Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Tag: Secret To Success
The Secret Network of Rebekah Mercer Exposed
Unveiled – U.S. Government Debated Secret Nuclear Deployments in Iceland
Become a Patron!
True Information is the most valuable resource and we ask you to give back.

During the Cold War the United States never deployed nuclear weapons in Iceland but a recently declassified State Department record shows that U.S. government officials debated whether they should do so, including through secret deployments. A letter from a U.S. ambassador to Iceland in August 1960, published today by the National Security Archive, rejected such proposals, but the revelation of internal discussions on the subject ties in to the broader issue of the practice of U.S. nuclear deployments overseas during the Cold War.
The author of the recently released letter, U.S. Ambassador Tyler Thompson, was aware that Icelandic authorities wondered whether Washington had ever deployed nuclear weapons there. Recognizing that Iceland’s ties to NATO and the Western security system were fragile, he argued that if Reykjavik learned about a secret deployment, it could leave NATO. Furthermore, a “dramatic row” could “be expected to have an unfortunate effect on our friends and allies, to affect adversely our interests as far as neutrals are concerned, and to provide a propaganda field day for our enemies.”
All references to Iceland were deleted from the archival release of Thompson’s letter but his signature and other evidence confirms that the subject matter was Iceland. Further research indicated that nuclear weapons had been an issue in U.S. relations with Iceland since the Korean War when Icelandic officials asked whether the U.S. had deployment plans. Washington did not, but at the time Thompson wrote the letter U.S. officials were exploring nuclear storage options and secret deployments. Moreover, archival documents discovered by an Icelandic historian and published here today demonstrate that the United States had plans for at least one nuclear weapons storage site in the event World War III broke out.
Included in today’s posting are:
▪ A request for assurance in November 1951 by Foreign Minister Bjarni Benediktsson that the United States was not planning an “atomic base” in Iceland
▪ A State Department telegram from December 1951 authorizing the U.S. minister to assure Benediktsson that the United States “has no (rpt no) intention [of] going beyond letter or spirit of [the] defense agreement” which had been negotiated earlier in the year.
▪ A question posed by Foreign Minister Guðmundur Í. Guðmundsson to ambassador Thompson in June 1960: was the United States keeping atomic bombs at Keflavik air base or carrying them through the base in transit?
▪ A draft reply to Guðmundsson’s question indicating that nuclear weapons had not been deployed in Iceland but noting that CINCLANT [Commander-in-Chief, Atlantic Command] had a “requirement” for a nuclear weapons storage site.
That the United States never deployed nuclear weapons to Iceland is a settled issue. In 1998, Robert S. Norris, William Arkin, and this writer published an article in The Bulletin of Atomic Scientists in which they analyzed a recently declassified Defense Department history of U.S. nuclear deployments from 1945 to 1978. The study included several alphabetically arranged lists of nuclear weapons deployments in various parts of the world, including Western European members of NATO. Because many country and place names were excised the writers made educated guesses about some of them. One guess was Iceland. Certain details, such as Strategic Air Command activities during the 1950s, appeared to support the conclusion. The report in The Bulletin was widely publicized and when the news reached Iceland it created a political furor; the Icelandic government quickly denied the premise and the Clinton administration immediately supported the denial. In a significant departure from the usual “neither confirm nor deny” approach to nuclear weapons locations, the U.S. deputy chief of mission in Reykjavik declared that putting Iceland on the list of Cold War nuclear deployment sites was “incorrect.” Further research led to the identification of Iwo Jima as the deployment site.[1]
The fact that the U.S. government never deployed nuclear weapons in Iceland does not mean, however, that it had no nuclear plans for Iceland. Previous research by Valur Ingimundarson and William Arkin demonstrates that during the Cold War Iceland was considered a potential storage site. As Ingimundarson discovered, at the end of the 1950s the U.S. Navy ordered the construction of a facility for storing nuclear depth bombs, an Advanced Underseas Weapons (AUW) Shop at the outskirts of Keflavik airport. The AUW facility was built by local Icelandic workers who thought its purpose was to store torpedoes. Whether Ambassador Thompson knew about it remains to be learned. During the 1980s Arkin reported that a presidential directive from the Nixon period treated Iceland as one of several “Conditional Deployment” locations, where nuclear weapons could be stored in the event of war. An AUW storage facility would make sense in that context. Nevertheless, all such arrangements were kept deeply secret because of the political sensitivity of the U.S. military presence in Iceland.[2]
The heavily excised release of the Thompson letter suggests that the U.S. national security bureaucracy does not presently acknowledge that Iceland figured in American nuclear weapons planning during the Cold War. This is not surprising because the U.S. government has not acknowledged the names of a number of other countries which directly participated in the NATO nuclear weapons stockpile program during the Cold War (and later): Belgium, Greece, Italy, the Netherlands, and Turkey (only West Germany and the United Kingdom have been officially disclosed). As for Iceland’s status as a “conditional” deployment site, even though the horse left the barn years ago in terms of the previous archival releases, time will tell whether declassifiers take that into account when making future decisions on classified historical documents concerning Iceland and nuclear weapons.
 Pictured here is a MK-101 “Lulu” nuclear depth bomb. which the U.S. Navy could have deployed to a storage site at Kefllavik airport, Iceland, in the event of World War III. Weighing 1,200 pounds, with an explosive yield of between 10 and 15 kilotons, the Lulu was in service from the late 1950s to 1971. An air-dropped weapon designed for use by all Navy aircraft, Lulu would have been available to British, Canadian, and Dutch naval forces under NATO nuclear sharing arrangements. (Source: photograph by Mike Fazarckly at Nuclear Weapons: A Guide to British Nuclear Weapons. Thanks to Stephen Schwartz for pointing out these photos.) Pictured here is a MK-101 “Lulu” nuclear depth bomb. which the U.S. Navy could have deployed to a storage site at Kefllavik airport, Iceland, in the event of World War III. Weighing 1,200 pounds, with an explosive yield of between 10 and 15 kilotons, the Lulu was in service from the late 1950s to 1971. An air-dropped weapon designed for use by all Navy aircraft, Lulu would have been available to British, Canadian, and Dutch naval forces under NATO nuclear sharing arrangements. (Source: photograph by Mike Fazarckly at Nuclear Weapons: A Guide to British Nuclear Weapons. Thanks to Stephen Schwartz for pointing out these photos.) |
DOCUMENTS
Document 1: U.S. Legation Reykjavik telegram number 82 to State Department, 18 November 1951, Secret
Source: U.S. National Archives, Record Group 59, Department of State records [RG 59], Central Decimal Files 1950-1954 [CDF], 711.56340B/11-1851
On 5 May 1951, Iceland and the United States secretly signed a defense agreement which became public just two days later. Under the agreement, the United States took over the defense of Iceland, a decision which local elites believed was necessary in light of the Korean War and Iceland’s historically disarmed status. The arrangement was nonetheless contentious for many citizens and by some accounts bordered on illegal; the three major non-Communist parties therefore agreed to keep parliament in recess to minimize controversy (when Iceland joined NATO in 1949, riots had broken out). Two days later, on 7 May, 300 U.S. troops arrived, the first of a contingent which the Icelandic government limited to a tightly sequestered 3,900 troops out of fear of adverse public reaction (to the point that Reykjavik successfully insisted on the exclusion of African-American soldiers).
While the fine print of the defense agreement was still being negotiated, in November 1951 Foreign Minister Benediktsson showed U.S. Chargé d’Affaires Morris N. Hughes a London Times article quoting Senator Edwin Johnson (D-CO) that Iceland, North Africa, and Turkey were better deployment sites for atomic weapons than the United Kingdom. To assuage the foreign minister’s concern that Communist Party members and other critics would exploit Johnson’s statement, Hughes recommended “official reassurance” that the United States had no plans to deploy atomic weapons in Iceland.
Document 2: U.S. Legation Reykjavik telegram number 85 to State Department, 24 November 1951, Secret
Source: RG 59, CDF, 711.56340B/11-2451
A few days after the above exchange, Benediktsonn told Hughes that he had showed him the Times article so he could tell “critics and worried colleagues” that he had immediately sought U.S. reassurances about U.S. atomic plans. When the foreign minister wondered whether an “appropriate quarter” could provide “some reassurance,” Hughes agreed to inform the State Department “of his anxiety.” The reference to McGaw is to General Edward John McGaw, the first commander of the Iceland Defense Force, the U.S. unified command which provided for Iceland’s military security from 1951 to 2006.
Document 3: U.S. Legation Reykjavik Despatch 198 to State Department, ““First Icelandic Reaction to Senator Johnson’s Statement on Atomic Bases,” 27 November 1951, Secret
Source: RG 59, CDF, 711.56340B/11-2751
Chargé Hughes reported that the Communist newspaper, Thjodviljinn [Will of the Nation] had commented on Senator Johnson’s statement, noting that the “Americans feel that it does not matter if Iceland should be subjected to the attack and horrors such bases would bring
upon the nation.”
Document 4: U.S. Legation Reykjavik telegram number 97 to State Department, 20 December 1951, Secret
Source: RG 59, CDF, 711.56340B/12-1951
With no answer to his question about atomic bases, Benediktsonn asked Hughes again about the problem, noting that Communist opponents could “embarrass” him.
Document 5: State Department telegram 98 to U.S. Legation Reykjavik, 21 December 1951, Top Secret
Source: RG 59, CDF, box 3180, 711.56340B/11-2451
Benediktsonn’s second query was the charm. Responding to Hughes’ message, a State Department telegram sent under the name of Secretary of State Dean Acheson warned that any public statements would violate the policy to “not deny or affirm rumors” about the locations of atomic weapons. That was a military necessity to prevent the Soviet Union from determining the “pattern” of U.S. defenses. Nevertheless, the Department authorized Hughes to inform Benediktsonn confidentially that the United States would “make no move without [the] full consultation and agreement” of Iceland’s government.
Document 6: U.S. Legation Reykjavik Despatch 238 to State Department, “Further Reaction to Threatened Use of Iceland as Atomic Base,” 29 December 1951, Secret
Source: RG 59, CDF, box 3180, 711.56340B/12-2951
Hughes provided a fuller account of his meeting with Benediktsonn on 20 December and of his efforts during the holidays to pass on the gist of the State Department message to the permanent undersecretary and then to the foreign minister himself at a dinner. Whether there were any follow-up discussions remains unclear because the records covering the 1952-1954 period in the 711.56340B decimal file series are missing from box 3181.[3]
Document 7: U.S. Department of State Executive Secretariat, “Top Secret Daily Staff Summary,” 22 June 1960, top secret, excerpt
Source: RG 59, Executive Secretariat, Daily Staff Summary, 1944-1971, box 45, Daily Staff Summary, Top Secret, June 1960
According to the State Department summary of telegram 367 from the U.S. Embassy in Iceland, in light of the recent U-2 crisis, Foreign Minister Guðmundur Í. Guðmundsson asked Ambassador Thompson whether the United States had used Keflavik air base for U-2 flights, had stored nuclear weapons there or had moved them through Keflavik. While the Foreign Minister had not asked for assurances about advance agreement, according to the summary Thompson “feels that the storage of atomic warheads in Iceland without the latter’s prior agreement would be a mistake and suggests that, if we have no intention to do this, we so inform the Icelandic Government without awaiting its request to this effect.” This conversation is cited on the bottom of page 2 of the Tyler Thompson letter (Document 8) with the references to Iceland excised.
Documents 8A-B: Answer to Gudmundsson’s Questions
A: Draft telegram to U.S. Embassy Iceland, 24 June 1960, Top Secret
B: Draft telegram to U.S. Embassy Iceland, circa 1 July 1960, Top Secret
Source: RG 59, Bureau of European Affairs, Office of Atlantic Political and Military Affairs, Subject Files, 1953-1962, box 11, Iceland Keflavick [sic] Air Base
In response to Guðmundsson’s questions about U-2 flights and nuclear weapons, State Department officials prepared a response; the finished, delivered version remains classified in State Department decimal files, but drafts of the response are available, of which the one dated 1 July 1960 is probably close to what was sent. The ambassador could assure the foreign minister that the U.S. had not stored nuclear weapons in Iceland or shipped them through Keflavik airbase. But this information was not for public consumption because of the U.S. government’s “neither confirm nor deny” policy. In response to Thompson’s suggestion that the U.S. pledge that it would consult the Icelandic government in advance about nuclear weapons deployments, the State Department believed this would “not [be] desirable.” Before any assurances could be given the subject would need careful study in Washington; if asked for such assurances, Thompson was to tell Guðmundsson that he needed to seek instructions. Thompson’s letter (below) does not indicate that a follow-up conversation with Guðmundsson had occurred, only the possibility that he might ask the question about nuclear deployments again.
The 24 June draft telegram mentions the CINCLANT requirement for a nuclear weapons storage site and its ongoing construction but that item was dropped from the 1 July draft, perhaps because of its sensitivity. The final version of the telegram remains classified but has been requested.
Document 9: Ambassador Tyler Thompson to Ivan White, 5 August 1960, top secret, excised copy
Source: RG 59, DF 1960-1963, 711.5611-8560
Probably to respond to the issues raised by Guðmundsson’s questions, Deputy Assistant Secretary of State for European Affairs Ivan White sent Thompson a letter on 21 July 1960. It was one of those “official informal” communications then used by State Department officials to communicate with its embassies on matters that were too complex and sensitive to handle by telegram. White’s letter has not surfaced and is not indexed in the State Department decimal files. But judging from the tenor of Thompson’s reply, White may have asserted that the U.S. government was free to deploy nuclear weapons in Iceland without securing the agreement of Reykjavik. If that was the case, the Eisenhower administration had departed from the Acheson policy of assuring “full consultation and agreement.” It is possible that the previous ambassador, John Muccio, was the individual whom Thompson described as “recommending against prior consultation” out of fear that information about the deployment would leak to the Soviets.
If war was imminent or had broken out, Thompson believed that a secret emergency deployment would be permissible, but under peacetime circumstances he recommended seeking Iceland’s consent. Given that the Soviets probably suspected that Iceland was already a storage site, Thompson believed that it would be worse if the government of Iceland discovered a secret deployment; that would produce a diplomatic crisis, including Iceland’s possible withdrawal from NATO under protest. Moreover, “from the point of view of respect for the rights and sovereignty of [Iceland], the fact that it might not agree to the storage of nuclear weapons here could be considered as making prior consultations all the more necessary.”
To make deployments technically possible, Thompson suggested the construction of storage areas, but consulting the government if Washington ever wanted to use them. If war was approaching it would be possible to deploy weapons under emergency conditions because the possibility of objections would be “minimized.” If, however, the United States wanted to use the storage areas for actual deployments it should consult the Icelandic government. Thompson may not have been aware of the SACLANT storage site mentioned in the draft telegram cited above.
Thompson’s letter met with some internal criticism, mainly on the first page: a handwritten “no” next to his observation that U.S. nuclear weapons storage in NATO countries depends on the agreement of the country concerned; a question mark next to the comment about Canadian consent for storage of nuclear weapons in Canada; a comment “No! Canada on record,” suggesting that Ottawa would accept clandestine U.S. storage; and another comment which is harder to decipher: “tech … doesn’t get UK OK.”
For the archival release of this letter the State Department and the Defense Department justified the excision on two grounds. The State Department cited Section 3.3 (b) (6) of Executive Order 13526 – that declassification would “reveal information, including foreign government information, that would cause serious harm to relations between the United States and a foreign government, or to ongoing diplomatic activities of the United States.” The Defense Department cited exemption (b) (6), ruling that declassification would “reveal formally named or numbered U.S. military war plans that remain in effect, or reveal operational or tactical elements of prior plans that are contained in such active plans.” Whether the declassification of a document which is well over half a century old could have such impacts on U.S. diplomacy or military planning appears highly doubtful.
Notes
[1]. William Arkin, Robert S. Norris, and William Burr, “They Were,” The Bulletin of the Atomic Scientists, November –December 1999, pp. 25-35; Arkin, Norris, and Burr, “How Much Did Japan Know,” The Bulletin of the Atomic Scientists, January-February 2000, pp. 11-13, 78-79.
[2] . Valur Ingimundarson, The Rebellious Ally: Iceland, the United States, and the Politics of Empire, 1945-2006(Dordrech, The Netherlands, 2011), 86; William Arkin, “Iceland Melts,” The Bulletin of the Atomic Scientists (50) January-February 2000, p. 80.
[3]. One relevant item that could show up in box 3181 was published in the Foreign Relations of the United States: a memorandum to the Deputy Under Secretary of State on “Additional Military Operating Requirements in Iceland,” dated 12 June 1952. It briefly recounts the discussions with the Icelandic foreign minister and mentions a NATO request to the U.S. and the Government of Iceland for a strategic air base in Iceland, but any further discussion of nuclear weapons was excised in the FRUS volume.
Us Government Jobs, Us Government Type, Us Government Shutdown, Us Government Spending, Us Government Budget, Us Government Security Clearance, Us Government Debt, Us Government News, Us Government Bonds, Us Government Passport, Us Government Agencies, Us Government Auctions, Us Government Accountability Office, Us Government And Politics, Us Government Articles, Us Government Annual Budget, Us Government And Politics Apex Answers, Us Government Ap Test, Us Government Arms Contracts, Us Government Assets, Us Government Budget, Us Government Bonds, Us Government Branches, Us Government Budget 2017, Us Government Budget 2016, Us Government Book, Us Government Bookstore, Us Government Bond Rates, Us Government Buildings, Us Government Bids, Us Government Contracts, Us Government Current Events, Us Government Corruption, Us Government Corporations, Us Government Checks And Balances, Us Government Credit Rating, Us Government Crash Course, Us Government Copyright Website, Us Government Chart, Us Government Clearance, Us Government Debt, Us Government Deficit, Us Government Definition, Us Government Debt To Gdp, Us Government Debt Clock, Us Government Data, Us Government Diagram, Us Government During Ww2, Us Government Documents, Us Government Definition Of Terrorism, Us Government Expenditures, Us Government Employees, Us Government Explained, Us Government Executive Branch, Us Government Employee Salaries, Us Government Exam Review, Us Government Employment, Us Government Education, Us Government Experiments, Us Government Expenditures 2016, Us Government Fiscal Year, Us Government Forms, Us Government For Dummies, Us Government Final Exam, Us Government Facts, Us Government Final Exam Study Guide, Us Government Free Credit Report, Us Government Funding, Us Government Flow Chart, Us Government Fiscal Year 2017, Us Government Grants, Us Government Grant Department, Us Government Gold Coins, Us Government Games, Us Government Gsa, Us Government Gs Pay Scale, Us Government Grant Money, Us Government Global Entry, Us Government Green Card, Us Government Gdp, Us Government Holidays, Us Government Hiring Freeze, Us Government Holidays 2017, Us Government Hierarchy, Us Government History, Us Government Healthcare, Us Government Healthcare Spending, Us Government Hacked, Us Government Health Insurance, Us Government House, Us Government Internships, Us Government Income, Us Government Id, Us Government Interest Reported As Dividends, Us Government Interest, Us Government Interest Taxable, Us Government Irs, Us Government Issues, Us Government Issued Id, Us Government Intelligence Agencies, Us Government Jobs, Us Government Jobs Abroad, Us Government Jobs In Japan, Us Government Jobs In Italy, Us Government Jobs In Germany, Us Government Judicial Branch, Us Government Jobs In Europe, Us Government Jeopardy, Us Government Jobs In Utah, Us Government Jobs In California, Us Government Killed Mlk, Us Government Kahoot, Us Government Kill List, Us Government Killed Dog, Us Government Killed Family Dog, Us Government Key Terms, Us Government Killed Jfk, Us Government Kaspersky, Us Government Kodi, Us Government Kenya Travel, Us Government Logo, Us Government Line Of Succession, Us Government License Plates, Us Government Leaders, Us Government Land For Sale, Us Government Loans, Us Government Legislative Branch, Us Government Laws, Us Government Lies, Us Government Leaks, Us Government Mint, Us Government Mileage Rate, Us Government Manual, Us Government Mileage Rate 2017, Us Government Medicare, Us Government Movies, Us Government Military Spending, Us Government Memes, Us Government Module 3 Dba, Us Government Mind Control, Us Government News, Us Government Net Worth, Us Government News Today, Us Government Number, Us Government Name, Us Government Notes, Us Government No Call List, Us Government News Articles, Us Government National Debt, Us Government Number Of Employees, Us Government Org Chart, Us Government Officials, Us Government Organizational Chart, Us Government Offices, Us Government Obligations, Us Government Organizations, Us Government Owned Companies, Us Government Official Mail, Us Government Online Textbook, Us Government Officials 2017, Us Government Passport, Us Government Per Diem, Us Government Printing Office, Us Government Passport Renewal, Us Government Pay Scale, Us Government Plates, Us Government Positions, Us Government Phone Number, Us Government Pension, Us Government Procurement, Us Government Quizlet, Us Government Quiz, Us Government Questions, Us Government Quotes, Us Government Quarters, Us Government Quizlet Chapter 2, Us Government Questions And Answers, Us Government Questions Test Practice, Us Government Quizlet Chapter 8, Us Government Quizlet Chapter 4, Us Government Revenue, Us Government Regents, Us Government Review, Us Government Revenue 2016, Us Government Retirement, Us Government Ranks, Us Government Renew Passport, Us Government Rfp, Us Government Revenue Sources, Us Government Regulations, Us Government Shutdown, Us Government Spending, Us Government Security Clearance, Us Government Shutdown 2017, Us Government System, Us Government Surplus, Us Government Spending Breakdown, Us Government Securities, Us Government Salaries, Us Government Savings Bonds, Us Government Type, Us Government Textbook, Us Government Travel Warnings, Us Government Tax Forms, Us Government Travel, Us Government Textbook Pdf, Us Government Test, Us Government Tax Revenue, Us Government Time, Us Government Trivia, Us Government Unclaimed Money, Us Government Unit 4, Us Government Unit 5, Us Government Unit 3, Us Government Unit 2 Quizlet, Us Government Unit 1, Us Government Ufo, Us Government Unit 5 Test Answers, Us Government Unit 1 Test, Us Government Unit 3 Test, Us Government Vocabulary, Us Government Visa, Us Government Vehicles, Us Government Videos, Us Government Vehicle Auction, Us Government Value Of Human Life, Us Government Vs German Government, Us Government Vs Ancient Rome, Us Government Venezuela, Us Government Veterans, Us Government Website, Us Government Worksheets, Us Government Wiki, Us Government Weather, Us Government Weed, Us Government Word Search, Us Government Whip, Us Government White Papers, Us Government Web Standards, Us Government Waste, Us Government X Files, Us Government Xml, Us Government Keystone Xl Pipeline, Us Government Windows Xp, Us Government Planet X, Us Government Yearly Budget, Us Government Yield Curve, Us Government Youtube, Us Government Yearly Revenue, Us Government Yields, Us Government Yellowbook, Us Government Year End, Us Government Youth Programs, Us Government Yearly Spending, Us Government Yemen, Us Government Zombie Plan, Us Government Zip Codes, Us Government Zombie, Us Government Zip Code Database, Us Government Zika, Us Government Zombie Protocol, Us Government Zero Coupon Bonds, Us Government Zombie Contingency Plan, Us Government Zombie Survival Guide, Us Government Zip Code Information, Secret Life Of Pets, Secret Service, Secret Garden, Secret World Legends, Secret Flying, Secret Life Of Bees, Secret Life Of Pets Cast, Secret Life Of The American Teenager, Secret Squirrel, Secret Shopper, Secret Agent Man, Secret Admirer, Secret Aardvark, Secret Agent, Secret Annex, Secret And Lies, Secret Agent Man Song, Secret App, Secret Asian Man, Secret Agent Man Lyrics, Secretbuilders, Secret Book, Secret Beach Kauai, Secret Beach, Secret Ballot, Secret Box, Secret Beach Maui, Secret Bay Dominica, Secret Base, Secret Band, Secret Circle, Secret Church, Secret Caverns, Secret Classroom Superpowers, Secret Codes, Secret Clinical Strength, Secret Clearance, Secret Circle Cast, Secret Conversations Facebook, Secret Cameras, Secret Deodorant, Secret Definition, Secret Diary Of A Call Girl, Secret Door, Secret Deodorant Coupons, Secret Diary, Secret Deodorant Commercial, Secret Decoder Ring, Secret Daughter, Secret Door Lyrics, Secret Empire, Secret Extensions, Secret Escapes, Secret Empire #1, Secret Empire Reading Order, Secret Entourage, Secret Empire #0, Secret Empire #2, Secret Eaters, Secret Emoji, Secret Flying, Secret Forest, Secret Forest Ep 11, Secret Falls Kauai, Secret Flask, Secret Formula, Secret Facebook Group, Secret Frappuccino, Secret For The Mad Lyrics, Secret Falls, Secret Garden, Secret Garden Song, Secret Garden Movie, Secret Garden Cafe, Secret Garden Musical, Secret Garden Lyrics, Secret Garden Denver, Secret Garden Book, Secret Google Games, Secret Garden Miami, Secret Hitler Rules, Secret Hitler Game, Secret History Of Twin Peaks, Secret Hitler Online, Secret Hair Extensions, Secret Handshake, Secret History, Secret Hotel Deals, Secret Heart, Secret Hiding Places, Secret In Their Eyes, Secret In Spanish, Secret Ingredient, Secret Island, Secret In Their Eyes Cast, Secret Invasion, Secret In N Out Menu, Secret Invisible Solid, Secret Island In Texas, Secret In French, Secret Jardin, Secret Jewels, Secret Journal, Secret Jobs, Secret Jamaica, Secret Jieun, Secret Jardin Lodge, Secret Journey Police, Secret Journey To Planet Serpo, Secret Jardin Dr90, Secret Kpop, Secret Keeper Girl, Secret Keeper, Secret Key, Secret Korean Drama, Secret Knock, Secret Knowledge, Secret Krabby Patty Formula, Secret Key Starting Treatment Essence, Secret Kingdom, Secret Life Of Pets, Secret Life Of Bees, Secret Life Of Pets Cast, Secret Life Of The American Teenager, Secret Love Song, Secret Life Of Walter Mitty, Secret Lab Chair, Secret Life Of An American Teenager Cast, Secret Language, Secret Life Of Pets Imdb, Secret Menu, Secret Menu Items, Secret Mage, Secret Menu Starbucks, Secret Menu In N Out, Secret Messages, Secret Meaning, Secret Movie, Secret Mountain Fort Awesome, Secret Mage Deck, Secret Nails, Secret Nyc, Secret Netflix, Secret Nail Salon, Secret Names, Secret Netflix Codes, Secret Numbers, Secret News, Secret Nature From Jeju Peeling Gel, Secret Nation, Secret Of Mana, Secret Of Nimh, Secret Of The Snowy Peaks, Secret Of The Cedars, Secret Of Kells, Secret Of Evermore, Secret Of The Wings, Secret Of Moonacre, Secret Of Mana Rom, Secret Of Mana 2, Secret Pizza, Secret Police, Secret Project Robot, Secret Place, Secret Passion Fruit, Secret Power, Secret Passages, Secret Pizza Party, Secret Paladin, Secret Place Lyrics, Secret Quotes, Secret Question, Secret Quest, Secret Questions To Ask, Secret Questions To Ask Siri, Secret Quests Ffxv, Secret Quests Skyrim, Secret Qr Codes, Secret Questions To Ask Alexa, Secret Quote Spongebob, Secret Romance, Secret Resorts, Secret Recipe, Secret Rooms, Secret Rare Pokemon Cards, Secret Rainbow Hair, Secret Rare Ultra Ball, Secret Rendezvous, Secret Relationship, Secret Roku Channels, Secret Service, Secret Squirrel, Secret Shopper, Secret Societies, Secret Synonym, Secret Starbucks Menu, Secret Service Jobs, Secret Sandwich Society, Secret Sisters, Secret Shopper Jobs, Secret Treasures, Secret Treasures Sleepwear, Secret Tunnel, Secret Things, Secret Tunnel Song, Secret The Pierces, Secret Thesaurus, Secret Travel, Secret Treasures Bra, Secret To Success, Secret Underground Cities, Secret Us Weapons, Secret Underground Bases, Secret Universe Of Names, Secret Underground, Secret Underground Medicine, Secret Upgrades Office Space, Secret Us Bases, Secret Us Military Bases, Secret Unscented, Secret Variety Training, Secret Village Of The Spellcasters, Secret Video Recorder, Secret Variety Training Ep 2, Secret Vault, Secret Vault 81, Secret Veneers, Secret Voice Recorder, Secret Video, Secret Volume, Secret World Legends, Secret Window, Secret Wood, Secret Wars, Secret Wood Rings, Secret World Legends Release Date, Secret World Of Arrietty, Secret Weapon, Secret Wars 2015, Secret Warriors, Secret X Folder, Secret Xtians, Secret Xscape, Secret X Folder Comic, Secret X, Secret Xbox One Gamerpics, Secret Xtend, Secret Xbox One Games, Secret Xbox One Codes, Secret X Folder Webtoon, Secret Youtube, Secret Yeahu, Secret Yellowstone, Secret Young Justice, Secret Youtube Videos, Secret Yosemite, Secret Youtube Tricks, Secret Youtube Website, Secret Yumiverse, Secret Yosemite Spots, Secret Zoo Series, Secret Zoo, Secret Zoo Book, Secret Zinger, Secret Zombies Calling Card, Secret Zodiac Sign, Secret Zion Hikes, Secret Zone, Secret Zombies Challenge Infinite Warfare, Secret Zombie Challenge, Secret Life Of Pets, Secret Service, Secret Garden, Secret World Legends, Secret Flying, Secret Life Of Bees, Secret Life Of Pets Cast, Secret Life Of The American Teenager, Secret Squirrel, Secret Shopper, Secret Agent Man, Secret Admirer, Secret Aardvark, Secret Agent, Secret Annex, Secret And Lies, Secret Agent Man Song, Secret App, Secret Asian Man, Secret Agent Man Lyrics, Secretbuilders, Secret Book, Secret Beach Kauai, Secret Beach, Secret Ballot, Secret Box, Secret Beach Maui, Secret Bay Dominica, Secret Base, Secret Band, Secret Circle, Secret Church, Secret Caverns, Secret Classroom Superpowers, Secret Codes, Secret Clinical Strength, Secret Clearance, Secret Circle Cast, Secret Conversations Facebook, Secret Cameras, Secret Deodorant, Secret Definition, Secret Diary Of A Call Girl, Secret Door, Secret Deodorant Coupons, Secret Diary, Secret Deodorant Commercial, Secret Decoder Ring, Secret Daughter, Secret Door Lyrics, Secret Empire, Secret Extensions, Secret Escapes, Secret Empire #1, Secret Empire Reading Order, Secret Entourage, Secret Empire #0, Secret Empire #2, Secret Eaters, Secret Emoji, Secret Flying, Secret Forest, Secret Forest Ep 11, Secret Falls Kauai, Secret Flask, Secret Formula, Secret Facebook Group, Secret Frappuccino, Secret For The Mad Lyrics, Secret Falls, Secret Garden, Secret Garden Song, Secret Garden Movie, Secret Garden Cafe, Secret Garden Musical, Secret Garden Lyrics, Secret Garden Denver, Secret Garden Book, Secret Google Games, Secret Garden Miami, Secret Hitler Rules, Secret Hitler Game, Secret History Of Twin Peaks, Secret Hitler Online, Secret Hair Extensions, Secret Handshake, Secret History, Secret Hotel Deals, Secret Heart, Secret Hiding Places, Secret In Their Eyes, Secret In Spanish, Secret Ingredient, Secret Island, Secret In Their Eyes Cast, Secret Invasion, Secret In N Out Menu, Secret Invisible Solid, Secret Island In Texas, Secret In French, Secret Jardin, Secret Jewels, Secret Journal, Secret Jobs, Secret Jamaica, Secret Jieun, Secret Jardin Lodge, Secret Journey Police, Secret Journey To Planet Serpo, Secret Jardin Dr90, Secret Kpop, Secret Keeper Girl, Secret Keeper, Secret Key, Secret Korean Drama, Secret Knock, Secret Knowledge, Secret Krabby Patty Formula, Secret Key Starting Treatment Essence, Secret Kingdom, Secret Life Of Pets, Secret Life Of Bees, Secret Life Of Pets Cast, Secret Life Of The American Teenager, Secret Love Song, Secret Life Of Walter Mitty, Secret Lab Chair, Secret Life Of An American Teenager Cast, Secret Language, Secret Life Of Pets Imdb, Secret Menu, Secret Menu Items, Secret Mage, Secret Menu Starbucks, Secret Menu In N Out, Secret Messages, Secret Meaning, Secret Movie, Secret Mountain Fort Awesome, Secret Mage Deck, Secret Nails, Secret Nyc, Secret Netflix, Secret Nail Salon, Secret Names, Secret Netflix Codes, Secret Numbers, Secret News, Secret Nature From Jeju Peeling Gel, Secret Nation, Secret Of Mana, Secret Of Nimh, Secret Of The Snowy Peaks, Secret Of The Cedars, Secret Of Kells, Secret Of Evermore, Secret Of The Wings, Secret Of Moonacre, Secret Of Mana Rom, Secret Of Mana 2, Secret Pizza, Secret Police, Secret Project Robot, Secret Place, Secret Passion Fruit, Secret Power, Secret Passages, Secret Pizza Party, Secret Paladin, Secret Place Lyrics, Secret Quotes, Secret Question, Secret Quest, Secret Questions To Ask, Secret Questions To Ask Siri, Secret Quests Ffxv, Secret Quests Skyrim, Secret Qr Codes, Secret Questions To Ask Alexa, Secret Quote Spongebob, Secret Romance, Secret Resorts, Secret Recipe, Secret Rooms, Secret Rare Pokemon Cards, Secret Rainbow Hair, Secret Rare Ultra Ball, Secret Rendezvous, Secret Relationship, Secret Roku Channels, Secret Service, Secret Squirrel, Secret Shopper, Secret Societies, Secret Synonym, Secret Starbucks Menu, Secret Service Jobs, Secret Sandwich Society, Secret Sisters, Secret Shopper Jobs, Secret Treasures, Secret Treasures Sleepwear, Secret Tunnel, Secret Things, Secret Tunnel Song, Secret The Pierces, Secret Thesaurus, Secret Travel, Secret Treasures Bra, Secret To Success, Secret Underground Cities, Secret Us Weapons, Secret Underground Bases, Secret Universe Of Names, Secret Underground, Secret Underground Medicine, Secret Upgrades Office Space, Secret Us Bases, Secret Us Military Bases, Secret Unscented, Secret Variety Training, Secret Village Of The Spellcasters, Secret Video Recorder, Secret Variety Training Ep 2, Secret Vault, Secret Vault 81, Secret Veneers, Secret Voice Recorder, Secret Video, Secret Volume, Secret World Legends, Secret Window, Secret Wood, Secret Wars, Secret Wood Rings, Secret World Legends Release Date, Secret World Of Arrietty, Secret Weapon, Secret Wars 2015, Secret Warriors, Secret X Folder, Secret Xtians, Secret Xscape, Secret X Folder Comic, Secret X, Secret Xbox One Gamerpics, Secret Xtend, Secret Xbox One Games, Secret Xbox One Codes, Secret X Folder Webtoon, Secret Youtube, Secret Yeahu, Secret Yellowstone, Secret Young Justice, Secret Youtube Videos, Secret Yosemite, Secret Youtube Tricks, Secret Youtube Website, Secret Yumiverse, Secret Yosemite Spots, Secret Zoo Series, Secret Zoo, Secret Zoo Book, Secret Zinger, Secret Zombies Calling Card, Secret Zodiac Sign, Secret Zion Hikes, Secret Zone, Secret Zombies Challenge Infinite Warfare, Secret Zombie Challenge, Nuclear Bomb, Nuclear Energy, Nuclear Fusion, Nuclear War, Nuclear Family, Nuclear Fission, Nuclear Stress Test, Nuclear Option, Nuclear Triad, Nuclear Medicine, Nuclear Arms Race, Nuclear Attack, Nuclear Accidents, Nuclear Assault, Nuclear Arsenal, Nuclear Age, Nuclear Arms Race Cold War, Nuclear Apocalypse, Nuclear Alarm, Nuclear Annihilation, Nuclear Bomb, Nuclear Blast, Nuclear Blast Radius, Nuclear Bomb Test, Nuclear Bunker, Nuclear Bomb Shelter, Nuclear Binding Energy, Nuclear Blast Records, Nuclear Bone Scan, Nuclear Bomb Video, Nuclear Chemistry, Nuclear Clock, Nuclear Countries, Nuclear Chemistry Worksheet, Nuclear Charge, Nuclear Codes, Nuclear Cataract, Nuclear Chain Reaction, Nuclear Cardiology, Nuclear Cooling Tower, Nuclear Definition, Nuclear Decay, Nuclear Disasters, Nuclear Deterrence, Nuclear Decay Worksheet, Nuclear Disarmament, Nuclear Dna, Nuclear Detonation, Nuclear Decay Worksheet Answers, Nuclear Division, Nuclear Energy, Nuclear Explosion, Nuclear Energy Definition, Nuclear Engineering, Nuclear Envelope, Nuclear Engineer Salary, Nuclear Energy Pros And Cons, Nuclear Energy Examples, Nuclear Explosion Gif, Nuclear Equations, Nuclear Fusion, Nuclear Family, Nuclear Fission, Nuclear Fusion Definition, Nuclear Football, Nuclear Fission Definition, Nuclear Fallout, Nuclear Family Definition, Nuclear Fusion Reactor, Nuclear Fallout Map, Nuclear Glass, Nuclear Gas Mask, Nuclear Gandhi, Nuclear Gun, Nuclear Gif, Nuclear Generator, Nuclear Gravity Bomb, Nuclear Games, Nuclear Gas, Nuclear Grenade, Nuclear Holocaust, Nuclear Heart Test, Nuclear Half Life, Nuclear Hazard Symbol, Nuclear Holocaust Movies, Nuclear Hormone Receptors, Nuclear Hoax, Nuclear History, Nuclear Household, Nuclear Hand Grenade, Nuclear Imaging, Nuclear Incidents, Nuclear In Spanish, Nuclear Isotopes, Nuclear Icebreaker, Nuclear Icbm, Nuclear Issues, Nuclear Industry, Nuclear Icon, Nuclear Instruments And Methods, Nuclear Jobs, Nuclear Japan, Nuclear Jet Engine, Nuclear Jokes, Nuclear Jellyfish, Nuclear Jet, Nuclear Js, Nuclear Jobs Overseas, Nuclear Jobs Florida, Nuclear Jellyfish Of New Jersey, Nuclear Korea, Nuclear Korean Noodles, Nuclear Kidney Test, Nuclear Kenyan Sand Boa, Nuclear Kinetic Energy, Nuclear Key, Nuclear Kit, Nuclear Keychain, Nuclear Kill Radius, Nuclear Kid, Nuclear Localization Signal, Nuclear Lamina, Nuclear Launch Codes, Nuclear Logo, Nuclear Lyrics, Nuclear Launch Detected, Nuclear Lake, Nuclear Launch, Nuclear Lamins, Nuclear Leak, Nuclear Medicine, Nuclear Medicine Technologist, Nuclear Membrane, Nuclear Missile, Nuclear Meltdown, Nuclear Membrane Function, Nuclear Map, Nuclear Membrane Definition, Nuclear Medicine Technologist Jobs, Nuclear Magnetic Resonance, Nuclear Non-proliferation Treaty, Nuclear News, Nuclear Nations, Nuclear North Korea, Nuclear Notation, Nuclear Noodles, Nuclear Norm, Nuclear Navy, Nuclear Nadal, Nuclear Nucular, Nuclear Option, Nuclear Oncology, Nuclear Option 2013, Nuclear Option Harry Reid, Nuclear Overhauser Effect, Nuclear Outage, Nuclear Operator Salary, Nuclear Or Nucular, Nuclear Operator, Nuclear Option Fallout 4, Nuclear Power, Nuclear Power Plants, Nuclear Proliferation, Nuclear Power Plants In Us, Nuclear Physics, Nuclear Physicist, Nuclear Power Definition, Nuclear Power Pros And Cons, Nuclear Pharmacy, Nuclear Power Plants In Texas, Nuclear Quotes, Nuclear Quadrupole Resonance, Nuclear Questions, Nuclear Quiz, Nuclear Quality Assurance, Nuclear Quizlet, Nuclear Quadrupole Moment, Nuclear Quantum Effects, Nuclear Quality Assurance Jobs, Nuclear Quantum Numbers, Nuclear Reactor, Nuclear Radiation, Nuclear Reaction, Nuclear Regulatory Commission, Nuclear Reactor Definition, Nuclear Reactor Diagram, Nuclear Receptor, Nuclear Reactors In Us, Nuclear Rocket, Nuclear Reaction Worksheet, Nuclear Stress Test, Nuclear Symbol, Nuclear Submarine, Nuclear Sclerosis, Nuclear Sign, Nuclear Shadow, Nuclear Shelter, Nuclear Secrecy, Nuclear Siren, Nuclear Scan, Nuclear Triad, Nuclear Throne, Nuclear Test Ban Treaty, Nuclear Test, Nuclear Technician, Nuclear Threat, Nuclear Throne Together, Nuclear Throne Wiki, Nuclear Technology, Nuclear Test Ban Treaty Apush, Nuclear Umbrella, Nuclear Uranium, Nuclear Uses, Nuclear Utilization Theory, Nuclear Ultrasound, Nuclear Us, Nuclear Usa, Nuclear Unit, Nuclear Union, Nuclear Ukraine, Nuclear Vs Atomic, Nuclear Vote, Nuclear Vs Nucular, Nuclear Valdez, Nuclear Vs Solar, Nuclear Vs Coal, Nuclear Vs Hydrogen Bomb, Nuclear Vs Extended Family, Nuclear Vs Mitochondrial Dna, Nuclear Video, Nuclear War, Nuclear Weapons, Nuclear Winter, Nuclear Waste, Nuclear Waste Disposal, Nuclear War Now, Nuclear Weapons Definition, Nuclear War Movies, Nuclear Waste Policy Act, Nuclear Weapons Facts, Nuclear X Ray, Nuclear X, Nuclear Explosion, Nuclear X Met Rx, Nuclear Explosion Gif, Nuclear X Ray Technician Salary, Nuclear Explosion In Space, Nuclear Explosion Video, Nuclear Explosion Simulator, Nuclear Explosion Radius, Nuclear Yield, Nuclear Yield Map, Nuclear Youtube, Nuclear Yellow, Nuclear Yellow Cake, Nuclear Yacht, Nuclear Yemen, Nuclear Ymir, Nuclear Yap, Nuclear Yucca Mountain, Nuclear Zone, Nuclear Zomboy, Nuclear Zero, Nuclear Zombies, Nuclear Zomboy Lyrics, Nuclear Zone Theory, Nuclear Zone Hypothesis, Nuclear Zec, Nuclear Zone Terraforming Mars, Nuclear Zone In Russia, Icelandair, Iceland Weather, Iceland Flag, Iceland Map, Iceland Population, Iceland Blue Lagoon, Iceland Currency, Iceland Vacation, Iceland Airport, Iceland Tours, Icelandair, Iceland Airport, Iceland Airlines, Iceland Airport Code, Iceland Attractions, Iceland Airwaves, Iceland Airbnb, Iceland Average Temperature, Icelandair Reviews, Iceland Air Business Class, Iceland Blue Lagoon, Iceland Black Sand Beach, Iceland Beaches, Iceland Beer, Iceland Best Time To Visit, Iceland Blue Lagoon Hotel, Icelandic Band, Iceland Backpacking, Iceland Black Beach, Iceland Blog, Iceland Currency, Iceland Capital, Iceland Car Rental, Iceland Climate, Iceland Cities, Iceland Cruise, Iceland Country Code, Iceland Continent, Iceland Culture, Iceland Camper Rental, Iceland Drinking Age, Iceland Day Tours, Iceland Demographics, Iceland Down Syndrome, Iceland Daylight, Iceland Dragon, Iceland Deals, Iceland Diving, Iceland Destinations, Iceland Driving, Iceland Economy, Iceland Europe, Iceland Elves, Iceland Exchange Rate, Iceland Excursions, Iceland Eu, Iceland Equal Pay, Iceland Earthquakes, Iceland Euro 2016, Iceland Expensive, Iceland Flag, Iceland Flights, Iceland Facts, Iceland Foods, Iceland Fjords, Iceland Fun Facts, Iceland Fishing, Iceland Financial Crisis, Iceland Flag Emoji, Icelandic Fermented Shark, Iceland Golden Circle, Iceland Government, Iceland Glacier, Iceland Golden Circle Map, Iceland Golden Circle Tour, Iceland Gdp, Iceland Guided Tours, Iceland Groupon, Iceland Geography, Iceland Geyser, Iceland Hotels, Iceland Hot Springs, Iceland Hostels, Iceland History, Iceland Hetalia, Iceland Honeymoon, Iceland Hiking, Iceland Horses, Iceland Hot Dogs, Iceland Horseback Riding, Iceland Ice Cream, Iceland In July, Iceland In September, Iceland In October, Iceland In August, Iceland In June, Iceland In November, Iceland In Spanish, Iceland In May, Iceland Itinerary, Iceland Jobs, Iceland July Weather, Iceland July, Iceland June Weather, Iceland June, Iceland Jersey, Iceland Jewelry, Iceland Jails Bankers, Iceland Jeep Tours, Iceland Jokes, Iceland Krona To Usd, Iceland Krona, Iceland Kayaking, Iceland Keflavik, Iceland Kef, Iceland Krona Symbol, Iceland Katla, Iceland Known For, Iceland Krona Exchange Rate, Iceland King, Iceland Language, Iceland Lagoon, Iceland Landscape, Iceland Location, Iceland Lonely Planet, Iceland Latitude, Iceland Lights, Iceland Life Expectancy, Iceland Last Names, Iceland Landmarks, Iceland Map, Iceland Money, Iceland Military, Iceland Music Festival, Iceland Money To Usd, Iceland Mountains, Iceland Marathon, Iceland Must See, Iceland Music, Iceland Mcdonalds, Iceland Northern Lights, Iceland News, Iceland Northern Lights Tour, Iceland New Hyde Park, Iceland National Park, Iceland National Team, Iceland Nightlife, Iceland Northern Lights Hotel, Icelandic Names, Iceland National Anthem, Iceland On Map, Iceland On World Map, Iceland Official Language, Iceland Outlets, Iceland On A Budget, Iceland October Weather, Iceland October, Iceland Outline, Iceland Off The Beaten Path, Iceland Ocean, Iceland Population, Iceland People, Iceland Poppy, Iceland Pictures, Iceland Population 2017, Iceland President, Iceland Photos, Iceland Plane Tickets, Iceland Packing List, Iceland Packages, Iceland Quotes, Iceland Quality Of Life, Iceland Quartz, Iceland Queen, Iceland Quick Facts, Iceland Quartz Countertops, Iceland Questions, Iceland Quiz, Iceland Quotes Mighty Ducks, Iceland Quicksand, Iceland Ring Road, Iceland Rental Car, Iceland Religion, Iceland Resorts, Iceland Restaurants, Iceland Ring Road Itinerary, Iceland Real Estate, Iceland Road Map, Iceland Rv Rental, Iceland Revolution, Iceland Soccer, Iceland Summer, Iceland Spar, Iceland Size, Iceland Summer Weather, Iceland Shark, Iceland Spa, Iceland Stopover, Iceland Sunset, Iceland Souvenirs, Iceland Tours, Iceland Time, Iceland Travel, Iceland Tourism, Iceland Temperature, Iceland Things To Do, Iceland Travel Guide, Iceland To Usd, Iceland Tickets, Iceland Travel Deals, Iceland University, Iceland Unemployment Rate, Iceland Usa, Iceland Uber, Iceland Unlimited, Iceland Uk, Iceland Us Embassy, Iceland Usd Conversion, Iceland Ultra Marathon, Iceland Us Visa, Iceland Vacation, Iceland Volcano, Iceland Visa, Iceland Vs Greenland, Iceland Vodka, Iceland Volcano Tour, Iceland Vikings, Iceland Virginia Beach, Iceland Volcano Eruption 2017, Iceland Visa Requirements, Iceland Weather, Iceland Women, Iceland Weather July, Iceland Waterfalls, Iceland Weather August, Iceland Wiki, Iceland Weather In May, Iceland Water, Iceland Weather In September, Iceland Weather In June, Iceland X Reader, Iceland X Reader Lemon, Iceland X Fridge, Iceland X Reader Fluff, Iceland X Reader Lime, Iceland X Reader X Norway Lemon, Iceland X Male Reader, Iceland X Reader X Norway, Iceland X Norway, Iceland X America, Iceland Yogurt, Iceland Youtube, Iceland Yearly Weather, Iceland Yoga Retreat, Iceland Yelp, Iceland Youth Hostels, Icelandic Yogurt Skyr, Iceland Yarn, Iceland Yearly Temperatures, Iceland Yurt, Iceland Zip Code, Iceland Zoo, Iceland Zika, Iceland Zip Line, Iceland Zillow, Iceland Zodiac Tours, Iceland Zoo Price, Iceland Zodiac Boat Tour, Iceland Zoo Reykjavik, Iceland Zesty Bean Quinoa
The U.S. Discovery of Israel’s Secret Nuclear Project
Israeli Cover Stories about the Dimona Reactor Dismayed Top Level Officials Who Saw a “Clearly Apparent Lack of Candor“
U.S. Embassy Telegram Quotes Ben-Gurion Aide That It Was a “Stupid Mistake” by Israel to Cloak the Nuclear Project in Secrecy
To Prevent Military Uses of the Facility, U.S. Officials Believed the International Atomic Energy Agency Should Monitor Dimona (It Never Has)
Today’s Posting Inaugurates the National Security Archive’s Special Web Site on Israeli Nuclear History
National Security Archive Electronic Briefing Book No. 510
Avner Cohen and William Burr, editors
For more information contact:
Avner Cohen at 202-489-6282 (mobile) or 831-647-6437 (office)
William Burr at 202/994-7000 or nsarchiv@gwu.edu
|
Washington, D.C., April 15, 2015 – The U.S. government first learned of Israel’s secret nuclear program at Dimona from an American corporate official talking to U.S. diplomats in Tel Aviv during mid-summer 1960, according to a declassified document published today for the first time by the National Security Archive, the Nuclear Proliferation International History Project, and the Center for Nonproliferation Studies of the Middlebury Institute of International Studies at Monterey. Other documents published today detail the discovery of the secret project that some in the U.S. government believed from the very start aimed at a weapons capability; the U.S. debates over Israel’s lack of candor; and U.S. government efforts to pressure the Israelis to answer key questions about the nature of the Dimona project.
This “discovery,” which came as the presidency of Dwight D. Eisenhower was drawing to a close, caused apprehension in Washington by raising concern about regional stability and nuclear proliferation, but it also produced annoyance because Israeli officials at all levels repeatedly provided less than credible answers to U.S. questions about Dimona. Thus, in September 1960, when embassy officials asked about a new construction site when they were on a helicopter ride nearby, an adroit Israeli official, Addy Cohen, improvised a story to keep the secret: it was the site of a textile factory, he said; a story that was not wholly false because there was a textile plant near Dimona. An interview with Addy Cohen detailing the episode appears in this posting for the first time.
Documents published in this collection shed light on a particularly notable intelligence failure: how Washington missed warning signs that the Israelis had a nuclear project underway, but also how the U.S. belatedly realized what the Israelis were doing, and how Eisenhower and his senior advisers reacted to this discovery. Among the documents are:
- The June 1959 Israel-Norway secret agreement providing for the sale of Norwegian heavy water to Israel (through the United Kingdom), transmitted by Oslo Embassy political officer Richard Kerry (father of Secretary of State John Kerry).
- Reports about information from a then-covert source — University of Michigan nuclear engineering professor Henry Gomberg — who learned that the Israelis had a secret nuclear reactor project that involved experiments with plutonium.
- A telegram from the U.S. embassy in Tel Aviv reporting on Finance Ministry official Addy Cohen’s statement that “we’ve been misbehaving,” and one by an unidentified official close to Prime Minister David Ben-Gurion that the secrecy surrounding Dimona was unjustifiable and that it was “a stupid mistake on the part of Israel.”
- Reports by U.S. Ambassador Ogden Reid on conversations with Ben-Gurion.
- A State Department message to the embassy in Tel Aviv conveying irritation that the responses of the Israeli government showed a “lack of candor.”
- Messages about a role for the International Atomic Energy Agency in inspecting and safeguarding Dimona.
* * * * *
The Eisenhower Administration and the Discovery of Dimona: March 1958-January 1961
By Avner Cohen and William Burr
In the last months of 1960 as the presidency of Dwight D. Eisenhower was coming to a close, the U.S. government discovered that Israel had been building, with French assistance, a secret nuclear reactor near Dimona in the Negev Desert that could give Israel a nuclear weapons potential. The discovery caused apprehension within the Eisenhower administration by invoking concerns about regional stability and nuclear proliferation, but it also produced annoyance because Israeli officials at all levels provided less than credible answers to U.S. questions about Dimona.
One episode that helped create a sense of deception was that, in response to initial U.S. official questions about the construction site, the Israelis said it would be a textile factory. Over the years the “textile factory” story has acquired legendary status, but exactly when the story came about has been a mystery. But recently unearthed U.S. government documents — an embassy telegram and a memorandum by the Deputy Chief of Mission — help solve this historical puzzle. They show that during a helicopter flight in September 1960, with American Ambassador Ogden Reid and others of his staff on board, not far from the reactor site, Ambassador Reid (or one of the travelers) asked what the big construction site was. Their host, Addy Cohen, a senior Treasury Ministry official, replied, “Why, that’s a textile plant.” In December 1960, when the Dimona issue was publicly exposed, Cohen was asked why he had said “textile factory.” He responded: “that was our story at the time.” Cohen acknowledged that “we have been misbehaving” by keeping Dimona secret, but justified the project as a “deterrent” against Arab neighbors.
Today the National Security Archive, the Nuclear Proliferation International History Project and the Center for Nonproliferation Studies of the Middlebury Institute of International Studies at Monterey publish for the first time these two items and other declassified documents on the “discovery” of Dimona. The documents provide new perspectives on how the Eisenhower administration learned about the secret reactor project, how it reacted to the discovery, and how the Israelis responded. Among the findings are these:
- The initial “discovery” by the U.S. embassy in Tel Aviv of the French-Israeli reactor project was probably in late July 1960, when a U.S. corporate official learned about it from an Israeli oil executive and told U.S. diplomats that the site would be a power reactor. This is the earliest known reference to Dimona.
- The admission by French Foreign Minister Maurice Couve de Murville on December 16 to Secretary of State Christian Herter that France had helped Israel build the reactor, a “replica of [the] Marcoule plant.” He also told Herter that under the bilateral agreement, France would supply Israel the raw materials and receive any plutonium produced by the plant. In reply to Herter’s question about the plant’s financing, Couve said that he “assumed the money came from [the United States]”
- Former Treasury Ministry official Addy Cohen ad libbed the “textile plant” story in response to questions on a helicopter tour [See above and sidebar].
- An unidentified official close to Prime Minister David Ben-Gurion, according to an Embassy telegram, told the Canadian ambassador that the secrecy surrounding Dimona was unjustifiable and that it was “a stupid mistake on the part of Israel.” Assistant Secretary for Near Eastern Affairs G. Lewis Jones agreed: It was “stupid of them” and an “unnecessary … Israeli caper.”
- The financial aspects of the Dimona project, i.e., cost, financing, and the role of U.S. money — through both the diversion of U.S. government aid and the use of tax-deductible individual charities — played an important role in the Eisenhower administration’s internal deliberations on Dimona. Washington considered applying, but apparently did not use, the power to withhold economic assistance as pressure on Israel.
- When the U.S. started asking questions about Dimona, and then when the issue was leaked to the press, an irritated Prime Minister Ben-Gurion asked Ambassador Ogden Reid: “Why in [the] States is everything being told [to] everybody?” Ben-Gurion stuck to the new Israeli cover story, namely, that the Dimona reactor was for peaceful purposes only, and for the economic development of the Negev in particular — no more than a step towards the building of nuclear power stations and the production of electric power, a badly needed resource.
- A State Department message to the embassy in Tel Aviv conveyed a sense of irritation with the responses of the Israeli government: Ben-Gurion’s explanations “appear evasive” and the “clearly apparent lack of candor [is] difficult to reconcile with [the] confidence which had traditionally characterized U.S.-Israel relations.” The Department wanted more questions asked and more detailed and frank answers from Ben-Gurion.
- In June 1959 Israel and Norway signed a secret agreement providing for Norway to sell heavy water to Israel (through the United Kingdom). According to the U.S. embassy first secretary in Oslo, Richard Kerry (father of Secretary of State John Kerry), disclosure of the agreement could be embarrassing to the Norwegian government in light of its efforts to play the role of an “honest broker” in international conflicts, including in the Middle East.
Also published in this collection are important documents that have been available in previous National Security Archive postings, but are a significant part of the record of the discovery of Dimona, including:
- A Special National Intelligence Estimate — SNIE 100-8-60 from 8 December 1960 — that formally determined that “Israel is engaged in construction of a nuclear reactor complex in the Negev near Beersheba” and “plutonium production for weapons is at least one major purpose of this effort.” The SNIE estimated “that Israel will produce some weapons grade plutonium in 1963-64 and possibly as early as 1962.” A significant portion of the SNIE is still classified.
- President Eisenhower’s meeting with top advisers on 19 December 1960 to discuss the Dimona problem, ponder the issues raised by Israeli fundraising in the United States, and discuss plans to encourage Israel to open up Dimona to visits by U.S. or reliable foreign scientists and to subject the reactor to International Atomic Energy Agency inspections. Some portions of this meeting record are also still classified.
- The post-mortem on SNIE 100-8-60 ordered by the U.S. Intelligence Board whereby the intelligence community tried to determine what pieces of information it had missed and to learn lessons from the intelligence failure.
The Eisenhower administration’s “discovery” during the last months of 1960 that Israel was secretly building a large nuclear complex at Dimona was a belated one indeed. It occurred more than five years after Israel had made a secret national commitment to create a nuclear program aiming at providing an option to produce nuclear weapons; more than three years after Israel had signed its secret comprehensive nuclear bargain with France; and two years or more after Israel had begun the vast excavation and construction work at the Dimona site.
The tardiness of the discovery was a major blunder, what is called in our times an intelligence failure. In comparative terms, it was probably as severe as (or more so than) the failures to anticipate the Indian nuclear tests of in 1974 and 1998. Some of the documents included in this e-book provide clues as to why the discovery was delayed and the roots and causes of the intelligence failure.
What amounted to an intelligence breakdown by the United States was a tremendous counterintelligence success for Israel. The U.S. bungle enabled Israel to buy precious time for the highly vulnerable Dimona project. One could argue that had the United States discovered Dimona two years earlier, perhaps even a year earlier, that the young and fragile undertaking might not have survived. Early political pressure from the United States on the two foreign suppliers, France and Norway, might have terminated it at the very start.
The documents presented here reveal how surprised and angry the Eisenhower administration was when it learned about Dimona — and yet how circumspect Washington was in its reaction to the discovery. There was a huge gap between what senior U.S. officials said to each other about Dimona and what they said to the Israelis. On the one hand, the Americans were convinced that the evidence they had amassed indicated that it was plutonium production-oriented project with weapons potential that posed a significant proliferation risk. They were irritated that the Israelis were trying to pull the wool over their eyes with all manner of evasive answers and misleading stories. Apparently they had many doubts about Ben-Gurion’s new cover story as well. On the other hand, the administration masked its anger and suspicions; opting for a cautious approach, it chose not to be confrontational but to confine itself largely to: 1) seeking answers about Dimona and Israel’s intentions, and 2) encouraging Israel to accept visits by U.S. scientists and consent to applying International Atomic Energy Agency (IAEA) safeguards to Dimona, as a way to constrain Israeli freedom of action. There are hints that U.S. diplomats warned the Israelis that U.S. economic aid could be jeopardized, but with only weeks left in office the Eisenhower administration was in no position to coerce its ally over the issue.
***
|
|
|
|
|
|
|
To appreciate the full historical context of the American intelligence failure we need to say a little bit about the Dimona project itself. In 1955, soon after David Ben-Gurion came back to power as Israel’s prime minister and minister of defense, he launched a secret feasibility initiative to determine whether, and how, Israel could build a nuclear infrastructure to support a program aiming at producing nuclear explosives. Ben-Gurion delegated that difficult task to a young (32 years of age) and highly ambitious lieutenant, Shimon Peres, whose formal position was then the director general of the Ministry of Defense. Within three years, from 1955 to 1958, Peres did almost the impossible: he managed to transform the idea of a national nuclear program from a vague vision of the future into a real technological project in the making.
Unlike the chair of the Israeli Atomic Energy Commission (IAEC), Professor David Ernst Bergmann, who preached self-reliance, Peres’s overall philosophy was that Israel must not (and cannot) reinvent the wheel and therefore must find a foreign supplier who could provide the most comprehensive nuclear package possible, one suited for a weapons-oriented program.[1]
Those three years were filled with internal deliberations, debates and planning. Often different courses of action were examined simultaneously, on parallel or even conflicting tracks. At least three countries were considered at one time or another to be the foreign supplier: the United States, France, Norway and, to a limited extent, the United Kingdom. In historical perspective, it appears that by 1958, the project’s international master plan had become firmly drawn: France would be the foreign supplier, Norway would provide the heavy water and possibly the backup in case the French card went wrong, and the United States would provide a small peaceful package, under “Atoms of Peace,” that could serve as the camouflage for the whole project, mostly as a way to conceal Israel’s real achievement — Dimona — from the United States.
This raises the issue of secrecy. The story of Dimona is one of a huge secret. Secrecy was essential in order to shield and insulate the highly vulnerable, newly born, project from a hostile outside. At the very core, of course, it is an Israeli secret – the largest, most comprehensive and longest-held secret Israel has ever generated. However, it is more than an Israeli secret; Israel had partners in this venture. The prime partner was the chief foreign supplier, France; the second was Norway, in concert with the British.
And then there was the United States. In a sense, the secrecy surrounding Dimona was aimed primarily against the United States. After all, of all the nations involved, the U.S. posed the greatest threat to the Israeli program. Since the time of the Baruch Plan in 1946 the United States had been on the record opposing the spread of nuclear weapons. Washington helped to create the IAEA in 1957 — the very same year the Dimona deal was signed — and since then it had promoted the creation of an international safeguards system. Should the Dimona secret have been compromised, the United States would have likely exercised pressure on France either to terminate the project altogether or at least to submit it to international safeguards.
The documents in this e-book involve Israel’s nuclear relations with the United States, France and Norway. What follows is some brief background on Israel’s efforts with each of them:
- The United States. On 12 July 1955, Israel was the second country to sign a general agreement with the United States for peaceful nuclear cooperation under “Atoms for Peace.” Initially, the leaders of the Israeli Atomic Energy Commission [IAEC] thought that American assistance could be the starting point for a largely indigenous Israeli nuclear program. Consistent with this vision, during 1955-56, IAEC Chairman Bergmann tried to find out whether the United States would provide assistance to build a “real reactor” — that is, a 10 MW natural uranium/heavy water reactor — but also to provide 10 tons of heavy water. Bergman made a formal request in July 1956 through a letter to AEC Chairman Lewis Strauss. In September the AEC notified Israel that it could be done but only under the aegis of a new bilateral nuclear power agreement which would require a more rigorous safeguards agreement than the original 1955 bilateral research accord. When Israel asked why, it was told that “plutonium production capabilities” necessitated stricter controls. When it became apparent the United States would insist on strict safeguards, Israel dropped its probe altogether.A year later, however, in 1957, Israel returned to the original U.S. “Atoms for Peace” offer to construct a small 1 MW swimming pool-type reactor, to be designed and installed by American Machines and Foundry (AMF) Atomics. The contract was signed on 20 March 1957 and in December of that year the long-awaited proposal was submitted to the USAEC by AMF on behalf of Israel for the Nachal Soreq (Rubin) site. Finally, on 19 March 1958, Israel signed a contract with AMF, expecting that the reactor startup date would be 15 months later. Construction on the Soreq site had begun in January 1958 and the small reactor reached criticality in a public ceremony in June 1960, six months prior to the discovery of Dimona.[2]Unlike Dimona, however, the Soreq (“Atoms for Peace”) reactor became subject to IAEA safeguards beginning in the mid-1960s.
- France. By early 1956, as French-Israeli military relations intensified, Peres became convinced that France could evolve into Israel’s foreign nuclear supplier and acted accordingly. But it was the nationalization of the Suez Canal that summer which created the political opening for a French-Israeli nuclear deal. In September 1956 the French Atomic Energy Commission and the IAEC reached an agreement in principle for the sale of a small EL type research reactor to Israel. A month later, as a side issue at the end of the secret Sevres conference (October 22-24) (site of the “collusion” that led to the Suez campaign), the nuclear deal received top-level political approval. The 1956 deal, however, was quite limited in size and scope; it also did not include a chemical separation plant and related reprocessing technology.It was in the context of the Suez campaign itself, when all three participants were subject to Soviet nuclear threats, that France reinforced its own earlier (1954) decision to become a nuclear power and agreed to help Israel to do the same. With France making its own nuclear decisions it became easier for Peres to be more explicit about the package that Israel actually wanted. The small EL-102 reactor that the CEA had planned for Israel in the fall of 1956 — similar to the experimental EL3 18 MW in Sacly — was upgraded to a large plutonium-producing reactor of generally the same order as the G-1 reactor at Marcoule. Following a year of highly intense discussions and negotiations in France, on 30 October 1957 Peres finally signed the Dimona package, which included both hardware and technological aid. In the wake of widespread rumors of French-Israeli nuclear cooperation in early 1958, U.S. embassy officials reported that Israel had plans to build an “experimental” reactor but the State Department did not investigate this further (See Documents 1A–B).[3]
- Norway. Beginning in 1955, Israeli AEC Chair Bergmann pressed his government to obtain 20 tons of heavy water cheaply and, if possible, without safeguards. Outside the United States, the Norwegian company Norsk Hydro was the only available producer of heavy water. In early 1956, Israel made a request to the United States but also approached Norway, informally via political channels, as to whether and when it could supply Israel with 20 tons of heavy water. Norway’s initial reply was that, due to current orders, it would be impossible to do so before the end of 1960. When the approach to Washington became hopeless, Israel grew more interested in the Norwegian supply. In August 1956, Bergmann wrote his friend Gunnar Randers, the director of the Norwegian Institute of for Atomic Energy, with a formal request to purchase 10 tons of heavy water. Randers responded noncommittally: supply was short but there was a “good chance” for a deal later on.Negotiations between Israel and Norway intensified in 1957-58, at the time that the Dimona deal was negotiated and signed. In a letter Randers wrote in August 1957 to Fredrik Moller, the director of NORATOM, a newly established company aimed at promoting the Norwegian nuclear industry, he explained that Israel needed the heavy water for a 40 MW “production reactor” fueled by natural uranium. As there were political and logistic difficulties with the Israeli order, to make it more attractive Randers presented it in the context of a larger nuclear cooperation agreement between NORATOM and the IAEC. In addition, to expedite the deal it became a three-party transaction: Israel purchased heavy water from NORATOM that had been sold and transferred two years earlier to Britain, but became surplus for them. The heavy water was shipped directly from the UK to Israel, without safeguards, as the issue of safeguards was left to the Norwegians. The paper record indicates that Randers was willing to be “creative” on controls, but the Norwegian Foreign Ministry insisted on safeguards to ascertain “peaceful use.” After long discussions Israel gave up on the question of safeguards and on 25 February 1959 the two countries exchanged documents on the heavy water sale with provisions to ensure that the use was peaceful. A few months later the Norwegian Foreign Ministry informed a U.S. AEC representative about the bilateral agreement, assuring him that it included safeguards and inspection rights (See Documents 2, 20).[4]
The discoveries of the French and Norwegian roles in the Israeli nuclear project were a revelation to the Eisenhower administration but it was even more surprised to discover that it already had in its possession clues that had not been followed up until it was too late. The documents below demonstrate how, during the short time it had available, the Eisenhower administration scrambled to pull the threads together by conducting an intelligence “post-mortem.” (See Document 27A). The post-mortem treated the missed opportunities as unfortunate but innocent errors caused by the deficient sharing of information and poor follow-up of instructions. But there have been more conspiratorial explanations of the missed opportunities: for example, the view that pro-Israeli officials in the AEC, CIA, and other agencies stove-piped important reports and information, and the open question that President Eisenhower himself may have chosen to look the other way during 1958-1959.[5]
A more delicate and complex dilemma faced by the Eisenhower administration was how to respond both publicly and privately to the challenge to U.S.-Israeli and U.S.-French relations posed by Dimona. Specifically, the administration had to decide how tough it should be and how to balance the Israeli proliferation concern against the rest of the U.S.-Israeli relationship. It is important to keep in mind that the administration was becoming aware of two things: (a) that Israel had made deliberate efforts to keep Dimona secret for as long as possible; and (b) that Washington could hardly take on faith the new Israeli “cover story” about Dimona, including Ben-Gurion’s public and private assurances. The administration remained skeptical, if not suspicious.
The possible public disclosure of Dimona also placed Israel, and specifically Prime Minister Ben-Gurion, in a dilemma: How should it react to the disclosure? How much should Israel tell and how truthful should it be? Could Israel tell the U.S. government one thing in private and something else to the world? The question was whether Israel should choose the path of truth or the path of ambiguity and deception. Because the first public statement would have great impact, this was a truly fateful decision. The internal Israeli deliberations about what to say are still unavailable, but it is possible to reconstruct the underlying reasoning based on important public and private statements made by Israeli officials, including Ben-Gurion.
Ben-Gurion chose the path of ambiguity and concealment: he declared that Dimona was purely a civilian scientific project, for training in the use of nuclear power for economic development. It was “exclusively for peaceful purposes,” he declared in his Knesset statement on 21 December 1960. In his private assurances to the United States Ben-Gurion provided some new information, but it was entirely consistent with his public version.[6] He would not tell the whole truth because the fate of the project was at stake. For Ben-Gurion this ambiguous, if not entirely deceitful, strategy had obvious short-term benefits: lessening U.S. anger and resulting pressure, and thereby avoiding a public showdown with Washington, while also calming the situation at home and in the region generally.[7]
It is apparent that the Eisenhower administration had no appetite to call Ben-Gurion’s bluff (either in private or in public). Nor was the departing president interested in escalating the Dimona problem into a diplomatic confrontation, which would not have even been possible given , with all that was already on his agenda (the Laos and Berlin crises, for example). Because relations with Israel had been relatively good, Israel had significant domestic support within the United States, and, perhaps most significantly, the Eisenhower administration was in its last few days in office, the White House let the State Department deal with the issue, keeping it under diplomatic control until the new Kennedy administration took office.
A determination to avoid a crisis encouraged senior officials such as Assistant Secretary of State G. Lewis Jones [Document 19] to try to “calm down” the agencies, including CIA, which he believed had been reacting intemperately, and to ensure that no one tried to cut off aid to Israel. At the same time, “calm”, secrecy, and the avoidance of publicity might make it possible for Washington to get answers from the Israeli and put quiet pressure on them to open up Dimona to visits by U.S. scientists and to accept safeguards by the IAEA (in fact, the last thing Ben-Gurion and his associates were likely to accept).
The dilemma the Eisenhower administration faced after the discovery of Dimona in December 1960-January 1961 would endure for the entire decade. From then on, three successive U.S. administrations — under presidents Kennedy, Johnson and Nixon — would have to deal with it as well. President Kennedy chose the toughest path of struggle and confrontation in his effort to check the program; President Johnson realized that the U.S. had limited leverage on the issue and planted the seeds of compromise and looking the other way; finally, in a bargain with Prime Minister Golda Meir, President Nixon accepted the Israel’s de facto nuclear status as long as it stayed secret, and in doing so created the present dilemma.
The documents that follow are illuminating but more is to be learned. Many records remain classified in the National Archives, not only in State Department files but also those of the Atomic Energy Commission. The papers of AEC Chairman John McCone at the National Archives include a file on Israel which is the subject of an earlier declassification request along with related State Department files. Moreover, the National Security Archive has pending requests with the Department of Energy, the Central Intelligence Agency, and the Dwight D. Eisenhower Library. In response to a request to re-review SNIE 100-8-60 (See Document 8), the CIA has held the line, refusing to release more information. The request is now under appeal.
THE DOCUMENTS
Documents 1A-B: Unnoticed Intelligence
A: Department of State Instruction A-128 to U.S. Embassy Israel, “Atomic Energy Developments,” 7 March 1958, Confidential
B: U.S. Embassy Tel Aviv Despatch No. 652 to State Department, “Israeli Exchanges With Other Countries Relating to Atomic Energy,” 16 April 1958,
Source for both: National Archives (College Park), Record Group 59, Department of State Records (hereinafter RG 59), Central Decimal Files, 1955-1959, 984a.801/4-1658.
Some in the U.S. intelligence community[8] regarded these communications as an early missed opportunity to discover the Dimona project a year or two earlier. In March 1958, in light of growing concern about the possibility of surreptitious nuclear weapons programs, the State Department saw an “urgent” need for information on the Israeli atomic energy program and asked its Tel Aviv embassy to report on “all phases” of Israeli nuclear-related activities, research and development, including any exchanges with foreign governments and organizations. As an example, the instruction cited a recent press report in the Jerusalem Post on French-Israeli atomic cooperation. The report included statements by the French minister of foreign affairs, Francois Benard, that France was supplying Israel’s uranium needs in exchange for “Israeli discoveries in atomic research for peace.”
In response the embassy set up a meeting on 15 April 1958 between embassy Second Secretary Lewis Townsend and Professor David Ernest Bergmann, the chairman of Israel’s Atomic Energy Commission. With respect to cooperation with France, Bergmann asserted flatly that Minister Benard “did not know what he was talking about.” Bergmann acknowledged that Israel had a nuclear agreement with France but the exchanges under the agreement were informational only. Under the agreement Israel received from France “unpublished reports” and sent students to study at French nuclear centers. He noted that the agreement had no provision under which France was obligated to supply Israel uranium as had been reported; nor had Israel ever received such supply. The substance of Bergmann’s commentary was close to what a US AEC representative would hear in Paris more than two years later in a similar inquiry (see Document 4). The comments were quite accurate as far as that (unpublished) 1954 bi-lateral exchange agreement was concerned (Bergmann mentioned that there was also a tri-lateral agreement on atomic energy research between Israel, France and the UK). Israel did not advertise the existence of those agreements, but did not treat them as classified either.[9]
Not surprisingly, however, Bergmann made no reference to the extremely secret French-Israeli Dimona agreement which had been signed in Paris on 3 October 1957. One must assume that he must have known something about that deal but it is not clear how much knew given that the IAEC was hardly consulted, let alone involved, in the decisions and actions that led to Dimona.[10] Bergmann’s most intriguing comment came at the end when he said that the principal decision to build a “power reactor had already been taken.” He seems to suggest two stages: first, “plans” which are currently “contemplated” to construct an “experimental nuclear reactor” within two or two-and-a-half years, and then five to seven years later “a large economically feasible [power] reactor could be put into operation.”
Was the reference to that “experimental reactor” an oblique reference to Dimona — as indeed Israel initially presented it — or was it a deliberate effort to confuse his American interlocutor? Or perhaps it was a mix of both? It is worth noting that Bergmann was known among Israelis as being loose on secrecy and this was apparently one of the reasons why he was bypassed on the Dimona project.[11]
In retrospect, according to the post-mortem investigation (see Document 27A) on why the United States discovered Dimona two years late, Bergmann’s loose comment on the “experimental reactor” was one of those major missing hints. In April 1958 U.S. intelligence wrongly assumed that the reference to the “experimental reactor” was to the US small swimming pool reactor at Soreq whose construction started in January that year at Nachal Soreq (see Document 3). Moreover, U.S. intelligence took on faith Bergmann’s statement about the limited nature of French-Israeli nuclear cooperation, although there had already been some reports about possible French-Israeli secret nuclear cooperation, even the possibility of joint nuclear weapons research. One way or another, a chance to investigate Bergmann’s claims and to seek further information about the “experimental reactor” was lost.
The numbers on the right side of these documents indicate that they are from the State Department’s central decimal files (whereby documents were filed using numerical combinations denoting subjects and countries). The 900 category signifies communications, transportation, and science; 84A stands for Israel; and 801 indicates research and development. The filing of the document in the R&D category, instead of the usual 1901 category for nuclear energy matters, would have hindered any U.S. government official who was interested in tracing intelligence on the Israeli nuclear program.
Documents 2A-C: “Certain Highly Classified Transactions with Israel”
A: Memorandum of Conversation, Norwegian Foreign Ministry, 5 June 1959, Secret, with 30 December 1960 routing slip [transcript attached]
B: Richard Kerry to Philip Farley, 15 June 1959, Secret
C: Richard Kerry to Philip Farley, 7 August 1959, enclosing copy of letter to Robert Brandin, and “Memorandum of conversation of August 6, 1959, at the Atomic Energy Institute, Kjeller, Norway,” Secret
Sources: A: RG 59, Records of Special Assistant to the Secretary of State for Atomic Energy and Outer Space, Records Relating to Atomic Energy Matters, 1948-1962 [SAE], box 305, File 12. Peaceful Uses of Atomic Energy Safeguards Sept-Dec 1960 Part 1 of 3; B: RG 59, SAE, box 501, Z1.50 Country File Israel d. General 1953-1961 Part 2 of 2 C: RG 59, SAE, box 313, Country File Norway d. General 1957-1961 Part 2 of 2
A critical piece of information that was known to the State Department, but for obscure reasons remained unknown to the U.S. intelligence community for many months (see Document 22), was the 20 tons of heavy water that Norway had quietly sold to Israel upon an agreement signed in Oslo on 25 February 1959. The Norwegians claimed that they wanted to keep the transaction under wraps because disclosure could hurt their diplomatic standing and interfere with business prospects in the Middle East. Evidently, Israel had equally strong reasons of her own to keep the heavy water deal secret as well. For this reason, but also due to an availability issue, Norway used the U.K. as a key third party in the deal: NORATOM (the Norwegian state-sponsored company to promote Norwegian nuclear energy industry) had originally sold heavy water to the United Kingdom for its nuclear weapons program. Then, as part of the three-party arrangement, the Norwegians asked the British to resell their excess heavy water back to NORATOM; even though the product would be shipped directly from the United Kingdom to Israel, it was NORATOM that was selling it. This also enabled NORATOM to avoid the political difficulty of having to apply to the Norwegian government for an export license.[12]
According to Olaf Solli, a nuclear energy expert with the Norwegian Foreign Ministry, some British officials wanted to “inform” Washington of the Israeli heavy water deal, but ultimately London did not share the information, according to British press reports in 2005 and 2006 based on new declassifications in British archives.[13]
In any event, on 5 June 1959, the Norwegian Foreign Ministry informed AEC official William M. Fullerton, a division chief at the Office of International Affairs, about the agreement to sell heavy water to Israel — subject to “safeguards and inspections” — but the size of the transaction was not reported. The U.S Embassy in Oslo prepared the memo of conversation and some days later, on 15 June, embassy political officer Richard Kerry forwarded it to Philip J. Farley, the assistant to the secretary of state for disarmament and atomic energy, asking that Fullerton and his boss, Algie Wells, receive copies.
For unknown reasons the memo was lost in the shuffle and was not disseminated above the middle levels of the State Department and the AEC. Top Department officials, not to mention those at the CIA or from State Department intelligence, did not see that June 1959 memo until December 1960, although months before the CIA had learned there had been a deal.[14] Accordingly, the questions about the sale that could have been asked of the Israelis, the Norwegians, and the British were not.
In a follow-up conversation, Richard Kerry learned more, indirectly, about the political sensitivity of Norwegian secret deals with Israel from Gunnar Randers, the director of the Atomic Energy Institute, and the key figure in Norwegian nuclear policy after World War II. Referring to NORATOM’s negotiations with the Egyptians over “isotope work,” Randers saw a “delicate” situation concerning transactions with Israel, but as long as they did not reach the public the Norwegians would not face any “difficulties” from Egyptian President Gamal Abdel Nasser. Randers was a close friend of the IAEC chair, David Bergmann, and this story supported Israel’s need for secrecy but it also suited Randers who had not kept the upper levels of the Norwegian Foreign Ministry in the picture (seeDocument 20).
Document 3: “French Atomic Energy Project in Israel”
U.S. Embassy Tel Aviv Despatch 75 to State Department, “French Atomic Energy Project in Israel,” 2 August 1960, Confidential
Source: National Archives (College Park), Record Group 59, Department of State records (RG 59), Central Decimal Files 1960-1963, 884A.1901/8-260
American Machine and Foundry (AMF) Atomics was the company which installed for Israel the 1 MW swimming pool type light water nuclear reactor at Nachal Soreq (known today as the Soreq Nuclear Research Center) that Israel received as a gift from the U.S. under the1955 “Atoms for Peace” bilateral agreement. In late July 1960, U.S. Embassy officials learned from a conversation with D. Anderson, an AMF employee, that French personnel were involved in building “a 60 megawatt atomic power reactor” in the Beersheba area. Anderson stated that this was his “impression, gained on conversations he had with an Israeli, Daniel Kimhi, the director of the Naptha Petroleum Company. According to Kimhi, the French nationals were working on a project described to him as ‘gas cooled power reactor capable of producing approximately 60 megawatts of electrical power.'” Anderson’s understanding was that the project had been under way for “about two years” with the completion date two years off.
As of this writing, this document is the first and earliest available declassified US document that makes explicit reference to the Dimona project. We should note that at the National Archives (College Park), over one hundred additional documents from 1960-1961 remain classified in the decimal files. A declassification request for them is pending.
The embassy reported this conversation to Washington and asked that the U.S. embassy in Paris look into the French government’s role, if any, in the alleged development. It took a few weeks before this information went to nuclear energy intelligence experts in Washington (at the AEC and CIA) who came to realize that they had missed other pieces of intelligence (See Document 27A) and began looking more closely at what was going on at the Dimona site.
Documents 4A-B: “The French CEA Was Not Collaborating with the Israelis”
A: State Department Instruction CA-3636 to U.S. Embassy Paris, “Reported Atomic Reactor Power Project at Beersheba,” 19 October 1960, confidential
B: U.S. Embassy Paris Airgram G-766 to State Department, 22 November 1960, Confidential
Sources: A: Record Group 84, Records of Foreign Service Posts, Classified Records of the U.S. Mission to the International Atomic Energy Agency, 1955-1963, box 1, Atomic Energy Developments Israel 1959-61; B: Freedom of Information release
When the U.S intelligence community got wind of the Tel Aviv embassy report on the French-Israeli reactor project (see Document 2), it took time to digest it; U.S. officials realized that more information was needed because apparently they had no independent sources to corroborate the report. (It is still a puzzle whether, and to what extent, U-2 overhead photographs were especially telling or whether they were being distributed within the intelligence community.)[15] According to the post-mortem (see Document 27A, PDF page 23), the CIA formulated a list of technical questions about French-Israeli collaboration, including the organizations involved in the project, reactor specifications, and plans for spent fuel, e.g. whether the Israelis were building a chemical separation plant. The State Department sent the CIA questions as an “Instruction” to the U.S. embassy in Israel, with the embassy in Paris and the U.S. mission to the IAEA also receiving copies. The request for information did not get high priority; it had a “Routine collection priority.”
If the U.S. embassy in Israel ever sent back a formal response, it is still classified. But U.S. military attaches at the Embassy in Tel Aviv did begin collecting information and sent photographs back to Washington. Another attempt to ferret out information is known: John Rouleau, the AEC’s representative in Paris, tried, but he met with complete denial from an unnamed member of the French Atomic Energy Commission. The latter, according to Rouleau’s account, “stated flatly that the French CEA was not collaborating with the Israelis in the construction of a nuclear power reactor.” Furthermore, the official denied that any French company could be working with the Israelis on a power reactor because “prior permission from the CEA would be required and such permission has neither been requested nor granted.”
While the French official denied any bilateral cooperation with Israel on a power reactor, he acknowledged the existence of an earlier 1954 agreement between the two national atomic energy commissions under which the bodies collaborated in two specific areas: (1) heavy water production and (2) extracting uranium from phosphates. In retrospect, it is impossible to say whether the CEA interlocutor truly knew nothing about the Dimona project-the Israeli-French deal was highly compartmentalized and secret within the CEA-or whether he made a deliberate effort to mislead the United States. Strictly speaking, however, his statement was not a lie because the Dimona reactor was not a power reactor.
Document 5: “The Know-How on Building Crude Atomic Bombs”
Memorandum of conversation, “Safeguards for Reactors,” 25 November 1960, Secret
Source: National Archives (College Park), Record Group 59, Department of State Records (hereinafter RG 59), Records of Special Assistant to the Secretary of State for Atomic Energy and Outer Space, Records Relating to Atomic Energy Matters, 1948-1962, box 305, 12H P.U.S File: 18. Safeguards September-December 1960 [Part 2 of 3]
Despite the lack of cooperation from the French government, Washington was piecing together information about the site in the Negev Desert from a variety of intelligence sources. By 25 November, Secretary of State Herter was confident enough in the information accumulated so far to share its essence with British Ambassador Harold Caccia. While intelligence experts in London and Washington had already been consulting each other (see chronology with Document 27A), Herter took it to a higher level by telling Caccia that Washington had unconfirmed reports that a “plutonium-producing reactor may be being built in Israel with French aid.” Furthermore, France may be giving the Israelis the “know how” to build “crude atomic bombs.” What made the existence of the Israeli reactor project of special concern was that for months Washington and its allies had been trying to build a consensus at the IAEA in favor of effective safeguards on nuclear power plants; this “new factor emphasized the importance of providing adequate atomic energy safeguards.”
Documents 6A-C: Professor Gomberg’s Discoveries
A: Paris Embassy Telegram 2162 to State Department, 26 November 1960, Secret
B: Memorandum of conversation, [Title excised], 1 December 1960, Secret, excised copy
C: Central Intelligence Agency, Information Report, “Nuclear Engineering/Large Nuclear and Electric Power Plant Near Beersheba/French Nuclear Assistance to Israel/Israeli Attitude Toward the Announcement of its Large Scale Nuclear Effort/Opportunity for U.S. Participation in Nuclear Powered Water Conversion,” 9 February 1961, Confidential
Sources: A: RG 59, Records of Special Assistant to the Secretary of State for Atomic Energy and Outer Space, Records Relating to Atomic Energy Matters, 1948-1962, box 305, 12H P.U.S File: 18. Safeguards September-December 1960 [Part 2 of 3], B: Freedom of Information release; C: RG 59, Records of Special Assistant to the Secretary of State for Atomic Energy and Outer Space, 1948-1961, box 501, Z1.50 Country File Israel f. Reactor 1960
Flying back to Ann Arbor on his way back from Israel, Professor Henry Gomberg, on the faculty of the University of Michigan’s nuclear engineering department, briefly stopped in Paris on 25 November and met with Roleau. As a guest of the Israeli Atomic Energy Commission and a consultant on matters of nuclear education, Gomberg had picked up some “urgent and secret” pieces of information — and suspicions — about the Israeli nuclear program that he wanted to share with U.S. government officials. He tantalized Rouleau by holding back what he had learned, but the little he said implied that Israel, with French aid, was engaged in some sort of a large scale secret nuclear power project. Gomberg also noted that he learned from an unnamed personal friend of Ben-Gurion [he probably meant Dr. Bergmann] that within a few weeks Israel would announce a five year [atomic energy] plan and would disclose the construction at the Beersheba site.
Several days later, on 1 December, Gomberg came to Washington for a full debriefing of AEC and State Department representatives. His name is redacted from this release of the memorandum of that conversation (declassified in the early 1990s) but it is evident that Gomberg was the subject of the debriefing. The same is true of the subsequent CIA report dated 9 February which also masked Gomberg’s identity. This document, apparently based on an interview at the time of Gomberg’s visit, contains detailed information, including his observations and tentative conclusions.
Based on various meetings in Israel, Gomberg became convinced that the large site the Israelis had described as an “agricultural experiment station” was actually a “large classified project.” It was evident to him that all his Israeli interlocutors were “thoroughly briefed to restrict their discussion within security bounds,” and yet his discussions at the Technion led him to believe that the Israelis were creating a much larger and more thorough nuclear training program than was needed by their own declared programs. He got a similar impression in his discussions at the Weizmann Institute (Plant [Machon] #4) where one person distressed his guide by mentioning that Plant [Machon] #4 was expected “to be working with gram quantities of Plutonium and curie quantities of polonium.” The plutonium issue was probably the most sensitive matter for the Israelis because of its weapons implications.
Gomberg concluded that the classified project was probably “a large nuclear and electrical power plant,” whose construction had been underway for some three years, located east of Beersheba. In another part of his report he described the reactor as “far beyond any kind of a training reactor and it will be capable of producing weapons grade plutonium.” Gomberg noted that he believed the Israelis had the technical capability to construct and operate a nuclear plant up to the level of 200 MW thermal. Then he estimated that the power level of the Beersheba project would be approximately 250 MW thermal. Later Gomberg noted that US photographs that were shown to him indicated a very close resemblance to the French G-1 reactor in Marcoule.
In his last meeting with Dr. Bergmann, Gomberg pressed him for information about “activities which were not freely discussed”; the latter acknowledged that the original intention was to announce the Beersheba facility later in 1961, but that because of the many rumors Ben-Gurion would make an announcement about a power reactor project in about three weeks time.
Document 7: The “Cover Story Would Not be Successful for Long”
Memorandum from Deputy Operations Coordinator Charles E. Rogers, Office of Under Secretary of State for Political Affairs, to Mr. Jones and Mr. Farley, 7 December 1960, Secret
Source: RG 59, Records of Special Assistant to the Secretary of State for Atomic Energy and Outer Space, Records Relating to Atomic Energy Matters, 1948-1962, box 501, CF 21.50 Israel F. Reactor 1960
While the U.S. intelligence community was finalizing its estimate of the secret Israeli reactor, senior officials had already discussed the problem and what to do about it at a luncheon meeting of the Operations Coordinating Board, which served as the coordinating and implementing unit for President Eisenhower’s National Security Council system. After Gordon Gray, the president’s national security assistant, opened the discussion, Deputy Under Secretary of State Livingston Merchant emphasized the subject’s “political sensitivity” and cautioned against any comments that cast doubt upon an anticipated Israeli announcement, even though it was generally agreed that the Israeli “cover story would not be successful for long.” This was probably a reference to the description of the plant as a “power reactor.” In the entire matter, “the Department of State would be the sole spokesman.” A skeptical reader, possibly Assistant Secretary of State for Near Eastern Affairs G. Lewis Jones, wrote “Ha!” next to the “sole spokesman” comment because Jones believed that too many other agencies “wanted to get into the act” (see Jones letter to Reid with Document 19 below).
Document 8: “Plutonium Production for Weapons Is At least One Major Purpose
Special National Intelligence Estimate Number 100-8-60, “Implications of the Acquisition by Israel of a Nuclear Weapons Capability,” 8 December 1960, with Memoranda to Holders Attached, 22 and 29 December 1960, attached, Secret, Excised copy
Source: MDR appeal to ISCAP, declassified in 2009, presently undergoing further review
On the basis of intelligence collected during the summer and fall of 1960 (of which much remains classified), possibly including the most recent information from Henry Gomberg, on 8 December 1958 Director of Central Intelligence Allen Dulles signed off on a Special National Intelligence Estimate (SNIE) entitled “Implications of the Acquisition by Israel of a Nuclear Weapons Capability.” The U.S. Intelligence Board, whose member agencies participated in the drafting process, concurred in the estimate that same day. The SNIE began with a firm factual determination that “Israel is engaged in construction of a nuclear reactor complex in the Negev near Beersheba.” Acknowledging that there could be various ways to interpret the function of the Dimona complex, the authors believed that “on the basis of all available evidence” that “plutonium production for weapons is at least one major purpose of this effort.” The “surrounding” secrecy and Dimona’s remote location was strong evidence of the military purposes. The SNIE estimated “that Israel will produce some weapons grade plutonium in 1963-64 and possibly as early as 1962.”
France’s extensive aid was noted but the exact nature of the assistance, including details on the reactor, and whether, and to what extent, the complex also included plutonium extraction (reprocessing), has been excised from this version of the SNIE. Also excised is the information mentioned in several subsequent updates (“Memorandum to Holders” on 22 and 29 December 1960). The Norwegian heavy water sale to Israel was noted — the CIA had discovered the purchase earlier in the year — but whether the State Department had rediscovered its documentation on the transaction by this point is not clear.
The SNIE also included a detailed discussion of the broader implications of the Dimona reactor: what it said about French and Israeli motivations, the possible reactions by the Arab world and the Soviet bloc, as well as the overall “repercussions” among western allies.
The SNIE became controversial as soon as it was published because senior intelligence officials were learning that the intelligence agencies and other U.S. government organizations had collected telling evidence several years earlier indicating that Israel had a secret nuclear reactor program under way. This recognition led to the production of an intelligence post-mortem to look at what had been missed and why (See Document 27A).
Document 9: Memorandum of Discussion at the 470th Meeting of the National Security Council, December 8, 1960, Top Secret, excised copy
Source: U.S. Department of State, Foreign Relations of the United States, 1958-1960 Volume XIII, Arab-Israeli Dispute; United Arab Republic; North Africa (Washington, D.C.: Government Printing Office, 1992)
The day that the SNIE was issued, the National Security Council met, with Eisenhower presiding, and received a briefing on the estimate by Director of Central Intelligence Allen Dulles who passed around photos of Dimona taken by the U.S. Army attaché. Dulles began by noting that Israel was constructing, with French assistance, a nuclear complex in the Negev. The complex contained a reactor capable of “producing weapons-grade plutonium.” His initial statement included three more lines which are still classified. As to the French assistance, it included equipment, personnel and training, as well as “fuel elements.” Neither CIA nor the AEC believed, contrary to Israel’s anticipated statement that the project was “solely for peaceful purposes.” Secretary of State Herter noted that the Arab reaction to the discovery would be “severe.” (At that point four-and-a-half lines of Herter’s comment are classified.) He also claimed that the cost of the reactor might be 40 to 80 million dollars.
During the discussion of the nuclear proliferation implications of an Israeli weapons program, the conversation briefly turned to how the plant was financed. Under Secretary of the Treasury Fred Scribner suggested that an important funding source may have been “Jewish charitable organizations in the U.S.” which received tax-deductible contributions. This had caused past problems because some charitable funds had been “diverted to government operations in Israel.”
The still-classified portions of this meeting record are the subject of a mandatory declassification review request filed in 2014.
Document 10: “Considerable Weapons Potential”
Telephone Call Logs of Secretary of State Christian Herter, 9 December 1960, Unclassified
Source: Dwight D. Eisenhower Library, Christian Herter Papers
On 9 December, Secretary of State Herter summoned Israeli ambassador Avraham Harman to the State Department and showed him photos of the Dimona reactor, asking for an explanation that would remove “bases for concern.” Harman said he knew nothing of the project but would inform his government. Later that afternoon, Herter called Claude Lebel, the chargé d’affaires at the French embassy, and asked about French involvement in the project. Herter prefaced his question by referring to a report he had received from his embassy in Tel Aviv that Prime Minister Ben-Gurion was about to announce that a new experimental reactor had been built in the Negev with French aid. Herter noted that, according to information the United States had ascertained, Israel had been involved since 1958 in constructing a reactor “which is at least ten times as large as claimed,” and that the design appeared to be not for power but for plutonium production, hence, it would provide Israel “considerable weapons potential.” Furthermore, Herter noted that the cost of the reactor was between 40 to 80 million dollars. Lebel had no information to offer and promised to pass the query on to Paris.
Document 11: “He Assumed the Money Came From” the United States
Paris Embassy Telegram CAHTO 4, 16 December 1960, Top Secret
Source: RG 59. Records of the Bureau of Near Eastern and South Asian Affairs, Office of the Country Director for Israel and Arab-Israeli Affairs, Records Relating to Israel, 1964-1966, box 8, Israel Atomic Energy Program
A week later, Herter was in Paris for a NATO meeting where he met with his French counterpart, Foreign Minister Maurice Couve de Murville. The latter directly acknowledged the secret French-Israeli deal to build a “replica of [the] Marcoule plant.” Under the agreement, Couve de Murville added, France would supply the raw materials and receive any plutonium produced by the plant. The Israelis would not make any public statement without first consulting the French government. In reply to Herter’s question about how the plant was financed, Couve stated that he “assumed the money came from US.” Herter understood that comment to mean that the project was financed by the “diversion of US government or private [American] aid.”
Document 12: Meet the Press
Memorandum of Conversation, ” Suggested Guidance for Chairman McCone’s Use in ‘Meet the Press’ Interview December 18 If Asked About Reported Israeli Atomic Weapons Developments,” 17 December 1960, Secret
Source: Dwight D. Eisenhower Library, Dwight D. Eisenhower Papers, White House Office, Office of the Staff Secretary, International Series, box 8, Israel (3):
With AEC Chairman John McCone slated to appear on “Meet the Press,” AEC and State Department officials met to develop an integrated approach to ensure that what he said comported with the government’s over-all position. The officials developed an approach that he could follow “with dignity” and not “be drawn into implications” that the U.S. was associated with an alleged Israeli nuclear weapons program. With respect to earlier press reports from London about an Israeli atomic bomb project, McCone would not comment. He could say that the U.S. opposed the proliferation of nuclear weapons capabilities, and that it was “firmly established policy” that “our law does not permit us to assist other countries to develop” such capabilities, If questioned, McCone could acknowledge U.S. support for Israeli research under the “Atoms for Peace” program.
In his comments on “Meet the Press,” McCone took his own approach; his main disclosure was an acknowledgement that the Israelis had not “revealed” the reactor to the U.S. He further stated that Washington was trying to get more information, that the existence of the reactor did not necessarily mean a bomb project, although the reactor could produce plutonium, and that Israeli compliance with IAEA safeguards would provide a good test case for inspection and “allay fear of weapons intent.”[16]
Documents 13A-B: “Israel Should Forthwith Open the Plants”
A: White House Office of the Staff Secretary, “Memorandum of Conference with the President December 19, 1960”, 12 January 1961, Secret, Excised Copy
B: Department of State, “U.S. Notes Reports of Israel’s Atomic Energy Activities,” 19 December 1961
Sources: A: Dwight D. Eisenhower Library, Dwight D. Eisenhower Papers, White House Office, Office of the Staff Secretary, International Series, box 8, Israel (3); B: Department of State Bulletin, 9 January 1961, No. 1124, page 45.
With the Washington Post and the New York Times publishing stories about Dimona, partly based on leaks by John McCone,[17] President Eisenhower convened his top aides to discuss the Israeli reactor, how to respond to the publicity, and what kind of a public stance it was appropriate to take. This record of a meeting between Eisenhower and his closest advisers was probably not the president’s first discussion of the discovery of Dimona and its implications, but it was probably the highest level formal gathering and the most wide-ranging discussion. The conference record reveals some remarkable points:
- Purpose of the Dimona Complex and Reliability of US knowledge : Secretary of Defense Thomas S. Gates pointed out that “our information is that the plant is not for peaceful uses.” The President’s science advisor, Dr. George Kistiakowsky, responded that “there is some doubt about this” because it is unclear whether a chemical separation is on site (or being constructed). AEC Chairman McCone responded that his people believed that “there is a chemical separation plant there.” He added that it would make no sense that the Israelis would do just “part of the job.” This issue, whether Dimona had or did not have a secret separation plant, would haunt the US intelligence community for at least a decade. In retrospect, Gates and McCone were right from the start.
- Cost and US financial Involvement: McCone observed that the Dimona plant “had probably been financed from US support to Israel” and Herter supported the claim, adding that “it is clear that they [the Israelis] have constructed this plant through diversions from private and public [US] aid to Israel.” Eisenhower himself noted that “we had evidence” that the project cost was in a range between $100 and $200 million. (Incidentally, these figures are more than double the figure Herter cited at the National Security Council meeting a week earlier.) The president added, “we do not know where they have obtained the funds,” but the US government has a strong interest in knowing “because of the aid we are giving them.” Eisenhower’s remark is one of the rare mentions of a financial estimate for the Dimona project.
- Inspection: When McCone urged that the U.S. insist the Dimona plant be under IAEA safeguards, Gates suggested that the Israelis be asked to open the plant for inspection because Israel had signed the agreement that established the IAEA. Eisenhower agreed: the US statement should express confidence that because Israel was an IAEA member and had claimed that the reactor was for peaceful uses, it should allow inspections. When national security assistant Gordon Gray asked whether the US would insist on visiting the site, Eisenhower replied that it would not be necessary if the US was successful in forcing IAEA inspections.
- Intentions and Concealment: CIA Director Allen Dulles noted that Israel was trying to create confusion by associating the Dimona plant, “which is a large production installation,” with the very small Soreq reactor built with U.S. aid.
The meeting ended with the decision that Dimona should be handled by the Department of State, not the White House. Since the issue had emerged in the very last weeks of the Eisenhower presidency it was apparent the White House could not set a lasting policy but if any public statement was to be made it was to be coordinated with Herter. Nevertheless, for Eisenhower, the key objective was for the government of Israeli to accept IAEA inspections on the plant so that they could demonstrate its peaceful purposes.
During the meeting Herter had said that a U.S. statement should “remove [us] from suspicion” because Washington was not complicit in Dimona. Thus, the public statement made later that day noted the press reports about the reactor and “welcomed” Israel’s assurance that the government had “no intention of producing nuclear weapons.” The U.S. had provided no assistance because that would be contrary to U.S. nonproliferation policy and the Atomic Energy Act. The U.S. was concerned about the Israeli project and had asked Ambassador Harman for information. “A response has not been received.”
Document 14: State Department telegram 3311 to U.S. Embassy London, 20 December 1960, Secret
Source: Dwight D. Eisenhower Library, Dwight D. Eisenhower Papers, White House Office, Office of the Staff Secretary, International Series, box 8, Israel (3)
On 20 December Herter met with Ambassador Harman for the second time to discuss Dimona. At this meeting Harman answered Herter’s earlier questions by providing a narrative that became Israel’s basic cover story: Yes, Israel was building an additional reactor in the Negev with 24 megawatt capacity, meaning, but it had “no industrial importance.” The purpose of the Dimona reactor was “the development of scientific knowledge for eventual industrial, agricultural, medical and other scientific purposes, as an interim step toward enabling Israel to build its own power reactors.” The project “would take some 3 to 4 years to complete and it would have no relationship to a weapons capacity.” Several times during the meeting Herter raised questions about safeguards and the plutonium that would be produced in the reactor; Harman could not answer them, but asserted that upon completion the facility would be open to students from “friendly counties” and that it was for peaceful purposes.
Document 15: “We have been misbehaving a little”
U.S. Embassy Tel Aviv telegram 574 to State Department, 23 December 1960, Secret
Source: National Archives, Record Group 469, U.S. Operations Mission to Israel, Executive Office Classified Central Files 1952-1961, box 10, Atomic Matters 1960
Far more candid than Harman was Addy Cohen, the Finance Ministry’s director of economic assistance; a graduate of Georgetown University’s School of Foreign Service, he served as a liaison to the U.S. embassy. Classified in the State Department’s “Roger Channel” for sensitive intelligence, this surprising telegram memorialized several conversations on 21 and 22 December between Cohen and U.S. diplomats and foreign aid officials: Deputy Chief of Mission Murat Williams, Director of the U.S. Operations Mission [USOM][18] C. Reed Liggit, and Agricultural Attaché Grover Chappell. In these discussions Cohen gave the impression that the reactor would “eventually be used for weapons purposes,” which could offer a “‘deterrent’ to Arab action against Israel.” He volunteered that he had concealed the nature of the “top secret” project during several helicopter fly-bys with U.S. officials; during one of them’, in February 1960, he had characterized the reactor construction site as a “textile plant” because as he put it “that was our story at the time.” Admitting that the government of Israel had “been misbehaving a little,” Cohen thought that displeasure over the reactor might be the reason why Washington had delayed the signing of the PL 480 agreement (on food aid to Israel). Finally, commenting on a recent Jerusalem Post article claiming that 250 million Israeli pounds had been spent on the project, Cohen said that Israel had not “spent that much yet.”
Also according to this message, an unidentified official close to Prime Minister Ben-Gurion had told the Canadian ambassador that the secrecy was unjustifiable and that it was “a stupid mistake on the part of Israel.” As to why the subject had come up at this time, December 1960, the same source speculated that the CIA had been “caught off guard” in 1956 when Israel invaded the Sinai desert and this time “did not want to be caught napping.”
Document 16: “Why in [the United] States is Everything Being Told [to] Everybody?”
U.S. Embassy Israel Telegram 577 to State Department, 24 December 1960, Secret
Source: Dwight D. Eisenhower Library, Dwight D. Eisenhower Papers, White House Office, Office of the Staff Secretary, International Series, box 8, Israel (3)
On 22 December Prime Minister Ben-Gurion gave a statement in the Knesset claiming the reactor was for peaceful purposes, a statement which the State Department welcomed.[19] Two days later, Ambassador Ogden Reid finally had a long discussion about Dimona with Ben-Gurion. The latter was plainly irritated about the questions and the press reports: “Why in [the] States is everything being told everybody?” He justified the secrecy because of the Arab boycott; the participating companies did not want their role disclosed so Israel had to protect their interests. Yet his account of the Dimona project consisted of the same story that he had told the Knesset (and the same story that he would use for his meeting with President Kennedy in late May 1961): the project was for the economic development of Israel and of the Negev in particular; electric power was a badly needed resource.[20]Yet when Reid asked if the reactor would be producing power, Ben-Gurion said no; it was for research and training.
On safeguards for plutonium, Ben-Gurion said that Israel was “three or four years” away from facing that problem. But, he declared: “When we get to that point we won’t be behind any power in the world in respect to safeguards.” A few weeks later, Ben-Gurion would take a different position (See Document 23).
Referring to Egyptian President Nasser’s declaration that an Israeli nuclear weapons program would mean war, Reid asked what Israel could do to alleviate those concerns; Ben-Gurion replied that the State Department’s statement welcoming the Israeli declarations, had been helpful.
Document 17: The Need for a Visit by “Internationally Known Scientists”
U.S. Embassy Israel Telegram 590 to State Department, 28 December 1960, Secret, excised copy
Source: Dwight D. Eisenhower Library, Dwight D. Eisenhower Papers, White House Office, Office of the Staff Secretary, International Series, box 8, Israel (3)
Mulling over Ben-Gurion’s evasions, Ambassador Reid suggested to the Department some ideas for bringing up the question of safeguards and inspection with Foreign Minister Golda Meir. One was to suggest a visit of “IAEA scientific designee or internationally known scientists”; another, a more low key approach, was to use an AEC inspection visit to the smaller American reactor in Nachal Rubin [Soreq] to ask Israel to visit the new [Dimona] reactor. While doubting whether Ben-Gurion would favor any such proposals, Reid thought State should press Israel to request IAEA safeguards as a step toward “tranquility and peace” in the region. Getting Ben-Gurion to go along would probably require concerted action by the U.S., France, and the United Kingdom. The note included also the embassy’s own estimate of the cost of the Dimona project, which by then was the lowest of all the U.S. estimates: 17.8 million dollars in foreign exchange and some 29.2 million in local currency (Israeli pounds) costs. In comments, Reid noted that Israel would need to be assured that the names of foreign firms involved in the project would be protected from inspectors. Moreover, until the Department agreed, Reid suggested deferring a proposal by Chief of Naval Operations Arleigh Burke for a visit to Dimona by a Navy nuclear expert, Commander Ragnwald Muller, who was with the Office of Naval Intelligence in Frankfurt, West Germany.
Document 18: Israel had “By No Means Come Clean with Us”
Memorandum from Under Secretary of State for Political Affairs Livingston Merchant to
Assistant Secretary of State for Near Eastern Affairs G. Lewis Jones, 28 December 1960, Secret
Source: RG 59, Records of Special Assistant to the Secretary of State for Atomic Energy and Outer Space, Records Relating to Atomic Energy Matters, 1948-1962, box 501, CF 21.50 Israel F. Reactor 1960
Under Secretary of State Merchant briefed Assistant Secretary Lewis Jones about an Operations Coordinating Board [OCB] discussion of the Israel nuclear problem where Allen Dulles had grumbled that Israel had “by no means come clean with us.” The participants were also annoyed that the Development Loan Fund (DLF) had authorized a loan to Israel despite the OCB’s agreement that such action should be delayed. Eisenhower’s national security assistant, Gordon Gray, emphasized that the president wanted further efforts to secure Israel’s agreement to IAEA inspections. Such efforts, however, were not to reach the press and any initiative should be “conducted quietly through diplomatic channels.”
Document 19: “It Was Stupid of Them”
Assistant Secretary of State for Near Eastern Affairs G. Lewis Jones to Under Secretary of State for Political Affairs Livingston Merchant, “Israel’s Atomic Energy Activities,” 30 December 1960, Secret, with attachments [Transcript of letter from Jones to Reid, 28 December 1960 attached]
Source: RG 59. Records of the Bureau of Near Eastern and South Asian Affairs, Office of the Country Director for Israel and Arab-Israeli Affairs, Records Relating to Israel, 1964-1966, box 8, Israel Atomic Energy Program
Responding to Merchant’s request for an update on recent developments, Lewis Jones sent him documents relating to six different actions that various offices within the State Department were taking relating to the Israeli reactor, including his recent letter to Ambassador Reid and a message to the Embassy in Norway. In the letter, Jones let his hair down, writing about the “intemperate reaction” in Washington, which his bureau was trying to “calm down,” the “unnecessary Israeli caper;” the widespread impression that “the Israelis have inexcusably duped us;” the need for Israel to dispel doubts by letting U.S. scientists visit the site; and the possibility that the situation will “worsen” as suspicion grows. A briefing that Jones gave to the Senate Foreign Relations Committee in early January conveyed a similar sense of being duped and the anger that influential members of the Senate felt about Israel’s secretiveness and evasive responses.
In the telegram to Oslo, the State Department asked the U.S. Embassy to seek further information on the Norwegian sale of heavy water to Israel and to ask that the government “exercise fully its safeguard rights” under the agreement. With the Norwegian heavy water sale being one of the pieces of the intelligence puzzle that Washington had missed, the administration was now investigating why, and what it had missed earlier.
Jones also enclosed a draft message to Ambassador Reid that had been prepared (not attached to this memo, but see Document 21) asking for replies to “unanswered questions” and to let Merchant know that other bureaus were preparing messages to get more information from the French and to advance the possibility of IAEA safeguards. Jones agreed with Merchant that what was most important was avoiding further publicity and the necessity for quiet diplomacy.
Document 20: “The Possibility of [It] Embarrassing the Government”
Letter from Richard Kerry, U.S. Embassy Oslo, to William Burdette, Office of British Commonwealth and Northern European Affairs, 30 December 1960, with Israeli-Norwegian agreement attached, with routine slip dated 6 January 1961
Source: RG 59, Records of Special Assistant to the Secretary of State for Atomic Energy and Outer Space, 1948-1961, box 512, Z1.69 Country File Norway a. Norway-Israel Agreement 1961
In response to the State Department request, embassy officers in Oslo obtained more information on the Israel-Norway heavy water deal and the terms of the sale agreement, which included a “peaceful uses” stipulation. On 30 December, political officer Richard Kerry obtained a copy of the agreement which he believed could be embarrassing to the Norwegian government in light of its efforts to play the role of “honest broker” in international conflicts, including the Middle East. The agreement included an Israeli commitment that the use of the heavy water was for peaceful purposes, including an inspection clause.
According to Kerry’s letter, a major problem was that the heavy water sale had been initially treated as a commercial sale by the Norwegian firm NORATOM without appropriate vetting by political experts at the Foreign Ministry (like an earlier controversial sale of weapons to the Batista dictatorship in Cuba). Kerry asked the State Department to keep the transaction a secret and so it stayed until the late 1970s when the Stockholm Institute of Peace Research disclosed it. Kerry did not mention the British role in the affair and may, in fact, have forgotten it.[21]
Document 21: “Clearly Apparent Lack of Candor”
State Department telegram 502 to U.S. Embassy Tel Aviv, 31 December 1960, Secret
Source: Dwight D. Eisenhower Library, Dwight D. Eisenhower Papers, White House Office, Office of the Staff Secretary, International Series, box 8, Israel (3)
This telegram, originally published in the FRUS in an excised version, showed how unhappy the State Department was with Ben-Gurion’s explanation of the Dimona reactor: his answers “appear evasive.” The State Department saw the “clearly apparent lack of candor [as] difficult to reconcile with [the] confidence which had traditionally characterized U.S.-Israel relations.” To restore confidence, Israel needed to answer questions about its plans to dispose of plutonium, the application of safeguards to plutonium produced, visits by IAEA or other scientists to the reactor site, and whether there were plans to build a third reactor. Moreover, “can Israel state unequivocally that it has no plans for producing nuclear weapons?”
Document 22: “Until All Reactors Are Treated as Equals”
Embassy Tel Aviv telegram 625, 4 January 1961, as summarized in a “Chronology of Israel Assurances of Peaceful Use of Atomic Energy and Related Events,” enclosed with a “Memorandum from Benjamin Read, Executive Secretary, Department of State, for McGeorge Bundy, The White House, “Israel’s Assurances Concerning Use of Atomic Energy,” 18 March 1964, Secret, published as document number 9 in National Security Archive Electronic Briefing Book No. 432
In early January, Ambassador Reid had a meeting with Ben-Gurion, who provided answers to the State Department’s questions. The reporting telegram remains classified at the National Archives but a summary is available. The essence of the matter, according to Ben-Gurion, was that: 1) Israel “has no plans for producing nuclear weapons,” 2) Israel had no plutonium but “as far as we know” returning the plutonium produced by the reactor was a “condition” imposed by the country (France) that sold the uranium, 3) it would not accept IAEA inspection, especially if Russians were involved, or international safeguards “until all reactors are treated as equals,” 3) visits by representatives of “friendly powers” were possible, and 4) Israel had absolutely no plans for a third reactor. How State Department officials interpreted these statements remains unknown, but some may have seen the statement about nuclear weapons as equivocal and evasive.[22]
Document 23: “Damaging Air of Secrecy or Suspicions”
State Department telegram 2821 to U.S. Embassy Paris, 6 January 1961, Secret
Source: Dwight D. Eisenhower Library, Dwight D. Eisenhower Papers, White House Office, Office of the Staff Secretary, International Series, box 8, Israel (3)
Believing that neither France nor Israel had been forthright and that the lack of candor had damaging implications for Middle East stability, Herter asked U.S. Ambassador Amory Houghton to meet with Couve de Murville and discuss his earlier statement about the French-Israeli nuclear project. If the Dimona project is a “large scale production reactor,” the French need to be “unequivocally clear that [their] assistance is directed solely to peaceful uses.” The reply to this telegram is not yet available, but the substance can be found in Document 26.
Documents 24A-B: Molotov: “I Stayed Awake All Night and Worried”
A: U.S. Mission to International Atomic Energy Agency (Vienna) telegram 1087 to State Department, 11 January 1961, Secret
B: State Department telegram 1194 to U.S. Mission to International Atomic Energy Agency (Vienna), 13 January 1961, Secret
Source for both: RG 59, Central Decimal Files 1960-1963, 398.1901-IAEA/1-1161
The U.S. Mission to the IAEA which had been in the forefront of U.S. efforts to develop an effective safeguards policy, asked for policy guidance if the Dimona issue came up for debate at the upcoming meeting of the Board of Governors. Ben-Gurion’s declaration to the Knesset that the reactor was for peaceful purposes was “hardly adequate” because the Mission had been at loggerheads with the Soviets and the Indians who had argued that assurances were the only safeguards that were needed. Recognizing that the Israeli situation would be used to support arguments for strong safeguards, Vayecheslav Molotov, one of the senior Soviet representatives to the Agency (and once Stalin’s right hand man) sarcastically commented that he had “stayed awake all night and worried” when he read about the Israel reactor program.
Following the approach recommended by Lewis Jones and others, the State Department advised the IAEA Mission of the importance of promoting a “period of calm.” In discussions in Vienna, the Mission should “avoid impugning” Israeli statements about peaceful purposes but also avoid a “whitewash” of the Israeli position. It was in the U.S. “interest” to send scientists to visit the reactor site and to get “first-hand information” but the Department noted that the Israelis have “reacted strongly” against any proposal for inspection and are not likely to change in the “immediate future.”
Document 25: “Some Israel[i] Evasions”
Murat W. Williams to William L. Hamilton, “A Catalog of Replies Regarding the Reactor,” 16 January 1961, Secret, with transcript attached
Source: RG 59, Records of Special Assistant to the Secretary of State for Atomic Energy and Outer Space, 1948-1961, box 501, Z1.50 Country File Israel f. Reactor 1961, Part 1 of 2
On his way to an ambassadorship in El Salvador, Murat W. Williams, who had just left his post as deputy chief of mission at the Embassy in Tel Aviv, provided background on the various Israeli cover stories for the Dimona project. Apparently the most truthful response came from Minister of Development director general Eliezer Preminger who told Jack [John James] Haggerty, then the USOM director, that the site was a “military installation” and that he should ask the military attaché to look into it. Williams recounted the dissembling responses from Addy Cohen and other Israeli Foreign Liaison Officers [FLO] who, as noted elsewhere in this posting, had told Ambassador Reid and others that the construction site was for a textile factory, metallurgical research, meteorological installation, and part of a research program at a “new university.”
Document 26: “Israel Has No Plans for the Production of Atomic Weapons”
Letter, William B. McComber, Assistant Secretary of State for Congressional Affairs, to James T. Ramey, Executive Director, Joint Congressional Committee on Atomic Energy, 19 January 1961, Secret
Source: FOIA release
As the Eisenhower administration was winding down, the State Department submitted this comprehensive report (also published in the FRUS) to the Joint Committee on Atomic Energy as a summary of all the information that the State Department had received officially from the Israeli and French governments in response to questions about the Dimona reactor. One must assume this body of information was used to brief the incoming Kennedy administration on what the Israelis and French had said on the record. Some of the answers may have been provided in response to the State Department telegram sent on 31 December (Document 21 above), for example, the statement that all plutonium to be produced in Dimona would be returned to France, and the ambiguous assurance that “Israel has no plans for the production of atomic weapons.” As for the French, they asserted that plutonium produced in the reactor would be returned to France, that France and Israel had agreed that the reactor was for “exclusively peaceful use,” and that French inspectors would be visiting the reactor. Oddly, what is missing is a claim, positive or negative, whether the complex actually included a chemical separation plant that could produce plutonium. Also, the financial estimate was a little different from that cited before (Document 13A).
Documents 27A-B: The Post-Mortem
A: U.S. Joint Atomic Energy Intelligence Committee, “Post-Mortem on SNIE 100-8-60: Implications of the Acquisition by Israel of a Nuclear Weapons Capability,” 31 January 1961, Draft, Secret
B: Memorandum, Phillip Farley to Hugh Cumming, Director of Intelligence and Research, “Post-Mortem on SNIE 100-8-60,” 28 January 1961
Source: RG 59, Records of Special Assistant to the Secretary of State for Atomic Energy and Outer Space, 1948-1961, box 501, Z1.50 Country File Israel f. Reactor 1961, Part 1 of 2
This “post-mortem” study on SNIE 100-8-60 is one of the most intriguing documents in this collection. Its aim was to explain why the US intelligence community had failed to detect in real time the Israeli nuclear project, and indeed how late it was in making that determination. The chronology, on pages 8 through 17, provides an account of what was known, and when, about the Israeli nuclear program, concluding that Washington might have seen through Israeli “secrecy or deception” and better understood Israeli intentions at least a year earlier if the “atomic energy intelligence community had properly interpreted” the available information. In essence, the overall conclusion was that the root cause of the delay was not so much the absence of information as that some important reports and items of information had been lost in the shuffle and the dots not properly connected.
As the classification of this document is only “secret,” and the document is relatively brief and deliberately vague about the intelligence means and sources employed in the final determination (e.g. it does not refer explicitly to the U-2 flights), it is possible that the intelligence community had more sensitive information that it excluded from this version of the post-mortem or that a more thorough report on the subject existed with higher classification.
[Note: Several of the documents reproduced above were first published 1998 in “Israel and the Bomb” edited by Avner Cohen.]
Thanks to Ori Rabinowitz (Tel Aviv University), Sharik Bashir (University of Michigan) and Alexandra Hale (George Washington University) for their assistance with this project.
NOTES
[1] Shimon Peres, Battling for Peace: Memoirs, Edited by David Landau (London: Weidenfeld and Nicolson, 1995), 133-35.
[2] Avner Cohen, Israel and the Bomb (New York: Columbia University Press, 1998), 44-47, 50-52, 65, 81-82.
[3] Cohen, Israel and the Bomb, 49-55, 57-60.
[4] Cohen, Israel and the Bomb, 32-34, 60-62, 83, 87.
[5] Note by Avner Cohen: During interviews I conducted in the 1990s for Israel and the Bomb I heard from different people more conspiratorial explanations for the U.S. intelligence failure on Dimona. Some interviewees claimed that certain people in the U.S. intelligence community were sympathetic to the Israelis and deliberately concealed or bypassed certain information instead of passing it along. For example, the late John Hadden, the CIA station chief in Tel Aviv from 1964-68, held that view strongly. He asked me to treat his suspicions with discretion so I did not publicize them when he was alive. According to Seymour Hersh’s The Samson Option (New York: Random House, 1991), the AEC chairman, Lewis Strauss, “knew as much about Dimona as anybody in the intelligence community by the time he left the AEC in 1958. There is no evidence, however, that he raised questions about the Israeli weapons program while in government. He most certainly did not tell McCone about it.” (83, 90) There are others who also believed that senior officials of the Eisenhower administration, including President Eisenhower himself , had known about Dimona early on but decided not to interfere. According to Dino A. Brugioni, who served at the CIA Photographic Intelligence Center, when U-2 photos of the excavations of the Beersheba site were taken sometimes in early-mid 1958 the activity was determined to be a “probable” nuclear-related site. The photos were shown by the Center director, Arthur C. Lundah, to both President Eisenhower and AEC chair Lewis Strauss, but neither reacted. “Lundhal and Brugioni were left with the impression that Eisenhower wanted Israel to acquire nuclear weapons” (Israel and the Bomb, 83). The same anecdote appears in much greater detail in Hersh’s The Samson Option (50-59).
[6] Cohen, Israel and the Bomb, 90-95; Avner Cohen, The Worst-Kept Bargain (New York: Columbia University Press, 2010), 60-62.
[7] Choosing this strategy created long-terms risks and problems as well. In essence, it made it much more difficult for Israel to extract any security benefits from, or for, the nuclear project, even if Israel was willing at some point in the future to trade the project’s products for other security benefits. For a more detailed analysis of this evasive disclosure strategy, see Cohen, The Worst-Kept Secret, 61-62.
[8] When we refer to intelligence community, we mean not only the CIA, but also intelligence offices of the Atomic Energy Commission, the Department of State, and the armed services, all of which played a role in colleting and/or analyzing information about Dimona.
[9] On the French-Israeli 1954 bilateral agreement of cooperation in the field of atomic energy, based on the Israeli patents, see Cohen, Israel and the Bomb, 32-34.
[10] Indeed, Bergmann and his IAEC were hardly consulted, let alone involved in the negotiations that Shimon Peres had conducted with the French. As became known years later, Peres, who was Dimona’s prime visionary and promoter, decided to compartmentalize and bypass Bergmann and the IAEC almost entirely about Dimona. In February 1958 all seven IAEC members except Bergmann resigned; the details of this incident remain obscure but it may have been a protest against the exclusion of the IAEC. There was even a time when Bergmann was not allowed to visit the Dimona site. See Cohen, Israel and the Bomb, 14-17, 67-71.
[11] Cohen, Israel and the Bomb, 16-17.
[12] For background, see Cohen, Israel and the Bomb, 60-62; Kristine Werdelin Bergan, editor, “The Norway-United Kingdom-Israel Heavy Water Deal, 1957-1959: New Translations from Norwegian Archives,” forthcoming electronic dossier for the Nuclear Proliferation International History Project.
[13] See “UK Helped Israel Get Nuclear Bomb,” BBC News, 4 August 2005; David Leigh, “US kept in the dark as secret nuclear deal was struck,” The Guardian, 3 August 2005; “Britain’s dirty secret: Exclusive – Secret papers show how Britain helped Israel make the A-bomb in the 1960s, ” The New Statesman, 13 March 2006. See also the Foreign Office Statement, 9 March 2006, BBC Two.
[14] Cohen, Israel and the Bomb, 62, 83.
[15] On the U-2 issue, Seymour Hersh provides a fascinating and persuasive account, but the recollections of key participants need to be supported by government records. See The Samson Option, at pages 50-58.
[16] Warren Kornberg, “Israel Reactor ‘Not Revealed to Us,’ Says McCone, Avoiding Word ‘Secret,'” The Washington Post, 19 December 1960. See also, Hersh, The Samson Option, 77.
[17] Ibid., 71-72, for McCone’s role in leaking to the New York Times.
[18] The U.S. Operations Mission managed U.S. foreign aid programs.
[19] “U.S. Welcomes Israel Promises on Reactor,” The Washington Post, 23 December 1960.
[20] Cohen, Israel and the Bomb, 92-93.
[21] In 1986, Norway asked Israel whether the heavy water had been used in ways that were consistent with the agreement’s “peaceful uses” conditions. See Charles R. Babcock, “Norway Eyes Israel’s Use of Nuclear Ingredient,”Washington Post, 10 November 1986.
[22] Cohen, Israel and the Bomb, 93-95.
Us Government Jobs, Us Government Type, Us Government Shutdown, Us Government Spending, Us Government Budget, Us Government Security Clearance, Us Government Debt, Us Government News, Us Government Bonds, Us Government Passport, Us Government Agencies, Us Government Auctions, Us Government Accountability Office, Us Government And Politics, Us Government Articles, Us Government Annual Budget, Us Government And Politics Apex Answers, Us Government Ap Test, Us Government Arms Contracts, Us Government Assets, Us Government Budget, Us Government Bonds, Us Government Branches, Us Government Budget 2017, Us Government Budget 2016, Us Government Book, Us Government Bookstore, Us Government Bond Rates, Us Government Buildings, Us Government Bids, Us Government Contracts, Us Government Current Events, Us Government Corruption, Us Government Corporations, Us Government Checks And Balances, Us Government Credit Rating, Us Government Crash Course, Us Government Copyright Website, Us Government Chart, Us Government Clearance, Us Government Debt, Us Government Deficit, Us Government Definition, Us Government Debt To Gdp, Us Government Debt Clock, Us Government Data, Us Government Diagram, Us Government During Ww2, Us Government Documents, Us Government Definition Of Terrorism, Us Government Expenditures, Us Government Employees, Us Government Explained, Us Government Executive Branch, Us Government Employee Salaries, Us Government Exam Review, Us Government Employment, Us Government Education, Us Government Experiments, Us Government Expenditures 2016, Us Government Fiscal Year, Us Government Forms, Us Government For Dummies, Us Government Final Exam, Us Government Facts, Us Government Final Exam Study Guide, Us Government Free Credit Report, Us Government Funding, Us Government Flow Chart, Us Government Fiscal Year 2017, Us Government Grants, Us Government Grant Department, Us Government Gold Coins, Us Government Games, Us Government Gsa, Us Government Gs Pay Scale, Us Government Grant Money, Us Government Global Entry, Us Government Green Card, Us Government Gdp, Us Government Holidays, Us Government Hiring Freeze, Us Government Holidays 2017, Us Government Hierarchy, Us Government History, Us Government Healthcare, Us Government Healthcare Spending, Us Government Hacked, Us Government Health Insurance, Us Government House, Us Government Internships, Us Government Income, Us Government Id, Us Government Interest Reported As Dividends, Us Government Interest, Us Government Interest Taxable, Us Government Irs, Us Government Issues, Us Government Issued Id, Us Government Intelligence Agencies, Us Government Jobs, Us Government Jobs Abroad, Us Government Jobs In Japan, Us Government Jobs In Italy, Us Government Jobs In Germany, Us Government Judicial Branch, Us Government Jobs In Europe, Us Government Jeopardy, Us Government Jobs In Utah, Us Government Jobs In California, Us Government Killed Mlk, Us Government Kahoot, Us Government Kill List, Us Government Killed Dog, Us Government Killed Family Dog, Us Government Key Terms, Us Government Killed Jfk, Us Government Kaspersky, Us Government Kodi, Us Government Kenya Travel, Us Government Logo, Us Government Line Of Succession, Us Government License Plates, Us Government Leaders, Us Government Land For Sale, Us Government Loans, Us Government Legislative Branch, Us Government Laws, Us Government Lies, Us Government Leaks, Us Government Mint, Us Government Mileage Rate, Us Government Manual, Us Government Mileage Rate 2017, Us Government Medicare, Us Government Movies, Us Government Military Spending, Us Government Memes, Us Government Module 3 Dba, Us Government Mind Control, Us Government News, Us Government Net Worth, Us Government News Today, Us Government Number, Us Government Name, Us Government Notes, Us Government No Call List, Us Government News Articles, Us Government National Debt, Us Government Number Of Employees, Us Government Org Chart, Us Government Officials, Us Government Organizational Chart, Us Government Offices, Us Government Obligations, Us Government Organizations, Us Government Owned Companies, Us Government Official Mail, Us Government Online Textbook, Us Government Officials 2017, Us Government Passport, Us Government Per Diem, Us Government Printing Office, Us Government Passport Renewal, Us Government Pay Scale, Us Government Plates, Us Government Positions, Us Government Phone Number, Us Government Pension, Us Government Procurement, Us Government Quizlet, Us Government Quiz, Us Government Questions, Us Government Quotes, Us Government Quarters, Us Government Quizlet Chapter 2, Us Government Questions And Answers, Us Government Questions Test Practice, Us Government Quizlet Chapter 8, Us Government Quizlet Chapter 4, Us Government Revenue, Us Government Regents, Us Government Review, Us Government Revenue 2016, Us Government Retirement, Us Government Ranks, Us Government Renew Passport, Us Government Rfp, Us Government Revenue Sources, Us Government Regulations, Us Government Shutdown, Us Government Spending, Us Government Security Clearance, Us Government Shutdown 2017, Us Government System, Us Government Surplus, Us Government Spending Breakdown, Us Government Securities, Us Government Salaries, Us Government Savings Bonds, Us Government Type, Us Government Textbook, Us Government Travel Warnings, Us Government Tax Forms, Us Government Travel, Us Government Textbook Pdf, Us Government Test, Us Government Tax Revenue, Us Government Time, Us Government Trivia, Us Government Unclaimed Money, Us Government Unit 4, Us Government Unit 5, Us Government Unit 3, Us Government Unit 2 Quizlet, Us Government Unit 1, Us Government Ufo, Us Government Unit 5 Test Answers, Us Government Unit 1 Test, Us Government Unit 3 Test, Us Government Vocabulary, Us Government Visa, Us Government Vehicles, Us Government Videos, Us Government Vehicle Auction, Us Government Value Of Human Life, Us Government Vs German Government, Us Government Vs Ancient Rome, Us Government Venezuela, Us Government Veterans, Us Government Website, Us Government Worksheets, Us Government Wiki, Us Government Weather, Us Government Weed, Us Government Word Search, Us Government Whip, Us Government White Papers, Us Government Web Standards, Us Government Waste, Us Government X Files, Us Government Xml, Us Government Keystone Xl Pipeline, Us Government Windows Xp, Us Government Planet X, Us Government Yearly Budget, Us Government Yield Curve, Us Government Youtube, Us Government Yearly Revenue, Us Government Yields, Us Government Yellowbook, Us Government Year End, Us Government Youth Programs, Us Government Yearly Spending, Us Government Yemen, Us Government Zombie Plan, Us Government Zip Codes, Us Government Zombie, Us Government Zip Code Database, Us Government Zika, Us Government Zombie Protocol, Us Government Zero Coupon Bonds, Us Government Zombie Contingency Plan, Us Government Zombie Survival Guide, Us Government Zip Code Information, Israel News, Israel Map, Israel Flag, Israel Keyes, Israel Houghton, Israel Kamakawiwo’ole, Israel Palestine, Israel Population, Israel Houghton Kids, Israel Capital, Israel And Palestine, Israel Airlines, Israel Abbreviation, Israel Airport, Israel Apartheid, Israeli Army, Israel Anti Boycott Act, Israel Allies, Israel And Syria, Israel And New Breed, Israel Bonds, Israel Broussard, Israel Birthright, Israel Bombs Syria, Israel Borders, Israel Bombing, Israel Boone, Israel Beaches, Israel Baseball Hat, Israeli Border Wall, Israel Capital, Israel Continent, Israel Country Code, Israel Consulate Chicago, Israeli Couscous, Israel Climate, Israel Cities, Israel Conflict, Israel Capital City, Israel Coins, Israel Del Toro, Israel Definition, Israel Defense Forces, Israel Duffus, Israel Demographics, Israel Desert, Israel Diamonds, Israel Discount Bank, Israel Desalination, Israel Declares Independence, Israel Englander, Israel Egypt War, Israel Exports, Israel Established, Israel Experts, Israel Egypt, Israeli Embassy, Israel Etf, Israel Enemies, Israel Education, Israel Flag, Israel Facts, Israel Founded, Israel Flag Emoji, Israeli Food, Israel Fun Facts, Israel Flights, Israel Finkelstein, Israel Free Spirit, Israel Flag Meaning, Israel Government, Israel Gdp, Israel Geography, Israel Gdp Per Capita, Israel God, Israel Gutierrez, Israel Gross, Israel Gonzalez, Israel Gun Laws, Israel Gaza, Israel Houghton, Israel Houghton Kids, Israel History, Israel Hands, Israel Hayom, Israel Houghton Songs, Israel Holidays, Israel Hodish, Israel Houghton You Are Good, Israel Houghton Wedding, Israel Iz Kamakawiwo\u02bbole, Israel Independence Day, Israel Independence, Israel Iron Dome, Israel In Hebrew, Israel Isis, Israel In The Bible, Israel Iran, Israel India, Israel Idonije, Israel Jerusalem, Israel Jewish, Israel Jordan, Israel Jewish Population, Israel Jimenez, Israel Jesus, Israel Jobs, Israel Jacob, Israel Jewelry, Israel Juarbe, Israel Keyes, Israel Kamakawiwo’ole, Israel Kamakawiwo’ole Wife, Israel Kamakawiwo’ole Songs, Israel Kamakawiwo’ole Somewhere Over The Rainbow, Israel Kristal, Israel Kali A K, Israel Kibbutz, Israel Kamakawiwo’ole Over The Rainbow, Israel Kamakawiwo’ole Net Worth, Israel Language, Israel Location, Israel Local Time, Israel Leader, Israel Liberzon, Israel Landscape, Israel Life Expectancy, Israel Literacy Rate, Israel Lebanon, Israel Lebanon War, Israel Map, Israel Meaning, Israel Museum, Israel Money, Israel Movie, Israel Music, Israel Middle East, Israel My Glory, Israel Meme, Israeli Military, Israel News, Israel Name Meaning, Israel National News, Israel National Anthem, Israel News Live, Israel Nash, Israel News Today, Israel Natural Resources, Israel Nukes, Israel Name, Israel On Map, Israel Of God, Israel Outdoors, Israel On World Map, Israel Official Language, Israel On The House, Israel Oil, Israel Or Palestine, Israel Outline, Israel Outlet, Israel Palestine, Israel Population, Israel Palestine Map, Israel Putnam, Israel Post, Israeli Prime Ministers, Israel Palestine Conflict Timeline, Israel Pictures, Israel Population 2017, Israel Pakistan, Israel Quotes, Israel Quizlet, Israel Qatar, Israel Quest, Israel Qatar Relations, Israel Quiz, Israel Questions, Israel Queen, Israel Quality Of Life, Israel Quest Reviews, Israel Religion, Israel Russia, Israel Regardie, Israel Real Estate, Israel Rodriguez, Israel Rose, Israel Radio, Israel Region, Israel Resources, Israel Railways, Israel Syria, Israel Settlements, Israel Size, Israel Somewhere Over The Rainbow, Israel Six Day War, Israel Square Miles, Israel Supports Isis, Israel Saudi Arabia, Israel Symbols, Israel Shamir, Israel Time, Israel Time Now, Israel Tours, Israel Travel, Israel Today, Israel Tourism, Israel Trump, Israel Trip, Israel Third Temple, Israel Timeline, Israel United In Christ, Israel Us Relations, Israel Update, Israel United In Christ Videos, Israel Un, Israel Unlimited, Israel Unemployment Rate, Israel Us Embassy, Israel Universal Health Care, Israel University, Israel Vs Palestine, Israel Vibration, Israel Video Network, Israel Vacation, Israel Visa, Israel Vs Iran, Israel Vaccinations, Israel Visa Requirements, Israel Vs Syria, Israel Vs Judah, Israel Wall, Israel World Baseball Classic, Israel Weather, Israel War, Israeli Women, Israel World Baseball Classic Roster, Israel Wikipedia, Israel World Map, Israel West Bank, Israel Western Wall, Israel X Factor, Israel Xp, Israeli X95, Israel X Factor 2016, Israel X, Israel X Factor 2017, Israeli X, Israel X Factor Judges, Israel Xbmc, Israel X Band Radar, Israel Youtube, Israel Year Of Independence, Israel Year, Israel Y Palestina, Israel Yad Vashem, Israel Yemen, Israel Young, Israel Y Moises, Israel Youtube Channel, Israel Yearly Weather, Israel Zangwill, Israel Zip Code, Israel Zamora, Israel Zin River, Israel Zionist, Israel Zolli, Israel Z, Israel Zangwill Melting Pot, Israeli Zoo, Israel Zip Code Lookup, Nuclear Bomb, Nuclear Energy, Nuclear Fusion, Nuclear War, Nuclear Family, Nuclear Fission, Nuclear Stress Test, Nuclear Option, Nuclear Triad, Nuclear Medicine, Nuclear Arms Race, Nuclear Attack, Nuclear Accidents, Nuclear Assault, Nuclear Arsenal, Nuclear Age, Nuclear Arms Race Cold War, Nuclear Apocalypse, Nuclear Alarm, Nuclear Annihilation, Nuclear Bomb, Nuclear Blast, Nuclear Blast Radius, Nuclear Bomb Test, Nuclear Bunker, Nuclear Bomb Shelter, Nuclear Binding Energy, Nuclear Blast Records, Nuclear Bone Scan, Nuclear Bomb Video, Nuclear Chemistry, Nuclear Clock, Nuclear Countries, Nuclear Chemistry Worksheet, Nuclear Charge, Nuclear Codes, Nuclear Cataract, Nuclear Chain Reaction, Nuclear Cardiology, Nuclear Cooling Tower, Nuclear Definition, Nuclear Decay, Nuclear Disasters, Nuclear Deterrence, Nuclear Decay Worksheet, Nuclear Disarmament, Nuclear Dna, Nuclear Detonation, Nuclear Decay Worksheet Answers, Nuclear Division, Nuclear Energy, Nuclear Explosion, Nuclear Energy Definition, Nuclear Engineering, Nuclear Envelope, Nuclear Engineer Salary, Nuclear Energy Pros And Cons, Nuclear Energy Examples, Nuclear Explosion Gif, Nuclear Equations, Nuclear Fusion, Nuclear Family, Nuclear Fission, Nuclear Fusion Definition, Nuclear Football, Nuclear Fission Definition, Nuclear Fallout, Nuclear Family Definition, Nuclear Fusion Reactor, Nuclear Fallout Map, Nuclear Glass, Nuclear Gas Mask, Nuclear Gandhi, Nuclear Gun, Nuclear Gif, Nuclear Generator, Nuclear Gravity Bomb, Nuclear Games, Nuclear Gas, Nuclear Grenade, Nuclear Holocaust, Nuclear Heart Test, Nuclear Half Life, Nuclear Hazard Symbol, Nuclear Holocaust Movies, Nuclear Hormone Receptors, Nuclear Hoax, Nuclear History, Nuclear Household, Nuclear Hand Grenade, Nuclear Imaging, Nuclear Incidents, Nuclear In Spanish, Nuclear Isotopes, Nuclear Icebreaker, Nuclear Icbm, Nuclear Issues, Nuclear Industry, Nuclear Icon, Nuclear Instruments And Methods, Nuclear Jobs, Nuclear Japan, Nuclear Jet Engine, Nuclear Jokes, Nuclear Jellyfish, Nuclear Jet, Nuclear Js, Nuclear Jobs Overseas, Nuclear Jobs Florida, Nuclear Jellyfish Of New Jersey, Nuclear Korea, Nuclear Korean Noodles, Nuclear Kidney Test, Nuclear Kenyan Sand Boa, Nuclear Kinetic Energy, Nuclear Key, Nuclear Kit, Nuclear Keychain, Nuclear Kill Radius, Nuclear Kid, Nuclear Localization Signal, Nuclear Lamina, Nuclear Launch Codes, Nuclear Logo, Nuclear Lyrics, Nuclear Launch Detected, Nuclear Lake, Nuclear Launch, Nuclear Lamins, Nuclear Leak, Nuclear Medicine, Nuclear Medicine Technologist, Nuclear Membrane, Nuclear Missile, Nuclear Meltdown, Nuclear Membrane Function, Nuclear Map, Nuclear Membrane Definition, Nuclear Medicine Technologist Jobs, Nuclear Magnetic Resonance, Nuclear Non-proliferation Treaty, Nuclear News, Nuclear Nations, Nuclear North Korea, Nuclear Notation, Nuclear Noodles, Nuclear Norm, Nuclear Navy, Nuclear Nadal, Nuclear Nucular, Nuclear Option, Nuclear Oncology, Nuclear Option 2013, Nuclear Option Harry Reid, Nuclear Overhauser Effect, Nuclear Outage, Nuclear Operator Salary, Nuclear Or Nucular, Nuclear Operator, Nuclear Option Fallout 4, Nuclear Power, Nuclear Power Plants, Nuclear Proliferation, Nuclear Power Plants In Us, Nuclear Physics, Nuclear Physicist, Nuclear Power Definition, Nuclear Power Pros And Cons, Nuclear Pharmacy, Nuclear Power Plants In Texas, Nuclear Quotes, Nuclear Quadrupole Resonance, Nuclear Questions, Nuclear Quiz, Nuclear Quality Assurance, Nuclear Quizlet, Nuclear Quadrupole Moment, Nuclear Quantum Effects, Nuclear Quality Assurance Jobs, Nuclear Quantum Numbers, Nuclear Reactor, Nuclear Radiation, Nuclear Reaction, Nuclear Regulatory Commission, Nuclear Reactor Definition, Nuclear Reactor Diagram, Nuclear Receptor, Nuclear Reactors In Us, Nuclear Rocket, Nuclear Reaction Worksheet, Nuclear Stress Test, Nuclear Symbol, Nuclear Submarine, Nuclear Sclerosis, Nuclear Sign, Nuclear Shadow, Nuclear Shelter, Nuclear Secrecy, Nuclear Siren, Nuclear Scan, Nuclear Triad, Nuclear Throne, Nuclear Test Ban Treaty, Nuclear Test, Nuclear Technician, Nuclear Threat, Nuclear Throne Together, Nuclear Throne Wiki, Nuclear Technology, Nuclear Test Ban Treaty Apush, Nuclear Umbrella, Nuclear Uranium, Nuclear Uses, Nuclear Utilization Theory, Nuclear Ultrasound, Nuclear Us, Nuclear Usa, Nuclear Unit, Nuclear Union, Nuclear Ukraine, Nuclear Vs Atomic, Nuclear Vote, Nuclear Vs Nucular, Nuclear Valdez, Nuclear Vs Solar, Nuclear Vs Coal, Nuclear Vs Hydrogen Bomb, Nuclear Vs Extended Family, Nuclear Vs Mitochondrial Dna, Nuclear Video, Nuclear War, Nuclear Weapons, Nuclear Winter, Nuclear Waste, Nuclear Waste Disposal, Nuclear War Now, Nuclear Weapons Definition, Nuclear War Movies, Nuclear Waste Policy Act, Nuclear Weapons Facts, Nuclear X Ray, Nuclear X, Nuclear Explosion, Nuclear X Met Rx, Nuclear Explosion Gif, Nuclear X Ray Technician Salary, Nuclear Explosion In Space, Nuclear Explosion Video, Nuclear Explosion Simulator, Nuclear Explosion Radius, Nuclear Yield, Nuclear Yield Map, Nuclear Youtube, Nuclear Yellow, Nuclear Yellow Cake, Nuclear Yacht, Nuclear Yemen, Nuclear Ymir, Nuclear Yap, Nuclear Yucca Mountain, Nuclear Zone, Nuclear Zomboy, Nuclear Zero, Nuclear Zombies, Nuclear Zomboy Lyrics, Nuclear Zone Theory, Nuclear Zone Hypothesis, Nuclear Zec, Nuclear Zone Terraforming Mars, Nuclear Zone In Russia, Secret Life Of Pets, Secret Service, Secret Garden, Secret World Legends, Secret Flying, Secret Life Of Bees, Secret Life Of Pets Cast, Secret Life Of The American Teenager, Secret Squirrel, Secret Shopper, Secret Agent Man, Secret Admirer, Secret Aardvark, Secret Agent, Secret Annex, Secret And Lies, Secret Agent Man Song, Secret App, Secret Asian Man, Secret Agent Man Lyrics, Secretbuilders, Secret Book, Secret Beach Kauai, Secret Beach, Secret Ballot, Secret Box, Secret Beach Maui, Secret Bay Dominica, Secret Base, Secret Band, Secret Circle, Secret Church, Secret Caverns, Secret Classroom Superpowers, Secret Codes, Secret Clinical Strength, Secret Clearance, Secret Circle Cast, Secret Conversations Facebook, Secret Cameras, Secret Deodorant, Secret Definition, Secret Diary Of A Call Girl, Secret Door, Secret Deodorant Coupons, Secret Diary, Secret Deodorant Commercial, Secret Decoder Ring, Secret Daughter, Secret Door Lyrics, Secret Empire, Secret Extensions, Secret Escapes, Secret Empire #1, Secret Empire Reading Order, Secret Entourage, Secret Empire #0, Secret Empire #2, Secret Eaters, Secret Emoji, Secret Flying, Secret Forest, Secret Forest Ep 11, Secret Falls Kauai, Secret Flask, Secret Formula, Secret Facebook Group, Secret Frappuccino, Secret For The Mad Lyrics, Secret Falls, Secret Garden, Secret Garden Song, Secret Garden Movie, Secret Garden Cafe, Secret Garden Musical, Secret Garden Lyrics, Secret Garden Denver, Secret Garden Book, Secret Google Games, Secret Garden Miami, Secret Hitler Rules, Secret Hitler Game, Secret History Of Twin Peaks, Secret Hitler Online, Secret Hair Extensions, Secret Handshake, Secret History, Secret Hotel Deals, Secret Heart, Secret Hiding Places, Secret In Their Eyes, Secret In Spanish, Secret Ingredient, Secret Island, Secret In Their Eyes Cast, Secret Invasion, Secret In N Out Menu, Secret Invisible Solid, Secret Island In Texas, Secret In French, Secret Jardin, Secret Jewels, Secret Journal, Secret Jobs, Secret Jamaica, Secret Jieun, Secret Jardin Lodge, Secret Journey Police, Secret Journey To Planet Serpo, Secret Jardin Dr90, Secret Kpop, Secret Keeper Girl, Secret Keeper, Secret Key, Secret Korean Drama, Secret Knock, Secret Knowledge, Secret Krabby Patty Formula, Secret Key Starting Treatment Essence, Secret Kingdom, Secret Life Of Pets, Secret Life Of Bees, Secret Life Of Pets Cast, Secret Life Of The American Teenager, Secret Love Song, Secret Life Of Walter Mitty, Secret Lab Chair, Secret Life Of An American Teenager Cast, Secret Language, Secret Life Of Pets Imdb, Secret Menu, Secret Menu Items, Secret Mage, Secret Menu Starbucks, Secret Menu In N Out, Secret Messages, Secret Meaning, Secret Movie, Secret Mountain Fort Awesome, Secret Mage Deck, Secret Nails, Secret Nyc, Secret Netflix, Secret Nail Salon, Secret Names, Secret Netflix Codes, Secret Numbers, Secret News, Secret Nature From Jeju Peeling Gel, Secret Nation, Secret Of Mana, Secret Of Nimh, Secret Of The Snowy Peaks, Secret Of The Cedars, Secret Of Kells, Secret Of Evermore, Secret Of The Wings, Secret Of Moonacre, Secret Of Mana Rom, Secret Of Mana 2, Secret Pizza, Secret Police, Secret Project Robot, Secret Place, Secret Passion Fruit, Secret Power, Secret Passages, Secret Pizza Party, Secret Paladin, Secret Place Lyrics, Secret Quotes, Secret Question, Secret Quest, Secret Questions To Ask, Secret Questions To Ask Siri, Secret Quests Ffxv, Secret Quests Skyrim, Secret Qr Codes, Secret Questions To Ask Alexa, Secret Quote Spongebob, Secret Romance, Secret Resorts, Secret Recipe, Secret Rooms, Secret Rare Pokemon Cards, Secret Rainbow Hair, Secret Rare Ultra Ball, Secret Rendezvous, Secret Relationship, Secret Roku Channels, Secret Service, Secret Squirrel, Secret Shopper, Secret Societies, Secret Synonym, Secret Starbucks Menu, Secret Service Jobs, Secret Sandwich Society, Secret Sisters, Secret Shopper Jobs, Secret Treasures, Secret Treasures Sleepwear, Secret Tunnel, Secret Things, Secret Tunnel Song, Secret The Pierces, Secret Thesaurus, Secret Travel, Secret Treasures Bra, Secret To Success, Secret Underground Cities, Secret Us Weapons, Secret Underground Bases, Secret Universe Of Names, Secret Underground, Secret Underground Medicine, Secret Upgrades Office Space, Secret Us Bases, Secret Us Military Bases, Secret Unscented, Secret Variety Training, Secret Village Of The Spellcasters, Secret Video Recorder, Secret Variety Training Ep 2, Secret Vault, Secret Vault 81, Secret Veneers, Secret Voice Recorder, Secret Video, Secret Volume, Secret World Legends, Secret Window, Secret Wood, Secret Wars, Secret Wood Rings, Secret World Legends Release Date, Secret World Of Arrietty, Secret Weapon, Secret Wars 2015, Secret Warriors, Secret X Folder, Secret Xtians, Secret Xscape, Secret X Folder Comic, Secret X, Secret Xbox One Gamerpics, Secret Xtend, Secret Xbox One Games, Secret Xbox One Codes, Secret X Folder Webtoon, Secret Youtube, Secret Yeahu, Secret Yellowstone, Secret Young Justice, Secret Youtube Videos, Secret Yosemite, Secret Youtube Tricks, Secret Youtube Website, Secret Yumiverse, Secret Yosemite Spots, Secret Zoo Series, Secret Zoo, Secret Zoo Book, Secret Zinger, Secret Zombies Calling Card, Secret Zodiac Sign, Secret Zion Hikes, Secret Zone, Secret Zombies Challenge Infinite Warfare, Secret Zombie Challenge
SECRET – FBI Finds “Minimal Correlation” Between Suicide Vests Used in Middle East and Europe
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Images of suicide vests and belts from an FBI’s intelligence note released after the November 2013 .
An analysis of recent suicide bombings throughout the Middle East, Europe and Africa by the FBI Terrorism Explosive Device Analytical Center (TEDAC) that was released after the terrorist attacks in Paris, France last month states that “suicide vest and belt improvised explosive devices (IEDs) in the Middle Eastern, African, and European regions likely . . . have minimal correlation” and do not indicate tactical migration.
Following the attacks in Paris, which featured seven separate suicide bombings, media coverage has focused on the prominent use of suicide vests as indicative a tactical shift for the Islamic State of Iraq and the Levant (ISIL). Though there are past examples of suicide attacks inside Europe, such as the 2005 London bombings, the use of suicide vests in the Paris attacks has been said to represent an entirely new type of threat, a tactic once relegated to the battlefields of Iraq and Syria now appearing in European cities. However, an External Intelligence Note issued by TEDAC on November 17 titled “Suicide Vest and Belt Improvised Explosive Device Tactics in the Middle Eastern, African, and European Regions Show Minimal Signs of Tactic Migration” and obtained by Public Intelligence presents a different view, attributing the tactical similarities to factors such as “available materials, training, and local or national counter-IED policies.”
While TEDAC would normally assume that “similarities between suicide vests and belts from different regions likely indicate common training or common IED facilitators,” the intelligence note states that these similarities “may be a product of independent open source research, thus resulting in a false link between devices and subjects.” Moreover, the similarities may “indicate tactic or construction influences” based on the nature of the devices and access to required materials. Similarities can include everything from “overall IED construction, wiring techniques, common explosives, initiators, switches, electronic diagrams, enhancements, and employment.”
When broadly examined, the types of “suicide vests and belt IEDs observed in each region” covered in the intelligence note “differ broadly in many characteristics, resulting in an inconclusive determination that the suicide vest and belt IEDs prevalent in any one area translate to tactic migration.”
A study by the Institute of National Security Studies found that there were approximately 370 suicide bombings in the Middle East region in 2014 claiming the lives of over 2,700 victims. Iraq, Yemen, Lebanon and Libya all saw a significant increase in the use of the tactic over the previous year. Prior to the attacks in Paris, suicide bombings in Europe have been primarily limited to Turkey and Russia.
| Middle East | Europe | Africa | |
| Common explosives used in suicide vests/belts | triacetone triperoxide (TATP), trinitrotoluene (TNT), Semtex, C4, Research Development Formula X (RDX), and pentaerythritol tetranitrate (PETN) | TNT and C4 | RDX, Ammonium Nitrate, and Urea Nitrate |
The intelligence note takes several quotes from an interview conducted by Der Spiegel with a captured ISIL leader named Abu Abdullah discussing the group’s target selection process and methods for constructing suicide vests. He describes how he used “explosive fill removed from artillery shells for car bombs” and “drilled open the shells of anti-aircraft guns to construct suicide belts because he believed the effect of the powder was more intense.” According to the interview, he would receive a potential bombers’ measurements in “advance from the leadership in order to be able to make a well-fitting belt” and “always had belts in different sizes prepared.”
Explosive vests in Yemen have also included similar design elements. A suicide bomber tied to Al Qaeda in the Arabian Peninsula (AQAP) was killed in July 2015 by Houthi forces prior to detonating his vest, allowing for forensic analysis. The device featured “dual grenade-pin detonators, a main charge wrapped with sheets of ball bearings, and detonation cord that was placed inside a pouch around the bomber’s waist.”
Similar to the Middle East, bombings in Turkey have often used either C4 or trinitrotoluene (TNT) in suicide vests. Vests used in the Middle East often included other high-powered explosives such as Semtex or Research Development Formula X (RDX) or triacetone triperoxide (TATP), the explosive that was reportedly used in the vests detonated during the Paris attacks.
Secret Life Of Pets, Secret Service, Secret Garden, Secret World Legends, Secret Flying, Secret Life Of Bees, Secret Life Of Pets Cast, Secret Life Of The American Teenager, Secret Squirrel, Secret Shopper, Secret Agent Man, Secret Admirer, Secret Aardvark, Secret Agent, Secret Annex, Secret And Lies, Secret Agent Man Song, Secret App, Secret Asian Man, Secret Agent Man Lyrics, Secretbuilders, Secret Book, Secret Beach Kauai, Secret Beach, Secret Ballot, Secret Box, Secret Beach Maui, Secret Bay Dominica, Secret Base, Secret Band, Secret Circle, Secret Church, Secret Caverns, Secret Classroom Superpowers, Secret Codes, Secret Clinical Strength, Secret Clearance, Secret Circle Cast, Secret Conversations Facebook, Secret Cameras, Secret Deodorant, Secret Definition, Secret Diary Of A Call Girl, Secret Door, Secret Deodorant Coupons, Secret Diary, Secret Deodorant Commercial, Secret Decoder Ring, Secret Daughter, Secret Door Lyrics, Secret Empire, Secret Extensions, Secret Escapes, Secret Empire #1, Secret Empire Reading Order, Secret Entourage, Secret Empire #0, Secret Empire #2, Secret Eaters, Secret Emoji, Secret Flying, Secret Forest, Secret Forest Ep 11, Secret Falls Kauai, Secret Flask, Secret Formula, Secret Facebook Group, Secret Frappuccino, Secret For The Mad Lyrics, Secret Falls, Secret Garden, Secret Garden Song, Secret Garden Movie, Secret Garden Cafe, Secret Garden Musical, Secret Garden Lyrics, Secret Garden Denver, Secret Garden Book, Secret Google Games, Secret Garden Miami, Secret Hitler Rules, Secret Hitler Game, Secret History Of Twin Peaks, Secret Hitler Online, Secret Hair Extensions, Secret Handshake, Secret History, Secret Hotel Deals, Secret Heart, Secret Hiding Places, Secret In Their Eyes, Secret In Spanish, Secret Ingredient, Secret Island, Secret In Their Eyes Cast, Secret Invasion, Secret In N Out Menu, Secret Invisible Solid, Secret Island In Texas, Secret In French, Secret Jardin, Secret Jewels, Secret Journal, Secret Jobs, Secret Jamaica, Secret Jieun, Secret Jardin Lodge, Secret Journey Police, Secret Journey To Planet Serpo, Secret Jardin Dr90, Secret Kpop, Secret Keeper Girl, Secret Keeper, Secret Key, Secret Korean Drama, Secret Knock, Secret Knowledge, Secret Krabby Patty Formula, Secret Key Starting Treatment Essence, Secret Kingdom, Secret Life Of Pets, Secret Life Of Bees, Secret Life Of Pets Cast, Secret Life Of The American Teenager, Secret Love Song, Secret Life Of Walter Mitty, Secret Lab Chair, Secret Life Of An American Teenager Cast, Secret Language, Secret Life Of Pets Imdb, Secret Menu, Secret Menu Items, Secret Mage, Secret Menu Starbucks, Secret Menu In N Out, Secret Messages, Secret Meaning, Secret Movie, Secret Mountain Fort Awesome, Secret Mage Deck, Secret Nails, Secret Nyc, Secret Netflix, Secret Nail Salon, Secret Names, Secret Netflix Codes, Secret Numbers, Secret News, Secret Nature From Jeju Peeling Gel, Secret Nation, Secret Of Mana, Secret Of Nimh, Secret Of The Snowy Peaks, Secret Of The Cedars, Secret Of Kells, Secret Of Evermore, Secret Of The Wings, Secret Of Moonacre, Secret Of Mana Rom, Secret Of Mana 2, Secret Pizza, Secret Police, Secret Project Robot, Secret Place, Secret Passion Fruit, Secret Power, Secret Passages, Secret Pizza Party, Secret Paladin, Secret Place Lyrics, Secret Quotes, Secret Question, Secret Quest, Secret Questions To Ask, Secret Questions To Ask Siri, Secret Quests Ffxv, Secret Quests Skyrim, Secret Qr Codes, Secret Questions To Ask Alexa, Secret Quote Spongebob, Secret Romance, Secret Resorts, Secret Recipe, Secret Rooms, Secret Rare Pokemon Cards, Secret Rainbow Hair, Secret Rare Ultra Ball, Secret Rendezvous, Secret Relationship, Secret Roku Channels, Secret Service, Secret Squirrel, Secret Shopper, Secret Societies, Secret Synonym, Secret Starbucks Menu, Secret Service Jobs, Secret Sandwich Society, Secret Sisters, Secret Shopper Jobs, Secret Treasures, Secret Treasures Sleepwear, Secret Tunnel, Secret Things, Secret Tunnel Song, Secret The Pierces, Secret Thesaurus, Secret Travel, Secret Treasures Bra, Secret To Success, Secret Underground Cities, Secret Us Weapons, Secret Underground Bases, Secret Universe Of Names, Secret Underground, Secret Underground Medicine, Secret Upgrades Office Space, Secret Us Bases, Secret Us Military Bases, Secret Unscented, Secret Variety Training, Secret Village Of The Spellcasters, Secret Video Recorder, Secret Variety Training Ep 2, Secret Vault, Secret Vault 81, Secret Veneers, Secret Voice Recorder, Secret Video, Secret Volume, Secret World Legends, Secret Window, Secret Wood, Secret Wars, Secret Wood Rings, Secret World Legends Release Date, Secret World Of Arrietty, Secret Weapon, Secret Wars 2015, Secret Warriors, Secret X Folder, Secret Xtians, Secret Xscape, Secret X Folder Comic, Secret X, Secret Xbox One Gamerpics, Secret Xtend, Secret Xbox One Games, Secret Xbox One Codes, Secret X Folder Webtoon, Secret Youtube, Secret Yeahu, Secret Yellowstone, Secret Young Justice, Secret Youtube Videos, Secret Yosemite, Secret Youtube Tricks, Secret Youtube Website, Secret Yumiverse, Secret Yosemite Spots, Secret Zoo Series, Secret Zoo, Secret Zoo Book, Secret Zinger, Secret Zombies Calling Card, Secret Zodiac Sign, Secret Zion Hikes, Secret Zone, Secret Zombies Challenge Infinite Warfare, Secret Zombie Challenge, Suicide Squad, Suicide Hotline, Suicide Squad 2, Suicide Squad Cast, Suicide Boys, Suicide Quotes, Suicide Forest, Suicide Doors, Suicide Squad Full Movie, Suicide Squad Joker, Suicide Awareness, Suicide Awareness Month, Suicide Awareness Ribbon, Suicide Attempt, Suicide Ann Arbor, Suicide Assessment, Suicide Awareness Day, Suicide Squad, Suicide Articles, Suicide Art, Suicide Boys, Suicide Bridge, Suicide By Cop, Suicide Bomber, Suicide Boys Merch, Suicide Boys Tour, Suicide Bunny, Suicide Boys Lyrics, Suicide Blonde, Suicide Band, Suicide Chat, Suicide Club, Suicide Contagion, Suicide Chat Line, Suicide Clutch, Suicide Challenge, Suicide Cluster, Suicide Caught On Tape, Suicide Cult, Suicide Causes, Suicide Doors, Suicide Definition, Suicide Disease, Suicide Drawings, Suicide Duck, Suicide Drink, Suicide Detroit, Suicide Documentary, Suicide Door Kit, Suicide Depression, Suicide Exercise, Suicide Emoji, Suicide Epidemic, Suicide Essay, Suicide Encouragement, Suicide Etymology, Suicide Effects, Suicide Evo, Suicide Education, Suicide Edits, Suicide Forest, Suicide Facts, Suicide Forest Movie, Suicide Facebook Live, Suicide Forum, Suicide Forest Stories, Suicide From Bullying, Suicide Forest Bodies, Suicide Facts 2017, Suicide For Dummies, Suicide Gif, Suicide Games, Suicide Grip, Suicide Grosse Pointe South, Suicide Gun, Suicide Golden Gate Bridge, Suicide Groups, Suicide Grip Bench, Suicide Grosse Pointe, Suicide Girls Blackheart Burlesque, Suicide Hotline, Suicide Hotline Text, Suicide Helpline, Suicide Hotline Michigan, Suicide Hotline Chat, Suicide Hotline Song, Suicide Help Chat, Suicide Handle, Suicide Howell Mi, Suicide Helmet, Suicide Is Painless, Suicide Is Badass, Suicide Ideation, Suicide In The Bible, Suicide Is Painless Lyrics, Suicide In Michigan, Suicide In Spanish, Suicide In Detroit, Suicide In Japanese, Suicide Is Not Selfish, Suicide Jokes, Suicide Jump, Suicide Jumpers, Suicide Jack, Suicide James, Suicide Joker, Suicide Jockey, Suicide Japan, Suicide Japanese, Suicide Jump Liveleak, Suicide Kings, Suicide Knob, Suicide King Card, Suicide Kings Cast, Suicide Kale, Suicide King Isaac, Suicide Kid Meme, Suicide Kermit, Suicide King Tattoo, Suicide Krannert, Suicide Letters, Suicide Lyrics, Suicide Line, Suicide Lane, Suicide Lifeline, Suicide Liveleak, Suicide Live, Suicide Lansing Mi, Suicide Life Insurance, Suicide Live Stream, Suicide Machines, Suicide Meme, Suicide Mouse, Suicide Movies, Suicide Meaning, Suicide Michigan, Suicide Machines Tour, Suicide Mission, Suicide Mickey, Suicide Mission Mass Effect 2, Suicide Notes, Suicide Number, Suicide Notes Book, Suicide News, Suicide Notes From Beautiful Girls, Suicide Nets, Suicide Northville, Suicide Note Poem, Suicide Note Lyrics, Suicide Netflix, Suicide On Facebook Live, Suicide On Camera, Suicide Online Chat, Suicide On Live Tv, Suicide On Video, Suicide On Facebook, Suicide Off Egg Rock Analysis, Suicide On Fb Live, Suicide Ocd, Suicide Organizations, Suicide Prevention, Suicide Poems, Suicide Prevention Month, Suicide Pact, Suicide Prevention Quotes, Suicide Plant, Suicide Prevention Chat, Suicide Pics, Suicide Prevention Ribbon, Suicide Pit Lyrics, Suicide Quotes, Suicide Quiz, Suicide Questions, Suicide Quotes Tumblr, Suicide Quotes Sad, Suicide Squad, Suicide Questionnaire, Suicide Quotes Images, Suicide Queen, Suicide Q, Suicide Rates, Suicide Room, Suicide Risk Assessment, Suicide Ribbon, Suicide Rate By Country, Suicide Rates By State, Suicide Rates In The Us, Suicide Risk Factors, Suicide Room Full Movie, Suicide Reddit, Suicide Squad, Suicide Squad 2, Suicide Squad Cast, Suicide Squad Full Movie, Suicide Squad Joker, Suicide Silence, Suicide Statistics, Suicide Squad Soundtrack, Suicide Squad Rating, Suicide Squad Imdb, Suicide Text Line, Suicide Tna, Suicide Tattoos, Suicide Trial, Suicide Text, Suicide Tree, Suicide Tuesday, Suicide Test, Suicide Today, Suicide Troy Mi, Suicide Unforgivable Sin, Suicide Urban Dictionary, Suicide Usa, Suicide Unmasked, Suicide Unemployment, Suicide Utah, Suicide University, Suicide Uk, Suicide Ukulele Chords, Suicide Understanding, Suicide Vest, Suicide Victims, Suicide Virgins, Suicide Veterans, Suicide Vs Homicide, Suicide Vector, Suicide Verb, Suicide Verses, Suicide Vest Jail, Suicide Ventricle, Suicide Watch, Suicide Warning Signs, Suicide Wrestler, Suicide Website, Suicide Wallpaper, Suicide Workout, Suicide Watch Meme, Suicide Watch Reddit, Suicide Wiki, Suicide Walk, Suicide Xanax, Suicide X, Suicide Xanax Alcohol, Suicide X Tna, Suicide Chat, Suicide Xanax Overdose, Suicide Club, Suicide Xanax Dose, Suicide X Factor, Suicide Xmas Day, Suicide Youtube, Suicide Yesterday, Suicideyear, Suicide Yourself, Suicide Young Adults, Suicide Yahoo Answers, Suicide Youth, Suicide Yearly Statistics, Suicide Youth Statistics, Suicide Yellow Ribbon, Suicide Zoo, Suicide Zoloft, Suicide Zoo 2017, Suicide Zero, Suicide Zion, Suicide Zion National Park, Suicide Zoloft Overdose, Suicide Squad, Suicide Zilwaukee Bridge 2017, Suicide Zolpidem, Europe Map, Europe Map Quiz, Europe Band, Europe West, Europe Countries, Europe Population, Europe News, Europe Train, Europe Countries Map, Europe Political Map, Europe After Ww1, Europe And Russia Map, Europe After Ww2, Europe And Asia Map, Europe After Ww2 Map, Europe And Asia, Europe Adapter, Europe And Russia Mapping Lab, Europe After Ww1 Map, Europe Airlines, Europe Band, Europe Blank Map, Europe Before Ww1, Europe By Train, Europe By Car, Europe Before Ww2, Europe Backpacking, Europe Beaches, Europe Bank Holidays, Europe Bodies Of Water, Europe Countries, Europe Countries Map, Europe Cruises, Europe Car Rental, Europe Continent, Europe Cities, Europe Currency, Europe Carrie, Europe Current Events, Europe Capitals, Europe Destinations, Europe Definition, Europe Drinking Age, Europe During Ww2, Europe During The Cold War, Europe Denmark Copenhagen, Europe During Ww1, Europe Day, Europe Date Format, Europe Deals, Europe East, Europe Etf, Europe Express, Europe East Map, Europe Economy, Europe Elections, Europe East Dna, Europe Ebay, Europe Economic Crisis, Europe Etymology, Europe Flag, Europe Flights, Europe First Strategy, Europe Final Countdown, Europe Facts, Europe Flight Deals, Europe First, Europe Food, Europe For Kids, Europe France, Europe Gyro, Europe Geography, Europe Gdp, Europe Geography Quiz, Europe Google Maps, Europe Government, Europe Geography Map, Europe Germany, Europe Guided Tours, Europe Gps, Europe History, Europe Hostels, Europe Honeymoon, Europe Holidays, Europe High Speed Rail, Europe Hotels, Europe Holidays 2017, Europe Hotel Killarney, Europe History Timeline, Europe High Speed Rail Map, Europe In 1914, Europe In Spanish, Europe In 1918, Europe In 1914 Map, Europe Itinerary, Europe In The Middle Ages, Europe Is Lost, Europe Is A Continent, Europe Immigration, Europe In December, Europe Jobs, Europe Jokes, Europe Jewish, Europe Jean Sizes, Europe Jewish Population, Europe June 2017, Europe Jade Dynasty, Europe June Weather, Europe Jersey, Europe July Weather, Europe King, Europe Kosovo, Europe Keyboard, Europe Knights, Europe Knife Laws, Europe Kitchen, Europe Killarney, Europe Katakana, Europe Known For, Europe Killing, Europa League, Europe Laptop Ban, Europe Languages, Europe Landmarks, Europa League Final, Europe Labeled Map, Europe Lead Singer, Europe Location, Europe Landforms, Europe Land Area, Europe Map, Europe Map Quiz, Europe Map 1914, Europe Map Blank, Europe Map Ww2, Europe Money, Europe Map 1939, Europe Mountains, Europe Music Festivals 2017, Europe Map Outline, Europe News, Europe Nails, Europe Nails Prices, Europe Natural Resources, Europe News Today, Europe No Go Zones, Europe Night Trains, Europe Nations, Europe Nails Robinson, Europe Names, Europe On A Map, Europe Outline, Europe Outlet, Europe On A Budget, Europe Outline Map, Europe Outlet Converter, Europe Outlet Adapter, Europe On World Map, Europe Oceans, Europe On A Shoestring, Europe Population, Europe Political Map, Europe Packing List, Europe Power Adapter, Europe Packages, Europe Physical Map, Europe Plunges Into War, Europe Physical Features, Europe Pictures, Europe Population 2016, Europe Quiz, Europe Quotes, Europe Quizlet, Europe Queen, Europe Qualifiers, Europe Questions, Europe Quiz Sporcle, Europe Qualifying 2018, Europe Quiz Lizard Point, Europe Qe, Europe River Cruises, Europe Rail, Europe Rail Pass, Europe Rental Car, Europe Rivers, Europe Rail Map, Europe Reddit, Europe Refugee Crisis, Europe Region, Europe Religion, Europe Songs, Europe Shoe Size, Europe Sim Card, Europe Square Miles, Europe Size, Europe Stock Market, Europe States, Europe Soccer, Europe Sim Card Prepaid, Europe Soccer Teams, Europe Time, Europe Train, Europe Tours, Europe Trip, Europe Trip Planner, Europe Time Zones, Europe Travel, Europe Train Map, Europe Train Pass, Europe Travel Packages, Europe Union, Europe Unemployment Rate, Europe Uk, Europe University, Europe Us Visa, Europe United Kingdom, Europe Uber, Europe Us Size Comparison, Europe Usa, Europa Universalis, Europe Vacation, Europe Visa, Europe Voltage, Europe Vs Usa, Europe Vs Usa Size, Europe Vs Asia, Europe Vacation Spots, Europe Visa From Usa, Europe Vacation Ideas, Europe Volcano, Europe West, Europe Weather, Europe World Map, Europe Ww2 Map, Europe Ww2, Europe With Kids, Europe Wiki, Europe Ww1 Map, Europe Wallpaper, Europe Weather In May, Europe Xenophobia, Europe Xi, Europe X, Europe Xl To Us, Europe X Factor Judges, Europe Xi Vs Manchester United, Europe Xmas Markets, Europe Xi 2017, Europe Xl, Europe Xiaomi, Europe Youtube, Europe Youth Hostels, Europe Youth Unemployment, Europe Yacht Week, Europe Yoga Retreat, Europe Yugoslavia, Europe Youth Hostel Pass, Europe Yacht Charter, Europe Yelp, Europe You Are Here Mugs, Europe Zip Codes, Europe Zillow, Europe Zika, Europe Zoo, Europe Zika Map, Europe Zara, Europe Zip Code Database, Europe Zone, Europe Z, Europa Zeus, Middle East Map, Middle East Countries, Middle East Market, Middle East News, Middle East Map Quiz, Middle East Flags, Middle East Airlines, Middle East Respiratory Syndrome, Middle East Restaurant, Middle East Current Events, Middle East Airlines, Middle East And North Africa Map, Middle East Asia, Middle East And North Africa, Middle East Articles, Middle East After Ww1, Middle East Asia Map, Middle East After Ww2, Middle East And Africa Map, Middle East Architecture, Middle East Blank Map, Middle East Boston, Middle East Bakery Near Me, Middle East Bodies Of Water, Middle East Breaking News, Middle East Before Islam, Middle East Bakery, Middle East Blood, Middle East Broadcasting Networks, Middle East Bakery Sterling Heights, Middle East Countries, Middle East Current Events, Middle East Conflict, Middle East Continent, Middle East Cambridge, Middle East Capitals, Middle East Countries Quiz, Middle East Culture, Middle East Countries List, Middle East Crisis, Middle East Definition, Middle East Desert, Middle East Downstairs, Middle East Documentary, Middle East Dictators, Middle East Desserts, Middle East During Ww2, Middle East During Cold War, Middle East Dbq, Middle East Democracy, Middle East Eye, Middle East Europe, Middle East Economy, Middle East Ethnic Groups, Middle East Explained, Middle East Ethnic Map, Middle East Events, Middle East Empires, Middle East Electronics Ban, Middle East Europe Map, Middle East Flags, Middle East Food Near Me, Middle East Food, Middle East Forum, Middle East Facts, Middle East Foreign Policy, Middle East For Dummies, Middle East Fashion, Middle East Flights, Middle East Food Market, Middle East Geography, Middle East Grocery Store, Middle East Geography Quiz, Middle East Government, Middle East Geography Map, Middle East Grocery, Middle East Garlic Sauce, Middle East Gdp, Middle East Games, Middle East Girl, Middle East History, Middle East History Books, Middle East Head Wrap, Middle East Holidays, Middle East Human Rights, Middle East Highest Mountain Range, Middle East Headwear, Middle East History Documentary, Middle East Houses, Middle East Historical Events, Middle East Institute, Middle East In Spanish, Middle East Inbreeding, Middle East In 1920, Middle East Issues, Middle East In The 70s, Middle East Israel, Middle East In Asia, Middle East Images, Middle East Instruments, Middle East Jobs, Middle East Journal, Middle East Journal Of Anesthesiology, Middle East Jokes, Middle East Jordan, Middle East Jesus, Middle East Jewelry, Middle East Jerusalem, Middle East Journal Of Culture And Communication, Middle East Judaism, Middle East Kuwait, Middle East Kings, Middle East Kingdoms, Middle East Kurds, Middle East Knife, Middle East Killings, Middle East Knives, Middle East Kabob, Middle East Kebab, Middle East Key Terms, Middle East Languages, Middle East Leaders, Middle East Lentil Soup, Middle East Location, Middle East Labeled Map, Middle East Laptop Ban, Middle East Lizard Point, Middle East Landforms, Middle East Landscape, Middle East Literacy Rate, Middle East Map, Middle East Market, Middle East Map Quiz, Middle East Monitor, Middle East Map Blank, Middle East Map Game, Middle East Map Israel, Middle East Music, Middle East Map Labeled, Middle East Memes, Middle East News, Middle East Near Me, Middle East Names, Middle East North Africa Map, Middle East Nations, Middle East Natural Resources, Middle East News Cnn, Middle East North Africa, Middle East Newspaper, Middle East Map, Middle East Oil, Middle East On Map, Middle East Outline Map, Middle East Oil Crisis, Middle East On World Map, Middle East Oil Reserves, Middle East Oil Map, Middle East Online, Middle East Oil Crisis Apush, Middle East Oil Production, Middle East Political Map, Middle East Population, Middle East Pastry, Middle East Physical Map, Middle East Physical Features, Middle East Peace, Middle East Physical Features Map, Middle East Problems, Middle East Politics, Middle East Pictures, Middle East Quiz, Middle East Quizlet, Middle East Quarterly, Middle East Qatar, Middle East Questions And Answers, Middle East Quartet, Middle East Quotes, Middle East Quinoa, Middle East Qatar Map, Middle East Quiz Game, Middle East Respiratory Syndrome, Middle East Restaurant, Middle East Religion, Middle East Restaurants Near Me, Middle East Region, Middle East Revolution, Middle East Rivers, Middle East Religion Map, Middle East Religious Intolerance, Middle East Restaurant Ann Arbor, Middle East Studies Association, Middle East Spiders, Middle East States, Middle East Scarf, Middle East Syria, Middle East Saudi Arabia, Middle East Spices, Middle East Studies, Middle East Seas, Middle East Sheppard Software, Middle East Technical University, Middle East Timeline, Middle East Time, Middle East Terrorism, Middle East Test, Middle East Trump, Middle East Terrorist Groups, Middle East Today, Middle East Travel, Middle East Travel Ban, Middle East Upstairs, Middle East University, Middle East Usa, Middle East United States, Middle East Union, Middle East Us, Middle East Union Attack On Titan, Middle East Us Allies, Middle East Uninhabitable, Middle East Unlabeled Map, Middle East Vocabulary, Middle East Vacation, Middle East Violence, Middle East Vs Near East, Middle East Video, Middle East Venture Partners, Middle East Virus, Middle East Venue, Middle East Village, Middle East Vacation Spots, Middle East War, Middle East Word Whizzle, Middle East World Map, Middle East War Movies, Middle East Wiki, Middle East Weather, Middle East Water Crisis, Middle East Ww1, Middle East Ww2, Middle East Water Map, Middle East Countries, Middle East X Words, Middle East Current Events, Middle East Conflict, Middle East Continent, Middle East Cambridge, Middle East Capitals, Middle East Countries Quiz, Middle East Culture, Middle East Countries List, Middle East Youtube, Middle East Yemen, Middle East Yogurt, Middle East Yogurt Drink, Middle East Youth Bulge, Middle East Youth Population, Middle East Youth Initiative, Middle East Yellow Rice Recipe, Middle East Youth Unemployment, Middle East Yogurt Sauce, Middle East Zionism, Middle East Zuzu, Middle East Zip Codes, Middle East Zinc Deficiency, Middle East Zksoftware, Middle East Zoo Association, Middle East Zone, Middle East Zone Free Of Nuclear Weapons, Middle East Zagros Mountains, Middle East Zucchini Recipes
Secret – U.S. Central Command Report on Medecins Sans Frontieres Kunduz Trauma Centre Airstrike
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
The following set of documents was released by U.S. Central Command on April 29, 2016. See also Medecins Sans Frontieres’ initial review of the attack.
Summary of the Airstrike on the MSF Trauma Center in Kunduz, Afghanistan on October 3, 2015; Investigation and Follow-on Actions
Page Count: 726 pages
Date: November 21, 2015
Restriction: None
Originating Organization: U.S. Central Command
File Type: pdf
File Size: 67,200,881 bytes
File Hash (SHA-256): E8BBC70849D607F5175549F670CC1887FE46C002CC5D74265298582E8F39471E
The U.S. Central Command extends its deepest condolences to those injured and to the families of those killed in this tragic incident. We are fully committed to learning from this tragedy and minimizing the risk of civilian casualties during future combat operations. This document includes a summary of the investigation and key follow-on actions by senior commanders, and reflects our commitment to transparency and improvement.
THE INVESTIGATION:
On Oct. 3, 2015, members of U.S. Forces-Afghanistan (USFOR-A) supporting a partnered Afghan force, conducted a combat operation that struck Trauma Center in Kunduz operated by Médecins Sans Frontières (MSF), also known as “Doctors without Borders.”
U.S. Army Gen. John Campbell, then the Commander of USFOR-A, directed an investigation to determine the cause of this incident. The lead investigating officer was Army Maj. Gen. William Hickman. He was assisted by Air Force Brig. Gen. Robert Armfield and Army Brig. Gen Sean Jenkins. All three generals were brought in from outside Afghanistan in order to provide an objective perspective. The investigation team included over a dozen subject matter experts from several specialty fields.
The investigative team visited the MSF Trauma Center site and several other locations in the city of Kunduz. The team interviewed more than 65 witnesses including personnel at the Trauma Center, members of U.S. and Afghan ground forces, members of the aircrew, and representatives at every echelon of command in Afghanistan. The team had full access to classified information, and the investigation includes more than 3,000 pages of documentary evidence, much of it classified. Gen. Campbell approved the investigation on Nov. 21, 2015.
GENERAL SUMMARY:
The investigation concluded that the personnel involved did not know that they were striking a medical facility. The intended target was an insurgent-controlled site which was approximately 400 meters away from the MSF Trauma Center. The investigation found that an AC-130U Gunship aircrew, in support of a U.S. Special Forces element that was supporting a partnered Afghan ground force, misidentified and struck the MSF Trauma Center. The investigation determined that all members of both the ground force and the AC-130U aircrew were unaware the aircrew was firing on a medical facility throughout the engagement.
The comprehensive investigation concluded that this tragic incident was caused by a combination of human errors, compounded by process and equipment failures. Fatigue and high operational tempo also contributed to the incident. These factors contributed to the “fog of war,” which is the uncertainty often encountered during combat operations. The investigation found that this combination of factors caused both the Ground Force Commander and the air crew to believe mistakenly that the air crew was firing on the intended target, an insurgent-controlled site approximately 400 meters away from the MSF Trauma Center.
The Commander of USFOR-A concluded that certain personnel failed to comply with the rules of engagement and the law of armed conflict. However, the investigation did not conclude that these failures amounted to a war crime. The label “war crimes” is typically reserved for intentional acts intentionally targeting civilians or intentionally targeting protected objects. The investigation found that the tragic incident resulted from a combination of unintentional human errors and equipment failures, and that none of the personnel knew that they were striking a medical facility.
Secret Life Of Pets, Secret Service, Secret Garden, Secret World Legends, Secret Flying, Secret Life Of Bees, Secret Life Of Pets Cast, Secret Life Of The American Teenager, Secret Squirrel, Secret Shopper, Secret Agent Man, Secret Admirer, Secret Aardvark, Secret Agent, Secret Annex, Secret And Lies, Secret Agent Man Song, Secret App, Secret Asian Man, Secret Agent Man Lyrics, Secretbuilders, Secret Book, Secret Beach Kauai, Secret Beach, Secret Ballot, Secret Box, Secret Beach Maui, Secret Bay Dominica, Secret Base, Secret Band, Secret Circle, Secret Church, Secret Caverns, Secret Classroom Superpowers, Secret Codes, Secret Clinical Strength, Secret Clearance, Secret Circle Cast, Secret Conversations Facebook, Secret Cameras, Secret Deodorant, Secret Definition, Secret Diary Of A Call Girl, Secret Door, Secret Deodorant Coupons, Secret Diary, Secret Deodorant Commercial, Secret Decoder Ring, Secret Daughter, Secret Door Lyrics, Secret Empire, Secret Extensions, Secret Escapes, Secret Empire #1, Secret Empire Reading Order, Secret Entourage, Secret Empire #0, Secret Empire #2, Secret Eaters, Secret Emoji, Secret Flying, Secret Forest, Secret Forest Ep 11, Secret Falls Kauai, Secret Flask, Secret Formula, Secret Facebook Group, Secret Frappuccino, Secret For The Mad Lyrics, Secret Falls, Secret Garden, Secret Garden Song, Secret Garden Movie, Secret Garden Cafe, Secret Garden Musical, Secret Garden Lyrics, Secret Garden Denver, Secret Garden Book, Secret Google Games, Secret Garden Miami, Secret Hitler Rules, Secret Hitler Game, Secret History Of Twin Peaks, Secret Hitler Online, Secret Hair Extensions, Secret Handshake, Secret History, Secret Hotel Deals, Secret Heart, Secret Hiding Places, Secret In Their Eyes, Secret In Spanish, Secret Ingredient, Secret Island, Secret In Their Eyes Cast, Secret Invasion, Secret In N Out Menu, Secret Invisible Solid, Secret Island In Texas, Secret In French, Secret Jardin, Secret Jewels, Secret Journal, Secret Jobs, Secret Jamaica, Secret Jieun, Secret Jardin Lodge, Secret Journey Police, Secret Journey To Planet Serpo, Secret Jardin Dr90, Secret Kpop, Secret Keeper Girl, Secret Keeper, Secret Key, Secret Korean Drama, Secret Knock, Secret Knowledge, Secret Krabby Patty Formula, Secret Key Starting Treatment Essence, Secret Kingdom, Secret Life Of Pets, Secret Life Of Bees, Secret Life Of Pets Cast, Secret Life Of The American Teenager, Secret Love Song, Secret Life Of Walter Mitty, Secret Lab Chair, Secret Life Of An American Teenager Cast, Secret Language, Secret Life Of Pets Imdb, Secret Menu, Secret Menu Items, Secret Mage, Secret Menu Starbucks, Secret Menu In N Out, Secret Messages, Secret Meaning, Secret Movie, Secret Mountain Fort Awesome, Secret Mage Deck, Secret Nails, Secret Nyc, Secret Netflix, Secret Nail Salon, Secret Names, Secret Netflix Codes, Secret Numbers, Secret News, Secret Nature From Jeju Peeling Gel, Secret Nation, Secret Of Mana, Secret Of Nimh, Secret Of The Snowy Peaks, Secret Of The Cedars, Secret Of Kells, Secret Of Evermore, Secret Of The Wings, Secret Of Moonacre, Secret Of Mana Rom, Secret Of Mana 2, Secret Pizza, Secret Police, Secret Project Robot, Secret Place, Secret Passion Fruit, Secret Power, Secret Passages, Secret Pizza Party, Secret Paladin, Secret Place Lyrics, Secret Quotes, Secret Question, Secret Quest, Secret Questions To Ask, Secret Questions To Ask Siri, Secret Quests Ffxv, Secret Quests Skyrim, Secret Qr Codes, Secret Questions To Ask Alexa, Secret Quote Spongebob, Secret Romance, Secret Resorts, Secret Recipe, Secret Rooms, Secret Rare Pokemon Cards, Secret Rainbow Hair, Secret Rare Ultra Ball, Secret Rendezvous, Secret Relationship, Secret Roku Channels, Secret Service, Secret Squirrel, Secret Shopper, Secret Societies, Secret Synonym, Secret Starbucks Menu, Secret Service Jobs, Secret Sandwich Society, Secret Sisters, Secret Shopper Jobs, Secret Treasures, Secret Treasures Sleepwear, Secret Tunnel, Secret Things, Secret Tunnel Song, Secret The Pierces, Secret Thesaurus, Secret Travel, Secret Treasures Bra, Secret To Success, Secret Underground Cities, Secret Us Weapons, Secret Underground Bases, Secret Universe Of Names, Secret Underground, Secret Underground Medicine, Secret Upgrades Office Space, Secret Us Bases, Secret Us Military Bases, Secret Unscented, Secret Variety Training, Secret Village Of The Spellcasters, Secret Video Recorder, Secret Variety Training Ep 2, Secret Vault, Secret Vault 81, Secret Veneers, Secret Voice Recorder, Secret Video, Secret Volume, Secret World Legends, Secret Window, Secret Wood, Secret Wars, Secret Wood Rings, Secret World Legends Release Date, Secret World Of Arrietty, Secret Weapon, Secret Wars 2015, Secret Warriors, Secret X Folder, Secret Xtians, Secret Xscape, Secret X Folder Comic, Secret X, Secret Xbox One Gamerpics, Secret Xtend, Secret Xbox One Games, Secret Xbox One Codes, Secret X Folder Webtoon, Secret Youtube, Secret Yeahu, Secret Yellowstone, Secret Young Justice, Secret Youtube Videos, Secret Yosemite, Secret Youtube Tricks, Secret Youtube Website, Secret Yumiverse, Secret Yosemite Spots, Secret Zoo Series, Secret Zoo, Secret Zoo Book, Secret Zinger, Secret Zombies Calling Card, Secret Zodiac Sign, Secret Zion Hikes, Secret Zone, Secret Zombies Challenge Infinite Warfare, Secret Zombie Challenge, Us Central Command Address, Us Central Command Area Of Responsibility, Us Central Command Qatar, Us Central Command Twitter, Us Central Command Tampa Fl, Us Central Command Statement, Us Central Command Hq, Us Central Command Forward Headquarters, Us Central Command Facebook, Us Central Command Bahrain, Us Central Command Address, Us Central Command Area Of Responsibility, Us Central Command Afghanistan, Central Us Command Airstrikes, Us Central Command Air Force, Us Central Command Africa, Us Central Command Area Of Operations, Us Central Command Account, Us Central Command Twitter Account, Us Central Command Twitter Account Hacked, Us Central Command Bahrain, Us Central Command Base, Us Central Command Breach, Us Central Command Badge, Us Central Command Bbc, Us Central Command Hacked By Isis, Us Navy Central Command Bahrain, Us Naval Forces Central Command Bahrain, Us Central Command Commander, Us Central Command Civilian Expeditionary Workforce, Us Central Command Cew Program, Us Central Command Countries, Us Central Command Centcom, Us Central Command Channel, Us Central Command Cyber Attack, Us Central Command China, Us Central Command Careers, Us Central Command Channel Youtube, Us Central Command Doha Qatar, Us Central Command Intelligence Directorate, Deputy Commander Us Central Command, Director Of Operations Us Central Command, Us Central Command Emblem, Us Central Command Europe, Us Central Command Civilian Expeditionary Workforce, Us Central Command Middle East, Us European Central Command, Us Army Element Hdqrs Central Command, Ap Exclusive Inside Us Central Command In Qatar, Us Central Command Florida, Us Central Command Forward Headquarters, Us Central Command Facebook, Us Central Command Forward, Us Central Command Forward Jordan, Us Central Command (Forward) – Jordan (Cf-j), Us Central Command Twitter Feed, Us Central Command Air Force, Us Central Command Tampa Florida, Us Central Command Tampa Fl, Us Central Command General, Us Central Command Gen. Joseph Votel, Us Central Command General Order 1b, Us Central Command Hq, Us Central Command Headquarters, Us Central Command Hacked, Us Central Command History, Us Central Command Homepage, Us Central Command’s Headquarters In Florida, Us Army Central Command Headquarters, Us Central Command Forward Headquarters, Us Military Central Command Hacked, Us Central Command Youtube Hacked, Us Central Command In Qatar, Us Central Command Isis, Us Central Command Iraq, Us Central Command Intelligence Directorate, Us Central Command Isis Twitter, Us Central Command Inherent Resolve, Us Central Command Commander In Chief, Us Central Command’s Headquarters In Florida, Us Central Command Operation Inherent Resolve, Us Air Forces Central Command Instruction 36-2903, Us Central Command Jobs, Us Central Command Joint Meritorious Unit Award, Us Central Command J2, Us Central Command J4, Us Central Command J5, Us Central Command J3, Us Central Command Forward Jordan, Us Central Command (Forward) – Jordan (Cf-j), Us Central Command Kobane, Us Army Central Command Kuwait, Us Central Command Location, Us Central Command Logo, Us Central Command Leadership, Us Central Command Middle East, Us Central Command Map, Us Central Command Macdill Afb, Us Central Command Macdill Afb Fl, Us Central Command Mission Statement, Us Central Command Mailing Address, Us Central Command Mosul, Us Central Command Joint Meritorious Unit Award, Us Central Command Social Media, Us Military Central Command Twitter, Us Central Command News, Us Central Command Navy, Us Central Command News Releases, Us Central Command Phone Number, Us Navy Central Command Bahrain, Us Navy Central Command Wiki, Us Central Command Organization Chart, Us Central Command On Twitter, Us Central Command Operation Inherent Resolve, Us Central Command Area Of Responsibility, Us Central Command Chief Of Staff, Us Central Command General Order 1b, Us Central Command Area Of Operations, Us Central Command Public Affairs Office, Us Central Command Change Of Command, Head Of Us Central Command, Us Central Command Public Affairs, Us Central Command Press Release, Us Central Command Patch, Us Central Command Portal, Us Central Command Pastebin, Us Central Command Cew Program, Us Army Central Command Patch, Us Central Command Twitter Page, Us Central Command Youtube Page, Us Central Command Home Page, Us Central Command Qatar, Us Forces Central Command Qatar, Us Central Command Doha Qatar, Us Army Forces Central Command Qatar, Ap Exclusive Inside Us Central Command In Qatar, Us Central Command Regulations, Us Central Command Red Team, Us Central Command Press Release, Us Central Command News Releases, Us Central Command Inherent Resolve, Us Central Command Area Of Responsibility, Us Central Command Operation Inherent Resolve, Us Central Command Statement, Us Central Command Syria, Us Central Command Structure, Us Central Command Social Media, Us Central Command Staff, Us Army Central Command Shaw Afb, Central Us Command Airstrikes, Us Central Command Mission Statement, The Us Central Command Said That A 20000 To 25000 Iraqi And Kurdish, The Us Central Command Said That A 20000, Us Central Command Twitter, Us Central Command Tampa Fl, Us Central Command Tampa, Us Central Command Twitter Hacked, Us Central Command Twitter Account Hacked, Us Central Command Tampa Florida, Us Central Command Twitter Feed Hacked, Us Central Command Twitter Isis, Hq Us Central Command Tampa Fl, Us Central Command Youtube, Us Central Command Youtube, Us Army Central Command (Arcent), Us Central Command Joint Meritorious Unit Award, Us Africa Command Us Central Command, Us Central Command Videos, Us Central Command Wiki, Us Central Command Website, Us Navy Central Command Wiki, Us Central Command Civilian Expeditionary Workforce, What Is Us Central Command, What Is Us Central Command Area Of Responsibility, Where Is Us Central Command Based, Us Central Command Youtube, Us Central Command Youtube Channel, Us Central Command Youtube Page, Us Central Command Youtube Hacked, Medecins Sans Frontiere Canada, Medecins Sans Frontiere Uk, Medecins Sans Frontiere France, Medecins Sans Frontieres, Medecins Sans Frontieres Jobs, Medecins Sans Frontieres Australia, Medecins Sans Frontieres Ebola, Medecins Sans Frontieres Wiki, Medecins Sans Frontieres Nepal, Medecins Sans Frontieres Hong Kong, Medecins Sans Frontiere Anglais, Medecins Sans Frontieres Australia, Medecins Sans Frontieres Afghanistan, Medecins Sans Frontieres Amsterdam, Medecins Sans Frontieres Abuja, Medecins Sans Frontieres Abu Dhabi, Medecins Sans Frontieres Anti-israel, Medecins Sans Frontieres Annual Report, Medecins Sans Frontieres Amman, Medecins Sans Frontieres Australia Bequest, Medecins Sans Frontiere Canada, Medecins Sans Frontiere Cameroun, Medecins Sans Frontieres Careers, Medecins Sans Frontieres Christmas Cards, Medecins Sans Frontieres Controversies, Medecins Sans Frontieres Contact, Medecins Sans Frontieres Cancel Donation, Medecins Sans Frontieres Calais, Medecins Sans Frontieres Cape Town, Medecins Sans Frontieres Charity Rating, Medecins Sans Frontiere Dons, Doctors Without Borders Medecins Sans Frontieres, Medecins Sans Frontieres Donate, Medecins Sans Frontiere Emploi, Medecins Sans Frontiere France, Medecins Sans Frontieres Francais, Medecins Sans Frontieres Facebook, Medecins Sans Frontieres Founders, Medecins Sans Frontieres Fundraising, Medecins Sans Frontieres Funding, Medecins Sans Frontieres Wiki Francais, Medecin Sans Frontiere Fondateur, Medecin Sans Frontiere Financement, Medecins Sans Frontieres France Address, Medecins Sans Frontiere Geneve, Medecins Sans Frontieres Glebe, Medecins Sans Frontieres Grece, Medecins Sans Frontieres Geneva Jobs, Medecins Sans Frontieres Gaza, Medecins Sans Frontieres Gifts, Medecins Sans Frontiere Histoire, Medecins Sans Frontieres Hong Kong, Medecins Sans Frontieres Haiti, Medecins Sans Frontieres Holland, Medecins Sans Frontieres Headquarters, Medecins Sans Frontieres History, Medecins Sans Frontieres Hospital Bombing, Medecins Sans Frontieres Head Office, Medecins Sans Frontieres Holland Jobs, Medecins Sans Frontieres Haiti Jobs, Medecins Sans Frontieres Ireland, Medecins Sans Frontieres Internship, Medecins Sans Frontieres Jobs, Medecins Sans Frontieres Jordan, Medecins Sans Frontieres Jobs Kenya, Medecins Sans Frontieres Jobs In Nigeria, Medecins Sans Frontieres Jobs Uk, Medecins Sans Frontieres Japan, Medecins Sans Frontieres Jobs Uganda, Medecins Sans Frontieres Jobs Usa, Medecins Sans Frontieres Jobs In Pakistan, Medecins Sans Frontieres Jobs In Haiti, Medecins Sans Frontieres Kashmir, Medecins Sans Frontieres Kenya, Medecins Sans Frontieres Kenya Contacts, Medecins Sans Frontieres Kunduz, Medecins Sans Frontieres Karachi, Medecins Sans Frontieres Kenya Tenders, Medecins Sans Frontieres Kos, Medecins Sans Frontieres Killed, Medecins Sans Frontieres Kosovo, Medecins Sans Frontieres Karachi Pakistan, Medecins Sans Frontieres Luxembourg, Medecins Sans Frontieres Lebanon, Medecins Sans Frontieres Logo, Medecins Sans Frontieres London, Medecins Sans Frontieres Lebanon Jobs, Medecins Sans Frontieres Logo Vector, Medecins Sans Frontieres Linkedin, Medecins Sans Frontieres London Office, Medecins Sans Frontieres Lebanon Office, Medecins Sans Frontieres Liberia, Medecins Sans Frontiere Montreal, Medecins Sans Frontiere Maroc, Medecins Sans Frontieres Mumbai, Medecins Sans Frontieres Malawi, Medecins Sans Frontieres Mission Statement, Medecins Sans Frontieres Myanmar, Medecins Sans Frontieres Melbourne, Medecins Sans Frontieres Malaysia, Medecins Sans Frontieres Mission, Medecins Sans Frontieres Mozambique, Medecins Sans Frontieres Nepal, Medecins Sans Frontieres Nigeria, Medecins Sans Frontieres Nobel Peace Prize, Medecins Sans Frontieres New York, Medecins Sans Frontieres Nz, Medecins Sans Frontieres News, Medecins Sans Frontieres Nyc, Medecins Sans Frontieres Netherlands, Medecins Sans Frontieres Nigeria Vacancies, Medecins Sans Frontieres Nairobi Office, Medecins Sans Frontiere Offre D’emploi, Medecins Sans Frontieres Origin, Medecins Sans Frontieres.org, Medecins Sans Frontieres Organizational Structure, Medecins Sans Frontieres Offices, Medecins Sans Frontieres Occupational Therapist, Medecins Sans Frontieres Oca, Medecins Sans Frontieres Ottawa, Medecins Sans Frontieres Or Doctors Without Borders, Medecins Sans Frontieres Oslo, Medecins Sans Frontiere Paris, Medecins Sans Frontieres Quebec, Medecins Sans Frontieres Quotes, Medecins Sans Frontieres Interview Questions, Medecins Sans Frontieres Qui Sommes Nous, Medecin Sans Frontiere Que Font Ils, Medecin Sans Frontiere C’est Quoi, Medecin Sans Frontiere Recrutement Quebec, Medecins Sans Frontiere Recrutement, Medecins Sans Frontieres Rustenburg, Medecins Sans Frontieres Review, Medecins Sans Frontieres Registered Charity Number, Medecins Sans Frontieres Refugee Crisis, Medecins Sans Frontieres Refugee Camp, Medecins Sans Frontieres Rating, Medecins Sans Frontieres Radiologist, Medecins Sans Frontiere Suisse, Medecins Sans Frontiere Syrie, Medecins Sans Frontiere Toulouse, Medecins Sans Frontiere Tunisie, Medecins Sans Frontieres T Shirt, Medecins Sans Frontieres Toronto, Medecins Sans Frontieres Twitter, Medecins Sans Frontieres Tanzania, Medecins Sans Frontieres Tax Receipt, Medecins Sans Frontieres Thailand, Medecins Sans Frontieres Tpp, Medecins Sans Frontieres Travailler, Medecins Sans Frontiere Uk, Medecins Sans Frontieres Usa, Medecins Sans Frontieres Uae, Medecins Sans Frontieres Uk Christmas Cards, Medecins Sans Frontieres Uganda, Medecins Sans Frontieres Uk Jobs, Medecins Sans Frontieres Uganda Contacts, Medecins Sans Frontieres Uk Address, Medecins Sans Frontieres Uk Nepal, Medecins Sans Frontieres Ouzbekistan, Medecins Sans Frontieres Volunteer, Medecins Sans Frontieres Volunteer Work, Medecins Sans Frontieres Video, Medecins Sans Frontieres Vision Statement, Medecins Sans Frontieres Vietnam, Medecins Sans Frontieres Vienna, Medecins Sans Frontieres Vs Red Cross, Medecins Sans Frontieres Vancouver, Medecins Sans Frontieres Values, Medecins Sans Frontieres Vanuatu, Medecins Sans Frontieres Wiki, Medecins Sans Frontieres Wikipedia.fr, Medecins Sans Frontieres Watch, Medecins Sans Frontieres Wiki Francais, Medecins Sans Frontieres Website, Medecins Sans Frontieres Work Experience, Medecins Sans Frontieres What They Do, Medecins Sans Frontieres Washington Dc, Medecins Sans Frontieres Wien, Medecins Sans Frontieres Work, Medecins Sans Frontieres Xmas Cards, Medecins Sans Frontiere Yaounde, Medecins Sans Frontieres Yemen, Medecins Sans Frontieres Youtube, Medecins Sans Frontieres Yangon, Medecins Sans Frontieres Yerevan, Medecins Sans Frontieres New York, Medecins Sans Frontieres New York Internship, Medecins Sans Frontieres Gap Year, Medecins Sans Frontieres New York Office, Medecins Sans Frontieres Zimbabwe, Medecins Sans Frontieres Zimbabwe Vacancies, Medecins Sans Frontieres Zurich, Medecins Sans Frontieres Zambia, Medecins Sans Frontieres New Zealand, Medecins Sans Frontieres Zewo, Medecins Sans Frontieres Artsen Zonder Grenzen, Medecins Sans Frontieres Zivildienst, Trauma Definition, Trauma Informed Care, Trauma Surgeon, Trauma Surgeon Salary, Trauma Nurse, Trauma Center, Trauma Bonding, Trauma Informed Schools, Trauma Shears, Trauma Focused Cbt, Trauma Assessment, Trauma And Recovery, Trauma And The Brain, Trauma Alert Level 2, Trauma And Stressor Related Disorders, Trauma And Loss Center, Trauma And Addiction, Trauma And Memory, Trauma Assessment Emt, Trauma Association, Trauma Bonding, Trauma Based Mind Control, Trauma Bag, Trauma Bay, Trauma Brain, Trauma Based Therapy, Trauma Burn Icu, Trauma Book, Trauma Based Cbt, Trauma Blanket, Trauma Center Levels, Trauma Center, Trauma Centers In Michigan, Trauma Conference 2017, Trauma Counseling, Trauma Center Game, Trauma Certification, Trauma Columbus, Trauma Center Second Opinion, Trauma Center Near Me, Trauma Definition, Trauma Doctor, Trauma Disorders, Trauma Doctor Salary, Trauma Dressing, Trauma Documentary, Trauma Down Under, Trauma Dissociation, Trauma Dolls, Trauma Defined, Trauma Examples, Trauma Egg, Trauma Er, Trauma Echo, Trauma Effects On Brain, Trauma Education, Trauma Etymology, Trauma Effects, Trauma Epigenetics, Trauma Explorations In Memory, Trauma Focused Cbt, Trauma Focused Cognitive Behavioral Therapy, Trauma Focused Therapy, Trauma First Aid Kit, Trauma Focused Cbt Workbook, Trauma Fellowship, Trauma Fx, Trauma First Aid Training, Trauma Facts, Trauma From Occlusion, Trauma Group Therapy, Trauma Guidelines, Trauma Gel, Trauma Golden Hour, Trauma Game, Trauma Gauze, Trauma Group, Trauma Guidelines 2017, Trauma Genetics, Trauma Grief, Trauma Hospitals In Michigan, Trauma Hospitals, Trauma Healing, Trauma Healing Institute, Trauma Hospitals In Detroit, Trauma Hospitals Near Me, Trauma History Questionnaire, Trauma Healing Retreat, Trauma Hotline, Traumahawk, Trauma Informed Care, Trauma Informed Care Training, Trauma Informed Schools, Trauma Informed Yoga, Trauma Informed Care Training Michigan, Trauma Icu, Trauma Icd 10, Trauma Informed Practice, Trauma Informed Policing, Trauma Informed Approach, Trauma Journal, Trauma Junkie, Trauma Jobs, Trauma Journals List, Trauma Journal Prompts, Trauma Jokes, Trauma James Cole, Trauma Junkie T Shirt, Trauma Juvenile Justice, Trauma Junkie Pdf, Trauma Kit, Trauma Kit List, Trauma Kit Amazon, Trauma Kit Supplies, Trauma Kit Contents, Trauma Kit Now, Trauma Kid Cudi, Trauma Kit Bag, Trauma Kit Pouch, Trauma Kit Alien Isolation, Trauma Levels, Trauma Level 2, Trauma Life In The Er, Trauma Learning Center, Trauma Life In The Er Detroit, Trauma Level Hospitals In Michigan, Trauma Labs, Trauma Life Young Living, Trauma Lens, Trauma Lyrics, Trauma Meaning, Trauma Meme, Trauma Movie, Trauma Medicine, Trauma Marvel, Trauma Man, Trauma Medical Definition, Trauma Medical Kit, Trauma Model, Trauma Memory, Trauma Nurse, Trauma Nurse Practitioner, Trauma Narrative, Trauma Nurse Salary, Trauma Nursing Core Course, Trauma Nurse Coordinator, Trauma Nursing Certification, Trauma Nurse Practitioner Programs, Trauma Nursing Conferences 2017, Trauma Np, Trauma Oil, Trauma One, Trauma Orthopedic Surgeon, Trauma Oil Recipe, Trauma On The Brain, Trauma Of Everyday Life, Trauma One Hospitals, Trauma Orange Book, Trauma Of Infidelity, Trauma Oil Uses, Trauma Protocol, Trauma Pad, Trauma Plate, Trauma Pa Salary, Trauma Psychology, Trauma Patient, Trauma Psychologist, Trauma Prayer, Trauma Physician Assistant, Trauma Pictures, Trauma Quotes, Trauma Queen, Trauma Queen Ffxiv, Trauma Quiz, Trauma Questionnaire, Trauma Quizlet, Trauma Questions, Trauma Queen Shirt, Trauma Queen Bandcamp, Trauma Queen Book, Trauma Registrar Jobs, Trauma Room, Trauma Registrar, Trauma Recovery, Trauma Release Exercises, Trauma Response, Trauma Registry, Trauma Registrar Salary, Trauma Recovery And Empowerment Model, Trauma Recovery Center Royal Oak, Trauma Surgeon, Trauma Surgeon Salary, Trauma Shears, Trauma Synonym, Trauma Smart, Trauma Surgery, Trauma Symptoms, Trauma Stewardship, Trauma Sensitive Schools, Trauma Symptom Checklist For Children, Trauma Therapy, Trauma Team, Trauma To A Joint Due To Injury To Ligaments, Trauma Training Michigan, Trauma Theory, Trauma Therapist, Trauma Training, Trauma Triad Of Death, Trauma Training For Teachers, Trauma Therapist Ann Arbor, Trauma Unit, Trauma Unit Nurse, Trauma Ultrasound, Trauma University, Trauma Used In A Sentence, Trauma Units Near Me, Trauma Under Toenail, Trauma Unit Vs Icu, Trauma Update, Trauma Usmle, Trauma Violence And Abuse, Trauma Victims, Trauma Videos, Trauma Vs Er, Trauma Vendor Alliance, Trauma Vs Ptsd, Trauma Vs Stress, Trauma Vortex, Trauma Victims And Relationships, Trauma Vest, Trauma Worksheets, Trauma Worksheets For Adults, Trauma Workbook, Trauma Work, Trauma Wound, Trauma Ward, Trauma Workbook Pdf, Trauma Workshops, Trauma Wound Icd 10, Trauma Wiki, Trauma X Ray Positioning, Trauma X Rays, Trauma X, Trauma Xray Pelvis, Trauma X Ray Series, Trauma Xray Knee, Trauma X Ray Views, Trauma X Ray Quiz, Trauma X-ray Interpretation, Trauma Yoga, Trauma Yoga Training, Trauma Yellow, Trauma Youtube, Trauma Yoga Training Online, Trauma Youngjae Lyrics, Trauma Yoga Dvd, Trauma Yoga Near Me, Trauma Youngjae, Trauma Youngjae English Lyrics, Trauma Zone, Trauma Zones Of Neck, Trauma Zones Of The Abdomen, Trauma Zombie, Trauma Zuba, Trauma Znacenje, Trauma Zero, Trauma Z Dzieci\u0144stwa Objawy, Trauma Znaczenie, Trauma Zwachtel, Kunduz Afghanistan, Kunduz Hospital, Kunduz Province, Kunduz Arma 3, Kunduz News, Kunduz Airstrike, Kunduz Taliban, Kunduz Dancing Boy, Kunduz Map, Kunduz Afghanistan News, Kunduz Afghanistan, Kunduz Arma 3, Kunduz Airstrike, Kunduz Afghanistan News, Kunduz Airlift, Kunduz Afghanistan Map, Kunduz Airport, Kunduz Attack, Kunduz Afghanistan Weather, Kunduz Airstrike 2009, Kunduz Bombing, Kunduz Battle, Kunduz Breaking News, Kunduz Baraj\u0131, Kunduz Bbc, Kunduz Bombing 2015, Kunduz Bombing 2009, Kunduz Bombing Investigation, Kunduz Bombing War Crime, Kunduz Buzkashi, Kunduz City, Kunduz City Map, Kunduz Chardara, Kunduz Carpet, Kunduz City Postal Code, Kunduz City Pictures, Kunduz City News, Kunduz Cnn, Kunduz Captured By Taliban, Kunduz Capture, Kunduz Dancing Boy, Kunduz Districts, Kunduz Doctors Without Borders, Kunduz District Map, Kunduz Delta, Kunduz Doctors, Kunduz Districts Afghanistan, Kunduz Dashti Archi, Kunduz Definition, Kunduz Daily Mail, Kunduz Ek\u015fi, Kunduz English, Kunduz Ethnic Groups, Kunduz Earthquake, Kunduz Explosion, Kunduz Economy, Kunduz Ethnicity, Kunduz Earthquake 2015, Kunduz Eti Yenir Mi, Kunduz Fighting, Kunduz Fall, Kunduz Falls To Taliban, Kunduz Fob, Kunduz Fighting Videos, Kunduz Fresh News, Kunduz Fuel Tanker, Kunduz Fob Afghanistan, Kunduz Facts, Kunduz Fact Finding, Kunduz Governor, Kunduz German, Kunduz Google Map, Kunduz German Base, Kunduz Governor Mohammad Omar, Kunduz Germany, Kunduz Guardian, Kunduz Geography, Kunduz Gunship, Kunduz Gallery, Kunduz Hospital, Kunduz Hayvan, Kunduz Hospital Bombing, Kunduz Hayvani, Kunduz History, Kunduz Hospital Investigation, Kunduz Hospital Report, Kunduz Hospital War Crime, Kunduz Hayvan\u0131 Hakk\u0131nda Bilgi, Kunduz Incident, Kunduz Investigation, Kunduz Ingilizcesi, Kunduz Ingilizce, Kunduz Imam Sahib, Kunduz In English, Kunduz Independent Investigation, Kunduz In Afghanistan, Kunduz Images, Kunduz Isis, Kunduz Jobs, Kunduz Jan Afghanistan Facebook, Kunduz Jang, Kunduz Jan Afghanistan, Kunduz Jail, Jundullah Kunduz, Kunduz Al Jazeera, Kunduz Weather January, Afghanistan Kunduz Jang, Kecha Va Kunduz Java, Kunduz Khanabad, Kunduz Kabul, Kunduz Kan\u0131, Kunduz Kan\u0131 Nerede Sat\u0131l\u0131r, Kunduz Kan\u0131 Fiyat\u0131, Kunduz Kanatbek Kyzy, Kunduz Kan\u0131 Sipari\u015f, Kunduz Kan\u0131 Kullananlar\u0131n Yorumlar\u0131, Kunduz Kan\u0131 Aktarlarda Var M\u0131, Kunduz Kan\u0131 Kullananlar, Kunduz Latest News, Kunduz Latest, Kunduz Live, Kunduz Location, Kunduz Live News, Kunduz Land Cover Map, Kunduz Liveleak, Kunduz Life, Kunduz Latest Images, Kunduz Luftangriff, Kunduz Map, Kunduz Msf, Kunduz Massacre, Kunduz Msf Hospital Bombing, Kunduz Map Arma 3, Kunduz Missie, Kunduz Msf Attack, Kunduz Map Afghanistan, Kunduz Meaning, Kunduz Map Google, Kunduz News, Kunduz Nedir, Kunduz Ne Demek, Kunduz Name, Kunduz Nato, Kunduz New Governor, Kunduz News 2015, Kunduz Nyt, Kunduz News Now, Kunduz News Facebook, Kunduz Offensive, Kunduz Open Door Scripts, Kunduz Operation, Kunduz Obama, Kunduz On Map, Kunduz Occupation, Kunduz October 2015, Kunduz Openstreetmap, Kunduz Oyunu, Kunduz Oyunlar\u0131, Kunduz Province, Kunduz Province Map, Kunduz Pronunciation, Kunduz Province News, Kunduz Police Chief, Kunduz Province Districts, Kunduz Population, Kunduz Postal Code, Kunduz Province Taliban, Kunduz Province Profile, Andrew Quilty Kunduz, Kecha Va Kunduz Qahramonlari, Kunduz River, Kunduz Report, Kunduz Rug, Kunduz Retaken, Kunduz Reuters, Kunduz Recaptured, Kunduz Regional Hospital, Kunduz Rehabilitation Agency, Kunduz Region, Kunduz Retake, Kunduz Startup, Kunduz Strike, Kunduz Taliban, Kunduz Trauma Centre, Kunduz Tang Dawg Strain, Kunduz Twitter, Kunduz Taliban Attack, Kunduz To Kabul, Kunduz Taliban 2017, Kunduz Taliban Video, Kunduz Taliban News, Kunduz Today, Kunduz University, Kunduz Update, Kunduz Us, Kunduz Us Air Strike, Kunduz Un, Kunduz Unama, Kunduz Under Taliban, Kunduz Under Taliban Control, Kunduz Us Army, Kunduz Under Attack, Kunduz Videos, Kunduz Victims, Kunduz Valley, Kunduz Villages, Kunduz Violence, Kunduz Vikipedi, Kunduz Videolar\u0131, Kunduz Ve Matematik, Kunduz Vanilya, Kunduz Weather, Kunduz Wiki, Kunduz War, Kunduz Weather Suation, Kunduz War Crime, Kunduz Waether, Kunduz Wikitravel, Kunduz War 2015, Kunduz Washington Post, Kunduz Whether, Kunduz X I 95, Kunduz Youtube, Kunduz Ya\u011f\u0131, Kunduz Ya\u011f\u0131 Ne I\u015fe Yarar, Kunduz Yuvas\u0131, Kunduz Yaylas\u0131, Kunduz Ya\u011f\u0131 Nedir, Kunduz Yavrusu, Kunduz Ya\u011f\u0131 Faydalar\u0131, Kunduz Yuvalar\u0131, Kunduz Yaylas\u0131 Konaklama, Kunduz Zip Code
Top Secret Photos from a Bizarre Illuminati Party Leaked
Become a Patron!
True Information is the most valuable resource and we ask you to give back.

A little over 40 years ago, Marie-Hélène de Rothschild held a party at her family’s massive castle-like mansion called Château de Ferrières. This party showcased surrealist costumes that are both intriguing and bizarre, even today. These photos have somehow leaked to the internet, despite the gatherings being held in secret. When you see these photos, you won’t believe what really went on behind closed doors.
The mansion was surrounded by lights that would give off the impression that it was on fire.

A little over 40 years ago, Marie-Hélène de Rothschild held a party at her family’s massive castle-like mansion called Château de Ferrières. This party showcased surrealist costumes that are both intriguing and bizarre, even today. These photos have somehow leaked to the internet, despite the gatherings being held in secret. When you see these photos, you won’t believe what really went on behind closed doors.
The mansion was surrounded by lights that would give off the impression that it was on fire.
Invitations couldn’t be read unless held in front of a mirror.

The party’s hosts were Guy de Rothschild & Marie-Hélène de Rothschild. As you can see, Marie-Hélène’s costume consists of a giant head with diamond tears.

And here she is pictured with Baron Alexis de Redé.

The Baron’s mask consisted of multiple faces, to give off the idea that he could stare at any and everyone, no matter where they were in the room.

Here is the hostess without her mask.

This guest paid homage to “The Son Of Man” painting with her costume.

Here you can see Mrs. Espírito Santo dining with the Baron.

Not only did people don bizarre masks, but birdcages were a common headdress.
Amongst guests, were Salvador Dali, who poses in front of his painting here.
There wasn’t one guest who didn’t rise to the challenge or incorporating both the beautiful and the strange.






As if the costumes weren’t creepy enough, dinner was even more terrifying.




The tables were decorated with beautiful flowers, but also sprinkled with dismembered doll.
It’s creepy that this took place in 1972. One can only imagine what the parties have become now…
In case you can not see the photos click here
Secret Life Of Pets, Secret Service, Secret Garden, Secret World Legends, Secret Flying, Secret Life Of Bees, Secret Life Of Pets Cast, Secret Life Of The American Teenager, Secret Squirrel, Secret Shopper, Secret Agent Man, Secret Admirer, Secret Aardvark, Secret Agent, Secret Annex, Secret And Lies, Secret Agent Man Song, Secret App, Secret Asian Man, Secret Agent Man Lyrics, Secretbuilders, Secret Book, Secret Beach Kauai, Secret Beach, Secret Ballot, Secret Box, Secret Beach Maui, Secret Bay Dominica, Secret Base, Secret Band, Secret Circle, Secret Church, Secret Caverns, Secret Classroom Superpowers, Secret Codes, Secret Clinical Strength, Secret Clearance, Secret Circle Cast, Secret Conversations Facebook, Secret Cameras, Secret Deodorant, Secret Definition, Secret Diary Of A Call Girl, Secret Door, Secret Deodorant Coupons, Secret Diary, Secret Deodorant Commercial, Secret Decoder Ring, Secret Daughter, Secret Door Lyrics, Secret Empire, Secret Extensions, Secret Escapes, Secret Empire #1, Secret Empire Reading Order, Secret Entourage, Secret Empire #0, Secret Empire #2, Secret Eaters, Secret Emoji, Secret Flying, Secret Forest, Secret Forest Ep 11, Secret Falls Kauai, Secret Flask, Secret Formula, Secret Facebook Group, Secret Frappuccino, Secret For The Mad Lyrics, Secret Falls, Secret Garden, Secret Garden Song, Secret Garden Movie, Secret Garden Cafe, Secret Garden Musical, Secret Garden Lyrics, Secret Garden Denver, Secret Garden Book, Secret Google Games, Secret Garden Miami, Secret Hitler Rules, Secret Hitler Game, Secret History Of Twin Peaks, Secret Hitler Online, Secret Hair Extensions, Secret Handshake, Secret History, Secret Hotel Deals, Secret Heart, Secret Hiding Places, Secret In Their Eyes, Secret In Spanish, Secret Ingredient, Secret Island, Secret In Their Eyes Cast, Secret Invasion, Secret In N Out Menu, Secret Invisible Solid, Secret Island In Texas, Secret In French, Secret Jardin, Secret Jewels, Secret Journal, Secret Jobs, Secret Jamaica, Secret Jieun, Secret Jardin Lodge, Secret Journey Police, Secret Journey To Planet Serpo, Secret Jardin Dr90, Secret Kpop, Secret Keeper Girl, Secret Keeper, Secret Key, Secret Korean Drama, Secret Knock, Secret Knowledge, Secret Krabby Patty Formula, Secret Key Starting Treatment Essence, Secret Kingdom, Secret Life Of Pets, Secret Life Of Bees, Secret Life Of Pets Cast, Secret Life Of The American Teenager, Secret Love Song, Secret Life Of Walter Mitty, Secret Lab Chair, Secret Life Of An American Teenager Cast, Secret Language, Secret Life Of Pets Imdb, Secret Menu, Secret Menu Items, Secret Mage, Secret Menu Starbucks, Secret Menu In N Out, Secret Messages, Secret Meaning, Secret Movie, Secret Mountain Fort Awesome, Secret Mage Deck, Secret Nails, Secret Nyc, Secret Netflix, Secret Nail Salon, Secret Names, Secret Netflix Codes, Secret Numbers, Secret News, Secret Nature From Jeju Peeling Gel, Secret Nation, Secret Of Mana, Secret Of Nimh, Secret Of The Snowy Peaks, Secret Of The Cedars, Secret Of Kells, Secret Of Evermore, Secret Of The Wings, Secret Of Moonacre, Secret Of Mana Rom, Secret Of Mana 2, Secret Pizza, Secret Police, Secret Project Robot, Secret Place, Secret Passion Fruit, Secret Power, Secret Passages, Secret Pizza Party, Secret Paladin, Secret Place Lyrics, Secret Quotes, Secret Question, Secret Quest, Secret Questions To Ask, Secret Questions To Ask Siri, Secret Quests Ffxv, Secret Quests Skyrim, Secret Qr Codes, Secret Questions To Ask Alexa, Secret Quote Spongebob, Secret Romance, Secret Resorts, Secret Recipe, Secret Rooms, Secret Rare Pokemon Cards, Secret Rainbow Hair, Secret Rare Ultra Ball, Secret Rendezvous, Secret Relationship, Secret Roku Channels, Secret Service, Secret Squirrel, Secret Shopper, Secret Societies, Secret Synonym, Secret Starbucks Menu, Secret Service Jobs, Secret Sandwich Society, Secret Sisters, Secret Shopper Jobs, Secret Treasures, Secret Treasures Sleepwear, Secret Tunnel, Secret Things, Secret Tunnel Song, Secret The Pierces, Secret Thesaurus, Secret Travel, Secret Treasures Bra, Secret To Success, Secret Underground Cities, Secret Us Weapons, Secret Underground Bases, Secret Universe Of Names, Secret Underground, Secret Underground Medicine, Secret Upgrades Office Space, Secret Us Bases, Secret Us Military Bases, Secret Unscented, Secret Variety Training, Secret Village Of The Spellcasters, Secret Video Recorder, Secret Variety Training Ep 2, Secret Vault, Secret Vault 81, Secret Veneers, Secret Voice Recorder, Secret Video, Secret Volume, Secret World Legends, Secret Window, Secret Wood, Secret Wars, Secret Wood Rings, Secret World Legends Release Date, Secret World Of Arrietty, Secret Weapon, Secret Wars 2015, Secret Warriors, Secret X Folder, Secret Xtians, Secret Xscape, Secret X Folder Comic, Secret X, Secret Xbox One Gamerpics, Secret Xtend, Secret Xbox One Games, Secret Xbox One Codes, Secret X Folder Webtoon, Secret Youtube, Secret Yeahu, Secret Yellowstone, Secret Young Justice, Secret Youtube Videos, Secret Yosemite, Secret Youtube Tricks, Secret Youtube Website, Secret Yumiverse, Secret Yosemite Spots, Secret Zoo Series, Secret Zoo, Secret Zoo Book, Secret Zinger, Secret Zombies Calling Card, Secret Zodiac Sign, Secret Zion Hikes, Secret Zone, Secret Zombies Challenge Infinite Warfare, Secret Zombie Challenge, Bizarre Foods, Bizarre Definition, Bizarre Love Triangle, Bizarre Holidays, Bizarre Foods Detroit, Bizarre Love Triangle Lyrics, Bizarre D12, Bizarre News, Bizarre States, Bizarre Facts, Bizarre Animals, Bizarre Art, Bizarre Adventure, Bizarre Antonym, Bizarre Animal Facts, Bizarre Accidents, Bizarre And Unique Holidays, Bizarre Bar, Bizarre Bark, Bizarre Bazaar, Bizarre Bodies, Bizarre Bizarre, Bizarre Behavior, Bizarre Baby Names, Bizarre Bath, Bizarre Crimes, Bizarre Creations, Bizarre Creatures, Bizarre Correlations, Bizarre Coincidences, Bizarre Clothing, Bizarre Crossword Clue, Bizarre Conspiracy Theories, Bizarre Definition, Bizarre D12, Bizarre Deaths, Bizarre Delusions, Bizarre Diseases, Bizarre Dinosaurs, Bizarre Disappearances, Bizarre Documentaries, Bizarre Er, Bizarre Entr’acte, Bizarre Er Narrator, Bizarre Er Full Episodes, Bizarre Foods, Bizarre Foods Detroit, Bizarre Facts, Bizarre Foods Chicago, Bizarre Foods Great Lakes, Bizarre Funerals, Bizarre Foods Puerto Rico, Bizarre Foods Cleveland, Bizarre Foods Full Episodes, Bizarre Foods Toronto, Bizarre Guitar, Bizarre Guitar Reno, Bizarre Guns, Bizarre Glass, Bizarre Holidays, Bizarre History, Bizarre Hair, Bizarre History Facts, Bizarre In Spanish, Bizarre Inc, Bizarre Images, Bizarre Interview Questions, Bizarre Icd 10 Codes, Bizarre Inventions, Bizarre In Sentence, Bizarre Jobs, Bizarre Justin Bieber, Bizarre Kooky Crossword Clue, Bizarre Kooky, Bizarre Love Triangle, Bizarre Love Triangle Lyrics, Bizarre Laws, Bizarre Love Triangle Frente, Bizarre Love Triangle Remix, Bizarre Love Triangle Ukulele, Bizarre Love Triangle Tabs, Bizarre Love Triangle Guitar Chords, Bizarre Meaning, Bizarre Murders, Bizarre Memes, Bizarre Meats Las Vegas, Bizarre Movie, Bizarre Meats, Bizarre Magic, Bizarre Music, Bizarre News, Bizarre Net Worth, Bizarre Names, Bizarre Nfl Quiz, Bizarre Of Bad Dreams, Bizarre Photos, Bizarre Phobias, Bizarre Plants, Bizarre Places, Bizarre Pronunciation, Bizarre Quotes, Bizarre Questions, Bizarre Questions To Ask Someone, Bizarre Rapper, Bizarre Ride Ii The Pharcyde, Bizarre Room Kingdom Hearts, Bizarre Records, Bizarre Religions, Bizarre Rituals, Bizarre Restaurant, Bizarre States, Bizarre Stories, Bizarre Show, Bizarre Sea Creatures, Bizarre Sports, Bizarre Scholarships, Bizarre States Facebook, Bizarre Things, Bizarre Tv, Bizarre Tv Show, Bizarre Tattoos, Bizarre Thesaurus, Bizarre True Stories, Bizarre Titan, Bizarre Trivia, Bizarre Tribe, Bizarre Traditions, Bizarre Uproar, Bazaarvoice, Bazaarvoice Careers, Bazaarvoice Rating Count, Bazaarvoice Stock, Bazaarvoice Login, Bazaarvoice Reviews, Bazaarvoice Wiki, Bazaarvoice Logo, Bazaarvoice Competitors, Bazaarvoice Api, Bizarre Words, Bizarre Weather, Bizarre World Records, Illuminati Song, Illuminati Symbols, Illuminati Card Game, Illuminati Confirmed, Illuminati Eye, Illuminati Definition, Illuminati Extracts, Illuminati Meaning, Illuminati Triangle, Illuminati Tattoos, Illuminati All Seeing Eye, Illuminati Art, Illuminati Ambigram, Illuminati Airport, Illuminati Aliens, Illuminati Agenda, Illuminati Application, Illuminati And Freemasons, Illuminati Anagram, Illuminati Artists, Illuminati Backwards, Illuminati Book, Illuminati Bloodlines, Illuminati Ball, Illuminati Background, Illuminati Beliefs, Illuminati Board Game, Illuminati Blood Sacrifice, Illuminati Baseball Team, Illuminati Brotherhood, Illuminati Card Game, Illuminati Confirmed, Illuminati Chester Bennington, Illuminati Conspiracy, Illuminati Cards, Illuminati Cartridges, Illuminati Confirmed Meme, Illuminati Confirmed Song, Illuminati Cloning, Illuminati Celebrity, Illuminati Definition, Illuminati Deepest Gobdip, Illuminati Drawings, Illuminati Darkest Gobcoat, Illuminati Disney, Illuminati Diamond, Illuminati Devil, Illuminati Deep Gobdip, Illuminati Dark Gobcoat, Illuminati Documentary, Illuminati Eye, Illuminati Extracts, Illuminati Emoji, Illuminati Exposed, Illuminati Extracts Cartridge, Illuminati Eye Tattoo, Illuminati Evidence, Illuminati Explained, Illuminati Evil, Illuminati Extracts Pen, Illuminati Fidget Spinner, Illuminati Facts, Illuminati Fake, Illuminati Families, Illuminati Founder, Illuminati Funny, Illuminati Font, Illuminati Facebook, Illuminati Fish, Illuminati Fidget Spinner Amazon, Illuminati Glass, Illuminati Gif, Illuminati Game, Illuminati Gobtwine, Illuminati Group, Illuminati Gobdip, Illuminati Goat, Illuminati God, Illuminati Gobcoat, Illuminati Gang, Illuminati History, Illuminati Hand Signs, Illuminati Hand Symbols, Illuminati Headquarters, Illuminati Handshake, Illuminati Hollywood, Illuminati Hat, Illuminati Hamilton, Illuminati Hand, Illuminati Hip Hop, Illuminati Itanimulli, Illuminati Is Real, Illuminati Images, Illuminati Initiation, Illuminati Instagram, Illuminati Is Fake, Illuminati In The Music Industry, Illuminati In Hollywood, Illuminati In Spanish, Illuminati In Detroit, Illuminati Join, Illuminati Jokes, Illuminati Jacket, Illuminati Jobs, Illuminati Jesus, Illuminati Jpg, Illuminati Juice, Illuminati Joke Program, Illuminati Jingle, Illuminati Jersey, Illuminati King, Illuminati Killers, Illuminati Killings, Illuminati Kfc, Illuminati Knowledge, Illuminati Kickstarter, Illuminati Keyboard Symbol, Illuminati Keyboard, Illuminati Kid Shows, Illuminati Kingdom, Illuminati Logo, Illuminati Leader, Illuminati Language, Illuminati Lyrics, Illuminati Lizard, Illuminati Location, Illuminati Light Meter, Illuminati Letter, Illuminati List, Illuminati Little League, Illuminati Music, Illuminati Meaning, Illuminati Meme, Illuminati Members, Illuminati Movies, Illuminati Marvel, Illuminati Mind Control, Illuminati Mask, Illuminati Money, Illuminati Membership, Illuminati Numbers, Illuminati News, Illuminati New World Order, Illuminati Necklace, Illuminati Near Me, Illuminati Numerology, Illuminati Names, Illuminati Noise, Illuminati Nba Finals 2017, Illuminati Nails, Illuminati Owl, Illuminati Official Website, Illuminati Og, Illuminati Origins, Illuminati Oils, Illuminati Oath, Illuminati On Money, Illuminati On Dollar, Illuminati One Eye, Illuminati Occult, Illuminati Pyramid, Illuminati Pictures, Illuminati Pizza Chicago, Illuminati Png, Illuminati Phone Number, Illuminati Proof, Illuminati Perch, Illuminati Popsocket, Illuminati Playing Cards, Illuminati People, Illuminati Quotes, Illuminati Queen, Illuminati Quiz, Illuminati Questions, Illuminati Que Es, Illuminati Quora, Illuminati Quotes Twitter, Illuminati Queen Poppy, Illuminati Quick Launch, Illuminati Quienes Son, Illuminati Rituals, Illuminati Ring, Illuminati Real, Illuminati Rappers, Illuminati Remix, Illuminati Roblox Id, Illuminati Religion, Illuminati Reddit, Illuminati Roblox, Illuminati Rules, Illuminati Song, Illuminati Symbols, Illuminati Signs, Illuminati Sound, Illuminati Secrets, Illuminati Shirt, Illuminati Sign Up, Illuminati Sacrifices, Illuminati Spinner, Illuminati Song Short, Illuminati Triangle, Illuminati Tattoos, Illuminati Theme Song, Illuminati Tautest Gobtwine, Illuminati Theory, Illuminati Taut Gobtwine, Illuminati Twitter, Illuminati Text, Illuminati Triangle Meaning, Illuminati Temple, Illuminati Urban Dictionary, Illuminati University, Illuminati Upside Down, Illuminati Update, Illuminati Unicode, Illuminati Unicorn, Illuminati Usa, Illuminati Underground, Illuminati Undercut, Illuminati Uniform, Illuminati Videos, Illuminati Vines, Illuminati Vape, Illuminati Vape Cartridges Review, Illuminati Voice, Illuminati Vape Cartridges, Illuminati Video Game, Illuminati Vapor, Illuminati Vector, Illuminati Vs God, Illuminati Website, Illuminati Wiki, Illuminati Wallpaper, Illuminatiwatcher, Illuminati What Is It, Illuminati Words, Illuminati Ww3, Illuminati Wife Tells All, Illuminati Water, Illuminati Writing, Illuminati X Files, Illuminati X, Illuminati X Files Vine, Illuminati X Reader, Illuminati X Factor, Illuminati X Files Trap Remix, Illuminati Youtube, Illuminati Yee, Illuminati Youth Baseball, Illuminati Y2k, Illuminati Youth Baseball Team, Illuminati Youtube 2017, Illuminati Yahoo Answers, Illuminati Y2k Cards, Illuminati Yellow, Illuminati Yoga, Illuminati Zeitgeist, Illuminati Zoa, Illuminati Zack And Cody, Illuminati Zombies, Illuminati Zoanthids, Illuminati Zelda, Illuminati Zodiac, Illuminati Zoom In, Illuminati Zionist, Illuminati Zionism, Photo Editor, Photo Booth, Photo Booth Rental, Photo Collage, Photo Books, Photoshop, Photo Search, Photo Printing, Photo Albums, Photo Editing Software, Photo Albums, Photo Apps, Photo Ark, Photo Album Book, Photoaffections, Photo Art, Photo Albums Target, Photo Albums Walmart, Photo Albums Amazon, Photo A Day Challenge, Photo Booth, Photo Books, Photo Booth Props, Photo Booth Rental, Photo Blanket, Photo Booth Rental Chicago, Photo Backdrops, Photobucket, Photo Booth Frame, Photo Booth App, Photo Collage, Photo Collage Maker, Photo Cropper, Photo Collage App, Photo Canvas, Photo Cards, Photo Contest, Photo Captions, Photo Credit, Photo Contest 2017, Photo Direct, Photo Definition, Photo Developing, Photo Display, Photo Director, Photo Dimensions, Photodetector, Photo Design, Photo Directory, Photo Download, Photo Editor, Photo Editing Software, Photo Editor App, Photo Editing Apps, Photo Essay, Photo Editing Software Free, Photo Editor For Mac, Photo Editing Online, Photo Effects, Photo Enlargements, Photo Frames, Photo Filters, Photo Finish, Photo Facial, Photo Factory, Photo Frame Sizes, Photo Finder, Photo Frame Prop, Photo Finish Crossword, Photo Filters Online, Photo Grid, Photo Gallery, Photo Gifts, Photo Google, Photo Generator, Photo Gift Ideas, Photo Gifts Walmart, Photo Grid Online, Photo Guest Book, Photo Gallery Website, Photo Hosting, Photo Holder, Photo Hosting Sites, Photo Hunt, Photo Hanger, Photo Hut, Photo Heart Booth Png, Photo Hiding App, Photo Headcovers, Photo Heart, Photo Id, Photo Invitations, Photo Ideas, Photo In Spanish, Photo Icon, Photo Identification, Photo Impressions, Photo Id Cards, Photo Identifier, Photo Illustration, Photojoiner, Photo Journal, Photo Jewelry, Photojournalism, Photo Job Zone, Photo Joes, Photojournalist, Photojojo, Photo Joe’s Westland Michigan, Photo Jet, Photo Keychain, Photo Keeper, Photokeeper Email, Photo Kano, Photo Kiosk, Photo Key, Photo Kiosk Near Me, Photo Keepsake Box, Photo Koozie, Photo Keeper Reviews, Photo Lookup, Photo Lab, Photo Library, Photo Logo, Photo Light Box, Photo Lab Near Me, Photo Lighting, Photo Layout, Photo Ledge, Photo Locket, Photomath, Photo Mechanic, Photo Mugs, Photo Magnets, Photo Montage, Photo Monkey, Photo Manipulation, Photo Maker, Photo Mosaic, Photo Mat, Photo Near Me, Photo Necklace, Photo Negative, Photo Negative Mickey, Photo Not Available, Photo Negative Scanner, Photo Ninja, Photo Notice, Photo Note Cards, Photo News, Photo Op, Photo Of The Day, Photo Organizer, Photo On Canvas, Photo Of A Tick, Photo On Wood, Photo Of Earth, Photo Overlay, Photo Of A Bed Bug, Photo Of Brown Recluse Spider, Photo Printing, Photo Printer, Photo Peach, Photo Paper, Photo Printing Near Me, Photo Props, Photo Printing Services, Photo Puzzle, Photo Pillows, Photo Phone Case, Photo Quotes, Photo Quilt, Photo Quality Printer, Photo Quality, Photo Quality Paper, Photo Quality Enhancer, Photo Quilt Patterns, Photo Quiz, Photo Quote Maker, Photo Quality Laser Printer, Photo Resizer, Photo Release Form, Photo Restoration, Photo Recovery, Photo Reverse, Photo Retouching, Photo Recognition, Photo Release, Photorealism, Photo Root Word, Photoshop, Photo Search, Photo Shoot, Photo Scanner, Photo Sizes, Photo Storage, Photo Sharing Sites, Photo Studio, Photo Studio Near Me, Photo Sharing, Photo To Canvas, Photo Transfer App, Photo Transfer To Wood, Photo Thank You Cards, Photo Tiles, Photo To Cartoon, Photo To Sketch, Photo Translator, Photo To Text, Photo Tachometer, Photo Upload, Photo Upload Sites, Photo Up, Photo Unavailable, Photo Umbrella, Photo Url, Photo Usa, Photo Upload App, Photo Upscaler, Photobucket, Photo Vault, Photo Viewer, Photo Video Maker, Photo Viewer Windows 10, Photo Video, Photo Viewer Update, Photovoice, Photo Viewer For Mac, Photo Vest, Photo Vault Apps, Photo Websites, Photo Wall, Photo Walgreens, Photo Walmart, Photo Wonder, Photo Wallpaper, Photo Wedding Invitations, Photo Wall Ideas, Photo Weaving, Photo Watermark, Photo X, Photo X Ray, Photo Xray Online, Photo Xpeditions, Photo Xxl, Photo Xcaret, Photo Xp-960, Photo X For Mac, Photo Xchng, Photo Exif, Photo Yankee Candle, Photo Yonas, Photo Yard Signs, Photo Yearbook, Photo Yonas Lyrics, Photo Youtube, Photo Yoga Mat, Photo Y Video, Photo Yahoo, Photo Yodobashi, Photo Zine, Photo Zoom, Photozone, Photo Zine Printing, Photo Zoomer, Photo Zoom App, Photo Zip, Photo Zoom Chrome, Photo Zoom Enhancer, Photo Zine Template, ,Party City, Party City Near Me, Party City Coupons, Party Express, Party Bus Rental, Party Bus, Party Supplies, Party Of Five, Party Rentals, Party In The Usa, Party Adventure, Party All The Time, Party Appetizers, Party At My Parents House, Party America, Party Animal, Party Apart, Party At Lewis, Party At The Moon Tower, Party And Food, Party Bus Rental, Party Bus, Party Buses, Party Bus Detroit, Party Bus Near Me, Party Bus Prices, Party Bus For Sale, Party Boat, Party Balloons, Party Background, Party City, Party City Near Me, Party City Coupons, Party City Novi, Party City Ann Arbor, Party City Livonia, Party City Balloons, Party City Dearborn, Party City Southfield, Party City Allen Park, Party Dresses, Party Decorations, Party Down, Party Down South, Party Definition, Party Decorations Stores, Party Dreams, Party Drinks, Party Depot, Party Dresses For Women, Party Express, Party Everyday, Party Emoji, Party Equipment Rental, Party Express Number, Party Entertainment, Party Eyes, Party Equipment Rental Near Me, Party Essentials, Party Entertainment Rentals, Party Favors, Party Food Ideas, Party Favor Ideas, Party Favors For Kids, Party For Less, Party Favor Bags, Party Finger Foods, Party Flyers, Party Foul, Party Favors For Adults, Party Games, Party Gif, Party Giant, Party Games For Kids, Party Girl, Party Game Rentals, Party Galaxy, Party Goblin, Party Girls Die In Pearls, Party Game Rentals Near Me, Party Heart, Party Hat, Party Hard, Party Halls Near Me, Party Hard 2, Party House, Party Hard Gif, Party Horn, Party Hut, Party Hat Template, Party In The Usa, Party In A Bathrobe, Party In The Usa Lyrics, Party Invitations, Party Ideas, Party In Spanish, Party In A Box, Party In The Cia, Party Invitation Template, Party Images, Party Jacks, Party Jokes, Party Jumpers, Party Jumpsuits, Party Junkie, Party In The Usa, Party Jesus, Party Jams, Patty Jenkins, Party Jollof, Party King, Party Kei, Party Karaoke Songs, Party Kazoo, Party King Gratiot, Party Kits, Party Keg, Party Karamu Fiesta Forever, Party King Grills, Party Katya, Party Lyrics, Party Lights, Party Legends, Party Line, Party Like A Rockstar, Partylite, Party Like It’s 1999, Party Land Canton Mi, Party Like A Pineapple, Party Lounge, Party Meme, Party Monster, Party Monster Lyrics, Party Music, Party Max, Party Maids, Party Monster Movie, Party Movies, Party Mix, Party Machine, Partynextdoor, Party Names, Party Napkins, Party Near Me, Party Noise Makers, Party Nail, Party Name Generator, Party Night, Party Noise Maker Sound, Party N Play, Party Of Five, Party On, Party Of Five Cast, Party Outfits, Party Of 5, Party On Garth, Party On The Purple, Party On Mccarty, Party Outfitters, Party Of Five Imdb, Party Place, Party Paradise, Party Potatoes, Party Pooper, Party Planner, Party Place Rental, Party Parrot, Party Panic, Party Poppers, Party Punch, Party Quotes, Party Questions, Party Q, Party Quirks, Party Quiz, Party Quotes Tumblr, Party Queen, Party Quotes Great Gatsby, Party Quirks Improv Game, Party Queen Hair, Party Rentals, Party Rock Anthem, Party Rental Near Me, Party Rock Anthem Lyrics, Party Raft, Party Rentals Michigan, Party Rentals Detroit, Party Rental Ann Arbor, Party Realignment, Party Rental Brighton Mi, Party Store Near Me, Party Supplies, Party Store, Party Source, Party Songs, Party Supply Stores, Party Subs, Party Supplies Near Me, Party Synonym, Party Supply Store Near Me, Party Tents, Party Themes, Party Time Rentals, Party Tent Rentals, Party Time, Party Town, Party Trays, Party Tour, Party Theme Ideas, Party Tent For Sale, Party Usa, Party Up Dmx, Party Up Lyrics, Party Urban Dictionary, Party Up Prince, Party Usher, Party Up Lyrics Prince, Party Up Prince Youtube, Party Universe, Party Usa Flint Mi, Party City, Party Venues Near Me, Party Venues, Party Venues In Detroit, Party Venues In Michigan, Party Van, Party City Near Me, Party Van Rental, Party Venues Columbus Ohio, Party Venues In Lansing Mi, Party Warehouse, Party World, Party Wall, Party Works, Party Wings, Party Whip Definition, Party Wristbands, Party With Pardi, Party Words, Party Wholesale, Party City, Party X, Party City Near Me, Party City Coupons, Party City Novi, Party City Ann Arbor, Party City Livonia, Party City Balloons, Party City Dearborn, Party X Cast, Parti Yorkie, Party Yacht, Party Youtube, Party Yacht Rental, Parti Yorkie For Sale, Party Your Body, Parti Yorkshire Terrier, Parti Yorkie For Sale In Michigan, Party Yard Signs, Party Your Blank Off, Party Zone, Party Zone Ip, Party Zones Inc, Party Zeppelin, Party Zone Pinball, Party Zone Minecraft, Party Zone Usa, Party Zone Cancun, Party Zoo, Party Zone Sign, Leak Detection, Leak Down Test, Leak Down Tester, Leak Detector, Leak Definition, Leak In Spanish, Leak Detection Pump, Leak Seal, Leak Stopper, Leakforums, Leak And Sons Funeral Home, Leak Alarm, Leak Ap Gov, Leak Amniotic Fluid, Leak Alert, Leak Around Chimney, Leake And Watts, Leek And Potato Soup, Leaked Albums, Leak At Water Meter, Leak B Gone, Leak Bros, Leak Barrier, Leak Base, Leak Bali, Leak Barrier Ms300, Leak Busters, Leak Behind Shower, Leak Behind Wall, Leak Before Break, Leak Channels, Leakcanary, Leak Crossword Clue, Leak Check, Leak Channels Definition, Leak Controller, Leak Code, Leak Catcher, Leak City, Leak Ceiling, Leak Detection, Leak Down Test, Leak Down Tester, Leak Detector, Leak Definition, Leak Detection Pump, Leak Detection Equipment, Leak Doctor, Leak Definition Government, Leak Defense System, Leak Ender 2000, Leak En Espanol, Leak Eliminators, Leaked Early, Leak Electric, Leak Experts, Leak En Francais, Leak Early Album, Leak Exhaust, Leak Emoji, Leakforums, Leak Freeze, Leek Food, Leak Finders, Leak Fix, Leakfrog, Leak Fixer, Leak Fix Spray, Leaked Forms, Leak Famous.com, Leak Gopher, Leak Guard, Leak Gif, Leak Geeks, Leak Guard Protection, Leaky Gut, Leak Garbage Disposal, Leak Guardian, Leak Girl, Leak Gopher Vs Fortrezz, Leak Heart Valve, Leak House Of Cards, Leak Hunters, Leak Hack, Leak Hose, Leek Hustle, Leak House Of Cards Season 5, Leak Head Gasket, Leek Hunting, Leek Herb, Leak In Spanish, Leak In Ceiling, Leak In Roof, Leak In Radiator, Leak In Basement, Leak In Pool, Leak In Tire, Leak In Basement Wall, Leak In The Boat, Leak In Heart, Leek Jack, Leak Jones, Leak Jet, Leak Jokes, Leak Jacob, Leek Jack Campus Girl, Leek Jack Lyrics, Leak Journalism, Leak James Comey, Leek Jack Age, Leak Kingdom, Leak King, Leak Kitchen Faucet, Leek Knife, Leak Kitchen Sink, Leak Kanseng, Leak Kitchen Sink Drain, Leak Khan Bombak Sne, Leak K Channels, Leaky Kohler Faucet, Leak Lock, Leak Live, Leak Like A Siv, Leak Locators, Leak Less, Leak Like A Sieve, Leak Location Services, Leak Light, Leak Lock Sds, Leak League Of Legends, Leak Meaning, Leak Masters, Leak Memory Chapel, Leak Meme, Lake Mead, Leak Music, Leak Master Roofing, Leak Movie, Leak Memorial, Leak Meaning In Hindi, Leak No More, Leak News, Leak No More For Dogs, Leak Nutrition, Leak Near Me, Leak No More Reviews, Leak No More York Pa, Leak Near Water Meter, Leaked Nsa, Leak No Stallin, Leak Off Test, Leak Out, Leak Oil, Leak Of Information, Leek Onion, Leak On Ceiling, Leak Of Orange Is The New Black, Leak On Roof, Leak Out Meaning, Leak Or Leakage, Leak Project, Leak Proof Underwear, Leak Proof, Leak Proof Travel Bottles, Leak Proof Containers, Leek Plant, Leak Proof Tape, Leak Proof Water Bottle, Leak Proof Bag, Leak Project Youtube, Leak Quotes, Leek Quiche, Leak Quizlet, Leek Quiche Recipes, Leek Quinoa, Leek Quiche Bacon, Leek Quiche Healthy, Leek Quiche Crustless, Leek Quiche Epicurious, Leek Quiche Allrecipes, Leak Repair, Leak Repair Tape, Leak Rate Calculator, Leak Rate, Leak Reddit, Leek Recipes, Leak Rate Units, Leak Rate Conversion, Leak Repair Spray, Leak Repair Putty, Leek Soup, Leak Seal, Leak Stopper, Leak Synonym, Leak Stop, Leak Sealer, Leek Spin, Leak Seal Tape, Leak Squad, Leak Source, Leak Test, Leak Tape, Leak Tester, Leak Threads, Leak Tamer, Leak Tech, Leak Tec, Leak Tools, Leak Test Solution, Leak Tracing Powder, Leak Under Sink, Leak Under Car, Leak Urine, Leak Under Toilet, Leak Under Slab, Leak Under Bathroom Floor, Leak Under Dishwasher, Leak Under Washer, Leak Under Toilet Tank, Leak Under House, Leak Video, Leek Vegetable, Leak Valve, Leak Veggie, Leek Veggie, Leek Vs Onion, Leek Vs Scallion, Leek Vegetable Soup, Leak Vrf To Global, Leak Or Leakage, Leak Wizard, Leak Water, Leak Website, Leak Wall House Rockingham Nc, Leak Week, Leaked White House, Leaked Winner, Leak Washington Post, Leak Water Heater, Leak Wrap, Leak Xenforo, Leak Xur, Leak Xbox One, Leak Xur 3 April, Leak You, Leak Your Ex, Leak Youtube, Leak Your Number, Leak Year, Leak You Up And Down, Leak Young Og Project, Leak Leaky, Leak Make Your Future Bleak, Liveleak Youtube, Leak Zip, Leak Z10, Leak Z4, Leak Zelda, Leak Zimbabwe, Leak Zhang Ziyi, Leak Zelda Wii U, Leak Zombies, Zircon Leak Alert, Zero Leak Gold
Revealed – The Secret CIA-Nazi Collaboration by the CIA History Staff – Top Secret
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Top Secret – Mossad: Putin prepares his military for World War III
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Secret Life Of Pets, Secret Service, Secret Garden, Secret World Legends, Secret Flying, Secret Life Of Bees, Secret Life Of Pets Cast, Secret Life Of The American Teenager, Secret Squirrel, Secret Shopper, Secret Agent Man, Secret Admirer, Secret Aardvark, Secret Agent, Secret Annex, Secret And Lies, Secret Agent Man Song, Secret App, Secret Asian Man, Secret Agent Man Lyrics, Secretbuilders, Secret Book, Secret Beach Kauai, Secret Beach, Secret Ballot, Secret Box, Secret Beach Maui, Secret Bay Dominica, Secret Base, Secret Band, Secret Circle, Secret Church, Secret Caverns, Secret Classroom Superpowers, Secret Codes, Secret Clinical Strength, Secret Clearance, Secret Circle Cast, Secret Conversations Facebook, Secret Cameras, Secret Deodorant, Secret Definition, Secret Diary Of A Call Girl, Secret Door, Secret Deodorant Coupons, Secret Diary, Secret Deodorant Commercial, Secret Decoder Ring, Secret Daughter, Secret Door Lyrics, Secret Empire, Secret Extensions, Secret Escapes, Secret Empire #1, Secret Empire Reading Order, Secret Entourage, Secret Empire #0, Secret Empire #2, Secret Eaters, Secret Emoji, Secret Flying, Secret Forest, Secret Forest Ep 11, Secret Falls Kauai, Secret Flask, Secret Formula, Secret Facebook Group, Secret Frappuccino, Secret For The Mad Lyrics, Secret Falls, Secret Garden, Secret Garden Song, Secret Garden Movie, Secret Garden Cafe, Secret Garden Musical, Secret Garden Lyrics, Secret Garden Denver, Secret Garden Book, Secret Google Games, Secret Garden Miami, Secret Hitler Rules, Secret Hitler Game, Secret History Of Twin Peaks, Secret Hitler Online, Secret Hair Extensions, Secret Handshake, Secret History, Secret Hotel Deals, Secret Heart, Secret Hiding Places, Secret In Their Eyes, Secret In Spanish, Secret Ingredient, Secret Island, Secret In Their Eyes Cast, Secret Invasion, Secret In N Out Menu, Secret Invisible Solid, Secret Island In Texas, Secret In French, Secret Jardin, Secret Jewels, Secret Journal, Secret Jobs, Secret Jamaica, Secret Jieun, Secret Jardin Lodge, Secret Journey Police, Secret Journey To Planet Serpo, Secret Jardin Dr90, Secret Kpop, Secret Keeper Girl, Secret Keeper, Secret Key, Secret Korean Drama, Secret Knock, Secret Knowledge, Secret Krabby Patty Formula, Secret Key Starting Treatment Essence, Secret Kingdom, Secret Life Of Pets, Secret Life Of Bees, Secret Life Of Pets Cast, Secret Life Of The American Teenager, Secret Love Song, Secret Life Of Walter Mitty, Secret Lab Chair, Secret Life Of An American Teenager Cast, Secret Language, Secret Life Of Pets Imdb, Secret Menu, Secret Menu Items, Secret Mage, Secret Menu Starbucks, Secret Menu In N Out, Secret Messages, Secret Meaning, Secret Movie, Secret Mountain Fort Awesome, Secret Mage Deck, Secret Nails, Secret Nyc, Secret Netflix, Secret Nail Salon, Secret Names, Secret Netflix Codes, Secret Numbers, Secret News, Secret Nature From Jeju Peeling Gel, Secret Nation, Secret Of Mana, Secret Of Nimh, Secret Of The Snowy Peaks, Secret Of The Cedars, Secret Of Kells, Secret Of Evermore, Secret Of The Wings, Secret Of Moonacre, Secret Of Mana Rom, Secret Of Mana 2, Secret Pizza, Secret Police, Secret Project Robot, Secret Place, Secret Passion Fruit, Secret Power, Secret Passages, Secret Pizza Party, Secret Paladin, Secret Place Lyrics, Secret Quotes, Secret Question, Secret Quest, Secret Questions To Ask, Secret Questions To Ask Siri, Secret Quests Ffxv, Secret Quests Skyrim, Secret Qr Codes, Secret Questions To Ask Alexa, Secret Quote Spongebob, Secret Romance, Secret Resorts, Secret Recipe, Secret Rooms, Secret Rare Pokemon Cards, Secret Rainbow Hair, Secret Rare Ultra Ball, Secret Rendezvous, Secret Relationship, Secret Roku Channels, Secret Service, Secret Squirrel, Secret Shopper, Secret Societies, Secret Synonym, Secret Starbucks Menu, Secret Service Jobs, Secret Sandwich Society, Secret Sisters, Secret Shopper Jobs, Secret Treasures, Secret Treasures Sleepwear, Secret Tunnel, Secret Things, Secret Tunnel Song, Secret The Pierces, Secret Thesaurus, Secret Travel, Secret Treasures Bra, Secret To Success, Secret Underground Cities, Secret Us Weapons, Secret Underground Bases, Secret Universe Of Names, Secret Underground, Secret Underground Medicine, Secret Upgrades Office Space, Secret Us Bases, Secret Us Military Bases, Secret Unscented, Secret Variety Training, Secret Village Of The Spellcasters, Secret Video Recorder, Secret Variety Training Ep 2, Secret Vault, Secret Vault 81, Secret Veneers, Secret Voice Recorder, Secret Video, Secret Volume, Secret World Legends, Secret Window, Secret Wood, Secret Wars, Secret Wood Rings, Secret World Legends Release Date, Secret World Of Arrietty, Secret Weapon, Secret Wars 2015, Secret Warriors, Secret X Folder, Secret Xtians, Secret Xscape, Secret X Folder Comic, Secret X, Secret Xbox One Gamerpics, Secret Xtend, Secret Xbox One Games, Secret Xbox One Codes, Secret X Folder Webtoon, Secret Youtube, Secret Yeahu, Secret Yellowstone, Secret Young Justice, Secret Youtube Videos, Secret Yosemite, Secret Youtube Tricks, Secret Youtube Website, Secret Yumiverse, Secret Yosemite Spots, Secret Zoo Series, Secret Zoo, Secret Zoo Book, Secret Zinger, Secret Zombies Calling Card, Secret Zodiac Sign, Secret Zion Hikes, Secret Zone, Secret Zombies Challenge Infinite Warfare, Secret Zombie Challenge, Putin Wife,Putin News,Putin Net Worth,Putin Height,Putin Bay,Putin Memes,Putin Trump,Putin On The Ritz,Putin Age,Putin Trump Meeting,Putin And Trump,Putin Age,Putin And Trump Meeting,Putin Approval Rating,Putin And Obama,Putin Ally Crossword,Putin Assad,Putin And North Korea,Putin And Reagan,Putin As A Child,Putin Bay,Putin Bear,Putin Birthday,Putin Biography,Putin Bay Hotels,Putin Badass,Putin Bay Weather,Putin Blueberry Hill,Putin Bay Ferry,Putin Black Belt,Putin Children,Putin Calendar,Putin Clown,Putin Cartoon,Putin Chechnya,Putin Crying,Putin Canada,Putin Crimea,Putin Corruption,Putin Clinton,Putin Daughters,Putin Dog,Putin Documentary,Putin Dead,Putin Dog Merkel,Putin Definition,Putin Dancing,Putin Dolphins,Putin Drawing,Putin Dancing Gif,Putin Election,Putin Eating Popcorn,Putin English,Putin Election Results,Putin Erdogan,Putin Education,Putin Economy,Putin Eyes,Putin Exxon Deal,Putin Eye Color,Putin Family,Putin Food,Putin Funny,Putin Face,Putin Facts,Putin French,Putin Fishing,Poutine Fries,Putin Fascist,Putin Funny Face,Putin Gif,Putin Genocide,Putin Global Warming,Putin Gymnast,Putin Wife,Putin Gun,Putin Glasses,Putin Gangster,Putin Government,Putin Gorbachev,Putin Height,Putin Horse,Putin House,Putin Horseback,Putin Hockey,Putin History,Putin Hunting,Putin Hillary,Putin Human Rights,Putin Home,Putin Interview,Putin Images,Putin Israel,Putin Iq,Putin Isis,Putin In French,Putin Island,Putin Inauguration,Putin In Power,Putin Instagram,Putin Judo,Putin Jill Stein,Putin Journalists,Putin John Oliver,Putin Jehovah,Putin Jw,Putin Judo Gif,Putin Jesus,Putin James Bond,Putin Jehovah Witness,Putin Kgb,Putin Korea,Putin Karate,Putin Kremlin,Putin Kleptocracy,Putin Kim Jong Un,Putin Kraft Ring,Putin Kabaeva,Putin Khuilo,Putin Kid,Putin Laughing,Putin Laughing Gif,Putin Le Pen,Putin Languages,Putin Latest News,Putin Loves Trump,Putin Lollipop,Putin Likes Trump,Putin Limo,Putin Leadership,Putin Memes,Putin Merkel Dog,Putin Married,Putin Merkel,Putin Makeup,Putin Mask,Putin Martial Arts,Putin Meaning,Putin Macron,Putin Mansion,Putin News,Putin Net Worth,Putin North Korea,Putin New Wife,Putin Netanyahu,Putin Nato,Putin Net Worth Wiki,Putin Name Meaning,Putin Nickname,Putin Nuclear War,Putin On The Ritz,Putin On A Horse,Putin On Trump,Putin On North Korea,Putin Obama,Putin On The Ritz Gif,Putin On Syria,Putin Opposition,Putin On Snl,Putin On The Ritz Meme,Putin President,Putin Piano,Putin Palace,Putin Political Party,Putin Picture,Putin Poison,Putin Propaganda,Putin Puns,Putin Pop Song,Putin Popularity,Putin Quotes,Putin Quotes On Obama,Putin Queen Elizabeth,Putin Quotes Funny,Putin Quizlet,Putin Queen Elizabeth Stairs,Putin Quotes On Trump,Putin Quora,Putin Quote Immigrants,Putin Quebec,Putin Russia,Putin Reagan,Putin Riding Trump,Putin Rise To Power,Putin Reelection,Putin Richest Man In The World,Putin Riding A Ritz Cracker,Putin Response,Putin Ritz,Putin Rainbow,Putin Snl,Putin Syria,Putin Song,Putin Smiling,Putin Speech,Putin Shirt,Putin Speaking English,Putin Singing,Putin Salary,Putin Super Bowl Ring,Putin Trump,Putin Trump Meeting,Putin Twitter,Putin Trump Meme,Putin Trump Horse,Putin Trump Kiss,Putin Term Limit,Putin Trump Gif,Putin Term,Putin Today,Putin Ukraine,Putin Ussr,Putin Us Visit,Putin Unicorn,Putin Us Elections,Putin Un,Putin Undercover,Putin Urban Dictionary,Putin United Nations,Putin Us Relations,Putin Vs Trump,Putin Vs Obama,Putin Vladimir,Putin Video,Putin Vodka,Putin Vs Stalin,Putin Visits Trump,Putin Visit To White House,Putin Vampire,Putin Vs Obama Meme,Putin Wife,Putin Wiki,Putin Wealth,Putin Wink,Putin War,Putin Ww3,Putin Watch,Putin Winking Gif,Putin With Animals,Putin Walking,Putin Xi Jinping,Putin X Obama,Putin X Reader,Putin Xi,Putin And Trump,Putin And Obama,Putin And Assad,Putin And North Korea,Putin And Reagan,Putin And The Ritz,Putin Young,Putin Youtube,Putin Yacht,Putin Youth,Putin Yeltsin,Putin Yume,Putin Years As President,Putin Young Pictures,Putin Youth Army,Putin Yarmulke,Putin Zodiac Sign,Putin Zakaria,Putin Zassal,Putin Zassal Lyrics,Putin Zero Hedge,Putin Zeman,Putin Zil Limousine,Putin Zuma,Putin Za Makedonija,Putin Zapretio Albancima, Mossad 101, Mossad Agent, Mossad 9\/11, Mossad Training, Mossad Motto, Mossad Homeland, Mossad 101 Review, Mossad 101 Season 2, Mossad Movies, Mossad Book, Mossad Agent, Mossad Assassinations, Mossad Aliyah Bet, Mossad Agent Salary, Mossad Agent In Danger, Mossad And 9\/11, Mossad Application, Massad Ayoob, Mossad And Trump, Mossad Assassination Dubai, Mossad Book, Mossad Blacklist, Mossad Badge, Mossad By Deception, Mossad Beretta, Mossad Building, Mossad Budget, Mossad Book Pdf, Mossad Blackmail, Mossad Bodyguards, Mossad Cia, Mossad Careers, Mossad Created Isis, Mossad Covert Affairs, Mossad Cell Phone Bomb, Mossad Contact, Mossad Cz 75, Mossad Chemical Attack, Mossad Cz, Mossad Character Homeland, Mossad Definition, Mossad Documentary, Mossad Did 911, Mossad Dubai, Mossad Dogs, Mossad Draw, Mossad Director Orli Elbaz, Mossad Deception, Mossad Documentary On Netflix, Mossad Dagan, Mossad Eichmann, Mossad Emblem, Mossad Exodus, Mossad Employment, Mossad Equipment, Mossad Ethiopia, Mossad Eagle, Mossad Elite Unit, Mossad Eichmann Movie, Mossad English Website, Mossad False Flag, Mossad Flag, Masada Fortress, Mossad Facepalm, Mossad Failures, Mossad Facts, Mossad Film, Mossad Founder, Mossad Foreign Recruitment, Mossad Funds Isis, Mossad Guns, Mossad Gal Gadot, Mossad Gov Il, Mossad Greatest Hits, Mossad Gun Choice, Mossad Girl, Mossad Group, Mossad Germany, Mossad Greatest Missions Pdf, Mossad Greatest Missions, Mossad Homeland, Mossad History, Mossad Harav Kook, Mossad Headquarters, Mossad Handgun, Mossad Hit Squad, Mossad Honey Trap, Mossad Head, Mossad Hits, Mossad Hamas, Mossad Israel, Mossad Isis, Mossad Images, Mossad In Syria, Mossad In Usa, Mossad In Homeland, Mossad In India, Mossad In Iran, Mossad Internship, Mossad In Dubai, Mossad Jobs, Mossad Jfk, Mossad Jfk Killing, Mossad Jokes, Mossad Join, Mossad Jfk Assassination, Mossad Jewish, Mossad Jacket, Mossad Job Application Form, Mossad Job Openings, Mossad Kidon, Mossad Kidon Training, Mossad Kushner, Mossad Knife, Mossad Killings, Mossad Killed Jfk, Mossad Katsa, Mossad Kennedy, Mossad Kidnapping, Mossad Kush, Mossad Logo, Mossad Lealiyah Bet, Mossad London Attack, Mossad Lillehammer, Mossad Lebanon, Mossad London, Mossad Libro, Mossad Libya, Mossad Logo Translation, Mossad Links To Isis, Mossad Motto, Mossad Movies, Mossad Meaning, Mossad Munich, Mossad Meme, Mossad Murders, Mossad Mission Statement, Mossad Marked Pistol, Mossad Michael Bar-zohar, Mossad Manchester, Mossad Ncis, Mossad Netflix, Mossad News, Mossad Norway, Mossad North Korea, Mossad Nazi, Mossad Name Origin, Mossad Novels, Mossad Nazi Executions, Mossad Nazi Assassinations, Mossad Officer, Mossad Operation, Mossad On Netflix, Mossad Operation In Dubai, Mossad On Twitter, Mossad Official Website, Mossad Olympic Revenge Movie, Mossad Official Motto, Mossad Og, Mossad Operations Youtube, Mossad Pistol, Mossad Pistol For Sale, Mossad Pdf, Mossad Pen, Mossad Podcast, Mossad Pistol Training, Mossad Paris, Mossad Phone Bomb, Mossad Pics, Mossad Pronunciation, Mossad Quotes, Mossad Quora, Mossad Qualifications, Mossad Qatar, Mossad Quiz, Mossad Que Es, Mossad’s Quest, Mossad Quick Draw, Kidon Mossad, Mossad Quotations, Mossad Recruitment Website, Mossad Recruitment, Mossad Russia, Mossad Reddit, Mossad Recruitment Process, Mossad Ranks, Mossad Riddle, Mossad Harav Kook, Mossad Reputation, Mossad Retraining, Mossad Syria, Mossad Spy, Mossad Stole My Shoe, Mossad Stories, Mossad Shirt, Mossad Slogan, Mossad Show Netflix, Mossad Self Defense, Mossad Season 2, Mossad Series, Mossad Training, Mossad Tanfoglio, Mossad Twitter, Mossad Trump, Mossad Tv Show, Mossad Tactical, Mossad T Shirts, Mossad Tactical Duffle Bag, Mossad Training School, Mossad The Greatest Missions, Mossad Uae, Mossad Usa, Mossad Units, Mossad Uniform, Mossad Uk, Mossad Uganda Operation, Mossad Unit 8200, Mossad Ukraine, Mossad Vs Cia, Mossad Vs Kgb, Mossad Video, Mossad Vs Assad, Mossad And Shin Bet, Mossad Vanunu, Mossad Vs Seals, Mossad Vs Navy Seal, Mossad Vs Isi, Mossad Vs Raw, Mossad Website, Mossad Wiki, Mossad Weapons, Mossad Worldwide, Mossad War By Deception, Mossad Workout, Mossad Wikileaks, Mossad Wrath Of God, Mossad Weapons Of Choice, Mossad Ww2, Mossad X, X Mossad Agent, Mossad Prisoner X, Mossad Committee X, Comitato X Mossad, Mossad Xaqida, Comite X Mossad, Mossad Youtube, Mossad Yossi Cohen, Mossad Yearly Cyber Challenge, Mossad Yousef, Mossad Yahudi, Mossad Yemen, Mossad Yahoo Answers, Mossad Yom Kippur War, Massad Ymca, Mossad Youtube Dubai, Mossad Zionist, Mossad Ziva David, Mossad Zippo, Mossad Zohar, Mossad Zoo, Mossad Zamir, Mossad Znacenje, Mossad Zimbabwe, Mossad Zinc, Mossad Zohar Pdf, World War 3 News, World War 3 2017, World War 3 Date, World War 3 Predictions, World War 3 May 13, World War 3 Draft, World War 3 Trump, World War 3 Sides, World War 3 Memes, World War 3 Roster, World War 3 Allies, World War 3 About To Start, World War 3 Article, World War 3 Already Happened, World War 3 Alert, World War 3 April 2017, World War 3 And The Bible, World War 3 Already Started, World War 3 Announced, World War 3 Approaching, World War 3 Bible, World War 3 Begins, World War 3 Book, World War 3 Black Gold, World War 3 Bbc, World War 3 Bible Code, World War 3 Bracket, World War 3 Book Series, World War 3 Breaking News, World War 3 Bunkers, World War 3 Cnn, World War 3 Coming, World War 3 Countries, World War 3 Combatants, World War 3 Call Of Duty, World War 3 Chances, World War 3 Countdown, World War 3 China, World War 3 Clock, World War 3 Conspiracy, World War 3 Date, World War 3 Draft, World War 3 Draft Age, World War 3 Declared, World War 3 Donald Trump, World War 3 Documentary, World War 3 Date 2017, World War 3 Draft Meme, World War 3 Draft Letter, World War 3 Definition, World War 3 End Times, World War 3 End, World War 3 Europe, World War 3 Emp, World War 3 Effects, World War 3 Explained, World War 3 Exact Date, World War 3 Enquirer, World War 3 Events, World War 3 Estimated Date, World War 3 Fox News, World War 3 Fiction Books, World War 3 Fake, World War 3 Facts, World War 3 Fears, World War 3 Fake News, World War 3 Fiction, World War 3 Fatima, World War 3 Film, World War 3 Fox, World War 3 Game, World War 3 Going To Happen, World War 3 Google Trends, World War 3 Guns, World War 3 Gas, World War 3 Gif, World War 3 Germany, World War 3 Games For Pc, World War 3 Game Unblocked, World War 3 Google, World War 3 Has Begun, World War 3 Hoax, World War 3 Has Started, World War 3 Happening, World War 3 How To Prepare, World War 3 Happening Soon, World War 3 History, World War 3 Huffington Post, World War 3 Happening Right Now, World War 3 Horacio, World War 3 Is Coming, World War 3 In The Bible, World War 3 Imminent, World War 3 In Spanish, World War 3 Is Here, World War 3 India, World War 3 In 2017, World War 3 In Space, World War 3 Inevitable, World War 3 Illuminati, World War 3 Jokes, World War 3 Japan, World War 3 Just Started, World War 3 June 2017, World War 3 Jonas Brothers Lyrics, World War 3 Just Around The Corner, World War 3 Jesus, World War 3 July 2017, World War 3 Jadakiss, World War 3 Jw.org, World War 3 Korea, World War 3 Kmfdm, World War 3 Kfc, World War 3 Know Your Meme, World War 3 Kim Jong Un, World War 3 Kab Hogi, World War 3 Ki Bhavishyavani, World War 3 Kaskus, World War 3 Kab Hoga, World War 3 Korea China, World War 3 Lyrics, World War 3 Lineup, World War 3 Lyrics Ruth B, World War 3 Lean, World War 3 Latest News, World War 3 List, World War 3 Location, World War 3 Looming, World War 3 Likely, World War 3 Live, World War 3 May 13, World War 3 Memes, World War 3 Map, World War 3 Movie, World War 3 May 13th, World War 3 May, World War 3 Mexico, World War 3 Mystic, World War 3 Molly, World War 3 Middle East, World War 3 News, World War 3 North Korea, World War 3 News Today, World War 3 News 2017, World War 3 News Cnn, World War 3 Near, World War 3 New York Times, World War 3 Nostradamus, World War 3 Nuclear, World War 3 Novels, World War 3 On The Way, World War 3 Odds, World War 3 On May 13, World War 3 On The Horizon, World War 3 Outcome, World War 3 Opponents, World War 3 Onu, World War 3 On The Brink, World War 3 On The Rise, World War 3 On Pay Tv, World War 3 Predictions, World War 3 Prophecy, World War 3 Possible, World War 3 Prank, World War 3 Prediction Date, World War 3 Probability, World War 3 Pictures, World War 3 Players, World War 3 Prediction 2017, World War 3 Preparations, World War 3 Quotes, World War 3 Quora, World War 3 Quran, World War 3 Quiz, World War 3 Questions, World War 3 Quizlet, World War 3 Queen, World War 3 Qatar, World War 3 Quote Albert Einstein, World War 3 Quote Einstein, World War 3 Roster, World War 3 Reddit, World War 3 Russia, World War 3 Ruth B, World War 3 Ruth B Lyrics, World War 3 Rumors, World War 3 Russia Usa, World War 3 Release Date, World War 3 Real Or Fake, World War 3 Ruff Ryders, World War 3 Sides, World War 3 Scenario, World War 3 Simulation, World War 3 Started, World War 3 Soon, World War 3 Star Trek, World War 3 Start Date, World War 3 Song, World War 3 Syria, World War 3 Simulation Game, World War 3 Trump, World War 3 Teams, World War 3 Timeline, World War 3 Twitter, World War 3 Theories, World War 3 Today, World War 3 The Movie, World War 3 Threat, World War 3 Targets, World War 3 Trending, World War 3 Update, World War 3 Usa, World War 3 United States, World War 3 Unlikely, World War 3 Us, World War 3 Us Allies, World War 3 United Nations, World War 3 Upon Us, World War 3 Un, World War 3 Uk, World War 3 Video, World War 3 Video Games, World War 3 Veteran Hat, World War 3 Veterans, World War 3 Visions, World War 3 Vedic Astrology, World War 3 Videos Youtube, World War 3 Virgin Mary, World War 3 Vladimir Putin, World War 3 Vs, World War 3 Wiki, World War 3 Wcw, World War 3 Will Not Happen, World War 3 Will Be Fought With Nuclear Weapons, World War 3 When, World War 3 Weapons, World War 3 Will Happen, World War 3 Who Would Win, World War 3 Watch, World War 3 Warning, World War 3 Youtube, World War 3 Year, World War 3 Yahoo, World War 3 Youtube 2017, World War 3 Yes Or No, World War 3 Yet, World War 3 Youtube April 2017, World War 3 Year Predictions, World War 3 Youtube 2016, World War 3 Youtube Video, World War 3 Zombie, World War 3 Zdf, World War 3 Zee News, World War 3 Zombie Movie, World War 3 Zombie Outbreak, World War 3 Zionist, World War 3 Zdf English, World War 3 Z, World War 3 Zombie Edition, World War Z 3 Full Movie
Revealed – Top Secret – Terrorist Financing
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
National Terrorist Financing Risk Assessment 2015
Page Count: 70 pages
Date: June 2015
Restriction: None
Originating Organization: Department of the Treasury
File Type: pdf
File Size: 1,425,075 bytes
File Hash (SHA-256): DDC42CE4FBD16
After the September 11, 2001 terrorist attacks, the United States adopted a preventive approach to combating all forms of terrorist activity. Efforts to combat the financing of terrorism (CFT) are a central pillar of this approach. Cutting off financial support to terrorists and terrorist organizations is essential to disrupting their operations and preventing attacks. To that end, the U.S. government has sought to identify and disrupt ongoing terrorist financing (TF) and to prevent future TF. The law enforcement community, including various components of the U.S. Departments of Justice, Homeland Security, and the Treasury, along with the intelligence community and the federal functional regulators, applies robust authorities to identify, investigate, and combat specific TF threats, enforce compliance with applicable laws and regulations, and prosecute supporters in order to deter would-be terrorist financiers. The U.S. Department of the Treasury (Treasury), which leads financial and regulatory CFT efforts for the U.S. government, employs targeted financial sanctions, formulates systemic safeguards, and seeks to increase financial transparency to make accessing the U.S. financial system more difficult and risky for terrorists and their facilitators. All of these efforts involve extensive international engagement to try to prevent any form of TF, particularly financing that does not necessarily originate in the United States, from accessing the U.S. financial system.
These efforts have succeeded in making it significantly more difficult for terrorists and their facilitators to access and abuse the regulated U.S. and international financial systems. At the time of the September 11, 2001 attacks, Al-Qaida (AQ) was relying on both a web of wealthy supporters that practically operated in the open and a financial system that let money for terrorists flow with minimal scrutiny. Operating such a financial network would be substantially more difficult today in the United States because of robust anti-money laundering (AML)/CFT standards. Additionally, several of the most significant sources of TF—such as the ability of terrorists to derive financial benefit through the control of territory—result from weak governance that the United States does not experience.
However, the threat from terrorism and terrorist financing is constantly evolving and requires adaptation by law enforcement, financial regulators, intelligence services, and policy makers. When examined over time, several fundamental lessons emerge: first, a wide range of terrorist organizations have sought to draw upon the wealth and resources of the United States to finance their organizations and activities; second, just as there is no one type of terrorist, there is no one type of terrorist financier or facilitator; and third, terrorist financiers and facilitators are creative and will seek to exploit vulnerabilities in our society and financial system to further their unlawful aims.
Thus, even with the safeguards described above, the U.S. financial system continues to face residual TF risk. The central role of the U.S. financial system within the international financial system and the sheer volume and diversity of international financial transactions that in some way pass through U.S. financial institutions expose the U.S. financial system to TF risks that other financial systems may not face. As Treasury Secretary Jacob Lew has observed, “The dollar is the world’s reserve currency and, for over 200 years, we have established ourselves as the backbone of the global financial system.” While U.S. counterterrorism (CT)/CFT efforts have resulted in better identification and faster action than prior to September 11, 2001, information obtained from financial institution reporting, TF-related prosecutions, and enforcement actions against financial institutions in the United States are powerful reminders of the TF risk that remains in the United States.
As described in detail in Section III, multiple terrorist organizations and radicalized individuals seek to exploit several vulnerabilities in the United States and in the U.S. financial system to raise and move funds, that despite ongoing efforts by the U.S. government to mitigate, still pose a residual risk of TF. Terrorist financiers use various criminal schemes to raise funds in the United States, and they continue to attempt to exploit the generosity of American citizens. Although coordinated law enforcement and regulatory efforts by the U.S. government, working with charitable organizations, has improved the resiliency of the charitable sector to abuse by TF facilitators, the large size and diversity of the U.S. charitable sector and its global reach means the sector remains vulnerable to abuse. A notable trend identified in the charitable sector involves individuals supporting various terrorist groups seeking to raise funds in the United States under the auspices of charitable giving, but outside of any charitable organization recognized by the U.S. government. Additionally, the growth of online communication networks, including social media, has opened up new avenues for terrorists and their supporters to solicit directly, and receive funds from, U.S. residents.
…
B. GLOBAL SOURCES OF TERRORIST FINANCING
In order to operate, however, each of these groups requires significant funding. While the cost of an individual terrorist attack can be quite low, maintaining a terrorist organization requires large sums. Organizations require significant funds to create and maintain an infrastructure of organizational support, to sustain an ideology of terrorism through propaganda, and to finance the ostensibly legitimate activities needed to provide a veil of legitimacy for terrorist organizations. As deceased AQ financial chief Sa’id al-Masri put it: “without money, jihad stops.” Although financial activities can vary significantly among different terrorist groups, several areas of commonality exist.
1. CRIMINAL ACTIVITY
a. Kidnapping for Ransom
Terrorist groups engage in a range of criminal activity to raise needed funds. Extensive revenue from kidnapping for ransom (KFR) and other criminal activities such as extortion have permitted AQ affiliates and other terrorist groups to generate significant revenue. KFR remains one of the most frequent and profitable source of illicit financing, and an extremely challenging TF threat to combat. The U.S. government estimates that terrorist organizations collected approximately $120 million in ransom payments between 2005 and 2012. In 2014 alone, ISIL acquired at least $20 million and as much as $45 million in ransom payments. In addition, AQAP, AQIM, and Boko Haram are particularly effective with KFR and are using ransom money to fund the range of their activities. Kidnapping targets are usually Western citizens of countries with governments that have established a pattern of paying ransoms, either directly or through third party intermediaries, for the release of individuals in custody. AQAP used ransom money it received for the return of European hostages to finance its over $20 million campaign to seize territory in Yemen between mid-2011 and mid-2012. AQIM is believed to have obtained a €30 million ransom payment in October 2013 for the release of four French hostages who worked for the French government-owned nuclear firm Areva. Also in 2013, Boko Haram kidnapped eight French citizens in northern Cameroon and obtained a substantial ransom payment for their release. Similarly, Al-Shabaab-affiliated groups received an approximately five million dollar ransom in exchange for the release of two Spanish hostages who were kidnapped in Kenya in October 2011.
b. Extortion
The exploitation of local populations and resources has become a key revenue source for numerous terrorist groups worldwide. Pioneered by groups such as Hamas and Al-Shabaab, this form of pseudosovereignty-based fundraising has spread to other un- or under-governed territories around the world, most recently Iraq and Syria. Not only does territorial occupation allow for fundraising from the theft of natural resources, but it also creates the opportunity to extort, under the threat of violence, local populations and businesses and generate funds from the seizure of public utility services and their accompanying revenues. Unlike taxation by local governing authorities, whereby tax revenue is used to pay for basic public services, terrorist groups extort funds from local populations with minimal corresponding provision of services in exchange, and under the threat of physical harm for non-payment. For example, Al-Shabaab, Al-Nusrah Front (ANF) and ISIL are all able to leverage their occupation of territory and the threat of violence to extort funds from the local population, as well as conduct criminal activity such as robbery and trafficking in stolen goods. ISIL generates significant revenue, up to several million dollars per week, from the sale of stolen and smuggled energy resources it controls inside Iraq and Syria. ISIL also operates sophisticated extortion rackets throughout Iraq and Syria, including extracting payments for the use of public highways and cash withdrawals from banks by depositors in cities such as Mosul. Through these schemes, ISIL can receive upwards of several million dollars a month of revenue. Despite losing control of the port of Kismayo, which was its key revenue source, Al-Shabaab continues to generate at least hundreds of thousands of dollars per month, primarily through extortion and the threat of violence, in its remaining strongholds in southern Somalia. Similarly, Hamas can also raise revenue from control of border crossings and avenues of commerce, as well as businesses and local populations.
c. Drug trafficking and other criminal activity
In addition, various terrorist groups derive significant financial benefit from other criminal activities, including through drug trafficking. Both the Revolutionary Armed Forces of Colombia (FARC) and the Taliban have utilized drug trafficking operations to finance their terrorist operations. The Haqqani Network is also financed by a wide range of revenue sources including businesses and proceeds derived from criminal activities such as smuggling, extortion, and KFR in Afghanistan and Pakistan. Hizballah supporters are often engaged in a range of criminal activities that benefit the group financially, such as smuggling contraband goods, passport falsification, drug trafficking, money laundering, and a variety of fraudulent schemes, including credit card, immigration, and bank fraud. BSA reporting specifically implicates individuals currently being investigated by the FBI for ties to Hizballah and Hamas in a wide variety of money laundering activity within the U.S. financial system, most prominently trade-based money laundering (TBML) activities including through the export of used cars.
Download
USTreasury-TerroristFinancing-2015
Secret Life Of Pets, Secret Service, Secret Garden, Secret World Legends, Secret Flying, Secret Life Of Bees, Secret Life Of Pets Cast, Secret Life Of The American Teenager, Secret Squirrel, Secret Shopper, Secret Agent Man, Secret Admirer, Secret Aardvark, Secret Agent, Secret Annex, Secret And Lies, Secret Agent Man Song, Secret App, Secret Asian Man, Secret Agent Man Lyrics, Secretbuilders, Secret Book, Secret Beach Kauai, Secret Beach, Secret Ballot, Secret Box, Secret Beach Maui, Secret Bay Dominica, Secret Base, Secret Band, Secret Circle, Secret Church, Secret Caverns, Secret Classroom Superpowers, Secret Codes, Secret Clinical Strength, Secret Clearance, Secret Circle Cast, Secret Conversations Facebook, Secret Cameras, Secret Deodorant, Secret Definition, Secret Diary Of A Call Girl, Secret Door, Secret Deodorant Coupons, Secret Diary, Secret Deodorant Commercial, Secret Decoder Ring, Secret Daughter, Secret Door Lyrics, Secret Empire, Secret Extensions, Secret Escapes, Secret Empire #1, Secret Empire Reading Order, Secret Entourage, Secret Empire #0, Secret Empire #2, Secret Eaters, Secret Emoji, Secret Flying, Secret Forest, Secret Forest Ep 11, Secret Falls Kauai, Secret Flask, Secret Formula, Secret Facebook Group, Secret Frappuccino, Secret For The Mad Lyrics, Secret Falls, Secret Garden, Secret Garden Song, Secret Garden Movie, Secret Garden Cafe, Secret Garden Musical, Secret Garden Lyrics, Secret Garden Denver, Secret Garden Book, Secret Google Games, Secret Garden Miami, Secret Hitler Rules, Secret Hitler Game, Secret History Of Twin Peaks, Secret Hitler Online, Secret Hair Extensions, Secret Handshake, Secret History, Secret Hotel Deals, Secret Heart, Secret Hiding Places, Secret In Their Eyes, Secret In Spanish, Secret Ingredient, Secret Island, Secret In Their Eyes Cast, Secret Invasion, Secret In N Out Menu, Secret Invisible Solid, Secret Island In Texas, Secret In French, Secret Jardin, Secret Jewels, Secret Journal, Secret Jobs, Secret Jamaica, Secret Jieun, Secret Jardin Lodge, Secret Journey Police, Secret Journey To Planet Serpo, Secret Jardin Dr90, Secret Kpop, Secret Keeper Girl, Secret Keeper, Secret Key, Secret Korean Drama, Secret Knock, Secret Knowledge, Secret Krabby Patty Formula, Secret Key Starting Treatment Essence, Secret Kingdom, Secret Life Of Pets, Secret Life Of Bees, Secret Life Of Pets Cast, Secret Life Of The American Teenager, Secret Love Song, Secret Life Of Walter Mitty, Secret Lab Chair, Secret Life Of An American Teenager Cast, Secret Language, Secret Life Of Pets Imdb, Secret Menu, Secret Menu Items, Secret Mage, Secret Menu Starbucks, Secret Menu In N Out, Secret Messages, Secret Meaning, Secret Movie, Secret Mountain Fort Awesome, Secret Mage Deck, Secret Nails, Secret Nyc, Secret Netflix, Secret Nail Salon, Secret Names, Secret Netflix Codes, Secret Numbers, Secret News, Secret Nature From Jeju Peeling Gel, Secret Nation, Secret Of Mana, Secret Of Nimh, Secret Of The Snowy Peaks, Secret Of The Cedars, Secret Of Kells, Secret Of Evermore, Secret Of The Wings, Secret Of Moonacre, Secret Of Mana Rom, Secret Of Mana 2, Secret Pizza, Secret Police, Secret Project Robot, Secret Place, Secret Passion Fruit, Secret Power, Secret Passages, Secret Pizza Party, Secret Paladin, Secret Place Lyrics, Secret Quotes, Secret Question, Secret Quest, Secret Questions To Ask, Secret Questions To Ask Siri, Secret Quests Ffxv, Secret Quests Skyrim, Secret Qr Codes, Secret Questions To Ask Alexa, Secret Quote Spongebob, Secret Romance, Secret Resorts, Secret Recipe, Secret Rooms, Secret Rare Pokemon Cards, Secret Rainbow Hair, Secret Rare Ultra Ball, Secret Rendezvous, Secret Relationship, Secret Roku Channels, Secret Service, Secret Squirrel, Secret Shopper, Secret Societies, Secret Synonym, Secret Starbucks Menu, Secret Service Jobs, Secret Sandwich Society, Secret Sisters, Secret Shopper Jobs, Secret Treasures, Secret Treasures Sleepwear, Secret Tunnel, Secret Things, Secret Tunnel Song, Secret The Pierces, Secret Thesaurus, Secret Travel, Secret Treasures Bra, Secret To Success, Secret Underground Cities, Secret Us Weapons, Secret Underground Bases, Secret Universe Of Names, Secret Underground, Secret Underground Medicine, Secret Upgrades Office Space, Secret Us Bases, Secret Us Military Bases, Secret Unscented, Secret Variety Training, Secret Village Of The Spellcasters, Secret Video Recorder, Secret Variety Training Ep 2, Secret Vault, Secret Vault 81, Secret Veneers, Secret Voice Recorder, Secret Video, Secret Volume, Secret World Legends, Secret Window, Secret Wood, Secret Wars, Secret Wood Rings, Secret World Legends Release Date, Secret World Of Arrietty, Secret Weapon, Secret Wars 2015, Secret Warriors, Secret X Folder, Secret Xtians, Secret Xscape, Secret X Folder Comic, Secret X, Secret Xbox One Gamerpics, Secret Xtend, Secret Xbox One Games, Secret Xbox One Codes, Secret X Folder Webtoon, Secret Youtube, Secret Yeahu, Secret Yellowstone, Secret Young Justice, Secret Youtube Videos, Secret Yosemite, Secret Youtube Tricks, Secret Youtube Website, Secret Yumiverse, Secret Yosemite Spots, Secret Zoo Series, Secret Zoo, Secret Zoo Book, Secret Zinger, Secret Zombies Calling Card, Secret Zodiac Sign, Secret Zion Hikes, Secret Zone, Secret Zombies Challenge Infinite Warfare, Secret Zombie Challenge, Terror Financing In India, Terror Financing And Money Laundering, Terror Financing Definition, Terror Financing In Pakistan, Terror Financing And Demonetisation, Terror Financing, Terror Financing Unit Of The Treasury Department, Terror Financing Convention, Terror Financing Meaning, Terror Financing In Bangladesh, Terror Financing And Money Laundering, Terror Financing And Demonetisation, Iran Terror Financing And The Tax Code, Anti Terror Financing, Financing Terror Bit By Bit, Terror Financing In Bangladesh, Terror Financing Convention, Terror Financing Cases, Terror Financing Challenges, Terror Financing Channels, Counter Terror Financing, Combating Terror Financing, Cyber Crime Terror Financing, Terror Financing Definition, Terror Financing Department, Define Terror Financing, Terror Financing Essay, Terror Financing Expert, Fight Terror Financing, Fbi Terror Financing, Terror Financing To Top G7 Meeting Agenda, Terror Financing In Hindi, Terror Financing In India, Terror Financing In Pakistan, Terror Financing In Bangladesh, Terror Financing In Hindi, Isis Terror Financing, Iran Terror Financing And The Tax Code, Kuwait Terror Financing, Terror Financing Meaning, Terror Financing Methods, Terror Financing To Top G7 Meeting Agenda, Terror Financing Unit Of The Treasury Department, Financing Of Terror, Terror Financing Pakistan, Qatar Terror Financing, Terror Financing Risk, Saudi Terror Financing, Terror Financing To Top G7 Meeting Agenda, Hezbollah Financing Terror Through Criminal Enterprise, Terror Financing Unit Of The Treasury Department, Iran Terror Financing And The Tax Code, Terror Financing Unit Of The Treasury Department, Terror Finance Briefing Book, Terror Finance Blog, Terror Finance Watch List, Terror Finance, Terror Finance Tracking Program, Terror Finance Transparency Act, Terror Finance Networks, Qatar Terror Finance, Counter Terror Finance, Terror Threat Finance Course, Terror Finance Abroad Touches Thanksgiving At Home, Terror Finance Transparency Act, Iran Terror Financing And The Tax Code, Terror Finance Briefing Book, Terror Finance Blog, Financing Terror Bit By Bit, Terror Financing In Bangladesh, Terror Financing Convention, Terror Financing Cases, Terror Financing Challenges, Terror Financing Channels, Terror Threat Finance Course, Counter Terror Finance, Terror Financing Definition, Terror Financing Department, Terror Financing Essay, Terror Financing Expert, Terror Financing In Hindi, Terror Financing In India, Terror Financing In Pakistan, Terror Financing In Bangladesh, Terror Financing In Hindi, Iran Terror Finance Transparency Act, Iran Terror Finance Transparency, Kuwait Terror Finance, Terror Financing Meaning, Terror Financing Methods, Terror Finance Networks, Qatar And Terror Finance Negligence, Terror Financing Unit Of The Treasury Department, Terror Financing Pakistan, Terror Finance Tracking Program, Qatar And Terror Finance Part Ii, Prosper Terror Finance, Qatar Terror Finance, Terror Financing Risk, Us Terror Finance Rules, Qatar And Terror Finance Report, Stop Terror Finance, Terror Finance Tracking Program, Terror Finance Transparency Act, Terror Financing To Top G7 Meeting Agenda, Terror Threat Finance Course, Iran Terror Finance Transparency, The Terror Finance Blog, Turkey Terror Finance, Terror Financing Unit Of The Treasury Department, Us Terror Finance Rules, Terror Finance Watch List
Secret – Gaza Underground Infrastructure Photos
Become a Patron!
True Information is the most valuable resource and we ask you to give back.
| Gaza Underground Infrastructure Photos
Like peoples in simplest caves from the beginning and high-technological cities and nations today, Gaza constructs underground infrastructure to evade undercover all-INT full-spectrum attack exhibited in the first pristine safely-bunkered military industrial media photo.
|
The Most Influential People of All Time – The Secret List
-
112073964
-
26982571642
-
31541801570
-
47022851879
-
5455182384
-
65241791564
-
76462191452
-
8391182427
-
94362351809
-
10354161469
-
11280158356
-
124612431869
-
133161681564
-
14256147551
-
15260163100
-
162841371809
-
17294178563
-
182361231473
-
19145581398
-
20272151173221
-
2271651818
-
222811561847
-
233702211929
-
244152061856
-
252431281743
-
2619378
-
272321511769
-
282891421706
-
292091541451
-
302491221847
-
313272581889
-
321711351162
-
3374271483
-
342041181863
-
35221130
The Wright Brothers
-
36178118
-
371661391856
-
3811542570
-
391451181596
-
402331471918
-
-
41118601475
-
422351581874
-
4312288742
-
44128113272
-
451371251870
-
462031531955
-
4760121756
-
482881712
added by: Polar Bear
-
4991745
-
50998118784
-
53121770
-
54904863
-
5566511724
-
56108911723
-
57103771796
-
58233686
added by: Polar Bear
-
5944161685
added by: EnriqueSanchez
-
602961759
added by: Polar Bear
-
613817
-
622971749
-
6365481694
-
64117991736
-
65215
Arminius
added by: Polar Bear
-
66233
new! Friedrich Nietzsche
1844 -
6773571882
-
6873661764
-
6982761469
-
701321421917
-
71216
Otto I the Great
added by: Polar Bear
-
72102921138
-
735229
-
742331813
added by: Polar Bear
-
752241797
added by: Polar Bear
-
7650201412
-
7765511874
-
782051880
added by: Polar Bear
-
79110911955
-
802061459
added by: Polar Bear
-
8154471027
-
8244131867
-
8332191672
-
8450391
-
8545301533
-
862961646
-
872491485
-
883527
-
8950511469
-
9039241599
-
915159
-
923271265
-
93223496
-
942615406
-
952241872
added by: Polar Bear
-
962231471
added by: Polar Bear
-
972015
-
9842361871
-
994244
-
10062741925
-
1012241594
added by: Polar Bear
-
1023271571
-
10322221429
added by: ذوالليندزكس
“ The Sultan of the Ottoman Empire from 1451-1481. Conquered Constantinople, or Istanbul. Ruling … more -
1042752400
-
105224
new! Fridtjof Nansen
1861added by: Polar Bear
-
1062291480
added by: Polar Bear
-
1074342576
-
10898921935
-
10957691889
-
11052591893
-
1112171707
-
1122721
-
11325211225
-
1142261728
added by: Polar Bear
-
11540411835
-
11642461712
-
1171531500
added by: Polar Bear
-
11839491711
-
119203325
-
120224
Arthur Schopenhauer
-
12117341912
-
122192287
added by: acalabr
-
12363751911
-
12437511913
-
12537391914
-
12652611881
-
12742581931
-
12814151833
added by: sebbzor
-
12945701961
-
1302981853
-
1312051606
-
13263921940
-
13327541820
-
13413181751
-
135981735
-
1361151822
-
13730561921
-
1382041274
added by: Polar Bear
-
13923441854
-
140812
-
-
14114251343
-
142155
-
14318390
-
1444229
-
145192484
-
14621341491
-
1471545259
-
14840551920
-
14923471130
-
15019151638
-
15125491918
-
152341890
added by: BruceFaitsch
-
1532131670
added by: Polar Bear
-
15437661946
-
15527551926
-
1561931864
added by: Polar Bear
-
15726581923
-
15823401805
-
15923511371
-
160167460
-
1612351270
added by: Coolza
-
162203
Rurik
830added by: Polar Bear
-
163144454
added by: Polar Bear
-
1641631899
added by: Polar Bear
-
165195495
added by: Polar Bear
-
1661741527
-
16713401916
-
16818331884
-
1691861812
-
170103
George Orwell
-
171961810
-
17212381919
added by: alex.mietchen
-
17318491035
-
174321304
added by: kilgore_trout
“ 14th Century Moroccan Explorer „ -
-
Secret Photos and Inside Viewws of the Scientology Headquarters “Gold Base”
The international headquarters of Church of Scientology, also called the Gold Base or Int Base,1 is located on a 500-acre parcel of land in San Jacinto in Riverside County, California. The Church of Scientology purchased the site, a former resort used by celebrities, in 1978. Many of Scientology’s organizations are headquartered there, including the Religious Technology Center, the Commodore’s Messenger Organization International and Golden Era Productions. Golden Era Productions manufactures the E-Meter and produces and distributes all church audio-visual materials, both internal and promotional. The motif of the facility is designed to look like a Scottish castle, perhaps as a reference to one of Hubbard’s largest ideological inspirations Aleister Crowley. Like Mr. Crowley’s Boleskine House, which is located near Loch Ness, Scotland, Mr. Hubbard also refers to his house in a singular epithet “Bonnie View”. 2 The two facilities also share architectural similarities and the Boleskine House is considered to be of great importance in Thelema, Crowley’s own psuedo-religious magical organization.
Scientology has a long, sometimes stormy history in the Inland area, dating to the 1960s, when the first mission opened in Grand Terrace. In 1974, the church opened a mission — then the largest worldwide — near University Avenue and Lime Street in Riverside, in what is now the Life Arts Center.
But Scientology’s largest presence here is the Gold Base — home to Golden Era Productions, where all the church’s training videos, books and audiotapes are made.
The compound is nestled against rolling green hills and bisected by winding, two-lane Gilman Springs Road. The movie studio is designed after a Scottish castle, with conical turrets and a sky-blue tiled roof.
Each of the three dozen buildings in the complex shares the motif. Flagstones line bright white exterior walls and gates are made of rough-hewn oak on wrought-iron hinges.
Fraser joked that people stop “about 50 times a day” just to ask what the place is.
The church bought the site, formerly a resort popular among Hollywood moguls, in 1978.
Golden Era’s high-tech studios produce 300 different videos, films and audiotapes a year for distribution worldwide, along with books, television commercials and E-Meters — the electronic devices used for personal counseling, an underlying feature of Scientology.
About 500 staff members live and work at the base, and another 100 or so non-Scientologists are employed there.
Photographs of Hubbard are everywhere, and several corridors are lined with signed photos of celebrity Scientologists, including John Travolta and Isaac Hayes.
Fraser said the site has hosted more than 100 fundraisers for local charities. She serves on the board of a youth museum, and another staff member is on the Hemet Public Library board and helped with a plan for San Jacinto’s Main Street.
Fraser gives free tours of Golden Era and has hosted Riverside County leaders. 3
Notable buildings and features in Gold Base include:4
Upper Villas—RTC offices and housing, where David Miscavige and other high level Scientologists live and work
BonnieView—L. Ron Hubbard’s fully-furnished mansion, still maintained and staffed in the belief that he will return in another body.
Cine Castle—main film studio in the shape of a castle, for producing church A/V materials
OGH buildings—Old Gilman House. Formerly “isolation” space for physically ill staff. Possibly now used for auditing or solo auditing.
Del Sol—CSI offices, and auditing rooms for staff.
Staff berthing—four buildings where staff live.
Qual Gold—Headquarters for Qual Sec, in charge of “quality control” as per the Hubbard organization policies. In practice this mostly means facilities staff auditing and training.
MCI—This large building is the staff dining hall, known as “Massacre Canyon Inn” from the building’s pre-Scientology name when the property was a resort.
Unusually Strong Security Measures at Gold Base
Gold Base has a number of unusually strong security measures, including razor-tipped fences, motion sensors, snipers nests and a large number of regular and infrared CCTV cameras. However, it is unclear whether the purpose of many of these security measures is to protect the base from outside threats or to keep unruly members inside the compound. The outer fences are lined with razors and motion sensors at regular intervals of approximately 20 ft. The facility also has infrared cameras, anti-protester speaker systems as well as floodlights arranged at regular intervals. There are are also “lookout posts” that are akin to snipers’ nests in the sides of the hills surrounding the complex.

Razor-tipped fences at Gold Base point both inward and outward.

Motion sensors are positioned at regular intervals along the outer fences of Gold Base.

Infrared cameras are positioned around Gold Base.
Address
19625 Gilman Springs Road
Gilman Hot Springs, California 92583
Golden Era Golf Course
19871 Gilman Springs Road
San Jacinto, CA 92583-2105
(951) 654-0130
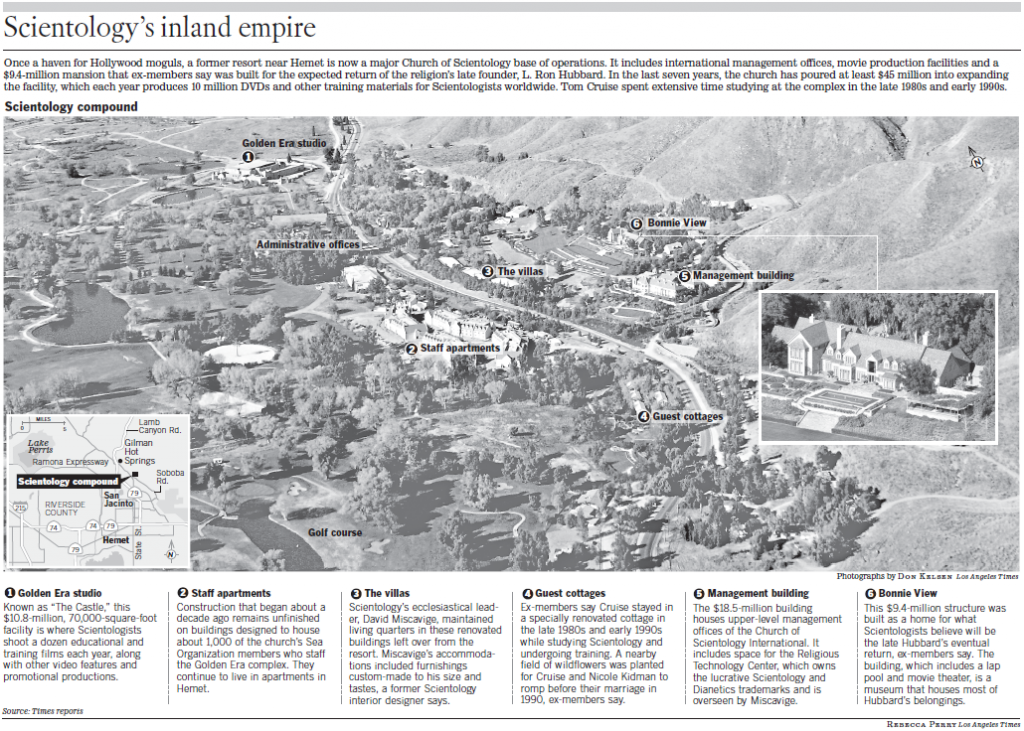
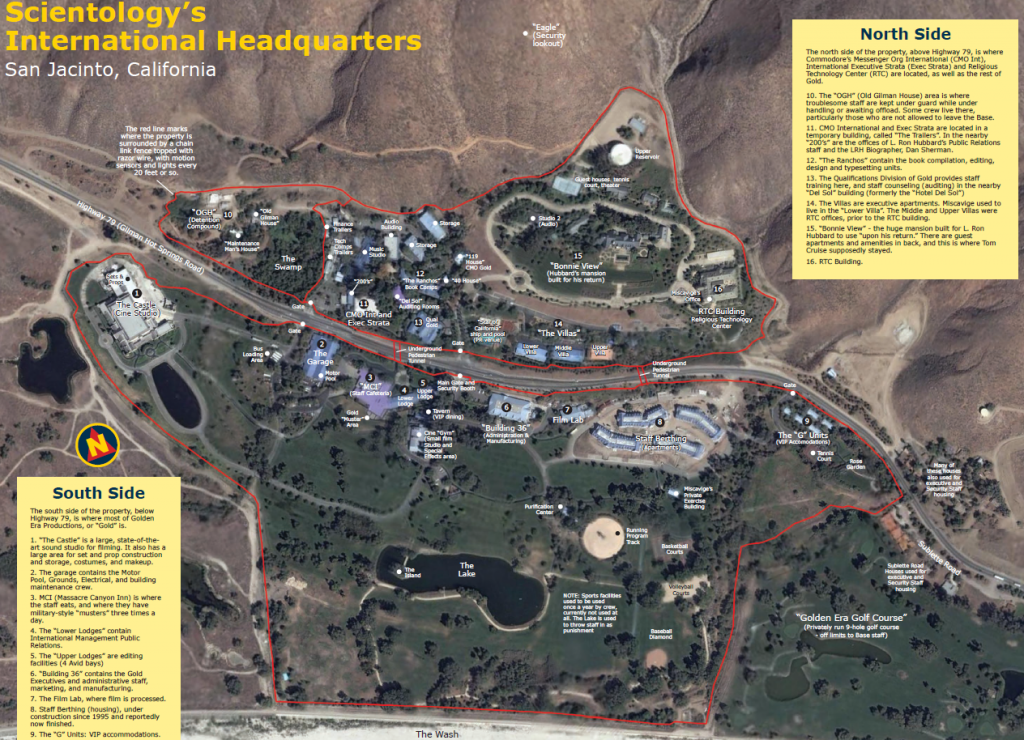

The large mansion at top right is L. Ron Hubbard’s former house “Bonnie View”.

Close up of L. Ron Hubbard’s former home. The Religious Technology Center Building is in the bottom right. David Miscavige’s office is located in the RTC building

Golden Era Productions and Golf Course. The building at right is “Building 36”. Building 36 contains the Gold Executives and administrative staff, marketing, and manufacturing.

Production studios for video and audio in upper portion of photo. Auditing rooms and “the Ranchos”, which are the book compilation, editing, design and typesetting units, are located to lower right. Flat-roofed building to the left is CMO International and Exec Strata are located in atemporary building, called “The Trailers”. In the nearby “200’s” are the offices of L. Ron Hubbard’s Public Relations staff and the LRH Biographer, Dan Sherman.

Cine Castle. “The Castle” is a large, state-of-the art sound studio for filming. It also has alarge area for set and prop construction and storage, costumes, and makeup.

Garage and motor pool at top. Massacre Canyon Inn is at lower right, where the staff eats, and where they have military-style “musters” three times a day.

The Running Program Track is used for punishment. The Rehabilitation Project Force uses the track to force offending members of the Sea Org to run consistently in circles, without stopping, for up to 12 hours at a time.
TOP-SECRET-Committee on National Security Systems Recommendations for Implementing FICAM on U.S. Secret Networks
Download the original document below
Threats to Federal information systems are rising as demands for sharing of information and intelligence between Federal Departments and Agencies increase. It is essential that the Federal Government devise an approach that addresses both challenges without compromising the ability to achieve either objective. Developing a common governance framework and set of Identity, Credential, and Access Management (ICAM) capabilities that enhance the security of our systems by ensuring that only authorized persons and systems from different Federal components have access to necessary information is a high priority. The Federal Identity, Credential and Access Management (FICAM) Roadmap and Implementation Guidance was developed to address the need for secure information sharing capabilities across the breadth of the Federal Government.
A recent gap analysis conducted to determine gaps between the current state of the Secret Fabric and FICAM revealed substantive differences between levels of adoption of this framework and served as the catalyst for this document. In addition to varying levels of FICAM maturity, the gap analysis also showed significant variations in levels of sharable information, connectivity, and governance structures which further complicate the aim of a common FICAM framework across the Secret Fabric.
Using the gap analysis as a starting point, this document provides four major recommendations:
Establish and Empower a Governance Structure for ICAM on All Networks
Develop a Common Interoperable ICAM Architecture for the Secret Fabric
Transition to a Common Interoperable ICAM Architecture
Prepare for the Evolution of ICAM on the Secret Fabric as New Technology Emerges and New Mission and Business Needs Arise
The following progress chart summarizes the recommendations with objective end states and suggested activities required to accomplish the objectives along a snapshot of status of ICAM on the Secret Fabric as of the publication date of this document. These recommendations, objectives and activities will be included in the FICAM Implementation Plan for the Secret Fabric currently under development by the National Security Systems (NSS) Identity and Access Management (IdAM) Working Group under the guidance of the Program Manager for the Information Sharing Environment (PM-ISE).
…
SECRET – Senate Permanent Subcommittee on Investigations Apple Offshore Profit Shifting Exhibits
The following exhibits were released May 21, 2013 by the Senate Permanent Subcommittee on Investigations Homeland Security and Governmental Affairs Committee.
U.S. Senate Permanent Subcommittee on Investigations Committee on Homeland Security and Governmental Affairs
- 142 pages
- May 21, 2013
- 4.4 MB
On May 21, 2013, the Permanent Subcommittee on Investigations (PSI) of the U.S. Senate Homeland Security and Government Affairs Committee will hold a hearing that is a continuation of a series of reviews conducted by the Subcommittee on how individual and corporate taxpayers are shifting billions of dollars offshore to avoid U.S. taxes. The hearing will examine how Apple Inc., a U.S. multinational corporation, has used a variety of offshore structures, arrangements, and transactions to shift billions of dollars in profits away from the United States and into Ireland, where Apple has negotiated a special corporate tax rate of less than two percent. One of Apple’s more unusual tactics has been to establish and direct substantial funds to offshore entities in Ireland, while claiming they are not tax residents of any jurisdiction. For example, Apple Inc. established an offshore subsidiary, Apple Operations International, which from 2009 to 2012 reported net income of $30 billion, but declined to declare any tax residence, filed no corporate income tax return, and paid no corporate income taxes to any national government for five years. A second Irish affiliate, Apple Sales International, received $74 billion in sales income over four years, but due in part to its alleged status as a non-tax resident, paid taxes on only a tiny fraction of that income.
In addition, the hearing will examine how Apple Inc. transferred the economic rights to its intellectual property through a cost sharing agreement with its own offshore affiliates, and was thereby able to shift tens of billions of dollars offshore to a low tax jurisdiction and avoid U.S. tax. Apple Inc. then utilized U.S. tax loopholes, including the so-called “check-the-box” rules, to avoid U.S. taxes on $44 billion in taxable offshore income over the past four years, or about $10 billion in tax avoidance per year. The hearing will also examine some of the weaknesses and loopholes in certain U.S. tax code provisions, including transfer pricing, Subpart F, and related regulations, that enable multinational corporations to avoid U.S. taxes.
A. Subcommittee Investigation
For a number of years, the Subcommittee has reviewed how U.S. citizens and multinational corporations have exploited and, at times, abused or violated U.S. tax statutes, regulations and accounting rules to shift profits and valuable assets offshore to avoid U.S. taxes. The Subcommittee inquiries have resulted in a series of hearings and reports. The Subcommittee’s recent reviews have focused on how multinational corporations have employed various complex structures and transactions to exploit taxloopholes to shift large portions of their profits offshore and dodge U.S. taxes.
At the same time as the U.S. federal debt has continued to grow – now surpassing $16 trillion – the U.S. corporate tax base has continued to decline, placing a greater burden on individual taxpayers and future generations. According to a report prepared for Congress: “At its post-WWII peak in 1952, the corporate tax generated 32.1% of all federal tax revenue. In that same year the individual tax accounted for 42.2% of federal revenue, and the payroll tax accounted for 9.7% of revenue. Today, the corporate tax accounts for 8.9% of federal tax revenue, whereas the individual and payroll taxes generate 41.5% and 40.0%, respectively, of federal revenue.”
Over the past several years, the amount of permanently reinvested foreign earnings reported by U.S. multinationals on their financial statements has increased dramatically. One study has calculated that undistributed foreign earnings for companies in the S&P 500 have increased by more than 400%. According to recent analysis by Audit Analytics, over a five year period from 2008 to 2012, total untaxed indefinitely reinvested earnings reported in 10-K filings for firms comprising the Russell 3000 increased by 70.3%. During the same period, the number of firms reporting indefinitely reinvested earnings increased by 11.4%.
The increase in multinational corporate claims regarding permanently reinvested foreign earnings and the decline in corporate tax revenue are due in part to the shifting of mobile income offshore into tax havens. A number of studies show that multinational corporations are moving “mobile” income out of the United States into low or no tax jurisdictions, including tax havens such as Ireland, Bermuda, and the Cayman Islands. In one 2012 study, a leading expert in the Office of Tax Analysis of the U.S. Department of Treasury found that foreign profit margins, not foreign sales, are the cause for significant increases in profits abroad. He wrote:
“The foreign share of the worldwide income of U.S. multinational corporations (MNCs) has risen sharply in recent years. Data from a panel of 754 large MNCs indicate that the MNC foreign income share increased by 14 percentage points from 1996 to 2004. The differential between a company’s U.S. and foreign effective tax rates exerts a significant effect on the share of its income abroad, largely through changes in foreign and domestic profit margins rather than a shift in sales. U.S.-foreign tax differentials are estimated to have raised the foreign share of MNC worldwide income by about 12 percentage points by 2004. Lower foreign effective tax rates had no significant effect on a company’s domestic sales or on the growth of its worldwide pre-tax profits. Lower taxes on foreign income do not seem to promote ‘competitiveness.’”
One study showed that foreign profits of controlled foreign corporations (CFCs) of U.S. multinationals significantly outpace the total GDP of some tax havens.” For example, profits of CFCs in Bermuda were 645% and in the Cayman Islands were 546% as a percentage of GDP, respectively. In a recent research report, JPMorgan expressed the opinion that the transfer pricing of intellectual property “explains some of the phenomenon as to why the balances of foreign cash and foreign earnings at multinational companies continue to grow at such impressive rates.”
…
C. Transfer Pricing and the Use of Shell Corporations
The Subcommittee’s investigations, as well as government and academic studies, have shown that U.S. multinationals use transfer pricing to move the economic rights of intangible assets to CFCs in tax havens or low tax jurisdictions, while they attribute expenses to their U.S. operations, lowering their taxable income at home. Their ability to artificially shift income to a tax haven provides multinationals with an unfair advantage over U.S. domestic corporations; it amounts to a subsidy for those multinationals. The recipient CFC in many cases is a shell entity that is created for the purpose of holding the rights. Shell companies are legal entities without any substantive existence – they have no employees, no physical presence, and produce no goods or services. Such shell companies are “ubiquitous in U.S international tax planning.” Typically, multinationals set up a shell corporation to enable it to artificially shift income to shell subsidiaries in low tax or tax haven jurisdictions.
According to a 2008 GAO study, “eighty-three of the 100 largest publicly traded U.S. corporations in terms of revenue reported having subsidiaries in jurisdictions list as tax havens or financial privacy jurisdictions….” Many of the largest U.S. multinationals use shell corporations to hold the economic rights to intellectual property and the profits generated from those rights in tax haven jurisdictions to avoid U.S. taxation. By doing this, multinational companies are shifting taxable U.S. income on paper to affiliated offshore shells. These strategies are causing the United States to lose billions of tax dollars annually. Moreover, from a broader prospective, multinationals are able to benefit from the tax rules which assume that different entities of a multinational, including shell corporations, act independently from one another. The reality today is that the entities of a parent multinational typically operate as one global enterprise following a global business plan directed by the U.S. parent. If that reality were recognized, rather than viewing the various affiliated entities as independent companies, they would not be able to benefit from creating fictitious entities in tax havens and shifting income to those entities. In fact, when Congress enacted Subpart F, discussed in detail below, more than fifty years ago in 1962, an express purpose of that law was to stop the deflection of multinational income to tax havens, an activity which is so prevalent today.
…
SECRET – Joint and Coalition Operational Analysis (JCOA)
Reducing and Mitigating Civilian Casualties: Enduring Lessons
17 pages
April 12, 2013
Download
The United States has long been committed to upholding the Law of Armed Conflict (LOAC) and minimizing collateral damage, which includes civilian casualties (CIVCAS) and unintended damage to civilian objects (facilities, equipment, or other property that is not a military objective). In support of these goals, the U.S. military developed capabilities for precision engagements and accurately identifying targets, such as the development of refined targeting processes and predictive tools to better estimate and minimize collateral damage. These capabilities permitted the conduct of combat operations with lower relative numbers of civilian casualties compared to past operations. However, despite these efforts, and while maintaining compliance with the laws of war, the U.S. military found over the past decade that these measures were not always sufficient for meeting the goal of minimizing civilian casualties when possible. Resulting civilian casualties ran counter to U.S. desires and public statements that the United States did “everything possible” to avoid civilian casualties, and therefore caused negative second-order effects that impacted U.S. national, strategic, and operational interests.
Afghanistan (2001-2002)
The United States reaffirmed its commitment to minimizing harm to the peaceful civilian population when it commenced major combat operations in Afghanistan and Iraq in 2001 and 2003, respectively. On 7 October 2001, U.S. forces began combat operations to capture Al Qaeda leadership and eliminate the use of Afghanistan as a launching point for terrorism. Within days of the start of operations, international media began reporting incidents of civilian casualties. Many of these incidents involved villages where suspected enemy were located, highlighting the challenge posed by fighting an enemy that eschews its obligations under the law of war (e.g., not wearing a uniform and hiding among the population). As a result, obtaining positive identification (PID) was more problematic, and U.S. engagements tended to rely more on self-defense considerations based on perceived hostile acts or intent. Probably the two highest profile incidents during this time were the 21 December 2001 attack on a convoy that the Afghan government claimed included tribal leaders; and the 1 July 2002 AC-130 attack on a group in Deh Rawud, central Afghanistan, that turned out to be a wedding party. In both attacks, U.S. aircraft had observed ground fire and engaged because of self-defense considerations.
Iraq Major Combat Operations (2003)
During major combat operations in Iraq, the ability to distinguish the enemy from the civilian population was simplified by the fact that the enemy was the Iraqi military. Iraqi forces were generally located away from civilian areas; their military equipment and uniforms reduced the ambiguity of engagement decisions relative to those faced by U.S. forces in Afghanistan. However, the Iraq military purposely violated law of war rules designed to protect the peaceful civilian population by employing human shields, misusing protected symbols for impartial humanitarian organizations (e.g., Red Crescent), and placing equipment in protected sites. In addition, Fedayeen Saddam forces did not wear uniforms and fought using irregular tactics, contributing to U.S. challenges in obtaining positive identification.
In contrast, the United States and its allies went to great lengths to minimize collateral damage; for example, in Iraq, similar to Afghanistan, most air engagements used precision-guided munitions. While no Department of Defense (DOD) assessment of civilian casualties during Iraq major combat operations could be found by this author, an independent assessment judged U.S. pre-planned attacks to be relatively effective in minimizing civilian casualties. The main concerns over civilian casualties centered on coalition forces conducting time-sensitive targeting of leadership in urban areas.
Counterinsurgencies in Iraq and Afghanistan
As insurgencies developed in Iraq and Afghanistan, the United States was forced to adopt a counterinsurgency (COIN) approach for which it was largely unprepared. With civilian protection being a central feature of COIN, the reduction and mitigation of CIVCAS became a key issue in these operations.
Counterinsurgency in Iraq
In Iraq, noncombatant casualties were primarily caused by escalation of force (EOF) incidents, both at check points and during convoy operations. These incidents resulted in a significant outcry from nongovernmental organizations (NGOs) and the media; the shooting of a vehicle containing Italian journalist Giuliana Sgrena and her rescuers during an EOF incident further increased visibility of this issue. In mid-2005, U.S. forces in Iraq adapted and made heightened efforts, widely seen as successful, to prevent and mitigate the effects of civilian casualties. Still, this issue was not completely resolved: later in the conflict, Multinational Forces – Iraq (MNF-I) pointed to the strategic importance of reducing CIVCAS from EOF and cited the lack of available nonlethal capabilities and inadequate training in their use as key deficiencies.
Counterinsurgency in Afghanistan
In Afghanistan, President Karzai made his first public statements regarding CIVCAS in 2005, asking the International Security Assistance Force (ISAF) to take measures to reduce such casualties. Initial initiatives to reduce CIVCAS in Afghanistan, such as the “Karzai 12” rules for approving operations in 2005 and the initial Commander, ISAF (COMISAF) Tactical Directive in 2007, were not successful in reducing high profile incidents. Additional efforts, including redrafting the COMISAF Tactical Directive in 2008, were made in response to several high profile, high casualty CIVCAS incidents; however, a May 2009 incident in Bala Balouk highlighted the lack of progress in effectively addressing the issue of civilian casualties.
The Bala Balouk incident served as an impetus for major efforts to reduce CIVCAS by both ISAF and the United States. Since mid-2009, ISAF leadership clearly and consistently emphasized the importance of reducing CIVCAS, and ISAF modified its policies and procedures to that end. Similarly, concerted efforts on the part of the United States—spearheaded by the U.S. Joint Staff CIVCAS Working Group, currently led by a three-star general officer—aided efforts to improve U.S. pre-deployment training to better prepare U.S. forces for CIVCAS reduction and mitigation in Afghanistan. This renewed focus addressed deficiencies in pre-deployment training regarding the use of nonlethal weapons (NLWs), amongst many other efforts. Collectively, these dedicated efforts bore fruit: because of improved guidance and training, ISAF forces adapted the way they conducted operations in light of CIVCAS concerns, and ISAF-caused CIVCAS decreased over time. Importantly, analysis of available data suggested that these CIVCAS mitigation efforts were a win-win, with no apparent cost to mission effectiveness or increase in friendly force casualties.
CIVCAS: An Enduring Issue
While the progress in Afghanistan is good news, to date the changes put into place have remained largely focused on supporting operations there. Sharing lessons between operations and institutionalization of those lessons are less apparent. For example, existing lessons from Iraq regarding EOF did not appear to migrate to Afghanistan, and lessons from Afghanistan regarding air-to-ground operations did not reach North Atlantic Treaty Organization (NATO) participants in Libya during Operation UNIFIED PROTECTOR (OUP). Further, a CIVCAS incident where a U.S. Navy ship engaged a small boat in the Persian Gulf and incidents regarding U.S. operations in Yemen and Pakistan (as reported in the international media) also suggest that the applicability of lessons regarding ways to minimize civilian casualties and mitigate their impact are not limited to Afghanistan. Former COMISAF, General David Petraeus, echoed this point, describing the enduring nature of the challenge of CIVCAS: “Avoiding civilian casualties is a central operational challenge in Afghanistan and Iraq and it will be a challenge in any future conflict as well.” Lessons learned in the past decade should therefore be looked at with an eye toward their application in future conflicts, as well as their continued importance to current operations in Afghanistan and elsewhere.
This paper identifies key CIVCAS lessons that are applicable to future operations conducted by the United States and its allies. These lessons were drawn from four years of analytic effort focused on understanding and effectively responding to the challenge of CIVCAS in Afghanistan, Iraq, and elsewhere. These lessons are not limited to COIN operations; rather, they apply to a wide range of potential combat activities, including major combat operations (in light of the political impact of CIVCAS during 1991 and 2003 Iraq wars), airpower-focused operations such as OUP in Libya, and counterterrorism operations such as the U.S. is currently conducting in Pakistan. Since each of these cases included an enemy that did not appropriately distinguish itself from the peaceful civilian population, these lessons should be particularly applicable in other, similar situations.
SECRECY NEWS – SUBPOENA OF AP PHONE RECORDS SAID TO DAMAGE PRESS FREEDOM
|
SECRECY NEWS – SENATE CONFIRMS CHAIR OF PRIVACY & CIVIL LIBERTIES BOARD
Almost a year and a half after he was nominated by President Obama in December 2011, the Senate yesterday confirmed David Medine to be the chairman of the Privacy and Civil Liberties Oversight Board by a vote of 53-45. http://www.fas.org/irp/congress/2013_cr/medine.html Republicans, led by Sen. Charles Grassley, opposed the nominee and voted against him. “I was disappointed that he failed to answer a basic yes-or-no question about national security law: ‘Do you believe that we are engaged in a war on terrorism?’,” Sen. Grassley said. “Instead of a simple yes or no, he opted for a more limited answer that military power is permissible in appropriate cases.” Democrats, led by Sen. Patrick Leahy, praised Mr. Medine and the Board that he will now lead. “The confirmation of this nominee is a significant victory for all Americans who care about safeguarding our privacy rights and civil liberties,” Sen. Leahy said. “The Privacy and Civil Liberties Oversight Board is a guardian of Americans’ privacy rights and civil liberties as well as an essential part of our national security strategy,” he said. But this seems like an overstatement. The size of the five-member Board and the resources available to it are not commensurate with the responsibilities it has nominally been assigned. It cannot possibly perform comprehensive oversight of the broad range of privacy or civil liberties concerns that arise in the national security domain. Expectations to the contrary are bound to be disappointed. At best, the Board may serve as a boutique oversight shop that tackles a couple of discrete policy issues each year. For background on the origins and development of the Board, see Privacy and Civil Liberties Oversight Board: New Independent Agency Status, Congressional Research Service, August 27, 2012: http://www.fas.org/sgp/crs/misc/RL34385.pdf INTERNATIONAL INTELLIGENCE AGREEMENTS, AND OTHER DOD DIRECTIVES The procedures by which the U.S. Air Force establishes international agreements for the exchange of intelligence information with foreign military services were described in a new Air Force Instruction. “Foreign military organizations being considered for inclusion in an IIA (international intelligence agreement) must clearly support U.S. security and foreign policy objectives. The foreign government must have favorable relations with the United States; a well-developed, secure intelligence service; and a stable domestic environment and military unity. Known national characteristics of the foreign government in question must fall within the guidelines of the United States national disclosure and security policy, and be reasonably expected to have adequate fiscal means, and conform to legal guidelines,” the Instruction states. Such agreements must “Provide for mutual support (quid pro quo)” and must “Provide intelligence that would otherwise be denied to the United States.” See Air Force Instruction 14-102, International Intelligence Agreements, April 29, 2013: http://www.fas.org/irp/doddir/usaf/afi14-102.pdf Another new Department of Defense Instruction governs records management within the Office of the Secretary of Defense. “It is DoD policy,” it states, “to limit the creation of records to those essential for the efficient conduct of official business and to preserve those of continuing value while systematically eliminating all others.” See OSD Records and Information Management Program, Administrative Instruction 15, May 3, 2013: http://www.fas.org/irp/doddir/dod/ai15.pdf Other noteworthy new military publications include the following. Information Operations (IO), DoD Directive 3600.01, May 2, 2013: http://www.fas.org/irp/doddir/dod/d3600_01.pdf DODD 5134.10 Defense Advanced Research Projects Agency (DARPA), DoD Directive 5134.10, May 7, 2013: http://www.fas.org/irp/doddir/dod/d5134_10.pdf THE U.S. SCIENCE AND ENGINEERING WORKFORCE, AND MORE FROM CRS New and updated reports from the Congressional Research Service that Congress has not made available to the public include the following. The U.S. Science and Engineering Workforce: Recent, Current, and Projected Employment, Wages, and Unemployment, May 6, 2013: http://www.fas.org/sgp/crs/misc/R43061.pdf Securing U.S. Diplomatic Facilities and Personnel Abroad: Background and Policy Issues, May 7, 2013: http://www.fas.org/sgp/crs/row/R42834.pdf Tax Reform in the 113th Congress: An Overview of Proposals, May 6, 2013: http://www.fas.org/sgp/crs/misc/R43060.pdf Border Security: Immigration Enforcement Between Ports of Entry, May 3, 2013: http://www.fas.org/sgp/crs/homesec/R42138.pdf Terrorist Watch List Screening and Background Checks for Firearms, May 1, 2013: http://www.fas.org/sgp/crs/terror/R42336.pdf Missing Adults: Background, Federal Programs, and Issues for Congress, May 7, 2013: http://www.fas.org/sgp/crs/misc/RL34616.pdf Kosovo: Current Issues and U.S. Policy, May 7, 2013: http://www.fas.org/sgp/crs/row/RS21721.pdf Central America Regional Security Initiative: Background and Policy Issues for Congress, May 7, 2013: http://www.fas.org/sgp/crs/row/R41731.pdf Expulsion, Censure, Reprimand, and Fine: Legislative Discipline in the House of Representatives, May 2, 2013: http://www.fas.org/sgp/crs/misc/RL31382.pdf No-Fly Zones: Strategic, Operational, and Legal Considerations for Congress, May 3, 2013: http://www.fas.org/sgp/crs/natsec/R41701.pdf Instances of Use of United States Armed Forces Abroad, 1798-2013, May 3, 2013: http://www.fas.org/sgp/crs/natsec/R42738.pdf _______________________________________________ Secrecy News is written by Steven Aftergood and published by the Federation of American Scientists. The Secrecy News Blog is at: http://www.fas.org/blog/secrecy/ To SUBSCRIBE to Secrecy News, go to: http://blogs.fas.org/secrecy/subscribe/ To UNSUBSCRIBE, go to http://blogs.fas.org/secrecy/unsubscribe/ OR email your request to saftergood@fas.org Secrecy News is archived at: http://www.fas.org/sgp/news/secrecy/index.html Support the FAS Project on Government Secrecy with a donation: https://members.fas.org/donate _______________________ Steven Aftergood Project on Government Secrecy Federation of American Scientists web: http://www.fas.org/sgp/index.html email: saftergood@fas.org voice: (202) 454-4691
Trotz Internet-Attacken der “GoMoPa”:Wer wirklich und tatsächlich Geld erhielt: “GoMoPa” und Genossen !
Alle Internettacken der mutmasslichen STASI-Typen der “GoMoPa” können die Wahrheit nicht stoppen.
Klar ist, nicht ich, sondern “GoMoPa” erhielt Geld von S&K.
Nicht ich, sondern “Dr. Rainer Zitelmann” wurde bei Springer als Immobilienredakteur entfernt, nachdem sich der Verlag mit seinen Schriften zu Adolf Hitler und Auschwitz auseinandergesetzt hat.
Ich habe nie bei Axel Springer gearbeitet. Dies kann jeder bei Springer nachprüfen.
Nicht ich, sondern “GoMoPa” und “Dr. Rainer Zitelmann” haben Beraterverträge mit deutschen Immobilienfirmen.
Die Latrinenparolen sollen doch nur von den tatsächlichem Korruptionsnetzwerk und den alten Genossen und deren Seilschaften ablenken,
wie dies bereits oft versucht wurde.
Und dann wenn alles nichts hilft, werden unseren Seiten gehackt und mit DDoS-Hacker-Attacken angegriffen…
Das leuchtet doch jedem ein ! Hilflose Versuche der korrupten Seilschaften von “GoMoPa” und Genossen.
Und ganz sicher ist auch: Ich bin kein Fähnchen im Wind !
Hier noch einmal meine detaillierte Stellungnahme.
Liebe Leser,
wieder einmal versucht die dubiose “GoMoPa” und deren Handlanger, Konsorten und Komparsen mutmasslich “Peter Ehlers” und “Nawito” von mutmasslich eigenen Taten abzulenken und mir perfide den “Schwarzen Peter” zuzuschieben.
Wie bereits im Falle meines angeblichen falschen Magistertitels, dem Fall Meridian Capital etc pp die Liste ist endlos.
Ein Sammelsurium von Kolportagen, Fabeln, Märchen und Latrinenpatrolen…
Dabei liegen die Beweis klar auf dem Tisch:
Die renommierten und etablierten Medien wie “ZEIT” und “Süddeutsche Zeitung” haben es aufgedeckt, was hier im Fall “S &K”/”GoMoPa” wirklich lief.
http://www.zeit.de/2013/11/Finanznachrichtendienst-Gomopa
http://www.sueddeutsche.de/geld/mutmassliche-anlagebetrueger-sk-die-akte-midas-1.1620191-4
Nachdem zahlreiche Internetangriffe nichts gebracht haben, nun wieder dieser Unsinn.
Hier noch einmal meine Stellungnahme zu der “GoMoPa”/Ehlers/Nawito-Absurdistan-Agit-Propaganda:
Dear Readers,
let me just briefly comment a mental cyberattack which should distract your attention from the real issues.
I have never had any consulting position or contract for any German company.
I have never worked for the Axel Springer Publishing House – not even as a freelance journalist.
These facts are clear and can be verified easily – just by calling Axel Springer.
The facts are
1) Dr. Rainer Zitelmann worked for the Axel Springer Company. You can esaily find out what happened there. I just mention the word “Auschwitz” in this context…As you see from his website and in the internet Zitelmann is in fact consulting many German companies.
2) “GoMoPa” had in fact a consultation contract with estavis and got in fact money from estavis and many various companies i.e. “S&K”
These contracts are known and 100% true and published by various media i.e. “ZEIT”, “MANAGER MAGAZIN”, “SUEDDEUTSCHE ZEITUNG” etc.
3) Meridian Capital was the subject of “GoMoPa”s articles.
4) “Nawito” whover or whatever it is did not even bother to contact us.
5) The “information” about one of our companies is false.
6) The “Nawito” informer “Peter Ehlers” did in fact attack Chancellor Merkel and the Minister of Finance Wolfgang Schäuble as “Deutschlands bekannteste Hehler” to name just one fact about “Peter Ehlers” or whatever his name might be who by the way got a lot of money from the bancrupt SAM AG which was also subject of “GoMoPa”‘s reporting and we know similiar cases of this endeavour.
7) The last editor who was attacked by such cyberattacks died in a very mysterious way, Heinz Gerlach. He might have been controversial but nevertheless – the truth is the truth.
He was the first journalist to publish the truth about the mysterious headquarter of “GoMoPa” in New York and their consulting contract with estavis and died suddenly and totally unexpected for most of us – not for all.
The circumstances of his death remain unsolved for me.
We are ready to proof this everytime and do not work with “colportations”.
Obviously cyberattacks on our websites since years are not enough to keep the truth down – defamation must be added – a wellknown STASI technique to irritate the public – MENTAL AND PYSICAL CYBERATTACKS done by the well-know suspects.
Sincerely your
Bernd Pulch
Magister Artium der Publizistik, Germanistik und Komparatistik
PS
COPIES OF PHYSICAL CYBER ATTACKS ON OUR SERVERS BY THE SUSPECTS AND “INFORMERS” OF “NAWITO”
The attacked website are for example:
http://www.investment-magazin.tv
and about 20 more.
Revealed – CipherCloud DMCA Takedown
SECRECY NEWS – FISA SURVEILLANCE APPLICATIONS ROSE SLIGHTLY IN 2012
“During calendar year 2012, the Government made 1,856 applications to the
Foreign Intelligence Surveillance Court for authority to conduct electronic
surveillance and/or physical searches for foreign intelligence purposes.”
That somewhat opaque statistic was disclosed in the Justice Department’s
latest annual report to Congress on the Foreign Intelligence Surveillance
Act, filed on Tuesday. As is usually the case, none of the requests for
electronic surveillance were denied by the Court.
No matter how it is sliced and diced, the newly disclosed number of
applications does not yield much substance. It means that the government
submitted an average of 5 requests per day last year for intelligence
surveillance or physical search. It is about 5% higher than the number of
applications the year before (1,745), but quite a bit lower than the figure
from 2007 (2,371).
The number of applications does not correspond directly to the number of
targets, since multiple applications may be submitted in the course of an
individual investigation. Nor is the outcome of the surveillance or search
activity indicated in a way that would tend to validate or invalidate the
authorization after the fact.
In any case, the FIS Court did not deny any of the government’s requests
for authority to conduct electronic surveillance in whole or in part, the
report said, although unspecified modifications were made to 40 proposed
orders. The report does not say whether or not any requests for physical
search were disapproved or modified.
The government also made 212 applications for access to business records
and “tangible things” for foreign intelligence purposes, almost the same as
the 205 the year before.
And also in 2012, the FBI submitted 15,229 National Security Letter
requests for information concerning 6,223 different U.S. persons
(“excluding requests for subscriber information only”), down somewhat from
the 16,511 requests (concerning 7,201 different persons) the year before.
As an instrument of public oversight, the annual reports on FISA are only
minimally informative. They register gross levels of activity, but they
provide no measures of quality, performance or significance. Neither
counterintelligence successes nor failures can be discerned from the
reports. Nor can one conclude from the data presented that the FISA
process is functioning as intended, or that it needs to be curbed or
refined.
Congressional leaders blocked efforts to impose new or stronger public
reporting requirements when the FISA Amendments Act was reauthorized late
last year. However, Sen. Jeff Merkley and several Senate colleagues asked
the FIS Court to summarize its opinions in such a way as to facilitate
their eventual declassification and disclosure. This request has produced
no known results to date.
The FISA itself is a product of a rich period of political ferment in the
1970s when public and private institutions converged to promote increased
transparency, improved oversight and meaningful new constraints on
government authority. Investigative journalists wrote groundbreaking
stories, Congressional committees held historic hearings, political
activists and ordinary citizens mobilized to defend their interests,
leading to real and lasting changes. On the legislative front, these
included passage of an invigorated Freedom of Information Act, along with
the Privacy Act, the Government in the Sunshine Act, and the FISA, which
subjected intelligence surveillance activities to at least a degree of
independent judicial review.
An interesting account of that momentous period can be found in the new
book “Reining in the State: Civil Society and Congress in the Vietnam and
Watergate Eras” by Katherine A. Scott, University Press of Kansas, March
2013.
http://amazon.com/Reining-State-Society-Congress-Watergate/dp/070061897X
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://blogs.fas.org/secrecy/subscribe/
To UNSUBSCRIBE, go to
http://blogs.fas.org/secrecy/unsubscribe/
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
https://members.fas.org/donate
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: http://www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
SECRECY NEWS – SEQUESTRATION SLOWS DOCUMENT DECLASSIFICATION
The process of declassifying national security records, which is hardly
expeditious under the best of circumstances, will become slower as a result
of the mandatory budget cuts known as sequestration.
Due to sequestration, “NARA has reduced funding dedicated to the
declassification of Presidential records,” the National Archives and
Records Administration (NARA) said in a report last week.
“Instead, NARA staff will prepare documents for declassification, in
addition to their existing duties. This will slow declassification
processes and delay other work, including FOIA responses and special access
requests,” said the new report, which also identified several other adverse
effects of the across-the-board cuts.
Meanwhile, because of the basic asymmetry between classification and
declassification, there is no particular reason to expect a corresponding
reduction in the rate at which new records are classified.
Classification is an integral part of the production of new national
security information that cannot be deferred, while declassification is a
distinct process that can easily be put on hold. Likewise, there is no
dedicated budget for “classification” to cut in the way that NARA has cut
declassification spending. And while Congress has erected barriers to
declassification (such as the Kyl-Lott Amendment to prohibit automatic
declassification of records without review), it has simultaneously allowed
declassification requirements to go overlooked and unenforced.
Some declassification is actually mandated by law. A 1991 statute on the
Foreign Relations of the United States series requires the Department of
State to publish a “thorough, accurate, and reliable documentary record of
major United States foreign policy decisions” no later than 30 years after
the fact, necessitating the timely declassification of the underlying
records. But law or no law, the government has not complied with this
publication schedule.
EGYPT AND THE IMF, AND MORE FROM CRS
A new report from the Congressional Research Service assesses the economic
state of post-revolution Egypt and finds it fairly grim.
“After more than two years of social unrest and economic stagnation
following the 2011 popular uprising, the government of Egypt is facing
serious economic pressures that, if not remedied, could lead to economic
collapse and possibly new levels of violence,” the report says.
“Egyptian authorities and the International Monetary Fund (IMF) have been
in negotiations for more than two years over an IMF loan to Egypt in
exchange for policy reforms that, if successful, could stave off economic
collapse and create more ‘inclusive’ growth…. [but] No agreement has been
finalized or implemented to date. Egyptian authorities have been reluctant
to commit to economic reforms that may be politically unpopular and
increase the country’s debt.”
Background on the negotiations and on U.S. aid to Egypt are presented in
Egypt and the IMF: Overview and Issues for Congress, April 29, 2013:
Some other CRS reports on Middle Eastern countries that have been recently
updated include the following.
Iraq: Politics, Governance, and Human Rights, April 26, 2013:
Iran Sanctions, April 24, 2013:
U.S. Foreign Aid to Israel, April 11, 2013:
Iran: U.S. Concerns and Policy Responses, April 4, 2013:
Jordan: Background and U.S. Relations, April 1, 2013:
INTERNATIONAL INVESTMENT AGREEMENTS, AND MORE FROM CRS
The international agreements that constitute the infrastructure of
international trade and investment are spotlighted in an informative new
report from the Congressional Research Service.
“In the absence of an overarching multilateral framework on investment,
bilateral investment treaties (BITs) and investment chapters in free trade
agreements (FTAs), collectively referred to as ‘international investment
agreements,’ have emerged as the primary mechanism for promoting a
rules-based system for international investment,” the new report explains.
“Presently, there are over 3,000 BITs globally. The United States has
concluded 47 BITs, 41 of which have entered into force.” These treaties
were tabulated by CRS and presented along with other little-known data on
the subject in U.S. International Investment Agreements: Issues for
Congress, April 29, 2013:
Other new or newly updated CRS reports obtained by Secrecy News include
the following.
Mountaintop Mining: Background on Current Controversies, April 29, 2013:
National Park System: Establishing New Units, April 25, 2013:
The Administrative Process by Which Groups May Be Acknowledged as Indian
Tribes by the Department of the Interior, April 26, 2013:
Social Security Disability Insurance (SSDI) Reform: An Overview of
Proposals to Reduce the Growth in SSDI Rolls, April 29, 2013:
Conventional Prompt Global Strike and Long-Range Ballistic Missiles:
Background and Issues, April 26, 2013:
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://blogs.fas.org/secrecy/subscribe/
To UNSUBSCRIBE, go to
http://blogs.fas.org/secrecy/unsubscribe/
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
https://members.fas.org/donate
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: http://www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Video – America’s Investigative Reports – Shooting the War
SECRECY NEWS – FBI TERRORISM INVESTIGATIONS, AND MORE FROM CRS
“Intelligence activity in the past decades has, all too often, exceeded
the restraints on the exercise of governmental power that are imposed by
our country’s Constitution, laws, and traditions,” according to the
Congressional Research Service.
The CRS, which shuns polemical claims, presents that assertion as a simple
statement of fact (although cautiously sourced to the 1976 Church Committee
report) in a newly updated report on FBI terrorism investigations.
The report reviews the FBI investigative process, the statutory framework
within which it operates, and the tools at its disposal, along with
oversight considerations for Congress. See The Federal Bureau of
Investigation and Terrorism Investigations, April 24, 2013:
Other new or newly updated CRS reports include the following.
Terrorism, Miranda, and Related Matters, April 24, 2013:
Terrorism Risk Insurance: Issue Analysis and Overview of Current Program,
April 26, 2013:
U.S. Air Force Bomber Sustainment and Modernization: Background and Issues
for Congress, April 23, 2013:
Multiyear Procurement (MYP) and Block Buy Contracting in Defense
Acquisition: Background and Issues for Congress, April 25, 2013:
U.S.-South Korea Relations, April 26, 2013:
Iran Sanctions, April 24, 2013:
Intelligence Issues for Congress, April 23, 2013:
Inflation-Indexing Elements in Federal Entitlement Programs, April 24,
2013:
Changes in the Arctic: Background and Issues for Congress, April 25, 2013:
Prevalence of Mental Illness in the United States: Data Sources and
Estimates, April 24, 2013:
DOD POLICY ON NON-LETHAL WEAPONS, AND OTHER NEW DIRECTIVES
The Department of Defense has revised its 1996 directive on non-lethal
weapons (NLW) to guide future development and procurement of this category
of weaponry.
“Unlike conventional lethal weapons that destroy their targets principally
through blast, penetration, and fragmentation, NLW employ means other than
gross physical destruction to prevent the target from functioning. NLW are
intended to have relatively reversible effects on personnel or materiel,”
the revised directive explains.
“It is DoD policy that NLW doctrine and concepts of operation will be
developed to reinforce deterrence and expand the range of options available
to commanders.”
The directive does not apply to information operations, cyber operations
or electronic warfare capabilities. See DoD Executive Agent for Non-Lethal
Weapons (NLW), and NLW Policy, DoD Directive 3000.03E, April 25, 2013:
Other noteworthy new or updated DoD issuances include the following.
DoD Nuclear Weapons Surety Program, DoD Directive 3150.02, April 24, 2013:
DoD Counterfeit Prevention Policy, DoD Instruction 4140.67, April 26,
2013:
Assistant to the Secretary of Defense for Intelligence Oversight
(ATSD(IO)), DoD Directive 5148.11, April 24, 2013:
Use of Excess Ballistic Missiles for Space Launch, Directive-Type
Memorandum (DTM) 11-008, July 5, 2011, Incorporating Change 3, April 25,
2013:
Click to access dtm-11-008.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://blogs.fas.org/secrecy/subscribe/
To UNSUBSCRIBE, go to
http://blogs.fas.org/secrecy/unsubscribe/
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
https://members.fas.org/donate
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: http://www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
SECRECY NEWS – GROUPS URGE WHITE HOUSE TO TAKE LEAD IN REDUCING SECRECY
The White House should undertake a focused effort to reduce national
security secrecy, some 30 public interest organizations urged President
Obama in a letter today.
The groups called upon the President to adopt a recommendation of the
Public Interest Declassification Board to set up a White House-led Security
Classification Reform Steering Committee.
http://www.archives.gov/declassification/pidb/
“A presidentially appointed Steering Committee would provide a mechanism
for identifying and coordinating needed changes and for overcoming internal
agency obstacles to change,” the group letter said. “It would also reflect
the urgency of reining in a classification system that is largely
unchecked.”
To be effective, though, the proposed Steering Committee would need to be
something more than just a deliberative, coordinating body, such as the
ill-fated Security Policy Board of the 1990s.
http://www.fas.org/sgp/spb/index.html
Specifically, it would require “a clear mandate to reduce the size and
scope of the national security classification system,” the group letter
said, as well as active White House participation to ensure agency
cooperation and compliance.
In principle, reductions in national security secrecy can actually benefit
government agencies by diminishing the significant financial and
operational costs they incur for classification. But in practice, such
reductions have been hard to accomplish and agencies have resisted any
externally imposed limits on their presumed autonomy to classify as they
see fit.
Of all the potential ways to reduce secrecy that could be envisioned, the
proposal for a White House-led Steering Committee is currently the most
salient. That’s because it was recommended by the Public Interest
Declassification Board, who developed it in response to a request from
President Obama himself.
“I also look forward to reviewing recommendations from the study that the
National Security Advisor will undertake in cooperation with the Public
Interest Declassification Board to design a more fundamental transformation
of the security classification system,” the President wrote in a December
29, 2009 memorandum.
http://www.fas.org/sgp/obama/wh122909.html
Now the recommendations that the President looked forward to are in hand,
and it will be up to the White House to act.
SURVEY OF FEDERAL WHISTLEBLOWER LAWS, AND MORE FROM CRS
Dozens of federal laws protect employees who report waste, fraud or abuse
by their employers. Some of those laws, particularly those that apply to
private-sector workers, have been strengthened in recent years, according
to a new survey from the Congressional Research Service.
“Eleven of the forty laws reviewed in this report were enacted after 1999.
Among these laws are the Sarbanes-Oxley Act, the FDA Food Safety
Modernization Act, and the Dodd-Frank Wall Street Reform and Consumer
Protection Act,” the CRS report said.
The report “focuses on key aspects of the federal whistleblower and
anti-retaliation laws. For each law, the report summarizes the activities
that are protected, how the law’s protections are enforced, whether the law
provides a private right of action, the remedies prescribed by the law, and
the year the law’s whistleblower or anti-retaliation provisions were
adopted and amended.”
The report does not address national security whistleblowers, or those who
disclose classified information with or without authorization. See Survey
of Federal Whistleblower and Anti-Retaliation Laws, April 22, 2013:
Other new or newly updated CRS reports that Congress has not made publicly
available include the following.
State Taxation of Internet Transactions, April 19, 2013:
Drought in the United States: Causes and Issues for Congress, April 22,
2013:
Department of Homeland Security Appropriations: A Summary of Congressional
Action for FY2013, April 22, 2013:
The FY2014 State and Foreign Operations Budget Request, April 18, 2013:
U.S.-EU Cooperation Against Terrorism, April 22, 2013:
Expediting the Return to Work: Approaches in the Unemployment Compensation
Program, April 18, 2013:
Economic Recovery: Sustaining U.S. Economic Growth in a Post-Crisis
Economy, April 18, 2013:
Federal Research and Development Funding: FY2013, April 19, 2013:
The U.S. Export Control System and the President’s Reform Initiative,
April 19, 2013:
Mexico’s Drug Trafficking Organizations: Source and Scope of the Violence,
April 15, 2013:
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://blogs.fas.org/secrecy/subscribe/
To UNSUBSCRIBE, go to
http://blogs.fas.org/secrecy/unsubscribe/
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
https://members.fas.org/donate
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: http://www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood







 This and the three other photographs of the construction site near Dinoma in the Negev desert for Israel’s then-secret nuclear reactor were taken during the last months of 1960. According to the U.S. Intelligence Board post-mortem (See
This and the three other photographs of the construction site near Dinoma in the Negev desert for Israel’s then-secret nuclear reactor were taken during the last months of 1960. According to the U.S. Intelligence Board post-mortem (See  President Eisenhower and Israel Prime Minister David Ben-Gurion during the latter’s visit in March 1960 to the United States. (Source:
President Eisenhower and Israel Prime Minister David Ben-Gurion during the latter’s visit in March 1960 to the United States. (Source: 













![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict71.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict62.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict70.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict63.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict54.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict64.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict55.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict56.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict61.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict58.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict59.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict57.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict50.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict46.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict48.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict49.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict51.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict52.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict53.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict65.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict66.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict67.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict68.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2014-info/gaza-ugi/pict69.jpg)













































































































































































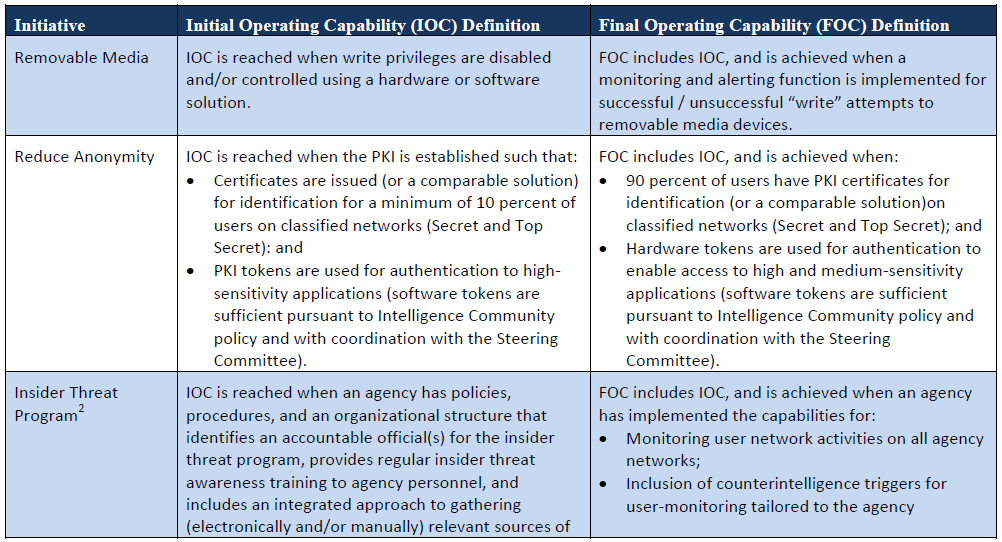


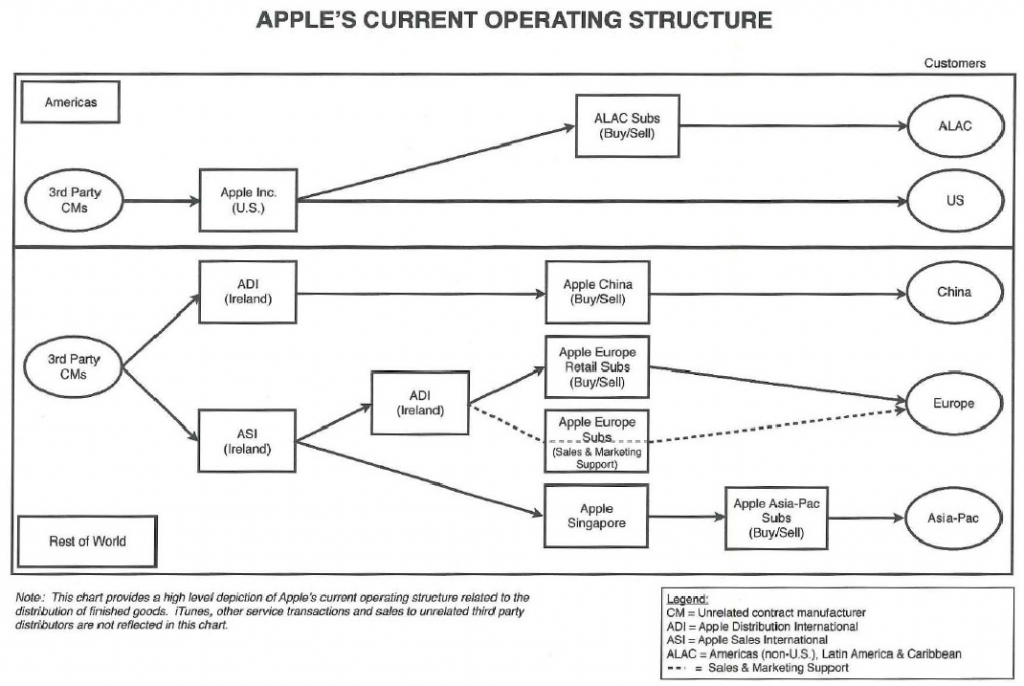











You must be logged in to post a comment.