Become a Patron!
True Information is the most valuable resource and we ask you to give back.
MS-ISAC Intel Paper: Common Cyber Threats to Universities
The following document was obtained from the website of the Missouri Department of Higher Education.
Common Cyber Threats to Universities
Page Count: 10 pages
Date: February 23, 2016
Restriction: For Official Use Only
Originating Organization: Multi-State Information Sharing and Analysis Center
File Type: pdf
File Size: 773,757 bytes
File Hash (SHA-256): 638A6DB7C124E3424BCD2627D2212274029FFAFBE9D93D82FC8BCA4B5676CC89
(U//FOUO) TLP: AMBER The Risk: The Multi-State Information Sharing and Analysis Center (MS-ISAC) assesses with high confidence that cyber threat actors routinely target universities, for the purposes of financial gain, notoriety, or entertainment, and often to gain access to personally identifiable information (PII) and/or sensitive research. MS-ISAC believes universities are inherently more vulnerable to cyber targeting than other state, local, tribal, and territorial (SLTT) government entities, due to the non-restrictive research environment with less compartmentalization and less access restriction, which results in more opportunity for infection, and when infection occurs, easier transmission through a network.
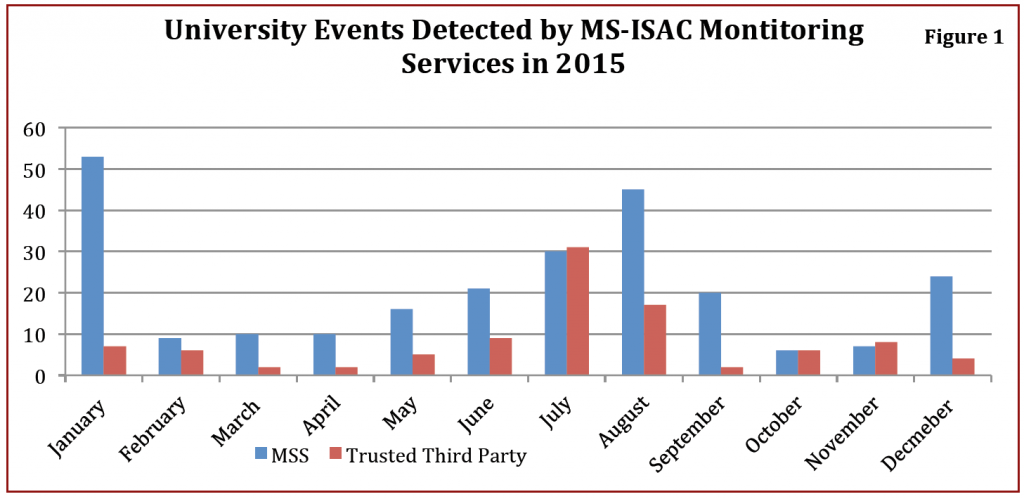
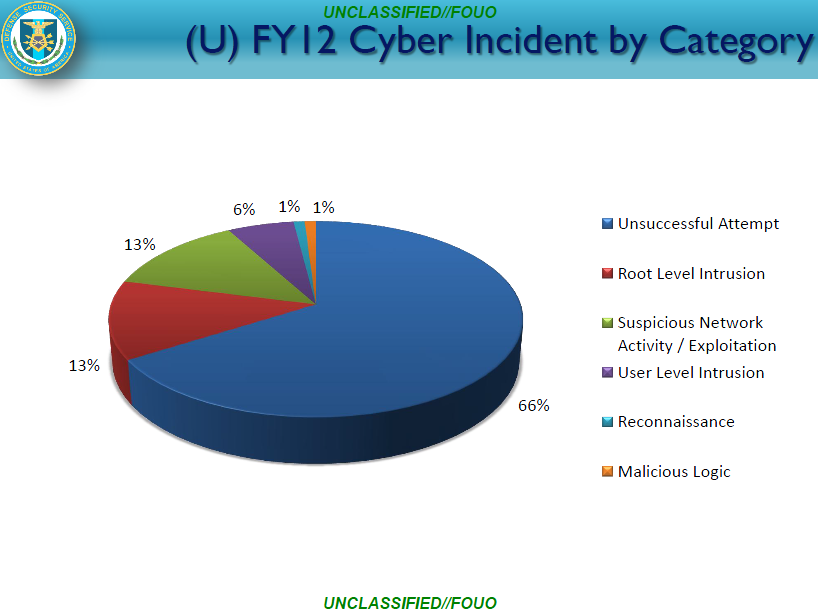
• Incident frequency remained relatively consistent in 2015 compared to 2014, but incidents spiked in July and August 2015 as seen in Figure 1. The August spike may be partially caused by the return of students to campus and increased traffic on university networks.
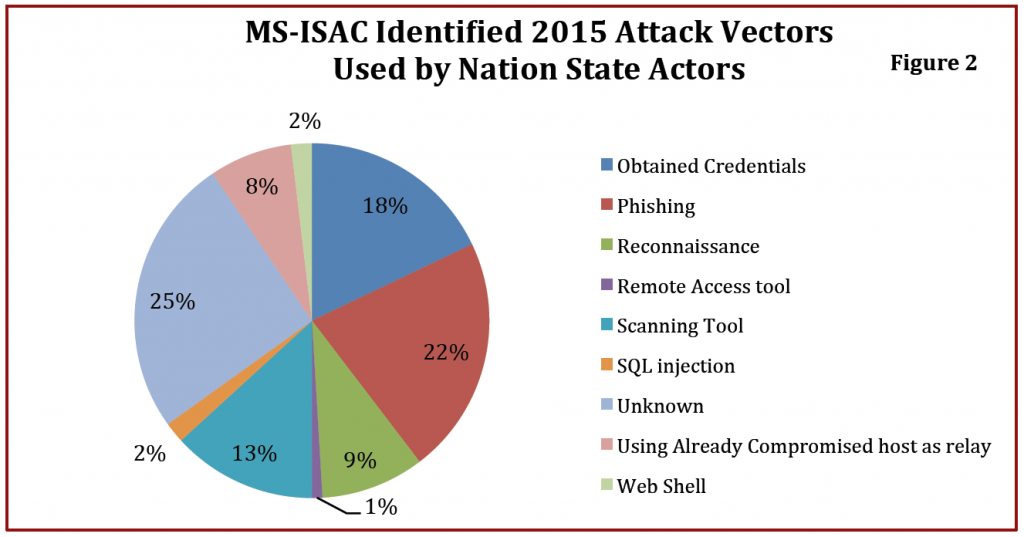
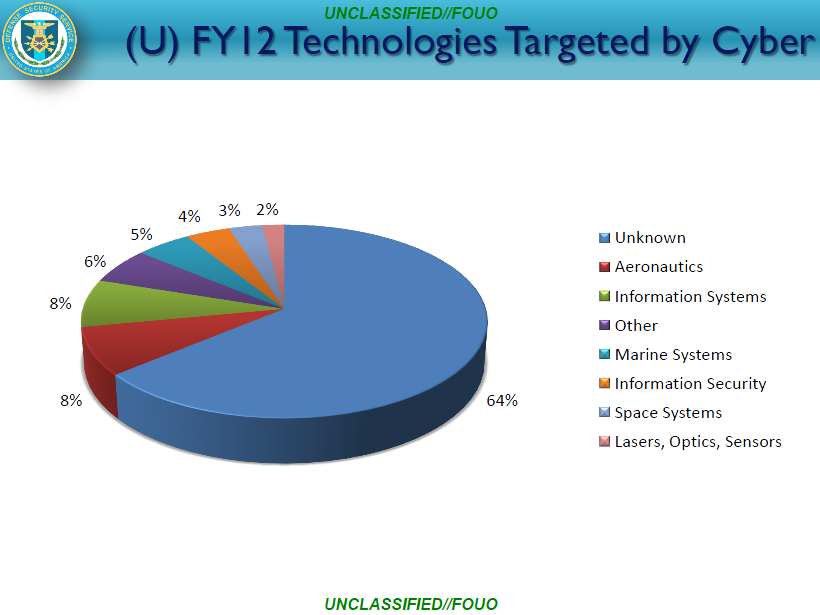
• Nation-‐state actors pose the gravest threat to universities systems and the greater national security interest. This is due to nation-‐state actor’s more advanced skill sets and tendency to strategically target universities with developed research programs, or those that are Cleared Defense Contractors (CDC) or Centers for Academic Excellence (CAE), which may contain engineering, health, science or defense research, crucial to the U.S. National Security interest.
• Based on MS-‐ISAC data, universities are most likely to be targeted via a phishing email, and malware infection is the most likely tactic, technique or procedure (TTP) a university will experience.
Cyber Monday 2017, Cyber Bullying, Cyber Security, Cyber Security Jobs, Cyber High, Cyber Monday 3s, Cyber Security Salary, Cyberpower, Cyber Goth, Cyber Security Degree, Cyber Attack, Cyber Awareness, Cyber Acoustics, Cyber Academy, Cyber Attack Map, Cyber Attack 2017, Cyberark, Cyber Attack On Electrical Grid, Cyber Angel, Cyber Awareness Army, Cyber Bullying, Cyber Bullying Statistics, Cyber Bullying Facts, Cyberbully, Cyber Bullying Stories, Cyber Bullying Quotes, Cyber Bullying Articles, Cyber Bullying Laws Michigan, Cyber Bites, Cyber Bullying Essay, Cyber Chase, Cybercoders, Cyber Chip, Cyber Crime, Cyber Check, Cyber Cafe, Cyber City Oedo 808, Cyber Cafe Near Me, Cyber Command, Cyber Currency, Cyber Dust, Cyber Dragon Infinity, Cyber Dragon, Cyber Dragon Deck, Cyberduck, Cyber Definition, Cyber Dragon Nova, Cyber Dojo, Cyber Dragon Deck 2017, Cyber Defense Jobs, Cyber End Dragon, Cyber Education Center, Cyber Education, Cyber Espionage, Cyber Education Center Lansing Mi, Cyber Ethics, Cyber Extortion, Cyber Eltanin, Cyber Engineering, Cyber Etymology, Cyber Forensics, Cyber Five, Cyber Force, Cyber Forensics Jobs, Cyber Formula, Cyber Font, Cyber Frauds, Cyber Forensics Degree, Cyberfair, Cyber Footprint, Cyber Goth, Cyberghost, Cyber Goth Dance, Cyber Ghetto, Cybergrants, Cyber Gadget, Cyber Goth Girl, Cyber Gadget Retro Freak, Cyber Goth Clothing, Cyber Gears, Cyber Hymnal, Cyber Harassment, Cyber High, Cyber Hacking, Cyber Hug, Cyber Harpie Lady, Cyber Hygiene, Cyber Helmet, Cyber Harassment Laws, Cyber Harassment Michigan, Cyber Insurance, Cyber Inc, Cyber Intelligence, Cyber Insurance Policy, Cyber Investigation, Cyber Intelligence Analyst, Cyber Illinois, Cyber Intelligence Degree, Cyber Insurance Providers, Cyber Infrastructure, Cyber Jar, Cyber Jobs, Cyberjapan Dancers, Cyber Junkie, Cyber Jack, Cyber Jihad, Cyber Jesus, Cyberjudas, Cyber Jar Banned, Cyber Jason, Cyber Kill Chain, Cyberknife, Cyber Knight, Cyber Kotori, Cyber Key, Cyber Kill Chain Model, Cyber King, Cyber Kidnapping, Cyber Kong, Cyber Kitty, Cyber Liability Insurance, Cyber Law, Cyberlink, Cyber Liquids, Cyber Love Live, Cyber Laser Dragon, Cyberlock, Cyber Liability Insurance Cost, Cyber Lawyer, Cyberlink Powerdirector, Cyber Monday 2017, Cyber Monday 3s, Cyber Monday, Cyber Monday 1s, Cyber Monday 2016, Cyber Meaning, Cyber Michigan, Cyber Marvel, Cyberman, Cybermen, Cyber News, Cyber Nico, Cyber Ninja, Cyber Nations, Cyber Ninja Hanzo, Cyber Nuke, Cyber Network, Cyber Nozomi, Cyber Net, Cyber Nanny, Cyber Operations, Cyber Optics Detroit, Cyber Operations Officer, Cyber Optics, Cyber Ops, Cyber Operations Specialist, Cyber Outlet, Cyber Ogre, Cyber Operations Specialist Salary, Cyber Officer Air Force, Cyberpower, Cyberpunk, Cyber Police, Cyber Physical Systems, Cyberpatriot, Cyber Pegasus, Cyberpunk 2077, Cyber Playground, Cyberpower Ups, Cyber Pink, Cyber Quest, Cyberq, Cyber Quest Soaring Eagle, Cyber Quotes, Cyber Queen, Cyberquery, Cybex Q Cloud, Cyber Questions, Cyber Quest Fort Gordon, Cyberq Manual, Cyber Research, Cyber Risk, Cyber Resilience, Cyber Range, Cyber Risk Management, Cyber Rain, Cyber Recruiter, Cyber Risk Insurance, Cyber Repair Plant, Cyber Rider Turbo, Cyber Security, Cyber Security Jobs, Cyber Security Salary, Cyber Security Degree, Cyber Security Training, Cyber Security News, Cyber Stalking, Cyber Security Certifications, Cyber Security Companies, Cyber Safety, Cyber Terrorism, Cyber Tech, Cyber Threat, Cyber Transport Systems, Cyber Terrorism Definition, Cyber Terminators, Cyber Threat Intelligence, Cyber Technology, Cyber Theft, Cyber Threat Alliance, Cyber Umi, Cyber University, Cyber U, Cyber Ups, Cyber Bullying, Cyber Umi Cosplay, Cyber Underground, Cyber Unit, Cyber Usa, Cyber Underwriter Salary, Cyber Valley, Cyber Vandalism, Cyber Violence, Cyber Vpn, Cyber Vulnerability, Cyber Victimization, Cyber Village Academy, Cyber Virus, Cyber Vision, Cyber Vulnerability Assessment, Cyber Warfare, Cyberweld, Cyber Woman With Corn, Cyber World, Cyber Warfare Definition, Cyber World Institute, Cyber Warrior, Cyber Weapons, Cyber Wars, Cyber Wallpaper, Cyber X, Cyber Xmen, Cyber X Games, Cyber X Link, Cyber X Designs, Cyber X 3d, Cyborg X Trailer, Cyber X Internet Cafe, Cyber X Games 2017, Cyber Xl, Cyber Yugioh, Cyber Yellow, Cyber Yog, Cyber Yugioh Cards, Cyber Yankee, Cyber Yankee 2017, Cyber Yellow Vans, Cyber Youtube, Cyber Youcam, Cyber You, Cyber Zilla, Cyber Zone, Cyber Zarya, Cyber Zombie, Cyber Z, Cyber Zoom, Cyberzone Internet Cafe, Cyber Zone Hours, Cyber Zilla Toy, Cyber Zone Opelika, Threat Definition, Threat Level Midnight, Threat Synonym, Threat In Spanish, Threat Modeling, Threat Stack, Threat Meaning, Threat Dynamics, Threat Intelligence, Threat Assessment, Threat Assessment, Threat Analysis, Threat Awareness And Reporting Program, Threat Antonym, Threat Actor, Threat Agent, Threat Assessment Model, Threat Assessment Training, Threat And Error Management, Threat Advice, Threat Based Threads, Threat Beast, Threat Brief, Threat Bias, Threat Basketball, Threat Board, Threat Blocked Avast, Threat Behavior, Threat Based Risk Assessment, Threat Blog, Threatconnect, Threatcrowd, Threat Charges, Threat Cloud, Threat Crime Cause Death\/gbi, Threat Ck2, Threat Control Override, Threatcon, Threatcon Delta, Threat Crime, Threat Definition, Threat Dynamics, Threat Detection, Threat Define, Threat Def, Threat Defense, Threat Display, Threat Detection And Response, Threat Disposal Nier, Threat Dynamics Hours, Threat En Espanol, Threat Expert, Threat Exchange, Threat Emulation, Threat Examples, Threat Error Management, Threat Environment, Threat Ender Crossword Clue, Threat Encyclopedia, Threat Emitter, Threat From North Korea, Threat Feeds, Threat From Xor, Threat Finance, Threat Fire, Threat From Russia, Threat From Above, Threat From The Thicket, Threat Finance Jobs, Threat From The Sea, Threat Grid, Threat Gif, Threat Group, Threat Generator, Threat Geek, Threat Graph, Threatguard, Threat Grid Login, Threat Group-4127, Threat Grid Api, Threat Hunting, Threathoops, Threat Hunting Tools, Threat Hunting With Splunk, Threat Hunting Training, Threat Hunting Techniques, Threat Hypothesis, Threat Has Been Detected, Threat Hunting Definition, Threat Hunting Summit, Threat In Spanish, Threat Intelligence, Threat Intelligence Feeds, Threat Intelligence Platform, Threat Intel, Threat In French, Threat Icon, Threat Intelligence Analyst, Threat Identification, Threat Intelligence Definition, Threat Jay Z Mp3, Threat Jay, Threat Journal, Threat Jokes, Threat Jail Time, Threat Jay Z Genius, Thread Java, Threat Jay Z Instrumental, Threat Jay Z Listen, Threat Jewellery, Threat Knowledge Group, Threat Kill Chain, Threat Level Midnight, Threat Knowledge, Threat Knowledge Group Isis, Threat Knights Of Pen And Paper, Threat Level Midnight Full Movie, Threat Level, Threat Level Midnight Episode, Threat Level Midnight Quotes, Threat Level Midnight, Threat Level Midnight Full Movie, Threat Level, Threat Level Midnight Episode, Threat Level Midnight Quotes, Threat Level Midnight Song, Threat Landscape, Threat Level Delta, Threat Level Midnight Poster, Threat Level Orange, Threat Modeling, Threat Meaning, Threat Matrix, Threat Map, Threat Management, Threat Management Group, Threat Modeling Tool, Threat Meme, Threat Modeling Designing For Security, Threat Management Gateway, Threat Note, Threat Neutralized, Threat North Korea, Threat Net, Threat Null, Threat News, Threat Narrative, Threat Neverwinter, Threat Networks, Threat Name Ws.reputation.1, Threat Of New Entrants, Threat Of Substitutes, Threat Of Joy Lyrics, Threat Of Nuclear War, Threat Of Joy, Threat Of War, Threat Of North Korea, Threat Of Substitute Products, Threat Of Terrorism, Threat Of Joy Chords, Threat Post, Threat Payday 2, Threat Pattern, Threat Prevention, Threat Perception, Threat Protection, Threat Profile, Threat Past Tense, Threat Point, Threat Plates, Threat Quotes, Threatquotient, Threat Questionnaire, Thread Queue, Threat Quotes And Sayings, Threat Quarantine, Threat Quotes In Hindi, Threat Quotes From Movies, Threat Response Solutions, Threat Response, Threat Report, Threat Rapper, Threat Range Pathfinder, Threat Rhyme, Threat Rigidity, Threat Research, Threat Radar, Threat Risk Assessment, Threat Synonym, Threat Stack, Threat Signal, Threat Simulation Theory, Threatstream, Threat Stack Careers, Threat Spanish, Threat Scan, Threat Scenarios, Threat Suppression, Threat To Survival, Threat To Internal Validity, Threat Thesaurus, Threat Tec, Threattrack, Threat To Biodiversity, Threat To Society, Threat To Validity, Threat To National Security, Threat To Us, Thread Up, Threat Update, Threat Us, Threat Used In A Sentence, Threat Uk, Threat Urban Dictionary, Thread Up Mens, Thread Up Review, Thread Up Maternity, Thread Up Sell, Threat Vector, Threat Vs Vulnerability, Threat Vulnerability Risk, Threat Vector Definition, Threat Vulnerability Assessment, Threat Verb, Threat Vs Warning, Threat Vault, Threat Vs Consequence, Threat Vs Challenge, Threat Wire, Threat With A Deadly Weapon, Threat Watch, Threat Wiki, Threat Warning, Thread Wallets, Threat Words, Threat Working Group, Threat Wow, Threat With A Gun, Threat X, Threat X Vulnerability = Risk, Threat And Risk, Threat X Impact, Threat Exchange, Threat Xword, X Factor Threat, Threat X3, X2 Threat, Xml Threat Protection In Datapower, Treat You Better Lyrics, Treat Yo Self, Treat You Better, Treat Yo Self Gif, Treat Your Feet, Treat You Better Chords, Treat Yo Self Meme, Treat Yo Self Episode, Treat Yo Self Day, Treat Yourself Meme, Threat Zero, Threat T\u0142umaczenie, Threat Zone, Thread Zigbee, Thread Zap, Zika Threat, Zp Theart, Zonealarm Threat Emulation, Zombie Threat, Zombie Threat Level, University Of Phoenix, University Of Washington, University Of Michigan, University Of Maryland, University Of Florida, University Of Chicago, University Of Texas, University Of Arizona, University Of South Carolina, University Of Alabama, University At Buffalo, University At Albany, University Apartments, University Athlete, University Academy, University Art, University Avenue, University At Buffalo Address, University Audi, University Accounting Services, University Bookstore, University Bowl, University Blue 12s, University Baptist Church, University Blue, University Bookstore Purdue, University Bookstore Hours, University Blue 11, University Boulevard, University Bikes, University Credit Union, University Club, University College London, University City, University College Dublin, University Commons, University Center, University Club Chicago, University City High School, University Co Op, University Definition, University Dodge, University Dental, University Drive, University District Seattle, University Downs, University Dermatology, University District, University Delaware, University Denver, University Edge, University Estates, University Electric, University Eye Center, University Endowments, University Edge Kent, University Eye Care, University Extension, University Enterprises, University Eye Associates, University Federal Credit Union, University Ford, University Florida, University Family Care, University Frames, University Falls, University Font, University Federal Credit Union Utah, University Foods, University Florist, University Gardens, University Grill, University Gateway, University Group, University Green, University Guest House, University Games, University Green Apartments, University Gastroenterology, University Georgia, University Hospital, University High School, University Heights, University Health, University House, University Health System, University Health Services, University Hospitals Jobs, University Hospital Cleveland, University Honda, University Inn, University In California, University In Melbourne, University In Texas, University In New York, University Inn Washington Dc, University In Florida, University In Spanish, University In Chicago, University In Boston, University Jobs, University Jewelry, University Jeep, University Jobs Usa, University Jordan 11, University Job Boards, University Jacksonville, University Jobs Nyc, University Jobs Chicago, University Jamestown, University Kia, University Kitchen, University Kentucky, University Kansas, University Kia Durham, University Kentucky Baseball, University Of, University K9, University Kia Huntsville Alabama, University Kansas City, University Library, University Lofts, University Logos, University Lanes, University Liquor, University Lake School, University Liggett, University Lutheran Church, University Lands, University Laundry, University Mall, University Medical Center, University Mall Hours, University Motors, University Mazda, University Mall Tampa, University Mall Theatres, University Mall Stores, University Michigan, University Medicine, University Near Me, University North Carolina, University Nevada Reno, University North Texas, University Notre Dame, University North Dakota, University Nails, University Northern Colorado, University North Florida, University New Mexico, University Of Phoenix, University Of Washington, University Of Michigan, University Of Maryland, University Of Florida, University Of Chicago, University Of Texas, University Of Arizona, University Of South Carolina, University Of Alabama, University Park, University Park Mall, University Place, University Park Apartments, University Park Pa, University Park Il, University Place Wa, University Pointe, University Plaza, University Prep, University Quotes, University Quiz, University Queensland, University Quarters, University Quarter System, University Quality Inn Lansing Mi, University Quad, University Quality Inn Lansing, University Quebec, University Quick Care, University Rankings, University Radiology, University Rankings 2017, University Ridge, University Realty, University Red 5s, University Roadhouse, University Rentals, University Reformed Church, University Registrar, University School, University South Carolina, University System Of Georgia, University San Diego, University School Of Milwaukee, University Southern California, University Square, University Settlement, University South Florida, University Suites, University Tees, University Towers, University Trails, University Town Center, University Tire, University Toyota, University Theater, University Terrace, University Texas Austin, University Tennessee, University United Methodist Church, University Urology, University Urgent Care, University Utah, University Union, University Unitarian Church, University Utah Credit Union, University Umc, University Utah Hospital, University Urbana Champaign, University Village, University Village Theatre, University Vs College, University View, University Village Stores, University Village Austin, University View Academy, University Vw, University Village Clemson, University Village Chicago, University Washington, University Wisconsin Madison, University Wafer, University West, University Walk, University Woods, University West Florida, University Writing Center, University West Georgia, University World Rankings, University Xavier, University X, University Xfinity, University Xamarin, University Credit Union, University Club, University College London, University City, University College Dublin, University Commons, University Ymca, University Yard Sale, University Yes Academy, University Ymca Seattle, University Ymca Charlotte Nc, University Yacht Club, University Ymca Hours, University Y, University Yale, University Yoga, University Zip Code, University Zurich, University Zagreb, University Zoka, University Zaragoza, University Zimbabwe, University Zipcar Rates, University Zambia, University Zurich Jobs, University Zaxby’s











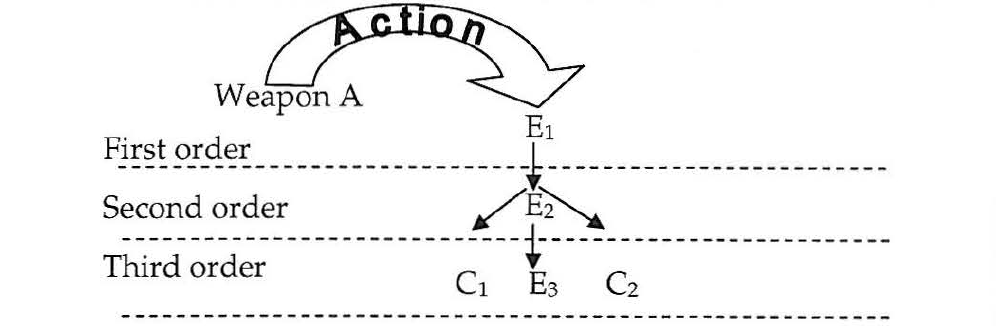
 A restricted document from U.S. Strategic Command provides insight into the underlying philosophy of military efforts to wage cyber warfare.
A restricted document from U.S. Strategic Command provides insight into the underlying philosophy of military efforts to wage cyber warfare.









You must be logged in to post a comment.