|
21 Alterman Natan st. Tel Aviv 69415 אלתרמן תל אביב 69415
|
|
|
|
Yaniv Zolicha יניב זוליכה
|
Second lieutenant סג”מ |
Givaati 432 Tsabar, Platoon Commander גבעתי |
22/09/87 |
300932365 |
||
| Yaron Finkelman ירון פינקלמן |
Lieutenant Colonel סא”ל |
Paratroopers מפקד |
25/04/75 | 32172702 |
37 Ra’anana 43255 החשמונאים רעננה 43255
|
||
 |
Yaron Simsulo ירון סימסולו |
Major
רס“ן |
Givati Reconnaissance Platoon Company מפקד |
13/05/82 | 60475142 |
36 Herzlia 46490 יהודה הרצליה 46490
|
|
| Yehosua (Shuki) Ribak יהושע |
Lieutenant Colonel סא”ל |
Golani 51 Habokim Battalion Commander גולנ |
04/05/75 | 32113557 |
Ein 79510 עין צורים 79510
|
||
|
Yehu יהוא עופר |
Colonel אל“מ |
Commander of Sde Dov Air Force Base מפקד בסיס חיל |
19/06/65 |
59584607
|
# Mishmeret 40695 משמרת 40695 |
||
 |
Yehuda Fuchs יהודה פוקס |
Colonel
אל“מ |
Southern Command Operations Officer קצין אג“מ |
10/04/69 | 24293128 | 46 Hadas st. Matan 45858 הדס מתן 45858 |
|
|
|
Yehuda יהודה הכהן |
Lietenant Colonel סא“ל |
Givaati 435 Rotem Commander גבעתי |
.
|
|||

|
Yigal Slovik יגאל סלוביק |
Colonel
אל”מ |
401 Regiment Commander מפקד |
16/06/68 |
23706096 |
52 Kefar 40300 טופז כפר–יונה 40300
|
|
| Yigal Sudri יגאל סודרי |
Major
רס“ן |
Paratroopers 202 Zefa, Deputy Battalion Commander צנחנים |
03/09/69 | 24445801 |
#48
Megadim 30875 מגדים 30875 |
||
| Yizhar Yona יזהר יונה |
Lieutenant Colonel סא”ל |
Head of the Field Compounds Team in the Air-land Cooperation Unit ראש צוות מכלולי |
24/08/66 |
22244834 |
11 Arnon st. Givataim 53529 ארנון גבעתיים 53529 |
||
 |
Yoav Galant יואב גלנט |
Major General אלוף |
Head of the Southern Command אלוף פיקוד |
08/11/58 |
55551832 |
Meshek Amikam 37830 משק עמיקם 37830 |
|
 |
Yoav Gertner יואב גרטנר |
Major (reserve) רס”ן |
Artillery Battery Commander מפקד סוללת |
30/01/79 |
36448439 |
33 Habashan st. Ariel 40700 הבשן אריאל 40700 |
|
|
|
Yoav Mordechai יואב |
Lieutenant סא”ל |
Golani 13 Gideon Battalion Commander (replaced Oren Cohen) גולני (החליף |
21/08/72 | 28893071 |
# 8
Kedumim 44856 קדומים 44856 |
|
 |
Yochai Siemann יוחאי זימן |
Captain
סרן |
Paratroopers 101 Peten, Company Commander צנחנים |
03/05/82 | 60631728 | ||
 |
Yochanan Locker יוחנן לוקר |
Brigadier General תא“ל |
Airforce Chief of Staff ראש מטה חיל |
17/09/56 | 54231030 |
1 Sapir st. Modi’in 71799
ספיר מודיעין– 71799
|
|
 |
Yom-Tov Samia יום–טוב |
Major General אלוף |
Deputy Head of the Southern Command in Emergency סגן אלוף פיקוד הדרום |
18/06/54 |
52204385 |
69 Levy Eshkol st. Tel-Aviv 69361 לוי תל–אביב 69361 |
|
 |
Yonathan Barenski יונתן ברנסקי |
Colonel
אל”מ |
“Negev” Reserve Regiment Commander מפקד |
27/07/71 |
28649697 | Eli
44828 עלי 44828
|
|

|
Yonathan Felman יונתן פלמן |
Captain
סרן |
401 Regiment 75 Romach, Company Commander חטיבה |
07/08/85 |
37042801 |
? | |
| Yoni Weitzner יוני וייצנר |
Sergeant סמל |
Kfir 93 Haruv, Squad Commander כפיר 93 |
16/11/88 |
200051209 | |||
 |
Yossi Abuzaglo יוסי אבוזגלו |
Major
רס“ן |
Southern Command Engineering Operations Officer פיקוד |
20/01/76 | 32380172 |
||
 |
Yossi Bahar יוסי בכר |
Brigadier General תא“ל |
Head of the Infantry Corps קצין חי“ר |
09/04/64 | 58815218 | Be’eri Kibbutz קיבוץ בארי |
|
 |
Yossi Beidaz יוסי ביידץ |
Brigadier General תא”ל |
Military Intelligence, Head of the Research Division אמ“ן, |
14/04/61 | 5710504 | # 332
Kfar 40692 כפר 40692 |
|
 |
Yotam Dadon יותם דדון |
Staff Sergeant סמ“ר |
Givaati 432 Tsabar, Platoon Sergeant
גבעתי |
10/10/87 | 301110466 | ||
 |
Yishai Ankri ישי אנקרי |
Lieutenant סגן |
Givati 424 Shaked, Deputy Company Commander גבעתי |
20/08/86 | 37991908 | ||
|
|
Yishai Green ישי גרין
|
lieutenant סגן
|
Golani “Orev” Unit, Squad Commander גולני |
29/12/84 |
36769156 | ||
| Yuval Halamish יובל חלמיש |
Brigadier General תא”ל |
Head of the Intelligence Corps קצין מודיעין |
20/12/57 |
55005797
|
|||
 |
Zion Bramli ציון ברמלי |
Advanced Staff Sergeant Major רס“ר |
601 Assaf engineering Battalion, Heavy Engineering Team Work manager (D-9 operators) גדוד |
01/02/79 | 35721471 |
||
 |
Zion Shankour ציון שנקור |
Major
רס“ן |
Gaza Division Northern Regiment, Operations Officer אוגדת |
1975 | 13692462 | 38 Yisaschar st. Modi’in- 71724 יששכר מודיעין–מכבים–רעות 71724 |
|
 |
Ziv Danieli זיו דניאלי
|
Staff Sergeant סמ”ר |
Paratroopers 101 Peten, Squad Commander צנחנים |
24/01/88 | 200361509 | ||
 |
Ziv Trabelsi זיו טרבלסי |
Lietenant Colonel סא“ל |
402 Reshef Artillery Battalion Commander מפקד |
15/01/76
|
38316709
|
# 46
Sharsheret 85391 שרשרת 85391 |
|
| Zuf Salomon צוף סלומון |
Second lieutenant סג”מ |
Paratroopers 101 Peten Logistics Officer צנחנים
|
12/01/90 | 200959005 | |||
| Zvi Fogel צבי פוגל |
Brigadier General (reserve) תא”ל |
Southern Command, Head of Fire Management מפקד מרכז האש |
03/11/56 | 54559059 |
1 Korazim 12933 ורד כורזים 12933 |
||
| Zvi Yehuda Kelner צבי יהודה קלנר
|
Lieutenant סגן
|
Givaati Reconnaissance Battalion, Squad Commadner גדס“ר |
1 |
TOP-SECRET – Israel Defense Forces Naksa Violence Presentation





Report – Congress Approves 2012 Intelligence Authorization
Congress last week enacted the Intelligence Authorization Act for Fiscal Year 2012.
“The legislation we are approving today keeps funding for intelligence essentially flat from fiscal year 2011, representing the a meaningful reduction from the President’s request,” said Senate Intelligence Committee chair Sen. Dianne Feinstein (D-CA) on December 14.
Curiously, Rep. Mike Rogers (R-MI), the chair of the House Intelligence Committee, described the outcome somewhat differently on December 16: “The bill is significantly below the President’s budget request for fiscal year 2012 and further still below the levels authorized and appropriated in fiscal year 2011.”
In both the House and the Senate action on the bill there was a conspicuous absence of public debate on any issue of intelligence policy. No dissenting views were expressed. Nor was there any discussion of or insight into current intelligence controversies. For that, one must turn to other venues, such as “Secrecy defines Obama’s drone war” by Karen DeYoung in today’s Washington Post.
UNCENSORED – FEMEN in Poland
TOP-SECRET from the White House – Spain-Germany Spy Organization 1944
DWONLAOD ORIGINAL DOCUMENTS BELOW
UNCENSORED – North Korea and the “Strangest Show on Earth”
Daytime exterior shots in this series can be as old as August 2010. However, many of the photos are from the recent Arirang Mass Games in Pyongyang in October 2010. For background on the Arirang Mass Games, see the Guardian’s 2005 article “Welcome to the strangest show on earth” which describes the games as “one of the greatest, strangest, most awe-inspiring political spectacles on earth.”
UNCENSORED – North Korea Kim Jong-il Hysterical Mourner Photos
 Pyongyang residents react as they mourn over the death of North Korean leader Kim Jong-il in Pyongyang, in this photo taken by Kyodo on December 19, 2011. Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme. REUTERS/Kyodo
Pyongyang residents react as they mourn over the death of North Korean leader Kim Jong-il in Pyongyang, in this photo taken by Kyodo on December 19, 2011. Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme. REUTERS/Kyodo
 Pyongyang residents react as they mourn over the death of North Korean leader Kim Jong-il in Pyongyang, in this photo taken by Kyodo on December 19, 2011. Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme. REUTERS/Kyodo
Pyongyang residents react as they mourn over the death of North Korean leader Kim Jong-il in Pyongyang, in this photo taken by Kyodo on December 19, 2011. Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme. REUTERS/Kyodo
 Pyongyang residents react as they mourn over the death of North Korean leader Kim Jong-il in Pyongyang, in this photo taken by Kyodo on December 19, 2011. Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme. REUTERS/Kyodo
Pyongyang residents react as they mourn over the death of North Korean leader Kim Jong-il in Pyongyang, in this photo taken by Kyodo on December 19, 2011. Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme. REUTERS/Kyodo
 Pyongyang residents react as they mourn the death of North Korean leader Kim Jong-il in Pyongyang, in this photo taken by Kyodo on December 19, 2011. REUTERS/Kyodo
Pyongyang residents react as they mourn the death of North Korean leader Kim Jong-il in Pyongyang, in this photo taken by Kyodo on December 19, 2011. REUTERS/Kyodo
 North Koreans cry and scream in a display of mourning for their leader Kim Jong Il at the foot of a giant statue of his father Kim Il Sung in Pyongyang, North Korea, after Kim Jong Ils death was announced Monday, Dec. 19, 2011. North Korea’s news agency reported that he had died at 8:30 a.m. Saturday after having a heart attack on a train, adding that he had been treated for cardiac and cerebrovascular diseases for a long time. He was 69. (AP Photo/APTN)
North Koreans cry and scream in a display of mourning for their leader Kim Jong Il at the foot of a giant statue of his father Kim Il Sung in Pyongyang, North Korea, after Kim Jong Ils death was announced Monday, Dec. 19, 2011. North Korea’s news agency reported that he had died at 8:30 a.m. Saturday after having a heart attack on a train, adding that he had been treated for cardiac and cerebrovascular diseases for a long time. He was 69. (AP Photo/APTN)
 Pyongyang residents reacts as they mourn over the death of North Korean leader Kim Jong-il in Pyongyang, in this photo taken by Kyodo on December 19, 2011. REUTERS/Kyodo
Pyongyang residents reacts as they mourn over the death of North Korean leader Kim Jong-il in Pyongyang, in this photo taken by Kyodo on December 19, 2011. REUTERS/Kyodo
 North Koreans mourn the death of their leader Kim Jong Il in Pyongyang on December 21, 2011. North Korea said that millions of grief-stricken people turned out to mourn “Dear Leader” Kim Jong-Il, whose death has left the world scrambling for details about his young successor. AFP PHOTO/Kyodo
North Koreans mourn the death of their leader Kim Jong Il in Pyongyang on December 21, 2011. North Korea said that millions of grief-stricken people turned out to mourn “Dear Leader” Kim Jong-Il, whose death has left the world scrambling for details about his young successor. AFP PHOTO/Kyodo
 Pyongyang residents reacts as they mourn over the death of North Korean leader Kim Jong-il in Pyongyang, in this photo taken by Kyodo on December 19, 2011. Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme. REUTERS/Kyodo
Pyongyang residents reacts as they mourn over the death of North Korean leader Kim Jong-il in Pyongyang, in this photo taken by Kyodo on December 19, 2011. Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme. REUTERS/Kyodo
 A woman and her son cry as they mourn the death of North Korean leader Kim Jong-il at a square on Mansu Hill in Pyongyang, in this photo taken by Kyodo on December 19, 2011. Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme. REUTERS/Kyodo
A woman and her son cry as they mourn the death of North Korean leader Kim Jong-il at a square on Mansu Hill in Pyongyang, in this photo taken by Kyodo on December 19, 2011. Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme. REUTERS/Kyodo
 North Korean men cry as they mourn the death of North Korean leader Kim Jong-il in Pyongyang December 19, 2011 in this picture released by the North’s official KCNA news agency on Monday. North Korean leader Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme. REUTERS/KCNA
North Korean men cry as they mourn the death of North Korean leader Kim Jong-il in Pyongyang December 19, 2011 in this picture released by the North’s official KCNA news agency on Monday. North Korean leader Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme. REUTERS/KCNA
 North Koreans mourn in front of a picture of their late leader Kim Jong Il in Pyongyang on December 21, 2011. North Korea said that millions of grief-stricken people turned out to mourn “Dear Leader” Kim Jong-Il, whose death has left the world scrambling for details about his young successor. AFP PHOTO/Kyodo
North Koreans mourn in front of a picture of their late leader Kim Jong Il in Pyongyang on December 21, 2011. North Korea said that millions of grief-stricken people turned out to mourn “Dear Leader” Kim Jong-Il, whose death has left the world scrambling for details about his young successor. AFP PHOTO/Kyodo
 North Koreans mourn as they pay their respects to their late leader Kim Jong Il in Pyongyang on December 21, 2011. North Korea said that millions of grief-stricken people turned out to mourn “Dear Leader” Kim Jong-Il, whose death has left the world scrambling for details about his young successor. AFP PHOTO/Kyodo
North Koreans mourn as they pay their respects to their late leader Kim Jong Il in Pyongyang on December 21, 2011. North Korea said that millions of grief-stricken people turned out to mourn “Dear Leader” Kim Jong-Il, whose death has left the world scrambling for details about his young successor. AFP PHOTO/Kyodo
 (111220) — BEIJING, Dec. 20, 2011 (Xinhua) — Nationals of the Democratic People’s Republic of Korea (DPRK) in China mourn the death of DPRK top leader Kim Jong Il at the DPRK embassy in Beijing, capital of China, Dec. 20, 2011. (Xinhua/Liu Weibing) (ry)
(111220) — BEIJING, Dec. 20, 2011 (Xinhua) — Nationals of the Democratic People’s Republic of Korea (DPRK) in China mourn the death of DPRK top leader Kim Jong Il at the DPRK embassy in Beijing, capital of China, Dec. 20, 2011. (Xinhua/Liu Weibing) (ry)
 North Koreans mourn for deceased leader Kim Jong-il in Pyongyang in this picture released by the North’s official KCNA news agency early December 21, 2011. North Korea was in seclusion on Tuesday, a day after it announced the death of its leader Kim Jong-il, as concern mounted over what would happen next in the deeply secretive nation that is trying to build a nuclear arsenal. REUTERS/KCNA
North Koreans mourn for deceased leader Kim Jong-il in Pyongyang in this picture released by the North’s official KCNA news agency early December 21, 2011. North Korea was in seclusion on Tuesday, a day after it announced the death of its leader Kim Jong-il, as concern mounted over what would happen next in the deeply secretive nation that is trying to build a nuclear arsenal. REUTERS/KCNA
 North Koreans mourn for deceased leader Kim Jong-il in Pyongyang in this picture released by the North’s official KCNA news agency early December 21, 2011. North Korea was in seclusion on Tuesday, a day after it announced the death of its leader Kim Jong-il, as concern mounted over what would happen next in the deeply secretive nation that is trying to build a nuclear arsenal. REUTERS/KCNA
North Koreans mourn for deceased leader Kim Jong-il in Pyongyang in this picture released by the North’s official KCNA news agency early December 21, 2011. North Korea was in seclusion on Tuesday, a day after it announced the death of its leader Kim Jong-il, as concern mounted over what would happen next in the deeply secretive nation that is trying to build a nuclear arsenal. REUTERS/KCNA
 North Koreans mourn for their deceased leader Kim Jong-il at the Kumsusan Memorial Palace in Pyongyang in this picture taken on December 21, 2011 and released by the North’s KCNA news agency on December 23, 2011. Kim Jong-il, who ruled isolated and impoverished North Korea from 1994, died on December 17, 2011, according to the state’s media. REUTERS/KCNA
North Koreans mourn for their deceased leader Kim Jong-il at the Kumsusan Memorial Palace in Pyongyang in this picture taken on December 21, 2011 and released by the North’s KCNA news agency on December 23, 2011. Kim Jong-il, who ruled isolated and impoverished North Korea from 1994, died on December 17, 2011, according to the state’s media. REUTERS/KCNA
 Pyongyang residents react as they mourn over the death of North Korean leader Kim Jong-il in Pyongyang, in this photo taken by Kyodo on December 19, 2011. Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme. REUTERS/Kyodo
Pyongyang residents react as they mourn over the death of North Korean leader Kim Jong-il in Pyongyang, in this photo taken by Kyodo on December 19, 2011. Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme. REUTERS/Kyodo
 Residents kneel down as they mourn the death of North Korean leader Kim Jong-il during a gathering in a square in Pyongyang in this December 19, 2011 still image taken from video. Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme. REUTERS/KCNA
Residents kneel down as they mourn the death of North Korean leader Kim Jong-il during a gathering in a square in Pyongyang in this December 19, 2011 still image taken from video. Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme. REUTERS/KCNA
 Employees of Pyongyang 326 Electric Wire Factory mourn over the death of North Korean leader Kim Jong-il, as they gather in a conference hall in Pyongyang December 19, 2011 in this still image taken from video. Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme.
Employees of Pyongyang 326 Electric Wire Factory mourn over the death of North Korean leader Kim Jong-il, as they gather in a conference hall in Pyongyang December 19, 2011 in this still image taken from video. Kim Jong-il died on a train trip on Saturday, state television reported on Monday, sparking immediate concern over who is in control of the reclusive state and its nuclear programme.
TOP-SECRET – TSA Female Suicide Bombers History Overview

Why Females?
- Terrorist organizations use females because:
- Like most suicide operations, it’s usually simple to plan and low costing.
- In some parts of the world, females have low social status and therefore are considered more expendable.
- Females tend to be more emotional and therefore easier to indoctrinate.
- Since bombers will most likely perish in the attack, there is little fear of them divulging information to security forces.
- Tamil “Black Tigers” carry cyanide pills just in case.
- Most are deliberately uninvolved in the planning in case of capture.
- The media coverage is extensive, especially if the attacker is female.
- Terrorists attempt to embarrass a powerful enemy and show the world that things are desperate that women are now fighting.
- Most importantly, females have the element of surprise!!
- Stealthier attack (tend to draw less attention); in fact on several occasions many female bombers spoke English & wore western clothing & makeup during the attack.
- Sensitivities in searching women (especially in conservative societies).
- Female stereotype (e.g. perceived as nonviolent, feminine, or motherly).
- Women increase the number of combatants to a groups’ depleted manpower.
- There is greater publicity for female bombers (attracts recruits).
- The psychological fear factor of the target (expect anyone can be a bomber).



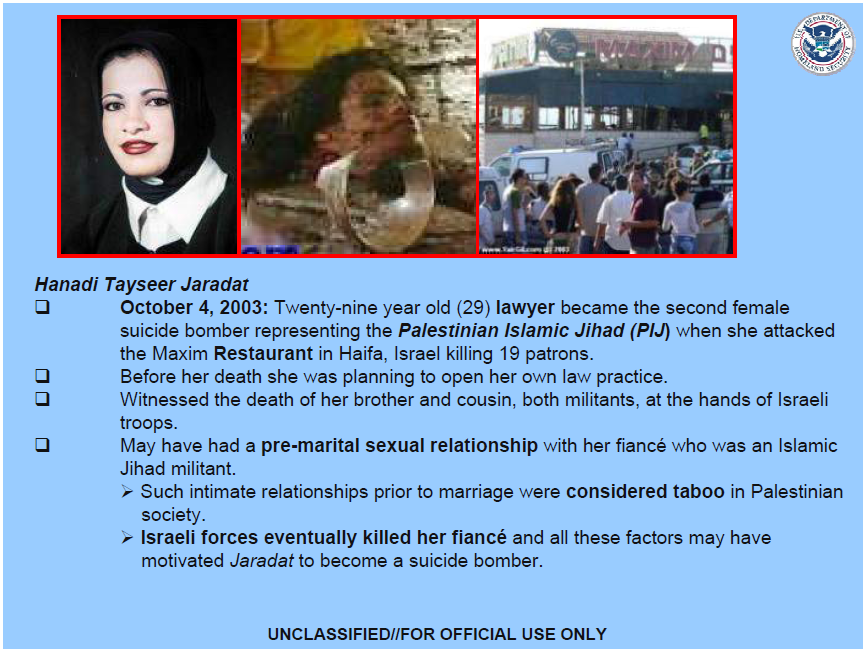
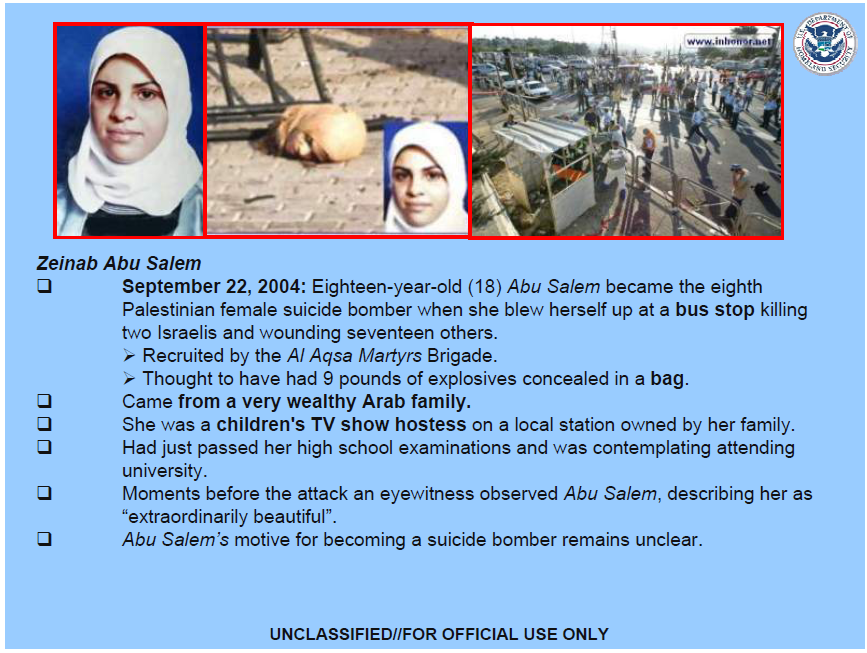


DOWNLOAD ORGINAL DOCUMENT HERE
Christmas greeting from Louis Armstrong – The Night Before Christmas – Wonderfull !
TOP-SECRET-FBI (U//FOUO) Preliminary Analysis of Christmas Day Underwear Bomb

(U//FOUO) The Terrorist Explosive Device Analytical Center (TEDAC) conducted a preliminary analysis of the approximately 30 pieces of evidence recovered after the 25 December 2009 attempted bombing of Northwest Airlines flight 253. The evidence consisted of a plastic syringe initiator with traces of Ethyl Glycol, a main charge of 76 grams of Pentaerythritol Tetranitrate (PETN) wrapped in a container made of thin soft “plastic” film-like material and tape and clothing worn by the bomber. The underwear worn by the bomber was modified to provide storage of the main charge which was anatomically congruent, possibly to avoid detection during screening. The underwear sustained thermal damage. Blue jeans worn by the bomber also sustained thermal damage (scorching) on the inside with small spots of melted plastic on the outside surface.
…




Recommendation – Spy Thriller E-Book Features National Security Archive
Washington, DC, December 24, 2011- The new E Books by bestselling thriller writer James Grady features the National Security Archive as the scene of a key plot sequence, and also as the location for Grady’s video introduction to the series.
The E-Book series includes Grady’s classic book SIX DAYS OF THE CONDOR – which became the basis for the acclaimed Robert Redford movie that subtracted three days – and the renamed and re-introduced thriller, THE NATURE OF THE GAME, featuring the Archive as a key source for the investigative journalist protagonist. Also included in the series are the new novella, CONDOR.NET, and the short story THIS GIVEN SKY.
Grady filmed his video introduction to the series, published by Open Road Integrated Media, in the Archive documents reading room this fall, and testifies, “The Archive’s help and support allowed me to make THE NATURE OF THE GAME more than just another thriller. The Archive’s work in revealing truth behind government and political spin is vital for our global culture.”
The Nature of the Game
In this classic thriller, presented with a new introduction by the author, a down-and-out ex-CIA operative runs from his former masters and propels us like a bullet through the secret spy history of America.
Jud is not too drunk to recognize the assassin. How the hit man found him in this hard-bitten roadhouse, Jud isn’t sure, but he’s not going to go down without a fight. His hands shaking too much for close combat, Jud perches himself on the bar’s roof and drops on the assassin when he steps into the darkness. Though Jud only meant to stun, the man is dead. Jud doesn’t care.
Quitting the CIA has not proven as easy as he hoped. Once one of the Agency’s top killers, Jud’s skills have been dulled by civilian life, and his only chance is to go into hiding. Before he disappears off the grid, he makes a call to Nick Kelley, a D.C. journalist who is one of the only men Jud can trust. Between the two of them, they have a shot atstopping the rot at the heart of the CIA. That is, if the rot doesn’t kill them first.
TOP-SECRET – LulzSec Release: EPIC Language of the Cartels Narco Terminology Report

The El Paso Intelligence Center DEA/CBP Gang Intelligence Unit has been providing intelligence reports on many National gangs affecting this region such as the Surenos, Mexican Mafia and the Nortenos. These reports are condensed and include a short history of the gang, identifiers and current trends for the purposes of providing quick reference and concise information to the street officer that may encounter these individuals throughout the course of their duty.
In 2009, the National Drug Intelligence Center (NDIC) assessed that Mexican drug trafficking organizations (DTOs) were operating in the U.S. in at least 1, 286 cities spanning nine regions. Moreover, NDIC assesses with high confidence that Mexican DTO’s in at least 143 of these U.S. cities were linked to a specific Mexican Cartel or DTO based in Mexico—the Sinaloa Cartel (at least 75 cities), the Gulf Cartel/Los Zetas (at least 37 cities), the Juárez Cartel (at least 33 cities), the Beltrán-Leyva DTO (at least 30 cities), La Familia Michoacán (at least 27 cities), or the Tijuana Cartel (at least 21 cities). NDIC assesses with high confidence that Mexican DTOs will further expand their drug trafficking operations in the United States. Due to the rise in violence throughout the Southwest Region and Mexico, members of the Cartels, their associates and their families have been suspected of moving into many U.S. cities along the border. As a result, agencies are requesting information on ways to identify those involved with drug trafficking organizations. The information included in this report is not set in stone as many of these criminal organizations are dynamic and will alter their methods and trends frequently to avoid detection by law enforcement.

DOWNLOAD THE ORGINAL DOCUMENT HERE
Confidential – Washington, D.C. Fusion Center: Officer Safety and Intelligence Issues

SEARCH OF A VEHICLE’S ELECTRONIC MEMORY: Due to the increased sophistication of automobile electronics, criminal investigators should consider establishing probable cause for a search of the automobile’s electronic memory prior to the execution of a search warrant on a suspect’s vehicle. Newer vehicles are commonly installed with Bluetooth technology which allows cellular telephones to link with the automobile and allow for hands free operation of the phone. Bluetooth technology can download or synchronize the cellular handset’s contact list to the vehicle’s electronic memory storage. The contact list/phonebook capacity varies from just over 100 to upwards of 10,000 entries according to the particular system installed. These entries can be stored and accessible even after the phone is no longer linked to the vehicle and after the ignition is disengaged. If a navigation system is also installed in the vehicle, the contact list may have addresses or GPS coordinates associated with the phone number entries. Although Bluetooth technology allows for two way exchange of data, the Bluetooth Profile implemented in vehicle systems does not allow phonebooks downloaded from one cellular handset to be uploaded to another handset or device. Thus, agents executing a search warrant should be prepared to manually record searched entries. The current trend indicates Bluetooth technology will become more common in vehicles as a means of operating a cellular phone while driving. California, Connecticut, New Jersey, New York, Oregon, Washington State, the District of Columbia, and the U.S. Virgin Islands have all adopted laws banning drivers from talking on handheld cellular phones while driving, with momentum building for the passage of laws in other states. Whereas a few years ago, only high end vehicles from luxury manufacturers provided Bluetooth technology as an option, many manufacturers offer Bluetooth technology as a factory installed option on lower end models such as the Ford Focus. MSNBC reports that by 2013, approximately 30 percent of all new car sales will be purchased with hands free features onboard. Numerous suppliers and manufacturers offer aftermarket kits to install the technology in vehicles lacking factory installation and the kits are selling in the millions. The exploitation of this feature presents investigators with a possible wealth of investigative evidence to be obtained from target’s vehicle by utilizing a search warrant to access the vehicle’s electronic memory. The search of a vehicle’s electronic systems for navigation information or telephone, address, or calendar information stored in a vehicle via a Bluetooth connection implicates the 4th Amendment. A search warrant or an exception to the search warrant requirement, such as exigent circumstances, search incident to arrest, or the vehicle exception may be required to conduct the search.

Confidential – Surenos Special Gang Report about Mexican Gangs

ORIGIN OF THE SURENOS
California’s Hispanic criminal street gangs are divided into the north (norteno) or south (sureno). The dividing line is generally recognized as being near the city of Delano but others argue the dividing line is Bakersfield or somewhere near the area of Kern County.
Historically, Hispanic gangs north of the dividing line have claimed allegiance to the Nortenos and those to the south claimed allegiance to the Surenos. All California Hispanic criminal street gangs claim allegiance to the Nortenos or Surenos, with the exception of the Fresno Bulldogs. Whether it’s on the streets or in the correctional facilities, the Fresno Bulldogs function independently and do not align themselves with Nortenos or Surenos. The Fresno Bulldogs are a unique California based gang that has the power, strength and a large enough membership to stand on its own and remain free from the politics of the Nortenos and Surenos. All other Hispanic criminal street gangs are forced to choose a side whether they want to join in or not.
SURENO
The word sureno translates to “southerner” in Spanish and the word “sur” translates to the word south. The Sureno gang or gang movement includes the three California “super” gangs–18th Street, Florencia 13 and Mara Salvatrucha–as well as hundreds of other Hispanic gangs. Surenos include all Southern California criminal street gangs except the Maravilla* gangs of East Los Angeles.
The Sureno gang structure is very loose and has no formal rank structure but there are well-known veteranos and “shot callers” who
have influence within the gangs. *The early residents of a lowcost housing project in East L.A. nicknamed the housing project maravillosa (Spanish for marvelous). In the early 1950s various maravillas were responsible for the creation of the Mexican Mafia prison gang. Several of the maravilla gangs members becames disillusioned with the newly-formed Mexican Mafia. Many of these maravilla gang members chose to no longer align themselves to the mafia. A gang that developed nearby called itself Maravilla and with the gang’s believe that due to its history and standing within the community, it should not and would not have a loyalty to the Mexican Mafia. Gang members determined they would not pay taxes as other gangs willingly had done. This blatant act of defiance and disrespect resulted in members of the Maravilla gangs being placed on a gang “green light” list by the Mexican Mafia. As a result of this kill on sight order by the Mexican Mafia, gangs claiming allegiance to the Surenos were bitter enemies with the Maravilla gangs on the street. Once incarcerated, however, Maravilla gang members sought protection to avoid being killed by members of the Mexican Mafia. It was not until recently that the “kill on sight” order against the Maravilla sets was recalled by the leadership of the Mexican Mafia.Currently there are several gangs in the Maravilla area that are loyal to the Mexican Mafia. There are also several Maravilla gangs in that area that aren’t aligned to the Mexican Mafia that are referred to as Los Maravillosos.They are led by those men that were disillusioned by the
original mafia.…
EAST L.A. GANGS
MARAVILLA
The Maravilla (MV) gangs, also called varrios, cover a large part of East Los Angeles and are broken up into various cliques such as Hoyo Mara (the “Hole” because of the lowered terrain it sat in), Ford Mara (after Ford Blvd.), Arizona Mara (a main street in East L.A.), Marillana Mara (MMV, sometimes confused with Mexican Mafia, they were around way before), Rock Mara (after a big rock in the projects), etc.
Maravilla predates the Mexican Mafia but at one time there were a lot of Maravillas in la EME. Joe Morgan, a figurehead for the EME for over 20 years was well known in East Los and Maravilla. There are other Maravilla gangs in the U.S., some may be connected to the East L.A. groups, and others may have just used the same name. Some MV and former EME members did not like the EME trying to tax them and telling them what to do in their own varrio. There was a green light put out by the EME on the MV’s for their rebellion. The MV had to be separated from EME and Sureño sympathizers in the L.A. County jail. To date this green light has not been lifted. One of the shotcallers for la EME is Alfred “Chato” Sandoval from Arizona Maravilla, so there are some MV still loyal to the EME and Sureños.
WHITE FENCE
One of the first barrios in Los Angeles to form its own gang was “White Fence.” The gang was called that because of a white picket fence that ran along much of its territory near railroad tracks near the Los Angeles River and downtown. WF’s original barrio is all of Boyle Heights and WF is still strong along Lorena Street. They allegedly used to have cliques throughout the San Gabriel Valley and Northeast L.A. Maravillas’ original barrio is farther in East L.A. These two gangs have a decades old rivalry, the longest ongoing feud in L.A. Both of these barrios have lost extensive territory and are now midgets compared to their former size, but in actual gang members, they are bigger than ever. There is some evidence that the Hazards, Avenues, Toonerville, and Frogtown were all once cliques off of White Fence, according to veterano members
from White Fence. Kilroy Roybal is with Victory Outreach and was recently in an accident.PRIMERA FLATS AND 4TH FLATS
These gangs were both historically part of the Aliso Village government housing projects. Primera Flats is of course more notable as far as street
gangs are concerned. It lies approximately three miles east of the Los Angeles City Hall. This area also has street gangs that came into prominence in the early 1940s. It also was originally built for military personnel, but like Hazard, it became a low-income housing project. Primera Flats also had some bitter fights with some of the same gangs that Hazard fought with. It, being closer to downtown, however, also had problems with many of those downtown gangs. Primera Flats, like Maravilla, have fights with street gangs within their own turf.HAZARD
The government housing project called Ramona Gardens is the oldest type of housing in the East Los Angeles area. It was built for the families of the military in 1941. As World War II waned toward the end of 1945, most of the military families had relocated and families that were either dependent on a stipend from Social Security, or were a low income family started moving in. This “barrio” has actually two separate areas: Big Hazard and Little
Hazard. Hazard got its name from a park at the end of Lancaster Avenue and Soto Street. There also is a street named Hazard. Big Hazard encompasses all the housing area and also the park. Little Hazard, is that area from west of Soto Street along Norfolk and to the railroad tracks across from Lincoln Park. Robert “Robot” Salas (deceased Dec. ’04) was from Hazard and was involved in the first major EME confrontation with the NF at San Quentin Sept. 16, 1968. Old EME shotcaller in the Fed-BOP Adolf “Champ” Reynoso is also from Hazard as is Manuel “Cricket” Jackson. This varrio has also been the focus of much violence over the years. EME David “Big Smilon” Gallardo from Hazard, “Pee-Wee” Aguire from the Aves, and “Cowboy” Therrien from Big Basset were found guilty of killing “Rocky” Luna who was from Hazard and an advisor on the movie by Edward James Olmos, “American Me.” Ana Lizarga, another movie consultant, also was killed. They were angry at her for snitching off a “dope house” and “Charlie Brown” Manriquez for not taking care of business and living like a bum when he got out. “Lives in Hazard” depicts some of these people and also includes a fairly new gang called M.C. Force, or Michigan Criminal Force, named after a street east of there in East L.A. street east of there in East L.A.
HOYO SOTO
Deceased EME shotcaller Benjamin “Topo” Peters claimed this varrio. EME Gilbert “Shotgun” Sanchez (deceased) also lived there. His son “Ray-Ray” dropped out.
VARRIO NUEVO ESTRADA
Hazard Gang also had trouble with Varrio Nuevo Estrada. The Estrada Courts Projects are just off of Olympic Street and just east of Soto Street and west of Lorena. There are many colorful murals in this project. VNE are not found much outside of the Estrada Courts area. Many other L.A. gangs are known even outside of CA. Ray “Mundo” Mendoza and “Eddie Sailor” Gonzales claimed VNE and rolled on the EME in the 70s. VNE has a reputation for being EME informants. EME Jimmy “Smokey” Sanchez is ok at the Bay.
SAN GABRIEL VALLEY (SGV)
The San Gabriel Valley grew tremendously in the 1960s and ’70s. Many families who were originally from East L.A. moved to the SGV. Later, some from SGV moved out to the Inland Empire. Gangs like El Monte Flores, El Monte Hicks, La Puente, Basset Grande, Bolen Parque (Baldwin Park), have been around for decades and have gang members very involved in La EME.
SANGRA
“Sangra” is a very old gang. A former member, “Stumpy” Valencia, was involved in a sanctioned homicide of EME member Alex “Moe” Ferrel. Ferrel had been involved in the rape of a woman outside of Sacramento soon after being paroled. This, combined with his siding with the Nico Velasquez of the Folsom EME faction and against Joe Morgan of the San Quentin faction concerning the BGF war, put him “in the hat.” Velasquez was later killed.
EL MONTE FLORES
El Monte Flores is an old clique that dominated gang activity in the City of Monte for decades. El Monte Hicks is another gang located in the city. David Alvarez from EMH was a SUR/EME rep at the L.A. county jail who would pass green-light lists. Both gangs declared war on North Side Monte and that clique was near the top of the EME green light list for years. Many members of EMF are also EME members. Louie “Pelon” Maciel was a EMF member involved in one of the RICO trails. He was found to be involved in a large drug running group at the L.A. Co. Jail that was busted up in “Operation Hard Candy.” Jo-Jo Perea was a “money man” for the prison gang. “Danger” Validivia was a EMF member who would do hits for La EME and was known to secrete a razor blade under his dentures.
LA PUENTE 13
La Puente or just Puente 13, is another large and old clica. They have since broken up into smaller factions who do not always affiliate with one another. The Happy Homes varrio (not to be confused with Happy Town in Pomona) does affiliate with La Puente on occasion. La Puente can also be found in the Valinda Flats area where they have intruded. Their rivals are Valinda Flats gang members and in recent years there has been violent gang activities in this area. Deceased Folsom EME Nico Velasquez was from La Puente.
BASSET GRANDE
Basset Grande, also known as Big Basset, dates back to the 1950s. The turf boundaries of BG varrio are roughly Fransiquito Blvd. on the north, Don Julian on the south, the 605 Freeway on the west, and Sunquist Blvd. on the east. It has had several members involved with La EME. The Huguez brothers are similar to the Grajeda family in that many of their blood relatives have been involved with La EME. A member named “Cowboy” Therion was involved in a RICO trial in L.A. of EME members. Cowboy has “Mafioso” tattooed across his abdomen and has now dropped out of the prison gang.
BOLEN PARQUE 13
Bolen Parque, in the city if Balwin Park, has several gangs in its area. Local citizens and community activists have resorted to painting dark green ivy murals on major streets to keep the tagging down. Gangs are very active in East Side Bolen Parque.
POMONA VALLEY GANGS
Pomona is a large and isolated city in the extreme East of the San Gabriel Valley in L.A. County. It is home to the L.A. County Fair at the famous Ganesha Park. It is home to many different various gangs. The biggest and oldest is the Pomona 12 Street gang named after a street there. It claims its origins back to the 40s. P12 is also called Sharkies and at one time they had their own “official” park which the city has tried to reclaim back from the gangsters. Their symbol is a shark with a “cherry” in its mouth. P12 has had several members in the past in La EME. A few P12 are in Oregon, Washington State, and even some in PA! The secondary gang is Cherry Ville, P12’s longtime rivals, which is at least from the 60s. Their territory lies right up to P12 and centers around Hamilton Park. Then there is P Michoacanos, E/S Carnales, W/S Happy Town, Pomona Sur XIII who are also rivals with P12 and many have now moved to the La Puente area or out to Las Vegas. There was a group which is now mostly defunct called North Side Pomona. There is a West Side Pomona who are also in Washington. There is even a Hazard clique, and a Dog Town clique, 18th Street and MS clique there too. Pomona is in L.A. County but closer to the Inland Empire than it is to L.A. so rivals with most varrios in the Inland Empire. Recent suppression efforts by law enforcement have reduced some of the violence.
INLAND EMPIRE GANGS
The San Gabriel Valley grew tremendously in the 1960s and ’70s, just as the Inland Empire did in the 1980s and ’90s. The greater L.A. area is very spread out; many families from East L.A. moved to the San Gabriel Valley, and some from SGV moved out to the Inland Empire past Fontana, Colton, and Rialto as land became more and more scarce, eating up valuable farmland, orchards, and vineyards.
The Ontario Black Angels are infamous for being the clique of disgraced EME shotcaller “Tupie” Hernandez’ varrio. They have junior cliques such as OVS or Ontario Varrio Sur. One member recently tried to make his bones by attempting to shoot at an Ontario cop. There are the Chino Sinners which “Tupie” got in trouble for when he stepped in while the EME wanted a “green light” on them. His mother also got involved in EME politics that resulted in several of his family being assaulted and in combination with his insults about Joe Morgan and not making a phone call for the carnales (brothers), led to him being stabbed in federal detention. Daryl Castrellon had the Black Angels’ reins in California Department of Corrections, but since parole has picked up “the Bible.” There is still a lot of money to be made in the fast growing Inland Empire! Back in Arizona in 1999, Officer Dale Thrush identified, with help from a CI, a Black Angel member named Frank “Smoky” Alcala, as OVS. He was wanted out of California on a parole violation. He had all the other gang members, from different gangs, scared of him and thinking he was EME. Reports were coming in that he was taxing other members, allegedly for the EME and was a suspect in a home invasion where a stabbing occurred. Alcala was a suspect in a stolen vehicle pursuit then fled on foot and two loaded pistols were left behind. That night he was in the parking lot of a Circle K, having just done a strong arm robbery on a 38th Street gang associate. He was in the process of carjacking the vehicle of a 38th Street gang member. Shots were fired and law enforcement responded. Dale pulled in and was about to exit the vehicle when “Smoky” drove the Dodge Ram right into the driver’s door. Luckily, Dale was able to jump inside. Alcala then rammed the door again. We put 16 rounds into the vehicle and would you believe he was only hit in the arm and butt! These guys are very serious! Along with other tattoos he had a large letter “B” on the back of his left arm and a large letter “A” on his right arm, along with “Ontario” on the back of his neck.
“Spider” Arriaga was an old EME members mistakenly killed a few years ago by his crime partner “Colorado” Arias from Colton (also EME) during a robbery. Members like Roland Berry have been involved in disputes around Bloomas. Recently, there was a police sting operation on EME operating in the IE. Unfortunately, police hit them too late so evidence was minimal. Word is, the EME carnales at Corcoran and Pelican Bay found out what was coming down, got word out and all mail stopped, which just goes to show they have a better network than we do! In Riverside, Casa Blanca, out in Rancho Cucamonga, the Cuca Kings, and Corona has various cliques, the oldest which centers around 6th Street.
Verdugo Gangsters are from San Berdoo (San Bernardino). West Side Verdugo is the predominant gang in the middle of the valley. The major cliques of WSV are 7th Street (CSL), Sur Crazy Ones (SCO), and Little Counts. As a whole though, the entire Verdugo gang has a lot of problems and is constantly being challenged by other gangs from mostly the Los Angeles areas. The two that are currently showing a presence here are Florencia Trece and King Boulevard Stoners (KBS). Then there is the perpetual WSV enemy East Side Trece. We see a lot of LA gang members moving into the area and causing problems, 18th Street being one of them.
NORTH L.A. GANGS
HIGHLAND PARK 13
This gang is located in the area just west of Pasadena. It has a high Hispanic population, and as the case in many of the barrios, a small percentage belong to HP13. They claim origins going back to the early 1940s.
AVENUES
Northeast Los is an old region of LA barrios. Its most famous, and perhaps most infamous gang is the Avenues or Avenidas gang, which is named after the numbered avenues off of Figueroa. They themselves have several cliques such as 43rd Avenue and Cypress Avenues and did not get along at first but later joined together for convenience. The 43rd allegedly broke off of Hazards and the Cypress allegedly broke off Frogtown. The Avenues is a very large gang in numbers and been subject to City/County Community Law Enforcement and Recovery (CLEAR). Alfred “Tigre” Salinas is from the Aves. EME member “Pee-Wee” Aguirre is from La EME. His brother “Lil One” had been causing problems in the L.A. Co. Jail. EME Black Bob Ramirez (deceased Sept. ‘05) claimed Aves and Canta Ranas.
…
WEST L.A. GANGS
18TH STREET
This gang started on the West Side of Los Angeles around 1965. It was originally made up largely of second generation Hispanic immigrants. As the 18th Street gang began to battle with more established Chicano gangs, they began to recruit outside of the Hispanic community. ILGIA estimates their size in 2006 to be 20,000+ members in over 120 U.S. cities. They are also big in Latin America. According to the Department of Justice, an estimated 60% were illegal immigrants. Colors are often black and grey (Raider colors), dark blue (to show support for SUR13), but they may wear red on the East Coast and beads as well. Common hand signs are forming an “18” or thrown sideways “E” (for Eighteen). Common 18th Street tats include 18, XV3, XVIII, Diesiocho, 666 (=18).
The 18th Street gang has chapters on the North (Hollywood area), in East L.A./County, and in South Central Los Angeles where their traditional enemies are the Florencia 13 gang. They also fight Black P-Stones (R20s) in South Central and in jail. They now have cliques in San Diego, Las Vegas, Inland Empire, the Bay Area, Chicago, Texas Florida, and even a clique in New York. They are big in Portland, Oregon, and in Washington state where they have a web site. They are seen in New Jersey where they fall under La Raza Unida umbrella. They have whole towns claiming allegiance to them in El Salvador, Guatemala, and Mexico with large cliques in Mexico City DF and Tijuana. They even show a clique from Australia on their main 18th Street website!
MARA SALVATRUCHA
When it comes to Sureno gangs, MS13 is not the biggest, but by most accounts is the most violent in the U.S. today. The Mara Salvatrucha (MS) gang was originally made up of mostly Salvadorans and originated in the Los Angeles area. During and after the civil war that was going on during the 1980s in El Salvador, many Salvadorans migrated to the Pico-Union District around the area of McArthur Park, which has the highest population density in the United States outside of New York City. Other neighborhoods that they moved into in Los Angeles County were Westlake, Hollywood, San Fernando Valley and East L.A. When the MS first started out, many of their members were called “MS Stoners.” They had long hair and would listen to loud heavy metal music and would drive souped-up muscle cars. A common MS handsign is the index finger and pinky finger held up. Some of the members were also into Satanism and were involved with a Salvadoran National Guard Unit called “Santanas.” There is another MS clique called “Sailor’s” allegedly started by former military members.
Allegedly many MS were initially members of soccer teams. Later, they evolved into a full-fledged gang, in part, to protect themselves from the 18th Street gang that was nearby and victimizing them. This is how Mara Salvatruch was originally translated from Spanish to English by law enforcement when they first learned of this violent gang. “Mara” meant gang, “Salva” was for El Salvador, and “trucha” for beware. However, it turns out that many MS gang members and the Central American community are in agreement that “Mara Salvatrucha” simply means Salvadoran Gang. “Mara” means gang or group, and “Salvatrucha” slang for Salvadoran, hence the meaning Salvadoran Gang. The MS did not consider themselves Sureños for approximately 15 years. Many of the older MS do not have any “13″ markings, just “MS” tattoos. Finally the Mara Salvatrucha joined the Sureño back in 1994, during the Black vs. Brown riots in the Los Angeles County Jail system. Several Mexican Mafia RICO suspects had strong ties to MS and it is now common to see MS13. Their original colors were black from their Santanas roots, but they will also wear blue and white colors, which match the Salvadorian flag. On the East Coast they often wear blue and white beads. The MS have started taxing street vendors, prostitutes, small businesses, and street level drug dealers working in their turf. Failure to pay will most likely result in some type of violence. Mexicans, Guatemalans, Hondurans, and other Central Americans may join MS, but not exclusively.
DOWNLOAD FULL REPORT HERE
TOP-SECRET – Vatican Bank May Have Used Clergy as Fronts for Mafia, Corrupt Businessmen
 Pope Benedict XVI talks to the head of the Vatican bank Ettore Gotti Tedeschi (R) in this September 26, 2010 file photo. Gotti Tedeschi has been placed under investigation by Rome magistrates for suspected money-laundering by the bank, judicial sources said on September 21, 2010. REUTERS/OSSERVATORE ROMANO/Files
Pope Benedict XVI talks to the head of the Vatican bank Ettore Gotti Tedeschi (R) in this September 26, 2010 file photo. Gotti Tedeschi has been placed under investigation by Rome magistrates for suspected money-laundering by the bank, judicial sources said on September 21, 2010. REUTERS/OSSERVATORE ROMANO/Files
Vatican Bank ‘allowed clergy to act as front for Mafia’ (Indepdendent.co.uk):
The Vatican Bank is under new scrutiny in a case involving money-laundering allegations that led police to seize €23m (£19.25m) in September.
The Vatican calls the seizure of assets a “misunderstanding” and expresses optimism it will be quickly cleared up. But fresh court documents show that prosecutors say the Vatican Bank deliberately flouted anti-laundering laws “with the aim of hiding the ownership, destination and origin of the capital”. The documents also reveal investigators’ suspicions that clergy may have acted as fronts for corrupt businessmen and Mafia.
The documents pinpoint two transactions that have not been reported: one in 2009 involving the use of a false name, and another in 2010 in which the Vatican Bank withdrew €650,000 from an Italian bank account but ignored bank requests to disclose where the money was headed.
The new allegations of financial impropriety could not come at a worse time for the Vatican, already hit by revelations that it sheltered paedophile priests. The corruption probe has given new hope to Holocaust survivors who tried unsuccessfully to sue in the United States, alleging that Nazi loot was stored in the Vatican Bank.
Yet the scandal is hardly the first for the bank, already distinguished from other banks by the fact that its cash machines are in Latin and priests use a private entrance.
In 1986, a Vatican financial adviser died after drinking cyanide-laced coffee in prison. Another, Roberto Calvi, was found dangling from a rope under London’s Blackfriars Bridge in 1982, his pockets stuffed with money and stones. The incidents blackened the bank’s reputation, raised suspicions of ties with the Mafia, and cost the Vatican hundreds of millions of dollars in legal clashes with Italian authorities.
On 21 September, financial police seized assets from a Vatican Bank account. Investigators said the Vatican had failed to furnish information on the origin or destination of the funds as required by Italian law.
The bulk of the money, €20 million, was destined for the American JP Morgan bank branch in Frankfurt, Germany, with the remainder going to Banca del Fucino, an Italian bank.
Vatican Bank mired in laundering scandal (AP):
The Vatican has pledged to comply with EU financial standards and create a watchdog authority. Gianluigi Nuzzi, author of “Vatican SpA,” a 2009 book outlining the bank’s shady dealings, said it’s possible the Vatican is serious about coming clean, but he isn’t optimistic.
“I don’t trust them,” he said. “After the previous big scandals, they said ‘we’ll change’ and they didn’t. It’s happened too many times.”
He said the structure and culture of the institution is such that powerful account-holders can exert pressure on management, and some managers are simply resistant to change.
The list of account-holders is secret, though bank officials say there are some 40,000-45,000 among religious congregations, clergy, Vatican officials and lay people with Vatican connections.
The bank chairman is Ettore Gotti Tedeschi, also chairman of Banco Santander’s Italian operations, who was brought in last year to bring the Vatican Bank in line with Italian and international regulations. Gotti Tedeschi has been on a very public speaking tour extolling the benefits of a morality-based financial system.
“He went to sell the new image … not knowing that inside, the same things were still happening,” Nuzzi said. “They continued to do these transfers without the names, not necessarily in bad faith, but out of habit.”
It doesn’t help that Gotti Tedeschi himself and the bank’s No. 2 official, Paolo Cipriani, are under investigation for alleged violations of money-laundering laws. They were both questioned by Rome prosecutors on Sept. 30, although no charges have been filed.
In his testimony, Gotti Tedeschi said he knew next to nothing about the bank’s day-to-day operations, noting that he had been on the job less than a year and only works at the bank two full days a week.
According to the prosecutors’ interrogation transcripts obtained by AP, Gotti Tedeschi deflected most questions about the suspect transactions to Cipriani. Cipriani in turn said that when the Holy See transferred money without identifying the sender, it was the Vatican’s own money, not a client’s.
Gotti Tedeschi declined a request for an interview but said by e-mail that he questioned the motivations of prosecutors. In a speech in October, he described a wider plot against the church, decrying “personal attacks on the pope, the facts linked to pedophilia (that) still continue now with the issues that have seen myself involved.”
…
In the scandals two decades ago, Sicilian financier Michele Sindona was appointed by the pope to manage the Vatican’s foreign investments. He also brought in Roberto Calvi, a Catholic banker in northern Italy.
Sindona’s banking empire collapsed in the mid-1970s and his links to the mob were exposed, sending him to prison and his eventual death from poisoned coffee. Calvi then inherited his role.
Calvi headed the Banco Ambrosiano, which collapsed in 1982 after the disappearance of $1.3 billion in loans made to dummy companies in Latin America. The Vatican had provided letters of credit for the loans.
Calvi was found a short time later hanging from scaffolding on Blackfriars Bridge, his pockets loaded with 11 pounds of bricks and $11,700 in various currencies. After an initial ruling of suicide, murder charges were filed against five people, including a major Mafia figure, but all were acquitted after trial.
While denying wrongdoing, the Vatican Bank paid $250 million to Ambrosiano’s creditors.
Both the Calvi and Sindona cases remain unsolved.
CONFIDENTIAL-Mafia, Biker Gang Criminal Cartels Conspire to Control Road Construction Contracts in Quebec

It’s been whispered about for years, but now the government’s anti-corruption squad says it has proof that organized crime has infiltrated the construction industry and influenced political parties.
The report by former Montreal police chief Jacques Duchesneau and Quebec’s anti-corruption squad and obtained by Radio-Canada and La Presse comes after a year-and-a-half-long investigation.
The UPAC (Unité permanente anticorruption) report, which does not name any firms or individuals, found that prices are regularly hiked by engineering consulting companies and that contractors regularly overrun their costs.
It said Quebec’s Transportation department is laidback about challenging prices, and when it challenges an invoice, the companies often launch a civil suit because they are aware the department will often settle out of court.
Even more damning, the report alleges that Transportation Ministry employees were paid to provide companies with privileged information so those businesses could win government contracts.
…
Radio Canada released the report in its entirety Thursday evening on its website.
“We have discovered a deeply-rooted and clandestine universe, of an unsuspected scope, that is harmful to our society – in terms of security, the economy, justice and democracy,” the report states.
It claims the road construction industry is run by “a small circle of professionals and business people who specialize in bending the rules in place to enrich themselves at the expense of taxpayers.”
However, it is admitted in the report that the extent of organized crime’s involvement in the industry is difficult to gauge.
“A large number of Quebec construction businesses maintain links with criminal organizations,” it states. “We therefore strongly presume that some among them have an influence on the contracts handed out by the government, and that they have even set foot on the (transport) ministry’s work sites. Even though it is impossible to evaluate the extent of it, we can suspect how much the mafia exerts a presence and its influence in the construction industry.”
Quebec report sheds light on ‘corruption and collusion’ (Globe and Mail):
The report, which was leaked to some media outlets, said that organized crime, biker gangs, construction companies and engineering firms conspired to inflate the cost of road-building projects, devising schemes that also involved kickbacks to political parties.
Cost overruns were planned and became common practice in the industry, according to the report. “Cartels” consisting of the Mafia, biker gangs and construction companies conspired to eliminate competition and manipulate the public-tendering process.
“The suspicions are persistent to the point that a criminal empire was on the verge of being consolidated in the area of road construction,” Mr. Duchesneau wrote in the report’s preamble.
Close ties between Mafia-controlled construction companies and engineering firms and political parties were particularly worrisome, the report said.
“The more contracts they get, the more they give; the more they give, the more influence they have; the more influence they have, the more contracts they get. And the influence is exercised everywhere whether it is by becoming members of foundations or doing fundraising for charity organizations. They become almost untouchable,” a former political aide told the investigators.
The report suggests the Transportation Ministry has lost control over roadwork projects by contracting out work to private firms. In doing so, it said, the ministry lost the expertise to supervise the projects properly, allowing collusion and influence peddling to become rampant.
In one example cited in the report, engineers would say 1,000 truckloads were needed to remove contaminated soil from a construction site, knowing that 100 would do, and the unused money would find its way into the pockets of crime organizations, engineering firms and political parties.
“The Ministry of Transportation has no means to sanction engineering firms who make up wrong cost evaluations and poor plans,” the report stated.
New transport minister won’t release damning document (Montreal Gazette):
A new era of transparency was promised by Pierre Moreau when he took over as transport minister.
But, a week into the job, Moreau has refused to make public a damning report into collusion in Quebec’s construction industry that points the finger at organized crime, construction and engineering firms, Transport Quebec and political parties.
An anti-collusion squad led by former Montreal police chief Jacques Duchesneau prepared the report. Transport Quebec hired him in 2010 to investigate allegations of price-fixing and influence peddling in road contracts.
A handful of media outlets have obtained and published excerpts of Duchesneau’s report. But few have read the entire 78-page document.
On Thursday, Moreau told reporters that when he promised more transparency, he was referring to inspection reports – not a document to be used in criminal probes.
Secret from the FBI – Former Union Leader Admits Theft of Union Funds
BUFFALO, NY—U.S. Attorney William J. Hochul, Jr. announced today that former union leader Ellis Woods, 61, of Clarence, N.Y., pleaded guilty to wire fraud before U.S. District Judge Richard J. Arcara. The charge carries a maximum penalty of 20 years in prison, a $250,000 fine or both.
Assistant U.S. Attorney Russell T. Ippolito, Jr., who is handling the case, stated that the defendant devised a scheme to defraud the Buffalo Educational Support Team (“BEST”). BEST is a union representing more than 900 teacher’s aides and assistants in the Buffalo school district. While working as the elected president of BEST, Woods was provided a union-issued credit card. Between November 18, 2008, and February 7, 2011, Woods used the union credit card to pay for personal expenses, including gambling expenses that he incurred at local area casinos. In total, Woods stole $44,987.70 in union funds.
“Union members contribute hard earned money to benefit the union as a whole, not to line the pockets of union leaders,” said U.S. Attorney Hochul. “Our office will not tolerate such behavior and will vigorously prosecute officials in any organization who seek to take advantage of members.”
The plea is the result of an investigation by the U.S. Department of Labor and the Federal Bureau of Investigation, under the direction of Christopher M. Piehota.
Sentencing is scheduled for April, 19, 2012 at 1:00 p.m. in Buffalo, N.Y. before Judge Arcara.
From the FBI – Convent Employee Charged with Embezzling More Than $100,000 from Catholic Nuns
SAN JOSE, CA—A former lay employee for the Sisters of the Holy Names of Jesus and Mary Catholic Convent (the Convent) in Los Gatos, Calif., was charged yesterday with 14 counts of wire fraud and three counts of mail fraud, United States Attorney Melinda Haag announced. According to the indictment, Linda Gomez (a/k/a Linda Surrett), 65, of Sunnyvale, Calif., used her administrative positions to embezzle cash and to charge personal expenses to a Convent charge card.
According to the indictment, between 1987 and 2010, Gomez worked for the Convent in various administrative capacities, including as the director of food services and the manager of an on-site convenience store. As part of her professional responsibilities, Gomez made purchases for the 75 Catholic nuns and 60 lay employees at the Convent. The Indictment charges that between March 2008 and her resignation in May 2010, Gomez used various methods to embezzle from the Convent, including obtaining fraudulent reimbursements or credits for products she falsely claimed she had purchased for the Convent and its nuns. The Indictment states that Gomez embezzled more than $100,000 from the Convent. In addition to embezzling more than $47,000 in cash, Gomez also fraudulently diverted more than $53,000 of Convent funds for personal expenses such as jewelry, high-end cutlery, purses, shoes, kitchen appliances, and numerous purchases on the QVC and Home Shopping Networks,
The defendant will be issued a summons to make an initial appearance on Jan. 10, 2012, before United States Magistrate Judge Paul S. Grewal. The case is assigned to United States District Court Judge Lucy Koh.
The maximum statutory penalty for wire fraud in violation of Title 18, United States Code, Section 1343, and mail fraud in violation of Title 18, United States Code, Section 1341, is 20 years in prison and a fine of $1 million, plus restitution. Any sentence following conviction would, however, be determined by the court after considering the federal sentencing guidelines, which take into account a number of factors, and would be imposed in the discretion of the court.
Please note: An indictment contains only allegations against an individual and, as with all defendants, Gomez must be presumed innocent unless and until proven guilty.
Assistant U.S. Attorney Joseph Fazioli is prosecuting the case with the assistance of Legal Assistant Kamille Singh. The prosecution is the result of an investigation by the Federal Bureau of Investigation.
Further Information:
Case #: CR 11-00955 LHK
TOP-SECRET – Iraq Biometric Automated Toolset (BAT) HIIDE Standard Operating Procedures
Multi-National Forces West Biometric Automated Toolset (BAT) Handheld Interagency Identity Detection Equipment (HIIDE) SOP and TTP



DOWNLOAD ORIGINAL DOCUMENTS HERE
The FBI reports – Fourteen Citizens of Romania Charged with Participating in Internet Phishing Scheme
David B. Fein, United States Attorney for the District of Connecticut, and Kimberly K. Mertz, Special Agent in Charge of the Federal Bureau of Investigation, today announced the unsealing of an indictment charging 14 Romanian citizens with conspiracy, fraud and identity theft offenses stemming from their alleged participation in an extensive Internet “phishing” scheme.
A phishing scheme uses the Internet to target large numbers of unwary individuals, using fraud and deceit to obtain private personal and financial information such as names, addresses, bank account numbers, credit card numbers, and Social Security numbers. Phishing schemes often work by sending out large numbers of counterfeit e-mail messages, which are made to appear as if they originated from legitimate banks, financial institutions or other companies.
Charged in the indictment are CIPRIAN DUMITRU TUDOR, MIHAI CRISTIAN DUMITRU, BOGDAN BOCEANU, BOGDAN-MIRCEA STOICA, OCTAVIAN FUDULU, IULIAN SCHIOPU, RAZVAN LEOPOLD SCHIBA, DRAGOS RAZVAN DAVIDESCU, ANDREI BOLOVAN, LAURENTIU CRISTIAN BUSCA, GABRIEL SAIN, DRAGOS NICOLAE DRAGHICI, STEFAN SORIN ILINCA and MIHAI ALEXANDRU DIDU, all residents of Romania.
The indictment alleges that, in June 2005, one or more defendants sent a spam e-mail to individuals, including a resident of Madison, Conn., which purported to be from Connecticut-based People’s Bank. The e-mail stated that the recipient’s online banking access profile had been locked and instructed recipients to click on a link to a web page where they could enter information to “unlock” their profile. The web page appeared to originate from People’s Bank, but was actually hosted on a compromised computer unrelated to People’s Bank. Any personal identifying and financial information provided by the individual would be sent by e-mail to one or more of the defendants or to a “collector” account, which was an e-mail account used to receive and collect the information obtained through phishing.
It is alleged that TUDOR, DUMITRU and others used and shared a number of collector accounts, which contained thousands of e-mail messages that contained credit or debit card numbers, expiration dates, CVV codes, PIN numbers, and other personal identification information such as names, addresses, telephone numbers, dates of birth, and Social Security numbers. The co-conspirators then used the personal and financial information to access bank accounts and lines of credit and to withdraw funds without authorization, often from ATMs in Romania.
In addition to People’s Bank, financial institutions and companies allegedly targeted by the defendants included Citibank, Capital One, Bank of America, JPMorgan Chase & Co., Comerica Bank, Regions Bank, LaSalle Bank, U.S. Bank, Wells Fargo & Co., eBay and PayPal.
On January 18, 2007, a federal grand jury sitting in New Haven returned an indictment charging TUDOR, DUMITRU and others with offenses stemming from this phishing scheme. On November 10, 2010, a grand jury returned a second superseding indictment charging TUDOR, DUMITRU and an additional 12 defendants. The second superseding indictment was sealed pending the extradition of the defendants.
Earlier this month, three of the charged defendants were extradited from Romania to the United States. On December 12, 2011, BOLOVAN, 27, appeared before U.S. Magistrate Judge Holly B. Fitzsimmons in Bridgeport, Conn., and the indictment was unsealed at that time. DAVIDESCU, 38, and BUSCA, 26, were arraigned in Bridgeport on December 21, 2011.
Each of the 14 defendants is charged with conspiracy to commit bank fraud, which carries a maximum term of imprisonment of 30 years and a fine of up to $1 million, and conspiracy to commit fraud in connection with access devices, which carries a maximum term of imprisonment of five years and a fine of up to $250,000. Certain defendants, including DAVIDESCU and BUSCA, also are charged with aggravated identity theft, which carries a mandatory consecutive two-year term of imprisonment.
BOLOVAN, DAVIDESCU and BUSCA, who have pleaded not guilty to the charges, are detained pending trial, which is currently scheduled for March 2012.
U.S. Attorney Fein stressed that an indictment is not evidence of guilt. Charges are only allegations, and each defendant is presumed innocent unless and until proven guilty beyond a reasonable doubt.
This matter is being investigated by the Federal Bureau of Investigation in New Haven, Conn., and the Connecticut Computer Crimes Task Force. U.S. Attorney Fein and Special Agent in Charge Mertz also acknowledged the critical assistance provided by the U.S. Department of Justice Office of International Affairs; the FBI Legal Attaché in Bucharest; Interpol in Zagreb and Washington, D.C.; the Romanian National Police; and the United States Marshals Service.
The case is being prosecuted by Assistant United States Attorney Edward Chang.
Uncensored – FEMEN against KBG
From the CIA – The Intelligence Officer’s Bookshelf
DOWNLOAD E-BOOK HERE
UNCENSORED AND NEW – Topless women FEMEN protesters
CONFIDENTIAL – FBI Joint Terrorism Task Force (JTTF) Model Memorandum of Understanding
TOP-SECRET – U.S. Army Afghanistan Smart Book, Third Edition
DER “GoMoPa” ADRESSEN-FRIEDHOF BUCHSTABE A UND DIE GEFÄLSCHTEN MITGLIEDERZAHLEN
gomopa-friedhof-adressen-verwaltung
Download Link oben
Die gefälschten Mitgliederzaheln von “GoMoPa”.
Gomopa dürfte ohnehin ein Glaubwürdigkeitsproblem haben, denn der Dienst fiel mit falschen oder fragwürdigen Äußerungen auf. So gibt es laut Website 57 345 Mitglieder (Stand 21. September 2010). Die Mitgliedschaft ist bis auf einen einmonatigen Test kostenpflichtig. Einnahmen aus den Beiträgen beziffert Maurischat in seiner Information aber nur auf um die 5000 Euro. Selbst wenn alle Mitglieder die günstigste Variante gewählt haben, ergäben sich rechnerisch weit weniger als 1000 zahlende Mitglieder. Gomopa äußert sich dazu nicht.
TOP-SECRET-European Countries Refuse to Release Information on CIA Rendition Flights

Romania’s National Registry Office for Classified Information (ORNISS) headquarters building is seen in the background of this image taken in Bucharest, December 9, 2011. International media has reported that between 2003 and 2006, the CIA operated a secret prison from the building’s basement, bringing in high-value terror suspects for interrogation and detention. ORNISS has denied hosting a CIA prison and the CIA has refused to comment.
A majority of 28 mostly European countries have failed to comply with freedom of information requests about their involvement in secret CIA flights carrying suspected terrorists, two human rights groups said Monday.London-based Reprieve and Madrid-based Access Info Europe accused European nations of covering up their complicity in the so-called “extraordinary rendition” program by failing to release flight-traffic data that could show the paths of the planes.
The groups said only seven of 28 countries had supplied the requested information. Five countries said they no longer had the data, three refused to release it and 13 had not replied more than 10 weeks after the requests were made.
Europe’s silence is in contrast to the United States, which handed over Federal Aviation Administration records with data on more than 27,000 flight segments.
The groups’ report said that the U.S. had provided “by far the most comprehensive response” and accused European countries of lagging behind when it came to transparency.
“Is it an access to information problem, or is it a problem with this particular issue? It’s a bit of both,” said Access Info Europe executive director Helen Darbishire. “European countries have not completely faced up to their role here.”
Human rights campaigners have worked for years to piece together information on hundreds of covert flights that shuttled suspected terrorists between CIA-run overseas prisons and the U.S. military base at Guantanamo Bay as part of the post-Sept. 11 “War on Terror.”
The CIA has never acknowledged specific locations, but prisons overseen by U.S. officials reportedly operated in Thailand, Afghanistan, Lithuania, Poland and Romania — where terror suspects including Khalid Sheik Mohammad, mastermind of the Sept. 11 attacks, were interrogated in the basement of a government building in the capital, Bucharest.
DOWNLOAD ORIGINAL FILE HERE
FEMEN – Against Political Prisoners


TOP-SECRET-Asymmetric Warfare Group Guide to Insider Threats in Partnering Environments

This guide assists in three areas. First, it aides military leaders and all personnel to be aware of the indicators associated with insider threat activity while serving in a partnering environment. Second, this guide informs commanders and other leaders by giving them options on how to deal with insider threat activities. This guide is not all encompassing so there are other options a commander has dependent on their operating environment. Lastly, this guide is meant to generate open dialogue between coalition partners and partner nation personnel. Partnering in itself is a sensitive mission and only by creating trust and having an open dialogue with all forces will the mission be accomplished.
…
Risk Factors
- Emotional Vulnerability
- Dissatisfaction with lack of accepted conflict resolution
- Personal connection to a grievance
- Positive view of violence
- Perceived benefit of political violence
- Social Networks (tech and non tech)
- In group de-legitimization of the out-group
- Placement, Access, and Capability
- External Support
- Perceived Threat
- Conflict
- Humiliation orloss of honor
- Competition
- Social Alienation
- Quid Pro Quo (services or items wanted or needed by an individual given in exchange for information or action)
- Disproportionate financial risks
- Susceptible to blackmail
- Civilian Casualty (CIVCAS) situations
- Highly emotional
- Unfair treatment or equipment differences
…
Cultural Awareness
- DO NOT use derogatory terms in any language (even in friendly conversation)
- DO NOT slander host nation or coalition partners (even if only jokingly)
- DO NOT physically harm host nation or coalition partners (except in self defense)
- DO NOT put down or slander any religion
- ALWAYS be courteous and thankful for host nation and coalition partner hospitalityAsymmetric

DOWNLOAD ORIGINAL DOCUMENT HERE
TOP-SECRET – Joint Center for International Security Force Assistance Iraqi Federal Police Advisor Guide
As the U. S. Defense Department scales back operations in Iraq, one of the most significant questions that remains is whether the Iraqi security forces will be capable of maintaining civil order on their own. This manual was produced by the Joint Center for International Security Force Assistance (JCISFA) to help prepare deploying advisors, trainers, and partner forces that will work directly with Iraqi police. The intent is to provide a basic understanding of the country of Iraq and a solid understanding of the current organization and utilization of the Iraqi police. This manual also provides guidance on what it means to work ” by, with and through” a counterpart, and includes observations and insights learned by your predecessors.
In a stable society, a key component to security is the police. While there has been significant progress in the development of the Iraqi police, there is still much work to be done. Historically, the Iraqi police have been held in lower public regard than other components of the security force infrastructure. The Iraqi public viewpoint toward law enforcement as an agency of public safety, security, and service to the community has been far different than law enforcement in most developed nations. Part of our job is to educate the Iraqi police, and the Iraqi population, about the important role police play in a society governed by the rule of law. Rule of law enables the framework for national sovereignty and provides restraints that serve as a check against abusive use of power. Without effective rule of law, we will never gain the security necessary for democratic institutions to be successful.


DOWNLOAD ORIGINAL DOCUMENT HERE
SZ – SÜDDEUTSCHE ZEITUNG über STALKING- UND ERPRESSER- METHODEN DER STASI-“GoMoPa”
FBI reports – Los Fresnos Man Gets 80 Years in Federal Prison for Child Pornography Convictions
BROWNSVILLE, TX—Mark William Woerner, 55, formerly of Las Vegas, Nev., has been sentenced to 960 months in federal prison for distribution and possession of child pornography, United States Attorney Kenneth Magidson announced today. Woerner was convicted by a federal jury on all five counts with which he was charged in June 2011 following one and a half days of trial and less than five minutes of deliberation.
United States District Court Judge Hilda G. Tagle sentenced Woerner to the maximum sentence of 10 years for each of two counts of possessing child pornography and 20 years on each of three counts of distributing child pornography. All sentences were ordered to run consecutively to each other for a total of 80 years in prison without parole. Judge Tagle also ordered him pay a fine of $25,000 and restitution in the amount of $2,246 to the victims.
Woerner was convicted by a jury on June 21, 2011. During trial, testimony and evidence revealed that during two separate undercover operations out of New York and Illinois in April and May of 2010, multiple images and videos of child pornography were downloaded from an online peer-to-peer file-sharing program. After the IP addresses used in each undercover operation were linked to Woerner at his residence in Los Fresnos, Texas, the leads were forwarded to the FBI for further investigation. The government also presented evidence that Woerner sent more than 1,300 images and 90 videos though his e-mail account over a six-month period. A juvenile witness testified that Woerner had given him a thumb drive containing child pornography and had suggested that the juvenile take it to school to share with other students. Woerner possessed and/or distributed more than 8,000 images, which included minors under the age of 12, as well as material that portrayed sadistic or masochistic conduct or other depictions of violence.
In ordering a sentence of the maximum term of imprisonment, Judge Tagle noted Woerner’s lack of acceptance of responsibility and his history of exploiting children who trusted him. Judge Tagle also took into account the total number of images and videos involved in the offenses and their content. Woerner’s sentence was further enhanced because he had distributed images and videos of child pornography to minors and requested that they send him child pornography in return and because he had engaged in a pattern of activity involving the sexual abuse or exploitation of minors. Judge Tagle also found that Woerner had attempted to obstruct justice during the investigation when he solicited the assistance of a fellow inmate to kill an FBI agent in an effort to prevent him from testifying at trial.
This case, prosecuted by Assistant United States Attorneys Carrie Wirsing and V. LaTawn Warsaw, was brought as part of Project Safe Childhood, a nationwide initiative to combat the growing epidemic of child sexual exploitation and abuse launched in May 2006 by the Department of Justice. Led by United States Attorneys’ Offices and the Criminal Division’s Child Exploitation and Obscenity Section, Project Safe Childhood marshals federal, state, and local resources to better locate, apprehend and prosecute individuals who exploit children via the Internet, as well as to identify and rescue victims. For more information about Project Safe Childhood, please visit www.projectsafechildhood.gov.
TOP-SECRET – Taliban Top 5 Most Deadly Tactics Techniques and Procedures

To gain an understanding of the Top 5 casualty producing Tactics, Techniques and Procedures in Afghanistan
To introduce the Top Threat Groups in Afghanistan and along the Pakistani border
To understand the location of hostile action in Afghanistan
To understand Threat weapon employment
– Attack data
– Technology used
– TTP
To introduce Threat use of Information Warfare (INFOWAR) across Tactics, Techniques, and Procedures


DOWNLOAD ORIGINAL DOCUMENT HERE
“GoMoPa”-STASI-STALKING VIDEO
Ex-Capital Chefredakteur Brunowsky entlarvt die STASI-Stalker- und Erpresser-Spekulanten-Methoden der “GoMoPa” am Beispiel WGF
Nepper Schlepper Bauernfänger im Internet
Das ganze funktioniert so: Ein kritischer Text in “www.börsennews.de” oder “www.gomopa.net“, anonym oder unter falschem Namen geschrieben, stellt Fragen, ob das Geld der Anleger sicher sei, ohne diese Frage zu beantworten. Der Schreiber sendet diesen Text anonym an Medien wie das Handelsblatt oder FTD. Ein kooperierender Anwalt spricht dann vielsagend von Gefahren für den Anleger. Die Anleger reagieren natürlich verunsichert, der Kurs stürzt ab. Leerverkäufer – wahrscheinlich aus dem Umfeld des Trios Finanzportal, Finanjournalist und Anwalt – haben sich rechtzeitig eingedeckt und sahnen einen kräftigen Gewinn ab.
Die größeren Medien sehen angesichts der Kursverluste nun ebenfalls das Unternehmen in Gefahr, berichten darüber und verunsichern die Anleger zusätzlich. Vom Finanzportal “gomopa.net” ist bekannt, dass es anschließend den Betroffenen einen PR-Beratungsvertrag aufdrücken wollte, den diese dann als “Erpressung” ablehnten, wie die Süddeutsche Zeitung am 3.9.2010 berichtete. Auch das Handelsblatt hat im April vor einiger Zeit über einen ähnlichen Fall berichtet.
Ich erlebe diese Methoden gerade bei einer ähnlichen Kampagne gegen meinen Mandanten WGF AG. Die WGF AG handelt mit Immobilien, entwickelt großartige Projekte und refinanziert sich mit Hypothekenanleihen. Am 15.11. wurde pünktlich die zweite mit 6,35% verzinste Hypothekenanleihe im Volumen von 30 Millionen Euro entgegen diversen Unkenrufen pünktlich und vollständig zurückgezahlt.
Im Juli war ein Text unter falschem Namen im Finanzportal “Börsennews” mit Zitaten eines Anwalts erschienen, den der Autor weiteren Medien zuspielte. Unmittelbar darauf stürzten die Kurse mehrere Anleihen von 100 auf teilweise bis zu 60 Prozent. Die Kurse erholten sich dann zwar wieder um 10 bis 15 Prozentpunkte, aber nicht so, dass Raum für die Platzierung neuer Anleihen mit einem Ausgabekurs von 100 blieb. Die WGF war dennoch in der Lage, aus dem gut laufenden operativen Geschäft heraus die Rückzahlung der zweiten Anleihe sicher zu stellen. Anfang der Woche, am Tag nach der Rückzahlung erschien wieder ein anonymer Artikel in “gomopa.net”. So geht die Kampagne weiter.
Selbstverständlich müssen alle Geschäftsmodelle kritisch hinterfragt werden. Unternehmen machen Fehler und müssen diese Fehler auch beheben. Es kann aber nicht sein, dass gewissenlose Leute im Internet ihr Unwesen treiben und ganze Unternehmen attackieren, um damit Geld zu verdienen: Der Anwalt, der dazu beiträgt, Unternehmen zu gefährden, um anschließend Klienten für seinen sogenannten Kapitalanlegerschutz zu generieren, ist genauso hinterhältig wie der Journalist, der sich nicht zu seinen Texten bekennt und anonym oder unter falschem Namen schreibt, um an Kursspekulationen mitzuverdienen.
Eingestellt von Ralf-Dieter Brunowsky
http://brunowsky.blogspot.com/2011/11/nepper-schlepper-bauernfanger-im.html#links
Über mich
- Ralf-Dieter Brunowsky
- Cologne, NRW, Germany
- 2002-today: PR-Agency BrunoMedia GmbH, Köln 1991-2001 Editor in Chief financial magazine CAPITAL 1989-1990 managing editor Impulse 1980-1989 correspondent and managing editor Wirtschaftswoche 1977-1979 editor Berliner Morgenpost 1975-1977 manager retail association 1969-1975 university Berlin 1968-1969 German Navy
New – House Homeland Security Committee Introduces Bill to Create National Cybersecurity Authority

Members of the House Homeland Security Committee introduced a cybersecurity bill on Thursday that would establish a quasi-governmental entity to oversee information-sharing with the private sector.
Like the other cybersecurity bills offered by the House GOP, the Promoting and Enhancing Cybersecurity and Information Sharing Effectiveness (PrECISE Act) encourages private firms to share information on cyber threats but stops short of mandating new security standards for sectors deemed critical to national security.
“The risk of cyberattack by enemies of the United States is real, is ongoing and is growing,” said Chairman Pete King (R-N.Y.). “The PrECISE Act, in line with the framework set forth by the Speaker’s Cybersecurity Task Force led by Rep. [Mac] Thornberry [R-Texas], protects our critical infrastructure without a heavy-handed and burdensome regulatory approach that could cost American jobs.”
The bill would clearly delineate the cybersecurity functions of the Department of Homeland Security by requiring DHS to evaluate cybersecurity risks for critical infrastructure firms and determine the best way to mitigate them.
“Cybersecurity is truly a team sport, and this bill gives DHS needed authorities to play its part in the federal government’s cybersecurity mission and enables the private sector to play its part by giving them the information and access to technical support they need to protect critical infrastructure,” said House Cybersecurity subcomittee Chairman Dan Lungren (R-Calif.).
ORIGINAL DOCUMENT SEE HERE
TOP-SECRET from the FBI – Ashburn Realtor Charged in $7 Million Mortgage Fraud Scheme
ALEXANDRIA, VA—A federal grand jury has charged Nadin Samnang, 29, of Ashburn, Va., with conspiracy and mortgage fraud charges related to his role in alleged fraudulent mortgage loan transactions involving at least 25 homes in northern Virginia and more than $7 million in losses to lenders.
Neil H. MacBride, United States Attorney for the Eastern District of Virginia; Daniel Cortez, Inspector in Charge of the Washington Division of the United States Postal Inspection Service; and James W. McJunkin, Assistant Director in Charge of the FBI’s Washington Field Office, made the announcement.
According to the 12-count indictment, from 2006 to 2008, Samnang is accused of using his position as a realtor and the owner of a title company to engage in a scheme to defraud mortgage lenders and profit from loan proceeds, commissions, and bonus payments.
According to the indictment, Samnang and other members of the conspiracy allegedly recruited unqualified buyers—usually individuals with good credit but insufficient assets or income to qualify for a particular loan—and used them as nominal purchasers in residential real estate transactions. As part of the conspiracy and fraud scheme, Samnang and others are accused of falsifying mortgage loan applications, creating fake documents to support the fraudulent applications, and adding the unqualified buyers as signatories on their bank accounts to make it appear to lenders as though the buyers possessed sufficient assets to qualify for the loans.
If convicted, Samnang faces a maximum penalty of 20 years in prison on each count.
The case is being investigated by the U.S. Postal Inspection Service and the FBI’s Washington Field Office. Assistant United States Attorney Paul J. Nathanson is prosecuting the case on behalf of the United States.
Criminal indictments are only charges and not evidence of guilt. A defendant is presumed to be innocent until and unless proven guilty.
Meridian Capital über die “GoMoPa”-Fälschung Pressreleaser und die Erpressung durch “GoMoPa”
Unveiled – The Nixon Administration and the Indian Nuclear Program

Trombay, the site of India’s first atomic reactor (Aspara), the CIRUS reactor provided by Canada, and a plutonium reprocessing facility, as photographed by a KH-7/GAMBIT satellite during February 1966. Provided under lax safeguards, the CIRUS reactor produced the spent fuel that India converted into plutonium for the May 1974 test (the heavy water needed to run the reactor was provided by the United States, also under weak safeguards).
 Raja Rammana, director of the Bhabha Atomic Research Center at Trombay, played a key role in the production, development, and testing of the May 1974 Indian “peaceful nuclear explosion.” In the Spring of 1973, John Pinajian, the Atomic Energy Commission’s representative in India, became suspicious that India was preparing for a nuclear test in part because Rammana rebuffed his requests for access to BARC so he could conduct an experiment which had been approved by the Indian Atomic Energy Commission (see document 17A)
Raja Rammana, director of the Bhabha Atomic Research Center at Trombay, played a key role in the production, development, and testing of the May 1974 Indian “peaceful nuclear explosion.” In the Spring of 1973, John Pinajian, the Atomic Energy Commission’s representative in India, became suspicious that India was preparing for a nuclear test in part because Rammana rebuffed his requests for access to BARC so he could conduct an experiment which had been approved by the Indian Atomic Energy Commission (see document 17A)
The Elephant in the Room: The Soviet Union and the Indian Nuclear Program
For more information on India and the Cold War superpowers, see an extraordinary collection of Hungarian Foreign Ministry documents, edited and translated by Balazs Szalontai, with a substantive “Working Paper,” recently published by the Nuclear Proliferation International History Project. Drawing on archival material from the 1960s through the 1980s, “The Elephant in the Room” provides significant insight into the Soviet Union’s nuclear relations with India. While Moscow was carefully to sell only safeguarded nuclear technology to New Delhi, the priority of maintaining good relations with India sometimes put nonproliferation goals in the backseat. For example, before the May 1974 “peaceful nuclear explosion” the Soviets had tried to discourage the Indians from testing–confirming what has been previously suspected–but once the latter had tested the Soviets did not criticize them. When Canada stopped providing reactor fuel and equipment as a penalty for the test (which Canadian technology had facilitated), the Soviets stepped in to fill the gap. Moreover, when Soviet-Pakistan relations deteriorated after the invasion of Pakistan, Moscow’s anger was so intense that it gave the “green light” to Indian military planning for a strike against Pakistani nuclear facilities. The documents also suggest that it was not until the mid-1980s, when U.S.-Soviet and Sino-Soviet détente were on the upswing, that the Soviets became concerned about India as a nuclear proliferation problem.
Washington, D.C., December 19, 2011 – India’s “peaceful nuclear explosion” on 18 May 1974 caught the United States by surprise in part because the intelligence community had not been looking for signs that a test was in the works. According to a recently declassified Intelligence Community Staff post-mortem posted today by the National Security Archive and the Nuclear Proliferation International History Project, Nixon administration policymakers had given a relatively low priority to the Indian program and there was “no sense of urgency” to determine whether New Delhi was preparing to test a nuclear device. Intelligence “production” (analysis and reporting) on the topic “fell off” during the 20 months before the test, the analysis concluded.[i]
In early 1972, however—two years before the test—the State Department’s Bureau of Intelligence and Research (INR) had predicted that India could make preparations for an underground test without detection by U.S. intelligence. Published for the first time today, the INR report warned that the U.S. government had given a “relatively modest priority to … relevant intelligence collection activities” which meant that a “concerted effort by India to conceal such preparations … may well succeed.”
The post-mortem [see document 21], the INR report [see document 2] and other new materials illustrate how intelligence priorities generally reflect the interests and priorities of top policymakers. The Nixon White House was focused on the Vietnam War and grand strategy toward Beijing and Moscow; intelligence on nuclear proliferation was a low priority. Compare, for example, the India case with that of Iraq during 2002-2003, when White House concerns encouraged—some say even compelled—intelligence producers to cherry pick raw information to demonstrate the development of WMD by the Saddam Hussein regime.
INR prepared its India report at a time when secret sources were telling U.S. intelligence that New Delhi was about to test a nuclear device. The “small spate” of reports about a test had such “congruity, apparent reliability, and seeming credibility” that they prompted a review of India’s nuclear intentions by INR and other government offices. In the end, government officials could not decide whether India had made a decision to test although a subsequent lead suggested otherwise.
According to the intelligence community’s post-mortem, obtained through a mandatory review appeal to the Interagency Security Classification Appeals Panel (ISCAP), one of the problems was that intelligence producers were not communicating with each other, so the “other guy” assumed that someone else was “primarily responsible for producing hard evidence of Indian intentions.” The analysis was especially critical of an August 1972 Special National Intelligence Estimate for its “waffling judgments” on Indian nuclear intentions.
Other declassified documents reproduced here from 1972 through 1974 illustrate the range of thinking on this sensitive topic:
- An INR report in February 1972 concluded that it could not “rule out a test” in the near future and it was “entirely possible that one or more nuclear devices have actually been fabricated and assembled.” All the same, “it our judgment that a decision to authorize a test is unlikely in the next few months and may well be deferred for several years.”
- During March and April 1972, Canadian and British intelligence concluded that they had no evidence that India had made a decision to test a nuclear device. Nevertheless, the Canadians believed that New Delhi could produce a device in less than a year.
- In June 1972, Japanese diplomat Ryohei Murata argued that the “Indians have decided to go ahead with a nuclear test” and that the Thar Desert in Rajasthan would be the test site. While basically correct, Murata’s estimate was discounted because it did not represent an official Foreign Ministry view.
- Special National Intelligence Estimate (SNIE) 31-72 published in August 1972 also held that the Indians could produce a device “within a few days to a year of a decision to do so,” but concluded that the chances that India had made a decision to test were “roughly even.”
- In 1973, the Atomic Energy Commission’s scientific representative in India told the U.S. consul in Bombay (Mumbai) that several “indications” suggested that India “may well have decided” to test a nuclear device.
- Five months before the test, the U.S. Embassy in New Delhi reported that the probability of an “early test” was at a “lower level than previous years.”
The rumors that India was going to test emerged in the wake of the South Asian crisis, when the Nixon White House tilted toward Pakistan, India’s archrival. Relations between New Delhi and Washington were already cool during the Nixon administration which treated India as a relatively low priority. Henry Kissinger’s secret trip to China underlined India’s low priority by suggesting that if New Delhi ever faced a crisis with Beijing it could not count on Washington for help. Relations became truly frosty during the balance of 1971 when New Delhi signed a friendship treaty with Moscow and India and Pakistan went to war. Later Nixon and Kissinger wanted to improve the relationship, but India’s nuclear intentions were not on their agenda. That India had refused to sign the Nuclear Nonproliferation Treaty was a non-issue for Nixon and Kissinger, who had little use for the NPT and treated nuclear proliferation as less than secondary. While the State Department cautioned India against nuclear tests in late 1970 [see document 6], concern did not rise to the top of policy hill.[2]
Whatever impact the events of 1971 may have had on India’s decision to test a nuclear device that decision was soon to be made. According to George Perkovich, an authority on the Indian nuclear program at the Carnegie Endowment for International Peace, “it may be conjectured that support in principle for developing a nuclear explosive device was solidified by late 1971, that concentrated work on building the vital components began in spring 1972, and that formal prime ministerial approval to make final preparations for a PNE occurred in September 1972.”[3] In this context, the reports collected by U.S. intelligence in late 1971 and early 1972 about a possible test may have been good examples of the old chestnut that “where there’s smoke, there’s fire.”
Yet, the analysts who wrote SNIE 31-72 decided that the smoke had no significance because they saw only a 50-50 chance that New Delhi had made a decision to test (even though New Delhi was closing in on a decision).
|
Documents
Document 1: “Various recent intelligence reports”
State Department cable 3088 to Embassy New Delhi, 6 January 1972, Secret
Source: U.S. National Archives, Record Group 59, Subject-Numeric Files 1970-1973 [hereinafter RG 59, SN 70-73] Def 12-1 India
For years, the U.S. intelligence establishment had been monitoring India’s nuclear program for signs of a decision to produce nuclear weapons, but in late 1971 and early 1972 it had to consider the possibility that a nuclear test was impending. Recently collected intelligence about an imminent test led the State Department to send a query to the U.S. Embassy in India for its assessment.
Document 2: “A Concerted Effort by India to Conceal Preparations May Well Succeed”
State Department Bureau of Intelligence and Research Intelligence Note, “India to Go Nuclear?” 14 January 1972, Secret
Source: RG 59, SN 70-73, Def 18-8 India
Before the Embassy sent a full response, a team of analysts at the State Department’s Bureau of Intelligence and Research produced their evaluation of varied report about India’s nuclear intentions: that it would test a device that month, sometime in 1972, or that the government was undertaking a program to test a “peaceful nuclear explosive.” According to INR, India had the capability to produce some 20-30 weapons, and it could easily test a device in an underground site, such as an abandoned mine, that would be hard to discover. Indeed, because the U.S. government had given a “relatively modest priority to … relevant intelligence collection activities” a “concerted effort by India to conceal such preparations … may well succeed.” What would motivate India to test, the analysts opined, were domestic political pressures and concerns about China and Pakistan. Nevertheless, the INR analysts saw a test as having more importance as a demonstration of “scientific and technological prowess”; the strategic significance would be “negligible” because India was “years away” from developing a “credible” deterrence against China “its only prospective enemy with a nuclear capability.”
Document 3: “Straws” Suggesting an Underground Test
U.S. Embassy Airgram A-20 to State Department, “India’s Nuclear Intentions,” 21 January 1972, Secret, Excised copy
Source: RG 59, SN 70-73, Def 18-8 India
In its response to the Department’s query, the Embassy identified a number of reasons that made it unlikely that India would a test a nuclear device in the coming weeks, but saw “straws” suggesting an underground test “sometime in future.” For example, the Government of India had publicly acknowledged ongoing work on the problem of safe underground testing . Moreover, India might have an interest in making its nuclear capabilities known to “enemies.” Whatever the Indians decided, external pressure would have no impact on a highly nationalist state and society: “we see nothing US or international community can presently do to influence GOI policy directions in atomic field.”
One of the sources mentioned, apparently a CIA asset (the reference is excised), had a connection with the Prime Minister’s secretariat. This may be the same informant, future Prime Minister Moraji Desai, who provided information to the CIA about Prime Minister Gandhi’s intentions during the recent South Asian crisis and whose cover was subsequently blown through press leaks published by Jack Anderson. He later told the CIA to “go to hell.”[4]
Document 4: “Increased Status of a Nuclear Power”
Memorandum from Ray Cline, Director, Bureau of Intelligence and Research, to Director of Central Intelligence Richard Helms, enclosing “Possibility of an Indian Nuclear Test,” 23 February 1972, Secret
Source: U.S. State Department, Foreign Relations of the United States, 1969–1976 Volume E–7, Documents on South Asia, 1969–1972, Document 228
At the request of Undersecretary of State John Irwin, INR prepared an assessment which included a detailed review of Indian’s nuclear facilities and their capacity to produce weapons-grade plutonium as well as capabilities to deliver nuclear weapons to target. While India had signed agreements with Canada and the United States that nuclear reactors were to be used for peaceful purposes, the Indians were likely to claim that an explosive device for “peaceful” purposes was consistent with the agreements. Whether the Indians were going to test in the near future was in doubt. INR could not “rule out” one in the near future. Further, the “strongest incentive [to test] may well be the desire for the increased status of a nuclear power.” All the same, “it our judgment that a decision to authorize a test is unlikely in the next few months and may well be deferred for several years.” Weighing against a test were the financial and diplomatic costs, for example, “India’s full awareness that assistance from the US and other countries (possibly including the USSR) would be jeopardized.”
Document 5: Trudeau’s Warning
U.S. Embassy Canada cable 391 to State Department, “India’s Nuclear Intentions,” 7 March 1972, Secret
Source: RG 59, SN 70-73, AE 1 India
With With Canada’s role as a supplier of nuclear technology, including the CIRUS research reactor, senior Canadian officials had close working relationships with their Indian counterpart. James Lorne Gray, the chairman of Canada’s Atomic Energy Board, had recently visited India and U.S. embassy officials interviewed him closely on his thinking about Indian nuclear developments. Having spoken with Homi Nusserwanji Sethna, Chairman of the Atomic Energy Commission, and other officials, Gray believed that Sethna opposed a test and that as long as Sethna and Indira Gandhi were in office “there was no chance” that India would test a nuclear device, which would take three to four years to prepare. Gray was mistaken, but was correct to declare that if a decision to test was made, Sethna would “undoubtedly” head the project. The embassy’s science attaché, Miller N. Hudson, met with other officials with the AECB who had a different take on Indian capabilities; based on their assessment of Indian’s ability to produce weapons grade plutonium, they argued that it would take no more than a year to produce a device.
The Canadians pointed out that about 18 months earlier there had been a “blackout” of statistical information on plutonium production. That led Canadian Prime Minister Pierre-Eliot Trudeau followed by other officials to “directly” warn the “Indians that Canadian plutonium should not be used for any kind of nuclear device.”
Document 6: Unlikely to Test in the “Near Future”
State Department cable 40378 to U.S. Embassy Ottawa, “Indian Nuclear Intentions,” 9 March 1972, Secret
Source: RG 59, SN 70-73, AE 1 India
State Department officers were also consulting with their counterparts at the Canadian embassy in Washington. During a discussion with the embassy counselor, country desk director David Schneider opined that Indian was unlikely to test a device in the “near future” but he wanted Ottawa’s prognosis. Schneider was also interested in whether the Soviets, with their close relationship with India, might be able to use their influence to “deter” a test. If India tested, the U.S. could respond with a “strong statement,” but whether “punitive” measures would be taken would depend on whether the test “violated existing agreements.” In October 1970, the State Department had cautioned the Indians that a “peaceful nuclear explosion” was indistinguishable from a weapons test and that the test of a nuclear device would be incompatible with U.S.-Indian nuclear assistance agreements. That the State Department issued this warning provides a telling contrast with Canada, which treated its admonition as a head of state issue.
Document 7: No Technical or Fiscal Obstacle to a Test
U.S. Embassy Canada cable 430 to State Department, “India’s Nuclear Intentions on South Asia Situation,” 14 March 1972, Secret
Source: RG 59, SN 70-73, AE 1 India
Elaborating on his earlier cable and responding to the general issues raised by the Department’s 9 March message, science attaché Hudson questioned Gray’s evaluation of Sethna, suggesting that by combining “guile” and “technical proficiency,” the latter could easily have “easily misled” the Canadian. Based on consultations with a variety of Canadian insiders with knowledge of and experience with the Indian nuclear program, the Embassy saw no technical or fiscal barriers to an Indian test. Moreover, any pressure on India not to test would increase the “likelihood” of that happening.
Document 8: “Leaving Their Options Open”
State Department cable 50634 to U.S. Embassy Canada, “Indian Nuclear Intentions,” 24 March 1972, Secret
Source: RG 59, SN 70-73, AE 1 India
Further discussions with the Canadian embassy counselor disclosed Ottawa’s view that it had no evidence of Indian intentions to test a nuclear weapon or a PNE. The Indians were “leaving their options open.” If they decided to test, however, it would be “impossible” for them to move forward “without revealing some indication of their intentions.”
Document 9: British See No Evidence of a Decision
State Department cable 59655 to U.S. Embassy United Kingdom, “Indian Nuclear Intentions, 7 April 1972, Secret
Source: RG 59, SN 70-73, AE 1 India
The British Government was taking the same view as the Canadians, seeing no evidence that the Indians had made a decision to test, although they had the “capability.”
Document 10: “Apparent Reliability and Seeming Credibility”
State Department cable 69551 to U.S. Embassy United Kingdom, “Indian Nuclear Intentions, 22 April 1972, Secret
Source: RG 59, SN 70-73, AE 1 India
The Canadian embassy had asked the State Department for information on the intelligence reports from earlier in the year that an Indian nuclear test was “imminent.” The State Department denied the request, but informed the Canadians that the reports were so numerous and their “congruity, apparent reliability, and seeming credibility” so striking that it had become necessary to update official thinking about Indian intentions.
Documents 11A-C: “The Indians Have Decided to Go Ahead”
A. State Department cable 113523 to U.S. Embassy India, “Japanese Views Regarding Indian Nuclear Plans,” 23 June 1972, Secret
B. U.S. Mission Geneva cable 2755 to State Department, “Japanese-Pakistani Conversations Regarding Indian Nuclear Plans,” 26 June 1972, Secret
C. U.S. Embassy Tokyo cable 67912 to State Department, “Japanese View Regarding Indian Nuclear Plans,” 27 June 1972, Secret
Source: RG 59, SN 70-73, AE 1 India
This group of telegrams discloses that one Japanese diplomat made a good guess about what was happening in India, but also illuminates the problem of verifying intelligence information. In response to a request from the State Department, Ryohei Murata[5], an official at the n officer from the Japanese embassy, reported that the Japanese government believed that for prestige reasons and as a “warning” to others, the “Indians have decided to go ahead with a nuclear test” which could occur at “any time;” The Thar Desert in Rajasthan would be the test site. Murata was correct on the latter point and close to correct on the decision: only weeks before the Indian AEC had begun work on building the components for a test device.[6] The cables that followed this report, however, raised doubts about Murata’s assessment.
Document 12: Request for a NSSM
Henry Kissinger to President Nixon, “Proposed NSSM on the Implications of an Indian Nuclear Test,” n.d., with cover memorandum from Richard T. Kennedy, 4 July 1972, Secret
Source: Nixon Presidential Library, National Security Council Institutional Files, box H-192, NSSM-156 [1 of 2]
Months after the initial flurry of intelligence reports, national security assistant Henry Kissinger asked President Nixon to approve a national security study memorandum [NSSM] on the implications of an Indian nuclear test for U.S. interests. The next day, 5 July 1972, Kissinger sent the agencies a request for a study which became NSSM 156.
Document 13: No Evidence of a Decision
U.S. Embassy India cable 9293 to State Department, “Indian Nuclear Intentions,” 26 July 1972, Secret
Source: RG 59, SN 70-73 Def 1 India
In an update of its thinking about the possibility of a test, the Embassy acknowledged that India had the “technical know-how and possibly materials to develop [a] simple nuclear device within period of months after GOI decision to do so.” Nevertheless, it saw no evidence that a decision had been made to test a device. Moreover, capabilities to deliver nuclear weapons were limited, with no plans in sight to “develop [a] missile launch system.”
Document 14: “Roughly Even”
Special National Intelligence Estimate 31-72, “Indian Nuclear Developments and their Likely Implications,”3 August 1972, Secret
Source: Foreign Relations of the United States, 1969–1976 Volume E–7, Documents on South Asia, 1969–1972, Document 298
Prepared as part of the NSSM 156 policy review, the 1974 post-mortem criticized this SNIE as “marred by waffled judgments.” The SNIE concluded that the chances of India making a decision to test were “roughly even,” but the post-mortem analysis [see document 21] argued that based on its own findings, the conclusion ought to have been 60-40 in favor of a decision to test. In its analysis of the pros and cons of testing, the SNIE found that the “strongest factors impelling India to set off a test are: the “belief that it would build up [its] international prestige; demonstrate India’s importance as an Asian power; overawe its immediate South Asian neighbors; and bring enhanced popularity and public support to the regime which achieved it.” The drafters further noted that a test would be “extremely popular at home, where national pride is riding high” and that supporters of a test believed that it would make the world see India as “one of the world’s principal powers.” The arguments against a test included adverse reactions from foreign governments that provided economic assistance, but the estimate noted that foreign reactions were “becoming less important” to India.
Document 15: “No Firm Intelligence”
Memorandum of Conversation, “Indian Nuclear Developments,” 21 September 1972, Secret
Source: RG 59, SN 70-73, Def 12 India
A meeting between British Foreign Office and State Department officials on the Indian nuclear problem occurred the same month that Indian Prime Minister Gandhi approved the “final preparations for a PNE.”[7] Deputy Assistant Secretary of State Christopher T. Van Hollen (the father of the future Maryland Congressman) and his colleagues followed the approach taken by the SNIE, which was close to that taken by the British Joint Intelligence Committee. According to country director David Schneider, the “odds were about even” that India would make a decision, but once it was made, India could test very quickly. There was “no firm intelligence” that a “go-ahead signal” to prepare for a test had been made. Schneider reviewed bilateral and multilateral steps, proposed in the NSSM 156 study, that the U.S. and others could take to try to discourage an Indian test and the range of reactions that would be available if India went ahead. A “weak” U.S. reaction, Schneider observed, would suggest that Washington would “acquiesce” if other countries followed India’s example.
Document 16: “A Set-Back to Nonproliferation Efforts”
H. Daniel Brewster to Herman Pollack, “Indian Nuclear Developments,” 16 January 1973, enclosing “Summary,” 1 September 1972, Secret
Source: RG 59, SN 70-73, AE 6 India
The interagency group prepared a response to NSSM 156 on 1 September 1972 and it was sent to Kissinger at whose desk it would languish, suggesting the low priority that the Nixon White House gave to nuclear proliferation issues. The summary of the study reproduced here includes the conclusion that an Indian test would be “a set-back to nonproliferation efforts” and that Washington should “do what [it] can to avert or delay” one. Thus, recommendations included a number of unilateral and multilateral actions that the United States government could take, noting that “given the poor state” of Indo-American relations, an “overly visible” U.S. effort would more likely speed up an Indian decision to test a device, Even non-US efforts were likely not to “be per se effective.”
Documents 17A-B: India “May Well Have Decided”
A. Bombay consulate cable 705 to Department of State, “India’s Nuclear Position,” 4 April 1973, Confidential
Source: RG 59, SN 70-73, Def 1 India
B. U.S. Embassy India cable 5797 to State Department forwarding Bombay consulate cable 983, “India’s Nuclear Position,” 17 May 1973, Confidential
Source: AAD 1973
The possibility that the GOI had made a decision to test surfaced in a message from the U.S. consulate in Bombay (Mumbai) signed off by Consul David M. Bane. The latter reported that Oak Ridge Laboratory scientist John J. Pinajian, then serving as the Atomic Energy Commission’s scientific representative in India, had pointed out several “indications”—notably his lack of access to key individuals and facilities in India’s atomic establishment–suggesting that India “may well have decided” to test a nuclear device. While stating that Pinajian’s evaluation was “subjective and impressionistic,” Consul Bane agreed that the atomic energy establishment did not want this American poking around because he might find out too much. Bane further observed that a nuclear test “in the not too distant future” could meet the GOI’s political goals and help attain “greater recognition major power status.”
Raja Rammana, the director of the Bhabha Atomic Research Center, one of the organizations that Pinajian was trying to contact, played a key role in directing the PNE project so his suspicions were on target.[8] In any event, a month later, Pinajian got some access to BARC, but noticed the absence of personnel responsible for experimental work. Moreover, he was getting cooperation from the Institute for Fundamental Research to conduct an experiment. Whether Pinajian remained suspicious needs to be learned, but the authors of the 1974 post-mortem pointed to the Consulate report as evidence that should have been considered (although it is worth noting that Secretary of State William Rogers was aware of the report and asked for more information).
Document 18: “The Likelihood of an Early Test [at] a Lower Level than Previous Years”
U.S. Embassy India cable 0743 to State Department, “India’s Nuclear Intentions,” 18 January 1974, Confidential
Source: http://static.history.state.gov/frus/frus1969-76ve08/pdf/d156.pdf
The embassy concluded that “deeper economic problems,” among other considerations militated against a nuclear test in the near future, even though the Indian government had the capabilities to produce and test a device. While there were no rumors about a test as there had been in 1972, “we know little about relevant internal government debate.” All in all, the embassy believed that economic conditions “tip the likelihood of an early test to a lower level than previous years.” Russell Jack Smith, previously the deputy director for intelligence at the CIA, and then serving as special assistant to the ambassador (station chief), was one of the officials who signed off on this cable.[9]
Document 19: “Rebound to their Credit Domestically”
U.S. Embassy India cable 6598 to State Department, “India’s Nuclear Explosion: Why Now?” 18 May 1974, Secret
Source: AAD
Having written off an early test, the day that it took place the Embassy scrambled to come up with an explanation. Deputy Chief of Mission David Schneider signed off on the telegram because Moynihan was in London. While the Embassy had no insight on the decision-making, it saw domestic politics and “psychological” explanations for the test: the need to offset domestic “gloom” and the need for India to “be taken seriously.” According to the telegram, “the decision will appeal to nationalist feeling and will be widely welcomed by the Indian populace.”
Document 20: “Enough Plutonium for Some 50-70 Nuclear Weapons”
State Department cable 104613 to Consulate, Jerusalem, “India Nuclear Explosion,” 18 May 1974, Secret
Source: State Department MDR release
The day of the test, INR rushed to update Kissinger, then in the Middle East negotiating with Israel and Syria. INR provided background on what had happened, how the United States and Canada had inadvertently helped India produce plutonium for the test device, earlier U.S. and Canadian demarches against “peaceful nuclear explosions,” and India’s capabilities to produce and deliver nuclear weapons. The report did not state whether India had made a decision to produce weapons, but it forecast that two large unsafeguarded reactors under construction could eventually “produce enough plutonium for 50-70 nuclear weapons.”
Document 21: “No Sense of Urgency in the Intelligence Community”
Intelligence Community Staff, Post Mortem Report, An Examination of the Intelligence Community’s Performance Before the Indian Nuclear Test of May 1974, July 1974, Top Secret, Excised copy
Source: Mandatory review request; release by ISCAP
After the test, policymakers in and out of the intelligence establishment wanted to know why the CIA and its sister agencies had missed it. As Jeffrey Richelson has observed, this was not an “epic failure,” but it was serious enough to produce a post-mortem investigation to determine what had gone wrong.[10] The partial release of the July 1974 post-mortem provides some answers, even if the full picture is denied because of massive excisions. Readers already know from the previous release published on the Archive’s Web site that two problems were especially important: 1) the lack of priority given to the Indian nuclear program for intelligence collection (further confirmed by the January 1972 INR report), and 2) the lack of communication between intelligence producers (analysts and estimators) and intelligence collectors (spies, NRO, etc.). The low priority meant that intelligence production “fell off” during the 20 months before the test (from October 1972 to May 1974). Moreover, there may have been a lack of communication between producers, with the “other guy” assuming that someone else was “primarily responsible for producing hard evidence of Indian intentions.”
Trying to explain the lack of follow-up on relevant “raw intelligence,” e.g. Pinjanians’s surmises about the Indian nuclear program, the post-mortem saw no “sense of urgency” in the intelligence community, which may have “reflected the attitudes of the policymakers.” Another problem was that the intelligence community focused more on “capabilities” than on “intentions,” which implicitly raised the difficult issue of breaching the nuclear establishment or Indira Gandhi’s small circle of decision-making.
The substantive discussion of satellite photography has been excised, but the recommendations were left intact, including the point that “The failure of production elements to ask NPIC [National Photographic Intelligence Center] to exploit photography that had been specifically requested from the National Reconnaissance Office suggests a weakness in the imagery requirements system.” The implication was that NRO satellites had imagery of the Thar Desert that could have been scrutinized for suspect activity, but no one asked NPIC to look into it. In any event, this and other failures fed into a number of recommendations, including the broader point that nuclear proliferation intelligence receive “much higher priority.”
Document 22: “India may not yet have decided whether to proceed with …. [the] development of a weapons capability”
Source: MDR release by CIA
A few months after the Indian test, the intelligence community prepared an overall estimate of the global nuclear proliferation situation. Such an estimate had not been prepared since the 1960s, no doubt because of the White House’s lack of interest. This estimate, SNIE 4-1-74, has been released before but this version includes more information, mainly a section on the Indian nuclear program, which had previously been withheld. While finding it “likely” that India would launch a covert program to produce a few weapons, the analysts were not sure that such a decision had been made and suggested that Moscow or Washington might be able to persuade the Indians from moving in that direction. The hypothesis about a covert program was mistaken because the Government of India did not make a basic decision to produce nuclear weapons until the 1980s.
Document 23: Whether the “Intelligence Community is Adequately Focused on Proliferation Matters”
Intelligence Community Staff, Director of Performance Evaluation and Improvement, to Deputy to the Director of Central Intelligence for the Intelligence Community, “Nuclear Proliferation and the Intelligence Community,” 12 October 1976, Top Secret, Excised copy
Source: CIA Research Tool [CREST], National Archives Library, College Park, MD
As this report indicates, the recommendations made in the 1974 post-mortem had little impact. The authors identified a basic disconnect between “national level users”—the top policymakers—and those who “set analytical and collection priorities in the intelligence community.” The latter were not sure how high a priority that the policymakers had given to nuclear proliferation intelligence. Moreover, a study for the Defense Department produced by MIT chemistry professor (and future DCI) John Deutch questioned whether the intelligence community “is adequately focused and tasked on proliferation matters.” This would be a recurring problem for the CIA and other intelligence agencies.
Notes
[i] For background, see Jeffrey Richelson, Spying on the Bomb: American Nuclear Intelligence from Nazi Germany to Iran and North Korea (New York: W.W. Norton, 2006), 218-235.
[1] For background, see Jeffrey Richelson, Spying on the Bomb: American Nuclear Intelligence from Nazi Germany to Iran and North Korea (New York: W.W. Norton, 2006), 218-235.
[2] For U.S.-India relations during the Nixon administration, see Dennix Kux, India and the United States: Estranged Democracies, 1941-1991 (Washington, D.C.: National Defense University Press, 1993), 279-314, and Perkovich, India’s Nuclear Bomb, 162-166. For the impact of Kissinger’s trip, see Andrew B. Kennedy, “India’s Nuclear Odyssey: Implicit Umbrellas, Diplomatic Disappointments, and the Bomb,” International Security 36 (2011): 136-139.
[3] Perkovich, India’s Nuclear Bomb, 172.
[4] Thomas Powers, The Man Who Kept the Secrets: Richard Helms & the CIA (New York: Knopf, 1979), 206-207; Mark Feldstein, Poisoning the Press: Richard Nixon, Jack Anderson, and the Rise of Washington’s Scandal Culture, (New York: Farrar, Straus and Giroux, 2010), 171.
[5] Murata would later rise to vice foreign minister and in 2009 revealed significant details about secret U.S.-Japanese understandings on nuclear weapons issues during the Cold War. http://search.japantimes.co.jp/cgi-bin/nn20090630a2.html
[6] Perkovich, India’s Nuclear Bomb, 171.
[9] Russell J. Smith, The Unknown CIA: My Three Decades with the Agency (Washington, D.C.: Pergamon-Brassey, 1989, 124.
Sources – Iran Reportedly Arrests Twelve CIA Agents
Senior Iranian parliamentary officials announced that the country has arrested 12 agents of the American Central Intelligence Agency.Member of the Iranian Parliament’s National Security and Foreign Policy Commission Parviz Sorouri said that the agents had been operating in coordination with Israel’s Mossad and other regional agencies, and targeted the country’s military and its nuclear program.
“The US and Zionist regime’s espionage apparatuses were trying to damage Iran both from inside and outside with a heavy blow, using regional intelligence services,” Sorouri told the Islamic republic news agency on Wednesday.
“Fortunately, with swift reaction by the Iranian intelligence department, the actions failed to bear fruit,” Sorouri said.
The lawmaker did not specify the nationality of the agents, nor when or where they had been arrested.
This current announcement follows the unraveling by Lebanon’s Hezbollah of a CIA spy ring in that country.
Hezbollah Leader Sheik Hassan Nasrallah revealed in June on television he had unmasked at least two CIA spies who had infiltrated the low ranks of the organization.
Though the US Embassy in Lebanon officially denied the accusation, American officials later confirmed Nasrallah’s announcement.
US officials confessed on Tuesday that Iranian intelligence forces and Hezbollah have unraveled the CIA’s spy network in Iran and Lebanon and arrested dozens of informants, severely damaging the intelligence agency’s reputation and ability to gather vital information on the two countries at a sensitive time in the region.
US officials said several foreign spies working for the CIA had been captured by Hezbollah in recent months. The blow to the CIA’s operations in Lebanon came after top agency managers were alerted last year to be especially careful handling informants in the Middle East country.
Separately, counterintelligence officers in Iran also succeeded in uncovering the identities of at least a handful of alleged CIA informants, Washington officials said.
A CIA-led program in the Middle East is up in the air after officials confirmed to news organizations today that paid informants in Iran and Lebanon working for the US government have disappeared while attempting to infiltrate Hezbollah.
During the past year, leaders of both Iran and Hezbollah have publicly announced the successes of their security and counterintelligence forces in uncovering CIA informants.
Iranian intelligence minister Heidar Moslehi announced in May that more than 30 US and Israeli spies had been discovered and he quickly took to Iranian television to broadcast information explaining the methods of online communication that the agents would use to trade intel. Only a month later, Hezbollah leader Seyed Hassan Nasrallah announced that two high-ranking officers within his own organization had been identified as CIA spies. Just now, however, does the US government confirm that not only is this information true, but they believe that the rest of their Hezbollah-targeted operations in the Middle East have been compromised.
TOP SECRET from the FBI Las Vegas – Sixteen Persons Charged in International Internet Fraud Scheme
LAS VEGAS—Federal charges have been unsealed against 16 individuals for their involvement in an international Internet scheme that defrauded online purchasers of purported merchandise such as automobiles and other items, announced Daniel G. Bogden, United States Attorney for the District of Nevada.
The defendants are charged with wire fraud, conspiracy to commit wire fraud, conspiracy to commit money laundering, and criminal forfeiture. Thirteen of the defendants were arrested in Las Vegas yesterday, December 14, 2011. Most of those defendants appeared before United States Magistrate Judge Robert J. Johnston yesterday, and pleaded not guilty to the charges. Several other defendants are scheduled for initial court appearances today beginning at 3:00 p.m. One individual was arrested at Washington Dulles International National Airport in Virginia, and appeared before a federal magistrate judge there, and the remaining two defendants have not yet been arrested.
According to the allegations in the indictment, from about December 2008 to December 2011, conspirators situated outside of the United States listed and offered items for sale on Internet sites (such as Craigslist and Autotrader) and occasionally also placed advertisements in newspapers. The items offered for sale included automobiles, travel trailers and watercraft. The conspirators typically offered the items at attractive prices and often stated that personal exigencies, such as unemployment, military deployment, or family emergencies, required that they sell the offered items quickly. To gain the confidence of prospective buyers, conspirators posing as owners of the items instructed buyers that the transactions were to be completed through eBay, Yahoo!Finance, or similar online services, which would securely hold the buyers’ funds until the purchased items were delivered. The conspirators sent e-mails to buyers which appeared or purported to be from eBay, Yahoo!Finance, or other such entities, and which instructed buyers to remit payment to designated agents of those entities who were to hold the purchase money in escrow until the transactions was concluded. In reality, the entire transaction was a sham: the conspirators did not deliver any of the items offered for sale; neither eBay, Yahoo!Finance, nor any similar entity participated in these transactions; and the purported escrow agents designated to receive buyers’ purchase money were actually participants in the scheme who received the funds fraudulently obtained from buyers on behalf of the conspiracy.
Relying on the schemers fraudulent representations, scores of buyers agreed to purchase items that the schemers offered online and in newspaper advertisements. The conspirators kept and converted the fraudulently obtained purchase money for their own purposes. The defendants and their associates allegedly obtained more than $3 million through the fraud scheme, which they distributed among the conspirators both inside and outside the United States.
Defendants:
- Eduard Petroiu, 28, Las Vegas resident
- Vladimir Budestean, 24, Las Vegas resident
- Bertly Ellazar, 27, Las Vegas resident
- Radu Lisnic, 25, Las Vegas resident
- Evghenii Russu, 25, Las Vegas resident
- Evgeny Krylov, 24, Las Vegas resident
- Eugeni Stoytchev, 35, Las Vegas resident
- Iavor Stoytchev, 28, Las Vegas resident
- Christopher Castro, 27, Las Vegas resident
- Delyana Nedyalkova, 23, Las Vegas resident
- Oleh Rymarchuk, 21, Las Vegas resident
- Melanie Pascua, 25, Las Vegas resident
- Manuel Garza, 23, Las Vegas resident
- Ryne Green, 25, Las Vegas resident
- Michael Vales, 22, Las Vegas resident
- Edelin Dimitrov, 20, Las Vegas resident
The indictment identifies Eduard Petroiu as a leader of the conspiracy, and six others, including Vladimir Budestean, Bertly Ellazar, Radu Lisnic, Evghenii Russu, and Eugeni Stoytechev, as subordinate managers of the conspiracy.
If convicted, the defendants face up to 60 years in prison and fines of up to $1 million.
The arrests result from a joint investigation by the FBI and the Las Vegas Metropolitan Police Department as part of its Nevada Cyber Crime and Southern Nevada Eastern European Organized Crime Task Forces. The case is being prosecuted by Assistant U.S. Attorney Timothy S. Vasquez.
The public is reminded that an indictment contains only charges and is not evidence of guilt. The defendants are presumed innocent and entitled to a fair trial at which the government has the burden of proving guilt beyond a reasonable doubt.
Anyone with information regarding these individuals is urged to call the FBI in Las Vegas at (702) 385-1281 or, to remain anonymous, call Crime Stoppers at (702) 385-5555 or visit http://www.crimestoppersofnv.com. Tips directly leading to an arrest or an indictment processed through Crime Stoppers may result in a cash reward.
UNCENSORED – Women Protest Worldwide Photos 10
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict34.jpg) Egyptian army soldiers rear arrest a woman protester wearing the Niqab during clashes near Cairo’s downtown Tahrir Square, Egypt, Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building. (Ahmed Ali) Egyptian army soldiers rear arrest a woman protester wearing the Niqab during clashes near Cairo’s downtown Tahrir Square, Egypt, Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building. (Ahmed Ali) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict0.jpg) Egyptian army soldiers beat a protester wearing a Niqab, an Islamic veil, during clashes near Cairo’s downtown Tahrir Square, Egypt, Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building. At background graffiti depicts members of the military ruling council and Arabic reads: “Killer”. (Ahmed Ali) Egyptian army soldiers beat a protester wearing a Niqab, an Islamic veil, during clashes near Cairo’s downtown Tahrir Square, Egypt, Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building. At background graffiti depicts members of the military ruling council and Arabic reads: “Killer”. (Ahmed Ali) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict1.jpg) Egyptian protesters threw rocks at military police during clashes near Cairo’s downtown Tahrir Square, Egypt, Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building. (Ahmed Ali) Egyptian protesters threw rocks at military police during clashes near Cairo’s downtown Tahrir Square, Egypt, Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building. (Ahmed Ali)
|
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict3.jpg) ![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict6.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict33.jpg) Egyptian army soldiers arrest a woman protester during clashes with military police near Cairo’s downtown Tahrir Square, Egypt Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building. Egyptian army soldiers arrest a woman protester during clashes with military police near Cairo’s downtown Tahrir Square, Egypt Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict32.jpg) Egyptian army soldiers arrest a woman protester during clashes with military police near Cairo’s downtown Tahrir Square, Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building. Egyptian army soldiers arrest a woman protester during clashes with military police near Cairo’s downtown Tahrir Square, Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict35.jpg) Egyptian soldiers arrested a female protester during the second day of clashes in Tahrir Square in Cairo on Saturday. Reuters Egyptian soldiers arrested a female protester during the second day of clashes in Tahrir Square in Cairo on Saturday. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict2.jpg) A woman is taken away by the Egyptian army during clashes in central Cairo on Dec. 16, 2011. (Khaled Elfiqi) A woman is taken away by the Egyptian army during clashes in central Cairo on Dec. 16, 2011. (Khaled Elfiqi) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict4.jpg) Egyptian anti-army protesters throw stones at pro-army protesters (not pictured) during clashes, in central Cairo, Egypt, 16 december 2011. EPA Egyptian anti-army protesters throw stones at pro-army protesters (not pictured) during clashes, in central Cairo, Egypt, 16 december 2011. EPA |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict7.jpg) Egyptian soldiers clash with protesters near Cairo’s Tahrir Square on December 16, 2011 after demonstrators threw petrol bombs and set fire to furniture in front of the nearby parliament. AFP Egyptian soldiers clash with protesters near Cairo’s Tahrir Square on December 16, 2011 after demonstrators threw petrol bombs and set fire to furniture in front of the nearby parliament. AFP
|
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict9.jpg) Anti-government protesters react to tear gas fired by riot police during clashes Saturday, Dec. 17, 2011, in Abu Saiba village west of the capital of Manama, Bahrain. It was the third straight day of clashes along a main highway where protesters have been trying to stage sit-ins against the government. (Hasan Jamali) Anti-government protesters react to tear gas fired by riot police during clashes Saturday, Dec. 17, 2011, in Abu Saiba village west of the capital of Manama, Bahrain. It was the third straight day of clashes along a main highway where protesters have been trying to stage sit-ins against the government. (Hasan Jamali) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict19.jpg) Protestors supporting Pfc. Bradley Manning gather outside Ft. Meade, Md., Saturday, Dec. 17, 2011, where military prosecutors are presenting their case against him as the source for the WikiLeaks website’s collection of U.S. military and diplomatic secrets. Manning, 24-year-old today, is blamed for the largest leak of classified material in American history. The purpose of the hearing is to determine whether prosecutors have enough evidence to bring Manning to trial. (Jose Luis Magana) Protestors supporting Pfc. Bradley Manning gather outside Ft. Meade, Md., Saturday, Dec. 17, 2011, where military prosecutors are presenting their case against him as the source for the WikiLeaks website’s collection of U.S. military and diplomatic secrets. Manning, 24-year-old today, is blamed for the largest leak of classified material in American history. The purpose of the hearing is to determine whether prosecutors have enough evidence to bring Manning to trial. (Jose Luis Magana) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict17.jpg) Activist of women’s movement FEMEN stand atop a fence during their protest in front of the cabinet of the Ministers building in Kiev on December 16, 2011. The young Ukrainian women climbed up a fence in front of the Cabinet of Ministers building and protested against the lack of women in the Prime Minister Mykola Azarov’s government. Getty Activist of women’s movement FEMEN stand atop a fence during their protest in front of the cabinet of the Ministers building in Kiev on December 16, 2011. The young Ukrainian women climbed up a fence in front of the Cabinet of Ministers building and protested against the lack of women in the Prime Minister Mykola Azarov’s government. Getty
|
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict10.jpg) Anti-government protesters gesture toward riot police (unseen) Thursday, Dec. 15, 2011, along a northern highway by the entry to the Shiite village of Saar, Bahrain, site of an opposition sit-in that was dispersed by police with tear gas and sound bombs. (Hasan Jamali) Anti-government protesters gesture toward riot police (unseen) Thursday, Dec. 15, 2011, along a northern highway by the entry to the Shiite village of Saar, Bahrain, site of an opposition sit-in that was dispersed by police with tear gas and sound bombs. (Hasan Jamali) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict11.jpg) Protestors hold on to a rope, forming a human chain, while marching to the finance ministry Thursday, Dec. 15 2011, in Lisbon. Civil servants’ unions organized the demonstration to protest the government’s austerity measures. Portugal needed a euro78 billion ($103 billion) bailout earlier this year as its high debt load pushed it close to bankruptcy and the government is enacting an austerity program of pay cuts and tax hikes. Banners read “Don’t rob the future”. (Armando Franca) Protestors hold on to a rope, forming a human chain, while marching to the finance ministry Thursday, Dec. 15 2011, in Lisbon. Civil servants’ unions organized the demonstration to protest the government’s austerity measures. Portugal needed a euro78 billion ($103 billion) bailout earlier this year as its high debt load pushed it close to bankruptcy and the government is enacting an austerity program of pay cuts and tax hikes. Banners read “Don’t rob the future”. (Armando Franca) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict12.jpg) In this photo taken Tuesday, Dec. 13, 2011, villagers chant slogans as they gather for a protest in Wukan village of Lufeng, China’s Guangdong province. China’s government is trying to defuse a revolt in the small fishing village, offering to investigate the land seizures that touched off the rebellion and vowing to punish leaders of the uprising. The village of Wukan has for months been the site of simmering protests by locals who say officials sold farmland to developers without their consent. In this photo taken Tuesday, Dec. 13, 2011, villagers chant slogans as they gather for a protest in Wukan village of Lufeng, China’s Guangdong province. China’s government is trying to defuse a revolt in the small fishing village, offering to investigate the land seizures that touched off the rebellion and vowing to punish leaders of the uprising. The village of Wukan has for months been the site of simmering protests by locals who say officials sold farmland to developers without their consent. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict13.jpg) Thousands of Lebanese private and public school teachers hold protest in front of the government building in downtown Beirut, Lebanon, Thursday, Dec. 15, 2011, to demand higher wages. The protest comes a week after the government approved a salary raise that many employees considered too low . (Bilal Hussein) Thousands of Lebanese private and public school teachers hold protest in front of the government building in downtown Beirut, Lebanon, Thursday, Dec. 15, 2011, to demand higher wages. The protest comes a week after the government approved a salary raise that many employees considered too low . (Bilal Hussein) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict14.jpg) Indian farmers stage a sit in protest as they demand adequate compensation for their farm land acquired for different government projects in Lucknow, India, Wednesday, Dec. 14, 2011. India’s transformation from a largely agrarian nation into a global economic power hinges on a steady supply of land for new factories, call centers, power plants and homes. As cities spill over their seams with ever more people, the government is increasingly seizing the farms around them for private development. Indian farmers stage a sit in protest as they demand adequate compensation for their farm land acquired for different government projects in Lucknow, India, Wednesday, Dec. 14, 2011. India’s transformation from a largely agrarian nation into a global economic power hinges on a steady supply of land for new factories, call centers, power plants and homes. As cities spill over their seams with ever more people, the government is increasingly seizing the farms around them for private development. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict15.jpg) Dozens of peasants and activists protest demanding the government to recognize them as victims of the country’s internal conflict, outside the Congress in Bogota, Colombia, Wednesday, Dec. 14, 2011. (William Fernando Martinez) Dozens of peasants and activists protest demanding the government to recognize them as victims of the country’s internal conflict, outside the Congress in Bogota, Colombia, Wednesday, Dec. 14, 2011. (William Fernando Martinez) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict16.jpg) Protesters with Occupy Seattle march to the Pat the Port of Seattle, Monday afternoon, Dec. 12, 2011 as part of a national effort to disrupt West Coast port traffic. Organizers called for the protests, hoping the day of demonstrations would cut into the profits of the corporations that run the docks and send a message that their movement was not over. (Mark Harrison) Protesters with Occupy Seattle march to the Pat the Port of Seattle, Monday afternoon, Dec. 12, 2011 as part of a national effort to disrupt West Coast port traffic. Organizers called for the protests, hoping the day of demonstrations would cut into the profits of the corporations that run the docks and send a message that their movement was not over. (Mark Harrison) |
TOP-SECRET – Taash Communications Network: Iranian Green Movement Support Plan

Among the lessons learned from the revolutions in Egypt and Tunisia is the value and affect of unencumbered access to information and communications technology (ISCT), including but not limited to independent information and social networking across multiple platforms, such as mobile, internet, web-based, and satellite broadcast.
The current ICT available in and outside Iran remain largely silod platforms (i.e. lacking technology that facilitates convergence of information and interactivity). In general, the younger generation that support reform and actively oppose the regime from within have not been able to effectively access newer technologies or have been dissuaded from participating in communications programs operated by less legitimate traditional opposition parties from outside. Most these platforms are either state sponsored, like VOA and BBC, or are exile opposition websites and channels out of Los Angeles with a political agenda and low tolerance for alternative viewpoints. Most have failed to stay up to date with the language, trends, mentality, culture, and sociopolitical situation of the today Iran. The partisan nature of the older generation opposition groups further limit their ability to reach the younger demographic.
The traditional opposition groups based outside Iran do not maintain the legitimacy, technical capability, or political synergies to collaborate with the new generation of civil society organizations in Iran. Moreover, none of the existing available communication platforms effectively leverage digital content and networking by combining interactive mobile, internet, web, and satellite based secure communications vehicles.
The Democracy Council, in response to requests from prominent activists and organizations representing the Green Movement and other emerging sectors of civil society to collaboratively develop and deploy a “virtual sanctuary” for reform – minded Iranians to communicate, inform, network, organize, and advocate with each other and the larger Iranian society as well as the outside world. Currently, a significant amount of digital networking and content is produced by organizations affiliated with the Green Movement and independent civil society organizations (CSOs) in and outside Iran. However, distribution and leveraging f such content is limited by: 1. Technology available to CSOs, 2. Unaccommodating regional distribution platforms, internet, web and satellite based, 3. Lack of resources or skills to circumvent censorship and security regimes, 4. Lack of shared practices and resources. TCN will provide solutions to these four issues. In addition, CSOs and activists will merge their communications’ operations into the TCN platform to facilitate immediate and leveraged impact in Iran and the Persian-speaking world. For example, TCN will leverage the databases, mailing lists, and informal and formal marketing and advocacy operations through the single branded portal. These individual CSOs and independent producers would continue to manage their networking and marketing operations through the larger platform.
Taash Communications Network (TCN), developed by the Democracy Council (the Council) in collaboration with the leading representatives from the Green Movement, will help to meet this demand by providing the first robust, multilevel (internet, web, mobile, and satellite broadcast) communications channel for regionally produced progressive (uncensored) content and communications. TCN will operate as branded technological distribution portal (platform) made available to independent content and communications produced by and for progressive and reform – minded Iranians.
TCN will be the Facebook, twitter, NPR, and C-Span of Persian media under one roof with a focus on social and political issues concerning the Iranian public inside the country, in the region, and abroad. It will be a uniting factor that is demand-driven (commercially sustainable).
TCN will not produce content but provide technical services for the benefit of Iranian civil society.
…
SUMMARY PROGRAM DESCRIPTION:
Developed in coordination with prominent civil society figures in Iran, including representatives of the Green Movement, TCN would serve as a secure, robust, multilevel communications platform by which civil society members can deliver Persian content through:
· Interactive Website
· Advanced online (e.g. social networking) and mobile tools to secure unfettered access, availability, and interactivity to the content.
· Branded Persian Language video broadcast platform TCN would be owned by the nonprofit TCN Foundation registered in a European country, such as Denmark. The foundation’s mission would be to make available an independent, branded Persianlanguage communications platform that is available for high-quality user-generated programming.TCN will serve as an independent distribution platform without production activities and distributing largely “homegrown” content. TCN would not produce or fund any content itself. Content will be broadly through independently produced user-generated local and regional programming. These contents will be supplemented by the purchase of Persian rights to acquisition of online or TV entertainment programming, with progressive themes from Hollywood to Bollywood. TCN will be an independently-owned multi layer open platform for progressive, reform-minded or “edgy” programming without censorship. A number of civil society organizations and other groups, such as prominent figures in the Green Movement have already expressed an interest and are committed in producing programming and
content for distribution by many different TCN platforms.For example, TCN has received written expressions of support and pledges to produce content from a broad spectrum of independent individuals and organizations, such as:
· Mohsen Sazegara, a leading dissident and one of the original founders of the Iranian Revolutionary Guard
· Democratic Party of Iranian Kurdistan
· Shideh Rezaei, co-founder of Iran-Rooyan
· Ahmad Batebi, Human Rights Activists
· Mohammad Sadeghi Esfahlani, founder and administrator of Mir Hossein Mousavi’s and Zahra Rahnavard’s Supporters’ Network on Facebook,This informative, educational, and entertaining medium will actively engage, inform, inspire, and link Iranians without censorship. To meet the demand of the target market, foreign films, generally illegal in Iran for containing progressive themes, would be acquired and dubbed to augment the original programming. Such content would be distributed and made accessible through multiple mediums: a secure website that contains social networking applications, and utilizes mobile and circumvention tools, and a robust satellite broadcast channel.
TCN would work collaboratively with local and regional CSO’s to design and deploy a strategic audience acquisition program leveraging new technologies and viral techniques. Each independent producer would manage their own networking and advocacy component as a back end to their own regular internet or TV programming. TCN provides the technical background to ensure high penetration, distribution, and secure accessibility.
DOWNLOAD ORIGINAL DOCUMENT HERE
CONFIDENTIAL – IMF, EU, European Central Bank “Troika” Greece Debt Sustainability Analysis October 21, 2011

DOWNLOAD ORIGINAL DOCUMENT ABOVE BY CLICKING
This draft analysis by the so-called “troika” of the IMF, European Commission, and the European Central Bank was leaked.
Since the fourth review, the situation in Greece has taken a turn for the worse, with the economy increasingly adjusting through recession and related wage-price channels, rather than through structural reform driven increases in productivity. The authorities have also struggled to meet their policy commitments against these headwinds. For the purpose of the debt sustainability assessment, a revised baseline has been specified, which takes into account the implications of these developments for future growth and for likely policy outcomes. It has been extended through 2030 to fully capture long term growth dynamics, and possible financing implications.
The assessment shows that debt will remain high for the entire forecast horizon. While it would decline at a slow rate given heavy official support at low interest rates (through the EFSF as agreed at the July 21 Summit), this trajectory is not robust to a range of shocks. Making debt sustainable will require an ambitious combination of official support and private sector involvement (PSI). Even with much stronger PSI, large official sector support would be needed for an extended period. In this sense, ultimately sustainability depends on the strength of the official sector commitment to Greece.
…
3. Under these assumptions, Greece’s debt peaks at very high levels and would decline at a very slow rate pointing to the need for further debt relief to ensure sustainability. Debt (net of collateral required for PSI) would peak at 186 percent of GDP in 2013 and decline only to 152 percent of GDP by end-2020 and to 130 percent of GDP by end-2030. The financing package agreed on July 21(especially lower rates on EFSF loans) does help the debt trajectory, but its impact is more than offset by the revised macro and policy framework. Greece would not return to the market until 2021 under the market access assumptions used, and cumulatively official additional financing needs (beyond what remains in the present program, and including the eventual rollover of existing official loans) could amount to some €252 billion from the present through to 2020.

DOWNLOAD ORIGINAL DOCUMENT HERE
Das renommierte unabhängige und objektive Handelsblatt über die kriminellen “GoMoPa”-Betrüger
Zitat: “Es ist allerdings nicht das erste Mal, dass Gomopa-Vertreter ins Zwielicht geraten. 2006 wurden Vornkahl und Mitgründer Klaus Maurischat wegen Betrugs an einem Anleger verurteilt. Maurischat gab gestern gegenüber dem Handelsblatt weitere Verurteilungen zu. Es habe sich dabei jedoch nicht um Anlagebetrug gehandelt.”
Tribute to a Legend – Christopher Hitchens: Whisky, Cigs & Jefferson
2006: Hitchens at D.G.Wills Books, 7461 Girard Avenue, La Jolla, Ca. 92037
http://www.vanityfair.com/online/daily/2011/12/In-Memoriam-Christopher-Hitche… Vanity Fair In Memoriam: Christopher Hitchens, 1949–2011, by Juli Weiner, Dec 15th 2011.
Christopher Hitchens—the incomparable critic, masterful rhetorician, fiery wit, and fearless bon vivant—died today at the age of 62. Hitchens was diagnosed with esophageal cancer in the spring of 2010, just after the publication of his memoir, Hitch-22, and began chemotherapy soon after. “My chief consolation in this year of living dyingly has been the presence of friends,” he wrote in the June 2011 issue. He died in their presence, too, at the MD Anderson Cancer Center in Houston, Texas. May his 62 years of living, well, so livingly console the many of us who will miss him dearly
——
Christopher Eric Hitchens (born 13 April 1949) is an Anglo-American author and journalist whose books, essays, and journalistic career span more than four decades. He has been a columnist and literary critic at The Atlantic, Vanity Fair, Slate, World Affairs, The Nation, Free Inquiry, and became a media fellow at the Hoover Institution in September 2008. He is a staple of talk shows and lecture circuits and in 2005 was voted the world’s fifth top public intellectual in a Prospect/Foreign Policy poll. He’s known for his admiration of George Orwell, Thomas Paine, and Thomas Jefferson and for his excoriating critiques of, among others, Mother Teresa, Bill and Hillary Clinton, and Henry Kissinger. His confrontational style of debate has made him both a lauded and controversial figure. As a political observer, polemicist and self-defined radical, he rose to prominence as a fixture of the left-wing publications in his native Britain and in the United States. His departure from the established political left began in 1989 after what he called the “tepid reaction” of the Western left following Ayatollah Khomeini’s issue of a fatwa- calling for the murder of Salman Rushdie. The 11 September 2001 attacks strengthened his internationalist embrace of an interventionist foreign policy, and his vociferous criticism of what he called “fascism with an Islamic face.” His numerous editorials in support of the Iraq War caused some to label him a neoconservative, although Hitchens insists he is not “a conservative of any kind”
TOP-SECRET from the CIA- Ronald Reagan: Intelligence and the End of the Cold War

Ronald Reagan became the 40th president of the United States more than thirty years ago, and ever since he stepped down to return to California eight years later, historians, political scientists, and pundits of all stripes have debated the meaning of his presidency. All modern presidents undergo reappraisal after their terms in office. Reagan has undergone a similar reappraisal. The old view, exemplified by Clark Clifford’s famous characterization that Reagan was “an amiable dunce,” posited Reagan as a great communicator, to be sure, but one without substance, a former actor who knew the lines others wrote for him, but intellectually an empty suit. Reagan, in the old narrative, simply could not be the architect of anything positive that happened while he was president. That perspective has changed forever and is marked by the continually improving regard historians have for Reagan.
DOWNLOAD ORIGINAL DOCUMENT HERE
SECRET – “Godfather” of Colombian Army Intelligence Acquitted in Palace of Justice Case
Washington, D.C. , December 18, 2011 – A Colombian army general acquitted today in one of the country’s most infamous human rights cases “actively” collaborated with paramilitary death squads responsible for dozens of massacres, according to formerly secret U.S. records obtained under the Freedom of Information Act by the National Security Archive.
Once the third-highest-ranking officer in the Colombian military and later a top adviser to President Álvaro Uribe’s Department of Administrative Security (DAS), Iván Ramírez Quintero was acquitted today in the torture and disappearance of Irma Franco, one of several people detained by the army during the November 1985 Palace of Justice disaster.
The exoneration comes despite substantial evidence, including declassified U.S. embassy cables, linking Ramírez to the disappearances. Among the documents are reports that the missing individuals were “tortured and killed” by members of the Charry Solano Brigade, the unit led by Ramírez at that time.
Two former senior army officers, Col. Alfonso Plazas Vega and Gen. Jesús Armando Arias Cabrales, have already been convicted in the Palace of Justice disaster and remain the only people sentenced in the now more than 25-year-old case. More than 100 people, including 11 Supreme Court justices, perished during military operations to retake the Palace of Justice from M-19 insurgents who seized the building in November 1985. A document previously published by the Archive blamed “soldiers under the command of Col. Alfonso Plazas Vega” for the deaths of individuals detained by the army following the raid.
The declassified file on Gen. Iván Ramírez Quintero, the so-called “godfather of army intelligence,” portrays him as a shrewd and corrupt spymaster who shared sensitive intelligence with illegal militia groups, cultivated relationships with drug traffickers and notorious paramilitary figures, and engaged in “scare tactics” to take down his political enemies.
“Portrait of a Corrupt General”
The declassified reports focus on ties between Ramírez, narco-traffickers, and the country’s illegal paramilitary groups in the 1990s, particularly while he was in charge of the army’s First Division, along Colombia’s Atlantic coast, where he maintained “direct links with paramilitaries,” according to intelligence sources cited in a 1996 Embassy cable. The following year, a special Defense Intelligence Agency report pictured Ramírez beneath the heading, “Portrait of a Corrupt General,” and next to a picture of “Drug Trafficker-Backed Paramilitary Forces.”
U.S. Ambassador Myles Frechette spoke with at least two different Colombian defense ministers about the general’s “suspected ties to narcotraffickers and paramilitaries.” In a November 1997 meeting with Colombian minister of defense Gilberto Echeverri, Frechette cited “more evidence suggesting that Ramirez is passing military intelligence to the paramilitaries, and that the intelligence is being used against the guerrillas.” Frechette had good reason for concern. A new U.S. law linking foreign military assistance to human rights performance had heightened the embassy’s focus on abusive officers, and Ramírez, despite pressure from the U.S. over his human rights record, had just been designated as the next army inspector general. Frechette bluntly told the defense minister “that if Ramirez were to attain higher rank or position, it would seriously compromise the USG’s [United States Government’s] ability to cooperate with the Colombian military.”
“Godfather of army intelligence”
U.S. contacts in the Colombian military took a similarly dim view of Ramírez. One former colonel said he was “convinced [that Ramírez] has gone far beyond the passive phase with paramilitaries and is actively supporting them.” The colonel was “concerned about the potential direction the Colar [Colombian army] could take if Ramirez abuses his position as IG [inspector general] or, worse, if he is allowed to rise to even higher positions in the armed forces hierarchy.” Ramírez is repeatedly characterized as the “godfather of army intelligence” with influence “so pervasive within the military intelligence community” that he maintained control over intelligence assignments even from non-intelligence posts.
Another retired Colombian officer told the Embassy that Ramírez had been the “godfather” of Colombia’s “intelligence mafia” for more than 20 years. The general “surrounded himself with loyal subordinates who ‘covered up for him'” and was connected to “shady elements” inside the army’s 20th Military Intelligence Brigade,” according to a cable reporting on the meeting.
The 20th Brigade was established in 1990 on the recommendations of a U.S. intelligence team, and Ramírez was its first commander. “Fundamentally designed for covert operations,” the brigade’s members were attached to army units across the country, according to a U.S. Army report (See page 79.). Personnel worked “undercover and in civilian clothes,” reporting only to division commanders and other intelligence officers.
The brigade became the most visible symbol of Colombia’s corrupt and abusive intelligence establishment, and was tied to political assassinations, the torture of suspected guerrillas, and Colombia’s brutal paramilitary forces. The State Department’s human rights report for 1997 singled out the intelligence brigade for “death squad activity,” a charge also leveled by Ambassador Frechette as he left the Bogotá post late that year.
Pulling the strings was the “godfather” Ramírez. One report addressed to the State Department’s under secretary for political affairs, Thomas Pickering, asserted that “Ramirez and some elements of the Bogota-based 20th Intelligence Brigade actively collaborate with paramilitaries by providing intelligence and other support.” The CIA connected Ramírez to Carlos Castaño, notorious head of the powerful United Self-defense Forces of Córdoba and Urabá (ACCU). A U.S. Embassy report from 1998 noted the army’s “new-found effectiveness in curbing the paramilitaries” since Ramírez had been removed from the First Division, adding that it seemed “more than coincidental that the recent anti-paramilitary actions have all taken place since the departure from northern Colombia of military personnel believed to favor paramilitaries.”
In May 1998, shortly before Colombia announced plans to dismantle the 20th Brigade, the State Department cancelled Ramírez’s U.S. visa. In an unusually passionate memo on the moral dilemma faced by U.S. policymakers in Colombia, the State Department’s desk officer for Andean Affairs, David Passage, made a rhetorical plea for self-reflection on the part of the Colombian army and the military intelligence system in particular. Colombia needed to develop “credible and defensible intelligence gathering techniques instead of 12-volt batteries and rubber hoses,” Passage asserted, strongly implying the Colombian military’s penchant for torture techniques.
Yes, we know the Colombian military doesn’t control all the paramilitary organizations – but we also know there are enough ties between many of them and Colombian military officers that it becomes impossible for us to turn a blind eye. NO, we’re not going to identify them; you know who they are. Heal yourselves before you ask us for help! If you don’t understand why we withdrew Gen Ivan Ramirez’s visa, then we’re too far apart to be able to cooperate with each other.
Three months later, a Washington Post report detailed extensive ties between Ramírez and paramilitary groups and also identified him as a “liaison and paid informant for the Central Intelligence Agency,” charges that he angrily denied. The damage done, Ramírez was passed up for promotion in 1999 and sent out of the country to serve as military attaché in Chile.
Never charged for his alleged paramilitary ties, Ramírez was appointed by President Álvaro Uribe as a special adviser to the country’s top civilian intelligence organization, the Administrative Department of Security (DAS) in 2006. The spy agency was subsequently found to be running a Watergate-style illegal-wiretapping operation targeting journalists, judges and human rights defenders.
Arrested for disappearances in the Palace of Justice case in 2008, Ramírez spent more than three years in preventive detention pending investigation and trial. Jailed former paramilitary chief Salvatore Mancuso has testified that both Ramírez and former DAS agents collaborated with his illegal forces.
The revelations about Gen. Ramírez are drawn from Colombia and the United States: Political Violence, Narcotics, and Human Rights, 1948-2010, a recent addition to the Digital National Security Archive. Edited by Michael Evans and published by ProQuest, the set consists of more than 3,000 declassified diplomatic and intelligence documents on Colombia’s decades-old conflict.
Confidential -Los Angeles Fusion Center: Detecting and Mitigating Cyber Threats

(U//FOUO) US citizens and assets – including the White House, the Central Intelligence Agency, InfraGard, the state of Arizona, and major defense contracting companies – experienced high-profile cyber threats and attacks in the first half of 2011. Most of the tactics and techniques used were not new, however the increase in attacks during the past few months exemplifies the growth of cyber incursions and reinforces the need to be aware of risks and mitigation techniques associated with cyber threats. Appendices A, B and C contain detailed lists of threats, potential indicators of attacks, and possible remedies; some areas may contain overlap.
(U) Different Actors, Different Motives, Different Threats
(U) Recent reporting has largely centered on attacks by “hacktivist” groups – loose collectives that conduct cyberactions to raise awareness regarding particular grievances or causes.ii These attacks generally garner significant media attention. While they are annoying, embarrassing, and disruptive to victims, they seldom result in meaningful losses or damage, beyond costs associated with website repair. More worrisome are sophisticated probes and attacks that exfiltrate sensitive data for malicious use, or plant software designed to disable systems. Attacks such as these may be conducted by state-sponsored actors or organized criminal enterprises, and may inflict greater damage and losses.
(U//FOUO) On 23 June, hacker group LulzSec released information taken from the Arizona Department of Public Safety – including personal information of law enforcement officers – to protest a controversial immigration law.
(U) A multi-phase attack between March and June 2011 against RSA, a secure token provider, and three major defense contractors, saw hackers use stolen and cloned token keys to breach and remove data from networks at the defense firms.
(U) The mid-2009 targeted Stuxnet virus temporarily disabled a uranium enrichment plant in Iran.
(U) Different Targets, Different Methods
(U//FOUO) A successful cyber attack can be detrimental to targeted systems, computers or individuals. Hackers may install programs that steal personal information, flood a browser with pop-up advertising, slow Internet connections, fill e-mail with advertisements and/or crash the system. They may take control of a computer, commit fraud or identity theft, or cause an individual to lose all data stored on that system. This can impact both personal and work systems, and can affect all aspects of an individual’s life.
(U//FOUO) Cyber threats can involve any aspect of communications and data infrastructure, but can be broadly categorized as threats to users, systems, and access devices, including mobile devices.
DOWNLOAD ORIGINAL DOCUMENT HERE
CONFIDENTIAL – (U//FOUO) FBI Threat to Law Enforcement From “Doxing”

(U//FOUO) The FBI assesses with high confidence a that law enforcement personnel and hacking victims are at risk for identity theft and harassment through a cyber technique called “doxing.” “Doxing” is a common practice among hackers in which a hacker will publicly release identifying information including full name, date of birth, address, and pictures typically retrieved from the social networking site profiles of a targeted individual.
(U//FOUO) In response to law enforcement activities that have occurred against Anonymous and LulzSecc since January 2011, members of these groups have increased their interest in targeting law enforcement in retaliation for the arrests and searches conducted. Hackers and hacktivists—hackers who commit a computer crime for communicating a socially or politically motivated message—have been openly discussing these activities on Twitter and posting information pertaining to law enforcement on their Twitter accounts and Internet Relay Chat (IRC) channels.
• (U//FOUO) In June 2011 members of Anonymous and LulzSec discussed an identified FBI agent in the IRC channel #lulzsec. The detailed information included when he or she started working for the FBI, training, assignments, and previous employment. FBI analysis suggests that this information was derived from a 2009 affidavit that was available on the Wired.com Web site.
• (U//FOUO) On 26 July 2011 the Twitter account OpMonsanto, an account used by members of Anonymous, warned of the intention to “dox” FBI agents following the 19 July 2011 arrests of 16 individuals for their presumed role in Anonymous’ activities: “OpMonsanto: To any FBI agent involved in the continued unjust raiding of peaceful Anons: Expect us. You are no longer entitled to your privacy.”
• (U) On 31 July 2011 more than 70 law enforcement Web sites were hacked and large amounts of confidential data was exfiltrated. These Web sites included state and local police departments that were not associated with the takedowns. The data consisted of email addresses, usernames, Social Security numbers, home addresses, phone numbers, password dumps, internal training files, informant lists, jail inmate databases, and active warrant information. Operation AntiSecd claimed that the intrusion was in response to “bogus, trumped-up charges” against the individuals associated with Anonymous’ attacks on PayPal.
(U//FOUO) Recently, Anonymous members have also “doxed” the employees of companies that were victims of their previous attacks, who are perceived as working with law enforcement.
• (U) In July 2011 a sealed search warrant affidavit pertaining to the 19 July takedown was available on the Internet. The affidavit contained the personal information of employees of two US companies, as well as FBI personnel. The personal information consisted of names, units, and job titles.
(U) Outlook and Implications
(U//FOUO) The 19 July takedown of Anonymous and LulzSec members has increased members’ interest in targeting law enforcement in retaliation for the arrests and searches conducted. As more arrests are made against suspected members of Anonymous and LulzSec, the FBI expects hacking activities and “doxing” that targets law enforcement and government interests will continue. This could compromise investigations and result in harassment and identity theft of the individuals named in the “dox.”
(U//FOUO) Precautionary measures to mitigate potential harassment and identity theft risk to being “doxed” include:
o Safeguarding material containing personal information pertaining to officers and named victims;
o Changing passwords and do not reuse passwords for multiple accounts;
o Using strong passwords;
o Monitoring credit reports;
o Monitoring online personal information, including what others post about you on services such as social networking sites;
o Being careful when giving out contact information; and
o Being aware of social engineering tactics aimed at revealing sensitive information.
DOWNLOAD ORIGINAL DOCUMENT HERE
Confidential-Statement by Director General Israel Atomic Energy Commission To the International Atomic Energy Agency

Mme President,
Distinguished Delegates,
Mme President, let me begin by congratulating you, on being elected President of the General Conference. I can assure you the fullest cooperation of the delegation of Israel, in carrying out your important and responsible tasks. I also wish to congratulate the kingdom of Cambodia and the Republic of Rwanda as new members of the Agency. Yesterday, the General Conference has confirmed Ambassador Yukiya Amano of Japan, to the most professional and distinguished post of IAEA’s Director General. Israel has known Ambassador Amano’s professional qualifications and personal integrity over the years, and looks forward to working with him in this new capacity. We wish Ambassador Amano much success in guiding the work of the Agency.
Mme President,
In my address, I intend to dwell mainly on two issues: The new prospects for civil nuclear energy, and the risks associated with it. The risks include diversion of nuclear materials to military programs; nuclear terror; and safety and security of nuclear installations.
The nuclear industry has recently begun witnessing the emergence of a world-wide renaissance. While the intensive development of nuclear energy is highly desirable, it is imperative to minimize proliferation risks – especially risks which are associated with nuclear fuel cycle technologies. The characteristics of these technologies are that they are inherently dual use in their nature. It is the firm view and the policy of Israel, that the right to use nuclear energy for peaceful purposes is based on the absolute duty of each state not to abuse this right.
Mme President,
Israel attaches great importance to the nuclear non-proliferation regime. The regime has recently been under growing pressure, from within, by states that are parties to the NPT. Despite the geo-political realities in the Middle East, it has been Israel’s long standing policy of supporting, and wherever possible, joining arms control and other international treaties. In doing so, we are very appreciative of those who are conscious and mindful of Israel’s narrow security margins. In recent years, Israel has actively followed developments in the fields of nonproliferation and arms control. This includes a renewed interest in multilateral nuclear arms control and disarmament led by US President Barak Obama. Israel has continued to contribute to the global non-proliferation regime, through its policy of responsible behavior and restraint in the nuclear domain. Israel has repeatedly stated that it will not be the first to introduce nuclear weapons in to the Middle East. It is therefore regrettable that the outgoing Director General of the
IAEA, repeatedly mispresented Israel’s long standing policy in this regard. The continuous growth of Israel’s energy needs, coupled with its total dependence on foreign energy sources, poses a complex national challenge. Israel possesses advanced nuclear expertise and know-how that will play an impressive role when it comes to the future development of Israel’s energy sources.Mme President,
I would like to address Israel’s vision and policy, regarding the transformation of the Middle East to a zone free of weapons of mass destruction. It has always been the position of Israel that the nuclear issue, as well as all other security issues, could only be realistically addressed within the regional context. The African Nuclear Weapon Free Zone Treaty, which has recently entered into force, provides an excellent example of such an approach.
It is our vision and policy, to establish the Middle East as a mutually verifiable zone free of weapons of mass destruction and their delivery systems. We have always emphasized, that such a process, through direct negotiations, should begin with confidence building measures. They should be followed by mutual recognition, reconciliation, and peaceful relations. Consequently conventional and non-conventional arms control measures will emerge. Israel’s long-term goals for Middle East regional security and arms control were approved by the Israeli Government. As the international community has accepted and recognized in other regions, the establishment of such a zone can only emanate from within the region.
In our view, progress towards realizing this vision cannot be made without a fundamental change in regional circumstances, including a significant transformation in the attitude of states in the region towards Israel. The constant efforts by member states in the region to single out the State of Israel in blatantly anti-Israeli resolutions in this General Conference, is a clear reflection of such hostile attitude.
Mme President,
Significant and grave developments regarding nuclear proliferation have taken place in the recent years. I want to emphasize, that the most widely recognized cases of non-compliance with legally binding non-proliferation obligations, have occurred in the Middle East, by states that are parties to the NPT. Grave and covert violations by Iran and Syria had been detected and then formally reported by the IAEA. The Agency’s investigations in these two countries have been hampered by continued lack of cooperation, denial of access, and efforts to conceal and mislead the inspectors.
Israel is following these developments in our region, with profound concern. We all hope that the IAEA investigations will get to the bottom of these activities. In so doing it will assist the international community in its efforts to prevent dangerous proliferation of nuclear weapons, and the abuse of the right to peaceful nuclear energy.
We believe that it is crucial to improve and enhance the IAEA verification and inspection capabilities. We are also of the firm view, that IAEA investigations should be conducted free of any extraneous influences. Above all, the activities of those countries that breach their international commitments and obligations must be met with concrete and immediate international measures. Violations cannot go unpunished.
Mme President,
Another important issue, which poses many challenges to the international community, is nuclear safety and security. Adequate safety and physical security measures are crucial to ensure international acceptance of the nuclear civil industry. It is the long standing policy of the Israel Atomic Energy Commission, to pursue uncompromising standards of safety in its two nuclear research centers.
Mme President, Distinguished delegates.
The threat of radiological and nuclear materials in the hand of terrorists, confronts us all. In a world of global terrorist networks supported by rogue regimes, a secret and sudden attack, with a weapon of mass destruction, has become a chilling reality. None of us can confront this global threat alone. We must work together to secure the materials terrorists would need to build a radiological or improvised nuclear device. In this regard, we commend the IAEA for addressing the prevention of illicit trafficking of radioactive and nuclear materials. In view of these realities, Israel has joined the US-Russia led Global Initiative to Combat Nuclear Terrorism (GICNT). It has also joined the Megaport Initiative led by the US Department of Energy to prevent possible illicit trafficking of radioactive and nuclear materials. We believe that no effort and resources should be spared worldwide, in denying terrorists these materials. In this spirit, the Government of Israel welcomes President Obama’s initiative, to host a Global Summit on Nuclear
Security next year.Mme President,
Given the global realities we all face, the peaceful uses of nuclear energy, should have been the main topics of this Annual General Conference. Regrettably, instead, some countries are imposing on this General Conference politically motivated agenda items. These efforts are either designed to single out the State of Israel, or to divert attention from violations and real issues of non-compliance by certain Middle East states.
First among these, is Agenda item 22 entitled “Israeli Nuclear Capabilities”. This Agenda item is no more than a version of an old agenda item that was removed by agreement in 1993, and never acted upon. Among the sponsors of this draft resolution are countries that do not recognize the State of Israel, and even call for its annihilation. I wonder what moral standing they possess as they criticize Israel
for pursuing policies designed to secure its very existence.Mme President,
The second is agenda item 21 entitled: “The application of IAEA Safeguards in the Middle East”. Israel has joined the consensus on this Agenda Item for 14 consecutive years. We have done so notwithstanding our grave reservations, regarding the modalities included in the resolution’s text, and the relevance of this forum in addressing the establishment of the Middle East as a nuclear weapon free zone. As I mentioned before, such a zone can only emanate from within the region on the basis of arrangements freely arrived at through direct negotiations, between all the states concerned. No IAEA Forum could replace direct negotiations between the regional parties.
Unfortunately, since 2006, the consensus on the Middle East issues was broken. The only reason for this setback is the uncompromising attitude of the sponsors of these two draft resolutions who are aiming at extraneous political goals. This raises also doubts whether the promotion of the Middle East into a nuclear weapon free zone, is indeed the aim of the sponsors.
During recent months, Israel has approached Egypt directly and through other Governments, hoping to reach an agreed language on Middle East issues in this General Conference. In the same spirit, Israel has responded positively in the recent days to sincere efforts by several delegations and the President of the Conference to work together towards a positive outcome. It is my firm belief that it is not too late to reach consensus based on our respective positions. I can assure you all of our fullest cooperation in trying to reach consensus based on negotiations in good faith.
Mme President,
Iran’s initiative to promote Agenda item 24 on “The Prohibition of Armed Attack or threat of Attack against Nuclear Installations” is a clear case of hypocrisy. Iran is driven by wishful thinking, that the international community will condone Iran’s violations of its commitments and obligations, and its deception campaign over many years. No diplomatic smoke screen and maneuvering in the IAEA’s General Conference can obscure the real facts and findings. Let me remind all delegates that the Director General, in his recent address to the Board of Governors, provided an account of Iran’s non-cooperation with the Agency and said: “If this information is real”, “there is a high probability that nuclear weaponization activities have taken place”. The Government of Israel and many others assess, that the information available to the Agency is accurate and real. Iran, which is systematically violating several United Nations Security Council Resolutions, is seeking the sympathy of the same international community whose authority it flouts. I call on all delegations, to reject Iran’s transparent and cynical move.
Mme President,
The international community is at a critical crossroad in confronting a fundamental challenge. We should work together in promoting peaceful uses of nuclear energy, while preventing the spread of nuclear weapons and proliferation of sensitive technologies and materials.
Mme President, Distinguished delegates.
This coming Friday is the eve of the Jewish New Year 5770. In our prayers we say: “Here ends a year with its maledictions and a new year begins with its blessings”.
We hope that this year holds blessings and peace for all.
Thank you Mme President.
DOWNLOAD ORIGINAL DOCUMENT HERE
Uncensored – Bradley Manning Protest 16 December 2011
|
|
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict22.jpg) Army Pfc. Bradley Manning, left, is escorted out of a courthouse at Fort Meade, Md., Friday, Dec. 16, 2011, after the first day of a military hearing that will determine if he should face court-martial for his alleged role in the WikiLeaks classified leaks case. Manning is suspected of being the source in one of the largest unauthorized disclosures of classified information in U.S. history. (Cliff Owen) Army Pfc. Bradley Manning, left, is escorted out of a courthouse at Fort Meade, Md., Friday, Dec. 16, 2011, after the first day of a military hearing that will determine if he should face court-martial for his alleged role in the WikiLeaks classified leaks case. Manning is suspected of being the source in one of the largest unauthorized disclosures of classified information in U.S. history. (Cliff Owen) |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict24.jpg) Army Pfc. Bradley Manning is escorted in handcuffs out of a courthouse in Fort Meade, Md., Friday, Dec. 16, 2011, after the first day of a military hearing that will determine if he should face court-martial for his alleged role in the WikiLeaks classified leaks case. Manning is suspected of being the source in one of the largest unauthorized disclosures of classified information in U.S. history. (Cliff Owen) Army Pfc. Bradley Manning is escorted in handcuffs out of a courthouse in Fort Meade, Md., Friday, Dec. 16, 2011, after the first day of a military hearing that will determine if he should face court-martial for his alleged role in the WikiLeaks classified leaks case. Manning is suspected of being the source in one of the largest unauthorized disclosures of classified information in U.S. history. (Cliff Owen) |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict26.jpg) Pfc. Bradley Manning is escorted from his his Article 32 hearing December 16, 2011 in Fort Meade, Maryland. Manning is accused of disclosing more than 260,000 diplomatic cables, more than 90,000 intelligence reports on the war in Afghanistan and one video of a military helicopter attack to WikiLeaks, a Web site dedicated to publishing secret documents. Getty Pfc. Bradley Manning is escorted from his his Article 32 hearing December 16, 2011 in Fort Meade, Maryland. Manning is accused of disclosing more than 260,000 diplomatic cables, more than 90,000 intelligence reports on the war in Afghanistan and one video of a military helicopter attack to WikiLeaks, a Web site dedicated to publishing secret documents. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict25.jpg) Army security offices stand watch moments before Army Pfc. Bradley Manning is escorted out of a courthouse in Fort Meade, Md., Friday, Dec. 16, 2011, after the first day of a military hearing that will determine if he should face court-martial for his alleged role in the WikiLeaks classified leaks case. Manning is suspected of being the source in one of the largest unauthorized disclosures of classified information in U.S. history. (Cliff Owen) Army security offices stand watch moments before Army Pfc. Bradley Manning is escorted out of a courthouse in Fort Meade, Md., Friday, Dec. 16, 2011, after the first day of a military hearing that will determine if he should face court-martial for his alleged role in the WikiLeaks classified leaks case. Manning is suspected of being the source in one of the largest unauthorized disclosures of classified information in U.S. history. (Cliff Owen) |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict20.jpg) In this courtroom sketch, Army Pfc. Bradley Manning, second from left, sits as his attorney, David E. Coombs, speaks during a military hearing in Fort Meade, Md. , Friday, Dec. 16, 2011, that will determine if Manning should face court-martial for his alleged role in the WikiLeaks classified leaks case. Manning is suspected of being the source in one of the largest unauthorized disclosures of classified information in U.S. history. AP In this courtroom sketch, Army Pfc. Bradley Manning, second from left, sits as his attorney, David E. Coombs, speaks during a military hearing in Fort Meade, Md. , Friday, Dec. 16, 2011, that will determine if Manning should face court-martial for his alleged role in the WikiLeaks classified leaks case. Manning is suspected of being the source in one of the largest unauthorized disclosures of classified information in U.S. history. AP |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict21.jpg) David E. Coombs, attorney for Army Pfc. Bradley Manning, right, leaves a courthouse in Fort Meade, Md. , Friday, Dec. 16, 2011, during a recess in a military hearing that will determine if Manning should face court-martial for his alleged role in the WikiLeaks classified leaks case. Manning is suspected of being the source in one of the largest unauthorized disclosures of classified information in U.S. history. AP David E. Coombs, attorney for Army Pfc. Bradley Manning, right, leaves a courthouse in Fort Meade, Md. , Friday, Dec. 16, 2011, during a recess in a military hearing that will determine if Manning should face court-martial for his alleged role in the WikiLeaks classified leaks case. Manning is suspected of being the source in one of the largest unauthorized disclosures of classified information in U.S. history. AP |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict1.jpg) Protestors supporting Pfc. Bradley Manning march outside the gate of Ft. Meade, Md., Friday, Dec. 16, 2011, where Manning will be attending a hearing to determine if he will be court martialed. (Susan Walsh) Protestors supporting Pfc. Bradley Manning march outside the gate of Ft. Meade, Md., Friday, Dec. 16, 2011, where Manning will be attending a hearing to determine if he will be court martialed. (Susan Walsh) |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict2.jpg) Protestors supporting Pfc. Bradley Manning gather outside Ft. Meade, Md., Friday, Dec. 16, 2011, where Manning will be attending a hearing to determine if he will be court martialed. The U.S. military is making its case for why Manning should be court-martialed on charges of endangering national security by stealing and leaking an enormous trove of government secrets. (Susan Walsh) Protestors supporting Pfc. Bradley Manning gather outside Ft. Meade, Md., Friday, Dec. 16, 2011, where Manning will be attending a hearing to determine if he will be court martialed. The U.S. military is making its case for why Manning should be court-martialed on charges of endangering national security by stealing and leaking an enormous trove of government secrets. (Susan Walsh) |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict3.jpg) Protestors supporting Bradley Manning gather outside Ft. Meade, Md., Friday, Dec. 16, 2011, where Manning will be attending a hearing to determine if he will be court martialed. (Susan Walsh) Protestors supporting Bradley Manning gather outside Ft. Meade, Md., Friday, Dec. 16, 2011, where Manning will be attending a hearing to determine if he will be court martialed. (Susan Walsh) |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict4.jpg) Richard Ochs of Baltimore, Md., protests outside of Ft. Meade, Md., Friday, Dec. 16, 2011, to support Pfc. Bradley Manning who will be attending a hearing to determine if he will be court martialed. (Susan Walsh) Richard Ochs of Baltimore, Md., protests outside of Ft. Meade, Md., Friday, Dec. 16, 2011, to support Pfc. Bradley Manning who will be attending a hearing to determine if he will be court martialed. (Susan Walsh) |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict5.jpg) A soldier stands guard at a roadblock outside of a courthouse in Fort Meade, Md., Friday, Dec. 16, 2011, during a military hearing that will determine if Army Pfc. Bradley Manning should face court-martial for his alleged role in the WikiLeaks classified leaks case. Manning is suspected of being the source in one of the largest unauthorized disclosures of classified information in U.S. history. (Patrick Semansky) A soldier stands guard at a roadblock outside of a courthouse in Fort Meade, Md., Friday, Dec. 16, 2011, during a military hearing that will determine if Army Pfc. Bradley Manning should face court-martial for his alleged role in the WikiLeaks classified leaks case. Manning is suspected of being the source in one of the largest unauthorized disclosures of classified information in U.S. history. (Patrick Semansky) |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict6.jpg) Dave Eberhardt of Baltimore, Md., protests outside Ft. Meade, Md., Friday, Dec. 16, 2011, in support Pfc. Bradley Manning. The U.S. military is making its case for why Manning should be court-martialed on charges of endangering national security by stealing and leaking an enormous trove of government secrets. (Susan Walsh) Dave Eberhardt of Baltimore, Md., protests outside Ft. Meade, Md., Friday, Dec. 16, 2011, in support Pfc. Bradley Manning. The U.S. military is making its case for why Manning should be court-martialed on charges of endangering national security by stealing and leaking an enormous trove of government secrets. (Susan Walsh) |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict18.jpg) Supporters of Pfc. Bradley Manning walk away after attending his Article 32 hearing, on December 16, 2011 in Fort Meade, Maryland. Manning is accused of disclosing more than 260,000 diplomatic cables, more than 90,000 intelligence reports on the war in Afghanistan and one video of a military helicopter attack to WikiLeaks, a Web site dedicated to publishing secret documents. Getty Supporters of Pfc. Bradley Manning walk away after attending his Article 32 hearing, on December 16, 2011 in Fort Meade, Maryland. Manning is accused of disclosing more than 260,000 diplomatic cables, more than 90,000 intelligence reports on the war in Afghanistan and one video of a military helicopter attack to WikiLeaks, a Web site dedicated to publishing secret documents. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict19.jpg) Military police talk to supprters of Pfc. Bradley Manning after they attended his Article 32 hearing December 16, 2011 in Fort Meade, Maryland. Pfc. Manning is accused of disclosing more than 260,000 diplomatic cables, more than 90,000 intelligence reports on the war in Afghanistan and one video of a military helicopter attack to WikiLeaks, a Web site dedicated to publishing secret documents. Getty Military police talk to supprters of Pfc. Bradley Manning after they attended his Article 32 hearing December 16, 2011 in Fort Meade, Maryland. Pfc. Manning is accused of disclosing more than 260,000 diplomatic cables, more than 90,000 intelligence reports on the war in Afghanistan and one video of a military helicopter attack to WikiLeaks, a Web site dedicated to publishing secret documents. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict7.jpg) People walk into a courthouse in Fort Meade, Md., Friday, Dec. 16, 2011, for a military hearing that will determine if Army Pfc. Bradley Manning should face court-martial for his alleged role in the WikiLeaks classified leaks case. Manning is suspected of being the source in one of the largest unauthorized disclosures of classified information in U.S. history. (Patrick Semansky) People walk into a courthouse in Fort Meade, Md., Friday, Dec. 16, 2011, for a military hearing that will determine if Army Pfc. Bradley Manning should face court-martial for his alleged role in the WikiLeaks classified leaks case. Manning is suspected of being the source in one of the largest unauthorized disclosures of classified information in U.S. history. (Patrick Semansky)
|
|
|
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict10.jpg) Supporters of U.S. Army Private Bradley Manning, an Army intelligence analyst, hold vigil outside the gates of U.S. Army Fort George G. Meade where Manning’s Article 32 preliminary hearing will begin December 18, 2011 in Fort Meade, Maryland. Manning is accused of disclosing more than 260,000 diplomatic cables, more than 90,000 intelligence reports on the war in Afghanistan and one video of a military helicopter attack to WikiLeaks, a Web site dedicated to publishing secret documents. Getty Supporters of U.S. Army Private Bradley Manning, an Army intelligence analyst, hold vigil outside the gates of U.S. Army Fort George G. Meade where Manning’s Article 32 preliminary hearing will begin December 18, 2011 in Fort Meade, Maryland. Manning is accused of disclosing more than 260,000 diplomatic cables, more than 90,000 intelligence reports on the war in Afghanistan and one video of a military helicopter attack to WikiLeaks, a Web site dedicated to publishing secret documents. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict11.jpg) A helicopter from the Anne Arundel County Sheriff’s Office circles above supporters of U.S. Army Private Bradley Manning, an Army intelligence analyst, as they hold vigil outside the gates of U.S. Army Fort George G. Meade, where Manning’s Article 32 preliminary hearing is being held, December 18, 2011 in Fort Meade, Maryland. Manning is accused of disclosing more than 260,000 diplomatic cables, more than 90,000 intelligence reports on the war in Afghanistan and one video of a military helicopter attack to WikiLeaks, a Web site dedicated to publishing secret documents. Getty A helicopter from the Anne Arundel County Sheriff’s Office circles above supporters of U.S. Army Private Bradley Manning, an Army intelligence analyst, as they hold vigil outside the gates of U.S. Army Fort George G. Meade, where Manning’s Article 32 preliminary hearing is being held, December 18, 2011 in Fort Meade, Maryland. Manning is accused of disclosing more than 260,000 diplomatic cables, more than 90,000 intelligence reports on the war in Afghanistan and one video of a military helicopter attack to WikiLeaks, a Web site dedicated to publishing secret documents. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict12.jpg) A military personnel directs a group of people outside the courthouse at Fort Meade, Maryland during the U.S. vs Private Bradley E. Manning Article 32 hearing December 16, 2011. An Army intelligence analyst suspected in the biggest leak of classified U.S. documents in history makes his first court appearance on Friday accused of multiple charges including aiding the enemy, which could bring life imprisonment. Reuters A military personnel directs a group of people outside the courthouse at Fort Meade, Maryland during the U.S. vs Private Bradley E. Manning Article 32 hearing December 16, 2011. An Army intelligence analyst suspected in the biggest leak of classified U.S. documents in history makes his first court appearance on Friday accused of multiple charges including aiding the enemy, which could bring life imprisonment. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict13.jpg) Supporters of U.S. Army Private Bradley Manning, an Army intelligence analyst, hold vigil outside the gates of U.S. Army Fort George G. Meade where Manning’s Article 32 preliminary hearing will begin December 18, 2011 in Fort Meade, Maryland. Manning is accused of disclosing more than 260,000 diplomatic cables, more than 90,000 intelligence reports on the war in Afghanistan and one video of a military helicopter attack to WikiLeaks, a Web site dedicated to publishing secret documents. Getty Supporters of U.S. Army Private Bradley Manning, an Army intelligence analyst, hold vigil outside the gates of U.S. Army Fort George G. Meade where Manning’s Article 32 preliminary hearing will begin December 18, 2011 in Fort Meade, Maryland. Manning is accused of disclosing more than 260,000 diplomatic cables, more than 90,000 intelligence reports on the war in Afghanistan and one video of a military helicopter attack to WikiLeaks, a Web site dedicated to publishing secret documents. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict16.jpg) Journalists stand outside the courthouse at Fort Meade, Maryland during the U.S. vs Private Bradley E. Manning Article 32 hearing December 16, 2011. An Army intelligence analyst suspected in the biggest leak of classified U.S. documents in history makes his first court appearance on Friday accused of multiple charges including aiding the enemy, which could bring life imprisonment. Reuters Journalists stand outside the courthouse at Fort Meade, Maryland during the U.S. vs Private Bradley E. Manning Article 32 hearing December 16, 2011. An Army intelligence analyst suspected in the biggest leak of classified U.S. documents in history makes his first court appearance on Friday accused of multiple charges including aiding the enemy, which could bring life imprisonment. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict17.jpg) David E. Coombs, attorney for Army Pfc. Bradley Manning, leaves a courthouse in Fort Meade, Md. , Friday, Dec. 16, 2011, during a recess in a military hearing that will determine if Manning should face court-martial for his alleged role in the WikiLeaks classified leaks case. Manning is suspected of being the source in one of the largest unauthorized disclosures of classified information in U.S. history. David E. Coombs, attorney for Army Pfc. Bradley Manning, leaves a courthouse in Fort Meade, Md. , Friday, Dec. 16, 2011, during a recess in a military hearing that will determine if Manning should face court-martial for his alleged role in the WikiLeaks classified leaks case. Manning is suspected of being the source in one of the largest unauthorized disclosures of classified information in U.S. history. |
TOP – SECRET – (U//FOUO) U.S. Marine Corps Afghan Drone Operations in Regional Command Southwest (RC (SW))

(U) Purpose: To inform Deputy Commandants (DCs) Aviation, Combat Development and Integration (CD&I), Plans, Policies, and Operations (PP&O), Installations and Logistics (I&L), Commanding General (CG), Training and Education Command (TECOM), Director of Intelligence, operating forces, and others on results of a Marine Corps Center for Lessons Learned (MCCLL) collection conducted April – May 2011 to document lessons and observations regarding unmanned aerial systems (UAS) operations in support of Regional Command Southwest (RC (SW)) during Operation Enduring Freedom (OEF).
Bottom Line up Front
(U//FOUO) The RQ-7B Shadow UAS employed by the Marine Corps is a U. S. Army program of record. Because it is an Army program the Shadow has very high frequency (VHF) but no ultra-high frequency (UHF) retransmission capability. UHF is the primary means of communication between key elements of the Marine air command and control system (MACCS), airborne Marine Corps aviation assets, and Marine joint terminal attack controllers (JTAC) and forward air controllers (FAC). Developing a UHF retransmission capability for an organic USMC UAS was regarded as a primary need.
(U//FOUO) USMC units were dependent on joint assets for armed UAS missions and competed with virtually every other combat unit in OEF to schedule armed UAS sorties. Developing an organic armed USMC UAS was regarded as a priority.
(U//FOUO) Third Marine Aircraft Wing (MAW) Forward (Fwd) conceived and initiated a staff organization called the Marine air ground task force (MAGTF) Aerial Reconnaissance Coordination Cell (MARCC). The intent of the MARCC was to ensure that all aviation combat element (ACE) intelligence, surveillance, and reconnaissance (ISR) capabilities, manned and unmanned, were coordinated and employed to maximum effectiveness.
(U//FOUO) The establishment of the MARCC initially generated operational friction between the RC (SW) ACE and the ground combat element (GCE). The ACE regarded the MARCC as a more efficient means of conducting command and control of ACE assets. However, the GCE had been accustomed to a greater degree of autonomy in employing UASs and perceived the establishment of the MARCC as an impediment to responsiveness and their ability to dynamically retask UASs as desired.
(U//FOUO) As the ground scheme of maneuver evolved, establishing and supporting UAS “hubs” and “spokes” in proximity to ground forces posed a significant challenge to 3d MAW (Fwd) planners. [MCCLL Note: A hub is a UAS airfield base of operations used to launch and recover UASs and a spoke is a scalable outlying UAS control site supported by the hub.] In addition to requiring facilities suitable for the launch, recovery, and maintenance of UASs, a key consideration was the appropriate manning of each hub and spoke. A significant limiting factor in the MAW’s ability to establish hubs and spokes was a lack of trained intelligence analysts, UAS mission commanders, and maintenance personnel (this included contract maintenance support for the ScanEagle UAS due to contractor habitability mandates subject to that contract).
(U//FOUO) The volume of UAS sorties and their importance to the MAGTF is expected to increase in the future, including the development of a logistics support UAS and a new small tactical unmanned aerial system (STUAS). This has generated a need to determine where UAS assets would best be located within the ACE of the MAGTF. The Marine Unmanned Aerial Vehicle Squadron ONE and TWO (VMU-1 / VMU-2) commanding officers believed they should be located within a Marine aircraft group (MAG) just as all USMC aviation squadrons. [MCCLL Note: The VMUs are located within the Marine air control group (MACG) in garrison. During OEF deployment the VMUs were located directly within the MAW (Fwd) because there were no deployed MAGs and the MACG was composed of a small detachment.]
Key Points:
(U//FOUO) The MARCC worked to incorporate all ACE ISR capabilities into overall ISR planning done by RC (SW), advised RC (SW) planners and leaders on which aviation assets could best fill ISR requirements and requests, ensured air tasking order (ATO) development included the RC (SW) commander’s prioritization for tasking of ISR assets, streamlined information flow regarding these assets in order to build situational awareness throughout the MACCS, and facilitated the dynamic retasking of ISR platforms as necessary.
(U//FOUO) VMU-1 established a “hot weather schedule” during the summer months due to temperatures that could reach as high as 135 degrees Fahrenheit on the runway. This extreme heat could cause the Shadow’s wings to swell and vent fuel. However, the ScanEagle did not have this significant a problem with the heat and has longer endurance, so, the VMU scheduled ScanEagle sorties earlier in the day but still sufficient to cover the hottest time of day and Shadow sorties in the morning or evening. This enabled the VMU to maintain coverage throughout the fly-day. VMU-1 also erected a large area maintenance shelter for aircraft maintenance (LAMS-A) in order to keep aircraft and personnel out of the heat.
(U//FOUO) UAS technologies and capabilities continue to be developed and fielded. Training and education of UAS users, including unit air officers, intelligence officers, FACs, JTACs, and joint fires observers (JFO), regarding new capabilities and how best to employ UASs is vital. In order to support this, sufficient UAS assets must be made available during pre-deployment training.
(U//FOUO) The Marine Corps has recently fielded the Satellite Wide-Area Network version 2 (SWANv2) that will be included in the VMU organic table of equipment. Unlike the Digital Video Broadcasting Return Channel via Satellite (DVB-RCS) system currently being used, SWANv2 is a Marine Corps program of record that will enable the VMUs to disseminate full-motion video (FMV) signals more effectively.
(U//FOUO) In July, 2010, a contract was awarded to Boeing subsidiary Insitu, Inc. for development and production of the STUAS. STUAS will be used by the U.S. Navy and Marine Corps to provide persistent maritime and land-based tactical reconnaissance, surveillance, and target acquisition (RSTA) data collection and dissemination. Unlike the current ScanEagle and Shadow UASs, STUAS will have a UHF retransmission capability and the modularity to carry “plug-and-play” mission payloads such as hyper-spectral imaging sensors, synthetic aperture radar sensors, and potentially small precision-guided munitions (PGM) among others.
(U//FOUO) The establishment of the MARCC initially created the perception within the GCE of two separate procedures for requesting UAS support – one procedure for requesting organic support and a different procedure for requesting joint support. However, the 3d MAW (Fwd) Future Operations Officer said that, the team that developed the MARCC specifically avoided creating any new procedures for the end users.
(U//FOUO) The MARCC officer-in-charge (OIC) developed a comprehensive kneeboard card that had information regarding all of the unmanned assets that were going to be airborne during a particular fly-day. This provided aircrew with situational awareness that was critical to safety of flight and helped reduce the chance of mid-air collisions. The kneeboard card also provided time, location, and contact frequency information that could be used to more effectively and efficiently employ or retask UASs.
(U//FOUO) The RC (SW) ISR officer noted that they were building a “collection strategy playbook” that would describe different tactics, techniques, and procedures (TTP) that have proved successful in integrating different intelligence collections effects. For example: layering ground-moving-target-indicator data with dismounted-moving-target-indicator assets (two different kinds of radar) and integrating those with a wide-area surveillance sensor (such as a UAS, Ground Based Operational Surveillance System (GBOSS), or Aerostat balloon) in support of real-time operations.
(U//FOUO) The fact that there is no primary military occupational specialty (MOS) designator for UAS officers degraded the ability of the VMUs to retain corporate knowledge and experience within the UAS community. Instead, officers were assigned to VMUs for 18 – 24 month tours of duty, a substantial portion of which was spent in training, and usually never returned to the UAS community after transferring out.

DOWNLOAD ORIGINAL DOCUMENT HERE
Victims-Opfer.com zeigen – Fake CV of Klaus Maurischat Pseudoym Siegfried Siewert-Gefälschter Lebenslauf von Klaus Maurischat-Pseudoym Siegfried Siewert
BÖRSE ONLINE ÜBER DIE GEFÄLSCHTEN MITGLIEDERZAHLEN VON STASI-“GoMoPa”
Gomopa dürfte ohnehin ein Glaubwürdigkeitsproblem haben, denn der Dienst fiel mit falschen oder fragwürdigen Äußerungen auf. So gibt es laut Website 57 345 Mitglieder (Stand 21. September 2010). Die Mitgliedschaft ist bis auf einen einmonatigen Test kostenpflichtig. Einnahmen aus den Beiträgen beziffert Maurischat in seiner Information aber nur auf um die 5000 Euro. Selbst wenn alle Mitglieder die günstigste Variante gewählt haben, ergäben sich rechnerisch weit weniger als 1000 zahlende Mitglieder. Gomopa äußert sich dazu nicht.
UNCENSORED – NEW – FEMEN protestes EURO 2012
STASI – Codes für noch nicht enttarnte STASI-Agenten
140520406118;00;00;00;;;;;0,00
040424506110;00;00;00;;;;;0,00
290829406144;00;00;00;;;;;0,00
130563500711;00;00;00;;;;;0,00
130551419182;00;00;00;;;;;0,00
050860421817;00;00;00;;;;;0,00
011220406115;00;00;00;;;;;0,00
051143421034;00;00;00;;;;;0,00
030660424986;00;00;00;;;;;0,00
171161406811;00;00;00;; 000000000000000:;;;0,00
201067428226;14;08;00;;*, *:;;;13225,00
010170516214;09;06;20;;, GABRIELA:;;;1460,00
040866419938;99;99;99;;::;;;2475,00
050368418114;99;99;99;;::;;;2475,00
040168425038;99;99;99;;::;;;2475,00
050367405629;99;99;99;;::;;;2475,00
040167407516;99;99;99;;::;;;2475,00
050168421327;99;99;99;;::;;;2475,00
031067411812;99;99;99;;::;;;2475,00
050167422811;99;99;99;;::;;;2475,00
031067430028;99;99;99;;::;;;2475,00
040567406141;99;99;99;;::;;;2475,00
031267403817;99;99;99;;::;;;2475,00
040167420710;99;99;99;;::;;;2475,00
031067404225;99;99;99;;::;;;2475,00
040967413113;99;99;99;;::;;;2475,00
031066402615;99;99;99;;::;;;2475,00
041166411112;99;99;99;;::;;;2475,00
031267412211;99;99;99;;::;;;2475,00
041067407329;99;99;99;;::;;;2475,00
030967403012;99;99;99;;::;;;2475,00
040767424010;99;99;99;;::;;;2475,00
060268425068;99;99;99;;::;;;2475,00
050264402142;99;99;99;;::;;;2475,00
051166419746;99;99;99;;::;;;2475,00
030168415316;99;99;99;;::;;;2475,00
060268422713;99;99;99;;::;;;2475,00
060267402120;99;99;99;;::;;;2475,00
060167412225;99;99;99;;::;;;2475,00
051165419816;99;99;99;;::;;;2475,00
051067415117;99;99;99;;::;;;2475,00
051167428118;99;99;99;;::;;;2475,00
051266419620;99;99;99;;::;;;2475,00
051167417742;99;99;99;;::;;;2475,00
040267412275;99;99;99;;::;;;2475,00
040267414211;99;99;99;;::;;;2475,00
050567402545;99;99;99;;::;;;2475,00
040268417318;99;99;99;;::;;;2475,00
050866430036;99;99;99;;::;;;2475,00
040368426713;99;99;99;;::;;;2475,00
050767421310;99;99;99;;::;;;2475,00
040267420224;99;99;99;;::;;;2475,00
050667422463;99;99;99;;::;;;2475,00
040368426510;99;99;99;;::;;;2475,00
050966403115;99;99;99;;::;;;2475,00
030965415159;99;99;99;;::;;;2475,00
051166405133;99;99;99;;::;;;2475,00
030267430060;99;99;99;;::;;;2475,00
030467413062;99;99;99;;::;;;2475,00
040367405718;99;99;99;;::;;;2475,00
030667409527;99;99;99;;::;;;2475,00
050866416146;99;99;99;;::;;;2475,00
030367430199;99;99;99;;::;;;2475,00
050467424990;99;99;99;;::;;;2475,00
030168427712;99;99;99;;::;;;2475,00
041167418711;99;99;99;;::;;;2475,00
030766426824;99;99;99;;::;;;2475,00
040967426811;99;99;99;;::;;;2475,00
040967417448;99;99;99;;::;;;2475,00
040368422413;99;99;99;;::;;;2475,00
030268420227;99;99;99;;::;;;2475,00
050767405644;99;99;99;;::;;;2475,00
040866403223;99;99;99;;::;;;2475,00
040767413936;99;99;99;;::;;;2475,00
040467400754;99;99;99;;::;;;2475,00
050565417321;99;99;99;;::;;;2475,00
030367412134;99;99;99;;::;;;2475,00
150168419321;99;99;99;;::;;;2595,00
021267414111;99;99;99;;::;;;2475,00
030468430198;99;99;99;;::;;;2475,00
040167430417;99;99;99;;::;;;2475,00
030767411536;99;99;99;;::;;;2475,00
040268409318;99;99;99;;::;;;2475,00
030767413910;99;99;99;;::;;;2475,00
040267422211;99;99;99;;::;;;2475,00
030867424713;99;99;99;;::;;;2475,00
050967428242;99;99;99;;::;;;2475,00
030867419826;99;99;99;;::;;;2475,00
050767412924;99;99;99;;::;;;2475,00
040567402415;99;99;99;;::;;;2475,00
050567402537;99;99;99;;::;;;2475,00
030667411248;99;99;99;;::;;;2475,00
050468424431;99;99;99;;::;;;2475,00
030368420574;99;99;99;;::;;;2475,00
041266404438;99;99;99;;::;;;2475,00
030667419928;99;99;99;;::;;;2475,00
041267422830;99;99;99;;::;;;2475,00
030567420729;99;99;99;;::;;;2475,00
041066430260;99;99;99;;::;;;2475,00
030666419723;99;99;99;;::;;;2475,00
060268407652;99;99;99;;::;;;2475,00
030667429237;99;99;99;;::;;;2475,00
250267430217;99;99;99;;::;;;2550,00
020928430019;99;99;99;;::;;;2562,50
040767409128;99;99;99;;::;;;2561,29
291266430128;99;99;99;;::;;;2550,00
291067406416;99;99;99;;::;;;2550,00
290666400222;99;99;99;;::;;;2550,00
270268413812;99;99;99;;::;;;2550,00
260666415320;99;99;99;;::;;;2550,00
260368421116;99;99;99;;::;;;2550,00
140367412262;99;99;99;;::;;;2550,00
250168405219;99;99;99;;::;;;2550,00
271066413923;99;99;99;;::;;;2570,00
231267426820;99;99;99;;::;;;2550,00
240168408955;99;99;99;;::;;;2550,00
210766400024;99;99;99;;::;;;2550,00
200667409219;99;99;99;;::;;;2550,00
190367430271;99;99;99;;::;;;2550,00
161267400654;99;99;99;;::;;;2550,00
160667406815;99;99;99;;::;;;2550,00
151167425070;99;99;99;;::;;;2550,00
060167426213;99;99;99;;::;;;2475,00
250766400119;99;99;99;;::;;;2550,00
020168419617;99;99;99;;::;;;2595,00
080371428222;99;99;99;;::;;;2040,00
130367412271;99;99;99;;::;;;2595,00
121167414227;99;99;99;;::;;;2595,00
120867411014;99;99;99;;::;;;2595,00
120367403237;99;99;99;;::;;;2595,00
110368404312;99;99;99;;::;;;2595,00
091267404638;99;99;99;;::;;;2595,00
091067413417;99;99;99;;::;;;2595,00
080666419729;99;99;99;;::;;;2595,00
201126404612;99;99;99;;::;;;2562,50
021267406410;99;99;99;;::;;;2595,00
081266415125;99;99;99;;::;;;2570,00
011267413611;99;99;99;;::;;;2595,00
231165409536;99;99;99;;::;;;2592,00
030567430142;99;99;99;;::;;;2592,00
280664421813;99;99;99;;::;;;2585,00
200763430085;99;99;99;;::;;;2585,00
120761402718;99;99;99;;::;;;2585,00
050228430074;99;99;99;;::;;;2580,00
010667400217;99;99;99;;::;;;2575,00
130367400836;99;99;99;;::;;;2550,00
061166426814;99;99;99;;::;;;2595,00
010667406117;99;99;99;;::;;;2515,65
050966406156;99;99;99;;::;;;2541,00
040367428346;99;99;99;;::;;;2541,00
300867408518;99;99;99;;::;;;2525,00
250967402719;99;99;99;;::;;;2525,00
201066400627;99;99;99;;::;;;2525,00
140367430153;99;99;99;;::;;;2525,00
061167420924;99;99;99;;::;;;2525,00
271267407060;99;99;99;;::;;;2520,00
140866400856;99;99;99;;::;;;2550,00
061169414827;99;99;99;;::;;;2520,00
061266406132;99;99;99;;::;;;2541,00
281269401331;99;99;99;;::;;;2506,93
280368410036;99;99;99;;::;;;2500,00
020563421338;99;99;99;;::;;;2500,00
250864522822;99;99;99;;::;;;2489,41
060467409116;99;99;99;;::;;;2475,00
060666414858;99;99;99;;::;;;2475,00
060665404834;99;99;99;;::;;;2475,00
060766408922;99;99;99;;::;;;2475,00
060266417515;99;99;99;;::;;;2475,00
091067422735;99;99;99;;::;;;2520,00
230767405247;99;99;99;;::;;;2541,00
120368421226;99;99;99;;::;;;2550,00
090667400113;99;99;99;;::;;;2550,00
071266401517;99;99;99;;::;;;2550,00
070667421725;99;99;99;;::;;;2550,00
061266409122;99;99;99;;::;;;2550,00
050566400759;99;99;99;;::;;;2550,00
020867413222;99;99;99;;::;;;2550,00
011166422746;99;99;99;;::;;;2550,00
210532530168;99;99;99;;::;;;2547,10
060268406422;99;99;99;;::;;;2541,00
281067425095;99;99;99;;::;;;2541,00
061266405113;99;99;99;;::;;;2541,00
211264406199;99;99;99;;::;;;2541,00
211067406157;99;99;99;;::;;;2541,00
200467423817;99;99;99;;::;;;2541,00
130967418319;99;99;99;;::;;;2541,00
101167405218;99;99;99;;::;;;2541,00
100867405038;99;99;99;;::;;;2541,00
091167406142;99;99;99;;::;;;2541,00
081066406144;99;99;99;;::;;;2541,00
021167413410;99;99;99;;::;;;2475,00
291167425032;99;99;99;;::;;;2541,00
210966423618;99;99;99;;::;;;2475,00
210667420521;99;99;99;;::;;;2475,00
260666420226;99;99;99;;::;;;2475,00
210567408912;99;99;99;;::;;;2475,00
260667424923;99;99;99;;::;;;2475,00
210867423911;99;99;99;;::;;;2475,00
260766415395;99;99;99;;::;;;2475,00
210967413411;99;99;99;;::;;;2475,00
260667407920;99;99;99;;::;;;2475,00
211267424317;99;99;99;;::;;;2475,00
260567421733;99;99;99;;::;;;2475,00
260566410610;99;99;99;;::;;;2475,00
260567417419;99;99;99;;::;;;2475,00
210867402117;99;99;99;;::;;;2475,00
260567421725;99;99;99;;::;;;2475,00
220167422116;99;99;99;;::;;;2475,00
260867411529;99;99;99;;::;;;2475,00
220167424947;99;99;99;;::;;;2475,00
261066410512;99;99;99;;::;;;2475,00
220267409234;99;99;99;;::;;;2475,00
200667408929;99;99;99;;::;;;2475,00
211067421816;99;99;99;;::;;;2475,00
201166405927;99;99;99;;::;;;2475,00
030268417781;99;99;99;;::;;;2475,00
200967408525;99;99;99;;::;;;2475,00
260167414411;99;99;99;;::;;;2475,00
200967422060;99;99;99;;::;;;2475,00
260368412236;99;99;99;;::;;;2475,00
200767424010;99;99;99;;::;;;2475,00
260168430325;99;99;99;;::;;;2475,00
201065416010;99;99;99;;::;;;2475,00
260268407026;99;99;99;;::;;;2475,00
260666400110;99;99;99;;::;;;2475,00
260268419318;99;99;99;;::;;;2475,00
210168418136;99;99;99;;::;;;2475,00
260367430053;99;99;99;;::;;;2475,00
201067402210;99;99;99;;::;;;2475,00
260168400513;99;99;99;;::;;;2475,00
210367424926;99;99;99;;::;;;2475,00
260366400717;99;99;99;;::;;;2475,00
210368424717;99;99;99;;::;;;2475,00
260766407635;99;99;99;;::;;;2475,00
210267403124;99;99;99;;::;;;2475,00
260967420545;99;99;99;;::;;;2475,00
201266422812;99;99;99;;::;;;2475,00
270467424434;99;99;99;;::;;;2475,00
270368414310;99;99;99;;::;;;2475,00
230268400812;99;99;99;;::;;;2475,00
270367424920;99;99;99;;::;;;2475,00
230368410110;99;99;99;;::;;;2475,00
270367406714;99;99;99;;::;;;2475,00
230367420210;99;99;99;;::;;;2475,00
270368419621;99;99;99;;::;;;2475,00
230267429234;99;99;99;;::;;;2475,00
261065405519;99;99;99;;::;;;2475,00
230567428241;99;99;99;;::;;;2475,00
221267408527;99;99;99;;::;;;2475,00
230866424515;99;99;99;;::;;;2475,00
270667406724;99;99;99;;::;;;2475,00
231066427122;99;99;99;;::;;;2475,00
270567420238;99;99;99;;::;;;2475,00
230767429222;99;99;99;;::;;;2475,00
270767428111;99;99;99;;::;;;2475,00
230865416214;99;99;99;;::;;;2475,00
270567417135;99;99;99;;::;;;2475,00
231067428303;99;99;99;;::;;;2475,00
270268407420;99;99;99;;::;;;2475,00
261166420216;99;99;99;;::;;;2475,00
211167422023;99;99;99;;::;;;2475,00
261266417129;99;99;99;;::;;;2475,00
220467415401;99;99;99;;::;;;2475,00
261167411215;99;99;99;;::;;;2475,00
220368411018;99;99;99;;::;;;2475,00
261167411928;99;99;99;;::;;;2475,00
220567424997;99;99;99;;::;;;2475,00
270167416918;99;99;99;;::;;;2475,00
220567413622;99;99;99;;::;;;2475,00
221167426613;99;99;99;;::;;;2475,00
220567415126;99;99;99;;::;;;2475,00
270367413738;99;99;99;;::;;;2475,00
220767417521;99;99;99;;::;;;2475,00
270167413020;99;99;99;;::;;;2475,00
220967415360;99;99;99;;::;;;2475,00
261267424953;99;99;99;;::;;;2475,00
220967421517;99;99;99;;::;;;2475,00
270267416923;99;99;99;;::;;;2475,00
221166407322;99;99;99;;::;;;2475,00
270367422773;99;99;99;;::;;;2475,00
251266404820;99;99;99;;::;;;2475,00
261267415395;99;99;99;;::;;;2475,00
010866403226;99;99;99;;::;;;2475,00
011167403627;99;99;99;;::;;;2475,00
010867409814;99;99;99;;::;;;2475,00
011167422035;99;99;99;;::;;;2475,00
010967416720;99;99;99;;::;;;2475,00
010767428911;99;99;99;;::;;;2475,00
010966414838;99;99;99;;::;;;2475,00
010767414835;99;99;99;;::;;;2475,00
010667415021;99;99;99;;::;;;2475,00
171267418917;99;99;99;;::;;;2475,00
020866421538;99;99;99;;::;;;2475,00
011066403214;99;99;99;;::;;;2475,00
010766400829;99;99;99;;::;;;2475,00
010967414610;99;99;99;;::;;;2475,00
010766405718;99;99;99;;::;;;2475,00
010567406814;99;99;99;;::;;;2475,00
010666419717;99;99;99;;::;;;2475,00
010867405223;99;99;99;;::;;;2475,00
161166419911;99;99;99;;::;;;2475,00
161267413017;99;99;99;;::;;;2475,00
251167413414;99;99;99;;::;;;2475,00
011067416439;99;99;99;;::;;;2475,00
010367405243;99;99;99;;::;;;2475,00
020767426210;99;99;99;;::;;;2475,00
020565422828;99;99;99;;::;;;2475,00
010467408513;99;99;99;;::;;;2475,00
010467426711;99;99;99;;::;;;2475,00
020667425042;99;99;99;;::;;;2475,00
010468429260;99;99;99;;::;;;2475,00
020867424028;99;99;99;;::;;;2475,00
010368427436;99;99;99;;::;;;2475,00
020367405031;99;99;99;;::;;;2475,00
010766407529;99;99;99;;::;;;2475,00
011166400619;99;99;99;;::;;;2475,00
020268413933;99;99;99;;::;;;2475,00
011167415396;99;99;99;;::;;;2475,00
010168411237;99;99;99;;::;;;2475,00
011167422772;99;99;99;;::;;;2475,00
010268422427;99;99;99;;::;;;2475,00
011066430079;99;99;99;;::;;;2475,00
020667414714;99;99;99;;::;;;2475,00
060567417113;99;99;99;;::;;;2475,00
020267403418;99;99;99;;::;;;2475,00
250267420035;99;99;99;;::;;;2475,00
010367409818;99;99;99;;::;;;2475,00
250966417775;99;99;99;;::;;;2475,00
250867413736;99;99;99;;::;;;2475,00
190567426314;99;99;99;;::;;;2475,00
250866409225;99;99;99;;::;;;2475,00
190368430265;99;99;99;;::;;;2475,00
250866400634;99;99;99;;::;;;2475,00
190767417711;99;99;99;;::;;;2475,00
250867428217;99;99;99;;::;;;2475,00
190667414417;99;99;99;;::;;;2475,00
250167404513;99;99;99;;::;;;2475,00
190767402325;99;99;99;;::;;;2475,00
181166407628;99;99;99;;::;;;2475,00
190966413828;99;99;99;;::;;;2475,00
251166417114;99;99;99;;::;;;2475,00
190967428263;99;99;99;;::;;;2475,00
251167413270;99;99;99;;::;;;2475,00
200167417749;99;99;99;;::;;;2475,00
251067407017;99;99;99;;::;;;2475,00
200266418317;99;99;99;;::;;;2475,00
251160415118;99;99;99;;::;;;2475,00
200467417142;99;99;99;;::;;;2475,00
250766424815;99;99;99;;::;;;2475,00
250368422443;99;99;99;;::;;;2475,00
171266408215;99;99;99;;::;;;2475,00
250467404013;99;99;99;;::;;;2475,00
180366407441;99;99;99;;::;;;2475,00
250567420221;99;99;99;;::;;;2475,00
180167415334;99;99;99;;::;;;2475,00
250566414428;99;99;99;;::;;;2475,00
180767424728;99;99;99;;::;;;2475,00
250467402739;99;99;99;;::;;;2475,00
180666426644;99;99;99;;::;;;2475,00
181165419619;99;99;99;;::;;;2475,00
180767426715;99;99;99;;::;;;2475,00
250767422774;99;99;99;;::;;;2475,00
180966428019;99;99;99;;::;;;2475,00
250367400517;99;99;99;;::;;;2475,00
181066400613;99;99;99;;::;;;2475,00
250767428228;99;99;99;;::;;;2475,00
181167427612;99;99;99;;::;;;2475,00
250866419036;99;99;99;;::;;;2475,00
181266416214;99;99;99;;::;;;2475,00
250767414328;99;99;99;;::;;;2475,00
150767408931;99;99;99;;::;;;2595,00
250368420528;99;99;99;;::;;;2475,00
250167408549;99;99;99;;::;;;2775,00
251267409519;99;99;99;;::;;;2775,00
050567416920;99;99;99;;::;;;2775,00
180368430100;99;99;99;;::;;;2775,00
040966430229;99;99;99;;::;;;2775,00
121267405627;99;99;99;;::;;;2775,00
030468409313;99;99;99;;::;;;2775,00
110867418428;99;99;99;;::;;;2775,00
030667428306;99;99;99;;::;;;2775,00
100467401812;99;99;99;;::;;;2762,67
270767413745;99;99;99;;::;;;2775,00
080967408513;99;99;99;;::;;;2775,00
141067413428;99;99;99;;::;;;2775,00
130368427619;99;99;99;;::;;;2775,00
110967410511;99;99;99;;::;;;2775,00
080568423636;99;99;99;;::;;;2773,33
310168405018;99;99;99;;::;;;2772,00
191066406125;99;99;99;;::;;;2772,00
150167405921;99;99;99;;::;;;2772,00
050367406138;99;99;99;;::;;;2772,00
160467415434;99;99;99;;::;;;2850,00
090666420219;99;99;99;;::;;;2775,00
180165405319;99;99;99;;::;;;2805,00
161266430018;99;99;99;;::;;;2700,00
290566423822;99;99;99;;::;;;2835,00
200467413723;99;99;99;;::;;;2835,00
051065413927;99;99;99;;::;;;2835,00
060267419328;99;99;99;;::;;;2825,00
130370407510;99;99;99;;::;;;2824,19
251252408812;99;99;99;;::;;;2820,00
260967426824;99;99;99;;::;;;2820,00
260367407443;99;99;99;;::;;;2820,00
060967412215;99;99;99;;::;;;2775,00
301160427226;99;99;99;;::;;;2805,00
270667413246;99;99;99;;::;;;2775,00
111262430226;99;99;99;;::;;;2805,00
070160417348;99;99;99;;::;;;2805,00
020260407440;99;99;99;;::;;;2805,00
201066400619;99;99;99;;::;;;2800,00
200967418715;99;99;99;;::;;;2795,00
291067422432;99;99;99;;::;;;2775,00
090466400731;99;99;99;;::;;;2775,00
300667407123;99;99;99;;::;;;2775,00
050537515397;99;99;99;;::;;;2760,01
180567416010;99;99;99;;::;;;2820,00
180967430030;99;99;99;;::;;;2700,00
200567403119;99;99;99;;::;;;2700,00
200667407934;99;99;99;;::;;;2700,00
Diese Liste beinhaltet die Namen von 90.598 Mitarbeitern des Ministeriums für Staatssicherheit der DDR. Die Liste ist nicht vollständig. Insbesondere Mitarbeiter der Führungsebene sind nicht enthalten.
This is a list of 90.598 members of the secret police of East Germany (Ministry for State Security), the list isn’t complete, because the most of the high Officiers lieke Colonel and higher have destroyed the personal Informations in the last days of Eastern Germany.
| Listen der Stasimitarbeiter-hier findest Du sie! Was bedeuten die Zahlen? |
| 1.Listen der Stasi-Diensteinheiten! Bem.:hier kannst du die Nr.(6-stellig) der Dienststellen heraussuchen. 2.Liste der Stasi-Mitarbeiter (Hauptamtlich) Bem.:Hoffentlich hast Du einen guten Rechner, denn die Liste ist erschreckend lang. Die ersten 6 Ziffern sind das Geburtsdatum + die nächsten 6 Ziffern = Dienstausweisnummer! Die zwei Ziffern hinter dem Geburtsdatum geben das Geschlecht an: 41 und 42 = Männlich, 51 und 52 = Weiblich! Wichtig für suchen und finden, sind die sechs Ziffern in den Semikolon vor den Namen: z.B. ;07;00;44; ! Das ist die Nummer der Dienststelle ! Also du suchst in der Liste der Dienststellen, die Nummer der Dienststelle, die Dich interessiert. Damit gehst Du in die Liste der Mitarbeiter und suchst Dir alle Mitarbeiter der entsprechenden Dienststelle heraus. Ich habe das für mein Wohnort getan und so alle Mitarbeiter gefunden. Ob die Liste Vollständig ist kann ich nicht einschätzen, aber zumindest er/kannte ich einige Exverräter vom Namen her. 3.Liste der OibE (Offiziere im besonderen Einsatz) |
CONFIDENTIAL – Amazon Location Tracking and Future Destination Prediction Patent
![]()
This patent was submitted by Amazon on December 6, 2011. It describes a method of tracking individuals through mobile phone GPS location data and then using the information to predict future shopping destinations to present more specifically targeted advertising.
Mobile device users may be tracked either via mobile-signal triangulation or via Global Positioning Satellite information. A mobile device user’s recent movements may be analyzed to determine trails or traffic patterns for device user among various locations. Mobile device trail information, either for an individual user or aggregated for multiple users, may be analyzed to determine a next destination for the user. Electronic advertising content, such as advertisements, coupons and/or other communications, associated with the next destination may be sent to an electronic device likely to be viewed by the mobile device user. Additionally, the identity of the mobile device user may be known and the advertisements or coupons may be tailored according to demographic information regarding the mobile device user. In addition, destinations may be recommended to mobile device users based on the recent locations the users have visited.
![]()
SUMMARY
The movements of mobile device users may be detected, recorded, tracked and analyzed in order to direct advertising content to the mobile device users based on the users’ predicted destinations. For example, location dependent advertising content may be provided to mobile device users based on a current and/or predicted location that the mobile device user is likely to visit. In some embodiments, mobile device users’ current and past travel patterns may be analyzed to determine a predicted next destination. For instance, by analyzing the recent movements of a mobile device user among stores in a shopping mall, it may be determined that a particular store is a predicted next destination for the mobile device user. Thus, advertising content for the predicted destination, such as coupons, may be sent to the mobile device user.
In some embodiments, a mobile device user’s travel or traffic patterns (e.g., a set of locations and the order in which those location are visited) may be analyzed to predict a next likely location or destination. Various types of advertising content, such as electronic coupons, and other advertisements may be directed to the mobile device user based on the predicted destination. For example, a mobile device user may be tracked as she shops at various stores in a shopping mall. Based on the stores she has recently visited, a traffic pattern analysis system may determine a next most likely store or other destination that the mobile device user may visit. The system may then send advertisements, coupons, or other commercial communication to the user’s mobile device or to another electronic display device, such as to offer a discount or other shopping benefit to the mobile device user if she visits the predicted destination.
For instance, in one embodiment, a mobile device user may be tracked as she visits several of the clothing stores in a shopping mall. Based on the type and location of the stores visited, the system may determine that she is likely to visit another clothing store in another part of the shopping mall. In response to determining a store that the mobile device user is likely to visit, the system may send advertising content, such as an electronic coupon good for 10% off any purchases made at the store that day, to the mobile device user. Thus, the mobile device user may be more likely to visit the store because of the added enticement of the discount.
DOWNLOAD THE DOCUMENT HERE
INSIDER – Congress Approves Insider Threat Detection Program to Combat Leakers

Congress ordered the Secretary of Defense to establish an information security program for detecting “unauthorized access to, use of, or transmission of classified or controlled unclassified information.” The provision was included by the FY2012 defense authorization act that was approved in conference this week (section 922).
The insider threat detection program, conceived as a response to WikiLeaks, is intended to “allow for centralized monitoring and detection of unauthorized activities.” Among other things, it is supposed to employ technology solutions “to prevent the unauthorized export of information from a network or to render such information unusable in the event of the unauthorized export of such information.”
H.R. 1540, NATIONAL DEFENSE AUTHORIZATION ACT FOR FISCAL YEAR 2012, SEC. 922. INSIDER THREAT DETECTION (Federation of American Scientists):
(a) Program Required.–The Secretary of Defense shall
establish a program for information sharing protection and
insider threat mitigation for the information systems of the
Department of Defense to detect unauthorized access to, use
of, or transmission of classified or controlled unclassified
information.
(b) Elements.–The program established under subsection (a)
shall include the following:
(1) Technology solutions for deployment within the
Department of Defense that allow for centralized monitoring
and detection of unauthorized activities, including–
(A) monitoring the use of external ports and read and write
capability controls;
(B) disabling the removable media ports of computers
physically or electronically;
(C) electronic auditing and reporting of unusual and
unauthorized user activities;
(D) using data-loss prevention and data-rights management
technology to prevent the unauthorized export of information
from a network or to render such information unusable in the
event of the unauthorized export of such information;
(E) a roles-based access certification system;
(F) cross-domain guards for transfers of information
between different networks; and
(G) patch management for software and security updates.
(2) Policies and procedures to support such program,
including special consideration for policies and procedures
related to international and interagency partners and
activities in support of ongoing operations in areas of
hostilities.
(3) A governance structure and process that integrates
information security and sharing technologies with the
policies and procedures referred to in paragraph (2). Such
structure and process shall include–
(A) coordination with the existing security clearance and
suitability review process;
(B) coordination of existing anomaly detection techniques,
including those used in counterintelligence investigation or
personnel screening activities; and
(C) updating and expediting of the classification review
and marking process.
(4) A continuing analysis of–
(A) gaps in security measures under the program; and
(B) technology, policies, and processes needed to increase
the capability of the program beyond the initially
established full operating capability to address such gaps.
(5) A baseline analysis framework that includes measures of
performance and effectiveness.
(6) A plan for how to ensure related security measures are
put in place for other departments or agencies with access to
Department of Defense networks.
(7) A plan for enforcement to ensure that the program is
being applied and implemented on a uniform and consistent
basis.
(c) Operating Capability.–The Secretary shall ensure the
program established under subsection (a)–
(1) achieves initial operating capability not later than
October 1, 2012; and
(2) achieves full operating capability not later than
October 1, 2013.
(d) Report.–Not later than 90 days after the date of the
enactment of this Act, the Secretary shall submit to the
congressional defense committees a report that includes–
(1) the implementation plan for the program established
under subsection (a);
(2) the resources required to implement the program;
(3) specific efforts to ensure that implementation does not
negatively impact activities in support of ongoing operations
in areas of hostilities;
(4) a definition of the capabilities that will be achieved
at initial operating capability and full operating
capability, respectively; and
(5) a description of any other issues related to such
implementation that the Secretary considers appropriate.
(e) Briefing Requirement.–The Secretary shall provide
briefings to the Committees on Armed Services of the House of
Representatives and the Senate as follows:
(1) Not later than 90 days after the date of the enactment
of this Act, a briefing describing the governance structure
referred to in subsection (b)(3).
(2) Not later than 120 days after the date of the enactment
of this Act, a briefing detailing the inventory and status of
technology solutions deployment referred to in subsection
(b)(1), including an identification of the total number of
host platforms planned for such deployment, the current
number of host platforms that provide appropriate security,
and the funding and timeline for remaining deployment.
(3) Not later than 180 days after the date of the enactment
of this Act, a briefing detailing the policies and procedures
referred to in subsection (b)(2), including an assessment of
the effectiveness of such policies and procedures and an
assessment of the potential impact of such policies and
procedures on information sharing within the Department of
Defense and with interagency and international partners.
(f) Budget Submission.–On the date on which the President
submits to Congress the budget under section 1105 of title
31, United States Code, for each of fiscal years 2014 through
2019, the Secretary of Defense shall submit to the
congressional defense committees an identification of the
resources requested in such budget to carry out the program
established under subsection (a).
STUDY- U.S. Corporate Executives Received a Pay Raise of 27-40% Last Year
Chief executive pay has roared back after two years of stagnation and decline. America’s top bosses enjoyed pay hikes of between 27 and 40% last year, according to the largest survey of US CEO pay. The dramatic bounceback comes as the latest government figures show wages for the majority of Americans are failing to keep up with inflation.
America’s highest paid executive took home more than $145.2m, and as stock prices recovered across the board, the median value of bosses’ profits on stock options rose 70% in 2010, from $950,400 to $1.3m. The news comes against the backdrop of an Occupy Wall Street movement that has focused Washington’s attention on the pay packages of America’s highest paid.
The Guardian’s exclusive first look at the CEO pay survey from corporate governance group GMI Ratings will further fuel debate about America’s widening income gap. The survey, the most extensive in the US, covered 2,647 companies, and offers a comprehensive assessment of all the data now available relating to 2010 pay.
Last year’s survey, covering 2009, found pay rates were broadly flat following a decline in wages the year before. Base salaries in 2009 showed a median increase of around 2%, and annual cash compensation increased just over 1.5%. The troubled stock markets took their toll, and added together CEO pay declined for the third year, though the decrease was marginal, less than three-tenths of a percent. The decline in the wider economy in 2007, 2008 and 2009 far outstripped the decline in CEO pay.
This year’s survey shows CEO pay packages have boomed: the top 10 earners took home more than $770m between them in 2010. As stock prices began to recover last year, the increase in CEO pay outstripped the rise in share value. The Russell 3000 measure of US stock prices was up by 16.93% in 2010, but CEO pay went up by 27.19% overall. For S&P 500 CEOs, the largest companies in the sample, total realised compensation – including perks and pensions and stock awards – increased by a median of 36.47%. Total pay at midcap companies, which are slightly smaller than the top firms, rose 40.2%.
DOWNLOAD ORIGINAL STUDY HERE
A-Z- 2.000 STASI OFFIZIERE IM BESONDEREN EINSATZ OibE – “SCHLÄFERLISTE DER STASI IN WESTDEUTSCHLAND”- STASI-SLEEPER LIST A-Z
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
The list was published earlier here:
http://stasiopfer.de/component/option,com_simpleboard/Itemid,/func,view/id,993815828/catid,4/
A link from the “Stasi Victim” offer leads to a website in the USA (www.jya.com), which also deals with the practices of secret services. There you could find earlier the “Fipro list”, the detailed “financial project” of the Stasi, made in the last days of the GDR in order to be able to prove the pension claims of the approximately 100,000 full-time employees of the MfS even after the collapse of the system. The “Fipro list” has been known for a long time and was used at the beginning of the nineties to identify the so-called OibE officers on special missions. This & nbsp; List “Officers on special operations” appeared in 1991 & nbsp; in the “ taz .
Zimmermann, Bernd; 07.08.39; HVA; 961500; 1080; 458/63, A belongs to the “GoMoPa” camarilla of former Stasi agents.
Continue reading “A-Z- 2.000 STASI OFFIZIERE IM BESONDEREN EINSATZ OibE – “SCHLÄFERLISTE DER STASI IN WESTDEUTSCHLAND”- STASI-SLEEPER LIST A-Z”TOP-SECRET – U.S. Treasury Strategic Direction Fiscal Years 2009-2011

The Intelligence Authorization Act of Fiscal Year 2004 created the Treasury Department’s Office of Intelligence and Analysis (OIA) and made it responsible for the receipt, analysis, collation, and dissemination of intelligence related to the operation and responsibilities of the Treasury Department. OIA was created to support the formulation of policy and the execution of Treasury authorities by providing expert analysis and intelligence production on financial and other support networks for terrorist groups, proliferators, and other key national security threats. In addition, OIA was charged with providing timely, accurate, and focused intelligence on the full range of economic, political, and security issues. On April 28, 2004, the Secretary of the Treasury established the Office of Terrorism and Financial Intelligence (TFI), which includes OIA, the Office of Terrorist Finance and Financial Crimes (TFFC), the Office of Foreign Assets Control (OFAC), the Financial Crimes Enforcement Network (FinCEN), and the Treasury Executive Office for Asset Forfeiture (TEOAF). TFI brings a wide range of intelligence and enforcement authorities together under a single umbrella to strategically target a number of threats. Since its creation in 2004, OIA has accomplished a great deal in the course of meeting ever growing demands from its customers. In its first year of operation, OIA focused on establishing a current intelligence process to meet the day-to-day information needs of decision makers in the Department, while also supporting the intelligence needs of the designation process under EO 13224.
• In 2005, President Bush signed EO 13382 aimed at freezing the assets of proliferators of weapons of mass destruction and their supporters; OIA expanded its analytic efforts in order to support implementation of the EO.
• In 2006, OIA enhanced its strategic analytic capability and began producing allsource intelligence assessments on terrorist finance and rogue state proliferation networks that leveraged Treasury’s unique expertise and perspective.
• In 2007, OIA expanded the breadth and depth of its analytic cadre to meet increased demand from policymakers.
• In 2008, OIA initiated a research program to examine the systemic issues behind the financing of national security threats, such as cash courier networks, informal remittance systems, and terrorist use of the Internet.


ADDRESSING THE GLOBAL FINANCIAL NETWORK:
A COMPREHENSIVE APPROACH TO FINANCIAL
INTELLIGENCE
Building on its accomplishments of the past several years, OIA plans to launch a comprehensive approach to financial intelligence that will allow us to better confront national security challenges by strengthening our understanding of the global financial network. The global financial network encompasses four areas: the financial underpinnings of national security threats, our adversaries’ financial vulnerabilities, the impact of targeted financial measures, and threats to international financial stability.
1. Assess Financial Underpinnings of National Security Threats: Terrorists, WMD proliferators, rogue states, and other nefarious actors require financial resources to support their activities. Without ready access to such resources, these actors are unable to indoctrinate, recruit, and train personnel; buy weapons, technology, and equipment; circulate propaganda; bribe officials; support the global networks of operatives essential to their existence; or launch attacks. The flow of funds to activities that threaten national security may not be shut off completely, but impeding the activities of these networks makes operating costlier, harder, and riskier for these threats.
2. Identify Adversaries’ Financial Vulnerabilities: The US Government is relying more heavily on targeted financial measures aimed at specific actors engaged in illicit conduct, as opposed to broad-based economic sanctions. Targeted financial measures allow decision makers to apply financial pressure and isolate terrorists, proliferators, and others whose goal is to undermine US security. They also allow US leaders to take punitive action against threats without resorting to military force. Applying targeted financial measures effectively, however, requires indepth knowledge of an adversary’s economic or financial well-being: its strengths, weaknesses, connectivity to global markets, and key dependencies.
3. Evaluate the Impact of Targeted Financial Measures: As targeted financial measures become an increasingly important policy tool, measuring their effectiveness is imperative. This area of inquiry involves questions such as: What impact have the measures had on the target’s economy and financial system? How is the target reacting? Are the measures having the desired effect on the target’s behavior? What steps is the target taking to evade or avoid the measures? Moreover, have the measures had any unintended consequences or caused any collateral damage?
4. Monitor Threats to International Financial Stability: The US financial system and the economic well-being of every American are inexorably linked to the health and stability of the international financial system. Globalization and convergence in the world economy only underscore this fact. Identifying threats to the global financial system’s integrity and to sustainable growth and development therefore is essential to America’s own security.
…

DOWNLOAD ORIGINAL DOCUMENT HERE
TOP-SECRET from the Worldbank – Interim Strategy Note for the Republic of Iraq 2009-2011

INTERIM STRATEGY NOTE FOR IRAQ (FY09-FY11)
EXECUTIVE SUMMARY
i. Recent positive developments suggest that Iraq has made important progress towards political and economic stabilization, although the situation remains fragile and reversible. Recent months have seen a sharp decline in incidents of violence, especially in the Baghdad area, and a corresponding decrease in the rate of internal displacement of the population. This reflects improved security as well as successful initial steps towards political reconciliation. Macroeconomic performance has also improved although growth has been volatile.
ii. The Government is signaling its commitment to reform and reconstruction, indicating that continued engagement with Iraq may produce further concrete results. The Government has succeeded in sharply reducing inflation and containing recurrent spending, while increasing capital expenditures to accelerate the recovery process. In addition, the machinery of government is slowly reviving as Iraq emerges from conflict. A more proactive and confident government is likely to devote more attention to the economy. Finally, high oil prices and – to a lesser extent – an increase in production produced an estimated US$70 billion of revenues in 2008, although a deterioration in Iraq’s fiscal balance is expected during part of the ISN period in view of
the recent declining trend in oil prices.
iii. However, results from past and ongoing reform efforts remain far from meeting the needs and expectations of the Iraqi people. Unemployment remains extremely high and access to basic services severely limited. Electricity supply is unreliable and is far exceeded by demand; access to clean water and sanitation is the lowest in the Region. Recent improvements in access to education and health services have not yet translated into significant welfare gains on the part of the people of Iraq.
iv. Iraq is resource rich and has benefited from a substantial increase in oil revenues over the past few years. At the same time, it is still subject to conflict, insecurity, political instability and revenue volatility. These features highlight Iraq’s uniqueness. As a conflict-affected, IBRD-eligible middle-income country, Iraq is clearly not the typical aid-dependent post-conflict country. The main challenge for the country – in addition to security and political stability – is to mobilize and effectively use its own
vast resources to improve the welfare of the Iraqi people and rebuild its infrastructure. The main role for the international community, including the World Bank Group, is therefore to help Iraq use its own resources more effectively.
v. Working in Iraq has been very challenging for the Bank Group and other donors. While some notable successes have been achieved, the effectiveness of assistance has been hampered by issues related to both the country’s operating environment and the approach followed by the donors. Operating environment issues – which also affect the Government’s ability to execute its own investment budget – include: the fragile political and security situation; the unstable policy and institutional environment; the Government’s weakened institutional capacity, and weaknesses in Iraq’s banking system. Issues related to the approach of the Bank to Iraq include the selectivity of assistance as well as business processes and fiduciary arrangements which have been unfamiliar to Iraqi counterparts and are challenging for Ministries with limited capacity.
vi. The design of this third Interim Strategy Note benefited from a stocktaking of the Bank Group’s engagement with Iraq to date. The goal of the stocktaking exercise was to identify the key bottlenecks for the implementation of the previous ISNs and extract lessons for this ISN. This exercise informed the design of this ISN: (i) the continuing centrality of institution building; (ii) the critical importance of interest and engagement on the part of ministries and implementing agencies; (iii) the need for increased selectivity in terms of the ability to identify and seize opportunities as they arise to achieve concrete results; (iv) the need to focus on reform efforts that do not overtax Iraq’s existing capacity and that more clearly reflect the country’s current political and security situation; and (v) the need for increased flexibility in the design and programming of Bank assistance and for experimentation with alternative implementation arrangements for the Bank’s assistance program for Iraq.
vii. The ISN also benefited from extensive consultations with the Government of Iraq, the donor community, and other stakeholders, including representatives from private sector and civil society organizations. These consultations were extremely helpful in identifying the country priorities, defining promising engagement arrangements to maximize Bank assistance results, and highlighting the centrality of donor coordination. Some of the main priority areas identified during the consultations include:
(i) public financial management; (ii) banking sector reform; (iii) support to planning processes and strategy design (not only at the central level, but also at the sectoral and provincial levels); (iv) private sector development; and (v) energy and services.
viii. Given Iraq’s unique characteristic of a well resource endowed Middle Income Country (MIC) with a fragile environment, this ISN is proposed for a longer time horizon than the typical ISN. The time horizon for this ISN is proposed to be from mid-FY09 through FY11, to be updated to a full Country Assistance Strategy if and when circumstances allow. This interim strategy contains lessons and principles of engagement. The work program beyond FY09 would be kept up to date through Annual Business Planning, jointly with the Iraqi Government to ensure it meets the evolving needs of the Government as well as evolving opportunities for engagement.
ix. The central guiding principle of this ISN is that Iraq is well-endowed with natural and financial resources, and that the main role for the World Bank in this context is to help Iraq use its resources more effectively and transparently. This principle impacts both the form and the content of the proposed work program for the next two years. However, it needs to be tempered by recent developments in the global economy and their impact on Iraq’s projected oil revenues for the next few years and its increasing need for external financing in the short-to-medium term. Hence, this ISN anticipates IBRD financial support as requested by the Iraqi authorities.
x. Regarding the form of the assistance, the main instruments of Bank Group support under this ISN include: (i) operational support to accelerate implementation of the current portfolio, totaling about US$1 billion; (ii) advisory services in selected sectors and areas; (iii) IBRD financial support in priority sectors to be selected on the basis of funding needs and implementation capacity; (iv) IFC investment and advisory services products; and (v) MIGA’s political risk guarantee products. Under this ISN, an IBRD envelope of US$500 million can be committed for investments projects over FY09-11. The Bank is currently administering 16 active grants funded from the Iraq Trust Fund, totaling US$471.6 million to provide textbooks, schools, health clinics, improved social safety nets, water supply and sanitation, irrigation and drainage, and a comprehensive household survey. The ongoing IDA portfolio consists of five projects, worth US$508.5 million, in the areas of education, roads, electricity, and water supply. IFC will support PSD through prioritized investments and advisory services in key sectors. The Bank’s Analytical and Advisory Activities (AAA) program will support the Government in its efforts to enhance its ability to effectively use its oil revenues to the benefit of the Iraqi people. Key analytical work undertaken since re-engagement in 2003 includes a study on subnational public financial management (2007), a joint IFC/IBRD Construction Industry study (2008), a Country Economic Memorandum (2006), a pension reform study (2005), a report on Iraq’s Public Distribution System (2005), an investment climate report (2004), and a study on stateowned
enterprise reform (2004). The Government has also expressed interest in borrowing from IBRD as the need arises, increasing IFC support, and getting MIGA guarantees that could leverage private financing. Other instruments include the State and Peace Building Fund, and possibly, Treasury services.
xi. With respect to the content of the assistance, activities under this ISN will fall under at least one of three thematic areas of engagement: (i) continuing to support ongoing reconstruction and socio-economic recovery; (ii) improving governance and the
management of public resources, including human, natural and financial; and (iii) supporting policies and institutions that promote broad-based, private-sector-led growth, with the goal of revitalizing the private sector and facilitating job creation. IFC and MIGA will play a key role particularly (but not exclusively) with respect to the third thematic area. New activities under the ISN will be chosen on the basis of criteria for selectivity reflecting opportunities to achieve concrete results on the ground.
xii. The three thematic areas are closely linked with the key goals of the International Compact with Iraq. The first ISN theme responds to the goals of the International Compact with Iraq (ICI) which are related to Iraq’s reconstruction and recovery efforts, including strengthening the energy sector and developing a stable, competitive and sustainable agriculture. The second ISN theme responds to the ICI goals of improving public financial management as well as strengthening institutions and improving governance. The third ISN theme responds to the ICI goals of implementing economic reform to create an enabling environment for private investments as a driver for broad-based growth.
xiii. To achieve tangible results in a relatively short term, the Bank Group will place a renewed emphasis on how this ISN will be implemented. Building on lessons learned from the implementation of the previous Interim Strategy Notes and the various
consultations held, this ISN will aim to: (a) enhance the effectiveness of instittion building and analytical and advisory activities; (b) strengthen the implementation of the current portfolio; (c) introduce more flexibility in the Bank Group’s programming and ability to experiment with alternative implementation arrangements; and (d) foster donor coordination. For planning purposes, this ISN is based on the assumption that progress in the security situation over the next two to three years would continue to be slow and incremental, with a risk of reversal.
xiv. Risks. There are high risks to the World Bank Group’s program in Iraq. The most important risk pertains to the political and security situation, which remains fragile, as does the country’s operating environment. To mitigate this risk, the strategy emphasizes flexibility, and the Bank will adjust its activities as appropriate. Given the current limitations on mobility within the country, maintaining a vibrant dialogue with counterparts on issues of policy reform as well as implementation, and ensuring adherence to core fiduciary and safeguard requirements will remain challenging. These risks are substantial despite the Bank’s mitigating measures, which include capacity building, local oversight capacity, and prudent financial management procedures.

DOWNLOAD ORIGINAL DOCUMENT HERE
WIE AUCH Sie STASI-“GoMoPa”-Rufmordopfer werden können
FBI – Three Maryland Men Indicted for Alleged Pension Plan Fraud
ALEXANDRIA, VA—Three Maryland men have been indicted for engaging in a scheme to steal nearly $10 million from Vienna-based Southern Management Corporation’s employee pension plan.
Neil H. MacBride, United States Attorney for the Eastern District of Virginia, and James W. McJunkin, Assistant Director in Charge of the FBI’s Washington Field Office, made the announcement.
Robert Fulton Rood IV, 44, of Potomac, Md., Nikolaos M. Hepler, 31, of Gaithersburg, Md., and Lloyd M. Mallory, Jr., 49, of Silver Spring, Md., were charged in a 16-count indictment of conspiracy to commit wire fraud, wire fraud and theft from an employee benefit plan. If convicted, each defendant faces a maximum penalty of 20 years on the conspiracy and each wire fraud count and five years in prison on each theft count.
According to the indictment, Rood conceived and led a scheme to defraud Southern Management Corporation Retirement Trust (“SMCRT”), a pension plan established by SMC for its employees. As of December 31, 2010, the plan’s assets were over $30 million, and prior to April 2006 SMCRT generally managed its own investments, which included short term (one year), high interest loans to real estate developers.
The indictment alleges that in April 2006, Rood persuaded SMC’s President and CEO to let Rood locate borrowers, negotiate loans to them, prepare the loan agreements, promissory notes and trust deeds and present loan application packages to the SMCRT loan committee, which would decide whether to purchase the proposed loans. If the committee decided to do so, it would wire the money to purchase the loan to a settlement company designated by Rood. Rood would use the money from SMCRT to fund the loan and would obtain from the borrower an executed loan agreement, promissory note and trust deed, which he would assign to SMCRT. In most cases, the borrowers were not aware of SMCRT’s involvement in the process.
Rood allegedly represented to both SMCRT and the borrowers that he would set up escrow accounts for the payment of interest to SMCRT and for construction payments to the borrowers. Instead, the indictment alleges that the moneys from all the loans were co-mingled into Rood’s principal bank account. When the project was finished and sold, the borrower was to pay back the amount borrowed to SMCRT.
From April 2006 to around October 2007, Rood allegedly sold to SMCRT approximately 32 mortgage loans that he had originated, of which 24 went into default after they were funded by SMCRT. According to the indictment, one loan, referred to as the “K Street” loan, never closed because the title company was unable to clear title to the property, and Rood is accused of simply keeping the money that SMCRT paid him to purchase the loan. Two other loans referenced in the indictment—the “Eastern Shore” and “Accom” loans—involved SMCRT loans that the borrowers refinanced with different lenders and sent their payoffs to Rood, who allegedly kept the payoff monies. In each case, Rood, assisted by Nikolaos M. Hepler, his employee, is accused of misrepresenting to SMCRT that the loans were in place and performing satisfactorily, including Rood’s making of the monthly interest payments to SMCRT on the nonexistent loans.
The indictment states that SMCRT requested an independent review of Rood’s accounts, and in February 2008, Rood engaged Mallory to perform a review of the loans, loans, disbursements and escrows. The accountant allegedly issued a report which falsely showed the status of the loans and the funds held by Rood.
This case was investigated by FBI’s Washington Field Office. Assistant United States Attorneys Michael E. Rich and Uzo Asonye are prosecuting the case on behalf of the United States.
Criminal indictments are only charges and not evidence of guilt. A defendant is presumed to be innocent until and unless proven guilty.
A copy of this press release may be found on the website of the United States Attorney’s Office for the Eastern District of Virginia at http://www.justice.gov/usao/vae. Related court documents and information may be found on the website of the District Court for the Eastern District of Virginia at http://www.vaed.uscourts.gov or on https://pcl.uscourts.gov.
FAZ über die Wirtschaftskriminellen der “GoMoPa”
TOP-SECRET – (U//FOUO) U.S. Army Guide to Political Groups in Afghanistan

 Political Parties in Afghanistan
Political Parties in Afghanistan
- Most political groupings in Afghanistan are based on alliances that were formed during the military struggles of 1979-2002
- Many have connections with ex-Mujahideen factions
- During the 2005 presidential election, since parties‟ identification was not allowed for candidates, party based coalition could not function in parliament
- In the 2009 presidential election, political parties could support a candidate who was a member
- In Afghanistan, political parties are seen as controversial and are not seen as a potential positive force by the government or the public
- The Political Parties Law of 2003 requires all political parties to be registered with the Ministry of Justice and observe the precepts of Islam
- Some 82 parties have gained such recognition as of the end 2007; but hundreds of political groups claim to be active in the country today, the majority of which have little to no political power
- The government fears that encouraging political parties will fuel civil tensions and contribute to the existing deteriorating security
- The government places emphasis on building national unity and preventing groups from forming in Parliament on the basis of ethnicity, language, region or any other potentially divisive factors1
- For most parties, particularly the new or smaller ones without well known leaders, their information is not known or widely disseminated
- There are numerous reasons why parties formed and are forming but two main raisons stand out:
- New opportunity
- Especially after the fall of the Taliban
- Disputes with current leadership
- Political groups in Afghanistan are very fluid, coalitions, fronts and political alliances form and dissolve quickly
- Allegiances between groups shift according to the convictions of their leaders rather than by ideology
- Individual parties split, reunify and/or rename themselves constantly, leading to confusion in party existence and names
…
Major Pro-government Parties
- Islamic Society of Afghanistan (Hezb-e-Jamihat-e-Islami-e-Afghanistan)
- Afghanistan‟s Islamic Mission Organization (Tanzim Dawat-e-Islami-e-Afghanistan)
- Islamic Unity Party of Afghanistan (Hezb-e-Wahdat-e-Afghanistan)
- National Islamic Front of Afghanistan (Hezb-e-Mahaz-e-Mili Islami-e-Afghanistan)
- Afghanistan National Liberation Front (Hezb-e-Tanzim Jabha Mili Nejat-e Afghanistan)
- Afghan Social Democratic Party (Hezb-e-Afghan Melat)
- National Movement of Afghanistan (Nahzat-e-Mili Afghanistan)
Major Opposition Parties
- The United National Front – UNF (Jabhe-ye-Motahed-e-Mili)
- New Afghanistan (Hezb-e-Afghanistan-e-Naween)
- Hezb-e-Islami Gulbuddin – HiG
- Party of Islam – HiK (Hezb-e-Islami)
- Party of Islamic Unity of The People of Afghanistan (Hezb-e-Wahdat-e Islami Mardom Afghanistan)
- National Movement of Afghanistan (Nahzat-e-Mili Afghanistan)
Other Political Parties
- Revolutionary Association of the Women of Afghanistan (RAWA)
- Rome Group
- Freedom Party of Afghanistan(Hezb-e Azadee-e-Afghanistan)
- The National Understanding Front-NUF (Jabahai Tafahim Millie)
- National Youth Union of Afghanistan (Hezb-e Hambastagi-yi Milli-yi Jawanan-i Afghanistan)
DOWNLOAD ORIGINAL DOCUMENT HERE
Video – Syrian Officers Had Shoot-to-kill Orders
The group Human Rights Watch has named Syrian commanders and officials who it says authorized or ordered the killing or torture of anti-government protesters. HRW put the name of Syrian President Bashar Assad on the list.
TOP-SECRET from the FBI – Lawyer for Preeminent Firms Pleads Guilty in $37 Million Insider Trading Scheme
A corporate lawyer who previously worked at four prominent international law firms admitted today to participating in an insider trading scheme that lasted for 17 years, relied on information he stole from his law firms and their clients, and netted more than $37 million in illicit profits, U.S. Attorney for the District of New Jersey Paul J. Fishman announced.
Matthew Kluger, 50, of Oakton, Va., pleaded guilty to all four counts charged in the information against him: conspiracy to commit securities fraud, securities fraud, conspiracy to commit money laundering and obstruction of justice. Kluger entered his guilty plea before U.S. District Judge Katharine S. Hayden in Newark federal court.
“Not only did Matthew Kluger defraud the investing public, he betrayed the colleagues and clients who depended on his confidentiality in some of the biggest deals of the last decade,” said U.S. Attorney Fishman. “In order to be confident in our markets, investors must have comfort that those with inside information won’t abuse positions of trust for personal gain.”
“In this time of economic uncertainty, securities fraud remains a top investigative priority for the FBI,” said Michael B. Ward, special agent in charge of the Newark Division of the FBI. “Millions of investors have entrusted their life savings to the integrity of the financial markets and the belief of a level playing field. Insider trading, such as the conduct attributable to Matthew Kluger, corrupts the process and tilts the playing field in favor of those privileged few with access to information not available to the public, and at the expense of unsuspecting and unknowing investors.”
According to documents filed in this case and statements made in court:
Kluger and two co-conspirators—Garrett D. Bauer, 44, of New York, and Kenneth Robinson, 45, of Long Beach, N.Y.,—engaged in an insider trading scheme that began in 1994. Kluger admitted that he passed inside information to Bauer and Robinson that the men used to trade ahead of more than 30 different corporate transactions.
During the scheme, Kluger worked at four of the nation’s premier mergers and acquisitions law firms. From 1994 to 1997, he worked first as a summer associate and later as a corporate associate at Cravath Swaine & Moore in New York. From 1998 to 2001, he worked at Skadden, Arps, Slate, Meagher & Flom in New York and Palo Alto, Calif., as an associate in their corporate department. From 2001 to 2002, Kluger worked as a corporate associate at Fried, Frank, Harris, Shriver & Jacobson LLP in New York. From Dec. 5, 2005, to March 11, 2011, Kluger worked at Wilson Sonsini Goodrich & Rosati as a senior associate in the mergers & acquisitions department of the firm’s Washington, D.C., office.
While at the firms, Kluger regularly stole and disclosed to Robinson material, nonpublic information regarding anticipated corporate mergers and acquisitions on which his firms were working. Early in the scheme, Kluger disclosed information relating to deals on which he personally worked. As the scheme developed, and in an effort to avoid law enforcement detection, Kluger took information which he found primarily by viewing documents on his firms’ computer systems.
Kluger admitted that once he provided the inside information to Robinson, Robinson passed it to Bauer. Bauer then purchased shares for himself, Kluger and Robinson in Bauer’s trading accounts, then sold them once the relevant deal was publicly announced and the stock price rose. Bauer gave Robinson and Kluger their shares of the illicit profits in cash—often tens or hundreds of thousands of dollars per deal—that Bauer withdrew in multiple transactions from ATM machines.
The three conspirators took greater efforts to prevent detection of their insider trading scheme after Kluger joined Wilson Sonsini. Among other techniques, they used pay phones and prepaid cellular phones that they referred to as “throwaway phones” to discuss the scheme.
Kluger also admitted that, after Robinson told him that the FBI and (Internal Revenue Service) had searched Robinson’s house and had asked questions about the illicit scheme, Kluger destroyed multiple pieces of evidence, including an iPhone and a computer. Kluger also instructed Robinson to destroy a prepaid phone.
As part of his guilty plea, Kluger agreed to forfeit $415,000, which is the approximate amount that he obtained from recent transactions in the scheme.
The maximum potential penalties Kluger faces per count are as follows:
| Count | Charge | Maximum Potential Penalty |
|---|---|---|
| 1 | Conspiracy to commit securities fraud | Five years in prison; $250,000 fine, or twice the aggregate loss to victims or gain to the defendants |
| 2 | Securities fraud | 20 years in prison; $5 million fine |
| 3 | Conspiracy to commit money laundering | 20 years in prison; $500,000 fine, or twice the value of the property involved in the transaction |
| 4 | Obstruction of justice | 20 years in prison; $500,000 fine |
Judge Hayden scheduled Kluger’s sentencing for April 9, 2012.
Bauer and Robinson have both pleaded guilty in connection with the scheme. Bauer is scheduled to be sentenced on March 13, 2011. Robinson is scheduled to be sentenced on March 6, 2012.
U.S. Attorney Fishman credited special agents of the FBI, under the direction of Special Agent in Charge Ward in Newark, for the investigation. He also thanked special agents of the IRS, under the direction of Special Agent in Charge Victor W. Lessoff, and the U.S. Securities and Exchange Commission’s Market Abuse Unit and Philadelphia Regional Office, under the direction of Daniel M. Hawke.
The government is represented by Assistant U.S. Attorneys Matthew E. Beck of the U.S. Attorney’s Office Economic Crimes Unit; Judith H. Germano, Chief of the Economic Crimes Unit; and Lakshmi Srinivasan Herman of the office’s Asset Forfeiture Unit in Newark.
This case was brought in coordination with President Barack Obama’s Financial Fraud Enforcement Task Force. President Obama established the interagency Financial Fraud Enforcement Task Force to wage an aggressive, coordinated, and proactive effort to investigate and prosecute financial crimes. The task force includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general, and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch, and with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes.
CONFIDENTIAL – DARPA Wants to Make $500 Million Space-Based Spy Telescope
 A visualization of the MOIRE system provided by DARPA.
A visualization of the MOIRE system provided by DARPA.
| If the U.S. military wants live video of a missile launcher vehicle halfway around the world, it must rely on spy planes or drones in danger of being shot down. Tomorrow, the Pentagon wants space telescopes hovering in geosynchronous orbit that could take real-time images or live video of any spot on Earth.Contrary to Hollywood’s ideas, today’s spy satellites that orbit the Earth at fast speeds and relatively lower altitudes can only snap photos for the U.S. military and intelligence agencies. Taking live video of a single location would require satellites to hover by matching the Earth’s rotation in geosynchronous orbit about 22,000 miles (36,000 kilometers) high — but creating and launching a space telescope with the huge optics arrays capable of seeing ground details from such high orbit has proven difficult.
As a solution, DARPA — the Pentagon’s research arm — envisions a lightweight optics array made of flexible membrane that could deploy in space. Ball Aerospace has just completed an early proof-of-concept review as part of a DARPA contract worth almost $37 million. “The use of membrane optics is an unprecedented approach to building large aperture telescopes,” said David Taylor, president and chief executive officer of Ball Aerospace in Boulder, Colo. DARPA eventually wants a space telescope with a collection aperture (light-collecting power) of almost 66 feet (20 meters) in diameter. By comparison, NASA’s next-generation James Webb Space Telescope is designed to have an aperture of 21 feet (6.5 m). Such a telescope should be able to spot missile launcher vehicles moving at speeds of up to 60 mph on the ground, according to the DARPA contract. That would also require the image resolution to see objects less than 10 feet (3 m) long within a single image pixel. But first, Ball Aerospace must create and test a 16-foot (5 m) telescope in the DARPA project’s second phase. Phase three would involve launching a 32-foot (10 m) telescope for flight tests in orbit. |
Watching for Scuds from Space:
MOIRE is intended to demonstrate technology for persistent, tactical, full-motion video surveillance from geosynchronous orbit. After delivery to GEO, the satellite would unfurl a micron-thin diffractive-optics membrane, to form a massive segmented lens.
With a target cost of less than $500 million a copy, the objective space telescope would have a 20-meter-dia. lens. It would be able to image an area greater than 100 x 100 km with a video update rate of at least one frame a second, providing a 99% chance of detecting a Scud-class missile launch.
Membrane Optical Imager for Real-Time Exploitation:
To meet national security requirements around the world, it would be optimal to have real-time images and video of any place on earth at any time—a capability that doesn’t currently exist. Today, aircraft are used for some imagery requirements. Because of the huge quantity of aircraft needed, and because aircraft do not fly high enough to see into denied territories, spacecraft are also used for imagery requirements.
Spacecraft, however, face different challenges in providing persistent coverage. The size (aperture) of the optics needed, and the limitations of producing and launching extremely large precision glass optics means it is infeasible to place such a system in geosynchronous earth orbit (GEO), approximately 36,000 kilometers high, where it could provide persistent coverage.MOIRE is a GEO-based system that uses a lightweight membrane optic etched with a diffractive pattern. The diffractive pattern is used to focus light on a sensor. The MOIRE program seeks to enable the technologies required for these very large optics for space platforms. The program aims to demonstrate the manufacturability of large membranes (up to 20 meters), large structures to hold the optics flat, and also demonstrate the secondary optical elements needed to turn a diffraction-based optic into a wide bandwidth imaging device.
The MOIRE program began in March 2010 and encompasses multiple phases: Phase 1 (proof of concept), Phase 2 (system design) and an option for a Phase 3 (system demonstration). The program is currently in Phase 1 and plans to transition to Phase 2 in Fall 2011.
New – Congress Authorizes Offensive Military Action in Cyberspace
Congress has given the U.S. military a green light to conduct offensive military activities in cyberspace.
“Congress affirms that the Department of Defense has the capability, and upon direction by the President may conduct offensive operations in cyberspace to defend our Nation, allies and interests,” said the FY 2012 defense authorization act that was adopted in conference this week (section 954).
The blanket authorization for offensive cyber operations is conditional on compliance with the law of armed conflict, and the War Powers Resolution, which mandated congressional consultation in decisions to go to war.
“The conferees recognize that because of the evolving nature of cyber warfare, there is a lack of historical precedent for what constitutes traditional military activities in relation to cyber operations and that it is necessary to affirm that such operations may be conducted pursuant to the same policy, principles, and legal regimes that pertain to kinetic capabilities,” the conference report on the defense authorization act said.
“The conferees also recognize that in certain instances, the most effective way to deal with threats and protect U.S. and coalition forces is to undertake offensive military cyber activities, including where the role of the United States Government is not apparent or to be acknowledged.”
“The conferees stress that, as with any use of force, the War Powers Resolution may apply.”
This is an odd formulation which suggests that the War Powers Resolution may also not apply. In any case, the Resolution is a weak reed that has rarely been used by Congress to constrain executive action.
According to the Congressional Research Service, “Debate continues on whether using the War Powers Resolution is effective as a means of assuring congressional participation in decisions that might get the United States involved in a significant military conflict.”
Proven – The Bloody History of Communism
Communism was the bloodiest ideology that caused more than 120 million innocent deaths in the 20th century. It was a nightmare which promised equality and justice, but which brought only bloodshed, death, torture and fear. This three-volume documentary displays the terrible savagery of communism and its underlying philosophy. From Marx to Lenin, Stalin, Mao or Pol Pot, discover how the materialist philosophy transforms humans into theorists of violence and masters of cruelty.
UNCENSORED News from FEMEN
Желание украинцев узнать источники их финансирования. Система оптимизации поиска Google.ua на запрос “кто финансирует” выделяет топ-тройку деятелей, чьи источники финансирования хотели бы знать украинцы. Топ-3 запроса “кто финансирует» выглядит следующим образом: первое место – FEMEN, второе – Гитлер, третье – Яценюк. Абсолютно не понятно, как малобюджетная женская организация затесалась в компанию таких финансовых монстров, как национал-социалистическая рабочая партия фюрера и Фронт Змiн Яценюка). Парадоксально, но людей больше интересует, где FEMEN берет деньги на краски и ватманы, чем источники финансирования солдат Вермахта и школьников Яценюка.
А вот москалей интересуют масоны проплачивающие футбол и развал России.
Ein Statement für den Gesamt-Markt: ETHIK BANK: “GoMoPa” IST TABU
TOP-SECRET-FBI-Eight Former Senior Executives and Agents of Siemens Charged in Alleged $100 Million Foreign Bribe Scheme
WASHINGTON—Eight former executives and agents of Siemens AG and its subsidiaries have been charged for allegedly engaging in a decade-long scheme to bribe senior Argentine government officials to secure, implement and enforce a $1 billion contract with the Argentine government to produce national identity cards, announced Assistant Attorney General Lanny A. Breuer of the Justice Department’s Criminal Division, U.S. Attorney Preet Bharara for the Southern District of New York and Ronald T. Hosko, Special Agent in Charge of the FBI, Washington Field Office’s Criminal Division.
The defendants charged in the indictment returned late yesterday are:
- Uriel Sharef, a former member of the central executive committee of Siemens AG;
- Herbert Steffen, a former chief executive officer of Siemens Argentina;
- Andres Truppel, a former chief financial officer of Siemens Argentina;
- Ulrich Bock, Stephan Signer, and Eberhard Reichert, former senior executives of Siemens Business Services (SBS); and
- Carlos Sergi and Miguel Czysch, who served as intermediaries and agents of Siemens in the bribe scheme.
The indictment charges the defendants and their co-conspirators with conspiracy to violate the Foreign Corrupt Practices Act (FCPA) and the wire fraud statute, money laundering conspiracy and wire fraud.
“Today’s indictment alleges a shocking level of deception and corruption,” said Assistant Attorney General Breuer. “The indictment charges Siemens executives, along with agents and conduits for the company, with committing to pay more than $100 million in bribes to high-level Argentine officials to win a $1 billion contract. Business should be won or lost on the merits of a company’s products and services, not the amount of bribes paid to government officials. This indictment reflects our commitment to holding individuals, as well as companies, accountable for violations of the FCPA.”
“As alleged, the defendants in this case bribed Argentine government officials in two successive administrations and paid off countless others in a successful effort to secure a billion dollar contract,” said U.S. Attorney Bharara. “When the project was terminated, they even sought to recover the profits they would have reaped from a contract that was awarded to them illegitimately in the first place. Bribery corrupts economic markets and creates an unfair playing field for law-abiding companies. It is critical that we hold individuals as well as corporations accountable for such corruption as we are doing today.”
“Backroom deals and corrupt payments to foreign officials to obtain business wear away public confidence in our global marketplace,” said FBI Special Agent in Charge Hosko of the Washington Field Office’s Criminal Division. “The investigation into this decades-long scheme serves as an example that the FBI is committed to curbing corruption and will investigate those who try to advance their businesses through foreign bribery.”
According to the indictment, the government of Argentina issued a tender for bids in 1994 to replace an existing system of manually created national identity booklets with state of the art national identity cards (the DNI project). The value of the DNI project was $1 billion. In 1998, the Argentine government awarded the DNI project to a special-purpose subsidiary of Siemens AG.
The indictment alleges that during the bidding and implementation phases of the project, the defendants and their co-conspirators caused Siemens to commit to paying nearly $100 million in bribes to sitting officials of the Argentine government, members of the opposition party and candidates for office who were likely to come to power during the performance of the project. According to the indictment, members of the conspiracy worked to conceal the illicit payments through various means. For instance, Bock made cash withdrawals from Siemens AG general-purpose accounts in Germany totaling approximately $10 million, transported the cash across the border into Switzerland and deposited the funds into Swiss bank accounts for transfer to officials. Bock, Truppel, Reichert, and other conspirators also allegedly caused Siemens to wire transfer more than $7 million in bribes to a bank account in New York disguised as a foreign exchange hedging contract relating to the DNI project. Over the duration of the conspiracy, the conspirators allegedly relied on at least 17 off-shore shell companies associated with Sergi, Czysch and other intermediaries to disguise and launder the funds, often documenting the payments through fake consulting contracts.
In May 1999, according to the indictment, the Argentine government suspended the DNI project, due in part to instability in the local economy and an impending presidential election. When a new government took power in Argentina, and in the hopes of getting the DNI project resumed, members of the conspiracy allegedly committed Siemens to paying additional bribes to the incoming officials and to satisfying existing obligations to officials of the outgoing administration, many of whom remained in influential positions within the government.
When the project was terminated in May 2001, members of the conspiracy allegedly responded with a multi-faceted strategy to overcome the termination. According to the indictment, the conspirators sought to recover the anticipated proceeds of the DNI project, notwithstanding the termination, by causing Siemens AG to file a fraudulent arbitration claim against the Republic of Argentina in Washington, D.C. The claim alleged wrongful termination of the contract for the DNI project and demanded nearly $500 million in lost profits and expenses. Members of the conspiracy allegedly caused Siemens to actively hide from the tribunal the fact that the contract for the DNI project had been secured by means of bribery and corruption, including tampered witness statements and pleadings that falsely denied the existence of corruption.
In related actions, the indictment also alleges that members of the conspiracy continued the bribe scheme, in part to prevent disclosure of the bribery in the arbitration and to ensure Siemens’ ability to secure future government contracts in Argentina and elsewhere in the region. In four installments between 2002 and 2007, members of the conspiracy allegedly caused Siemens to pay approximately $28 million in further satisfaction of the obligations. Conspirators continued to conceal these additional payments through various means. For example, Sharef, Truppel and other members of the conspiracy allegedly caused Siemens to transfer approximately $9.5 million through fictitious transactions involving a Siemens business division that had no role in the DNI project. They also caused Siemens to pay an additional $8.8 million in 2007 under the legal cover of a separate arbitration initiated in Switzerland by the intermediaries to enforce a sham $27 million contract from 2001 between SBS and Mfast Consulting, a company controlled by their co-conspirator intermediaries, which consolidated existing bribe commitments into one contract. The conspirators caused Siemens to quietly settle the arbitration, keeping all evidence of corruption out of the proceeding. The settlement agreement included a provision preventing Sergi, Czysch and another intermediary from testifying in, or providing information to, the Washington arbitration.
Siemens’s corrupt procurement of the DNI project was not exposed during the lifespan of the conspiracy, and, in February 2007, the arbitral tribunal in Washington sided with Siemens AG, awarding the company nearly $220 million on its DNI claims, plus interest. On Aug. 12, 2009, following Siemens’ corporate resolutions with the U.S. and German authorities—new management of Siemens caused Siemens AG to forego its right to receive the award and, as a result, the company never claimed the award money.
The indictment charges the defendants with conspiracy to violate the anti-bribery, books and records and internal control provisions of the FCPA; conspiracy to commit wire fraud; conspiracy to commit money laundering; and substantive wire fraud.
The charges announced today follow the Dec. 15, 2008, guilty pleas by Siemens AG and its subsidiary, Siemens S.A. (Siemens Argentina), to criminal violations of the FCPA. As part of the plea agreement, Siemens AG and Siemens Argentina agreed to pay fines of $448.5 million and $500,000, respectively.
In a parallel civil action, the Securities and Exchange Commission (SEC) announced charges against executives and agents of Siemens. The department acknowledges and expresses its appreciation of the significant assistance provided by the staff of the SEC during the course of these parallel investigations.
Today’s charges follow, in large part, the laudable actions of Siemens AG and its audit committee in disclosing potential FCPA violations to the department after the Munich Public Prosecutor’s Office initiated an investigation. Siemens AG and its subsidiaries disclosed these violations after initiating an internal FCPA investigation of unprecedented scope; shared the results of that investigation; cooperated extensively and authentically with the department in its ongoing investigation; and took remedial action, including the complete restructuring of Siemens AG and the implementation of a sophisticated compliance program and organization.
The department and the SEC closely collaborated with the Munich Public Prosecutor’s Office in bringing this case. The high level of cooperation, including sharing information and evidence, was made possible by the use of mutual legal assistance provisions of the 1997 Organization for Economic Cooperation and Development Convention on Combating Bribery of Foreign Public Officials in International Business Transactions.
The case is being prosecuted by Principal Deputy Chief Jeffrey H. Knox of the Criminal Division’s Fraud Section, and by Assistant U.S. Attorneys Jason P. Hernandez and Sarah McCallum of the U.S. Attorney’s Office for the Southern District of New York. The Fraud Section of the Justice Department’s Criminal Division and the Complex Frauds Unit of the U.S. Attorney’s Office for the Southern District of New York are handling the case. The case was investigated by FBI agents who are part of the Washington Field Office’s dedicated FCPA squad. The Criminal Division’s Office of International Affairs provided significant assistance in this matter.
Secret – USAF Operating Next-Generation Remotely Piloted Aircraft for Irregular Warfarehttp://publicintelligence.net/wp-content/uploads/2011/12/USAF-RemoteIrregularWarfare.png

The United States Air Force has long envisioned a strategic role for remotely piloted and autonomous aircraft. As early as May 1896, Samuel Pierpont Langley developed an unpiloted heavier-than-air vehicle which flew over the Potomac River. On V-J Day in August 1945, General Hap Arnold, US Army Air Forces, observed:
“We have just won a war with a lot of heroes flying around in planes. The next war may be fought by airplanes with no men in them at all … Take everything you’ve learned about aviation in war, throw it out of the window, and let’s go to work on tomorrow’s aviation. It will be different from anything the world has ever seen.”
Since these early days, extended range, persistence, precision, and stealth have characterized remotely piloted aircraft (RPA) advancements. RPAs have been employed in multiple combat roles and increasingly contested environments. This year, for the first time in history, the President’s budget proposed a larger investment in RPAs than manned aircraft. A seemingly insatiable operational appetite for RPAs, however, has led to an Air Force manning bottleneck. This is exacerbated by a lack of common ground stations, unsatisfactory integration with civilian and international airspace, and vulnerabilities in communications and command and control links. Further complicating efforts, yet essential in irregular warfare, are directives to minimize civilian casualties. General David Petraeus sees this need as a direct way to support a key center of gravity:
“…We must fight the insurgents, and will use the tools at our disposal to both defeat the enemy and protect our forces. But we will not win based on the number of Taliban we kill, but instead on our ability to separate insurgents from the center of gravity – the people …”
Our Panel conducted an extensive set of visits and received numerous briefings from a wide range of key stakeholders in government, industry, and academia. Taking a human-centered, evidence-based approach, our study seeks to address operational challenges as well as point to new opportunities for future RPAs. That RPAs will be a foundational element of the Air Force’s force structure is no longer debatable. The real question is how to maximize their current and future potential. Our intention is that this study will help provide both vector and thrust in how to do so in the irregular warfare context, as well as other applications.
…
RPAs are revolutionary surveillance and weapons delivery systems – changing the way the Air Force builds situation awareness and engages enemy forces – but their full potential has yet to be realized. To begin to address this issue, the Air Force initiated this study to review the state-of-the-art in RPA operations, focusing on control and connectivity in an irregular warfare (IW) environment. The Panel was specifically tasked to identify RPA architectures and operational concepts centered on human-systems integration, distributed systems operations, and effective command and control – a cluster of concepts and technologies we subsequently labeled as “mission management” enablers. The Panel was also tasked to recommend mid- to far-term S&T development roadmaps for advancing these technologies to improve the flexibility and capability of RPA operations. The study terms of reference (TOR) identified a number of core issues which were further articulated by the Study Panel to include:
1. Issue #1: Manning and personnel shortfalls are concerns in RPA deployment. Exploiters represent the largest manning dependency (39 percent), exacerbated by expected significant exploiter growth from new sensor suites (e.g., ARGUS-IS, Gorgon Stare). Current sensors (e.g., Constant Hawk and Angel Fire) and expected sensors (e.g., ARGUS-IS) produce data at rates of 10 to over 1000 times projected communications data transmission capacities, and will far exceed human analytic capacity.
2. Issue #2: Manually intensive airspace management and integration requiring exclusion zones and Certificates of Authorization (COAs) make inefficient use of national and international airspace, will not scale to accommodate future RPA growth, hampers manned/unmanned integration, and presents special challenges for small RPAs.
3. Issue #3: Minimizing collateral damage (CD) and fratricide is not a requirement unique to RPA strike operations. For manned and unmanned platforms, the lack of positive ID (PID) and tactical patience are the most significant causes of civilian casualties (CIVCAS) in current conflicts (8 percent CIVCAS compared with 66 percent caused by insurgents). Persistence; up-close access; highresolution intelligence, surveillance, and reconnaissance (ISR); improved situation awareness; and improved mission management will permit RPAs to minimize CD/fratricide. Small-focused lethality munitions and non-lethal options
for RPAs promise to further minimize CD and CIVCAS (e.g., as low as 5 percent).4. Issue #4: In spite of current low RPA losses, inexpensive physical threats (e.g., MANPADS, low-end SAMs, air-to-air missiles) and electronic threats (e.g., acoustic detectors, low cost acquisition radars, jammers) threaten future operations.
…
2.3 Issue (3): Minimizing Collateral Damage/Fratricide
A third issue identified by the Study Panel was collateral damage/fratricide (Figure 2-8). RPAs, originally developed for ISR operations, have become important weapons platforms for tactical and special strike missions in IW. Their expanded use in CAS missions in the future requires technology improvements for mission management to minimize fratricide, collateral damage (CD), and civilian casualties (CIVCAS).
In IW, success requires winning the “hearts and minds” of the population in the face of an adaptable and agile adversary hiding amongst them. A missile fired (e.g. Hellfire missile) from a RPA is no different from a Hellfire missile fired from other platforms like the AH-64 Apache. Causing collateral damage is not an issue unique to RPAs. Data obtained from the Afghanistan AOR17 confirms that insurgents have caused approximately two thirds of CIVCAS. The exact number of CIVCAS caused by US forces was not reported, but an estimate from available data suggests the figure to be less than 10 percent. Of these CIVCAS, approximately half were caused by air-to-ground munitions, but the role of RPAs in these CIVCAS was also not reported. In the majority of these CIVCAS, inadequate acquisition and maintenance of positive target
identification (PID) was the primary cause, and the ability to provide tactical patience during operations would have improved mission success and minimized CIVCAS. In an article by the Washington Post, it was reported that within a recent 15-month period, the CIA conducted 70 RPA strikes using the low collateral damage focused lethality Scorpion weapon, killing 400 terrorists and insurgents while causing 20 CIVCAS. This CIVCAS figure was based on the use of RPAs to conduct pre-strike ISR and post-strike battle damage assessments. Because of precision targeting and focused lethality, CIVCAS is now primarily dependent on the human intelligence and situation awareness upon which the targeting decision is based.…
3.3.4 Encryption and Potential C2 Link Vulnerabilities
Historically, sensor/data downlinks for some RPAs have not been encrypted or obfuscated. Unencrypted sensor data (e.g., FMV) is beneficial because the downlink is used to feed ROVER systems used by Joint Terminal Attack Controllers (JTAC) and other ground personnel, including uncleared coalition members and contractors. This is a life-saving capability. Nevertheless, not protecting against interception of sensor data has been criticized. “Fixing” this security issue by mandating NSA Type 1 encryption is likely to lead to an unacceptable key management burden because of the large number of users of RPA data that have a wide variety of access rights. However, commercial-grade, NSA-approved cryptography is available (“Suite B”). Commercial cryptography of this kind does not require the same degree of rigor in handling key material and encryption devices, and is not limited in operation to cleared personnel. There is relevant Department of Defense (DOD) activity in this general area.
Encryption has generally been used on C2 messages because the risks associated with compromise are higher (loss of the vehicle), and there is a greatly reduced need for sharing of the C2 data as compared with sensor data. However, crypto issues will likely be exacerbated when doing coalition/joint swarming across platforms that require shared C2 across security domains – a capability that is desired to fully exploit the potential of networked RPA operations.
DOWNLOAD ORIGINAL DOCUMENT HERE
CONFIDENTIAL – British Police Testing Non-Lethal Laser Rifle That Temporarily Blinds Rioters
 A rendering of the SMU 100 from a Photonic Security Systems brochure.
A rendering of the SMU 100 from a Photonic Security Systems brochure.
A shoulder-mounted laser that emits a blinding wall of light capable of repelling rioters is to be trialled by police under preparations to prevent a repeat of this summer’s looting and arson.
The technology, developed by a former Royal Marine commando, temporarily impairs the vision of anyone who looks towards the source.It has impressed a division of the Home Office which is testing a new range of devices because of the growing number of violent situations facing the police.
The developer, British-based Photonic Security Systems, hopes to offer the device to shipping companies to deter pirates. Similar devices have been used by ISAF troops in Afghanistan to protect convoys from insurgents.
The laser, resembling a rifle and known as an SMU 100, can dazzle and incapacitate targets up to 500m away with a wall of light up to three metres squared. It costs £25,000 and has an infrared scope to spot looters in poor visibility.
Looking at the intense beam causes a short-lived effect similar to staring at the sun, forcing the target to turn away.
…
A Home Office spokesman said scientists at its Centre for Applied Science and Technology believe the use of lasers “has merit” and that it will be piloted by at least one police force. However, they will have to be satisfied the technology does not cause long-term health damage before it can be approved by the Home Secretary.
Other technology being studied includes ‘wireless electronic interceptors’ that can be fired a greater distance than Tasers, and long-range chemical irritant projectiles.
The STASI role model – Cheka and NKVD Marxist holocaust
Uploaded by Perseiden2 on Nov 17, 2009
“Let the enemies of the working class remember that any person who is arrested with a gun in his hands, without the corresponding permission and identification, is subject to immediate execution, and any person who dares to talk against Soviet power will be immediately arrested and put in a concentration camp. The members of the bourgeoise must feel the heavy hand of the working class. All capitalist robbers, marauders, and speculators will be sent to compulsory public works, their property will be confiscated, and persons involved in counter-revolutionary plots will be destroyed and smashed by the heavy hammer of the revolutionary proletariat.”
~Vice Chairman Peters of the Cheka.
TOP-SECRET – (U//FOUO/LES) Los Angeles Fusion Center: Methods to Defeat Law Enforcement Crowd Control

(U//FOUO//LES) The purpose of this bulletin is officer awareness. Officers should know that instigators involved in violent demonstrations might be familiar with, and might try to apply, techniques from the “Crowd Control and Riot Manual.” The handbook, from Warrior Publications teaches protestors how to defeat law enforcement crowd control techniques. Although it does not address specific groups or organizations, the information is widely applicable.
…
(U) Anti-Crowd Control Measures
(U) The handbook addresses methods used by police to control crowds and countermeasures to defeat them. Figure 1, from the chapter Riot Training, illustrates police protective gear, and then identifies its potential vulnerabilities. The chapter goes on to recommend effective weapons for rioters to carry, offers tactical guidelines, and suggests ways to counter tactical operations by police:
• (U) While an officer’s uniform contains fire retardant material, it may still be set on fire if fuel lands upon it
• (U) Although specialized gear provides protection against projectile and baton strikes, it can limit mobility on hot days; constant running and maneuvering with this gear may cause intense
• (U) Lightly equipped riot police may be vulnerable to projectile and baton strikes
• (U) Patrol vehicles may be damaged with projectiles, destroyed with Molotov cocktails, blinded with paint bombs or disabled with cut/punctured tires; these tactics are also effective against armored vehicles
• (U) Barricades (including those made with burning tires) may be used to limit vision and mobility
• (U) When encountering small arms open fire, return fire may be the best counter • (U) The best response to a baton charge is a heavy barrage of projectiles and the use of barricades
• (U) If an arrest squad (also called a “snatch squad”) is identified, they should be targeted with a heavy barrage of projectiles when they exit police lines
• (U) The use of individual riot weapons is important; primary targets are commanders, ARWEN gunners, snatch squads and K-9 units, as none of these typically carry shields (see
Figure 2)
• (U) Against riot police, the 3’ long Hambo (also known as a long baton) is a preferred weapon to break through Plexiglas shields and visors: metal pipes or aluminum baseball bats are also good, as they have solid impact against riot armor
• (U) Pepper/bear spray is good against police not wearing gas masks, as well as vigilante citizens
• (U) Slingshots are useful against both vehicles and police; when used against people, they should be aimed at the face
• (U) Improvised paint bombs (condoms, empty eggs, spray paint cans) are effective when thrown at masks, visors or shields
• (U) Additional effective projectiles include concrete/bricks, flares, fireworks, bottles and rocks
• (U) Projectiles should be thrown from the front of a crowd to avoid injuring cohorts
• (U) In order to escape arrest, team members should practice and rehearse holds, locks, strikes and escaping from holds and locks; individuals should fight back and attempt escape
• (U) Ambushes can be laid for police if the opportunity arises; assailants can hide behind a corner, vehicle, in a building entrance, roof-top, overhanging bridge, etc.
DOWNLOAD ORIGINAL DOCUMENT HERE
Zyklon B – Das Mittel für den Massenmord – Dokumentation
Die Dokumentation zeigt die erste Hinrichtung eines Menschen durch Giftgas, wie das Zyklon B an Menschen und Tieren getestet – und schließlich gegen die Juden eingesetzt wurde.Mit dem vom Frankfurter IG-Farben-Konzern produzierten Granulat Zyklon B ermordeten die Nazis unzählige Menschen.Getestet wurde die verheerende Wirkung von Zyklon B bereits 1941 an Kriegsgefangenen.Die streng geheimen Informationen über die Giftgasproduktion in Deutschland wurden schon früh an die Amerikaner verraten.
Am 3. September 1941 führte die SS im Konzentrationslager Auschwitz ein streng geheimes Experiment durch, das den Beginn des Holocaust markierte.Mehrere Hundert Kriegsgefangene wurden mit Zyklon B ermordet, einem Granulat, das hochgiftige Blausäure freisetzt.Wenige Wochen später übergab der Repräsentant des deutschen IG-Farben-Konzerns in der Schweiz in seiner Villa am Vierwaldstätter See amerikanischen Kurieren streng geheime Dokumente über Hitlers Giftgasproduktion, auch über das von den IG Farben produzierte Zyklon B.Gelangten auf diesem Wege schon früh Informationen über die geplante sogenannte “Endlösung der Judenfrage” in die USA?
In den USA war Blausäure schon 1924 zur Exekution von Menschen eingesetzt worden. Damals starb im Staatsgefängnis von Nevada erstmals ein Straftäter durch das Giftgas.In den 30er Jahren forschte das amerikanische Chemieunternehmen Du Pont über Blausäure als Insektenkiller, aber auch als Mittel der Wahl für Hinrichtungen in der Gaskammer.Du Pont stand dabei in engem Informationsaustausch mit den Experten des IG-Farben-Konzerns in Frankfurt. Diese Beziehungen blieben sogar bestehen, nachdem Amerika im Dezember 1941 in den Krieg gegen Hitler-Deutschland eingetreten war.Der deutsche Wirtschaftsberater Erwin Respondek, der erst an den Kartellvereinbarungen zwischen IG Farben und Du Pont beteiligt war, dann zum Spion wurde versorgte die Amerikaner mit Geheimnissen über Hitlers Giftgasproduktion.
TOP-SECRET – (U//FOUO) U.S. Army Intelligence Officer’s Handbook


OVERVIEW
1-1. The intelligence warfighting function is one of six warfighting functions. A warfighting function is a group of tasks and systems (people, organizations, information, and processes) united by a common purpose that commanders use to accomplish missions and training objectives (FM 3-0).
1-2. The intelligence warfighting function is the related tasks and systems that facilitate understanding of the operational environment. It includes tasks associated with intelligence, surveillance, and reconnaissance operations and is driven by the commander (FM 3-0). Intelligence is more than just collection; it is a continuous process that involves analyzing information from all sources and conducting operations to develop the situation. The intelligence warfighting function includes the following tasks:
• Support to force generation.
• Support to situational understanding.
• Conduct intelligence, surveillance, and reconnaissance (ISR).
• Provide intelligence support to targeting and information superiority.
…
INTELLIGENCE CATEGORIES
1-6. As discussed in FM 2-0, Army unit intelligence staffs produce and receive, directly or indirectly, six categories of intelligence support from the U.S. intelligence community. Intelligence categories are distinguishable primarily by their intelligence product purposes. The categories can overlap and the same intelligence can be used in each category. Intelligence organizations use specialized procedures to develop these categories. The following information describes each category and the responsible organization:
• Indications and warning (I&W). Analysis of time-sensitive information that could involve a threat to U.S. and multinational military forces, U.S. political or economic interests, or to U.S. citizens. While the G-2/S-2 produces I&W intelligence, every Soldier, such as the one conducting a presence patrol, contributes to the I&W through awareness of the CCIRs and by reporting related information.
• Current intelligence. The G-2/S-2 produces accurate reporting on the current threat situation— which becomes a portion of the common operational picture (COP)—projects the threat’s anticipated situation and the implication to friendly operations.
• General military intelligence (GMI). GMI focuses on the military capabilities of foreign countries, organizations, or on topics relating to Armed Forces capabilities, including threat characteristics (previously order of battle factors) and area or terrain intelligence. The G-2/S-2 develops initial intelligence preparation of the battlefield (IPB) products from various GMI databases, and then develops and maintains the unit’s GMI database on potential threat forces and areas of concern based on the commander’s guidance. This database supports the unit’s plan, preparation, execution, and assessment of operations.
• Target intelligence. The analysis of threat units, dispositions, facilities, and systems to identify and nominate specific assets or vulnerabilities for attack, reattack, or exploit.
• Scientific and technical intelligence (S&TI). The collection, evaluation, and interpretation of foreign engineering science and technology with warfare potential, including military systems, weapons, weapons systems, materiel, research and development, and production methods. The G-2/S-2 establishes instructions in standing operating procedures (SOPs), orders, and plans for handling and evacuating captured enemy material for S&TI exploitation.
• Counterintelligence (CI). Identifying and recommending countermeasures against threats by foreign intelligence services and the ISR activities of nonstate entities, such as organized crime, terrorist groups, and drug traffickers.
INTELLIGENCE DISCIPLINES
1-7. Intelligence disciplines are categories of intelligence functions. There are nine major intelligence disciplines:
• All-source intelligence.
• CI.
• Human intelligence (HUMINT).
• Geospatial intelligence (GEOINT).
• Imagery intelligence (IMINT).
• Measurement and signature intelligence (MASINT).
• Open-source intelligence (OSINT).
• Signals intelligence (SIGINT).
• Technical intelligence (TECHINT).

DOWNLOAD ORGINAL DOCUMENT HERE
…
UNCENSORED – Women Protest Worldwide Photos 9
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict71.jpg) Russian nationalists rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko) Russian nationalists rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict74.jpg) Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky) Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict62.jpg) A woman wearing fake horns holds a banner during a demonstration against bullfighting in Mexico City December 10, 2011. More than hundred demonstrators took part in a protest against bullfighting in the country. Bullfighting has been one of the most popular sport in Mexico for the last 400 years, according to local media. The banner reads “Torture”. Reuters A woman wearing fake horns holds a banner during a demonstration against bullfighting in Mexico City December 10, 2011. More than hundred demonstrators took part in a protest against bullfighting in the country. Bullfighting has been one of the most popular sport in Mexico for the last 400 years, according to local media. The banner reads “Torture”. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict59.jpg) French Occupy protesters participate in a rally as part of the 63rd anniversary of the Universal Declaration of the Human Rights, on December 10, 2011 in center Paris. The activists, angered by state spending cuts that hurt ordinary people and high unemployment have called for a nationwide protest. Placard reads : ‘Time for Outrage. Getty French Occupy protesters participate in a rally as part of the 63rd anniversary of the Universal Declaration of the Human Rights, on December 10, 2011 in center Paris. The activists, angered by state spending cuts that hurt ordinary people and high unemployment have called for a nationwide protest. Placard reads : ‘Time for Outrage. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict58.jpg) Women dressed in violet clothes march from El Zocalo Square to the Revolution monument along Juarez Avenue on December 10, 2011 in Mexico City to protest against violence The activity called ‘The Rally of the One Thousand Women’ promotes to put an end to the discrimination and violence against women. Getty Women dressed in violet clothes march from El Zocalo Square to the Revolution monument along Juarez Avenue on December 10, 2011 in Mexico City to protest against violence The activity called ‘The Rally of the One Thousand Women’ promotes to put an end to the discrimination and violence against women. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict61.jpg) Member of the Association of Parents of Disappeared Persons (APDP) hold portraits of missing relatives during a demonstration to mark International Human Rights Day in Srinagar on December 10, 2011. Demonstrations were held in Srinagar to protest against alleged human rights violations by Indian security forces on Kashmiris. Rights groups say as many as 8,000 people, mostly young men, have ‘disappeared’ by security forces in India-administered Kashmir since an armed insurgency erupted in the Muslim-majority region. Getty Member of the Association of Parents of Disappeared Persons (APDP) hold portraits of missing relatives during a demonstration to mark International Human Rights Day in Srinagar on December 10, 2011. Demonstrations were held in Srinagar to protest against alleged human rights violations by Indian security forces on Kashmiris. Rights groups say as many as 8,000 people, mostly young men, have ‘disappeared’ by security forces in India-administered Kashmir since an armed insurgency erupted in the Muslim-majority region. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict55.jpg) In this photo taken with a fisheye lens protesters gather during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky) In this photo taken with a fisheye lens protesters gather during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict52.jpg) An elderly demonstrator holds a poster showing an edited photo of Prime Minister Vladimir Putin and signed “2050. No” during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. An elderly demonstrator holds a poster showing an edited photo of Prime Minister Vladimir Putin and signed “2050. No” during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict53.jpg) Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel) Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict54.jpg) Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel) Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict56.jpg) Protesters light flares during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin) Protesters light flares during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin)
|
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict22.jpg) A supporter of Ivory Coast Prime Minister and leader of news forces the former rebel groupe looks on during a legislative election meeting in Ferkessedougou, north of Ivory Coast, on December 9, 2011. The December 11 polls are boycotted by former Ivorian President Laurent Gbagbo’s Ivorian Popular Front party (FPI) and its allies in protest against his arrest and transfer to the International Criminal Court in The Hague. Nearly 1,000 candidates are in the fray for the 255 parliamentary seats. Getty A supporter of Ivory Coast Prime Minister and leader of news forces the former rebel groupe looks on during a legislative election meeting in Ferkessedougou, north of Ivory Coast, on December 9, 2011. The December 11 polls are boycotted by former Ivorian President Laurent Gbagbo’s Ivorian Popular Front party (FPI) and its allies in protest against his arrest and transfer to the International Criminal Court in The Hague. Nearly 1,000 candidates are in the fray for the 255 parliamentary seats. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict20.jpg) People protest in the halls of the venue of UN Climate Talks on December 9, 2011, to demand that nations not sign a “death sentence” during the UN Framework Convention on Climate Change (UNFCCC) in Durban. Standing side-by-side with delegates from some of the world’s most vulnerable countries, civil society representatives sang traditional South African freedom songs and chanted slogans like, “Listen to the People, Not the Polluters. In the last 48 hours, over 700,000 people have signed petitions calling on major emitters to stand with the nations of Africa and resist any attempts to delay climate action until 2020. UN climate talks entered their second week entangled in a thick mesh of issues with no guarantee that negotiators and their ministers will be able to sort them out. The 194-nation process is facing, for the second time in two years, the prospect of a bustup, even as scientists warn against the mounting threat of disaster-provoking storms, droughts, flood and rising seas made worse by global warming. Getty People protest in the halls of the venue of UN Climate Talks on December 9, 2011, to demand that nations not sign a “death sentence” during the UN Framework Convention on Climate Change (UNFCCC) in Durban. Standing side-by-side with delegates from some of the world’s most vulnerable countries, civil society representatives sang traditional South African freedom songs and chanted slogans like, “Listen to the People, Not the Polluters. In the last 48 hours, over 700,000 people have signed petitions calling on major emitters to stand with the nations of Africa and resist any attempts to delay climate action until 2020. UN climate talks entered their second week entangled in a thick mesh of issues with no guarantee that negotiators and their ministers will be able to sort them out. The 194-nation process is facing, for the second time in two years, the prospect of a bustup, even as scientists warn against the mounting threat of disaster-provoking storms, droughts, flood and rising seas made worse by global warming. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict19.jpg) Journalists demonstrate during a protest against the murders of their counterparts outside the Presidential house in Tegucigalpa December 9, 2011. 17 journalists have been shot dead in Honduras since 2010, making the small Central American nation one of the world’s most dangerous places for reporters, according human rights groups. Reuters Journalists demonstrate during a protest against the murders of their counterparts outside the Presidential house in Tegucigalpa December 9, 2011. 17 journalists have been shot dead in Honduras since 2010, making the small Central American nation one of the world’s most dangerous places for reporters, according human rights groups. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict18.jpg) Bahraini women watch as hundreds of anti-government protesters (unseen) run Friday, Dec. 9, 2011, through the Musalla area of Manama, Bahrain, toward an area that had been the hub of Bahrain’s spring uprising and is now a heavily militarized zone that protesters seek to reclaim. The protesters were forced back by riot police just short of the area. Writing on the wall reads “freedom” above pictures of political prisoners. (Hasan Jamali) Bahraini women watch as hundreds of anti-government protesters (unseen) run Friday, Dec. 9, 2011, through the Musalla area of Manama, Bahrain, toward an area that had been the hub of Bahrain’s spring uprising and is now a heavily militarized zone that protesters seek to reclaim. The protesters were forced back by riot police just short of the area. Writing on the wall reads “freedom” above pictures of political prisoners. (Hasan Jamali) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict17.jpg) Russian opposition leader Sergei Udaltsov’s wife Anastasia, left, speaks to the media as environmental activist and leader of the Khimki forest defenders Yevgenia Chirikova looks at her during a news conference in Moscow, Russia, Friday Dec. 9, 2011. Energized activists and anxious authorities are bracing for anti-government protests planned across Russia’s sprawling expanse Saturday that promise to be the largest demonstration of public outrage since the dying days of the Soviet Union. Russian opposition leader Sergei Udaltsov’s wife Anastasia, left, speaks to the media as environmental activist and leader of the Khimki forest defenders Yevgenia Chirikova looks at her during a news conference in Moscow, Russia, Friday Dec. 9, 2011. Energized activists and anxious authorities are bracing for anti-government protests planned across Russia’s sprawling expanse Saturday that promise to be the largest demonstration of public outrage since the dying days of the Soviet Union. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict7.jpg) Occupy Boston Protestors reacted to the announcement that their downtown encampment would not be evicted on December 9, 2011, in Boston, Massachusetts. Boston Mayor Thomas M. Menino set a midnight deadline for Occupy Boston protestors to leave their downtown encampment in Dudley Square, or face eviction. In response, many of the protestors chose to take down their tents, and by the midnight deadline much of the camp was gone. At approximately 1:15AM on December 9, 2011, the Boston police announced that they would not evict the protestors from Dudley Square. Protestors took to the street in celebration, and further protest. Getty Occupy Boston Protestors reacted to the announcement that their downtown encampment would not be evicted on December 9, 2011, in Boston, Massachusetts. Boston Mayor Thomas M. Menino set a midnight deadline for Occupy Boston protestors to leave their downtown encampment in Dudley Square, or face eviction. In response, many of the protestors chose to take down their tents, and by the midnight deadline much of the camp was gone. At approximately 1:15AM on December 9, 2011, the Boston police announced that they would not evict the protestors from Dudley Square. Protestors took to the street in celebration, and further protest. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict9.jpg) Worker Pat Revell pickets outside Unilever’s Port Sunlight factory on the Wirral, Merseyside on December 9, 2011 in Port Sunlight, England. The workers are on strike in protest against the company’s plan to axe their final salary pension scheme. The strike is the first in the history of the consumer goods manufacturer who lists PG Tips tea and Persil washing detergent amongst its products. Getty Worker Pat Revell pickets outside Unilever’s Port Sunlight factory on the Wirral, Merseyside on December 9, 2011 in Port Sunlight, England. The workers are on strike in protest against the company’s plan to axe their final salary pension scheme. The strike is the first in the history of the consumer goods manufacturer who lists PG Tips tea and Persil washing detergent amongst its products. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict8.jpg) Supporters of the Serbian Radical Party stand in front of policemen while holding posters with a picture of party leader Vojislav Seselj during a protest against Serbia’s efforts to become an official candidate for the European Union membership in front of Serbia’s Presidency building in Belgrade December 9, 2011. The posters read, “We don’t want in the European Union” (L), and “Tadic don’t humiliate Serbs”. Reuters Supporters of the Serbian Radical Party stand in front of policemen while holding posters with a picture of party leader Vojislav Seselj during a protest against Serbia’s efforts to become an official candidate for the European Union membership in front of Serbia’s Presidency building in Belgrade December 9, 2011. The posters read, “We don’t want in the European Union” (L), and “Tadic don’t humiliate Serbs”. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict6.jpg) People sit as others lay on the ground as they watch a movie in the main entrance of Germans Trias i Pujol hospital during a protest against spending cuts in Catalonia’s public healthcare system, in Badalona, near Barcelona city, Spain, Friday Dec. 9, 2011. The leaders of the 17 countries that use the euro, plus six others, have tentatively agreed to a new treaty that enforces stricter budget rules seen as crucial to solving Europe’s debt crisis and holding the currency-bloc together. An agreement on fiscal discipline is considered a critical first step before the European Central Bank, the International Monetary Fund and others would commit more financial aid to help countries like Italy and Spain, which have large debts and unsustainable borrowing costs. AP People sit as others lay on the ground as they watch a movie in the main entrance of Germans Trias i Pujol hospital during a protest against spending cuts in Catalonia’s public healthcare system, in Badalona, near Barcelona city, Spain, Friday Dec. 9, 2011. The leaders of the 17 countries that use the euro, plus six others, have tentatively agreed to a new treaty that enforces stricter budget rules seen as crucial to solving Europe’s debt crisis and holding the currency-bloc together. An agreement on fiscal discipline is considered a critical first step before the European Central Bank, the International Monetary Fund and others would commit more financial aid to help countries like Italy and Spain, which have large debts and unsustainable borrowing costs. AP |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict5.jpg) Members of the Red Shirt movement joke with a Thai police officer as they gather to protest against former Thai Prime Minister Abhisit Vejjajiva outside Metropolitan Police headquarters in Bangkok, Thailand Friday, Dec. 9, 2011. Abhisit was called in to give information to a police investigation team on the government’s crackdown on red-shirt demonstrators last year during which 91 people were killed. (Apichart Weerawong) Members of the Red Shirt movement joke with a Thai police officer as they gather to protest against former Thai Prime Minister Abhisit Vejjajiva outside Metropolitan Police headquarters in Bangkok, Thailand Friday, Dec. 9, 2011. Abhisit was called in to give information to a police investigation team on the government’s crackdown on red-shirt demonstrators last year during which 91 people were killed. (Apichart Weerawong) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict63.jpg) Panamanian people protest against the return of former General Manuel Noriega to Panama, in Panama City on December 09,2011. Noriega returns to Panama without the trappings of political or military clout, but with something of incalculable value — detailed knowledge of the skeletons that lurk in the Central American nation’s closet. Getty Panamanian people protest against the return of former General Manuel Noriega to Panama, in Panama City on December 09,2011. Noriega returns to Panama without the trappings of political or military clout, but with something of incalculable value — detailed knowledge of the skeletons that lurk in the Central American nation’s closet. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict4.jpg) Thousands of people gather outside the main courthouse during the first trial of 22 leftist students who were jailed after they staged a demonstration to protest a police crackdown on anti-government demonstrators in the northern town of Hopa, Black Sea, ahead of general elections in June, in Ankara, Turkey, Friday, Dec. 9, 2011. (Burhan Ozbilici) Thousands of people gather outside the main courthouse during the first trial of 22 leftist students who were jailed after they staged a demonstration to protest a police crackdown on anti-government demonstrators in the northern town of Hopa, Black Sea, ahead of general elections in June, in Ankara, Turkey, Friday, Dec. 9, 2011. (Burhan Ozbilici) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict10.jpg) Activists of the Ukrainian women’s movement FEMEN stage a performance in front of the Christ the Saviour Cathedral in Moscow, on December 9, 2011, to protest against alleging mass fraud in the Russian December 4 parliamentary polls and demanding Russia’s Prime Minister Vladimir Putin that he stop his political activities. Putin, who became premier in 2008 after serving two Kremlin terms, filed this week his application to stand in the March elections. Getty Activists of the Ukrainian women’s movement FEMEN stage a performance in front of the Christ the Saviour Cathedral in Moscow, on December 9, 2011, to protest against alleging mass fraud in the Russian December 4 parliamentary polls and demanding Russia’s Prime Minister Vladimir Putin that he stop his political activities. Putin, who became premier in 2008 after serving two Kremlin terms, filed this week his application to stand in the March elections. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict0.jpg) Activists of Ukraine’s protest group Femen, protest outside the Christ the Saviour cathedral in Moscow, Russia, Friday, Dec. 9, 2011. The post-election protests in Moscow drew thousands and continued for several days in the biggest ever challenge to Putin, reflecting a growing public frustration with his rule that may complicate his bid to reclaim the presidency in next March’s vote. (Ivan Sekretarev) Activists of Ukraine’s protest group Femen, protest outside the Christ the Saviour cathedral in Moscow, Russia, Friday, Dec. 9, 2011. The post-election protests in Moscow drew thousands and continued for several days in the biggest ever challenge to Putin, reflecting a growing public frustration with his rule that may complicate his bid to reclaim the presidency in next March’s vote. (Ivan Sekretarev)
|
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict45.jpg) Medical workers rally at the Latvian Saeima (Parliament) building to protest budget cuts in health care on December 8, 2011 in Riga. The protesters are holding black balloons and various placards, urging the government to care for medical workers and warning that many health care workers may leave Latvia. Placards read: ‘Left country. Everyone has rights to receive health care’. Getty Medical workers rally at the Latvian Saeima (Parliament) building to protest budget cuts in health care on December 8, 2011 in Riga. The protesters are holding black balloons and various placards, urging the government to care for medical workers and warning that many health care workers may leave Latvia. Placards read: ‘Left country. Everyone has rights to receive health care’. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict44.jpg) Demonstrators protest about high inflation and low interest rates outside the Bank of England in the City of London December 8, 2011. The Bank of England voted on Thursday to stick to its four-month programme to pump an extra 75 billion pounds of quantitative easing into the rapidly slowing economy. Reuters Demonstrators protest about high inflation and low interest rates outside the Bank of England in the City of London December 8, 2011. The Bank of England voted on Thursday to stick to its four-month programme to pump an extra 75 billion pounds of quantitative easing into the rapidly slowing economy. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict43.jpg) Pakistani protesters carry national flags as they march during a demonstration in Islamabad on December 8, 2011 against the cross-border NATO air strike on Pakistani troops. Several hundred journalists, labour leaders and traders on December 8, took to streets to condemn a recent air strike by NATO on Pakistani military checkposts that killed 24 soldiers. Pakistan shut the only supply route in Khyber tribal region for international troops in Afghanistan, boycotted the Bonn conference and announced to revisit policy towards the US in protest against the attack. Getty Pakistani protesters carry national flags as they march during a demonstration in Islamabad on December 8, 2011 against the cross-border NATO air strike on Pakistani troops. Several hundred journalists, labour leaders and traders on December 8, took to streets to condemn a recent air strike by NATO on Pakistani military checkposts that killed 24 soldiers. Pakistan shut the only supply route in Khyber tribal region for international troops in Afghanistan, boycotted the Bonn conference and announced to revisit policy towards the US in protest against the attack. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict42.jpg) Fundamentalist Christians protest on December 8, 2011 in Paris, near the Rond-Point theatre where Argentina-born author Rodrigo Garcia’s play ‘Golgota Picnic’ is performed which they judge ‘blasphemous’. Getty Fundamentalist Christians protest on December 8, 2011 in Paris, near the Rond-Point theatre where Argentina-born author Rodrigo Garcia’s play ‘Golgota Picnic’ is performed which they judge ‘blasphemous’. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict41.jpg) People pose with a protester wearing a mock mask depicting Russian Prime Minister Vladimir Putin during a rally in downtown St.Petersburg, Russia, Thursday, Dec. 8, 2011. More than five hundred people protested in St.Petersburg against Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky) People pose with a protester wearing a mock mask depicting Russian Prime Minister Vladimir Putin during a rally in downtown St.Petersburg, Russia, Thursday, Dec. 8, 2011. More than five hundred people protested in St.Petersburg against Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict40.jpg) Occupy Boston protester Heather McCann, of Watertown, Mass., center, loads a crate of books into a truck at the Dewey Square encampment while dismantling the camps library, in Boston, Thursday, Dec. 8, 2011. Boston Mayor Thomas Menino said Thursday that Occupy Boston protesters must leave their encampment in the city’s financial district by midnight Thursday or face eviction by police. (Steven Senne) Occupy Boston protester Heather McCann, of Watertown, Mass., center, loads a crate of books into a truck at the Dewey Square encampment while dismantling the camps library, in Boston, Thursday, Dec. 8, 2011. Boston Mayor Thomas Menino said Thursday that Occupy Boston protesters must leave their encampment in the city’s financial district by midnight Thursday or face eviction by police. (Steven Senne) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict31.jpg) A veiled Kashmiri government employee participates in a protest against the government in Srinagar, India, Thursday, Dec. 8, 2011. Dozens of government employees demanded release of arrears and regularization of jobs for daily wage workers. (Dar Yasin) A veiled Kashmiri government employee participates in a protest against the government in Srinagar, India, Thursday, Dec. 8, 2011. Dozens of government employees demanded release of arrears and regularization of jobs for daily wage workers. (Dar Yasin) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict30.jpg) Protesters march to join fellow protesters who camped out outside a Catholic church near the Presidential Palace in Manila, Philippines Thursday Dec. 8, 2011 to await news of the scheduled execution of a Filipino man convicted in China for drug trafficking. Philippine officials said, the Filipino man, who was convicted on drug trafficking, was executed in China on Thursday despite an appeal for clemency from President Benigno Aquino III on humanitarian grounds. (Bullit Marquez) Protesters march to join fellow protesters who camped out outside a Catholic church near the Presidential Palace in Manila, Philippines Thursday Dec. 8, 2011 to await news of the scheduled execution of a Filipino man convicted in China for drug trafficking. Philippine officials said, the Filipino man, who was convicted on drug trafficking, was executed in China on Thursday despite an appeal for clemency from President Benigno Aquino III on humanitarian grounds. (Bullit Marquez) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict29.jpg) Kashmiri government employees participate in a protest against the government in Srinagar, India, Thursday, Dec. 8, 2011. Dozens of government employees demanded release of arrears and regularization of jobs for daily wage workers. (Dar Yasin) Kashmiri government employees participate in a protest against the government in Srinagar, India, Thursday, Dec. 8, 2011. Dozens of government employees demanded release of arrears and regularization of jobs for daily wage workers. (Dar Yasin) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict28.jpg) A small group of demonstrators screams slogans demanding UN protection for Iranian dissidents in Camp Ashraf, Iraq, as they protest outside the Dutch Foreign Ministry during U.S. Secretary of State Hillary Rodham Clinton’s visit in The Hague, Netherlands, Thursday Dec. 8, 2011. (Peter Dejong) A small group of demonstrators screams slogans demanding UN protection for Iranian dissidents in Camp Ashraf, Iraq, as they protest outside the Dutch Foreign Ministry during U.S. Secretary of State Hillary Rodham Clinton’s visit in The Hague, Netherlands, Thursday Dec. 8, 2011. (Peter Dejong) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict27.jpg) Police officers detain an opposition activist during a rally in downtown St.Petersburg, Russia, Thursday, Dec. 8, 2011. More than five hundreds people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky) Police officers detain an opposition activist during a rally in downtown St.Petersburg, Russia, Thursday, Dec. 8, 2011. More than five hundreds people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict26.jpg) French far-right leader Marine Le Pen arrives at their demonstration in Paris Thursday, Dec. 8, 2011. The demonstration was to oppose a bill on which the Senate were voting Thursday afternoon, a private members bill calling for the right for foreigners to be able to vote in French municipal elections. (Jacques Brinon) French far-right leader Marine Le Pen arrives at their demonstration in Paris Thursday, Dec. 8, 2011. The demonstration was to oppose a bill on which the Senate were voting Thursday afternoon, a private members bill calling for the right for foreigners to be able to vote in French municipal elections. (Jacques Brinon) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict25.jpg) People living near nuclear plant sites shout slogans during an anti-nuclear protest in New Delhi, India, Thursday, Dec. 8, 2011. The protesters demanded scrapping of projects that endanger people’s safety and threaten livelihoods, according to a press release. Placard reads “Stop displacement of people in the name of development.” (Manish Swarup) People living near nuclear plant sites shout slogans during an anti-nuclear protest in New Delhi, India, Thursday, Dec. 8, 2011. The protesters demanded scrapping of projects that endanger people’s safety and threaten livelihoods, according to a press release. Placard reads “Stop displacement of people in the name of development.” (Manish Swarup) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict23.jpg) An Israeli musician covers her face in protest, as she performs during a rally against gender segregation, in Jerusalem, Wednesday, Dec. 7, 2011. Hundreds of women and women’s rights activists gathered in central Jerusalem Wednesday night for a rally organized by the New Israel Fund, themed “women will be seen and heard”, to protest discrimination against women in Israel. (Sebastian Scheiner) An Israeli musician covers her face in protest, as she performs during a rally against gender segregation, in Jerusalem, Wednesday, Dec. 7, 2011. Hundreds of women and women’s rights activists gathered in central Jerusalem Wednesday night for a rally organized by the New Israel Fund, themed “women will be seen and heard”, to protest discrimination against women in Israel. (Sebastian Scheiner) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict49.jpg) Nepalese Buddhist monks and nuns take out a protest in Katmandu, Nepal, Wednesday, Dec. 7, 2011. Hundreds of Buddhists demonstrated in Nepal’s capital to protest the appointment of Maoist party chief Pushpa Kamal Dahal to head a project to develop the area where Buddha was believed born in southern Nepal. The protestors demanded that there should not be any political involvement in the project to develop Lumbini, located 150 miles (240 kilometers) southwest of Katmandu. AP Nepalese Buddhist monks and nuns take out a protest in Katmandu, Nepal, Wednesday, Dec. 7, 2011. Hundreds of Buddhists demonstrated in Nepal’s capital to protest the appointment of Maoist party chief Pushpa Kamal Dahal to head a project to develop the area where Buddha was believed born in southern Nepal. The protestors demanded that there should not be any political involvement in the project to develop Lumbini, located 150 miles (240 kilometers) southwest of Katmandu. AP |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict48.jpg) A Libyan girl holds a placard that reads in Arabic ‘Thank you our brave rebels, but now let us live in peace’ during a protest in Tripoli’s landmark Martyrs Square on December 7, 2011 against former rebels who toppled Moamer Kadhafi but are still camping out in the capital and still have their weapons. Getty A Libyan girl holds a placard that reads in Arabic ‘Thank you our brave rebels, but now let us live in peace’ during a protest in Tripoli’s landmark Martyrs Square on December 7, 2011 against former rebels who toppled Moamer Kadhafi but are still camping out in the capital and still have their weapons. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict47.jpg) Members of the Canadian Youth Delegation stage a protest as Canada’s Minister of Environment Peter Kent addresses the United Nations Climate Change Conference (COP17) in Durban in this handout picture released by the Canada Youth Delegation, December 7, 2011. Reuters Members of the Canadian Youth Delegation stage a protest as Canada’s Minister of Environment Peter Kent addresses the United Nations Climate Change Conference (COP17) in Durban in this handout picture released by the Canada Youth Delegation, December 7, 2011. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict46.jpg) Two protesters look at each other as they await processing after being arrested by Washington DC Metropolitan Police during an Occupy DC protest in Washington, December 7, 2011. Police arrested economic protesters in Washington on Wednesday as they blocked streets and disrupted traffic in an area famous as a center for the offices of lobbyists. Reuters Two protesters look at each other as they await processing after being arrested by Washington DC Metropolitan Police during an Occupy DC protest in Washington, December 7, 2011. Police arrested economic protesters in Washington on Wednesday as they blocked streets and disrupted traffic in an area famous as a center for the offices of lobbyists. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict24.jpg) An Occupy DC demonstrator sits on a chair as demonstrators blocked an intersection on K St., in Washington, Wednesday, Dec. 7, 2011. (Evan Vucci) An Occupy DC demonstrator sits on a chair as demonstrators blocked an intersection on K St., in Washington, Wednesday, Dec. 7, 2011. (Evan Vucci) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict32.jpg) Occupy Wall Street activists carry house warming gifts to a house warming party during a tour of foreclosed homes in the East New York neighborhood of the Brooklyn borough of New York, Tuesday, Dec. 6, 2011. Finding it increasingly difficult to camp in public spaces, Occupy protesters across the country are reclaiming foreclosed homes and boarded-up properties, signaling a tactical shift for the movement against wealth inequality. Occupy Wall Street activists carry house warming gifts to a house warming party during a tour of foreclosed homes in the East New York neighborhood of the Brooklyn borough of New York, Tuesday, Dec. 6, 2011. Finding it increasingly difficult to camp in public spaces, Occupy protesters across the country are reclaiming foreclosed homes and boarded-up properties, signaling a tactical shift for the movement against wealth inequality. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict50.jpg) A Colombian woman living in Panama holds a Colombian national flag during a protest march against the Revolutionary Armed Forces of Colombia (FARC), in Panama City December 6, 2011. Outraged by the killing of four captives by FARC rebels, Colombians protested on Tuesday to demand an end to half a century of guerrilla violence and kidnapping. The words on the flag read: “Release them”. Reuters A Colombian woman living in Panama holds a Colombian national flag during a protest march against the Revolutionary Armed Forces of Colombia (FARC), in Panama City December 6, 2011. Outraged by the killing of four captives by FARC rebels, Colombians protested on Tuesday to demand an end to half a century of guerrilla violence and kidnapping. The words on the flag read: “Release them”. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict51.jpg) Colombian demonstrators take part in a protest march against Revolutionary Armed Forces of Colombia FARC rebels in Cali December 6, 2011. Outraged by the execution of four captives by FARC rebels, tens of thousands of Colombians protested across the nation on Tuesday to demand an end to half a century of guerrilla violence and kidnapping. Reuters Colombian demonstrators take part in a protest march against Revolutionary Armed Forces of Colombia FARC rebels in Cali December 6, 2011. Outraged by the execution of four captives by FARC rebels, tens of thousands of Colombians protested across the nation on Tuesday to demand an end to half a century of guerrilla violence and kidnapping. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict33.jpg) In this Nov. 2, 2011 file photo, occupy Oakland protesters march through the Port of Oakland in Oakland, Calif. Protesters want to shut down ports up and down the U.S. West Coast on Monday, Dec.12,2011, to gum up the engines of global commerce. But organizers who are partly billing this effort as a show of solidarity with longshoremen have not won the support of the powerful union representing thousands of dock workers. (Noah Berger) In this Nov. 2, 2011 file photo, occupy Oakland protesters march through the Port of Oakland in Oakland, Calif. Protesters want to shut down ports up and down the U.S. West Coast on Monday, Dec.12,2011, to gum up the engines of global commerce. But organizers who are partly billing this effort as a show of solidarity with longshoremen have not won the support of the powerful union representing thousands of dock workers. (Noah Berger)
|
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict35.jpg) An activist of a local women’s rights watchdog FEMEN, with writing “I am independent” and Ukraine’s’ national flag on her belly, seen during celebrities on the occasion of Ukraine’s 19th Independence in Kiev, Ukraine, Tuesday, Aug. 24, 2010. (Efrem Lukatsky) An activist of a local women’s rights watchdog FEMEN, with writing “I am independent” and Ukraine’s’ national flag on her belly, seen during celebrities on the occasion of Ukraine’s 19th Independence in Kiev, Ukraine, Tuesday, Aug. 24, 2010. (Efrem Lukatsky) |
STASI-STALKING- “DIE WELT” ÜBER DIE DIFFAMIERUNGSMETHODEN DER STASI – VORBILD FÜR “GoMoPa”
UNCENSORED – Women Protest Worldwide Photos 8
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict0.jpg) Kashmir Sutherland huddles with other protesters for warmth in Shemanski Park after police told them to take down tents or be kicked out Monday, Dec. 5, 2011, in Portland, Ore. The Oregonian reports the demonstrators agreed to take down a tent to stay in the park Sunday night. On Saturday night police arrested 19 demonstrators setting up structures in the South Park blocks. Police evicted demonstrators on Nov. 13 from two downtown parks. Kashmir Sutherland huddles with other protesters for warmth in Shemanski Park after police told them to take down tents or be kicked out Monday, Dec. 5, 2011, in Portland, Ore. The Oregonian reports the demonstrators agreed to take down a tent to stay in the park Sunday night. On Saturday night police arrested 19 demonstrators setting up structures in the South Park blocks. Police evicted demonstrators on Nov. 13 from two downtown parks. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict44.jpg) A woman shouts slogans during a rally in Moscow, Monday, Dec. 5, 2011. Several thousand people have protested in Moscow against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. A group of several hundred then marched toward the Central Elections Commission near the Kremlin, but were stopped by riot police and taken away in buses. (Sergey Ponomarev) A woman shouts slogans during a rally in Moscow, Monday, Dec. 5, 2011. Several thousand people have protested in Moscow against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. A group of several hundred then marched toward the Central Elections Commission near the Kremlin, but were stopped by riot police and taken away in buses. (Sergey Ponomarev) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict26.jpg) A blind woman rests in front of a police line during a protest by Greek blind people outside Parliament in Athens, on Monday, Dec. 5, 2011. Dozens of people took part in the demonstration, to protest against government welfare spending cuts. Greece is in the throes of an acute financial crisis and has implemented a harsh austerity programme in exchange for international rescue loans. (Petros Giannakouris) A blind woman rests in front of a police line during a protest by Greek blind people outside Parliament in Athens, on Monday, Dec. 5, 2011. Dozens of people took part in the demonstration, to protest against government welfare spending cuts. Greece is in the throes of an acute financial crisis and has implemented a harsh austerity programme in exchange for international rescue loans. (Petros Giannakouris) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict37.jpg) Occupy DC protesters stand inside a structure set up overnight in McPherson Square, Sunday, Dec. 4, 2011 in Washington. Protesters are refusing to dismantle the unfinished wooden structure erected in the park. (Manuel Balce Ceneta) Occupy DC protesters stand inside a structure set up overnight in McPherson Square, Sunday, Dec. 4, 2011 in Washington. Protesters are refusing to dismantle the unfinished wooden structure erected in the park. (Manuel Balce Ceneta) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict43.jpg) In this Nov. 17, 2011 file photo, students clash with police during a demonstration in Milan, Italy, as university students protest against budget cuts and a lack of jobs, hours before new Italian Premier Mario Monti reveals his anti-crisis strategy in Parliament. Europe’s sovereign-debt crisis, which has dragged on for more than two years, is entering a pivotal week, as leaders across the continent converge to prevent a collapse of the euro and a financial panic from spreading. In this Nov. 17, 2011 file photo, students clash with police during a demonstration in Milan, Italy, as university students protest against budget cuts and a lack of jobs, hours before new Italian Premier Mario Monti reveals his anti-crisis strategy in Parliament. Europe’s sovereign-debt crisis, which has dragged on for more than two years, is entering a pivotal week, as leaders across the continent converge to prevent a collapse of the euro and a financial panic from spreading. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict35.jpg) A female activist carries a sign promoting gender equality as protesters march through downtown Rabat calling for greater democracy. Moroccan pro-democracy activists called for a day of rage on Dec. 4, 2011, a week after legislative elections but few turned out. (Paul Schemm) A female activist carries a sign promoting gender equality as protesters march through downtown Rabat calling for greater democracy. Moroccan pro-democracy activists called for a day of rage on Dec. 4, 2011, a week after legislative elections but few turned out. (Paul Schemm) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict66.jpg) Animal rights activists of the AnimaNaturalis international organization stage a naked protest in the middle of the Plaza de Espana square in the centre of Madrid on December 4, 2011, to denounce the slaying of animals to make fur coats. The men and women, covered in red paint that resembled blood, lay down and curled up against each other under a sunny sky in the busy square which is home to several cinemas, cafes and restaurants. Placard reads ‘How many lives for a coat?’. Getty Animal rights activists of the AnimaNaturalis international organization stage a naked protest in the middle of the Plaza de Espana square in the centre of Madrid on December 4, 2011, to denounce the slaying of animals to make fur coats. The men and women, covered in red paint that resembled blood, lay down and curled up against each other under a sunny sky in the busy square which is home to several cinemas, cafes and restaurants. Placard reads ‘How many lives for a coat?’. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict67.jpg) Participants attend the Slutwalk Singapore event held at the Speakers’ Corner on December 4, 2011. Supporters of the global SlutWalk movement against sexual violence held a rally in Singapore, attracting dozens to a rare protest in the strictly policed city-state. Getty Participants attend the Slutwalk Singapore event held at the Speakers’ Corner on December 4, 2011. Supporters of the global SlutWalk movement against sexual violence held a rally in Singapore, attracting dozens to a rare protest in the strictly policed city-state. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict64.jpg) Russian police officers detain opposition demonstrators during an unsanctioned rally in downtown Moscow, Russia, Sunday, Dec. 4, 2011. The rally was staged by a few dozen activists of the Left Front opposition group to protest against Sunday’s elections. (Misha Japaridze) Russian police officers detain opposition demonstrators during an unsanctioned rally in downtown Moscow, Russia, Sunday, Dec. 4, 2011. The rally was staged by a few dozen activists of the Left Front opposition group to protest against Sunday’s elections. (Misha Japaridze)
|
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict72.jpg) Police officers try to arrest activists of the Ukrainian women’s movement FEMEN as they protest on December 3, 2011 against a meeting of opposition parties in Kiev. FEMEN activists protested against the event, saying that peeple came to the meeting because its organizers promised them money. Police officers try to arrest activists of the Ukrainian women’s movement FEMEN as they protest on December 3, 2011 against a meeting of opposition parties in Kiev. FEMEN activists protested against the event, saying that peeple came to the meeting because its organizers promised them money. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict71.jpg) Body-painted environmental activists demonstrate outside the United Nations Climate Change conference (COP17) in Durban December 3, 2011. The protest march was part of a Global Day of Action to demand a fair climate change deal. Reuters Body-painted environmental activists demonstrate outside the United Nations Climate Change conference (COP17) in Durban December 3, 2011. The protest march was part of a Global Day of Action to demand a fair climate change deal. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict69.jpg) An opponent of reelected Nicaraguan President Daniel Ortega holds a banner reading ‘Fraud=Poverty’, as she takes part in a protest called ”march against fraud” in Managua on December 3, 2011. About five thousand people marched in Nicaragua denouncing electoral fraud in past November 6 elections in Nicaragua and demanding a new election with foreign observers. Getty An opponent of reelected Nicaraguan President Daniel Ortega holds a banner reading ‘Fraud=Poverty’, as she takes part in a protest called ”march against fraud” in Managua on December 3, 2011. About five thousand people marched in Nicaragua denouncing electoral fraud in past November 6 elections in Nicaragua and demanding a new election with foreign observers. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict65.jpg) Occupy LA protesters march from Pershing Square to the Los Angeles County Men’s Central Jail where protesters, who were arrested on Wednesday, were being held, in Los Angeles, on Saturday, Dec. 3, 2011. (David Zentz) Occupy LA protesters march from Pershing Square to the Los Angeles County Men’s Central Jail where protesters, who were arrested on Wednesday, were being held, in Los Angeles, on Saturday, Dec. 3, 2011. (David Zentz) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict61.jpg) Andean people protest against Newmont Mining’s Conga gold project during a march near the Cortada lagoon at Peru’s region of Cajamarca, November 24, 2011. Peru’s prime minister on December 2, 2011, said Newmont Mining must set aside money to finance social projects and any environmental damage as a precondition for moving forward on a stalled $4.8 billion gold mine project. Opponents of Newmont Mining’s $4.8 billion Conga project refused to end their rallies on November 30, 2011, saying Peru must permanently cancel the proposed mine after temporarily halting work on it to avert violence. Protesters and farmers say the mine would cause pollution and hurt water supplies by replacing a string of alpine lakes with artificial reservoirs. Picture taken November 24, 2011. Andean people protest against Newmont Mining’s Conga gold project during a march near the Cortada lagoon at Peru’s region of Cajamarca, November 24, 2011. Peru’s prime minister on December 2, 2011, said Newmont Mining must set aside money to finance social projects and any environmental damage as a precondition for moving forward on a stalled $4.8 billion gold mine project. Opponents of Newmont Mining’s $4.8 billion Conga project refused to end their rallies on November 30, 2011, saying Peru must permanently cancel the proposed mine after temporarily halting work on it to avert violence. Protesters and farmers say the mine would cause pollution and hurt water supplies by replacing a string of alpine lakes with artificial reservoirs. Picture taken November 24, 2011. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict56.jpg) A woman protester join others as they shout slogans during the observance of World Climate Day Saturday, Dec. 3, 2011 near the U.S. Embassy in Manila, Philippines. The protest coincided with the annual climate talks of the Conference of Parties (COP17) in Durban, South Africa. (Pat Roque) A woman protester join others as they shout slogans during the observance of World Climate Day Saturday, Dec. 3, 2011 near the U.S. Embassy in Manila, Philippines. The protest coincided with the annual climate talks of the Conference of Parties (COP17) in Durban, South Africa. (Pat Roque) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict60.jpg) A woman holds aplacard during a protest march against the war in Afghanistan on December 3, 2011 in the western German city of Bonn where a major international conference on December 5 will discuss the country’s future beyond 2014, when NATO-led international combat troops will leave. Getty A woman holds aplacard during a protest march against the war in Afghanistan on December 3, 2011 in the western German city of Bonn where a major international conference on December 5 will discuss the country’s future beyond 2014, when NATO-led international combat troops will leave. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict57.jpg) A survivor of the Bhopal gas tragedy lies on a railway track as others sit around to stop train movement during a protest in Bhopal, India, Saturday, Dec. 3, 2011. Thousands of survivors of the world’s worst industrial accident blocked trains through a central Indian city on Saturday to demand more compensation. A survivor of the Bhopal gas tragedy lies on a railway track as others sit around to stop train movement during a protest in Bhopal, India, Saturday, Dec. 3, 2011. Thousands of survivors of the world’s worst industrial accident blocked trains through a central Indian city on Saturday to demand more compensation. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict58.jpg) Female Iranian demonstrators hold posters showing supreme leader Ayatollah Ali Khamenei, left in the posters, and late revolutionary founder Ayatollah Khomeini, during a demonstration to welcome Iranian diplomats expelled from London in retaliation for attacks on British compounds in Tehran, at the Mehrabad airport in Tehran, Iran, early Saturday, Dec. 3, 2011. Female Iranian demonstrators hold posters showing supreme leader Ayatollah Ali Khamenei, left in the posters, and late revolutionary founder Ayatollah Khomeini, during a demonstration to welcome Iranian diplomats expelled from London in retaliation for attacks on British compounds in Tehran, at the Mehrabad airport in Tehran, Iran, early Saturday, Dec. 3, 2011. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict59.jpg) Students are arrested during a protest against the government to demand changes in the public state education system in Santiago, December 2, 2011. Chilean students have been protesting against what they say is profiteering in the state education system. Reuters Students are arrested during a protest against the government to demand changes in the public state education system in Santiago, December 2, 2011. Chilean students have been protesting against what they say is profiteering in the state education system. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict41.jpg) Demonstrators walk on a protest march in central London November 30, 2011. Teachers, nurses and border guards walked out on Wednesday as up to two million state workers staged Britain’s first mass strike for more than 30 years in a growing confrontation with a deficit-cutting coalition government. Reuters Demonstrators walk on a protest march in central London November 30, 2011. Teachers, nurses and border guards walked out on Wednesday as up to two million state workers staged Britain’s first mass strike for more than 30 years in a growing confrontation with a deficit-cutting coalition government. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict31.jpg) Thousands of Bulgarians gather in front of the Bulgarian parliament to protest against government austerity measures in Sofia, Wednesday, Nov 30, 2011. Thousands joined a mass rally on Wednesday to protest government-proposed austerity measures that include raising the retirement age by one year. (Valentina Petrova) Thousands of Bulgarians gather in front of the Bulgarian parliament to protest against government austerity measures in Sofia, Wednesday, Nov 30, 2011. Thousands joined a mass rally on Wednesday to protest government-proposed austerity measures that include raising the retirement age by one year. (Valentina Petrova)
|
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict36.jpg) Activists of Ukrainian women movement FEMEN hold placards reading ‘EURO-2012 without prostitution’, ‘UEFA attacked our gates’ and others during a protest in front of the Olimpisky Stadium in Kie, a few hours prior the UEFA EURO-2012 Final Draw ceremony on December 2, 2011. Getty Activists of Ukrainian women movement FEMEN hold placards reading ‘EURO-2012 without prostitution’, ‘UEFA attacked our gates’ and others during a protest in front of the Olimpisky Stadium in Kie, a few hours prior the UEFA EURO-2012 Final Draw ceremony on December 2, 2011. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict33.jpg) Hundreds of workers on strike block the entrance gate of Hi-P International factory during a protest in a suburban area of Shanghai December 2, 2011. More than 200 workers at a Singapore-owned electronics plant in the commercial hub of Shanghai went on strike for a third day on Friday to protest against planned layoffs, the latest sign of labour unrest in the world’s second-largest economy. Reuters Hundreds of workers on strike block the entrance gate of Hi-P International factory during a protest in a suburban area of Shanghai December 2, 2011. More than 200 workers at a Singapore-owned electronics plant in the commercial hub of Shanghai went on strike for a third day on Friday to protest against planned layoffs, the latest sign of labour unrest in the world’s second-largest economy. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict28.jpg) A police officer detains a topless woman protesting against alleged attempts to legalize prostitution during the Euro 2012 in Ukraine prior to the final draw for the Euro 2012 soccer tournament in Kiev, Ukraine, Friday, Dec. 2, 2011. Ukrainian women’s rights activists staged a topless demonstration at Kiev’s Olympic Stadium to protest what they say are attempts to legalize prostitution during the 2012 European Championship. (Ferdinand Ostrop) A police officer detains a topless woman protesting against alleged attempts to legalize prostitution during the Euro 2012 in Ukraine prior to the final draw for the Euro 2012 soccer tournament in Kiev, Ukraine, Friday, Dec. 2, 2011. Ukrainian women’s rights activists staged a topless demonstration at Kiev’s Olympic Stadium to protest what they say are attempts to legalize prostitution during the 2012 European Championship. (Ferdinand Ostrop) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict1.jpg) Survivors of the Bhopal gas tragedy, the world’s worst industrial disaster in India, along with other supporters shout slogans during a protest against a sponsorship deal with Dow Chemicals for the 2012 Olympics, in Bhopal, India, Friday, Dec. 2, 2011. Friday’s protests come on the eve of the 27th anniversary of a lethal gas leak from a Union Carbide pesticide plant in Bhopal where an estimated 15,000 people died and tens of thousands were maimed in 1984. Survivors of the Bhopal gas tragedy, the world’s worst industrial disaster in India, along with other supporters shout slogans during a protest against a sponsorship deal with Dow Chemicals for the 2012 Olympics, in Bhopal, India, Friday, Dec. 2, 2011. Friday’s protests come on the eve of the 27th anniversary of a lethal gas leak from a Union Carbide pesticide plant in Bhopal where an estimated 15,000 people died and tens of thousands were maimed in 1984. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict39.jpg) Iranian dissidents hold banners as they protest in Brussels, Thursday, Dec. 1, 2011. The protesters called for prevention of compulsory displacement of the Camp Ashraf residents inside Iraq and the annulment of the deadline for closure of Camp Ashraf by the end of December. Camp Ashraf, an enclave in eastern Iraq that houses more than 3,000 people, many of whom are dedicated to overthrowing the government of Iran. Iranian dissidents hold banners as they protest in Brussels, Thursday, Dec. 1, 2011. The protesters called for prevention of compulsory displacement of the Camp Ashraf residents inside Iraq and the annulment of the deadline for closure of Camp Ashraf by the end of December. Camp Ashraf, an enclave in eastern Iraq that houses more than 3,000 people, many of whom are dedicated to overthrowing the government of Iran. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict38.jpg) Afghan girls hold placards during a demonstration in Kabul December 1, 2011. Hundreds of Afghans from the Solidarity Party of Afghanistan took to the streets of Kabul on Thursday to protest against plans for a long-term partnership deal with the United States. Reuters Afghan girls hold placards during a demonstration in Kabul December 1, 2011. Hundreds of Afghans from the Solidarity Party of Afghanistan took to the streets of Kabul on Thursday to protest against plans for a long-term partnership deal with the United States. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict34.jpg) A woman disguised as muppet character Miss Piggy takes a mud bath in front of the House of Representatives in The Hague on December 1, 2011 during a protest with Dutch environmental organization Milieudefensie against the expansion of livestock farming. Getty A woman disguised as muppet character Miss Piggy takes a mud bath in front of the House of Representatives in The Hague on December 1, 2011 during a protest with Dutch environmental organization Milieudefensie against the expansion of livestock farming. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict25.jpg) A protester is detained by police during a march demanding education reform in Santiago, Chile, Thursday, Dec. 1, 2011. Chilean students clashed with police on Thursday during a protest demanding more funding for public education, while students in Colombia and Argentina also took to the streets in simultaneous demonstrations.(Luis Hidalgo) A protester is detained by police during a march demanding education reform in Santiago, Chile, Thursday, Dec. 1, 2011. Chilean students clashed with police on Thursday during a protest demanding more funding for public education, while students in Colombia and Argentina also took to the streets in simultaneous demonstrations.(Luis Hidalgo) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict27.jpg) Protesters shout anti-austerity slogans during a 24-hour general strike in Athens on Thursday, Dec. 1, 2011. Thousands of protesters bitterly opposed to government austerity measures marched through the Greek capital Thursday, as another general strike closed schools and public services, left hospitals functioning on reduced staff and confined ferries to port. (Petros Giannakouris) Protesters shout anti-austerity slogans during a 24-hour general strike in Athens on Thursday, Dec. 1, 2011. Thousands of protesters bitterly opposed to government austerity measures marched through the Greek capital Thursday, as another general strike closed schools and public services, left hospitals functioning on reduced staff and confined ferries to port. (Petros Giannakouris) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict29.jpg) An Occupy Raleigh protester shouts during a speech by John Stumpf, the CEO and president of Wells Fargo, on Wednesday, Nov. 30, 2011, in Raleigh, N.C. Stumpf was about 30 minutes into his speech when protesters interrupted him as he talked about the importance of small business. (Chuck Liddy) An Occupy Raleigh protester shouts during a speech by John Stumpf, the CEO and president of Wells Fargo, on Wednesday, Nov. 30, 2011, in Raleigh, N.C. Stumpf was about 30 minutes into his speech when protesters interrupted him as he talked about the importance of small business. (Chuck Liddy) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict30.jpg) A protester from Portland, Maine, warms her hand with her breath while eating a sandwich at the Occupy Boston encampment, in Boston on Wednesday, Nov. 30, 2011. In the past few weeks police broke up encampments in Portland, Ore., Oakland, Calif., and New York, where the sit-down protests against social inequality and corporate excesses began in mid-September. Protesters remain in place in Boston and Washington, which each had camps of about 100 tents Wednesday. (Steven Senne) A protester from Portland, Maine, warms her hand with her breath while eating a sandwich at the Occupy Boston encampment, in Boston on Wednesday, Nov. 30, 2011. In the past few weeks police broke up encampments in Portland, Ore., Oakland, Calif., and New York, where the sit-down protests against social inequality and corporate excesses began in mid-September. Protesters remain in place in Boston and Washington, which each had camps of about 100 tents Wednesday. (Steven Senne) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict40.jpg) A woman is led away in handcuffs by police after being removed from Panton House in central London November 30, 2011. Demonstrators broke into an office building used by mining company Xstrata in central London on Wednesday and hung protest banners on the roof before police regained control of the building. A group of about 60 from the “Occupy” movement entered the offices in Haymarket in protest at the pay of the company’s chief executive, Occupy said in a statement. Reuters A woman is led away in handcuffs by police after being removed from Panton House in central London November 30, 2011. Demonstrators broke into an office building used by mining company Xstrata in central London on Wednesday and hung protest banners on the roof before police regained control of the building. A group of about 60 from the “Occupy” movement entered the offices in Haymarket in protest at the pay of the company’s chief executive, Occupy said in a statement. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict24.jpg) A female protestor displays her hands with Yemen’s flag and writing Arabic that reads,”you will prosecuted,” during a demonstration demanding the prosecution of Yemen’s President Ali Abdullah Saleh in Sanaa, Yemen, Tuesday, Nov. 29, 2011. Hundreds of thousands of Yemenis are demonstrating across the country to demand President Ali Abdullah Saleh face trial for charges ranging from corruption to deadly crackdowns on protests. (Hani Mohammed) A female protestor displays her hands with Yemen’s flag and writing Arabic that reads,”you will prosecuted,” during a demonstration demanding the prosecution of Yemen’s President Ali Abdullah Saleh in Sanaa, Yemen, Tuesday, Nov. 29, 2011. Hundreds of thousands of Yemenis are demonstrating across the country to demand President Ali Abdullah Saleh face trial for charges ranging from corruption to deadly crackdowns on protests. (Hani Mohammed) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict19.jpg) Supporters of Sri Lanka’s main opposition United National Party (UNP) protest in Colombo on November 29, 2011. They were protesting the jailing of the former army chief Darath Fonseka, a business take over bill and the government’s 2012 budget proposals. Getty Supporters of Sri Lanka’s main opposition United National Party (UNP) protest in Colombo on November 29, 2011. They were protesting the jailing of the former army chief Darath Fonseka, a business take over bill and the government’s 2012 budget proposals. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict21.jpg) Members of India’s National Domestic Workers Movement from the southern state of Andhra Pradesh (AP) region are watched by co-ordinator Sister Mea Yaragani (2L) as they sign a sheet while participating in a protest meet and signature campaign in Hyderabad on November 29, 2011. The protesors are demanding the ratification of the 189th International Labour Organization (ILO) convention by the Indian government and their inclusion in the Sexual Harassment Bill 2010. There are between 120000-150000 domestic workers in the state. Getty Members of India’s National Domestic Workers Movement from the southern state of Andhra Pradesh (AP) region are watched by co-ordinator Sister Mea Yaragani (2L) as they sign a sheet while participating in a protest meet and signature campaign in Hyderabad on November 29, 2011. The protesors are demanding the ratification of the 189th International Labour Organization (ILO) convention by the Indian government and their inclusion in the Sexual Harassment Bill 2010. There are between 120000-150000 domestic workers in the state. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict23.jpg) Workers protest as they shout slogans demanding higher wages in front of Indonesia’s presidential palace in Jakarta, November 29, 2011. Indonesia has been hit by a series of strikes in recent months and is expected to see more labour disputes, as workers demanded a greater share of profits in one of Asia’s fastest growing economies. Reuters Workers protest as they shout slogans demanding higher wages in front of Indonesia’s presidential palace in Jakarta, November 29, 2011. Indonesia has been hit by a series of strikes in recent months and is expected to see more labour disputes, as workers demanded a greater share of profits in one of Asia’s fastest growing economies. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict20.jpg) Miss Water South Africa Kirsten Dukes poses in front of a banner during a protest by environmental activists outside the United Nations Framework Convention on Climate Change Conference of the Parties meeting (COP17) in Durban, November 29, 2011. The gathering runs until December 9. Reuters Miss Water South Africa Kirsten Dukes poses in front of a banner during a protest by environmental activists outside the United Nations Framework Convention on Climate Change Conference of the Parties meeting (COP17) in Durban, November 29, 2011. The gathering runs until December 9. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict18.jpg) Student, wearing niqabs, protest on November 29, 2011 in the building housing the office of the dean of the Faculty of Arts at the University of Manuba, 25 kms west of Tunis. Several hundred people gathered at the university to demand the right for female students to wear full face veils in class and pass exams. A group of Salafists disrupted classes on November 28 at the university, demanding a stop to mixed-sex classes and for female students to wear full face veils. Getty Student, wearing niqabs, protest on November 29, 2011 in the building housing the office of the dean of the Faculty of Arts at the University of Manuba, 25 kms west of Tunis. Several hundred people gathered at the university to demand the right for female students to wear full face veils in class and pass exams. A group of Salafists disrupted classes on November 28 at the university, demanding a stop to mixed-sex classes and for female students to wear full face veils. Getty |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict17.jpg) Workers take part in a rally during a protest against government austerity measures organized by the PAME Communist-affiliated union in central Athens Tuesday, Nov. 29, 2011. The 17 finance ministers of the countries that use the euro converged on EU headquarters Tuesday in a desperate bid to save their currency – and to protect Europe, the United States, Asia and the rest of the global economy from a debt-induced financial tsunami. AP Workers take part in a rally during a protest against government austerity measures organized by the PAME Communist-affiliated union in central Athens Tuesday, Nov. 29, 2011. The 17 finance ministers of the countries that use the euro converged on EU headquarters Tuesday in a desperate bid to save their currency – and to protect Europe, the United States, Asia and the rest of the global economy from a debt-induced financial tsunami. AP |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict16.jpg) Supporters of Pakistan Tehreek-i-Insaf (Pakistan’s Movement for Justice) pray after a demonstration against NATO cross-border attack in Lahore November 29, 2011. Pakistan’s government confirmed it would not attend an international conference on the future of Afghanistan in Bonn next week to protest against a NATO cross-border attack that killed two dozen Pakistani soldiers. Reuters Supporters of Pakistan Tehreek-i-Insaf (Pakistan’s Movement for Justice) pray after a demonstration against NATO cross-border attack in Lahore November 29, 2011. Pakistan’s government confirmed it would not attend an international conference on the future of Afghanistan in Bonn next week to protest against a NATO cross-border attack that killed two dozen Pakistani soldiers. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict15.jpg) Riot police detain two students inside the national congress during a protest against the government to demand changes in the public state education system in Valparaiso city, about 121 km (75 miles) northwest of Santiago, November 29, 2011. Chilean students have been protesting against what they say is the profiteering in the state education system. Reuters Riot police detain two students inside the national congress during a protest against the government to demand changes in the public state education system in Valparaiso city, about 121 km (75 miles) northwest of Santiago, November 29, 2011. Chilean students have been protesting against what they say is the profiteering in the state education system. Reuters |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict2.jpg) Pakistani protesters rally to condemn NATO strikes on Pakistani soldiers, in Lahore, Pakistan, Tuesday, Nov. 29, 2011. Pakistan pulled out of an upcoming meeting in Germany on the future of Afghanistan to protest the deadly attack by U.S.-led forces on its troops, widening the fallout on Tuesday from an incident that has sent ties between Washington and Islamabad into a tailspin. Placard at right reads “run NATO and wake Pakistan army”. (K.M. Chaudary) Pakistani protesters rally to condemn NATO strikes on Pakistani soldiers, in Lahore, Pakistan, Tuesday, Nov. 29, 2011. Pakistan pulled out of an upcoming meeting in Germany on the future of Afghanistan to protest the deadly attack by U.S.-led forces on its troops, widening the fallout on Tuesday from an incident that has sent ties between Washington and Islamabad into a tailspin. Placard at right reads “run NATO and wake Pakistan army”. (K.M. Chaudary) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict3.jpg) A demonstrator holds a sign that reads in Portuguese: “The fight on the forest starts in the streets”, during a protest against the approval of the new Brazilian forest code in Brasilia, Brazil, Tuesday, Nov. 29, 2011. Brazil’s lower house in May approved changes to the law that would ease environmental restrictions in the Amazon and other regions in Brazil. Brazil’s Senate is expected to approve the measure this week, though President Dilma Rousseff has promised to veto some parts of the bill. A demonstrator holds a sign that reads in Portuguese: “The fight on the forest starts in the streets”, during a protest against the approval of the new Brazilian forest code in Brasilia, Brazil, Tuesday, Nov. 29, 2011. Brazil’s lower house in May approved changes to the law that would ease environmental restrictions in the Amazon and other regions in Brazil. Brazil’s Senate is expected to approve the measure this week, though President Dilma Rousseff has promised to veto some parts of the bill. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict4.jpg) Female Iranian protesters attend a demonstration in front of the British Embassy, as one of them holds a poster of supreme leader Ayatollah Ali Khamenei, in Tehran, Iran, Tuesday, Nov. 29, 2011. Dozens of hard-line Iranian students stormed the British Embassy in Tehran on Tuesday, bringing down the Union Jack flag and throwing documents from windows in scenes reminiscent of the anger against Western powers after the 1979 Islamic Revolution. Female Iranian protesters attend a demonstration in front of the British Embassy, as one of them holds a poster of supreme leader Ayatollah Ali Khamenei, in Tehran, Iran, Tuesday, Nov. 29, 2011. Dozens of hard-line Iranian students stormed the British Embassy in Tehran on Tuesday, bringing down the Union Jack flag and throwing documents from windows in scenes reminiscent of the anger against Western powers after the 1979 Islamic Revolution. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict5.jpg) An elderly protestor flashes the victory sign during a demonstration demanding the prosecution of Yemen’s President Ali Abdullah Saleh in Sanaa, Yemen, Tuesday, Nov. 29, 2011. Hundreds of thousands of Yemenis are demonstrating across the country to demand President Ali Abdullah Saleh face trial for charges ranging from corruption to deadly crackdowns on protests. (Hani Mohammed) An elderly protestor flashes the victory sign during a demonstration demanding the prosecution of Yemen’s President Ali Abdullah Saleh in Sanaa, Yemen, Tuesday, Nov. 29, 2011. Hundreds of thousands of Yemenis are demonstrating across the country to demand President Ali Abdullah Saleh face trial for charges ranging from corruption to deadly crackdowns on protests. (Hani Mohammed) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict6.jpg) Mariachi musicians perform as Greenpeace activists demand Brazil’s President Dilma Rousseff protect the Amazon as they protest outside Brazil’s embassy in Mexico City, Tuesday Nov. 29, 2011. Brazil’s government has authorized the construction of one the world’s largest hydroelectric dams, the Belo Monte dam, in the state of Para, and the federal prosecutors’ office in Para has said they will go to the Supreme Court to appeal the ruling. Mariachi musicians perform as Greenpeace activists demand Brazil’s President Dilma Rousseff protect the Amazon as they protest outside Brazil’s embassy in Mexico City, Tuesday Nov. 29, 2011. Brazil’s government has authorized the construction of one the world’s largest hydroelectric dams, the Belo Monte dam, in the state of Para, and the federal prosecutors’ office in Para has said they will go to the Supreme Court to appeal the ruling. |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict7.jpg) Malaysian lawyers hold placards as they shout slogans during a protest in Kuala Lumpur, Malaysia, Tuesday, Nov. 29, 2011. Hundreds of Malaysian lawyers staged a rare protest march Tuesday demanding that the government abandon plans for a law that will forbid street rallies. (Lai Seng Sin) Malaysian lawyers hold placards as they shout slogans during a protest in Kuala Lumpur, Malaysia, Tuesday, Nov. 29, 2011. Hundreds of Malaysian lawyers staged a rare protest march Tuesday demanding that the government abandon plans for a law that will forbid street rallies. (Lai Seng Sin) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict9.jpg) Protesters shout slogans as they hold candles with placards reading “Invalidity, FTA between South Korea and the U.S.” during a candle rally, denouncing the passing of a bill on ratification of a South Korea-U.S. free trade agreement in Seoul, South Korea, Tuesday, Nov. 29, 2011. South Korea’s president on Tuesday signed a slew of laws needed to implement the country’s free trade deal with the United States, amid growing protests denouncing the accord at home. (Lee Jin-man) Protesters shout slogans as they hold candles with placards reading “Invalidity, FTA between South Korea and the U.S.” during a candle rally, denouncing the passing of a bill on ratification of a South Korea-U.S. free trade agreement in Seoul, South Korea, Tuesday, Nov. 29, 2011. South Korea’s president on Tuesday signed a slew of laws needed to implement the country’s free trade deal with the United States, amid growing protests denouncing the accord at home. (Lee Jin-man) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict10.jpg) UCLA students walk past a line of demonstrators lying on the Quad outside a meeting of the Board of Regents at the University of California, on the campus at UCLA in Los Angeles, Monday, Nov. 28, 2011. The regents were originally scheduled to meet in mid-November at the San Francisco-Mission Bay campus, but the session was scrapped when law enforcement warned that protests could turn violent. (Reed Saxon) UCLA students walk past a line of demonstrators lying on the Quad outside a meeting of the Board of Regents at the University of California, on the campus at UCLA in Los Angeles, Monday, Nov. 28, 2011. The regents were originally scheduled to meet in mid-November at the San Francisco-Mission Bay campus, but the session was scrapped when law enforcement warned that protests could turn violent. (Reed Saxon) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict14.jpg) Supporters of Progressive Organization of Women raise slogans during a protest rally in New Delhi, India, Monday, Nov. 28, 2011. The protesters demanded introduction of a bill in the ongoing session of parliament for a separate statehood of Telangana region from the existing Andhra Pradesh state in southern India. (Gurinder Osan) Supporters of Progressive Organization of Women raise slogans during a protest rally in New Delhi, India, Monday, Nov. 28, 2011. The protesters demanded introduction of a bill in the ongoing session of parliament for a separate statehood of Telangana region from the existing Andhra Pradesh state in southern India. (Gurinder Osan) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict12.jpg) Police officers stand during a demonstration by security forces in Tunis, Monday, Nov.28, 2011. Security forces are protesting against police officers sued on trial for their alleged role in the revolution. On armband reads: “Stop, break the silence”. (Hassene Dridi) Police officers stand during a demonstration by security forces in Tunis, Monday, Nov.28, 2011. Security forces are protesting against police officers sued on trial for their alleged role in the revolution. On armband reads: “Stop, break the silence”. (Hassene Dridi) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict11.jpg) Members of Occupy Philly, from right to left, Shawn Grant, Brianne Murphy, and Diane Isser, demonstrate at Dilworth Plaza, in Philadelphia, on Sunday Nov. 27, 2011, in defiance of the city’s 5 p.m. eviction order. (Joseph Kaczmarek) Members of Occupy Philly, from right to left, Shawn Grant, Brianne Murphy, and Diane Isser, demonstrate at Dilworth Plaza, in Philadelphia, on Sunday Nov. 27, 2011, in defiance of the city’s 5 p.m. eviction order. (Joseph Kaczmarek) |
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict13.jpg) A member of Occupy Philly who identified herself as Laura watches the demonstration at Dilworth Plaza, in Philadelphia, Sunday Nov. 27, 2011, held in defiance of the city’s 5 p.m. eviction order. (Joseph Kaczmarek) A member of Occupy Philly who identified herself as Laura watches the demonstration at Dilworth Plaza, in Philadelphia, Sunday Nov. 27, 2011, held in defiance of the city’s 5 p.m. eviction order. (Joseph Kaczmarek) |
STASI – Strahlen-Opfer wurden bewusst verseucht und getötet – von Peter Wensierski
für Staatssicherheit (MfS) herum, es gehöre „zum Apparat“ im Nebenzimmer. Die wenigen Mitglieder des Geraer Bürgerkomitees, die an jenem 27. Dezember 1989 den berüchtigten Stasi-Knast in der Rudolf-Diener-Straße betraten, sahen dort aber zunächst einmal nichts Besonderes.
Vor einer weißen Pappwand befand sich ein Stuhl aus der Gestapo-Zeit. Er ließ sich durch eine Hebelmechanik um genau 90 Grad drehen. So konnten die Wärter von den darauf sitzenden Gefangenen die üblichen Sträflingsfotos schießen: einige von vorn, einige von der Seite, jeweils mit Registriernummer. Ansonsten standen im Raum noch Scheinwerfer und Stative, mehr nicht.
Aber hinter der Pappwand war noch ein Vorhang. Als der aufgezogen wurde, entdeckten die Bürgerrechtler – in Kopfhöhe hinter dem Stuhl – ein merkwürdiges Röntgengerät. Die Besucher waren zwar befremdet, fotografierten den Raum und stellten noch Fragen nach Sinn und Zweck des mysteriösen Apparats, doch in den turbulenten Wendetagen ging die Sache am Ende unter. Bei einer späteren Besichtigung war das Gerät spurlos verschwunden.
Für einige der damals Beteiligten ist die Aufklärung des bizarren Fundes jetzt, zehn Jahre später, jedoch wieder höchst aktuell. So war der Landesbeauftragte für Stasi-Unterlagen in Mecklenburg-Vorpommern, Jörn Mothes, Ende März auf Spurensuche im Geraer Stasi-Gefängnis, das noch immer als Haftanstalt dient. Mothes fordert, daß Staatsanwälte endlich seine Strafanzeige wegen „missbräuchlicher Anwendung von Röntgengeräten durch das „MfS“ verfolgten, bevor das Gefängnis samt Fotoraum demnächst wie geplant abgerissen wird.
Eine Reihe von Indizien spricht seiner Ansicht nach dafür, daß mit der Strahlenkanone missliebige Häftlinge im Rahmen von „MfS-Zersetzungsmaßnahmen“ unbemerkt verseucht wurden – um ihnen langfristig Schäden zuzufügen. Eine Theorie wie aus einem James-Bond-Film.
Aber drei der prominentesten DDR-Dissidenten sind in den letzten Jahren in der Tat an seltenen Arten von Krebsleiden erkrankt. So starb Rudolf Bahro 1997 an einem Non-Hodgkin-Lymphom, vergangenes Jahr verstarb der Leipziger Liedermacher Gerulf Pannach ebenfalls an Krebs. Letzte Woche erlag schließlich der Schriftsteller Jürgen Fuchs, erst 48 Jahre alt, einer seltenen Blutkrebskrankheit, dem Plasmozytom. „Jürgen Fuchs hegte die Vermutung, daß seine tödliche Krankheit nicht gottgewollt war, sondern menschengemacht“, so der Bürgerrechtler und Fuchs-Freund Wolf Biermann […].
Alle drei Krebsopfer saßen längere Zeit in Stasi-Haft. Einige Oppositionelle mögen ihr Schicksal nicht als Zufall abtun: Eindeutige Belege für Langzeitmordanschläge sind in den Akten der Betroffenen zwar nicht zu finden, doch es gibt Indizien. Auch lässt sich beweisen, daß die Stasi überlegte, wie Menschen durch Strahlen geschädigt werden können – etwa durch eine Ausarbeitung, die 1988 bei der Stasi-nahen „Sektion Kriminalistik“ der Ost-Berliner Humboldt-Universität entstand.
Auf 911 Seiten wird da unter dem Studien-Titel „Toxdat“ jede nur erdenkliche Möglichkeit angeführt, wie man Menschen durch Gift ums Leben bringen kann. Die Studie nennt mehr als 200 toxische und strahlende Substanzen und beschreibt detailliert, wie sie eingesetzt werden könnten.
Im Kapitel „Schädigung durch Beibringung radioaktiver Stoffe“ werden dem Toxdat-Papier Radionuklide besonderer Gefährlichkeit genannt, von Strontium-90 bis Plutonium-238 – aber auch „Mikromengen abgebrannter Brennstäbe“ aus Kernkraftwerken. Solche Stoffe würden beim Menschen eine „kombinierte Schädigung“ hervorrufen, „da der resultierende biologische Effekt aus einer chemischen (Gift) und einer physikalischen (Energie) Wirkung resultiert“. Beigebracht, „beispielsweise in Speisen und Getränken“, bewirkten sie „zu Siechtum führende Blut/ Knochenmarkschäden und Krebs“.
Diese Wirkungen ließen sich bereits mittels „Dosen im Mikro- bis Milligrammbereich“ erzielen. Aus der langen Zeit zwischen Attacke und Ausbruch von tödlichen Krankheiten ergebe sich ein „hohes Verschleierungspotenzial“. Schon „während der langen Latenzzeit manifestieren sich irreversible Schäden“, ohne daß der Betroffene etwas davon wahrnehme.
Bereits in den siebziger Jahren waren Stasi-Mitarbeiter zudem im Umgang mit radionukliden und in „nichtmedizinischer Röntgentechnik“ ausgebildet worden. Das geht aus einem anderen Dokument hervor, dem MfS-Jahresbericht der „Hauptabteilung XXII“ von Januar 1979. Die Stasi-Leute arbeiteten – laut einer „Aufgabenstellung des Dienstbereiches 2“ – „an der Anwendung radioaktiver Isotope“.
Ausgerechnet die MfS-Bezirksverwaltung Gera, Betreiberin der Strahlenkanone, zeigte sich nachweislich nicht zimperlich im Umgang mit radioaktiver Materie. Ihre „Abteilung 26“ übergab im Dezember 1978 in der Geraer Stasi-Zentrale strahlendes Material an einen aus Jena angereisten MfS-Mann. Der benutzte es, um einem im Kombinat Carl Zeiss Jena tätigen Physiker kontaminierte Akten unterzuschieben. Der Agent sollte den Wissenschaftler mit Hilfe radioaktiver Spuren der Spionage überführen können. Er selbst durfte nur 20 Minuten Kontakt zu den gefährlich strahlenden Papieren haben.
Den Verdacht, daß die Strahlenkanone im berüchtigten Gefängnis der Geraer Stasi gegen missliebige Bürger eingesetzt worden sein könnte, nährt auch die kaum glaubhafte Aussage des dortigen letzten Stasi-Chefs Michael Trostorff. Im Dezember 1989 beantwortete er die Frage nach dem Zweck der Anlage damit, daß sie „zum Kontrollieren von West-Paketen an die Untersuchungshäftlinge gedient“ habe. Die Geraer Gefangenen bekamen aber nicht gerade massenhaft West-Pakete. Außerdem erinnert sich der Jenaer Bürgerrechtler Thomas Auerbach ebenso wie andere Häftlinge: „Wenn etwas von draußen kam, erhielten wir die Sachen stets ausgepackt in einer offenen Holzkiste.“ Warum sollte die Stasi Pakete durchleuchten, die sie ohnehin öffnet? Und warum sollte sie ein Gerät zur Postkontrolle dort verstecken, wo Häftlinge fotografiert wurden?
Ein Geraer Röntgentechniker sah sich in den Wendetagen die Anlage genauer an, bevor sie für immer verschwand. Der Fachmann entdeckte, daß es sich keineswegs um ein Industrie-Serienprodukt handelte, sondern um unorthodox „zusammengestellt Komponenten“ auf Basis „eines Generators TuR DE 824501“. Die Anlage verstieß gegen DDR-Gesetze, war illegal und nicht angemeldet beim DDR-Amt für Atomsicherheit und Strahlenschutz. Durch „die fehlende Fixierung des Strahlers“ konnte der „auf den ca. einen Meter davor befindlichen fest am Boden verschraubten Stuhl in Kopfhöhe ausgerichtet“ werden.
Wurde der Primärstrahl auf einen Menschen gerichtet, der auf dem Stuhl saß, betrug die Dosis bei einstündiger Bestrahlung 1,1 Gray. Krebspatienten erhalten in der Strahlentherapie 40 bis 60 Gray pro vierwöchigen Behandlungszyklus. Die Geraer maschine war somit viel zu schwach, um zu töten, dazu bedarf es intensiver Ganzkörperbestrahlung. Auch um einen heftigen Strahlenkater, Hautrötung oder Haarausfall zu erzeugen, hätte das Opfer mindestens zehn Stunden damit traktiert werden müssen. Aber mit dem Gerät konnten die Stasi-Leute Opfern Strahlendosen verpassen, die hoch genug waren, um nach einigen Jahren möglicherweise Blutkrebs auszulösen.
Schriftliches zum Einsatz der Strahlenkanone hat die Stasi in Gera kaum hinterlassen. Zu finden sind ein paar Einmeßprotokolle der Anlage, die beweisen, daß sie zwischen 1976 und 1983 in Betrieb war. Die nach der Entdeckung befragten Stasi-Leute gaben an, der Apparat sei „höchstens zehnmal benutzt“ worden, seit einem Defekt 1983 dann nicht mehr – angeblich, so ein Stasi-Mann, „weil der bestellte Monteur bis zur Auflösung des MfS 1989 nicht gekommen“ sei.
Man konnte den Apparat auch von außen einschalten, und es war üblich, daß Strafgefangene allein im Fotoraum warten mussten. Dissident Auerbach erinnert sich noch genau, daß er einmal drei Stunden auf dem Stuhl sitzen musste – ohne daß jemand anders den Raum betrat. „Es gab recht häufig Fototermine, die sich meist eine Weile hinzogen, selbst kurz vor meiner Abschiebung 1983 saß ich auf dem Stuhl“, sagt auch der ehemalige Gera-Häftling Roland Jahn, Bürgerrechtler aus Jena.
Bei Sitzungen des „Runden Tischs“ und unter Stasi-Auflösern kursierten im Januar 1990 Berichte darüber, daß in den Fotoräumen anderer Haftanstalten zwar keine kompletten Geräte mehr zu finden seien, jedoch noch Reste: ein Sockel etwa, eine Bleiglasscheibe, ein Dosimeter.
Handfeste Belege gibt es dafür allerdings nicht – weder in Magdeburg noch in Berlin-Hohenschönhausen, wo Jürgen Fuchs neun Monate einsaß. Als er wegen seines Blutkrebses Strahlentherapie erhielt, erinnerten ihn die Nebenwirkungen an die „schlagartigen Gesundheitsveränderungen“ bei Stasi-Fototerminen, die ihn „körperlich reduzierten“. Damals habe er angeschnallt auf dem Stuhl gesessen und ein sehr lautes Lampengeräusch vernommen.
Alles Einbildung? Möglicherweise. Nur wurde im Mai 1990 hinter einem Vorhang im Regal des Fotoraums von Hohenschönhausen ein Lehrbuch für Strahlenkunde entdeckt.
Sehr konkret sind die Erinnerungen des Geraers Wolfgang Schatzberg an den Stasi-Knast in Chemnitz. Er durfte sich auf dem dortigen Fotostuhl nicht rühren: „Hinter mir gab es, kaum war ich allein, ein seltsames Geräusch. Ich traute mich zuerst nicht, dann hob ich den Vorhang etwas an und sah einen Röntgenapparat.“ Sein Schreck war groß, ihm dämmerte: „Das war gefährlich. Ich dreht mich von der Kante des Stuhles zum Boden hin, versuchte, meinen Kopf in Deckung zu bringen, wollte wenigstens aus dem Hauptstrahlenbereich heraus.“ Schatzberg hat inzwischen Strafanzeige erstattet.
Die Mitarbeiter der Magdeburger „Gedenkstätte Moritzplatz“ wollen es ihm jetzt nachtun. Ehemalige Insassen des dortigen Gefängnisses berichten, sie seien auffallend oft unmotiviert geröntgt worden. Eine weitere Strafanzeige ging bereits bei der Berliner Staatsanwaltschaft ein, vom Jenaer Maler Frank Rub. Der Freund und Mitstreiter von Fuchs erhofft sich etwa durch Untersuchungen der Räume in Gera und in Berlin-Hohenschönhausen neue Hinweise.
Daß es kaum Dokumente über mörderische „Zersetzungsmaßnahmen“ gab, hatte System, das belegt ein Stasi-Protokoll von 1988. Darin forderten Mitarbeiter freie Hand: Sie wollten die übliche Bürokratie umgehen, um keine Spuren zu hinterlassen. Es ging, so das Protokoll, „um die Orientierung, alles allein zu entscheiden, es darf keiner wissen, keine Hinweise auf Abstimmung/ Bestätigung“.
Daher wurde, so ein leitender Berliner MfS-Mann laut Protokoll, „entschieden, alle Aufzeichnungen/ Unterlagen zu vernichten“, denn: „Das Zeug musste weg.“ Ein anderer MfS-Offizier, spezialisiert auf die Bekämpfung von Bürgerrechtlern wie Ralf Hirsch und Roland Jahn, sagte, worum es ging: „Zum Beispiel hatten wir Gedankengänge, Ralf Hirsch, der viel trank, in einer strengen Winternacht Alkohol einzuflößen, daß er erfriert; weitere Vorstellungen an Zersetzungsmaßnahmen bestanden im Anbohren der Bremsleitung von Autos, in Paket enthaltene Flaschen was reinmischen.“
Dabei war den Stasi-Leuten etwa im Fall Hirsch (Operativvorgang „Blauvogel“) laut Protokoll „unklar, wie weit man bei Zersetzungsmaßnahmen gehen kann“, wenn schriftliche Genehmigungen und Unterschriften von Diensthöheren fehlen. „Es muß aber was gemacht werden“, so das Fazit der Offiziere, also: „Jeder macht etwas nach seinem Gefühl.“
Quelle: Der Spiegel, 20/ 1999, S. 42-44.
 |
STASI – Tödliche Strahlung – von Paul Leonhard
Was die wohl mit dem Zeug wollen? Vielleicht hat sich der Mann diese Frage einmal gestellt, sie aber dann als einen lästigen Gedanken beiseite gewischt. Schließlich war er als Gesellschaftlicher Mitarbeiter (GMS) auf das Ministerium für Staatssicherheit eingeschworen. Regelmäßig empfing Karl J., Leiter der Hauptabteilung Radioaktive Präparate des Zentralinstituts für Kernforschung Rossendorf, die Mielke-Männer und händigte ihnen die gewünschten radioaktiven Stoffe aus. Das war schließlich rechtens, in einem Vertrag geregelt, den die Stasi 1971 mit dem bei Dresden ansässigen Forschungszentrum geschlossen hatte. Es sei für ihn noch heute undenkbar, daß radioaktive Stoffe entgegen den gesetzlichen Bestimmungen an Menschen eingesetzt werden, sagt der inzwischen als Fachbereichsleiter in Rossendorf tätige J.
Bereits im Mai 1999 war das Kernforschungsinstitut in die Schlagzeilen geraten. Damals berichtete eine Boulevard-Zeitung über geheime Lieferungen. Wir haben Flüssigkeitspräparate-Kobalt 58, Scandium 46 in Zehn-Milliliter-Ampullen an die Stasi geliefert, bestätigte J. am 21. Mai gegenüber der Bild-Zeitung. Da stand der ungeheuerliche Verdacht bereits im Raum: Waren DDR-Dissidenten durch die Staatssicherheit heimlich verstrahlt worden? Der Spiegel hatte über entsprechende Hinweise berichtet und der Jenaer Maler Frank Rub Strafanzeige bei der Berliner Staatsanwaltschaft gestellt. Auslöser war der Tod seines Freundes, des Regimegegners und Schriftstellers Jürgen Fuchs. Dieser war Anfang Mai 1999 im Alter von 48 Jahren einem Plasmozytom erlegen, einer seltenen Blutkrebsart, die durch Strahlung verursacht werden kann.
Bürgerrechtler fordern seit Jahren Aufklärung
Jürgen Fuchs hegte die Vermutung, daß seine tödliche Krankheit nicht gottgewollt war, sondern menschengemacht, erinnerte sein Freund Wolf Biermann. Ein Mord auf Raten? Den Verdacht, Fuchs und andere Dissidenten seien im berüchtigten Stasi-Knast Berlin-Hohenschönhausen mit Röntgenstrahlen traktiert worden, äußerten mehrere ehemalige Bürgerrechtler. Seit einem Jahr fordern sie rückhaltlose Aufklärung.
Zu den bald ermittelten Spuren gehörte ein unorthodox konstruiertes Röntgengerät, das Mitglieder eines Bürgerkomitees Ende Dezember 1989 im Stasi-Untersuchungsgefängnis Gera entdeckt hatten. Die Strahlenkanone stand hinter einem Vorhang versteckt im Fotoraum der Anstalt. Der Strahler habe sich etwa in Kopfhöhe des davor sitzenden Gefangenen befinden, erinnern sich Zeugen. Ähnliche Geräte gab es auch im Magdeburger, Chemnitzer und Bautzner Stasi-Knast. In Hohenschönhausen wurde 1990 im Fotoraum ein verstecktes Lehrbuch für Strahlenkunde entdeckt.
In seinem Schlüsselroman “Magdalena” hatte Jürgen Fuchs aus einer Veröffentlichung der Stasi-nahen Sektion Kriminalistik der Humboldt-Universität Berlin zitiert. Da ging es um radioaktive Gifte und darum, wie man diese spurlos gegen Menschen einsetzen kann. Nach Fuchs’ Tod gewann das Thema auch deswegen Brisanz, weil bereits im Mai 1998 Gerulf Pannach (48), früherer Liedermacher und Texter der DDR-Rockband Renft, an Nierenkrebs, und ein Jahr zuvor der Regimegegner Rudolf Bahro (61), Verfasser des Buches “Die Alternative”, an einem Non-Hodgkin-Lymphom gestorben waren. Alle drei hatten 1976/77 in Hohenschönhausen gesessen.
Wurden mißliebige Häftlinge im Rahmen von MfS-Zersetzungsmaßnahmen mittels Strahlenkanone unbemerkt verseucht, um ihnen langfristig Schaden zuzufügen? Es gibt zwar keine Beweise, dafür aber genug Indizien.
Mielkes Männer experimentierten nachweislich seit den siebziger Jahren mit strahlenden Substanzen. Akten beweisen, daß sie im Umgang mit Radionukliden und nichtmedizinischer Röntgentechnik ausgebildet wurden. Eine ganze Liste besonders gefährlicher Substanzen ist beispielsweise im Jahresplan 1979 des Dienstbereiches 2 unter der Rubrik “Schädigung durch Beibringen radioaktiver Stoffe” aufgelistet. Auch an der Anwendung radioaktiver Isotope arbeiteten die Stasi-Experten.
Eine über 900 Seiten starke Studie der Humboldt-Universität unter dem Titel “Toxdat” führt jede erdenkliche Art auf, wie Menschen mit Gift umgebracht werden können. Die für die Stasi entstandene Ausarbeitung aus dem Jahr 1988 nennt mehr als 200 toxische und strahlende Substanzen und beschreibt detailliert, wie diese eingesetzt werden könnten. Im Kapitel “Schädigung durch Beibringung radioaktiver Stoffe” werden besonders gefährliche Radionuklide genannt: von Strontium-90 bis Plutonium-238, aber auch Mikromengen abgebrannter Brennstäbe aus Kernkraftwerken.
Aus den Papieren erfuhren die Geheimdienstler, welche Wirkung ein Einsatz dieser Stoffe beim Menschen hätte. Von einer kombinierten Schädigung war die Rede. Der biologische Effekt resultiere aus einem chemischen Gift und einer physikalischen Wirkung. Beigebracht in Speisen und Getränken könnten sie zu Siechtum führende Blut-/Knochenmarkschäden und Krebs bewirken. Das sei natürlich abhängig gewesen von der psycho-physischen Reaktion der Einzelperson, sagte Fuchs in einem Interview, in dem er die Möglichkeit einschloß, daß durch Strahlung gesundheitliche Schäden verursacht werden können, nicht bei allen Gefangenen, aber bei denen, von denen man glaubt, es machen zu müssen, zu sollen, zu dürfen, auf Befehl. Die Wissenschaftler der Humboldt-Uni nannten das eine Liquidationsmethode mit hohem Verschleierungspotential durch spät einsetzende unspezifische Initialsymptomatik.
Mielke-Ministerium wollte Strahlenunfälle herbeiführen
Fuchs selbst waren Dokumente in die Hände gefallen, in denen ein handliches Gamma-Gert polnischer Herkunft eine Rolle spielte, das punktförmig Neutronenstrahlen aussendet. Sein Einsatz, bei dem das biologische Gewebe beschädigt wurde, hinterließ keine Spuren, später würde es diffuse, aber bedrohliche Erkrankungen erzeugen. Experten bestätigen inzwischen, daß die Strahlendosis der Röntgengeräte in den Stasi-Gefängnissen bei einstündiger Bestrahlung 1,1 Gray betragen haben könnte. Damit wären die Geräte zwar viel zu schwach, um einen Menschen zu töten, aber die möglichen Strahlendosen hätten ausgereicht, um nach einigen Jahren bei den Opfern Blutkrebs auszulösen.
Die Stasi beschäftigte sich ebenfalls mit Möglichkeiten, kleine Atomminen in Westdeutschland einzusetzen und Kernkraftwerke zu beschädigen, um Strahlenunfälle herbeizuführen. Erst im vergangenen Jahr stieß die Gauck-Behörde auf Unterlagen der Stasi-Abteilung Operativ-Technischer Sektor. Damit war der Beweis erbracht, daß das Mielke-Ministerium mit dem Einsatz radioaktiven Materials experimentierte, um alles mögliche zu überwachen.
Grundlage dafür bot die Kooperation mit den Kernforschern in Rossendorf. Hier fanden die Bestrahlungen im Reaktor statt. Hier wurden Stoffe aktiviert wie Stecknadeln, die später Regimegegnern an die Kleidung geheftet wurden. Einem der Stasi verdächtigen Physiker im Kombinat Carl Zeiss Jena wurden 1978 radioaktiv präparierte Dokumente untergeschoben. Manuskripte von Bürgerrechtlern wurden mit flüssigem nuklearen Material beschichtet. Auch wurden Autos markiert, indem per Luftgewehr radioaktive Munition auf die Reifen geschossen wurde. Man überlegte, wie man Personen bespritzen könnte, um sie später wiederzufinden, beschrieb Joachim Gauck, Leiter der Stasi-Akten-Behörde, in einem Interview die Methoden. Fest steht, daß das Manuskript von Bahros “Alternative” radioaktiv markiert wurde. Die Stasi wollte so den Versandwegen nachspüren und Adressaten ausfindig machen.
Aber nicht nur gegen Dissidenten wurden radioaktive Stoffe eingesetzt. So verschickte die Stasi in einem Fall radioaktiv-markiertes Westgeld, um herauszufinden, wer in einem Postamt aus Briefen Geldscheine stiehlt. Wenn jemand drei dieser Scheine einsteckte, konnte das durchaus gesundheitliche Folgen haben, schätzt Gauck ein.
Insgesamt hat es in den siebziger Jahren hundert Markierungsfälle jährlich gegeben. In den achtziger Jahren sind es 50. Die Stasi benutzte 21 verschiedene Substanzen von Caesium-137 bis zu Kobalt-59 oder Silber-110. Erschreckend sei, daß beteiligte Wissenschaftler bis heute schweigen würden und einen guten Ruf hätten, sagte Gauck im März. Diese Spezialisten hätten aber der Stasi in Kenntnis möglicher Gesundheitsgefahren geholfen. Zwar gibt es bisher nach Aussage Gaucks keinen Beweis, der den schlimmen Verdacht bewußter radioaktiver Bestrahlung in Haftanstalten bestätigt, aber unter dem Decknamen “Wolke” setzten die Mielke-Leute radioaktive Substanzen zur Markierung von Personen und Gegenständen ein. Gesundheitliche Schäden wurden dabei billigend in Kauf genommen. Ein Markierungseinsatz konnte den heute geltenden Grenzwert um das 267fache überschreiten, ermittelte ein im Auftrag der Gauck-Behörde tätiger Gutachter.
Vorwürfe von Fuchs an die bundesdeutsche Justiz
Die Aktionen überschritten selbst die Sicherheitsnormen der DDR. Auch im Fall des Geraer Röntgengerätes, das zumindest zwischen 1976 und 1983 im Stasi-Knast eingesetzt wurde und nach der Wende spurlos verschwand. Es verstieß schon dadurch gegen die DDR-Gesetze, daß es nicht beim Amt für Strahlenschutz gemeldet war.
Man habe die Bedeutung von Zersetzung nicht begriffen, warf Fuchs kurz vor seinem Tod der BRD-Justiz vor. Es werde nicht wahrgenommen, daß ein System wie das der DDR mit einer historischen Mission in Andersdenkenden ideologische Feinde sah, bei deren Ausschaltung jedes Mittel vom Zweck geheiligt ist. Ein Betroffener ist vielleicht in der Lage, die letzten, die allerletzten Beweise zu bringen, wenn er gestorben ist und eine Knochenanalyse vorgenommen wird, sagte er bezüglich der Nachforschungen für den Einsatz radioaktiver Stoffe in den Haftanstalten.
Wie vor den Kopf geschlagen zeigt sich angesichts der jüngsten Enthüllungen auch der Rossendorfer Kernforscher J.: Eine Anwendung an Menschen, die nicht der medizinischen Diagnose oder Therapie dient, verurteile er mit aller Schärfe.
DDR-Regimegegner Rudolf Bahro: Das Manuskript seines Buches “Die Alternative” wurde von der Stasi radioaktiv verstrahlt
von Paul Leonhard
TOP-SECRET-American Nazi Party E-Mails hacked
A sends:
Remember the idiot bloggers saying “Nazis throw support at OWS”? They were talking about these guys, all they did was tweet.
http://antiracistaction.org/?q=node%2F149#tehemails
http://nsoldguard.blogspot.com/
Mirror to the zip archive download
http://www.multiupload.com/3VCKPO4XZ0
http://www.uploadhere.com/XEXKAGN47N
http://depositfiles.com/files/5b551f4od
http://www.uploadking.com/7LV3SDZ5OT
http://www.filesonic.fr/file/4127147645/john.t.bowles.anp.hacked.emails.zip
http://www.wupload.fr/file/2608826227/john.t.bowles.anp.hacked.emails.zip
http://www.megaupload.com/?d=8UAI6DDL
http://hotfile.com/dl/136974593/4e3b161/john.t.bowles.anp.hacked.emails.zip.html
CONFIDENTIAL – Russia Has Lost More Than $500 Billion to Illicit Money Outflows Since 2000
Capital flight from Russia, already at $64 billion this year, is likely to intensify in coming months as a weak showing by Prime Minister Vladimir Putin’s United Russia party in parliamentary elections heightens political uncertainty, economists said.The net capital outflow, blamed on European banks and wealthy Russians concerned about a government shake-up, is now expected to exceed $85 billion in 2011, acting Finance Minister Anton Siluanov said late Monday.
The bearish forecast came as Fitch Ratings warned about political uncertainty in Russia, a day after voting ended in the Duma election, with Putin’s United Russia getting less than 50% of the vote. Mr. Putin on Tuesday said he sees “serious and substantial renewals” in government personnel after presidential elections set for March of next year–which he is still expected to win handily.
“People at the moment don’t have an idea which officials will be around next year and who will be gone,” said Julia Tsepliaeva, chief economist at BNP Paribas in Moscow. “If you’re a businessman or a company that has an arrangement with a certain bureaucrat, this lack of clarity may lead you to move capital abroad.”
The exodus of capital this year has weighed on the ruble, which has weakened by more than 15% from its peak this year, even as the average price for Russia’s oil this year is higher than ever before. UniCredit SpA’s Moscow unit sent at least $5.5 billion abroad in the third quarter through loans to non-Russian banks, including other units of UniCredit, as European lenders sought additional liquidity amid a debt scare linked to Greece and other euro-zone nations. Politics aside, a steep drop in oil prices or a worsening of the debt crisis in Europe could suck even more cash out of Moscow.
NEW – UNCESONDERD – FEMEN – Dnepr
VORSICHT ! STASI ! Juricon über “GoMoPa”
TOP-SECRET from the FBI – Identity Thief Sentenced in Virginia to 12 Years in Prison for Managing East Coast Credit Card Fraud Ring
WASHINGTON—A Brooklyn, N.Y., man was sentenced today in U.S. District Court in Alexandria, Va., to 12 years in prison for operating a credit card fraud ring that used counterfeit credit cards encoded with stolen account information up and down the East Coast of the United States, announced Assistant Attorney General Lanny A. Breuer of the Criminal Division and U.S. Attorney Neil H. MacBride for the Eastern District of Virginia.
Jonathan Oliveras, 26, was sentenced by U.S. District Judge Gerald Bruce Lee. In addition to his prison term, Oliveras was ordered to forfeit $770,646 and to serve three years of supervised release. Oliveras pleaded guilty on Aug. 10, 2011, to one count of wire fraud and one count of aggravated identity theft.
In his plea, Oliveras admitted that he managed a ring of co-conspirators who used stolen credit card account information in New York, New Jersey and the Washington, D.C., area. According to court documents, Oliveras sent payments to individuals he believed to be in Russia for the stolen account information. Oliveras then distributed the stolen account information, which was re-encoded onto plastic cards and used to purchase gift cards. The gift cards were used to buy merchandise that ultimately was returned for cash.
Federal and local law enforcement executing a search warrant in July 2010 at Oliveras’ apartment found, among other things, credit card encoding equipment and more than 2,300 stolen credit card numbers. According to court documents, credit card companies have identified thousands of fraudulent transactions using the account numbers found in Oliveras’ possession, totaling more than $750,000.
The case was prosecuted by Michael Stawasz, a Senior Counsel in the Criminal Division’s Computer Crime & Intellectual Property Section and Special Assistant U.S. Attorney in the Eastern District of Virginia, and Assistant U.S. Attorney Ryan Dickey of the U.S. Attorney’s Office for the Eastern District of Virginia. The case was investigated jointly by the Washington Field Offices of both the U.S. Secret Service and the FBI, with assistance from the New York and New Jersey Field Offices of both agencies.
UNCENSORED – Topless in Vatican: FEMEN strips against ‘Catholic witch-hunt’
UNCENSORED – Russia Protest Photos
|
11 December 2011 |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict80.jpg) http://varlamov.me/img/–/planeta_miting.jpg http://varlamov.me/img/–/planeta_miting.jpg |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict69.jpg) Russian nationalists hold a banner reads as “All for one and one for all” and wave old Russian imperial flags during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko) Russian nationalists hold a banner reads as “All for one and one for all” and wave old Russian imperial flags during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict70.jpg) Russian nationalists rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko) Russian nationalists rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict68.jpg) Russian nationalists shout holding old Russian imperial flags during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko) Russian nationalists shout holding old Russian imperial flags during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict78.jpg) A young masked Russian nationalist holds a banner in front of a police officer during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko) A young masked Russian nationalist holds a banner in front of a police officer during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict76.jpg) Russian police troops patrol near closed Red Square, with St. Basil Cathedral at the background, in Moscow, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Misha Japaridze) Russian police troops patrol near closed Red Square, with St. Basil Cathedral at the background, in Moscow, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Misha Japaridze)
|
|
10 December 2011 |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict64.jpg) In this photo taken Saturday, Dec. 10, 2011, protesters gather to protest near the Kremlin, background, against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia. Tens of thousands of people held the largest anti-government protests that post-Soviet Russia has ever seen to criticize electoral fraud and demand an end to Vladimir Putin’s rule. (Dmitriy Chistoprudov) In this photo taken Saturday, Dec. 10, 2011, protesters gather to protest near the Kremlin, background, against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia. Tens of thousands of people held the largest anti-government protests that post-Soviet Russia has ever seen to criticize electoral fraud and demand an end to Vladimir Putin’s rule. (Dmitriy Chistoprudov) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict65.jpg) In this photo taken Saturday, Dec. 10, 2011, protesters gather to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia. Tens of thousands of people held the largest anti-government protests that post-Soviet Russia has ever seen to criticize electoral fraud and demand an end to Vladimir Putin’s rule. (Dmitriy Chistoprudov) In this photo taken Saturday, Dec. 10, 2011, protesters gather to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia. Tens of thousands of people held the largest anti-government protests that post-Soviet Russia has ever seen to criticize electoral fraud and demand an end to Vladimir Putin’s rule. (Dmitriy Chistoprudov) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict38.jpg) Police cars and trucks block a square where demonstrators gather together during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. Police cars and trucks block a square where demonstrators gather together during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict27.jpg) Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin) Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict26.jpg) Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr) Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict45.jpg) Protesters hold a red banner reads as “Rot Front” shouting anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011, with the Kremlin is the background. Russians angered by allegedly fraudulent parliamentary elections and the country’s ruling party took part in protests Saturday in cities from the freezing Pacific Coast to the southwest, eight time zones away. Protesters hold a red banner reads as “Rot Front” shouting anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011, with the Kremlin is the background. Russians angered by allegedly fraudulent parliamentary elections and the country’s ruling party took part in protests Saturday in cities from the freezing Pacific Coast to the southwest, eight time zones away. |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict44.jpg) A protester holds an old Russian flag with the words “We are Russians, God with us” and shows a V-sing during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011, with the Kremlin is the background. Russians angered by allegedly fraudulent parliamentary elections and the country’s ruling party took part in protests Saturday in cities from the freezing Pacific Coast to the southwest, eight time zones away. A protester holds an old Russian flag with the words “We are Russians, God with us” and shows a V-sing during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011, with the Kremlin is the background. Russians angered by allegedly fraudulent parliamentary elections and the country’s ruling party took part in protests Saturday in cities from the freezing Pacific Coast to the southwest, eight time zones away. |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict24.jpg) Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr) Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict40.jpg) People stand on the bridge as they attend a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. The banner on the bridge reads: “Crooks Give Us the Election Back.” People stand on the bridge as they attend a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. The banner on the bridge reads: “Crooks Give Us the Election Back.” |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict29.jpg) Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko) Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict25.jpg) Protesters shout anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr) Protesters shout anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict41.jpg) Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel) Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict34.jpg) Protesters light flares during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin) Protesters light flares during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict48.jpg) Demonstrators stand in front of police line during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel) Demonstrators stand in front of police line during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict43.jpg) Opposition leader Edouard Limonov shouts anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. Opposition leader Edouard Limonov shouts anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict50.jpg) An elderly demonstrator holds a poster showing an edited photo of Prime Minister Vladimir Putin and signed “2050. No” during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. An elderly demonstrator holds a poster showing an edited photo of Prime Minister Vladimir Putin and signed “2050. No” during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict47.jpg) Protesters listen to an orator during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.(Alexander Zemlianichenko Jr) Protesters listen to an orator during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.(Alexander Zemlianichenko Jr) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict36.jpg) Protesters seen during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Sergey Ponomarev) Protesters seen during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Sergey Ponomarev) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict35.jpg) Masked protesters seen during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin) Masked protesters seen during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict32.jpg) A protester shouts slogans in front of police line during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel) A protester shouts slogans in front of police line during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict37.jpg) Protesters light flares holding an Old Russian flags during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Name) Protesters light flares holding an Old Russian flags during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Name) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict39.jpg) Police guards the Red Square area during a mass protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Sergey Ponomarev) Police guards the Red Square area during a mass protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Sergey Ponomarev) |
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict28.jpg) Police vehicles seen on a Zamoskvoretsky bridge during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.(Ivan Sekret) Police vehicles seen on a Zamoskvoretsky bridge during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.(Ivan Sekret) |
CONFIDENTIAL – DHS TRIPwire Domestic IED OSINT Report October 2011
The following is an example of a monthly report released through the Department of Homeland Security’s TRIP program that documents bomb threats and other incidents related to the domestic use of improvised explosive devices. The report is compiled from open source information gathered around the country. The reports are not released publicly.



DOWNLOAD ORIGINAL DOCUMENT HERE
FBI-Alleged Terrorist Indicted in New York for the Murder of Five American Soldiers
NEW YORK—Today, a federal grand jury in Brooklyn, N.Y., returned an indictment charging Faruq Khalil Muhammad ‘Isa, 38, aka “Faruk Khalil Muhammad ‘Isa,” “Sayfildin Tahir Sharif” and “Tahir Sharif Sayfildin,” with aiding in the murder of five American soldiers in a suicide-bomb attack in Iraq in April 2009.
Specifically, he is charged with the murders of Staff Sergeant Gary L. Woods, 24, of Lebanon Junction, Ky.; Sergeant First Class Bryan E. Hall, 32, of Elk Grove, Calif.; Sergeant Edward W. Forrest Jr., 25, of St. Louis; Corporal Jason G. Pautsch, 20, of Davenport, Iowa; and Army Private First Class Bryce E. Gaultier, 22, from Cyprus, Calif.
The indictment also charges the defendant with conspiring to kill Americans abroad and providing material support to that terrorist conspiracy to kill Americans abroad.
In January 2011, the defendant was arrested and detained in Canada after he was charged by a federal complaint in the Eastern District of New York. The United States is seeking the defendant’s extradition from Canada in relation to the federal complaint in the Eastern District of New York. He remains in custody, and the defendant’s extradition hearing in Canada is currently scheduled for Jan. 30 to Feb. 1, 2012.
The charges were announced by Loretta E. Lynch, U.S. Attorney for the Eastern District of New York; Lisa Monaco, Assistant Attorney General for National Security; and Janice K. Fedarcyk, Assistant Director in Charge of the New York Field Office of the FBI.
The government’s investigation is being conducted by the FBI New York Joint Terrorism Task Force, with assistance provided by the Department of Defense, the Royal Canadian Mounted Police and the government of Tunisia.
If convicted, the defendant faces a maximum sentence of life in prison.
The government’s case is being prosecuted by Assistant U.S. Attorneys Zainab Ahmad, Carter H. Burwell and Berit W. Berger, with assistance provided by Mary Futcher and Stephen Ponticiello of the Counterterrorism Section in the Department of Justice’s National Security Division. The Criminal Division’s Office of International Affairs also provided assistance in this matter.
The charges in the indictment are merely allegations, and the defendant is presumed innocent unless and until proven guilty.
SCRET-JFIIT Intelligence Surveillance and Reconnaissance (ISR) Systems Handbook

The purpose of the JFIIT Tactical Leaders Handbook (version 5) is to provide ground maneuver commanders, battle staffs, and soldiers with information regarding Joint Intelligence, Surveillance, and Reconnaissance (ISR) and attack systems and how to leverage these combat multipliers during planning, preparation, and execution of military operations. JFIIT publishes a classified version of this document on the SIPRNET. The For Official Use Only (FOUO) Web version can be located at the NIPRNET address listed below.





DWONLOAD ORIGINAL DOCUMENT HERE
The FBI-Mafia Family Fraud The Case of the Stolen Company
It’s a criminal’s dream—owning a financial company that can be looted at will. That’s just what 13 individuals—including two with ties to organized crime families—are accused of in a federal indictment announced last month in New Jersey.
Among those charged in the 25-count indictment is Nicodemo Scarfo—a member of the Lucchese crime family and son of Nicodemo Scarfo Sr., the imprisoned former boss of the Philadelphia La Cosa Nostra (LCN) crime family. Also charged were Salvatore Pelullo—an associate of the Lucchese and Philadelphia LCN families—and 11 others…all in connection with an alleged criminal takeover of FirstPlus Financial Group (FPFG), a publicly held company based in Texas. The takeover resulted in honest FPFG shareholders losing at least $12 million; the company ultimately filed for bankruptcy.
The group was charged with various crimes in connection with this racketeering conspiracy, including securities fraud; wire, mail, and bank fraud; extortion; money laundering; and obstruction of justice. In addition to Scarfo and Pelullo, other members of the criminal enterprise included five attorneys, a certified public accountant, and Scarfo’s wife.
How did they do it? According to the indictment, members of the criminal enterprise devised a plan in 2007 to take over FPFG by replacing its board of directors and management with individuals who would serve at the direction of Scarfo and Pelullo. To accomplish this, they allegedly accused board members of financial improprieties that, if brought to light, would result in costly lawsuits. Eventually, through threats and intimidation, every member of the board and executive management left.
After gaining control of the company, the looting began:
- The new board approved the acquisition of “companies” owned by Scarfo and Pelullo for millions of dollars and several hundred thousand shares of FPFG stock—except that these companies were really nothing more than shell corporations and had virtually no value. Proceeds from the sale of the companies ended up in the pockets of the criminal conspirators.
- The new board also approved a number of “consulting” agreements for hundreds of thousands of dollars. This consulting work was never performed, and the proceeds went to the criminals.
Scarfo and Pelullo allegedly purchased items like expensive homes, luxury vehicles, yachts, and jewelry. And like any good mob soldiers, they also allegedly purchased weapons.
Since FPFG was a public company, it was obligated to file reports with the Securities and Exchange Commission (SEC). The indictment alleges that, in order to conceal the involvement of former felons Scarfo and Pelullo in the company, their henchman at FPFG filed fraudulent paperwork. Scarfo is also accused of concealing his involvement in FPFG from his probation officer—at the time of the scheme, he had been released from prison and was under federal supervision.
In addition, the indictment alleges that the Scarfo-Pelullo conspiracy was operated with the assistance and direction of members and associates of La Cosa Nostra and that some of the financial proceeds from the scheme ended up in the hands of the LCN.
This multi-year investigation was very complex and required not only using sensitive investigative techniques, but also carefully analyzing voluminous financial records and following the money trail through various financial accounts. And we didn’t do it alone—we worked with the Department of Labor’s Inspector General; the Bureau of Alcohol, Tobacco, Firearms, Explosives; and the SEC.
UNCENSORED – FEMEN – A PORTRAIT
OPFER ÜBER DIE PLEITE-FIRMEN DER FINGIERTEN SCHEISSHAUSFLIEGEN-“GoMoPa” (Eigenbezeichnung) SEIT JAHREN INSOLVENT
TOP-SECRET-U.S. Army Taliban Insurgent Syndicate Intelligence Operations Report
TOP-SECRET-(U//FOUO) Asymmetric Warfare Group Afghan Key Leader Engagement (KLE) Reference Card
CONFIDENTIAL-Council of Europe Committee of Ministers Declaration in Support of Whistleblowing Websites
December 9, 2011 in Council of Europe
The following statement was released on December 7, 2011 by the Council of Europe Committee of Ministers.
Declaration of the Committee of Ministers on the protection of freedom of expression and freedom of assembly and association with regard to privately operated Internet platforms and online service providers
(Adopted by the Committee of Ministers on 7 December 2011 at the 1129th meeting of the Ministers’ Deputies)
1. Freedom of expression and the right to receive and impart information and its corollary, freedom of the media, are indispensable for genuine democracy and democratic processes. Through their scrutiny and in the exercise of their watchdog role, the media provide checks and balances to the exercise of authority. The right to freedom of expression and information as well as freedom of the media must be guaranteed in full respect of Article 10 of the European Convention on Human Rights (ETS No. 5, hereinafter “the Convention”). The right to freedom of assembly and association is equally essential for people’s participation in the public debate and their exercise of democratic citizenship, and it must be guaranteed in full respect of Article 11 of the Convention. All Council of Europe member States have undertaken, in Article 1 of the Convention, to “secure to everyone within their jurisdiction the rights and freedoms” protected by the Convention (without any online/offline distinction).
2. People, notably civil society representatives, whistleblowers and human rights defenders, increasingly rely on social networks, blogging websites and other means of mass communication in aggregate to access and exchange information, publish content, interact, communicate and associate with each other. These platforms are becoming an integral part of the new media ecosystem. Although privately operated, they are a significant part of the public sphere through facilitating debate on issues of public interest; in some cases, they can fulfil, similar to traditional media, the role of a social “watchdog” and have demonstrated their usefulness in bringing positive real-life change.
3. In addition to opportunities, there are challenges to the effective exercise of freedom of expression and to the right to impart and receive information in the new media ecosystem. Direct or indirect political influence or pressure on new media actors may lead to interference with the exercise of freedom of expression, access to information and transparency, not only at a national level but, given their global reach, also in a broader international context. Decisions concerning content can also impinge on the right to freedom of assembly and association.
4. Distributed denial-of-service attacks against websites of independent media, human rights defenders, dissidents, whistleblowers and other new media actors are also a matter of growing concern. These attacks represent an interference with freedom of expression and the right to impart and receive information and, in certain cases, with the right to freedom of association. Companies that provide web hosting services lack the incentive to continue hosting those websites if they fear that the latter will come under attack or if their content may be regarded as sensitive. Furthermore, the companies concerned are not immune to undue interference; their decisions sometimes stem from direct political pressure or from politically motivated economic compulsion, invoking justification on the basis of compliance with their terms of service.
5. These developments illustrate that free speech online is challenged in new ways and may fall victim to action taken by privately owned Internet platforms and online service providers. It is therefore necessary to affirm the role of these actors as facilitators of the exercise of the right to freedom of expression and the right to freedom of assembly and association.
6. Interference with content that is released into the public domain through these means or attempts to make entire websites inaccessible should be judged against international standards designed to secure the protection of freedom of expression and the right to impart and receive information, in particular the provisions of Article 10 of the Convention and the related case law of the European Court of Human Rights. Furthermore, impediments to interactions of specific interest communities should be measured against international standards on the right to freedom of assembly and association, in particular the provisions of Article 11 of the Convention and the related case law of the European Court of Human Rights.
7. The Committee of Ministers, therefore:
– alerts member States to the gravity of violations of Articles 10 and 11 of the European Convention on Human Rights which might result from politically motivated pressure exerted on privately operated Internet platforms and online service providers, and of other attacks against websites of independent media, human rights defenders, dissidents, whistleblowers and new media actors;
– underlines, in this context, the necessity to reinforce policies that uphold freedom of expression and the right to impart and receive information, as well as the right to freedom of assembly and association, having regard to the provisions of Articles 10 and 11 of the Convention and the related case law of the European Court of Human Rights;
– confirms its commitment to continue to work to address the challenges that these matters pose for the protection of freedom of expression and access to information.
VIDEO – FEMEN DSK PARIS
Wkipedia entry – https://en.wikipedia.org/wiki/FEMEN
FEMEN (Ukrainian:Фемен) is a Ukrainian protest group based in Kiev, founded in 2008. The organisation became internationally known for organizing topless protests against sex tourists, international marriage agencies, sexism and other social, national and international ills.[1][4][5][6][7][8][9] Some of the goals of the organisation are: “To develop leadership, intellectual and moral qualities of the young women in Ukraine” and “To build up the image of Ukraine, the country with great opportunities for women”.[3]
|
|
The organisation
Female university students between 18 and 20 years old form the backbone of the movement.[2] In Kiev, there are about 300 active participants in the movement.[10] There are few male members of FEMEN.[1] The group comprises some 20 topless activists and 300 fully clothed members.[11][12] Most of its demonstrations are staged in Kiev,[4][8] but FEMEN has also held actions in cities like Odessa,[13] Dnipropetrovsk[14] and Zaporizhia.[15] While most of the protests have been ‘topless’ in 2010 one FEMEN protester exposed her buttocks outside a locked toilet in a demonstration to protest about the lack of public toilets in Kiev.[11]
The goals of the organization is “to shake women in Ukraine, making them socially active; to organize in 2017 a women’s revolution.”[10] The group has stated it has enjoyed limited success in pushing its agenda.[16] As of late April 2010 the organisation is contemplating becoming a political party to run for seats in the next Ukrainian parliamentary election.[1][10]
FEMEN justifies its provocative methods stating “This is the only way to be heard in this country. If we staged simple protests with banners, then our claims would not have been noticed”.[17] The organisation plans to become the biggest and the most influential feminist movement in Europe.[3][10]
Some members claim their involvement in FEMEN caused their families to become alienated from them.[10][18]
FEMEN receives small financial backing by individuals[10][11][19] (including DJ Hell[18]).
Facebook initially blocked the FEMEN page because it suspected it was pornographic.[18]
Late April 2011 the organization claimed it was setting up international branches in Warsaw, Zurich, Rome, Tel Aviv and Rio de Janeiro.[20][21] They also claimed that after the early 2010 election of President Viktor Yanukovych the Security Service of Ukraine has attempted to intimidate the FEMEN activists.[18]
FEMEN occasionally holds rallies outside Ukraine.[22][23][24][25]

FEMEN protest in Kiev during the 2010 Ukrainian presidential election
The movement was founded in 2008 by Anna Hutsol (born 1983, most FEMEN members are younger[2]) after she became attuned to the sad stories of Ukrainian woman duped by false promises from abroad:[2] “I set up FEMEN because I realised that there was a lack of women activists in our society; Ukraine is male-oriented and women take a passive role.”[26] Since then the organization has staged noticeable erotically-flavored rallies (among others) near the building of the Cabinet of Ministers, at Maidan Nezalezhnosti, the Turkish embassy in Ukraine[2] and in front of the Iranian embassy to oppose the expected execution of Sakineh Mohammadi Ashtiani.[27]
Hutsol is adamantly opposed to legalizing prostitution in Ukraine.[2] FEMEN proposed the introduction of criminal responsibility for the use of sex industry services late in May 2009.[28]
A demonstration by a group called RU FEMEN in the Russian capital Moscow late April 2011[29] was immediately denounced as a fake offspring of FEMEN.[20][21] FEMEN accused Russian political party United Russia of having set up this RU FEMEN.[20][21]
Cultural and political image
FEMEN’s actions received criticisms in Ukraine for “being meaningless” or “being outright tasteless”.[11] According to Ukrainian gender studies expert Tetyana Bureychak most Ukrainian women are unimpressed by FEMEN.[30] According to sociologist Oleh Demkiv of the Lviv University FEMEN does not enjoy popular support.[31]
According to Reuters “Femen represents — albeit on a modest scale — one of the few regular street protest movements”.[12] In Ukraine the FEMEN activists have been labeled “girls Tymoshenko” and/or “Putin‘s agents[10][relevant? – discuss]; some parents of FEMEN activists have wondered if they were addicted to drugs.[10] But the organization claims to be an independent organization “Beyond politics and beyond religion”.[10]
The group’s actions have been reported in news-outlets such as CNN, BBC News,[6] Der Spiegel, Die Welt, Independent.ie,[3] France 24,[26] on Euronews,[27] Kyiv Post,[32] Mizozo,[33] USA Today,[34] Reuters[12] and The Washington Post.
PERVERS – DIE METHODEN DER ANAL-FIXIERTEN “GoMoPa”-SCHEISSHAUS-FLIEGEN (EIGENBEZEICHNUNG)
DIE FÄLSCHER – Meridian Capital about GoMoPa STASI-FÄLSCHUNGEN DER “GoMoPa”
OPFER IM FOKUS – DIE LISTE DER OPFER DER “GoMoPa”-STASI-Stalker
Warnung vor STASI-“GoMoPa”-Trojaner Facebook
NEW-TOP-SECRET – White House Strategic Plan for Preventing Violent Extremism

aw enforcement and government officials for decades have understood the critical importance of building relationships, based on trust, with the communities they serve. Partnerships are vital to address a range of challenges and must have as their foundation a genuine commitment on the part of law enforcement and government to address community needs and concerns, including protecting rights and public safety. In our efforts to counter violent extremism, we will rely on existing partnerships that communities have forged with Federal, State, and local government agencies. This reliance, however, must not change the nature or purpose of existing relationships. In many instances, our partnerships and related activities were not created for national security purposes but nonetheless have an indirect impact on countering violent extremism (CVE).
At the same time, this Strategic Implementation Plan (SIP) also includes activities, some of them relatively new, that are designed specifically to counter violent extremism. Where this is the case, we have made it clear. It is important that both types of activities be supported and coordinated appropriately at the local level.
…
Current Activities and Efforts
The Federal Government has held a series of consultative meetings with communities, local government and law enforcement, civil society organizations, foundations, and the private sector to better understand how it can facilitate partnerships and collaboration. This leverages a key strength identified in the National Strategy for Empowering Local Partners: “The Federal Government, with its connections to diverse networks across the country, has a unique ability to draw together the constellation of previously unconnected efforts and programs to form a more cohesive enterprise against violent extremism.” Examples of this include the following:
- DHS Secretary Napolitano tasked her Homeland Security Advisory Council (HSAC) to develop recommendations on how the Department can best support law enforcement and communities in their efforts to counter violent extremism. An HSAC CVE Working Group convened multiple meetings with local law enforcement, local elected officials, community leaders (including faith-based leaders), and academics. The working group released its recommendations in August 2010, highlighting the importance of: (1) research and analysis of violent extremism; (2) engagement with communities and leveraging existing partnerships to develop information-driven, community-based solutions to violent extremism and violent crime; and (3) community oriented policing practices that focus on building partnerships between law enforcement and communities.
- DHS and NCTC began raising awareness about violent extremism among private sector actors and foundations and connected them with community civic activists interested in developing programs to counter violent extremism. DHS is now working with a foundation to pilot resiliency workshops across the country that address all hazards, including violent extremism.
We also began exploring how to incorporate CVE as an element of programs that address broader public safety, violence prevention, and resilience issues. This has the advantage of leveraging preexisting initiatives and incorporates CVE in frameworks (such as safeguarding children) used by potential local partners who may otherwise not know how they fit into such efforts. For example, although many teachers, healthcare workers, and social service providers may not view themselves as potentially contributing to CVE efforts, they do recognize their responsibilities in preventing violence in general. CVE can be understood as a small component of this broader violence prevention effort. Departments and agencies will review existing public safety, violence prevention, and resilience programs to identify ones that can be expanded to include CVE as one among a number of potential lines of effort.
- As an example, the Federal Government helped support a community-led initiative to incorporate CVE into a broader program about Internet safety. The program addressed protecting children from online exploitation, building community resilience, and protecting youth from Internet radicalization to violence.
Future Activities and Efforts
Planned activities to expand support to local partners include the following:
- The Federal Government will help broker agreements on partnerships to counter violent extremism between communities and local government and law enforcement to help institutionalize this locally focused approach. (Lead: DHS)
- DHS and DOJ will work to increase support for local, community-led programs and initiatives to counter violent extremism, predominantly by identifying opportunities within existing appropriations for incorporating CVE as an eligible area of work for public safety, violence prevention, and community resilience grants. (Leads: DHS and DOJ)
- DHS is working to increase funding available to integrate CVE into existing community-oriented policing efforts through FY12 grants. (Lead: DHS)
- DHS is establishing an HSAC Faith-Based Community Information Sharing Working Group to determine how the Department can: (1) better share information with faith communities; and (2) support the development of faith-based community information sharing networks. (Lead: DHS)
- DHS is developing its Hometown Security webpage to include resources such as training guidance, workshop reports, and information on CVE for both the general public and law enforcement. (Lead: DHS)
- The Treasury will expand its community outreach regarding terrorism financing issues. (Lead: Treasury; Partners: State, DOJ, DHS, FBI, and the U.S. Agency for International Development)3
- Depending on local circumstances and in consultation with the FBI, U.S. Attorneys will coordinate, as appropriate, any efforts to expand connections and partnerships at the local level for CVE, supported by the National Task Force where needed. (Lead: DOJ; Partners: All)
- Departments and agencies will expand engagement with the business community by educating companies about the threat of violent extremism and by connecting them to community civic activists focused on developing CVE programs and initiatives. (Lead: DHS; Partner: NCTC)
DOWNLOAD ORIGINAL DOCUMENT HERE
NEW AND UNCENSORED – FEMEN Ukraine
TOP-SECRET FROM THE NSA-U.S. ESPIONAGE AND INTELLIGENCE
U.S. ESPIONAGE AND INTELLIGENCE

Organization, Operations, and Management, 1947-1996
In the aftermath of World War II, with the Cold War looming on the horizon, the United States began the process of developing an elaborate peacetime intelligence structure that would extend across a number of government departments. The operations of the U.S. intelligence community during the Cold War would range from running single agents, to marshaling the talents of thousands to build and deploy elaborate spy satellites.
The end of the Cold War brought major changes, but not the end of the U.S. government’s requirement for an elaborate intelligence structure. A number of intelligence organizations have been consolidated or altogether eliminated. New organizations have been established to provide more coherent management of activities ranging from military espionage, to imagery collection, to the procurement of airborne intelligence systems. The end of the Cold War has brought about the declassification of much information about intelligence organization and espionage activities that took place prior to the collapse of the Soviet Union.
Focus of the Collection
 U.S. Espionage and Intelligence: Organization, Operations, and Management, 1947-1996 publishes together for the first time recent unclassified and newly declassified documents pertaining to the organizational structure, operations, and management of the U.S. intelligence community over the last fifty years, cross-indexed for maximum accessibility. This set reproduces on microfiche 1,174 organizational histories, memoranda, manuals, regulations, directives, reports, and studies, representing over 36,102 pages of documents from the Office of the Director of Central Intelligence, the Central Intelligence Agency, National Reconnaissance Office, National Security Agency, Defense Intelligence Agency, military service intelligence organizations, National Security Council and other organizations. U.S. Espionage and Intelligence presents a unique look into the internal workings of America’s intelligence community. The documents gathered here shed further light on U.S. intelligence organization and activities during the Cold War, and describe the consolidation and reevaluation of the intelligence community in the post-Cold War era. They are drawn from diverse sources, including the National Archives, manuscript collections in the Library of Congress, court files of major espionage prosecutions, presidential libraries, and most importantly, Freedom of Information Act requests. The result of this effort is an authoritative documents publication which, together with the National Security Archive’s previous collection on the structure and operations of the U.S. intelligence community,
U.S. Espionage and Intelligence: Organization, Operations, and Management, 1947-1996 publishes together for the first time recent unclassified and newly declassified documents pertaining to the organizational structure, operations, and management of the U.S. intelligence community over the last fifty years, cross-indexed for maximum accessibility. This set reproduces on microfiche 1,174 organizational histories, memoranda, manuals, regulations, directives, reports, and studies, representing over 36,102 pages of documents from the Office of the Director of Central Intelligence, the Central Intelligence Agency, National Reconnaissance Office, National Security Agency, Defense Intelligence Agency, military service intelligence organizations, National Security Council and other organizations. U.S. Espionage and Intelligence presents a unique look into the internal workings of America’s intelligence community. The documents gathered here shed further light on U.S. intelligence organization and activities during the Cold War, and describe the consolidation and reevaluation of the intelligence community in the post-Cold War era. They are drawn from diverse sources, including the National Archives, manuscript collections in the Library of Congress, court files of major espionage prosecutions, presidential libraries, and most importantly, Freedom of Information Act requests. The result of this effort is an authoritative documents publication which, together with the National Security Archive’s previous collection on the structure and operations of the U.S. intelligence community,
U.S. Espionage and Intelligence provides a wealth of information and documentation on key aspects of intelligence organization and operations during and after the Cold War, including such extraordinary topics as:
- the evolution of the CIA
- the development and operation of key reconnaissance systems (SR-71, CORONA)
- the consolidation of Defense Department intelligence
- intelligence performance during the Persian Gulf War
- damage assessments of Aldrich Ames’ espionage activities
Significance of the Collection
The U.S. intelligence community has played a key role in advising presidents from Harry Truman to Bill Clinton on the intentions and activities of the Soviet Union, as well as of other nations. It also came to absorb a significant portion of the federal budget, reaching an approximate high of $30 billion in the late 1980s.
U.S. Espionage and Intelligence allows scholars direct access to the newly declassified, detailed primary documents that contain the history of the military, diplomatic, and intelligence components of the Cold War, and which go far beyond what is available in secondary sources. This new information is essential for reaching an accurate understanding of what was happening behind the scenes and how it related to the more public aspects of Cold War policy and operations.
The material contained in this set concerning the post-Cold War era is crucial in assessing the intelligence community’s performance in critical areas such as the Persian Gulf War and the Aldrich Ames case. The material is also vital in understanding the evolution of the intelligence community since the end of the Cold War and its possible future–for that evolution may significantly influence the ability of the intelligence community to deal with critical threats such as proliferation of weapons of mass destruction and terrorism.
One-Stop Access to Critical Documents
It would take a monumental effort, as well as many thousands of dollars, to duplicate the information contained in this collection. U.S. Espionage and Intelligenceallows a researcher– whether interested in the CIA, military intelligence, intelligence performance in the Persian Gulf War, or post-Cold War intelligence reform–to use one source at one location to access the thousands of pages of declassified material on the U.S. intelligence community available in this set.
Through U.S. Espionage and Intelligence the researcher gains access to a wide variety of documents: internal histories of the CIA and a variety of military intelligence organizations; program histories of the SR-71 and CORONA; director of central intelligence and Department of Defense directives establishing organizations such as the National Reconnaissance Office and the National Imagery and Mapping Agency; plans for the consolidation and reform of Defense intelligence organizations after the Cold War and memoranda implementing the reforms; and assessments of intelligence community performance in a number of areas.
In-depth Indexing Makes Every Document Accessible
The National Security Archive prepares extensive printed finding aids for its collections. In- depth indexing offers users remarkable ease and precision of access to every document in the set. The printed Index provides document-level access to subjects, individuals, and organizations, and represents a major research contribution in itself. Important transactions within each document are indexed individually using a controlled subjects vocabulary.
The Guide includes an essay, events chronology, glossaries of key individuals, organizations, and terms, document catalog, and a bibliography of secondary sources.
Research Vistas
With its depth of documentary detail, the collection enables researchers to explore
- U.S. intelligence performance
- Cold War history
- evolution of the U.S. intelligence community and its components
- U.S. intelligence collection activities
The Collection is a Necessity For:
- Scholars and students of
- intelligence
- national security organization and operations
- Cold War history
- Journalists
- Librarians and bibliographers
- Concerned citizens
Sample Document Titles
01/15/62 Legal Basis for Cold-War Activities, Lawrence Houston, [Classification Excised] Memorandum
03/27/64 Directive 5105.23, National Reconnaissance Office, Department of Defense, Top Secret Directive 05/23/67 Report on Plots to Assassinate Fidel Castro, Central Intelligence Agency, Secret Memorandum
07/00/73 Allen Welsh Dulles as Director of Central Intelligence, 26 February 1953-29 November 1961, Central Intelligence Agency, Top Secret Biographic Sketch
00/00/82 History of the Navy HUMINT Program, United States Navy, Top Secret History
03/15/91 Plan for Restructuring Defense Intelligence, Assistant Secretary of Defense for Command, Control, and Communication Intelligence, Secret Report
01/06/92 Task Force Report on Greater CIA Openness, Director of Central Intelligence, [Classification Excised] Memorandum
06/01/92 DCID 2/9, Management of National Imagery Intelligence, Director of Central Intelligence, Secret Intelligence Directive
09/00/92 Appendixes A, B, and C to the Final Report: National Reconnaissance Program Task Force for the Director of Central Intelligence, National Reconnaissance Program Task Force, Secret Report
12/18/92 Directive 5200.37, Centralized Management of Department of Defense Human Intelligence (HUMINT) Operations, Department of Defense, [Classification Unknown] Directive
08/00/93 Intelligence Successes and Failures in Operations Desert Shield/Storm, House Committee on Armed Services, [Classification Unknown] Report
01/21/94 A Description of Procedures and Findings Related to the Report of the U.S. Environmental Task Force, King Publishing, Paper
12/07/95 Statement of the Director of Central Intelligence on the Clandestine Services and the Damage Caused by Aldrich Ames, Director of Central Intelligence, Statement
03/01/96 Preparing for the 21st Century: An Appraisal of U.S. Intelligence, Commission on the Roles and Capabilities of the United States Intelligence Community, Report
12/19/96 United States of America v. Harold J. Nicholson, Superseding Indictment, U.S. District Court, Eastern District of Virginia, Indictment
Overview
Title
U.S. Espionage and Intelligence: Organization, Operations, and Management, 1947-1996
Content
Reproduces on microfiche 1,174 U.S. government records totaling 36,102 pages of documentation concerning the organizational structure, operations, and management of the intelligence community from World War II to the present.
Materials were identified, obtained, assembled, and indexed by the National Security Archive.
Series
The Special Collections
Arrangement
Microfiche are arranged chronologically. For ease of use, each document bears a unique accession number to which all indexing is keyed.
Standards
The documents are reproduced on 35mm silver halide archivally permanent positive microfiche conforming to NMA and BSI standards. Any microfiche found to be physically substandard in any way will be replaced free of charge.
Indexing
A printed Guide and Index accompanies the microfiche collection. The Guide contains an events chronology, glossaries, chronological document catalog and a bibliography of secondary sources. The Index provides in-depth, document level access to subjects and individuals.
U.S. Espionage and Intelligence Project Staff
Project Director
Dr. Jeffrey T. Richelson, project director, is a senior fellow at the National Security Archive and coordinates the Archive’s projects on U.S. policy toward China and ongoing documentation on U.S. intelligence issues. He previously edited the Archive’s collections on presidential national security documents, the history of the U.S. intelligence community, and the military uses of space. A former associate professor at American University, he received his Ph.D. in political science from the University of Rochester. Among his many books are Sword and Shield: Soviet Intelligence and Security Apparatus (1986), American Espionage and the Soviet Target (1988), America’s Secret Eyes in Space (1990), and A Century of Spies: Intelligence in the Twentieth Century (1995). His articles have appeared in a wide variety of professional journals and in publications ranging from Scientific American to the Washington Post. He is a regular commentator on intelligence and military issues for national television and radio.
Project Staff
Michael Evans, Research Assistant
Jane Gefter, Research Assistant
Michael Watters, Research Assistant
U.S. Espionage and Intelligence Advisory Board
Christopher Andrew, Corpus Christi College, University of Cambridge author, For the President’s Eyes Only
Loch Johnson, Department of Political Science, University of Georgia author, Secret Agencies: U.S. Intelligence in a Hostile World
David Wise, author, Nightmover: How Aldrich Ames Sold the CIA to the KGB for $4.6 Million
Praise for U.S. Espionage and Intelligence, 1947-1996
“Serious students of the structure and operations of American intelligence rely on the work of the National Security Archive. The new collection of intelligence documents, compiled for the Archive by Jeffrey T. Richelson, helps to pierce the labyrinth.”
David Wise
Author of Nightmover: How Aldrich Ames Sold the CIA to the KGB for $4.6 Million
“An invaluable supplement to the National Security Archive’s previous collection, The U.S. Intelligence Community 1947-1989, this brings the most recently declassified documents to the reader. Jeffrey Richelson’s useful introduction also serves to detail changes that have occurred in the structure of the U.S. espionage establishment.”
John Prados
Author of Presidents’ Secret Wars
GOOGLE UNTERWANDERT DURCH STASI-“GoMoPa”
Anal-Wahn, Kinderportal uned “Sexualerziehung der STASI-“GoMoPa”
TOP-SECRET FROM THE NSA-The Soviet Estimate: U.S. Analysis of the Soviet Union, 1947-1991

The Soviet Estimate:
U.S. Analysis of the Soviet Union,
1947-1991
Focus of the Collection
The Soviet Estimate: U.S. Analysis of the Soviet Union, 1947- 1991, publishes together for the first time the highest-level U.S. intelligence assessments of the Soviet Union, cross- indexed for maximum use. This set reproduces on microfiche more than 600 intelligence estimates and reports, representing nearly 14,000 pages of documentation from the office of the Director of Central Intelligence, the National Intelligence Council, the Central Intelligence Agency, the Defense Intelligence Agency, and other organizations. The set includes several hundred pages of debriefing transcripts and other documentation related to Colonel Oleg Penkovskii, the most important human source operated by the CIA during the Cold War, who later was charged with treason and executed by the Soviet Union. Also published here for the first time is the Pentagon’s Top Secret 1,000-page internal history of the United States-Soviet Union arms race.
The Soviet Estimate presents the definitive secret history of the Cold War, drawn from many sources: the hundreds of documents released by the CIA to the National Archives in December 1994, comprising the most important source of documents for the set, including intelligence estimates from 1946 to 1984; documents obtained under the Freedom of Information Act from the Pentagon, the CIA, the DIA, State Department, Pacific Command, and other agencies; and documents obtained from the National Archives and from various presidential libraries. The result of this effort is the most extensive and authoritative collection of declassified primary-source materials documenting the intelligence community’s effort to gather information on Soviet foreign policy, nuclear weapons, military policy and capabilities, weapons systems, the economy, science and technology, and the Soviet domestic political situation.
The Soviet Estimate provides a wealth of information and documentation on key intelligence issues, including:
- The missile gap controversy, which helped John F. Kennedy to win the presidency in 1960
- The “Team A”/”Team B” intelligence report controversy in 1976
- Whether the CIA foresaw the decline of the Soviet economy
- Advance warning from the CIA to President Bush about the hard-line coup attempt against Gorbachev in 1991.
Significance of the Collection
(54398) 1961/05/27
The Soviet Union was the major concern of U.S. national security decisionmakers for more than 40 years, and represented the most important single target of all U.S. intelligence collection efforts. The ultimate policies adopted by the U.S. during the Cold War were the result of many factors, not the least of which was an understanding of Soviet objectives and capabilities, shaped and influenced by the intelligence reports included in this set.
Until recently scholars have had to address issues such as the performance of U.S. intelligence analysis with respect to the Soviet Union or the impact of intelligence on policy without access to most of the key documents. Prior to December 1994, all of the National Intelligence Estimates related to the birth and death of the so-called “missile gap” were classified; scholars were often forced to rely either on other government documents that reproduced some of the information in estimates (for example, Department of Defense posture statements), or unofficial sources. The Soviet Estimate, with its diverse sources, permits scholars direct reference to the primary documents used in formulating much Cold War policy.
One-Stop Access to Critical Intelligence Documents
It would take an enormous effort, and many thousands of dollars, to duplicate the information contained in this collection. The Soviet Estimate allows a researcher– whether interested in the Soviet military, the Soviet economy, or Soviet internal politics–to use one source at one location to access the thousands of pages of declassified U.S. intelligence documents on the Soviet Union.
Through The Soviet Estimate the researcher gains access to a wide variety of documents, including National Intelligence Estimates, Special National Intelligence Estimates, National Intelligence Council memoranda, interagency intelligence studies, Defense Intelligence Estimates, and intelligence reports produced by DIA, military service, and unified command intelligence organizations.
Among the specific areas covered in the collection are:
- Developments in Soviet nuclear forces from the early 1950s to the 1980s
- The deteriorating political and economic situation under Mikhail Gorbachev in the late 1980s
- Soviet relations with the United States, European countries, and other nations
- The Soviet space program and developments in science and technology
- The Soviet economic system and economy
In-depth Indexing Makes Every Document Accessible
The National Security Archive prepares extensive printed finding aids for its collections. In-depth indexing offers users remarkable ease and precision of access to every document in the set. The printed Index provides document- level access to subjects, individuals, and organizations, and represents a major historical contribution itself. Important transactions within each document are indexed individually using a controlled subjects vocabulary.
The Guide includes an events chronology, glossaries of key individuals and organizations, chronological document catalog, and a bibliography of relevant secondary sources.
Research Vistas
With its depth of documentary detail and balance of perspectives, this collection enables researchers to explore in greater detail:
- Soviet studies
- Cold War history
- U.S. intelligence performance
- The intelligence-policy relationship
The Collection is a Necessity for:
- Scholars and students of
- The Soviet Union
- The history of the Cold War
- The U.S. intelligence community
- Policy formation
- Policy analysts
- Journalists
- Concerned citizens
- Librarians and bibliographers
Sample Document Titles
- 4/6/50 ORE 91-49
- Estimate of the Effects of the Soviet Possession of the Atomic Bomb Upon the Security of the U.S.
- 10/5/54 NIE 11-6-54
- Soviet Capabilities and Probable Programs in the Guided Missile Field
- 9/21/61 NIE 11-8/1-61
- Strength and Deployment of Soviet Long-Range Ballistic Missile Forces, September 21, 1961
- 3/2/67 NIE 11-1-67
- The Soviet Space Program
- 2/19/70 SNIE 11-16-70
- Soviet Attitudes Toward SALT
- 6/76 United States Air Force
- A History of Strategic Arms Competition, 1945-1972: Volume 3: A Handbook of Selected Soviet Weapon and Space Systems (May-Steinbruner-Wolfe Report)
- 12/76 NIO M 76-021J
- Soviet Strategic Objectives: An Alternative View (“Team B” Report)
- 5/27/81 SNIE 11-2-81
- Soviet Support for International Terrorism and Revolutionary Violence
- 7/7/81 M/M NIE 11-4-78
- Soviet Goals and Expectations in the Global Power Arena
- 4/83 NIC M 83-10006
- Dimensions of Civil Unrest in the Soviet Union
- 3/6/84 NIE 11-3/8-83
- Soviet Capabilities for Strategic Nuclear Conflict, 1983-93
- 4/89 CIA
- Rising Political Instability Under Gorbachev: Understanding the Problem and Prospects for Resolution
- 4/25/91 CIA, Office of Soviet Analysis
- The Soviet Cauldron
Overview
Title:
- The Soviet Estimate: U.S. Analysis of the Soviet Union, 1947 – 1991
- Content:
- Reproduces on microfiche more than 600 intelligence estimates and reports, representing nearly 14,000 pages of documentation recording the intelligence community’s effort to gather information on Soviet foreign policy, nuclear weapons, military policy and capabilities, weapons systems, the economy, science and technology, and the Soviet domestic political situation.
- Arrangement and Access:
- Documents are arranged chronologically. For ease of use, the unique identification numbers assigned to the documents are printed in eye-legible type at the top right-hand corner and precede each document on the microfiche strip.
- Standards:
- Documents are reproduced on silver halide positive- reading microfiche at a nominal reduction of 24x in envelopes. They are archivally permanent and conform to AIIM, BSI, and ANSI standards. Any microfiche found to be substandard will be replaced free of charge.
- Indexing:
- A printed Guide and Index totaling over 390 pages accompanies the microfiche collection. The Guide contains an essay; an events chronology; glossaries of acronyms and abbreviations, names, organizations, and technical terms; and a bibliography of secondary sources. The Index provides in-depth, document-level access to subjects, individuals, and organizations.
- Date of Publication:
- December 1995
- Orders and Inquiries
The National Security Archive
Founded in 1985, the National Security Archive has developed a reputation as the most prolific and successful nonprofit user of the Freedom of Information Act (FOIA). Through its FOIA expertise, the Archive has built what the Christian Science Monitor called “the largest collection of contemporary declassified national security information outside the United States government.” Located at The George Washington University, the Archive serves librarians, scholars, journalists, members of Congress, policymakers, public interest groups, and the general public. Foundation grants and publication royalties underwrite the Archive’s budget.
The Archive’s editorial process focuses on high-level policy-making and implementation, with special attention to inter-agency decisionmaking processes. Archive analysts target all U.S. government documents used by policymakers during the period covered by the collection, as well as other significant materials of direct relevance to the subject.
This research establishes a roadmap for future scholarship and “freezes” the documentary record with official requests for declassification before normal governmental document destruction process can diminish the historical record. The result is an “unusual” series of publications, as Microform Review noted, which make available documents “from the twilight zone between currently released government information, and normal declassification” periods.
Accompanied by highly sophisticated item-level catalogs, indexes, and other finding aids–which Government Publications Review hailed as “gold mines in and of themselves”–the Archive’s collections, according to the Washington Journalism Review, constitute “a ‘Nexis’ of national security . . . [a] state-of-the-art index to history.”
Praise for The Soviet Estimate
“The National Security Archive has performed a valuable service by compiling the most extensive and authoritative file of declassifed, official U.S. National Intelligence Estimates on the Soviet Union. The compilation The Soviet Estimate is a gold mine for analyzing Soviet developments on the Cold War, and no less important, contemporary American intelligence assessments of those developments. With the benefit of hindsight and new information, the validity of those estimates can be studied, and their impact on U.S. policy and the Cold War evaluated. ”
–Raymond Garthoff,
Senior Fellow, Foreign Policy Studies Program, Brookings Institution, former U.S. Ambassador to Bulgaria, veteran of the U.S. Department of State and Central Intelligence Agency, and author of many publications, including Deterrence and the Revolution in Soviet Military Doctrine (1990), The Great Transition: American-Soviet Relations and the End of the Cold War (1994), and Détente and Confrontation: American-Soviet Relations from Nixon to Reagan (1994).
The National Security Archive Soviet Estimate Project Staff
- Project Editor
- Jeffrey T. Richelson, Ph.D., Project Editor, is a senior fellow at the National Security Archive and coordinates the Archive’s projects on U.S. policy toward China and ongoing documentation on U.S. Intelligence issues. He previously edited the Archive’s collections on presidential national security documents, the history of the U.S. intelligence community, and the military uses of space. A former associate professor at American University, he received his Ph.D. in political science from the University of Rochester. Among his many books are Sword and Shield: Soviet Intelligence and Security Apparatus (1986), American Espionage and the Soviet Target (1988), America’s Secret Eyes in Space (1990), and A Century of Spies: Intelligence in the Twentieth Century (1995). His articles have appeared in a wide variety of professional journals and in publications ranging from Scientific American to the Washington Post. He is a regular commentator on intelligence and military issues for national television and radio.
- Project Staff
- Jane Gefter, Research Assistant
Ian Stevenson, Research Assistant
Kristin Altoff, Intern
STASI im 21. Jahrhundert mit Hilfe der alten SED-Die Liste der “GoMoPa”- Opfer
Die Mörder sind unter uns – NEO-NAZIS UND NEO-STASI- der Beweis
FINANCIAL TIMES ÜBER STASI – “GoMoPa” und deren mutmassliche Hintermänner wie z.B. “Anleger-Anwalt” Resch
Kurssturz – Millionen über nacht vernichtet durch die STASI “GoMoPa” – Wirecard Lüge – LKA ermittelt weiter
“Sexualaufklärung” für Kinder durch STASI-“GoMoPa” im Internet
STASI “GoMoPa” handelt nach dem alten Göring-Motto:”Wo gehobbelt wird, da fallen Späne “-BÖRSE ONLINE berichtet
Gruner und Jahrs Medium BÖRSE ONLINE über STASI-“GoMoPa”-Betrug und RA Resch
BÖRSE ONLINE: STASI -“GoMoPa” – Entstellung und Leugnung von Fakten
UNCENSORED- Alexandra – FEMEN
TOP-SECRET-ISAF Afghanistan Detainee Operations Standard Operating Procedures

1. Reference G is the current operational level guidance on detention issues. This TACSOP gives further direction and guidance to commanders and staff responsible for detention operations within Afghanistan. Commanders at all levels are to ensure that detention operations are conducted in accordance with applicable international law and human rights standards and that all detainees are treated with respect and dignity at all times. The strategic benefits of conducting detention operations in a humanitarian manner are significant. Detention operations that fail to meet the high standards mandated herein will inevitably have a detrimental impact on the ISAF Mission. All ISAF Detention operations will be subject to internal and external scrutiny.
2. The policy contained within this TACSOP applies to actions taken by ISAF troops under the ISAF Mission. It does not apply to PW or to persons indicted for war crimes (PIFWC) pursuant to the lawful exercise of authority by the International Criminal Court or other lawfully constituted tribunals. It does, however, give direction to Regional Commands on the reporting of detainees taken within their AOO by troops operating under the Counter-Terrorist mandate (Reference H refers) or by ANSF operating jointly with ISAF.
DEFINITIONS
3. The following definitions are used throughout this SOP.
a. NATO Holding Facility / NATO Detention Facility. This term refers to any facility used, designed or adapted to facilitate the detention of individuals.
b. ISAF Detention Authority. This is defined in the main body of this SOP as a specified individual authorised to make detention decisions. These individuals are listed in Para 6 below.
c. Period of Detention. This is regarded as the period of detention, not to exceed 96 hours, which starts on arrest (ie; the act by which a non-ISAF person is deprived of his liberty by ISAF personnel) until the moment a detainee is handed over to the ANSF or GOA officials or is released by ISAF.
d. ANSF. The abbreviation ANSF stands for Afghan National Security Forces and includes, Afghan National Army (ANA), Afghan National Police (ANP), Afghan Border Police, Afghan Highway Police, Afghan Counter-Narcotics Police and any authorised Afghan national or regional government agency involved with security or detention facilities.
e. Age / Date of Birth. Consideration must be given to the fact that in many areas, individuals may not know their age or date of birth. For the purpose of this SOP, the following definitions are used:
(1) Adult. An adult is considered to be any person aged 18 or over.
(2) Juvenile. A juvenile is considered to be between the age of 15 up to 18.
(3) Child A child is considered to be below the age of 15.
LEGAL APPLICATIONS
4. Authority to Detain. The only grounds upon which a person may be detained under current ISAF Rules of Engagement (ROE) are: if the detention is necessary for ISAF force protection; for the self-defence of ISAF or its personnel; for accomplishment of the ISAF mission.
5. Detention. If an arrest and/or detention is effected by ANSF with ISAF support, then the individual is not considered to be an ISAF detained person and the provisions of this TACSOP do not apply. An individual will not be considered as an ISAF detained person until and unless ISAF assumes control and places that individual into detention. In all cases of detention HQ ISAF is to be informed. The current policy for ISAF is that Detention is permitted for a maximum of 96 hours after which time an individual is either to be released or handed into the custody of the ANSF / GOA.
6. Detention Authority. As soon as practicable after an detention has taken place, the decision to continue to detain must be considered by an appropriate authority. The ISAF Detention authority must be able to support the grounds by a reasonable belief in facts. The requirement for detention must be kept under continuous review. The following persons may act as an ISAF Detention Authority to determine if the grounds set out in paragraph 4 are met:
a. COMISAF2;
b. A Regional Commander (RC);
c. A National Contingent Commander;
d. The Theatre Task Force Commander;
e. A Battalion Commander;
f. A Provincial Reconstruction Team (PRT) Commander;
g. Base Commander;
h. An On-Scene Commander; and
i. Commander of the Theatre Detention Facility.
7. The powers of the Detention Authority. A Detention Authority may authorize detention for up to 96 hours following initial detention. Should the Detention Authority believe that continued detention beyond 96 hours is necessary then, prior to the expiration of the 96-hour period, the Detention Authority shall refer the matter via the chain of command to HQ ISAF.

DOWNLOAD ORIGINAL DOCUMENT HERE
The FBI-Former Illinois Governor Rod R. Blagojevich Sentenced to 14 Years in Prison for Corruption in Office
CHICAGO—Former Illinois Gov. Rod R. Blagojevich was sentenced today to 14 years in federal prison following his conviction at trials in 2010 and 2011 on 18 felony counts of corruption during his tenure as governor, including his effort in 2008 to illegally trade the appointment of a United States Senator in exchange for $1.5 million in campaign contributions or other personal benefits. Blagojevich was also sentenced for shaking down the chief executive of a children’s hospital for $25,000 in campaign contributions in exchange for implementing an increase to pediatric reimbursement rates; holding up the signing of a bill to benefit the Illinois horse racing industry in an attempt to illegally obtain $100,000 in campaign contributions; and lying to the FBI in 2005.
Blagojevich, who will turn 55 on Dec. 10, was ordered to surrender to the U.S. Bureau of Prisons on Feb. 16, 2012, to begin serving his sentence. The prison term is the longest-ever imposed on a former governor in the Northern District of Illinois.
“When it is the governor who goes bad, the fabric of Illinois is torn, disfigured and not easily repaired,” U.S. District Judge James Zagel said in imposing the sentence after a two-day hearing. “The harm here is not measured in the value of money or property . . . the harm is the erosion of public trust in government,” he said.
The judge imposed a fine of $20,000 and two years of supervised release after incarceration. Blagojevich also must pay a special assessment of $1,800, or $100 on each count of conviction.
During the sentencing hearing, Judge Zagel agreed with the government that the properly calculated advisory federal sentencing guidelines provided for a sentencing range of 30 years to life. He also agreed with the government that the range was not appropriate within the context of this case, and found an “effective” guideline range of 188 to 235 months in prison, which was proximate to the government’s recommended sentence of 15 to 20 years. The judge further reduced the range to 151 to 188 months after finding that Blagojevich accepted responsibility for his crimes at sentencing.
In sentencing papers, the government contended that “Blagojevich’s criminal activity was serious, extended, and extremely damaging.” The crimes proven at trial were not isolated incidents, but, instead, were part of an approach to public office that Blagojevich adopted from the moment he became governor after he was first elected in 2002 on the heels of gubernatorial corruption and running on a campaign to end “pay-to-play” politics.
“Blagojevich betrayed the trust and faith that Illinois voters placed in him, feeding great public frustration, cynicism and disengagement among citizens. People have the right to expect that their elected leaders will honor the oath they swear to, and this sentence shows that the justice system will stand up to protect their expectations,” said Patrick J. Fitzgerald, United States Attorney for the Northern District of Illinois.
“The sentence handed down today represents a repayment of the debt that Blagojevich owes to the people of Illinois. While promising an open and honest administration, in reality, the former governor oversaw a comprehensive assault on the public’s trust,” said Robert D. Grant, Special Agent in Charge of the Chicago Office of the Federal Bureau of Investigation.
Thomas P. Brady, Inspector in Charge of the U.S. Postal Inspection Service in Chicago, said: “The United States Postal Inspection Service is proud to be one of the federal law enforcement agencies to help ferret out this type of political corruption in Illinois. The Inspection Service is committed to increasing the public’s trust and confidence through our investigations of fraudulent activity. While the sentencing today closes one chapter, we must adhere to a renewed standard of accountability to ensure that the citizens of our state are not victimized by political corruption and greed.”
Alvin Patton, Special Agent in Charge of the Internal Revenue Service Criminal Investigation Division in Chicago, said: “Today’s sentence sends a loud message that public corruption will not be tolerated. The IRS Criminal Investigation Division, together with the U.S. Attorney’s Office and our law enforcement partners, will continue to aggressively pursue violators of the public trust. Regardless of political office or position, no one is above the law.”
James Vanderberg, Special Agent in Charge of the Chicago Regional Office of the U.S. Department of Labor, Office of Inspector General, said: “This sentence sends a clear message that public officials cannot engage in corruption for personal benefit in exchange for political favors.
Blagojevich, a lawyer and former state prosecutor, state legislator, and U.S. Representative, was arrested on Dec. 9, 2008, while serving his second term as governor. He was accused of using his office in numerous matters involving state appointments, business, legislation and pension fund investments to seek or obtain such financial benefits as money, campaign contributions, and employment for himself and others, in exchange for official actions, including trying to leverage his authority to appoint a United States Senator to replace then President-Elect Obama.
Blagojevich went to trial in the summer of 2010 and was convicted of lying to FBI agents when he falsely told them in an interview on March 16, 2005, that he did not track, or want to know, who contributed to him or how much money they contributed to him, but the jury was deadlocked on all remaining counts.
He went to trial again in the spring of 2011 and was convicted on 17 additional counts, including 10 counts of wire fraud, two counts of attempted extortion, two counts of conspiracy to commit extortion, one count of soliciting bribes, and two counts of conspiracy to solicit and accept bribes.
The prosecution was part of Operation Board Games, a public corruption investigation of pay-to-play schemes, including insider-dealing, influence-peddling and kickbacks involving private interests and public duties. The investigation began in 2003 and has resulted in convictions against 15 defendants, including two former chiefs of staff for Blagojevich while he was governor.
The government is being represented in the Blagojevich case by Assistant U.S. Attorneys Reid Schar, Carrie Hamilton and Christopher Niewoehner.
TOP-SECRET FROM THE NSA-Info Age requires rethinking 4th Amendment limits and policies,
Washington, D.C., December 8, 2011 – The largest U.S. spy agency warned the incoming Bush administration in its “Transition 2001” report that the Information Age required rethinking the policies and authorities that kept the National Security Agency in compliance with the Constitution’s 4th Amendment prohibition on “unreasonable searches and seizures” without warrant and “probable cause,” according to an updated briefing book of declassified NSA documents posted today on the World Wide Web.
Wiretapping the Internet inevitably picks up mail and messages by Americans that would be “protected” under legal interpretations of the NSA’s mandate in effect since the 1970s, according to the documents that were obtained through the Freedom of Information Act by Dr. Jeffrey Richelson, senior fellow of the National Security Archive at George Washington University.
The NSA told the Bush transition team that the “analog world of point-to-point communications carried along discrete, dedicated voice channels” is being replaced by communications that are “mostly digital, carry billions of bits of data, and contain voice, data and multimedia,” and therefore, “senior leadership must understand that today’s and tomorrow’s mission will demand a powerful, permanent presence on a global telecommunications network that will host the ‘protected’ communications of Americans as well as targeted communications of adversaries.”
The documents posted today also include a striking contrast between the largely intact 1998 NSA organizational chart for the Directorate of Operations and the heavily redacted 2001 chart for the Signals Intelligence Directorate (as the operations directorate was renamed), which contains no information beyond the name of its director. “The 2001 organization charts are more informative for what they reveal about the change in NSA’s classification policy than for what they reveal about the actual structure of NSA’s two key directorates,” commented Dr. Richelson. The operations directorate organization chart was provided within three weeks of its being requested in late 1998. In contrast, the request for the Signals Intelligence Directorate organization chart was made on April 21, 2001, and NSA did not provide its substantive response until April 21, 2004 – three years instead of three weeks.
Introduction
The National Security Agency (NSA) is one of the most secret (and secretive) members of the U.S. intelligence community. The predecessor of NSA, the Armed Forces Security Agency (AFSA), was established within the Department of Defense, under the command of the Joint Chiefs of Staff, on May 20, 1949. In theory, the AFSA was to direct the communications intelligence and electronic intelligence activities of the military service signals intelligence units (at the time consisting of the Army Security Agency, Naval Security Group, and Air Force Security Service). In practice, the AFSA had little power, its functions being defined in terms of activities not performed by the service units. (Note 1)
The creation of NSA resulted from a December 10, 1951, memo sent by Walter Bedell Smith to James B. Lay, Executive Secretary of the National Security Council. The memo observed that “control over, and coordination of, the collection and processing of Communications Intelligence had proved ineffective” and recommended a survey of communications intelligence activities. The proposal was approved on December 13, 1951, and the study authorized on December 28, 1951. The report was completed by June 13, 1952. Generally known as the “Brownell Committee Report,” after committee chairman Herbert Brownell, it surveyed the history of U.S. communications intelligence activities and suggested the need for a much greater degree of coordination and direction at the national level. As the change in the security agency’s name indicated, the role of the NSA was to extend beyond the armed forces. (Note 2)
In the last several decades some of the secrecy surrounding NSA has been stripped away by Congressional hearings and investigative research. In the late 1990s NSA had been the subject of criticism for failing to adjust to the post-Cold War technological environment as well as for operating a “global surveillance network” alleged to intrude on the privacy of individuals across the world. The following documents provide insight into the creation, evolution, management and operations of NSA, including the controversial ECHELON program. Also included are newly released documents (11a – 11g) that focus on the restrictions NSA places on reporting the identities of U.S. persons – including former president Jimmy Carter and first lady Hillary Clinton, and NSA Director Michael Hayden’s unusual public statement (Document 24) before the House Intelligence Committee.
Some of the documents that appear for the first time in this update shed additional light on the history of NSA. They concern the NSA’s participation in the space reconnaissance program (Document 3), NSA’s success in deciphering Soviet communications in the 1960s (Document 4), the efficacy of NSA activities in the late mid-to-late 1960s (Document 5), and Israel’s attack on the USS Liberty during the 1967 war (Document 10). Others provide new insight on NSA’s assessment of key issues in the new century (Document 21, Document 23), on NSA’s attempts to adapt to the changing world and communications environment, (Document 22), on the agency’s regression to old policies with regard to organizational secrecy (Document 26a, Document 26b), and on NSA activities before and after the events of 9/11 (Document 25).
Several of these documents also appear in either of two National Security Archive collections on U.S. intelligence. The U.S. Intelligence Community: Organization, Operations and Management: 1947-1989 (1990) and U.S. Espionage and Intelligence: Organization, Operations, and Management, 1947-1996 (1997) publish together for the first time recently declassified documents pertaining to the organizational structure, operations and management of the U.S. Intelligence Community over the last fifty years, cross-indexed for maximum accessibility. Together, these two sets reproduce on microfiche over 2,000 organizational histories, memoranda, manuals, regulations, directives, reports, and studies, totalling more than 50,000 pages of documents from the Office of the Director of Central Intelligence, the Central Intelligence Agency, National Reconnaissance Office, National Security Agency, Defense Intelligence Agency, military service intelligence organizations, National Security Council, and other official government agencies and organizations.
Documents
Note: The following documents are in PDF format.
You will need to download and install the free Adobe Acrobat Reader to view.
Document 1: NSCID 9, “Communications Intelligence,” March 10, 1950
National Security Council Intelligence Directives have provided the highest-level policy guidance for intelligence activities since they were first issued in 1947.
This document establishes and defines the responsibilities of the United States Communications Intelligence Board. The Board, according to the directive, is to provide “authoritative coordination of [the] Communications Intelligence activities of the Government and to advise the Director of Central Intelligence in those matters in the field of Communications Intelligence for which he is responsible.”
The particularly sensitive nature of communications intelligence (COMINT) activities was highlighted by paragraph 6, which noted that such activities should be treated “in all respects as being outside the framework of other or general intelligence activities.” Thus, regulations or directives pertaining to other intelligence activities were not applicable to COMINT activities.
Document 2a: Memorandum from President Harry S. Truman to the Secretary of State, the Secretary of Defense, Subject: Communications Intelligence Activities, October 24, 1952
Document 2b: National Security Council Intelligence Directive No. 9, Communications Intelligence, December 29, 1952
President Truman’s memorandum revokes the provisions of NSCID 9 with regard to the composition, responsibilities, and procedures of the U.S. Communications Intelligence Board. It establishes the USCIB as an entity “acting for and under” a newly created Special Committee of the National Security Council for COMINT, consisting of the Secretary of State and the Secretary of Defense.
More significantly, Truman’s memo, along with a Department of Defense directive, established NSA, and transformed communications intelligence from a military activity divided among the three services to a unified national activity. (Note 3) Thus, the first sentence states that “The communications intelligence (COMINT) activities of the United States are a national responsibility.”
The memorandum instructs the Special Committee to issue a directive to the Secretary of Defense which defines the COMINT mission of NSA as being to “provide an effective, unified organization and control of the communications intelligence activities of the United States conducted against foreign governments.” Thus, “all COMINT collection and production resources of the United States are placed under his operational and technical control.”
The directive provided the NSA director with no authority regarding the collection of electronic intelligence (ELINT)—such as intelligence obtained from the interception of the emanations of radarsor of missile telemetry. Responsibility for ELINT remained with the military services.
NSCID 9 of December 1952 replaces its 1950 predecessor as mandated by Truman’s directive. Often using identical language to that in the Truman directive, it revises the responsibilities of the United States Communications Intelligence Board as well as defining the role of the newly created National Security Agency and enumerating the responsibilities of its director.
New Document 3: Memorandum of Agreement Concerning NSA Participation in the (S) National Reconnaissance Office, August 1, 1962. Top Secret
The National Reconnaissance Office was established in September 1961 to provide a central coordinating authority for the nation’s overhead reconnaissance activities, which included efforts by the Central Intelligence Agency, Air Force, and Navy. An early issue was the division of responsibilities for the development and operation of satellite systems. At a conference in May 1962, it was agreed by CIA and NRO officials that the National Security Agency, despite its responsibility for signals intelligence activities, would not be allowed to develop SIGINT satellites as part of the national reconnaissance program. Herbert Scoville, the CIA’s deputy director for research, argued that the Secretary of Defense was the government’s executive agent for SIGINT activities and since he had chosen to assign the mission to the NRO, the NSA was excluded from undertaking such development activities. (Note 4)
The Secretary’s decision did not mean, however, that NSA, was to play no role in the development and operation of signals intelligence satellites. This represents the first agreement specifying how NSA would be permitted to participate in the National Reconnaissance Program.
New Document 4: Richard Bissell, Review of Selected NSA Cryptanalytic Efforts, February 18, 1965 Top Secret Codeword
Richard Bissell joined the CIA in 1954, serving first as the special assistant to CIA Director Allen Dulles, and then as the agency’s Deputy Director (Plans). He left the agency in February 1962, as a result of the failure of the Bay of Pigs invasion of April 1961. Before and during his tenure as the CIA’s operations chief Bissell directed the development and operation of several key technical collection systems – including the U-2 and OXCART aircraft, and the CORONA reconnaissance satellite.
In his memoirs he reported that, in October 1964, “I accepted a brief assignment from John McCone at the CIA, which involved looking into very highly classified business of another agency of the government. My job was to write a report on what I had learned from visits and interviews with authorities on the problem.” (Note 5) Bissell provided no further information.
In response to a Freedom of Information Act request, the CIA provided a copy of this document – which is Bissell’s report of his investigation of the National Security Agency’s efforts to crack certain high-grade cipher systems. Although the identity of the nation whose ciphers were being attacked is deleted throughout the report, the target country is clearly the Soviet Union. The report discusses the prospects of breaking into high-level Soviet codes and concludes with three principal recommendations – which concern the extent of the overall cryptologic effort, the desirability of reallocating some cryptologic resources, and the possibility of a systematic comparison of the intelligence produced via the successful exploitation of two different components of the cryptanalytic effort.
New Document 5: Letter, Frederick M. Eaton to Richard M. Helms, Director of Central Intelligence, August 16, 1968, Top Secret Codeword w/TS Codeword attachment
This letter, along with the attachment, represents the report of the four-member group, which included Eaton, a New York lawyer and banker, General Lauris Norstad, the Defense Department’s Eugene Fubini, and ambassador Livingston T. Merchant, that was commissioned by DCI Richard Helms in September 1967 to examine the national signals intelligence effort.
The topics examined by the group included program guidance, the DCI and the National Intelligence Resources Board, central review and coordination, management of the cryptologic community, NSA staff organization, COMINT, Telemetry, and ELINT resources, and the communications and dissemination of the information. The letter from Eaton to Helms conveys the group’s nineteen recommendations and the conclusion that
“there must be no slackening in the US cryptologic effort if essential military and other national needs are to be met.”
According to James Bamford’s The Puzzle Palace, Eaton was forced to write the conclusions himself when “many of the staff turned in their pens” because Eaton “recommended no reductions and concluded that all of NSA’s programs were worthwhile,” despite “accumulated substantial evidence that much of the NSA’s intelligence collection was of little or marginal uses to the various intelligence consumers in the community.” (Note 6)
Document 6: Memo to President Johnson, September 6, 1968
This memo, from national security adviser Walt Rostow to President Johnson, provides information concerning North Vietnamese/Viet Cong military and political strategy during the last months of Johnson’s presidency. The last item in the memo notes that its conclusions were partly a function of the author’s access to relevant intercepted communications.
The memo specifically notes unusual, high-priority message traffic between Hanoi and subordinate units directing forces in South Vietnam as well as urgent messages from the Military Affairs Committee of COSVN (Central Office for South Vietnam) to subordinates. It does not reveal how extensively the U.S. was able to decrypt the messages.
Document 7: Department of Defense Directive S-5100.20, “The National Security Agency and the Central Security Service,” December 23, 1971
Originally classified Secret, this directive remains in effect today, with minor changes. Key portions of the directive specify the NSA’s role in managing the signals intelligence effort for the entire U.S. government, the role of the Secretary of Defense in appointing and supervising the work of the NSA’s director, the authorities assigned to the director of NSA, and the relationships that NSA is expected to maintain with other components of the government.
Among the specific responsibilities assigned to the director are preparation of a consolidated SIGINT program and budget for Defense Department SIGINT activities, the “exercise of SIGINT operational control over SIGINT activities of the United States,” and the production and dissemination of SIGINT “in accordance with the objectives, requirements, and priorities established by the Director of Central Intelligence.”
The directive reflects the 1958 addition of electronic intelligence to NSA’s responsibilities, making it the national authority for both components of signals intelligence.
Document 8a: NSCID 6, “Signals Intelligence,” February 17, 1972
Document 8b: Department of Justice, “Report of the Inquiry into CIA-Related Electronic Surveillance Activities,” 1976, pp. 77-9
NSCID 6 is the most recently available NSCID concerning SIGINT. It was still in effect at least as late as 1987. An earlier version of the directive was issued in 1958, when NSA was first assigned responsibility for electronics intelligence.
The version released by the NSC in 1976 contains little more than the definitions for COMINT and ELINT. However, a Justice Department report obtained by author James Bamford while researching his book, The Puzzle Palace, quoted additional portions of the directive.
The directive specifies that the Director of NSA is to produce SIGINT in response to the objectives, requirements and priorities of the Director of Central Intelligence. It also empowers the director to issue direct instructions to any organizations engaged in SIGINT operations, with the exception of certain CIA and FBI activities, and states that the instructions are mandatory.
Document 9a: NSA COMINT Report, “Capital Projects Planned in India,” August 31, 1972
Document 9b: NSA, “India’s Heavy Water Shortages,” October 1982
These two documents provide examples of NSA reporting, as well as demonstrating that NSA’s collection targets have included Indian atomic energy programs. Portions of each document that discuss or reveal the contents of the intercepts have been redacted. However, the classification of the documents indicates that high-level communications intelligence was used in preparing the report. UMBRA is the highest-level compartment of the three compartments of Special Intelligence—the euphemism for COMINT. The lower level compartments are MORAY and SPOKE.
The classification (either TSU [TOP SECRET UMBRA] or MORAY) of the 25 reports which Document 6b was derived from indicate that the report relied extensively on COMINT. The report also demonstrates how NSA, often to the annoyance of the CIA, has gone far beyond its formal collection and processing responsibilities and into the analysis of the data it has collected. (Note 7)
New Document 10: William D. Gerhard and Henry W. Millington, National Security Agency, Attack on a SIGINT Collector, the USS Liberty, 1981. Top Secret Umbra
One of the most controversial events in the history of U.S.-Israeli relations was the attack by Israeli aircraft, during the midst of the Six-Day War of June 1967, on the USS Liberty, a ship assigned to gather signals intelligence on behalf of the National Security Agency. The attack left thirty-four Americans dead and 171 wounded.
In additional to internal studies conducted by both countries there have been numerous books, portions of books, and articles that have sought to review the events and assess blame. The most controversial issue has been whether Israel knowingly attacked a ship it knew to belong to the U.S., which was cruising in international waters off the Sinai Peninsula, to prevent it from monitoring Israeli actions in the midst of the war. Authors have reached diametrically opposite conclusions on this issue. (Note 8)
This extensive report, written by a former head of the NSA element that produced studies of SIGINT crisis situations and the former head of the NSA library, examines the political-military background, consideration’s leading to the ship’s deployment, deployment to the Mediterranean, the attack, Israel’s explanation, recovery and initial assessment, reviews of the incident, and “a final look.” In their conclusion, the authors deal with the issues of possible Israeli foreknowledge of the ship’s nationality and possible Israeli motivations for an attack. They report that a CIA assessment prepared within week of the attack, drawing heavily on communications intercepts, concluded (p. 64) that Israeli forces had not deliberately attacked a ship they knew to be American.
Document 11a: United States Signals Intelligence Directive [USSID] 18, “Legal Compliance and Minimization Procedures,” July 27, 1993
While NSCIDs and DoD Directives offer general guidance on the activities of NSA and the United States SIGINT System (USSS), far more detailed guidance is provided by the director of NSA in the form of United States Signals Intelligence Directives (USSIDs). The directives fall into at least nine different categories: policy, collection, processing, analysis and reporting, standards, administration, training, data processing, and tasking.
In the aftermath of revelations in the 1970s about NSA interception of the communications of anti-war and other political activists new procedures were established governing the interception of communications involving Americans. (Note 9) The version of USSID 18 currently in force was issued in July 1993 and “prescribes policies and procedures and assigns responsibilities to ensure that the missions and functions of the United States SIGINT System (USSS) are conducted in a manner that safeguards the constitutional rights of U.S. persons.” Section 4 (“Collection,” pp.2-6) specifies the circumstances under which U.S. SIGINT activities may intercept communications of or about U.S. persons, as well as the authorities of the Foreign Intelligence Surveillance Court, the Attorney General, and the Director of NSA to approve the collection of such information.
Section 5 (“Processing,” pp.6-7) focuses on the restrictions on processing intercepted communications involving U.S. persons–including domestic communications collected during foreign communications collection operations. Section 6 (“Retention,” p.8) deals with the retention of intercepted communications about U.S. persons. Section 7 (“Dissemination,” pp.8-10) concerns restrictions on dissemination. It requires that all SIGINT reports be written “so as to focus solely on the activities of foreign entities and persons and their agents.” It also specifies some of the conditions under which U.S. persons can be identified in SIGINT reports–for example, when the communications indicate the person is an agent of a foreign power.
Document 11b: NSA, “USSID 18: Dissemination of U.S. Government Organizations and Officials (U)–INFORMATION MEMORANDUM,” February 5, 1993
This NSA memo indicates that the conditions for identification of U.S. officials by title in NSA reporting varies depending on whether or not the individual is a member of the executive branch. Senior officials of the executive branch may be identified by title, without prior approval from higher authority, when the official’s title is necessary to understand or assess foreign intelligence. In contrast, officials from the legislative and judicial branches cannot be identified by title, even if that information is necessary to understand foreign intelligence, unless approval is obtained from higher authority. The memo implies that, under the assumed conditions, the use of names is not permitted.
Document 11c: NSA, “USSID 18: Reporting Guidance on References to the First Lady,” July 8, 1993
This memo followed a U.S. Court of Appeals ruling that Hillary Clinton was a full-time government official. It notes that she could be identified in reports by title (Chairperson of the President’s Task Force on National Health Care Reform) without prior approval when that title was necessary to understand or assess foreign intelligence and when the information related to her official duties. The memo also contains guidance on reports containing information about information concerning Mrs. Clinton that is not clearly foreign intelligence.
Document 11d: National Security Agency/Central Security Service, “U.S. Identities in SIGINT,” March 1994
This 48-page document is intended to provide detailed guidance concerning on the use of U.S. identities in SIGINT reports as well as the dissemination of U.S. identities to consumers outside the United States SIGINT System. It consists of 12 sections (including ones on requests for U.S. identities, accountability, dissemination, and collection and processing), and five appendices (including those on approved generic references and USSID 18 criteria for dissemination).
Document No. 11e: NSA, USSID 18: Reporting Guidance on Former President Carter’s Involvement in the Bosnian Peace Process (U)– Information Guidance, December 15, 1994
The issue of when the identity or even title of a U.S. citizen can be included in reporting based on communications intercepts is a major focus of USSID 18. This NSA memo was prepared in response to the invitation to former President Carter to travel to Bosnia and Herzegovina to participate in efforts to end the war. It specifies that as long as Carter is acting as a private citizen he may be referred to only as a “U.S. person” in any reports.
Document 11f: NSA, “Understanding USSID 18 and Contextual Identifications,” September 30, 1997
The issue of identification by context is the subject of this memo. It notes that, in describing U.S. entities, analysts are required, in general, to substitute sufficiently generic terms for the entities–terms that do not “directly lead to the identification of a U.S. entity even though the identity has been obscured in the report.” Violation of the “contextual identification rule” requires that the report “must be cancelled, reworded and reissued to eliminate the identifying information.” The guidance clearly does not apply to those cases where inclusion of more specific information is necessary to evaluate foreign intelligence.
Document 11g: NSA, “USSID 18 Guide,” February 1998
The introduction to this document notes that it is an informal guide to the provisions of USSID 18 with respect to the issue of the COMINT collection and and dissemination of U.S. identities. One section focues on USSID 18 issues with respect to threat situations, including when an individual is held captive by a foreign power or group or when an intercept reveals a threat to a U.S. person. The section on non-threat situations contains guidance on the disposition of the inadvertent intercept of communciations between U.S. persons, on processing and reporting of incidentally intercepted communications of a U.S. person during foreign intelligence collection, and the handling of U.S. identities in reports.
Document 12: Director of Central Intelligence Directive (DCID) 6/1, “SIGINT Committee,” May 12, 1982
The SIGINT Committee, now known as the National SIGINT Committee, was first established in 1958 to oversee key aspects of U.S. SIGINT activities—the identification of collection requirements, evaluation of how well U.S. and allied SIGINT activities satisfy requirements, and the production of recommendations concerning SIGINT arrangements with foreign governments. This directive is the most recent available version of DCID 6/1. While the directive remains formally classified, the full text of the document has been published previously in scholarly works and on the world wide web. (Note 10)
The SIGINT Committee operated for many years with two permanent subcommittees—the SIGINT Requirements Validation and Evaluation Subcommittee (SIRVES) and the SIGINT Overhead Reconnaissance Subcommittee (SORS). In the mid-1990s two new groups were established: The Weapons and Space Systems Advisory Group, to “coordinate SIGINT on foreign weapons and space systems,” and the National Emitter Intelligence Subcommittee, which focuses on SIGINT production concerning foreign radars and other non-communications signals. (Note 11)
Document 13: NAVSECGRU Instruction C5450.48A, Subj: Mission, Functions and Tasks of Naval Security Group Activity (NAVSECGRUACT) Sugar Grove, West Virginia, September 3, 1991
While NSA directs and manages U.S. SIGINT activities, almost all collection activity is actually carried out by the military service SIGINT units—including the Naval Security Group Command. The role of the unit at Sugar Grove in intercepting the international leased carrier (ILC) communications passing through INTELSAT satellites was first revealed in James Bamford’s The Puzzle Palace. (Note 12)
The regulation reveals that Sugar Grove is associated with what has become a highly controversial program in Europe, North America, Australia, and New Zealand. The program, codenamed ECHELON, has been described as a global surveillance network that intercepts and processes the world’s communications and distributes it among the primary partners in the decades-old UKUSA alliance—the United States, Canada, the United Kingdom, Australia, and New Zealand. (Note 13)
In reality, ECHELON is a more limited program, allowing the UKUSA allies to specify intelligence requirements and automatically receive relevant intercepts obtained by the UKUSA facilities which intercept satellite communications (but not the U.S. facilities that receive data from SIGINT satellites). It is also limited by both technological barriers (the inability to develop word-spotting software so as to allow for the automatic processing of intercepted conversations) and the limitations imposed on collection activities by the UKUSA allies—at least as regards the citizens of those countries. (Note 14) Thus, the NAVSECGRU instruction also specifies that one of the responsibilities of the commander of the Sugar Grove site is to “ensure the privacy of U.S. citizens are properly safeguarded pursuant to the provisions of USSID 18.”
Document 14: Farewell from Vice Admiral William O. Studeman to NSA Employees, April 8, 1992
This address by the departing director of NSA, William Studeman, examines NSA’s post-Cold War mission, likely budgetary limitations, and other challenges facing the agency. Reflecting the increasing emphasis on “support to military operations,” Studeman notes that “the military account is basic to NSA as a defense agency, and the lack of utter faithfulness to this fact will court decline.” He also observes that “the demands for increased global access are growing” and that “these business areas (SMO and global access) will be the two, hopefully strong legs on which NSA must stand.” He also argues that “technical and operational innovation to deal with a changing and changed world must continue to dominate.”
Document 15: Letter, Stewart A. Baker, General Counsel, NSA to Gerald E. McDowell, Esq., September 9, 1992
In the wake of disclosures about the role of the Banca Nazionale del Lavoro (BNL), particularly its Atlanta branch, in the provision of financial assistance to the regime of Saddam Hussein, questions were raised about whether the intelligence community was providing sufficient support to law enforcement.
This letter, from NSA’s general counsel, answers a series of questions from the Justice Department pertaining to NSA’s knowledge of, or involvement in, BNL activities. The responses appear to indicate that NSA had not derived any intelligence concerning BNL activities from its intercept operations. The letter also stresses NSA’s sensitivity to the issue of the privacy of American citizens (noting that “NSA improperly targeted the communications of a number of Americans opposed to the Vietnam War”) and the restrictions on reporting information concerning U.S. citizens or corporations.
Document 16: “Activation of Echelon Units,” from History of the Air Intelligence Agency, 1 January – 31 December 1994, Volume I (San Antonio, TX: AIA, 1995)
The first extract from the Air Intelligence Agency’s 1994 annual history provides additional information on the ECHELON network. ECHELON units include components of the AIA’s 544th Intelligence Group. Detachment 2 and 3 are located at Sabana Seca, Puerto Rico and Sugar Grove, West Virginia respectively. The second reference to Detachment 3 is apparently a typo that should read Detachment 4 (located at Yakima, Washington). The deleted words appear to be “civilian communications,” “NAVSECGRU” and “NSA.”
The second extract notes that AIA’s participation in a classified activity “had been limited to LADYLOVE operations at Misawa AB [Air Base], Japan.” The Misawa LADYLOVE activity was initiated during the Cold War to intercept Soviet military communications transmitted via satellite—along with similar operations at Menwith Hill, UK; Bad Aibling, Germany; and Rosman, North Carolina. This extract suggests that both Guam and Misawa have, at the least, been considered as possible sites for ECHELON operations.
Document 17: NSA Point Paper, “SIGINT Reporting on Murders of Michael DeVine in 1990 and the Disappearance of Efraín Bamaca in 1992 in Guatemala,” March 24, 1995
On March 23, 1995, Rep. Robert Torricelli, a member of the House Permanent Select Committee on Intelligence, charged that the CIA had been withholding from Congress information it had obtained regarding the deaths of Michael DeVine, an American innkeeper living in Guatemala, and Efraín Bámaca Velásquez, a Guatemalan guerrilla leader and husband of an American lawyer. Both murders, according to Torricelli, were linked to a Guatemalan army colonel, Julio Roberto Alpírez, a paid intelligence asset of the CIA. (Note 15)
The revelations set off a firestorm of criticism and caused the Clinton administration to order a government-wide investigation over these and other cases of torture and murder attributed to Guatemalan security forces. While the CIA was the main target of such criticism, Torricelli had also reportedly received an anonymous fax from someone inside the NSA alleging that documents pertaining to the Bámaca and DeVine cases were being destroyed. (Note 16)
This Top Secret NSA position paper responds to these allegations. NSA claims that SIGINT reporting related to these cases is limited to “Guatemalan government reaction to U.S. and international human rights concerns,” and does not include specific information regarding the circumstances of death or the involvement of Colonel Alpírez. The document is one of only a handful of declassified records in which the NSA even acknowledges specific SIGINT activities or reports.
Document 18: Memorandum, Daniel C. Kurtzer, Acting Assitant Secretary, Bureau of Intelligence and Research to Vice Admiral J.M. McConnell, Director, National Security Agency, Subject: Proposed Declassification of the “Fact of” Overhead SIGINT Collection, September 6, 1995
In 1978, President Jimmy Carter acknowledged that the U.S. employed reconnaissance satellites to collect imagery of foreign targets. Early in 1995, President Clinton declassified details concerning early satellite imagery programs such as CORONA. However, even the existence of SIGINT satellites remained classified until late 1995 when Director of Central Intelligence John Deutch authorized the official acknowledgement of space-based SIGINT operations. (Note 17)
The process involved soliciting the opinions of U.S. government departments whose interests might be affected by disclosure. The State Department’s memo expressed concern about the impact in certain countries. Despite the deletions, it is clear that the department was anxious about the impact in the foreign countries where the U.S. operates ground stations for SIGINT satellites—the United Kingdom (at Menwith Hill), Germany (at Bad Aibling), and Australia (at Pine Gap). The memo also indicates that the proposal for declassification emanated from the National Reconnaissance Office.
Document 19: NSA, Recent Classification Decisions, June 2, 1998. Confidential
The increased openness at NSA in the late 1990s extended to historical as well as contemporary matters. In addition to memos announcing individual declassification decisions, summary memos were also issued on occasion. This one covers declassification decisions with regard to a number of categories, including signals intelligence targeting, NSA’s presence abroad, the use of airborne platforms for SIGINT collection, and the codenames used to indicate intelligence obtained from communications or electronic intelligence collection.
Document 20: Organization Chart, NSA Operations Directorate, November 6, 1998
The organization chart of NSA’s Directorate of Operations is notable for several reasons. Traditionally, such information was not released by NSA, which under the provisions of Public Law 86-36 is not required to release even unclassified organizational information. In recent years, however, NSA has released more information about organization and administrative matters, and acknowledged the use of a variety of aircraft for SIGINT collection.
The organization chart also shows how the operations directorate has been reorganized since the end of the Cold War. Throughout much of the Cold War, the directorate consisted of three key regional groups—A (Soviet Bloc), B (Asian Communist), and G (All Other). After the Soviet collapse the regional groups were reduced to one for European nations and one for all other. The new organizational structure reflects the increasing empahsis on transnational activities, which cut across nations and regions.
New Document 21: James R. Taylor, Deputy Director of Operations, Subject: Thoughts on Strategic Issues for the Institution, April 9, 1999. Secret
This memorandum was written early in the tenure of NSA Director Lt. Gen. Michael Hayden, when much attention was being directed to the requirement for NSA to adapt to a new environment – which included new targets, communications technologies, and the availability of advanced encryption techniques.
Taylor notes that money and technology, while among the top five issues facing NSA, are not among the first three. The first and most important issue, according to Taylor, was NSA’s need to reform the management and leadership system. His discussion foreshadowed Hayden’s reorganization of NSA to clearly establish the primacy of the two components – the directorates for signals intelligence and information assurance – responsible for carrying out NSA’s fundamental missions.
A second key issue identified in the memo is the “strengthening and leveraging of [NSA’s] strategic alliances.” This includes NSA’s relationships with foreign SIGINT services, the CIA, and the service cryptologic elements (SCE’s) that carry out much of the collection work for NSA. The discussion of NSA’s relationship with the CIA indicates the increasing importance of human intelligence support to NSA – which can come in the form of acquisition of cipher materials or the clandestine placement of eavesdropping equipment.
The third issue identified is the need to properly staff “our two missions and to spot and nurture talent and leadership for the future.”
New Document 22: Lt. Gen. Jim Clapper, NSA Scientific Advisory Board, Panel on Digital Network Intelligence (DNI), Report to the Director, June 28, 1999, Secret Comint
This study, a complement to another study on conventional collection, is another example of NSA’s attempt to address the changing communication environment. Digital network intelligence is defined as “the intelligence from intercepted digital data communications transmitted between, or resident on, networked computers.”
The study, which has been heavily redacted prior to release, notes an imperative to “re-tool: organizationally, programmatically, and technologically” and examines issues concerning the access and collection of digital network intelligence, processing and extraction of intelligence from the data collected, analysis and reporting, and dissemination.
New Document 23: SSO [Special Security Office], DIA Subject: Implementation Guidance for Elimination of Codewords, October 22, 1999. Unclassified
During the Cold War, as an extension of the system developed in World War II to protect the security of communications intelligence operations, the U.S. established the category of Special Intelligence (SI). Within SI were a number of compartments, which corresponded to the different degrees of sensitivity attached to communications intelligence activities and products. In 1960, with the launch of the first reconnaissance satellites, the U.S. also established the TALENT-KEYHOLE (TK) system, with compartments for satellite imagery (RUFF), satellite ELINT (ZARF), and aerial imagery from the U-2, and later, SR-71.
This message reflects the attempt to simplify the system by eliminating three key codenames from the SI category and one from the TK system.
Document 24: Statement for the Record of NSA Director Lt Gen Michael V. Hayden, USAF before the House Permanent Select Committee on Intelligence, April 12, 2000
In a rare public appearance by the NSA director, Lt. Gen. Michael Hayden outlines the regulatory safeguards and oversight mechanisms that are in place to ensure that the agency’s electronic surveillance mission does not infringe upon the privacy of U.S. persons, and to respond to recent allegations that NSA provides intelligence information to U.S. companies.
The agency may only target the communications of U.S. persons within the United States after obtaining a federal court order suggesting that the individual might be “an agent of a foreign power.” The number of such cases have been “very few” since the passage of the Foreign Intelligence Surveillance Act in 1978. In cases where the NSA wishes to conduct electronic surveillance on U.S. persons overseas, the agency must first obtain the approval of the Attorney General, who must have probable cause to believe that the individual “is an agent of a foreign power, or a spy, terrorist, saboteur, or someone who aides or abets them.” With regard to the unintentional collection of communications to, from, or about U.S. citizens, Hayden stresses that such information is not retained “unless the information is necessary to understand a particular piece of foreign intelligence or assess its importance.”
In response to other allegations, Hayden asserts that NSA cannot request that another country “illegally” collect intelligence on U.S. persons on their behalf, and also that the agency “is not authorized to provide signals intelligence information to private U.S. companies.”
New Document 25: National Security Agency, Transition 2001, December 2000. Secret
This document, prepared for the incoming administration of George W. Bush, was intended to provide a background on NSA’s organization and mission, as well as of the issues facing NSA in the years ahead. Its main sections include those devoted to management, external process, budget, and personnel, policy/issues.
In the discussion of major policy issues, the document notes the changing environment in which the “analog world of point-to-point communications carried along discrete, dedicated voice channels” is being replaced by communications that are “mostly digital, carry billions of bits of data, and contain voice, data and multimedia.” In addition, it states that “global networks leave US critical information infrastructure more vulnerable to foreign intelligence operations and to compromise by a host of non-state entities.” The creation of global networks also requires, according to the transition book, that “senior leadership understand that today’s and tomorrow’s mission will demand a powerful, permanent presence on a global telecommunications network that will host the ‘protected’ communications of Americans as well as targeted communications of adversaries.”
New Document 26a: Organization Chart, Signals Intelligence Directorate
New Document 26b: Organization Chart, Information Assurance Directorate
These two heavily redacted organization charts are more informative for what they reveal about the change in NSA’s classification policy than for what they reveal about the 2001 organizational structure of NSA’s two key directorates.
In contrast to Document 19, the largely intact 1998 organization chart for the Directorate of Operations, Document 26a, the chart for the Signals Intelligence Directorate (as the operations directorate was renamed) contains no information beyond the name of its director. The late 1990s was a period when NSA significantly loosened restrictions on information – not only historical information, but then current organizational information. As a result the operations directorate organization chart was provided within three weeks of its being requested in late 1998. In contrast, the request for the Signals Intelligence Directorate organization chart was made on April 21, 2001 and NSA provided its substantive response on April 21, 2004.
Similarly, in the late 1990s, NSA released detailed organizational information on its Information Security directorate, in contrast to the small amount of it detail it has released on the successor Information Assurance Directorate.
Document 27: Statement for the Record by Lieutenant General Michael V. Hayden, Director, National Security Agency/Central Security Service Before the Joint Inquiry of the Senate Select Committee on Intelligence and the House Permanent Select Committee on Intelligence, October 17, 2002, Unclassified
Hayden, in his testimony to the joint committee intelligence performance prior to the terrorist attacks on New York and Washington of September 11, 2001, addresses three major questions: what did NSA know prior to September 11, what did NSA learn in retrospect, and what had NSA done in response? In his conclusions, Hayden addresses a number of issues – including the relationship between SIGINT and law enforcement, and the line between the government’s need for counterterrorism information and the privacy interests of individuals residing in the United States.
Notes
1. Report to the Secretary of State and the Secretary of Defense by a Special Committee Appointed Pursuant to Letter of 28 December 1951 to Survey Communications Intelligence Activities of the Government, June 13, 1952, pp. 47-48, 119; RG 457, SR-123, Military Reference Branch, NARA; The National Cryptologic School, On Watch: Profiles from the National Security Agency’s Past 40 Years (Ft. Meade, Md.: NCS, 1986), p. 17.
2. Walter Bedell Smith, “Proposed Survey of Communications Intelligence Activities,” December 10, 1951; Report to the Secretary of State and the Secretary of Defense by a Special Committee, p. 118; U.S. Congress, Senate Select Committee to Study Governmental Operations with Respect to Intelligence Activities, Final Report, Book III: Foreign and Military Intelligence (Washington, D.C.: U.S. Government Printing Office, 1976), p. 736; National Security Agency/Central Security Service, NSA/CSS Manual 22-1 (Ft. Meade, MD: NSA, 1986), p. 1.
3. National Security Agency, NSA/CSS Manual 22-1 (Ft. Meade, Md.: NSA, 1986), p. 7.
4. Jeffrey T. Richelson, The Wizards of Langley: Inside the CIA’s Directorate of Science and Technology (Boulder, Co.: Westview, 2001), p. 60.
5. Richard M. Bissell Jr. with Jonathan E. Lewis and Frances T. Pudlo, Reflections of a Cold Warrior: From Yalta to the Bay of Pigs (New Haven, Ct.: Yale University Press, 1996), p. 239.
6. James Bamford, The Puzzle Palace: A Report on NSA, America’s Most Secret Agency (Boston: Houghton-Mifflin, 1982), p. 334.
7. Stansfield Turner, Secrecy and Democracy: The CIA in Transition (Boston: Houghton-Mifflin, 1985), pp. 235-236.
8. James Bamford, Body of Secrets: Anatomy of the Ultra-Secret National Security Agency (New York: Doubleday, 2001), pp. 185-239; A. Jay Cristol, The Liberty Incident: The 1967 Israeli Attack on the U.S. Navy Spy Ship (Washington, D.C.: Brassey’s 2002); James M. Ennes Jr., Assault on the Liberty: The True Story of the Israeli Attack on an American Intelligence Ship (New York: Ivy, 1979).
9. Bob Woodward, “Messages of Activists Intercepted,” Washington Post, October 13, 1975, pp. A1, A14.
10. See Jeffrey T. Richelson, The U.S. Intelligence Community (Cambridge: Ballinger, 2nd ed., 1989/Boulder: Westview Press, 3rd ed., 1995; 4th ed., 1999); See also the World Wide Web site of the Federation of American Scientists, http://fas.org/irp/offdocs/dcid16.htm
11. Lois G. Brown, “National SIGINT Committee,” NSA Newsletter, February 1997, p. 2.
12. James Bamford, The Puzzle Palace: A Report on NSA, America’s Most Secret Agency (Boston, MA: Houghton-Mifflin, 1982), p. 170.
13. Patrick S. Poole, ECHELON: America’s Secret Global Surveillance Network (Washington, D.C.: Free Congress Foundation, October 1998).
14. Duncan Campbell, Interception Capabilities 2000 (Luxembourg: European Parliament, 1999); Jeffrey T. Richelson, “Desperately Seeking Signals,” Bulletin of the Atomic Scientists, Vol. 56, No. 2, pp. 47-51.
15. Dana Priest, “Torricelli Admits Violating House Secrecy Oath,” Washington Post, April 8, 1995, p. A7.
16. Kim Masters, “Truth or Consequences; Rep. Bob Torricelli Leaked the Goods on the CIA. Was It Loyalty or Betrayal?” Washington Post, April 17, 1995, p. C1.
17. DIRNSA, “Fact of Overhead SIGINT Collection,” January 4, 1996.
SECRET- Tracking Cell Phones and Vehicles: The Legal Context
A new report from the Congressional Research Service explores ongoing legal debates over the tracking of private cell phones and vehicles by law enforcement agencies.
“It is undeniable that… advances in technology threaten to diminish privacy,” the CRS report says. “Law enforcement’s use of cell phones and GPS devices to track an individual’s movements brings into sharp relief the challenge of reconciling technology, privacy, and law.”
The 22 page CRS report provides a survey of relevant Fourth Amendment law, federal electronic surveillance statutes and case law, pending GPS-vehicle tracking cases, and electronic surveillance legislation that is before Congress.
“The primary debate surrounding cell phone and GPS tracking is not whether they are permitted by statute but rather what legal standard should apply: probable cause, reasonable suspicion, or something less,” the report says.
A copy of the CRS report was obtaine. See “Governmental Tracking of Cell Phones and Vehicles: The Confluence of Privacy, Technology, and Law,” December 1, 2011.
Download Original Document here
CONFIDENTIAL-UNCENSORED – Greece Riot Photos December 2011
 Riot police try to avoid molotov cocktails and stones trown by demonstrators outside parliament in Athens on December 6, 2011 during a demonstration to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO/ LOUISA GOULIAMAKI
Riot police try to avoid molotov cocktails and stones trown by demonstrators outside parliament in Athens on December 6, 2011 during a demonstration to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO/ LOUISA GOULIAMAKI A masked youth throws a petrol bomb at police in Athens’ Syntagma (Constitution) square during clashes December 6, 2011. Greek police fired tear gas on Tuesday at dozens of black-clad protesters in Athens who hurled petrol bombs and stones, while hundreds marched to parliament to mark the 2008 shooting of a student by police. REUTERS/Yannis Behrakis
A masked youth throws a petrol bomb at police in Athens’ Syntagma (Constitution) square during clashes December 6, 2011. Greek police fired tear gas on Tuesday at dozens of black-clad protesters in Athens who hurled petrol bombs and stones, while hundreds marched to parliament to mark the 2008 shooting of a student by police. REUTERS/Yannis Behrakis Youths clash with riot police outside the parliament during a demonstration in Athens on December 6, 2011, to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO/ Angelos Tzortzinis
Youths clash with riot police outside the parliament during a demonstration in Athens on December 6, 2011, to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO/ Angelos Tzortzinis A protester throws looks towards riot police by the parliament in Athens on December 6, 2011 during a demonstration to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO/ LOUISA GOULIAMAKI
A protester throws looks towards riot police by the parliament in Athens on December 6, 2011 during a demonstration to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO/ LOUISA GOULIAMAKI A protester carries a petrol bomb during a protest at the northern port city of Thessaloniki, Greece, Tuesday, Dec. 6, 2011. Protesting high school students hurled rocks and bottles during a rally to mark the third anniversary of the fatal police shooting of a teenager in central Athens. (AP Photo/Nikolas Giakoumidis)
A protester carries a petrol bomb during a protest at the northern port city of Thessaloniki, Greece, Tuesday, Dec. 6, 2011. Protesting high school students hurled rocks and bottles during a rally to mark the third anniversary of the fatal police shooting of a teenager in central Athens. (AP Photo/Nikolas Giakoumidis) A youth gathers stones near the parliament in Athens on December 6, 2011 during a demonstration to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO/ LOUISA GOULIAMAKI
A youth gathers stones near the parliament in Athens on December 6, 2011 during a demonstration to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO/ LOUISA GOULIAMAKI Riot police look on as a molotov cocktail thrown by youths exploeds in front of the parliament in Athens on December 6, 2011 during a demonstration to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO/ARIS MESSINIS
Riot police look on as a molotov cocktail thrown by youths exploeds in front of the parliament in Athens on December 6, 2011 during a demonstration to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO/ARIS MESSINIS Riot police chase a youth during clashes outside the parliament on December 6, 2011, as about 1,000 school pupils marched to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO / ARIS MESSINIS
Riot police chase a youth during clashes outside the parliament on December 6, 2011, as about 1,000 school pupils marched to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO / ARIS MESSINIS Youths clash with riot police outside the parliament during a demonstration on December 6, 2011, to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO / ARIS MESSINIS
Youths clash with riot police outside the parliament during a demonstration on December 6, 2011, to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO / ARIS MESSINIS Youths clash with riot police outside the parliament during a demonstration on December 6, 2011, to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO / ARIS MESSINIS
Youths clash with riot police outside the parliament during a demonstration on December 6, 2011, to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO / ARIS MESSINIS A protester throws a petrol bomb against riot police guarding the parliament in Athens’ Syntagma (Constitution) square during clashes December 6, 2011. Greek police fired tear gas on Tuesday at dozens of black-clad protesters in Athens who hurled petrol bombs and stones, while hundreds marched to parliament to mark the 2008 shooting of a student by police. REUTERS/Yannis Behrakis
A protester throws a petrol bomb against riot police guarding the parliament in Athens’ Syntagma (Constitution) square during clashes December 6, 2011. Greek police fired tear gas on Tuesday at dozens of black-clad protesters in Athens who hurled petrol bombs and stones, while hundreds marched to parliament to mark the 2008 shooting of a student by police. REUTERS/Yannis Behrakis ATHENS, GREECE – DECEMBER 6: Cars are parked in front of graffiti displayed on a building on December 6, 2011 in Athens, Greece. Graffiti artists throughout the city are expressing the effects of austerity measures that have plagued the community as Greece continues to struggle in debt while lawmakers today are set to pass next year’s budget. (Photo by Milos Bicanski/Getty Images)
ATHENS, GREECE – DECEMBER 6: Cars are parked in front of graffiti displayed on a building on December 6, 2011 in Athens, Greece. Graffiti artists throughout the city are expressing the effects of austerity measures that have plagued the community as Greece continues to struggle in debt while lawmakers today are set to pass next year’s budget. (Photo by Milos Bicanski/Getty Images) Riot police walk past burning debris outside the parliament in Athens on December 6, 2011, during demonstrations to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO/ Angelos Tzortzinis
Riot police walk past burning debris outside the parliament in Athens on December 6, 2011, during demonstrations to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO/ Angelos Tzortzinis A protester throws a petrol bomb towards riot police guarding the parliament in Athens’ Syntagma (Constitution) square during evening clashes December 6, 2011. Fresh clashes broke out between demonstrators and Greek police outside parliament on Tuesday evening, hours after police fired teargas to disperse youths hurling petrol bombs at them.Protesters, many dressed in black, threw makeshift bombs and stones at police, who responded with teargas and formed a cordon outside parliament. Inside, lawmakers were in the final stages of a debate on the 2012 budget packed with unpopular austerity measures. REUTERS/Yannis Behrakis
A protester throws a petrol bomb towards riot police guarding the parliament in Athens’ Syntagma (Constitution) square during evening clashes December 6, 2011. Fresh clashes broke out between demonstrators and Greek police outside parliament on Tuesday evening, hours after police fired teargas to disperse youths hurling petrol bombs at them.Protesters, many dressed in black, threw makeshift bombs and stones at police, who responded with teargas and formed a cordon outside parliament. Inside, lawmakers were in the final stages of a debate on the 2012 budget packed with unpopular austerity measures. REUTERS/Yannis Behrakis A protestor throws a stone at riot police outside the parliament in Athens on December 6, 2011, during demonstrations to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO/ Angelos Tzortzinis
A protestor throws a stone at riot police outside the parliament in Athens on December 6, 2011, during demonstrations to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis. AFP PHOTO/ Angelos Tzortzinis A protestor throws a molotov cocktail at riot police outside the parliament in Athens on December 6, 2011, during demonstrations to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis.
A protestor throws a molotov cocktail at riot police outside the parliament in Athens on December 6, 2011, during demonstrations to commemorate the police killing of a student three years ago which sparked violent riots lasting weeks. Pupils and students marched to mark the December 6, 2008 death of Alexis Grigoropoulos, 15, shot by police as Greece first came under pressure from the eurozone debt crisis.FEMEN-UNCUT-UNCENSORED-Stop Raping Ukraine!
Members of the activist group FEMEN protest at what they see as the manipulation of the democratic system at a polling station in Kiev, Ukraine, Sunday, Feb. 7, 2010. The signs read “The War Begins Here” and “Stop Raping the Country.”
http://www.tsn.ua
TOP-SECRET-CIA Bucharest Prison Eyeball
| In northern Bucharest, in a busy residential neighborhood minutes from the center of Romania’s capital city, is a secret that the Romanian government has tried for years to protect.
For years, the CIA used a government building — codenamed Bright Light — as a makeshift prison for its most valuable detainees. There, it held al-Qaida operatives Khalid Sheik Mohammad, the mastermind of 9/11, and others in a basement prison before they were ultimately transferred to Guantanamo Bay in 2006, according to former U.S. intelligence officials familiar with the location and inner workings of the prison. The existence of a CIA prison in Romania has been widely reported but its location has never been made public until a joint investigation by The Associated Press and German public television, ARD Panorama. The news organizations located the former prison and learned details of the facility where harsh interrogation tactics were used. ARD’s program on the CIA prison will air Dec 8. The Romanian prison was part of a network of so-called black sites that the CIA operated and controlled overseas in Thailand, Lithuania and Poland. All the prisons were closed by May 2006, and the CIA’s detention and interrogation program ended in 2009. Unlike the CIA’s facility in Lithuania’s countryside or the one hidden in a Polish military installation, the CIA’s prison in Romania was not in a remote location. It was hidden in plain sight, a couple blocks off a major boulevard on a street lined with trees and homes, along busy train tracks. The building is used as the National Registry Office for Classified Information, which is also known as ORNISS. Classified information from NATO and the European Union is stored there. Former intelligence officials both described the location of the prison and identified pictures of the building. |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict13.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict11.jpg)
|
| Google Mapshttp://bit.ly/vDKcPW
|
CIA Prisoner Unloading Route via Side Street According to AP. 2005 Aerial Photo (Google Earth).![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict14.jpg) |
| Following oblique views by Bing.com/maps: http://binged.it/vAOoi0 |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict4.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict5.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict7.jpg) |
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict8.jpg) |
“Kinder-Portal” und Analwahn – “GoMoPa” und der “Scheisshausfliegenblog” – Vorbestrafte Betrüger und STASI-Schergen
Liebe Leser,
über 4.000 Menschen und Firmen wurden und werden von STASI-”GoMoPa” gestalkt und erpresst. Nunmehr auch und vor allem der Berliner Justizsenator Braun.
Offensichtlich bewegen sich die STASI-Schergen von STASI-Oberst Ehrenfried Stelzer und seiner Nachfolger in Berlin und Ostdeutschland wie weiland der Nationalsozialistische Untergrund unbehelligt von der Polizei und Justiz – die STASI-Seilschaften in der SED-Nachfolge-Organisation “Linke” sowie ein Netzwerk in Medien, Blogs – aber anscheinend auch in der Justiz und der Polizei und bei Google unterstützen sie dabei mutmasslich.
Ihr “Kinder-Portal” mit Sexualaufklärung für Kinder, Tausende von Rufmorden und Erpressungen, mysteriöse Todesfälle all das hat es so bisher noch nie weltweit in einer kriminellen Organisation gegeben.
Dies hat zu einem – so erste Schätzungen von Schadensexperten – Schaden von über € 1 Milliarde geführt, nimmt man als Berechnungsgrundlage
die im Falle von Meridian Capital geforderte Erpressungssumme.
Der immaterielle Schäden durch zerstörte menschliche Leben und Schicksale, dieser “Dämonen im Internet” (Eigenbezeichnung von Ober-Stalker “Klaus Maurischat”) ist noch viel höher und nur mit dem von der DDR-Gestapo angerichteten Schaden vergleichbar, deren Nachfolgeorganisation die fingierten “Goldman, Morgenstern u. Partner” – “GoMoPa” zweifelsohne sind.
Darunter sind auch etliche Todesfälle und viele Personen und Firmen, die nicht auf der 4.000 Fälle umfassenden “Warnliste”, besser Stalking, Betrugs- und Erpresserliste auftauchen.
Organisierte Kriminalität im ganz grossen Stil.
Müssen erst Opfer mit gezielt mit Schüssen Bomben attackiert werden ´, bevor der Verfassungsschutz und andere Behörden in Gang kommen?
Im Ausland schüttlet man über Deutschland mittlerweile den Kopf und niemand versteht, wie so etwas möglich ist.
Herzlichst Ihr
Bernd Pulch
Magister Artium der Publizistik, Germanistik und Komparatistik
TOP-SECRET – NSA- THE NRO DECLASSIFIED

n September 1992 the Department of Defense acknowledged the existence of the National Reconnaissance Office (NRO), an agency established in 1961 to manage the development and operation of the nation’s reconnaissance satellite systems. The creation of the NRO was the result of a number of factors.
On May 1, 1960 Francis Gary Powers took off from Peshawar, Pakistan on the U-2 mission designated Operation GRAND SLAM. The flight was planned to take him over the heart of the Soviet Union and terminate at Bodo, Norway. The main target was Plesetsk, which communications intercepts had indicated might be the site of an ICBM facility.1 When the Soviet Union shot down his plane and captured him alive, they also forced President Dwight Eisenhower to halt aerial overflights of Soviet territory.
At that time the U.S. had two ongoing programs to produce satellite vehicles that could photograph Soviet territory. Such vehicles would allow far more frequent coverage than possible with manned aircraft. In addition, they would avoid placing the lives of pilots at risk and eliminate the risks of international incidents resulting from overflights.
The Air Force program, designated SAMOS, sought to develop a number of different satellite systems–including one that would radio its imagery back to earth and another that would return film capsules. The CIA program, CORONA, focused solely on developing a film return satellite.
However, both the CIA and Air Force programs were in trouble. Launch after launch in the CORONA program, eleven in all by May 1, 1960, eight of which carried cameras, had resulted in failure–the only variation was in the cause. Meanwhile, the SAMOS program was also experiencing difficulties, both with regard to hardware and program definition.2
Concerns over SAMOS led President Eisenhower to direct two groups to study both the technical aspects of the program as well as how the resulting system would be employed. The ultimate result was a joint report presented to the President and NSC on August 25, 1960.3
As a result of that meeting Eisenhower approved a first SAMOS launch in September, as well as reorientation of the program, with the development of high-resolution film-return systems being assigned highest priority while the electronic readout system would be pursued as a research project. With regard to SAMOS management, he ordered that the Air Force institute special management arrangements, which would involve a direct line of authority between the SAMOS project office and the Office of the Air Force Secretary, bypassing the Air Staff and any other intermediate layers of bureaucracy.4
Secretary of the Air Force Dudley C. Sharp wasted little time creating the recommended new structure and procedures. On August 31st Sharp signed Secretary of the Air Force Order 115.1, establishing the Office of Missile and Satellite Systems within his own office to help him manage the SAMOS project. With Order 116.1, Sharp created a SAMOS project office at the Los Angeles headquarters of the Air Force Ballistic Missile Division (AFBMD) as a field extension of the Office of the Secretary of the Air Force to carry out development of the satellite.5
The impact of the orders, in practice, was that the director of the SAMOS project would report directly to Under Secretary of the Air Force Joseph V. Charyk, who would manage it in the Secretary’s name. In turn, Charyk would report directly to the Secretary of Defense.6
The changes would not stop there. The urgency attached to developing a successful reconnaissance satellite led, ultimately, to the creation of a top secret program and organization to coordinate the entire national reconnaissance effort.
Several of the documents listed below also appear in either of two National Security Archive microfiche collections on U.S. intelligence. The U.S. Intelligence Community: Organization, Operations and Management: 1947-1989 (1990) and U.S. Espionage and Intelligence: Organization, Operations, and Management, 1947-1996 (1997) publish together for the first time recently declassified documents pertaining to the organizational structure, operations and management of the U.S. Intelligence Community over the last fifty years, cross-indexed for maximum accessibility. Together, these two sets reproduce on microfiche over 2,000 organizational histories, memoranda, manuals, regulations, directives, reports, and studies, totaling more than 50,000 pages of documents from the Office of the Director of Central Intelligence, the Central Intelligence Agency, National Reconnaissance Office, National Security Agency, Defense Intelligence Agency, military service intelligence organizations, National Security Council, and other official government agencies and organizations.
Document 1
Joseph Charyk, Memorandum for the Secretary of Defense
Management of the National Reconnaissance Program
24 July 1961
Top Secret
1 p.
The organizational changes resulting from the decisions of August 25, 1960 and their implementation left some unsatisfied. In particular, James Killian and Edwin Land, influential members of the President’s intelligence advisory board pushed for permanent and institutionalized collaboration between the CIA and Air Force. After the Kennedy administration took office the push to establish a permanent reconnaissance organization took on additional life. There was a strong feeling in the new administration, particularly by Secretary of Defense Robert McNamara and his deputy, Roswell Gilpatric, that a better, more formalized relationship was required.7
On July 24, 1961, Air Force Undersecretary Joseph Charyk sent a memorandum to McNamara attaching two possible memoranda of agreement for creation of a National Reconnaissance Program, along with some additional material.
Document 2
Memorandum of Understanding
Management of the National Reconnaissance Program (Draft)
20 July 1961
Top Secret
5 pp.
This memo specified establishment of a National Reconnaissance Program (NRP) consisting of “all satellite and overflight reconnaissance projects whether overt or covert,” and including “all photographic projects for intelligence, geodesy and mapping purposes, and electronic signal collection projects for electronic signal intelligence and communications intelligence.”
To manage the NRP, a National Reconnaissance Office (NRO) would be established on a covert basis. The NRO director (DNRO) would be the Deputy Director for Plans, CIA (at the time, Richard Bissell) while the Under Secretary of the Air Force would serve as Deputy Director (DDNRO). The DNRO would be responsible for the management of CIA activities, the DDNRO and the Air Force for Defense Department activities. The DoD, specifically the Air Force acting as executive agent, would be primarily responsible for technical program management, scheduling, vehicle operations, financial management and overt contract administration, while the CIA would be primarily responsible for targeting each satellite. The office would operate under streamlined management procedures similar to those established in August 1960 for SAMOS.
Document 3
Memorandum of Understanding
Management of the National Reconnaissance Program (Draft)
21 July 1961
Top Secret
4 pp.
This secondary memorandum was prepared at the suggestion of Defense Department General Counsel Cyrus Vance. It offered a quite different solution to the problem. As with the primary memo, it established a NRP covering both satellite and aerial reconnaissance operations. But rather than a jointly run program, it placed responsibility for management solely in the hands of a covertly appointed Special Assistant for Reconnaissance, to be selected by the Secretary of Defense. The office of the Special Assistant would handle the responsibilities assigned to the NRO in the other MOU. The CIA would “assist the Department of Defense by providing support as required in areas of program security, communications, and covert contract administration.”
Document 4
Memorandum
Pros and Cons of Each Solution
Not dated
Top Secret
2 pp.
The assessment of pros and cons favored the July 20 memorandum, listing five pros for the first solution and only two for the second. The first solution would consolidate responsibilities into a single program with relatively little disruption of established management, represented a proven solution, would require no overt organizational changes, would allow both agencies to retain authoritative voices in their areas of expertise, and provided a simplified management structure. The two cons noted were the division of program responsibility between two people, and that “successful program management depends upon mutual understanding and trust of the two people in charge of the NRO.” It would not be too long before that later observation would take on great significance.
In contrast, there were more cons than pros specified for the second solution. The only two points in its favor were the consolidation of reconnaissance activities into a single program managed by a single individual and the assignment of complete responsibility to the agency (DoD) with the most resources. Foremost of the six cons was the need for DoD to control and conduct large-scale covert operations, in as much as it was an entity “whose normal methods are completely foreign to this task.”
Document 5
Roswell Gilpatric, Letter to Allen Dulles
Management of the National Reconnaissance Program
6 September 1961
Top Secret
4 pp.
On July 28, 1961, four days after receiving Charyk’s memorandum and draft memoranda of understanding, McNamara instructed Air Force Undersecretary Joseph Charyk to continue discussions with the key officials and advisers in order to resolve any organizational difficulties that threatened to impede the satellite reconnaissance effort. The ultimate result was this letter from Deputy Secretary of Defense Roswell Gilpatric to Dulles, which confirmed “our agreement with respect to the setting up of the National Reconnaissance Program.”
The letter specified the creation of a NRP. It also established the NRO, a uniform security control system, and specified that the NRO would be directly responsive to the intelligence requirements and priorities specified by the United States Intelligence Board. It specified implementation of NRP programs assigned to the CIA through the Deputy Director for Plans. It designated the Undersecretary of the Air Force as the Defense Secretary’s Special Assistant for Reconnaissance, with full authority in DoD reconnaissance matters.
The letter contained no specific assignment of responsibilities to either the CIA or Defense Department, stating only that “The Directors of the National Reconnaissance Office will … insure that the particular talents, experience and capabilities within the Department of Defense and the Central Intelligence Agency are fully and most effectively utilized in this program.”
The letter provided for the NRO to be managed jointly by the Under Secretary of the Air Force and the CIA Deputy Director for Plans (at the time, still Richard Bissell). A May 1962 agreement between the CIA and Defense Department established a single NRO director. Joseph Charyk was named to the directorship shortly afterward.
Document 6
Joseph Charyk
Memorandum for NRO Program Directors/Director, NRO Staff
Organization and Functions of the NRO
23 July 1962
Top Secret
11 pp.
This memorandum represents the fundamental directive on the organization and functions of the NRO. In addition to the Director (there was no provision for a deputy director), there were four major elements to the NRO–the NRO staff and three program elements, designated A, B, and C. The staff’s functions included assisting the director in dealing with the USIB and the principal consumers of the intelligence collected.
The Air Force Office of Special Projects (the successor to the SAMOS project office) became NRO’s Program A. The CIA reconnaissance effort was designated Program B, while the Navy’s space reconnaissance effort, at the time consisting of the Galactic Radiation and Background (GRAB) satellite, whose radar ferret mission involved the collection of Soviet radar signals, became Program C. Although the GRAB effort was carried out by the Naval Research Laboratory, the director of the Office of Naval Intelligence would serve as Program C director until 1971.8
Document 7
Agreement between the Secretary of Defense and the Director of Central Intelligence on Management of the National Reconnaissance Program
13 March 1963
Top Secret
6 pp.
In December 1962, Joseph Charyk decided to leave government to become president of the COMSAT Corporation. By that time a number of disputes between the CIA and NRO had contributed to Charyk’s view that the position of the NRO and its director should be strengthened. During the last week of February 1963, his last week in office, he completed a revision of a CIA draft of a new reconnaissance agreement to replace the May 1962 agreement (which had replaced the September 6, 1961 agreement). Charyk took the revision to Deputy Secretary of Defense Roswell Gilpatric. It appears that some CIA-suggested changes were incorporated sometime after Charyk left office. On March 13, Gilpatric signed the slightly modified version on behalf of DoD. It was sent to the CIA that day and immediately approved by DCI John McCone, who had replaced Allen Dulles in November 1961.9
The new agreement, while it did not include all the elements Charyk considered important, did substantially strengthen the authority of the NRO and its director. It named the Secretary of Defense as the Executive Agent for the NRP. The program would be “developed, managed, and conducted in accordance with policies and guidance jointly agreed to by the Secretary of Defense and the Director of Central Intelligence.”
The NRO would manage the NRP “under the direction, authority, and control of the Secretary of Defense.” The NRO’s director would be selected by the Defense Secretary with the concurrence of the DCI, and report to the Defense Secretary. The NRO director was charged with presenting to the Secretary of Defense “all projects” for intelligence collection and mapping and geodetic information via overflights and the associated budgets, scheduling all overflight missions in the NRP, as well as engineering analysis to correct problems with collection systems. With regard to technical management, the DNRO was to “assign all project tasks such as technical management, contracting etc., to appropriate elements of the DoD and CIA, changing such assignments, and taking any such steps he may determine necessary to the efficient management of the NRP.”
Document 8
Department of Defense Directive Number TS 5105.23
Subject: National Reconnaissance Office
27 March 1964
Top Secret
4 pp.
This directive replaced the original June 1962 DoD Directive on the NRO, and remains in force today. The directive specifies the role of the Director of the NRO, the relationships between the NRO and other organizations, the director’s authorities, and security. It specified that documents or other material concerning National Reconnaissance Program matters would be handled within a special security system (known as the BYEMAN Control System).
Document 9
President’s Foreign Intelligence Advisory Board
Memorandum for the President
Subject: National Reconnaissance Program
2 May 1964
Top Secret
11 pp.
The 1963 CIA-DoD agreement on the NRP did not end the battles between the CIA and NRO–as some key CIA officials, including ultimately DCI John McCone, sought to reestablish a major role for the CIA in the satellite reconnaissance effort. The continuing conflict was examined by the PFIAB.
The board concluded that “the National Reconnaissance Program despite its achievements, has not yet reached its full potential.” The fundamental cause for the NRP’s shortcomings was “inadequacies in organizational structure.” In addition, there was no clear division of responsibilities and roles between the Defense Department, CIA, and the DCI.
The recommendations of the board represented a clear victory for the NRO and its director. The DCI should have a “large and important role” in establishing intelligence collection requirements and in ensuring that the data collected was effectively exploited, according to the board. In addition, his leadership would be a key factor in the work of the United States Intelligence Board relating to the scheduling of space and airborne reconnaissance missions.
But the board also recommended that President Johnson sign a directive which would assign to NRO’s Air Force component (the Air Force Office of Special Projects) systems engineering, procurement, and operation of all satellite reconnaissance systems.
Document 10
Agreement for Reorganization of the National Reconnaissance Program
13 August 1965
Top Secret
6 pp.
Despite the recommendations of the May 2, 1964 PFIAB report, which were challenged by DCI John McCone, no action was taken to solidify the position of the NRO and its director. Instead prolonged discussions over a new agreement continued into the summer of 1965. During this period the CIA continued work on what would become two key satellite programs–the HEXAGON/KH-9 imaging and RHYOLITE signals intelligence satellites.
In early August, Deputy Secretary of Defense Cyrus Vance and CIA official John Bross reached an understanding on a new agreement, and it was signed by Vice Adm. William F. Raborn (McCone’s successor) and Vance on August 13, 1965. It represented a significant victory for the CIA, assigning key decision-making authority to an executive committee, authority that was previously the prerogative of the NRO director as the agent of the Secretary of Defense.
The Secretary of Defense was to have “the ultimate responsibility for the management and operation of the NRO and the NRP,” and have the final power to approve the NRP budget. The Secretary also was empowered to make decisions when the executive committee could not reach agreement.
The DCI was to establish collection priorities and requirements for targeting NRP operations, as well as establish frequency of coverage, review the results obtained by the NRP and recommend steps for improving its results if necessary, serve on the executive committee, review and approve the NRP budget, and provide security policy guidance.
The NRP Executive Committee established by the agreement would consist of the DCI, Deputy Secretary of Defense, and Special Assistant to the President for Science and Technology. The committee was to recommend to the Secretary of Defense the “appropriate level of effort for the NRP,” approve or modify the consolidated NRP and its budget, approve the allocation of responsibility and the corresponding funds for research and exploratory development for new systems. It was instructed to insure that funds would be adequate to pursue a vigorous research and development program, involving both CIA and DoD. The executive committee was to assign development of sensors to the agency best equipped to handle the task.
The Director of the NRO would manage the NRO and execute the NRP “subject to the direction and control of the Secretary of Defense and the guidance of the Executive Committee.” His authority to initiate, improve, modify, redirect or terminate all research and development programs in the NRP, would be subject to review by the executive committee. He could demand that all agencies keep him informed about all programs undertaken as part of the NRP.
Document 11
Analysis of “A $1.5 Billion Secret in Sky” Washington Post, December 9, 1973
Not dated
Top Secret
33 pp.
Throughout the 1960s, the United States operation of reconnaissance satellites was officially classified, but well known among specialists and the press. However, it was not until January 1971 that the NRO’s existence was first disclosed by the media, when it was briefly mentioned in a New York Times article on intelligence and foreign policy.
A much more extensive discussion of the NRO appeared in the December 9, 1973 Washington Post as a result of the inadvertent mention of the reconnaissance office in a Congressional report. The NRO prepared this set of classified responses to the article, clearly intended for those in Congress who might be concerned about the article’s purported revelations about the NRO’s cost overruns and avoidance of Congressional oversight.
Document 12
E.C. Aldridge, Jr. (Director, NRO)
Letter to David L. Boren, Chairman,
Senate Select Committee on Intelligence
21 November 1988
Secret
3 pp.
The late 1980s saw the beginning of what eventually would be a wide-ranging restructuring of the NRO. In November 1988 NRO director Edward “Pete” Aldridge wrote to Senator David Boren, Chairman of the Senate Select Committee on Intelligence, concerning the findings of an extensive study (the NRO Restructure Study) of the organizational structure of the NRO.
Aldridge proceeded to report that, after having discussed the study’s recommendations with Secretary of Defense Frank Carlucci and Director of Central Intelligence William Webster, he was directing the development of plans to implement the recommendations. Specific changes would include the creation of a centralized systems analysis function “to conduct cross-system trades and simulations within the NRO,” creation of a “User Support” function to improve NRO support to intelligence community users as well as to the growing number of operational military users, and the dispersal of the NRO Staff to the new units, with the staff being replaced by a group of policy advisers. In addition, Aldridge foresaw the establishment of an interim facility “to house the buildup of the new functions and senior management.” The ultimate goal, projected for the 1991-92 period, would be the “collocation of all NRO elements [including the Los Angeles-based Air Force Office of Special Projects] . . . in the Washington, D.C. area.”
Document 13
Memorandum of Agreement
Subject: Organizational Restructure of the National Reconnaissance Office
15 December 1988
Secret
2 pp.
This memorandum of agreement, signed by the Director of the NRO and the directors of the NRO’s three programs commits them to the restructuring discussed in Edward Aldridge’s November 21 letter to Senator Boren.
Many changes recommended by Aldridge, who left office at the end of 1988, were considered by a 1989 NRO-sponsored review group and subsequently adopted.
Document 14
Report to the Director of Central Intelligence
DCI Task Force on The National Reconnaissance Office, Final Report
April 1992
Secret
35 pp.
This report was produced by a panel chaired by former Lockheed Corporation CEO Robert Fuhrman, whose members included both former and serving intelligence officials. It focused on a variety of issues other than current and possible future NRO reconnaissance systems. Among the issues it examined were mission, organizational structure, security and classification.
One of its most significant conclusions was that the Program A,B,C structure that had been instituted in 1962 (see Document 6) “does not enhance mission effectiveness” but “leads to counterproductive competition and makes it more difficult to foster loyalty and to maintain focus on the NRO mission.” As a result, the panel recommended that the NRO be restructured along functional lines with imagery and SIGINT directorates. This change was made even before the final version of the report was issued.
The report also noted that while the NRO’s existence was officially classified it was an “open secret” and that seeking to attempt to maintain such “open secrets … weakens the case for preserving ‘real’ secrets.” In addition, such secrecy limited the NRO’s ability to interact with customers and users. The group recommended declassifying the “fact of” the NRO, as well as providing information about the NRO’s mission, the identities of senior officials, headquarters locations, and the NRO as a joint Intelligence Community-Defense Department activity.
Document 15
National Security Directive 67
Subject: Intelligence Capabilities: 1992-2005
30 March 1992
Secret
2 pp.
NSD 67 directed a number of changes in U.S. intelligence organization and operations. Among those was implementation of the plan to restructure the NRO along functional lines–eliminating the decades old Program A (Air Force), B (CIA), and C (Navy) structure and replacing it with directorates for imaging, signals intelligence, and communication systems acquisition and operations–as recommended by the Fuhrman panel. As a result, Air Force, CIA, and Navy personnel involved in such activities would now work together rather than as part of distinct NRO components.
Document 16
Email message
Subject: Overt-Covert-DOS-REP-INPUT
27 July 1992
Secret
1 p.
In addition to the internal restructuring of the NRO, 1992 saw the declassification of the organization, as recommended by the Fuhrman report (Document 14), for a number of reasons–to facilitate interaction with other parts of the government, to make it easier for the NRO to support military operations, and in response to Congressional pressure to acknowledge the obvious. As part of the process of considering declassification NRO consulted Richard Curl, head of the Office of Intelligence Resources of the State Department’s Bureau of Intelligence and Research–the office which provides INR with expertise and support concerning technical collection systems. Curl recommended a low-key approach to declassification.
Document 17
Memorandum for Secretary of Defense, Director of Central Intelligence
Subject: Changing the National Reconnaissance Office (NRO) to an Overt Organization
30 July 1992
Secret
3 pp.
w/ attachments:
Document 17a: Mission of the NRO, 1 p.
Document 17b: Implications of Proposed Changes, 4 pp. (Two versions)
Version One
Version Two
These memos, from Director of the NRO Martin Faga, represent key documents in the declassification of the NRO. The memo noted Congressional pressure for declassification and that Presidential certification that declassification would result in “grave damage to the nation … would be difficult in this case.”
Faga reported that as a result of an NRO review he recommended declassifying the fact of NRO’s existence, issuing a brief mission statement, acknowledging the NRO as a joint DCI-Secretary of Defense endeavor, and identifying top level NRO officials. He also noted that his recommendations attempted to balance concerns about classifying information that realistically could not be protected, while maintaining an ability to protect matters believed to require continued protection.
Secretary of Defense Richard Cheney, DCI Robert Gates, and President Bush approved the recommendations in September and a three-paragraph memorandum to correspondents acknowledging the NRO and NRP was issued on September 18, 1992.
Document 17b comes in two versions, representing different security reviews. Material redacted from the first version includes provisions of National Security Directive 30 on space policy, expression of concern over “derived disclosures,” and the assessment that the “high degree of foreign acceptance of satellite reconnaissance, and the fact that we are not disclosing significant new data,” would not lead to any significant foreign reaction. Another redacted statement stated that “legislation . . . exempting all NRO operational files from [Freedom of Information Act] searches” was required.
Document 18
Final Report: National Reconnaissance Program Task Force for the Director of Central Intelligence
September 1992
Top Secret
15 pp.
The end of the Cold War and collapse of the Soviet Union required the U.S. intelligence community and NRO to reconsider how U.S. overhead reconnaissance systems were employed and what capabilities future systems should possess. To consider these questions DCI Robert Gates appointed a task force, chaired by his eventual successor, R. James Woolsey.
The final report considers future needs and collection methods, industrial base considerations, procurement policy considerations, international industrial issues, and transition considerations. Its recommendations included elimination of both some collection tasks as well as some entire types of present and planned collection systems.
Document 19
NRO Protection Review, “What is [BYEMAN]?”
6 November 1992
Top Secret
18 pp.
Traditionally, the designations of Sensitive Compartmented Information (SCI) compartments–such as UMBRA to indicate particularly sensitive communications intelligence and RUFF to intelligence based on satellite imagery–have themselves been classified. In recent years, however, the NSA and CIA have declassified a number of such terms and their meaning. One exception has been the term “BYEMAN”– the BYEMAN Control System being the security system used to protect information related to NRO collection systems (in contrast to their products) and other aspects of NRO activities, including budget and structure. Thus, the term BYEMAN has been deleted in the title of the document and throughout the study–although the term and its meaning has become known by specialists and conveys no information beyond the text of any particular document.
This study addresses the use of the BYEMAN classification within the NRO, its impact on contractors and other government personnel, and the consequences of the current application of the BYEMAN system. The study concludes that placing information in the highly restrictive BYEMAN channels (in contrast to classifying the information at a lower level) may unduly restrict its dissemination to individuals who have a legitimate need to know.
Document 20
NRO Strategic Plan
18 January 1993
Secret
19 pp.
A study headed by James Woolsey (Document 18), President Clinton’s first DCI, heavily influenced the contents of this early 1993 document. The plan’s introduction notes that while some collection tasks will no longer be handled by overhead reconnaissance the “uncertain nature of the world that is emerging from the end of the ‘cold war’ places a heavy premium on overhead reconnaissance.” At the same time, “this overhead reconnaissance challenge must be met in an era of a likely reduced national security budget.”
The strategic plan is described in the introduction, as “the ‘game plan’ to transition current overhead collection architectures into a more integrated, end-to-end architecture for improved global access and tasking flexibility.”
The document goes on to examine the strategic context for future NRO operations, NRO strategy, strategic objectives, and approaches to implementation. Strategic objectives include improving the responsiveness of NRO systems by developing an architecture that spans the entire collection and dissemination process, from the identification of requirements to dissemination of the data collected.
Document 21
National Reconnaissance Office: Collocation Construction Project, Joint DOD and CIA Review Report
November 1994
Unclassified
28 pp.
In an August 8, 1994 press conference, Senators Dennis DeConcini (D-Az.) and John Warner (R-Va.), the chairman and vice chairman of the Senate Select Committee on Intelligence accused the NRO of concealing from Congress the cost involved in building a new headquarters to house government and contractor employees. Previously NRO activities in the Washington area were conducted from the Pentagon and rented space in the Washington metropolitan area. The collocation and restructuring decisions of the late 1980s and early 1990s had resulted in a requirement for a new headquarters facility.10
The accusations were followed by hearings before both the Senate and House intelligence oversight committees–with House committee members defending the NRO and criticizing their Senate colleagues. While they noted that some of the documents presented by the NRO covering total costs were not presented with desirable clarity, the House members were more critical of the Senate committee for inattention to their committee work.11
This joint DoD and CIA review of the project, found “no intent to mislead Congress” but that “the NRO failed to follow Intelligence Community budgeting guidelines, applicable to all the intelligence agencies,” that would have caused the project to be presented as a “New Initiative,” and that the cost data provided by the NRO “were not presented in a consistent fashion and did not include a level of detail comparable to submissions for . . . intelligence community construction.”
Document 22
Memorandum for Director of Central Intelligence
Subject: Small Satellite Review Panel
Unclassified
July 1996
The concept of employing significantly smaller satellites for imagery collection was strongly advocated by Rep. Larry Combest during his tenure (1995-97) as chairman of the House Permanent Select Committee on Intelligence. As a result the DCI was instructed to appoint a panel of experts to review the issue.12
Panel members included former NRO directors Robert Hermann and Martin Faga; former NRO official and NSA director Lew Allen; scientist Sidney Drell and four others. The panel’s report supported a radical reduction in the size of most U.S. imagery satellites. The panel concluded that “now is an appropriate time to make a qualitative change in the systems architecture of the nation’s reconnaissance assets,” in part because “the technology and industrial capabilities of the country permit the creation of effective space systems that are substantially smaller and less costly than current systems.” Thus, the panel saw “the opportunity to move towards an operational capability for . . . imagery systems, that consists of an array of smaller, cheaper spacecraft in larger number with a total capacity which is at least as useful as those currently planned and to transport them to space with substantially smaller and less costly launch vehicles.”13
The extent to which those recommendations have influenced NRO’s Future Imagery Architecture plan is uncertain–although plans for large constellations of small satellites have not usually survived the budgetary process.
Document 23
Defining the Future of the NRO for the 21st Century, Final Report, Executive Summary
August 26, 1996
Unclassified
30 pp.
This report was apparently the first major outside review of the NRO conducted during the Clinton administration, and the first conducted after the NRO’s transformation to an overt institution and its restructuring were firmly in place.
Among those conducting the review were former Vice Chairman of the Joint Chiefs of Staff, Adm. David E. Jeremiah, former NRO director Martin Faga, and former Deputy Director of Central Intelligence John McMahon. Issues studied by the panel included, inter alia, the existence of a possible alternative to the NRO, NRO’s mission in the 21st Century, support to military operations, security, internal organization, and the relationship with NRO’s customers.
After reviewing a number of alternatives, the panel concluded that no other arrangement was superior for carrying out the NRO mission. It did, however, recommend, changes with regards to NRO’s mission and internal organization. The panel concluded that where the NRO’s current mission is “worldwide intelligence,” its future mission should be “global information superiority,” which “demands intelligence capabilities unimaginable just a few years ago.” The panel also recommended creation of a fourth NRO directorate, which was subsequently established, to focus solely on the development of advanced systems, in order to “increase the visibility and stature of technology innovation in the NRO.”
NEO-STASI-OPFER: LKA BAYERN ERMITTELT GEGEN “GoMoPa” UND DEREN KRIMINELLE PARTNER
CONFIDENTIAL – Georgia Tech Helps to Develop System That Will Detect Insider Threats from Massive Data Sets
![[Image]](https://i0.wp.com/cryptome.org/isp-spy/ga-tech-spy/pict2.jpg)
Georgia Tech DARPA ADAMS leaders
![[Image]](https://i0.wp.com/cryptome.org/isp-spy/ga-tech-spy/pict0.jpg)
Georgia Tech DARPA ADAMS team
![[Image]](https://i0.wp.com/cryptome.org/isp-spy/ga-tech-spy/pict1.jpg)
Data collection environment
When a soldier in good mental health becomes homicidal or a government employee abuses access privileges to share classified information, we often wonder why no one saw it coming. When looking through the evidence after the fact, a trail often exists that, had it been noticed, could have possibly provided enough time to intervene and prevent an incident.
With support from the Defense Advanced Research Projects Agency (DARPA) and the Army Research Office, researchers at the Georgia Institute of Technology are collaborating with scientists from four other organizations to develop new approaches for identifying these “insider threats” before an incident occurs. The two-year, $9 million project will create a suite of algorithms that can detect multiple types of insider threats by analyzing massive amounts of data — including email, text messages and file transfers — for unusual activity.
The project is being led by Science Applications International Corporation (SAIC) and also includes researchers from Oregon State University, the University of Massachusetts and Carnegie Mellon University.
“Analysts looking at the electronically recorded activities of employees within government or defense contracting organizations for anomalous behaviors may now have the bandwidth to investigate five anomalies per day out of thousands of possibilities. Our goal is to develop a system that will provide analysts for the first time a very short, ranked list of unexplained events that should be further investigated,” said project co-principal investigator David A. Bader, a professor with a joint appointment in the Georgia Tech School of Computational Science and Engineering and the Georgia Tech Research Institute (GTRI).
Under the contract, the researchers will leverage a combination of massively scalable graph-processing algorithms, advanced statistical anomaly detection methods and knowledge-based relational machine learning algorithms to create a prototype Anomaly Detection at Multiple Scales (ADAMS) system. The system could revolutionize the capabilities of counter-intelligence community operators to identify and prioritize potential malicious insider threats against a background of everyday cyber network activity.
The research team will have access to massive data sets collected from operational environments where individuals have explicitly agreed to be monitored. The information will include electronically recorded activities, such as computer logins, emails, instant messages and file transfers. The ADAMS system will be capable of pulling these terabytes of data together and using novel algorithms to quickly analyze the information to discover anomalies.
“We need to bring together high-performance computing, algorithms and systems on an unprecedented scale because we’re collecting a massive amount of information in real time for a long period of time,” explained Bader. “We are further challenged because we are capturing the information at different rates — keystroke information is collected at very rapid rates and other information, such as file transfers, is collected at slower rates.”
In addition to Bader, other Georgia Tech researchers supporting key components of this program include School of Interactive Computing professor Irfan Essa, School of Computational Science and Engineering associate professor Edmond Chow, GTRI principal research engineers Lora Weiss and Fred Wright, GTRI senior research scientist Richard Boyd, and GTRI research scientists Joshua L. Davis and Erica Briscoe.
“We look forward to working with DARPA and our academic partners to develop a prototype ADAMS system that can detect anomalies in massive data sets that can translate to significant, often critical, actionable insider threat information across a wide variety of application domains,” said John Fratamico, SAIC senior vice president and business unit general manager.
Research News & Publications Office
Georgia Institute of Technology
75 Fifth Street, N.W., Suite 314
Atlanta, Georgia 30308 USA
Media Relations Contacts: Abby Robinson (abby[at]innovate.gatech.edu; 404-385-3364) or John Toon (jtoon[at]gatech.edu; 404-894-6986)
Writer: Abby Robinson
Scandal – FEMEN attacked Paris Hilton in Kiev
TOP-SCRET FROM THE HOMELAND SECURITY- Anonymous Upcoming U.S. Operations Overview

(U) The loosely organized hacking collective known as “Anonymous” has announced through several mediums that they plan on conducting cyber attacks, peaceful protests, and other unspecified activity targeting a variety of organizations. The purpose of this product is to judge the likelihood of occurrence for these events, as well as the potential impact.
(U//FOUO) Occupy Wall Street (OWS): DHS/NCCIC assesses that it is likely peaceful protests will occur on Wall Street on 17 September 2011. These protests may be accompanied by malicious cyber activity conducted by Anonymous.
(U//FOUO) Operation FaceBook (OPFB): DHS/NCCIC assesses that it is unlikely that a coordinated or sophisticated cyber attack will be conducted by Anonymous (at large) targeting FaceBook.com (FB) on 5 November 2011. However, there remains the possibility that low-level or lone-wolf attempts may occur.
(U//FOUO) Project Mayhem (PM): DHS/NCCIC assesses that a combination of inconsequential physical mischief and potentially disruptive malicious cyber activity will be conducted leading up to the culmination date of 21 December 2012. At this point, specific tactics, techniques and procedures (TTP) are unknown.
(U//FOUO) Operation Halliburton: Little is known about this potential upcoming operation. DHS/NCCIC assesses that targeting US corporations is consistent with past Anonymous targets.
(U) Anonymous has devoted resources to creating new cyber attack and exploitation tools:
(U) Anonymous claimed publicly it will be deploying a new DDoS tool called #RefRef in September. There have been several publicly disclosed tools claiming to be versions of #RefRef however there has been nothing to validate these claims.
(U//FOUO) The recent release of a distributed denial of service (DDOS) tool known as “Apache Killer,” that could be leveraged by Anonymous poses a significant risk to organizations that are operating vulnerable internet facing Apache web servers.
…
(U//FOUO) DHS/NCCIC’S OWS ASSESSMENT: The ideologies set forth by Adbusters seem to align at a basic level with the stated intent of Anonymous’ newly adopted Hacktivist agenda. These protests are highly likely to occur due to the high level of media attention garnered by the partnership between Adbusters and Anonymous, and due to the heightened media response to the San Francisco BART protests. Though the protests will likely to be peaceful in nature, like any protest, malicious individuals may use the large crowds as cover to conduct illegal activity such as vandalism. Judging based on past behaviors by the group, Anonymous’ participation in these protests may include malicious cyber activity, likely in the form of DDOS attacks targeting financial institutions and government agencies.
…
(U) Several racist, homophobic, hateful, and otherwise maliciously intolerant cyber and physical incidents throughout the past decade have been attributed to Anonymous, though recently, their targets and apparent motivations have evolved to what appears to be a hacktivist agenda.
(U) Anonymous utilizes a crude target nomination procedure, outlined below, that is coordinated on one of several communications mediums – IRC, websites (#chan, etc), insurgency wiki, or anonymous meme themed website:
1. An individual on the communications medium posts an appeal to Anonymous leadership requesting members to target a victim;
2. Those individuals who agree, follow suit with vague details given as to intentions and/or tactics;
3. “Lulz ensue,” or they don’t;
4. If “lulz ensue,” go back to step 2 and see if more people join the action, or;
5. Lose interest.
(U) Anonymous utilizes several tactics to humiliate victim individuals and organizations. The most common involve:
- “Dropping someone’s docs,” or exfiltrating information from a compromised system and posting it publicly;
- Pranks targeting victims in real life (IRL) leveraging stolen personally identifiable information (PII), such as unwanted pizza delivery, telephone or fax machine harassment, and other tactics;
- Defacing websites or social network profile pages to embarrass and/or annoy organizations; DOS / DDOS attacks.
DOWNLOAD THE ORGINAL DOCUMENT HERE
MERIDIAN CAPITAL – “GoMoPa” in detention
FREI ERFUNDENE LÜGEN DER FINGIERTEN STASI-“GoMoPA”- FALL MINISTER STELTER
TOP-SECRET from the FBI-Sheets, Sails, and Dormer Lights: The Case of the Pearl Harbor Spy

On February 21, 1942, just 76 days after the tragic attack on Pearl Harbor, Bernard Julius Otto Kuehn (pictured) was found guilty of spying and sentenced to be shot “by musketry” in Honolulu. What was a German national doing in Hawaii in the days leading up to the attack? What exactly did Kuehn do to warrant such a sentence? Here’s the story…
Bed sheets on clothes lines. Lights in dormer windows. Car headlights. A boat with a star on its sail.
Otto Kuehn had a complex system of signals all worked out. A light shining in the dormer window of his Oahu house from 9 to 10 p.m., for example, meant that U.S. aircraft carriers had sailed. A linen sheet hanging on a clothes line at his home on Lanikai beach between 10 and 11 a.m. meant the battle force had left the harbor. There were eight codes in all, used in varying combinations with the different signals.
In November 1941, Kuehn had offered to sell intelligence on U.S. warships in Hawaiian waters to the Japanese consulate in Hawaii. On December 2, he provided specific—and highly accurate—details on the fleet in writing. That same day, he gave the consulate the set of signals that could be picked up by nearby Japanese subs.
Kuehn—a member of the Nazi party—had arrived in Hawaii in 1935. By 1939, the Bureau was suspicious of him. He had questionable contacts with the Germans and Japanese. He’d lavishly entertained U.S. military officials and expressed interest in their work. He had two houses in Hawaii, lots of dough, but no real job. Investigations by the Bureau and the Army, though, never turned up definite proof of his spying.
Not until the fateful attack of December 7, 1941. Honolulu Special Agent in Charge Robert Shivers immediately began coordinating homeland security in Hawaii and tasked local police with guarding the Japanese consulate. They found its officials trying to burn reams of paper. These documents—once decoded—included a set of signals for U.S. fleet movements.
All fingers pointed at Kuehn. He had the dormer window, the sailboat, and big bank accounts. Kuehn was arrested the next day and confessed, though he denied ever sending coded signals. His sentence was commuted—50 years of hard labor instead of death “by musketry”—and he was later deported.
Today, his story reminds us how much damage espionage can do to our country. And why the FBI continues to rank counterintelligence as a top investigative priority.
Secret-The FBI about Pearl Harbor Legacy – Remembering Robert Shivers

The attack on Pearl Harbor. Photo courtesy of the National Archives.
12/07/09
It was 68 years ago this morning—December 7, 1941—that a torrent of bombs fell on Pearl Harbor, a stealth attack that took the lives of more than 2,400 Americans and thrust the nation headlong into its second major war of the century. It was a day—filled with sacrifices and heroism—that will never be forgotten.
The contributions of one man who made a major impact in the aftermath of the attack should also not be forgotten. His name is Robert L. Shivers, and he was the special agent in charge of our office in Honolulu on that fateful day.
Shivers had been handpicked by Director J. Edgar Hoover to run the Honolulu office precisely because of his leadership skills. Smart and genteel, Shivers was minted as a special agent in 1920. After serving across the South and Midwest and in New York, the Tennessee native was tapped to lead field offices in Pittsburgh, Buffalo, and Miami. But because of nagging health issues, he went on restricted duty in the late 1930s.
 |
|
Special Agent in Charge Robert L. Shivers |
In the summer of 1939, however, Europe was on the verge of war, and with the U.S. supporting the Allied cause, the FBI was plenty busy trying to prevent espionage and sabotage at home. In August, Hoover turned to Shivers to re-open the now strategically important FBI division in Honolulu.
Shivers got to work. Within a few months, he developed strong relationships with local police as well as with Army and Navy forces, and he also began making contacts in the islands’ Japanese communities. These deepened when he and his wife began caring for a Japanese schoolgirl named Shizue Kobatake (later Suzanne or Sue). Despite the differences in their backgrounds, they became like a family.
Then came December 7. Within minutes of the attack, Shivers alerted Director Hoover, who quickly put the Bureau’s contingency war plans into effect.
For his part, Shivers—who had already made progress in sorting out the FBI’s division of intelligence and security responsibilities with the Navy—immediately placed the Japanese Consulate under police guard, both to protect the diplomats from retaliation and to prevent their escape. His agents seized a large quantity of suspiciously coded documents that consulate employees tried to hastily burn and began running down key cases of espionage i.e.of Otto Kuehn.
Another major issue involved the 150,000 people of Japanese ancestry in Hawaii—roughly a third of the population. Some argued that they should be taken into custody. Shivers and key members of the armed services and territorial government strongly disagreed and made a vital difference in preventing the kind of mass internment that happened on the mainland (which Director Hoover opposed, but that’s another story). Only a few thousand Japanese nationals considered a security risk ended up being detained.
 |
|---|
Shivers soon gained respect across the island, earning significant authority from its military governor. His only critic was a local U.S. Attorney, who thought he dealt with the Japanese on the islands “too leniently.”
History has taken a different view—and so did Shivers’ contemporaries. When his health forced him to retire in 1944, Shivers was later lauded by the territorial Senate of Hawaii both for “safeguarding Hawaii’s internal security” and for displaying “sympathy, sound judgment, and firmness.”
TOP-SECRET – THE FBI and PEARL HARBOR
Seventy years ago today—on December 7, 1941—a sneak attack on Pearl Harbor took the lives of more than 2,400 Americans, stunning the nation and catapulting it into war.
For the FBI, the attack and the onset of war opened a new chapter in national security. Even as Japanese bombs rained down, FBI Special Agent in Charge Robert Shivers in Honolulu was patched through via telephone to Director J. Edgar Hoover, who immediately put the Bureau on a 24/7 wartime footing according to its already well-made plans. In the days and months that followed, the FBI diligently and successfully worked to protect the American homeland from spies and saboteurs, building important new capabilities along the way.
Pearl Harbor Attack Mobilizes FBI War Plans
On December 7, 1941—as bombs fell on American battleships at Pearl Harbor—Robert L. Shivers, Special Agent in Charge of the FBI’s Honolulu office, was on the phone. Headquarters relayed his anxious call to New York, where Director Hoover was visiting.
“The Japanese are bombing Pearl Harbor. It’s war,” Shivers said. “You may be able to hear it yourself. Listen!”
Director Hoover immediately flew back to Washington, mindful of the plans that his agency had made for this eventuality. Some 2,400 brave U.S. sailors had already died in the early hours of that fateful Sunday.
The attack was a surprise; that Japan was readying war against America was not. Contingency plans had been made throughout the U.S. government, and they were immediately implemented to ensure American security in the weeks, months, and years after the surprise attack.
And what about FBI plans? What had the Bureau set in place in the event of war?
- It had made the investigation of sabotage, espionage, and subversion a top priority—and agents made surveys of industrial plants that were vital to American security in order to prevent sabotage and espionage.
- It had expanded its intelligence programs, including undercover work in South and Central America to identify Nazi spies.
- It had performed—and continued to perform—exhaustive background checks on federal workers, to keep enemy agents from infiltrating the government.
- It had been directed to draw up plans for a voluntary board, turned over to and headed by a newspaperman, to review media stories in order to prevent information from being released that might harm American troops. Mindful of free speech protections, this independent board operated with the voluntary cooperation of the media.
- It had expanded the number of professionally trained police through its National Academy program to aid the Bureau in times of crisis. This cadre of professionals effectively forestalled well-meaning but overzealous civilian plans to “help” law enforcement with vigilantism. The FBI had learned a lesson from World War I when groups like the American Protective League abused the civil rights of Americans in its efforts to identify German spies, draft resisters, and other threats.
- And it had identified German, Italian, and Japanese aliens who posed a clear threat to the United States in the event of war so that when President Roosevelt ordered it—and he did, on the evening of December 7—the Bureau could immediately arrest these enemies and present them to immigration for hearings (represented by counsel) and possible deportation. A few—like Bernard Julius Otto Kuehn, the German national involved in signaling the Japanese invasion fleet headed for Pearl Harbor—were arrested and prosecuted for espionage and other crimes against the U.S.
- Now, on December 7, it immediately implemented a 24/7 schedule at Headquarters and in its field operations.
What was the upshot? By war’s end the FBI had captured hundreds of Axis agents, investigated more than 16,000 sabotage cases, and handled all of its other criminal responsibilities besides. It had played a significant role in keeping Americans safe and free.
FBI – CONFIDENTIAL-Alpha Natural Resources, Inc. and Department of Justice Reach $209 Million Agreement Related to Upper Big Branch Mine Explosion
WASHINGTON—Alpha Natural Resources Inc. has agreed to make payments and safety investments totaling $209 million in connection with the criminal investigation of the April 5, 2010, explosion at the Upper Big Branch mine (UBB) in Montcoal, W.Va., announced Attorney General Eric Holder, U.S. Attorney R. Booth Goodwin II for the District of West Virginia and officials with the FBI and Department of Labor’s Office of Inspector General.
The explosion at the UBB mine claimed the lives of 29 coal miners and injured two others. At the time of the explosion, the mine was owned by Massey Energy Company, whose operations came under Alpha’s control in a June 1, 2011, merger.
“The tragedy at Upper Big Branch will never be forgotten, and the families affected by it will never be made completely whole again. Today’s agreement represents the largest-ever resolution in a criminal investigation of a mine disaster and will ensure appropriate steps are taken to improve mine safety now and will fund research to enhance mine safety in the future,” said Attorney General Holder. “While we continue to investigate individuals associated with this tragedy, this historic agreement—one of the largest payments ever for workplace safety crimes of any type—will help to create safer work environments for miners in West Virginia and across the country.”
“There should never be another UBB, and this announcement is aimed squarely at that goal. For far too long, we’ve accepted the idea that catastrophic accidents are an inherent risk of being a coal miner. That mindset is unacceptable,” said U.S. Attorney Goodwin. “Collectively, these requirements will set a new standard for what can and should be done to protect miners. We look forward to a future in which coal mining is as safe as any other occupation.”
As part of the non-prosecution agreement, Alpha will invest at least $80 million in mine safety improvements at all of its underground mines, including those formerly owned by Massey. Alpha will also place $48 million in a mine health and safety research trust, to be used to fund academic and non-profit research that will advance efforts to enhance mine safety. In addition, the company will pay criminal restitution of $1.5 million to each of the families of the 29 miners who died at UBB and to the two individuals who were injured, for a total restitution payment of $46.5 million. Alpha also will pay a total of up to $34.8 million in penalties owed to the Mine Safety and Health Administration (MSHA), including all penalties that arise from the UBB accident investigation.
The remedial safety measures included in the agreement include the following:
- Installation of digital monitoring systems in all its underground mines to continuously monitor compliance with ventilation requirements and to ensure mines are free of potentially explosive methane gas;
- Implementation of a plan to ensure that each of its underground mines has the personnel and resources necessary to meet all legal requirements concerning incombustible material and accumulations of coal dust and loose coal;
- Purchase state-of-the-art equipment to monitor its mines for explosive concentrations of coal dust and use that equipment in all its underground mines;
- Purchase next-generation rock dusting equipment (pending MSHA approval), further enhancing its ability to combat explosion hazards;
- Installation of oxygen cascading systems to help miners make their way to safety if a serious accident should occur; and
- Building of a state-of-the-art training facility and implementation of a full training curriculum to train Alpha miners, which will be available to other mining companies.
The agreement announced today is the largest-ever resolution in a criminal investigation of a mine disaster. It addresses only the corporate criminal liability of the former Massey, not potential criminal charges for any individual. The criminal investigation of individuals associated with Massey remains ongoing.
E-BOOK – DOWNLOAD – “Seduced by Secrets” by Kristie Macrakis – The STASI inside
Seduced-by-Secrets-Inside-the-Stasis-Spy-Tech-World-2008-Macrakis
Click on Download Link above
More fascinating than fiction, Seduced by Secrets takes the reader inside the real world of one of the most effective and feared spy agencies in history. The book reveals, for the first time, the secret technical methods and sources of the Stasi (East German Ministry for State Security) as it stole secrets from abroad and developed gadgets at home, employing universal, highly guarded techniques often used by other spy and security agencies.
Seduced by Secrets draws on secret files from the Stasi archives, including CIA-acquired material, interviews and friendships, court documents, and unusual visits to spy sites, including “breaking into” a prison, to demonstrate that the Stasi overestimated the power of secrets to solve problems and created an insular spy culture more intent on securing its power than protecting national security. It recreates the Stasi’s secret world of technology through biographies of agents, defectors, and officers and by visualizing James Bond-like techniques and gadgets.
In this highly original book, Kristie Macrakis adds a new dimension to our understanding of the East German Ministry for State Security by bringing the topic into the realm of espionage history and exiting the political domain.
- Reveals previously secret methods and sources used by all spy agencies
- Reveals formulas and methods for invisible ink for the first time
- Includes visits to spy sites
Studie-BKA-Historie und die NS-Einflüsse
Knapp drei Jahre lang hat ein unabhängiges Wissenschaftlerteam unter Leitung des Historikers Patrick Wagner von der Universität Halle alte Personal- und Ermittlungsakten des BKA analysiert, dazu Memoranden, Vermerke und Papiere in diversen Archiven.
Die Auftragsarbeit steht in einer Reihe von jüngst erschienenen Publikationen über die NS-Belastung von Ministerien und Behörden. Das Bundesverkehrsministerium etwa veröffentlichte 2007 einen schmalen Band über seine Vorgängerinstitution, ebenso das Verbraucherschutzministerium. Die vor über einem Jahr erschienene umstrittene Studie über das Auswärtige Amt sorgt immer noch für Diskussionen.
Einen ähnlichen Aufruhr wird die BKA-Studie kaum verursachen, weil sich die Autoren im Gegensatz zu ihren Kollegen mit allzu steilen Thesen zurückhalten und ihre Folgerungen gut belegen.
Doch erfreulich für den Auftraggeber ist das Ergebnis nicht. Denn die Historiker präsentieren keine Erfolgsgeschichte. Sicherlich seien die braunen Traditionen nach und nach verblasst, befinden die Wissenschaftler, doch ohne aktives Zutun von Belasteten. Statt eines Lernprozesses, so Historiker Wagner, habe man nur einen “Prozess des institutionalisierten Vergessens” feststellen können.
http://www.spiegel.de/panorama/justiz/0,1518,802215,00.html
DOWNLOAD ORIGINAL DOCUMENT HERE
CONFIDENTIAL-The Nixon Administration and the Indian Nuclear Program, 1972-1974
U.S. Post-Mortem on 1974 Indian Test Criticized Intelligence Community Performance for “Waffling Judgments” and Not Following Up Leads
National Security Archive Electronic Briefing Book No. 367
|
Washington, D.C., December 7, 2011 – India’s “peaceful nuclear explosion” on 18 May 1974 caught the United States by surprise in part because the intelligence community had not been looking for signs that a test was in the works. According to a recently declassified Intelligence Community Staff post-mortem posted today by the National Security Archive and the Nuclear Proliferation International History Project, Nixon administration policymakers had given a relatively low priority to the Indian program and there was “no sense of urgency” to determine whether New Delhi was preparing to test a nuclear device. Intelligence “production” (analysis and reporting) on the topic “fell off” during the 20 months before the test, the analysis concluded.[i]
In early 1972, however—two years before the test—the State Department’s Bureau of Intelligence and Research (INR) had predicted that India could make preparations for an underground test without detection by U.S. intelligence. Published for the first time today, the INR report warned that the U.S. government had given a “relatively modest priority to … relevant intelligence collection activities” which meant that a “concerted effort by India to conceal such preparations … may well succeed.”
The post-mortem [see document 21], the INR report [see document 2] and other new materials illustrate how intelligence priorities generally reflect the interests and priorities of top policymakers. The Nixon White House was focused on the Vietnam War and grand strategy toward Beijing and Moscow; intelligence on nuclear proliferation was a low priority. Compare, for example, the India case with that of Iraq during 2002-2003, when White House concerns encouraged—some say even compelled—intelligence producers to cherry pick raw information to demonstrate the development of WMD by the Saddam Hussein regime.
INR prepared its India report at a time when secret sources were telling U.S. intelligence that New Delhi was about to test a nuclear device. The “small spate” of reports about a test had such “congruity, apparent reliability, and seeming credibility” that they prompted a review of India’s nuclear intentions by INR and other government offices. In the end, government officials could not decide whether India had made a decision to test although a subsequent lead suggested otherwise.
According to the intelligence community’s post-mortem, obtained through a mandatory review appeal to the Interagency Security Classification Appeals Panel (ISCAP), one of the problems was that intelligence producers were not communicating with each other, so the “other guy” assumed that someone else was “primarily responsible for producing hard evidence of Indian intentions.” The analysis was especially critical of an August 1972 Special National Intelligence Estimate for its “waffling judgments” on Indian nuclear intentions.
Other declassified documents reproduced here from 1972 through 1974 illustrate the range of thinking on this sensitive topic:
- An INR report in February 1972 concluded that it could not “rule out a test” in the near future and it was “entirely possible that one or more nuclear devices have actually been fabricated and assembled.” All the same, “it our judgment that a decision to authorize a test is unlikely in the next few months and may well be deferred for several years.”
- During March and April 1972, Canadian and British intelligence concluded that they had no evidence that India had made a decision to test a nuclear device. Nevertheless, the Canadians believed that New Delhi could produce a device in less than a year.
- In June 1972, Japanese diplomat Ryohei Murata argued that the “Indians have decided to go ahead with a nuclear test” and that the Thar Desert in Rajasthan would be the test site. While basically correct, Murata’s estimate was discounted because it did not represent an official Foreign Ministry view.
- Special National Intelligence Estimate (SNIE) 31-72 published in August 1972 also held that the Indians could produce a device “within a few days to a year of a decision to do so,” but concluded that the chances that India had made a decision to test were “roughly even.”
- In 1973, the Atomic Energy Commission’s scientific representative in India told the U.S. consul in Bombay (Mumbai) that several “indications” suggested that India “may well have decided” to test a nuclear device.
- Five months before the test, the U.S. Embassy in New Delhi reported that the probability of an “early test” was at a “lower level than previous years.”
The rumors that India was going to test emerged in the wake of the South Asian crisis, when the Nixon White House tilted toward Pakistan, India’s archrival. Relations between New Delhi and Washington were already cool during the Nixon administration which treated India as a relatively low priority. Henry Kissinger’s secret trip to China underlined India’s low priority by suggesting that if New Delhi ever faced a crisis with Beijing it could not count on Washington for help. Relations became truly frosty during the balance of 1971 when New Delhi signed a friendship treaty with Moscow and India and Pakistan went to war. Later Nixon and Kissinger wanted to improve the relationship, but India’s nuclear intentions were not on their agenda. That India had refused to sign the Nuclear Nonproliferation Treaty was a non-issue for Nixon and Kissinger, who had little use for the NPT and treated nuclear proliferation as less than secondary. While the State Department cautioned India against nuclear tests in late 1970 [see document 6], concern did not rise to the top of policy hill.[2]
Whatever impact the events of 1971 may have had on India’s decision to test a nuclear device that decision was soon to be made. According to George Perkovich, an authority on the Indian nuclear program at the Carnegie Endowment for International Peace, “it may be conjectured that support in principle for developing a nuclear explosive device was solidified by late 1971, that concentrated work on building the vital components began in spring 1972, and that formal prime ministerial approval to make final preparations for a PNE occurred in September 1972.”[3] In this context, the reports collected by U.S. intelligence in late 1971 and early 1972 about a possible test may have been good examples of the old chestnut that “where there’s smoke, there’s fire.”
Yet, the analysts who wrote SNIE 31-72 decided that the smoke had no significance because they saw only a 50-50 chance that New Delhi had made a decision to test (even though New Delhi was closing in on a decision).
|
Documents
Document 1: “Various recent intelligence reports”
State Department cable 3088 to Embassy New Delhi, 6 January 1972, Secret
Source: U.S. National Archives, Record Group 59, Subject-Numeric Files 1970-1973 [hereinafter RG 59, SN 70-73] Def 12-1 India
For years, the U.S. intelligence establishment had been monitoring India’s nuclear program for signs of a decision to produce nuclear weapons, but in late 1971 and early 1972 it had to consider the possibility that a nuclear test was impending. Recently collected intelligence about an imminent test led the State Department to send a query to the U.S. Embassy in India for its assessment.
Document 2: “A Concerted Effort by India to Conceal Preparations May Well Succeed”
State Department Bureau of Intelligence and Research Intelligence Note, “India to Go Nuclear?” 14 January 1972, Secret
Source: RG 59, SN 70-73, Def 18-8 India
Before the Embassy sent a full response, a team of analysts at the State Department’s Bureau of Intelligence and Research produced their evaluation of varied report about India’s nuclear intentions: that it would test a device that month, sometime in 1972, or that the government was undertaking a program to test a “peaceful nuclear explosive.” According to INR, India had the capability to produce some 20-30 weapons, and it could easily test a device in an underground site, such as an abandoned mine, that would be hard to discover. Indeed, because the U.S. government had given a “relatively modest priority to … relevant intelligence collection activities” a “concerted effort by India to conceal such preparations … may well succeed.” What would motivate India to test, the analysts opined, were domestic political pressures and concerns about China and Pakistan. Nevertheless, the INR analysts saw a test as having more importance as a demonstration of “scientific and technological prowess”; the strategic significance would be “negligible” because India was “years away” from developing a “credible” deterrence against China “its only prospective enemy with a nuclear capability.”
Document 3: “Straws” Suggesting an Underground Test
U.S. Embassy Airgram A-20 to State Department, “India’s Nuclear Intentions,” 21 January 1972, Secret, Excised copy
Source: RG 59, SN 70-73, Def 18-8 India
In its response to the Department’s query, the Embassy identified a number of reasons that made it unlikely that India would a test a nuclear device in the coming weeks, but saw “straws” suggesting an underground test “sometime in future.” For example, the Government of India had publicly acknowledged ongoing work on the problem of safe underground testing . Moreover, India might have an interest in making its nuclear capabilities known to “enemies.” Whatever the Indians decided, external pressure would have no impact on a highly nationalist state and society: “we see nothing US or international community can presently do to influence GOI policy directions in atomic field.”
One of the sources mentioned, apparently a CIA asset (the reference is excised), had a connection with the Prime Minister’s secretariat. This may be the same informant, future Prime Minister Moraji Desai, who provided information to the CIA about Prime Minister Gandhi’s intentions during the recent South Asian crisis and whose cover was subsequently blown through press leaks published by Jack Anderson. He later told the CIA to “go to hell.”[4]
Document 4: “Increased Status of a Nuclear Power”
Memorandum from Ray Cline, Director, Bureau of Intelligence and Research, to Director of Central Intelligence Richard Helms, enclosing “Possibility of an Indian Nuclear Test,” 23 February 1972, Secret
Source: U.S. State Department, Foreign Relations of the United States, 1969–1976 Volume E–7, Documents on South Asia, 1969–1972, Document 228
At the request of Undersecretary of State John Irwin, INR prepared an assessment which included a detailed review of Indian’s nuclear facilities and their capacity to produce weapons-grade plutonium as well as capabilities to deliver nuclear weapons to target. While India had signed agreements with Canada and the United States that nuclear reactors were to be used for peaceful purposes, the Indians were likely to claim that an explosive device for “peaceful” purposes was consistent with the agreements. Whether the Indians were going to test in the near future was in doubt. INR could not “rule out” one in the near future. Further, the “strongest incentive [to test] may well be the desire for the increased status of a nuclear power.” All the same, “it our judgment that a decision to authorize a test is unlikely in the next few months and may well be deferred for several years.” Weighing against a test were the financial and diplomatic costs, for example, “India’s full awareness that assistance from the US and other countries (possibly including the USSR) would be jeopardized.”
Document 5: Trudeau’s Warning
U.S. Embassy Canada cable 391 to State Department, “India’s Nuclear Intentions,” 7 March 1972, Secret
Source: RG 59, SN 70-73, AE 1 India
With Canada’s role as the supplier of the CANDU reactor, senior Canadian officials had close working relationships with their Indian counterpart. Lauren Gray, the chairman of Canada’s Atomic Energy Board, had recently visited India and U.S. embassy officials interviewed him closely on his thinking about Indian nuclear developments. Having spoken with Homi Nusserwanji Sethna, Chairman of the Atomic Energy Commission, and other officials, Gray believed that Sethna opposed a test and that as long as Sethna and Indira Gandhi were in office “there was no chance” that India would test a nuclear device, which would take three to four years to prepare. Gray was mistaken, but was correct to declare that if a decision to test was made, Sethna would “undoubtedly” head the project. The embassy’s science attaché, Miller N. Hudson, met with other officials with the AECB who had a different take on Indian capabilities; based on their assessment of Indian’s ability to produce weapons grade plutonium, they argued that it would take no more than a year to produce a device.
The Canadians pointed out that about 18 months earlier there had been a “blackout” of statistical information on plutonium production. That led Canadian Prime Minister Pierre-Eliot Trudeau followed by other officials to “directly” warn the “Indians that Canadian plutonium should not be used for any kind of nuclear device.”
Document 6: Unlikely to Test in the “Near Future”
State Department cable 40378 to U.S. Embassy Ottawa, “Indian Nuclear Intentions,” 9 March 1972, Secret
Source: RG 59, SN 70-73, AE 1 India
State Department officers were also consulting with their counterparts at the Canadian embassy in Washington. During a discussion with the embassy counselor, country desk director David Schneider opined that Indian was unlikely to test a device in the “near future” but he wanted Ottawa’s prognosis. Schneider was also interested in whether the Soviets, with their close relationship with India, might be able to use their influence to “deter” a test. If India tested, the U.S. could respond with a “strong statement,” but whether “punitive” measures would be taken would depend on whether the test “violated existing agreements.” In October 1970, the State Department had cautioned the Indians that a “peaceful nuclear explosion” was indistinguishable from a weapons test and that the test of a nuclear device would be incompatible with U.S.-Indian nuclear assistance agreements. That the State Department issued this warning provides a telling contrast with Canada, which treated its admonition as a head of state issue.
Document 7: No Technical or Fiscal Obstacle to a Test
U.S. Embassy Canada cable 430 to State Department, “India’s Nuclear Intentions on South Asia Situation,” 14 March 1972, Secret
Source: RG 59, SN 70-73, AE 1 India
Elaborating on his earlier cable and responding to the general issues raised by the Department’s 9 March message, science attaché Hudson questioned Gray’s evaluation of Sethna, suggesting that by combining “guile” and “technical proficiency,” the latter could easily have “easily misled” the Canadian. Based on consultations with a variety of Canadian insiders with knowledge of and experience with the Indian nuclear program, the Embassy saw no technical or fiscal barriers to an Indian test. Moreover, any pressure on India not to test would increase the “likelihood” of that happening.
Document 8: “Leaving Their Options Open”
State Department cable 50634 to U.S. Embassy Canada, “Indian Nuclear Intentions,” 24 March 1972, Secret
Source: RG 59, SN 70-73, AE 1 India
Further discussions with the Canadian embassy counselor disclosed Ottawa’s view that it had no evidence of Indian intentions to test a nuclear weapon or a PNE. The Indians were “leaving their options open.” If they decided to test, however, it would be “impossible” for them to move forward “without revealing some indication of their intentions.”
Document 9: British See No Evidence of a Decision
State Department cable 59655 to U.S. Embassy United Kingdom, “Indian Nuclear Intentions, 7 April 1972, Secret
Source: RG 59, SN 70-73, AE 1 India
The British Government was taking the same view as the Canadians, seeing no evidence that the Indians had made a decision to test, although they had the “capability.”
Document 10: “Apparent Reliability and Seeming Credibility”
State Department cable 69551 to U.S. Embassy United Kingdom, “Indian Nuclear Intentions, 22 April 1972, Secret
Source: RG 59, SN 70-73, AE 1 India
The Canadian embassy had asked the State Department for information on the intelligence reports from earlier in the year that an Indian nuclear test was “imminent.” The State Department denied the request, but informed the Canadians that the reports were so numerous and their “congruity, apparent reliability, and seeming credibility” so striking that it had become necessary to update official thinking about Indian intentions.
Documents 11A-C: “The Indians Have Decided to Go Ahead”
A. State Department cable 113523 to U.S. Embassy India, “Japanese Views Regarding Indian Nuclear Plans,” 23 June 1972, Secret
B. U.S. Mission Geneva cable 2755 to State Department, “Japanese-Pakistani Conversations Regarding Indian Nuclear Plans,” 26 June 1972, Secret
C. U.S. Embassy Tokyo cable 67912 to State Department, “Japanese View Regarding Indian Nuclear Plans,” 27 June 1972, Secret
Source: RG 59, SN 70-73, AE 1 India
This group of telegrams discloses that one Japanese diplomat made a good guess about what was happening in India, but also illuminates the problem of verifying intelligence information. In response to a request from the State Department, Ryohei Murata[5], an official at the n officer from the Japanese embassy, reported that the Japanese government believed that for prestige reasons and as a “warning” to others, the “Indians have decided to go ahead with a nuclear test” which could occur at “any time;” The Thar Desert in Rajasthan would be the test site. Murata was correct on the latter point and close to correct on the decision: only weeks before the Indian AEC had begun work on building the components for a test device.[6] The cables that followed this report, however, raised doubts about Murata’s assessment.
Document 12: Request for a NSSM
Henry Kissinger to President Nixon, “Proposed NSSM on the Implications of an Indian Nuclear Test,” n.d., with cover memorandum from Richard T. Kennedy, 4 July 1972, Secret
Source: Nixon Presidential Library, National Security Council Institutional Files, box H-192, NSSM-156 [1 of 2]
Months after the initial flurry of intelligence reports, national security assistant Henry Kissinger asked President Nixon to approve a national security study memorandum [NSSM] on the implications of an Indian nuclear test for U.S. interests. The next day, 5 July 1972, Kissinger sent the agencies a request for a study which became NSSM 156.
Document 13: No Evidence of a Decision
U.S. Embassy India cable 9293 to State Department, “Indian Nuclear Intentions,” 26 July 1972, Secret
Source: RG 59, SN 70-73 Def 1 India
In an update of its thinking about the possibility of a test, the Embassy acknowledged that India had the “technical know-how and possibly materials to develop [a] simple nuclear device within period of months after GOI decision to do so.” Nevertheless, it saw no evidence that a decision had been made to test a device. Moreover, capabilities to deliver nuclear weapons were limited, with no plans in sight to “develop [a] missile launch system.”
Document 14: “Roughly Even”
Special National Intelligence Estimate 31-72, “Indian Nuclear Developments and their Likely Implications,”3 August 1972, Secret
Source: Foreign Relations of the United States, 1969–1976 Volume E–7, Documents on South Asia, 1969–1972, Document 298
Prepared as part of the NSSM 156 policy review, the 1974 post-mortem criticized this SNIE as “marred by waffled judgments.” The SNIE concluded that the chances of India making a decision to test were “roughly even,” but the post-mortem analysis [see document 21] argued that based on its own findings, the conclusion ought to have been 60-40 in favor of a decision to test. In its analysis of the pros and cons of testing, the SNIE found that the “strongest factors impelling India to set off a test are: the “belief that it would build up [its] international prestige; demonstrate India’s importance as an Asian power; overawe its immediate South Asian neighbors; and bring enhanced popularity and public support to the regime which achieved it.” The drafters further noted that a test would be “extremely popular at home, where national pride is riding high” and that supporters of a test believed that it would make the world see India as “one of the world’s principal powers.” The arguments against a test included adverse reactions from foreign governments that provided economic assistance, but the estimate noted that foreign reactions were “becoming less important” to India.
Document 15: “No Firm Intelligence”
Memorandum of Conversation, “Indian Nuclear Developments,” 21 September 1972, Secret
Source: RG 59, SN 70-73, Def 12 India
A meeting between British Foreign Office and State Department officials on the Indian nuclear problem occurred the same month that Indian Prime Minister Gandhi approved the “final preparations for a PNE.”[7] Deputy Assistant Secretary of State Christopher T. Van Hollen (the father of the future Maryland Congressman) and his colleagues followed the approach taken by the SNIE, which was close to that taken by the British Joint Intelligence Committee. According to country director David Schneider, the “odds were about even” that India would make a decision, but once it was made, India could test very quickly. There was “no firm intelligence” that a “go-ahead signal” to prepare for a test had been made. Schneider reviewed bilateral and multilateral steps, proposed in the NSSM 156 study, that the U.S. and others could take to try to discourage an Indian test and the range of reactions that would be available if India went ahead. A “weak” U.S. reaction, Schneider observed, would suggest that Washington would “acquiesce” if other countries followed India’s example.
Document 16: “A Set-Back to Nonproliferation Efforts”
H. Daniel Brewster to Herman Pollack, “Indian Nuclear Developments,” 16 January 1973, enclosing “Summary,” 1 September 1972, Secret
Source: RG 59, SN 70-73, AE 6 India
The interagency group prepared a response to NSSM 156 on 1 September 1972 and it was sent to Kissinger at whose desk it would languish, suggesting the low priority that the Nixon White House gave to nuclear proliferation issues. The summary of the study reproduced here includes the conclusion that an Indian test would be “a set-back to nonproliferation efforts” and that Washington should “do what [it] can to avert or delay” one. Thus, recommendations included a number of unilateral and multilateral actions that the United States government could take, noting that “given the poor state” of Indo-American relations, an “overly visible” U.S. effort would more likely speed up an Indian decision to test a device, Even non-US efforts were likely not to “be per se effective.”
Documents 17A-B: India “May Well Have Decided”
A. Bombay consulate cable 705 to Department of State, “India’s Nuclear Position,” 4 April 1973, Confidential
Source: RG 59, SN 70-73, Def 1 India
B. U.S. Embassy India cable 5797 to State Department forwarding Bombay consulate cable 983, “India’s Nuclear Position,” 17 May 1973, Confidential
Source: AAD 1973
The possibility that the GOI had made a decision to test surfaced in a message from the U.S. consulate in Bombay (Mumbai) signed off by Consul David M. Bane. The latter reported that Oak Ridge Laboratory scientist John J. Pinajian, then serving as the Atomic Energy Commission’s scientific representative in India, had pointed out several “indications”—notably his lack of access to key individuals and facilities in India’s atomic establishment–suggesting that India “may well have decided” to test a nuclear device. While stating that Pinajian’s evaluation was “subjective and impressionistic,” Consul Bane agreed that the atomic energy establishment did not want this American poking around because he might find out too much. Bane further observed that a nuclear test “in the not too distant future” could meet the GOI’s political goals and help attain “greater recognition major power status.”
Raja Rammana, the director of the Bhabha Atomic Research Center, one of the organizations that Pinajian was trying to contact, played a key role in directing the PNE project so his suspicions were on target.[8] In any event, a month later, Pinajian got some access to BARC, but noticed the absence of personnel responsible for experimental work. Moreover, he was getting cooperation from the Institute for Fundamental Research to conduct an experiment. Whether Pinajian remained suspicious needs to be learned, but the authors of the 1974 post-mortem pointed to the Consulate report as evidence that should have been considered (although it is worth noting that Secretary of State William Rogers was aware of the report and asked for more information).
Document 18: “The Likelihood of an Early Test [at] a Lower Level than Previous Years”
U.S. Embassy India cable 0743 to State Department, “India’s Nuclear Intentions,” 18 January 1974, Confidential
Source: http://static.history.state.gov/frus/frus1969-76ve08/pdf/d156.pdf
The embassy concluded that “deeper economic problems,” among other considerations militated against a nuclear test in the near future, even though the Indian government had the capabilities to produce and test a device. While there were no rumors about a test as there had been in 1972, “we know little about relevant internal government debate.” All in all, the embassy believed that economic conditions “tip the likelihood of an early test to a lower level than previous years.” Russell Jack Smith, previously the deputy director for intelligence at the CIA, and then serving as special assistant to the ambassador (station chief), was one of the officials who signed off on this cable.[9]
Document 19: “Rebound to their Credit Domestically”
U.S. Embassy India cable 6598 to State Department, “India’s Nuclear Explosion: Why Now?” 18 May 1974, Secret
Source: AAD
Having written off an early test, the day that it took place the Embassy scrambled to come up with an explanation. Deputy Chief of Mission David Schneider signed off on the telegram because Moynihan was in London. While the Embassy had no insight on the decision-making, it saw domestic politics and “psychological” explanations for the test: the need to offset domestic “gloom” and the need for India to “be taken seriously.” According to the telegram, “the decision will appeal to nationalist feeling and will be widely welcomed by the Indian populace.”
Document 20: “Enough Plutonium for Some 50-70 Nuclear Weapons”
State Department cable 104613 to Consulate, Jerusalem, “India Nuclear Explosion,” 18 May 1974, Secret
Source: State Department MDR release
The day of the test, INR rushed to update Kissinger, then in the Middle East negotiating with Israel and Syria. INR provided background on what had happened, how the United States and Canada had inadvertently helped India produce plutonium for the test device, earlier U.S. and Canadian demarches against “peaceful nuclear explosions,” and India’s capabilities to produce and deliver nuclear weapons. The report did not state whether India had made a decision to produce weapons, but it forecast that two large unsafeguarded reactors under construction could eventually “produce enough plutonium for 50-70 nuclear weapons.”
Document 21: “No Sense of Urgency in the Intelligence Community”
Intelligence Community Staff, Post Mortem Report, An Examination of the Intelligence Community’s Performance Before the Indian Nuclear Test of May 1974, July 1974, Top Secret, Excised copy
Source: Mandatory review request; release by ISCAP
After the test, policymakers in and out of the intelligence establishment wanted to know why the CIA and its sister agencies had missed it. As Jeffrey Richelson has observed, this was not an “epic failure,” but it was serious enough to produce a post-mortem investigation to determine what had gone wrong.[10] The partial release of the July 1974 post-mortem provides some answers, even if the full picture is denied because of massive excisions. Readers already know from the previous release published on the Archive’s Web site that two problems were especially important: 1) the lack of priority given to the Indian nuclear program for intelligence collection (further confirmed by the January 1972 INR report), and 2) the lack of communication between intelligence producers (analysts and estimators) and intelligence collectors (spies, NRO, etc.). The low priority meant that intelligence production “fell off” during the 20 months before the test (from October 1972 to May 1974). Moreover, there may have been a lack of communication between producers, with the “other guy” assuming that someone else was “primarily responsible for producing hard evidence of Indian intentions.”
Trying to explain the lack of follow-up on relevant “raw intelligence,” e.g. Pinjanians’s surmises about the Indian nuclear program, the post-mortem saw no “sense of urgency” in the intelligence community, which may have “reflected the attitudes of the policymakers.” Another problem was that the intelligence community focused more on “capabilities” than on “intentions,” which implicitly raised the difficult issue of breaching the nuclear establishment or Indira Gandhi’s small circle of decision-making.
The substantive discussion of satellite photography has been excised, but the recommendations were left intact, including the point that “The failure of production elements to ask NPIC [National Photographic Intelligence Center] to exploit photography that had been specifically requested from the National Reconnaissance Office suggests a weakness in the imagery requirements system.” The implication was that NRO satellites had imagery of the Thar Desert that could have been scrutinized for suspect activity, but no one asked NPIC to look into it. In any event, this and other failures fed into a number of recommendations, including the broader point that nuclear proliferation intelligence receive “much higher priority.”
Document 22: “India may not yet have decided whether to proceed with …. [the] development of a weapons capability”
Source: MDR release by CIA
A few months after the Indian test, the intelligence community prepared an overall estimate of the global nuclear proliferation situation. Such an estimate had not been prepared since the 1960s, no doubt because of the White House’s lack of interest. This estimate, SNIE 4-1-74, has been released before but this version includes more information, mainly a section on the Indian nuclear program, which had previously been withheld. While finding it “likely” that India would launch a covert program to produce a few weapons, the analysts were not sure that such a decision had been made and suggested that Moscow or Washington might be able to persuade the Indians from moving in that direction. The hypothesis about a covert program was mistaken because the Government of India did not make a basic decision to produce nuclear weapons until the 1980s.
Document 23: Whether the “Intelligence Community is Adequately Focused on Proliferation Matters”
Intelligence Community Staff, Director of Performance Evaluation and Improvement, to Deputy to the Director of Central Intelligence for the Intelligence Community, “Nuclear Proliferation and the Intelligence Community,” 12 October 1976, Top Secret, Excised copy
Source: CIA Research Tool [CREST], National Archives Library, College Park, MD
As this report indicates, the recommendations made in the 1974 post-mortem had little impact. The authors identified a basic disconnect between “national level users”—the top policymakers—and those who “set analytical and collection priorities in the intelligence community.” The latter were not sure how high a priority that the policymakers had given to nuclear proliferation intelligence. Moreover, a study for the Defense Department produced by MIT chemistry professor (and future DCI) John Deutch questioned whether the intelligence community “is adequately focused and tasked on proliferation matters.” This would be a recurring problem for the CIA and other intelligence agencies.
Notes
[i] For background, see Jeffrey Richelson, Spying on the Bomb: American Nuclear Intelligence from Nazi Germany to Iran and North Korea (New York: W.W. Norton, 2006), 218-235.
[1] For background, see Jeffrey Richelson, Spying on the Bomb: American Nuclear Intelligence from Nazi Germany to Iran and North Korea (New York: W.W. Norton, 2006), 218-235.
[2] For U.S.-India relations during the Nixon administration, see Dennix Kux, India and the United States: Estranged Democracies, 1941-1991 (Washington, D.C.: National Defense University Press, 1993), 279-314, and Perkovich, India’s Nuclear Bomb, 162-166. For the impact of Kissinger’s trip, see Andrew B. Kennedy, “India’s Nuclear Odyssey: Implicit Umbrellas, Diplomatic Disappointments, and the Bomb,” International Security 36 (2011): 136-139.
[3] Perkovich, India’s Nuclear Bomb, 172.
[4] Thomas Powers, The Man Who Kept the Secrets: Richard Helms & the CIA (New York: Knopf, 1979), 206-207; Mark Feldstein, Poisoning the Press: Richard Nixon, Jack Anderson, and the Rise of Washington’s Scandal Culture, (New York: Farrar, Straus and Giroux, 2010), 171.
[5] Murata would later rise to vice foreign minister and in 2009 revealed significant details about secret U.S.-Japanese understandings on nuclear weapons issues during the Cold War. http://search.japantimes.co.jp/cgi-bin/nn20090630a2.html
[6] Perkovich, India’s Nuclear Bomb, 171.
[9] Russell J. Smith, The Unknown CIA: My Three Decades with the Agency (Washington, D.C.: Pergamon-Brassey, 1989, 124.
UNCENSORED – FEMEN Cyber War against Sex Tourism
FEMEN fights sex-tourism with BORDEL.NET programme for the Internet. Report by 1+1
FBI – Former Prince George’s County Executive Jack Johnson Sentenced to Over Seven Years in Federal Prison for Federal Extortion and Bribery
GREENBELT, MD—U.S. District Judge Peter J. Messitte sentenced former Prince George’s County Executive Jack B. Johnson, age 62, of Mitchellville, Maryland, today to 87 months in prison followed by three years of supervised release for his leadership role in an extortion conspiracy wherein in exchange for bribes, Jack Johnson corruptly used his public office to engage in fraudulent actions including steering millions of dollars in federal and local funds to favored developers; and tampering with a witness and evidence. Judge Messitte also ordered that Jack Johnson pay a $100,000 fine and forfeit $78,000 and an antique Mercedes Benz.
The sentence was announced by United States Attorney for the District of Maryland Rod J. Rosenstein; Special Agent in Charge Richard A. McFeely of the Federal Bureau of Investigation; and Acting Special Agent in Charge Jeannine A. Hammett of the Internal Revenue Service-Criminal Investigation, Washington, D.C. Field Office.
“Jack Johnson could have been a role model for integrity, but he chose to be a poster child for greed,” said U.S. Attorney Rod J. Rosenstein. “The facts of this case read like a dime novel because the defendant acted as if corruption was the normal way of doing business. It is our responsibility to prove him wrong.”
“Identifying and investigating public corruption remains one of our highest priorities,” stated FBI Special Agent in Charge Richard A. McFeely. “We hope today’s sentencing reaffirms the federal government’s proactive stance to stamp out corruption by those elected officials who have betrayed the public trust.”
“Public officials, whether elected or appointed, hold positions of trust in the eyes of the public. That trust is broken when these officials commit crimes,” said Acting IRS Special Agent in Charge Jeannine Hammett. “Today’s sentencing sends a clear message that no public official gets a free pass to ignore the laws.”
Jack Johnson was Prince George’s County Executive from 2002 to December 2010. Prior to 2002, Jack Johnson was the county’s State’s Attorney, and spent nearly a decade as an attorney for the IRS Office of Chief Counsel.
In September 2009, Jack Johnson appointed James Johnson to serve as the Director of DHCD, which administered the HOME Investment Partnerships program to provide federal grants to states and localities to fund the construction, purchase and/or rehabilitation of affordable housing for rent or home-ownership. Patrick Ricker is a developer in Prince George’s County, and had an interest in Greenbelt Metropark, which sought to build a mixed-use project near the Greenbelt Metro Station, called Greenbelt Station. Mirza Baig is a physician and a commercial and residential developer in the County since at least 1992. Leslie Johnson was an elected County Councilwoman and Jack Johnson’s wife.
According to Jack Johnson’s guilty plea and court documents, from 2003 through at least November 12, 2010, Jack Johnson orchestrated a conspiracy in which Baig, Ricker and other business persons offered bribes, including money, trip expenses, meals, drinks, hotel rooms, airline tickets, rounds of golf, employment, mortgage payments, and monetary and in-kind campaign contributions to Jack and James Johnson and other state and local government officials. Baig and James Johnson pleaded guilty to being part of the conspiracy from 2006 through 2010, and Ricker pleaded guilty to being part of the conspiracy from about 1997 through at least September 11, 2008. According to court documents, the amount of bribes extorted by Jack Johnson and his co-conspirators total over $1.6 million.
In exchange for the bribes, Jack Johnson, James Johnson, and other County officials performed and agreed to perform favorable official actions for Baig, Ricker and other developers, business owners and their companies. The official acts included obtaining a waiver of a HOME Program regulation, securing millions of dollars in HOME funds; assisting in the acquisition of surplus property and land from the County for development by certain developers, including Baig and Ricker; providing the conspirators with non-public County information; obtaining necessary state and local approvals and permits for certain developments and businesses in the County, including Greenbelt Station, one of Ricker’s projects; obtaining employment with the County; obtaining management rights for County bond funds; obtaining County funding for certain developments and businesses in the County; assisting with state and County legislation regarding liquor store hours; influencing certain County officials to approve and/or facilitate County business; and, securing County commitments to lease property from certain developers at developments in the County. According to court documents, the value of the benefits received by the individuals paying the bribes totaled $10,098,496.
According to court documents, Jack Johnson intended to continue his corrupt scheme after his term of office ended, through his wife’s new position on the County Council and through other candidates for county offices. In meetings with Baig which were recorded by the FBI, Jack Johnson is heard promising to have Leslie Johnson use her position on the County Council to “take care of things” for Baig. Jack Johnson was also overheard in recorded conversations with county officials, a lobbyist, a developer and other business owners to extort donations for Leslie Johnson’s campaign for a county council seat and another candidate’s campaign for county executive. During the course of the scheme, Jack Johnson also regularly sought payments and employment that were to be awarded to him once he left office, in return for Jack Johnson providing official assistance while he was still county executive.
Additionally, just prior to his arrest on November 12, 2010, Jack Johnson and his wife Leslie Johnson exchanged a series of telephone calls. During one of those calls, as federal agents were knocking on the door of Johnsons’ home to execute a search warrant, Jack told Leslie to destroy the $100,000 check provided to him by Baig and to hide cash that he had hidden in their home. Specifically, Jack Johnson told Leslie to flush the check down the toilet and hide the cash in her underwear. Federal agents entered the home and recovered approximately $79,600 from Leslie who had hidden the cash in her underwear.
Leslie Johnson pleaded guilty on June 30, 2011 to conspiracy to commit witness and evidence tampering in order to obstruct a federal corruption investigation. As part of her plea agreement, Leslie Johnson will forfeit proceeds of the scheme, including $79,600 in cash. She faces a maximum sentence of 20 years in prison and a $250,000 fine at her sentencing scheduled for December 9, 2011 at 10:30 a.m.
Former Director of the Prince George’s County Department of Housing and Community Development (DHCD) James Edward Johnson, age 66, of Temple Hills, Maryland, pleaded guilty on January 28, 2011 to conspiracy to commit extortion. James Johnson and Jack Johnson are not related. Dr. Mirza Hussain Baig, age 67, of Burtonsville, Maryland, pleaded guilty on April 11, 2011 to conspiracy to commit extortion in connection with paying bribes to Jack Johnson and James Johnson. Patrick Q. Ricker, age 52, of Bowie, Maryland, pleaded guilty on December 30, 2009 to conspiring to commit honest services fraud and to make false statements to the Federal Election Commission; and to tax evasion.
James Johnson and Mirza Baig face a maximum sentence of five years in prison for the conspiracy to commit extortion at their sentencing scheduled for March 12 and 19, 2012, respectively. Patrick Ricker faces a maximum sentence of five years in prison for honest services fraud, false statements conspiracy and tax evasion at his sentencing scheduled for March 23, 2012.
A total of 15 defendants have been convicted to date in the related investigations of corruption in Prince George’s County.
United States Attorney Rod J. Rosenstein praised the FBI and IRS-CI for their work in the investigation. Mr. Rosenstein thanked Assistant United States Attorneys James A. Crowell IV, A. David Copperthite, Sujit Raman and Christen A. Sproule, who are prosecuting these cases.
Hubertus Knabe, Chef der STASI-Gedenkstätte Hohenschönhausen: “Rufmord an Justizsenator ist STASI-Racheakt”
Uncensored – New – FEMEN Video
TOP-SECRET – U.S. Army Commander’s Guide to Female Engagement Teams

Complex operations often require the development of specialized teams with multidisciplinary perspectives. Examples of these groups include human terrain teams, provincial reconstruction teams, and, most recently, female engagement teams (FETs). These specialized programs are tasked with engaging local populations to ascertain information on civil-society needs and problems; address security concerns; and to form links between the populace, military, and interagency partners.
History has taught us that most insurgent fighters are men. But, in traditional societies, women are extremely infl uential in forming the social networks that insurgents use for support. Co-opting neutral or friendly women — through targeted social and economic programs — builds networks of enlightened self-interest that eventually undermines the insurgents. To do this effectively requires your own female counterinsurgents. Win the women, and you own the family unit. Own the family, and you take a big step forward in mobilizing the population on your side.
Men, women, and children are part of the triangle of knowledge that must be targeted for information collection. In Afghanistan, we observe rather consistent themes. Men interpret information and tell you what they think you want to hear. Women see and hear what goes on behind the walls. Children run free in the community and see, watch, and are involved in nearly every activity in the community.
…
Initial Female Engagement Team Concept
FETs are not a new concept in Afghanistan. They have existed in one form or another for more than nine years. Civil affairs teams have performed this type of mission on a regular basis for years in both Afghanistan and Iraq, along with countries like Bosnia and Kosovo, but not under that name. The Marines picked up on the FET concept and employed it on a large scale well before the Army and they have had great success using it. Currently, there is little consistency in the FET programs between deployed Army brigade combat teams (BCTs) in Afghanistan. The BCTs are having varying degrees of success in contributing to the information repository covering the total Afghan population that is required to be understood as part of the COIN environment. The Army has been slow picking up on the FET concept; it is now being codifi ed and an Army wide FET training program is being developed based on the U.S. Army Special Operations Command (USASOC) Cultural Support Team (CST) program.
DOWNLOAD ORIGINAL DOCUMENT HERE
CONFIDENTIAL – STUDY – State Department Exploring Women’s Roles in Afghanistan
TOP-SECRET – City of London Police Occupy London Domestic Terrorism/Extremism Warning

These are photos and the text of a bulletin disseminated to local businesses by the City of London Police warning of possible extremist/terrorist threats arising from the Occupy London protests.
Terrorism/Extremism update for the City of London Business community
2 December 2011
The threat to the UK from international terrorism is SUBSTANTIAL.
The threat to Great Britain from Irish Republican Terrorism is SUBSTANTIAL.
UK/International
Columbia: The Revolutionary Armed Forces of Columbia (FARC) killed four of its longest held captives on Saturday during combat with Columbian forces. A fifth hostage allegedly survived after fleeing into the jungle after being held captive for 12 years, in what has been reported as a failed rescue attempt. It is FARC policy to kill prisoners if rescue attempts are made.
Al Qaeda/Pakistan: Al Qaeda has reportedly been holding Warren Weinsten, a 70-year-old American aid worker, hostage in Pakistan for three months. The al Qaeda leader, Ayman al-Zawahiri has said in a video that Weinstein would be released only if the US ceases its air strikes on Pakistan and Afghanistan and frees prisoners. The video offered no evidence that the aid worker is still alive.
Belarus: Two men have been sentenced to death for bombing the underground railway in the capital, Minsk, earlier this year. The attack on 11 April killed 15 people and wounded hundreds of others. Dmity Konovalov, 25, was found guilty of carrying out the explosion and Vladislav Kovalyov, also 25, of assisting in an act of terrorism. They were also found guilty of involvement in three earlier bomb attacks in 2005 and 2008, which together injured more than 100 people.
Domestic
Occupy London, ongoing
The Occupy London sites at St Paul’s Cathedral and Finsbury Square remain in place with the number of protesters present remaining fairly consistent. The majority of peaceful demonstrators from the St Paul’s camp appear to have moved on to the other camps. Demonstrations originating from the camp have decreased and lacked the support and momentum of earlier actions.
There are now three ‘Occupations’ by activists in or near the City of London. As the worldwide Occupy movement shows no sign of abating, it is likely that activists aspire to identify other locations to occupy, especially those they identify capitalism. City of London Police has received a number of hostile reconnaissance reports concerning individuals who would fit the anti-capitalist profile.
All are asked to be vigilant regarding suspected reconnaissance, particularly around empty buildings. Any signs of access or new markings should also be reported. You may encounter an increase in persons filming for the purpose of national or activist media. All are reminded that any encounters with suspected activists could be recorded and then uploaded or live-streamed to the internet.
Intelligence suggests that urban explorers are holding a discussion at the Sun Street squat. This may lead to an increase in urban exploration activity at abandoned or high profile sites in the capital.
Suspected hostile reconnaissance should be reported to the City of London Police immediately.
Climate Justice Collective, 3 December
‘Stand Up for Climate Justice’ is holding a vigil on the bank of the Thames from 11.30pm to 1.00am Friday Night, as well as climate prayers at 11.30am Saturday morning at St. Mary Le Bow church, Cheapside.
Saturday continues with a ‘Walk of Shame’ past alleged environmental and economic justice offenders along with a ‘teach-out’. This meets at St Paul’s at 10.30am, and is followed by a march to Parliament, meeting at Blackfriars Bridge at 12.00pm. Around 2.30pm the march will congregate outside Parliament. The event is planned to finish around 3.30pm.
The Canary Wharf Experience, 6 December
Occupy London will meet at St Paul’s around 4.15opm, from which they will attend and ‘tour’ Canary Wharf.
Electrician’s Strike, 7 December
Electricians will be takingindustrial action at Balfour Beatty sites across the country.
SHAC ‘Santa SHAC Supplier Shakedown week of action’, 5-11 December
Stop Huntingdon Animal Cruelty has advertised a week of action between these dates. It is expected that SHAC protesters will visit the customary targets during the period.
Ensure that your own security arrangements are adequate and robust at all times. Report any suspicious activity to Police immediately.
Confidential Anti Terrorist Hotline: 0800 789 321 or dial 999


UNCENSORED AND UNCUT – FEMEN Do you want me?
Creative idea explanation: The goal of the ‘Do you want me?’ project was to draw attention of the international web-community to a problem of sex-tourism in Ukraine, and to show that, as mentioned by Femin activists, ‘Ukraine is no brothel’.. Website do-you-want.me gives every user a chance to find himself in an urban den of inquity, pick a girl or a guy (tastes differ) for a paid ‘one time pleasure’. Before the erotic dance starts, the user must prove his solvency by activating the webcam and showing a banknote. Onlyafter the virtual character sees the money, will the story continue. Few will like the way the story goes – a trivial plot, so it seems… evolves into a naked truth(both literally and metaphorically) – we see how our paid sex-partner is being beaten up and addicted to drugs.
VERLEUMDUNGSKAMPAGNEN DER NEO-STAZI “GoMoPa” GEGEN JUSTIZSENATOR BRAUN, MINISTER STELTER UND MICH SOWIE WEITERE KOLLEGEN
Liebe Leser,
es ist offensichtlich, welches Spiel die NEO-STAZI “GoMoPa” spielt: Aus Angst davor, dass es Ihnen, die viel besser organisiert sind und viel gefährlicher sind, als der “Nationalsozialistische Untergrund” endlich an den Kragen geht, starten sie die Verleumdungskampagnen gegen ihre Gegner, Justizsenator Braun, Ex-Minister Stelter und mich sowie weitere Kollegen.
Die Frechheit der anyomen Scheisshausfliegen ist dabei schon aberwitzig, vor allem da sie mittlerweile nicht mehr “anonym” sind.
Herzlichst Ihr
Bernd Pulch, Magister Artium der Publizistik, Germanistik und Komparatistik
TOP-SECRET – Detainee Provisions in the National Defense Authorization Bills
Both House and Senate bills competing to become the National Defense Authorization Act for FY2012 contain a subtitle addressing issues related to detainees at the U.S. Naval Station at Guantanamo Bay, Cuba, and more broadly, hostilities against Al Qaeda and other entities. At the heart of both bills’ detainee provisions appears to be an effort to confirm or, as some observers view it, expand the detention authority that Congress implicitly granted the President via the Authorization for Use of Military Force (AUMF, P.L. 107-40) in the aftermath of the terrorist attacks of September 11, 2001.
H.R. 1540, as passed by the House of Representatives on May 26, 2011, contains provisions that would reaffirm the conflict and define its scope; impose specific restrictions on the transfer of any non-citizen wartime detainee into the United States; place stringent conditions on the transfer or release of any Guantanamo detainee to a foreign country; and require that any foreign national who has engaged in an offense related to a terrorist attack be tried by military commission if jurisdiction exists.
Shortly before H.R. 1540 was approved by the House, the White House issued a statement regarding its provisions. While supportive of most aspects of the bill, it was highly critical of those provisions concerning detainee matters. The Administration voiced strong opposition to the House provision reaffirming the existence of the armed conflict with Al Qaeda and arguably redefining its scope. It threatened to veto any version of the bill that contains provisions that the Administration views as challenging critical executive branch authority, including restrictions on detainee transfers and measures affecting review procedures.
In June, the Senate Armed Services Committee reported its initial version of the bill, S. 1253. The bill included many provisions similar to the House bill, but also included a provision requiring the military detention of certain terrorist suspects. After the White House and the chairs of other Senate committees objected to some of the provisions, Senate Majority Leader Reid delayed consideration of S. 1253 pending a resolution of the disputed language. The Senate Armed Services Committee reported a second version of the authorization bill on November 15, 2011, addressing some, but not all of the concerns. The new bill, S. 1867, would authorize the detention
of certain categories of persons and require the military detention of a subset of them; regulate status determinations for persons held pursuant to the AUMF, regardless of location; regulate periodic review proceedings concerning the continued detention of Guantanamo detainees; and continue current funding restrictions that relate to Guantanamo detainee transfers to foreign countries. Unlike the House bill, the Senate bill would not bar the transfer of detainees into the United States for trial or perhaps for other purposes.Despite the revisions to the detainee provisions, the Administration threatened to veto “any bill that challenges or constrains the President’s critical authorities to collect intelligence, incapacitate dangerous terrorists, and protect the Nation.”
This report offers a brief background of the salient issues raised by H.R. 1540 and S. 1867 regarding detention matters, provides a section-by-section analysis of the relevant subdivision of each bill, and compares the bills’ approaches with respect to the major issues they address.
DOWNLOAD ORIGINAL DOCUMENT HERE
CONFIDENTIAL-Carrier IQ Cellular Phone Intelligence Software Training Materials



The following presentation was included in a collection of materials related to Trevor Eckhart’s research into the “mobile service intelligence” software produced by Carrier IQ. The document was specifically mentioned in a cease and desist order that the company sent to Eckhart demanding that he remove their “confidential training materials” and take down his analysis of the company’s software. Though the company later withdrew the legal complaint, this presentation remains unavailable from its original location and is only available via a number of mirrors at file-hosting sites. Cryptome is offering a full mirror of Eckhart’s research, which includes this presentation.
DOWNLOAD ORIGIAL DOCUMENT HERE
VIDEO – CIA Archives: What Was the Katyn Massacre? (1973)
UNCENSORED AND UNCUT – FEMEN US
VERLEUMDUNGSKAMPAGNE DER FINGIERTEN STASI-“GoMoPa” GEGEN BERLINER JUSTIZMINISTER
Liebe Leser,
lesen Sie hier mehr über die STASI-“GoMoPa”, ihre Hintermänner, dubiosen Methoden und Ziele sowie Aktuelles zu dem Rufmord an dem Berliner Justizminister Braun.
http://www.victims-opfer.com/?p=24687
Diese Kampagne soll den Berliner Justiz-Minister Michael Braun an einem Vorgehen gegen “GoMoPa” und deren mutmassliche Hintermänner Resch, Maurischat, Bennewirtz, Ehlers & Co. hindern – nach dem alten STASI-Grundsatz “Rufmord ist die beste STASI-Verteidung”
Der CDU-Politiker wies die Vorwürfe zurück. ‘Ich habe als Notar nicht zu beurteilen, ob eine Immobilie werthaltig ist oder nicht’, sagte Braun. Er habe sich keine Verfehlung vorzuwerfen. ‘Das ist von einer Gruppe initiiert, die in engem Kontakt zur Stasi stand.”
Ich füge hinzu: “STEHT und genauso arbeitet !”
Herzlichst Ihr
Bernd Pulch, Magister Artium der Publizistik, Germanistik und Komparatistik
UNCENSORED – FEMEN against bribing of voters
VIDEO – Nazi Concentration and Prison Camps: WW2 Documentary Film (1945)
CONFIDENTIAL – El Dorado County Sheriff’s Department Use of Force Policy
VIDEO – Neo-Nazis Take Over German Village
FBI – Virginia Man Pleads Guilty to Providing Material Support to Terrorist Organization
ALEXANDRIA, VA—Jubair Ahmad, 24, a native of Pakistan and resident of Woodbridge, Va., pleaded guilty today to providing material support to Lashkar-e-Tayyiba (LeT), a designated foreign terrorist organization.
Neil H. MacBride, U.S. Attorney for the Eastern District of Virginia; Lisa Monaco, Assistant Attorney General for National Security; and James W. McJunkin, Assistant Director in Charge of the FBI’s Washington Field Office, made the announcement after the plea was accepted by U.S. District Judge T.S. Ellis III.
Ahmad faces a maximum penalty of 15 years in prison when he is sentenced on April 13, 2012.
“Foreign terrorist organizations such as LeT use the Internet as part of well-orchestrated propaganda campaigns to radicalize and recruit individuals to wage violent jihad and to promote the spread of terror,” said U.S. Attorney MacBride. “Today’s conviction of Jubair Ahmad demonstrates that we will aggressively investigate and prosecute anyone who provides material support to a terrorist organization in whatever form it takes.”
“This prosecution sheds light on some of the methods terrorist organizations employ to produce and publish their extremist propaganda,” said Assistant Attorney General Monaco. “Today, Jubair Ahmad is being held accountable for his role in providing this form of material support to Lashkar-e-Tayyiba.”
“By preparing and posting a graphic video that glorified violent extremism, Mr. Ahmad directly supported the mission of a designated terrorist organization,” said FBI Assistant Director in Charge McJunkin. “The FBI will track down and disrupt those who communicate with terrorist groups for the purpose of recruiting others to inflict harm on the U.S. and its interests overseas.”
LeT, or “Army of the Pure,” serves as the military arm of the political movement Markaz al-Dawa wal-Irshad in Pakistan. The mission of LeT is to conduct and promote violent jihad against those considered to be the enemies of Islam. On Dec. 24, 2001, the U.S. Department of State designated LeT as a foreign terrorist organization. The focus of LeT operations has been attacks on the neighboring country of India, in particular the disputed region of Kashmir between Pakistan and India.
According to a statement of facts filed with the plea agreement, Ahmad was born and raised in Pakistan and in 2007, after receiving a visa from the U.S. Department of State, Ahmad moved from Pakistan to the United States with his family.
Ahmad admitted today that in September 2010, while at his residence in Woodbridge, he engaged in a series of communications with an individual named Talha Saeed, who was in Pakistan. Talha Saeed is the son of Hafiz Muhammad Saeed, the leader of LeT. Talha Saeed requested Ahmad to prepare a video that would contain a prayer by Hafiz Saeed calling for the support of jihad and the mujahideen. In addition, Talha Saeed instructed Ahmad to present a variety of violent images on the video while Hafiz Saeed’s prayer is heard in the background.
Talha Saeed directed Ahmad to begin the LeT video with a number of pictures of Hafiz Saeed, then show scenes where atrocities have been inflicted on Muslims, followed by the activities of the mujahideen conducting attacks in Kashmir. At one point, Ahmad asked Talha Saeed if he wanted to include an image of the Mumbai attack to show the power of LeT. This is a reference to LeT’s operation against the city of Mumbai, India, on Nov. 26, 2008, which resulted in the death of over 160 people, including six Americans. Talha replied that he should not use anything referring to Mumbai.
Ahmad admitted that Talha Saeed told him to search for “Lashkar-e-Taiba” on YouTube to find additional images of mujahideen operations to include in the video. Talha Saeed further stated that the video will be popular in Pakistan and will run continuously on significant media programs and presentations.
On Sept. 25, 2010, Ahmad completed the LeT video and uploaded it to a YouTube account on the Internet. The next day, Ahmad sent a communication to another person overseas in which he explained that “Hafiz Saeed’s son Talha Saeed” had requested him to prepare the video. Forensic examination by the FBI subsequently confirmed that Ahmad had constructed the LeT video on his computer.
This case is being investigated by the FBI’s Washington Field Office. Assistant U.S. Attorney Stephen M. Campbell from the National Security and International Crimes Unit of the Eastern District of Virginia and Trial Attorney John T. Gibbs from the Counterterrorism Section of the National Security Division in the U.S. Department of Justice are prosecuting the case on behalf of the United States.
From the FBI – Ten Years Later: The Enron Case
 |
|---|
| More than 3,000 boxes of evidence and more than four terabytes of digitized data were collected by agents in the weeks after Enron declared bankruptcy Dec. 2, 2001. |
It was 10 years ago this month that the collapse of Enron precipitated what would become the most complex white-collar crime investigation in the FBI’s history.
Top officials at the Houston-based company cheated investors and enriched themselves through complex accounting gimmicks like overvaluing assets to boost cash flow and earnings statements, which made the company even more appealing to investors. When the company declared bankruptcy in December 2001, investors lost millions, prompting the FBI and other federal agencies to investigate.
The sheer magnitude of the case prompted creation of the multi-agency Enron Task Force, a unique blend of investigators and analysts from the FBI, the Internal Revenue Service-Criminal Investigation Division, the Securities and Exchange Commission, and prosecutors from the Department of Justice.
Agents conducted more than 1,800 interviews and collected more than 3,000 boxes of evidence and more than four terabytes of digitized data. More than $164 million was seized; to date about $90 million has been forfeited to help compensate victims. Twenty-two people have been convicted for their actions related to the fraud, including Enron’s chief executive officer, the president/chief operating officer, the chief financial officer, the chief accounting officer, and others.
“The Enron Task Force’s efforts resulted in the convictions of nearly all of Enron’s executive management team,” said Michael E. Anderson, assistant special agent in charge of the FBI’s Houston Division, who led the FBI’s Enron Task Force in Houston. “The task force represented a model task force—the participating agencies selflessly and effectively worked together in accomplishing significant results. The case demonstrated to Wall Street and the business community that they will be held accountable.”
CONFIDENTIAL-California Peace Officer Standards and Training Crowd Management and Civil Disobedience Guidelines

Penal Code Section 13514.5 requires the Commission on Peace Officer Standards and Training to establish guidelines and training for law enforcement’s response to crowd management and civil disobedience.
These guidelines contain information for law enforcement agencies to consider when addressing the broad range of issues related to crowd management and civil disobedience. The guidelines do not constitute a policy, nor are they intended to establish a standard for any agency. The Commission is sensitive to the needs for agencies to have individualized policies that reflect concern for local issues. The Commission intends these guidelines to be a resource for law enforcement executives that will provide maximum discretion and flexibility in the development of individual agency policies.
…
In the United States all people have the right of free speech and assembly guaranteed by the First Amendment of the Federal Constitution and California State Constitution. Law enforcement recognizes the right of free speech and actively protects people exercising that right.
The rights all people have to march, demonstrate, protest, rally, or perform other First Amendment activities comes with the responsibility to not abuse or violate the civil and property rights of others. The responsibility of law enforcement is to protect the lives and property of all people. Law enforcement should not be biased by the opinions being expressed nor by the race, gender, sexual orientation, physical disabilities, appearances, or affiliation of anyone exercising his/her lawful First Amendment rights. Law enforcement personnel must have the integrity to keep personal, political or religious views from affecting their actions.
When it becomes necessary to control the actions of a crowd that constitutes an unlawful assembly, the commitment and responsibility of law enforcement is to control lawfully, efficiently, and with minimal impact upon the community. A variety of techniques and tactics may be necessary to resolve a civil disobedience incident. Only that force which is objectively reasonable may be used to arrest violators and restore order.
All agencies should familiarize themselves with the terms, definitions, and guidelines set forth in this document. These are the generally accepted principles by which agencies respond to lawful and unlawful assemblies. The material in this document is designed to assist law enforcement executives in addressing the broad range of issues surrounding civil disobedience.
…
Guideline #9: Use of Force: Force Options
Agencies should develop use of force policies, procedures, and training for managing crowds and civil disobedience.
Discussion:
When dealing with crowds and civil disobedience situations, law enforcement must be a disciplined and well-organized control force. The decisions to use force and the force options that may be applied in response to these incidents range from law enforcement presence to deadly force. Peace officers need not use the least intrusive force option, but only that force which is objectively reasonable under the totality of the circumstances (Scott v. Henrich, 39 F. 3d 912, 9th Cir. 1994, and Forrester v. City of San Diego, 25 F. 3d 804 9th Cir. 1994). Graham v. Connor, 490 U.S. 386, 109 S. Ct. 1865, 104 L. Ed. 2d 443 (1989). The reasonableness of the force used to affect a particular seizure is analyzed under the Fourth Amendment and determined by balancing the nature and quality of the intrusion on the individual’s Fourth Amendment interests against the governmental interests at stake.
Prior to an event, agencies should continually review their use of force alternatives in response to potential actions by protesters. Training should reflect reasonable use of force alternatives in order that officers are prepared to consider the tactics/force options available. Chew v. Gates, 27 F. 3d 1432, 1443 (9th Cir. 1994).
* A Sampling of Use of Force Considerations:
- Determine compliance or non-compliance of crowd
- Physically moving non-compliant offenders
- Anticipate possible actions of demonstrators
- Identify criminal violations involved
- Develop arrest protocol
- Develop use of pain compliance protocol
- Plan for disabled, elderly, and children demonstrators
- Determine availability of personnel
- Evaluate availability of other public safety resources
- Include protection devices for involved personnel
- Plan for the safety of bystanders
- Evaluate mobility of suspects/protestors
- Determine avenues of controlled departure
- Anticipate potential for medical resources
- Establish protocols for less lethal munitions
* A Sampling of Force Options:
- Law enforcement presence
- Verbalization
- Firm grip
- Compliance techniques
- Control devices
- Nonlethal chemical agents
- Electrical control devices
- Impact weapons/batons
- Less lethal (i.e., sting balls, grenades, bean bags)
- Deadly force
DOWNLOAD ORIGINAL DOCUMENT HERE
UNCENSORED – NEW FEMEN VIDEO – Femen травили шкідливих комах на мітингу Фронту змін
CONFIDENTIAL-California Bluebook Law Enforcement Mutual Aid Plan

As you read this, somewhere in California one law enforcement agency is providing mutual aid to another. Mutual aid is an everyday occurrence in a state as large and diverse as California. This is the continuation of the decades-long process of “neighbor helping neighbor.” The law enforcement mutual aid system is an ongoing cooperative effort among law enforcement agencies to ensure an effective and organized response to a wide range of emergencies. There is a misconception that mutual aid is something used only during a riot or disaster. The mutual aid system has been used successfully for many other situations, including large criminal investigations, deployment of special teams such as Special Weapons and Tactics Teams, Bomb Squads, etc.
How will your agency use the mutual aid system? Planning, preparation and operational activities of law enforcement agencies in support of the mutual aid system must be consistent with each department’s policies and procedures and must also comply with the Standardized Emergency Management System (SEMS) and the National Incident Management System (NIMS).
All law enforcement executives, administrators, managers and field supervisors should familiarize themselves with this plan and its application. The personnel of the Cal EMA Law Enforcement Division are career peace officers and are available to assist you with planning, training and when necessary, emergency response coordination. It is important to note however, that Cal EMA does not “own” the mutual aid system. It is a part of California law enforcement, and those that participate each benefit – and bear part of the burden – of “neighbor helping neighbor.”
…
State of War Emergency
“State of War Emergency” means the condition which exists immediately, with or without a proclamation thereof by the Governor, whenever this state or nation is attacked by an enemy of the United States, or upon receipt by the state of a warning from the federal government indicating that such an enemy attack is probable or imminent. (Section 8558 (a) GC) During a state of war emergency, the Governor has complete authority over all agencies of state government and the right to exercise within the area or regions designated, all police power vested in the state by the Constitution and laws of the State of California (GC, Article 12, Section 8620 and Article 13, Section 8627, “California Emergency Services Act”). During a state of war emergency, mutual aid is mandatory. (Discussed later in the Plan.)
State of Emergency
“State of Emergency” means the duly proclaimed existence of conditions of disaster or of extreme peril to the safety of persons and property within the state caused by such conditions as air pollution, fire, flood, storm, epidemic, riot, drought, sudden and severe energy shortage, plant or animal infestation or disease, the Governor’s warning of an earthquake or volcanic prediction, or an earthquake, complications resulting from the Year 2000 Problem, or other conditions, other than conditions resulting from a labor controversy or conditions causing a “state of war emergency,” which, by reason of their magnitude, are or are likely to be beyond the control of the services, personnel, equipment, and facilities of any single county, city and county, or city and require the combined forces of a mutual aid region or regions to combat, or with respect to regulated energy utilities, a sudden and severe energy shortage requires extraordinary measures beyond the authority vested in the California Public Utilities Commission. (Section 8558 (b)(GC))
During a state of emergency, the Governor has complete authority over all agencies of state government and the right to exercise within the area or regions designated, all police power vested in the state by the Constitution and laws of the State of California (GC, Article 12, Section 8620 and Article 13, Section 8627, “California Emergency Services Act”). During a state of emergency, mutual aid is mandatory. (Discussed later in the Plan)
DOWNLOAD DOCUMENT HERE
CONFIDENTIAL-California Redbook Law Enforcement Guide for Emergency Operations


The California Emergency Management Agency’s original Law Enforcement Guide for Emergency Operations was developed in response to the need for standardization and uniformity of organization and response on the part of law enforcement agencies involved in major multi-jurisdictional and multi-agency incidents such as a civil disorder, technological disaster, or natural disaster.
The revised and expanded 2009 Law Enforcement Guide for Emergency Operations is designed to be a practical field-oriented guide to assist law enforcement personnel throughout the State of California with implementation of the Field Level Incident Command System. The intended primary users of this guide are watch commanders and field supervisors. The guide can also be an excellent emergency response tool for law enforcement managers, as well as line officers and deputies.
This updated edition incorporates the concept and statutory requirement of the Standardized Emergency Management System (SEMS). Additionally, the Law Enforcement Incident Command System (LEICS), as approved by the SEMS Law Enforcement Specialist Committee, is presented in this publication. Please disregard earlier editions of this guide. The Law Enforcement Guide for Emergency Operations is organized in a user-friendly format consisting of overview text, diagrams, organization charts, checklists, forms, and a glossary. Several sections are suitable for photocopying and distribution to field personnel. Our ultimate goal is to provide practical guidance for California law enforcement agencies in using the SEMS and LEICS organizational framework for efficient and safe response, management, and coordination of major emergencies and disasters.
DOWNLOAD ORGINAL DOCUMENT HERE
UNCENSORED – FEMEN-protesters arrested – Kiev Euro 2012 stadium opening ceremony
Topless women were arrested at the opening ceremony for the Euro 2012 stadium in Kiev after they invaded the pitch as part of a feminist protest.
One woman had to be carried off the pitch by a steward, wearing only a pair of black leggings with two footballs painted over her breasts.
The Ukrainian activists, Femen – who have a history of getting their kit off to promote their causes – believe the tournament will increase sex tourism in their country.
 Bare with me: A steward drags a topless activist off the pitch at the Euro 2012 opening ceremony in Kiev
Bare with me: A steward drags a topless activist off the pitch at the Euro 2012 opening ceremony in Kiev Final whistle: Stewards carry the blonde protester out of the Olympiyskiy Stadium
Final whistle: Stewards carry the blonde protester out of the Olympiyskiy StadiumThe demonstrators said in a statement: ‘Femen demands that UEFA initiate an explanatory campaign for football fans about the impermissibility of sex tourism and funding the sex industry, and the Ukrainian authorities criminalise the visiting of prostitutes.’
 Dressed for impact: A topless Ukrainian feminist is escorted away after her pitch invasion
Dressed for impact: A topless Ukrainian feminist is escorted away after her pitch invasionIt is believed that four women were arrested after police arrived at the Olympiisky National Sports Complex, which will host some games during next year’s tournament.
Their ‘Euro without prostitution’ protest followed a more modest performance by Colombian pop star Shakira and a whopping 2,000 other artists in front of 60,000 fans.
The group, many of whom are students, have previously stripped in front of Paris Hilton and at the Miss Ukraine beauty contest to show their belief that the beauty industry is a form of prostitution.
Femen also once organised mud wrestling competitions in the capital’s main square to protest against what they called the ‘dirty’ politics of president Viktor Yushchenkos.
Their actions are reminiscent of the controversial feminist ‘SlutWalks’, in which women dress provocatively for anti-rape demonstrations.
The reconstructed stadium’s opening ceremony came as teams from around Europe compete in qualifiers for the competition, which will take place in Ukraine and Poland.
Prostitution in Ukraine is illegal but reports say the country remains one of the main suppliers of prostitutes to Western Europe.
UEFA chief Michel Platini arrived last Monday for an inspection of the 70,000-seat building, and was at yesterday’s event alongside the Ukrainian president.
Mr Yanukovich said before the celebrations: ‘It’s a holiday for the whole of Ukraine.
‘The stadium’s successful renovation is undoubtedly an exhibition project for Ukraine’s image.’
But there was more embarrassment when fireworks set fire to some of the stage props, forcing the evacuation of the two central sectors.


Skilful moves: The sex tourism protesters gave stewards at the football stadium the runaround
Stadium staff hurried to put the flames out before spectators were allowed to return to their seats for the rest of the show.
Critics also claim the Olympiskiy’s estimated £300million reconstruction was overpriced and the costs were not transparent.
The first official football match at the new stadium is scheduled for November 11, when Ukraine will host Germany in a friendly match.
FEMEN-VIDEO -Roma Landyk – Go to Prison
TOP-SECRET-IMF Bermuda Anti-Money Laundering and Terrorist Financing Report

This assessment of the anti-money laundering (AML) and combating the financing of terrorism (CFT) regime of Bermuda is based on the Forty Recommendations 2003 and the Nine Special Recommendations on Terrorist Financing 2001 of the Financial Action Task Force (FATF). It was prepared using the AML/CFT assessment Methodology 2004, as updated in June 2006. The assessment team considered all the materials supplied by the authorities, the information obtained on-site during their mission from May 7 to 23, 2007, and other information subsequently provided by the authorities soon after the mission. During the mission, the assessment team met with officials and representatives of all relevant government agencies and the private sector. A list of the bodies met is set out in Annex 1 to the detailed assessment report.
The assessment was conducted by a team of assessors composed of staff of the International
Monetary Fund (IMF) and three expert(s) acting under the supervision of the IMF. The evaluation
team consisted of: Manuel Vasquez (LEG, team leader and financial sector expert); Antonio
Hyman-Bouchereau (LEG, legal expert); Ross Delston (legal expert under LEG supervision,
lawyer); and John Abbott (expert under LEG supervision, Designated Non-Financial Businesses
and Professions) (DNFBP). The assessors reviewed the institutional framework, the relevant
AML/CFT laws, regulations, guidelines and other requirements. The mission also reviewed the
regulatory and other institutional systems in place to counter money laundering (ML) and the
financing of terrorism (FT) through financial institutions (FIs) and DNFBP. The assessors also
examined the capacity, implementation, and effectiveness of all these systems.This report provides a summary of the AML/CFT measures in place in Bermuda at the time
of the mission and shortly thereafter. It describes and analyzes those measures, sets out Bermuda’s
levels of compliance with the FATF 40+9 Recommendations (see Table 1) and provides
recommendations on how certain aspects of the system could be strengthened (see Table 2). The
report was produced by the IMF as part of the assessment of Bermuda under the Offshore Financial
Center Assessment Program (OFC). It was presented to the Caribbean Financial Action Task Force
(CFATF) and endorsed by this organization at ministerial meeting in November, 2007.…
Preventive Measures–—Financial Institutions
9. The scope of the AML regulatory framework does not address CFT issues, and does
not cover key areas of the financial sector, including life insurance business and certain
elements of the investment/mutual funds sector. The lack of coverage in these areas constitutes
an important deficiency in Bermuda’s AML/CFT regime, particularly in light of its role in the
international financial system, even though life insurance does not account for the largest share of
this sector. The POC Regulations and GNs remain practically unchanged since the last IMF
assessment mission in 2003; this in spite of the weaknesses previously identified, a major upgrade of the international AML/CFT standards in 2003, and continued growth in the financial services
industry. At the time of the mission, the authorities had prepared draft new Regulations and were
contemplating amending the GNs, pending passage of proposed new legislation that was passed
subsequent to the mission in June 2007.….
3.4 Financial institution secrecy or confidentiality (R.4)
3.4.1 Description and Analysis
Legal Framework:
337. Inhibition of Implementation of FATF Recommendations (c. 4.1): Bermuda has no general statutory law on secrecy other than with respect to the regulatory laws discussed below and the common law
principles of confidentiality that apply to the customers of banks and other FIs. The authorities have cited the leading precedent on confidentiality, an English Court of Appeal case, Tournier v. National Provincial and Union Bank of England [1924] 1KB461 which, according to a leading text on the issue, held that – “. . . a bank owes to its customer an implied contractual duty to keep his affairs secret, but that the duty is qualified. The duty arises at the commencement of the relationship and continues after the customer has closed his account in relation to information gained during the period of the account. It covers information about the customer’s affairs gained by virtue of the banking relationship and is not limited to information from or about the account itself.”R. G. Toulson and C. M. Phipps, Confidentiality, 2nd ed. (Sweet & Maxwell, 2006), p. 257.
338. There are four qualifications, or exceptions to this duty:
(a) Where disclosure is under compulsion by law; (b) where there is a duty to the public to disclose; (c) where the interests of the bank require disclosure; (d) where the disclosure is made by the express
or implied consent of the customer.Tournier, at 471-472 and 473, cited in Toulson and Phipps, p. 258.
339. According to the authorities, Bermudian case law has followed this precedent, one example being Brian Lines v. Lines Overseas Management Ltd. [2006] Bda LR 43, 236, at 242.
340. The exception relating to disclosure under compulsion by law is embodied in a number of places in Bermudian statutory law. All of the five regulatory laws (the only exception being the MSB Regulations)
provide for confidentiality of information with gateways to the authorities. The Banks and Deposit Companies Act 1999 is typical: Section 52(1) provides that “no person who under or for the purposes of this Act receives information relating to the business or other affairs of any person; and . . . no person who obtains such information directly or indirectly from a person who has received it as aforesaid, shall disclose the information without the consent of the person to whom it relates and (if different) the person from whom it was received as aforesaid.” Disclosure of information in contravention of the statute is a criminal offense with penalties of up to $100,000 and five years imprisonment or both, under Section 52(3). Subsequent sections have a series of gateways allowing disclosure of information to the BMA, the Minister of Finance, the DPP and police, as well as disclosures by them to foreign authorities. See Sections 53 – 55. See also Sections 52, 52A, 52B, 52C of the Insurance Act 1978, Sections 78 – 81 of the Investment Business Act 2003, Sections 68 – 71 of the Investment Funds Act 2006, and Sections 48 – 51 of the Trusts (Regulation of Trust Business) Act 2003.341. However, there is no explicit gateway in any of these laws for disclosures to the FIA, since it was not in existence at the time those laws were enacted and therefore consideration should be given to remedying this deficiency by amending relevant laws.
…
352. Obtain Originator Information for Wire Transfers (applying c. 5.2 & 5.3 in R.5, c.VII.1):
Customer identification for one-off transactions below the equivalent of US$10,000 (BD$10,000) are not covered by CDD (identification) requirements in the regulations or otherwise. Consequently, wire transfers between the equivalent of US$1,000 and US$9,999 are not subject to customer identification requirements and hence FIs are not required to obtain and maintain full originator information. For wire transactions above US$10,000, the non-mandatory Guidance Notes (G94 to G98) set out the type of detail records that should be maintained to identify a customer, but do not specify such details to include account numbers, address or other substitute information as allowed for by SRVII. G98 only states that FIs should retain records of electronic payments with “sufficient detail” to enable them to establish the identity of the remitting customer and as far as
possible the identity of the ultimate recipient. While not specific to wire transfers, such detail may be available
in the Guidance Notes under Methods of Verification (G56 to G70) which include address, date of birth and
other information. In discussions with banks, there appears to be no restrictions in law or practice on the
inclusion of names and account numbers in outgoing wire transfers.DOWNLOAD ORIGINAL REPORT HERE
CBS – The murder of an American Nazi
Lesley Stahl reports on the murder of a neo-Nazi leader – killed by his 10-year-old son – and captures a growing subculture of hate playing out in America’s backyards and alongside the border.
VICTIMS: STASI”GoMoPa” and Neo-Nazi Murder Gang Linked To German Intelligence
TOP-SECRET-United Kingdom “Contest” Strategy for Countering Terrorism 2011
1.1 This is the third published version of the United Kingdom’s counter-terrorism strategy, CONTEST. This new strategy reflects the changing terrorist threat and incorporates new Government policies on counter-terrorism.
1.2 The aim of CONTEST is to reduce the risk to the UK and its interests overseas from terrorism, so that people can go about their lives freely and with confidence.
Strategic context
1.3 Last year, over 10,000 people were killed by terrorists around the world. But international law enforcement and military collaboration are changing the threats we face.
1.4 The leadership of Al Qa’ida is now weaker than at any time since 9/11. It has played no role in recent political change in North Africa and the Middle East. Its ideology has been widely discredited and it has failed in all its objectives. Continued international pressure can further reduce its capability. But Al Qa’ida continues to pose a threat to our own security; and groups affiliated to Al Qa’ida – notably in Yemen and Somalia – have emerged over the past two years to be a substantial threat in their own right.
1.5 Al Qa’ida is responsible for only a small fraction of terrorist attacks. Other groups, independent from Al Qa’ida but broadly sympathetic to its aims, continue to emerge and to conduct attacks around the world.
1.6 We judge that four factors will continue to enable terrorist groups to grow and to survive: conflict and instability; aspects of modern technology; a pervasive ideology; and radicalisation.
1.7 The threats we face here reflect global trends. Al Qa’ida, groups affiliated to Al Qa’ida, other terrorist groups and lone terrorists have all tried to operate in this country. Some have planned attacks here which we have disrupted. Others have recruited people for attacks overseas, spread propaganda and raised funds.
1.8 The threat level in the UK from international terrorism has been SEVERE for much of the period, meaning that we judge a terrorist attack in the UK to be ‘highly likely’. Threat levels continue to be set independently by JTAC.
1.9 For much of this period the greatest threat to the UK has come from terrorist groups based in Pakistan. British nationals (amongst hundreds of other Europeans) are training or operating in Pakistan and some intend to travel to Afghanistan. But over the past 12 months, the threat to UK interests from terrorists in Yemen and Somalia has significantly increased. People from the UK are also travelling to these countries to engage in terrorist related activity; some are returning to the UK to plan and conduct terrorist operations.
1.10 Over the past two years the threat from Northern Ireland Related Terrorism (NIRT) has also grown: there were 40 terrorist attacks in Northern Ireland in 2010 and there have been 16 terrorist attacks in Northern Ireland up to 30 June 2011.1 The threat from NIRT to Great Britain has increased.
1.11 Between January 2009 and December 2010 over 600 people were arrested for terrorist related activity in the UK. This is more than in any other European country. 67 people have been prosecuted and 58 people convicted for terrorist related offences.
Our response
1.12 Our counter-terrorism strategy will continue to be organised around four workstreams, each comprising a number of key objectives
• Pursue: to stop terrorist attacks;
• Prevent: to stop people becoming terrorists or supporting terrorism;
• Protect: to strengthen our protection against a terrorist attack; and
• Prepare: to mitigate the impact of a terrorist attack.1.13 The Strategic Defence and Security Review (SDSR) emphasises the need to tackle the root causes of instability. This approach is reflected in contest. For terrorism we need to address not only the immediate threat of attacks but the longer term factors which enable terrorist groups to grow and flourish. Some of these factors cannot be addressed within a counter-terrorism strategy and are much wider Government priorities. Coordination between CONTEST and other government programmes is essential. Working closely with other countries will remain a priority.
1.14 CONTEST will reflect our fundamental values and, in particular, our commitment not only to protect the people of this country and our interests overseas but to do so in a way that is consistent with and indeed advances our commitment to human rights and the rule of law. Our strategy will be proportionate to the risks we face and only engage in activity which is necessary to address those risks. It will be transparent: wherever possible and consistent with national security we will seek to make more information available in order to help the public to hold the Government to account over its policy and spending decisions.
1.15 We recognise that success has been achieved through international collaboration. That will continue to be the case in future.
Pursue
1.16 The purpose of Pursue is to stop terrorist attacks in this country and against our interests overseas. This means detecting and investigating threats at the earliest possible stage, disrupting terrorist activity before it can endanger the public and, wherever possible, prosecuting those responsible.
1.17 In 2011-2015 we want to:
• Continue to assess our counter-terrorism powers and ensure they are both effective and proportionate;
• Improve our ability to prosecute and deport people for terrorist-related offences;
• Increase our capabilities to detect, investigate and disrupt terrorist threats;
• Ensure that judicial proceedings in this country can better handle sensitive and secret material to serve the interests of both justice and national security; and
• Work with other countries and multilateral organisations to enable us to better tackle the threats we face at their source.…
2.48 Terrorists continue to use new technologies to communicate propaganda. While radicalisation continues to primarily be a social process involving contact between vulnerable people and radicalisers (not least because internet penetration in many countries with a high incidence of terrorism is still low) – the internet provides radicalisers with a vast range of materials to use once the process of radicalisation has begun. It allows for secure communication between private communities in which extremist ideas are shared and become normalised within that community. The internet also extends the reach of ideologues overseas, enabling them to preach to groups and reinforce messages of violence.
2.49 Use of social networking sites and video sharing is now commonplace. There have been a number of attempts by terrorist and extremist groups to ‘invade’ Facebook. Twitter will be used to repost media or forum articles enabling extremist content to be shared more quickly, widely and amongst people who would not normally search for extremist content. Estimates of the number of terrorism-related websites, made by experts in the field, range from several hundred to several thousand. It is clear that a few dozen are highly influential and frequented by terrorists.
DOWNLOAD ORIGINAL DOCUMENT HERE
TOP-SECRET-Israel’s Dubai Assassination in Photos
 The mother of Palestinian militant Mahmoud al-Mabhouh, who was recently killed, holds up a photo of him at their home in the Jebaliya refugee camp, northern Gaza Strip, Friday, Jan. 29, 2010. Hamas claimed on Friday that Israeli agents assassinated one of the Palestinian militant group’s veteran operatives in a killing allegedly carried out last week in Dubai, and vowed to retaliate. (AP Photo/Hatem Moussa)
The mother of Palestinian militant Mahmoud al-Mabhouh, who was recently killed, holds up a photo of him at their home in the Jebaliya refugee camp, northern Gaza Strip, Friday, Jan. 29, 2010. Hamas claimed on Friday that Israeli agents assassinated one of the Palestinian militant group’s veteran operatives in a killing allegedly carried out last week in Dubai, and vowed to retaliate. (AP Photo/Hatem Moussa) Father of senior Hamas military commander Mahmoud al-Mabhouh poses with his son’s picture at his family house in the northern Gaza Strip January 29, 2010. Israel assassinated al-Mabhouh, who played a major role in a Palestinian uprising in the 1980s, in Dubai, an official in the Islamist group said on Friday. Israeli officials had no immediate comment. REUTERS/Mohammed Salem
Father of senior Hamas military commander Mahmoud al-Mabhouh poses with his son’s picture at his family house in the northern Gaza Strip January 29, 2010. Israel assassinated al-Mabhouh, who played a major role in a Palestinian uprising in the 1980s, in Dubai, an official in the Islamist group said on Friday. Israeli officials had no immediate comment. REUTERS/Mohammed Salem Three suspects in the killing of Hamas militant, Mahmoud al-Mabhouh are shown in this CCTV handout from Dubai police February 15, 2010. Israel’s foreign minister said on Wednesday the use of the identities of foreign-born Israelis by a hit squad suspected of killing Hamas militant, Mahmoud al-Mabhouh, in Dubai did not prove the Mossad spy agency assassinated him. Men with the same names as seven of the 11 suspects whose European passport photos were distributed by Dubai live in Israel, and those reached by reporters insisted their identities had been stolen and noted the pictures were not a match. Handout dated February 15, 2010. REUTERS/Dubai Police/Handout
Three suspects in the killing of Hamas militant, Mahmoud al-Mabhouh are shown in this CCTV handout from Dubai police February 15, 2010. Israel’s foreign minister said on Wednesday the use of the identities of foreign-born Israelis by a hit squad suspected of killing Hamas militant, Mahmoud al-Mabhouh, in Dubai did not prove the Mossad spy agency assassinated him. Men with the same names as seven of the 11 suspects whose European passport photos were distributed by Dubai live in Israel, and those reached by reporters insisted their identities had been stolen and noted the pictures were not a match. Handout dated February 15, 2010. REUTERS/Dubai Police/Handout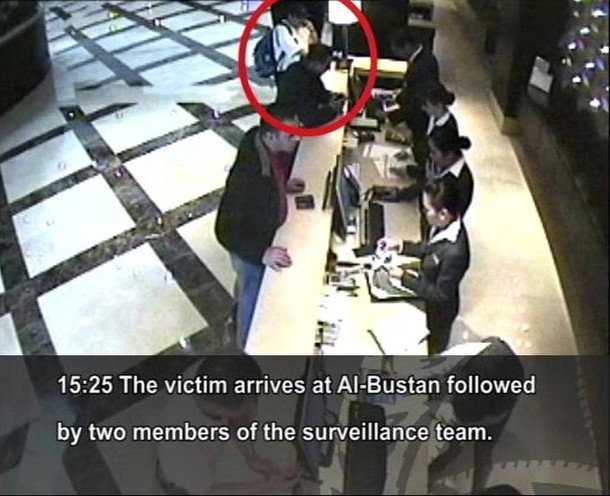 Hamas militant, Mahmoud al-Mabhouh (ringed), is shown arriving at his hotel in this CCTV handout from Dubai police February 15, 2010. Israel’s foreign minister said on Wednesday the use of the identities of foreign-born Israelis by a hit squad suspected of killing Hamas militant, Mahmoud al-Mabhouh, in Dubai did not prove the Mossad spy agency assassinated him. Men with the same names as seven of the 11 suspects whose European passport photos were distributed by Dubai live in Israel, and those reached by reporters insisted their identities had been stolen and noted the pictures were not a match. Handout dated February 15, 2010. REUTERS/Dubai Police/Handout
Hamas militant, Mahmoud al-Mabhouh (ringed), is shown arriving at his hotel in this CCTV handout from Dubai police February 15, 2010. Israel’s foreign minister said on Wednesday the use of the identities of foreign-born Israelis by a hit squad suspected of killing Hamas militant, Mahmoud al-Mabhouh, in Dubai did not prove the Mossad spy agency assassinated him. Men with the same names as seven of the 11 suspects whose European passport photos were distributed by Dubai live in Israel, and those reached by reporters insisted their identities had been stolen and noted the pictures were not a match. Handout dated February 15, 2010. REUTERS/Dubai Police/Handout Hamas militant, Mahmoud al-Mabhouh (bottom), is shown being followed by his alleged killers in this CCTV handout from Dubai police February 15, 2010. Israel’s foreign minister said on Wednesday the use of the identities of foreign-born Israelis by a hit squad suspected of killing Hamas militant, Mahmoud al-Mabhouh, in Dubai did not prove the Mossad spy agency assassinated him. Men with the same names as seven of the 11 suspects whose European passport photos were distributed by Dubai live in Israel, and those reached by reporters insisted their identities had been stolen and noted the pictures were not a match.
Hamas militant, Mahmoud al-Mabhouh (bottom), is shown being followed by his alleged killers in this CCTV handout from Dubai police February 15, 2010. Israel’s foreign minister said on Wednesday the use of the identities of foreign-born Israelis by a hit squad suspected of killing Hamas militant, Mahmoud al-Mabhouh, in Dubai did not prove the Mossad spy agency assassinated him. Men with the same names as seven of the 11 suspects whose European passport photos were distributed by Dubai live in Israel, and those reached by reporters insisted their identities had been stolen and noted the pictures were not a match.
TOP-SECRET – Mossad Dubai Assassins Travel Routes Maps
UNCENSORED – FEMEN: Акция “Изыди”
TOP-SECRET – IMF Report on Switzerland Fiscal Transparency
I. INTRODUCTION
1. This report provides an assessment of the fiscal transparency practices of Switzerland against the requirements of the IMF Code of Good Practices on Fiscal Transparency (2007). The first part is a description of practices, prepared by IMF staff on the basis of discussions with the authorities and their responses to the fiscal transparency questionnaire, and drawing on other available information. The second part is an IMF staff commentary on fiscal transparency in Switzerland. The two appendices summarize the staff’s assessments, comment on the observance of good practices, and document the public availability of information.
2. This assessment focuses primarily on fiscal transparency at the central
government (confederation) level. Given the unique character of political economy and
fiscal federalism in Switzerland, and that less than a third of general government expenditure
or revenue is accounted for by the confederation, this does not give a complete picture.
Cantons are responsible for important areas of economic and social policy, and have a strong
influence on the composition and impact of public spending, and the overall stance of fiscal
policy. Further work would be needed to prepare a comprehensive assessment of fiscal
transparency and fiscal risk covering the whole of general government.II. DETAILED DESCRIPTION OF PRACTICE
A. Clarity of Roles and Responsibilities
Definition of government activities
3. General government is defined consistently with Government Finance Statistics
(GFS) principles and is well covered in the budget process. 1.1.1
General government is defined in accordance with the principles of the Government Finance
Statistics Manual (GFSM 2001) and comprises four main sectors (Box 1): The federal
government comprises seven departments and related offices, the federal chancellery, and
four special funds. The special funds cover (i) railway projects; (ii) infrastructure;
(iii) technical universities; and (iv) the alcohol board. There are 26 cantonal governments.
The cantons are sovereign states with considerable autonomy. There are 2715 communes,
which likewise have considerable autonomy. The four social security institutions cover
(i) old age and survivors protection schemes; (ii) the disability protection scheme;
(iii) income compensation allowances in case of mandatory service and maternity; and
(iv) unemployment insurance. These schemes operate essentially on a pay-as-you-go basis.…
Box 2. The SNB’s Support for UBS as a Quasi-Fiscal Activity
The SNB has justified its recent support of UBS in relation to its role as lender-of-the-last resort. This explanation rests on three considerations, namely: that UBS is a systemically important institution; could provide sufficient collateral; and was solvent. On the last point, the SNB obtained advice from the Federal Banking Commission that UBS was solvent, enabling it to provide emergency support. It did so by funding 90 percent of the purchase price of distressed assets to the value of US$60 billion.1 These assets were valued by external assessors, and transferred to a Special Purpose Vehicle (SPV) under the SNB’s control. To reduce the risks of not fully recovering the funds of the SPV, the SNB has set up several safeguards against potential losses. UBS’ equity contribution to the stabilization fund, amounting to 10 percent of the assets purchased, serves as the primary loss protection. In the case of a loss on the SNB loan, the SNB’s warrant for 100 million UBS shares serves as secondary loss protection. This transaction should be classified as a QFA given the risk that the SNB may fail to recover all of its investment. In this case, the profits of the SNB distributed to the federal government would be lower, with a negative impact on the budget.
________________________
1/ On February 10, 2009, it was announced that the stabilization fund would acquire UBS assets for a lower
maximum amount than originally planned (approximately US$ 40 billion).…
68. There are some areas, however, where the authorities could consider taking
further measures, in consultation with parliament where appropriate, to enhance fiscal
transparency and the presentation and management of fiscal risks. These are summarized
below.Disclosure of additional fiscal information by the federal government
69. Support provided by the federal government and the SNB to UBS and other
financial institutions affected by the global crisis is reported in, respectively, the
confederation’s and the SNB’s financial statements, supplemented by quarterly updates
by the SNB. However, in order to provide a comprehensive assessment, the federal
government should consider publishing in its financial statements information on the SNB’s
support operations alongside the report of its own activities.70. The government should publish its findings on tax expenditures and regularly
update them. Tax expenditures do not need to be appropriated each year, thereby escaping
scrutiny and the need to compete with other fiscal priorities in the budget process. Over time,
tax expenditures can result in insidious erosion of the tax base. The volume of tax
expenditures is significant, as a recent study by the FTA indicates. The government is aware
of the importance of keeping tax expenditures in check. It could consider publishing an
annual tax expenditure statement with the annual budget.3671. The government should make an effort to disclose information on specific fiscal
risks, including contingent liabilities and QFAs, with the budget, in line with the IMF’s
Guidelines for Fiscal Risk Disclosure and Management, and eventually publish a single
statement of fiscal risks.37 In particular, the universal services provided by Swiss Post, Swiss
Rail, and others are partly financed through cross-subsidies, which represent a form of
interpersonal redistribution, and taxes and transfer payments from the budget are considered
more desirable to support such activities from a transparency perspective. QFAs are
disclosed only to a very limited extent.72. The Social Security Funds should be clearly distinguished. Apart from the
unemployment insurance scheme, the other three funds are jointly operated. The old age and
disability pension funds are cross-financing each other, with the first fund running persistent
surpluses that are used to finance the deficits of the second. Clearly, separating the three
funds would make the financial health of each of them more transparent and facilitate the
necessary policy discussion about the sustainability of current policies. Parliament has
already passed a bill to separate the old-age and disability pension funds into two separate
funds. A referendum on the issue will be held in September 2009. In addition, an overview of
the finances of the social security sector and its relationship with the budget in the short to
medium term, in the context of an assessment of long-term fiscal sustainability, should be
included in the budget documents. More forward-looking information on the finances of the special funds would also be useful. Together, these measures would provide a better basis for
assessing the sustainability of current fiscal policy.73. More information should be published on the sensitivity of the budget to changes
in macroeconomic variables and an alternative macroeconomic and fiscal scenario,
building on the useful analysis already published by the government. This would provide
a better basis for assessing the uncertainties surrounding the budget.38 In addition, the federal
government could consider extending and formalizing the process of external review of
macroeconomic forecasts and assessments of economic developments.74. An overview of the finances of public corporations could also be provided in the
budget. Some corporations receive significant funding from the budget, and others conduct
QFAs, making it important to consider their financial position and profitability in the context
of fiscal policy.75. Additional information should be reported on public debt management, namely,
the debt management strategy and performance against it, and the impact of parameter
changes on debt-servicing costs.76. A summary statement of all new policy measures that are reflected in the budget
proposals, with an estimate of their fiscal impact, should be published, to supplement the
summary data on expenditure by tasks already provided in Volume 3 of the budget
documents.77. Each federal government department should be encouraged to publish an
annual report that summarizes relevant information concerning their goals and objectives,
strategic priorities, operational risks, financial results, and nonfinancial performance. This
would be in line with practice in many OECD countries.DOWNLOAD ORIGINAL DOCUMENT HERE
INISDE VIEW – FBI’s Largest Division Provides Information to Protect the Nation
 |
|---|
| The FBI’s Criminal Justice Information Services Division, or CJIS, is located in West Virginia. |
A Year of Records for CJIS
Part 1: FBI’s Largest Division Provides Information to Protect the Nation
The FBI’s Criminal Justice Information Services Division—better known as CJIS—provides critical information to help our partners fight crime and protect the nation. Whether it’s answering a patrolman’s request for a subject’s criminal record during a traffic stop, verifying that a potential gun buyer is not a felon, or ensuring that a local municipality is not hiring a teacher who is a registered sex offender, CJIS receives millions of electronic requests every day for criminal information records and returns responses with amazing speed and accuracy.
 |
|
|---|---|
| David Cuthbertson, assistant director of CJIS. |
FBI.gov recently spoke with Special Agent David Cuthbertson, the newly appointed assistant director of CJIS, about the division’s accomplishments in 2011 and what to expect from the FBI’s largest division in the future.
Q: CJIS has been described as a lifeline to law enforcement. What are some of the division’s main programs?
Cuthbertson: The term “lifeline” aptly describes what we do day in and day out at CJIS. Our main programs include NCIC—the National Crime Information Center—and the Interstate Identification Index, which is the nation’s criminal history repository. NCIC is searched by law enforcement nearly 8 million times every day. And those requests—related to stolen property and information on wanted, missing, and unidentified persons—are returned to officers on the street within fractions of a second. NICS—the National Instant Criminal Background Check System—helps keep guns out of felons’ hands. In the last fiscal year, NICS conducted more than 15.9 million background checks in accordance with federal law, and more than 76,000 gun transfers were denied based on buyers’ criminal records. Our Law Enforcement National Data Exchange—N-DEx—provides a secure, online national information-sharing system for records related to bookings, arrests, probation, and parole report data. More than 4,100 agencies contribute to N-DEx, and the system has more than 124 million searchable records. And, of course, CJIS maintains the largest collection of fingerprint records in the world. During the last fiscal year, the Integrated Automated Fingerprint Identification System—IAFIS—identified more than 307,000 fugitives. These programs are only part of the important work we do at CJIS. Our recently released annual report highlights other programs and many of our record-setting accomplishments.
Q: Does CJIS share information with partners outside of law enforcement?
Cuthbertson: Absolutely. We provide information to the U.S. intelligence community for national security matters, and our data is also relied upon for civil uses such as criminal checks for employment and licensing. Teachers and school bus drivers, for example, are subject to background checks as required by state law, and CJIS systems provide that information to authorized users.
Q: Given the vast number of records in CJIS databases, how do you safeguard Americans’ privacy and civil liberties?
Cuthbertson: We balance civil liberties with everything we do. It’s important to remember that we only retain information related to a person’s criminal history based on lawful contacts with law enforcement. We don’t retain files on employment checks, for instance. By law, even gun background checks that come to us through NICS are destroyed every night—unless the purchase was lawfully denied. There are many similar protections in place to protect the privacy of American citizens.
Next: Biometrics and continued growth.
CONFIDENTIAL – Money Laundering Banks Fuel Mexican Drug Cartels
International banks have aided Mexican drug gangs (Los Angeles Times):
|
Mexico seeks to fill drug war gap with focus on dirty money
Tainted drug money runs like whispered rumors all over Mexico’s economy — in gleaming high-rises in beach resorts such as Cancun, in bustling casinos in Monterrey, in skyscrapers and restaurants in Mexico City that sit empty for months. It seeps into the construction sector, the night-life industry, even political campaigns.Piles of greenbacks, enough to fill dump trucks, are transformed into gold watches, showrooms full of Hummers, aviation schools, yachts, thoroughbred horses and warehouses full of imported fabric.
Officials here say the tide of laundered money could reach as high as $50 billion, a staggering sum equal to about 3% of Mexico’s legitimate economy, or more than all its oil exports or spending on prime social programs.
Mexican leaders often trumpet their deadly crackdown against drug traffickers as an all-out battle involving tens of thousands of troops and police, high-profile arrests and record-setting narcotics seizures. The 5-year-old offensive, however, has done little to attack a chief source of the cartels’ might: their money.
Even President Felipe Calderon, who sent the army into the streets to chase traffickers after taking office in 2006, an offensive that has seen 43,000 people die since, concedes that Mexico has fallen short in attacking the financial strength of organized crime.
“Without question, we have been at fault,” Calderon said during a meeting last month with drug-war victims. “The truth is that the existing structures for detecting money-laundering were simply overwhelmed by reality.”
Experts say the unchecked flow of dirty money feeds a widening range of criminal activity as cartels branch into other enterprises, such as producing and trading in pirated merchandise.
UNCENSORED – FEMEN vs UEFA EURO 2012

Topless FEMEN activists hold signs with football balls hanging from their underwear.

Topless FEMEN activists hold signs with football balls hanging from their underwear.

FEMEN activists take off clothing, so they can begin their protest.

Topless FEMEN activists hold signs with football balls hanging from their underwear.

Topless FEMEN activists hold signs with football balls hanging from their underwear.

Topless FEMEN activists hold signs with football balls hanging from their underwear.

Topless FEMEN activists hold signs with football balls hanging from their underwear.

Topless FEMEN activists hold signs with football balls hanging from their underwear.

Topless FEMEN activists hold signs with football balls hanging from their underwear.

Topless FEMEN activists hold signs with football balls hanging from their underwear.

Topless FEMEN activists hold signs with football balls hanging from their underwear.

Arrests begin.

Arrests begin.

Topless FEMEN activists are arrested and placed in police vehicles.

Topless FEMEN activists are arrested and placed in police vehicles.

Topless FEMEN activists are arrested and placed in police vehicles.
SECRET-DHS Wants to Create a “Federated Information Sharing System”
To understand the extent of the Federated Information Sharing System proposal, see our overview of just one of the databases maintained by a DHS component agency: Immigration and Customs Enforcement’s ICEPIC system which contains over 332,000,000 records on more than 254,000,000 entities as of early 2011.
The Department Of Homeland Security Wants All The Information It Has On You Accessible From One Place (Forbes):
|
Oversharing Is Never a Good Thing, Especially When it’s With DHS (ACLU):
|
Privacy Office – DHS Data Privacy and Integrity Advisory Committee Membership (dhs.gov):
Chairman: Richard V. Purcell,Chief Executive Officer, Corporate Privacy Group, Nordland, Wash. Mr. Purcell runs an independent privacy consulting group, focusing on policies, practices, and education. He is currently Chairman of TRUSTe and was formally the Chief Privacy Officer for the Microsoft Corporation.
Ana I. Anton, Professor of Computer Science at North Carolina State University, Raleigh, N.C. Dr. Anton is a distinguished research professor in the software engineering field and is the Director of privacy research team that is partially funded by the National Science Fund comprised of researchers at three universities. She has extensive professional expertise with research concerning privacy and security.
Ramon Barquin, President, Barquin International, Washington, D.C. Dr. Barquin has extensive technical and policy experience in data mining, system interoperability, and computer ethics. He worked at IBM for many years in both management and technical assignments prior to starting his own business developing information system strategies for public and private sector enterprises.
J. Howard Beales III, Associate Professor of Strategic Management and Public Policy, The George Washington University, Arlington, Va. Mr. Beales recently stepped down from his position as Director of Consumer Protection at the Federal Trade Commission, where privacy was a key initiative during his tenure.
Renard Francois, Attorney, Data Protection and Policy, Caterpillar, Inc., Peoria, Ill. Mr. Francois is in the firm’s Regulatory-Data Privacy, Legal Services Division where he works on privacy investigations. Prior to joining Caterpillar Inc., he was an attorney at Bass, Berry & Sims in Nashville, Tenn., where he worked in the firm’s Litigation Department on corporate internal investigations. He also has an LL.M. in Information Technology and Privacy Law.
A. Michael Froomkin, Professor of Law and Director of Faculty Development in the University of Miami’s School of Law. Professor Froomkin’s current research explores the legal and technical aspects of identification and authentication. Professor Froomkin also serves on the Electronic Frontier Foundation’s Advisory Board.
Joanna L. Grama, Information Security Policy and Compliance Director for Purdue University. Ms. Grama leads the University’s information technology policy and compliance activities related to security and privacy of personally identifiable information.
David A. Hoffman, Director of Security Policy and Global Privacy Officer, Intel Corporation, Hillsboro, Ore. Mr. Hoffman has experience in privacy policy issues at the business and technical level, working on issues of interoperability, improved data quality, and data retention. He serves on the board of directors for the non-profit privacy compliance organization, TRUSTe.
Lance Hoffman, Distinguished Research Professor, The George Washington University, Washington, D.C. Professor Hoffman is a professor of Computer Science and founded and leads the George Washington University computer security program.
Joanne McNabb, Chief, Office of Privacy Protection, California Department of Consumer Affairs, Sacramento, Calif. Ms. McNabb provides consumer education and practice recommendations on privacy issues to California state residents, businesses and government.
Lisa S. Nelson, Assistant Professor, Graduate School of Public and International Affairs, University of Pittsburgh, and Affiliated Assistant Professor, University of Pittsburgh School of Law. Professor’s Nelson research focuses on the implications of biometric technology for privacy, autonomy, and policy.
Greg Nojeim, Director, Project on Freedom, Security, & Technology, Center for Democracy and Technology. Mr. Nojeim is a former legislative counsel for the American Civil Liberties Union responsible for national security, immigration, and privacy.
Charles Palmer, Chief Technology Officer, Security and Privacy, Associate Director of Computer Science Research at IBM, Yorktown Heights, N.Y. Dr. Palmer manages the Security, Networking, and Privacy Departments at the IBM Thomas J. Watson Research Center, where various teams around the world are developing privacy-related technology and exploring how technology can help preserve privacy while improving data quality.
Lydia Parnes, Partner, Wilson Sonsini Goodrich & Rosati, P.C. Ms. Parnes leads the firm’s Privacy and Consumer Regulatory Practice Group. She served as Director of the Federal Trade Commission’s Bureau of Consumer Protection from 2004-2009 and as Deputy Director from 1992-2004.
Christopher Pierson, Chief Privacy Officer and Senior Vice President, Citizens Financial Group, Inc. (Royal Bank of Scotland- RBS). Dr. Pierson was President and Chairman of the Board of the Intraguard Phoenix Member’s Alliance, Inc., from 2003-2007 and served on the Arizona Office of Homeland Security’s Homeland Security Coordinating Council from 2003-2006.
Jules Polonetsky, Co-Chair and Director, Future Privacy Forum. Mr. Polonetsky focuses on privacy issues posed by new technologies and new uses of personal data, including government use of Web 2.0 technologies. He was formerly Vice President, Integrity Assurance, at America Online, Inc., and Chief Privacy Officer and Special Counsel at DoubleClick.
John Sabo, Director, Global Government Relations, CA Technologies, Washington D.C. Mr. Sabo has over 17 years experience addressing privacy, cybersecurity, and trust issues with both CA Technologies and the Social Security Administration. He is President of the International Security Trust and Privacy Alliance and board member of the Information Technology – Information Sharing and Analysis Center.
Ho Sik Shin, General Counsel and Chief Privacy Officer, Millennial Media, Inc. Mr. Shin is an Adjunct Professor in the Georgetown University Sports Industry Management Program, and was formerly General Counsel for Octagon Athletes & Personalities and General Counsel for Advertising.com, Inc.
Lisa J. Sotto, Partner at Hunton & Williams, New York, N.Y. Ms. Sotto heads the firm’s Privacy & Information Management Practice and works extensively with the firm’s Center for Information Policy Leadership on topics ranging from improved privacy notices to responsible pattern analysis. She is a member of the family of a 9/11 victim.
Barry Steinhardt, Senior Advisor, Privacy International. From 1993-2009 Mr. Steinhardt served in various leadership roles in the American Civil Liberties Union, most recently as Director of the ACLU’s Technology and Liberty Project working on issues including airline passenger screening, video surveillance, database privacy, and border security.
Video-FEMEN DSK PARIS
FEMEN – Video – Roma Landyk – Go to Prison
CONFIDENTIAL – Banks Profited from Trillions in Secret Fed Bailout Programs
 JPMorgan Chase chief Jamie Dimon speaks to a lunchtime gathering of the Portland Business Alliance, Thursday, Nov. 3, 2011 at the Portland Hilton in Portland, Ore. As CEO of JP Morgan Chase, he told shareholders that his bank used the Fed’s Term Auction Facility “at the request of the Federal Reserve to help motivate others to use the system.” He neglected to mention that the bank’s total TAF borrowings were almost twice its cash holdings. (AP Photo/The Oregonian, Randy L. Rasmussen)
JPMorgan Chase chief Jamie Dimon speaks to a lunchtime gathering of the Portland Business Alliance, Thursday, Nov. 3, 2011 at the Portland Hilton in Portland, Ore. As CEO of JP Morgan Chase, he told shareholders that his bank used the Fed’s Term Auction Facility “at the request of the Federal Reserve to help motivate others to use the system.” He neglected to mention that the bank’s total TAF borrowings were almost twice its cash holdings. (AP Photo/The Oregonian, Randy L. Rasmussen)Secret Fed Loans Helped Banks Net $13B (Bloomberg):
The Federal Reserve and the big banks fought for more than two years to keep details of the largest bailout in U.S. history a secret. Now, the rest of the world can see what it was missing.
The Fed didn’t tell anyone which banks were in trouble so deep they required a combined $1.2 trillion on Dec. 5, 2008, their single neediest day. Bankers didn’t mention that they took tens of billions of dollars in emergency loans at the same time they were assuring investors their firms were healthy. And no one calculated until now that banks reaped an estimated $13 billion of income by taking advantage of the Fed’s below-market rates, Bloomberg Markets magazine reports in its January issue.
Saved by the bailout, bankers lobbied against government regulations, a job made easier by the Fed, which never disclosed the details of the rescue to lawmakers even as Congress doled out more money and debated new rules aimed at preventing the next collapse.
A fresh narrative of the financial crisis of 2007 to 2009 emerges from 29,000 pages of Fed documents obtained under the Freedom of Information Act and central bank records of more than 21,000 transactions. While Fed officials say that almost all of the loans were repaid and there have been no losses, details suggest taxpayers paid a price beyond dollars as the secret funding helped preserve a broken status quo and enabled the biggest banks to grow even bigger.
…
The amount of money the central bank parceled out was surprising even to Gary H. Stern, president of the Federal Reserve Bank of Minneapolis from 1985 to 2009, who says he “wasn’t aware of the magnitude.” It dwarfed the Treasury Department’s better-known $700 billion Troubled Asset Relief Program, or TARP. Add up guarantees and lending limits, and the Fed had committed $7.77 trillion as of March 2009 to rescuing the financial system, more than half the value of everything produced in the U.S. that year.
“TARP at least had some strings attached,” says Brad Miller, a North Carolina Democrat on the House Financial Services Committee, referring to the program’s executive-pay ceiling. “With the Fed programs, there was nothing.”
Bankers didn’t disclose the extent of their borrowing. On Nov. 26, 2008, then-Bank of America (BAC) Corp. Chief Executive Officer Kenneth D. Lewis wrote to shareholders that he headed “one of the strongest and most stable major banks in the world.” He didn’t say that his Charlotte, North Carolina-based firm owed the central bank $86 billion that day.
“When you see the dollars the banks got, it’s hard to make the case these were successful institutions,” says Sherrod Brown, a Democratic Senator from Ohio who in 2010 introduced an unsuccessful bill to limit bank size. “This is an issue that can unite the Tea Party and Occupy Wall Street. There are lawmakers in both parties who would change their votes now.”
The size of the bailout came to light after Bloomberg LP, the parent of Bloomberg News, won a court case against the Fed and a group of the biggest U.S. banks called Clearing House Association LLC to force lending details into the open.
…
The Treasury Department relied on the recommendations of the Fed to decide which banks were healthy enough to get TARP money and how much, the former officials say. The six biggest U.S. banks, which received $160 billion of TARP funds, borrowed as much as $460 billion from the Fed, measured by peak daily debt calculated by Bloomberg using data obtained from the central bank. Paulson didn’t respond to a request for comment.
The six — JPMorgan, Bank of America, Citigroup Inc. (C), Wells Fargo & Co. (WFC), Goldman Sachs Group Inc. (GS) and Morgan Stanley — accounted for 63 percent of the average daily debt to the Fed by all publicly traded U.S. banks, money managers and investment-services firms, the data show. By comparison, they had about half of the industry’s assets before the bailout, which lasted from August 2007 through April 2010. The daily debt figure excludes cash that banks passed along to money-market funds.
…
TARP and the Fed lending programs went “hand in hand,” says Sherrill Shaffer, a banking professor at the University of Wyoming in Laramie and a former chief economist at the New York Fed. While the TARP money helped insulate the central bank from losses, the Fed’s willingness to supply seemingly unlimited financing to the banks assured they wouldn’t collapse, protecting the Treasury’s TARP investments, he says.
“Even though the Treasury was in the headlines, the Fed was really behind the scenes engineering it,” Shaffer says.
Congress, at the urging of Bernanke and Paulson, created TARP in October 2008 after the bankruptcy of Lehman Brothers Holdings Inc. made it difficult for financial institutions to get loans. Bank of America and New York-based Citigroup each received $45 billion from TARP. At the time, both were tapping the Fed. Citigroup hit its peak borrowing of $99.5 billion in January 2009, while Bank of America topped out in February 2009 at $91.4 billion.
Lawmakers knew none of this.
They had no clue that one bank, New York-based Morgan Stanley (MS), took $107 billion in Fed loans in September 2008, enough to pay off one-tenth of the country’s delinquent mortgages. The firm’s peak borrowing occurred the same day Congress rejected the proposed TARP bill, triggering the biggest point drop ever in the Dow Jones Industrial Average. The bill later passed, and Morgan Stanley got $10 billion of TARP funds, though Paulson said only “healthy institutions” were eligible.
Mark Lake, a spokesman for Morgan Stanley, declined to comment, as did spokesmen for Citigroup and Goldman Sachs.
Had lawmakers known, it “could have changed the whole approach to reform legislation,” says Ted Kaufman, a former Democratic Senator from Delaware who, with Brown, introduced the bill to limit bank size.
STASI-NAMEN ALPHABETISCH BUCHSTABE WR-ZI – STASI-NAMES IN ALPHABETICAL ORDER – WR-ZI
Die Liste wurde bereits früher hier publiziert:
http://stasiopfer.de/component/option,com_simpleboard/Itemid,/func,view/id,993815828/catid,4/
Vom “Stasiopfer”-Angebot führt ein Link zu einer Website in den USA (www.jya.com), die sich auch mit den Praktiken von Geheimdiensten beschäftigt. Dort findet sich die “Fipro-Liste”, das detaillierte “Finanzprojekt” der Stasi, angefertigt in den letzten Tagen der DDR, um die Rentenansprüche der rund 100 000 hauptamtlichen Mitarbeiter des MfS auch nach dem Zusammenbruch des Systems belegen zu können. Die “Fipro-Liste” ist seit langem bekannt und diente Anfang der neunziger Jahre etwa zur Identifizierung der so genannten OibE – Offiziere im besonderen Einsatz. Diese Liste „Offiziere im besonderen Einsatz“im Jahre 1991 erschien in der “taz. Die Echtheit kann beim BStU überprüft werden.
Siehe u.a. http://www.spiegel.de/spiegel/print/d-22539439.html
Auf Druck ehemaliger STASI-Leute und Ihrer Genossen wurde die Liste aus dem Verkehr gezogen.
Hier ist sie wieder:
021068428270;17;00;00;;WRANIK, DIRK:;;;8300,00
300646428216;14;31;00;;WRANIK, HANS-GEORG:;;;28125,00
091055427723;14;00;46;;WRANIK, VOLKER:;;;23632,50
200271413625;18;33;00;;WREDE, ANDREAS:;;;2720,00
190459500847;30;83;00;;WREDE, CHRISTINE:;;;22979,51
130470404528;04;69;00;;WREDE, MARCO:;;;9555,00
070156400842;30;47;00;;WREDE, PETER:;;;22342,50
280141404627;04;00;43;;WREHDE, SIEGMAR:;;;19125,00
150369412214;18;32;00;;WRENZYCKI, STEFFEN:;;;9600,00
010440429744;97;08;00;;WRESCH, GERHARD:;;;27000,00
170162430077;98;20;00;;WRESCH, THOMAS:;;;20460,00
310755406154;04;06;00;;WROBEL, BERND:;;;19262,50
060159408920;18;29;00;;WROBEL, FRANK:;;;19512,50
181239404744;04;19;00;;WROBEL, GERT:;;;28620,00
110964400748;03;51;00;;WROBEL, MAIK:;;;17105,00
100471511416;07;19;00;;WROBEL, MANUELA:;;;4980,00
290669410311;18;33;00;;WROBEL, SILVIO:;;;9600,00
160265408017;06;51;00;;WROBEL, VOLKMAR:;;;17352,50
030854414858;99;40;00;;WROBLEWSKI, DIETER:;;;24480,00
160963406166;04;06;00;;WRUBLICK, ROLF:;;;17930,00
181253408979;99;51;00;;WRUCK, BERNFRIED:;;;23940,00
180957415128;30;63;00;;WRUCK, FRANK:;;;16603,75
281253403818;94;65;00;;WRUCK, GUENTER:;;;19600,00
070348403845;99;43;00;;WRUCK, HANS-ULRICH:;;;23250,00
040270400873;01;06;24;;WRUCK, HEIKO:;;;6806,61
280735406144;04;14;00;;WRUCK, HEINZ:;;;29250,00
040349403866;03;00;47;;WRUCK, HELMUT:;;;18000,00
160471429724;94;65;00;;WRUCK, MARKO:;;;2870,00
290333506168;04;80;00;;WRUCK, ROSEL:;;;19875,00
040838429717;99;43;00;;WRUCK, WOLFGANG:;;;26250,00
311250415404;07;00;57;;WRYCZA, HASSO:;;;25200,00
091268426513;18;35;00;;WU(E)NSCH, OLIVER:;;;9675,00
271067409512;98;84;00;;WU(E)NSCH, RALF:;;;14919,00
230463522233;12;00;55;;WU(E)NSCHE, ANGELIKA:;;;15455,00
160369428223;18;31;00;;WU(E)NSCHE, TOM:;;;9986,44
011062421327;12;80;00;;WU(E)NSCHMANN, JO(E)RG:;;;15592,50
261169420326;18;31;00;;WU(E)RSTL, FRANK:;;;6705,00
100657406913;96;15;00;421/79, F:;WU(E)RZBURG, GERD;1157;STOLZENFELSSTR. 2;
100657406913;96;15;00;421/79, F:;WU(E)RZBURG, GERD;1157;STOLZENFELSSTR. 2;
141069406168;18;38;00;;WU(E)STENHAGEN, DIRK:;;;9600,00
210448420011;15;09;00;;WUCHERT, DIETER:;;;25500,00
081247416229;97;06;00;;WUCKEL, BERND:;;;23937,50
301248516223;99;77;00;;WUCKEL, GABRIELE:;;;17160,00
100150412310;07;15;00;;WUCKELT, BURKHARD:;;;26580,00
091049509925;07;51;00;;WUCKELT, ERIKA:;;;23250,00
221067407239;18;35;00;;WUDKA, PETER:;;;9675,00
121155419725;11;20;00;;WUDY, INGO:;;;22400,00
071063419725;18;80;00;;WUDY, MICHAEL:;;;19965,00
201154512231;30;39;00;;WUEBBENHORST, SABINE:;;;17465,00
301251503714;98;83;00;;WUEHLER, BAERBEL:;;;19150,81
080251407320;99;09;00;;WUEHLER, ULRICH:;;;24735,00
040168427615;14;00;51;;WUENDISCH, INGO:;;;12600,00
250342421821;12;29;00;;WUENDRICH, WOLFGANG:;;;25500,00
221041429720;98;84;00;;WUENSCH, DIETER:;;;25687,50
201267427738;14;06;00;;WUENSCH, FRANK:;;;13244,00
210964422750;12;18;00;;WUENSCH, GERD:;;;11084,00
030642530224;98;83;00;;WUENSCH, GISELA:;;;20085,00
030955403613;04;00;43;;WUENSCH, HARALD:;;;21901,93
020269409522;06;69;00;;WUENSCH, JENS:;;;12775,00
160434407235;96;15;13;;WUENSCH, LOTHAR:;;;28500,00
240362413723;97;01;00;;WUENSCH, RALF:;;;16830,00
131163427732;12;06;00;;WUENSCH, ROBERTO:;;;17580,49
230769420539;12;69;00;;WUENSCH, STEFFEN:;;;8055,00
200230406154;98;18;00;;WUENSCH, WALTER:;;;30687,50
070157530112;99;40;00;;WUENSCHE, ELKE:;;;18735,42
231052404632;97;01;00;;WUENSCHE, HANS-JUERGEN:;;;21060,00
221246426523;05;80;00;;WUENSCHE, HANS-JUERGEN:;;;25437,50
281139430273;98;19;00;;WUENSCHE, JOACHIM:;;;25500,00
010751404640;04;00;50;;WUENSCHE, JOACHIM:;;;27360,00
230851416213;97;06;00;;WUENSCHE, KLAUS-DIETER:;;;23760,00
270730428943;14;51;00;;WUENSCHE, MANFRED:;;;23250,00
251052420518;30;48;00;;WUENSCHE, PETER:;;;24720,00
110259430116;94;30;00;;WUENSCHE, UTZ:;;;17940,24
281228430013;98;19;00;;WUENSCHE, WOLFGANG:;;;35250,00
120658422729;12;80;00;;WUENSCHMANN, DIETMAR:;;;17077,50
130551417777;09;08;00;;WUERBACH, HERBERT:;;;22500,00
120140419349;10;53;00;;WUERBACH, HERBERT:;;;27000,00
310855417758;09;80;00;;WUERBACH, LUTZ:;;;18967,50
180447430088;30;47;00;;WUERDIG, REINER:;;;24414,00
121152412253;18;35;00;;WUERFEL, ECKHARD:;;;25920,00
210570407523;05;69;00;;WUERFEL, ENRICO:;;;9060,00
300954412240;07;51;00;;WUERFEL, KLAUS-DIETER:;;;25200,00
300746430057;96;15;09;;WUERFEL, KONRAD:;;;28500,00
100570400826;01;06;24;;WUERFEL, STEFFEN:;;;2896,61
040457421711;12;00;51;;WUERFEL, WILFRIED:;;;22080,00
150568418926;18;35;00;;WUERKER, HOLGER:;;;10475,00
040542530138;18;27;00;;WUERKER, INGRID:;;;24000,00
050643429724;18;29;00;;WUERKER, JOACHIM:;;;28500,00
060355419619;95;45;00;;WUERTENBERGER, FRANK:;;;21797,50
200149407336;07;55;00;;WUERTZ, MANFRED:;;;18625,00
290536420321;98;20;00;;WUERZ, ROLF:;;;27000,00
290952414449;97;08;00;;WUERZBERGER, HANS-DIETER:;;;23760,00
060130430040;94;30;00;;WUERZBERGER, HEINZ:;;;27750,00
041044511510;99;40;00;;WUERZBERGER, HELGA:;;;25500,00
141129414419;97;08;00;;WUERZBERGER, WERNER:;;;27750,00
291053406933;15;00;44;;WUERZBURG, CHRISTIAN:;;;33060,00
061250417726;09;80;00;;WUERZBURG, ERHARD:;;;18937,50
060234506919;30;50;00;;WUERZBURG, MARGARETE:;;;20056,01
100468430279;99;43;00;;WUERZBURG, TIM:;;;9675,00
271231406912;99;49;00;;WUERZBURG, WERNER:;;;19735,89
080566413039;08;00;42;;WUERZNER, STEFFEN:;;;15026,27
040943407528;05;08;00;;WUESTE, PETER:;;;22500,00
280336406163;97;08;00;;WUESTEMANN, BODO:;;;30750,00
291263508516;04;53;00;;WUESTEMANN, GRIT:;;;12321,47
030661406114;04;15;00;;WUESTEMANN, RALPH:;;;18947,50
101055408318;30;47;00;;WUESTEMANN, SIEGFRIED:;;;29035,00
221168408927;18;35;00;;WUESTENBERG, KNUT:;;;9825,00
290167400711;01;08;00;;WUESTENBERG, ROY:;;;14052,00
040934400412;01;06;22;;WUESTENBERG, WOLF-DIETER:;;;20375,00
290834406181;94;03;00;;WUESTENECK, DIETER:;;;37500,00
040758504617;99;40;00;;WUESTENECK, DORIS:;;;14828,09
160639530173;98;50;00;;WUESTENECK, HANNELORE:;;;30000,00
240856406136;99;40;00;;WUESTENECK, JOERG:;;;22597,50
061133529710;99;77;00;;WUESTENECK, MARGA:;;;39000,00
080249427613;97;06;00;;WUESTNER, FRANK:;;;24750,00
090433430125;96;15;21;;WUESTNER, WOLFGANG:;;;27000,00
060355528276;30;47;00;;WUJAK, BRIGITTE:;;;18760,82
290751429812;30;47;00;;WUJAK, VOLKER:;;;20514,18
251132406134;30;56;00;;WUJANZ, JOHANNES:;;;35160,00
091165416216;09;15;00;;WUJESCH, FRANK:;;;11016,00
250563416225;99;40;00;;WUJESCH, JENS:;;;19085,00
310768524627;13;00;50;;WUKASCH, ANNETT:;;;12155,00
221068420523;18;35;00;;WUKASCH, MIRKO:;;;9825,00
011259408417;97;01;00;;WULF, ANDREAS:;;;25530,00
050961402711;02;00;47;;WULF, ARNE:;;;21120,00
030243530059;30;63;00;;WULF, BARBARA:;;;16560,00
290348402716;02;20;00;;WULF, CLAUS-DIETER:;;;33660,00
180651401348;01;00;45;;WULF, DIETRICH:;;;28290,00
120729401811;02;51;00;;WULF, GUENTER:;;;24000,00
230453414423;99;43;00;;WULF, HANS-JOACHIM:;;;20880,00
121167403413;18;35;00;;WULF, JOERG:;;;10600,00
220567410835;97;01;00;;WULF, MARCO:;;;6264,00
280471406182;18;35;00;;WULF, SEBASTIAN:;;;2795,00
160564402520;94;03;00;;WULF, SIEGMAR:;;;15048,00
101044402527;02;06;00;;WULF, ULRICH:;;;24625,00
090635400864;01;26;00;;WULFF, DIETER:;;;26250,00
100943402809;02;06;00;;WULFF, GUENTHER-JOACHI:;;;27000,00
110265401530;99;40;00;;WULFF, HENRY:;;;20415,00
210168430223;15;65;00;;WULFF, HOLGER:;;;9872,00
050450400212;02;00;42;;WULFF, HORST:;;;25245,00
250343429745;15;00;47;;WULFF, INGBERT:;;;30000,00
230251405828;04;08;00;;WULFF, NORBERT:;;;19215,00
191247404233;04;02;00;;WULFF, OTTO:;;;32722,50
220171401510;01;69;00;;WULFF, RONNY:;;;2896,61
231268404818;04;06;00;;WULFF, THOMAS:;;;13750,00
261155401917;02;03;00;;WULFF, UWE:;;;21975,00
270542401540;99;02;00;;WULFF, WINFRIED:;;;24000,00
230129430018;96;15;26;;WULKE, WERNER:;;;44250,00
220245517728;09;78;00;;WUNDER, CHRISTEL:;;;22802,42
270442417721;09;29;00;;WUNDER, DIETER:;;;33750,00
221067417779;18;33;00;;WUNDER, DIRK:;;;9611,12
020470417743;09;69;00;;WUNDER, FRANK:;;;12442,50
300455422882;12;80;00;;WUNDER, HORST:;;;22712,50
101161519046;10;77;00;;WUNDER, PETRA:;;;14280,17
300156419018;10;51;00;;WUNDER, ROLAND:;;;22942,50
281065415328;08;51;00;;WUNDER, STEFFEN:;;;16042,50
020130419013;10;09;00;;WUNDER, WERNER:;;;33187,50
060270422210;12;69;00;;WUNDERLICH, ANDRE:;;;2849,35
160261430137;18;25;00;;WUNDERLICH, ANDRE:;;;18710,31
110151429789;94;65;00;;WUNDERLICH, BORIS:;;;21600,00
270257516621;98;85;00;;WUNDERLICH, BRIGITTE:;;;17833,79
210244422218;12;08;00;;WUNDERLICH, DIETER:;;;14547,50
080249428923;14;51;00;;WUNDERLICH, EBERHARD:;;;21937,50
010537428924;14;80;00;;WUNDERLICH, EBERHARD:;;;21625,00
110250422718;97;06;00;;WUNDERLICH, EDGAR:;;;24000,00
150558524987;12;00;55;;WUNDERLICH, ELKE:;;;2535,29
141246528271;14;80;00;;WUNDERLICH, EVA:;;;17460,00
280565415397;08;00;64;;WUNDERLICH, FRANK:;;;14652,00
300370427422;18;32;00;;WUNDERLICH, FRANK:;;;9510,00
111259407439;18;71;20;;WUNDERLICH, FRANK:;;;19430,00
070361424616;99;40;00;;WUNDERLICH, FRANK:;;;21615,00
030459407615;98;82;00;;WUNDERLICH, GERD:;;;22080,00
270648400028;01;06;24;;WUNDERLICH, GERD:;;;19687,50
221246422821;97;06;00;;WUNDERLICH, GERD:;;;24000,00
011243424914;13;20;00;;WUNDERLICH, GERHARD:;;;19875,00
151253420938;99;40;00;;WUNDERLICH, GUENTER:;;;24480,00
010145428925;14;00;54;;WUNDERLICH, HANSJOCHEN:;;;24000,00
240738406135;97;08;00;;WUNDERLICH, HANS-PETER:;;;24687,50
290743529725;99;77;00;;WUNDERLICH, HEIDI:;;;24750,00
140643429715;97;06;00;;WUNDERLICH, HEIKO:;;;27750,00
250435429750;99;99;99;::;WUNDERLICH, HEINZ;1165;HORTWINKELER WEG 29;
250435429750;99;99;99;::;WUNDERLICH, HEINZ;1165;HORTWINKELER WEG 29;
060757428921;98;83;00;;WUNDERLICH, HEINZ:;;;18630,00
220140528949;14;80;00;;WUNDERLICH, HELENE:;;;11040,36
091030430029;98;18;00;;WUNDERLICH, HELMAR:;;;44250,00
220954422035;99;43;00;;WUNDERLICH, INGOLF:;;;26640,00
240165503623;99;53;00;;WUNDERLICH, IRINA:;;;14778,59
111165430160;94;65;00;;WUNDERLICH, JAN:;;;15463,50
260549428915;14;06;00;;WUNDERLICH, JOACHIM:;;;22880,00
061255400026;99;43;00;;WUNDERLICH, JOACHIM:;;;21317,50
090256429923;15;80;00;;WUNDERLICH, JOERG:;;;17940,00
210546428244;14;80;00;;WUNDERLICH, JOERG:;;;19875,00
240161423845;30;61;00;;WUNDERLICH, JOERG:;;;16082,50
150456427764;30;49;00;;WUNDERLICH, JOHANNES:;;;13254,00
030237400880;01;06;00;;WUNDERLICH, JUERGEN:;;;27000,00
141237427436;14;06;00;;WUNDERLICH, KARL:;;;29250,00
190838430324;98;18;00;;WUNDERLICH, KARLHEINZ:;;;27240,00
120338406199;04;53;00;;WUNDERLICH, KARL-HEINZ:;;;27000,00
150264400831;99;51;00;;WUNDERLICH, KAY:;;;19965,00
260258524966;99;77;00;;WUNDERLICH, KERSTIN:;;;20700,00
290450428154;14;06;00;;WUNDERLICH, KLAUS:;;;23625,00
270833506115;04;02;00;;WUNDERLICH, MAGDALENA:;;;23250,00
160255429930;94;30;00;;WUNDERLICH, MANFRED:;;;21600,00
131240506179;04;20;00;;WUNDERLICH, MARGIT:;;;21375,00
300752426724;18;77;00;;WUNDERLICH, MARTIN:;;;31625,00
060669427419;18;28;00;;WUNDERLICH, MICHAEL:;;;6570,00
281148428933;99;51;00;;WUNDERLICH, RAIMUND:;;;25500,00
031269406165;18;35;00;;WUNDERLICH, RENGO:;;;2795,00
290746524938;13;80;00;;WUNDERLICH, ROSMARIE:;;;21000,00
100669400818;94;03;00;;WUNDERLICH, ROY:;;;14250,00
090338430071;99;49;00;;WUNDERLICH, SIEGFRIED:;;;37500,00
100253513616;95;45;00;;WUNDERLICH, SYLVIA:;;;20160,00
040170428238;96;15;14;;WUNDERLICH, TINO:;;;2700,00
100840530058;98;97;00;;WUNDERLICH, URSULA:;;;26250,00
060560428928;90;65;40;4037/79,;WUNDERLICH, UWE;1140;BRUNO-LEUSCHNER-STR. 25;
120350424015;99;43;00;;WUNDERLICH, VOLKER:;;;20360,00
260133427425;14;00;54;;WUNDERLICH, WALTER:;;;28500,00
160130528919;14;06;00;;WUNDERLICH, WANDA:;;;23250,00
201063412286;07;15;00;;WUNDERLING, ANDRE:;;;17950,00
240951411443;07;00;53;;WUNDERLING, CLAUS-DIETER:;;;23460,00
040348407910;06;00;48;;WUNDEROW, FRANK:;;;28375,00
190170407924;06;00;42;;WUNDEROW, JENS:;;;2700,00
150471407913;18;34;00;;WUNDEROW, TORSTEN:;;;2795,00
221062418625;10;06;00;;WUNDERWALD, DETLEF:;;;18535,00
291053407514;05;00;45;;WUNDKE, HARALD:;;;24420,00
280269422461;18;34;00;;WUNDRACK, DIRK:;;;12225,00
100447412223;07;18;00;;WUNDRICH, GERD:;;;25500,00
290738407520;05;40;00;;WUNGER, GERHARD:;;;25625,00
070163407524;05;80;00;;WUNGER, MICHAEL:;;;15922,50
190547407319;04;06;00;;WUNGLUECK, HARRY:;;;23250,00
310769404221;03;69;00;;WUNSCH, ANDREAS:;;;9617,26
161270407611;05;69;00;;WUNSCH, FRANK:;;;2870,00
040939429716;99;51;00;;WUNSCH, LOTHAR:;;;26250,00
010470413217;18;35;00;;WUNSCH, MARIO:;;;2795,00
200560409120;06;00;54;;WUNSCH, ROLAND:;;;6750,00
010253422862;12;18;00;;WUNSCH, WOLFGANG:;;;20625,00
280669406815;17;00;00;;WUNTKE, AXEL:;;;8300,00
030267406837;05;00;40;;WUNTKE, HEIKO:;;;11016,00
230762403226;03;00;49;;WURCH, ECKARD:;;;21725,00
020433411115;07;00;51;;WURCH, HANS-ARTUR:;;;18750,00
070141429722;97;07;00;;WURCH, INGO:;;;21937,50
250948413156;99;26;00;;WURCH, JOCHEN:;;;25500,00
240937530307;97;07;00;;WURCH, RENATE:;;;15840,00
191150518517;10;51;00;;WURZBACHER, ANGELIKA:;;;25242,58
020171418519;97;22;00;;WURZBACHER, DIRK:;;;2835,00
310750418519;10;00;47;;WURZBACHER, SIEGMAR:;;;29587,50
260535530281;15;80;00;;WURZEL, BRIGITTE:;;;17767,50
100339507241;97;06;00;;WURZEL, BRIGITTE:;;;21750,00
211066403114;03;55;00;;WURZEL, DIETMAR:;;;13932,00
280558430118;15;00;45;;WURZEL, JUERGEN:;;;24150,00
310168413712;08;00;00;;WURZEL, UWE:;;;11958,00
180170424813;99;43;00;;WURZIGER, RENE:;;;9600,00
030269413424;94;03;00;;WURZLER, MICHAEL:;;;9825,00
241152413420;17;00;00;;WURZLER, WOLF-RUEDIGER:;;;27660,00
230170426539;94;03;00;;WUSCHEK, RONNY:;;;9510,00
051051530030;99;40;00;;WUSCHKO, REGINE:;;;20821,93
270449421213;99;02;00;;WUSCHKO, STEFAN:;;;27437,50
110369408518;18;31;00;;WUSK, MAIK:;;;10500,00
140363413030;99;43;00;;WUSKE, HANS-PETER:;;;17820,00
270170421814;18;35;00;;WUSSOW, MAIK:;;;9060,00
260360514414;94;03;00;;WUST, DIANA:;;;17820,00
180658415128;94;03;00;;WUST, HANS-DIETER:;;;20585,00
140846412278;07;14;00;;WUSTERHAUS, BERND:;;;21390,00
131158409521;97;29;00;;WUSTMANN, GERD:;;;22110,00
290770407520;05;69;00;;WUSTMANN, RAIK:;;;2870,00
160362527026;14;96;00;;WUSTRACK, CARMEN:;;;0,00
200869417524;18;34;00;;WUTH, MATTHIAS:;;;6706,77
170144417557;09;00;51;;WUTH, WILFRIED:;;;28937,50
100567403428;97;22;00;;WUTSCHKE, ANDRE:;;;15552,00
110767413232;18;35;00;;WUTTIG, GERALD:;;;10725,00
130160405648;97;06;00;;WUTTIG, GUNTER:;;;24092,50
110670425421;99;49;00;;WUTTIG, HOLGER:;;;7969,52
280738425164;99;49;00;;WUTTIG, MANFRED:;;;31500,00
171167424922;17;00;00;;WUTTIG, ULF:;;;9872,00
051259422813;12;65;00;;WUTTKE, ANDREAS:;;;17882,50
110864430165;99;43;00;;WUTTKE, ANDREAS:;;;18150,00
281051402729;97;01;00;;WUTTKE, DIETMAR:;;;27360,00
110454413039;99;43;00;;WUTTKE, FRANK:;;;26640,00
021058406123;99;77;00;;WUTTKE, FRANK:;;;18179,28
251162503410;99;77;00;;WUTTKE, GERLIND:;;;17490,00
130632429729;99;43;00;;WUTTKE, GUENTER:;;;27000,00
030164408039;06;07;00;;WUTTKE, JENS:;;;19381,50
140166524014;98;19;00;;WUTTKE, KATRIN:;;;12947,41
301062430114;94;30;00;;WUTTKE, MICHAEL:;;;16610,00
140761508035;18;35;00;;WUTTKE, MONIKA:;;;15576,78
190768422811;12;69;00;;WUTTKE, RENE:;;;14100,00
070667430234;99;13;00;;WUTTKE, STEFAN:;;;16146,00
230262409576;99;43;00;;WUTTKE, STEPHAN:;;;20009,00
290862408539;06;02;00;;WUTTKE, TORSTEN:;;;16665,00
110339530053;30;83;00;;WUTTKE, URSULA:;;;2214,01
171068427511;94;03;00;;WUTZLER, ANDREAS:;;;10545,00
090269429252;18;32;00;;WUTZLER, BERT:;;;9675,00
200439430032;98;83;00;;WUTZLER, DIETMAR:;;;24750,00
021047420923;04;55;00;;WUTZLER, GUENTER:;;;21750,00
290150418325;94;30;00;;WUTZLER, KLAUS:;;;24660,00
050170426522;06;69;00;;WUTZLER, MARIO:;;;3253,87
291156527711;96;15;22;;WUTZLER, SILVIA:;;;17537,50
161039507417;30;31;00;;WYBIEREK, ANITA:;;;20880,00
040570409546;06;69;00;;WYDRA, THOMAS:;;;2870,00
020463405656;04;00;54;;WYLEZOL, RAOUL:;;;20075,00
090868505114;15;80;00;;WYLEZOL, UTE:;;;1137,10
160646427721;14;15;00;;WYREMBEK, BERND:;;;28500,00
291158411528;07;06;00;;WYREMBEK, RONALD:;;;17820,00
291160414234;08;00;65;;WYRWA, KLAUS-PETER:;;;15247,50
241057430273;15;08;00;;WYSTERSKI, JU(E)RGEN:;;;20700,00
241152529853;30;47;00;;WZIONTEK, GUDRUN:;;;14760,00
050346422753;12;06;00;;XII/1165/88, :;;;26250,00
160659522808;12;06;00;;XII/1334/89, :;;;17365,00
240434422742;12;02;00;;XII/1338/87, :;;;24750,00
290539422744;12;06;00;;XII/1339/87, :;;;33750,00
310836422834;12;07;00;;XII/1340/87, :;;;31500,00
130836422852;12;07;00;;XII/1341/87, :;;;36000,00
080344422810;12;07;00;;XII/1342/87, :;;;26250,00
080433422716;12;18;00;;XII/1344/87, :;;;25500,00
080537422737;12;18;00;;XII/1345/87, :;;;25500,00
130333421524;12;18;00;;XII/1346/87, :;;;25500,00
070830421523;12;18;00;;XII/1347/87, :;;;24480,00
060637422787;12;18;00;;XII/1348/87, :;;;29250,00
051034422847;12;20;00;;XII/1350/87, :;;;26437,50
190935422908;12;18;00;;XII/1352/87, :;;;27000,00
250439422716;12;00;58;;XII/1353/87, :;;;23287,50
100634418444;12;00;42;;XII/1354/87, :;;;28500,00
180736420556;12;00;42;;XII/1355/87, :;;;25958,34
190852420720;12;00;40;;XII/1357/87, :;;;25200,00
290637421032;12;00;40;;XII/1358/87, :;;;26250,00
250540421849;12;00;52;;XII/1359/87, :;;;21573,92
210541422804;12;06;00;;XII/1885/89, :;;;29250,00
240447429724;12;20;00;;XII/1895/89, :;;;32760,00
181243530188;12;19;00;;XII/2404/88, :;;;13006,44
050261410411;12;20;00;;XII/2405/88, :;;;19200,00
180237422223;12;00;47;;XII/2406/88, :;;;27000,00
030142422825;12;06;00;;XII/2655/87, :;;;23207,50
070428422712;12;06;00;;XII/2657/87, :;;;38250,00
231133522729;12;06;00;;XII/2658/87, :;;;21750,00
300328422767;12;07;00;;XII/2660/87, :;;;27000,00
270631422757;12;09;00;;XII/2663/87, :;;;29250,00
030132422792;12;18;00;;XII/2664/87, :;;;24000,00
260540422736;12;18;00;;XII/2665/87, :;;;24420,00
050549422753;12;19;00;;XII/2666/87, :;;;23017,50
080130422831;12;20;00;;XII/2667/87, :;;;27000,00
061050422846;12;00;41;;XII/2668/87, :;;;22320,00
250333422814;12;00;40;;XII/2669/87, :;;;29187,50
130341422746;12;00;40;;XII/2670/87, :;;;24000,00
070340422910;12;00;40;;XII/2671/87, :;;;28500,00
190244406415;12;00;53;;XII/2673/87, :;;;24750,00
210143422024;12;00;53;;XII/2674/87, :;;;21680,00
021052522043;12;19;00;;XII/2747/87, :;;;21045,00
200459422793;12;19;00;;XII/2748/87, :;;;19635,00
080854422802;12;19;00;;XII/2749/87, :;;;24945,00
071131414118;12;20;00;;XII/2750/87, :;;;31500,00
030635422110;12;29;00;;XII/2753/87, :;;;31500,00
260143422775;12;06;00;;XII/414/89, :;;;31437,50
091169403922;18;33;00;;ZA(E)DOW, HEIKO:;;;9600,00
251169430242;18;31;00;;ZA(E)NKER, RALPH:;;;6705,00
070452416232;94;30;00;;ZAAB, KARL:;;;20460,00
171256416211;18;35;00;;ZAAB, RUDI:;;;24092,50
041169411425;07;06;00;;ZAACKE, PETER:;;;8592,10
140559415134;94;03;00;;ZABEL, ANDREAS:;;;20642,50
141138530323;30;55;00;;ZABEL, ANITA:;;;18000,00
201155410130;99;99;99;::;ZABEL, DIETMAR;1058;OBERBERGER STR. 53;
201155410130;99;99;99;::;ZABEL, DIETMAR;1058;OBERBERGER STR. 53;
240352404612;98;82;00;;ZABEL, ECKHARD:;;;20880,00
211051429776;99;09;00;;ZABEL, GERD:;;;25200,00
281230430039;98;83;00;;ZABEL, GUENTER:;;;34229,17
190927430019;97;06;00;;ZABEL, GUENTER:;;;27750,00
090730415335;08;15;00;;ZABEL, HANS-JOACHIM:;;;32375,00
230450403411;03;80;00;;ZABEL, HANS-WERNER:;;;17365,00
250561430090;18;33;00;;ZABEL, HEINER:;;;20460,00
260339409927;04;06;00;;ZABEL, HORST:;;;21125,00
061137429725;94;65;00;;ZABEL, KARL:;;;24000,00
160745423929;13;00;44;;ZABEL, KARL-HEINZ:;;;24007,50
051068423928;99;49;00;;ZABEL, KARSTEN:;;;10575,00
290558500410;01;06;20;;ZABEL, LIANE:;;;16238,00
311243429744;98;80;00;;ZABEL, LOTHAR:;;;26937,50
151238429715;30;77;00;;ZABEL, MANFRED:;;;17250,00
030555429865;98;97;00;;ZABEL, MARIO:;;;24745,16
060767423913;11;96;63;;ZABEL, MARIO:;;;14460,00
200471405013;18;40;00;;ZABEL, MATTHIAS:;;;2720,00
310151429769;98;84;00;;ZABEL, MICHAEL:;;;27010,00
150570412523;07;06;00;;ZABEL, MICHAEL:;;;12460,00
061263430188;18;35;00;;ZABEL, MIRKO:;;;19745,00
280344424425;13;80;00;;ZABEL, RALF:;;;26187,50
010261415355;97;22;00;;ZABEL, SVEN:;;;20765,00
161169430155;18;35;00;;ZABEL, TINO:;;;2795,00
261067430187;97;22;00;;ZABEL, TORSTEN:;;;14969,00
140168417722;18;00;50;;ZABEL, TORSTEN:;;;10425,00
240631403428;03;09;00;;ZABEL, WERNER:;;;36562,50
230157403025;01;06;20;;ZABEL, WINFRIED:;;;17940,00
131258512219;99;77;00;;ZACH, BARBARA:;;;16930,97
110655406142;94;64;00;;ZACH, HELMUT:;;;25210,00
011156406128;04;08;00;;ZACH, MICHAEL:;;;18975,00
011134506187;17;00;00;;ZACHARIAS, ERIKA:;;;19440,00
160335512910;08;12;00;;ZACHARIAS, ILSE:;;;20160,00
030234412915;08;60;00;;ZACHARIAS, KURT:;;;33750,00
010355412913;08;51;00;;ZACHARIAS, PETER:;;;21600,00
060766410838;07;06;00;;ZACHARIAS, RALF:;;;16832,32
240965410134;18;40;00;;ZACHARIAS, SVEN:;;;19102,00
080135415403;09;00;46;;ZACHARIAS, VOLKHARD:;;;24750,00
110852429829;30;47;00;;ZACHARIAS, WOLFGANG:;;;23192,50
240151422048;97;08;00;;ZACHE, STEFFEN:;;;22260,00
220253422091;99;43;00;;ZACHE, WERNER:;;;22980,00
060551416730;99;43;00;;ZACHER, FRIEDRICH:;;;22552,50
251259405315;07;06;00;;ZACHER, GERD:;;;22770,00
101152429735;15;12;00;;ZACHER, MANFRED:;;;21600,00
010554529786;99;43;00;;ZACHER, MARINA:;;;19445,00
270260510810;07;00;49;;ZACHER, PETRA:;;;5179,50
010454503730;15;11;00;;ZACHER, RITA:;;;19074,19
010548411714;07;40;00;;ZACHERT, BURKHARD:;;;27360,00
310171423815;18;35;00;;ZACHMANN, RONNY:;;;2795,00
130470422419;18;31;00;;ZACHMANN, VOLKER:;;;6570,00
191169409521;18;32;00;;ZACHOW, ADRIAN:;;;9510,00
250948404612;04;00;43;;ZACHOW, HANS-JUERGEN:;;;28687,50
280762404320;03;00;52;;ZACHOW, HELGO:;;;12884,00
250261403437;98;85;00;;ZACHOW, RAINER:;;;16963,62
300662515336;98;83;00;;ZACHOW, SABINE:;;;14653,61
060838403427;03;08;00;;ZACHOW, WERNER:;;;23000,00
280852412279;07;08;00;;ZACK, FRANK-DETLEF:;;;16991,25
310544414111;08;07;00;;ZACK, JUERGEN:;;;24750,00
201161416432;09;02;00;;ZACK, REINER:;;;22055,00
220256421211;18;35;00;;ZACKE, ECKARD:;;;21160,00
250152429881;15;40;00;;ZACKE, ROLF:;;;23220,00
280869413112;18;27;30;;ZACKER, VOLKMAR:;;;9510,00
301064412251;99;43;00;;ZADE, FRANK:;;;16170,00
260957427516;99;02;00;;ZAEBISCH, ANDREAS:;;;23460,00
310550416711;09;06;00;;ZAECKE, KLAUS-INGO:;;;21960,00
060461410116;94;03;00;;ZAEHLE, THOMAS:;;;18810,00
110769407020;97;06;00;;ZAEHLER, THOMAS:;;;13500,00
180544530240;99;77;00;;ZAEHR, KARIN:;;;22385,00
100965430077;97;22;00;;ZAEHR, THOMAS:;;;13979,81
180942429738;98;18;00;;ZAEHR, WOLFGANG:;;;27000,00
221250428935;96;15;04;;ZAENGRY, JUERGEN:;;;21600,00
221250428927;14;06;00;;ZAENGRY, KLAUS:;;;25200,00
270656512222;96;15;13;;ZAENGRY, PETRA:;;;17659,92
280438530050;94;30;00;;ZAENKER, HELGA:;;;23250,00
030766430030;98;82;00;;ZAENKER, JAN:;;;15984,00
200661417787;09;02;00;;ZAENKER, JUERGEN:;;;17490,00
230360427620;18;31;00;;ZAENKER, MATTHIAS:;;;23460,00
110840430056;94;30;00;;ZAENKER, PETER:;;;26750,00
131234529710;99;77;00;;ZAENKER, RENATE:;;;22500,00
261133429716;98;82;00;;ZAENKER, WOLFGANG:;;;35250,00
200453529274;14;00;61;;ZAENSLER, BRUNHILDE:;;;7741,67
110467406911;15;00;40;;ZAETZSCH, STEFFEN:;;;11016,00
251256406937;99;43;00;;ZAETZSCH, WOLF-GUNTER:;;;22770,00
030468430171;97;06;00;;ZAGACKI, TIMO:;;;16650,00
120457416234;97;01;00;;ZAGER, JUERGEN:;;;25100,04
190269403712;18;33;00;;ZAGLER, ULRICH:;;;7758,87
070170400419;18;32;00;;ZAHARZEWSKI, JO(E)RG:;;;9330,00
190356418517;10;00;45;;ZAHL, DIETMAR:;;;22770,00
130960418519;98;85;00;;ZAHL, FRANK:;;;18022,50
220171416958;18;35;00;;ZAHM, MICHAEL:;;;2795,00
250369411113;18;40;00;;ZAHMEL, MARIO:;;;10500,00
020761406710;99;41;00;;ZAHN, BERND:;;;17737,50
210370422024;98;83;00;;ZAHN, GERALD:;;;10035,00
180362408922;06;08;00;;ZAHN, GERD:;;;12600,00
250147423610;13;08;00;;ZAHN, GUENTER:;;;22320,00
250559430112;98;82;00;;ZAHN, GUNNAR:;;;18285,00
190539506712;98;83;00;;ZAHN, HILDEGARD:;;;17344,59
270339406741;98;82;00;;ZAHN, JOACHIM:;;;27750,00
110369406141;18;33;00;;ZAHN, MARIO:;;;9600,00
230567405728;04;00;52;;ZAHN, OLAF:;;;14742,00
200159416463;94;30;00;;ZAHN, REINHOLD:;;;20983,67
160449427538;14;06;00;;ZAHN, STEFAN:;;;22140,00
140969428018;99;43;00;;ZAHN, THOMAS:;;;9600,00
120169410145;18;33;00;;ZAHN, TORSTEN:;;;9510,00
300451415335;08;09;00;;ZAHN, ULRICH:;;;26656,01
060536405662;04;00;50;;ZAHNKE, HELMUT:;;;23250,00
280666503820;98;20;00;;ZAHNOW, KORNELIA:;;;14628,00
061154409523;06;18;00;;ZAHR, JUERGEN:;;;23460,00
011057427513;94;65;00;;ZAHRADNIK, JUERGEN:;;;19112,26
190768427719;18;31;00;;ZAJIC, UWE:;;;9825,00
300768422891;18;35;00;;ZAJONZ, FALK:;;;9875,00
230651429802;15;09;00;;ZAKONSKY, KLAUS-PETER:;;;26640,00
130939430337;98;82;00;;ZAKRZEWSKI, GERHARD:;;;21000,00
051264405217;30;62;00;;ZALACHOWSKI, INGO:;;;13619,00
130245424426;13;00;48;;ZALESKY, STEFFEN:;;;20625,00
210869424424;13;69;00;;ZALESKY, UWE:;;;9420,00
150945430032;99;53;00;;ZALEWSKI, OTTOMAR:;;;21750,00
090857403411;03;26;00;;ZAMPICH, BURGHARD:;;;21332,50
091062400510;04;30;00;;ZAMZOW, HARTMUT:;;;17930,00
260253417117;97;06;00;;ZAMZOW, KLAUS-DIETER:;;;26100,00
271136400520;01;00;44;;ZAMZOW, ULRICH:;;;22500,00
090663406147;04;09;00;;ZANDER, AXEL:;;;11220,00
231067514826;08;09;00;;ZANDER, BIRGIT:;;;13721,00
040448526212;04;80;00;;ZANDER, CHRISTA:;;;17647,50
220351407530;05;08;00;;ZANDER, DETLEF:;;;24120,00
090559413451;99;43;00;;ZANDER, DIETER:;;;22080,00
020751429767;30;47;00;;ZANDER, DIETRICH:;;;23640,00
230468430266;99;40;00;;ZANDER, DIRK:;;;10355,00
150940506114;17;00;00;;ZANDER, EDDA:;;;23250,00
010565413017;04;06;00;;ZANDER, ERIK:;;;15348,00
281170413033;18;31;00;;ZANDER, FRANK:;;;2795,00
140561413031;94;03;00;;ZANDER, FRANK:;;;19825,00
290670412111;07;69;00;;ZANDER, GERD:;;;2911,13
110140429724;99;43;00;;ZANDER, GERD:;;;21750,00
120234406143;04;51;00;;ZANDER, HANS-JOACHIM:;;;22875,00
030944412215;07;00;40;;ZANDER, HANS-ULRICH:;;;24480,00
151162505311;06;00;45;;ZANDER, HEIKE:;;;5912,50
151248402532;94;03;00;;ZANDER, HEINZ-DIETER:;;;21500,00
030469418318;10;69;00;;ZANDER, HENRY:;;;10155,00
110469400118;18;34;00;;ZANDER, HOLGER:;;;9600,00
240569400612;01;69;00;;ZANDER, INGO:;;;12575,00
281255415118;09;20;00;;ZANDER, JOCHEN:;;;22275,00
240638429727;94;11;00;;ZANDER, MANFRED:;;;22687,50
090570400221;18;77;00;;ZANDER, MARIO:;;;6780,00
230753530063;99;78;00;;ZANDER, MARION:;;;17160,00
201159419634;11;08;00;;ZANDER, MICHAEL:;;;18112,50
021155405114;30;54;00;;ZANDER, NORBERT:;;;21162,50
280942413144;97;06;00;;ZANDER, PETER:;;;20880,00
030660408812;06;08;00;;ZANDER, RALF:;;;15565,00
060757403214;02;06;00;;ZANDER, RALF:;;;19262,50
091261404610;99;43;00;;ZANDER, RALF:;;;18480,00
110541412210;07;03;00;;ZANDER, ROLF:;;;22500,00
230230430012;98;80;00;;ZANDER, RUDI:;;;35250,00
030640429712;99;43;00;;ZANDER, RUEDIGER:;;;24750,00
201036518413;10;00;46;;ZANDER, RUTH:;;;17245,97
131070427514;99;43;00;;ZANDER, SILVIO:;;;6780,00
161269425046;18;35;00;;ZANDER, STEFFEN:;;;9510,00
060667413427;99;02;00;;ZANDER, THOMAS:;;;11016,00
060269425094;95;45;00;;ZANDER, THOMAS:;;;14175,00
190165413617;08;69;00;;ZANDER, TINO:;;;17496,00
300858402528;02;51;00;;ZANDER, ULRICH:;;;18227,50
040828430036;98;83;00;;ZANDER, WALTER:;;;21000,00
070238406199;04;00;40;;ZANDER, WERNER:;;;29250,00
041159406112;99;43;00;;ZANDER, WOLFGANG:;;;17023,30
290835424947;30;47;00;;ZANG, JUERGEN:;;;28800,00
020949419724;11;06;21;;ZANG, KLAUS:;;;19440,00
180664419010;10;07;00;;ZANGE, PETER:;;;19653,00
141169420530;18;31;00;;ZANGE, RENE:;;;9600,00
090768420551;18;35;00;;ZANGE, TORSTEN:;;;9067,26
291159414827;08;00;59;;ZANGER, STEFFEN:;;;17660,00
230353428297;94;11;00;;ZANGOLIES, WOLFGANG:;;;20010,00
240536429726;17;00;00;;ZANK, HORST:;;;39750,00
050542529718;17;00;00;;ZANK, RITA:;;;22861,61
120233429730;97;06;00;;ZANTER, GERHARD:;;;21500,00
040335404518;04;00;41;;ZANTKE, ERNST:;;;31500,00
121148529272;99;40;00;;ZAPEL, GABRIELE:;;;19977,12
251050400927;18;41;30;;ZAPEL, KARL-HEINZ:;;;27645,00
191268412291;18;38;00;;ZAPF, GORDON:;;;9675,00
120648405714;04;53;00;;ZAPF, HARRY:;;;24420,00
260758507521;05;78;00;;ZAPF, KARIN:;;;18579,92
140246401516;02;00;46;;ZAPF, PETER:;;;29520,00
190161428969;14;06;00;;ZAPF, UWE:;;;17365,00
191267417752;09;15;00;;ZAPFE, HOLGER:;;;12672,00
011067415399;90;65;40;953/87, :;ZAPKE, HELGE-JENS;1156;FRANZ-JACOB-STR. 1;15239,00
270443410310;06;06;00;;ZAPKE, ROLAND:;;;23640,00
030452508536;30;83;00;;ZAPPE, KARIN:;;;13858,02
270137417821;09;53;00;;ZAPPE, REINHOLD:;;;33750,00
171168406718;05;69;00;;ZARECKY, ANDRE:;;;9675,00
030270405210;18;32;00;;ZAREMBA, MIKE:;;;9510,00
180468406431;18;35;00;;ZARETZKE, HOLGER:;;;9600,00
261056405824;30;40;00;;ZARGES, DIETER:;;;14490,00
120841429718;97;06;00;;ZARGUS, KLAUS-PETER:;;;27943,55
150562500902;01;08;00;;ZARMSDORF, MARIANNE:;;;16865,75
281057400812;01;08;00;;ZARMSDORF, NORBERT:;;;19435,00
081069402763;02;80;00;;ZARNCKE, RENE:;;;7620,00
280468426916;97;22;00;;ZARSCHLER, STEFFEN:;;;14994,00
060571426936;18;34;00;;ZARSCHLER, THOMAS:;;;2795,00
060157413179;08;00;43;;ZARSKI, ERHARD:;;;21780,00
061045416724;09;06;00;;ZART, GEORG:;;;20340,00
301060500617;01;96;43;;ZARTL, SABINE:;;;15745,00
110571409215;06;00;53;;ZARUBA, RENE:;;;3253,87
140733406146;04;40;00;;ZARWEL, GERD:;;;23937,50
270370425473;18;33;00;;ZASCHKE, KARSTEN:;;;2795,00
210343414256;99;02;00;;ZASCHKE, REINER:;;;32125,00
250865422014;94;65;00;;ZASTRAU, HEIKO:;;;11016,00
290738422026;96;15;02;;ZASTRAU, HORST:;;;27750,00
190970403219;94;65;00;;ZASTROW, GUNNAR:;;;2870,00
141150401321;01;06;24;;ZASTROW, HERBERT:;;;19620,00
070935530072;30;79;00;;ZASTROW, ROSEMARIE:;;;15120,00
020737430032;99;51;00;;ZASTROW, SIEGFRIED:;;;23250,00
290644417322;09;00;49;;ZASWORKA, WALTER:;;;27000,00
090858430059;30;47;00;;ZAUBER, LUTZ:;;;21507,00
030967405026;99;43;00;;ZAUFT, RALF:;;;9675,00
030461427519;14;06;00;;ZAUMSEIL, FRANK:;;;18645,00
310348408910;97;22;00;;ZAUMSEIL, GERD:;;;25530,00
270948419011;10;00;43;;ZAUMSEIL, GERT:;;;26250,00
230857408919;99;55;00;;ZAUMSEIL, HARALD:;;;20872,50
030566403214;18;96;00;;ZAWADZINSKI, THOMAS:;;;15795,00
310359416238;98;82;00;;ZAWALSKI, KLAUS-PETER:;;;19320,00
200363418829;10;00;50;;ZAWORKA, STEFFEN:;;;19140,00
121053400644;94;65;00;;ZBLEWSKI, DETLEF:;;;20160,00
050142400915;01;09;00;;ZBLEWSKI, EGON:;;;25437,50
050266400917;15;00;43;;ZBLEWSKI, JAN:;;;18682,50
020642429717;99;43;00;;ZDUNEK, GERD:;;;24000,00
030859430021;97;01;00;;ZEBISCH, VOLKER:;;;24723,31
071152500613;17;00;00;;ZECH, ANNELORE:;;;20160,00
090457510840;99;77;00;;ZECH, FRAUKE:;;;19001,60
091141530049;30;31;00;;ZECH, HANNA:;;;16560,00
210360406434;97;08;00;;ZECH, HARTMUT:;;;15943,80
040569426314;18;32;00;;ZECH, HOLGER:;;;9675,00
120850406155;17;00;00;;ZECH, HOLGER:;;;20160,00
160751407538;96;15;00;4598/87, F:;ZECH, JU(E)RGEN;1055;LENINALLEE 127;
160751407538;96;15;00;4598/87, F:;ZECH, JU(E)RGEN;1055;LENINALLEE 127;
060969415401;08;69;00;;ZECH, MATTHIAS:;;;9600,00
301069409596;06;69;00;;ZECH, MATTHIAS:;;;9600,00
090167400889;18;33;00;;ZECH, MATTHIAS:;;;10291,13
040160424954;94;03;00;;ZECH, MATTHIAS:;;;19722,50
271260426314;18;28;00;;ZECH, PETER:;;;18932,50
091055400846;94;65;00;;ZECH, RALF:;;;18802,50
070663418916;10;51;00;;ZECH, STEFFEN:;;;17429,68
140230422232;12;80;00;;ZECHEL, INGOLF:;;;9661,93
181070406110;18;34;00;;ZECHLIN, TORSTEN:;;;2795,00
061257412223;94;03;00;;ZEDLER, DIRK:;;;22942,50
010953409917;30;76;00;;ZEDLER, GERALD:;;;23115,00
231133500810;01;80;00;;ZEDLER, INGE:;;;20937,50
130371415723;18;35;00;;ZEDLER, JENS:;;;2795,00
301159424714;99;14;00;;ZEDLER, MATTHIAS:;;;19400,00
030959402220;02;20;00;;ZEECK, GERD-MICHAEL:;;;24150,00
300867409529;06;06;00;;ZEFFLER, OLAF:;;;13175,00
200958408443;99;13;00;;ZEGELIN, CHRISTIAN:;;;23460,00
030935429736;99;43;00;;ZEGGEL, WALTER:;;;28500,00
140653408926;94;30;00;;ZEH, DIETMAR:;;;20640,00
280960418619;10;18;00;;ZEH, EDGAR:;;;20692,50
241254402562;02;07;00;;ZEH, HANS-JOACHIM:;;;24140,00
150348428911;99;40;00;;ZEH, HELMUT:;;;26640,00
220350528912;96;15;21;;ZEH, INGRID:;;;20625,00
020958519612;11;96;61;;ZEH, MARGIT:;;;14203,21
180269413233;18;29;30;;ZEH, MICHAEL:;;;8350,00
120834418615;10;00;45;;ZEH, SIEGFRIED:;;;36000,00
070454529724;94;30;00;;ZEH, URSEL:;;;18148,07
250270405733;18;32;00;;ZEHE, LARS:;;;6570,00
241267405359;18;32;00;;ZEHE, TORSTEN:;;;9675,00
161070425460;18;32;00;;ZEHL, AXEL:;;;2795,00
070138400937;01;06;00;553/75, :;ZEHL, KLAUS;2510;BEETHOVENSTR. 38;
070138400937;01;06;00;553/75, :;ZEHL, KLAUS;2510;BEETHOVENSTR. 38;
020369405318;04;69;00;;ZEHLE, MARIO:;;;9675,00
010651401717;17;00;00;;ZEHM, PETER:;;;26580,00
190235529712;96;15;17;;ZEHM, WALTRAUD:;;;24750,00
160633429728;96;15;12;;ZEHM, WERNER:;;;35250,00
290169424960;13;69;00;;ZEHMISCH, TOM:;;;9555,00
031269419716;08;69;00;;ZEHNEL, MARCO:;;;9555,00
090461424718;18;33;00;;ZEHRFELD, DIETMAR:;;;22865,00
160869424819;99;43;00;;ZEHRFELD, KAI:;;;9510,00
270866424415;13;00;48;;ZEHRFELD, RENE:;;;15228,00
160354518517;10;06;00;;ZEHRMANN, GABRIELE:;;;9435,00
090938429744;97;06;00;;ZEHRTNER, HORST:;;;25500,00
020767430260;18;35;00;;ZEHRTNER, MIRKO:;;;9825,00
150958422111;30;59;00;;ZEIBIG, BERND:;;;14520,00
071154422137;12;80;00;;ZEIBIG, DIETER:;;;15592,50
311250529751;97;08;00;;ZEIBIG, EDELTRAUT:;;;21170,00
050243429741;97;08;00;;ZEIBIG, GOTTFRIED:;;;24750,00
070850511446;30;61;00;;ZEIBIG, INGE:;;;14962,50
270467421014;97;08;00;;ZEIBIG, KARSTEN:;;;16470,00
180363413627;99;02;00;;ZEIDLER, ANDREAS:;;;20295,00
221237413616;08;00;48;;ZEIDLER, DIETER:;;;27000,00
010252427418;60;90;00;;ZEIDLER, DIETMAR:;;;
180849429768;15;08;00;;ZEIDLER, ECKHARD:;;;26250,00
071258419020;99;55;00;;ZEIDLER, FRANK:;;;20192,09
151258408970;06;00;51;;ZEIDLER, GERD:;;;16215,00
220827430016;97;07;00;;ZEIDLER, GERHARD:;;;18951,61
281255415396;08;96;00;;ZEIDLER, HARTMUT:;;;22720,00
140256509213;30;51;00;;ZEIDLER, HEIDEMARIE:;;;12210,00
140570428032;18;35;00;;ZEIDLER, HEIKO:;;;9510,00
050371421111;18;35;00;;ZEIDLER, HEIKO:;;;2795,00
060769424960;18;31;00;;ZEIDLER, JENS:;;;9510,00
141256515319;13;78;00;;ZEIDLER, MARTINA:;;;27600,00
100953403434;03;00;42;;ZEIDLER, MICHAEL:;;;28290,00
300866507311;01;14;00;;ZEIDLER, REGINA:;;;3899,93
160660515349;13;26;00;;ZEIDLER, SIGRID:;;;17765,00
301169407926;18;31;00;;ZEIDLER, UDO:;;;9600,00
070169424229;94;03;00;;ZEIDLER, UWE:;;;14250,00
020749521548;12;00;50;;ZEIGER, INGEBURG:;;;14204,50
021244430207;96;15;15;;ZEIGERT, DIERK:;;;30750,00
220567506116;17;00;00;;ZEIHN, ANETT:;;;13775,96
190652421227;98;18;00;;ZEILER, ANDREAS:;;;20160,00
300853522790;94;30;00;;ZEILER, INGRID:;;;19140,26
110241412219;07;11;00;;ZEILER, WERNER:;;;31500,00
281269424322;18;31;00;;ZEIN, ANDRE:;;;9600,00
241168412262;17;00;00;;ZEIN, HENDRIK:;;;8950,00
030646412268;99;49;00;;ZEIN, WOLFGANG:;;;30750,00
140367416933;99;43;00;;ZEINERT, HEIKO:;;;15390,00
190457422734;97;01;00;;ZEINERT, HOLGER:;;;26220,00
051244407223;18;99;00;;ZEININGER, KLAUS-DIETER:;;;38362,50
300667507255;99;77;00;;ZEININGER, PATRICIA:;;;9000,00
241053402339;60;90;00;;ZEIPELT, ULRICH:;;;
241053402339;60;90;00;;ZEIPELT, ULRICH:;;;19432,90
290364403225;18;27;30;;ZEISBERG, FRANK:;;;20559,00
210344429724;98;84;00;;ZEISBERG, JOACHIM:;;;22500,00
190152404527;12;00;53;;ZEISBERG, WOLFGANG:;;;28347,50
110450427521;14;00;55;;ZEISBRICH, PETER:;;;24150,00
260848526339;15;09;00;;ZEISE, BRIGITTE:;;;23700,00
270462513227;08;40;00;;ZEISE, CHRISTINE:;;;15222,84
231270418522;18;29;30;;ZEISE, FRANK:;;;3070,16
220263506205;97;06;00;;ZEISE, HEIKE:;;;2062,50
300966430040;99;78;00;;ZEISE, HENDRIK:;;;14969,00
190256415327;97;06;00;;ZEISE, INGOLF:;;;21620,00
250144429734;99;09;00;;ZEISE, JOERG:;;;27750,00
250754425060;17;00;00;;ZEISE, MATTHIAS:;;;20160,00
210470411824;18;32;00;;ZEISE, RALF:;;;9510,00
260432424910;13;80;00;;ZEISE, ROLF:;;;25500,00
120463415369;30;31;00;;ZEISE, THOMAS:;;;2695,00
260757415449;08;40;00;;ZEISE, UDO:;;;22770,00
190361430019;15;09;00;;ZEISEWEIS, BERND:;;;21285,00
190867430198;96;15;21;;ZEISEWEIS, JOERG:;;;8950,00
020537429723;99;53;00;;ZEISEWEIS, KURT:;;;42562,50
111162430026;15;20;00;3299/88, :;ZEISEWEIS, RALF;1140;HEINRICH-RAU-STR. 390;
111162430026;15;20;00;3299/88, :;ZEISEWEIS, RALF;1140;HEINRICH-RAU-STR. 390;
051250429795;05;41;00;;ZEISING, BERND:;;;29980,00
160861406130;17;00;00;;ZEISING, BERT:;;;17113,87
070852507627;05;60;00;;ZEISING, EVA:;;;19012,45
061039505915;99;77;00;;ZEISING, HANNELORE:;;;21600,00
170153430032;96;15;18;;ZEISING, HARALD:;;;26640,00
220357413413;08;96;00;;ZEISING, LUTZ:;;;17595,00
090157507228;94;65;00;;ZEISING, MARINA:;;;18329,52
220454513416;08;06;00;;ZEISING, MARITTA:;;;20880,00
311265518510;10;51;00;;ZEISING, MARLEN:;;;12252,60
131253425079;97;06;00;;ZEISING, MICHAEL:;;;23760,00
150555422803;99;02;00;;ZEISING, NORBERT:;;;27242,50
200141429725;98;85;00;;ZEISING, RAINER:;;;22500,00
260929430013;98;20;00;;ZEISING, RALF:;;;30000,00
130265511236;17;00;00;;ZEISING, SUSANNE:;;;13764,75
170149413416;08;29;00;;ZEISING, VOLKER:;;;28500,00
160664408938;18;32;00;;ZEISKE, ANDREAS:;;;20625,00
230541529722;96;15;27;;ZEISKE, GISELA:;;;23250,00
180670421344;98;27;00;;ZEISKE, JOERG:;;;3620,00
050453408930;18;33;00;;ZEISKE, JUERGEN:;;;25200,00
270567528281;18;33;00;;ZEISKE, KATRIN:;;;16800,00
270761430042;96;15;00;2614/84, F:;ZEISKE, TINO;1143;BERNBURGER STR. 12;
270761430042;96;15;00;2614/84, F:;ZEISKE, TINO;1143;BERNBURGER STR. 12;
280639500616;01;00;49;;ZEISLER, CHRISTINE:;;;22500,00
040750407417;05;15;00;;ZEISLER, FRANK:;;;27260,00
111143429716;97;08;00;;ZEISLER, HORST:;;;25500,00
020353401734;05;26;00;;ZEISLER, KLAUS-DIETER:;;;22770,00
140967430245;18;35;00;;ZEISLER, MARKUS:;;;9825,00
301160400613;99;43;00;;ZEISLER, MICHAEL:;;;19430,00
050859400613;99;43;00;;ZEISLER, VOLKER:;;;19377,50
120840429740;99;14;00;;ZEISZ, KLAUS:;;;33000,00
210739419010;60;90;00;;ZEISZ, MANFRED:;;;
210739419010;60;90;00;;ZEISZ, MANFRED:;;;25200,00
030664430216;95;45;00;;ZEISZ, THOMAS:;;;16940,00
300553423643;96;15;27;;ZEISZIG, KLAUS:;;;20880,00
040451427928;14;08;00;;ZEISZIG, WOLFGANG:;;;22707,50
090262409523;06;00;53;;ZEISZLER, JUERGEN:;;;20625,00
120567408411;17;00;00;;ZEISZLER, RALF:;;;13670,00
181167409246;99;43;00;;ZEITLER, ANDREAS:;;;9675,00
160841430264;30;84;00;;ZEITLER, GUENTER:;;;21600,00
231246416017;09;14;00;;ZEITSCH, WOLFGANG:;;;25500,00
060657419315;18;71;20;;ZEITSCHEL, MATTHIAS:;;;22022,50
060948424990;13;20;00;;ZEITSCHEL, WOLFGANG:;;;30250,00
260870407627;18;80;00;;ZEITZ, MARIO:;;;6780,00
291166430112;98;84;00;;ZEKALLE, TORSTEN:;;;15822,00
181169413038;94;03;00;;ZELAZO, MARCO:;;;9510,00
280246400411;01;06;20;;ZELCK, FRIEDRICH-WILHE:;;;24000,00
200868500414;01;80;00;;ZELCK, MANUELA:;;;12675,00
020770400417;01;69;00;;ZELCK, TORSTEN:;;;2896,61
050340405610;18;27;30;;ZELDER, WERNER:;;;20886,25
270564407468;99;78;00;;ZELL, CHRIS:;;;17490,00
170168403619;03;20;00;;ZELL, HOLGER:;;;5375,00
130343507428;18;71;20;;ZELL, INGE:;;;18285,00
120563407411;96;15;22;;ZELL, UTZ:;;;16500,00
180444530067;30;47;00;;ZELLER, BRIGITTE:;;;26280,00
030939430216;30;31;00;;ZELLER, PETER:;;;26130,00
280637422829;98;82;00;;ZELLER, SIEGFRIED:;;;27000,00
020563410815;97;01;00;;ZELLHORN, DIRK:;;;23760,00
020363420138;99;12;00;;ZELLMANN, FRANK:;;;17600,00
180236420111;11;00;46;;ZELLMANN, GUENTER:;;;29250,00
041255429832;90;65;40;3620/77,;ZELLMER, BERND;1136;CHARLOTTENSTR. 10;
160440403425;03;80;00;;ZELLMER, GUENTER:;;;20550,80
130171403728;18;33;00;;ZELLMER, TORSTEN:;;;2795,00
160757503619;30;47;00;;ZELLMER, VIOLA:;;;15942,50
250242506158;17;00;00;;ZELLNER, ILSE-DORE:;;;20625,00
090135406186;17;00;00;;ZELLNER, PETER:;;;20625,00
110961402537;02;69;00;;ZELM, HOLGER:;;;18370,00
110870424028;98;19;00;;ZELSMANN, JAN:;;;2700,00
260869418118;10;69;00;;ZELSMANN, MIKE:;;;2870,00
090849419034;10;20;00;;ZELT, UWE:;;;33000,00
210861422803;12;00;48;;ZEMANN, UWE:;;;20460,00
080563404612;30;56;00;;ZEMELLA, THOMAS:;;;14190,00
270357530025;98;83;00;;ZEMKE, GUDRUN:;;;18379,60
031154417120;97;01;00;;ZEMKE, HANS-GERHARD:;;;26640,00
081070424222;18;32;00;;ZEMLA, JENS:;;;2795,00
181154520228;99;77;00;;ZEMMIN, MARTINA:;;;20010,00
210869430082;18;32;00;;ZEMMRICH, ANDREAS:;;;9510,00
151248530067;30;83;00;;ZEMMRICH, LORE:;;;17820,00
030863430235;17;00;00;;ZEMMRICH, VOLKER:;;;15510,00
080337424412;13;00;48;;ZEMMRICH, WOLFGANG:;;;27000,00
080148402126;02;00;41;;ZENGEL, ERWIN:;;;25500,00
290457405529;04;06;00;;ZENGEL, FRANK:;;;19435,00
070658405512;18;28;00;;ZENGEL, JOERG:;;;23460,00
100238412219;07;19;00;;ZENGERLING, ALFRED:;;;38250,00
140350428938;97;01;00;;ZENGERLING, HELMUT:;;;33000,00
300658412262;07;08;00;;ZENGERLING, HILMAR:;;;18572,50
260570426519;18;28;00;;ZENGERLING, RENE:;;;10514,84
211161412246;07;09;00;;ZENGERLING, RONALD:;;;20185,00
100468425015;18;32;00;;ZENK, RAINER:;;;10725,00
100968412253;07;55;00;;ZENKE, DIRK:;;;12406,46
160467405236;04;80;00;;ZENKE, FERNANDO:;;;11158,00
191069424994;05;69;00;;ZENKE, KAI-UWE:;;;3220,00
250342405223;04;60;00;;ZENKE, ULRICH:;;;31437,50
300453429888;30;80;00;;ZENKER, ALEXEY:;;;23460,00
010965427223;14;30;00;;ZENKER, ANDRE:;;;14094,00
241051427321;14;00;52;;ZENKER, ANDREAS:;;;14795,00
071256430154;15;08;00;;ZENKER, ANDREAS:;;;20700,00
210264425029;13;03;00;;ZENKER, BRANKO:;;;17160,00
240651424015;12;19;00;;ZENKER, EBERHARD:;;;26562,00
301250422891;12;30;00;;ZENKER, FRANK:;;;23040,00
210367409523;94;30;00;;ZENKER, HEIKO:;;;16146,00
280940417555;97;08;00;;ZENKER, HELMUT:;;;28500,00
040841427229;14;00;50;;ZENKER, JUERGEN:;;;22320,00
070356518415;15;06;00;;ZENKER, KARIN:;;;19952,50
020253422845;12;19;00;;ZENKER, KARL-HEINZ:;;;21600,00
221144424930;30;32;00;;ZENKER, LOTHAR:;;;21390,00
311254522792;12;00;53;;ZENKER, UTE:;;;16355,88
130451418422;15;15;00;;ZENKER, WOLFGANG:;;;28260,00
260251423628;99;14;00;;ZENNER, JOACHIM:;;;22320,00
160355403420;99;02;00;;ZENT, DIETMAR:;;;22267,50
070742419829;11;08;00;;ZENTGRAF, EGON:;;;26250,00
300133403013;03;51;00;;ZENTNER, ARNOLD:;;;27000,00
280841400897;01;29;00;2254/84, :;ZENTSCH, PETER;2500;STRANDSTR. 2;
280841400897;01;29;00;2254/84, :;ZENTSCH, PETER;2500;STRANDSTR. 2;
050962430052;94;03;00;;ZENTSCH, RONALD:;;;18231,61
290447421314;99;02;00;;ZENTSCH, UWE:;;;26062,50
051270404026;18;31;00;;ZEPERNICK, HEIKO:;;;2795,00
010155513912;97;22;00;;ZEPERT, GUDRUN:;;;25012,50
110252427424;97;22;00;;ZEPERT, KARL-ERNST:;;;20880,00
121130401916;02;00;43;;ZEPEZAUER, PAUL:;;;38129,04
051159401919;99;09;00;;ZEPEZAUER, PETER:;;;21562,50
221157408526;06;09;00;;ZEPEZAUER, THOMAS:;;;22110,00
190340417712;09;65;00;;ZEPNEK, HANS-JOACHIM:;;;24437,50
120362402761;02;06;00;;ZEPPELIN, KERSTEN:;;;16540,34
010170401564;01;06;22;;ZEPPER, FRANK:;;;9510,00
290839407239;05;99;20;;ZEPTER, HERMANN:;;;26250,00
120341507222;05;80;00;;ZEPTER, LUCIE:;;;18180,00
010749403817;04;06;00;;ZERAHN, MANFRED:;;;19215,00
010362404022;03;08;00;;ZERBE, DIRK:;;;15922,50
010540425003;30;32;00;;ZERBE, FRIEDMAR:;;;20160,00
240455403364;03;00;44;;ZERBE, JOACHIM:;;;16450,00
210371414827;18;35;00;;ZERBE, MAIK:;;;2795,00
200171429726;03;69;00;;ZERBEL, ALF:;;;2870,00
031068430011;03;69;00;;ZERBEL, ARIAN:;;;10142,50
250471424017;18;38;00;;ZERBS, HEIKO:;;;2795,00
140457415125;99;43;00;;ZERBSTER, HELMUT:;;;20010,00
150951423912;13;00;44;;ZERBSTER, MAX:;;;26542,50
300751415126;98;83;00;;ZERBSTER, PETER:;;;21647,15
020669427148;94;65;00;;ZERFASS, THOMAS:;;;9510,00
080969417755;18;34;00;;ZERFASS, TORSTEN:;;;6736,77
161241417773;09;08;00;;ZERFASS, WALDEMAR:;;;27750,00
141240505618;99;43;00;;ZERFOWSKI, ERIKA:;;;13918,06
230557406946;05;60;00;;ZERFOWSKI, JOERG:;;;20010,00
230837405614;04;00;50;;ZERFOWSKI, WERNER:;;;23760,00
150539427137;14;06;00;;ZERGE, GUENTER:;;;21875,00
151057530152;99;77;00;;ZERGIEBEL, ANDREA:;;;19507,34
070736419021;98;19;00;;ZERGIEBEL, HELMUT:;;;30750,00
021268414228;18;35;00;;ZERN, ANDREAS:;;;9675,00
191249530030;99;53;00;;ZERN, CHRISTIANE:;;;25616,67
080150429811;99;77;00;;ZERN, RUEDIGER:;;;36000,00
180470429747;18;31;00;;ZERN, TORSTEN:;;;9195,00
260340409211;30;51;00;;ZERNA, WOLFGANG:;;;13860,00
311058422786;12;80;00;;ZERNDT, KARLHEINZ:;;;16905,00
260541430041;99;51;00;;ZERNIKOW, GUENTER:;;;37500,00
300568430168;18;31;00;;ZERNIKOW, STEFFEN:;;;9590,00
031142411514;07;06;00;;ZERNITZ, GERHARD:;;;21750,00
081167414733;10;08;00;;ZERRENNER, KARSTEN:;;;14460,00
190970414727;10;69;00;;ZERRENNER, RAIK:;;;3220,00
131041422212;18;29;00;;ZERRENNER, SIEGMAR:;;;27000,00
160247412231;07;26;00;;ZERSON, HANSI:;;;26447,50
190157506127;17;00;00;;ZERULL, ANTJE:;;;15089,69
300155511728;99;40;00;;ZERULL, GERLINDE:;;;20599,36
310850406144;17;00;00;;ZERULL, KLAUS-DIETER:;;;21600,00
171249506112;17;00;00;;ZERULL, MARION:;;;13146,63
131163406157;04;06;00;;ZERULL, MICHAEL:;;;15180,00
220745400841;01;19;69;;ZERULL, NORBERT:;;;24750,00
031269400812;01;06;26;;ZERULL, RENE:;;;8350,00
020854406189;17;00;00;;ZERULL, UDO:;;;18285,00
241049426952;14;19;00;;ZESCH, OLAF:;;;23760,00
181245406922;09;03;00;;ZESCHMAR, WALTER:;;;23437,50
181055422788;99;77;00;;ZESEWITZ, JOACHIM:;;;18156,63
280459422710;12;51;00;;ZESEWITZ, PETER:;;;19435,00
100857421317;99;09;00;;ZESSACK, ANDREAS:;;;21562,50
280856416816;97;01;00;;ZESSIN, PETER:;;;19492,50
220331430039;98;18;00;;ZETSCHE, WOLFGANG:;;;28500,00
300644428992;14;00;54;;ZETTEL, BERND:;;;24480,00
140554507128;05;06;00;;ZETTIER, BAERBEL:;;;18180,00
171140429758;08;08;00;;ZETTIER, DIETER:;;;28500,00
200240530044;08;78;00;;ZETTIER, HELENE:;;;22500,00
090337407320;05;07;00;;ZETTIER, HORST:;;;27000,00
200452407128;05;06;00;;ZETTIER, JUERGEN:;;;19837,50
220266430082;99;77;00;;ZETTIER, MARCEL:;;;15930,00
090368530049;97;01;00;;ZETTIER, SIMONE:;;;2527,42
090958407518;05;40;00;;ZETTIER, UWE:;;;25702,50
310349429780;97;01;00;;ZETTL, BERND:;;;22500,00
241049502417;97;22;00;;ZETTL, ILSE:;;;22038,94
210764427944;14;00;51;;ZETTL, PETER:;;;18645,00
180330530210;98;83;00;;ZETTL, RUTH:;;;21375,00
200351403419;99;53;00;;ZETTLER, WOLFGANG:;;;23040,00
060351422220;97;01;00;;ZETTLITZ, ULRICH:;;;27835,00
050544402120;95;45;00;;ZETTWITZ, DIETER:;;;21000,00
090440402130;02;06;00;;ZETTWITZ, HORST:;;;21187,50
281054428297;96;15;05;;ZETZL, HEINZ:;;;20340,00
090162419724;11;02;00;;ZETZMANN, ANDRE:;;;19140,00
100861419738;94;64;00;;ZETZMANN, BERND:;;;16830,00
151066419712;98;85;00;;ZETZMANN, CARSTEN:;;;16038,00
151269419712;11;69;00;;ZETZMANN, HEIKO:;;;9555,00
131169414756;99;43;00;;ZETZMANN, HEIKO:;;;9510,00
281170401323;18;34;00;;ZETZMANN, VOLKER:;;;2795,00
160559530034;18;77;00;;ZETZSCHE, ANNEKATRIN:;;;19691,66
200553422116;97;01;00;;ZETZSCHE, BERND:;;;19440,00
141248515319;08;60;00;;ZETZSCHE, CHRISTA:;;;20437,50
200543415369;08;11;00;;ZETZSCHE, HANS-JOACHIM:;;;28500,00
270963423836;30;62;00;;ZETZSCHE, JOERG:;;;15925,16
161052426929;90;65;40;1753/80,;ZETZSCHE, JU(E)RGEN;1144;EHM-WELK-STR. 44;
161052426929;90;65;40;1753/80,;ZETZSCHE, JU(E)RGEN;1144;EHM-WELK-STR. 44;
140653424619;13;07;00;;ZETZSCHE, KLAUS:;;;24085,16
280665415407;97;22;00;;ZETZSCHE, RALF:;;;18396,00
231253424429;94;65;00;;ZEUG, HARTMUT:;;;20880,00
010651417778;11;78;00;;ZEUGHARDT, MANFRED:;;;22252,50
020151426562;94;03;00;;ZEUGNER, HANS-ULLRICH:;;;27102,50
020350526320;94;03;00;;ZEUGNER, KARIN:;;;21574,59
151133400115;01;43;00;;ZEUMER, CARL-AUGUST:;;;23125,00
170143529725;94;30;00;;ZEUN, BAERBEL:;;;24000,00
021250520719;12;06;00;;ZEUN, BIRGIT:;;;18015,00
140747427212;14;40;00;;ZEUN, FRIEDER:;;;24875,00
200734429720;15;00;42;;ZEUN, HARDY:;;;30750,00
040739429711;97;06;00;;ZEUN, HARTMUT:;;;24750,00
190530530011;94;94;00;;ZEUN, LEONORE:;;;24000,00
031055427227;14;00;50;;ZEUN, THOMAS:;;;24500,00
111049422833;12;06;00;;ZEUN, WERNER:;;;20062,50
270265404128;03;00;50;;ZEUNER, DIRK:;;;4968,00
270252422757;30;53;00;;ZEUNER, FRANK:;;;12164,00
100850417729;98;27;00;;ZEUNER, GUENTER:;;;24975,00
160164422231;30;70;00;;ZEUNER, HARTMUT:;;;15441,74
080369418519;18;33;00;;ZEUNER, HEIKO:;;;9555,00
290934419625;99;40;00;;ZEUNER, JOHANNES:;;;27000,00
291067428914;18;35;00;;ZEUNER, MARIO:;;;9675,00
210762424416;94;64;00;;ZEUNER, MICHAEL:;;;18177,50
270670428019;18;28;00;;ZEUNER, MIKE:;;;2720,00
260160509514;98;85;00;;ZEUSCHNER, INGRA:;;;16555,97
310857413427;98;27;00;;ZEUSCHNER, UDO:;;;17940,00
020952403854;03;51;00;;ZEUSKE, HARTMUT:;;;19440,00
100650423630;94;03;00;;ZEYNER, GUNTER:;;;22080,00
160338412210;07;80;00;;ZGODZAJ, HELMUT:;;;24750,00
280963422242;99;43;00;;ZGODZAJ, MARIO:;;;19195,00
101169416922;09;69;00;;ZGODZINSKI, ROY:;;;9510,00
Diese Liste beinhaltet die Namen von 90.598 Mitarbeitern des Ministeriums für Staatssicherheit der DDR. Die Liste ist nicht vollständig. Insbesondere Mitarbeiter der Führungsebene sind nicht enthalten.
This is a list of 90.598 members of the secret police of East Germany (Ministry for State Security), the list isn’t complete, because the most of the high Officiers lieke Colonel and higher have destroyed the personal Informations in the last days of Eastern Germany.
| Listen der Stasimitarbeiter-hier findest Du sie! Was bedeuten die Zahlen? |
| 1.Listen der Stasi-Diensteinheiten! Bem.:hier kannst du die Nr.(6-stellig) der Dienststellen heraussuchen. 2.Liste der Stasi-Mitarbeiter (Hauptamtlich) Bem.:Hoffentlich hast Du einen guten Rechner, denn die Liste ist erschreckend lang. Die ersten 6 Ziffern sind das Geburtsdatum + die nächsten 6 Ziffern = Dienstausweisnummer! Die zwei Ziffern hinter dem Geburtsdatum geben das Geschlecht an: 41 und 42 = Männlich, 51 und 52 = Weiblich! Wichtig für suchen und finden, sind die sechs Ziffern in den Semikolon vor den Namen: z.B. ;07;00;44; ! Das ist die Nummer der Dienststelle ! Also du suchst in der Liste der Dienststellen, die Nummer der Dienststelle, die Dich interessiert. Damit gehst Du in die Liste der Mitarbeiter und suchst Dir alle Mitarbeiter der entsprechenden Dienststelle heraus. Ich habe das für mein Wohnort getan und so alle Mitarbeiter gefunden. Ob die Liste Vollständig ist kann ich nicht einschätzen, aber zumindest er/kannte ich einige Exverräter vom Namen her. 3.Liste der OibE (Offiziere im besonderen Einsatz) |
SECRET-Director of National Intelligence Classification and Control Markings Manual Version 1.2
The following Classification and Control Markings Manual gives descriptions of every major classification and control marking used in the U.S. Intelligence Community along with its legal justifications and goes with the Authorized Classification and Control Markings Register. Newer versions of the manual have been released via FOIA requests, however they contain a number of redactions.
(U) Authority
(U) DCID 6/6 dated 13 July 2001, mandates a classification marking system for the Intelligence Community (IC). This system uses a uniform list of security classification and control markings authorized for all dissemination of classified national intelligence information by components of the IC. This marking system augments and further defines the markings requirements established in Executive Order 12958, as amended, for portion markings and overall classification. This system does not stipulate or modify the classification authority information required by EO 12958, as amended.
(U) These classification and control markings, and their authorized abbreviations and portion markings, are compiled in the Authorized Classification and Control Markings Register maintained by the Controlled Access Program Coordination Office (CAPCO) (hereafter, referred to as the CAPCO Register) of the Director of National Intelligence Special Security Center (DNI SSC) pursuant to DCID 6/11.
(U) Purpose
(U) The Implementation Manual is a companion document developed to provide amplifying and explanatory guidance on the syntax and use of the markings contained in the CAPCO Register. While not the policy basis for individual agencies’ use of any particular marking, the Implementation Manual cites the applicable authority and sponsor for each marking. Some of the Dissemination Controls and Non-Intelligence Community Dissemination Control Markings are restricted to use by certain agencies. They are included to provide guidance on handling documents that bear them. Their inclusion in the manual does not authorize other Agencies to use these markings. Non-US Classification and Joint Classification Markings are restricted to the respective countries or international organizations.
(U) Certain unpublished controlled access program markings or markings that only determine addressing or routing of information are not included in the Implementation Manual per the CAPCO Register. The unpublished markings are contained in a separate unpublished Register maintained by CAPCO. Contact the CAPCO staff if you have questions regarding these items.
…
Unveiled – FEMEN Paris – Revisited
CONFIDENTIAL from the FBI – Silver Spring Man Sentenced to 20 Years in Prison for Distributing Child Pornography
GREENBELT, MD—U.S. District Judge Alexander Williams, Jr. sentenced Gary Callis, age 42, of Silver Spring, Maryland, today to 20 years in prison, followed by supervised release for life, for two counts of distributing child pornography. Judge Williams ordered Callis to pay approximately $24,000 in restitution to one of the victims of his sexual abuse for treatment and counseling expenses. Finally, Judge Williams ordered that upon his release from prison, Callis must register as a sex offender in the place where he resides, where he is an employee, and where he is a student, under the Sex Offender Registration and Notification Act (SORNA).
The sentence was announced by United States Attorney for the District of Maryland Rod J. Rosenstein; Special Agent in Charge Richard A. McFeely of the Federal Bureau of Investigation; Colonel Marcus L. Brown, Superintendent of the Maryland State Police; and Montgomery County State’s Attorney John McCarthy.
According to Callis’ plea agreement, in November and December, 2009, two separate FBI undercover operations in San Diego and Richmond, respectively, used file-sharing programs to download images from a user, later determined to be Callis, which depicted minors engaged in sexually explicit conduct. The Richmond undercover agent also engaged Callis in a chat, during which Callis stated he looked forward to trading images and that he “had some boy relations” with boys aged 6 to 14 and was presently looking for 14- to 20-year-old boys. Callis specifically described to the undercover agent his molestation of a boy from the time the child was 6 years old until he was 12 years old.
On February 26, 2010, law enforcement executed a search warrant at Callis’ residence in Silver Spring, and seized three external hard drives, two laptop computer, a computer tower and a memory card. A subsequent forensic examination of the digital media revealed that Callis possessed over 866,000 images and 8,100 movies portraying the sexual abuse of children. Agents found that the collection was highly organized, divided into folder titles with a number or letter, then further subdivided by a child’s name or a description of the contents. Callis’ computers also revealed that his primary means of trading child pornography was through the file-sharing program where the FBI undercover officers discovered Callis.
Callis was present during the search of his residence and admitted to investigators that in 2000 he had sexually molested a teenaged neighbor who was visiting his house, and in 2003 had begun molesting the son of his girlfriend, who was 7 years old at the time.
As part of the plea agreement, Callis has also agreed to plead guilty in a related case in Montgomery County Circuit Court, and agreed that the Circuit Court shall impose a sentence of 17 years in prison in that case, to run concurrent with Callis’ federal sentence. Callis remains detained.
This case was brought as part of Project Safe Childhood, a nationwide initiative to combat the growing epidemic of child sexual exploitation and abuse launched in May 2006 by the Department of Justice. Led by United States Attorneys’ Offices and the Criminal Division’s Child Exploitation and Obscenity Section (CEOS), Project Safe Childhood marshals federal, state and local resources to better locate, apprehend and prosecute individuals who exploit children via the Internet, as well as to identify and rescue victims. For more information about Project Safe Childhood, please visit www.projectsafechildhood.gov. Details about Maryland’s program are available at http://www.justice.gov/usao/md/Safe-Childhood/index.html.
United States Attorney Rod J. Rosenstein commended the FBI, Maryland State Police, and Montgomery County State’s Attorney’s Office for their work in this investigation and prosecution. Mr. Rosenstein thanked Special Assistant U.S. Attorney LisaMarie Freitas and Assistant U.S. Attorney Stacy Dawson Belf, who prosecuted the case.
TOP-SECRET from the NSA -CHILEAN JUDGE REQUESTS EXTRADITION OF U.S. MILITARY OFFICIAL IN “MISSING” CASE
|
CHILEAN JUDGE REQUESTS EXTRADITION OF U.S. MILITARY OFFICIAL IN “MISSING” CASECapt. Ray Davis Indicted in Chile for alleged role in murder of Charles Horman, Frank TeruggiDeclassified U.S. Documents Used Extensively in Court IndictmentArchive Posts Documents cited in Indictment, including FBI Intelligence Reports Containing Teruggi’s Address in Chile |
Washington D.C., November 30, 2011 –Thirty-eight years after the military coup in Chile, a Chilean judge has formally indicted the former head of the U.S. Military Group, Captain Ray Davis, and a Chilean intelligence officer, Pedro Espinoza for the murders of two American citizens in September 1973. The judge, Jorge Zepeda, said he would ask the Chilean Supreme Court to authorize an extradition request for Davis as an “accessory” to the murders of Charles Horman and Frank Teruggi.
Both Horman and Teruggi were seized separately at their homes in Santiago by Chilean soldiers and subsequently executed while in detention. Their murders, and the seeming indifference of U.S. officials, were immortalized in the Oscar-award winning movie “Missing” which focused on the search by Horman’s wife and father for him in the weeks following the U.S.-supported coup.
The indictment accused the U.S. MilGroup of passing intelligence to the Chilean military on the “subversive” activities of Teruggi that contributed to his arrest; it stated that Davis “was in a position” to stop the executions “given his coordination with Chilean agents” but did not do so.
In his indictment, Judge Zepeda cited a number of declassified U.S. government documents as the basic foundation for the case-although none of them tie Davis or Espinoza to the crimes. “These documents are providing the blocks for building a case in these famous killings,” said Peter Kornbluh who directs the Chile Documentation Project at the Archive, “but they do not provide a smoking gun.” To successfully advance court proceedings as well as a successful extradition request, according to Kornbluh, the judge will have to present concrete evidence of communications between U.S. and Chilean military officers regarding Horman and Teruggi prior to their detentions and their deaths.
The Archive today posted a number of the documents cited in the indictment, including key FBI memos that contained Frank Teruggi’s Santiago address, as well as other records relevant to the Horman and Teruggi case. The documents derive from an indexed collection: Chile and the United States: U.S. Policy toward Democracy, Dictatorship, and Human Rights, 1970-1990. The collection, just published this week by the Archive and Proquest, contains over 180 documents on the Horman and Teruggi case.
Read the Documents:
Document 1
Department of State, SECRET Memorandum, “Charles Horman Case,” August 25, 1976
This memo by three state department officers implies that the U.S. government could have prevented the murder of Charles Horman. The memo, written after a review of the files on the case, explains that there is “circumstantial evidence” to suggest “U.S. intelligence may have played an unfortunate part in Horman’s death. At best, it was limited to providing or confirming information that helped motivate his murder by the GOC. At worst, U.S. intelligence was aware the GOC saw Horman in a rather serious light and U.S. officials did nothing to discourage the logical outcome of GOC paranoia.” When this document was initially declassified pursuant to a FOIA lawsuit filed by the Horman family, this critical passage was blacked out. The document was released without redaction in 1999. It was not cited in Judge Zepeda’s indictment, but appears to reflect the judicial argument he is pursuing.
Document 2
Department of State, SECRET, “Charles Horman Case: Gleanings,”(Undated but written in August 1976)
This detailed chronology, based on a review of files available to the State Department, contains key information on what the U.S. knew and did in the case of Charles Horman. It also evaluates the possible role of the U.S. in the murder. The document cites the admissions of a Chilean intelligence agent, Rafael Gonzalez, who told U.S. reporters the story of Horman being interrogated in General Augusto Lutz’s office and then killed because “he knew too much.” Gonzalez claimed there was an American in the room when the interrogation took place, but decades later he would recant that story. In January 2004, he was indicted by Judge Zepeda in the Horman case as an “accessory to murder” for his role in the interrogation, death and secret burial of Charles Horman.
Document 3
United States Embassy, Unclassified Notice, “Missing United States Citizen,” October 9, 1973
This document cited in the indictment, states that the U.S. government has received a note from the Chilean Foreign Office dated October 3, 1973, recording that Charles Horman was detained at the National Stadium on September 20 for a curfew violation but had been released on September 21 for “lack of merit.” The document includes a photograph of Horman, his date of birth, address in Chile, and fingerprint classification. Horman was actually detained at his home on September 17, 1973.
Document 4
Department of State, Memorandum (classification excised), “Film by Charles Horman,” April 12, 1974
In this memo to Assistant Secretary Harry Shlaudeman, State Department officer George Lister describes the film work of Charles Horman. A film that he apparently worked on before the coup was completed after the coup by friends titled “Chile: With Poems and Guns.” (The document leaves the impression that Charles “made” the film, but clearly he did not work on it following the coup.) The film describes Chilean history, and the achievements of the Allende government, along with alleged atrocities of the coup and U.S. involvement. Lister goes so far as to imply that Horman’s film making in Chile could have been what “led to his death.”
Document 5
Chilean Armed Forces, Memorandum, “Antecedentes sobre Fallecimiento de 2 ciudadanos norteamericanos,” Octobeer 30, 1973
Chief of Chilean Military Intelligence Service General Augusto Lutz reports on the death of Charles Horman and Frank Teruggi. He asserts that Horman and Teruggi were political extremists attempting to discredit Chilean junta. While he acknowledges that they were both detained by the Chilean military, he maintains that they were later released and that the Chilean military was not involved in their deaths. The document is the only information known to have been provided by the Chilean military to the U.S. embassy after the disappearance of Horman and Teruggi.
Document 6
U.S. Military Group Chile, Memorandum (classification unknown), “Case of Charles Horman,” January 14, 1975
Ray Davis forwards a list of documents on the interactions of the U.S. Military Group in Chile with Charles Horman to be provided to the General Accounting Office. The documents raise the issue of the role of embassy officials in the disappearance and death of Horman, and make “certain allegations and statements about members of the Navy Mission, in Valparaiso; comments about a ride given by COMUSMILGP, Captain Davis.”
Document 7
Department of State, CONFIDENTIAL Memorandum, “Horman Case,” April 20, 1987
This memorandum of conversation reports on an informant who has appeared at the Embassy to give testimony on the death of Charles Horman. According to this informant, Horman was seized by Chilean intelligence units and taken to the Escuela Militar for questioning. He was then transferred to the National Stadium, where they determined he was an extremist. He was forced to change clothes, shot three times, and his body was dumped on the street to appear he had died in a confrontation. The informant said that “the person at the stadium who made the decision on who was to die was Pedro Espinoza, of later DINA fame.” The document is the first to tie Pedro Espinoza to the Horman case. He was involved in military intelligence and detainees at the time of the coup. However, the commander of the National Stadium at the time was another military officer named Jorge Espinosa Ulloa.
Document 8
United States Embassy Santiago, CONFIDENTIAL cable, ‘[Excised] Reports on GOC Involvement in Death of Charles Horman, Asks Embassy for Asylum and Aid,’ April 28, 1987
In a report on the informant’s information, the Embassy cables Washington with his account of Horman’s death. Horman was picked up in a routine sweep, the informant suggests, and was found in possession of “extremist” materials. He was then taken the National Stadium where he was interrogated and later executed on the orders of Pedro Espinoza. Embassy officials note that his story “corresponds with what we know about the case and the [Chilean government] attempt to cover up their involvement,” suggesting that the informant is probably telling the truth. In later cables, the Embassy begins to question the credibility of the informant who is never identified.
Document 9
FBI, SECRET Memorandum, [Frank Teruggi’s Contact with Anti-War Activist], October 25, 1972
This FBI report cites information provided by “another U.S. government agency” on Frank Teruggi’s contacts with an anti-war activist who resides in West Germany. The report also contains his address in Santiago. The document was generated by surveillance of a U.S. military intelligence unit in Munich on an American anti-war dissident who was in contact with Teruggi. The FBI subsequently decides to open a file on Teruggi. This series of FBI documents were cited by Judge Zepeda in his indictment which infers-but offers no proof– that intelligence from them was shared with Chilean military intelligence in the days following the coup.
Document 10
FBI, SECRET Memorandum, “Frank Teruggi,” October 25, 1972
This FBI memorandum requests investigation of Frank Teruggi and the Chicago Area Group for the Liberation of Americas of which he was a member nearly a year prior to his death following the Chilean coup.
Document 11
FBI, SECRET Memorandum, “[Excised] SM- Subversive,” November 28, 1972
This FBI document again requests investigation on Teruggi based on his contact with a political activist in West Germany. The document mentions that Teruggi is living in Chile editing a newsletter “FIN” of Chilean information for the American left, and that he is closely affiliated with the Chicago Area Group for the Liberation of Americas.
Document 12
FBI, Memorandum (classification unknown), “Frank Teruggi,” December 14, 1972
This FBI memorandum demonstrates ongoing efforts to gather information on Frank Teruggi in the year proceeding the Chilean coup. Here, the FBI reports on his attendance at a conference of returned Peace Corps volunteers and his membership in political organizations supporting socialism and national liberation movements in Latin America.
TOP-SECRET – (U//FOUO) Director of National Intelligence Classification Markings Register Version 1.2
Unveiled – FEMEN Paris
STASI-NAMEN ALPHABETISCH BUCHSTABE WL-WR – STASI-NAMES IN ALPHABETICAL ORDER – WL-WR
Die Liste wurde bereits früher hier publiziert:
http://stasiopfer.de/component/option,com_simpleboard/Itemid,/func,view/id,993815828/catid,4/
Vom “Stasiopfer”-Angebot führt ein Link zu einer Website in den USA (www.jya.com), die sich auch mit den Praktiken von Geheimdiensten beschäftigt. Dort findet sich die “Fipro-Liste”, das detaillierte “Finanzprojekt” der Stasi, angefertigt in den letzten Tagen der DDR, um die Rentenansprüche der rund 100 000 hauptamtlichen Mitarbeiter des MfS auch nach dem Zusammenbruch des Systems belegen zu können. Die “Fipro-Liste” ist seit langem bekannt und diente Anfang der neunziger Jahre etwa zur Identifizierung der so genannten OibE – Offiziere im besonderen Einsatz. Diese Liste „Offiziere im besonderen Einsatz“im Jahre 1991 erschien in der “taz. Die Echtheit kann beim BStU überprüft werden.
Siehe u.a. http://www.spiegel.de/spiegel/print/d-22539439.html
Auf Druck ehemaliger STASI-Leute und Ihrer Genossen wurde die Liste aus dem Verkehr gezogen.
Hier ist sie wieder:
240240510816;07;00;49;;WLACH, HERTA:;;;15640,00
260668410822;07;06;00;;WLACH, MICHAEL:;;;12625,00
290970405028;04;69;00;;WLADACZ, UWE:;;;2870,00
070561430033;98;84;00;;WLADIMIROW, KLAUS:;;;17077,50
300341419044;10;00;40;;WLASAK, KARL-HEINZ:;;;29250,00
091263419066;99;43;00;;WLASAK, UWE:;;;18590,00
050447430103;15;18;00;;WLOCHAL, BERND:;;;27000,00
160638429727;94;65;00;;WLOCKA, DIETER:;;;33000,00
240152418438;09;00;44;;WLOCKA, KARL-HEINZ:;;;25127,50
151050508921;06;00;51;;WLODARCZAK, MARINA:;;;18130,00
131262420552;94;03;00;;WLOKA, ANDREAS:;;;16775,00
150861509552;99;77;00;;WLOKA, INES:;;;12556,63
181161420567;94;03;00;;WLOKA, MICHAEL:;;;17875,00
291146529713;98;18;00;;WLOKA, URSULA:;;;21750,00
291151406435;15;54;00;;WLONEWSKI, LOTHAR:;;;23760,00
120362409111;18;28;00;;WNUCK-V-LIPINSKI, UWE:;;;22440,00
020369508923;18;33;00;;WNUCK-VON-LIPINSKI, KATI:;;;13560,00
220768414218;18;33;00;;WO(E)HLBIER, THOMAS:;;;9825,00
090569411214;18;31;00;;WO(E)HLERT, UWE:;;;9600,00
210770430242;18;96;00;;WO(E)HNER, JAN:;;;2945,00
030569423843;13;69;00;;WO(E)LFER, TORSTEN:;;;10600,00
311230413241;96;15;00;2953/77, J:;WO(E)LLER, KLAUS;1020;KARL-LIEBKNECHT-STR. 9;27000,00
011254418421;10;00;46;;WO(E)LLNER, JU(E)RGEN:;;;21877,50
050568415313;18;34;00;;WO(E)RDEMANN, DIRK:;;;10800,00
280369412287;18;00;50;;WO(E)TZEL, MARKO:;;;9720,00
030170426313;18;34;00;;WO(E)TZEL, MICHAEL:;;;9510,00
290547421039;14;51;00;;WOBAT, JOHANNES:;;;21390,00
190149515429;94;03;00;;WOBBROCK, DORIS:;;;23040,00
151140522743;12;51;00;;WOBST, ERIKA:;;;21097,50
061267419082;10;08;00;;WOBST, FRANK:;;;4472,00
030564422710;94;65;00;;WOBST, JOERG:;;;18645,00
050152528277;14;00;40;;WOBST, MARGIT:;;;18020,50
270471408971;18;33;00;;WOBST, MATHIAS:;;;2636,33
280250519618;11;06;20;;WOBST, SIEGLINDE:;;;17163,75
120645428224;14;09;00;;WOBST, STEFFEN:;;;24125,00
071051409124;94;65;00;;WOCHATZ, KLAUS:;;;14608,78
030953424736;94;30;00;;WOCHE, REINER:;;;23460,00
030864413218;99;43;00;;WOCHNICK, RALF:;;;17572,50
260466422868;99;43;00;;WOCHNIK, RALPH:;;;14946,00
190547409111;06;06;00;;WOCHNIK, WOLFGANG:;;;20640,00
300469403420;18;33;00;;WOCKENFUS(Z), DIRK:;;;9465,00
300756504224;03;00;51;;WOCKENFUSZ, EDDA:;;;16468,00
061036402718;02;03;00;;WODACH, RUDOLF:;;;23250,00
170938429752;94;65;00;;WODAEGE, HANS-JOACHIM:;;;22500,00
250951429810;94;65;00;;WODAEGE, PETER:;;;20160,00
020763430298;94;64;00;;WODAEGE, THOMAS:;;;18205,00
050359400836;01;80;00;;WODARZ, DETLEF:;;;16673,14
270453415131;05;08;00;;WODE, HANS-JUERGEN:;;;25020,00
220160401814;02;00;42;;WODITSCH, RAINER:;;;22712,50
220464405259;04;06;00;;WODNICK, HARDY:;;;17270,00
290856405737;04;06;00;;WODTKE, HELMUT:;;;19952,50
110659506132;04;18;00;;WODTKE, PETRA:;;;12585,10
061258405711;04;80;00;;WODTKE, SIEGFRIED:;;;16905,00
061061403712;30;63;00;;WOEBS, ANDRE:;;;14623,80
151057430194;96;15;22;;WOEHL, HANS:;;;19320,00
130959406123;04;08;00;;WOEHL, PETER:;;;15840,00
180969409913;07;06;00;;WOEHLBIER, ENRICO:;;;12460,00
041031430041;98;80;00;;WOEHLECKE, DIETER:;;;26250,00
180653510812;07;06;00;;WOEHLER, BAERBEL:;;;20416,01
120852411927;07;06;00;;WOEHLER, HARALD:;;;20880,00
090351416469;09;00;44;;WOEHLER, HILMAR:;;;18480,00
050753411912;07;00;57;;WOEHLER, VOLKER:;;;17365,00
100853414216;08;51;00;;WOEHLERT, HANS-JOACHIM:;;;20160,00
091250412236;07;03;00;;WOEHLERT, MANFRED:;;;20880,00
180230412217;07;53;00;;WOEHLERT, WOLFGANG:;;;24000,00
301144429758;15;03;00;;WOEHNER, HARTMUT:;;;29000,04
150969419727;99;43;00;;WOEHNER, JENS:;;;13285,00
150437500815;01;12;00;;WOEHNER, KAETE:;;;22500,00
161242530081;30;61;00;;WOEHRL, BARBARA:;;;20700,00
040940429721;94;30;00;;WOEHRL, HEINER:;;;28062,50
180856408818;06;00;49;;WOEHRMANN, EBERHARD:;;;17020,00
060862414337;99;40;00;;WOELBLING, MICHAEL:;;;17875,00
290764412235;99;43;00;;WOELFEL, JENS:;;;17928,00
250370428828;97;01;00;;WOELFEL, NORBERT:;;;8712,50
150568417771;09;69;00;;WOELFEL, THOMAS:;;;14574,07
180851424915;13;08;00;;WOELFER, MICHAEL:;;;22552,50
200868412254;18;35;00;;WOELFER, RENE:;;;9600,00
230763503229;99;43;00;;WOELFL, GERLIND:;;;452,41
181060403215;98;82;00;;WOELFL, MATTHIAS:;;;17490,00
241167405220;18;00;50;;WOELK, ANDREAS:;;;10305,00
310563530054;99;77;00;;WOELK, CAROLA:;;;13968,01
071162422719;15;14;00;;WOELK, CARSTEN:;;;19140,00
031050415040;08;80;00;;WOELK, EBERHARD:;;;31680,00
231237400822;01;26;00;;WOELK, GERHARD:;;;24375,00
031243415012;08;00;60;;WOELK, HANSJUERGEN:;;;33000,00
050931429729;99;40;00;;WOELK, HEINZ:;;;28500,00
110471415028;08;19;00;;WOELK, KARSTEN:;;;2700,00
150652406178;04;80;00;;WOELK, PETER:;;;24150,00
310559417534;18;35;00;;WOELK, RALF-PETER:;;;19320,00
270362507217;15;53;00;;WOELK, SABINE:;;;3636,18
130258514412;08;53;00;;WOELK, SYLVIA:;;;20148,00
211033529714;95;60;00;;WOELK, URSULA:;;;23250,00
050757403311;30;47;00;;WOELKE, GERHARD:;;;21718,75
060949406129;04;14;00;;WOELKE, GUENTHER:;;;20720,00
310853408268;06;00;42;;WOELKERLING, UWE:;;;20160,00
110553403928;03;78;00;;WOELKI, LOTHAR:;;;21600,00
160365404216;03;00;51;;WOELKI, MICHAEL:;;;5130,00
190768406926;98;83;00;;WOELKY, LARS:;;;10541,13
180470400717;01;06;24;;WOELLER, FRANK:;;;9510,00
240256400216;01;00;42;;WOELLER, HORST:;;;17882,50
160562428022;94;03;00;;WOELLNER, ANDREAS:;;;19965,00
231152418943;10;26;00;;WOELLNER, BERND:;;;23220,00
031148530039;94;30;00;;WOELLNER, GISELA:;;;21500,00
181042418413;96;15;11;;WOELLNER, GUENTER:;;;22942,50
200245418414;94;30;00;;WOELLNER, KLAUS:;;;28025,00
251061423833;97;01;00;;WOELLNER, MICHAEL:;;;18468,00
160163522740;99;51;00;;WOELLNER, PETRA:;;;16946,30
300565427510;14;03;00;;WOELLNER, RAINER:;;;15152,50
100458430152;94;03;00;;WOELLNER, RALF:;;;20700,00
290946518428;96;15;05;;WOELLNER, REGINA:;;;24274,09
110740429728;15;00;50;;WOERFEL, HELMUT:;;;28933,04
170167430105;98;83;00;;WOERFEL, JENS:;;;15513,30
011162430036;15;08;00;;WOERNER, MICHAEL:;;;18095,00
280344506113;04;51;00;;WOERZ, EVAMARIA:;;;22625,00
150470405326;17;00;00;;WOESNER, SVEN:;;;9555,00
260441513819;08;00;53;;WOETZEL, BRIGITTE:;;;24000,00
111165530137;99;53;00;;WOETZEL, DELIA:;;;409,33
230646429728;99;43;00;;WOETZEL, DIETER:;;;24000,00
120358428221;95;60;23;;WOETZEL, GERHARD:;;;18745,00
161142427714;99;09;00;;WOETZEL, LOTHAR:;;;24750,00
290838428230;14;29;00;;WOETZEL, MANFRED:;;;24000,00
070863427331;98;83;00;;WOETZEL, MATTHIAS:;;;17662,10
120757418119;95;45;00;;WOETZEL, RALF:;;;18112,50
051162428223;14;07;00;;WOETZOLD, TORSTEN:;;;19965,00
031148403224;03;00;43;;WOHLAN, WOLFGANG:;;;19125,00
120849417113;09;06;00;;WOHLBEREDT, GUENTER:;;;22560,00
200662415134;97;01;00;;WOHLER, KAI:;;;22165,00
250962417436;98;85;00;;WOHLERT, LUTZ:;;;17820,00
070370424941;18;32;00;;WOHLFAHRT, DIRK:;;;9060,00
280552410829;98;19;00;;WOHLFAHRT, HANS-JOACHIM:;;;28740,00
100461426728;97;01;00;;WOHLFAHRT, JUERGEN:;;;23100,00
050769418449;18;33;00;;WOHLFAHRT, KAI:;;;9600,00
120149419660;99;02;00;;WOHLFAHRT, KARL-HEINZ:;;;29520,00
131065416220;09;00;43;;WOHLFAHRT, KIRSTEN:;;;16852,00
260345530168;99;77;00;;WOHLFARTH, BRIGITTE:;;;17966,00
150835418526;10;06;00;;WOHLFARTH, ERICH:;;;19740,00
200331417717;09;11;00;;WOHLFARTH, GERHARD:;;;33750,00
010669412238;18;35;00;;WOHLFARTH, JENS:;;;9675,00
100861417740;99;13;00;;WOHLFARTH, OLAF:;;;17737,50
190949428972;10;00;50;;WOHLFARTH, ROLAND:;;;22860,00
231144429765;94;30;00;;WOHLFARTH, ULRICH:;;;23000,00
100630418818;10;00;50;;WOHLFARTH, WERNER:;;;28500,00
020656425012;97;08;00;;WOHLFELD, NORBERT:;;;20010,00
160859430131;98;83;00;;WOHLGEMUTH, BERND:;;;18457,50
011041422849;12;65;00;;WOHLGEMUTH, DIETER:;;;20187,50
090636407240;94;03;00;;WOHLGEMUTH, ERWIN:;;;24062,50
130649411429;07;03;00;;WOHLGEMUTH, KLAUS:;;;21600,00
270956411458;99;02;00;;WOHLGEMUTH, PETER:;;;24322,50
020665428282;04;20;00;;WOHLGEMUTH, RALPH:;;;11016,00
310534429715;97;06;00;;WOHLGEMUTH, RUDI:;;;30774,20
021258511411;97;29;00;;WOHLGEMUTH, SONJA:;;;18802,50
150561401929;02;06;00;;WOHLGEMUTH, UDO:;;;18425,00
050551428230;14;60;00;;WOHLGEMUTH, ULLRICH:;;;26300,00
080743406172;04;00;40;;WOHLLEBE, BERND:;;;21750,00
031236430206;96;15;15;;WOHLLEBE, GERHARD:;;;30750,00
080634424419;13;00;48;;WOHLLEBE, KONRAD:;;;20250,00
270350424430;13;00;40;;WOHLLEBE, MANFRED:;;;25602,50
010551426722;14;08;00;;WOHLLEBE, WOLFGANG:;;;21600,00
150962420223;11;20;00;;WOHLLEBEN, INGO:;;;19140,00
030936430229;98;18;00;;WOHLLEBEN, MANFRED:;;;30750,00
121260503216;99;77;00;;WOHLRAB, ASTRID:;;;19564,28
300854422791;12;15;00;;WOHLRAB, BERND:;;;24840,00
040954526565;14;96;00;;WOHLRAB, BRUNHILDE:;;;1538,19
050668418415;10;69;00;;WOHLRAB, DIRK:;;;12455,00
200543420344;99;49;00;;WOHLRAB, EDGAR:;;;25125,00
160934429713;94;64;00;;WOHLRAB, HEINZ:;;;24687,50
051146424986;13;80;00;;WOHLRAB, HERBERT:;;;20375,00
090758428250;99;09;00;;WOHLRAB, HINRICH:;;;20355,00
190370426513;14;69;00;;WOHLRAB, JENS:;;;12085,00
140869430161;18;31;00;;WOHLRAB, OLAF:;;;9600,00
290847429710;98;83;00;;WOHLRAB, PETER:;;;20213,83
040846530145;98;83;00;;WOHLRAB, RITA:;;;18391,91
310754426524;14;96;00;;WOHLRAB, ROLAND:;;;18660,00
110742405631;04;00;50;;WOHLRAB, ROLF:;;;27000,00
220148426541;14;26;00;;WOHLRAB, WERNER:;;;23125,00
070452426545;14;00;51;;WOHLRAB, WOLFGANG:;;;23760,00
181256413917;99;55;00;;WOHLRAB, WOLFGANG:;;;21160,00
180267411728;07;00;55;;WOHLT, CHRISTIAN:;;;11016,00
040858509511;06;77;00;;WOHMANN, ANNETTE:;;;17732,72
010662407911;06;00;42;;WOHMANN, BERND:;;;15785,00
140258407915;06;00;40;;WOHMANN, PETER:;;;22252,50
160751523838;98;50;00;;WOHNER, ADELHEID:;;;22320,00
250248417770;97;07;00;;WOHNER, KLAUS:;;;29625,00
210940530044;15;55;00;;WOICIECHOWSKI, URSULA:;;;23280,00
240129428224;99;51;00;;WOICKE, GERD:;;;42000,00
100568423818;18;35;00;;WOIDAK, MATTHIAS:;;;9317,58
050170407612;18;32;00;;WOIDE, SWEN:;;;9510,00
251135421823;12;80;00;;WOIDICH, ANTON:;;;20875,00
181034521816;12;80;00;;WOIDICH, EVELINE:;;;18562,50
290358522113;12;51;00;;WOIDICH, GUDRUN:;;;13640,84
010761422789;12;08;00;;WOIDICH, NORBERT:;;;17820,00
030769403230;18;28;00;;WOIKE, CLAUDIO-MATHIAS:;;;9510,00
131047411258;03;03;00;;WOIKE, DIETER:;;;20250,00
311055503628;03;80;00;;WOIKE, MARLIS:;;;19726,20
160760503214;99;77;00;;WOITALLA, GUNDULA:;;;17870,10
070339422876;30;57;00;;WOITAS, HARRY:;;;14400,00
251050522748;30;57;00;;WOITAS, ULRIKE:;;;13138,52
150759409512;06;08;00;;WOITASKE, HEIKO:;;;15657,50
131063409545;60;90;00;;WOITASKE, RAIK:;;;
131063409545;60;90;00;;WOITASKE, RAIK:;;;16265,00
060759428124;30;34;00;;WOITE, CARSTEN:;;;19200,00
020737407617;99;09;00;;WOITE, HERBERT:;;;24750,00
110463430244;18;71;20;;WOITHE, JO(E)RG:;;;20515,00
210843530384;30;83;00;;WOITKE, BARBARA:;;;21429,60
030648409521;06;51;00;;WOITO, JOACHIM:;;;21300,00
050435430157;30;47;00;;WOITOWITZ, OTTO:;;;17550,00
091164411413;07;06;00;;WOITZIK, CARSTEN:;;;17765,00
091069403423;03;69;00;;WOITZIK, PETER:;;;10192,50
020451412939;97;01;00;;WOITZIK, WOLFGANG:;;;27360,00
150953405929;04;60;00;;WOIWODE, RALF:;;;19440,00
271265421846;99;77;00;;WOJACK, MAIK:;;;11274,67
171261400863;97;01;00;;WOJAK, UWE:;;;22605,00
171253402236;97;01;00;;WOJATSCHKE, BERND:;;;28800,00
240846402115;03;07;00;;WOJCIECHOWSKI, HORST:;;;26250,00
070466408444;99;43;00;;WOJCIK, JENS:;;;15768,00
190655408431;97;06;00;;WOJCIK, MANFRED:;;;21700,00
220454416819;09;06;00;;WOJNA, HARALD:;;;20872,50
200745408423;06;06;00;;WOJTAS, GUENTER:;;;23400,00
140267403748;30;36;00;;WOJTAS, TORSTEN:;;;13316,00
020755423610;99;43;00;;WOJTCZAK, MATTHIAS:;;;21000,00
260166414815;08;00;59;;WOJTYNA, DIRK:;;;16736,00
240768422240;18;34;00;;WOKAL, MIKE:;;;9675,00
160133429713;15;40;00;;WOKITTEL, HANS-PETER:;;;27750,00
311062422818;96;15;00;4228/83, F:;WOKURKA, ULF;1055;RUDOLF-SCHWARZ-STR. 32;5600,00
190438507222;97;06;00;;WOLARZ, EDITH:;;;23812,50
271137407214;97;29;00;;WOLARZ, JOERG:;;;27750,00
220457406130;18;32;00;;WOLARZ, LEON:;;;24840,00
081035429714;97;08;00;;WOLARZ, WERNER:;;;33000,00
290963400042;94;03;00;;WOLDEGK, DIRK:;;;15925,16
260140500029;94;03;00;;WOLDEGK, INGE:;;;18498,75
010632410511;97;01;00;;WOLF, ALFRED:;;;31500,00
310769426527;97;01;00;;WOLF, ANDRE:;;;3070,16
220660511120;15;20;00;;WOLF, ANDREA:;;;16265,02
121163406158;04;00;40;;WOLF, ANDREAS:;;;19965,00
180171407820;05;69;00;;WOLF, ANDREAS:;;;2870,00
300963428260;04;06;00;;WOLF, ANDREAS:;;;17490,00
181061428211;14;80;00;;WOLF, ANDREAS:;;;15768,50
131266407582;99;43;00;;WOLF, ANDREAS:;;;13896,00
090957426725;99;77;00;;WOLF, ANDREAS:;;;23517,50
240460426827;99;55;00;;WOLF, ANDREAS:;;;19320,00
160261430225;99;26;00;;WOLF, ANDREAS:;;;19002,50
040860424023;94;65;00;;WOLF, ANDREAS:;;;17820,00
041154416039;09;00;42;;WOLF, ANDREAS:;;;26220,00
300153522212;99;77;00;;WOLF, ANGELA:;;;21056,24
270949429721;99;51;00;;WOLF, AXEL:;;;25500,00
180866414314;94;11;00;;WOLF, AXEL:;;;17464,50
110245529713;96;15;00;804/83/1, F:;WOLF, BARBARA;1595;HANS-MARCHWITZA-RING 14;
110245529713;96;15;00;804/83/1, F:;WOLF, BARBARA;1595;HANS-MARCHWITZA-RING 14;
110851513754;94;30;00;;WOLF, BARBARA:;;;18917,50
251043413252;08;15;00;;WOLF, BERND:;;;23040,00
121060420010;11;65;00;;WOLF, BERND:;;;16857,50
281141429714;97;08;00;;WOLF, BERND:;;;24000,00
190941420351;30;37;00;;WOLF, BERNHARD:;;;31860,00
250740530396;18;80;00;;WOLF, BRIGITTE:;;;19125,00
101155525028;97;07;00;;WOLF, BRIGITTE:;;;21510,00
271255407223;98;85;00;;WOLF, BURGHARD:;;;19600,00
181055506922;98;83;00;;WOLF, BURGLIND:;;;16034,80
300560430040;15;08;00;;WOLF, CARSTEN:;;;17029,50
270768428017;18;34;00;;WOLF, CARSTEN:;;;9675,00
281065424929;99;13;00;;WOLF, CARSTEN:;;;11067,00
130535528231;14;14;00;;WOLF, CHRISTA:;;;20379,04
301155428275;14;15;00;;WOLF, CHRISTIAN:;;;24500,00
130745515316;96;15;10;;WOLF, CHRISTINA:;;;16915,92
221256508928;17;00;00;;WOLF, CHRISTINE:;;;23985,62
171165511221;99;77;00;;WOLF, CLAUDIA:;;;4093,98
270651424952;99;43;00;;WOLF, CLAUS-FRANZ:;;;25695,00
060856510832;07;14;00;;WOLF, DAGMAR:;;;17498,49
250543429731;13;40;00;;WOLF, DIETER:;;;23250,00
111135429716;99;43;00;;WOLF, DIETER:;;;24000,00
280237406141;17;00;00;;WOLF, DIETER:;;;33000,00
201047422783;94;30;00;;WOLF, DIETER:;;;21500,00
281244428933;14;51;00;;WOLF, DIETMAR:;;;24000,00
131248428128;02;03;00;;WOLF, DIETMAR:;;;22500,00
091069409315;18;31;00;;WOLF, DIRK:;;;10500,00
200551520329;30;61;00;;WOLF, DORIS:;;;18000,00
281147428288;14;06;00;;WOLF, EBERHARD:;;;20125,00
211247420335;11;51;00;;WOLF, EBERHARD:;;;29187,50
290447428284;97;08;00;;WOLF, EBERHARD:;;;27750,00
190832430032;94;03;00;;WOLF, EBERHARD:;;;24000,00
260132505620;98;20;00;;WOLF, EDELTRAUD:;;;18170,00
060935406128;04;53;00;;WOLF, EHRHARD:;;;28500,00
030365421221;12;96;67;;WOLF, ENRICO:;;;10830,00
070870423128;18;35;00;;WOLF, ERIK:;;;6705,00
201137506112;04;03;00;;WOLF, ERIKA:;;;27500,04
230449528268;14;08;00;;WOLF, EVA-MARIA:;;;20187,50
100760528214;14;80;00;;WOLF, EVELIN:;;;13811,33
281263430158;97;01;00;;WOLF, FRANK:;;;25223,00
300166415360;08;09;00;;WOLF, FRANK:;;;15895,50
070350416039;09;06;00;;WOLF, GEORG:;;;28500,00
061046422771;12;06;00;;WOLF, GERALD:;;;20240,00
050955427517;06;08;00;;WOLF, GERD:;;;19262,50
090851405643;15;08;00;;WOLF, GERHARD:;;;20520,00
070158430084;97;22;00;;WOLF, GERNOT:;;;24633,74
211253516827;98;83;00;;WOLF, GERTRUD:;;;19372,50
040471505620;04;00;53;;WOLF, GINA:;;;4476,77
271138521510;12;08;00;;WOLF, GISELA:;;;16500,00
090745407514;05;02;00;;WOLF, GUENTER:;;;31687,50
030654421535;12;00;50;;WOLF, GUENTER:;;;21907,50
080954419635;11;00;47;;WOLF, GUENTER:;;;23182,50
280426406917;99;43;00;;WOLF, GUENTER:;;;54750,00
010337429738;99;41;00;;WOLF, GUENTER:;;;33000,00
290149422837;12;80;00;;WOLF, GUENTHER:;;;18720,00
090761422810;12;06;00;;WOLF, GUNTER:;;;17765,00
220153428269;94;30;00;;WOLF, GUNTER:;;;21664,53
161269413010;18;34;00;;WOLF, HAGEN:;;;9510,00
061068424989;13;00;47;;WOLF, HAIKO:;;;13525,00
180230430239;96;15;05;;WOLF, HANS:;;;42000,00
070848419624;11;00;45;;WOLF, HANS-DIETER:;;;22987,09
271153405614;15;40;00;;WOLF, HANS-JOCHEN:;;;24261,43
230754406945;97;22;00;;WOLF, HANS-JUERGEN:;;;25920,00
110754414439;08;00;45;;WOLF, HANS-JUERGEN:;;;25200,00
271061430230;30;31;00;;WOLF, HANS-PETER:;;;17574,00
180856404315;97;01;00;;WOLF, HARALD:;;;22770,00
050740412211;07;06;00;;WOLF, HARALD:;;;22500,00
260851408931;97;07;00;;WOLF, HARTMUT:;;;26640,00
270171400214;01;69;00;;WOLF, HARTMUT:;;;2896,61
070153520320;11;80;00;;WOLF, HEIDRUN:;;;19320,00
130653507554;94;30;00;;WOLF, HEIDRUN:;;;19044,00
230865428290;99;43;00;;WOLF, HEIKO:;;;15949,50
030469428284;18;28;00;;WOLF, HEIKO:;;;9675,00
171241429255;14;18;00;;WOLF, HEIN:;;;29110,00
100767422121;18;32;00;;WOLF, HEIN:;;;9675,00
071226405628;98;20;00;;WOLF, HEINZ:;;;28500,00
150648429756;15;03;00;;WOLF, HEINZ:;;;27187,50
120960408936;06;01;00;;WOLF, HEINZ-DIETER:;;;13852,50
090237419746;11;06;21;;WOLF, HELMUT:;;;18000,00
280334430039;99;26;00;;WOLF, HELMUT:;;;26250,00
250368413010;18;71;10;;WOLF, HENNING:;;;9900,00
030962427517;14;06;00;;WOLF, HENRY:;;;17105,00
270951428285;98;80;00;;WOLF, HOLGER:;;;26220,00
190141430041;94;03;00;;WOLF, HOLGER:;;;24000,00
030335420113;11;00;46;;WOLF, HORST:;;;21000,00
041056503622;99;43;00;;WOLF, ILONA:;;;2932,51
240852529729;99;77;00;;WOLF, ILONA:;;;21390,00
200661530042;99;40;00;;WOLF, INES:;;;16747,50
020559400411;94;65;00;;WOLF, INGOLF:;;;19320,00
040150522841;12;51;00;;WOLF, INGRID:;;;16895,72
080567425090;18;35;00;;WOLF, JAN:;;;9675,00
240967430200;97;22;00;;WOLF, JENS:;;;14994,00
140768425056;13;69;00;;WOLF, JO(E)RG:;;;9675,00
250351426560;14;00;44;;WOLF, JOACHIM:;;;28080,00
110136429713;99;43;00;;WOLF, JOACHIM:;;;33000,00
140851416433;94;30;00;;WOLF, JOACHIM:;;;23230,00
151051416818;94;11;00;2741/77, :;WOLF, JU(E)RGEN;1140;MURTZANER RING 64;
151051416818;94;11;00;2741/77, :;WOLF, JU(E)RGEN;1140;MURTZANER RING 64;
270755424957;13;20;00;;WOLF, JU(E)RGEN:;;;24695,00
121057428011;98;84;00;;WOLF, JUERGEN:;;;20182,50
270458421530;12;51;00;;WOLF, JUERGEN:;;;18372,50
030952413744;99;43;00;;WOLF, JUERGEN:;;;19440,00
091145406168;17;00;00;;WOLF, JUERGEN:;;;25500,00
100236429711;99;09;00;;WOLF, JUERGEN:;;;39750,00
171143415351;97;08;00;;WOLF, JUERGEN:;;;28500,00
020445427915;30;48;00;;WOLF, JUERGEN:;;;24480,00
091152426626;30;48;00;;WOLF, JUERGEN:;;;19440,00
180841427936;30;48;00;;WOLF, JUERGEN:;;;25140,00
110435405228;04;26;00;;WOLF, KARL:;;;23250,00
120950419754;11;65;00;;WOLF, KARL-HEINZ:;;;19380,00
140546409536;06;80;00;;WOLF, KARSTEN:;;;23040,00
300768427916;18;32;00;;WOLF, KARSTEN:;;;9675,00
021269407644;05;69;00;;WOLF, KAY:;;;2870,00
280566514522;08;06;00;;WOLF, KERSTIN:;;;15974,00
011264528237;14;80;00;;WOLF, KERSTIN:;;;6849,19
231064507524;01;96;51;;WOLF, KERSTIN:;;;12875,00
300355413110;90;65;40;2012/78,;WOLF, KLAUS;1095;WARNEMU(E)NDER STR. 6;
300355413110;90;65;40;2012/78,;WOLF, KLAUS;1095;WARNEMU(E)NDER STR. 6;
080351411124;04;09;00;;WOLF, KLAUS:;;;25920,00
210956405651;15;00;40;;WOLF, KLAUS:;;;25631,58
281243417749;09;08;00;;WOLF, KLAUS:;;;16125,00
060261416011;99;43;00;;WOLF, KLAUS-UWE:;;;19085,00
270545521812;14;08;00;;WOLF, KRYSTYNA:;;;17274,19
280149427313;94;03;00;;WOLF, KURT:;;;27937,50
220144428275;14;08;00;;WOLF, LOTHAR:;;;27000,00
060643429715;99;43;00;;WOLF, LOTHAR:;;;24000,00
250361418433;97;08;00;;WOLF, LOTHAR:;;;20100,00
160148424974;97;01;00;;WOLF, LUTZ:;;;35250,00
270957421332;12;64;00;;WOLF, LUTZ:;;;19320,00
270451427438;12;29;00;;WOLF, LUTZ-HENRY:;;;23040,00
171067525021;99;40;00;;WOLF, MADELEINE:;;;4680,00
200153424913;98;85;00;;WOLF, MANFRED:;;;23562,00
070831428217;14;40;00;;WOLF, MANFRED:;;;26937,50
181251409572;94;11;00;;WOLF, MANFRED:;;;23940,00
310770505310;04;19;00;;WOLF, MANUELA:;;;3950,00
120362530018;96;15;12;;WOLF, MARCELLA:;;;2380,59
311067424417;94;11;00;;WOLF, MARIO:;;;9675,00
200966521024;18;71;20;;WOLF, MARION:;;;14625,00
110159530064;99;02;00;;WOLF, MARION:;;;18975,00
071053513443;98;82;00;;WOLF, MARTINA:;;;21458,63
181160417753;09;12;00;;WOLF, MATHIAS:;;;17420,00
241160430079;96;15;00;3051/89, E:;WOLF, MATTHIAS;1090;BIESENBROWER STR. 42;
241160430079;96;15;00;3051/89, E:;WOLF, MATTHIAS;1090;BIESENBROWER STR. 42;
211169414131;18;33;00;;WOLF, MATTHIAS:;;;9444,00
050869406736;18;31;00;;WOLF, MATTHIAS:;;;2795,00
181070411227;18;31;00;;WOLF, MATTHIAS:;;;2795,00
090565430047;99;02;00;;WOLF, MATTHIAS:;;;14473,00
250852422808;94;30;00;;WOLF, MATTHIAS:;;;23057,50
240856406910;98;20;00;;WOLF, MICHAEL:;;;24970,00
080664430254;15;14;00;;WOLF, MICHAEL:;;;18150,00
240257428317;14;65;00;;WOLF, MICHAEL:;;;20067,50
280646430150;94;30;00;;WOLF, MICHAEL:;;;24112,26
290960420742;30;47;00;;WOLF, MICHAEL:;;;11447,50
060967416240;18;33;00;;WOLF, MIKE:;;;9600,00
120348527613;14;00;47;;WOLF, MONIKA:;;;19707,50
221152529740;30;83;00;;WOLF, MONIKA:;;;19380,00
070158430033;15;19;00;;WOLF, NORBERT:;;;18371,25
110659413729;17;00;00;;WOLF, NORBERT:;;;24322,50
200768415116;18;35;00;;WOLF, OLAF:;;;9986,44
171251420123;11;00;46;;WOLF, OTTOMAR:;;;23760,00
041146406121;04;06;00;;WOLF, PETER:;;;23187,50
200651426778;14;08;00;;WOLF, PETER:;;;21600,00
130552426915;15;18;00;;WOLF, PETER:;;;25740,00
160257422222;12;00;55;;WOLF, PETER:;;;24667,50
040466429248;14;53;00;;WOLF, PETER:;;;14566,29
270351406920;01;06;00;;WOLF, PETER:;;;23440,00
090556529846;15;06;00;;WOLF, PETRA:;;;17349,55
241262508316;99;43;00;;WOLF, PETRA:;;;16830,00
220259427213;90;65;40;1548/80,;WOLF, RAINER;1130;FRANKFURTER ALLEE 178;
220259427213;90;65;40;1548/80,;WOLF, RAINER;1130;FRANKFURTER ALLEE 178;
090444428282;12;03;00;;WOLF, RAINER:;;;23187,50
131051419017;01;00;40;;WOLF, RAINER:;;;30360,00
280963416467;99;09;00;;WOLF, RAINER:;;;17160,00
051144427454;97;29;00;;WOLF, RAINER:;;;26250,00
130356529837;98;83;00;;WOLF, REGINA:;;;20010,00
220338506112;04;80;00;;WOLF, REGINA:;;;26250,00
091248426620;14;00;45;;WOLF, REINER:;;;30750,00
230353408528;98;81;00;;WOLF, REINHARD:;;;20160,00
051254414718;60;90;00;;WOLF, REINHARD:;;;
051254414718;60;90;00;;WOLF, REINHARD:;;;17090,00
271150413731;94;30;00;;WOLF, REINHARD:;;;24240,00
021168430263;15;00;47;;WOLF, RENE:;;;13875,00
230570409113;18;33;00;;WOLF, RENE:;;;9510,00
280258424998;97;08;00;;WOLF, RENE:;;;18630,00
160570424814;94;03;00;;WOLF, RENE:;;;9510,00
290664429232;99;43;00;;WOLF, ROLAND:;;;17820,00
130368421524;97;01;00;;WOLF, RONNY:;;;15384,00
260733421510;12;54;00;;WOLF, RUDOLF:;;;27187,50
091231406914;97;22;00;;WOLF, RUDOLF:;;;29250,00
270537417775;09;51;00;;WOLF, RUDOLF:;;;21000,00
201152408967;99;13;00;;WOLF, RUEDIGER:;;;22854,19
281235524915;13;26;00;;WOLF, RUTH:;;;23937,50
140263515363;08;53;00;;WOLF, SABINE:;;;15028,23
060849511925;07;00;57;;WOLF, SABINE:;;;23250,00
060443512290;07;06;00;;WOLF, SABINE:;;;22320,00
240960506145;04;12;00;;WOLF, SABINE:;;;14640,41
180459525033;13;77;00;;WOLF, SABINE:;;;15654,28
200949528259;14;80;00;;WOLF, SABINE:;;;17430,00
190669417427;09;08;00;;WOLF, SASCHA:;;;11516,94
070259402752;94;65;00;;WOLF, SIEGFRIED:;;;19262,50
230949507519;99;02;00;;WOLF, SIEGLINDE:;;;20230,53
291052412258;97;06;00;;WOLF, SIEGMAR:;;;23040,00
290565530191;99;02;00;;WOLF, SIMONE:;;;16204,32
230763427414;14;80;00;;WOLF, STEFFEN:;;;15592,50
280859426817;14;20;00;;WOLF, STEFFEN:;;;21440,00
051069428931;18;31;00;;WOLF, STEFFEN:;;;9600,00
180267415446;99;40;00;;WOLF, STEFFEN:;;;16038,00
080267417419;96;15;16;;WOLF, STEFFEN:;;;11016,00
080565416449;98;20;00;;WOLF, STEPHAN:;;;18776,29
260770424032;98;83;00;;WOLF, SVEN:;;;7305,00
140869401918;02;69;00;;WOLF, SVEN:;;;9555,00
291069427317;18;32;00;;WOLF, SVEN:;;;9510,00
190551506133;17;00;00;;WOLF, SYBILLE:;;;18100,50
290861530057;30;31;00;;WOLF, SYLVIA:;;;14210,91
280858422128;98;20;00;;WOLF, THOMAS:;;;22770,00
020670408913;18;34;00;;WOLF, THOMAS:;;;9510,00
220571412112;18;32;00;;WOLF, THOMAS:;;;2795,00
240968413920;18;31;00;;WOLF, THOMAS:;;;9600,00
181264407517;01;96;51;;WOLF, THOMAS:;;;15620,00
140269427524;14;69;00;;WOLF, TORSTEN:;;;13475,00
060969421828;18;31;00;;WOLF, TORSTEN:;;;6705,00
150568409536;18;35;00;;WOLF, TORSTEN:;;;9675,00
120865402747;99;09;00;;WOLF, TORSTEN:;;;11016,00
130343429714;96;15;00;804/83, F:;WOLF, ULRICH;1595;HANS-MARCHWITZA-RING 14;
130343429714;96;15;00;804/83, F:;WOLF, ULRICH;1595;HANS-MARCHWITZA-RING 14;
011055427413;99;55;00;;WOLF, ULRICH:;;;21390,00
100139504310;07;40;00;;WOLF, URSULA:;;;20160,00
070544522796;12;51;00;;WOLF, URSULA:;;;23933,34
160460500863;99;40;00;;WOLF, UTE:;;;14697,03
041263425022;15;11;00;;WOLF, UWE:;;;16830,00
190859428303;14;08;00;;WOLF, UWE:;;;17250,00
261153428251;14;03;00;;WOLF, UWE:;;;22320,00
170957424973;13;18;00;;WOLF, UWE:;;;22367,50
100659424023;99;43;00;;WOLF, UWE:;;;20700,00
200958400855;99;51;00;;WOLF, UWE:;;;20911,45
100358400415;01;51;00;;WOLF, UWE:;;;17250,00
090853526713;14;80;00;;WOLF, VERONIKA:;;;15514,80
090440421817;14;00;40;;WOLF, WALTER:;;;21000,00
110754424944;60;90;00;;WOLF, WILFRIED:;;;
260748404027;03;08;00;;WOLF, WILFRIED:;;;22812,50
220250410327;02;08;00;;WOLF, WILFRIED:;;;18750,00
141048415022;99;51;00;;WOLF, WILFRIED:;;;25145,83
110754424944;60;90;00;;WOLF, WILFRIED:;;;19560,00
290643417419;09;60;00;;WOLF, WILFRIED:;;;33750,00
260749403827;03;51;00;;WOLF, WINFRIED:;;;19750,00
211153406911;05;00;47;;WOLF, WOLFGANG:;;;28020,00
031047406135;17;00;00;;WOLF, WOLFGANG:;;;21295,72
140340430153;18;80;00;;WOLF, WOLFGANG:;;;24891,54
111167416442;99;43;00;;WOLFERSDORF, MARIO:;;;14025,00
220451419053;10;08;00;;WOLFERSDORF, SIEGFRIED:;;;23040,00
221158430143;99;43;00;;WOLFF, ANDRE:;;;21850,00
271067409846;99;77;00;;WOLFF, ANDRE:;;;9872,00
160868408710;97;06;00;;WOLFF, ANDRE:;;;14100,00
220967405648;04;00;00;;WOLFF, ANDREAS:;;;8954,00
201149413626;96;15;08;;WOLFF, BERND-RUEDIGER:;;;24600,00
270667528211;14;54;00;;WOLFF, BIRGIT:;;;12675,00
210642429730;99;53;00;;WOLFF, BURKHARD:;;;22500,00
110271431218;97;22;00;;WOLFF, CARSTEN:;;;2835,00
080565405619;04;00;50;;WOLFF, DIRK:;;;15840,00
150568403038;18;35;00;;WOLFF, DIRK:;;;9825,00
020837529718;99;09;00;;WOLFF, ELSBETH:;;;24750,00
210152411116;07;00;54;;WOLFF, FRANK:;;;19665,00
310829415425;08;41;00;;WOLFF, GERHARDT:;;;42750,00
240763428328;14;00;61;;WOLFF, GUNNAR:;;;19965,00
070370430735;18;32;00;;WOLFF, GUNNAR:;;;2795,00
040751429781;15;15;00;;WOLFF, HELMUT:;;;29880,00
091153405229;04;65;00;;WOLFF, HORST:;;;19620,00
040255405123;99;43;00;;WOLFF, JOACHIM:;;;22685,00
020169403617;03;69;00;;WOLFF, JOERG:;;;11261,61
200244407422;18;80;00;;WOLFF, JOERG-PETER:;;;26568,55
210554412226;07;07;00;;WOLFF, JUERGEN:;;;20700,00
070740403620;03;07;00;;WOLFF, KARL-WILHELM:;;;38250,00
191263414212;08;00;54;;WOLFF, KLAUS-DIETER:;;;19800,00
290354409826;97;01;00;;WOLFF, LUTZ:;;;26220,00
090749407511;98;18;00;;WOLFF, MANFRED:;;;29250,00
211243415360;60;90;00;;WOLFF, MANFRED:;;;
220654406148;04;18;00;;WOLFF, MANFRED:;;;26722,50
231141406437;04;60;00;;WOLFF, MANFRED:;;;22500,00
211243415360;60;90;00;;WOLFF, MANFRED:;;;23400,00
260166405126;04;06;00;;WOLFF, MARIO:;;;15849,00
010365429292;99;51;00;;WOLFF, MARIO:;;;17982,28
240432403433;30;45;00;;WOLFF, MARTIN:;;;21240,00
270267400833;01;06;20;;WOLFF, MATTHIAS:;;;14850,00
180461409138;15;00;46;;WOLFF, MICHAEL:;;;23450,00
190359408015;99;02;00;;WOLFF, MICHAEL:;;;20987,50
070566406921;94;65;00;;WOLFF, MICHAEL:;;;11016,00
021030406922;99;43;00;;WOLFF, PAUL:;;;27000,00
190342408721;06;80;00;;WOLFF, PETER:;;;19500,00
281059403611;03;06;00;;WOLFF, PETER:;;;18195,00
061040422869;12;00;58;;WOLFF, PETER:;;;26250,00
130758406936;99;02;00;;WOLFF, PETER:;;;23460,00
230456406410;04;00;42;;WOLFF, REINHARD:;;;23747,50
081070415158;97;01;00;;WOLFF, RENE:;;;3070,16
091059506146;04;11;00;;WOLFF, SONJA:;;;14030,81
130170420112;11;69;00;;WOLFF, STEFAN:;;;9404,19
220271424728;18;35;00;;WOLFF, STEFFEN:;;;2795,00
071255401546;18;38;00;;WOLFF, UDO:;;;22080,00
301234400748;01;06;24;;WOLFF, ULRICH:;;;22562,50
051065417776;09;06;00;;WOLFF, UWE:;;;15342,75
090735404416;03;00;53;;WOLFF, WALTER:;;;16560,00
250961403331;03;65;00;;WOLFF, WINFRIED:;;;16445,00
140366406119;15;00;45;;WOLFFGRAM, REIK:;;;17902,50
040264415411;08;18;00;;WOLFGANG, FRANK:;;;16830,00
130869415341;08;69;00;;WOLFGANG, KARSTEN:;;;9600,00
100456523611;12;00;58;;WOLFGRAMM, BRIGITTE:;;;15077,75
180752400854;99;26;00;;WOLFGRAMM, HOLGER:;;;27360,00
050748429747;97;06;00;;WOLFGRAMM, HORST:;;;24000,00
230149400852;01;22;00;;WOLFGRAMM, INGO:;;;21300,00
140748402236;97;06;00;;WOLFGRAMM, MANFRED:;;;26937,50
191270405031;18;35;00;;WOLFGRAMM, MARKUS:;;;2795,00
300355529869;99;26;00;;WOLFGRAMM, RITA:;;;21723,87
250659413424;97;01;00;;WOLFGRAMM, ROLAND:;;;18285,00
191246407117;98;82;00;;WOLFRADT, MANFRED:;;;21000,00
160941524911;13;41;00;;WOLFRAM, ANNEROSE:;;;21750,00
220650519014;14;53;00;;WOLFRAM, CHRISTINE:;;;23560,39
300351423944;13;26;00;;WOLFRAM, DIETER:;;;22552,50
210358410848;99;09;00;;WOLFRAM, FRANK:;;;17940,00
030140426718;14;00;57;;WOLFRAM, GERD:;;;26437,50
280736530219;30;63;00;;WOLFRAM, GISELA:;;;17280,00
290554408318;06;40;00;;WOLFRAM, HANS-JUERGEN:;;;23700,00
260239402525;02;19;00;;WOLFRAM, HEINZ:;;;26250,00
240566416459;09;00;44;;WOLFRAM, HEINZ:;;;14616,00
290471422448;18;31;00;;WOLFRAM, INGO:;;;2795,00
180870417112;18;32;00;;WOLFRAM, JAN:;;;2795,00
060170419620;18;40;00;;WOLFRAM, KAI:;;;9720,00
260257500217;99;09;00;;WOLFRAM, KARIN:;;;3987,43
150661524520;18;78;00;;WOLFRAM, KATRIN:;;;16547,83
230669427725;99;43;00;;WOLFRAM, RENE:;;;13285,00
070967407319;94;03;00;;WOLFRAM, SVEN:;;;14944,00
100161427331;14;20;00;;WOLFRAM, ULRICH:;;;21817,50
010769415014;08;69;00;;WOLFRAM, UWE:;;;13075,00
300939410829;07;06;00;;WOLFRAM, WALDEMAR:;;;24000,00
050747428937;98;84;00;;WOLFRUM, HARALD:;;;20250,00
250436418527;10;00;43;;WOLFRUM, KLAUS:;;;27000,00
060559406123;04;07;00;;WOLFSOHN, BERND:;;;22770,00
111159403617;90;65;40;1598/81,;WOLFSTELLER, ROLAND;2080;FU(E)RSTENBERGER STR. 46;
111159403617;90;65;40;1598/81,;WOLFSTELLER, ROLAND;2080;FU(E)RSTENBERGER STR. 46;
030138529718;99;41;00;;WOLGAST, ANNELIESE:;;;25500,00
270243402543;02;00;44;;WOLGAST, MANFRED:;;;29250,00
160450429717;15;80;00;;WOLGAST, PETER:;;;4860,00
021155406723;98;83;00;;WOLGAST, WILFRIED:;;;18630,00
110439429729;97;08;00;;WOLGAST, WOLFGANG:;;;23750,00
180638501811;02;12;00;;WOLK, URSULA:;;;24000,00
020369407428;05;69;00;;WOLKE, ALEXANDER:;;;9675,00
011035400870;99;13;00;;WOLKE, GUENTER:;;;33000,00
090335418616;96;15;00;962/64, M:;WOLKENSTEIN, DIETRICH;1281;DORFSTR. 47G;
090335418616;96;15;00;962/64, M:;WOLKENSTEIN, DIETRICH;1281;DORFSTR. 47G;
251263418610;96;15;00;6480/82, M:;WOLKENSTEIN, HUBERTUS;1142;LUDWIG-RENN-STR. 32;
251263418610;96;15;00;6480/82, M:;WOLKENSTEIN, HUBERTUS;1142;LUDWIG-RENN-STR. 32;
051269418615;05;06;00;;WOLKENSTEIN, JENS:;;;12975,00
230833518611;96;15;00;962/64/1, M:;WOLKENSTEIN, RENATE;1281;DORFSTR. 47G;
230833518611;96;15;00;962/64/1, M:;WOLKENSTEIN, RENATE;1281;DORFSTR. 47G;
010569412257;99;43;00;;WOLKO, DAVID:;;;9510,00
290455417710;09;96;00;;WOLL, THOMAS:;;;21780,00
010470408944;06;69;00;;WOLLANEK, FRANK:;;;9510,00
050756407513;15;09;00;;WOLLANK, GERD:;;;23460,00
030360514517;15;19;00;;WOLLANK, PETRA:;;;17820,00
241258404020;03;00;50;;WOLLATZ, KLAUS:;;;5400,00
130655404022;03;06;00;;WOLLATZ, LOTHAR:;;;20700,00
160749403415;03;06;00;;WOLLATZ, SIEGESMUND:;;;24150,00
300570407522;97;06;00;;WOLLBOLD, RONNY:;;;9037,26
280866401351;01;06;00;;WOLLBRUECK, MIKE:;;;10015,00
100452422768;96;15;07;;WOLLE, JOERG:;;;24790,00
111050400850;01;00;47;;WOLLE, SIEGFRIED:;;;25200,00
101055407518;94;30;00;;WOLLEK, WOLFGANG:;;;23400,00
140362415421;14;69;00;;WOLLENBERG, ANDREAS:;;;19140,00
310171423823;18;35;00;;WOLLENBERG, JAN:;;;2795,00
050847403147;03;20;00;;WOLLENBURG, HANS-JUERGEN:;;;29250,00
190852403314;96;15;22;;WOLLENBURG, WILFRIED:;;;20340,00
220369417411;18;34;00;;WOLLENHAUPT, GERD:;;;6705,00
120155400886;01;80;00;;WOLLENHAUPT, RONALD:;;;17365,00
070646406120;30;40;00;;WOLLENSCHLAEGER, CLAUS:;;;25100,00
250849404019;03;00;49;;WOLLENZIEN, HANS-JUERGEN:;;;17918,75
230554404013;99;43;00;;WOLLENZIEN, HEINZ:;;;23040,00
250866503422;03;02;00;;WOLLENZIN, BARBARA:;;;16173,00
040157403415;97;01;00;;WOLLENZIN, MICHAEL:;;;25530,00
110158500621;99;77;00;;WOLLENZIN, PETRA:;;;18947,17
190161403411;99;43;00;;WOLLENZIN, STEPHAN:;;;23045,00
131261403435;03;02;00;;WOLLER, ANDREAS:;;;16912,50
050471400019;01;69;00;;WOLLER, JAN:;;;2896,61
070161427011;97;07;00;;WOLLER, UWE:;;;22657,48
030139503624;17;00;00;;WOLLERMANN, INGE:;;;23250,00
090439403638;17;00;00;;WOLLERMANN, ULRICH:;;;38062,50
101049404214;03;00;51;;WOLLERT, BERND:;;;24480,00
141051510311;07;12;00;;WOLLERT, ELKE:;;;18815,14
140151404212;03;60;00;;WOLLERT, FRITZ:;;;21600,00
190253404219;99;51;00;;WOLLERT, KLAUS:;;;27420,00
300670430228;18;35;00;;WOLLIN, RENE:;;;2795,00
080358507428;98;18;00;;WOLLINA, ANDREA:;;;20258,55
220561422878;99;02;00;;WOLLINA, FRANK:;;;21780,00
031040429764;99;02;00;;WOLLINJACK, GERHARD:;;;24750,00
230441404412;03;08;00;;WOLLKOWSKI, MANFRED:;;;23125,00
181267404418;18;32;00;;WOLLKOWSKI, RENE:;;;9675,00
120864504418;03;08;00;;WOLLKOWSKI, SIMONE:;;;16802,50
210637418113;10;40;00;;WOLLMANN, ERICH:;;;21750,00
240837424945;13;20;00;;WOLLMANN, ERNST:;;;30250,00
150536525065;13;53;00;;WOLLMANN, HERTA:;;;21750,00
280159530234;98;50;00;;WOLLMANN, IRIS:;;;5038,32
290845429725;97;08;00;;WOLLMANN, KLAUS:;;;24750,00
050459415322;08;80;00;;WOLLMANN, LARS:;;;17163,75
300360500868;99;77;00;;WOLLMANN, LISA-YVONNE:;;;17443,23
020560418117;99;77;00;;WOLLMANN, MICHAEL:;;;19225,00
110956417726;94;65;00;;WOLLMANN, PETER:;;;19262,50
290156406114;04;80;00;;WOLLMANN, RAINER:;;;19780,00
081136527727;10;00;40;;WOLLMANN, RENATE:;;;17737,82
190469409537;18;35;00;;WOLLMANN, THORSTEN:;;;2795,00
181241407418;10;00;41;;WOLLMERSTAEDT, DIETER:;;;26250,00
110442428241;14;80;00;;WOLLNER, DIETMAR:;;;19500,00
240759418530;94;11;00;;WOLLNER, FRANK:;;;20872,50
160362508327;94;11;00;;WOLLNER, KARIN:;;;18150,00
310346528222;14;80;00;;WOLLNER, MONIKA:;;;17910,00
031052401574;01;11;00;;WOLLNER, ROLF:;;;20880,00
050369422262;18;35;00;;WOLLNITZ, MATTHIAS:;;;10825,00
180136423841;99;99;99;::;WOLLNITZA, HORST;7222;HOPFENGARTENSTR. 25;
180136423841;99;99;99;::;WOLLNITZA, HORST;7222;HOPFENGARTENSTR. 25;
200555429995;98;84;00;;WOLLNY, KLAUS-PETER:;;;25500,00
280369406426;18;32;00;;WOLLNY, THOMAS:;;;9675,00
260334402523;30;44;00;;WOLLNY, WERNER:;;;16148,00
220331429716;97;08;00;;WOLLNY, WILLY:;;;39750,00
300744426812;30;37;00;;WOLLSCHLAEGER, ALFRED:;;;20500,00
250763430355;95;45;00;;WOLLSCHLAEGER, RALF:;;;16830,00
020965401313;94;65;00;;WOLNA, ANDREAS:;;;15876,00
100364401326;01;08;00;;WOLNA, AXEL:;;;17435,00
280261401324;99;51;00;;WOLNA, JOERG:;;;20770,00
220862401317;01;06;26;;WOLNA, NORBERT:;;;16239,66
011150505918;99;12;00;;WOLSCHENDORF, HELGA:;;;23246,12
020153419032;99;51;00;;WOLSCHENDORF, PETER:;;;21480,00
280858408246;30;80;00;;WOLSCHKE, HANS-PETER:;;;16560,00
030754503810;15;06;00;;WOLSDORFF, MARIANNE:;;;17352,50
201051406735;99;51;00;;WOLSDORFF, RUEDIGER:;;;24480,00
160549519739;99;77;00;;WOLSKI, BRIGITTE:;;;21600,00
130449424524;94;65;00;;WOLSKI, JOERGEN:;;;23250,00
190170410023;18;31;00;;WOLSKI, LARS:;;;6705,00
140256412235;15;00;46;;WOLSKY, BERND:;;;23460,00
291231412210;07;07;00;;WOLSKY, HORST:;;;40312,50
220734420548;12;00;42;;WOLSTERMANN, HELMUT:;;;27000,00
031263430068;18;38;00;;WOLTER, ANDREAS:;;;16390,00
280967405669;18;35;00;;WOLTER, ANDREAS:;;;9825,00
061254506910;99;02;00;;WOLTER, BEATE:;;;20080,47
120352404616;98;83;00;;WOLTER, BERND:;;;19440,00
040155401918;18;80;00;;WOLTER, BERNFRIED:;;;19440,00
171254406722;98;82;00;;WOLTER, BERNHARD:;;;20160,00
160949400868;01;15;00;;WOLTER, DIETER:;;;25200,00
071166400517;18;71;20;;WOLTER, DIRK:;;;13878,00
310157404212;18;27;00;;WOLTER, ERWIN:;;;23632,50
090658413115;97;01;00;;WOLTER, FRANK:;;;17595,00
271261430315;99;51;00;;WOLTER, FRANK:;;;19965,00
111159400758;03;00;49;;WOLTER, FRED:;;;21770,50
021031424612;99;49;00;;WOLTER, GERHARD:;;;31629,04
121240429725;99;13;00;;WOLTER, GUENTER:;;;35250,00
110951400917;01;02;00;;WOLTER, HANS:;;;24480,00
290440430103;30;63;00;;WOLTER, HANS:;;;16380,00
160136404714;05;60;00;;WOLTER, HANS-JOACHIM:;;;16920,00
011257400817;05;51;00;;WOLTER, HARTMUT:;;;20125,00
280860424712;97;06;00;;WOLTER, HARTMUT:;;;18427,50
230346524918;13;00;41;;WOLTER, HELGA:;;;22437,50
010734400832;01;18;00;;WOLTER, HORST:;;;27000,00
260439510627;07;00;42;;WOLTER, IRMGARD:;;;17940,00
080670426518;18;31;00;;WOLTER, JO((E)RG:;;;6705,00
140247512218;17;00;00;;WOLTER, KARIN:;;;22062,50
070537430121;30;31;00;;WOLTER, KARL-HEINZ:;;;16830,00
060870403822;18;32;00;;WOLTER, KARSTEN:;;;2795,00
081270411530;18;35;00;;WOLTER, LARS:;;;2795,00
100270419031;10;69;00;;WOLTER, MARIO:;;;9555,00
260468404719;05;69;00;;WOLTER, MICHAEL:;;;12725,00
300470422020;18;32;00;;WOLTER, MICHAEL:;;;9510,00
080456402734;02;08;00;;WOLTER, NORBERT:;;;21945,00
051061500628;98;85;00;;WOLTER, PETRA:;;;18187,25
040539504713;05;60;00;;WOLTER, REGINA:;;;17595,00
220540412216;17;00;00;;WOLTER, RUDI:;;;34687,50
151046530173;98;97;00;;WOLTER, SIEGLINDE:;;;18630,00
231252524989;97;01;00;;WOLTER, TAMARA:;;;18728,12
201044429728;99;43;00;;WOLTER, UDO:;;;30000,00
270247423915;13;15;00;;WOLTER, WERNER:;;;20437,50
230153400118;99;43;00;;WOLTER, WOLFGANG:;;;21600,00
280936407274;94;30;00;;WOLTER, WOLFGANG:;;;21000,00
180732418635;10;06;00;;WONDRA, HELMUT:;;;23437,50
190635518617;10;06;00;;WONDRA, RUTH:;;;22437,50
070558418615;94;03;00;;WONDRA, THOMAS:;;;20355,00
110770415028;18;31;00;;WONDRACK, SVEN:;;;6705,00
150660414151;99;02;00;;WONNEBERGER, BERND:;;;20295,00
010653421113;98;20;00;;WONNEBERGER, MICHAEL:;;;28980,00
171269419323;18;35;00;;WONNEBERGER, STEFFEN:;;;9510,00
030833406728;05;12;00;;WONTROBA, WILLI:;;;21937,50
270837406154;04;06;00;;WOOP, GUSTAV:;;;22375,00
300169417759;18;32;00;;WORBIS, SVEN:;;;6705,00
220870422222;18;31;00;;WORBS, ANDRE:;;;6705,00
280143400849;01;55;00;;WORBS, HEINZ-DIETER:;;;24000,00
310751413648;94;30;00;;WORCH, EGBERT:;;;23940,00
290860515111;08;00;45;;WORCH, SABINE:;;;15510,00
020270411937;18;34;00;;WORCH, TORSTEN:;;;9986,44
141269402233;02;06;00;;WORDELL, RENALD:;;;12925,00
061234429743;97;06;00;;WORF, FRITZ:;;;20500,00
140343402721;02;53;00;;WORLITSCHEK, BERND:;;;23760,00
311058430161;94;03;00;;WORM, FRANK:;;;18285,00
030450429826;18;27;00;;WORM, GUENTER:;;;26730,00
090644424999;98;18;00;;WORM, HELMUT:;;;27000,00
050439528266;14;17;00;;WORM, INGRID:;;;23250,00
110944430245;97;08;00;;WORM, PETER:;;;24000,00
261242417511;09;00;51;;WORM, RUDI:;;;29250,00
140670408813;18;35;00;;WORM, STEFFEN:;;;6705,00
190354407259;17;00;00;;WORM, UWE:;;;24420,00
100154409522;99;02;00;;WORM, WINFRIED:;;;25494,19
091264406160;97;08;00;;WORONIECKI, BURKHARD:;;;16089,00
310149412220;07;19;00;;WORRACK, RALF:;;;30285,00
040652429866;15;19;00;;WORSCH, EBERHARD:;;;24840,00
180356519618;15;80;00;;WORSCH, ELKE:;;;26565,00
140754529911;97;08;00;;WORSCH, ELKE:;;;21390,00
280948429710;94;11;00;339/73, :;WORSCH, JU(E)RGEN;1140;HEINRICH-RAU-STR. 66;
280948429710;94;11;00;339/73, :;WORSCH, JU(E)RGEN;1140;HEINRICH-RAU-STR. 66;
040249530200;96;15;00;339/73/2, E:;WORSCH, URSULA;1140;HEINRICH-RAU-STR. 66;
150555429933;15;00;42;;WORSCH, WOLFGANG:;;;28800,00
290861400826;01;06;24;;WORSCHECH, UDO:;;;15618,00
050965404319;97;06;00;;WORTHA, HOLGER:;;;11016,00
171246430167;99;55;00;;WORTMANN, INGO:;;;32250,00
090936402716;02;51;00;;WOSCHNICK, HORST:;;;20250,00
131052407536;30;42;00;;WOSCHOFIUS, HEINZ:;;;21872,50
010363428923;14;00;47;;WOSCIDLO, EKKEHARD:;;;21725,00
200270408015;02;69;00;;WOSCIDLO, JAN:;;;9655,50
280563406948;95;45;00;;WOSINEK, JOERG:;;;16739,52
250151427438;30;48;00;;WOSIPIWO, HEINZ:;;;22990,00
230968407011;18;34;00;;WOSNIZEK, ULF:;;;12300,00
121169404858;04;06;00;;WOTHE, UWE:;;;12000,00
260969424611;97;06;00;;WOTSCHADLO, UWE:;;;14175,00
090663500862;01;20;00;;WOTT, BA(E)RBEL:;;;13149,42
280461400860;01;08;00;;WOTT, HOLGER:;;;18150,00
231050407012;05;03;00;;WOTZINSKI, GUENTER:;;;22350,00
270747401544;01;00;40;3391/89, :;WOTZKA, JO(E)RG-MICHAEL;2520;STEPHAN-JANTZEN-RING 40;
270747401544;01;00;40;3391/89, :;WOTZKA, JO(E)RG-MICHAEL;2520;STEPHAN-JANTZEN-RING 40;
220440406193;04;06;00;;WOTZLAW, DIETRICH:;;;28250,04
190471506344;99;77;00;;WOTZLAW, JANA:;;;3620,00
030248506146;04;06;00;;WOTZLAW, RUTH:;;;20820,00
260461407052;18;27;30;;WOYCZESCHKE, HEIKO:;;;23100,00
200571404421;18;32;00;;WOYDA, THOMAS:;;;2795,00
110759406913;99;12;00;;WOYDE, BERND:;;;19682,50
030962530151;99;02;00;;WOYE, GUNHILD:;;;15600,48
181056404514;04;00;50;;WOYE, HARTMUT:;;;15812,50
060950404825;99;02;00;;WOYTHE, BERND:;;;24420,00
030747419311;10;06;00;;WOYWODT, REINER:;;;20010,00
240549530233;98;83;00;;WOZNIAK, ANDREA:;;;19440,00
181039406198;99;77;00;;WOZNIAK, BRUNO:;;;25500,00
130142529719;94;30;00;;WOZNIAK, ELKE:;;;21500,00
260944429723;94;30;00;;WOZNIAK, FRITZ:;;;21500,00
181039506172;99;77;00;;WOZNIAK, HERTA:;;;21750,00
100461404836;18;33;00;;WOZNIAK, RONALD:;;;19305,00
071069430036;15;69;00;;WOZNIAK, TORSTEN:;;;13010,00
240248430132;30;58;00;;WOZNIAK, WOLFGANG:;;;20125,00
230369415378;18;38;00;;WOZNY, MIRKO:;;;9675,00
Diese Liste beinhaltet die Namen von 90.598 Mitarbeitern des Ministeriums für Staatssicherheit der DDR. Die Liste ist nicht vollständig. Insbesondere Mitarbeiter der Führungsebene sind nicht enthalten.
This is a list of 90.598 members of the secret police of East Germany (Ministry for State Security), the list isn’t complete, because the most of the high Officiers lieke Colonel and higher have destroyed the personal Informations in the last days of Eastern Germany.
| Listen der Stasimitarbeiter-hier findest Du sie! Was bedeuten die Zahlen? |
| 1.Listen der Stasi-Diensteinheiten! Bem.:hier kannst du die Nr.(6-stellig) der Dienststellen heraussuchen. 2.Liste der Stasi-Mitarbeiter (Hauptamtlich) Bem.:Hoffentlich hast Du einen guten Rechner, denn die Liste ist erschreckend lang. Die ersten 6 Ziffern sind das Geburtsdatum + die nächsten 6 Ziffern = Dienstausweisnummer! Die zwei Ziffern hinter dem Geburtsdatum geben das Geschlecht an: 41 und 42 = Männlich, 51 und 52 = Weiblich! Wichtig für suchen und finden, sind die sechs Ziffern in den Semikolon vor den Namen: z.B. ;07;00;44; ! Das ist die Nummer der Dienststelle ! Also du suchst in der Liste der Dienststellen, die Nummer der Dienststelle, die Dich interessiert. Damit gehst Du in die Liste der Mitarbeiter und suchst Dir alle Mitarbeiter der entsprechenden Dienststelle heraus. Ich habe das für mein Wohnort getan und so alle Mitarbeiter gefunden. Ob die Liste Vollständig ist kann ich nicht einschätzen, aber zumindest er/kannte ich einige Exverräter vom Namen her. 3.Liste der OibE (Offiziere im besonderen Einsatz) |
FEMEN Roma against Berlusconi
Femen EuroTour
directed by Alain Margot




![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/nudity-protests/pict26.jpg)
































































































![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict18.jpg)


![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/manning-protest/pict9.jpg) Police officers from U.S. Army Fort George G. Meade walk outside the base gates to talk with journalists and demonstrators protesting in supprt of U.S. Army Private Bradley Manning December 18, 2011 in Fort Meade, Maryland. Manning is accused of disclosing more than 260,000 diplomatic cables, more than 90,000 intelligence reports on the war in Afghanistan and one video of a military helicopter attack to WikiLeaks, a Web site dedicated to publishing secret documents. Getty
Police officers from U.S. Army Fort George G. Meade walk outside the base gates to talk with journalists and demonstrators protesting in supprt of U.S. Army Private Bradley Manning December 18, 2011 in Fort Meade, Maryland. Manning is accused of disclosing more than 260,000 diplomatic cables, more than 90,000 intelligence reports on the war in Afghanistan and one video of a military helicopter attack to WikiLeaks, a Web site dedicated to publishing secret documents. Getty







![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict57.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict34.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict68.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict32.jpg)


![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict77.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict75.jpg) Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. The poster reads: “One for all and all for one”. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky)
Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. The poster reads: “One for all and all for one”. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict72.jpg) Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky)
Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict23.jpg) In this photo taken with a fisheye lens protesters gather during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
In this photo taken with a fisheye lens protesters gather during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict42.jpg) Protesters shout slogans during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
Protesters shout slogans during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict46.jpg) A protester walks in smoke of a smoke bomb during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign [not shown] reads “Such election is a spit at people’s face”. More than 10,000 people have protested in St. Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers say was rigged. (Dmitry Lovetsky)
A protester walks in smoke of a smoke bomb during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign [not shown] reads “Such election is a spit at people’s face”. More than 10,000 people have protested in St. Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers say was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict49.jpg) A protester holds a badminton racket as he shouts slogans during a rally in St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than 10,000 people are protesting in St. Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers say was rigged. (Dmitry Lovetsky)
A protester holds a badminton racket as he shouts slogans during a rally in St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than 10,000 people are protesting in St. Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers say was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict30.jpg) An opposition activist fights with a police officer during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousand people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
An opposition activist fights with a police officer during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousand people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict31.jpg) Riot police detain a protester during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
Riot police detain a protester during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict33.jpg) Protesters seen during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
Protesters seen during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)








![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict12.jpg)


























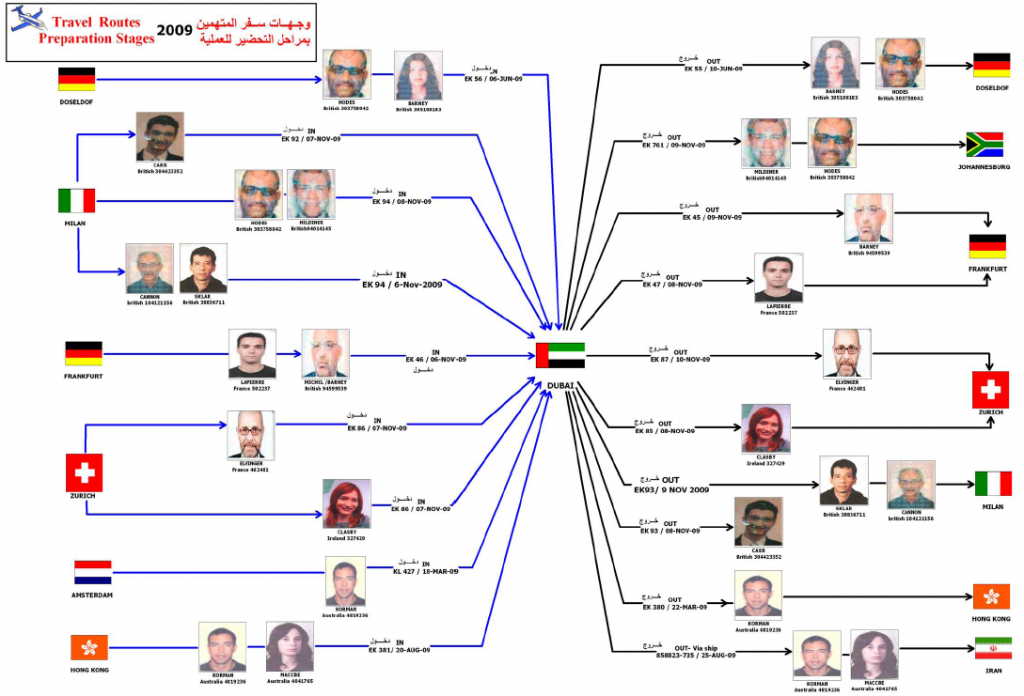
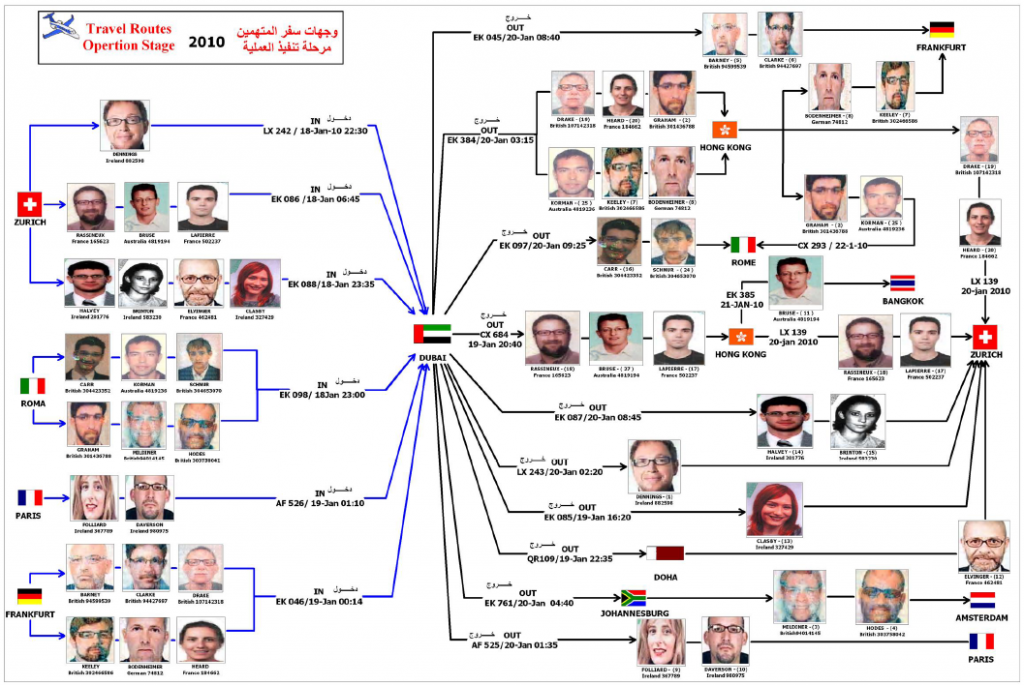

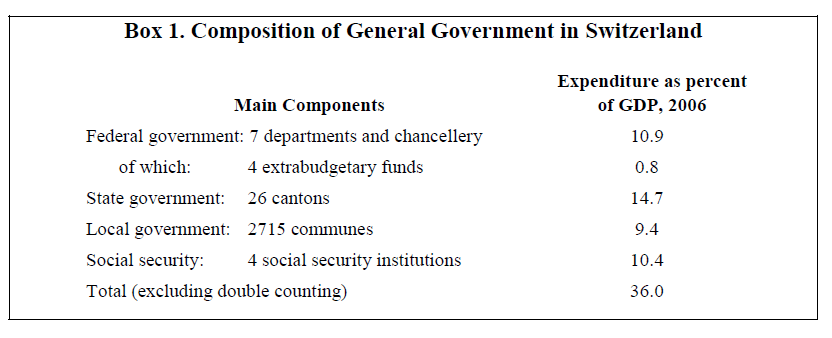


















You must be logged in to post a comment.