|
Tag: femen
Public Intelligence – Ohio Fusion Center Report: Bath Salts and Officer Safety

(U//FOUO) The Ohio State Highway Patrol Criminal Intelligence Unit recently partnered with the Ohio Strategic Analysis and Information Center (SAIC) and gathered information regarding bath salts via a survey. The objective of the study was to assist Law Enforcement by creating an officer safety awareness product relating to the dangers of encountering people on bath salts.
(U//FOUO) A survey was distributed to law enforcement and 5 agencies responded back with pertinent information regarding the use and possession of bath salts. The agencies which contributed to this analysis are as follows:
Barberton Police Department, OH; Ohio State Highway Patrol; Powell Police Department, OH; Reynoldsburg Division of Police; and West Virginia State Police – Wheeling Division (Parcel Interdiction).
(U//FOUO) Information was obtained on 161 incidents involving bath salts.
(U//FOUO) OVERVIEW AND ANALYSIS OF RESULTS:
- Out of the 161 incidents reported, officers made 77 arrests involving bath salt use/possession. Many of the incidents occurred before legislation was passed; therefore mere possession was not criminal at the time of many of these reports.
- There were 27 use of force reports involving bath salts.
- There were 3 incidents that involved fleeing of suspects.
- 7 suspects were taken to hospital associated with bath salt use.
- 7 offenders were pinked slipped and taken to mental health facilities.
- There were 4 reports of deaths associated with bath salt use (Note: cause of death results did NOT find that bath salts use was the sole contributor in any of these deaths).
- There was 1 report of suicide; 2 suicide attempts; and 1 suicide threat involving bath salt use.
- Suspects reported paying approximately $20-$25 for bath salts.
- The offenders reported multiple ways of using bath salts including: snorting, injection with a needle syringe, and drinking the bath salts by mixing it with fluid.
- Many offenders admitted to combining bath salts with other drugs.
- When reported, most people said they got the bath salts from independently owned convenient stores and drive-thrus, gas stations or markets. A WV State Police (parcel narcotics interdiction) Officer reported that a prominent internet company is: Southern Burn LLC from South Carolina.
(U//FOUO) OFFICER SAFETY CONCERNS
- Use of force incidents included: use of Taser (3 incidents), hands on, escorts, restrained by medical professionals, and bean bag use.
- One “officer in trouble” call was reported, involving an officer fighting with a person on bath salts.
- Both officers in a Reynoldsburg Police case were surprised after a Taser was used on a suspect. They explained that the Taser was shot and the probes penetrated in the torso of the suspect, however it had minimal effects; the suspect fought through the electric current and rose to his feet.
- Injuries sustained to suspects included: bruises, cuts, Taser punctures, and minimal injuries from bean bag rounds.
- Officers sustained injuries including: injury to knee, injury to back, injury to groin, ankles, scrapes and bruises, and multiple injuries from strikes to the face.
- 2 officers and 7 offenders were taken to the hospital resulting from physical force.
- One incident involved the use of the SWAT team and another involved escalated use of force involving bean bag rounds.
(U//FOUO) PHYSIOLOGICAL REACTIONS FROM BATH SALT USE
- Suspects showed the following physical reactions to bath salts: Hyperventilation, cramps, dehydration, vomiting, shaking, loss of memory, pale, emaciated, jittery, lethargy, incoherent speech, rambling, rapid movement, rapid speech, disoriented, itchy skin, and several suspect admitted to a lack of sleep for multiple days.
- An offender described bath salts as giving him a “cocaine rush” and it being a very “intense” high.
- Witnesses described bath salt users as:
- Hostile, violent, unpredictable, out of control, paranoid, and reckless.
- Additional reports by Law Enforcement involving people on bath salts:
- Officer described one suspect as having unusual superhuman strength.
- Officer described suspect as shooting off the ground like a “flash of light.”
- One suspect bent the hinged handcuffs during the arrest.
- The following hallucinations were reported:
- A hit-skip offender said he saw a brick wall, which in turn caused a crash.
- A male, using bath salts, reported raccoons setting fire inside his home. As a result, he proceeded to destroy his home and used a hatchet to cut up his deck, while attempting to locate the fire-setting raccoons. He also believed the raccoons stole his cell phone.
- A male, using bath salts, believed he was being followed by police helicopters and police officers were using mirrors, snipers and different types of scopes to look through his walls. He called police requesting to negotiate with them, however there were no police at the residence when the call was made.
- During the course of speaking to an offender and officer reported, he yelled, “AT&T calling, may I help you, AT&T is calling, a million dollars, two black guys……it’s not a racial thing, it’s not a racial thing.”
- A bath salt user reported he hears voices; one voice was going to beat him with a ball bat.
- The domestic violence offender using bath salts reported his mother was practicing demonology & witchcraft and she was poisoning his food. He was arrested for choking her.
- DOWNLOAD THE ORIGINAL DOCUMENT HERE:
- OHSP-BathSalts
FEMEN – Topless Female Protest Group Set To Disrupt 2012 Euro Cup
Unveiled – Barclays Bank PLC Admits Misconduct Related to Submissions for the London InterBank Offered Rate and the Euro InterBank Offered Rate and Agrees to Pay $160 Million Penalty
WASHINGTON—Barclays Bank PLC, a financial institution headquartered in London, has entered into an agreement with the Department of Justice to pay a $160 million penalty to resolve violations arising from Barclays’ submissions for the London InterBank Offered Rate (LIBOR) and the Euro Interbank Offered Rate (EURIBOR), which are benchmark interest rates used in financial markets around the world, announced Assistant Attorney General Lanny A. Breuer of the Justice Department’s Criminal Division and Assistant Director in Charge James W. McJunkin of the FBI’s Washington Field Office.
As part of the agreement with the Department of Justice, Barclays has admitted and accepted responsibility for its misconduct set forth in a statement of facts that is incorporated into the agreement. According to the agreement, Barclays provided LIBOR and EURIBOR submissions that, at various times, were false because they improperly took into account the trading positions of its derivative traders, or reputational concerns about negative media attention relating to its LIBOR submissions. The Justice Department’s criminal investigation into the manipulation of LIBOR and EURIBOR by other financial institutions and individuals is ongoing. The agreement requires Barclays to continue cooperating with the department in its ongoing investigation.
“LIBOR and EURIBOR are critically important benchmark interest rates,” said Assistant Attorney General Breuer. “Because mortgages, student loans, financial derivatives, and other financial products rely on LIBOR and EURIBOR as reference rates, the manipulation of submissions used to calculate those rates can have significant negative effects on consumers and financial markets worldwide. For years, traders at Barclays encouraged the manipulation of LIBOR and EURIBOR submissions in order to benefit their financial positions; and, in the midst of the financial crisis, Barclays management directed that U.S. Dollar LIBOR submissions be artificially lowered. For this illegal conduct, Barclays is paying a significant price. To the bank’s credit, Barclays also took a significant step toward accepting responsibility for its conduct by being the first institution to provide extensive and meaningful cooperation to the government. Its efforts have substantially assisted the Criminal Division in our ongoing investigation of individuals and other financial institutions in this matter.”
“Barclays Bank’s illegal activity involved manipulating its submissions for benchmark interest rates in order to benefit its trading positions and the media’s perception of the bank’s financial health,” said Assistant Director in Charge McJunkin. “Today’s announcement is the result of the hard work of the FBI special agents, financial analysts, and forensic accountants as well as the prosecutors who dedicated significant time and resources to investigating this case.”
Barclays was one of the financial institutions that contributed rates used in the calculation of LIBOR and EURIBOR. The contributed rates are generally meant to reflect each bank’s assessment of the rates at which it could borrow unsecured interbank funds. For LIBOR, the highest and lowest 25 percent of contributed rates are excluded from the calculation and the remaining rates are averaged to calculate the fixed rates. For EURIBOR, the highest and lowest 15 percent are excluded, and the remaining 70 percent are averaged to calculate the fixed rates.
Futures, options, swaps, and other derivative financial instruments traded in the over-the-counter market and on exchanges worldwide are settled based on LIBOR. Further, mortgages, credit cards, student loans, and other consumer lending products often use LIBOR as a reference rate. According to the agreement, an individual bank’s LIBOR or EURIBOR submission cannot appropriately be influenced by the financial positions of its derivatives traders or the bank’s concerns about public perception of its financial health due to its LIBOR submissions.
According to the agreement, between 2005 and 2007, and then occasionally thereafter through 2009, certain Barclays traders requested that the Barclays LIBOR and EURIBOR submitters contribute rates that would benefit the financial positions held by those traders. The requests were made by traders in New York and London, via electronic messages, telephone conversations, and in-person conversations. The employees responsible for the LIBOR and EURIBOR submissions accommodated those requests on numerous occasions in submitting the bank’s contributions. On some occasions, Barclays’s submissions affected the fixed rates.
In addition, between August 2005 and May 2008, certain Barclays traders communicated with traders at other financial institutions, including other banks on the LIBOR and EURIBOR panels, to request LIBOR and EURIBOR submissions that would be favorable to their or their counterparts’ trading positions, according to the agreement.
When the requests of traders for favorable LIBOR and EURIBOR submissions were taken into account by the rate submitters, Barclays’ rate submissions were false and misleading.
Further, according to the agreement, between approximately August 2007 and January 2009, in response to initial and ongoing press speculation that Barclays’ high U.S. Dollar LIBOR submissions at the time might reflect liquidity problems at Barclays, members of Barclays management directed that Barclays’ dollar LIBOR submissions be lowered. This management instruction often resulted in Barclays’ submission of false rates that did not reflect its perceived cost of obtaining interbank funds. While the purpose of this particular conduct was to influence Barclays’ rate submissions, as opposed to the resulting fixes, there were some occasions when Barclays’ submissions affected the fixed rates.
The agreement and monetary penalty recognize Barclays’ extraordinary cooperation. Barclays made timely, voluntary, and complete disclosure of its misconduct. After government authorities began investigating allegations that banks had engaged in manipulation of benchmark interest rates, Barclays was the first bank to cooperate in a meaningful way in disclosing its conduct relating to LIBOR and EURIBOR. Barclays’ disclosure included relevant facts that at the time were not known to the government. Barclays’s cooperation has been extensive, in terms of the quality and type of information and assistance provided, and has been of substantial value in furthering the department’s ongoing criminal investigation. Barclays has made a commitment to future cooperation with the department and other government authorities in the United States and the United Kingdom.
Assistant Attorney General Breuer further stated, “As today’s agreement reflects, we are committed to holding companies accountable for their misconduct while, at the same time, giving meaningful credit to companies that provide full and valuable cooperation in our investigations.”
In addition, Barclays has implemented a series of compliance measures and will implement additional internal controls regarding its submission of LIBOR and EURIBOR contributions, as required by the Commodity Futures Trading Commission (CFTC). Barclays will also continue to be supervised and monitored by the FSA.
The agreement and monetary penalty further recognize certain mitigating factors to Barclays’ misconduct. At times, Barclays employees raised concerns with the British Bankers’ Association, the United Kingdom Financial Services Authority (FSA), the Bank of England, and the Federal Reserve Bank of New York in late 2007 and in 2008 that the Dollar LIBOR rates submitted by contributing banks, including Barclays, were too low and did not accurately reflect the market. Further, during this time, notwithstanding Barclays’s improperly low dollar LIBOR submissions, those submissions were often higher than the contributions used in the calculation of the fixed rates.
As a result of Barclays’s admission of its misconduct, its extraordinary cooperation, its remediation efforts and certain mitigating and other factors, the department agreed not to prosecute Barclays for providing false LIBOR and EURIBOR contributions, provided that Barclays satisfies its ongoing obligations under the agreement for a period of two years. The non-prosecution agreement applies only to Barclays and not to any employees or officers of Barclays or any other individuals.
In a related matter, the CFTC brought attempted manipulation and false reporting charges against Barclays, which the bank agreed to settle. The CFTC imposed a $200 million penalty and required Barclays to implement detailed measures designed to ensure the integrity and reliability of its benchmark interest rate submissions.
The FSA issued a final notice regarding its enforcement action against Barclays and has imposed a penalty of £59.5 million against it.
The case is being handled by Deputy Chief Daniel Braun, Assistant Chiefs Rebecca Rohr and Robertson Park, Trial Attorney Alexander Berlin, and Special Trial Attorney Luke Marsh of the Criminal Division’s Fraud Section. The investigation is being conducted by the FBI’s Washington Field Office, jointly with the Antitrust Division of the Department of Justice.
The Department acknowledges and expresses its appreciation for the significant assistance provided by the CFTC’s Division of Enforcement, which referred the conduct to the department, as well as the FSA’s Enforcement and Financial Crime Division.
This agreement is part of efforts underway by President Barack Obama’s Financial Fraud Enforcement Task Force. President Obama established the interagency Financial Fraud Enforcement Task Force to wage an aggressive, coordinated, and proactive effort to investigate and prosecute financial crimes. The task force includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch and, with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes. For more information about the task force visit: http://www.stopfraud.gov.
TOP-SECRET from the FBI – Texas Resident Convicted on Charge of Attempted Use of Weapon of Mass Destruction
AMARILLO, TX—Khalid Ali-M Aldawsari, 22, a citizen of Saudi Arabia and resident of Lubbock, Texas, was convicted by a federal jury today on an indictment charging one count of attempted use of a weapon of mass destruction in connection with his purchase of chemicals and equipment necessary to make an improvised explosive device (IED) and his research of potential U.S. targets, including persons and infrastructure.
The verdict, which was reached in the Northern District of Texas, was announced by Sarah R. Saldaña, U.S. Attorney for the Northern District of Texas; Lisa Monaco, Assistant Attorney General for National Security; and Diego G. Rodriguez, Special Agent in Charge of the FBI Dallas Field Division.
Sentencing has been scheduled for October 9, 2012, in Amarillo. Aldawsari, who was lawfully admitted into the United States in 2008 on a student visa and was enrolled at South Plains College near Lubbock, faces a maximum sentence of life in prison and a $250,000 fine. He was arrested on February 23, 2011 on a criminal complaint and later charged in a March 9, 2011 federal indictment with attempting to use a weapon of mass destruction.
According to court documents and evidence presented during trial, at the time of his arrest last year, Aldawsari had been researching online how to construct an IED using several chemicals as ingredients. He had also acquired or taken a substantial step toward acquiring most of the ingredients and equipment necessary to construct an IED, and he had conducted online research of several potential U.S. targets, the affidavit alleges. In addition, he had allegedly described his desire for violent jihad and martyrdom in blog postings and a personal journal.
“While many people are responsible for thwarting Aldawsari’s threat and bringing him to justice, we owe a debt of gratitude to all the members of the North Texas Joint Terrorism Task Force, and especially to the hundreds of hardworking and dedicated FBI agents, analysts, linguists, and others,” said U.S. Attorney Saldaña. “Their efforts, coupled with the hard work and excellent cooperation from the Lubbock Police Department and the Texas Tech Police Department, are the reason we were able to stop this defendant from carrying out a catastrophic act of terrorism.”
“As this trial demonstrated, Aldawsari purchased ingredients to construct an explosive device and was actively researching potential targets in the United States. Thanks to the efforts of many agents, analysts, and prosecutors, this plot was thwarted before it could advance further,” said Assistant Attorney General Monaco. “This case serves as another reminder of the need for continued vigilance both at home and abroad.”
“Today’s guilty verdict shows how individuals in the United States with the intent to do harm can acquire the knowledge and materials necessary to carry out an attack,” said SAC Rodriguez. “Our success in locating and preventing Mr. Aldawsari from carrying out an attack is a result of cooperation within the law enforcement and intelligence communities, particularly, the North Texas Joint Terrorism Task Force, the Texas Tech Police Department, the Lubbock Police Department, and the Lubbock County Sheriff’s Office, but also a demonstration of information sharing across FBI divisions, as well as assistance from the community. I want to thank the dedicated agents, officers, and analysts; the computer forensics team; and linguists that worked diligently on this investigation, as well as prosecutors serving in the U.S. Attorney’s Office in the Northern District.”
The government presented evidence that on February 1, 2011, a chemical supplier reported to the FBI a suspicious attempted purchase of concentrated phenol by a man identifying himself as Khalid Aldawsari. Phenol is a toxic chemical with legitimate uses, but it can also be used to make the explosive trinitrophenol, also known as T.N.P., or picric acid. Ingredients typically used with phenol to make picric acid, or T.N.P., are concentrated sulfuric and nitric acids.
Aldawsari attempted to have the phenol order shipped to a freight company so it could be held for him there, but the freight company told Aldawsari that the order had been returned to the supplier and called the police. Later, Aldawsari falsely told the supplier he was associated with a university and wanted the phenol for “off-campus, personal research.” Frustrated by questions being asked over his phenol order, Aldawsari cancelled his order, placed an order with another company, and later e-mailed himself instructions for producing phenol. In December 2010, he had successfully purchased concentrated nitric and sulfuric acids.
Aldawsari used various e-mail accounts in researching explosives and targets and often sent e-mails to himself as part of this process. He e-mailed himself a recipe for picric acid, which was described in the e-mail as a “military explosive” and also e-mailed himself instructions on how to convert a cell phone into a remote detonator and how to prepare a booby-trapped vehicle using household items. Aldawsari also purchased many other items, including a Hazmat suit, a soldering iron kit, glass beakers and flasks, a stun gun, clocks, and a battery tester.
Excerpts from a journal found at Aldawsari’s residence indicated that he had been planning to commit a terrorist attack in the United States for years. One entry describes how Aldawsari sought and obtained a particular scholarship because it allowed him to come directly to the United States and helped him financially, which he said “will help tremendously in providing me with the support I need for Jihad.” The entry continues, “And now, after mastering the English language, learning how to build explosives and continuous planning to target the infidel Americans, it is time for Jihad.”
In another entry, Aldawsari wrote that he was near to reaching his goal and near to getting weapons to use against infidels and their helpers. He also listed a “synopsis of important steps” that included obtaining a forged U.S. birth certificate; renting a car; using different driver’s licenses for each car rented; putting bombs in cars and taking them to different places during rush hour; and leaving the city for a safe place.
Aldawsari conducted research on various targets and e-mailed himself information on these locations and people. One of the documents he sent himself, with the subject line listed as “Targets,” contained the names and home addresses of three American citizens who had previously served in the U.S. military and had been stationed for a time at Abu Ghraib prison in Iraq. In others, Aldawsari sent himself the names of 12 reservoir dams in Colorado and California and listed two categories of targets: hydroelectric dams and nuclear power plants. He also sent himself an e-mail titled “Tyrant’s House,” in which he listed the Dallas address for former President George W. Bush. Aldawsari also conducted research that indicated he considered using infant dolls to conceal explosives and the possible targeting of a nightclub with an explosive concealed in a backpack.
This case was investigated by the FBI’s Dallas Joint Terrorism Task Force, with assistance from the Lubbock Police Department and the Texas Tech Police Department. The prosecution is being handled by Assistant U.S. Attorneys Jeffrey R. Haag, Denise Williams, James T. Jacks, and Matthew J. Kacsmaryk and Trial Attorney David Cora from the Counterterrorism Section of the Justice Department’s National Security Division.
Murder at the Manor – Full Movie
TOP-SECRET – The Creation of the U.S. Spy Satellites
In September 1992 the Department of Defense acknowledged the existence of the National Reconnaissance Office (NRO), an agency established in 1961 to manage the development and operation of the nation’s reconnaissance satellite systems. The creation of the NRO was the result of a number of factors.
On May 1, 1960 Francis Gary Powers took off from Peshawar, Pakistan on the U-2 mission designated Operation GRAND SLAM. The flight was planned to take him over the heart of the Soviet Union and terminate at Bodo, Norway. The main target was Plesetsk, which communications intercepts had indicated might be the site of an ICBM facility.1 When the Soviet Union shot down his plane and captured him alive, they also forced President Dwight Eisenhower to halt aerial overflights of Soviet territory.
At that time the U.S. had two ongoing programs to produce satellite vehicles that could photograph Soviet territory. Such vehicles would allow far more frequent coverage than possible with manned aircraft. In addition, they would avoid placing the lives of pilots at risk and eliminate the risks of international incidents resulting from overflights.
The Air Force program, designated SAMOS, sought to develop a number of different satellite systems–including one that would radio its imagery back to earth and another that would return film capsules. The CIA program, CORONA, focused solely on developing a film return satellite.
However, both the CIA and Air Force programs were in trouble. Launch after launch in the CORONA program, eleven in all by May 1, 1960, eight of which carried cameras, had resulted in failure–the only variation was in the cause. Meanwhile, the SAMOS program was also experiencing difficulties, both with regard to hardware and program definition.2
Concerns over SAMOS led President Eisenhower to direct two groups to study both the technical aspects of the program as well as how the resulting system would be employed. The ultimate result was a joint report presented to the President and NSC on August 25, 1960.3
As a result of that meeting Eisenhower approved a first SAMOS launch in September, as well as reorientation of the program, with the development of high-resolution film-return systems being assigned highest priority while the electronic readout system would be pursued as a research project. With regard to SAMOS management, he ordered that the Air Force institute special management arrangements, which would involve a direct line of authority between the SAMOS project office and the Office of the Air Force Secretary, bypassing the Air Staff and any other intermediate layers of bureaucracy.4
Secretary of the Air Force Dudley C. Sharp wasted little time creating the recommended new structure and procedures. On August 31st Sharp signed Secretary of the Air Force Order 115.1, establishing the Office of Missile and Satellite Systems within his own office to help him manage the SAMOS project. With Order 116.1, Sharp created a SAMOS project office at the Los Angeles headquarters of the Air Force Ballistic Missile Division (AFBMD) as a field extension of the Office of the Secretary of the Air Force to carry out development of the satellite.5
The impact of the orders, in practice, was that the director of the SAMOS project would report directly to Under Secretary of the Air Force Joseph V. Charyk, who would manage it in the Secretary’s name. In turn, Charyk would report directly to the Secretary of Defense.6
The changes would not stop there. The urgency attached to developing a successful reconnaissance satellite led, ultimately, to the creation of a top secret program and organization to coordinate the entire national reconnaissance effort.
Several of the documents listed below also appear in either of two National Security Archive microfiche collections on U.S. intelligence. The U.S. Intelligence Community: Organization, Operations and Management: 1947-1989 (1990) and U.S. Espionage and Intelligence: Organization, Operations, and Management, 1947-1996 (1997) publish together for the first time recently declassified documents pertaining to the organizational structure, operations and management of the U.S. Intelligence Community over the last fifty years, cross-indexed for maximum accessibility. Together, these two sets reproduce on microfiche over 2,000 organizational histories, memoranda, manuals, regulations, directives, reports, and studies, totaling more than 50,000 pages of documents from the Office of the Director of Central Intelligence, the Central Intelligence Agency, National Reconnaissance Office, National Security Agency, Defense Intelligence Agency, military service intelligence organizations, National Security Council, and other official government agencies and organizations.
![]() Document 1
Document 1
Joseph Charyk, Memorandum for the Secretary of Defense
Management of the National Reconnaissance Program
24 July 1961
Top Secret
1 p.
The organizational changes resulting from the decisions of August 25, 1960 and their implementation left some unsatisfied. In particular, James Killian and Edwin Land, influential members of the President’s intelligence advisory board pushed for permanent and institutionalized collaboration between the CIA and Air Force. After the Kennedy administration took office the push to establish a permanent reconnaissance organization took on additional life. There was a strong feeling in the new administration, particularly by Secretary of Defense Robert McNamara and his deputy, Roswell Gilpatric, that a better, more formalized relationship was required.7
On July 24, 1961, Air Force Undersecretary Joseph Charyk sent a memorandum to McNamara attaching two possible memoranda of agreement for creation of a National Reconnaissance Program, along with some additional material.
![]() Document 2
Document 2
Memorandum of Understanding
Management of the National Reconnaissance Program (Draft)
20 July 1961
Top Secret
5 pp.
This memo specified establishment of a National Reconnaissance Program (NRP) consisting of “all satellite and overflight reconnaissance projects whether overt or covert,” and including “all photographic projects for intelligence, geodesy and mapping purposes, and electronic signal collection projects for electronic signal intelligence and communications intelligence.”
To manage the NRP, a National Reconnaissance Office (NRO) would be established on a covert basis. The NRO director (DNRO) would be the Deputy Director for Plans, CIA (at the time, Richard Bissell) while the Under Secretary of the Air Force would serve as Deputy Director (DDNRO). The DNRO would be responsible for the management of CIA activities, the DDNRO and the Air Force for Defense Department activities. The DoD, specifically the Air Force acting as executive agent, would be primarily responsible for technical program management, scheduling, vehicle operations, financial management and overt contract administration, while the CIA would be primarily responsible for targeting each satellite. The office would operate under streamlined management procedures similar to those established in August 1960 for SAMOS.
![]() Document 3
Document 3
Memorandum of Understanding
Management of the National Reconnaissance Program (Draft)
21 July 1961
Top Secret
4 pp.
This secondary memorandum was prepared at the suggestion of Defense Department General Counsel Cyrus Vance. It offered a quite different solution to the problem. As with the primary memo, it established a NRP covering both satellite and aerial reconnaissance operations. But rather than a jointly run program, it placed responsibility for management solely in the hands of a covertly appointed Special Assistant for Reconnaissance, to be selected by the Secretary of Defense. The office of the Special Assistant would handle the responsibilities assigned to the NRO in the other MOU. The CIA would “assist the Department of Defense by providing support as required in areas of program security, communications, and covert contract administration.”
![]() Document 4
Document 4
Memorandum
Pros and Cons of Each Solution
Not dated
Top Secret
2 pp.
The assessment of pros and cons favored the July 20 memorandum, listing five pros for the first solution and only two for the second. The first solution would consolidate responsibilities into a single program with relatively little disruption of established management, represented a proven solution, would require no overt organizational changes, would allow both agencies to retain authoritative voices in their areas of expertise, and provided a simplified management structure. The two cons noted were the division of program responsibility between two people, and that “successful program management depends upon mutual understanding and trust of the two people in charge of the NRO.” It would not be too long before that later observation would take on great significance.
In contrast, there were more cons than pros specified for the second solution. The only two points in its favor were the consolidation of reconnaissance activities into a single program managed by a single individual and the assignment of complete responsibility to the agency (DoD) with the most resources. Foremost of the six cons was the need for DoD to control and conduct large-scale covert operations, in as much as it was an entity “whose normal methods are completely foreign to this task.”
![]() Document 5
Document 5
Roswell Gilpatric, Letter to Allen Dulles
Management of the National Reconnaissance Program
6 September 1961
Top Secret
4 pp.
On July 28, 1961, four days after receiving Charyk’s memorandum and draft memoranda of understanding, McNamara instructed Air Force Undersecretary Joseph Charyk to continue discussions with the key officials and advisers in order to resolve any organizational difficulties that threatened to impede the satellite reconnaissance effort. The ultimate result was this letter from Deputy Secretary of Defense Roswell Gilpatric to Dulles, which confirmed “our agreement with respect to the setting up of the National Reconnaissance Program.”
The letter specified the creation of a NRP. It also established the NRO, a uniform security control system, and specified that the NRO would be directly responsive to the intelligence requirements and priorities specified by the United States Intelligence Board. It specified implementation of NRP programs assigned to the CIA through the Deputy Director for Plans. It designated the Undersecretary of the Air Force as the Defense Secretary’s Special Assistant for Reconnaissance, with full authority in DoD reconnaissance matters.
The letter contained no specific assignment of responsibilities to either the CIA or Defense Department, stating only that “The Directors of the National Reconnaissance Office will … insure that the particular talents, experience and capabilities within the Department of Defense and the Central Intelligence Agency are fully and most effectively utilized in this program.”
The letter provided for the NRO to be managed jointly by the Under Secretary of the Air Force and the CIA Deputy Director for Plans (at the time, still Richard Bissell). A May 1962 agreement between the CIA and Defense Department established a single NRO director. Joseph Charyk was named to the directorship shortly afterward.
![]() Document 6
Document 6
Joseph Charyk
Memorandum for NRO Program Directors/Director, NRO Staff
Organization and Functions of the NRO
23 July 1962
Top Secret
11 pp.
This memorandum represents the fundamental directive on the organization and functions of the NRO. In addition to the Director (there was no provision for a deputy director), there were four major elements to the NRO–the NRO staff and three program elements, designated A, B, and C. The staff’s functions included assisting the director in dealing with the USIB and the principal consumers of the intelligence collected.
The Air Force Office of Special Projects (the successor to the SAMOS project office) became NRO’s Program A. The CIA reconnaissance effort was designated Program B, while the Navy’s space reconnaissance effort, at the time consisting of the Galactic Radiation and Background (GRAB) satellite, whose radar ferret mission involved the collection of Soviet radar signals, became Program C. Although the GRAB effort was carried out by the Naval Research Laboratory, the director of the Office of Naval Intelligence would serve as Program C director until 1971.8
![]() Document 7
Document 7
Agreement between the Secretary of Defense and the Director of Central Intelligence on Management of the National Reconnaissance Program
13 March 1963
Top Secret
6 pp.
In December 1962, Joseph Charyk decided to leave government to become president of the COMSAT Corporation. By that time a number of disputes between the CIA and NRO had contributed to Charyk’s view that the position of the NRO and its director should be strengthened. During the last week of February 1963, his last week in office, he completed a revision of a CIA draft of a new reconnaissance agreement to replace the May 1962 agreement (which had replaced the September 6, 1961 agreement). Charyk took the revision to Deputy Secretary of Defense Roswell Gilpatric. It appears that some CIA-suggested changes were incorporated sometime after Charyk left office. On March 13, Gilpatric signed the slightly modified version on behalf of DoD. It was sent to the CIA that day and immediately approved by DCI John McCone, who had replaced Allen Dulles in November 1961.9
The new agreement, while it did not include all the elements Charyk considered important, did substantially strengthen the authority of the NRO and its director. It named the Secretary of Defense as the Executive Agent for the NRP. The program would be “developed, managed, and conducted in accordance with policies and guidance jointly agreed to by the Secretary of Defense and the Director of Central Intelligence.”
The NRO would manage the NRP “under the direction, authority, and control of the Secretary of Defense.” The NRO’s director would be selected by the Defense Secretary with the concurrence of the DCI, and report to the Defense Secretary. The NRO director was charged with presenting to the Secretary of Defense “all projects” for intelligence collection and mapping and geodetic information via overflights and the associated budgets, scheduling all overflight missions in the NRP, as well as engineering analysis to correct problems with collection systems. With regard to technical management, the DNRO was to “assign all project tasks such as technical management, contracting etc., to appropriate elements of the DoD and CIA, changing such assignments, and taking any such steps he may determine necessary to the efficient management of the NRP.”
![]() Document 8
Document 8
Department of Defense Directive Number TS 5105.23
Subject: National Reconnaissance Office
27 March 1964
Top Secret
4 pp.
This directive replaced the original June 1962 DoD Directive on the NRO, and remains in force today. The directive specifies the role of the Director of the NRO, the relationships between the NRO and other organizations, the director’s authorities, and security. It specified that documents or other material concerning National Reconnaissance Program matters would be handled within a special security system (known as the BYEMAN Control System).
![]() Document 9
Document 9
President’s Foreign Intelligence Advisory Board
Memorandum for the President
Subject: National Reconnaissance Program
2 May 1964
Top Secret
11 pp.
The 1963 CIA-DoD agreement on the NRP did not end the battles between the CIA and NRO–as some key CIA officials, including ultimately DCI John McCone, sought to reestablish a major role for the CIA in the satellite reconnaissance effort. The continuing conflict was examined by the PFIAB.
The board concluded that “the National Reconnaissance Program despite its achievements, has not yet reached its full potential.” The fundamental cause for the NRP’s shortcomings was “inadequacies in organizational structure.” In addition, there was no clear division of responsibilities and roles between the Defense Department, CIA, and the DCI.
The recommendations of the board represented a clear victory for the NRO and its director. The DCI should have a “large and important role” in establishing intelligence collection requirements and in ensuring that the data collected was effectively exploited, according to the board. In addition, his leadership would be a key factor in the work of the United States Intelligence Board relating to the scheduling of space and airborne reconnaissance missions.
But the board also recommended that President Johnson sign a directive which would assign to NRO’s Air Force component (the Air Force Office of Special Projects) systems engineering, procurement, and operation of all satellite reconnaissance systems.
![]() Document 10
Document 10
Agreement for Reorganization of the National Reconnaissance Program
13 August 1965
Top Secret
6 pp.
Despite the recommendations of the May 2, 1964 PFIAB report, which were challenged by DCI John McCone, no action was taken to solidify the position of the NRO and its director. Instead prolonged discussions over a new agreement continued into the summer of 1965. During this period the CIA continued work on what would become two key satellite programs–the HEXAGON/KH-9 imaging and RHYOLITE signals intelligence satellites.
In early August, Deputy Secretary of Defense Cyrus Vance and CIA official John Bross reached an understanding on a new agreement, and it was signed by Vice Adm. William F. Raborn (McCone’s successor) and Vance on August 13, 1965. It represented a significant victory for the CIA, assigning key decision-making authority to an executive committee, authority that was previously the prerogative of the NRO director as the agent of the Secretary of Defense.
The Secretary of Defense was to have “the ultimate responsibility for the management and operation of the NRO and the NRP,” and have the final power to approve the NRP budget. The Secretary also was empowered to make decisions when the executive committee could not reach agreement.
The DCI was to establish collection priorities and requirements for targeting NRP operations, as well as establish frequency of coverage, review the results obtained by the NRP and recommend steps for improving its results if necessary, serve on the executive committee, review and approve the NRP budget, and provide security policy guidance.
The NRP Executive Committee established by the agreement would consist of the DCI, Deputy Secretary of Defense, and Special Assistant to the President for Science and Technology. The committee was to recommend to the Secretary of Defense the “appropriate level of effort for the NRP,” approve or modify the consolidated NRP and its budget, approve the allocation of responsibility and the corresponding funds for research and exploratory development for new systems. It was instructed to insure that funds would be adequate to pursue a vigorous research and development program, involving both CIA and DoD. The executive committee was to assign development of sensors to the agency best equipped to handle the task.
The Director of the NRO would manage the NRO and execute the NRP “subject to the direction and control of the Secretary of Defense and the guidance of the Executive Committee.” His authority to initiate, improve, modify, redirect or terminate all research and development programs in the NRP, would be subject to review by the executive committee. He could demand that all agencies keep him informed about all programs undertaken as part of the NRP.
![]() Document 11
Document 11
Analysis of “A $1.5 Billion Secret in Sky” Washington Post, December 9, 1973
Not dated
Top Secret
33 pp.
Throughout the 1960s, the United States operation of reconnaissance satellites was officially classified, but well known among specialists and the press. However, it was not until January 1971 that the NRO’s existence was first disclosed by the media, when it was briefly mentioned in a New York Times article on intelligence and foreign policy.
A much more extensive discussion of the NRO appeared in the December 9, 1973 Washington Post as a result of the inadvertent mention of the reconnaissance office in a Congressional report. The NRO prepared this set of classified responses to the article, clearly intended for those in Congress who might be concerned about the article’s purported revelations about the NRO’s cost overruns and avoidance of Congressional oversight.
![]() Document 12
Document 12
E.C. Aldridge, Jr. (Director, NRO)
Letter to David L. Boren, Chairman,
Senate Select Committee on Intelligence
21 November 1988
Secret
3 pp.
The late 1980s saw the beginning of what eventually would be a wide-ranging restructuring of the NRO. In November 1988 NRO director Edward “Pete” Aldridge wrote to Senator David Boren, Chairman of the Senate Select Committee on Intelligence, concerning the findings of an extensive study (the NRO Restructure Study) of the organizational structure of the NRO.
Aldridge proceeded to report that, after having discussed the study’s recommendations with Secretary of Defense Frank Carlucci and Director of Central Intelligence William Webster, he was directing the development of plans to implement the recommendations. Specific changes would include the creation of a centralized systems analysis function “to conduct cross-system trades and simulations within the NRO,” creation of a “User Support” function to improve NRO support to intelligence community users as well as to the growing number of operational military users, and the dispersal of the NRO Staff to the new units, with the staff being replaced by a group of policy advisers. In addition, Aldridge foresaw the establishment of an interim facility “to house the buildup of the new functions and senior management.” The ultimate goal, projected for the 1991-92 period, would be the “collocation of all NRO elements [including the Los Angeles-based Air Force Office of Special Projects] . . . in the Washington, D.C. area.”
![]() Document 13
Document 13
Memorandum of Agreement
Subject: Organizational Restructure of the National Reconnaissance Office
15 December 1988
Secret
2 pp.
This memorandum of agreement, signed by the Director of the NRO and the directors of the NRO’s three programs commits them to the restructuring discussed in Edward Aldridge’s November 21 letter to Senator Boren.
Many changes recommended by Aldridge, who left office at the end of 1988, were considered by a 1989 NRO-sponsored review group and subsequently adopted.
![]() Document 14
Document 14
Report to the Director of Central Intelligence
DCI Task Force on The National Reconnaissance Office, Final Report
April 1992
Secret
35 pp.
This report was produced by a panel chaired by former Lockheed Corporation CEO Robert Fuhrman, whose members included both former and serving intelligence officials. It focused on a variety of issues other than current and possible future NRO reconnaissance systems. Among the issues it examined were mission, organizational structure, security and classification.
One of its most significant conclusions was that the Program A,B,C structure that had been instituted in 1962 (see Document 6) “does not enhance mission effectiveness” but “leads to counterproductive competition and makes it more difficult to foster loyalty and to maintain focus on the NRO mission.” As a result, the panel recommended that the NRO be restructured along functional lines with imagery and SIGINT directorates. This change was made even before the final version of the report was issued.
The report also noted that while the NRO’s existence was officially classified it was an “open secret” and that seeking to attempt to maintain such “open secrets … weakens the case for preserving ‘real’ secrets.” In addition, such secrecy limited the NRO’s ability to interact with customers and users. The group recommended declassifying the “fact of” the NRO, as well as providing information about the NRO’s mission, the identities of senior officials, headquarters locations, and the NRO as a joint Intelligence Community-Defense Department activity.
![]() Document 15
Document 15
National Security Directive 67
Subject: Intelligence Capabilities: 1992-2005
30 March 1992
Secret
2 pp.
NSD 67 directed a number of changes in U.S. intelligence organization and operations. Among those was implementation of the plan to restructure the NRO along functional lines–eliminating the decades old Program A (Air Force), B (CIA), and C (Navy) structure and replacing it with directorates for imaging, signals intelligence, and communication systems acquisition and operations–as recommended by the Fuhrman panel. As a result, Air Force, CIA, and Navy personnel involved in such activities would now work together rather than as part of distinct NRO components.
![]() Document 16
Document 16
Email message
Subject: Overt-Covert-DOS-REP-INPUT
27 July 1992
Secret
1 p.
In addition to the internal restructuring of the NRO, 1992 saw the declassification of the organization, as recommended by the Fuhrman report (Document 14), for a number of reasons–to facilitate interaction with other parts of the government, to make it easier for the NRO to support military operations, and in response to Congressional pressure to acknowledge the obvious. As part of the process of considering declassification NRO consulted Richard Curl, head of the Office of Intelligence Resources of the State Department’s Bureau of Intelligence and Research–the office which provides INR with expertise and support concerning technical collection systems. Curl recommended a low-key approach to declassification.
![]() Document 17
Document 17
Memorandum for Secretary of Defense, Director of Central Intelligence
Subject: Changing the National Reconnaissance Office (NRO) to an Overt Organization
30 July 1992
Secret
3 pp.
w/ attachments:
Document 17a: Mission of the NRO, 1 p.
Document 17b: Implications of Proposed Changes, 4 pp. (Two versions)
Version One
Version Two
These memos, from Director of the NRO Martin Faga, represent key documents in the declassification of the NRO. The memo noted Congressional pressure for declassification and that Presidential certification that declassification would result in “grave damage to the nation … would be difficult in this case.”
Faga reported that as a result of an NRO review he recommended declassifying the fact of NRO’s existence, issuing a brief mission statement, acknowledging the NRO as a joint DCI-Secretary of Defense endeavor, and identifying top level NRO officials. He also noted that his recommendations attempted to balance concerns about classifying information that realistically could not be protected, while maintaining an ability to protect matters believed to require continued protection.
Secretary of Defense Richard Cheney, DCI Robert Gates, and President Bush approved the recommendations in September and a three-paragraph memorandum to correspondents acknowledging the NRO and NRP was issued on September 18, 1992.
Document 17b comes in two versions, representing different security reviews. Material redacted from the first version includes provisions of National Security Directive 30 on space policy, expression of concern over “derived disclosures,” and the assessment that the “high degree of foreign acceptance of satellite reconnaissance, and the fact that we are not disclosing significant new data,” would not lead to any significant foreign reaction. Another redacted statement stated that “legislation . . . exempting all NRO operational files from [Freedom of Information Act] searches” was required.
![]() Document 18
Document 18
Final Report: National Reconnaissance Program Task Force for the Director of Central Intelligence
September 1992
Top Secret
15 pp.
The end of the Cold War and collapse of the Soviet Union required the U.S. intelligence community and NRO to reconsider how U.S. overhead reconnaissance systems were employed and what capabilities future systems should possess. To consider these questions DCI Robert Gates appointed a task force, chaired by his eventual successor, R. James Woolsey.
The final report considers future needs and collection methods, industrial base considerations, procurement policy considerations, international industrial issues, and transition considerations. Its recommendations included elimination of both some collection tasks as well as some entire types of present and planned collection systems.
![]() Document 19
Document 19
NRO Protection Review, “What is [BYEMAN]?”
6 November 1992
Top Secret
18 pp.
Traditionally, the designations of Sensitive Compartmented Information (SCI) compartments–such as UMBRA to indicate particularly sensitive communications intelligence and RUFF to intelligence based on satellite imagery–have themselves been classified. In recent years, however, the NSA and CIA have declassified a number of such terms and their meaning. One exception has been the term “BYEMAN”– the BYEMAN Control System being the security system used to protect information related to NRO collection systems (in contrast to their products) and other aspects of NRO activities, including budget and structure. Thus, the term BYEMAN has been deleted in the title of the document and throughout the study–although the term and its meaning has become known by specialists and conveys no information beyond the text of any particular document.
This study addresses the use of the BYEMAN classification within the NRO, its impact on contractors and other government personnel, and the consequences of the current application of the BYEMAN system. The study concludes that placing information in the highly restrictive BYEMAN channels (in contrast to classifying the information at a lower level) may unduly restrict its dissemination to individuals who have a legitimate need to know.
![]() Document 20
Document 20
NRO Strategic Plan
18 January 1993
Secret
19 pp.
A study headed by James Woolsey (Document 18), President Clinton’s first DCI, heavily influenced the contents of this early 1993 document. The plan’s introduction notes that while some collection tasks will no longer be handled by overhead reconnaissance the “uncertain nature of the world that is emerging from the end of the ‘cold war’ places a heavy premium on overhead reconnaissance.” At the same time, “this overhead reconnaissance challenge must be met in an era of a likely reduced national security budget.”
The strategic plan is described in the introduction, as “the ‘game plan’ to transition current overhead collection architectures into a more integrated, end-to-end architecture for improved global access and tasking flexibility.”
The document goes on to examine the strategic context for future NRO operations, NRO strategy, strategic objectives, and approaches to implementation. Strategic objectives include improving the responsiveness of NRO systems by developing an architecture that spans the entire collection and dissemination process, from the identification of requirements to dissemination of the data collected.
![]() Document 21
Document 21
National Reconnaissance Office: Collocation Construction Project, Joint DOD and CIA Review Report
November 1994
Unclassified
28 pp.
In an August 8, 1994 press conference, Senators Dennis DeConcini (D-Az.) and John Warner (R-Va.), the chairman and vice chairman of the Senate Select Committee on Intelligence accused the NRO of concealing from Congress the cost involved in building a new headquarters to house government and contractor employees. Previously NRO activities in the Washington area were conducted from the Pentagon and rented space in the Washington metropolitan area. The collocation and restructuring decisions of the late 1980s and early 1990s had resulted in a requirement for a new headquarters facility.10
The accusations were followed by hearings before both the Senate and House intelligence oversight committees–with House committee members defending the NRO and criticizing their Senate colleagues. While they noted that some of the documents presented by the NRO covering total costs were not presented with desirable clarity, the House members were more critical of the Senate committee for inattention to their committee work.11
This joint DoD and CIA review of the project, found “no intent to mislead Congress” but that “the NRO failed to follow Intelligence Community budgeting guidelines, applicable to all the intelligence agencies,” that would have caused the project to be presented as a “New Initiative,” and that the cost data provided by the NRO “were not presented in a consistent fashion and did not include a level of detail comparable to submissions for . . . intelligence community construction.”
![]() Document 22
Document 22
Memorandum for Director of Central Intelligence
Subject: Small Satellite Review Panel
Unclassified
July 1996
The concept of employing significantly smaller satellites for imagery collection was strongly advocated by Rep. Larry Combest during his tenure (1995-97) as chairman of the House Permanent Select Committee on Intelligence. As a result the DCI was instructed to appoint a panel of experts to review the issue.12
Panel members included former NRO directors Robert Hermann and Martin Faga; former NRO official and NSA director Lew Allen; scientist Sidney Drell and four others. The panel’s report supported a radical reduction in the size of most U.S. imagery satellites. The panel concluded that “now is an appropriate time to make a qualitative change in the systems architecture of the nation’s reconnaissance assets,” in part because “the technology and industrial capabilities of the country permit the creation of effective space systems that are substantially smaller and less costly than current systems.” Thus, the panel saw “the opportunity to move towards an operational capability for . . . imagery systems, that consists of an array of smaller, cheaper spacecraft in larger number with a total capacity which is at least as useful as those currently planned and to transport them to space with substantially smaller and less costly launch vehicles.”13
The extent to which those recommendations have influenced NRO’s Future Imagery Architecture plan is uncertain–although plans for large constellations of small satellites have not usually survived the budgetary process.
![]() Document 23
Document 23
Defining the Future of the NRO for the 21st Century, Final Report, Executive Summary
August 26, 1996
Unclassified
30 pp.
This report was apparently the first major outside review of the NRO conducted during the Clinton administration, and the first conducted after the NRO’s transformation to an overt institution and its restructuring were firmly in place.
Among those conducting the review were former Vice Chairman of the Joint Chiefs of Staff, Adm. David E. Jeremiah, former NRO director Martin Faga, and former Deputy Director of Central Intelligence John McMahon. Issues studied by the panel included, inter alia, the existence of a possible alternative to the NRO, NRO’s mission in the 21st Century, support to military operations, security, internal organization, and the relationship with NRO’s customers.
After reviewing a number of alternatives, the panel concluded that no other arrangement was superior for carrying out the NRO mission. It did, however, recommend, changes with regards to NRO’s mission and internal organization. The panel concluded that where the NRO’s current mission is “worldwide intelligence,” its future mission should be “global information superiority,” which “demands intelligence capabilities unimaginable just a few years ago.” The panel also recommended creation of a fourth NRO directorate, which was subsequently established, to focus solely on the development of advanced systems, in order to “increase the visibility and stature of technology innovation in the NRO.”
Notes
1. Michael R. Beschloss, Mayday: Eisenhower, Khrushchev and the U-2 Affair (New York: Harper & Row, 1986), pp.241-42; John Ranelagh, The Agency: The Rise and Decline of the CIA, From Wild Bill Donovan to William Casey (New York: Simon & Schuster, 1986), p. 319; Gregory W. Pedlow and Donald Welzenbach, The Central Intelligence Agency and Overhead Reconnaissance: The U-2 and OXCART Programs, 1954-1974 (Washington, D.C.: CIA, 1992), pp. 170-93.2. Kenneth Greer, “Corona,” Studies in Intelligence, Supplement 17, Spring 1973 in Kevin C. Ruffner (Ed.), CORONA: America’s First Satellite Program (Washington, D.C.: Central Intelligence Agency, 1995), pp. 3-40; Gen. Thomas D. White, Air Force Chief of Staff to General Thomas S. Power, Commander in Chief, Strategic Air Command, June 29, 1960, Thomas D. White Papers, Library of Congress, Box 34, Folder “2-15 SAC.”3. “Special Meeting of the National Security Council to be held in the Conference Room of the White House from 8:30 a.m. to 10 a.m., Thursday, August 25, 1960, undated, National Security Council Staff Papers, 1948-61, Executive Secretary’s Subject File Series, Box 15, Reconnaissance Satellites [1960], DDEL.
4. “Reconnaissance Satellite Program,” Action No.1-b at Special NSC Meeting on August 25, 1960, transmitted to the Secretary of Defense by Memo of September 1, 1960; G.B. Kistiakowsky to Allen Dulles, August 25, 1960, Special Assistant for Science and Technology, Box No. 15, Space [July-Dec 1960], DDEL.
5. Carl Berger, The Air Force in Space Fiscal Year 1961, (Washington, D.C.: Air Force Historical Liaison Office, 1966), pp.41-42; Secretary of the Air Force Order 115.1, “Organization and Functions of the Office of Missile and Satellite Systems,” August 31, 1960; Robert Perry, A History of Satellite Reconnaissance, Volume 5: Management of the National Reconnaissance Program, 1960-1965, (Washington, D.C., NRO, 1969), p. 20; Secretary of the Air Force Order 116.1, “The Director of the SAMOS Project,” August 31, 1960.
6. Perry, A History of Satellite Reconnaissance, Volume 5, p. 20.
7. Jeffrey T. Richelson, “Undercover in Outer Space: The Creation and Evolution of the NRO,” International Journal of Intelligence and Counterintelligence, 13, 3 (Fall 2000): 301-344.
8. Ibid.; GRAB: Galactic Radiation and Background (Washington, D.C.: NRL, 1997); Dwayne A. Day, “Listening from Above: The First Signals Intelligence Satellite,” Spaceflight, August 1999, pp. 339-347; NRO, Program Directors of the NRO: ABC&D, 1999.
9. Perry, A History of Satellite Reconnaissance, Volume 5, pp. 93, 96-97.
10. Pierre Thomas, “Spy Unit’s Spending Stuns Hill,” Washington Post, August 9, 1994, pp. A1, A6.
11. Walter Pincus, “Spy Agency Defended by House Panel,” Washington Post, August 12, 1994, p. A21; U.S. Congress, House Permanent Select Committee on Intelligence, NRO Headquarters Project (Washington, D.C.: U.S. Government Printing Office, 1995), pp. 3-4.
12. Walter Pincus, “Congress Debates Adding Smaller Spy Satellites to NRO’s Menu,” Washington Post, October 5, 1995, p. A14; Joseph C. Anselmo, “House, Senate at Odds Over Intel Small Sats,” Aviation Week & Space Technology, January 1, 1996, p. 19.
13. Small Satellite Review Panel, Memorandum for: Director of Central Intelligence, Subject: Small Satellite Review Panel, July 1996.
Revealed – Former CIA Officer Kiriakou Calls Leak Prosecution Selective, Vindictive
Former CIA officer John Kiriakou, who is charged with unauthorized disclosure of a covert officer’s identity and other classified information, says that the case against him is driven by government animosity, and that he is a target of selective prosecution.
“When White House aides leaked stories about the heroes who killed Osama Bin Laden, they were not prosecuted. When the Washington Post was granted access to the covert director of the CTC for a profile of those directing America’s ‘war on terror,’ no one was prosecuted,” his attorneys wrote in a newly disclosed motion for dismissal.
“But when John Kiriakou gave an interview where he admitted the United States used waterboarding and when he further opined that waterboarding was ineffective, the government went after him,” the motion stated.
“The United States has improperly selected him for prosecution based on his exercise of his constitutional rights and on the animus the United States holds toward him” while “the government has tolerated other disclosures because they resulted in press favorable to the government.”
A copy of the June 12 defense motion was cleared for public release yesterday.
In a separate motion for dismissal, Mr. Kiriakou’s attorneys challenged the constitutionality of the statutes under which he is being prosecuted, including the Intelligence Identities Protection Act and section 793(d) of the Espionage Act, which they argued are “unconstitutionally vague and overbroad.”
Furthermore, because overclassification is rampant, they said, the classification status of any particular information is not a reliable index of its sensitivity.
“The government’s acknowledged practice of over-classification means that not all classified information actually has the potential to damage national security if released…. The fact that information is classified does not actually clarify whether its disclosure… could cause any injury to the United States.”
A government response to the defense motions is due by July 2.
TMZ – Kate Upton — New TOPLESS Photos!!!
Anatoly S. Chernyaev Diary, 1972 – TOP-SECRET from the NSA
 click for full sizeFirst trip with Gorbachev. Chernyaev in Belgium, October 1972. |
Anatoly S. Chernyaev Diary, 1972
Soviet government official Anatoly Chernyaev records an insider’s view of the Brezhnev era
National Security Archive Electronic Briefing Book No. 379
| Translated and edited by Anna Melyakova and Svetlana Savranskaya “Anatoly Chernyaev’s diary is one of the great internal records of the Gorbachev years, a trove of irreplaceable observations about a turning point in history. There is nothing else quite like it, allowing the reader to sit at Gorbachev’s elbow at the time of perestroika and glasnost, experiencing the breakthroughs and setbacks. It is a major contribution to our understanding of this momentous period.” — David E. Hoffman, Pulitzer Prize-winning author of The Dead Hand “Remarkable diary …”
Washington, D.C., May 25, 2012 – Today the National Security Archive publishes excerpts from Anatoly S. Chernyaev’s diary of 1972 for the first time in English translation with edits and postscript by the author. While the diary for the Gorbachev years, 1985-1991, published before and widely used in scholarly work on the end of the Cold War provided a major source on the Gorbachev reforms, the earlier years of the diary give the reader a very rare window into the workings of the Brezhnev inner circle in the 1970s. The portrait of the Soviet leader Leonid Brezhnev, whom most Americans remember from his later years as frail and incomprehensible, emerges very differently from the earliest in the series of diaries donated by Anatoly Sergeyevich Chernyaev to the National Security Archive. In 1972, Chernyaev, deputy head of the International Department of the Central Committee, started keeping a systematic diary, recording his attendance at Politburo meetings, his participation in meetings at the state dacha in Zavidovo (where the experts and speechwriters met to draft speeches and reports for the General Secretary), visits abroad, and the daily life of a high-level Soviet apparatchik. In 1972, Brezhnev is a skillful negotiator, who prepares seriously for Richard Nixon’s first visit to Moscow, who discusses texts of his speeches with leading Moscow intellectuals whom he brought into his inner circle as speechwriters and consultants, who is essentially non-ideological in his dealings with foreign leaders-negotiating arms control and economic agreements with Nixon while the U.S. forces are bombing the Soviet communist ally Vietnam, preferring Georges Pompidou to the leader of French communists Georges Marchais, and”brainwashing” Pakistani leader Bhutto. The two most striking differences between the aging Brezhnev of the late 1970s-early 1980s and the Brezhnev of this diary are that the General Secretary is clearly in charge of the Politburo sessions and that he actively consults with leading experts and intellectuals, such as Georgy Arbatov, Nikolai Inozemtsev, Alexander Bovin and Chernyaev himself. Chernyaev’s daily duties are centered around the international communist movement, interactions with representatives from European communist parties. The reader sees Chernyaev’s emerging disillusionment with his work, which in comparison to real foreign policy, like preparation for Nixon’s visit, feels meaningless. Chernyaev comes to believe that “the Communist Movement right now is nothing more than an ideological addendum to our foreign policy,” and that the Soviet authority in the progressive movements in the world is shrinking: “nobody believes us anymore, no matter how we portray the Chinese and try to explain our Marxist-Leninist purity.” He sees the future in a different direction. After Nixon’s visit, Chernyaev is asked to draft Brezhnev’s speech on Soviet-American relations and thus is allowed to see all the materials from the meeting, including all transcripts of conversation. Impressed with the quality of interaction and the non-ideological spirit of it, Chernyaev anticipates a new era: “Be that as it may, but we’ve crossed the Rubicon. The great Rubicon of world history. These weeks of May 1972 will go down in history as the beginning of an era of convergence.” But the new era will only come thirteen years later. In 1972, he sees the first almost imperceptible sign from the future. In October 1972, he is asked to accompany first secretary of the Stavropol region on a trip to Belgium. This is where Chernyaev meets and spends time with Mikhail Gorbachev for the first time. Astonishingly, as Chernyaev later admits, he did not record this meeting in the diary at the time. Only photographs documented this auspicious meeting where Chernyaev sits on the left hand of the future Soviet leader, whose right hand he was destined to become in the late 1980s.
|
SECRET from Cryptome – FAA Sets Large ND Drone Training Airspace
|
TMZ – Kim Kardashian — The Great Ass Debate
Das neue “GoMoPa”-System der WordPress – Blogs oder “Der Bauer erkennt seine Schweine am Gang.”
Liebe Leser,
“GoMoPa” hat mit immer neuen WordPress-Blogs zwei Dinge vor:
– von negativen Meldungen abzulenken
– themenspezifische Angriffe zu starten.
Früher bediente sich die dubiose selbsternannte “Finanznachrichtenagentur” eines Blog-Netzwerkes aus teilweise fremden Blogs.
Scheinbar sind wohl diese Blogger auf Distanz zu der laut Eigenaussage “Financial Intelligence” gegangen.
Im Übrigen bedeutet Intelligence im Englischen Sprachgebrauch “Geheimdienst”.
Wohl kein Zufall – sieht man sich das STASI-Netzwerk um den STASI-Obersten Ehrenfried Stelzer, den “Ersten Kriminologen der DDR” an.
Wie schreibt “GoMoPa” so schön und ich darf die dubiosen Genossen hier – als Sohn eines Landwirtes, der auf dem Bauernhof groß geworden ist, – mit besonderer Freude zitieren: “Der Bauer erkennt seine Schweine am Gang !”
Eben…
Herzlichst Ihr
Bernd Pulch
Magister der Publizistik, Germanistik und Komparatistik
Leaked Video – Kim Kardashian Nude and Naughty for Playboy
TOP-SECRET from the FBI – Leader of Crips Gang Pleads Guilty in Virginia to Prostituting Eight Juveniles
ALEXANDRIA, VA—Justin Strom, aka “Jae,” “Jae Dee,” or “J-Dirt,” 26, of Lorton, Virginia, pleaded guilty today to recruiting at least eight juvenile girls to engage in commercial sex for his street gang’s prostitution business.
Neil H. MacBride, U.S. Attorney for the Eastern District of Virginia; Kenneth T. Cuccinelli, II, Attorney General of Virginia; Colonel David Rohrer, Fairfax County, Virginia Chief of Police; and Ronald T. Hosko, Special Agent in Charge of the FBI’s Washington Field Office Criminal Division, made the announcement after the plea was accepted by U.S. District Judge James C. Cacheris.
“For six years, Justin Strom profited from preying on teenage girls and others he recruited as prostitutes in a commercial sex ring,” said U.S. Attorney MacBride. “Strom is the fifth and final Underground Gangster Crips gang member to plead guilty to sex trafficking a juvenile—a very serious crime that carries a potential life sentence.”
“Justin Strom robbed these girls of their childhoods, their innocence, and their trust, and he did that in the most base, vile, and despicable way possible,” said Attorney General Cuccinelli. “Nothing can ever repair the damages Strom inflicted on his victims, but it’s our hope that today’s guilty plea will help them begin a path towards healing and moving forward.”
“Today, a fifth member of the Underground Gangster Crips pleaded guilty to strong-arming and pimping underage girls in the illegal sex trade—a trade that is taking place here in some of the most affluent neighborhoods in our nation,” said Special Agent in Charge Hosko. “These gang members admitted that they beat and intimidated young girls they met on the Internet or in Metro stops in our area. They preyed on some of the most vulnerable in our society, and today Justin Strom admitted to these crimes.”
“This gang-driven prostitution ring was a direct threat to the safety and welfare of young women,” said Chief Rohrer. “With the help of our federal partners, we will continue to work aggressively and consistently to rid Fairfax County of gang violence and criminal operations wherever and whenever we find it.”
Strom pleaded guilty to sex trafficking of a child, which carries a mandatory minimum of 10 years in prison and maximum penalty of life in prison. Sentencing is scheduled for September 14, 2012.
According to a statement of facts filed with his plea agreement and other court records, Strom is a member of the Underground Gangster Crips (UGC) set based in Fairfax County. From 2006 through March 2012, Strom misrepresented his identity online to recruit females—including juveniles—through online social networking sites such as Facebook, MySpace, and Datehookup and enticed the girls to use their good looks to earn money through prostitution. He and others posted numerous advertisements on Backpage, Craigslist, and other websites to solicit customers to pay to have sex with juvenile and adult prostitutes.
Strom admitted that he knowingly enticed at least eight juvenile girls to engage in prostitution for his business and that he received proceeds from this illicit conduct for approximately six years.
On March 28, 2012, Strom was among five members and associates of the UGC set based in Fairfax County charged with running a prostitution business that recruited and trafficked high school girls. Four previously pleaded guilty, and Strom’s guilty plea today marks the fifth and final conviction in this case.
Donyel Pier Dove, aka “Bleek,” 27, of Alexandria, Virginia, pleaded guilty on May 17, 2012 to sex trafficking of a juvenile. He also pleaded guilty to use of a firearm during a crime of violence in relation to two armed robberies of 7-11 stores in Manassas, Virginia, in March 2012 and to possession of a firearm by a convicted felon in Fairfax, which also occurred in March 2012. Dove faces a mandatory minimum penalty of five years and a maximum of life on the use of a firearm charge and a maximum of 10 years in prison on the possession of a firearm charge. He is scheduled to be sentenced on August 10, 2012 by U.S. District Judge Anthony J. Trenga.
On May 14, 2012, Henock Ghile, aka “Knots,” 23, of Springfield, Virginia, pleaded guilty to sex trafficking of a juvenile. In court, Ghile admitted that he was a UGC gang associate and that from May 2011 through September 2011, he transported two 17-year-old girls to work as prostitutes. Sentencing has been scheduled for August 3, 2012, before U.S. District Judge Claude M. Hilton.
On April 14, 2012, two others associated with the UGC prostitution operation—Michael Tavon Jefferies, aka “Loc,” 21, of Woodbridge, Virginia; and Christopher Sylvia, 23, of Springfield, Virginia—pleaded guilty to sex trafficking of a juvenile. Jefferies is scheduled to be sentenced on July 6, 2012 before U.S. District Judge Leonie M. Brinkema. Sylvia is scheduled for sentencing on July 20, 2012 before U.S. District Judge Gerald Bruce Lee.
This case was investigated by the Fairfax County Police Department and the FBI’s Washington Field Office, with assistance from the Northern Virginia Human Trafficking Task Force. Virginia Assistant Attorney General and Special Assistant U.S. Attorney Marc Birnbaum and Assistant U.S. Attorney Inayat Delawala are prosecuting the case on behalf of the United States.
Founded in 2004, the Northern Virginia Human Trafficking Task Force is a collaboration of federal, state, and local law enforcement agencies—along with non-governmental organizations—dedicated to combating human trafficking and related crimes.
Unveiled and Uncensored – Euro Cup FEMEN Protester Arrest
Video – Rihanna Is the Sexiest Woman Alive
Watch this exclusive Rihanna Esquire video set to “We Found Love,” then pick up the November issue of Esquire for more.
SECRET – New York Fusion Center Bulletin: Use of Cloned Vehicles in Terrorist or Criminal Operations

Criminals and terrorists have long used official vehicles, “cloned” vehicles (those painted/decorated to appear official), or seemingly legitimate vehicles (e.g. livery, maintenance or delivery) to circumvent security measures at targets of interest.
There have been numerous terrorist attacks overseas wherein operatives used police vehicles or ambulances (or vehicles painted to resemble same) to conceal improvised explosive devices. Within the US Homeland, the most common use of cloned official vehicles by criminals is for drug smuggling; however, at least one terrorist targeting New York envisioned misusing vehicles that would appear to be legitimate, in order to conduct an attack. Dhiren Barot, an al Qaeda operative involved in the 2004 Financial Centers Plot, allegedly plotted to detonate three limousines packed with explosives and gas cylinders in underground parking lots in Manhattan. While the limousines would not have masqueraded as “official vehicles” per se they would have appeared to be legitimately entering those parking structures.
Law enforcement officials and the general public should remain alert to potential fake or cloned official vehicles, with special attention near high-profile targets and mass gatherings at special events, such as upcoming Memorial Day and 4th of July holiday parades and celebrations, or large sporting events scheduled this summer across the State. These events provide the opportunity for terrorists to inflict mass casualties and evade detection by blending into large crowds.
Officials should also be mindful of locations where official vehicles may gain exclusive access, such as parking garages or loading docks proximate to potential targets of interest. Officials at such locations should know how to verify markings on any official vehicles likely to be present. Law enforcement outreach to security staff at these locations during routine patrols is encouraged.
DOWNLOAD THE ORIGINAL DOCUMENT HERE
TOP-SECRET from the FBI – Manhattan U.S. Attorney and FBI Assistant Director in Charge Announce 24 Arrests in Eight Countries as Part of International Cyber Crime Takedown
Preet Bharara, the United States Attorney for the Southern District of New York, and Janice K. Fedarcyk, the Assistant Director in Charge of the New York Field Office of the Federal Bureau of Investigation (FBI), announced today the largest coordinated international law enforcement action in history directed at “carding” crimes—offenses in which the Internet is used to traffic in and exploit the stolen credit card, bank account, and other personal identification information of hundreds of thousands of victims globally. Today’s coordinated action—involving 13 countries, including the United States—resulted in 24 arrests, including the domestic arrests of 11 individuals by federal and local authorities in the United States, and the arrests of 13 individuals abroad by foreign law enforcement in seven countries. In addition, the federal and local authorities and authorities overseas today conducted more than 30 subject interviews and executed more than 30 search warrants. Today’s coordinated actions result from a two-year undercover operation led by the FBI that was designed to locate cybercriminals, investigate and expose them, and disrupt their activities.
Eleven individuals were arrested today, and one last night, in the United States: Christian Cangeopol, a/k/a “404myth,” was arrested today in Lawrenceville, Georgia; Mark Caparelli, a/k/a “Cubby,” was arrested in San Diego, California; Sean Harper, a/k/a “Kabraxis314,” was arrested in Albuquerque, New Mexico; Alex Hatala, a/k/a “kool+kake,” was arrested in Jacksonville, Florida; Joshua Hicks, a/k/a “OxideDox,” was arrested in Bronx, New York; Michael Hogue, a/k/a “xVisceral,” was arrested in Tucson, Arizona; Mir Islam, a/k/a “JoshTheGod,” was arrested in Manhattan, New York; Peter Ketchum, a/k/a “IwearaMAGNUM,” was arrested in Pittsfield, Massachusetts; Steven Hansen, a/k/a “theboner1,” was arrested in Wisconsin, where he is currently serving a prison sentence on state charges. In addition, two minors, whose names will not be made public, were arrested by local authorities in Long Beach and Sacramento, California. Hicks and Islam will be presented later today before a magistrate judge in the Southern District of New York. The other federally arrested defendants will be presented before magistrate judges in the corresponding federal districts of arrest.
Another 13 individuals were arrested today in seven foreign countries. Eleven of those individuals were arrested as a result of investigations commenced in foreign jurisdictions based in part on information arising out of the undercover operation and provided by the FBI to foreign law enforcement. Those 11 arrests occurred in the United Kingdom (6 arrests), Bosnia (2), Bulgaria (1), Norway (1), and Germany (1). Two additional defendants were arrested today in foreign countries based on provisional arrest warrants obtained by the United States in connection with complaints unsealed today in the Southern District of New York. Those two individuals are Ali Hassan, a/k/a/ “Badoo,” who was arrested in Italy; and Lee Jason Juesheng, a/k/a “iAlert,” a/k/a “Jason Kato,” who was arrested in Japan. Australia, Canada, Denmark, and Macedonia conducted interviews, executed search warrants, or took other coordinated action in connection with today’s takedown.
Charges were also unsealed in the Southern District of New York against four additional defendants who remain at large.
Manhattan U.S. Attorney Preet Bharara said, “As the cyber threat grows more international, the response must be increasingly global and forceful. The coordinated law enforcement actions taken by an unprecedented number of countries around the world today demonstrate that hackers and fraudsters cannot count on being able to prowl the Internet in anonymity and with impunity, even across national boundaries. Clever computer criminals operating behind the supposed veil of the Internet are still subject to the long arm of the law.
The allegations unsealed today chronicle a breathtaking spectrum of cyber schemes and scams. As described in the charging documents, individuals sold credit cards by the thousands and took the private information of untold numbers of people. As alleged, the defendants casually offered every stripe of malware and virus to fellow fraudsters, even including software-enabling cyber voyeurs to hijack an unsuspecting consumer’s personal computer camera. To expose and prosecute individuals like the alleged cyber criminals charged today will continue to require exactly the kind of coordinated response and international cooperation that made today’s arrests possible.”
FBI Assistant Director in Charge Janice K. Fedarcyk said, “From New York to Norway and Japan to Australia, Operation Card Shop targeted sophisticated, highly organized cyber criminals involved in buying and selling stolen identities, exploited credit cards, counterfeit documents, and sophisticated hacking tools. Spanning four continents, the two-year undercover FBI investigation is the latest example of our commitment to rooting out rampant criminal behavior on the Internet.
Cyber crooks trade contraband and advance their schemes online with impunity, and they will only be stopped by law enforcement’s continued vigilance and cooperation. Today’s arrests cause significant disruption to the underground economy and are a stark reminder that masked IP addresses and private forums are no sanctuary for criminals and are not beyond the reach of the FBI.”
The following allegations are based on the Complaints unsealed today in Manhattan federal court:
Background on Carding Crimes
“Carding” refers to various criminal activities associated with stealing personal identification information and financial information belonging to other individuals—including the account information associated with credit cards, bank cards, debit cards, or other access devices—and using that information to obtain money, goods, or services without the victims’ authorization or consent. For example, a criminal might gain unauthorized access to (or “hack”) a database maintained on a computer server and steal credit card numbers and other personal information stored in that database. The criminal can then use the stolen information to, among other things, buy goods or services online; manufacture counterfeit credit cards by encoding them with the stolen account information; manufacture false identification documents (which can be used in turn to facilitate fraudulent purchases); or sell the stolen information to others who intend to use it for criminal purposes. Carding refers to the foregoing criminal activity generally and encompasses a variety of federal offenses, including, but not limited to, identification document fraud, aggravated identity theft, access device fraud, computer hacking, and wire fraud.
“Carding forums” are websites used by criminals engaged in carding (“carders”) to facilitate their criminal activity. Carders use carding forums to, among other things, exchange information related to carding, such as information concerning hacking methods or computer-security vulnerabilities that could be used to obtain personal identification information; and to buy and sell goods and services related to carding—for example, stolen credit or debit card account numbers, hardware for creating counterfeit credit or debit cards, or goods bought with compromised credit card or debit card accounts. Carding forums often permit users to post public messages—postings that can be viewed by all users of the site—sometimes referred to as threads. For example, a user who has stolen credit card numbers may post a public thread offering to sell the numbers. Carding forums also often permit users to communicate one-to-one through so-called private messages. Because carding forums are, in essence, marketplaces for illegal activities, access is typically restricted to avoid law enforcement surveillance. Typically, a prospective user seeking to join a carding forum can only do so if other, already established users vouch for him or her, or if he or she pays a sum of money to the operators of the carding forum. User accounts are typically identified by a username and access is restricted by password. Users of carding forums typically identify themselves on such forums using aliases or online nicknames (“nics”).
Individuals who use stolen credit card information to purchase goods on the Internet are typically reluctant to ship the goods to their own home addresses, for fear that law enforcement could easily trace the purchases. Accordingly, carders often seek out “drop addresses”—addresses with which they have no association, such as vacant houses or apartments—where carded goods can be shipped and retrieved without leaving evidence of their involvement in the shipment. Some individuals used carding forums to sell “drop services” to other forum members, usually in exchange for some form of compensation. One frequently used form of compensation is a “1-to-1” arrangement in which the carder wishing to ship to the drop must ship two of whatever items he has carded—one for the provider of the drop to forward to the carder and the other for the provider of the drop to keep as payment in kind for the carder’s use of the drop. Another frequently used compensation arrangement is for the carder and the drop provider to agree to resell the carded items shipped to the drop and to split the proceeds between them.
Background on the Undercover Operation
In June 2010, the FBI established an undercover carding forum called “Carder Profit” (the “UC Site”), enabling users to discuss various topics related to carding and to communicate offers to buy, sell, and exchange goods and services related to carding, among other things. Since individuals engaged in these unlawful activities on one of many other carding websites on the Internet, the FBI established the UC Site in an effort to identify these cybercriminals, investigate their crimes, and prevent harm to innocent victims. The UC Site was configured to allow the FBI to monitor and to record the discussion threads posted to the site, as well as private messages sent through the site between registered users. The UC Site also allowed the FBI to record the Internet protocol (IP) addresses of users’ computers when they accessed the site. The IP address is the unique number that identifies a computer on the Internet and allows information to be routed properly between computers.
Access to the UC Site, which was taken offline in May 2012, was limited to registered members and required a username and password to gain entry. Various membership requirements were imposed from time to time to restrict site membership to individuals with established knowledge of carding techniques or interest in criminal activity. For example, at times, new users were prevented from joining the site unless they were recommended by two existing users who had registered with the site or unless they paid a registration fee.
New users registering with the UC Site were required to provide a valid e-mail address as part of the registration process. The e-mail addresses entered by registered members of the site were collected by the FBI.
Harm Prevented by the Undercover Operation
In the course of the undercover operation, the FBI contacted multiple affected institutions and/or individuals to advise them of discovered breaches in order to enable them to take appropriate responsive and protective measures. In doing so, the FBI has prevented estimated potential economic losses of more than $205 million, notified credit card providers of over 411,000 compromised credit and debit cards, and notified 47 companies, government entities, and educational institutions of the breach of their networks.
The Charged Conduct
As alleged in the complaints unsealed today in the Southern District of New York, the defendants are charged with engaging in a variety of online carding offenses in which they sought to profit through, among other means, the sale of hacked victim account information, personal identification information, hacking tools, drop services, and other services that could facilitate carding activity.
Michael Hogue, a/k/a “xVisceral,” offered malware for sale, including remote access tools (RATs) that allowed the user to take over and remotely control the operations of an infected victim-computer. Hogue’s RAT, for example, enabled the user to turn on the web camera on victims’ computers to spy on them and to record every keystroke of the victim-computer’s user. If the victim visited a banking website and entered his or her user name and password, the key logging program could record that information, which could then be used to access the victim’s bank account. Hogue sold his RAT widely over the Internet, usually for $50 per copy and boasted that he had personally infected “50-100” computers with his RAT and that he’d sold it to others who had infected “thousands” of computers with malware. Hogue’s RAT infected computers in the United States, Canada, Germany, Denmark, Poland, and possibly other countries.
Jarand Moen Romtveit, a/k/a “zer0,” used hacking tools to steal information from the internal databases of a bank, a hotel, and various online retailers, and then sold the information to others. In February 2012, in return for a laptop computer, Romtveit sold credit card information to an individual he believed to be a fellow carder, but who, in fact, was an undercover FBI agent.
Mir Islam, a/k/a “JoshTheGod,” trafficked in stolen credit card information and possessed information for more than 50,000 credit cards. Islam also held himself out as a member of “UGNazi,” a hacking group that has claimed credit for numerous recent online hacks, and as a founder of “Carders.Org,” a carding forum on the Internet. Last night, Islam met in Manhattan with an individual he believed to be a fellow carder—but who, in fact, was an undercover FBI agent—to accept delivery of what Islam believed were counterfeit credit cards encoded with stolen credit card information. Islam was placed under arrest after he attempted to withdraw illicit proceeds from an ATM using one of the cards. Today, the FBI seized the web server for UGNazi.com and seized the domain name of Carders.org, taking both sites offline.
Steven Hansen, a/k/a “theboner1,” and Alex Hatala, a/k/a, “kool+kake,” sold stolen CVVs, a term used by carders to refer to credit card data that includes the name, address, and zip code of the card holder, along with the card number, expiration date, and security code printed on the card. Hatala advertised to fellow carders that he got “fresh” CVVs on a “daily” basis from hacking into “DBs [databases] around the world.”
Ali Hassan, a/k/a “Badoo,” also sold “fulls,” a term used by carders to refer to full credit card data including cardholder name, address, Social Security number, birthdate, mother’s maiden name, and bank account information. Hassan claimed to have obtained at least some of them by having hacked into an online hotel booking site.
Joshua Hicks, a/k/a “OxideDox,” and Lee Jason Jeusheng, a/k/a “iAlert, a/k/a “Jason Kato,” each sold “dumps,” which is a term used by carders to refer to stolen credit card data in a form in which the data is stored on the magnetic strips on the backs of credit cards. Hicks sold 15 credit card dumps in return for a camera and $250 in cash to a fellow carder who, unbeknownst to Hicks, was an undercover FBI agent. Hicks met the undercover agent in downtown Manhattan to consummate the sale. Similarly, Jeusheng sold 119 credit card dumps in return for three iPad 2s to a carder who was an undercover FBI agent. Jeusheng provided his shipping address in Japan to the undercover agent, which in part led to his identification and arrest.
Mark Caparelli, a/k/a “Cubby,” engaged in a so-called “Apple call-in” scheme in which he used stolen credit cards and social engineering skills to fraudulently obtain replacement products from Apple Inc., which he then resold for profit.The scheme involved Caparelli obtaining serial numbers of Apple products he had not bought. He would then call Apple with the serial number, claim the product was defective, arrange for a replacement product to be sent to an address he designated, and give Apple a stolen credit card number to charge if he failed to return the purportedly defective product. Caparelli sold and shipped four iPhone 4 cell phones that he had stolen through the Apple call-in scheme to an individual whom he believed to be a fellow-carder, but who, in fact, was an undercover FBI agent.
Sean Harper, a/k/a “Kabraxis314,” and Peter Ketchum, a/k/a “iwearaMAGNUM,” each sold drop services to other carders in return for money or carded merchandise. Harper provided drop addresses in Albuquerque, New Mexico, to which co-conspirators sent expensive electronics, jewelry, and clothing, among other things. Ketchum advertised drop locations “spread across multiple cities” in the United States and allegedly received and shipped carded merchandise including sunglasses and air purifiers, as well as synthetic marijuana.
Christian Cangeopol CANGEOPOL, a/k/a “404myth,” engaged in illegal “instoring” at Walmart to obtain Apple electronic devices with stolen credit cards. Instoring is a term used by carders to refer to using stolen credit card accounts to make in-store, as opposed to online, purchases of items using stolen credit card information and matching fake identifications. As part of the alleged scheme, Cangeopol and a co-conspirator used stolen credit card data to order electronic devices on Walmart’s website; in selecting a delivery option, they opted to have items delivered to various Walmart stores in Georgia; Cangeopol then picked up the items using a fake identification; Cangeopol and the co-conspirator then resold the carded electronics and split the proceeds.
* * *
The attached chart reflects the name, age, residence of, and pending charges against each individual charged in the Southern District of New York.
Mr. Bharara praised the outstanding investigative work of the FBI and its New York Cyber Crime Task Force, which is a federal, state, and local law enforcement task force combating cybercrime. Mr. Bharara also commended the U.S. Attorney’s offices in the following districts: New Mexico, Arizona, Delaware, Massachusetts, California (Central and Southern districts), Florida (Middle district), Georgia (Northern), as well as the Manhattan District Attorney’s Office. He also thanked the following domestic law enforcement partners for their assistance: the New York City Police Department; the Essex, Vermont Police Department; the Eaton, Ohio Police Department; the Butler County, Ohio Sheriff’s Office; the Cedar Bluff, Alabama Police Department; the Modesto, California Police Department; the Louisiana State Police; the Suffolk County, New York Police Department; the Bakersfield, California Police Department; the Kern County, California District Attorney’s Office; the Long Beach, California Police Department; the Louisville, Kentucky Metro Police Department; and the Nelson County, Kentucky Sheriff’s Office.
Mr. Bharara acknowledged and thanked the following international law enforcement agencies: the United Kingdom’s Serious Organised Crime Agency, Royal Military Police, Thames Valley Police, Greater Manchester Police, Leicestershire Police, Hertfordshire Police, and Wiltshire Police; the Australian Federal Police; Bosnia’s Republika Srpska Ministry of Interior; the Bulgarian Ministry of Interior, General Directorate for Combating Organized Crime; the Danish National Police; the Royal Canadian Mounted Police; the French National High-Tech Crime Unit (OCLCTIC) of the Central Directorate of the Police Judiciaire; the German Bundeskriminalamt (BKA); the Italian Polizia di Stato, Compartimento Polizia Postale e delle Comunicazioni; the National Police Agency of Japan, Tokyo Metropolitan Police Department (Cyber Crimes Control Division), Ministry of Justice of Japan, Tokyo High Prosecutors Office, and the Ministry of Foreign Affairs of Japan; the Macedonian Ministry of Interior, Department Against Organized Crime; and the Norwegian National Police for their efforts. He also thanked the Computer Crime and Intellectual Property Section of the Department of Justice, as well as the Office of International Affairs at the Department of Justice.
This case is being handled by the Office’s Complex Frauds Unit. AUSAs James Pastore, Serrin Turner, Timothy Howard, Rosemary Nidiry, Alexander Wilson, and Sarah McCallum are in charge of the prosecution.
The relevant charging documents can be found on the SDNY website at: http://www.justice.gov/usao/nys/pressreleases/index.html.
List of Arrested Defendants Charged in SDNY Complaints
|
Defendant |
SDNY Complaint Numer |
Residence |
Age |
Charges and Maximum Penalties |
| Christian Cangeopol, a/k/a “404myth” | 12 Mag. 1667 | Lawrenceville, Georgia | 19 |
|
| Mark Caparelli,
a/k/a “Cubby” |
12 Mag. 1640 | San Diego, California | 20 |
|
| Steven Hansen, a/k/a “theboner1” | 12 Mag. 1641 | Kentucky (in prison in Wisconsin) | 23 |
|
| Sean Harper, a/k/a “Kabraxis314” | 12 Mag. 1638 | Albuquerque, New Mexico | 23 |
|
| Ali Hassan, a/k/a “Mr Badoo,” a/k/a “Mr.Badoo,” a/k/a “Badoo” | 12 Mag. 1565 | Milan, Italy | 22 |
|
| Alex Hatala, a/k/a “kool+kake” | 12 Mag. 1669 | Jacksonville, Florida | 19 |
|
| Joshua Hicks, a/k/a “OxideDox” | 12 Mag. 1639 | Bronx, New York | 19 |
|
| Michael Hogue, a/k/a “xVisceral” | 12 Mag. 1632 | Tucson, Arizona | 21 |
|
| Lee Jason Juesheng, a/k/a “iAlert,” a/k/a “Jason Kato” | 12 Mag. 1605 | Tokyo, Japan | 23 |
|
| Peter Ketchum, Jr., a/k/a “iwearaMAGNUM” | 12 Mag. 1651 | Pittsfield, Massachusetts | 21 |
|
| Jarand Moen Romtveit, a/k/a “zer0,” a/k/a “zer0iq” | 12 Mag. 1656 | Porsgrunn, Norway | 25 |
|
| Mir Islam, a/k/a “JoshTheGod” | — | Bronx, New York | 18 |
|
ESQUIRE TV – Kate Upton and a Pair of Scissors
FEMEN Action against Ucraine Prostitution
CIA ALLOWED TO SUSTAIN COVER-UP OF BAY OF PIGS HISTORY
Washington, DC, June 26, 2012 – More than year after the National Security Archive sued the CIA to declassify the full “Official History of the Bay of Pigs Operation,” a U.S. District Court judge today sided with the Agency’s efforts to keep the last volume of the report secret in perpetuity. In her ruling, Judge Gladys Kessler accepted the CIA’s legal arguments that, because Volume V was a “draft” and never officially approved for inclusion in the Agency’s official history, it was exempt from declassification under the “deliberative process privilege” despite having been written over 30 years ago.
The National Security Archive called the decision “a regrettable blow to the right-to-know” and vowed to press the Obama administration to force the CIA to adhere to the President’s Executive Order 13526 that “no information shall remain classified indefinitely.”
The volume, titled “CIA’s Internal Investigations of the Bay of Pigs Operations,” was written by CIA historian Jack Pfeiffer in 1981. It forcefully critiqued the scathing investigative report written in the immediate aftermath of the paramilitary attack – by the CIA’s own Inspector General, Lyman Kirkpatrick – which held CIA planners fully responsible for the worst debacle in the Agency’s covert history. In court papers, CIA officials described Pfeiffer’s critique as “a polemic of recriminations against CIA officers who later criticized the operation.”
“When it comes to protecting its own, the CIA appears to have a double-standard on history,” said Peter Kornbluh who directs the National Security Archive’s Cuba Documentation Project which brought the FOIA lawsuit. Kornbluh noted that the CIA had no problem declassifying Volume IV of the official history–also a draft– in which Pfeiffer attacked both President Kennedy for his role in setting restrictions on the overt elements of what was supposed to be a covert, and “plausibly deniable,” operation, as well as Attorney General Robert Kennedy for his role in the Presidential commission, led by Gen. Maxwell Taylor, that investigated the failed invasion.
“Apparently, the CIA sees no problem in the American public reading a ‘polemic of recriminations’ against the White House,” according to Kornbluh. “But the CIA claims ‘historical accuracy’ as a reason to withhold documents critical of its own officials.”
In her ruling, Judge Kessler stated that “disclosure of a draft history would risk public release of inaccurate historical information.” She also cited the arguments of CIA Chief Historian David Robarge that “disclosure of Volume V would have a chilling effect on CIA’s current historians who would henceforth be inhibited from trying out innovative, unorthodox or unpopular interpretations in a draft manuscript.”
But the Archive characterized the CIA’s effort to cast itself as guardian of accurate and honest history as an exercise in cynicism. “The idea that the CIA can advance the cause of accurate historical analysis by hiding history from the peer review of the public is preposterous,” Kornbluh stated. He noted that it was the Agency’s selective declassification of the Pfeiffer volumes that fostered inaccurate historical information. “The real chilling effect of the CIA’s selective cover up is on the public’s ability to access and analyze the complete historical record on the Bay of Pigs.”
The Archive’s lawsuit did yield the release of Volumes I, II, and IV. Volume III was previously released under the Kennedy Assassination Records Act in 1998. Those four volumes can be read here.
Kate Upton and a Pair of Scissors – Esquire Video
Murder in the OC – Full Movie
TOP-SECRET – DoD Current and Projected Unmanned Aircraft Systems (UAS) Inventory Levels Through 2017
The following tables display the current Department of Defense unmanned aircraft systems (UAS) inventory levels (FY2012 budgeted inventory) and planned inventory through FY2017. The first table was taken from the recent Department of Defense Report to Congress on Future Unmanned Aircraft Systems Training, Operations, and Sustainability which was originally obtained and published by InsideDefense.com. The second table displays the total inventories by service.
UAS Inventory Levels (FY12 budgeted inventory with noted exception)
| Service Branch | UAS System Name | Current Inventory | FY12 | FY13 | FY14 | FY15 | FY16 | FY17 |
|---|---|---|---|---|---|---|---|---|
| Air Force | MQ-1B Predator | 163 | 152 | 141 | 130 | 121 | 115 | 110 |
| Air Force | MQ-9A Reaper | 70 | 96 | 135 | 167 | 199 | 229 | 256 |
| Air Force | RQ-4B Global Hawk* | 23 | 23 | 15 | 15 | 15 | 15 | 15 |
| Army | RQ-11B Raven | 5394 | 6294 | 6528 | 6717 | 6921 | 7074 | 7074 |
| Army | RQ-7B Shadow | 408 | 408 | 408 | 408 | 408 | 408 | 408 |
| Army | MQ-5B Hunter | 45 | 45 | 45 | 45 | 45 | 45 | 45 |
| Army | MQ-1C Gray Eagle | 19 | 45 | 74 | 110 | 138 | 152 | 152 |
| Navy | RQ-4A Global Hawk | 5 | 5 | 0 | 0 | 0 | 0 | 0 |
| Navy | MQ-4C BAMS | 0 | 0 | 2 | 2 | 5 | 9 | 13 |
| Navy | MQ-8B Firescout/TUAV | 5 | 9 | 14 | 18 | 25 | 32 | 37 |
| Navy | RQ-21A STUAS | 0 | 1 | 2 | 3 | 4 | 4 | 4 |
| Navy | RQ-21A Scan Eagle | 122 | 122 | 122 | 122 | 122 | 122 | 122 |
| Navy | X-47B UCAS-D | 2 | 2 | 2 | 2 | 0 | 0 | 0 |
| Navy | UCLASS | 0 | 0 | 0 | 0 | 2 | 2 | 4 |
| Marine Corps | RQ-7B Shadow | 52 | 52 | 52 | 52 | 52 | 52 | 52 |
| Marine Corps | RQ-21A STUAS | 8 | 8 | 8 | 23 | 48 | 73 | 100 |
* Reflects RQ-4B Block 20/40 invent0ry remaining after FY 2012 (Block 30 cancelled in President’s 2013 Budget submission).
UAS Total Inventory by Service
| Service Branch | Current Inventory | FY12 | FY13 | FY14 | FY15 | FY16 | FY17 |
|---|---|---|---|---|---|---|---|
| Air Force | 256 | 271 | 291 | 312 | 335 | 359 | 381 |
| Army | 5866 | 6792 | 7055 | 7280 | 7512 | 7679 | 7679 |
| Navy | 134 | 139 | 142 | 147 | 158 | 169 | 180 |
| Marine Corps | 60 | 60 | 60 | 75 | 100 | 125 | 152 |
| Total | 6316 | 7262 | 7548 | 7814 | 8105 | 8332 | 8392 |
TOP-SECRET from the FBI – Mortgage Rescue Business Owner Sentenced to 90 Months for Fraud
ALEXANDRIA, VA—Howard R. Shmuckler, 68, of Virginia Beach, Virginia, was sentenced today to 90 months in prison, followed by three years of supervised release, for running a fraudulent mortgage rescue business that received substantial fees but actually modified clients’ mortgages in only a few cases. The court ordered that this sentence be served consecutive to a 75-month federal sentence Shmuckler received on April 5, 2012 in the District of Columbia involving a counterfeit check scheme.
Neil H. MacBride, United States Attorney for the Eastern District of Virginia; James W. McJunkin, Assistant Director in Charge of the FBI’s Washington Field Office; Jon T. Rymer, Inspector General of the Federal Deposit Insurance Corporation (FDIC-OIG); and Christy Romero, Special Inspector General for the Troubled Asset Relief Program (SIGTARP); made the announcement after sentencing by United States District Judge Leonie M. Brinkema.
“Mr. Shmuckler is a cunning criminal who took advantage of distressed homeowners in desperate need of help,” said U.S. Attorney MacBride. “Today’s sentence should send a clear warning to other fraudsters of the heavy price they will pay for preying on vulnerable people looking for help to save their homes.”
“Mr. Schmuckler portrayed himself as a successful attorney and mortgage advisor who was able to rescue mortgages and provide relief to homeowners, but, in reality, he was a fraud,” said Assistance Director in Charge McJunkin. “The public should be wary of such individuals who offer a service or product that seems too good to be true. It probably is.”
“At a time when homeowners across the nation are struggling to keep their homes, Shmuckler actively targeted the most vulnerable of them with his mortgage modification scam,” said Special Inspector General Romero of SIGTARP. “Shmuckler exploited homeowners desperately seeking support through federal housing programs such as HAMP by essentially guaranteeing the homeowners mortgage modifications in exchange for an upfront fee. Shmuckler performed little, if any, service in return for the fees, and in many cases, the homeowners’ properties fell into foreclosure. SIGTARP and its partners in law enforcement will aggressively shut down these scams and hold their perpetrators accountable for their crimes.”
On April 10, 2012, Shmuckler pled guilty to six counts of wire fraud. According court records, Shmuckler, a convicted felon and disbarred attorney, owned and operated a Vienna, Virginia mortgage-rescue business known as The Shmuckler Group (TSG). From June 2008 through March 2009, TSG took in nearly $2.8 million from approximately 865 clients whose mortgages were in distress and who came to Shmuckler looking for relief. Shmuckler aggressively recruited new clients and pocketed their money while pretending he was successful, was an attorney, and that the business had restructured hundreds of mortgages, stopped hundreds of foreclosures, and negotiated hundreds of short sales. In reality, TSG was able to obtain relief for approximately 4.5 percent of its clients.
Court records indicate that Shmuckler instructed clients to terminate contact with their mortgage companies and to stop making payments to their lenders. TSG never facilitated a modification of the mortgages referenced in the statement of facts filed with his plea agreement.
This case was investigated by the FBI’s Washington Field Office, the FDIC-OIG, and SIGTARP. Assistant United States Attorneys Timothy D. Belevetz and Uzo Asonye are prosecuting the case on behalf of the United States.
A copy of this press release may be found on the website of the United States Attorney’s Office for the Eastern District of Virginia at http://www.justice.gov/usao/vae.
Unveiled – Mila Kunis: Exclusive Esquire Video of a Woman We Love
My Mothers Murder – Full Movie
C-Cup 2012 – Comedy Central Germany HD – Model Football – UEFA EURO Soccer 2012
Cryptome – US Promotes Jobs by Deathcraft – SECRET
http://www.state.gov/r/pa/prs/ps/2012/06/192408.htm
Briefing on Department of State Efforts to Expand Defense Trade
Special Briefing
Andrew J. Shapiro
Assistant Secretary, Bureau of Political-Military Affairs
Via Teleconference
June 14, 2012
MR. TONER: Thank you so much. And thanks to everyone for joining us. Promoting U.S. businesses abroad and expanding U.S. exports our top priorities for the U.S. Department of State. And Assistant Secretary of State for Political and Military Affairs Andrew Shapiro joins us today to talk about how the Bureau of Political-Military Affairs is engaging with allies and partners to expand the defense trade that’s critical both to our national security as well as a part of our larger economic statecraft efforts on this Economic Statecraft Day.
Just before I hand it over to Assistant Secretary Shapiro, I just want to remind everybody this is an on-the-record briefing and you’ll have a chance for questions after he says a few words. So go ahead, Assistant Secretary.
ASSISTANT SECRETARY SHAPIRO: Thank you, Mark. And I’m delighted to be able to speak to you all today as part of Global Economic Statecraft Day. And as Mark noted, Global Economic Statecraft Day is a global event that we’re holding to highlight America’s commitment to put strengthening American jobs at the center of our foreign policy and to use diplomacy to advance America’s economic renewal. We’re using diplomatic tools to strengthen the economic foundations of America’s global leadership. And we are elevating the strategic role of economics, both in what we choose to prioritize and how we pursue solutions to some of the world’s most pressing challenges.
Our work in the Political-Military Bureau, to expand security cooperation with our allies and partners, is critical to America’s national security and economic prosperity. And it is also an important part of the State Department’s economic statecraft efforts. It also serves critical national security interests by helping allies and partners more capably secure their countries and contribute to international security efforts. And that’s a point that I want to emphasize. The purpose of our sales is to serve national security interests and that is a theme that runs through every sale that we conduct. We evaluate for how it will support U.S. national security and foreign policy interests.
So let me be clear about why the State Department oversees U.S. security cooperation, and that’s because security cooperation is fundamentally a foreign policy act. It is therefore the Secretary of State that is given the authority to oversee and authorize all arms sales in order to ensure they advance U.S. foreign policy.
The Bureau of Political-Military Affairs, which I oversee, implements the Secretary’s authority in this area and ensures that any assistance in the U.S Government – that the U.S. Government provides is fully in line with U.S. foreign policy. All sales and arms transfers are reviewed and assessed through the Conventional Arms Transfer Policy. This means we take into account political, military, economic, arms control, and human rights conditions in making decisions on the provisions of military equipment and the licensing of direct commercial sales to any country. We only allow a sale after we carefully examine issues like human rights, regional security, and nonproliferation concerns, and determine a sale is in the best foreign policy and national security interests of the United States.
Review and monitoring are also an integral part of our work. We work to make sure that items of U.S. origin are being used in the manner intended and are consistent with our legal obligations, foreign policy goals, and our values. If a license or transfer is approved, recipients are bound by end use restrictions and conditions. This grants U.S. Government officials full access to monitor how that defense article is being used throughout its lifetime. We also investigate all potential violations and take appropriate action depending on the nature and scope of the infraction.
Additionally, the transfer of items above a certain value requires the approval of Congress. We therefore work closely with Congress on all significant sales. The arm – to be quite frank, the arms transfer process sometimes causes consternation among our international partners who will gripe about onerous rules and procedures. And at times it makes countries, to be honest, reluctant to partner with the United States. But these safeguards are critical to our foreign policy, and I can assure you that they are aggressively enforced.
So therefore, what I think is remarkable is that despite our very high bar for approving transfers and our aggressive monitoring, more and more countries want to partner with the United States. At the State Department, when we deem that cooperating with an ally or partner in the security sector will advance our national security, we advocate tirelessly on behalf of U.S. companies abroad, and I think I have the frequent flyer miles to prove it.
It’s no longer just our ambassadors who promote U.S. security cooperation abroad. Senior State Department officials regularly advocate on behalf of the U.S. bidders on foreign government and foreign military procurements. We do so when we meet with officials on our travels abroad, on margins of international conferences, and in regular diplomatic correspondents to foreign government officials. And these efforts are having an impact. Despite the global economic strain, demand for U.S. defense products and services is stronger than ever.
Last week, we released the 655 Report, which is an annual report of defense articles and services that were authorized for export. This report focuses on direct commercial sales, and it showed that there was a more than $10 billion increase in Fiscal Year 2011 in items authorized for transfer. In 2011, the Directorate for Defense Trade Controls, which is part of the Political-Military Bureau, processed more than 83,000 licenses, the most ever. Today, I can confirm that this is already a record-breaking year for foreign military sales, which are government-to-government sales. We have already surpassed $50 billion in sales in Fiscal Year 2012. This represents at least a $20 billion increase over Fiscal Year 2011, and we still have more than a quarter of the fiscal year left.
To put this in context, Fiscal Year 2011 was a record-setting year at just over 30 billion. This fiscal year will be at least 70 percent greater than Fiscal Year 2011. These sales support tens of thousands of American jobs, which is welcome news for the economy.
So I’ll just take a minute or so to briefly outline why I think we are seeing such strong interest in U.S. systems. First, it’s because countries want to partner with the United States of America. This Administration has worked aggressively to improve America’s image abroad, to build new partnerships, and strengthen existing ones. We have seen tremendous growth and sales with developing countries and emerging powers such as Brazil and India, and this speaks volumes about our diplomatic efforts.
For a country to be willing to cooperate in the area of national defense, perhaps the most sensitive area for any nation, they have to be sure about the nature of the relationship with the United States. When a country buys an advanced U.S. defense system through our FMS, DCS, or Foreign Military Financing programs, they aren’t simply buying a product. They are also seeking a partnership with the United States. These programs both reinforce our diplomatic relations and establish a long-term security relationship.
The complex and technical nature of advanced defense systems frequently requires constant collaboration and interaction between countries over the life of that system, decades in many cases. This cooperation therefore helps build bilateral ties and creates strong incentives for recipient countries to maintain good relations with the United States. The fact that more countries want to deepen their defense trade partnership with the United States is a sign that our broader diplomatic efforts are having an impact.
For many countries, procurement decisions aren’t simply based on the specifications of the given system. Our advocacy helps demonstrate that the U.S. Government believes these sales are critical to our diplomatic relationship.
Second, countries want to buy the best. And to get the best, they rightly turn to U.S. defense systems. These systems are made in America, and the growth in defense sales abroad demonstrates the capabilities of American manufacturing and of American workers. This Administration has worked hard to support the U.S. defense industry abroad, because it supports our national security and supports jobs here at home.
For example, our agreement in December to expand our security cooperation with Saudi Arabia is projected to have a significant impact on the U.S. economy. According to industry experts, this agreement will support more than 50,000 American jobs. It will engage 600 suppliers in 44 states and provide $3.5 billion in annual economic impact to the U.S. economy. This will support jobs not only in the aerospace sector, but also on our manufacturing base and support chain, which are all crucial for sustaining our national defense.
Lastly, we are also working to improve our ability to cooperate with our partners. Nothing shows our commitment to expanding U.S. exports more than our export control reform efforts. The current system operates under laws written in the 1970s and was designed to address the challenges of the Cold War. It’s bad for U.S. business, it’s bad for enforcing our export control requirements, and it hurts our ability to prosecute those who violate U.S. export control laws.
The goals of our export control reform efforts are ultimately about making sure that our system protects the things it needs to protect. This will allow the U.S. Government to focus its limited resources on safeguarding and monitoring the most sensitive items. Our reform efforts will also allow us to streamline access to export-controlled items for our close allies. This will help improve interoperability with our allies as well as bolster our defense industrial base. And we are making substantial progress. We have almost finished our interagency work on all the list categories, and we’re working to have this process completed by the end of the year.
Another way we have worked to facilitate defense trade is through the defense trade treaties with the UK and Australia. This past April, the United States and UK signed an exchange of notes which brought the U.S.-UK Defense Trade Treaty into force. This treaty is the first of its kind and allows for the more efficient transfer of certain defense articles between the U.S. and UK. We’re also making progress in the implementation of the treaty with Australia, which we hope to be completed in the next year.
So with that, I’d be happy to take any questions.
MR. TONER: Okay. We’re ready to take any questions you might have now, Operator.
OPERATOR: Okay, thank you. We will now begin the question-and-answer session. If you would like to ask a question, please press *1. Please un-mute your phone and record your name clearly when prompted. If you need to withdraw your request, press *2. Again, to ask a question, it’s *1. It will be one moment, please, for the first question.
And our first question comes from Kate Brannen with Defense News.
QUESTION: Hi. I just wanted to clarify quickly a point and then ask a question. You said $50 billion in sales so far for 2012. Are those sales that the State Department has authorized? Is that the correct way to phrase it?
ASSISTANT SECRETARY SHAPIRO: Well, I believe that those are – and I’ll confirm this for you, but I believe that those are ones in which they’re authorized and the sales have been – the contracts have been negotiated.
QUESTION: Okay. And I was hoping to get an update on some of the changes the State Department has proposed to the Congressional notification process. I know there was some pushback on the Hill, and I was just curious what the current status is of – are you using that new notification process to inform Congress of sales?
ASSISTANT SECRETARY SHAPIRO: Yes, we are. And again, changes to the notification process were designed to ensure – to give Congress more information earlier than they’ve had it before, but also to provide some predictability to the length of the process and to identify which sales Congress has the most concerns about, so we’re able to address those concerns. But yes, we are proceeding with the new process.
QUESTION: Okay, thank you.
MR. TONER: Next question, please.
OPERATOR: And our next question comes from Eli Lake with Newsweek.
QUESTION: Hi. Thank you very much, Assistant Secretary. Could you break down in a little bit more detail what is responsible for this pretty significant uptick for what you anticipate for this fiscal year? Was it just more than the Saudi Arabia – can you get into that?
And if I can sneak in another one, how does the – these latest numbers kind of effect next month’s negotiations on, I guess, what would be a kind of global arms control – arms trade treaty?
ASSISTANT SECRETARY SHAPIRO: For your first question, obviously the sale to Saudi Arabia was very significant. It’s a sale worth $29.4 billion. And Saudi Arabia signed a letter of offer and acceptance in December for the sale, up to 84 advanced F-15SA fighter aircraft. It also includes upgrades of – to its current fleet of 70 F-15 aircraft, as well as munitions, spare parts, training, maintenance, and logistics. But this number also includes the sale of the Joint Strike Fighter to Japan, which is valued at approximately $10 billion.
In terms of the arms trade treaty, I’ll have to admit that’s not an issue that my bureau follows closely, and we work closely with our nonproliferation bureau led by Tom Countryman on this, so I’m going to allow – boot your question over to him and get you back an answer on that.
QUESTION: Thanks.
MR. TONER: All right. Next question, please.
OPERATOR: And next is Jen Dimascio with Aviation Week. And Jen, your line is open. Check your mute button.
QUESTION: Hello.
OPERATOR: Yes. Please continue.
QUESTION: Okay, sorry. I wanted to follow up on this record breaking year and kind of push it forward to next year. I mean, are you anticipating another record breaking year in FY13? And do you expect additional sales from countries like India?
ASSISTANT SECRETARY SHAPIRO: It’s too early to predict what FY13 will look like. Obviously, we’re going to continue to press and advocate for U.S. arms sales. We are hopeful that arms sales to India will increase. We’ve made tremendous progress in the relationship over the last decade. We went from nearly zero sales to about $8 billion in sales.
Going forward, there’s a number of tenders which we hope we’re successful on, including a tender for Apache helicopters. And we continue to advocate for them, and we’re hopeful that we’ll be successful on a number of sales over the coming year with India.
MR. TONER: All right. Next question please.
OPERATOR: And next is Austin Wright with Politico.
QUESTION: Hi. Can you give us a quick update on your efforts to push some export control reform initiatives through Congress? And there’s been some grumbling on the Hill, and I’m wondering if you think you’re going to make progress on this, given that many administrations have tried and have been unable to get these kind of reforms through the Hill.
ASSISTANT SECRETARY SHAPIRO: Right. Thanks. As you know, export control reform has many components, one of which is to revise both the State U.S. Munitions List and the Commerce Control List so that there is a clear distinction between what is controlled on each list. And our goal has been to complete the list reviews and publish the revised control list categories in proposed form this year and to both publish the revised categories in final form on a rolling basis, and that remains the goal. We’ve almost finished our interagency work on all the list categories, and we have people working from across our – the interagency working hard on this as we speak, and we are committed to meeting this goal.
I know that a lot of others have tried and failed and that there is skepticism that we can get this done, but let me be clear: Any speculation that export control reform is stalled is absolutely false. We’re making significant progress, interagency teams are making progress every day, and this has been a long, tough slide but we’re close to the finish line. And we published a number of categories and we have more in pipeline. We’re nearly halfway through rewriting the categories, and we have thus far briefed our Congressional committees on 13 categories.
QUESTION: Thank you.
MR. TONER: Great, thanks. Next questioner, please.
OPERATOR: And as a reminder, press *1 to ask a question. And next is Raymond Barrett with PAR.
QUESTION: Would you be able to expand on how completing that list and the categories and how maybe some of the individual categories might boost the domestic industry here in the States?
ASSISTANT SECRETARY SHAPIRO: Well, for example, we anticipate that – and Secretary Gates was quite eloquent in describing some of the challenges in our current export control reform system where a part or component for a previously approved aircraft would need a license. And it’s our hope that for those types of items, including thousands of parts and components, that once they move from the U.S. Munitions List to the Commerce Control List, it’ll improve the ability of our partners to acquire those parts and components (inaudible) it will streamline the system, make it easier for our partners to acquire those types of parts and components and help our manufacturing base as a result.
QUESTION: And also, just – you mentioned that the Defense Trade Cooperation Treaty with Australia might be done by the end of the year. Is that treaty going to be as extensive in nature as the one with the UK? As in – so if you can maybe compare the two.
And also, are there any other nations that you’re looking at signing a similar treaty with? Are there any ones that are (inaudible) proposed, that are next on the list after Australia?
ASSISTANT SECRETARY SHAPIRO: Well, there may be some minor differences in the text of the defense cooperation treaties between the UK and Australia. We anticipate that they will have the same broad impact in encouraging defense trade between both of our – between both the UK and Australia and the United States. And so we very much anticipate that this will have an impact.
What was your second question again?
QUESTION: Basically, who’s next? Okay, so –
ASSISTANT SECRETARY SHAPIRO: Oh. I’ll be quite clear. I testified before Congress that these would be – that we would not – that the Administration would not seek any further defense cooperation treaties. So any decision to reverse that will have to leave – be left to my successor.
QUESTION: All right.
ASSISTANT SECRETARY SHAPIRO: Okay.
QUESTION: Thank you.
OPERATOR: And our next question comes from Larry Shaughnessy from CNN.
QUESTION: Hello. This is Larry. My question is about the Secretary’s comments earlier this week alleging Russia is selling armed attack helicopters to Syria. How does the Department answer the Russian insistence that the U.S. is supplying crowd control weapons to places like Bahrain, and how do these issues differ?
ASSISTANT SECRETARY SHAPIRO: Well, I don’t have a lot to add to Toria’s response from yesterday where she – and today where she’s directly addressed this. But what I will say is it’s a totally specious comparison. Our – we have made clear that we’re not selling equipment to Bahrain now that can be used for internal security purposes until there is improvement on human rights; and whereas, as Secretary Clinton pointed out, the sales to Syria are directly implicated in attacking innocent people, innocent civilians. So we believe that that comparison does not hold water.
MR. TONER: Next question, please? And time for just a couple more, I think.
OPERATOR: Okay. And our next question comes from Adam Behsudi with Inside U.S. Trade.
QUESTION: Yes. Hi. I wanted to – you’d mentioned earlier that the goal on the export control reform would be to publish all the proposed rules this year and then final rules on a rolling basis. I mean, how many final categories or final rules for categories do you expect to be done this year, if any? And is there an effort to get more of that done based on the fact that it’s an election year, and maybe if there’s a change in administration this won’t be picked up as well by the next White House?
And then finally, what does the – in terms of Congressional pushback on wanting more notification on some of the categories that – on the items that are moving from one category to another, I mean, what is State Department doing in terms of working with Congress on their – on the 38 – Section 38(f) notification process?
ASSISTANT SECRETARY SHAPIRO: In response to your question, I’m not going to give you a precise estimate of how many will be published, because we do want to consult with Congress. And this will be a dialogue with Congress, and we want to make sure we have – take their concerns into account as we’re going through this system. And we intend to have robust consultations with Congress before we issue 38(f) notifications.
In terms of the timing, my view is by January of next year we’ll either be done or we’ll be so close to the goal line that it’ll just be up to the next administration to dive over the goal line and do a touchdown dance.
MR. TONER: Great, thank you. And I think it’s going to have to be our last question, unfortunately.
OPERATOR: And our last question comes from Jim Berger with Washington Trade Daily.
QUESTION: Yeah. Thank you. I guess – I don’t know – I don’t think you answered the second part of the previous question, but have you worked out a system with Congress on notifying as the products move from the Munitions List to the CCL? As I understand it, it’s such a large number, it’s very impractical to do it one by one.
ASSISTANT SECRETARY SHAPRIO: We’ve discussed – we are having discussion with Congress on each of the categories as they come up. And our goal, as I mentioned, is to have robust consultations with Congress. And we intend to follow the law regarding Congressional notification. And so we will provide the requisite notification for any of these changes to the United States Munitions List or Commerce Control List.
But this is – again, this is an iterative process. We are having discussions with Congress on a continuing basis about how best to provide them the information they need and solicit their input.
QUESTION: Thank you.
MR. TONER: Well, thank you all for joining us. And thanks certainly to Assistant Secretary Shapiro. Hope it was informative, and have a great afternoon.
PRN: 2012/990
TOP-SECRET – Former NYPD Officer Sentenced to 57 Months for Extortion and Criminal Civil Rights Violation
Earlier today, former New York City Police Officer Michael Daragjati was sentenced to nine months of imprisonment for violating the civil rights of an African-American man by falsely charging him with a crime, and a consecutive sentence of 48 months for threatening and assaulting another man whom Daragjati thought had stolen his snowplow equipment. The sentencing proceeding took place before United States District Judge William F. Kuntz, II.
The sentence was announced by Loretta E. Lynch, United States Attorney for the Eastern District of New York; Janice K. Fedarcyk, Assistant Director in Charge, Federal Bureau of Investigation, New York Field Office; and Raymond W. Kelly, Commissioner, New York City Police Department.
Daragjati was arrested on October 17, 2011 and has remained in custody since then. On January 24, 2012, Daragjati pleaded guilty to extortion and willfully violating the civil rights of the African-American victim.
As detailed in the sentencing letter filed by the government on June 20, 2012, on April 15, 2011, Daragjati falsely arrested an African-American man in Staten Island and fabricated charges against him, keeping the victim in jail for nearly two days. Soon after the incident, Daragjati was recorded telling a friend on the telephone that he had just “fried another n——-.” As also detailed in the government’s sentencing letter, on March 4, 2011, Daragjati and a group of associates assaulted and threatened a man in Staten Island in retaliation for the victim allegedly stealing Daragjati’s snowplow equipment. Daragjati later threatened to commit further acts of violence against the second victim if he went to the authorities.
“The sentence imposed today reflects the seriousness of the crimes committed by a former police officer—false arrest and imprisonment motivated by racial animus and engaging in vigilante justice. Crimes such as these erode the public’s confidence in our system of justice and will be met by the full resources of this office,” stated United States Attorney Lynch. Ms. Lynch expressed her grateful appreciation to the FBI and the NYPD Internal Affairs Bureau, the agencies responsible for leading the government’s investigation, and thanked the Richmond County District Attorney’s Office for its assistance.
The government’s case is being prosecuted by Assistant United States Attorney Paul Tuchmann.
Name Rank Serial Killer – Full Movie
FEMEN – Ukrainian Activists Go Topless In Prostitution Protest
TOP-SECRET from the NSA – Update: The Guatemalan Death Squad Diary and the Right to Truth
Washington, D.C., June 24, 2012 – On April 25, 2012, Kate Doyle, senior analyst and director of the Guatemala Documentation Project at the National Security Archive, provided expert witness testimony before the Inter-American Court of Human Rights in the case of the Diario Militar (Case 12.590, Gudiel Álvarez et al. (Diario Militar) vs. Guatemala) during the Court’s 45th Extraordinary Session held in Guayaquil, Ecuador. Doyle’s prepared testimony was followed by questioning by the Petitioners’ legal representatives, and nearly 45 minutes of questioning by the seven judges. The representatives for the State chose to not ask questions.
The following text is an excerpt of Doyle’s testimony. Slides referenced in testimony can be found in a copy of the power point presentation (9.08 MB).
25 April 2012
Guayaquil, Ecuador
To begin, the State of Guatemala has systematically hidden the information in its power about the internal armed conflict. The Guatemalan Army, the Police and the intelligence services are intrinsically opaque, secretive and closed institutions, and it has been almost impossible to gain access to their records. This policy of silence has survived the peace accords; it has survived the Historical Clarification Commission; and it continues today – despite the discovery of archives, the exhumations of clandestine cemeteries, the criminal convictions of perpetrators of human rights violations, and the unceasing demand for information by families of the disappeared.
In the 1980s, the State’s counterinsurgency strategy to kidnap, secretly detain, torture and execute men and women because of their political activities mobilized family members desperate to learn of the whereabouts of their loved ones. [SLIDE 1] They not only searched in hospitals, jails, cemeteries and morgues; they also directly confronted military officials and the chief of State. But the response was always the same: silence, ridicule, threats or worse.
That was also the experience of the Historical Clarification Commission (Comisión para el Esclarecimiento Histórico-CEH), [SLIDE 2], which from its earliest days tried to obtain information from State security agencies, but without success. I worked in collaboration with the commissioners and was witness to their frustration before the government’s repeated refusals to provide access to their archives. It had such an impact that in the final (twelfth) volume of their report the CEH reproduced dozens of letters between the three commissioners and the high command of the security institutions; letters that capture their exasperation in trying to obtain documents. [SLIDE 3] The letters also capture the implacable response of the authorities: No. There were no documents, documents did not exist, they had been destroyed, they had been lost, or they remained under the seal of national security.
During the very same week in which the CEH report was made public, in February 1999, the Military Logbook appeared. [SLIDE 4] The document was turned over to me and I made it public three months later in a press conference in Washington. It was exactly the kind of information sought repeatedly by the CEH, without success.
It was not until four years later that the first records of the Guatemalan Army emerged, with the dismantling of the Presidential General Staff ( Estado Mayor Presidencial-EMP) in 2003. It was a purged and fragmentary collection, and only recovered through the efforts of non-governmental organizations that insisted on copying them. Later the Human Rights Ombudsman (Procurador de Derechos Humanos-PDH) asked my organization to create a data base of the documents in order to facilitate access to them, but as far as I know there is still no public access to the database or the documents themselves.
We had our first real glimpse inside the State security apparatus during the conflict when the archives of the National Police were discovered in 2005. In fact employees of the PDH found them by accident during a visit to a police base in Guatemala City. [SLIDE 5] The accumulation of millions of pages of records was in a condition of extreme deterioration and abandon, hidden inside poorly maintained storage spaces. But after years of work to rescue, clean, organize and scan the documents, the archive is now fully accessible to the Guatemalan public without limit or restriction.
The Historical Archive of the National Police (Archivo Histórico de la Policía Nacional-AHPN) represents the entire documentary history generated by the National Police during more than 100 years. It contains an estimated eight linear kilometers of paper, videos, audiotapes, photographs, license plates, books and the ephemera of the revolutionary groups. Within the collection is every type of documentation: military and police plans for counterinsurgency operations [SLIDE 6], orders from the Director, political files on individuals [SLIDE 7], surveillance reports, interrogation transcripts [SLIDE 8], habeas corpus requests, telegrams, daily reports, circulars – many with the names and signatures of the officers in charge [SLIDE 9]. In short, it represents all of the paper necessary in order to make possible the flow of communications among the different National Police corps, and between the Police and other entities of the State, including the chief of State and the Army. To date, 2,530 documents have been found inside the AHPN with a direct relation to the captures registered in the Military Logbook.
Before the discovery of the archives, neither the families of the disappeared nor the CEH received a single page of these documents, despite their petitions to the State.
Today the Guatemalan Army’s policy of access regarding its own records continues to be a policy of denial. In 2009, the Defense Ministry responded to a judicial order that required it to produce four military documents as evidence in the genocide case, but it turned over only one complete record. The Ministry alleged that the others – including a key set of records relating to the 1982 counterinsurgency sweep called “Operation Sofía” – did not exist in its archives [SLIDE 10].
One month later, a person who requested anonymity gave me a package that contained the Operation Sofía documents, which I subsequently turned over to the Guatemalan Public Ministry. And that is how, in a national judicial process concerning crimes against humanity initiated in 2001, the petitioners did receive a Guatemalan document containing critical evidence – not from the institutions of the State that created it, but through my organization, a non-governmental group based in the United States.
Most recently, the Army responded to society’s demand for truth by opening a collection of “military archives” in June 2011. I have studied the archive – an unnecessarily difficult task, due to the lack of any index or guide – and I see no relevance in the documents to the study of the armed conflict. It is an apparently arbitrary collection, without any evident or transparent logic to its declassification, which contains thousands of pages of trivial and useless records that do not serve human rights investigators. Furthermore, according to the Ministry of Defense, there are no declassified records in the archive covering the most repressive period of the internal conflict, 1980-85.
The Army’s posture – and the legacy of silence about historic repression on the part of the State – has left survivors of the conflict and the family members of victims with less than nothing, with expectations raised by a peace process that to date has not resulted with the fundamental information they require: What happened and why? Who is responsible? And where are the disappeared?
Thank you.
Watch the recording of the Diario Militar hearing in three parts here, (in Spanish):
Playing With Fire – Full Movie
Unveiled – Euro 2012 Prostitution Focus in Ukraine
SECRET from Cryptome – Prez Orders Broadband Expansion Speed-Up
[Federal Register Volume 77, Number 119 (Wednesday, June 20, 2012)] [Presidential Documents] [Pages 36903-36906] From the Federal Register Online via the Government Printing Office [www.gpo.gov] [FR Doc No: 2012-15183] Presidential Documents Federal Register / Vol. 77, No. 119 / Wednesday, June 20, 2012 / Presidential Documents [[Page 36903]] Executive Order 13616 of June 14, 2012 Accelerating Broadband Infrastructure Deployment By the authority vested in me as President by the Constitution and the laws of the United States of America, including section 301 of title 3, United States Code, and in order to facilitate broadband deployment on Federal lands, buildings, and rights of way, federally assisted highways, and tribal and individual Indian trust lands (tribal lands), particularly in underserved communities, it is hereby ordered as follows: Section 1. Policy. Broadband access is essential to the Nation's global competitiveness in the 21st century, driving job creation, promoting innovation, and expanding markets for American businesses. Broadband access also affords public safety agencies the opportunity for greater levels of effectiveness and interoperability. While broadband infrastructure has been deployed in a vast majority of communities across the country, today too many areas still lack adequate access to this crucial resource. For these areas, decisions on access to Federal property and rights of way can be essential to the deployment of both wired and wireless broadband infrastructure. The Federal Government controls nearly 30 percent of all land in the United States, owns thousands of buildings, and provides substantial funding for State and local transportation infrastructure, creating significant opportunities for executive departments and agencies (agencies) to help expand broadband infrastructure. Sec. 2. Broadband Deployment on Federal Property Working Group. (a) In order to ensure a coordinated and consistent approach in implementing agency procedures, requirements, and policies related to access to Federal lands, buildings, and rights of way, federally assisted highways, and tribal lands to advance broadband deployment, there is established a Broadband Deployment on Federal Property Working Group (Working Group), to be co-chaired by representatives designated by the Administrator of General Services and the Secretary of Homeland Security (Co-Chairs) from their respective agencies, in consultation with the Director of the Office of Science and Technology Policy (Director) and in coordination with the Chief Performance Officer (CPO). (b) The Working Group shall be composed of: (i) a representative from each of the following agencies, and the Co- Chairs, all of which have significant ownership of, or responsibility for managing, Federal lands, buildings, and rights of way, federally assisted highways, and tribal lands (Broadband Member Agencies): (1) the Department of Defense; (2) the Department of the Interior; (3) the Department of Agriculture; (4) the Department of Commerce; (5) the Department of Transportation; (6) the Department of Veterans Affairs; and (7) the United States Postal Service; (ii) a representative from each of the following agencies or offices, to provide advice and assistance: [[Page 36904]] (1) the Federal Communications Commission; (2) the Council on Environmental Quality; (3) the Advisory Council on Historic Preservation; and (4) the National Security Staff; and (iii) representatives from such other agencies or offices as the Co-Chairs may invite to participate. (c) Within 1 year of the date of this order, the Working Group shall report to the Steering Committee on Federal Infrastructure Permitting and Review Process Improvement, established pursuant to Executive Order 13604 of March 22, 2012 (Improving Performance of Federal Permitting and Review of Infrastructure Projects), on the progress that has been made in implementing the actions mandated by sections 3 through 5 of this order. Sec. 3. Coordinating Consistent and Efficient Federal Broadband Procedures, Requirements, and Policies. (a) Each Broadband Member Agency, following coordination with other Broadband Member Agencies and interested non-member agencies, shall: (i) develop and implement a strategy to facilitate the timely and efficient deployment of broadband facilities on Federal lands, buildings, and rights of way, federally assisted highways, and tribal lands, that: (1) ensures a consistent approach across the Federal Government that facilitates broadband deployment processes and decisions, including by: avoiding duplicative reviews; coordinating review processes; providing clear notice of all application and other requirements; ensuring consistent interpretation and application of all procedures, requirements, and policies; supporting decisions on deployment of broadband service to those living on tribal lands consistent with existing statutes, treaties, and trust responsibilities; and ensuring the public availability of current information on these matters; (2) where beneficial and appropriate, includes procedures for coordination with State, local, and tribal governments, and other appropriate entities; (3) is coordinated with appropriate external stakeholders, as determined by each Broadband Member Agency, prior to implementation; and (4) is provided to the Co-Chairs within 180 days of the date of this order; and (ii) provide comprehensive and current information on accessing Federal lands, buildings, and rights of way, federally assisted highways, and tribal lands for the deployment of broadband facilities, and develop strategies to increase the usefulness and accessibility of this information, including ensuring such information is available online and in a format that is compatible with appropriate Government websites, such as the Federal Infrastructure Projects Dashboard created pursuant to my memorandum of August 31, 2011 (Speeding Infrastructure Development Through More Efficient and Effective Permitting and Environmental Review). (b) The activities conducted pursuant to subsection (a) of this section, particularly with respect to the establishment of timelines for permitting and review processes, shall be consistent with Executive Order 13604 and with the Federal Plan and Agency Plans to be developed pursuant to that order. (c) The Co-Chairs, in consultation with the Director and in coordination with the CPO, shall coordinate, review, and monitor the development and implementation of the strategies required by paragraph (a)(i) of this section. (d) Broadband Member Agencies may limit the information made available pursuant to paragraph (a)(ii) of this section as appropriate to accommodate national security, public safety, and privacy concerns. Sec. 4. Contracts, Applications, and Permits. (a) Section 6409 of the Middle Class Tax Relief and Job Creation Act of 2012 (Public Law 112-96) contains provisions addressing access to Federal property for the deployment of wireless broadband facilities, including requirements that the General Services [[Page 36905]] Administration (GSA) develop application forms, master contracts, and fees for such access. The GSA shall consult with the Working Group in developing these application forms, master contracts, and fees. (b) To the extent not already addressed by section 6409, each Broadband Member Agency with responsibility for managing Federal lands, buildings, or rights of way (as determined by the Co-Chairs) shall, in coordination with the Working Group and within 1 year of the date of this order, develop and use one or more templates for uniform contract, application, and permit terms to facilitate nongovernment entities' use of Federal property for the deployment of broadband facilities. The templates shall, where appropriate, allow for access by multiple broadband service providers and public safety entities. To ensure a consistent approach across the Federal Government and different broadband technologies, the templates shall, to the extent practicable and efficient, provide equal access to Federal property for the deployment of wireline and wireless facilities. Sec. 5. Deployment of Conduit for Broadband Facilities in Conjunction with Federal or Federally Assisted Highway Construction. (a) The installation of underground fiber conduit along highway and roadway rights of way can improve traffic flow and safety through implementation of intelligent transportation systems (ITS) and reduce the cost of future broadband deployment. Accordingly, within 1 year of the date of this order: (i) the Department of Transportation, in consultation with the Working Group, shall review dig once requirements in its existing programs and implement a flexible set of best practices that can accommodate changes in broadband technology and minimize excavations consistent with competitive broadband deployment; (ii) the Department of Transportation shall work with State and local governments to help them develop and implement best practices on such matters as establishing dig once requirements, effectively using private investment in State ITS infrastructure, determining fair market value for rights of way on federally assisted highways, and reestablishing any highway assets disturbed by installation; (iii) the Department of the Interior and other Broadband Member Agencies with responsibility for federally owned highways and rights of way on tribal lands (as determined by the Co-Chairs) shall revise their procedures, requirements, and policies to include the use of dig once requirements and similar policies to encourage the deployment of broadband infrastructure in conjunction with Federal highway construction, as well as to provide for the reestablishment of any highway assets disturbed by installation; (iv) the Department of Transportation, after outreach to relevant nonfederal stakeholders, shall review and, if necessary, revise its guidance to State departments of transportation on allowing for-profit or other entities to accommodate or construct, safely and securely maintain, and utilize broadband facilities on State and locally owned rights of way in order to reflect changes in broadband technologies and markets and to promote competitive broadband infrastructure deployment; and (v) the Department of Transportation, in consultation with the Working Group and the American Association of State Highway and Transportation Officials, shall create an online platform that States and counties may use to aggregate and make publicly available their rights of way laws and joint occupancy guidelines and agreements. (b) For the purposes of this section, the term ``dig once requirements'' means requirements designed to reduce the number and scale of repeated excavations for the installation and maintenance of broadband facilities in rights of way. Sec. 6. General Provisions. (a) This order shall be implemented consistent with all applicable laws, treaties, and trust obligations, and subject to the availability of appropriations. [[Page 36906]] (b) Nothing in this order shall be construed to impair or otherwise affect: (i) the authority granted by law to an executive department, agency, or the head thereof; or (ii) the functions of the Director of the Office of Management and Budget relating to budgetary, administrative, or legislative proposals. (c) Independent agencies are strongly encouraged to comply with this order. (d) This order is not intended to, and does not, create any right or benefit, substantive or procedural, enforceable at law or in equity by any party against the United States, its departments, agencies, or entities, its officers, employees, or agents, or any other person. (Presidential Sig.) THE WHITE HOUSE, Washington, June 14, 2012. [FR Doc. 2012-15183 Filed 6-19-12; 8:45 am] Billing code 3295-F2-P
TOP-SECRET – DHS-FBI Bulletin: Terrorist Interest in Attacking Theaters and Mass Gatherings

(U//FOUO) An early April 2012 suicide bombing of a theater in Somalia and a violent extremist communication advocating attacks on US theaters highlight terrorists’ continued interest in attacking such venues. Although we have no specific or credible information indicating that terrorists plan to attack theaters in the United States, terrorists may seek to emulate overseas attacks on theaters here in the United States because they have the potential to inflict mass casualties and cause local economic damage.
— (U//FOUO) On 4 April 2012, an al-Shabaab female suicide bomber detonated explosives at the National Theater in Mogadishu, Somalia during a speech by the Somali Prime Minister attended by multiple cabinet members. The bomber blended in with the audience until her attack, which targeted the VIPs in attendance.
— (U//FOUO) On 7 April 2012, an al-Qa‘ida-linked violent extremist urged others to emulate the 2002 Moscow theater hostage attack—in which Chechen terrorists seized the Dubrovka Theater and held over 800 people captive for three days until Russian security forces gassed the theater—by seizing crowded facilities in the United States, including movie theaters; taking hostages; and demanding the release of captured al-Qa‘ida-linked or -inspired violent extremists.
(U//FOUO) These recent instances demonstrate that mass gatherings such as those associated with theaters likely remain attractive terrorist targets. We encourage facility owners and operators, security personnel, and first responders to remain vigilant and report suspicious activities and behaviors that may indicate a potential attack.
(U//FOUO) Potential Suspicious Activity Indicators
— (U//FOUO) Persons in crowded areas wearing clothing that is unusually bulky or atypical for the season, possibly to conceal suicide explosives or weapons.
— (U//FOUO) Persons asking about theater security screening and evacuation procedures.
— (U//FOUO) Packages—possibly containing explosives—left unattended in open areas or hidden in trash receptacles, lockers, or similar containers.
— (U//FOUO) Suspicious or illegally parked vehicles near a theater or where crowds gather prior to or following performances and events.
Megapark 2012 – Sexy Russian Football Girls posing for C-Cup – Fussball EM – UEFA EURO 2012
TOP-SECRET from Cryptome – Julian Assange Casa Ecuador Embassy London
Julian Assange Casa Ecuador Embassy London
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict22.jpg)
A woman poses for a candid photograph alongside a protester wearing a Guy Fawkes mask and holding a sign reading ‘I’m Julian’ as he demonstrates outside the Ecuadorian embassy in London, on June 23, 2012, where Wikileaks founder Julian Assange is seeking political asylum. Ecuador today recalled its ambassador to Britain to discuss what to do about WikiLeaks founder Julian Assange, who has sought refuge in their diplomatic mission in London. Assange, an Australian national, sought refuge in the Ecuadoran embassy on June 19 and asked Quito to give him asylum as he seeks to avoid extradition to Sweden on allegations of rape, fearing Stockholm will turn him over to the United States. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict23.jpg)
Women walk past protest placards outside the Ecuadorian embassy in London, on June 23, 2012, where supporters of Wikileaks founder Julian Assange gathered to demonstrate. Ecuador today recalled its ambassador to Britain to discuss what to do about WikiLeaks founder Julian Assange, who has sought refuge in their diplomatic mission in London. Assange, an Australian national, sought refuge in the Ecuadoran embassy on June 19 and asked Quito to give him asylum as he seeks to avoid extradition to Sweden on allegations of rape, fearing Stockholm will turn him over to the United States. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict25.jpg)
Photographers take pictures of protesters showing their support for Julian Assange outside the Ecuadorian embassy on June 22, 2012 in London, England. Julian Assange, the founder of the WikiLeaks whistle-blowing website, has sought refuge in Ecuador’s London embassy to prevent him from being extradited to Sweden on allegations of rape and assault. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict26.jpg)
Protesters show their support for Julian Assange outside the Ecuadorian embassy on June 22, 2012 in London, England. Julian Assange, the founder of the WikiLeaks whistle-blowing website, has sought refuge in Ecuador’s London embassy to prevent him from being extradited to Sweden on allegations of rape and assault. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict27.jpg)
A British police officer stands guard outside the Ecuadorian Embassy, in London, Friday, June 22, 2012. WikiLeaks founder Julian Assange entered the embassy on Monday in an attempt to gain political asylum to prevent him from being extradited to Sweden to face allegations of sex crimes, which he denies. In a telephone interview with the Australian Broadcasting Corporation (ABC) from inside the embassy, the 40-year-old Australian said he did not know when the decision about his plea for asylum would be made. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict24.jpg)
A man reads a book in front of a demonstration outside the Ecuadorian embassy in London, on June 22, 2012, where Wikileaks founder Julian Assange is seeking political asylum. President Rafael Correa said Ecuador would discuss WikiLeaks founder Julian Assange’s bid for asylum with other countries and did not want to ‘offend anyone,’ including Britain. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict21.jpg)
Sarah Saunders, a personal friend and contributor toward the bail of WikiLeaks founder Julian Assange, speaks to the media outside the Ecuadorian embassy in central London on June 21, 2012, where Assange is still holed up seeking political asylum. Assange will remain inside Ecuador’s embassy in London until his case is resolved, in a process that could take ‘hours or days’, a spokesman for the whistleblower website said June 21. Assange, 40, turned up in the embassy on June 19 and sought asylum in a dramatic bid to avoid extradition to Sweden over allegations of rape and sexual assault. Getty [Assange was reportedly housed most recently at the rural home of Sarah Saunders, a successful caterer.]
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/assange-ambassador.jpg)
Ecuadorian ambassador to London Ana Alban gets out of a car as she arrives at the embassy in central London on June 21, 2012 where Wikileaks founder Julian Assange is holed up while Ecuador consider his application for asylum. Ecuador’s president said Thursday his government would take its time in deciding whether to grant asylum to Julian Assange as the WikiLeaks founder spent a second night at its embassy in London. The 40-year-old Australian sparked a stand-off with British police after he turned up in the embassy on June 19 and asked for asylum in a dramatic bid to avoid extradition to Sweden over allegations of rape and sexual assault. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict18.jpg)
Police stand guard outside the Ecuadorian Embassy, London, Wednesday June 20, 2012. WikiLeaks chief Julian Assange has made a run for the Ecuadorean Embassy in London, seeking asylum in a long shot move that, if successful, would place him in a small, friendly South American country rather than in Sweden facing questioning about alleged sex crimes. Tuesday’s unexpected caper has added a new and bizarre twist to Assange’s increasingly desperate bid to avoid extradition to Scandinavia. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict19.jpg)
Police patrol outside the Ecuadorian Embassy, London, Wednesday June 20, 2012. WikiLeaks chief Julian Assange has made a run for the Ecuadorean Embassy in London, seeking asylum in a long shot move that, if successful, would place him in a small, friendly South American country rather than in Sweden facing questioning about alleged sex crimes.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict20.jpg)
Police officers stand outside Ecuador’s embassy in London June 20, 2012. WikiLeaks’ founder Julian Assange has taken refuge in Ecuador’s embassy in London and asked for asylum, officials said on Tuesday, in a last-ditch bid to avoid extradition to Sweden over sex crime accusations. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict17.jpg)
Police officers stand outside the Ecuadorian embassy in London Wednesday June 20, 2012 where the Wikileaks founder Julian Assange is seeking political asylum. Assange has made a run for the Ecuadorean Embassy in London, seeking asylum in a long shot move that, if successful, would place him in a small, friendly South American country rather than in Sweden facing questioning about alleged sex crimes. Tuesday’s unexpected caper has added a new and bizarre twist to Assange’s increasingly desperate bid to avoid extradition to Scandinavia. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict13.jpg)
Supporters of WikiLeaks Founder Julian Assange gather outside Ecuador’s Embassy in central London June 20, 2012. Assange has taken refuge in Ecuador’s embassy in London and asked for asylum, officials said on Tuesday, in a last-ditch bid to avoid extradition to Sweden over sex crime accusations. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict14.jpg)
Television crews and journalists gather outside the Ecuadorian Embassy (Background) in central London, on June 20, 2012, where Wikileaks founder Julian Assange is seeking political asylum as he fights extradition to Sweden over alleged sex crimes. Assange, who has sought political asylum inside the Ecuadorian embassy in London, has breached bail conditions and is subject to arrest, British police said Wednesday. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict15.jpg)
Supporters of Wikileaks founder Julian Assange rally with placards outside Ecuador’s embassy in central London on June 20, 2012, where Assange is seeking political asylum as he fights extradition to Sweden over alleged sex crimes. Assange, who last week exhausted all his legal options in Britain, walked into the embassy on June 19 and applied for political asylum, as time ran out in his marathon legal battle to avoid being sent to Sweden. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict16.jpg)
Demonstrators protest outside the Ecuadorian consulate on June 20, 2012 in London, England. Wikileaks Founder Julian Assange has sought asylum at the Ecuadorian embassy in Knightsbridge as he continues to fight against his possible extradition to Sweden over alleged sex crimes. Getty
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict2.jpg)
Ecuador’s Minister of Foreign Affairs Ricardo Patino (C), Vice Minister of Foreign Affairs Marco Albuja (R) and Undersecretary for North America and Europe, Paul Villagomez attend a news conference regarding WikiLeaks’ founder Julian Assange in Quito June 19, 2012. Assange is seeking asylum in Ecuador after arriving at the South American nation’s embassy in London, Ecuador’s foreign minister said on Tuesday, a move that may help the self-styled anti-secrecy crusader avoid extradition to Sweden. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict3.jpg)
Members of the media gather outside Ecuador’s embassy where Wikileaks founder Julian Assange has sought political asylum, in London June 19, 2012. Assange is seeking asylum in Ecuador after arriving at the South American nation’s embassy in London, Ecuador’s foreign minister said on Tuesday, a move that may help the self-styled anti-secrecy crusader avoid extradition to Sweden. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict4.jpg)
Members of the media gather outside Ecuador’s embassy where WikiLeaks founder Julian Assange has sought political asylum, in London June 19, 2012. Assange is seeking asylum in Ecuador after arriving at the South American nation’s embassy in London, Ecuador’s foreign minister said on Tuesday, a move that may help the self-styled anti-secrecy crusader avoid extradition to Sweden. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict0.jpg)
A police officer gestures outside Ecuador’s embassy where WikiLeaks founder Julian Assange has sought political asylum, in London June 19, 2012. Assange is seeking asylum in Ecuador after arriving at the South American nation’s embassy in London, Ecuador’s foreign minister said on Tuesday, a move that may help the self-styled anti-secrecy crusader avoid extradition to Sweden. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict1.jpg)
A police officer leaves Ecuador’s embassy where WikiLeaks founder Julian Assange has sought political asylum, in London June 19, 2012. Assange is seeking asylum in Ecuador after arriving at the South American nation’s embassy in London, Ecuador’s foreign minister said on Tuesday, a move that may help the self-styled anti-secrecy crusader avoid extradition to Sweden. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict5.jpg)
Police officers stand outside Ecuador’s embassy where WikiLeaks founder Julian Assange has sought political asylum, in London June 19, 2012. Assange is seeking asylum in Ecuador after arriving at the South American nation’s embassy in London, Ecuador’s foreign minister said on Tuesday, a move that may help the self-styled anti-secrecy crusader avoid extradition to Sweden. Reuters
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict6.jpg)
Two men walk out of the Embassy of Ecuador in London, carrying legal books about diplomatic law , in London Tuesday, June 19, 2012. Embattled WikiLeaks chief Julian Assange took refuge Tuesday in Ecuador s embassy in London and is seeking political asylum, his organization and the South American nation s foreign minister said. Foreign Minister Ricardo Patino said the leftist government of President Rafael Correa was weighing the request. He did not indicate when a decision might be made. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict7.jpg)
A general view of the Embassy of Ecuador in London Tuesday, June 19, 2012. Embattled WikiLeaks chief Julian Assange took refuge Tuesday in Ecuador s embassy in London and is seeking political asylum, his organization and the South American nation s foreign minister said. Foreign Minister Ricardo Patino said the leftist government of President Rafael Correa was weighing the request. He did not indicate when a decision might be made. AP
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict9.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/assange-casa/pict12.jpg)
FEMEN – Euro 2012 Prostitution
TOP-SECRET – Open Source Center Master Narratives Report: Muslim Communities of France

Understanding master narratives can be the difference between analytic anticipation and unwanted surprise, as well as the difference between communications successes and messaging gaffes. Master narratives are the historically grounded stories that reflect a community’s identity and experiences, or explain its hopes, aspirations, and concerns. These narratives help groups understand who they are and where they come from, and how to make sense of unfolding developments around them. As they do in all countries, effective communicators in France speaking to Muslim communities invoke master narratives in order to move audiences in a preferred direction. French influencers rely on their native familiarity with these master narratives to use them effectively. This task is considerably more challenging for US communicators and analysts because they must place themselves in the mindset of foreign audiences who believe stories that — from an American vantage point — may appear surprising, conspiratorial, or even outlandish.
This report serves as a resource for addressing this challenge in two ways. First, it surfaces a set of nine master narratives carefully selected based on their potency in the context of France’s Muslim communities, and their relevance to US strategic interests. Second, this report follows a consistent structure for articulating these narratives and explicitly identifies initial implications for US communicators and analysts. The set outlined here is not exhaustive: these nine master narratives represent a first step that communicators and analysts can efficiently apply to the specific messaging need or analytic question at hand. For seasoned experts on French Muslim communities, these narratives will already be familiar — the content contained in this report can be used to help check assumptions, surface tacit knowledge, and aid customer communications. For newcomers to European Islam accounts, these narratives offer deep insights into the stories and perceptions that shape French Muslim identity and worldviews that may otherwise take years to accumulate.
Some master narratives cut across broad stretches of the French Muslim populace, while others are held only by particular audience sub-segments. This study divides France’s Muslim communities into eight audience sub-segments that demonstrate how different master narratives resonate with different sections of the populace. Each of the nine master narratives aligns with one or more of the following segments: Cultural Muslims, Personal Practitioners, Civic Islamists, Wealthy Secularists, Old Guard, Strict Practitioners, Young Banlieuesards, and Indigènes (see the Appendix for a detailed description of these audience segments).
…
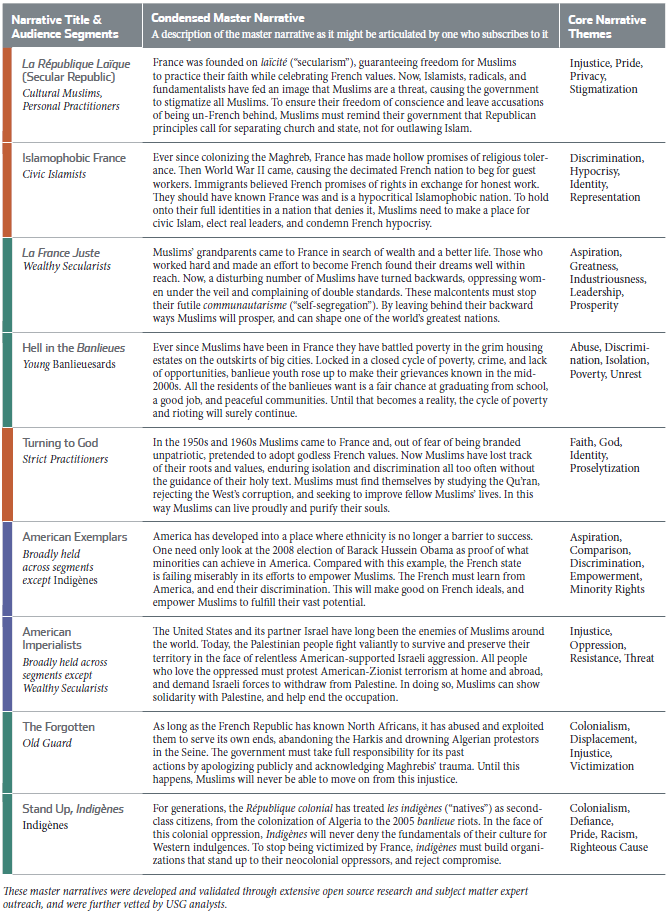
DOWNLOAD THE ORIGINAL DOCUMENT HERE
SECRET – FBI Releases 2011 Bank Crime Statistics
Today, the FBI released bank crime statistics for calendar year 2011. Between January 1, 2011 and December 31, 2011, there were 5,014 robberies, 60 burglaries, 12 larcenies, and seven extortions of financial institutions1 reported to law enforcement. The total 5,093 reported violations represent a decrease from 2010, during which 5,641 violations of the Federal Bank Robbery and Incidental Crimes Statute were reported.
Highlights of the report include:
- Of the 5,086 total reported bank robberies, burglaries, and larcenies, loot was taken in 4,534 incidents (89 percent). Loot was taken during two of the seven reported bank extortions.
- The total amount taken was valued at more than $38 million. More than $8 million was recovered and returned to financial institutions.
- During the reported bank robberies, burglaries, and larcenies, the following modus operandi were the most common: demand note (2,958 incidents); oral demand (2,678 incidents); weapon threatened (2,331 incidents); and firearm used (1,242 incidents). Of the seven reported extortions, perpetrators used or threatened the use of explosive devices during one incident and made threats by telephone during four incidents.2
- Acts of violence were committed during 201 of the reported robberies, burglaries, and larcenies. These acts included 70 instances involving the discharge of firearms, 116 instances involving assaults, and one instance involving an explosive device.3 No acts of violence occurred during the seven reported bank extortions.
- Acts of violence during the reported robberis, burglaries, and larcenies resulted in 88 injuries, 13 deaths, and 30 persons being taken hostage. No injuries, deaths, or hostage takings occurred during the reported bank extortions.
- Most violations occurred on Friday. Regardless of the day of the week, violations between the hours of 9:00 a.m. and 11:00 a.m. were the most common.
- Most violations occurred in the Southern region of the U.S., with 1,576 reported incidents.
These statistics were recorded as of April 24, 2012. Note that not all bank crimes are reported to the FBI, and therefore the report is not a complete statistical compilation of all bank crimes that occurred in the United States.
1 Financial institutions include commercial banks, mutual savings banks, savings and loan associations, and credit unions.
2 More than one modus operandi may have been used during an incident
3 One or more acts of violence may occur during an incident.
Chasing the Barefoot Bandit – Full Movie
TOP-SECRET – Open Source Center Master Narratives Country Report: Somalia

Understanding master narratives can be the difference between analytic anticipation and unwanted surprise, as well as the difference between communications successes and messaging gaffes. Master narratives are the historically grounded stories that reflect a community’s identity and experiences, or explain its hopes, aspirations, and concerns. These narratives help groups understand who they are and where they come from, and how to make sense of unfolding developments around them. As they do in all countries, effective communicators in Somalia invoke master narratives in order to move audiences in a preferred direction. Somali influencers rely on their native familiarity with these master narratives to use them effectively. This task is considerably more challenging for US communicators and analysts because they must place themselves in the mindset of foreign audiences who believe stories that — from an American vantage point — may appear surprising, conspiratorial, or even outlandish.
This report serves as a resource for addressing this challenge in two ways. First, it surfaces a set of eight master narratives carefully selected based on their potency in the Somali context and relevance to US strategic interests. Second, this report follows a consistent structure for articulating these narratives and explicitly identifies initial implications for US communicators and analysts. The set outlined here is not exhaustive: these eight master narratives represent a first step that communicators and analysts can efficiently apply to the specific messaging need or analytic question at hand. For seasoned Somali experts, these narratives will already be familiar — the content contained in this report can be used to help check assumptions, surface tacit knowledge, and aid customer communications. For newcomers to Somalia accounts, these narratives offer deep insights into the stories and perceptions that shape the Somali political context that may otherwise take years to accumulate.
Some master narratives cut across broad stretches of the Somali populace, while others are held only by particular audience segments. This study divides Somalia into six audience segments that demonstrate how different master narratives resonate with different sections of the populace. Each of the eight master narratives aligns with one or more of the following segments: Centralists, Regionalists, Somaliland Nationalists, Salafi Islamists, Sufi Islamists, and Moderate Islamists. (See the Appendix for a detailed description of these audience segments.) This audience segmentation is tailored specifically to surface important Somali master narratives and the interactions between them. Somali society is heavily influenced by longstanding clan structures, with some clan affiliations creating intractable intergroup conflict while other affiliations are more fluid in response to shifting political priorities. Some of the master narratives profiled in this report are deeply informed by clan dynamics, while others transcend clan allegiances altogether. Based on this, the audience segmentation is this report provides an additional lens for understanding competing and interconnected camps in Somali politics and society.
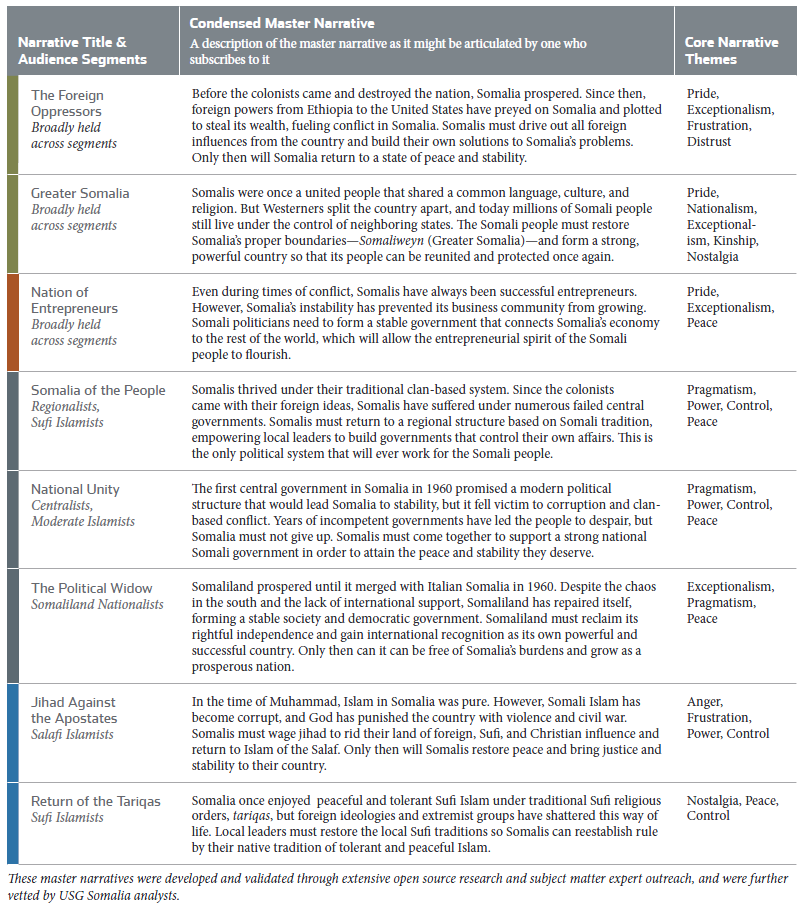
DOWNLOAD THE ORIGINAL DOCUMENT HERE
The FEMEN active in Poland – Uncensored
TOP-SECRET from the FBI – Texas Man Indicted for Threatening to Bomb Islamic Center in Murfreesboro
WASHINGTON—Javier Alan Correa, 24, of Corpus Christi, Texas, was indicted by a federal grand jury in Nashville, Tennesee, today and charged with violating the civil rights of members of a Murfreesboro, Tennessee mosque. Correa is charged in the Middle District of Tennessee with one count of intentionally obstructing by threat of force the free exercise of religious beliefs and one count of using an instrument of interstate commerce to communicate a threat to destroy a building by means of an explosive device. The indictment was announced today by Assistant Attorney General Thomas E. Perez for the Civil Rights Division; Jerry E. Martin, U.S. Attorney for the Middle District of Tennessee; and Aaron T. Ford, Special Agent in Charge of the Memphis Division of the FBI.
According to the indictment, on September 5, 2011, Correa called on a cell phone from Corpus Christi to the Islamic Center of Murfreesboro and left a threatening, explicative-ridden voice message saying, amongst other things, “On September 11, 2011, there’s going to be a bomb in the building.“
“The Department of Justice, the FBI, and our law enforcement partners intend to protect the rights afforded under the Constitution to all individuals, including the most basic right to exercise freedom of religious beliefs,” said Jerry E. Martin, U.S. Attorney of the Middle District of Tennessee. “The controversy and criminal activity surrounding the construction of this particular place of worship has impeded the ability of people to exercise that most basic right. We will continue to monitor the progress of construction and legal proceedings at the local level to insure these citizens are able to enjoy all basic liberties guaranteed under the Constitution.”
“The FBI is tasked with defending civil rights in the United States and takes very seriously its responsibilities to protect people of all religions from intimidation and violence,” said Aaron T. Ford, Special Agent in Charge of the Memphis Division of the FBI. “The FBI and our law enforcement partners pursued this investigation with great tenacity and will always strive to ensure those who attempt to take religious freedoms from others are brought to face justice.”
Correa faces a maximum penalty of 20 years for the count one and 10 years for count two of the indictment, as well as a fine of up to $250,000 for each offense.
This case was investigated by the FBI and is being prosecuted by Assistant U.S. Attorney Lee Deneke and Civil Rights Division Trial Attorney Adriana Vieco.
An indictment is merely an accusation. All persons are presumed innocent unless and until proven guilty and have the right to a trial, at which, the government must bear the burden of proof beyond a reasonable doubt.
Megapark 2012 – Micaela Schaefer | Fussball EM C-Cup | Mallorca GER-NED Deutschland Holland
The Shocking Truth – Nigel Farage: “Listen! The Whole Thing’s a Giant Ponzi Scheme!”
U.K. Independence Party Leader Nigel Farage on the causes of the financial crisis in Europe.
*You know an interview is gonna be good when it starts with Farage calling Barroso a deluded idiot and communist supporter of Mao.*
TOP-SECRET – Public Intelligence – ITU CWG-WCIT12 US Comments on Draft Proposals
The following document details comments of the U.S. delegation on a compilation of draft proposals for modifications to International Telecommunications Regulations (ITRs) under the International Telecommunication Union. The collection of draft proposals being commented on CWG-WCIT12 TEMPORARY DOCUMENT 36 (CWG-WCIT12/TD – 36) is also available.
| CWG-WCIT12 CONTRIBUTION 45 (CWG-WCIT12/C – 45) “U.S. comments on Temporary Document 36″ | 65 pages | August 24, 2011 | Download |
Der Mord an dem DDR-Reichsbahnminister durch die STASI und Mielke – Dokument
STASI DOKUMENT kann als PDF heruntergeladen werden
Megapark 2012 – Sexy Espania Backstage! Football Girls C-Cup | BH | Fussball EM
TOP-SECRET from the FBI – Another Assault Linked to Potomac River Rapist
he Metropolitan Police Department announced today that forensic evidence from a sexual assault that occurred on July 20, 1996 in the 4900 block of MacArthur Boulevard, NW has been linked to other sexual assaults and a murder committed by a single assailant who attacked women in the Washington, DC metropolitan area.
“We are asking for the public’s help in identifying and locating this violent offender who is responsible for numerous brutal attacks,” said Police Chief Cathy L. Lanier.
The Potomac River Rapist is wanted for a total of ten sexual assaults that occurred between May 1991 and August 1998, one of which resulted in a homicide in Washington, DC.
On August, 1, 1998, Christine Mirzayan, a 28-year-old intern, was sexually assaulted and murdered while walking to her residence in the Georgetown area. During the violent attack, she was struck multiple times in the head with a rock and her body was left yards from Canal Road. The other eight sexual assaults occurred in Montgomery County, Md.
“The 1996 assault in the 4900 block of MacArthur Boulevard, NW and the murder in 1998 occurred less than two miles apart – which could indicate that the offender may have ties to this area,” said Chief Lanier.
The case is being investigated by the Metropolitan Police Department, Montgomery County, Md., Police Department, and the FBI’s Washington Field Office with assistance from the U.S. Attorney’s Office for the District of Columbia.
In the 1996 assault, the subject is described as a black or black/Hispanic male, with a light to medium complexion and high, pronounced cheekbones.
Throughout the entire investigation, he has been described as being approximately 5’8” – 6’0” in height, with a muscular build, especially in his upper body. The individual was in his late 20s to early 30s at the time of the offenses. He was wearing a polo-type shirt and khaki pants, and has been described as neatly attired.
Most of the Maryland assaults followed a particular pattern. The assailant used a “blitz” attack by throwing a blanket or towel over the victim’s head. All of the sexual assault victims, with the exception of the Washington, DC attacks, were attacked in their homes or private residences. Both the DC sexual assault and murder victims were walking on sidewalks when they were pulled into wooded areas and sexually assaulted on a Saturday night.
The dates and locations of these assaults are:
|
Date |
Approximate Time |
Subdivision |
Location |
| Monday, May 6, 1991 | 8:00 p.m. – 11:00 p.m. | Washingtonian Woods | Gaithersburg, Md. |
| Thursday, Sept. 5, 1991 | 10:00 p.m. – 10:30p.m. | Watkins Meadows | Germantown, Md. |
| Thursday, Nov. 21, 1991 | 9:00 p.m. – 10:00 p.m. | Potomac Village/Downtown | Bethesda, Md. |
| Wednesday, Dec. 11, 1991 | 8:30 p.m. – 9:00 p.m. | Quince Orchard Knolls | North Potomac, Md. |
| Friday, Jan. 24, 1992 | 9:00 p.m. | Potomac Grove | North Potomac, Md. |
| Tuesday, March 8, 1994 | 7:00 p.m. – 8:00 p.m. | Highwood | Rockville, Md. |
| Saturday, July 20, 1996 | 8:30 p.m. – 8:45 p.m. | 4900 block of MacArthur Boulevard, NW | Washington, DC |
| Wednesday, Feb. 26, 1997 | 7:00 p.m. – 8:00 p.m. | Rock Creek Manor | Rockville, Md. |
| Friday, Nov. 14, 1997 | 7:30 p.m. – 8:00 p.m. | New Hampshire Avenue/Rt. 198 | Silver Spring, Md. |
| Saturday, Aug. 1, 1998 | 10:30 p.m. – 11:00 p.m. | 3600 block Canal Road, Georgetown | Washington, D.C. |
The public is asked to review the information and consider whether they know someone who generally fits this description, who lived or had ties to the area around the times of the assaults or who may have been known to spend considerable amounts of time in those areas.
People who know the suspect may not believe that he is capable of committing these crimes. He may not necessarily have a violent criminal history. Because investigators are in possession of DNA evidence that can either positively link the suspect to his crimes or exclude innocent parties, citizens should not hesitate to provide information, even if it is just the name of a potential suspect.
Law enforcement agencies are asking anyone with information to contact MPD at (202) 727-9099 or the FBI at 1-800-CALL-FBI (1-800-225-5324). Additionally, anonymous information may be submitted to the police department’s TEXT TIP LINE by text messaging 50411.
For more information about this investigation, go to http://fbi.gov/potomacriverrapist.
Composites below are of the same assailant from two separate incidents.
Funny – Ohio Police Describe Strange Hallucinations of Bath Salts Users
Last month the Ohio State Highway Patrol partnered with the Ohio Strategic Analysis and Information Center (SAIC) to survey local police departments about their encounters with suspects under the influence of bath salts. Since its release last month, the survey has been circulated by law enforcement around the country, discussed online in forums by concerned police officers and has even begun to garner press attention for its disturbing reports of the effects of the designer drug, including superhuman strength and highly bizarre hallucinations that often result in violent behavior.
According to the survey, suspects under the influence of bath salts display symptoms of “hyperventilation, cramps, dehydration, vomiting, shaking, loss of memory” or display “rapid movement, rapid speech.” Bath salts users often appear “disoriented … pale, emaciated, jittery,” have “itchy skin” and sometimes admit to not having slept for several days. Suspects under the influence of bath salts have also been reported by witnesses as being “hostile, violent, unpredictable, out of control, paranoid, and reckless.”
One section of the report offers several examples of hallucinations and irrational behavior exhibited by suspects using bath salts:
A male, using bath salts, reported raccoons setting fire inside his home. As a result, he proceeded to destroy his home and used a hatchet to cut up his deck, while attempting to locate the fire-setting raccoons. He also believed the raccoons stole his cell phone.A male, using bath salts, believed he was being followed by police helicopters and police officers were using mirrors, snipers and different types of scopes to look through his walls. He called police requesting to negotiate with them, however there were no police at the residence when the call was made. During the course of speaking to an offender and officer reported, he yelled, “AT&T calling, may I help you, AT&T is calling, a million dollars, two black guys……it’s not a racial thing, it’s not a racial thing.”
Another incident described in the report involved a man who was on bath salts and was arrested for choking his mother after he reportedly told officers that she had been “practicing demonology” and poisoning his food. These hallucinations can be increasingly dangerous as the survey found that bath salts often make people exhibit “unusual superhuman strength” and seemingly be resistant to pain. An incident reported by Reynoldsburg Police involved the use of a Taser against a subject where the “probes penetrated in the torso of the suspect,” yet the “suspect fought through the electric current and rose to his feet.”
Of course, it is unclear how many of these incidents are truly attributable to bath salts as the report notes that in approximately 50% of these incidents other narcotics were discovered on the suspect, including Marjijuana, Cocaine and prescription medication.
FEMEN activists strip in protest against UEFA EURO 2012
Daddy’s Girl – Full Movie
TOP-SECRET from the FBI – Hogsett Announces 30-Year Sentence for Woman Guilty of Production of Child Pornography
EVANSVILLE—“As a prosecutor, and as a parent, it is difficult to put into words damage done as a result of the horrific acts committed by these two people,” said Joseph H. Hogsett, the United States Attorney, while announcing today that Emma Dell Hodge, age 44, of Evansville, was sentenced to 30 years in prison this morning by Chief United States District Judge Richard L. Young. This follows Ms. Hodge’s May 2, 2012 guilty plea to the charges of production of sexually explicit material involving minors and conspiracy to produce sexually explicit material involving minors. Today’s decision also follows the sentencing of Larry Everett Hodge, Ms. Hodge’s spouse, to 115 years in prison several weeks ago.
“Our hope is that through this prosecution and the sentences handed down by Judge Young, justice has been given to the young victim in this case and the healing process can begin,” Hogsett stated.
In November 2010, the Evansville Police Department responded to a report of child abuse from a concerned individual who had been sent images depicting the sexual abuse of a minor on her cell phone. That individual indicated that she had received the images from Larry Everett Hodge. Child abuse detectives were contacted to initiate an investigation.
Detectives went to the Hodge residence to speak with the couple, at which point it was immediately apparent that both knew about the abuse of the child, later identified as an 8-year-old female. Larry Hodge admitted in an interview with law enforcement that he had engaged in oral sex with the victim and was arrested on charges of child molestation.
The full extent of the abuse was later established during an examination of a Memorex data storage disc taken during a search of the Hodge residence. Agents identified at least seven separate digital photography sessions and two videos that were saved on the disc by Larry Hodge, all of which depicted sexual abuse of the minor. Some of the videos and images depicted sexual abuse by Larry Hodge himself, while others depicted sexual abuse by Emma Dell Hodge.
Further investigation revealed that the couple had gained access to the child by volunteering to assist the child’s parents by caring for the child after school and at various other times. Larry Hodge has also admitted to distributing the images and videos of the victim to a co-defendant, George K. Jackson. A sentencing hearing in the matter of Jackson is expected later today before Judge Young.
According to Assistant U.S. Attorney Todd S. Shellenbarger, who prosecuted the case for the government, Chief Judge Young also imposed lifetime supervision following Emma Hodge’s release from prison. During the period of supervised release, Hodge must comply with all sex offender registration laws, must not have unsupervised contact with minors, and must submit to an examination of any computer devices she uses.
This case was the result of an investigation by the Evansville Police Department and the Federal Bureau of Investigation and was brought as part of the U.S. Attorney’s Project Safe Childhood, a nationwide initiative launched in May 2006 by the Department of Justice to combat the growing epidemic of child sexual exploitation and abuse.
Led by the United States Attorneys’ Offices and the Criminal Division’s Child Exploitation and Obscenity Section, Project Safe Childhood marshals federal, state, and local resources to locate, apprehend, and prosecute individuals who sexually exploit children, and to identify and rescue victims. For more information about Project Safe Childhood, please visit http://www.usdoj.gov/psc.
Megapark 2012 – Croatia! Penalty Shoot-Out. Sexy Football Girls – C-Cup | Fussball EM
TOP-SECRET from the FBI – Second Recruiter Convicted in City Nursing Scheme
HOUSTON—Gwendolyn Kay Frank, 43, of Houston, has entered a plea of guilty to conspiracy to violate the Anti-Kickback Statue for her role in role in the $45 million City Nursing health care scandal, United States Attorney Kenneth Magidson announced today.
The Anti-Kickback Statute prohibits referring beneficiaries to business that bill federal health care programs in return for payments. According to the plea agreement, Frank referred at least 28 Medicare beneficiaries to the owner of City Nursing in return for $24,500. City Nursing then billed Medicare for approximately $1,051,392 worth of services for those individuals which were not provided and received $712,052 in payments from Medicare and Medicaid.
Frank is the second recruiter to plead guilty to conspiracy to violate the Anti-Kickback Statue this month and one of a growing list of individuals convicted in the Houston-based City Nursing health care fraud conspiracy. Floyd Leslie Brooks, 45, of Houston, pleaded guilty earlier this month. The owner of City Nursing, Umawa Oke Imo, was convicted in May 2011 and sentenced to more than 27 years in federal prison for his role in the health care fraud conspiracy which included making cash payments to both Medicare beneficiaries and recruiters bringing Medicare beneficiaries to City Nursing.
Frank was permitted to remain on bond pending her sentencing hearing, set for September 14, 2012. At that time, she faces up to five years in prison and a $250,000 fine.
This case has been investigated by the FBI, Internal Revenue Service-Criminal Investigations, the Department of Health and Human Services-Office of Inspector General and the Texas Attorney General’s Office-Medicare Fraud Control Unit. Assistant United States Attorney Julie Redlinger is prosecuting the case.
Megapark 2012 – Sexy Russian Football Girls posing – C-Cup Fussball EM | Comedy Central
TOP-SECRET from Public Intelligence – ITU CWG-WCIT12 Draft Compilation of Proposals/Options
The following documents are compilations of draft proposals for modifications to International Telecommunications Regulations (ITRs) under the International Telecommunication Union. The current version of the proposed changes to the ITRs (CWG-WCIT12 Temporary Document 64) was recently leaked in response to a lack of publicly available information on the proposals. These documents help to provide background and context on the development of the current proposal.
| CWG-WCIT12 TEMPORARY DOCUMENT 43 (CWG-WCIT12/TD – 43) “Draft compilation of options” | 137 pages | November 24, 2011 | Download |
| CWG-WCIT12 TEMPORARY DOCUMENT 36 (CWG-WCIT12/TD – 36) “Draft compilation of proposals” | 53 pages | June 13, 2011 | Download |
FEMEN – Topless Female Protest Group Set To Disrupt 2012 Euro Cup
Dark Side of Paradise – Full Movie
The FBI – Manhattan U.S. Attorney and FBI Assistant Director in Charge Announce Guilty Plea of Expert Networking Firm Consultant to Insider Trading Conspiracy Charge
Preet Bharara, the United States Attorney for the Southern District of New York, and Janice K. Fedarcyk, the Assistant Director in Charge of the New York Field Office of the Federal Bureau of Investigation (FBI), announced that Alnoor Ebrahim pled guilty today in Manhattan federal court to one count of conspiracy to commit securities fraud and wire fraud in connection with an insider trading scheme in which Ebrahim, formerly an associate director of channel marketing at AT&T, provided material, non-public information to members of the investment community. The information concerned product sales for AT&T’s handset devices, including Apple Inc.’s iPhone and Research in Motion Limited’s Blackberry products. Ebrahim pled guilty before U.S. District Judge Paul J. Oetken.
According to the information, statements made during today’s guilty plea proceeding, and evidence from the trial of Ebrahim’s co-conspirator, James Fleishman:
Between 2008 and 2010, Ebrahim provided material, non-public information concerning, among other things, product sales information for AT&T’s handset devices, including Apple Inc.’s iPhone and Research in Motion Limited’s Blackberry products (the “inside information”), in breach of his duties of trust and loyalty to AT&T. Ebrahim and his co-conspirators used an “expert networking” firm (the “firm”) for the purpose of facilitating “consultation calls,” during which Ebrahim provided the inside information to firm clients. Many of the consultation calls in which Ebrahim provided the inside information were with employees of investment firms located in New York, New York. During this time period, the firm paid Ebrahim more than $180,000 for his consultation calls.
***
Ebrahim, 57, of Alpharetta, Georgia, pled guilty to one count of conspiracy to commit securities fraud and wire fraud. The conspiracy count carries a maximum sentence of five years in prison. Ebrahim also faces a maximum fine of $250,000, or twice the gross gain or loss from the offense on the conspiracy count, and agreed as part of his plea agreement to forfeit the proceeds he obtained as a result of the offense.
Ebrahim is scheduled to be sentenced by Judge Oetken on October 25, 2012 at 2:00 p.m.
Mr. Bharara praised the investigative work of the Federal Bureau of Investigation. He also thanked the U.S. Securities and Exchange Commission.
This case was brought in coordination with President Barack Obama’s Financial Fraud Enforcement Task Force, on which Mr. Bharara serves as a Co-Chair of the Securities and Commodities Fraud Working Group. President Obama established the interagency Financial Fraud Enforcement Task Force to wage an aggressive, coordinated, and proactive effort to investigate and prosecute financial crimes. The task force includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general, and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch and, with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes.
Assistant U.S. Attorneys Antonia M. Apps and Reed Brodsky are in charge of the prosecution.
Megapark 2012 – Schamlippen Deospray! Manolo No1 | Football Girls Fussball EM
Dark Voyage – Full Movie
TOP-SECRET – Restricted U.S. Army Psychological Operations Process Tactics, Techniques, and Procedures Manual

Field Manual (FM) 3-05.301 describes the tactics, techniques, and procedures (TTP) for the implementation of United States (U.S.) Army Psychological Operations (PSYOP) doctrine presented in the higher-level publication, FM 3-05.30, Psychological Operations. FM 3-05.301 provides general guidance for commanders, staffs, and Soldiers who plan and conduct PSYOP across the range of military operations. The TTP in this manual are presented within the framework of the seven-phase PSYOP process, a mainstay for effective PSYOP executed at the tactical, operational, and strategic levels.
FM 3-05.301 is the principal reference for the PSYOP process. The contents of this manual supersede the discussion of the PSYOP process in FM 3-05.302, Tactical Psychological Operations Tactics, Techniques, and Procedures (28 October 2005). Any mention of the PSYOP process in other preceding doctrine or training literature should be validated by the contents of FM 3-05.301. This manual incorporates updated organizational structures, terminology, and capabilities to provide PSYOP Soldiers with the latest guidance to support a broad range of missions. This manual describes procedures and strategies derived from applied scientific and academic disciplines in an effort to improve the efficacy of the PSYOP process. These TTP are designed to facilitate the successful execution of each phase of the process: planning; target audience analysis; series development; product development and design; approval; production, distribution, and dissemination; and evaluation.
The PSYOP community, in general, is the intended audience for this manual. Members of the tactical, regional, and dissemination PSYOP battalions should find the information particularly useful. Written to give PSYOP officers, noncommissioned officers (NCOs), enlisted Soldiers, and civilians standardized PSYOP doctrine, FM 3-05.301 is a comprehensive how-to guide that focuses on critical PSYOP tasks, duties, and responsibilities.
…
Behavior Modification
2-58. Behavior can be modified by changing the conditions or situations that lead up to the TA’s current behavior. Behavior can also be modified by the manipulation of the consequences of the TA’s current behavior or by introducing new consequences (rewards and punishments) a TA receives for engaging in a behavior.
2-59. Decreasing a behavior involves devaluing or reducing the positive consequences and increasing the value of the negative consequences a TA receives. Removing something desirable or pleasant to a TA that is currently reinforcing a behavior, or introducing something into the TA’s environment that it finds unpleasant, are ways of decreasing a behavior.
2-60. Increasing a behavior involves increasing the value of the positive consequences and decreasing the value of the negative consequences a TA receives. Introducing or emphasizing things in the TA’s environment that are desirable or pleasant when it engages in the desired behavior, or removing things that are unpleasant when it engages in the desired behavior, are ways of increasing a behavior.
…
Psychographics
2-66. Psychographics are psychological characteristics of a TA. These are internal psychological factors— attitudes, values, lifestyles, motivations, and opinions. Psychographics might include characteristics such as fears, loves, hates, cultural norms, and values. Psychographics are vulnerabilities because they provoke an emotional response from the TA that can be used to increase the effectiveness of a PSYOP argument or PSYACT. Although often difficult to derive from standard intelligence and open sources, they can prove to be very effective in persuasion.
2-67. Psychographics include the following:
• Fears: What does the TA fear?
• Hates: What does the TA hate?
• Anger: What angers the TA?
• Loves: What does the TA love?
• Shame or embarrassment: What does the TA consider shameful or embarrassing?
• What is the TA dissatisfied with? (What are its gripes?)
• What are the cultural norms? (How is the TA expected to act?)
• What does the TA value? (What is important to the TA?)
• What are the frustrations? (What does the TA want that it cannot get?)Some examples of psychographics include the following:
• Green Tribe fighters have a very acute fear of fire/being burned alive based upon past experiences while fighting the Ruskinian Army in the 1980s. The Ruskinians used incendiaries, to include napalm, on Green Tribe positions.
• TA considers any effeminate characteristics/actions by males to be very shameful/embarrassing. These actions include crying, caring for children, housework, and physical displays of affection, such as holding hands and hugging between men.
• Male members of the TA are expected to work outside the home and provide for their immediate family and often other elderly/infirm members of their extended family.
• Red Tribesmen in the Birmingville area are highly dissatisfied with the perceived lack of progress on the electrical distribution system in the city.
• TA places a high value on education and will make great sacrifices to ensure the best education for its children.…
Appeals
2-95. An appeal is the overall approach used to present the main argument. It is the flavor or tone of the argument. Appeals gain the TA members’ attention and maintain their interest throughout the argument. Appeals are selected based upon the conditions and vulnerabilities of the TA. For example, a TA that does not believe the government of its country is legitimate will not be swayed by an appeal to legitimacy, whereas a military TA may be greatly affected by an appeal to authority. The following is a list of general persuasive appeals commonly used in PSYOP:
• Legitimacy.
• Inevitability.
• In group-out group.
• Bandwagon.
• Nostalgia.
• Self-interest (gain/loss).2-96. Legitimacy appeals use law, tradition, historical continuity, or support of the people. The following are types of legitimacy appeals:
• Authority: An appeal to laws or regulations, or to people in superior positions in the social hierarchy. For example, the Uniform Code of Military Justice, NCOs and officers, police officers, parents, or government officials. The TA must recognize the authority for the appeal to work.
• Reverence: An appeal to a belief-teaching institution or individual that is revered or worshiped; for example, the Dalai Lama, the Roman Catholic Church, or even a sports figure such as Michael Jordan.
• Tradition: An appeal to that which the TA is already used to. It is behavior that is repeated continually without question. Why do people have turkey on Thanksgiving? Because it has always been that way.
• Loyalty: An appeal to groups to which the TA belongs. Examples are military units, family, or friends. This appeal is usually used to reinforce behavior that already occurs.2-97. Inevitability appeals most often rely on the emotion of fear, particularly fear of death, injury, or some other type of harm. For example, if a person does not surrender, he will die, or if a person does not pay his taxes, he will go to jail. It can also be an appeal to logic. Both require proof that the promised outcome will actually occur. Therefore, it is crucial that credibility be gained and maintained throughout
the argument.2-98. An in group-out group appeal seeks to divide a TA or separate two TAs. It creates an enemy of one group, and encourages the other group to rebel/discriminate against them. This appeal frequently points out major differences between TAs, or factions of a TA. If PSYOP cannot effectively portray the in group in a negative manner, the appeal will fail.
2-99. Bandwagon appeals play upon the TA’s need to belong or conform to group standards. The two main types of bandwagon appeal are an appeal to companionship and an appeal to conformity. Peer pressure is an example of the conformity type of bandwagon appeal.
2-100. Nostalgia appeals refer to how things were done in the past. This appeal can be used to encourage or discourage a particular behavior. In a positive light, it refers to the “good old days” and encourages the TA to behave in a manner that will return to those times. In the negative, it points out how things were bad in the past and how a change in behavior will avoid a repeat of those times.
2-101. Self-interest appeals are those that play directly to the wants and desires of the individuals that make up a TA. This type of appeal can play upon the TA’s vulnerability for acquisition, success, or status. A self-interest appeal can be presented in the form of a gain or loss. An appeal to loss would be exploiting the fact that if the TA does not engage in the desired behavior, PSYOP cannot satisfy a want. An appeal to gain would inform the TA that to satisfy a want, the TA must engage in a desired behavior.
Techniques
2-102. For the purposes of TAA, techniques refer to the specific methods used to present information to the TA. Effective persuasion techniques are based on the conditions affecting the TA and the type of information being presented. Determining the most effective technique or combination of techniques to persuade the TA is only accomplished through a cultivated understanding of the TA and its behavior.
2-103. Persuasion and influence are the primary tools of PSYOP. As such, PSYOP Soldiers must strive to become familiar with, and ultimately develop, tactical and technical proficiency in the use of persuasion techniques. The following are some specific techniques used to present supporting arguments to the TA:
• Glittering generalities. These are intense, emotionally appealing words so closely associated with highly valued concepts and beliefs that the appeals are convincing without being supported
by fact or reason. The appeals are directed toward such emotions as love of country and home, and desire for peace, freedom, glory, and honor.
• Transference. This technique projects positive or negative qualities of a person, entity, object, or value to another. It is generally used to transfer blame from one party in a conflict to another.
• Least of evils. This technique acknowledges that the COA being taken is perhaps undesirable, but emphasizes that any other COA would result in a worse outcome.
• Name-calling. Name-calling seeks to arouse prejudices in an audience by labeling the object of the propaganda as something the TA fears, loathes, or finds undesirable.
• Plain folks or common man. This approach attempts to convince the audience that the position noted in the PSYOP argument is actually the same as that of the TA. This technique is designed to win the confidence of the audience by communicating in the usual manner and style of the audience. Communicators use ordinary or common language, mannerisms, and clothes in face-to-face and other audiovisual communications when they attempt to identify their point of view with that of the average person.
• Testimonials. Testimonials are quotations (in and out of context) that are cited to support or reject a given policy, action, program, or personality. The reputation or the role of the individual giving the statement is exploited. There can be different types of testimonial authority. Official testimonials use endorsements or the approval of people in authority or well known in a particular field. Personal sources of testimonials may include hostile leaders, fellow soldiers, opposing leaders, famous scholars, writers, popular heroes, and other personalities.
• Insinuation. Insinuation is used to create or increase TA suspicions of ideas, groups, or individuals as a means of dividing the adversary. The PSYOP Soldier hints, suggests, and implies, but lets the TA draw its own conclusions.
• Presenting the other side. Some people in a TA believe that neither of the belligerents is entirely virtuous. To them, messages that express concepts solely in terms of right and wrong may not be credible. Agreement with minor aspects of the enemy’s point of view may overcome this cynicism.
• Simplification. In this technique, facts are reduced to either right, wrong, good, or evil. The technique provides simple solutions for complex problems and offers simplified interpretations of events, ideas, concepts, or personalities.
• Compare and contrast. Two or more ideas, issues, or choices are compared and differences between them are explained. This technique is effective if the TA has a needs conflict that must be resolved.
• Compare for similarities. Two or more ideas, issues, or objects are compared to try and liken one to the other. This technique tries to show that the desired behavior or attitude (SPO) is
similar to one that has already been accepted by the TA.
• Illustrations and narratives. An illustration is a detailed example of the idea that is being presented. It is an example that makes abstract or general ideas easier to comprehend. If it is in a story form, it is a narrative.
• Specific instances. These are a list of examples that help prove the point.
• Statistics. Statistics have a certain authority, but they must be clear enough to show the TA why they are relevant. In most cases, it is best to keep the statistical evidence simple and short so the TA can easily absorb it.
• Explanations. These are used when a term or idea is unfamiliar to the TA.Primary Influence Tactics
2-104. These primary influence tactics are widely applicable to many situations, cultures, and TAs. By using the appropriate influence tactics in products and actions, the persuasiveness of PSYOP will be magnified. The following are examples of primary influence tactics:
• Rewards and punishments: “If you do X, you will get Y,” or “if you do not do X, Y will happen to you.” Example: “Surrender, and you will be treated well; continue to fight, and you will be killed.”
• Expertise: “Speaking as an authority on the subject, I can tell you that rewards/punishments will occur if you do or do not do X.” Example: “Oil Minister Gregor (key communicator/expert) states that if rebel groups continue to sabotage oil pipelines, the national economy will be seriously affected.”
• Gifts: Giving something as a gift before requesting compliance. The idea is that the target will feel the need to reciprocate later. Example: “This well and cistern are a gift to the people of Birmingville from the coalition forces…demonstration of our good will and hope for mutual cooperation in the future.”
• Debt: Calling in past favors. Example: “Coalition forces have done a lot for Birmingville, Elder Chang: the new school, the well in the center of town… these insurgents are endangering all we have worked for together. We need your help in stopping these groups by reporting any information you and your people may discover.”
• Aversive stimulation: Continuous punishment, and the cessation of punishment, is contingent on compliance. Example: “We will continue to bomb your position unless you surrender immediately.”
• Moral appeal: Entails finding moral common ground, and then using the moral commitments of a person to obtain compliance. Example: “The killing of innocent civilians is wrong; please help the security forces stop this tragic loss of innocent life by reporting any information on terrorist activities.”
• Positive and negative self-feeling: “You will feel better/bad if you do X.” Example: “Become part of something bigger than yourself, know honor and take pride in your work…join the national security forces!”
• Positive and negative altercasting: “Good people do X / Bad people do Y.” Example: “Red Tribe members are brave and honorable people who care about the future of their country and are not intimidated by rebel groups. Call and report insurgent activity now on the coalition hotline.”
• Positive and negative esteem of others: “Other people will think highly/less of you if you do X.” Example: “Earn the respect of your friends and the pride of your family…join the Patriotsville National Guard now!”
• Fear: “Bad things will happen to you if you do X.” Example: “Only death and fire await those who continue to fight…surrender now.”
TOP-SECRET from the NSA – New Documents Spotlight Reagan-era Tensions over Pakistani Nuclear Program
|
Washington, D.C., June 18, 2012 – Tensions between the United States and Pakistan rose through the 1980s over intelligence reports that suggested to U.S. officials that Pakistani leader Zia ul-Haq had repeatedly lied to them about his country’s nuclear program, according to recently declassified records published today by the National Security Archive and the Nuclear Proliferation International History Project. Zia’s apparent mendacity posed an immediate challenge to U.S. nonproliferation goals, but also threatened the even higher priority of providing aid to Islamabad and to the Mujahedin resistance fighting Soviet forces in Afghanistan.
Preventing the spread of nuclear weapons has been a significant objective for U.S.presidents, but there have been instances when diplomatic and other interests have overridden concerns about nuclear proliferation. Israel since the late 1960s is one example and Pakistan during the 1980s is another. Concerned by new intelligence about the Pakistani nuclear program, in July 1982, the Reagan administration sent former CIA deputy director General Vernon Walters to meet secretly with Pakistani dictator General Muhammad Zia-ul-Haq. U.S. intelligence had detected an upswing of clandestine Pakistani efforts to procure nuclear weapons-related technology and unwanted publicity could jeopardize U.S. government economic and military aid to Pakistan, a key partnerin the secret war against Soviet forces in Afghanistan.
Confronted with the evidence, Zia acknowledged that the information “must be true,” but then denied everything, leading Walters to conclude that either Zia “did not know the facts” or was the “most superb and patriotic liar I have ever met.” While Zia restated earlier promises not to develop a nuclear weapon and made pledges to avoid specific nuclear “firebreaks,” officials from Secretary of State George Shultz on down would conclude time and time again, that Zia was breaking his word.
In 1986, Arms Control and Disarmament Agency (ACDA) director Kenneth Adelman wrote in a memorandum to the White House that Zia “has lied to us again,” and warned that failure to act would lead the General to conclude that he can “lie to us with impunity.” While the Reagan administration was concerned about nuclear proliferation, it gave a greater priority to securing aid to Pakistan so it could support the Afghan anti-Soviet insurgency. The White House and the State Department leadership hoped that building a strong bilateral relationship would dissuade Pakistan from building nuclear weapons.
Top levels of the U.S. government let relations with a friendly government supersede nonproliferation goals as long as there was no public controversy that could “embarrass” the President the documents show. Indeed, Reagan administration officials feared that if the Pakistanis had told them the “truth” about the purpose and scope of their nuclear activities, it would have made it impossible for the administration to certify to Congress that Pakistan was not developing nuclear weapons. On that certification rode the continued flow of aid to assist the Afghanistan resistance. For the sake of that aid, senior Reagan administration officials gave Pakistan much slack by obscuring its nuclear activities, but that they wrote about lying and “breaking … assurances” suggests that lack of trust and confidence was an important element in the U.S.-Pakistan relationship, as it is today.
Among the disclosures in today’s publication:
- By the early summer of 1981, State Department intelligence estimated that the Pakistanis were “probably capable of producing a workable device at this time,” although the Kahuta enrichment plant was unlikely to produce enough fissile material for a test until 1983.
- Pakistan was slated to acquire F-16 fighter-bombers from the U.S. That prospective sale troubled Indian leaders because a nuclear Pakistan with advanced fighter bombers would be a more formidable adversary.
- During the spring of 1982 U.S. diplomats and intelligence collectors found that Pakistani agents were trying to acquire “fabricated shapes” (metal hemispheres for producing nuclear explosive devices) and other sensitive technology for a nuclear program. Suggesting that Pakistan was starting to cross the line by building a nuclear weapon, these discoveries contributed to the decision to send former CIA deputy director Vernon Walters to meet secretly with General Zia in July and October 1982.
- During Walters’ October 1982 visit, Zia told him of his meeting with Saudi Arabia’s King Fahd who had told him that agents from an unspecified country had attempted to sell him a nuclear device for $250 million. Zia advised Fahd not to “touch the offer with a barge pole.”
- A controversial element in the F-16 sale was whether the U.S. would comply with Pakistani requests that it include the same radar system as the most advanced U.S. model. While top CIA officials warned that the Pakistanis were likely to share the technology with China, Secretary of State George Shultz and other officials believed, ironically, that denying Pakistani requests would make that country less responsive to U.S. nonproliferation goals.
- With Pakistan’s efforts to acquire sensitive technology continuing, in December 1982 Secretary of State Shultz warned President Reagan of the “overwhelming evidence that Zia has been breaking his assurances.” He also expressed concern that Pakistan would make sensitive nuclear technology available to “unstable Arab countries.”
- In June 1986 ACDA director Kenneth Adelman wrote that Zia has “lied to us again” about violations of agreements not to produce highly-enriched uranium above a five-percent level. If Washington did not apply real pressure it would reinforce Zia’s belief “that he can lie to us with impunity.”
- In the spring of 1987, senior State Department officials wrote that Pakistani nuclear development activities were proceeding apace and that General Zia was approaching a “threshold which he cannot cross without blatantly violating his pledge not to embarrass the President.”
Until 1990, after the Soviets had left Afghanistan, Washington never allowed events to reach a point where public controversy over Pakistani nuclear weapons activities could force a decision that to cut off aid and threaten Pakistan’s role as a go—between to the Afghan resistance. The tough sanctions that have been used against countries like Iran and North Korea were never given serious consideration because the Reagan administration believed that embracing close associates like Pakistan in a “broader bilateral relationship” could discourage them from testing a nuclear device. U.S. policymakers unsuccessfully tried to jawbone their Pakistani counterparts from enriching uranium and building a nuclear weapon.
The other side of U.S. policy was the organized multilateral effort, begun during the Carter administration, to prevent sensitive technology from reaching Pakistan. This largely consisted of efforts to persuade other nuclear suppliers to bar exports of dual-use technology. While international export controls could not stop the Pakistani program, U.S. officials believed that they could “delay” and even “set [it] back”. Those activities were at a high tempo during the early 1980s but whether they continued at the same pace during the rest of the decade is not clear. More declassifications may shed light on that.
The White House and the State Department worked successfully at offsetting Congressional pressures to impose tough nonproliferation standards, although arrests by the U.S. Customs Service raised inconvenient questions. The first major case was Nazir Ahmed Vaid’s arrest in June 1984 for trying to purchase nuclear weapons technology. U.S. government officials may have interfered in the case to minimize adverse publicity that could weaken Congressional support for aid to Pakistan. Nevertheless, Congressional pressure continued. In 1985, Senator John Glenn (D-Oh), among others, wanted the administration to certify, as a condition for further aid, that Pakistan neither possessed nor was developing a nuclear weapon. But the White House and its supporters in Congress won support for a weaker version: an amendment, supported by Senator Larry Pressler (R-SD), requiring annual certification that Pakistan did not possess a nuclear device and that U.S. aid would reduce the risk that Pakistan would acquire one. [1]
In 1986 Reagan certified that Pakistan was in compliance with the Pressler amendment, but months later participants in the Khan network were caught again. In July 1987 U.S. Customs officials arrested Arshad Pervez for trying to buy supplies for the Kahuta enrichment plant. Nevertheless, the administration insisted that nothing was amiss, arguing that it was too early to conclude the Pervez had official support in Pakistan. [2] Even after Pervez was convicted later that year, Reagan certified again that Pakistan did not possess a nuclear device, thereby ensuring that aid flowed without interruption. Congress, however, showed its concern by letting the five- year Symington amendment waiver expire, which temporarily halted “new commitments of aid.” When Congress reinstated a new waiver, it would be only for two-and-a- half years, instead of the six years that Reagan had proposed. 1990 would become a year of decision for future U.S. aid to Pakistan. [3]
This is the third in a series of Electronic Briefing Books on U.S. policy toward the Pakistani nuclear program. The first was on the Carter administration’s policy; the second was on the efforts to work with allies to prevent the export of sensitive technology to Pakistan. The National Security Archive has filed numerous declassification requests to U.S. government agencies on important developments during the 1970s, 80s, and early 1990s, and as significant material becomes declassified the Archive will update this series of EBBs.
READ THE DOCUMENTS
Document 1:”Reached a Dead End”
U.S. Department of State Cable 145139 to U.S. Embassy India [repeating cable sent to Embassy Pakistan], “Non-Proliferation in South [Asia],” 6 June 1979, Secret
Source: MDR request
By the spring of 1979, the Carter administration decided that it had “reached a dead end” in its efforts to stop the spread of nuclear technology to South Asia and that a “new strategy” was necessary to check the spread of nuclear weapons in the region. Given close security ties with Pakistan and concerns about that country’s stability, the State Department was not going to take a hard-line approach, such as embargoes. to force a nuclear roll-back. Thus, Washington would maintain “vigilance” to ensure that sensitive supplies did not reach Pakistan, but the administration no longer saw it possible to reverse Pakistan’s efforts to construct uranium enrichment facilities. More serious dangers were a South Asian nuclear arms race and the threat to U.S. nonproliferation policy which “will collapse under the weight of two additional nuclear-weapons states.” By playing the role of an “honest broker,” and offering appropriate inducements, Washington would make a “sincere attempt to convince South Asians that nuclear weapons are not a viable option.”
Three interrelated actions were necessary. Pakistan would have to be persuaded not to stage a “peaceful nuclear explosion,” along the line of India’s 1974 test, because that would push India to develop a nuclear arsenal and even consider preemptive action. The U.S. would have to seek assurances from Prime Minister Desai that India would not produce nuclear weapons. Finally, Washington would need China’s support, e.g. security assurances to India. To make these arrangements work, Washington would have sell nuclear fuel to India and lift the Symington amendment sanctions against Pakistan that the enrichment program had triggered. Policy success was by no means assured–China might not cooperate–and other uncertainties could complicate matters, for example, if Pakistan helped other Muslim states develop an “Islamic bomb.”
Document 2: “Two-Step Carrot-Stick Approach”
Anthony Lake, director, Policy Planning Staff, to Secretary of State Vance, “The Pakistan strategy and Future Choices,” 8 September 1979, Secret
Source: National Archives, Record Group 59, Records of Anthony Lake, box
The previous document was a marker for policy change, but carrying it out was difficult because of the difficulty of balancing “good relations” with Pakistan with global nonproliferation interests. Concerns about a nuclear test and the transfer of sensitive technology to other states had crystallized into a “no-test/no-transfer” approach, but Washington needed help from other Western aid donors to persuade General Zia’s government to accept those parameters. To try to forge an understanding with Pakistan, Lake describes a “two-step carrot-stick” approach, involving pressures by aid donors. As Lake’s report to Vance makes clear, there were significant divisions in the Carter administration over what “carrots” could be offered and under what conditions, for example, whether sale of F-16 fighter-jets could win the military’s support for scaling back the nuclear program, and how to deal with the Symington amendment. If the “two-step” approach failed Washington might have to consider a “third step” which could either be a resumption of pressure or a waiver of the Symington amendment in exchange for a no-test/no-transfer understanding.
The next month, Secretary of State Vance and Ambassador Gerard C. Smith met with Foreign Minister Shahi, warning him that a nuclear test would harm U.S. –Pakistani relations, with Smith arguing that Pakistan was “entering the valley of death” because India “can utterly destroy you.” Apparently Shahi responded that “he did not have to be a nuclear expert to understand that ‘the value of a nuclear capability lies in its possession, not in its use.” Smith soon traveled to Europe and discussed Pakistan with donor governments, but found little support for applying pressure. [4]
Document 3: “Set the Nuclear Issue Aside”
Secretary of Defense Harold Brown to Ambassador-at-Large Gerard C. Smith, 31 January 1980, enclosing excerpts from memoranda of conversations with Geng Biao and Deng Xiaoping, 7 and 8 January 1980, Top Secret
Source: FOIA release
The Soviet invasion of Afghanistan in December 1979 had an immediate impact on U.S. policy toward Pakistan as indicated by Secretary of Defense Brown’s talks with top Chinese officials. In light of the high priority of funneling aid through Islamabad to the anti-Soviet resistance and concern that Moscow might put Islamabad under pressure, interest in improved relations with Pakistan further lowered the nuclear issue’s priority, although efforts to block sensitive exports continued. As Brown explained to Deng, “we will set [the nuclear issue] aside for the time being and concentrated on strengthening Pakistan against possible Soviet action.” In other words, Cold War objectives had priority over nonproliferation concerns. [5] While Deng claimed that Beijing opposed Pakistan’s nuclear program, China and Pakistan had already developed a special nuclear relationship and ambivalence was evidence in Deng’s advice that the United States “not mention” the nuclear issue in talks with Pakistan.
Document 4: “Pakistan Will Not Give up This Program”
Bureau of Intelligence and Research, U.S. Department of State, “Pakistan and the US: Seeking Ways to Improve Relations,” Report 97-PA, 23 March 1981, Secret
Source: Department of State FOIA release, copy courtesy of Jeffrey Richelson
According to INR analysts, the Pakistani leadership wanted to improve relations with Washington and certainly get a bigger aid package than the “peanuts” offered by the Carter administration. Nevertheless, INR recommended caution about getting too close to General Zia; he would be gone someday and “too close a US tie … might harm future relations.” Moreover, better relations would not make the nuclear problem go away: “Pakistan will not give up this program.” There was some chance that Pakistanis could be persuaded not to test a device but this “would be difficult to accomplish.” The Indians might react badly if Washington gets too close to Pakistan: “they might well retaliate by moving closer to the Soviets.”
Document 5: A “Broader Bilateral Relationship”
Special Assistant for Nuclear Proliferation Intelligence, National Foreign Assessment Center, Central Intelligence Agency, to Resource Management Staff, Office of Program Assessment et al, “Request for Review of Draft Paper on the Security Dimension of Non-Proliferation,” 9 April 1981, Secret, excised copy
Source: MDR release
A new presidential administration wanted to put its own stamp on nonproliferation policy and the Department of State helped begin the process with a draft paper on the “security dimensions of nonproliferation.” Convinced that further spread of nuclear capabilities could have an adverse impact on U.S. security, the report emphasized the importance of perceptions of insecurity as a motive leading states to opt for a nuclear explosive program. While denial of sensitive technology and equipment remained “fundamental,” State Department officials believed that a “broader bilateral relationship” based on the integration of political incentives and security assistance could persuade friendly threshold states that they did not need nuclear weapons. By contrast, “more negative methods of dissuasion” would apply to countries which had poor relations with Washington.
The State Department’s review of threshold states, from Argentina and Brazil to Libya and Iraq, include a discussion of Pakistan, where the “broad bilateral relationship” approach was taken into account. The U.S. objective should be a “closer security relationship which builds confidence in us and makes the Paks feel more secure.” Such a relationship would be “more likely to provide Pakistan with incentives to forego, or at least delay, a nuclear test than any alternative approach.” Following the Carter administration, the Reagan team had minimal goals: preventing a Pakistani nuclear test, not dismantling the enrichment program, had become the key objective. Nevertheless, State’s politico-military analysts argued that Washington should not give the impression that was acquiescing in Pakistan nuclear activity: it was necessary to “lay down a marker” by making Pakistani officials understand the “political costs” of continuing a weapons program.
Document 6: More “Carrots and Sticks”
Lewis A. Dunn, Arms Control and Disarmament Agency, “Implications for U.S. Policy of a Pakistani Nuclear Test,” 11 June 1981, Secret
Source: FOIA release
Signs of the Reagan team’s emphasis on propitiating Islamabad are evident in a memorandum that incoming ACDA official Lewis Dunn had prepared just before he left Herman Kahn’s Hudson Institute. Seeing Pakistan as likely to test a weapon once it had enough fissile material (a test site had already been discovered [6]) Dunn believed that prospects for halting a test were “dimming.” If Pakistan did test, however, there could be a range of U.S. responses, but he favored a “muted” one, owing to regional security considerations and the importance of “holding down” Pakistani nuclear activities. In that regard, Dunn saw “carrots and sticks” as relevant; if Pakistan tested, offers of military assistance or civilian nuclear technology might discourage further nuclear activities. He identified no “sticks.” Dunn also believed it useful to encourage Indian-Pakistan dialogue and regional arms control measures (e.g., no first use pledges and confidence building activities). Pakistan did not test for years, but the Reagan administration would hope in vain that “yes” was the answer to one of Dunn’s questions: “Would the prospect of access to U.S. arms enhance Pakistani incentives for nuclear restraint?”
Document 7: “Probably Capable of Producing a Workable Device at this time”
Bureau of Intelligence and Research, U.S. Department of State, “India-Pakistani Views on a Nuclear Weapons Options and Potential Repercussions,” Report 169-AR, 25 June 1981, confidential
Source: Department of State FOIA release, copy courtesy of Jeffrey Richelson
This report provides an overview of the state of the Indian and the Pakistani nuclear programs, reviewing motivations, the technical situation, possible decisions to test, and the implications of a Pakistani test. According to INR, the Pakistanis are “probably capable of producing a workable device at this time,” but the Kahuta plant was unlikely to produce enough fissile material for a test until 1983. While the Indians had stated publicly that they were preparing their test site that declaration may have been for political effect because they may have wanted the Pakistanis make the “first move.” If Zia decided to do so, he would have to decide whether to risk worsening relations with Washington and a heightened regional nuclear arms race. Indira Gandhi would likely order retaliatory nuclear tests and quiet work on a weapons program. But if Pakistan went further and began an active nuclear weapons program, India was not likely to take risky preventive action because of the difficulty of taking out “Pakistan’s well-defended nuclear facilities” and the risk of “antagonizing China.” INR analysts opined that a nuclear South Asia would not be a stable region: “it is difficult to be optimistic that a stable, long-term mutual deterrence relationship would be established.”
Document 8: A “Great Security Threat” to India
Acting Special Assistant for Nuclear Proliferation Intelligence, National Foreign Assessment Center, to Director and Deputy Director of Central Intelligence, “Warning Report – Nuclear Proliferation,” 20 August 1981, Top Secret, Excised Copy
Source: Mandatory Review Request
An International Atomic Energy Agency report that Pakistan may have diverted plutonium from the Karachi nuclear power plant was raising questions about the adequacy of safeguards, but
Intelligence repots suggested that the Pakistanis “were not overly concerned.” More serious were the implications of U.S.-Pakistani discussions of the sale of advanced F-16 fighter-bombers as part of a larger U.S. aid package to secure Pakistan’s collaboration in the covert war against Soviet forces in Afghanistan. Indian Prime Minister Indira Gandhi worried that Pakistan’s nuclear program and its slated acquisition of F-16s posed a “great security threat” that raised the risk of war.
Document 9: The Danger of Indian Preventive Action
John N. McMahon, Deputy Director for National Foreign Assessment, to Ambassador Richard T. Kennedy,Under Secretary of State for Management, “Special National Intelligence Estimate on Indian Reactions to Nuclear Developments in Pakistan,” 21 September 1981, enclosing SNIE 31-32/81, Secret, excised copy
Source: FOIA release
The heightened Indian concerns about Pakistan discussed in the August “Warning Report” raised enough hackles in the Reagan administration for the CIA to produce a Special National Intelligence Estimate on the possibility of Indian preventive action against Pakistan’s nuclear program. While the estimators could not be sure, they believed that Prime Minister Gandhi would take a “wait-and-see” approach as to whether Pakistan 1) was going to test a device and 2) keep producing fissile material for weapons. India would have to decide whether to stage an “answering test” (for which preparatory work had already been undertaken), but also whether to take preventive action before Pakistan had a weapons stockpile.
Israel’s use of F-16s to destroy Iraq’s Osirak nuclear reactor in June 1981 and Washington’s announcement on 14 September of the F-16 sale to Pakistan made Indian defense officials wonder whether preventive action against nuclear facilities was necessary before Islamabad had the fighter-bombers (for which nuclear-capable versions existed). If India took such action it would have to face the prospect of a “severe” international reaction as well as the possibility that China might intervene on Pakistan’s behalf. One alternative for India was to develop a nuclear stockpile superior to Pakistan’s. That would take a high-level decision to produce nuclear weapons, while financial, technological, and other considerations might encourage Gandhi to move slowly. Nevertheless, the possibility that India (or even Israel) would take preventive action against the Pakistani nuclear program would be a continuing concern.
Document 10: “In All Probability We Would Choose to Cut off Assistance”
Secretary of State Alexander Haig to Senator Mark Hatfield (R-Or), 21 November 1981, Confidential
Source: State Department FOIA release
While concerned about what India might do, the Reagan administration focused on working with Pakistan to weaken the Soviet position in Afghanistan. Facilitating that involved a multi-billion military and economic aid package to Pakistan which included a five year waiver of the Symington amendment to eliminate automatic triggers that would cut aid if Washington detected evidence of nuclear weapons work. Nevertheless, Congress imposed some conditions, namely that aid would stop if Pakistan tested a nuclear weapon. To confirm that the administration was on board, Senator Mark Hatfield, who had long been concerned about nuclear proliferation, asked Secretary of State Alexander Haig how the U.S. government would react to a Pakistani nuclear test. Haig replied that “in all probability”, Washington would cut aid. Haig might have thought that there would be no problem because General Zia had assured Under Secretary of State James Buckley that he would not develop or test a nuclear weapon (See document 11A for that assurance). On human rights, another of Hatfield’s concerns, the Reagan administration was departing from the human rights emphasis of its predecessor. Haig would make no commitments because of Pakistan’s “limited tradition of representative government.”
Document 11: “Significant” Chinese Aid on Nuclear Design
Note for [name excised] from [name excised], “State/INR Request for Update of Pak SNIE, and Assessment of Argentine Nuclear Program,” 4 June 1982, Secret, excised copy
Source: CREST
A planned update of a Special National Intelligence Estimate concluded that the Pakistani nuclear program was keeping its momentum and that new evidence, apparently acquired by British intelligence, suggested a “significant” Chinese role, at least in providing assistance on weapons design. [7] CIA was apparently adjusting its earlier estimate—late 1982/1983-84–for the availability of fissile material for weapons. The implication was that a Pakistani test was not imminent, thus reducing pressure on India.
Document 12: Discoveries and Demarches
Terry Jones, Office of Nonproliferation and Export Policy, Department of State, to J. Devine et al., enclosing summaries of State Department cable traffic during 1981-1982 relating to demarches on attempted purchase of sensitive nuclear-related products, 17 June 1982
Source: State Department FOIA release
The Reagan administration gave Pakistan some slack, but it continued the campaign of demarches, begun under Jimmy Carter, to try to prevent the export of sensitive nuclear technology to Pakistan, among others. (See EBB “Demarches and Non-Papers”) As before, Pakistan was a special target of concern, but these summaries of State Department telegrams, some in the sensitive intelligence-related “Roger” channel, show that Washington was also trying to prevent sales of nuclear-related technology to a host of countries: Argentina, Brazil, China, India, Iraq, Israel, Korea, Libya, Romania, South Africa, and Syria. For example, cable traffic on Syria showed concern about Damascus’s interest in acquiring a research reactor, while messages on Libya show U.S. government efforts to discourage Belgian sale of a plant to produce uranium tetraflouride (the precursor to uranium hexaflouride, used for uranium enrichment).
The name A. Q. Khan was not mentioned in these cables, but his fingerprint showed up, for example, in the attempted purchases of electrical inverters (used for gas centrifuges). These attempts were probably by the Khan network. But the group of Pakistani agents seeking to purchase nuclear-related technology was broaderthan Khan’s. For example, the nuclear reprocessing technology program was directed by Pakistan Atomic Energy Commission chief Munir Ahmad Khan, who had a procurement network in Europe directedby S.A. Butt. The cable summaries for Pakistan showed a number of attempted and completed purchases by Pakistani agents from suppliers in a variety of countries, including Belgium, Finland, Japan, Sweden, andTurkey. Besides the inverters, agents were seeking such items as fabricated shapes” (metal hemispheres for producing nuclear explosive devices), coaxial cables, fuel chopping machines(to help reprocess plutonium), nuclear power plants, and “flash X-ray units”(diagnostic instrument used in tests of neutron initiators for nuclear weapons).[8] Suggesting that Pakistan was starting to cross the line into producing a nuclear weapon, these efforts raised alarm bells in Washington. [Updated 4 May 2012. Thanks to Mansoor Ahmed for information]
Documents 13A-B: “The Most Superb and Patriotic Liar”
A. U.S. Embassy Pakistan cable 10239 to State Department, “My First Meeting with President Zia,” 5 July 1982, Secret
B. U.S. Embassy Pakistan cable 10276 to State Department, “My Final Meeting with President Zia,” 6 July 1982, Secret
Source: State Department MDR release
Much needs to be learned about White House decision-making but evidently the alleged Pakistani efforts to purchase sensitive technology discussed above, and possibly the intelligence on Chinese weapon design assistance, prompted concern that Congress would find out and stop aid if it believed that Pakistan was developing a capability for a nuclear test. To keep the situation in check, Reagan sent General Vernon Walters, former Deputy Director of Central Intelligence and personal translator for U.S. presidents, among other high-level and sensitive positions, to take a presidential letter to General Zia. During their 4 July meeting, Walter told Zia that Washington had “incontrovertible intelligence” that Pakistani representatives had “transferred designs and specifications for nuclear weapons components to purchasing agents in several countries for the purpose of having these nuclear weapons components fabricated for Pakistan.” Under the law, Walters told Zia, the administration would have to inform the U.S. Congress. Zia denied everything: Pakistan did not have a weapons development program and repeated assurances made to Under Secretary of State James Buckley that Pakistan would not develop or test a nuclear weapon. Zia said that he was sure that no one was buying nuclear equipment, but he would check with his subordinates to be sure. Walter later commented: “either he really does not know or is the most superb and patriotic liar I have ever met.”
In what Walters saw as a diversion from the main discussion, the conversion turned to the problem of the IAEA inspection of the Karachi Nuclear Power Plant and recommendations on safeguards to prevent diversion of spent fuel. Zia repeated his earlier assurances on nuclear weapons and insisted that Pakistan would not “embarrass” the U.S. government. Walters reported that Zia “took the matter somewhat better than I had expected.”
The conversation the next day showed that Zia was a master of double-talk. Verbally, he admitted that U.S. intelligence was on to something: “The president must be right. Your information must be right. I accept its authenticity.” But he would not put that in writing and in a formal response to Reagan’s letter, Zia argued that the U.S. information was a “total fabrication.” This, Walter argued, was a matter of keeping “face”: what Zia was saying was “it did not happen but you can be sure it won’t happen again.” “I think he has the message,” Walter concluded, although he did not explain whether he believed that there would be any changes in Pakistani policy.
Documents 14A-B: “Word of Honor”
A. U.S. Embassy Pakistan cable 15696 to State Department, “Pakistan Nuclear Issue: Meeting with General Zia,” 17 October 1982, Secret
B. State Department cable 299499 to U.S. Embassy Islamabad, “Pakistan Nuclear Issue: Meeting with General Zia,” 25 October 1982, Secret
Source: State Department MDR release
What Zia said to Walters was irrelevant because U.S. intelligence detected continuing efforts to procure sensitive technology and materials (see next document). Thus, Walters returned to Islamabad for another demarche in October, to warn Zia that U.S. aid was in “grave jeopardy.” (see document 16 below). Walter showed drawings of Chinese-influenced nuclear weapons designs that U.S. intelligence had obtained, but Zia denied that there was anything untoward: Pakistan’s reprocessing and enrichment programs were entirely peaceful and there was “nothing” in the nuclear weapons field. Pakistan would do nothing that would jeopardize its aid and other relationships with Washington. Any information on clandestine nuclear activities, he suggested, had been concocted by Pakistan’s “enemies.” As for the items that Pakistan was allegedly attempting to procure, such as “spheres”, Zia argued, there was nothing that could not be produced internally. Walter said he would review the U.S. evidence, but observed that intelligence advisers had assured him that there was “no possibility of fabrication or disinformation.”
The delivery of the F-16s to Pakistan was nearing and Zia wanted to make sure that they were equipped with the ALR-69 radar warning receiver, the most advanced radar warning technology in the U.S. Air Force’s inventory. What had held up delivery was concern in Washington that Pakistan might give the Chinese access to this advanced technology. Walters said he would look into it.
Zia concluded the meeting with a story based on conversations with Saudi Arabia’s King Fahd. The latter had told him that agents from an unspecified country had attempted to sell a nuclear device to Saudi Arabia for $250 million. He had advised Fahd not to “touch the offer with a ‘barge pole.'”
In a follow-up message, prepared after he was back in Washington, Walters noted that at the end of the conversation, Zia had given his “word of honor” that Pakistan “will not develop a nuclear device or a weapon.”
Document 15A-B: “A Serious Blow to U.S. Worldwide Nonproliferation Efforts”
A. Excerpt from Intelligence Report, “Pakistan-US: Demarche on F-16 Equipment,” 8 November 1982, enclosed with memorandum from Deputy CIA Director John N. McMahon to Deputy Secretary of Defense Frank Carlucci, “Risk Assessment of the Sale of AN/ALR-69 Radar Warning Receiver to Pakistan,” 8 November 1982, with excerpt from National Intelligence Estimate on Pakistan attached, n.d., Secret
B. Henry S. Rowen, National Intelligence Council, to DDCI [Deputy Director of Central Intelligence McMahon], 19 November 1982, with attached memorandum from National Intelligence Council staffer [name excised], “Pakistan,” same date, Secret
Source: CREST
Whether the Pakistanis, and presumably the Chinese, should get access to advanced F-16 technology was hotly contested. CIA officials acknowledged that, despite an agreement not to disclose military information, the Pakistanis were likely to give Beijing access to the AN/ALR-radar warning system, especially if “major strains” in the U.S.-Pakistan relationship developed. Because ALR-69 technology would allow a “potential adversary” to use radar equipment to defeat an F-16, Deputy CIA Director McMahon advised against releasing it to Pakistan. Secretary of State George Shultz wanted to meet Pakistani requirements and an official at CIA’s National Intelligence Council, supported by Henry Rowen, provided supporting arguments. Sanguine about the risk of disclosure to Beijing, they argued that failure to supply the F-16 with “USAF radar” would deprive Washington of “leverage” that made possible General Walter’s access to Zia. Highly sanguine about the political influence associated with arms sales, CIA analysts argued that failure to meet Pakistani demands would constitute a “serious blow to U.S. worldwide nonproliferation efforts.” This optimistic view prevailed and the Air Force was constrained to provide the AN/ALR-69 to Pakistan. [9]
Document 16: “Overwhelming Evidence that Zia Has Been Breaking His Assurances”
Secretary of State George Schultz to President Reagan, “How Do We Make Use of the Zia Visit to Protect Our Strategic Interests in the Face of Pakistan’s Nuclear Weapons Activities,” 26 November 1982, Secret
Source: CREST
George Shultz probably saw the ALR-69 issue as a minor problem compared to the “overwhelming evidence that Zia has been breaking his assurances” on Pakistan’s nuclear weapons program, Shultz may have accepted the interpretation that Zia was a patriotic liar” but this raised a tough diplomatic problem because the General would soon be in Washington to meet President Reagan. Citing an interagency report on issues and options, Shultz saw high risks because good relations with Pakistan, especially while the war in Afghanistan was in progress, were a major strategic interest. Yet, if Pakistan continued its nuclear weapons work, Congress could cut off aid. Moreover, a South Asian nuclear arms race could destabilize the region, not to mention the dangers of Indian and/or Israeli preemptive action against Pakistan, and the possibility that the latter could transfer nuclear technology to “unstable Arab countries.”
Options presented to Reagan ranged from cutting off aid directly if Pakistan kept trying to procure sensitive technology to warning Zia that continued activities would “seriously jeopardize our security relationship.” Shultz did not make a recommendation in this paper, but he it was evident that he wanted to avoid action other than a warning so as not to jeopardize the relationship. Records of his talks with Zia on 6 December and Zia’s meeting with President Reagan the next day are not yet available, but the Kenneth Adelman memorandum produced below (see document 20) discloses that Reagan laid out specific parameters to Zia: no assembly or test of nuclear devices, no transfer of technology for such devices, no violation of international safeguards, and no unsafeguarded reprocessing. [10]
Document 17: “Punish an Indian Attack So Severely that it will be Deterred to Begin With”
Bureau of Intelligence and Research, U.S. Department of State, “Pakistan: Security Planning and the Nuclear Option,” Report 83-AR, 1983 [full date cut off copy], Limited Official Use
Source: Department of State FOIA release, copy courtesy of Jeffrey Richelson
Based on a contract study prepared by University of Illinois political scientist (presently affiliated with Brookings) Stephen P. Cohen, after he had made three visits to Pakistan, this report focuses on the Pakistani military’s approach to deterrence. While the Pakistani military had once emphasized the value of using force first, the danger of war with India has produced a strategic doctrine that stresses the “use of military force to deter an Indian attack.” This doctrinal shift was creating a consensus in the military on the value of a “modest, ‘limited’ [nuclear] weapons program.” Pakistani military leaders did not like nuclear weapons, but they believed that they would “enable them to do what their armored divisions and air force can no longer” do in conventional terms: “punish an Indian attack so severely that it will be deterred to begin with.”
On the problem of Pakistani command-and-control over nuclear weapons, the summary of Cohen’s report observed that “Pakistan’s military has done self-destructive things in the past, and one cannot assume that it will not do them in the future.” Yet with greater professionalism in the Army, it was not “likely to make [decisions on nuclear weapons] any more irresponsibility than other states confronted with the same perplexing set of security constraints.” Cohen did not believe that Washington could do much to reverse nuclearization in South Asia, but U.S. influence could help ensure that proliferation did not lead to greater instability, for example, by limiting the buildup of stockpiles and supporting regional “mutual balanced force reductions” arrangements.
Document 18: “Supplying Conventional Weapons … Can be a Positive Force Against Proliferation”
Hugh Montgomery, director, Bureau of Intelligence and Research, U.S. Department of State, to Ambassador Ronald Spiers, 17 February 1984, enclosing “India-Pakistan: Pressures for Nuclear Proliferation,” Report 778-AR, 10 February 1984, Limited Official Use
Source: Department of State FOIA release, copy courtesy of Jeffrey Richelson
This interesting review of the South Asian nuclear problem starts by exploring the India-Pakistan nuclear dynamic. If Pakistan tested a weapon, India might resist following through on a weapons option, but might begin a series of tests. Both countries could covertly begin a weapons program. Despite speculation about an Indian preemptive strike against Pakistani nuclear installations, such an occurrence was unlikely because of the serious risks for India, not least the spread of “deadly radiation poisoning.” While New Delhi had resisted internal pressures for weaponization, changes in the security environment could weaken resistance, for example, if relations with Beijing worsened or if Chinese-Soviet relations improved (which would make the Indians more worried about Moscow’s reliability). The INR analyst believed that Washington had the most “leverage” with Pakistan because of the latter’s dependence on U.S. supplies of conventional weapons. “Supplying conventional weapons to Pakistan can be a positive force against proliferation” because they “can give Pakistan sufficient confidence in its own security that it would find the nuclear option less attractive and unnecessary.” This may have been the basis of State Department thinking that not meeting Pakistani desiderata on such issues as the F-16 would be a blow to nuclear non-proliferation policy. The challenge, however, was to not over-arm Pakistan because that could threaten Indian security and “increase the danger of nuclear proliferation in South Asia.”
Document 19: Pakistan Has “Produced an Atomic Weapon”
Defense Intelligence Agency cable to [excised location], “Pakistan-China: Nuclear Weapons Production and Testing,” 7 December 1985, Secret, excised copy
Source: DIA FOIA release
Only months after Congress enacted the Pressler amendment, an intelligence source claimed that Pakistan with Chinese assistance had “produced an atomic weapon in early October.” DIA had received similar reports and was trying to confirm this one. That U.S. intelligence believed that Pakistan was producing enough HEU for at least one device becomes evident in the next document.
Document 20: “He Lied to Us Again”
Kenneth Adelman, director, Arms Control and Disarmament Agency, o Assistant to the President for National Security Affairs, “Pakistan’s Nuclear Weapons Programs and U.S. Security Assistance,” 16 June 1986, Top Secret
Source: MDR release
More declassification actions will elucidate what the United States discovered during 1982-1986 about the Pakistani nuclear program, the renewed efforts to prevent procurement of sensitive technology, and high-level pressures to discourage secret nuclear work, but this memorandum by ACDA director Adelman gives perspective on some developments after the Reagan-Zia meeting in late 1982. The points that President Reagan made to Zia in December 1982 were re-stated in a May 1984 “non-paper” and then refined the following September when Reagan informed Zia that enriching uranium above 5 percent would be just as problematic as unsafeguarded plutonium reprocessing. But Reagan never put serious pressure on Zia to comply.
According to Adelman, the Pakistanis had been producing enriched uranium above the five percent level and, after overcoming an important “hurdle,” were enriching uranium at levels high enough (presumably close to 90 percent) to produce “one or more nuclear devices.” Adelman insisted that Zia was lying to Washington about this and that these activities jeopardized U.S. aid to Pakistan. The problem was that Washington had only “jawboned” General Zia instead of applying real pressure, thus undermining Reagan’s credibility and reinforcing “Zia’s belief that he can lie to us with impunity.” This raised serious problems for Congressional approval of aid, not only for certifying that Pakistan did not “possess” an explosive device, but also for renewing the 1982 Foreign Assistance Act that had exempted Pakistan from more rigorous nonproliferation standards.
Adelman recommended the precise application of pressure—to give Zia the “stark choice” of continued aid or the enrichment program. The possibility that Zia might resist could make it necessary to “tough it out” with Congress to assure the continuity of aid. But Adelman thought it possible that pressure would work and that Zia would conclude that “payoff” of U.S. aid and military sales was too high to forego.
Document 21: “Annual certification … very problematic”
Briefing Book, “Visit of Prime Minister Junejo of Pakistan, July 15-21, 1986,” Secret
Source: MDR Release
With Prime Minister Junejo about to visit Washington ACDA director had suggested that the U.S. tell him that pending a policy review on the Pakistani nuclear program “all actions involving military sales” have been halted . But this harder-line view apparently found no takers because the State Department briefing book for the Junejo visit only suggested tacit threats, not the “stark choice” that Adelman had recommended, that certification was “very problematic” without “positive Pak actions to help convince the Congress” which meant “quiet Pak actions to restrain [the enrichment] program.”
On the status of the Pakistani program, the briefing book included an intelligence finding [page 39 of pdf] that if the Kahuta plant operated at capacity it could produce enough m for “several nuclear devices per year.” Nevertheless, it was “our assessment … that Pakistan does not possess a device.” The highest levels of the Department were taking the position that Pakistan was in compliance with the Pressler amendment.
Document 22: “Absolute Criticality … of Restraint”
State Department cable 229696 to U.S. Embassy France et al., “Visit of Pakistani Primin Mohammad Khan Junejo to Washington – 15-18 July 1986,” 23 July 1986, Secret
Source: MDR Release
The only record of the meetings with Junejo that is available so far is this telegram that went out to a number of embassies. Impressing administration officials who found him “astute and well briefed,” Junejo professed to be responsive to the U.S. emphasis on the “absolute criticality” of “restraint” in Pakistani nuclear activities. In meetings with the press, Junejo “specifically affirmed” commitment not to enrich uranium above the five percent level, but this would continue to be a problem.
Document 23: “He Has Approached a Threshold”
Fred McGoldrick, Acting Director, Office of Nonproliferation and Export Policy, to John Negroponte, Assistant Secretary of State for Environment, Oceans and Fisheries, “Pakistan,” 9 April 1987, Secret, enclosing memorandum from Richard Murphy, Assistant Secretary for Near East and South Asian Affairs, “Action Plan on Pakistan Nuclear And Security Problems,” to Secretary of State, n.d., Secret
Source: MDR Release
In the fall of 1986, Reagan certified Pakistan’s compliance with the Pressler amendment although it was manifest that U.S. aid was not preventing Pakistan from doing what it could to produce a nuclear device. With the White House’s request for a new assistance program under review, Congress was contemplating a shorter, two-year, waiver of the Symington amendment or possibly tying aid directly to a halt of enriched uranium production. In early 1987 the Pakistani nuclear program was getting in the news again—-statements by A.Q. Khan about a “nuclear weapons capability,” Zia declaring that “Pakistan can build a bomb whenever it wishes,” and a speech by Ambassador Dean Hinton stating that Pakistan’s nuclear efforts were “inconsistent” with a peaceful program—which could only raise Congressional objections to aid to Pakistan. [11] In this context, according to Assistant Secretary Murphy, the danger was that Zia “has approached a threshold which he cannot cross without blatantly violating his pledge not to embarrass the President.”
Arguing that the administration needed “to obtain specific actions demonstrating restraint,” Murphy acknowledged that Pakistan was “unlikely” to do so, especially because Zia had “not so far responded constructively” to previous requests. Nevertheless, he proposed an “action plan” that included a new demarche on enrichment and other “nuclear firebreaks,” a message to India also asking for “restraint,” a “Congressional game plan,” and a presidential envoy to “engage” both India and Pakistan in the nuclear issue.
With the U.S. considering sales of airborne early warning aircraft (AEW) to Pakistan, Richard Kennedy, the ambassador-at-large for nonproliferation matters, had suggested that Washington directly link the sales to “Pakistani action on nonproliferation,” but other officials opposed such linkage. Perhaps Murphy raised the issue to see if Shultz had any interest in pursuing it.
What action Shultz may have taken on Murphy’s proposal remains to be learned, but any pressure exerted was likely to have been weak. Later in 1987, Reagan certified that Pakistan did not possess a nuclear advice; the aid kept flowing.
NOTES
[1] Dennis Kux,The United States and Pakistan, 1947-2000: Disenchanted Allies (Washington, D.C.: Woodrow Wilson Center Press; Baltimore : Johns Hopkins University Press, 2001), 276-277; Adrian Levy and Catherine Scott-Clark, Deception: Pakistan, the United States, and the Secret Trade in Nuclear Weapons (New York: Walker & Co.: 2007), 116; David Armstrong and Joseph Trento, America and the Islamic Bomb: The Deadly Compromise (Hanover NH: Steerforth Press, 2007), 122-137.
[3] Kux, The United States and Pakistan, 282-286; Armstrong and Trento, America and the Islamic Bomb, 142-154, and Levy and Scott-Clark, Deception, 156-163.
[4] For details on the Shahi-Vance-Smith talks, see Kux, The United States and Pakistan. 240-241. For Smith’s report on his talks, see http://www.gwu.edu/~nsarchiv/nukevault/ebb333/index.htm, document 45.
[6] For detection of Pakistan’s test site, see Jeffrey Richelson, Spying on the Bomb: American Nuclear Intelligence from Nazi Germany to Iran and North Korea (New York: W.W. Norton, 2006), 341.
[7] David Albright, Peddling Peril: How the Secret Nuclear Trade Arms America’s Enemies (New York: Free Press, 2010), 50.
[8] For the Pakistani purchasing networks, see BrunoTertrais, “Not a ‘Wal-Mart’, but an ‘Imports-Exports Enterprise’: Understanding the Nature of the A.Q. Khan Network,”Strategic Insights (August 2007) http://www.nps.edu/Academics/centers/ccc/publications/OnlineJournal/2007/Aug/tertraisAug07.pdf . See also Albright, Peddling Peril, 48.
[9] T. V. Paul, “influence through Arms Transfers: Lessons from the US-Pakistani Relationship,” Asian Survey 32 (Dec. 1992), 1086.
[10] Shultz does not mention his 1982 meeting with Zia in his memoir, Turmoil and Triumph: My Years As Secretary of State (New York: Charles Scribner’s Sons, 1993), although at 493-494, he covers a 1984 discussion after Indira Gandhi’s funeral. Zia said that Pakistan was “nowhere near” building a nuclear weapon and that “We have no intention of making such a weapon.”
Dirty Little Secrets – Full Movie
FEMEN protests against UEFA EUROCUP 2012
Cryptome unveils Cyberwarhawks
Cyberwarhawks
http://www.hsgac.senate.gov/imo/media/doc/CYBER%20letter%20from%20top%20security%20guys.pdf
![[Image]](https://i0.wp.com/cryptome.org/2012/06/cyberwarhawks.jpg)
http://www.hsgac.senate.gov/issues/cybersecurity
United States Senate Homeland Security and Governmental Affairs Committee
Cybersecurity
Last February, in the 112th Congress, Senators Lieberman, Collins, and Carper introduced The Cybersecurity and Internet Freedom Act, S.413, which was very similar to the Cyber Space as a National Asset legislation. Since other committees had related legislation, Majority Leader Reid directed all committees of jurisdiction to come together and produce a single bill. That bill is the Cybersecurity Act of 2012, S. 2105, which was introduced February 14, 2012, by Senators Lieberman, Collins, Rockefeller, and Feinstein.
The measure would protect federal civilian systems and the systems of the nation’s most critical infrastructure, most ofs which is owned by the private sector. The Cybersecurity Act of 2012 is the result of months of negotiations with other Committees of jurisdiction; the energy, financial services, and chemical industries; national security and privacy and civil liberties groups; and a number of other government agencies. The Senate is expected to debate the measure in the coming weeks. Read letters of praise and support below.
The FBI against Cybercrimes
 |
|---|
Update on March 12, 2012: To assist victims affected by the DNSChanger malicious software, the FBI obtained a court order authorizing the Internet Systems Consortium (ISC) to deploy and maintain temporary clean DNS servers. This solution is temporary, providing additional time for victims to clean affected computers and restore their normal DNS settings. The clean DNS servers will be turned off on July 9, 2012, and computers still impacted by DNSChanger may lose Internet connectivity at that time. |
Operation Ghost Click
International Cyber Ring That Infected Millions of Computers Dismantled
11/09/11
Six Estonian nationals have been arrested and charged with running a sophisticated Internet fraud ring that infected millions of computers worldwide with a virus and enabled the thieves to manipulate the multi-billion-dollar Internet advertising industry. Users of infected machines were unaware that their computers had been compromised—or that the malicious software rendered their machines vulnerable to a host of other viruses.
Details of the two-year FBI investigation called Operation Ghost Click were announced today in New York when a federal indictment was unsealed. Officials also described their efforts to make sure infected users’ Internet access would not be disrupted as a result of the operation.
| FBI Statement: Janice Fedarcyk, New York Assistant Director in Charge
|
|---|
The indictment, said Janice Fedarcyk, assistant director in charge of our New York office, “describes an intricate international conspiracy conceived and carried out by sophisticated criminals.” She added, “The harm inflicted by the defendants was not merely a matter of reaping illegitimate income.”
Beginning in 2007, the cyber ring used a class of malware called DNSChanger to infect approximately 4 million computers in more than 100 countries. There were about 500,000 infections in the U.S., including computers belonging to individuals, businesses, and government agencies such as NASA. The thieves were able to manipulate Internet advertising to generate at least $14 million in illicit fees. In some cases, the malware had the additional effect of preventing users’ anti-virus software and operating systems from updating, thereby exposing infected machines to even more malicious software.
“They were organized and operating as a traditional business but profiting illegally as the result of the malware,” said one of our cyber agents who worked the case. “There was a level of complexity here that we haven’t seen before.”
DNS—Domain Name System—is a critical Internet service that converts user-friendly domain names, such as http://www.fbi.gov, into numerical addresses that allow computers to talk to each other. Without DNS and the DNS servers operated by Internet service providers, computer users would not be able to browse websites or send e-mail.
| Success Through Partnerships
A complex international investigation such as Operation Ghost Click could only have been successful through the strong working relationships between law enforcement, private industry, and our international partners. Announcing today’s arrests, Preet Bharara, (above left) U.S. Attorney for the Southern District of New York, praised the investigative work of the FBI, NASA’s Office of Inspector General (OIG), the Estonian Police and Border Guard Board, and he specially thanked the National High Tech Crime Unit of the Dutch National Police Agency. In addition, the FBI and NASA-OIG received assistance from multiple domestic and international private sector partners, including Georgia Tech University, Internet Systems Consortium, Mandiant, National Cyber-Forensics and Training Alliance, Neustar, Spamhaus, Team Cymru, Trend Micro, University of Alabama at Birmingham, and members of an ad hoc group of subject matter experts known as the DNS Changer Working Group (DCWG). |
|---|
DNSChanger was used to redirect unsuspecting users to rogue servers controlled by the cyber thieves, allowing them to manipulate users’ web activity. When users of infected computers clicked on the link for the official website of iTunes, for example, they were instead taken to a website for a business unaffiliated with Apple Inc. that purported to sell Apple software. Not only did the cyber thieves make money from these schemes, they deprived legitimate website operators and advertisers of substantial revenue.
The six cyber criminals were taken into custody yesterday in Estonia by local authorities, and the U.S. will seek to extradite them. In conjunction with the arrests, U.S. authorities seized computers and rogue DNS servers at various locations. As part of a federal court order, the rogue DNS servers have been replaced with legitimate servers in the hopes that users who were infected will not have their Internet access disrupted.
It is important to note that the replacement servers will not remove the DNSChanger malware—or other viruses it may have facilitated—from infected computers. Users who believe their computers may be infected should contact a computer professional. They can also find additional information in the links on this page, including how to register as a victim of the DNSChanger malware. And the FBI’s Office for Victim Assistance will provide case updates periodically at 877-236-8947.
Resources:
– Press release
– Statement by New York ADIC Janice Fedarcyk
– Learn more about DNSChanger malware and how it can affect your computer
– Check your computer’s DNS settings
– Register as a victim of the DNSChanger malware
– Cyber Crimes stories
Every Picture Tells a Story – Full Movie
TOP-SECRET from the FBI – Economic Espionage
 |
|---|
| American industry and private sector businesses are the choice target of foreign intelligence agencies, criminals, and industry spies. The above image on the cost of economic espionage to the U.S. can currently be seen on digital billboards—courtesy of Clear Channel and Adams Outdoor Advertising—in several regions of the country with a concentration of high-tech research and development companies, laboratories, major industries, and national defense contractors. If you suspect economic espionage, report it to the FBI at tips.fbi.gov. | Download high-resolution image |
Economic Espionage
How to Spot a Possible Insider Threat
05/11/12
This past February, five individuals and five companies were charged with economic espionage and theft of trade secrets for their roles in a long-running effort to obtain information for the benefit of companies controlled by the government of the People’s Republic of China.

What Do They Want From Us? According to the latest economic espionage report to Congress from the Office of the National Counterintelligence Executive, although foreign collectors will remain interested in all aspects of U.S. economic activity and technology, they’re probably most interested in the following areas: – Information and communications technology, which form the backbone of nearly every other technology; – Business information that pertains to supplies of scarce natural resources or that provides global actors an edge in negotiations with U.S. businesses or the U.S. government; – Military technologies, particularly marine systems, unmanned aerial vehicles, and other aerospace/aeronautic technologies; and – Civilian and dual-use technologies in fast-growing sectors like clean energy, health care/pharmaceuticals, and agricultural technology. |
|---|
According to the superseding indictment, the PRC government was after information on chloride-route titanium dioxide (TiO2) production capabilities. TiO2 is a commercially valuable white pigment with numerous uses, including coloring paints, plastics, and paper. DuPont, a company based in Wilmington, Delaware, invented the chloride-route process for manufacturing TiO2 and invested heavily in research and development to improve the process over the years. In 2011, the company reported that its TiO2 trade secrets had been stolen.
Among the individuals charged in the case? Two long-time DuPont employees…one of whom pled guilty in fairly short order.
Foreign economic espionage against the U.S. is a significant and growing threat to our country’s economic health and security…and so is the threat from corporate insiders willing to carry it out.
And because we’re now in the digital age, insiders—who not so many years ago had to photocopy and smuggle mountains of documents out of their offices—can now share documents via e-mail or download them electronically on easy-to-hide portable devices.
Why do insiders do it? Lots of reasons, including greed or financial need, unhappiness at work, allegiance to another company or another country, vulnerability to blackmail, the promise of a better job, and/or drug or alcohol abuse.
How to stop them? Obviously, a strong organizational emphasis on personnel and computer security is key, and the FBI conducts outreach efforts with industry partners—like InfraGard—that offer a variety of security and counterintelligence training sessions, awareness seminars, and information.
| Successful Investigation of ‘Insiders’
– In Detroit, a car company employee copied proprietary documents, including some on sensitive designs, to an external hard drive…shortly before reporting for a new job with a competing firm in China. Details – In Indianapolis, an employee of an international agricultural business stole trade secrets on organic pesticides from his employer and shared them with individuals in China and Germany. Details In Boston, a technology company employee e-mailed an international consulate in that city and offered proprietary business information. He later provided pricing and contract data, customer lists, and names of other employees…to what turned out to be a federal undercover agent. Details All three subjects pled guilty. But in two of the three cases, the stolen secrets probably ended up in the hands of global businesses that will use them to attempt to gain an unfair competitive edge over the United States. Podcasts Gotcha: Special agent discusses 2010 economic espionage case. FBI, This Week: The FBI is seeing an increase in cases involving spying from foreign intelligence agencies, criminals, and others who wish America harm. |
|---|
You can help as well. In our experience, those who purloin trade secrets and other sensitive information from their own companies and sell them overseas exhibit certain behaviors that co-workers could have picked up on ahead of time, possibly preventing the information breaches in the first place. Many co-workers came forward only after the criminal was arrested. Had they reported those suspicions earlier, the company’s secrets may have been kept safe.
Here are some warning signs that MAY indicate that employees are spying and/or stealing secrets from their company:
- They work odd hours without authorization.
- Without need or authorization, they take proprietary or other information home in hard copy form and/or on thumb drives, computer disks, or e-mail.
- They unnecessarily copy material, especially if it’s proprietary or classified.
- They disregard company policies about installing personal software or hardware, accessing restricted websites, conducting unauthorized searches, or downloading confidential material.
- They take short trips to foreign countries for unexplained reasons.
- They engage in suspicious personal contacts with competitors, business partners, or other unauthorized individuals.
- They buy things they can’t afford.
- They are overwhelmed by life crises or career disappointments.
- They are concerned about being investigated, leaving traps to detect searches of their home or office or looking for listening devices or cameras.
If you suspect someone in your office may be committing economic espionage, report it to your corporate security officer and to your local FBI office, or submit a tip online at https://tips.fbi.gov/.
Megapark 2012 – Sexy Russian Football Girls posing – UEFA2012 EM – Video
Larry King Interview with Admiral General Aladeen – Sacha Barron Cohen Video
Family Affair – Full Movie
Uncensored – FEMEN Female Fighters
TOP-SECRET from the FBI – Former Chief Financial Officer of Taylor, Bean, & Whitaker Sentenced to 60 Months in Prison for Fraud Scheme
WASHINGTON—Delton de Armas, a former chief financial officer (CFO) of Taylor, Bean, & Whitaker Mortgage Corp. (TBW), was sentenced today to 60 months in prison for his role in a more than $2.9 billion fraud scheme that contributed to the failure of TBW.
De Armas was sentenced today by U.S. District Judge Leonie M. Brinkema in the Eastern District of Virginia. The sentence was announced today by Assistant Attorney General Lanny A. Breuer of the Criminal Division; U.S. Attorney Neil H. MacBride for the Eastern District of Virginia; Christy Romero, Special Inspector General, Office of the Special Inspector General for the Troubled Asset Relief Program (SIGTARP); Assistant Director in Charge James W. McJunkin of the FBI’s Washington Field Office; David A. Montoya, Inspector General of the Department of Housing and Urban Development (HUD-OIG); Jon T. Rymer, Inspector General of the Federal Deposit Insurance Corporation (FDIC-OIG); Steve A. Linick, Inspector General of the Federal Housing Finance Agency (FHFA-OIG); and Richard Weber, Chief of the Internal Revenue Service Criminal Investigation (IRS-CI).
De Armas, 41, of Carrollton, Texas, pleaded guilty in March to one count of conspiracy to commit bank and wire fraud and one count of making false statements.
“For years, Mr. de Armas, the CFO of one of the country’s largest private mortgage companies, helped defraud financial institutions by concealing from them billions of dollars in losses,” said Assistant Attorney General Breuer. “His lies and deceits contributed to the devastating losses suffered by major institutional investors. As a consequence for his crimes, he will now spend the next five years of his life behind bars.”
“As CFO, Mr. de Armas could have—and should have—put a stop to the massive fraud at TBW the moment he discovered it,” said U.S. Attorney MacBride. “Instead, he and others lied for years on end to investors, banks, regulators, and auditors and caused more than $2.4 billion in losses to major financial institutions.”
“Rather than blow the whistle on billions of dollars in fraud, de Armas chose to help conceal it,” said Special Inspector General Romero. “This CFO lied to investors, banks, regulators, and auditors to cover up the massive fraud scheme which resulted in the failure of both TBW and Colonial Bank. The court’s decision to sentence de Armas to five years in prison reflects the seriousness of his role as a gatekeeper within TBW and the contribution of his crime to our nation’s financial crisis.”
“The actions of Mr. De Armas and others resulted in the loss of billions of dollars to major financial institutions,” said Assistant Director in Charge McJunkin. “Today’s sentence serves as a warning to anyone who attempts to take advantage of investors and our banking system. Together with our law enforcement partners, the FBI will pursue justice for anyone involved in such fraudulent schemes.”
According to court documents, de Armas joined TBW in 2000 as its CFO and reported directly to its chairman, Lee Bentley Farkas, and later to its CEO, Paul Allen. He previously admitted in court that from 2005 through August 2009, he and other co-conspirators engaged in a scheme to defraud financial institutions that had invested in a wholly-owned lending facility called Ocala Funding. Ocala Funding obtained funds for mortgage lending for TBW from the sale of asset-backed commercial paper to financial institutions, including Deutsche Bank and BNP Paribas. The facility was managed by TBW and had no employees of its own.
According to court records, shortly after Ocala Funding was established, de Armas learned there were inadequate assets backing its commercial paper, a deficiency referred to internally at TBW as a “hole” in Ocala Funding. De Armas knew that the hole grew over time to more than $700 million. He learned from the CEO that the hole was more than $1.5 billion at the time of TBW’s collapse. De Armas admitted he was aware that, in an effort to cover up the hole and mislead investors, a subordinate who reported to him had falsified Ocala Funding collateral reports and periodically sent the falsified reports to financial institution investors in Ocala Funding and to other third parties. De Armas acknowledged that he and the CEO also deceived investors by providing them with a false explanation for the hole in Ocala Funding.
De Armas also previously admitted in court that he directed a subordinate to inflate an account receivable balance for loan participations in TBW’s financial statements. De Armas acknowledged that he knew that the falsified financial statements were subsequently provided to Ginnie Mae and Freddie Mac for their determination on the renewal of TBW’s authority to sell and service securities issued by them.
In addition, de Armas admitted in court to aiding and abetting false statements in a letter the CEO sent to the U.S. Department of Housing and Urban Development, through Ginnie Mae, regarding TBW’s audited financial statements for the fiscal year ending on March 31, 2009. De Armas reviewed and edited the letter, knowing it contained material omissions. The letter omitted that the delay in submitting the financial data was caused by concerns its independent auditor had raised about the financing relationship between TBW and Colonial Bank and its request that TBW retain a law firm to conduct an internal investigation. Instead, the letter falsely attributed the delay to a new acquisition and TBW’s switch to a compressed 11-month fiscal year.
“We are pleased to have joined our law enforcement colleagues in bringing Mr. de Armas to justice,” said Inspector General Rymer. “The former chief financial officer’s actions contributed to one of the largest bank frauds in the country and led to the demise of TBW. His punishment, along with the earlier sentencings of other co-conspirators involved in the Colonial Bank and TBW scheme, sends a clear message that those who abuse their positions of trust and seek to undermine the integrity of the financial services industry will be held accountable. We will continue to pursue such cases in the interest of ensuring the safety and soundness of our nation’s banks and the strength of the financial services industry as a whole.”
“Delton de Armas was a key player in the TBW fraud; the significant sentence of 60 months handed down today appropriately takes that role into account,” said Inspector General Linick.
In April 2011, a jury in the Eastern District of Virginia found Lee Bentley Farkas, the chairman of TBW, guilty of 14 counts of conspiracy, bank, securities, and wire fraud. On June 30, 2011, Judge Brinkema sentenced Farkas to 30 years in prison. In addition, six individuals have pleaded guilty for their roles in the fraud scheme, including: Paul Allen, former chief executive officer of TBW, who was sentenced to 40 months in prison; Raymond Bowman, former president of TBW, who was sentenced to 30 months in prison; Desiree Brown, former treasurer of TBW, who was sentenced to six years in prison; Catherine Kissick, former senior vice president of Colonial Bank and head of its Mortgage Warehouse Lending Division (MWLD), who was sentenced to eight years in prison; Teresa Kelly, former operations supervisor for Colonial Bank’s MWLD, who was sentenced to three months in prison; and Sean Ragland, a former senior financial analyst at TBW, who was sentenced to three months in prison.
The case is being prosecuted by Deputy Chief Patrick Stokes and Trial Attorney Robert Zink of the Criminal Division’s Fraud Section and Assistant U.S. Attorneys Charles Connolly and Paul Nathanson of the Eastern District of Virginia. This case was investigated by SIGTARP, FBI’s Washington Field Office, FDIC-OIG, HUD-OIG, FHFA-OIG, and the IRS-Criminal Investigation. The Financial Crimes Enforcement Network (FinCEN) of the Department of the Treasury also provided support in the investigation. The department would also like to acknowledge the substantial assistance of the SEC in the investigation of the fraud scheme.
This prosecution was brought in coordination with President Barack Obama’s Financial Fraud Enforcement Task Force. President Obama established the interagency Financial Fraud Enforcement Task Force to wage an aggressive, coordinated, and proactive effort to investigate and prosecute financial crimes. The task force includes representatives from a broad range of federal agencies, regulatory authorities, inspectors general, and state and local law enforcement who, working together, bring to bear a powerful array of criminal and civil enforcement resources. The task force is working to improve efforts across the federal executive branch and, with state and local partners, to investigate and prosecute significant financial crimes, ensure just and effective punishment for those who perpetrate financial crimes, combat discrimination in the lending and financial markets, and recover proceeds for victims of financial crimes.
Liebe Freunde von der STASI & CO
Sehr wenig verehrenswürdige STASI-“GoMoPa”-Freunde und deren Allierte,
vor 2 Jahren sagte ich, ich werde Euch outen und dies habe ich trotz all Eurer
Morddrohungen, Rufmorde und vieler anderer Schädigungen getan.
Und es kommt noch besser !
Die Vorfreude ist doch die schönste Freude !
Freuen wir uns doch alle !
Herzlichst
Bernd Pulch
Magister Artium, Publizistik, Germanistik, Komparatistik
Fatal Choice – Full Movie
Nach KGB-STASI-Art – FEMEN-Alexandra Shevchenko, Yana Zhdanova und Anna Bolshakova gekidnappt
-

Die Femen-Aktivistinnen Alexandra Shevchenko, Yana Zhdanova und Anna Bolshakova sind spurlos verschwunden:
Drei Mitglieder der ukrainischen Frauengruppe Femen sind in der Stadt Donezk spurlos verschwunden. Möglicherweise wurden sie entführt.
Eine Gruppe von 15 Männern habe die Aktivistinnen seit deren Ankunft in dem ostukrainischen EM-Spielort verfolgt, teilte die Organisation mit. In Donezk hatten die Frauen einen Protest gegen die Fußball-Europameisterschaft geplant.
Am Nachmittag sei der Kontakt zur Aktivistin Alexandra Shevchenko abgebrochen, teilte Femen am Freitagabend weiter mit. Eine Stunde später konnten dann auch Anna Bolshakova und Yana Zhdanovea nicht mehr erreicht werden.
Die örtliche Miliz suche nach den verschwundenen Frauen, meldete die Agentur Interfax.
Femen-Aktivistinnen hatten zuvor schon in Warschau und Kiew gegen Sextourismus und Prostitution demonstriert, vor den Stadien blank gezogen.
Am 10. Juni tauchten sie auf der Reeperbahn in Hamburg auf, nannten Prostitution eine neue Form des Faschismus.
Im Dezember 2011 wurden drei Femen-Mitglieder nach einer Protestaktion gegen den weißrussischen Präsidenten Alexander Lukaschenko aus Minsk verschleppt.
Bei Temperaturen um den Gefrierpunkt seien die Frauen in einem Wald mit Öl übergossen und mit dem Tode bedroht worden, hieß es seinerzeit. Die Aktivistinnen wurden nackt ausgesetzt, konnten aber wieder Kontakt zu ihrer Organisation aufnehmen.
Uncensored – FEMEN Bewegung in Ukrain
http://www.dailymotion.com/video/xnj95w_femen-bewegung-in-ukraine_sexy?search_algo=1
FEMEN Bewegung in Ukraine: Die Organisation tritt für die Selbstbestimmung des Menschen,
insbesondere der Frauen ein.
Sie ist international für Oben-ohne Proteste gegen Wahlfälschungen, Sextourismus, Sexismus, Wladimir Putin, geplante staatliche Verhaltensvorschriften während der Fußball-Europameisterschaft 2012 u.a. bekannt geworden
Uncensored – FEMEN Protest Abortion Ban in Kiev
FEMEN Protest Abortion Ban in Kiev
A topless activists of Ukrainian feminist movement Femen holds a placard which translates as ‘I give birth not for you’ as others strike the bells after they barricaded St. Sophia’s cathedral bell tower in Kiev on April 10, 2012. The protest was held to oppose a draft law being proposed to prohibit abortions.
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-kiev/femen-kiev-5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-kiev/femen-kiev-7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012-info/femen-kiev/femen-kiev-6.jpg)

![[Image]](https://i0.wp.com/cryptome.org/2012/06/wikileaks-trap1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/2012/06/wikileaks-trap2.jpg)











 “Today, with the flip of a switch, the FBI and our partners dismantled the Rove criminal enterprise. Thanks to the collective effort across the U.S. and in Estonia, six leaders of the criminal enterprise have been arrested and numerous servers operated by the criminal organization have been disabled. Additionally, thanks to a coordinated effort of trusted industry partners, a mitigation plan commenced today, beginning with the replacement of rogue DNS servers with clean DNS servers to keep millions online, while providing ISPs the opportunity to coordinate user remediation efforts.”
“Today, with the flip of a switch, the FBI and our partners dismantled the Rove criminal enterprise. Thanks to the collective effort across the U.S. and in Estonia, six leaders of the criminal enterprise have been arrested and numerous servers operated by the criminal organization have been disabled. Additionally, thanks to a coordinated effort of trusted industry partners, a mitigation plan commenced today, beginning with the replacement of rogue DNS servers with clean DNS servers to keep millions online, while providing ISPs the opportunity to coordinate user remediation efforts.” 



You must be logged in to post a comment.