
Preface
The National Gang Intelligence Center (NGIC) prepared the 2011 National Gang Threat Assessment (NGTA) to examine emerging gang trends and threats posed by criminal gangs to communities throughout the United States. The 2011 NGTA enhances and builds on the gang-related trends and criminal threats identified in the 2009 assessment. It supports US Department of Justice strategic objectives 2.2 (to reduce the threat, incidence, and prevalence of violent crime) and 2.4 (to reduce the threat, trafficking, use, and related violence of illegal drugs). The assessment is based on federal, state, local, and tribal law enforcement and corrections agency intelligence, including information and data provided by the National Drug Intelligence Center (NDIC) and the National Gang Center. Additionally, this assessment is supplemented by information retrieved from open source documents and data collected through April 2011.
Scope and Methodology
In 2009, the NGIC released its second threat assessment on gang activity in the United States. The NGIC and its law enforcement partners documented increases in gang proliferation and migration nationwide and emerging threats. This report attempts to expand on these findings. Reporting and intelligence collected over the past two years have demonstrated increases in the number of gangs and gang members as law enforcement authorities nationwide continue to identify gang members and share information regarding these groups. Better reporting and collection has contributed greatly to the increased documentation and reporting of gang members and gang trends.
Information in the 2011 National Gang Threat Assessment-Emerging Trends was derived from law enforcement intelligence, open source information, and data collected from the NDIC, including the 2010 NDIC National Drug Threat Survey (NDTS). NGIC law enforcement partners provided information and guidance regarding new trends and intelligence through an online request for information via the NGIC Law Enforcement Online (LEO) Special Interest Group (SIG), which is now NGIC Online. Law enforcement agencies nationwide continuously report new and emerging gang trends to the NGIC, as the NGIC continues to operate as a repository and dissemination hub for gang intelligence. This information provided by our law enforcement partners was used to identify many of the trends and issues included in this report.
Reporting used to quantify the number of street and outlaw motorcycle gangs and gang members was primarily derived from the 2010 NDIC NDTS data and some supplemental NGIC reporting from our law enforcement partners. NDIC annually conducts the NDTS to collect data on the threat posed by various illicit drugs in the United States. A stratified random sample of nearly 3,500 state and local law enforcement agencies was surveyed to generate national, regional, and state estimates of various aspects of drug trafficking activities including the threat posed by various drugs, the availability and production of illicit drugs, as well as the role of street gangs and outlaw motorcycle gangs in drug trafficking activity. Weighted national, regional, and state-level statistical estimates derived from NDTS 2010 data was based on responses received from 2,963 law enforcement agencies out of a sample of 3,465 agencies. In calculating the number of street and outlaw motorcycle gang members, respondents in each region were asked to select from a series of ranges of numbers. The median numbers of each range were aggregated to generate an estimate for the total number of gang members. In calculating the number of street and outlaw motorcycle gangs, the low end of each range was aggregated to generate an estimate for the total number of gangs and gang members. Prison gang member estimates were derived directly from the US Federal Bureau of Prisons (BOP) and state correctional institutions across the country.
About the NGIC
The NGIC was established by Congress in 2005 to support law enforcement agencies through timely and accurate information sharing and strategic/tactical analysis of federal, state, and local law enforcement information focusing on the growth, migration, criminal activity, and association of gangs that pose a significant threat to communities throughout the United States. The NGIC is comprised of representatives from the Federal Bureau of Investigation (FBI), US Drug Enforcement Administration (DEA), US Bureau of Alcohol, Tobacco, Firearms, and Explosives (ATF), US Bureau of Prisons (BOP), United States Marshals Service (USMS), US Immigration and Customs Enforcement (ICE), US Department of Defense (DOD), National Drug Intelligence Center (NDIC), and US Customs and Border Protection (CBP). This multi-agency fusion center integrates gang intelligence assets to serve as a central intelligence resource for gang information and analytical support.
To assist in the sharing of gang intelligence with law enforcement, the NGIC has established NGIC Online, an information system comprised of a set of web-based tools designed for researching gang-related intelligence and sharing of information with federal, state, local and tribal law enforcement partners. The system’s Request for Information (RFI) portal encourages users to contribute new data as well as conduct gang research through custom threat assessments and/or liaison with NGIC’s network of national subject matter experts. NGIC Online functions include RFI submissions and responses; Gang Encyclopedia WIKI; General Intelligence Library; and a Signs, Symbols, and Tattoos (SST) database with user submissions.
Gang Definitions
| Gang |
Definition |
| Street |
Street gangs are criminal organizations formed on the street operating throughout the United States. |
| Prison |
Prison gangs are criminal organizations that originated within the penal system and operate within correctional facilities throughout the United States, although released members may be operating on the street. Prison gangs are also self-perpetuating criminal entities that can continue their criminal operations outside the confines of the penal system. |
| Outlaw Motorcycle (OMGs) |
OMGs are organizations whose members use their motorcycle clubs as conduits for criminal enterprises. Although some law enforcement agencies regard only One Percenters as OMGs, the NGIC, for the purpose of this assessment, covers all OMG criminal organizations, including OMG support and puppet clubs. |
One Percenter
OMGs |
ATF defines One Percenters as any group of motorcyclists who have voluntarily made a commitment to band together to abide by their organization’s rules enforced by violence and who engage in activities that bring them and their club into repeated and serious conflict with society and the law. The group must be an ongoing organization, association of three (3) or more persons which have a common interest and/or activity characterized by the commission of or involvement in a pattern of criminal or delinquent conduct. ATF estimates there are approximately 300 One Percenter OMGs in the United States. |
| Neighborhood/Local |
Neighborhood or Local street gangs are confined to specific neighborhoods and jurisdictions and often imitate larger, more powerful national gangs. The primary purpose for many neighborhood gangs is drug distribution and sales. |
Regional Breakdown:
Maps and data in this assessment are presented according to the FBI’s Safe Streets Gang Task Force regions.
| Region |
States |
| North Central |
Illinois, Indiana, Iowa, Kansas, Kentucky, Michigan, Minnesota, Missouri, Nebraska, North Dakota, Ohio, South Dakota, Wisconsin |
| Northeast |
Connecticut, Maine, Massachusetts, New Hampshire, New Jersey, New York, Pennsylvania, Rhode Island, Vermont, West Virginia |
| South Central |
Alabama, Arkansas, Louisiana, Mississippi, Oklahoma, Tennessee, Texas |
| Southeast |
Delaware, District of Columbia, Florida, Georgia, Maryland, North Carolina, Puerto Rico, South Carolina, Virginia |
| West |
Alaska, Arizona, California, Colorado, Hawaii, Idaho, Montana, Nevada, New Mexico, Oregon, Utah, Washington, Wyoming |
Executive Summary
Gangs continue to commit criminal activity, recruit new members in urban, suburban, and rural regions across the United States, and develop criminal associations that expand their influence over criminal enterprises, particularly street-level drug sales. The most notable trends for 2011 have been the overall increase in gang membership, and the expansion of criminal street gangs’ control of street-level drug sales and collaboration with rival gangs and other criminal organizations.a
Key Findings
Gangs are expanding, evolving and posing an increasing threat to US communities nationwide. Many gangs are sophisticated criminal networks with members who are violent, distribute wholesale quantities of drugs, and develop and maintain close working relationships with members and associates of transnational criminal/drug trafficking organizations. Gangs are becoming more violent while engaging in less typical and lower-risk crime, such as prostitution and white-collar crime. Gangs are more adaptable, organized, sophisticated, and opportunistic, exploiting new and advanced technology as a means to recruit, communicate discretely, target their rivals, and perpetuate their criminal activity. Based on state, local, and federal law enforcement reporting, the NGIC concludes that:
- There are approximately 1.4 million active street, prison, and OMG gang members comprising more than 33,000 gangs in the United States. Gang membership increased most significantly in the Northeast and Southeast regions, although the West and Great Lakes regions boast the highest number of gang members. Neighborhood-based gangs, hybrid gang members, and national-level gangs such as the Sureños are rapidly expanding in many jurisdictions. Many communities are also experiencing an increase in ethnic-based gangs such as African, Asian, Caribbean, and Eurasian gangs.
- Gangs are responsible for an average of 48 percent of violent crime in most jurisdictions and up to 90 percent in several others, according to NGIC analysis. Major cities and suburban areas experience the most gang-related violence. Local neighborhood-based gangs and drug crews continue to pose the most significant criminal threat in most communities. Aggressive recruitment of juveniles and immigrants, alliances and conflict between gangs, the release of incarcerated gang members from prison, advancements in technology and communication, and Mexican Drug Trafficking Organization (MDTO) involvement in drug distribution have resulted in gang expansion and violence in a number of jurisdictions.
- Gangs are increasingly engaging in non-traditional gang-related crime, such as alien smuggling, human trafficking, and prostitution. Gangs are also engaging in white collar crime such as counterfeiting, identity theft, and mortgage fraud, primarily due to the high profitability and much lower visibility and risk of detection and punishment than drug and weapons trafficking.
- US-based gangs have established strong working relationships with Central American and MDTOs to perpetrate illicit cross-border activity, as well as with some organized crime groups in some regions of the United States. US-based gangs and MDTOs are establishing wide-reaching drug networks; assisting in the smuggling of drugs, weapons, and illegal immigrants along the Southwest Border; and serving as enforcers for MDTO interests on the US side of the border.
- Many gang members continue to engage in gang activity while incarcerated. Family members play pivotal roles in assisting or facilitating gang activities and recruitment during a gang members’ incarceration. Gang members in some correctional facilities are adopting radical religious views while incarcerated.
- Gangs encourage members, associates, and relatives to obtain law enforcement, judiciary, or legal employment in order to gather information on rival gangs and law enforcement operations. Gang infiltration of the military continues to pose a significant criminal threat, as members of at least 53 gangs have been identified on both domestic and international military installations. Gang members who learn advanced weaponry and combat techniques in the military are at risk of employing these skills on the street when they return to their communities.
- Gang members are acquiring high-powered, military-style weapons and equipment which poses a significant threat because of the potential to engage in lethal encounters with law enforcement officers and civilians. Typically firearms are acquired through illegal purchases; straw purchases via surrogates or middle-men, and thefts from individuals, vehicles, residences and commercial establishments. Gang members also target military and law enforcement officials, facilities, and vehicles to obtain weapons, ammunition, body armor, police gear, badges, uniforms, and official identification.
- Gangs on Indian Reservations often emulate national-level gangs and adopt names and identifiers from nationally recognized urban gangs. Gang members on some Indian Reservations are associating with gang members in the community to commit crime.
- Gangs are becoming increasingly adaptable and sophisticated, employing new and advanced technology to facilitate criminal activity discreetly, enhance their criminal operations, and connect with other gang members, criminal organizations, and potential recruits nationwide and even worldwide.
Current Gang-Related Trends and Crime
Gang membership continues to expand throughout communities nationwide, as gangs evolve, adapt to new threats, and form new associations. Consequently, gang-related crime and violence is increasing as gangs employ violence and intimidation to control their territory and illicit operations. Many gangs have advanced beyond their traditional role as local retail drug distributors in large cities to become more organized, adaptable, and influential in large-scale drug trafficking. Gang members are migrating from urban areas to suburban and rural communities to recruit new members, expand their drug distribution territories, form new alliances, and collaborate with rival gangs and criminal organizations for profit and influence. Local neighborhood, hybrid and female gang membership is on the rise in many communities. Prison gang members, who exert control over many street gang members, often engage in crime and violence upon their return to the community. Gang members returning to the community from prison have an adverse and lasting impact on neighborhoods, which may experience notable increases in crime, violence, and drug trafficking.
Gang Membership and Expansion
Approximately 1.4 million active street, OMG, and prison gang members, comprising more than 33,000 gangs, are criminally active within all 50 US states, the District of Columbia, and Puerto Rico (see Appendix A). This represents a 40 percent increase from an estimated 1 million gang members in 2009. The NGIC attributes this increase in gang membership primarily to improved reporting, more aggressive recruitment efforts by gangs, the formation of new gangs, new opportunities for drug trafficking, and collaboration with rival gangs and drug trafficking organizations (DTOs). Law enforcement in several jurisdictions also attribute the increase in gang membership in their region to the gangster rap culture, the facilitation of communication and recruitment through the Internet and social media, the proliferation of generational gang members, and a shortage of resources to combat gangs.
More than half of NGIC law enforcement partners report an increase in gang-related criminal activity in their jurisdictions over the past two years. Neighborhood-based gangs continue to pose the greatest threat in most jurisdictions nationwide.
- NGIC and NDIC data indicates that, since 2009, gang membership increased most significantly in the Northeast and Southeast regions, although the West and North Central regions—particularly Arizona, California, and Illinois—boast the highest number of gang members.
|
2011 Estimated Gang Membership
|
|
Members
|
Gangs
|
| Street |
1,140,344
|
30,313
|
| OMG |
44,108
|
2,965
|
| Prison |
231,136**
|
n/a
|
| Total |
1,415,578
|
33,278
|
| *Based on 2010 and 2011 NGIC and NDIC data**Based on reporting from 32 states |
|
2011 Estimated Street and OMG Membership by Region
|
| North Central |
260,022
|
| Northeast |
159,158
|
| South Central |
167,353
|
| Southeast |
117,205
|
| West |
480,715
|
| Total |
1,184,453
|
| *Based on 2010 and 2011 NGIC and NDIC data |
- Sureño gangs, including Mara Salvatrucha (MS-13), 18th Street, and Florencia 13, are expanding faster than other national-level gangs, both in membership and geographically. Twenty states and the District of Columbia report an increase of Sureño migration into their region over the past three years. California has experienced a substantial migration of Sureño gangs into northern California and neighboring states, such as Arizona, Nevada, and Oregon.
- Law enforcement reporting indicates a significant increase in OMGs in a number of jurisdictions, with 44,108 members nationwide comprising approximately 2,965 gangs.b Jurisdictions in Alaska, Arizona, Colorado, Connecticut, Delaware, Florida, Georgia, Iowa, Missouri, Montana, Oregon, Pennsylvania, South Carolina, Tennessee, Utah, and Virginia are experiencing the most significant increase in OMGs, increasing the potential for gang-related turf wars with other local OMGs. The Wheels of Soul (WOS), Mongols, Outlaws, Pagans and Vagos have expanded in several states.
Table 1. Recent Expansion of Major OMGs:
| Gang |
Region |
| Mongols |
Arizona, Arkansas, California, Colorado, Illinois, Kentucky, Montana, Nevada, New York, Oklahoma, Oregon, Washington |
| Outlaws |
Arkansas, Montana, Maryland, North Carolina, New York |
| Pagans |
Delaware, New Jersey, Ohio |
| Vagos |
California, Florida, Georgia, Mississippi, Nevada, New Mexico, New York,
Oregon, Pennsylvania, Rhode Island, South Dakota |
| Wheels of Soul |
Alabama, Arkansas, California, Colorado, Illinois, Kentucky, New York |
Source: ATF
Figure 1. Nationwide Gang Presence

Source: NGIC and NDIC 2010 National Drug Survey Data
Chart 1. Threat Posed by Gangs, According to Law Enforcement.
The NGIC collected intelligence from law enforcement officials nationwide in an attempt to capture the threat posed by national-level street, prison, outlaw motorcycle, and neighborhood-based gangs in their communities.

Source: 2011 NGIC National data
Gang-Related Violent Crime
Gang-related crime and violence continues to rise. NGIC analysis indicates that gang members are responsible for an average of 48 percent of violent crime in most jurisdictions and much higher in others. Some jurisdictions in Arizona, California, Colorado, Illinois, Massachusetts, Oklahoma, and Texas report that gangs are responsible for at least 90 percent of crime. A comparison of FBI Uniform Crime Reporting (UCR) 2009 violent crime data and 2010 NGIC gang data illustrates that regions experiencing the most violent crime—including southern California, Texas, and Florida—also have a substantial gang presence (see Figure 1 and Map 7). Street gangs are involved in a host of violent criminal activities, including assault, drug trafficking, extortion, firearms offenses, home invasion robberies, homicide, intimidation, shootings, and weapons trafficking. NDIC reporting indicates that gang control over drug distribution and disputes over drug territory has increased, which may be responsible for the increase in violence in many areas. Conflict between gangs, gang migration into rival gang territory, and the release of incarcerated gang members back into the community has also resulted in an increase in gang-related crime and violence in many jurisdictions, according to NGIC reporting.
Table 2. Percentage of Violent Crime Committed by Gangs as reported by NGIC Law Enforcement Partners
|
% of violent crime committed by gangs
|
% of LE Officials
|
|
1-25%
|
34.0%
|
|
26-50%
|
28.4%
|
|
51-75%
|
22.7%
|
|
76-100%
|
14.9%
|
Chart 2. Threat Posed by Gangs, as Reported by Law Enforcement.
The NGIC collected intelligence from its law enforcement partners nationwide in an effort to capture the criminal threat posed by national-level street, prison, outlaw motorcycle, and neighborhood-based gangs in their communities. The following chart represents the percentage of gang involvement in crime.

Source: 2011 NGIC data
According to National Youth Gang Survey reporting, larger cities and suburban counties accounted for the majority of gang-related violence and more than 96 percent of all gang homicides in 2009.1 As previous studies have indicated, neighborhood-based gangs and drug crews continue to pose the most significant criminal threat in these regions.
- Law enforcement officials in the Washington, DC metropolitan region are concerned about a spate of gang-related violence in their area. In February 2011, ICE officials indicted 11 MS-13 members for a two-year spree of murders, stabbings, assaults, robberies, and drug distribution. Likewise, gangs such as MS-13 and Bloods in Prince George’s County, Maryland, are suspected to be involved in up to 16 homicides since January 2011.2
- USMS reported 5,705 gang-affiliated felony fugitives in 2010, a 14 percent increase from the number of gang fugitives in 2009. California and Texas report the highest number of gang fugitives, with 1,284 and 542 respectively.
Gang-Related Drug Distribution and Trafficking
Gang involvement and control of the retail drug trade poses a serious threat to public safety and stability in most major cities and in many mid-size cities because such distribution activities are routinely associated with lethal violence. Violent disputes over control of drug territory and enforcement of drug debts frequently occur among gangs in both urban and suburban areas, as gangs expand their control of drug distribution in many jurisdictions, according to NDIC and NGIC reporting. In 2010, law enforcement agencies in 51 major US cities reported moderate to significant levels of gang-related drug activity.
NDIC survey data indicates that 69 percent of US law enforcement agencies report gang involvement in drug distribution.
- In June 2010, a joint federal-state law enforcement operation led to the arrest of eight people linked to a San Gabriel Valley street gang involved in violent crimes and methamphetamine trafficking in support of the California Mexican Mafia (La Eme).3
NDIC reporting suggests that gangs are advancing beyond their traditional role as local retail drug distributors in large cities and becoming more influential in large-scale drug trafficking, resulting in an increase in violent crime in several regions of the country.4
- Law enforcement reporting indicates that gang-related drug distribution and trafficking has resulted in an increase of kidnappings, assaults, robberies and homicides along the US Southwest border region.
Gang involvement in drug trafficking has also resulted in the expansion and migration of some gangs into new US communities, according to NDIC reporting.
- Gang members from the Midwest are migrating to southern states to expand their drug trafficking operations.
Figure 3. Major Cities Reporting Gang-Related Drug Activity in 2010

Source: NDIC 2010 National Drug Threat Survey
Juvenile Gangs
Many jurisdictions are experiencing an increase in juvenile gangs and violencec, which is often attributed, in part, to the increased incarceration rates of older members and the aggressive recruitment of juveniles in schools. Gangs have traditionally targeted youths because of their vulnerability and susceptibility to recruitment tactics, as well as their likelihood of avoiding harsh criminal sentencing and willingness to engage in violence.
NGIC reporting indicates that juvenile gangs are responsible for a majority of crime in various jurisdictions in Arizona, California, Connecticut, Florida, Georgia, Illinois, Maryland, Michigan, Missouri, North Carolina, New Hampshire, South Carolina, Texas, Virginia, and Washington.
- Juvenile gang members in some communities are hosting parties and organizing special events which develop into opportunities for recruiting, drugs, sexual exploitation, and criminal activity.
- Gangster Rap gangs, often comprised of juveniles, are forming and are being used to launder drug money through seemingly legitimate businesses, according to NGIC reporting.
Gang Alliances and Collaboration
Collaboration between rival gangs and criminal organizations and increased improvement in communications, transportation, and technology have enabled national-level gangs to expand and secure their criminal networks throughout the United States and in other countries.
- According to NGIC reporting, gang members in California are collaborating with members of rival gangs to further criminal activities such as drug distribution, prostitution of minors, and money laundering.
- Gangs in the correctional system are committing crimes for other gangs in an effort to confuse and evade law enforcement.
Gang Sophistication
Gang members are becoming more sophisticated in their structure and operations and are modifying their activity to minimize law enforcement scrutiny and circumvent gang enhancement laws. Gangs in several jurisdictions have modified or ceased traditional or stereotypical gang indicia and no longer display their colors, tattoos, or hand signs. Others are forming hybrid gangs to avoid police attention and make to it more difficult for law enforcement to identify and monitor them, according to NGIC reporting. Many gangs are engaging in more sophisticated criminal schemes, including white collar and cyber crime, targeting and infiltrating sensitive systems to gain access to sensitive areas or information, and targeting and monitoring law enforcement.
Expansion of Ethnic-Based and Non-Traditional Gangs
Law enforcement officials in jurisdictions nationwide report an expansion of African, Asian, Eurasian, Caribbean, and Middle Eastern gangs, according to NGIC reporting. Many communities are also experiencing increases in hybrid and non-traditional gangs.
Asian Gangs
Asian gangs, historically limited to regions with large Asian populations, are expanding throughout communities nationwide. Although often considered street gangs, Asian gangs operate similar to Asian Criminal Enterprises with a more structured organization and hierarchy. They are not turf-oriented like most African-American and Hispanic street gangs and typically maintain a low profile to avoid law enforcement scrutiny. Asian gang members are known to prey on their own race and often develop a relationship with their victims before victimizing them.5 Law enforcement officials have limited knowledge of Asian gangs and often have difficulty penetrating these gangs because of language barriers and gang distrust of non-Asians.6
Law enforcement officials in California, Georgia, Maryland, Massachusetts, Michigan, Montana, Pennsylvania, Rhode Island, Virginia, and Wisconsin report a significant increase in Asian gangs in their jurisdictions.
Asian gangs are involved in a host of criminal activities to include violent crime, drug and human trafficking, and white collar crime.
- Asian gang members in New England and California maintain marijuana cultivation houses specifically for the manufacturing and distribution of high potency marijuana and pay members of the Asian community to reside in them, according to 2010 NDIC and open source reporting.7
Some law enforcement agencies attribute the recent increase in Asian gang membership in their jurisdictions to the recruitment of non-Asian members into the gang in order to compete more effectively with other street gangs for territory and dominance of illicit markets.
East African Gangs
Somali Gangs
Somali gang presence has increased in several cities throughout the United States. Somali gangs are most prevalent in the Minneapolis-St. Paul, Minnesota; San Diego, California; and Seattle, Washington areas, primarily as a result of proximity to the Mexican and Canadian borders, according to ICE, NGIC, and law enforcement reporting. Somali gang activity has also been reported in other cities throughout the United States such as Nashville, Tennessee; Clarkston, Georgia; Columbus, Ohio; East Brunswick, New Jersey; and Tucson, Arizona. Unlike most traditional street gangs, Somali gangs tend to align and adopt gang names based on clan or tribe, although a few have joined national gangs such as the Crips and Bloods.
NGIC reporting indicates that East African gangs are present in at least 30 jurisdictions, including those in California, Georgia, Minnesota, Ohio, Texas, Virginia, and Washington.
Somalian gangs are involved in drug and weapons trafficking, human trafficking, credit card fraud, prostitution, and violent crime. Homicides involving Somali victims are often the result of clan feuds between gang members. Sex trafficking of females across jurisdictional and state borders for the purpose of prostitution is also a growing trend among Somalian gangs.
Figure 4. Somali Outlaws set in Minneapolis, MN

Source: Minneapolis Police Department
- In November 2010, 29 suspected Somalian gang members were indicted for a prostitution trafficking operation, according to open source reporting. Over a 10 year period, Somalian gang members transported underage females from Minnesota to Ohio and Tennessee for prostitution.8
- In February 2009, five Somali gang members were arrested for murdering drug dealers in Dexter and Athens, Ohio, during home invasion robberies, according to law enforcement reporting.9
Although some Somali gangs adopt Bloods or Crips gang monikers, they typically do not associate with other African-American gangs. Somali nationals—mostly refugees displaced by the war(s) in Somalia and surrounding countries—tend to migrate to specific low-income communities, which are often heavily controlled by local Bloods and Crips street gangs. The Somali youth may emulate the local gangs, which frequently leads to friction with other gangs, such as Bloods and Crips, as well as with Ethiopian gangs.
Sudanese Gangs
Sudanese gangs in the United States have been expanding since 2003 and have been reported in Iowa, Minnesota, Nebraska, North Dakota, South Dakota, and Tennessee. Some Sudanese gang members have weapons and tactical knowledge from their involvement in conflicts in their native country.
- The African Pride (AP) gang is one of the most aggressive and dangerous of the Sudanese street gangs in Iowa, Minnesota, Nebraska, and North and South Dakota.
Caribbean Gangs
Although largely confined to the East Coast, Caribbean gangs, such as Dominican, Haitian, and Jamaican gangs, are expanding in a number of communities throughout the United States.
Dominican Gangs
The Trinitarios, the most rapidly-expanding Caribbean gang and the largest Dominican gang, are a violent prison gang with members operating on the street. The Trinitarios are involved in homicide, violent assaults, robbery, theft, home invasions, and street-level drug distribution. Although predominate in New York and New Jersey, the Trinitarios have expanded to communities throughout the eastern United States, including Georgia, Massachusetts, Pennsylvania, and Rhode Island. Dominicans Don’t Play (DDP), the second largest Dominican gang based in Bronx, New York, are known for their violent machete attacks and drug trafficking activities in Florida, Michigan, New Jersey, New York, and Pennsylvania.
An increase in the Dominican population in several eastern US jurisdictions has resulted in the expansion and migration of Dominican gangs such as the Trinitarios. This has led to an increase in drug trafficking, robberies, violent assaults in the Tri-state area.
Figure 5. Trinitarios Insignia

Source: ATF
Haitian Gangs
Haitian gangs, such as the Florida-based Zoe Pound, have proliferated in many states primarily along the East Coast in recent years according to NGIC reporting. According to NGIC reporting, Haitian gangs are present in Connecticut, Florida, Georgia, Indiana, Maryland, Massachusetts, New Jersey, New York, North Carolina, South Carolina, and Texas.
- The Zoe Pound gang, a street gang founded in Miami, Florida by Haitian immigrants in the United States, is involved in drug trafficking, robbery, and related violent crime. In February 2010, 22 suspected Zoe Pound members in Chicago, Illinois, were charged with possession of and conspiracy to traffic powder and crack cocaine from Illinois to Florida, according to FBI reporting.10
- The Haitian Boys Posse and Custer Street Gang are involved in a myriad of criminal activities including drug and weapons trafficking, robberies, shootings and homicides along the East Coast.
| Trinitario members arrested for drug and firearms violations |
In August 2010, the FBI arrested three Rhode Island Trinitario members for conspiracy to distribute MDMA and firearms violations. Seventeen other Trinitario members also allegedly collected money to buy weapons, hire lawyers, and aid members (brothers) in prison.
Source: DOJ: District of Rhode Island, August 26, 2010
Jamaican Gangs
Traditional Jamaican gangs operating in the United States are generally unsophisticated and lack a significant hierarchical structure, unlike gangs in Jamaica. Many active Jamaican gangs operating in the United States maintain ties to larger criminal organizations and gangs in Jamaica, such as the Shower Posse or the Spangler Posse. Jamaican gang members in the United States engage in drug and weapons trafficking.
NGIC reporting indicates that Jamaican gangs are most active in California, Maryland, Missouri, and New Jersey.
Non-Traditional Gangs
Hybrid Gangs
The expansion of hybrid gangs—non-traditional gangs with multiple affiliations—is a continued phenomenon in many jurisdictions nationwide. Because of their multiple affiliations, ethnicities, migratory nature, and nebulous structure, hybrid gangs are difficult to track, identify, and target as they are transient and continuously evolving. Furthermore, these multi-ethnic, mixed-gender gangs pose a unique challenge to law enforcement because they are adopting national symbols and gang members often crossover from gang to gang. Hybrid gangs are of particular concern to law enforcement because members often escalate their criminal activity in order to gain attention and respect.
Hybrid gangs, which are present in at least 25 states, are fluid in size and structure, yet tend to adopt similar characteristics of larger urban gangs, including their own identifiers, rules, and recruiting methods.11 Like most street gangs, hybrid gang members commit a multitude of street and violent crime.12 Law enforcement reporting suggests that hybrid gangs have evolved from neighborhood crews that formed to expand drug trafficking, or from an absence of or loyalty to nationally recognized gangs in their region.
- Law enforcement officials in many jurisdictions nationwide report an increase in juvenile gang membership and violent crime among hybrid and local gangs, according to 2010 NGIC reporting.
- NGIC reporting indicates that hybrid gangs are dominating nationally recognized gangs in some jurisdictions and merging with other gangs to expand their membership.
Juggalos
The Juggalos, a loosely-organized hybrid gang, are rapidly expanding into many US communities. Although recognized as a gang in only four states, many Juggalos subsets exhibit gang-like behavior and engage in criminal activity and violence. Law enforcement officials in at least 21 states have identified criminal Juggalo sub-sets, according to NGIC reporting.d
| Hybrid and Almighty Latin King Nation (ALKN) Gang Members Arrested on Drug Charges |
In November 2010, hybrid gang members in Pontiac, Michigan, known the “New World Order,” were charged along with members of the ALKN for numerous drug offenses. Several guns, drugs, dozens of cell phones and $10,000 in cash were
seized by FBI, DEA and local police departments. Many of the gang members arrested were juveniles and young adults.
Source: Online article “7 Members of 2 Gangs n Pontiac Face Drug charges” MyFoxdetroit.com; November 14, 2010
- NGIC reporting indicates that Juggalo gangs are expanding in New Mexico primarily because they are attracted to the tribal and cultural traditions of the Native Americans residing nearby.
Most crimes committed by Juggalos are sporadic, disorganized, individualistic, and often involve simple assault, personal drug use and possession, petty theft, and vandalism. However, open source reporting suggests that a small number of Juggalos are forming more organized subsets and engaging in more gang-like criminal activity, such as felony assaults, thefts, robberies, and drug sales. Social networking websites are a popular conveyance for Juggalo sub-culture to communicate and expand.
- In January 2011, a suspected Juggalo member shot and wounded a couple in King County, Washington, according to open source reporting.13
Juggalos’ disorganization and lack of structure within their groups, coupled with their transient nature, makes it difficult to classify them and identify their members and migration patterns. Many criminal Juggalo sub-sets are comprised of transient or homeless individuals, according to law enforcement reporting. Most Juggalo criminal groups are not motivated to migrate based upon traditional needs of a gang. However, law enforcement reporting suggests that Juggalo criminal activity has increased over the past several years and has expanded to several other states. Transient, criminal Juggalo groups pose a threat to communities due to the potential for violence, drug use/sales, and their general destructive and violent nature.
Although law enforcement officials in Arizona, California, Pennsylvania, Utah, and Washington report the most Juggalo gang-related criminal activity, Juggalos are present in Colorado, Delaware,
Florida, Illinois, Iowa, Kansas, Massachusetts, Michigan, New Mexico, New Hampshire, North Carolina, Oklahoma, Oregon, Pennsylvania,
Tennessee, Texas, and Virginia, according to NGIC reporting.
- In January 2010, two suspected Juggalo associates were charged with beating and robbing an elderly homeless man.14
Figure 6. Juggalo member

Source: ATF
Gangs and Alien Smuggling, Human Trafficking, and Prostitution
Gang involvement in alien smuggling, human trafficking, and prostitution is increasing primarily due to their higher profitability and lower risks of detection and punishment than that of drug and weapons trafficking. Over the past year, federal, state, and local law enforcement officials in at least 35 states and US territories have reported that gangs in their jurisdictions are involved in alien smuggling, human trafficking, or prostitution.e
Alien Smuggling
Many street gangs are becoming involved in alien smuggling as a source of revenue. According to US law enforcement officials, tremendous incentive exists for gangs to diversify their criminal enterprises to include alien smuggling, which can be more lucrative and less risky than the illicit drug trade. Over the past two years numerous federal, state, and local law enforcement agencies nationwide have reported gang involvement in incidents of alien smuggling. In some instances, gang members were among those being smuggled across the border into the United States following deportation. In other cases, gang members facilitated the movement of migrants across the US-Mexico border.f
| Increasing Coordination between Mexican Drug Cartels, Alien Smuggling Networks, and US-Based Gangs |
Federal, state, and local law enforcement officials are observing a growing nexus between the Mexican drug cartels, illegal alien smuggling rings, and US-based gangs. The alien smuggling networks that operate along the Southwest border are unable to move human cargo through drug cartel controlled corridors without paying a fee. The typical Mexican illegal alien now pays approximately $1,200 to $2,500 for entry into the United States. The fee is considerably higher for aliens smuggled from countries other than Mexico, which may even be more alluring for the cartels. It is estimated that criminals earn billions of dollars each year by smuggling aliens through Mexico into the United States.
Source: House Committee on Homeland Security, US Congress
Figure 7. An immigrant is smuggled in a vehicle

Source: FBI
| Human Trafficking Global Statistics |
- 18,000 to 20,000 individuals are trafficked into the United States each year.
- 12.3 million worldwide victims of forced labor, bonded labor, and prostitution.
- 1.2 million worldwide victims are children; 1.4 million are victims of commercial sexual exploitation, of which 98% are women and girls.
- 32% of the victims are used for forced
economic exploitation, of which 56% are women and girls
Sources: US Dept. of State TIP Report 2010; UN GIFT Global Report on TIP Feb. 2010
The Barrio Azteca, Mexican Mafia, MS-13, 18th Street Gang, and Somali gangs have all reportedly been involved in alien smuggling, according to NGIC and law enforcement reporting.
- In October 2009, ICE agents in Los Angeles, California, arrested suspects linked to a drug trafficking and alien smuggling ring with close ties to the Drew Street clique of the Avenues (Sureño) street gang in Los Angeles. The ring allegedly smuggled more than 200 illegal aliens per year into the United States from Mexico, concealing them in trucks and hidden compartments of vehicles and then hiding them in a store house in Los Angeles (See Figure 8).15
Human Trafficking
Human trafficking is another source of revenue for some gangs. Victims—typically women and children—are often forced, coerced, or led with fraudulent pretense into prostitution and forced labor.16 The Bloods, MS-13, Sureños, and Somali gangs have been reportedly involved in human trafficking, according to multiple law enforcement and NGIC reporting.
- Some gangs in the New England area are combining human trafficking and drug trafficking operations, where females are used to courier drugs and participate in prostitution.
- In November 2010, federal law enforcement officials indicted 29 members of a Somalian gang in Minneapolis for operating an interstate sex trafficking ring that sold and transported underage African-American and Somalian females from Minneapolis, Minnesota, to Columbus, Ohio, and Nashville, Tennessee, for prostitution, according to FBI and ICE reporting.17
Prostitution
Prostitution is also a major source of income for many gangs. Gang members often operate as pimps, luring or forcing at-risk, young females into prostitution and controlling them through violence and psychological abuse.g Asian gangs, Bloods, Crips, Gangster Disciples, MS-13, Sureños, Vice Lords, and members of OMGs are involved in prostitution operations, according to FBI, NGIC, and multiple law enforcement reporting.
NGIC law enforcement partners report that gangs in their jurisdiction are involved in prostitution, some of which involves child prostitution.
- Prostitution is reportedly the second largest source of income for San Diego, California, gangs. According to November 2010 open source reporting, African-American street gangs in San Diego are pimping young females to solicit males.18
Gangs and Criminal Organizations
Gangs & Drug Trafficking Organizations
Many US-based gangs have established strong working relationships with Central America and Mexico-based DTOs to perpetuate the smuggling of drugs across the US-Mexico and US-Canada borders. MDTOs control most of the cocaine, heroin, methamphetamine, and marijuana trafficked into the United States from Mexico and regularly employ lethal force to protect their drug shipments in Mexico and while crossing the US-Mexico border, according to NGIC and NDIC reporting.h
Mexican Drug Trafficking Organizations
MDTOs are among the most prominent DTOs largely because of their control over the production of most drugs consumed in the United States. They are known to regularly collaborate with US-based street and prison gang members and occasionally work with select OMG and White Supremacist groups, purely for financial gain (see Appendix B). The prospect of financial gain is resulting in the suspension of traditional racial and ideological division among US prison gangs, providing MDTOs the means to further expand their influence over drug trafficking in the United States.19 NDIC reporting indicates that Hispanic and African American street gangs are expanding their influence over drug distribution in rural and suburban areas and acquire drugs directly from MDTOs in Mexico or along the Southwest border.20
| Many Los Angeles-based Sinaloa cartel members use local gang members to assist in or commit kidnappings, acquire or sell drugs, and collect drug proceeds. |
Source: DHS September 2010; DEA November 2010
NGIC law enforcement partners report that gangs in their jurisdiction have ties to Mexican criminal organizations, such as MDTOs.
- Well-established US prison gangs such as the Hermanos de Pistoleros Latinos (HPL), La Eme, the Texas Syndicate, Barrio Azteca and the Tango Blast are reportedly aligned with or connected to MDTOs.
- NDIC reporting indicates that street gangs such as the Latin Kings, MS-13, Sureños, and Norteños maintain working relationships with MDTOs.21 Sureños in California and South Carolina maintain an association with the Los Zetas Cartel in Mexico, according to 2010 NGIC reporting.
- According to 2010 California Department of Corrections and Rehabilitation (CDCR) and open source reporting, some Aryan Brotherhood and La Eme prison gang members—bitter rivals inside prison—work together with MDTOs to smuggle drugs into California and prisons, steal vehicles, smuggle illegal weapons into Mexico, and intimidate rivals of the Mexican cartels.22
| US-Based Gangs with Ties to MDTOs |
Arizona New Mexican
Mafia
Aryan Brotherhood
Avenues
Bandidos
Barrio Azteca
Barrio Westside
Black Guerilla Family
Bloods
California Mexican
Mafia (Eme)
Crips
Hardtimes 13
Happytown Pomona
Hells Angels
Hermanos de
Pistoleros Latinos
(HPL)
La Nuestra Familia
Latin Kings
Lennox 13 |
Mara Salvatrucha
(MS-13)
Mexican Mafia
Mongols
Norteños
Satins Disciples
Sureños
Tango Blast
Texas Mexican Mafia
(Mexikanemi)
Texas Syndicate
Tri-City Bombers
Vagos
Vatos Locos
Westside Nogalitas
Wetback Power
Wonder Boys
18th Street Gang |
Figure 8. Mexican Drug Cartels

Source: Stratfor Global Intelligence
MDTOs contract with street and prison gangs along the Southwest border to enforce and secure smuggling operations in Mexico and the United States, particularly in California and Texas border communities.23 Gang members who are US citizens are valuable to MDTOs, as they can generally cross the US-Mexico border with less law enforcement scrutiny and are therefore less likely to have illicit drug loads interdicted.24 MDTOs use street and prison gang members in Mexico, Texas, and California to protect smuggling routes, collect debts, transport illicit goods, including drugs and weapons, and execute rival traffickers.25 Many of these crimes are committed in exchange for money and drugs, and as a result, street and prison gangs in the United States have gained greater control over drug distribution in rural and suburban areas. Gang members, including Barrio Azteca, MS-13 and Sureños have been intercepted driving with weapons and currency toward Mexico from such states as California, Colorado, Georgia, and Texas according to open source reporting.
| Major Mexican Drug Trafficking Organizations |
Arellano Felix
Beltran Leyva
Vicente Carrillo-
Fuentes
Gulf Cartel |
Los Zetas
Sinaloa
La Familia
Michoacana |
Gangs’ increased collaboration with MDTOs has altered the dynamics of the drug trade at the wholesale level. US gangs, which traditionally served as the primary organized retail or mid-level distributor of drugs in most major US cities, are now purchasing drugs directly from the cartels, thereby eliminating the mid-level wholesale dealer. Furthermore, advanced technology, such as wireless Internet and Voice over Internet Protocol (VoIP) capabilities, has made the recruitment, collaboration, and coordination of criminal activity more efficient and lucrative, and allows direct contact between the gangs and DTOs.26 To increase their control over drug trafficking in smaller markets, street gangs have acquired large wholesale quantities of drugs at lower prices directly from DTOs in Mexico and along the US Southwest border.27
- Recent intelligence indicates that the MDTO La Familia Michoacana has established US-based command-and-control groups which report to leaders in Mexico who manage street-level distribution in US cities.28
Gangs and Organized Criminal Groups
January 2010 FBI reporting indicates that some OMGs and street gangs are closely collaborating with African, Asian, Eurasian, and Italian organized criminal groups to facilitate street-level crimes such as extortion, enforcement, debt collection, and money laundering.
- In May 2010, New Jersey authorities indicted 34 members of the Lucchese crime family on racketeering, weapons offenses, bribery, money laundering, and conspiracy charges. The investigation revealed that members of the Lucchese family in New Jersey were working with the Nine Trey Gangster Bloods to smuggle drugs and cell phones into the East Jersey State Prison for fellow inmates, according to open source reporting.29
NGIC reporting indicates that some gangs are suspected of associating with African, Asian, and Eurasian criminal groups in California and Washington.i
- Law enforcement officials in Washington suspect that some Asian gangs, including the Oriental Boyz and the Tiny Rascal Gangsters, are involved with Asian organized crime and marijuana cultivating groups.
- In February 2011, authorities in southern California charged 99 Armenian Power gang members with kidnapping, extortion, bank fraud, and drug trafficking. Armenian Power members reportedly have ties to high-level crime figures in Armenia, Russia, and Georgia.30
Chart 3. Gang Associations with Criminal Organizations.
The NGIC collected intelligence from law enforcement officials nationwide in an effort to identify associations between gangs and criminal organizations. The following figures represent the percentage of law enforcement who report that gangs in their jurisdiction have ties to various criminal organizations.

Gangs and Corrections Issues
Prison gang-related crime and violence in the nation’s corrections system poses a significant threat to facility employees and a growing threat in many communities. Once incarcerated, most street gang members join an established prison gang to ensure their protection. Based on data provided by federal and state correctional agencies, the NGIC estimates that there are approximately 231,136 gang members incarcerated in federal and state prisons nationwide. Their large numbers and dominant presence allows prison gangs to employ bribery, intimidation, and violence to exert influence and control over many correctional facilities. Violent disputes over control of drug territory and enforcement of drug debts frequently occur among incarcerated gang members.
Figure 9. A US prison yard

Prison/Street Gang Connections
Many incarcerated gang members continue to engage in gang activities following incarceration and use their connections inside prison to commit crime in the community. Prison gang members influence and control gang activity on the street, and exploit street gangs for money and other resources.
Figure 10. Incarcerated MS-13 Members

Law enforcement officials report associations between street gang members and incarcerated gang members in their area.
- MS-13 members send funds not only to gang members on the street and in prison, but also to gang members in El Salvador, according to NGIC reporting.
Prison/Family Connection
A gang member’s incarceration often prompts his or her family to move closer to the correctional facility where the gang member is being housed. In some cases, family members assist or facilitate gang criminal activity and recruiting.
Family members of gangs operate as outside facilitators, serving as messengers, drug couriers, or in any capacity benefiting the gang. Outside facilitators are provided instructions by the incarcerated gang member, often during a social or legal visit, and in turn pass this information to gang members on the streets. Family members have also been used to assist prison escapes and smuggle contraband into correctional facilities, allowing incarcerated gang members to continue their operations inside prison.
Gangs in Contact with Incarcerated
Gang Members |
18th Street
415 Kumi
Arizona New Mexican
Mafia
Aryan Brotherhood
Aryan Brotherhood of
Texas
Aryan Circle
Bandidos
Barrio Azteca
Black Guerilla Family
Black Gangster
Disciples
Black P-Stone Nation
Bloods
California Mexican
Mafia
Colorado Aryan
Brotherhood
Crips
Dead Man Inc.
Dirty White Boys
Gangster Disciples
(GD)
Grupo 25 (G-25)
Grupo 27 (G-27)
Hells Angels (MC)
Hermanos de
Pistoleros Latinos
(HPL) |
La Nuestra Familia
Latin Kings
Los Carnales
MS-13
Nazi Low Riders
Ñetas
Norteños
Northern Riders
Northern Structure
Outlaws
Paisas
Raza Unida
Simon City Royals
Skinheads
Sureños
Syndicato De Nuevo
Mexico
Texas Chicano
Brotherhood
Texas Mexican Mafia
(Mexikanemi-EMI)
Texas Syndicate
United Blood Nation
Valluco Tango Blast
Vice Lords
West Texas Tangos |
Communication
Incarcerated gang members often rely on family, friends, corrupt lawyers and corrections personnel to transmit their messages to gang members on the street. Incarcerated gang members exploit attorney-client privileges, which include unmonitored visiting and legal mail, to pass coded or concealed communications.j
Contraband Cell Phones
Smuggled cell phones are a continuing problem for prison administrators in correctional facilities throughout the country. Smuggled cell phones and Smart Phones afford incarcerated gang members more influence and control over street gangs through unrestricted access and unmonitored conversations via voice calling, Internet access, text messaging, email, and social networking websites. Instances of violence directed by inmates using mobile devices are also a growing concern for corrections officials. Incarcerated gang members communicate covertly with illegal cell phones to plan or direct criminal activities such as drug distribution, assault, and murder.
Cell phones smuggled into correctional facilities pose the greatest threat to institution safety, according to NGIC and BOP reporting.
- In 2010 a New Jersey inmate was prosecuted for using a contraband cell phone to order the murder of his former girlfriend in retaliation for her cooperation with police regarding an investigation involving the inmate.31
| Illegal Cell Phones in California Prisons |
The majority of illegal cell phones in California prisons are smuggled in by visitors or correctional staff. Many cell phones have also been discovered
in legal mail and quarterly packages. In 2010, more than 10,000 illegal cell phones were confiscated from prisoners in California.
Historically, correctional staff who have been caught smuggling phones have been successfully prosecuted only when the phone was connected to a more serious charge such as drug distribution,
and district attorney offices rarely prosecute unless a more serious offense is involved. In March 2011, legislation was approved in the California State Senate to criminalize the use of cell phones in prison, including penalties for both smugglers and inmates.
Sources: US Bureau of Prisons and CDCR; California State Senate Press Release, 22 March 2011
- In March 2010, an off-duty captain in the South Carolina Department of Corrections was shot in his home by an armed intruder. Although the captain survived, the assault had been ordered by a South Carolina inmate using a smuggled cell phone.32
Leadership
Gang members who have been incarcerated are often more respected on the streets by younger gang members, which makes it easier to establish or re-establish themselves in leadership positions and order younger gang members to commit crimes.k These gang leaders also use connections made in prison to establish contacts and criminal networks in the community, which allows them to more successfully control gang operations. Also, in the wake of leadership disorganization at the street level due to indictments and arrests, a released gang member may find it easy to use his influence and status as an ‘original gangster’ (OG) or Veterano to assume control of the gang.
Law enforcement officials report that released prison gang members in some jurisdictions are establishing or re-establishing leadership roles or active roles in local gangs.
Prison Radicalization
Gang members’ vulnerability to radicalization and recruitment for involvement in international or domestic terrorism organizations is a growing concern to law enforcement. Gang members’ perceptions of disenfranchisement from or rejection of mainstream society and resentment towards authority makes them more susceptible to joining such groups and can be attractive and easy targets for radicalization by extremist groups.
NGIC reporting indicates that incarcerated gang members in some jurisdictions are adopting radical religious views in prison.
Prison gangs that tend to be dedicated to political or social issues are often more susceptible to influence by extremist ideologies. In some instances, prison gang members may even emulate various terrorist movements by embracing their symbolism and ideology to enhance the gang’s own militant image within the prison setting.
Prison and street gang members are also susceptible on an individual basis to radicalization. Various correctional agencies have reported individual members of the Black Peace Stones, Crips, Latin Kings, and Insane Latin Disciples embracing radical ideologies.
Gang Infiltration of Corrections, Law Enforcement, and Government
Gang infiltration of law enforcement, government, and correctional agencies poses a significant security threat due to the access criminals have to sensitive information pertaining to investigations or protected persons. Gang members serving in law enforcement agencies and correctional facilities may compromise security and criminal investigations and operations, while acquiring knowledge and training in police tactics and weapons. Corrupt law enforcement officers and correctional staff have assisted gang members in committing crimes and have impeded investigations.
NGIC reporting indicates that gang members in at least 57 jurisdictions, including California, Florida, Tennessee, and Virginia, have applied for or gained employment within judicial, police, or correctional agencies.
- A Crip gang member applied for a law enforcement position in Oklahoma.
- OMGs engage in routine and systematic exploitation and infiltration of law enforcement and government infrastructures to protect and perpetrate their criminal activities. OMGs regularly solicit information of intelligence value from government or law enforcement employees.
NGIC reporting indicates that gang members in at least 72 jurisdictions have compromised or corrupted judicial, law enforcement, or correctional staff within the past three years.
- In November 2010, a parole worker in New York was suspended for relaying confidential information to a Bloods gang member in Albany, according to open source reporting.33
- In July 2010, a Riverside County, California detention center sheriff deputy was convicted of assisting her incarcerated Eme boyfriend with murdering two witnesses in her boyfriend’s case.34
- In April 2010, a former Berwyn, Illinois police officer pleaded guilty to charges of conspiracy to commit racketeering and to obstruct justice for his part in assisting an OMG member in targeting and burglarizing rival businesses.35
Gangs and Indian Country
Native American gang presence has increased on Indian Reservations and in federal and state prison systems throughout the United States over the past few years, according to Bureau of Justice Statistics reporting.36,l Native American gang members, operating on numerous reservations throughout the United States, are emulating Hispanic gangs such as the Barrio Aztecas, Norteños, and Sureños; African American gangs such as the Bloods and Crips; and predominately Caucasian gangs such as the Juggalos. Some gangs, such as the Native Mob and Native Pride—which primarily operates in North Dakota, Minnesota, South Dakota, and Wisconsin—formed in the prison system and then expanded to reservations, according to NGIC reporting. Although most gangs in Indian Country are disorganized, lack significant structure and ties to national-level gangs, and are incapable of attaining control over large geographic areas or populations, some are involved in serious crimes and violent activities and utilize Indian Reservations to facilitate and expand their drug operations.
| Indian Country and the US Border |
The shared international border and geography of some Indian Reservations make it conducive to cross-border drug trafficking activity while also inhibiting interdiction efforts. Increased security at US/Mexican borders has resulted in the discovery of illicit marijuana farms from
California to South Dakota, primarily operated by Mexican gangs. Tighter border security makes it difficult for MDTOs to smuggle marijuana north thus raising the price of marijuana in the United States higher than in Mexico. Marijuana (stems and leaves) grown in Mexico costs $500 to $700 per pound, whereas a pound of marijuana grown in Washington State can cost $2,500 to $6,000 when sold on the East Coast.
Online News Article; The Wall Street Journal; “Mexican Pot Gangs Infiltrate Indian Reservations in US;” 5 November 2009; available at http://online.wsj.com/article/SB125736987377028727.html.
The growth of gangs on Indian Reservations is heavily influenced by the urban gang culture and media attention. Gang members on Indian Reservations often emulate national-level gangs and adopt names and identifiers from nationally recognized urban gangs. However, emulation is most often limited to identifiers—colors, signs, symbols, names—and leadership structure is often loosely organized or absent. NGIC reporting indicates that national-level gangs such as the Barrio Azteca, Bloods, Crips, Mexican Mafia, and Norteños are operating on a number of Indian Reservations. Native American gang members on reservations are also involved in gang-related activity with gang members in communities outside of reservations.
NGIC reporting indicates that urban gangs such as the Norteños and Sureños associate and/or influence the gang culture on several Indian Reservations.
In some jurisdictions, Native American gang members are associated with or involved in gang-related criminal activity with gang members off the reservation, including drug distribution, money laundering, assaults, and intimidation. Partnerships are often established for financial gain, drug distribution, and to evade law enforcement.
Figure 12. Graffiti on Ft. Apache-San Carlos Indian Reservation

Source: FBI
- The Warm Springs Indian Reservation in Oregon is becoming an ideal location for illicit marijuana farms because of its fertile grounds and isolated location. Within the past few years authorities have seized at least 12,000 harvested adult marijuana plants with an estimated street value of $10 million.37
Geography, as well as the extent of law enforcement monitoring of the reservations, make some Indian Reservations conducive to cross-border drug trafficking.
- As much as 20 percent of all high-potency marijuana produced in Canada each year is smuggled through the St. Regis Mohawk Reservation in New York, according to NDIC reporting.
- Marijuana produced in Mexico is transported by MDTOs through the Tohono O’odham Reservation in Arizona largely due to the 75 miles of lightly patrolled border with Mexico, according to NDIC reporting.
Gangs and the Military
Gang recruitment of active duty military personnel constitutes a significant criminal threat to the US military. Members of nearly every major street gang, as well as some prison gangs and OMGs, have been reported on both domestic and international military installations, according to NGIC analysis and multiple law enforcement reporting. Through transfers and deployments, military-affiliated gang members expand their culture and operations to new regions nationwide and worldwide, undermining security and law enforcement efforts to combat crime. Gang members with military training pose a unique threat to law enforcement personnel because of their distinctive weapons and combat training skills and their ability to transfer these skills to fellow gang members.
NGIC reporting indicates that law enforcement officials in at least 100 jurisdictions have come into contact with, detained, or arrested an active duty or former military gang member within the past three years.
- Gang members have been reported in every branch of the US militarym, although a large proportion of these gang members and dependent gang members of military personnel are affiliated with the US Army, Army Reserves, and National Guard branches.
Figure 13. ‘Support your local Hells Angels’ graffiti on military vehicle in Iraq

Source: FBI
Figure 14. A soldier in a combat zone throwing gang signs

Source: FBI
Many street gang members join the military to escape the gang lifestyle or as an alternative to incarceration, but often revert back to their gang associations once they encounter other gang members in the military. Other gangs target the US military and defense systems to expand their territory, facilitate criminal activity such as weapons and drug trafficking, or to receive weapons and combat training that they may transfer back to their gang. Incidents of weapons theft and trafficking may have a negative impact on public safety or pose a threat to law enforcement officials.
As of April 2011, the NGIC has identified members of at least 53 gangs whose members have served in or are affiliated with US military. Among the identified gangs with military-trained members are street gangs such as the Asian Boyz, Bloods, Crips, Gangster Disciples, Latin Kings, MS-13, Sureños, Tiny Rascal Gangsters, and the Juggalos; the Aryan Brotherhood, Barrio Azteca, and Texas Syndicate prison gangs; and OMGs including the Bandidos, Hells Angels, Mongols, Outlaws, and Vagos. Some gangs, particularly OMGs, actively recruit members with military training or advise members without criminal records to join the military for necessary weapons and combat training.
- Younger gang members without criminal records are attempting to join the military, as well as concealing tattoos and gang affiliation during the recruitment process, according to NGIC reporting.
Deployments have resulted in integrating gang members with service members and/or dependents on or near overseas military installations, including those in Afghanistan, Germany, Iraq, Italy, Japan, and South Korea. US military officials have reported a rise in gang graffiti both on and off post in Afghanistan and Iraq (see Figure 14).
Table 3. Gangs with Members Who have Served in the US Military
| Gang Name |
Type |
Military Branch(s) |
| 18th Street Gang |
Street |
Army, Marines, Navy |
| Aryan Brotherhood |
Prison |
Army, Marines, Navy |
| Asian Boyz |
Street |
Army |
| Asian Crips |
Street |
Army |
| Avenues Gang |
Street |
Marines |
| Bandidos |
OMG |
Army, Marines |
| Barrio Azteca |
Prison |
Marines |
| Black Disciples |
Street |
Army, Marines, Navy |
| Black Guerilla Family* |
Prison |
Army |
| Bloods |
Street |
Army, Army Reserves, Coast Guard, Marines, Navy |
| Brotherhood |
OMG |
Marines |
| Crips |
Street |
Army, Air Force, Marines, Navy |
| Devils Disciples |
OMG |
Unknown |
| East Side Longos |
Street |
Army, Special Forces |
| Florencia 13 |
Street |
Army, Marines |
| Fresno Bulldogs |
Street |
National Guard, Marines |
| Gangster Disciples |
Street |
Army, Marines, Navy, National Guard |
| Georgia Boys (Folk Nation) |
Street |
Army |
| Haitian Mob |
Street |
Army |
| Hells Angels |
OMG |
All branches |
| Iron Horsemen |
OMG |
Army |
| Juggalos/ICP |
Street |
Army, Air Force |
| Korean Dragon Family |
Street |
Marines |
| Latin Kings |
Street |
Army, Army Reserves, Marines, Navy |
| Legion of Doom |
OMG |
Air Force |
| Life is War |
Street |
Army |
| Los Zetas |
Street |
Army |
| Maniac Latin Disciples |
Street |
Marines |
| Mexican Posse 13 |
Street |
Army |
| Military Misfits |
OMG |
Marines, Navy |
| Molochs |
OMG |
Marines |
| Mongols |
OMG |
Marines, Navy |
| Moorish Nation |
Separatist |
Army |
| MS-13 |
Street |
Army, Marines, Navy |
| Norteños |
Street |
Army, Marines, National Guard, Navy |
| Outlaws |
OMG |
All branches |
| Peckerwoods |
Street |
Marines, Navy, National Guard, Reserves |
| Red Devils |
OMG |
Army/ Coast Guard |
| Simon City Royals |
Street |
Navy |
| Sons of Hell |
OMG |
Marines |
| Sons of Samoa |
Street |
Army |
| Southside Locos |
Street |
Army |
| Sureños |
Street |
Army, Marines, Navy |
| Tango Blast |
Prison |
Army* |
| Texas Syndicate |
Prison |
Army, Marines |
| Tiny Rascal Gangsters |
Street |
Army |
| United Blood Nation |
Street |
Army |
| Vagos |
OMG |
Army, Marines, Navy |
| Vatos Locos |
Street |
Army |
| Vice Lords |
Street |
Army |
| Wah Ching Gang |
Street |
Army |
| Warlocks |
OMG |
Air Force, Marines |
* Only gang graffiti was identified
Gangs and the US Border
Figure 15. The Southwest Border Region

Source: America.gov
The Southwest Border
The US Southwest Border regionn represents a continuing criminal threat to the United States. The rugged, rural, and porous area along the nearly 2,000 miles of contiguous US-Mexican territory invites widespread criminal activity, including drug and arms trafficking, alien smuggling, human trafficking, extortion, kidnapping, and public corruption. US-based gangs, MDTOs, and other criminal enterprises in both the United States and Mexico are readily exploiting this fluid region and incur enormous profit by establishing wide-reaching drug networks; assisting in the smuggling drugs, arms, and illegal immigrants; and serving as enforcers for MDTO interests on the US side of the border.
Violence in Mexico—particularly in its northern border states—has escalated with over 34,000 murders committed in Mexico over the past four years.38 While intensified scrutiny from Mexican law enforcement has forced significant disruptions in several dangerous MDTOs, such disruptions have also served to disrupt the balance of power among these organizations. This has prompted drug cartel rivalries to employ more aggressive tactics as they attempt to assert control over the Southwest border region and its highly lucrative drug trafficking corridors.39 Although the majority of the violence from feuding drug cartels occurs in Mexico,o Mexican drug cartel activity has fueled crime in the porous US Southwest Border region, where easy access to weapons, a high demand for drugs, ample opportunity for law enforcement corruption, and a large Hispanic population ripe for recruitment and exploitation exists.40
Hispanic prison gangs along the Southwest border region are strengthening their ties with MDTOs to acquire wholesale quantities of drugs, according to NDIC reporting.41 In exchange for a consistent drug supply, US-based gangs smuggle and distribute drugs, collect drug proceeds, launder money, smuggle weapons, commit kidnappings, and serve as lookouts and enforcers on behalf of the MDTOs. MDTOs subsequently profit from increased drug circulation in the United States, while US-based gangs have access to a consistent drug supply which expands their influence, power, and ability to recruit.42
According to NDIC reporting, more than 45 percent of law enforcement agencies in the Southwestern United States report that gangs in their jurisdiction are moderately to highly involved in drug activity, while 30 percent indicate that street gang involvement in drug activity increased within the past year.
Gang-related activity and violence has increased along the Southwest border region, as US-based gangs seek to prove their worth to the drug cartels, compete with other gangs for favor, and act as US-based enforcers for cartels which involves home invasions, robbery, kidnapping, and murder.
- In July 2010, Mexican authorities arrested two members of the Barrio Azteca for the murders of a US Consulate employee and her husband in Juarez, Mexico. The gang, who allegedly committed the murders on behalf of the Juarez Cartel, has also made several threats against law enforcement officials.43,p
Arrangements between gangs operating along the Southwest border and MDTOs are the result of physical proximity and strong familial ties that many US-based Hispanic gang members retain with family and friends in Mexico.
Northern Border
Gangs pose a growing problem for law enforcement along the US-Canada border, particularly the border areas in the New England and Pacific Regions. Gangs smuggle drugs, cigarettes, firearms, and immigrants across the US-Canada borders, according to NDIC reporting.44 Members of several regional- and national-level gangs, including Asian Boyz, Hells Angels, and Outlaws, smuggle large quantities of illicit drugs across the US-Canada border in New England, often conducting their smuggling operations in association with members of transnational criminal and drug trafficking organizations. According to law enforcement officials in the Pacific Region, members of several gangs, including the Hells Angels and Asian gangs, engage in cross-border criminal activity in their jurisdictions.
| Los Zetas Drug Trafficking Organization |
Los Zetas organization was established in the late 1990s as the enforcement arm of the Gulf Cartel drug trafficking organization to protect and expand the Gulf Cartel’s operations. Consisting of highly trained soldiers who defected from the Mexican Special Air Mobile Force Group (GAFE), the Zetas have evolved from a wing of the Gulf Cartel into their own drug trafficking organization.
- Hells Angels members have reportedly smuggled MDMA (Ecstasy) from British Columbia, Canada into Bellingham, Washington, according to 2010 open source reporting.
- Asian DTOs smuggle large quantities of MDMA through and between ports of entry along the US-Canada border, according to 2010 NDIC reporting.45
Figure 16. Los Zetas Commando Medallion

Source: ATF
Canadian DTOs smuggle significant amounts of cash generated from the US distribution of Canada-produced drugs into Canada, according to NDIC reporting. The Akwesasne Territory, which straddles the US–Canada border, is one of the most prominent smuggling corridors for Canada-bound bulk cash. The topography of the US-Canada border is conducive to bulk cash smuggling because currency interdiction by law enforcement officials is often hampered by the border’s length and rugged terrain.46
Gangs, Technology, and Communication
Gangs are becoming increasingly savvy and are embracing new and advanced technology to facilitate criminal activity and enhance their criminal operations. Prepaid cell phones, social networking and microblogging websites, VoIP systems, virtual worlds, and gaming systems enable gang members to communicate globally and discreetly. Gangs are also increasingly employing advanced countermeasures to monitor and target law enforcement while engaging in a host of criminal activity.
Internet Use for Propaganda, Intimidation, and Recruitment
According to open sources and law enforcement reporting, since 2005, MDTOs have exploited blogs and popular websites like YouTube and MySpace for propaganda and intimidation. MDTOs have posted hundreds of videos depicting interrogations or executions of rival MDTO members. Other postings include video montages of luxury vehicles, weapons, and money set to the music of songs with lyrics that glorify the drug lifestyle. While some of these postings may offer specific recruitment information, they serve more as tools for propaganda and intimidation.
Gang members routinely utilize the Internet to communicate with one another, recruit, promote their gang, intimidate rivals and police, conduct gang business, showcase illegal exploits, and facilitate criminal activity such as drug trafficking, extortion, identity theft, money laundering, and prostitution. Social networking, microblogging, and video-sharing websites—such as Facebook, YouTube, and Twitter—are now more accessible, versatile, and allow tens of thousands of gang members to easily communicate, recruit, and form new gang alliances nationwide and worldwide.q
NGIC reporting indicates that a majority of gang members use the Internet for recruitment, gang promotion, and cyber-bullying or intimidation. Many also use the Internet for identity theft, computer hacking, and phishing schemes.
- According to NGIC reporting, gang recruitment and intimidation is heavily facilitated through the Internet. Gangs use social networking sites such as Facebook to promote their gang, post photos of their gang lifestyle, and display their bravado, which ultimately influences other youth to join gangs.
- NGIC law enforcement partners report that gangs in their jurisdiction are frequently using the Internet to recruit and communicate with gang members throughout the region, nationwide, and in Central and South America. Law enforcement officials in Texas report that incarcerated gang members use Facebook and MySpace to recruit.
- Police in Missouri report a rise in “promotion teams”—often consisting of gang members—using Internet chat rooms to promote clubs and parties for a fee, according to NGIC reporting.
The proliferation of social networking websites has made gang activity more prevalent and lethal—moving gangs from the streets into cyber space. Gang members, criminals, and drug traffickers are using the Internet not only to recruit and build their social networks, but to expand and operate their criminal networks without the proximity once needed for communication. Likewise, youth in other regions and countries are influenced by what they see online and may be encouraged to connect with or emulate a gang, facilitating the global spread of gang culture.
- Gang members in Missouri and Nebraska are increasingly using social media to recruit and communicate with other gang members, according to NGIC reporting.
Second Life Virtual World
Second Life is a computer-based virtual world with a simulated environment where users inhabit and interact via avatars, or graphical representations. The virtual world may depict a real world or a fantasy world. Users communicate through text-chat and real-time voice-based chat. Second Life provides versatility and anonymity and allows for covert communications. Because of its anonymity and versatility, gang members could potentially use Second Life to recruit, spread propaganda, commit other crimes such as drug trafficking, and receive training for real-world criminal operations.
Source: Information available at http://www.secondlife.com
According to information obtained from multiple state and federal law enforcement sources, incarcerated gang members are accessing micro-blogging and social networking web sites such as MocoSpace and Twitter with smuggled prepaid cellular telephones and using the messaging features to coordinate criminal activity.
Street gang members are also involved in cyber attacks, computer hacking, and phishing operations, often to commit identity theft and fraud.
Gangs and Weapons
Gang members are acquiring high-powered, military-style weapons and equipment, resulting in potentially lethal encounters with law enforcement officers, rival gang members, and innocent bystanders. Law enforcement officials in several regions nationwide report gang members in their jurisdiction are armed with military-style weapons, such as high-caliber semiautomatic rifles, semiautomatic variants of AK-47 assault rifles, grenades, and body armor.
Figure 17. Weapons recovered from Barrio Azteca Members in Ciudad Juarez, Mexico


Source: ATF
Law enforcement officials in 34 jurisdictions report that the majority of gang-related crime is committed with firearms.
Gang members acquire firearms through a variety of means, including illegal purchases; straw purchases through surrogates or middle-men; thefts from individuals, vehicles, residences and commercial establishments; theft from law enforcement and military officials, from gang members with connections to military sources of supply, and from other gangs, according to multiple law enforcement and NGIC reporting.
Gang members are becoming more sophisticated and methodical in their methods of acquiring and purchasing firearms. Gang members often acquire their firearms through theft or through a middleman, often making a weapons trace more difficult.
Enlisted military personnel are also being utilized by gang members as a ready source for weapons.
- In November 2010, three former US Marines were arrested in Los Angeles, California, for selling illegal assault weapons to Florencia 13 gang members, according to open souce reporting.47
- In November 2010, a US Navy Seal from San Diego and two others were arrested in Colorado for smuggling at least 18 military issued machine guns and 14 other firearms from Iraq and Afghanistan into the United States for sale and shipment to Mexico, according to open source reporting.48
Gang members are employing countermeasures to monitor, intercept, and target law enforcement, sometimes with elaborate weapons and devices.
- In February 2010, a Riverside County gang task force officer in California was nearly killed when suspected members of a White Supremacist gang rigged a zip gun on a gang task force security fence to discharge if anyone entered their property (see Figure 20). In December 2009, the same group staged a natural gas explosion at their property intended for law enforcement entering the premises.49
Figure 18. Zip gun attached to the fence of a Gang Task Force in Hemet, CA

Source: ATF
Gangs and White Collar Crime
NGIC reporting indicates that gangs are becoming more involved in white collar crime, including identity theft, bank fraud, credit card fraud, money laundering, fencing stolen goods, counterfeiting, and mortgage fraud, and are recruiting members who possess those skill sets. Law enforcement officials nationwide indicate that many gangs in their jurisdiction are involved in some type of white collar crime.
| Gang Members Targeting Law Enforcement Vehicles for Weapons |
In 2009, suspected gang members in Broward County and West Palm Beach, Florida burglarized nearly a dozen marked and unmarked law enforcement vehicles stealing firearms, ballistic vests, and police identification.
Source: FBI-NGIC, “Gangs Targeting Law Enforcement for Weapons and Equipment Theft; Intelligence Bulletin; 21 December 2009
- NGIC reporting indicates that the Bloods, Crips, Gangster Disciples, Vice Lords, Latin Kings, Mexican Mafia, Sureños, Norteños, La Nuestra Familia, Texas Syndicate, Aryan Brotherhood, various OMG and Asian gangs, and neighborhood-based gangs are engaging in white collar crime.
Many gang members are engaging in counterfeiting because of its low risks and high financial rewards.
- In July 2010, a Florencia 13 gang member in Los Angeles was arrested for operating a lab from his home that manufactured pirated video games.50
- In April 2010, a member of the East Coast Crips was arrested in Los Angeles, California, for the sale of counterfeit goods and drug trafficking at a clothing store he co-owned. Police confiscated 824 counterfeit items from the store worth $43,762.51
Gang members are laundering profits from criminal activities such as drug trafficking and prostitution, through front companies such music businesses, beauty shops, auto repair shops, law firms, and medical offices.
- Members of the Black Guerilla Family in Maryland used pre-paid retail debit cards as virtual currency inside Maryland prisons to purchase drugs and further the gangs’ interests, according to August 2010 open source reporting.52
Some gangs, such as the Bloods and Gangster Disciples, are committing sophisticated mortgage fraud schemes by purchasing properties with the intent to receive seller assistance loans and, ultimately retain the proceeds from the loans, or to comingle illicit funds through mortgage payments. Gang members are also exploiting vulnerabilities in the banking and mortgage industries for profit.
- According to open source reporting, in April 2009, members of the Bloods in San Diego, California were charged with racketeering and mortgage fraud.53
Law Enforcement Actions and Resources
Gang units and task forces are a vital component in targeting gangs and have played a substantial role in mitigating gang activity in a number of US communities. The majority of NGIC law enforcement partners report that their agency has or participates in a gang task force, and most utilize a gang database to track and monitor gang members in their jurisdictions. There are 168 FBI Violent Gang Task Forces in the United States, Puerto Rico, and the US Virgin Islands. In addition, ATF operates 31 Violent Crime Impact Teams (VCIT) and ICE operates eight Operation Community Shield (OCS) Initiatives nationwide (see Appendix C). The collaboration and coordination of federal, state, and local law enforcement agencies has resulted in a number of successes involving gang suppression efforts.
NGIC law enforcement partners in at least 107 jurisdictions report that law enforcement action has resulted in a decrease of gangs or gang activity in their region.
- In March 2011, officials from DHS, CBP, ICE, ATF, and local San Diego police were involved in the arrest of over 67 gang members and associates for drugs and cross-border crimes in the San Diego, California area. Operation Allied Shield III, a part of a San Diego County initiative to focus on prevention, detection, and suppression of crimes in areas impacted by border-related crime, aimed to seize drugs and weapons and to identify and observe gang members in a proactive way.54
- In March 2011, 35 leaders, members, and associates of the Barrio Azteca gang in Texas were charged in a federal indictment for various counts of racketeering, murder, drug offenses, money laundering, and obstruction of justice. Ten subjects were charged with the March 2010 murders of a US Consulate employee, her husband, and the husband of another consulate employee, in Juarez, Mexico.55
- In February 2011, FBI, ATF, ICE, and DHS, and numerous state and local officials charged 41 gang members and associates from several different gangs in five districts with multiple offenses, including racketeering conspiracy, murder, drug and gun trafficking. The indictment involved members from the Click Clack gang in Kansas City, Missouri; the Colonias Chiques gang in Los Angeles; the Sureno 13 and San Chucos gangs in Las Vegas; MS-13 in Washington; and 13 Tri-City Bomber members and associates in the McAllen, Texas area.56
Outlook
Street, prison, and motorcycle gang membership and criminal activity continues to flourish in US communities where gangs identify opportunities to control street level drug sales, and other profitable crimes. Gangs will not only continue to defend their territory from rival gangs, but will also increasingly seek to diversify both their membership and their criminal activities in recognition of potential financial gain. New alliances between rival gangs will likely form as gangs suspend their former racial ideologies in pursuit of mutual profit. Gangs will continue to evolve and adapt to current conditions and law enforcement tactics, diversify their criminal activity, and employ new strategies and technology to enhance their criminal operations, while facilitating lower-risk and more profitable schemes, such as white collar crime.
The expansion of communication networks, especially in wireless communications and the Internet, will allow gang members to form associations and alliances with other gangs and criminal organizations—both domestically and internationally—and enable gang members to better facilitate criminal activity and enhance their criminal operations discreetly without the physical interfacing once necessary to conduct these activities.
Changes in immigrant populations, which are susceptible to victimization and recruitment by gangs, may have the most profound effect on street gang membership. Continued drug trafficking-related violence along the US Southwest border could trigger increased migration of Mexicans and Central Americans into the United States and, as such, provide a greater pool of victims, recruits, and criminal opportunities for street gangs as they seek to profit from the illegal drug trade, alien smuggling, and weapons trafficking. Likewise, increased gang recruitment of youths among the immigrant population may result in an increase in gang membership and gang-related violence in a number of regions.
Street gang activity and violence may also increase as more dangerous gang members are released early from prison and re-establish their roles armed with new knowledge and improved techniques. Prison gang members, already an ideal target audience for radicalization, may expand their associations with foreign gang members or radical criminal organizations, both inside correctional institutions and in the community upon their release.
Gang members armed with high-powered weapons and knowledge and expertise acquired from employment in law enforcement, corrections, or the military may pose an increasing nationwide threat, as they employ these tactics and weapons against law enforcement officials, rival gang members, and civilians.
Globalization, socio-political change, technological advances, and immigration will result either in greater gang expansion and gang-related crime or displace gang members as they search for criminal opportunities elsewhere. Stagnant or poor economic conditions in the United States, including budget cuts in law enforcement, may undercut gang dismantlement efforts and encourage gang expansion as police agencies redirect their resources and disband gang units and taskforces, as reported by a large number of law enforcement agencies.
Maps. Gang Presence in the United States
Map 1. US Nationwide Gang Presence

Map 2. West Region

Map 3. South Central Region

Map 4. North Central Region

Map 5. Southeast Region

Map 6. Northeast Region

Map 7. FBI Uniform Crime Report (UCR) Violent Crime, 2009

APPENDIX A. Gangs by State
ALABAMA
31st Street Mob
33rd Street Posse
400 Block
4th Ward Bloods
Alberta City Boys
Alpha Tau Omega
Aryan Brotherhood
Avenue Piru Gangsters Bandaleros
Bandidos MC
Bay Boys
Black Cherry 8 Balls
Black Gangster Disciples
Black Mafia Family
Black Pistons MC
Bloods Boom Squad
Brown Pride
Central Park Bloods
Central Park Boys
Collegeville Posse
Corner Boys Crips
Devils Disciples MC
Eastside Bloods
Ensley Town Killers
Evergreen Bottom Boys
Gad Town Klowns
Gangsta G’s
Gangster Disciples
Ghettie Boyz
Give No Fucks
Green Acres Crips
Hazel Green Boys
Hells Lovers MC
Imperial Gangster Disciples
Insane Gangster Disciples
Juggalos
La Familia
La Quemada
Latin Kings
Latino Bloods Crips
Little Trouble Makers
Los Bolinos
Los Zetas
Lovemans Village Posse
Lynch Mob
Malditos 13
Melos 13
Northside Bloods
Northsiders 62 Po Boys
On Fire Boys
On Fire Girls
Outcast MC
Pistoleros MC
Outlaws MC
Pratt Boys
Riley Boys
Seven Deadly Sins
Sherman Heights Posse
Sin City Disciples MC
Six Deuce Brims
Smithfield Posse
Southern Brotherhood
Southside Cyclones
Southside Locos
Southside Youngsters
Sur-13
T Dub
Tango Blast
Technical Knockout
Titusville Posse
Toney Project Boys
Trap Boys
Trap Girls
Tribe MC
United Together Forever
Vatos Locos
Vice Hill Posse
Vice Lords
View Mob
Westside Crips
Wheels of Soul MC
Wylam Boys
ALASKA
50150 Crips
88 Street Crips
Almighty Latin King Nation
Almighty Vice Lord Nation
Altadena Crip Gangster
American Front
Aryan Brotherhood
Baby Hamo Tribe
Black Gangster Disciples
Blackwood Mafia
Chaos Drama Family
Combat Crips
Compton Swamp Crips
Deuce
Faceside Bloods
Fam Bam
Franklin Family Piru
Fresno Bulldogs
Full Time Criminals
Gangster Disciples
Goonies For Life
Hamo Tribe
Hells Angels MC
Hmong Nation Society
Hollow Tip Crew
Iceberg Clique
Juvenile Delinquents
Korrupt(ed) Crew
Laos Oriental Soldiers
Laotian Blood Killers
Laotian Thugz
Locc Down Crips
Loco Latin Crips
Los Malditos
MS-13
Member of Blood
Menace of Destruction
Mongolian Boys Society
Mountain View Crips
Murder Mob
Northside Damu
Outlawz
Peckerwoods
Real ‘Bout It Individuals
Royal Samoan Posse
Samoan Dynasty
Sons of Samoa
Soulja Crew
Southside Mesa
Sureños
The Family
The Low Lifes
Tiny Rascals Gang
Tongang Crip Gang
Top Notch Ballers
Uso 4 Life
Uso Squad
Westside City Crips
Westside Inland Empire Projects
Yellow Oriental Troop
Young Gangsta Niggas
ARIZONA
“A” Mountain Crips
10th Ave JP Crips
12th Ave Crips
29th Street Bloods
36th Street Vista Bloods
36th Street Vista Chicanos
4th Ave Crips
Aryan Brotherhood
Barrio Anita
Barrio Centro
Barrio Chicano Southside
Barrio Hollywood
Barrio Libre
Barrio Loco
Barrio Nuevo Locos
Barrio Savaco
Bilby Street Crips
Black Rags
Duce Nine Crips
Eastside Bloods
Eastside Crips
Eastside Maria Crips
Eastside Torrance
Folk Nation
Gangster Disciples
Grandale
Hells Angels MC
Hollywood Soma
Juggalos
Jollyville Crips
La Tusa
La Victoria Locos
Little Town
Little Town Crips
Locos Bloodline
Manzanita Lynch Mob Crips
Maryvale Gangsta Crips
Mau Mau
Mexican Mafia
Midvale Park Bloods
Mission Manor Park Bloods
Mongols
New Mexican Mafia
Northside Chicanos
Northside White Pride
Okie Town
Old Mexican Mafia
Old Pascua
Peckerwoods
Skinheads
Sons of Hell
South Palo Verde Bloods
South Park Family Gangsters
Southeast Hustler Bloods
Southside Boyz
Southside Brown Pride
Southside Harbor City
Southside Posse Bloods
Sureños
Trekell Park Crips
Varrio Loco
V-12 Bloods
Vagos MC
Vindlanders
West Mesa
West Ross Street Piru
Western Hills Posse Bloods
Westside Brown Pride
Wet Back Power
Warrior Society
Western Hills Bloods
ARKANSAS
Bandidos MC
Blood
Crips
Folk Nation
Outlaws MC
People Nation
Sons of Silence MC
Wheels of Soul MC
CALIFORNIA
18th St
159th Avenue
17th St
38th Avenue Locos
38th Street
415 Kumi
49 St hustler Crips
5/9 Brims
51st Avenue locos
51st St locos
A Street
AC Acorn
Acre Boys
Al Capone
Aryan Brotherhood
Asian Boyz
Asian Crips
Asian Insane Boys
Asian Street Walkers
Asian Warriors
Atascadero 13
AVE 39
AVE 51
AVE 53
Aztec Tribe Cholos
Azusa 13
B Street
Bahala Na’ Barkada
Bakersfield Bastards MC
Barrio San Juan 13
Barrio Cathedral City
Barrio Eastside
Barrio Pobre
Barrio San Juan
Barrio Small Town
Brown Brotherhood
Brown Crowd Locos
Barrio Central Vallejo
Black Guerilla Family
Block Boys
Blue Team
Blvd Crips
Bolen
Border Brothers
Bratz
Brick Block Crips
Broderick Boys
Brown Brotherhood
Brown Life Familia
Brown Pride Soldiers
Brown Pride Soldiers 13
Brown Pride Sureño
Browns Town
Bulldogs
Burger Team
Calle Ocho (8th street)
Campbell Village Gangsters
Campos Ramos Locos
Canta Ranas 13
Carmelas 13
Carps
Central Vallejo Clicka
Chankla Bulldogs
Chino Sinners
City Heights Trece Juniors
Clairemont Locos
Coachella Tiny Locos
CoCo County Boys
Cold Nigga Mafia
Colonia Bakers
Compton Varrio Tortilla Flats
Corona Varrio Locos
Country Boy Crips
COVINA 13
Crazy Brothers Clan
Crazy Brown Norteños
Crazy Fucking Mexicans
Crazy Krooks
Crazy Royal Kings
Crow Village
Cudahy 13
Cut Throat Mob
Davis Street Locos
Dead End Street
Death Crowd 13
Del Sol
Delhi Alley Boys
Desperados MC
Dirty Thirties
Dog Soldiers
Dreamhomes
Droppin Niggas Instantly
Down To Scrap Krew
East Coast Crips
Eastbound Loco
Eastside Familia
Eastside Longos
Eastside Rivas
Eastside SD El Cajon Locos
El Hoyo Palmas
EL Monte Flores
Elm St Watts
Eastside Montalvo
Exotic Foreign City Crips
Family Affiliated Irish Mafia Fain
Familia Hispana
Farmerside Bulldogs
Florencia 13
Four Corner Block Crips
Fresnecks Ftroop
Fuck My Enemies
Fuck the World
Gardenview Locos
Gas Team
Gateway Posse Crips
Ghetto Assassins
Ghostown
Goleta 13
H Street
Hard Side Clique
Hard Times
Hawaiian Gardens 13
Hells Angels MC
Highly Insane Criminals
Hispanic Kings
Homicidal Family
Hoodlum Family
Hop Sing Boyz
Humboldt
Humboldt County Gangsters
Imperials
Indian Pride
Inglewood Family Gangster
Inglewood Trece
Insane Crips
Insane Viet Thugz
Jackson Terrace
Jamaican Mafia Family
Juggalos
Kansas Street
Kings Of Cali MC
Krazy Ass Samoans
Krazy Assassins
Kumi
La Nuestra Familia
LB Suicidal Punks
Lennox
Lincoln Park Piru
Lincoln Town Sureños
Linda Vista 13
Lo Mob
Logan 30ta
Logan Heights
Logan Red Steps
Loma Bakers
Lomita Village 70’s
Long Beach Locos
Lorenzo Team
Los Marijuanas Smokers
Los Nietos 13
Los Padrinos
Low Profile Kings
Lo Boys
Lunatics On Crack
Lynwood Dukes
Mac Mafia
Manor Dro Boyz
Manor Park Gangsters
Marijuana Locos
Mayfair Santa Rosa Criminals
Mexican Klan Locos
Mexican Mafia
Mexican Pride 13
Midcity Stoners
Midtown Proyectos
Mission Bay Locos
Mitchel Street Norteños
Mob Squad
Mob To Kill
Molochs
Mongols MC
Mountain View Sureños
MS-13
National City Locos
Nazi Low Riders
Neighborhood Crips
Nip Killer Squad
Nipomo 13 Norte
North Town Stoners
Northern Riders
Northern Structure
Northside Hayward
Northside Indio
Northside Longos
Nuestra Raza
Nutty Side Paramount
Oaktown Crips
Oceano 13
O-hood Crips
Okie Bakers
Old Town National City
Olivo Bulldogs
Oriental Boy Soldiers
Oriental Boys
Oriental Killer Boys
Oriental Lazy Boys
Orphans
Otay
Palm City
Paradise Hills Locos
Paso Robles 13
Peckerwoods
Public Enemy Number One (PENI)
Pierpont Rats
Pierpont-Ventura
Playa Larga
Pomona 12th Street
Power of Vietnamese
Puente 13
Pure Mexican Raza
Puro Raza Loco
Puro Varrio Campo
Quiet Assassins
Quiet Village 13
Quince Southside Locos
Red Team
Res Boys
Ridezilla
Rockcreek
Rollin 20 Crips
S. Central Locos
Sacramaniacs
San Dimas Rifa
San Jose Crazy Crips
San Jose Grande
San St Paramount
Santa Monica Gang
Santa Nita
Saticoy- Ventura Eastside
Screamin Demons MC
Shandon Park Locos 13 Shelltown
Shelltown Gamma
Sherman Lomas Market Street
Sidro
Skinheads
Skyline Piru
So Gate Tokers
Sobrante Park
Solano Side
Sons of Samoa
Sotel 13
South Gate Smokers
South Vietnam
Southeast Locos
Southern Locos Gangsters 13
Southside Bakers
Southside Criminals
Southside Huntington Beach
Southside Indio
Southside Playboys
Southside Players
Southside Whittier 13
Spring Valley Locos
Squeeze Team
Sucidals Sunny Block Crips
Sunnyvale Sur Trece
Sur Santos Pride
Sur Town Locos
Sureño Unidos Trece
Sureños Por Vida
Tangas
Tehachapi 13
Tiny Rascal Gang
Tongan For Life
Top Hatters
Underworld Zilla
Untouchables
USO Squad
Ventura Avenue Gangsters
Vagos MC
Valinda Flats
Varrio Concord Norte
Varrio Northside
Varrio Nueva Estrada
Varrio Simi Valley
Varrio Bakers
Varrio Chula Vista
Varrio Coachella Rifa
Varrio Coachella Rifa 52
Varrio Coachella Rifa 53
Varrio Encanto Locos
Varrio Grinfas
Varrio Horseshoe
Varrio Locos
Varrio Meadow Fair
Varrio Mecca Rifa
Varrio Mountain View
Varrio Norwalk 13
Varrio Nuevo Coachella
Varrio Oasis Rifa
Varrio Palmas Gang
Varrio Penn West
Varrio South Garden
Varrio Sur Rifa
Varrio Tamilee Gangsters
Varrio Thermal Rifa
Varrio Xechos Locos
Vatos Locos
Venice 13
Venice Shoreline Crips
Viet Outlaws
Vietnam
Wah Ching
Walnut Creek 13
Warlord Bloods
West Coast Crips
West Covina 13
West Covina Crips
West Covina MOB
West Drive Locos
West Myrtle Townsend Street
Westside Hustlers
Westside Islanders
Westside Locos
Westside Longos
Westside MOB
Westside Stoners
Wheels of Soul MC
White Power
Whittier
Wicked Minded Sureños
Wicked Minded Sureños 13
Willow Street
Young Crazy Thugs
Young Cutties
Zetas
COLORADO
18th Street
211 Crew
81st Street Crips
American Nazi Party
Bandidos MC
Brown Pride Sureños
Carver Park Crips
Eastside Dukes
Folks
Gallant Knights
Gangster Disciples
GKI 211 Crew Bloods
Hells Angels
Insane Norteños
Juaritos
Kraziest Thugs Around
Los Primer Padres
Mexican Mafia
MS-13
Mongols MC
Murder All Cliques
Norteños
Northside Criminals
Northside Mafia
Oldies 13
Outlaws MC
Paisas
Parkside Varrio
Peckerwoods
Playboys
Sons of Silence MC
Southside Locos
Sureño Desert Empire
Sureños
Two Eleven
CONNECTICUT
Battalion 14
Blake Street Goonies
Bloods
Carmel Street Goons
Charter Oak Crips
Cruel 36 Family
Diablos MC
Eastern Circle Projects 3x
Fairside 2x
G-25
G-27
G-Side Projects
Hells Angels MC
Hill Most Wanted
Hillside 4x
La Familia
Latin Kings and Queens
Manor 5x
MS-13
Netas
Outlaws MC
Solidos
The Ave
Tiny Mami Squad
Tiny Papi Squad
Tre 3x
Tribe 3x
Trinitarios
Ville 2x
DISTRICT OF COLUMBIA
18th Street
Bloods
Crips
Latin Kings
MS-13
DELAWARE
135 Bloods
9 Trey
9 Triggaz
924 Bloods
Anybody Gets It
Bounty Hunter Bloods
Bush Babies
Cash Hoe Murda
Certified Ballina Killers
Crips
Dawg City Piru
East Coast Bloods
Gangster Disciples
Latin Kings
Netas
Ochos
Pagans
South Los
Sur-13
Street Piru Bloods
FLORIDA
1000 Block
103rd St Buck Wild CA Latin Lingo
10th St Gang
110th St Bloods
1200 Block
12th Court Cowboys
13th Avenue Hotboys
13th Street Gang
170 Boyz
181
187
1887
18th Street
20 Deep
21 Gunz
211 Crips
2150 EAP
22nd Street
23rd Street Trail Blazers
24th Street Gang
25 Mafia
27’s Puerto Rico PG
2nd Line Goons
300 Block
311 Westside KTP
312 Crips
7414 Gangster Disciples
34th Folk Boys
39th Street Boys
3KN
4 Way Boys
45th St FAM
46 Ave Boyz
5 Deuce Hoover Crips
5 Trey Bloods
5% 386
5020 Peckerwood
5150 Piru Bloods
52 Hoover Crips
551 Crips
58th Ave.
59 Hoover Crips
7 Trey Crips
700 Block
74 Gangster Disciples
7414 Gangster Disciples
8 Tre Crips
8 Trey Gangster Crips
800 Bound
813 Black Gangster Disciples
819 Boys
9 Trey Gangsters
9 Trey Murk Squad Blood
9-Tech Bloods
A&E Bird Gang
Ace Boon Goons
All City Certified Gangstas
Almighty Latin King and Queen Nation
American Nazi Party Anarchist
Anarchist
Any Body Killas
APK Boys
Aryan Brotherhood
Aryan Nation
Barrio Boys
Batchelors
Behind the Plaza Boys
Beruit Snakes
Big Money Posse
Bithlo Bike Crew
Black Angels
Black Flag Mafia
Black Gangster Disciple
Black Mafia
Black MOB
Black P Stone Nation
Black Pines
Black Pistons MC
Black Spade Squad
Black T Mafia
Blue Angel
Blue Devil Gangster Crips
Booker Heights Posse
Border Brothers
Brookhill Hillboys Most Wanted
Brown Pride
Bruise Brothers MC
Buck Block
Camphor Way Boys
Cartel Southside Gansta Crips
Carver Shore Boys
Cash Feenz
CFL Most Wanted
Chicago Bloods
Chico Cracker Klique
Chico’s In Action
Click Tight
Clown Boiz Crips
Cold Side Posse
College Park Thugs
Confederate Hammerskins
Corner Boy Mafia
Crazy Brown Boys
Crazy Gangster Disciple
Crazy Insane Disciples
Crazy Killer Zoes
Criminal Gangsters
Cut Throat Crew/Committee
D-BOYZ
Dirty White Boys
Down 4 Whatever
Dark Angels
Darkside Boyz
Deaths Last Clique
Deland Regulators
DeLeon Springs
Deuce Crips
Deuce Deuce
Dirty Game
Dirty South Mafia
Dirty White Boys
Disciples of Discipline
Doo Doo Creek
Doom Squad
Dover Locos
Down For Life
Down South Florida Boys
Down South Gangster
Downtown Crips
DRAK BOYS
Draks
Dred Mafia
East Orlando Warriors
Eastside 9 Trey Gangster Bloods
Eastside Bloods
Eastside Crips
Eastside Jack Boyz
Eastside Piru
Eastside Rolling 60’s Crips
Elm Street Piru Bloods
Eternal Gangster
Eureka Garden Goons
Every Niggas Nightmare
Family of Hustlers
Flag Street
Flip Star Crips
Florencia 13
Folk
Folk Disciples
Folk Nation
For The Warriors
Front Street Boyz
G Shine Bloods
G Stone Crip
G25
Gangster Killer Bloods
Gangsta Piru
Gangstas For Life
Gangster Disciples
Gangster Imperial Gangsters
Gangster Prophet
Gangsters 4 Life
Get Up Kids
Ghostrider Crips
Golden Gate Goons
Goyams
Grand Park Grape Street Crips
Guardians
Guk-Get Up Kids
Gun Clap N Crips
Hammerskins
Hill Top Boys
Hoover Crip
Hoover Deuce Crips
Hope Circle Bois
Hot Boys
Hustle Harder
Imperial Gangster Disciples
Imperial Gangsters
Imperial Kings Inland Empire
Insane Dragons
Insane Gangster Crips
Insane Gangster Disciple
Insane MOB Boys
Insane Spanish Lords
International Folk Posse
International Posse
International Posse 13th
Island Boys Clique
Jack Boys
Jensen Beach Clique
Juggalos
Knock Out Squad
King Con Sureños
Keep On Spraying
Ken Knight
Krazy Getdown Boys
Kruption Boys
Kuntry Boyz
La Raza
Lady Knock Out Squad
Lakawanna Boys Latin Crew
Latin Disciples
Latin Eagles
Latin Kings
Latin Life
Latin Lingo Legacy Mafia
Latin Syndicates
Legion of Doom
Little Altamonte Goons
Little Haiti Bloods
Livingston Dawgs
Lockhart Boyz
Loco Trece
Los 27
Los Chicanos
Los Salidos
Lost Boys
Lusoanderson Boys
M.A.C. Crip
Mafia Kings
Mafia Street Gangsta Crips
Main Street Posse
Maniac Campbell Disc Ñeta
Maniac Gangster Disciples
Maniac Latin Disciples
Mascotte City Gangster Folk Nation
Mayan Pride
Melbourne Town Soldiers
Mexican Diplomats
Mexican Mafia
Midway Goons
Milla Southside
Miller Gangsta Blood
Miller Set
MOB Folks
Mohawk Boys
Moncrief “MCT”
Money Mafia
Morgan Boys
Most Hated Brothers
Mother Fuckin Goons
Money Power Respect
MS-13
Murda Grove Boys
Murder Set Bloods
Murk
Myrtle Avenue
Nazi Juggalo
Ñeta
New Smyrna Beach Boyz
New York Outlaws
Nuestra Familia
Nine Trey Blood
Nine Trey Gangsters
Nines Techs & Grenades Norte 14
Northlake Boys
Not Fair Ones
Nuccio Boys
Oak Ridge Jungle Boys
Oaktown Niggaz
Oceanway Mafia
OLD Gang
One Love Nation
Orange City Boys
Orange County Gangs 1400 Block
Orange Flag Boys
Out East Outlaws
Out of Control Gangster
Outlaw Crips Outlawz
Outlaw Gangster Crips
Outlaws MC
O.V. BOYS
Oviedo Soldiers
P.O. Boys
Payback Crips
Pagans MC
Paisa Palm River Boys
Palm City Locals
Palmdale
Parramore Snakes
Paxon Boys
Pearl World
People Nation
Phantom MC
Picketville Hustle House
Pine Hills Pimp Boyz
Pine Manor Piru Bloods
Piru Bloods
Platoon 187
Playboy Crew
Polk Street Goons
Port Orange Boys
Power Progress
Project Boys
Projects of Vietnam
P-Town
PYC Raw Dawgz
Renegades MC
Ridge Manor Boys
Rollin 20s Crips
Rollin 30’s
Rolling 60 Crips
Rough Riders
Royal Family Ace Clique
Salerno Boyz
Satan Disciples
Satan Gangster Disciples
Satanist
Savage Squad
Sex Money Murder Bloods
Sherwood
Shores Boys
Sin City Boyz
Six Point Crips
Skinheads
Smooth Fellas
So Bout It Boiz
Solo G
Sons of Silence MC
Southern Pitbulls
Southside
Southside Bloods
Southside Crips
Spanish Lords
St. Lucie Bloods Chicos in Action
Stand and Deliver
Str8drop Gang
Straight Drop
Street Runners
Supreme White Power
Sur-13
Sureños
Swamp Boyz
Tangos
TC Boys
The Fresh Kings
Third World Family
Thunder Cats
Tri-State
Top Shottas
Tre 4
Troop 31 Slum Boys Aryan Nations
Tru Soldiers
Unforgiven
Unforgiven International Posse
United Crip Nation
United King
Unknown Soldiers
Up Top Mafia
Valentine Bloods
Vandalize The Hood
Vagos
Vato Locos
Vice Lord
Victory Boyz
Villa Boyz
Villa Killas
Village Boys
V-Side Gangsters
Warlocks MC
Washington Oaks Goons
Watauga Boys
Watts City Crips
Westside
Westside Chico Boys
Westside Crips
Westside Rolling 60’s Crips
Westside Rolling 90’s Crips
White Aryan Resistance
White Power
White Pride
Wildside Young Boon Goons
Winter Garden
Wolfpack MC
Woodlands Crew
Woods Boyz
Wynwood
Y-B Zoe Pound
Y-Lo-C
Young Godz
Young Guz
Young Latin Organization
Young Outlaw Gangster Crips
Zellwood Boys
Zoe Mafia
Zoe Mafia Family
Zoe Pound
Zone 1
Zulus MC
GEORGIA
30 Deep
4WB Fourth Ward Boys
All About Cash
All About Finesse
All About Money
Atlanta Blood Gang Squad
ATL Riders
Bang Bang Anywhere Gang
Bank First Play Later
Bethel Towers Crew
Black Pistons MC
BMB Blood Money Boys
Bloods
Campbelton Road Gangsters
Certified Street Niggas
Certified Paper Chasers
Check Gang
Crips
Cross the Track Boys
Da Fam
Dem Franchise Boys
Deadly Killer Click
DTS Dogwood Trap Starts
Fuck Being Broke
Gangsta Azz Nicca
Gangster Disciples
GD 74
Gett Money Play Later Click
Guapaholic Hard Times 13
Gwalla Boys
Hard Times
Hot Boy Click
Insane Gangster Disciples
Irwin Street Gorillas
James Gang MC
Merk Squad
Most Dangerous Click
Niggas Bout Action
Niggas for Life
No Mercy/ Trained to Go
Oakland City Posse
Outcast MC
Outlaws MC
Partners of the Struggle
Pittsburgh Jack Boys
RACK Crew
Raised on Cleveland
Rollin 20’s Bloods
Rollin 60’s Crips
Runts
Simpson Road Gangsters
Stealing Everything (SIMPSET)
Sureños
Sur-13
Southside 13
Sur King Locos
Ten Little Niggas
Trained to Go
Vagos
Vatos Locos
Vice Lords
White Boi Gang
Young Block Boys
Young Choppa Fam
Young Committed Partnas
Young Cushman Boys
Young Get Money Gangsters
Young Gunna Click
Young Money Makers
Young Niggas Get Money
Young Paper Chasers
Young Crew
YSet/ Y3/ Sak Takerz
HAWAII
Vagos MC
IDAHO
Bandidos MC
Brothers Speed MC
Mexican Mafia
Northside Big Tyme
Nuestra Familia
Russian Gangs
Vagos MC
Westside 18th Street
Westside Loma Locos
ILLINOIS
12th St Players
Almighty Popes
Ambrose
Black Disciples
Black Gangster Disciples
Black P Stones
Black Pistons MC
Folks Nation
Gangster Disciples
Hells Angels
Hobo’s Imperial Gangsters
Insane Dragons
Jivers Jousters
Krazy Get Down Boys
La Raza
Latin Counts
Latin Kings
Latin Saints
Latin Souls
Leafland Street Boys
Latins Out of Control
Maniac Latin Disciples
Mickey Cobra’s
Outlaws MC
Party People
People Nation
Popes
Satan Disciples
Satin Disciples
Simon City Rollers
Sons of Silence
Spanish Cobras
Sur-13
Two Six
Vice Lords
Wheels of Soul MC
INDIANA
13’s Sureños
14’s Norteños
18th Street
American Mexican Gangster
Aryan Brotherhood
Back Pistons MC
Black Angels
Black Gangster Disciples
Black P Stones
Bloods
BPS 13
Brown Pride Gang
Buffalo Soldiers
Click Clack
Cloven Hoofs MC
Code Red
Code Red
Rollin’s 20’s Crips
Cossacks
D-Boyz
Devil Disciples
Diablos MC
Dirty White Boys
Gangster Disciples
Goons Squad
Grim Reapers MC
Haughville Syndicate
Hells Angels MC
Insane Gangster Disciples
Jimtown Boys
Kentuckiana Gunslingers
Latin Kings
Latino Riders
Locos 18
Luchiana Boyz
Mad Dog MC
Mexican Mafia
Midnight Riders MC
Milwaukee Iron
Mistic Dragons
Money Over Bitches
Mongols MC
MS-13
Murda Squad
Naptown Riders
Norteño
Northside Vatos Locos
Outlaws MC
Peace Stones
Pop It Off Boys
Pussy and Cash
Ratchet Boyz
Rebel Cause
Righteous Riders
Savages and White Boys
Saxon Knights
Sons of Silence MC
Stone Drifters
Straight Edge
Sur-13
The Cool Kids
Vice Lords
Westside Crew
Wheels of Soul MC
Zoe Pound
IOWA
18th Street
319 Crew
7 Deuces
Ambrose
Aryan Brotherhood
Aryan Nation
Aztec Kings
Black Cross
Black Disciples
Black Gangster Disciples
Black Gangsters
Black Mafia
Black P Stones
Black Panthers
Black P-Stone Nation
Black Soul Block Burners
Blackstone Rangers
Bloods
Bogus Boys
Branded Breed MC
Carney Pride
Chosen Few MC
Church of the Creator
Church of the New Song
Code Red
Custom Riders MC
Crips
Dirty White Boys
Down South Boys
Eagle Riders
Eastside Locos
Eastsiders
El Foresteros MC
El Rukens
Familia Stones
Fathers of Anarchy
Florencia 13
Four Corner Hustlers
Gangster Disciples
Grim Reapers MC
Hang Out Boys
Hells Angels MC
Imperial Gangsters
Insane Deuces
Insane Gangsters
Insane Majestics
Insane Popes
Insane Spanish Cobras
Insane Vikings
Iron Horse MC
Juggalos
La Familia
La Raza
Lao Crip
Lao Family Blood
Latin Counts
Latin King
Latin Pachucos
Lomas13
Lomax XIII
Los Chicos
Los Pelones
Lower Riders
Maniac Latin Disciples
Maple Street Goons
MS-13
Matadors MC
Mexican Mafia
Mickey Cobras
Midnight Riders MC
Ñetas
New Breed
Norteños
Northfront Occult
Outlaws MC
P13 Punte
Paisa
Peckerwoods
Players Club Posse
Posse Comitatus
Really Cocky Asshole Killers
Rebel Knights MC
Saints
San Fernando Mexicans
Satan Disciples
Satin Disciples
SHARP
Sioux City Boys
Skinheads
Sons of Freedom MC
Sons of Liberty
Sons of Silence MC
Southside 21
Spanish Cobras
Spanish Disciples Sureño
The Cool Kids
The Fellows
Two Six Nation
United Metro Front
Vagos MC
Vice Lords
Viet Solo Boys
Westside Knights
Westside Locos
Westside Mafia
Westside Mobsters
Westside Villains
Westsiders
White Aryan Resistance
White Boys Only
White Pride X-Club
Young and Wasted
Young Bloods
KANSAS
13 Folks-GDS
357 Crips
4 Corner Hustlers
Bandidos
Bloods
Eastside Locos Sureños
Eastside Vato Locos
El Foresteros MC
Folks
Hoover Crips
Juggalos
Latin Kings
Lawrence Mob
Northsiders
School Yard Crips
Somos Pocos Para Locos
Sons of Silence MC
Sur-13
Traveling Vice Lords
Tru Valley Crips
Vice Lords
Westside Riders
KENTUCKY
Bloods
Crips
Gangster Disciples
Hells Angels MC
Iron Horsemen MC
Latin Kings
MS-13
Outlaws MC
Pagans
Sons of Silence MC
Vice Lords
Wheels of Soul
LOUISIANA
1100 Block Gang
31 Flava’s
3-Unit Black-Out Boys
5 Nine Bloods
5-Deuce Crips
5/2 Rock Boys
6th Street Boys
700 Block Gang
7th Ward Hard Heads
800 Block Gang
8th Ward Animals
900 Block Gang
Algiers 1.5
Baby Goonies
Bandidos MC
Bienville Boyz
Blackhawks
Byrd Gang
D-BlockHandy Family
Foucha Gang
Frenchman Money Boys
Gangster Disciples
Garden District Crips
Gray Ghosts
Harvey Hustlers
Jerome Group
Josephine Dog Pound
Lower Third Crips
Maffioso
MS-13
Northside Levin Crips
Northside Posse
Old Mill Quarters Crips
Orange Boy’s
Pack of Bastards MC
Prieur & Columbus Boyz
Skull Squad Mafia
Smoke One Click
Sonia Quarter Crips
Sons of Silence MC
Sureños
Tango Blast
Young Cut Boys
Young Gunners
Young Magnolia Melph
MAINE
All Jumpers
Aryan Nation
Crips
Disciples
Exiles
Folk Nation
Fuck Shit Up Gang
Hells Angels MC
Iron Horsemen MC
Latin Kings
L-Town
MS-13
Ñetas
Outlaws MC
P Town Soldiers
Peckerwoods
Saracens
Skinheads
True Somali Bloods
Vice Lords
MARYLAND
18th Street
25 Crew
51 Sandbox
Aryan Brother Hood
Black Guerilla Family
Blitzkrieg MC
Bloods
Crips
Dead Man Incorporated
Folk
Gangster Disciples
Get Money Goons
Go Go Crews
Hells Angels MC
Iron Horsemen MC
Latin Kings
Mara Locos
Mexican Locos
MS-13
Murder Incorporated
Murder Mafia Bloods
New Blood MC
Outlaws MC
Pagan MC
Phantoms MC
Pop Off Mafia
Savage Boys
Street Thug Criminals
Sur-13
Sureños
Thunderguards MC
Trinitarios
Vatos Locos
Warlocks MC
Wheels of Soul MC
Wild Boyz
MASSACHUSETTS
1850 Washington
18th Street
1937 Dorchester Avenue
20 Love
214 Harvard
700 Block
Academy
Academy Homes
Annunciation
Archdale
Aryan Nation Brotherhood
Asian Boyz
Bailey
Barrio Aztecas
Beechland
Bergin Circle Posse
Bicknell
Big Head Boys
Black Gangster Disciples
Black P Stone Nation
Bloods
Bonanno Crime Family
Boylston
Boylston Street
Boyos
Bristol Street Posse
Brunswick / Fayston
Cameron
Carew Block
Castle Square
Castlegate
Cathedral
Cedar Street
Charlame 1
Charlame 2
Cholos
Codman Square
Colombo Crime Family
Colorado / Favre
Columbia Point
Columbia Rd
Crown Path
Crystal Park Fellaz
Cape Verdean Outlaws
Dark Side Niggaz
Dangerous Little Bloods
DC Crew
Dominicans Don’t Play
Deuce Boys
Diablos
Dogg Town Crips
Draper
Dudley Street Posse
Eastern Ave Posse
Eastern Avenue Boys
El Combo que no de deja
Fairmount Family Plan Farve St.
Five Percenters
Forest Hills Pistons
Flatbush
Flatbush Posse
Folks
Forest Park Gangsters
Franklin Field
Franklin Hill
Franklin Street Posse
Gangster Disciples
Gangsters
G-Block
Genovese Crime Family
G-Mob
Greenfield
Greenwood
Greenwood Ave
Greenwood Street
Grey Rag
Grupo 25
Grupo 27
Gunn Square Posse
H-Block
Heath St
Hells Angels MC
Hendry
Highland
Hi-Point
Hit-Fam
Hizbollah
Holworthy
Homes Ave
Hooligans
Humboldt & Harrishof
Indian Orchard Posse
Insane Blood Gang
James Gang MC
Jr Kaos
Juggalos
Kilby Junior
Kilby Minor
Kilby Original
Kilby Young
Knox St Posse
La Familia
La Lowell
Latin Kings
Latin Queens
Lenox
Lenox St
Little Tiger
Long Riders MC
Los Solidos
Lowell St Posse
Lucerne St
Mafilia
Mafilia Mass Mobb
Main Street Goons
Maniac Latin Disciples
Mass Ave
Massassoit Street Posse
Mexikanemi
Mission Hill
Magnolia
Minoritys Up
Mongols MC
Morse / Norfolk
Morse St
Mozart
MS-13
Morton St Bricks
Mulato Mafia
Ñetas
New Born Tigers
Norfolk
Olney / Norton
Orchard Park
Orchard St Boyz
Orchard Street Bouriquas
Outlaws MC
Outlawz
Paisa
Phantom Lords MC
Road Demons MC
Rosewood / Thetford
Ruff Side
Russian Gangs
Russian Mob
Ruthless For Life MC
S.W.A.T.
Satans Disciples
Skinheads
Southern Ave
Southside
Southside Posse
Speedwell
Spencer
St James
St Joseph’s
Stockton
Sycamore St
Sycamore Street Posse
The Crazy Boys
Tiny Rascal Gangsters
Torrey Street
Vice Lords
Vietnam Vets MC
Villa Victoria
Vine & Forest / Mt Pleasant
Wainwright
Walk Hill
Walnut Pk
Warren Gardens
Wendover
Westville
Wheatland
Wilcock
Wolf Pac
Wood Ave
Woodledge
Woodward
Woolson
Worthington Street Posse
Young Chavos
MICHIGAN
300 Block
Aguitas 16
Avengers MC
Bemis Wealthy Street Boys
Black Gangster Disciple
Black Pistons MC
Brave Heart Ruff Riders
BUG Gang
Campau Cream Team
Cash Ave
Crips
Dallas Neland Alexander
D-Block
Devils Brigade
Devils Disciples MC
Dynasty Gorillas
East Ave
Eastern Worden
Eastside Boys
European Latin Kings
Folks
Forbidden Wheels MC
Gangster Disciples
Good Squad/Full Time Grinders
Grandville Gangsters
Highland’s Finest
Highwaymen
Holland Zeeland
Hustle Boys
Insane Unknowns
Ionia Boys
Jefferson Street Gangsters
Jokers MC
Juggalos
Kalamazoo Boys
Kartel of the Streets
La Kilcka
La Raza
Latin Counts
Latin Kings
Leak Boy Mafia
Madison Ave
Maniac Latin Disciples
Mason Street
Mexican Gangster Soldiers
Mexican Mafia
Mexican Mob
New Age Crip
Ñetas
Newman Lane Posse
Nishnob Mob
North North
New World Order
Oakdale Eastern
Outlaws MC
Pine Street
Polo Boyz
Prospect Paper Chasers
Purple Guns
Quimby Boys
Rebels MC
Rikochet Road Knights
Nation Royal Trinity Soldiers
Sheldon Logan
Spanish Cobras
Suicide Locos
Sur-13’s
Sureños
Taliban Team
Thug Life
Tres Manos Gangsters
Wanted Thug Brotherhood Nation
Vatos Locos
Vice Lords
Wood street
MINNESOTA
Almighty Vice Lords
Black P Stones
Black Panthers
Brown Pride for Life
Cash Money Boys
Gangster Disciples
Hells Angels MC
Latin Kings
Los Quientes Locas
Mexican Mafia
Native Mob
Native Vice Lords
Norteños 14
Prison Motorcycle Brotherhood
P-Stones
Rough Tough Somalis
Royal Cambodian Bloods
Shotgun Crips
Somali Gangs
Sons of Silence MC
Sureños 13
Texas Syndicate
Vatos Locos
Vice Lords
White Supremacists
MISSISSIPPI
211 Boys
Aryan Brotherhood
Asgards Pistoleros
Bandidos MC
Black Gangster Disciples Bloods
Crips
Gangster Disciples
Galloping Gooses
Handsboro Veterans
Hellified Drama Click
Latin Kings
Mexican Mafia
Simon City Royals
Sons of Silence
Vagos
Vice Lords
Viet Boys
MISSOURI
13 Lennox Wino
10 9 Folks
10 Street Crips
1019 Southside Folks
107 Hoover Crip
10-9 Gangster Disciples
11th Street
124th Athens Park Blood
12th St – Five Ace Deuce
12th Street
12th Street Blood
12th Street Crips
12th Street Disciples
12th Street Hoover Crips
135th Street Piru
13th Street Kcks
16th Street Crew
18th Street King Familia
18th Street Modesto Clique
2 Hard Posse
21st East Bottom Gangsters
21 Hilltop
21 Street Westside
21st Posse Crips
21st Street
21st Street Blood
22nd Street
22nd Street Crips
22nd Street Trey
23rd Street Blood
23rd Street Crips
23rd Street Hard Cores
23rd Street Hustlers
2400 Mob
24th St – Five Ace Deuce
24th Street
24th Street Bloods
24th Street Chelsea Bloods
24th Street Crips
25th Street
25th Street Bloods
25th Street Crips
25th Street Posse Gang
25th Street Quincy Bloods
26th Street Hoover Crips
27 St Belleview Gangsters
2700 Block
2700 Eastside
27th Street
27th Street Bloods
27th Street Crips
27th Street Mob
27th Street Pros
29th Street
29th Street Bloods
29th Street Crips
29th Street Hustlers
29th Street Pros
30’s
31st Boys
31st Street
31st Street Crips
31st Street Posse
32nd Street
33rd St K.C. Soldiers
33rd Street
33rd Street Bloods
33rd Street Crips
3400 Woodland
34th Street
35th Street
35th Street Bloods
35th Street Crips
36th Street
36th Street Bloods
36th Street Crips
36th Street Kings
37th Street
38th Street
38th Street Crips
3900 Block
39th Street Midwest Gangsters
39th Street
39th Street Tre-Block
39th Street Bloods
39th Street Crips
39th Street Dogs
39th Street Holy Temple Crips
39th Street Posse
3rd Tre Dog Hustler
3rd Wall Bloods
3rd Wall Crips
3rd World Syndicate
3rd World Players
4 Block 4 Trey
43 Hoover Crips
400 Block Player
40th & Wabash Crips
40th Street
40th Street Crips
41st Street Ghost
42nd Street Crips
4300 Block Insane Gangster
4300 Blood
4300 Brim Side Bloods
4300 Gangsters In Black
43rd 4 Trey Crips
43rd Insane Gangster Crips
43rd St Brooklyn Park Mafia
43rd St
43rd Street Thugs
43rd Street/The Dirty Eastside
44th Street
4500 Bloods
45th
45th Street
45th Street Crips
49th Street
49th Street Bloods
49th Street Dawgs
49th Street Gangster Crips
4th Street Crips
4th Street Guinotte Manor Crip
5 Deuce Brims Bloods
5.2 Eu Crips
50’s
50th Crips
5100 Gangsters
51st Bloods
51st Street / 5-Block
51st Street Crips
51st Street Hustlers
5-2 Eastside
52 Pueblo Bloods
52nd Street Gangster Crips
53rd Avalon Gangster Crips
53rd Street
53rd Street Crips
54th Street Blood
54th Street Crips
55th Street Bloods
56th Street Bloods
56th Street Boys
56th Street Crips
56th Street Villains
57 Road Dog Villains
5700 Wc Block Mob
57th Street
57th Street / 5-Block
57th Street Bloods
57th Street Hustler
57th Street Road Dogs
57th Street Rogue Dogs
58th Street / 5-Block
58th Street Hill Dogs
59th Street
59th Street Bloods
59th Street Gangsters
59th Street Hoover Crips
5-Duece Crips
6 Deuce Brims Bloods
60th Blood Hound
60th Street
61st Street
62nd Street
6300 Street
63rd Street Crips
66th Street Blood
67th Street
67th Street Blood
67th Street Crips
68 Mob
6800 Swap Side
68th Street
68th Street Blood
68th Street Crips
68th Street Hustlers
69th Street Bloods
69th Street Crips
69th Street Dawgs
69th Street Niggas
6th Street Crips
7 Duce Crips
7 Miles Blood
7 Oaks Crips
72nd Street Hustlers
73rd Street Crips
74 Folk Crips
74th St Santana Block Crip
74th Street Hoover Crip
75th Street Crips
7th Street Folks
8 Balls
9 Deuce Crips
9-Deuce Bloods
9th Street Dawgs
9th Street Dogs
9th Street Hoover Crips
Ace Block
Aryan Nation
Ashland Park Crips
Asian Boyz
Asian Crips
Asian For Life
Asian Girlz
Athens Park Bloods
Bandits
Banger Squad
Barrio Pobre
Black Gangster Disciples
Black Guerilla Family
Black Mafia Gangster Blood
Blood Game
Blood Lennox
Blood Stone Villains
Bounce Out Boys
Bonner Springs
Blood Border Brothers
Borderland Gang
Bounty Hunter Bloods
Boys From Chihuahua
Broadway Gangsters
Broadway Park Blood
Brown Image Gangsters
Brown Pride Family
Brown Side Locos
Buk
Lao Killers
C-13 Cambridge Crips
Cash Money Boyz
Chain Gang Parolees
Chelsea Bronx
Chelsea Crips
Chestnut Mafia
Circle City Crips
Click Clack Gang
Compton Crips
Corrington Crew
Crazy Ass White Boys
Crimeboyz
Crip Loc Da Gutta Sqaud
Dark Side Posse
Dead Everlasting Gangster
Dead-end Gang
Denver Lane Bloods
Desert Flat Sex Terks
Deuce Blocc
Deuces
Dime Block
Dlb Capone
Double Deuces
Dragon Family
Du Roc Crips
Deuce 4 Gangsters
Deuce 9 Folks
Deuce Deuce Blood
Deuce Deuce Crips
Deuce Lime Brim Bloods
Deuced-Deuce Posse
East Coast Crips
Eastside 15
Eastside Blood
Eastside Click
Eastside Crips
Eastside Folks
Eastside Gangster
Eastside Hathorn Piru Gangster
Eastside Hilltop
Eastside Insane
Eastside Latin Counts
Eastside Locos
Eastside Mexican Locos
Eastside Oceanside Crips
Eastside Posse
Eastside Rollin 20’s Crips
Eastside Wet Back Power
Eight Ball Crips
El Foresteros MC
Englewood Family Bloods
Five Ace Deuce
Florencia 13
Fambino’s
Familia Chueca
Family Locos
Five Trey Crips
Fog 5100 Original Gangsters
Folks
Freaks
Fremont Hustlers
Frostwood Mob
Galloping Goose MC
Gangster Crips
Gangster Disciples
Gangsters Gear
Gangster Crips
Gracemore Boys
Grape Street Watts Crips
Greenfield Village Posse
Guardian Angels
Guardian Disciples
Hardkore Gangsters
Hells Lovers MC
Hillside Crips
Hillside Hustler
Hillside Mafia
Hilltop
Hilltop Blood
Hoodbound 6700
Hoodsquad
Hoover Crip Gang
107 Hoover Gangster Crips
I’ll Rock You Crew
Imperial Gangster Crips
Imperial Valley
Imperial Village
Indian Posse
Indoes Willis Avenue
Inland Empire
Insane Disciples
Insane Family Gangster Blood
Insane Gangster Crips
Insane Gangster Folks
Insane Vato Gangsters
Insane Village Crips
International Gangster Family
Invaders
Jamaican
Jeffrey Manor Gangster Crip
Joplin Honky
Juniper Garden Crips
Knockafella Flame Gang
Kalizion Kansas City Villains
Kingsman Crips
Knocc Out Boyz
Krazy Boyz
La Soul Mafia
La Familia
Langdon Laos Bloods
Laos Boys
Latin Counts
Latin Kings
Latin People
Little Tiny Bitches
Lokitos Gang
Lonely Vets
Lords Of Chaos
Los Madanado
Lynch Mob
Lynwood Mob Bloods
Macken Gangster Crips Malditos
Mexican Disciples
Mexican Boyz
Mexican Kings
Mexican Loco’s
Mexican Mafia
Midwest Drifters MC
Money Over Bitches
Money Over Broke Bitches
Moorish Science Temple
MS-13
Mulvthina Loca
Natoma Boyz
Ne Side Blood
700 Block Neighborhood Crips
Neo Nazi
Nes Niggers On Woodland
Nine Nine Mafia Crip
Norteños
North KC Hustlers Crips
North Oak Posse
North Pole Crips
Northeast Side Bloods
Northeast Side Gangsters
Northside Gorilla
Northside Posse
Northwest Evans Park
Norton Block Gangsters Notorious
Nutty Block Crip
O.G.Crips
Original Agnes Gangster
Outlaw Mafia
Pachucos
Parkwood Bloods
Parvin Crew
People 5
People Nation
Pura Familia Loka
Piru Bloods
Playboy Gangsters
Players Club
Pleasure Time
Playboy
Pueblo Bishop
Puma Boys Crips
Quincy Bloods
Quintos In Mexico
Rebels 13
Raymond Street Hustlers
Rearview Players Crips
Red Mob Gangsters
Riverside Posse Crips
Rogue Dog Villains
Rollin 20’s Crips
Rollin 30’s Crips
Rollin 40’s Crips
Rollin 60’s Blood
Rollin 60’s Crips
Rollin 80’s Bloods
Ready To Kill
Ruskin Way Boys
Saddle Tramps
Saint Disciples
Saint Margaret
Samoan Satans
Spanish Disciples
Scarface School Yard Crips
Six Eight Gang
Southeast Pachucos
Seven Deuce Lime Street Bloods
Shotgun Crips
Six Deep Crips
Six Duce Crips
Six Deuce Brim
Six Tra
Six-Deuce Bloods
Sk7 Skaters
Skinheads
Somali Gangs
Sons Of Samoa
Southside 13
Southside 60’s
Southside Crips
Southside Family Bloods
Southside Posse
Southside Villains
Spanish Disciple
Spanish Gangsters
Sur Por Vida
Sur-13
Sureños
Swampside Taggers
Tas-Dog Crips
Taliban Gang
Terrace Lake Crips
Tra Dog Crips
Tra Side Gangster
Tra-9
Tra-Side
Traside Mobb
Tre Wall Tre-Tre
Tre Block 33
Tre-9
Tre-Deuce Gangster Crips
Tree Top Piru
Tre Side Gangsters
Tra-Side Gorillas
Twampside/1/4 Block
Underground Crips
Uptown Players
Vagos Trece
Vagos MC
Vatos Loco
V-Boys
Varrio Delinquentes
Viet For Life
Vice Lords
Vietnamese Crips
Village Boyz Bloods
Waldo Crip
Westbluff Blood
Western Bloods
Westside 111 Crips
Westside 18 Malandros
Westside 23 Holly Block Gang
Westside 41st Crip
Westside Bloods
Westside Chronicles Blood
Westside El Centro
Westside Hoover Crips
Westside Latin Counts
Westside Locos
Westside Pride Family Loco
Westside Player
Westside Rollin 40’s
Westside Rolling 60’s
Westside Traviesos
Wheels Of Soul MC
Wiggers
Woodland Crips
Young Oriental Gangsters
MONTANA
406 Dedicated Family
Aryan Circle of Texas
Bandidos MC
Bandits
Bloods
Cossacs
Crips
Dirty White Boys
Galloping Goose MC
Gangster City Family
Gangster Disciples
Hombres
Insane Vice Lords
Juggalo
Latin Kings
Modern
Modern Outlaws
Mongols MC
National Socialist Skinheads
Norteños
Outlaws MC
Peckerwoods
Pride Member Bandidos
Soldier of Seven
Suicide Mafia
Supreme White Power
Sureños
Texas Dirty White Boys
White Supremacist
NEBRASKA
18th Street
AM Vets
Bandidos MC
Crips
Eastside Loco 13
Eastside Locos
Gangster Disciples
Goon Squad
Hells Angels
Latin Kings
Lomas
MS-13
MSR137
Must Be Criminal
Norteños
Rebels 13
South Family Bloods
Southside 13
Southside Winos
Sureños
Under Age Kriminal
NEVADA
28th Street
Bandidos
Barrio Naked City
Lil Lokes
Mongols
Nevada Trece
Norteños
San Chucos
Sureños
Skinheads
Vagos
NEW HAMPSHIRE
Bay State Skinheads
Bloods
Brothers of the White Warriors
Chinese Mafia
Combatants
Crips
Diamond Kings
Dominions
Folk
Gangster Disciples
Hells Angels MC
Iron Eagles MC
Juggalos
Kaotic Kings of Destruction
Latin Gangster Disciples
Latin Kings
Milford & Company
Mountain Men MC
MS-13
Outlaws MC
Pagans MC
Red Villain Gangstas
Rough Riders
Sureños
Trinitarios
NEW JERSEY
135 Piru
464Piru
793 Bloods
Brick City Brims
Haitian Outlaws
Hoover Crips
Grape Street Crips
G-Shine Bloods
Hells Angels MC
Latin Kings
MS-13
Ñetas
Pagans
Trinitarios
Sex Money Murder
NEW MEXICO
Bandidos
Eastside
Juggalos
Los Padillas Gang
MS-13
San Jose Gang
Southside Loco
Sureños
Thugs Causing Kaos
Vagos
Westside
Westside Locos
NEW YORK
18th Street
Aryan Brotherhood
Bishops
Black Gangster Disciple
Black Panther
Bloods
Crips
El Grupo 27
Haitian Mafia
Hells Angels MC
Juggalos
Latin Kings
Mexikanemi
MS-13
Ñetas
Outlaws
Pagans MC
Paisa
Peoples Nation
Raza Unida
Skinheads
Sureños
Texas Syndicate
Thug Out Players
Trinitarios
Vagos
Vatos Locos
Warlocks MC
Wheels of Soul MC
NORTH CAROLINA
13 Meadow Wood Memphis Bloods
18th Street
174 Valentine Bloods
20’s Neighborhood Piru
21st Crips
318 Crips
4-Trey Gangster Crips
5 Deuce Hoover Crips
5 Line Eastside Bounty Hunters
8 Trey Crips
9 Tek
9 Trey
9 Trey Gangsters
910 MOB
A Squad
Aryan Brotherhood
Aryan Nation
Ashboro St Bloods
Ashton Forrest Bloods
Asian Boyz
Avalon Gangster Crips
B St Bloods
Beaver Creek South
BL-50 Bloods
Black Gangster Disciples
Black Guerilla Family
Black P Stones
Bonnie Doone Folk
Bounty Hunter Assassins
Bounty Hunter Bloods
Bounty Hunter Villains
Brown Pride
Brown Pride Aztecs
Bunce Road Bloods
Cambridge Arms Bloods
Conservative Vice Lords
D-Block Bloods
DC Bounty Hunters
Dead Man Incorporated
Desperados MC
Deuce 13
Eastside MOB Piru
Eastside Murder Boyz
Eight Trey Crips
Fairlane Acres Crips
Five Percenters
Flame Squad
Folk Nation
Foxfire Bloods
Fruit Town Brims
Gangster Disciples
Get Money Clique
Ghost Gangster Disciples
Gangster Killer Bloods
Grape Street Crips
Graveyard Crips
Hells Angels MC
Hoover 107 Crips
HTO Bloods
IGC 973
Insane Gangster Crips
Insane Gangster Disciples
Jbirds
Juggalos
Kings/Dons
Latin Kings
Loch Boys
Major Grind
Mafia Malditos
Mexican Mafia
Misplaced Souls MC
Money Over Bitches Bloods
Money Money
Hungry Soldiers
Money Maker Squad
MS-13
Murch Mob
Murder Bloods
Nazi Low Riders
Ñetas
New Jersey Mafia
Norte-14
Norteños
NWA Bloods
Outlaws MC
People Nation
P-NOX
Queensmore Bloods
Real Street Niggas
Red Devils MC
Rollin 20’s Crips
Rollin 30’s Crips
Rollin 40’s Crips
Rollin 60’s Crips
Savoy Heights Posse
Seabrook Bloods
Sex Shaw Road Crips
South Central 81st Crips
Sur-13
Tiny Rascals Gang
Trap Squad
United Blood Nation
Valentine’s Day
Vatos Locos
Westside MOB Piru
Westside Piru
NORTH DAKOTA
Folk Nation
Gangster Disciples
Native Mob Crips & Bloods
Sons of Silence
OHIO
1300 Area Rap Gang
187 Boys
33rd Street
4-Block
52/52 Niggas
600 Block/Hill Top Gangsters
614 Boy Foundation
22nd Piru Bloods
9 Kings
A.C. 357
Akron Larceny Boys
Ak-Town / 330/ 440 / 216
All About Money
Aryan Brotherhood
Aryan Nation
Asian Crips
Avengers MC
Ayers Street Playas
Baller Boy Mafia
Banished Brothers MC
Black Pistons MC
Bloodline
Bottom Hawks
Brick Boys
Brothers MC
Brother’s of the Hammer MC
Buckeye Folks
Chest Block Gangsters
Chestola
Da Kennel
Dayton View Hustlers
D-Block/21st Street Killers
Dem Block Boys
Derelects MC
Diamond Cut
Diamond Dogs MC
Dirt and Grime MC
Dirty South
Down the Way
Down Town Area Rap Gang
Eastside Bloods
Eastside Connection
Folks Gangster Afficial
Gangster Disciple Folks
Gangster Disciples
Gangster Killer Bloods
Get Money Boys
Get Money Goonies
Goonies
Greenwich Village Crew
G-Unit Crips
Hammerskins
Head Bustin Niggas
Heartless Felonies
Heightz Boyz
Hells Angels MC
Hilltop 7714 Crips
Hough Heights Boys/Hough
Harlem Boys
Hunnid Block Gang
Iceberg Bloods
Johnston Block
Kaika Klan Outlaws
King Cobra Boys
Kinsman County/Rollin 40 Crips
K-Town Gangsters
Laffer Block
Laird Block Gangsters
Lake Boys
Lakeshore Boys
Laotian Crips
Latin Kings
Lovers Lane Crips
Laclede Parkview Ave
Madison Madhouse
Middle Avenue Zone
Money Go Gettas
Money Over Bitches
MS-13
New Northside Gangsters
Niggas From Laffer
North Coast MC
North Coast XII MC
Northside Gangstas
Original Killers
Otterbien Blood Mafia
Outlaws MC
Quinn Street Crew
Pagans MC
Rated R
Renegades MC
Rollin 20 Crips
S1W Southwest
Satans MC
Sherwood Ave
Shorb Block
Shorb Block Hustlers
Sin City Disciples MC
Skinheads Against Racial Prejudice
Skinheads Skulls
Soup City Boys
South Block Gangsters
Southwest Akron Thugs
Southwest Boyz
Southwest Gangsters
Southside Gangsters
StarBoyz
Stay Focus Rap Gang
Strays MC
Suffocated Records
Sureños 13
The Breed MC
The Brother’s MC
The Circle
The Notch Boys
The Team /The Squad
The Unit
Tribe
Up the Way
Valley Boys
Valley Niggas On Top
Valley-Lo
Vice Lords
Wages
Wheels of Soul MC
White Supremacists
Young Blooded Thugs
Young Kaika Boys
Young Kaika Girls
Young Kelly Boys
Young Street Goonies
Zone 3 Bloods
Zone 7
Zone 8
Zulus MC
OKLAHOMA
Asian Gang
Bandidos MC
Bloods
Border Brothers
Crips
Hoovers
Indian Brotherhood
Juggalos
Mongols MC
MS-13
Native American Gang
Nazi Low Riders
Norteño
Mexican Mafia
Outlaws MC
Sur Trece
Carnales
Sureños
Unidos en Uno
Universal Aryan Brotherhood
USO Family
OREGON
18th Street
Brother Speed
Brown Pride
Columbia Villa Crips
Gangster Disciples
Hmong Pride
Hoover Criminal
Kerby Blocc Crips
Lincoln Park Bloods
Masters of Destruction
MS-13
Mongols MC
Norteños
Rolling 60’s Crips
Southside Trece
Unthank Park Hustler
Vagos MC
West Coast Mafia Crip
Westside Mob Crips
Woodlawn Park Bloods
PENNSYLVANIA
18th Street
AC Skins
Aryan Brotherhood
Aryan Circle
Aryan Resistance Militia
Asian Boyz
Barbarians MC
Barrios Aztecas
Black Gangster Disciples
Black Guerilla Family
Black Jack MC
Bloods
Border Brothers
Breed Brick Yard Mafia
DC Crews
Dirty White Boys
G-27
Gangster Disciples
Green Dragons
Hells Angels
HPL Il Morte
Insane Gangster Disciple
Insane Unknowns
Juggalos
Kensington 215
Keystone United
Latin Kings
Low Crips
Mavericks
Mexican Mafia
Mexikanemi
MS-13
Nazi Low Riders
Neo Nazi
Ñetas
New Mexico Syndicate
Norteños
Nuestra Familia
Outlaws MC
Pagans MC
Paisa
Raza Unida
Sin City Disciples MC
Skinheads
Soldiers of Aryan Culture
Street Familia
StrongArm Production
Mexican Mafia
Sureño 13
Sureños
Tangos
Tango Blast
Texas Chicano Brotherhood
Texas Family
Texas Syndicate
Tribe MC
Trinitarios
Vagos
Vice Lords
Wardogs MC
Warlocks MC
Warrior Society
Wheels of Soul MC
PUERTO RICO
Borinquen Street Gang
Brisas De Salinas
Grupo 25
Grupo 27
La Marina
La Montaña Public Housing
Latin Kings
Los Ñetas
Los 31
Los 25
Nuevo Grupo 25
ONU Rompe
San Andres Public Housing
RHODE ISLAND
18 Street
Black Gangster Disciples
Clown Town Crip
Darkside Rascals
Hanover Boyz
Hells Angels MC
Latin Kings
Laos Pride
MS-13
Ñetas
Oriental Rascals
Original Bloods
Original Crip Gang
Providence Street Boyz
South Street Boys
Sur-13
Vagos MC
Young Bloods
SOUTH CAROLINA
031 Piru
1212
10 Mile Boys
18th Street
3rd Pound
3VL
4-4
4 Mile Boys
41 Boys
48 Boys
4G
5 Percenters
58Tres
6 Mile Boys
8 Trey Crips
9 Tre Boys
9th Ward
Adams Run Bottom Boyz
Band of Brothers MC
Bedroc
Black Gangster Disciples
Black Mafia Black “P” Stone
Bloods-031
Bloods MC
Boogie Woogie
Bounty Hunters
Church Hill Boyz
Converse Street Gang
County Boys
Creekside Crips
Cross Cut
Cross The Track
Dem Country Bois
Devils Rejects
Down the Island
Duncan Park Gang
East West Forest/Forest Boys
Eastside
Eastside Crips
Eastside Folk
Farside/West Cash
Ferry Ferry
Folk Nation
G Shine
Gangster Killer Bloods
Gangster Disciples
Gatas Petersfield Jungle Boyz
Geddy’s Ville Boyz
Greenview Thugs
Hells Angels MC
Hilltop-Crips
Hoover Crips
Insane Gangster Disciples
Johns Island Bloods
Kampa Bois
Kampa Style Villa Posse
Kings Court
Laos Crips and Bloods
Latin Kings
Lemon Tree Bois
Misguided Brotherhood
MS-13
Natural Born Assassins
New Black Panthers
Neighborhood Bloods
Norte 14
Northside Bloods
Northside Gang
OB Orleans Garden Boys
Outlaws MC
Paisas
Park Hill Gang
Parkers Pine Hurst Posse
Pineland Slap Boyz
Red Devils MC
Rivaside Goons
Rollin 20’s
Rollin 90 Crips
Souf Santee
Sosik Clik
Southside
Southside 3rd Ward
Straight Shooters MC
Sur-13
Sureños
SWAMP
Texas Community Gangsta
The Doolie Hill Gang
The Sand Hill Gang
The Ville Thunderguards
Tibwin Bois
Trap Star Soldiers
Tree Top Piru
Town Gorillas
Trey 9 Bloods
Tville Bloods
UpTop Soldiers
Urban Warriors
Vatos Locos
Warhorse Brotherhood
Warlocks MC
Westside
Westside Bloods
Wild Bunch
SOUTH DAKOTA
Bandidos
Conservative Vice Lords
Darkside Family
East River Skins
East River Souls
Eastside Thugs
Gangster Disciples
Main Street Crips
Native Latin Kings
Nomadz
Northside Gangster Disciples
Red Iron Players
Sur-13
The Boyz
Thug Line
Tre Tre Gangster Crips
True Villain Bloodz
Vagos
Warlords
West Mafia Crip Family
Westside Piru Bloodz
TENNESSEE
103 Watts Varrio Grape Street Crips
107 Hoover Crips
Five Percenters
52 Hoover Crips
Aryan Brotherhood
Aryan Circle
Aryan Nation
Asian Pride
Athens Park Bloods
Boone Height Mafia Crips
Bounty Hunter Bloods
Brotherhood Forever
Brown Pride
Confederate Sons MC
Crazy White Boys
E87 Kitchen Crips
Gangster Disciples
Ghost Vice Lords
Imperial Insane Vice Lords
Juggalos
Kempo Drive Posse
Kurdish Pride
Latin Kings
Memphis Mob
Mexican Mafia
MS-13
Outlaws MC
Prison Motorcycle Brotherhood
Renegades MC
Rollin 60’s Crips
Skyline Piru
Sureños
Sureños 13
Tiny Rascal Gangsters
Traveling Vice Lords
TreeTop Piru
Unknown Vice Lords
Vice Lords
White Aryan Resistance
Woodlawn Crips
TEXAS
Aryan Brotherhood
Aryan Brotherhood of Texas
Aryan Circle
Asian Pride
Bandidos MC
Barrio Azteca
Barrio Azteca Sureños
Black Gangster Disciples
Bloods
Brown Pride
Cliques
Combes Crazy Clique
Crips
Cuchillos
Drop City Thugz
Eastside Homeboys
Eastside Locos
Eastside Pharr
Fair Park
Ghetto Starz
Hermanos Pistoleros Latinos
Highland Hills Posse
Ironriders MC
Kings Loco 8 Bandidos
Krazy Jokers
Las Palmas Indios
Latin Kings
Loco 13
Los Compadres MC
Los Homeboys
Mexican Mafia
Mexikanemi
MS-13
NOR 14
Norteños
North Dallas Vagos
Northside Locos
Notorious Thugs
Orejons Partido Revolucionario Mexicanos
Pharrolitos
Pleasant Grove Vatos
Po’Boys
PRM Valluco
Puro Tango Blast
Raza Unida
Southside Bandidos
Southside Donna
Southside EVW
Southside Folk
Sur-13
Sureño 13
Tango Blast
Texas Chicano Brotherhood
Texas Mafia
Texas Mexican Mafia
Texas Syndicate
Tongo Westside
Tri-City-Bombers
Vagos MC
Vallucos
Varrio Northside
Varrio Northside Vato Locos
West Texas Tangos
Westside Aquas Harlingen
Westside Bowie Town A’s
Westside Filmore A’s
Westside Los Vecinos
White Knights
UTAH
Asian Boyz
Baby Regulators
Bandidos MC
Barons
Black Mafia Gangsters
Brother Speed
Crown Latin Kings
Fourth Reich
Iraqi Taliban
Kerberos
King Mafia Disciples
Mongols MC
MS-13
Murder One Family
Norteños
Oriental Boy Soldiers
Oriental Laotian Gangsters
Samoans in Action
Silent Aryan Warriors
Soldiers of the Aryan Culture
Sons of Samoa
Sons of Silence MC
Sundowners
Tiny Oriental Posse
Tongan Crip Gangsters
Vagos MC
Sudanese Gangs
Sureños
Varrio Loco Town
Vice Lords
VERMONT
No reporting
VIRGINIA
18th Street Gang
36th Street Bang Squad
43/Hollywood Church Boyz
43 MOB
44 MOB
52 Hoover Crips
9 Trey Bloods
9 Trey Gangsters
Aryan Brotherhood
Asian Dragon Family
Bang Squad
Black Gangster Disciples
Black P Stone Nation
Black Pistons MC
Blackout Bloods
Bloods
Bounty Hunter Bloods
Brown Pride
Camp Grove Killas
Ching-A-Lings MC
Cross Roads Crew
Culmore City
Cypress Manor Posse Crips
Cypress Manor Posse Bloods
Devils Grip
Dragon Family
Dump Squad
Fifth Ward
Five Percenters
Florencia 13
Folk Nation
Freeney Boyz
Gangster Killer Bloods
Gangster Disciples
Ghost Riders MC
Hells Angels MC
Hill Street
Hoffler Boyz
Holiday Death Chamber
Holiday Death Crew
Hot Boyz
Illusions MC
Insane Gangster Disciples
Iron Coffins MC
Kings of Richmond County
La Primera
La Privada Riderz
Lake Kennedy Posse Bloods
Latin Homies
Latin Kings
La Clique Original
MS-13
Marauders MC
Merciless Souls
Mexican Mafia
Mexican Pride
Mongols MC
MS-13
Murk Squad
Nine Trey Gangsta
Nomads MC
Norteños 14
OO6 Blitz
Outlaws MC
Pagans MC
People Nation
Piru Pound Property
Renegades MC
Road Dragons
Rolling 90’s
San Diego Eastside Piru
Scorpions MC
Shoot-em Up Boys
South Suffolk Gangsters Crips
Southside/202 SQUAD
Southside Locos
Sureños
Stack Squad
Sur-13
The Good Ones
Titans MC
Tradesmen MC
Tiny Rascal Gangsters
Tribe MC
Tucker Hill
Unknown Fools
Valentines Bloods
Vice Lords
Virginia Raiders MC
Warlocks MC
Warlords
Zetas
WASHINGTON
18th Street
74 Hoover Criminals
74 Hoover Crips
Aryan Brotherhood
Aryan Family
Bandidos MC
Black Gangster Disciples
Big Dog Norteños
Black Guerilla Family
Chinese Triads
Deuce 8 Black Gangster Disciples
Deuce 8 Gangster Disciples
Deuce-0’s
Deuce-9’s
Down With the Crew Gangster
Disciples
Drama Boyz
East African Gangs
European Kindred
Florencia 13
Green Rags
Hakenkreuz
Hells Angels MC
Hilltop
Holly Park Crips
Hoover Crips
Juggalos
Kitchen Crips
La Fuma Bloods
Lakewood Hustler Crips
Latin Kings
Lil Valley Lokos 13
Lil Valley Lokotes 13
Low Profile Gangsters
Little Valley Locotos
Magic Wheels
MS-13
Mexican Mafia
Mongols
Native Son Bloods
Nine Street Crips
Norteños
Northwest Boot Boys
Oriental Boyz
Oriental Fantasy Boys
Outlaws MC
Paisas
Peckerwoods
Playboy Gangster
Playboys 13
Rancho San Pedro 3rd Street Skinheads
Somali Gangs
Sons of Samoa
South Asian Gangs
South Asian Gangsters
Southside Tokers
Street Mobb
Sur-13
Sureños
Tiny Rascal Gangsters
Union Street Black Gangster Disciples
Varrio Campo Vida
Varrio Locos 13
Vatos Locos
Yesler Terrace Bloods
Young Oriental Troop
Young Seattle Boys
WEST VIRGINIA
Black Guerilla Family
Junk Yard Dogs
Latin Kings
Pagans MC
Warlocks MC
WISCONSIN
10th St Gangster Disciples
12th St Gangster Disciples
16 Gun Clique
2-1’s
25 Vice Lords
26 Vice Lords
29 Hard Heads
6th St Gangster Disciples
Big O Ones
Black Cobras MC
Black Gangster Disciples
Black Mob
Black P Stones
Black Pistons MC
Block 25th
Brothers Of The Struggle
Brown Pride 13
Burleigh Zoo
Chicago Gangster Disciples
Chicago Vice Lords
City Of Clybourne
Clanton 13
Conservative Vice Lords
Dirty South Gangster Disciples
Dukes 13
Eastside Gangsters
Eastside Mafiosos
Everybody Knows
El Rukins
Four Corner Hustler
Gangster Disciples
Gangster Pimpin
Getto Boys
Hot Boys
Imperial Gangsters
Imperial Gangster Disciples
Insane Unknowns
Insane VL
La Familia
Latin Bloods
Latin Kings
Los Primos
Los Veteranos 13
Maniac Latin Disciples
Maple Street
Mexican Posse 13
Mexican Sureños Locos Ochos
Midtown Gangster Disciples
Murda Mobb
Nash Street Boys
Native Mob
Northside Gangster Disciples
Orchestra Alanis
Outlaws MC
Players
Sons Of Loyalty
Sovereign Nation Warriors
Spanish Cobras
Spanish Gangster Disciples
Sureños 13
The 4’s
The Loonies
Tiny Locos 13
Traveling Vice Lords
Tre Eights
Vice Lords
Wild 100’s
WYOMING
307 Southside
Bandidos
Bloods
Brown Pride
Gangster Disciples
Juggalos
Kriniminals Sureños
Lincoln Park
Southside Locos
Sur-13
Wreck Team
APPENDIX B. MDTOs Alliances and Rivals
| Cartel |
Aligned With |
Rivals |
| The Sinaloa Cartel (aka Guzman-Loera Organization or Pacific Cartel) |
Hermanos de Pistoleros Latinos |
New Mexico Syndicate
Los Carnales
Latin Kings
Mexican Mafia (California)
Sureños
MS-13
Arizona Mexican Mafia (Old & New)
Wet Back Power
Sinaloa Cowboys
West Texas Tangos
Los Negros
Valencia Cartel (Considered a branch of the Sinaloa Cartel)
Sonora Cartel (Considered a branch of the Sinaloa Cartel)
Colima Cartel (Considered a branch of the Sinaloa Cartel)
Border Brothers (California)
Border Brothers (Arizona)Los Zetas
Cardenas-Guillen Cartel (Gulf)
Tijuana Cartel
Beltran-Leyva Cartel
Juarez CartelLa Familia Michoacana Cartel (Formerly part of Los Zetas under the authority of the Gulf Cartel)Sinaloa Cartel
Cardenas-Guillen Cartel (Gulf)
Surenos
MS-13
West Texas TangosLos Zetas
Cardenas-Guillen Cartel (Gulf Cartel)
The Beltran-Leyva Cartel
Vincente Carrillo-Fuentes Cartel
(Juarez Cartel)Los ZetasVincente Carrillo-Fuentes Cartel (Juarez)
Beltran-Leyva Cartel
Barrio Azteca
Hermanos de Pistoleros Latinos
Mexikanemi
Texas Syndicate
MS-13Arellano-Felix Cartel (Tijuana)
Cartel de la Sierra (Sierra Cartel)
Sinaloa Cartel
La Familia Michoacana Cartel
Cardenas-Guillen Cartel (Gulf)Cardenas-Guillen Cartel (Gulf Cartel)
Sinaloa Cartel
La Familia Michoacana Cartel
Hermanos de Pistoleros Latinos
Partido Revolutionary Mexicano
Raza Unida
Texas Chicano BrotherhoodLos Zetas
La Familia Michoacana Cartel
The Sinaloa CartelVincente Carrillo-Fuentes Cartel (Juarez Cartel)
Los Zetas
Hermanos de Pistoleros Latinos
Barrio Azteca
New Mexico Syndicate
Los CarnalesThe Sinaloa Cartel
La Familia Michoacana CartelThe Beltran-Leyva Cartel (expected to soon be taken over by the Sierra Cartel)Los ZetasLos Zetas
La Familia Michoacana CartelArellano-Felix Cartel (Tijuana Cartel)Mexican Mafia (California)
Sureños
Arizona Mexican Mafia (Old & New)
Border Brothers (California)Los Zetas
The Sinaloa Cartel
APPENDIX C. Federal Gang Task Forces
FBI Safe Streets Gang Task Forces
Alabama
Mobile Violent Crime Joint Task Force
Northeast Alabama Safe Streets Task Force
Alaska
Anchorage Safe Street Task Force
Arizona
Northern Arizona Violent Gang Task Force
Southwest Arizona Safe Streets Task Force
Violent Street Gang Task Force
Arkansas
Metro Gang-Joint Task Force
California
Central Coast Safe Streets Violent Gang Task Force
Central Valley Gang Impact Team Task Force
East County Regional Gang Task Force
Gang Impact Team (Riverside)
Imperial Valley Safe Streets Task Force
Kern County Violent Crime/Gang Task Force
Los Angeles Metro Task Force On Violent Gangs
North Bay Regional Gang Task Force
North Central Coast Gang Task Force
North County Regional Gang Task Force
Sacramento Valley Gang Suppression Team
Safe Streets East Bay Task Force
San Francisco Safe Streets Violent Crimes Task Force
San Gabriel Valley Safe Streets Violent Gang Task Force
Santa Ana Gang Task Force
Santa Clara County Violent Gang Task Force
Solano County Violent Gang Safe Streets Task Force
South LA County Violent Crimes Task Force
Stockton Violent Crime Task Force
Ventura County RIACT
Violent Crime Task Force-Gang Group
Colorado
Denver Metro Gang Safe Streets Task Force
Southern Colorado Violent Gang Safe Streets Task Force
Connecticut
Bridgeport Safe Streets Gang Violent Crimes Task Force
New Haven Safe Streets Task Force
Northern Connecticut Violent Crimes Gang Task Force
Delaware
Delaware Violent Crime Safe Streets Gang Task Force
Florida
Daytona Beach Safe Streets Task Force
Jacksonville Criminal Enterprise Investigative Task Force
Metro Orlando Safe Streets Gang Task Force
Palm Beach County Gang and Criminal Organization
Task Force
South FL. Gang/Criminal Organization Task Force
Tampa Bay Safe Streets Task Force
Georgia
Atlanta Criminal Enterprise Task Force
Central Savannah River Area Safe Streets Gang Task Force
Conasauga Major Offenders Task Force
Hall County Major Offenders Task Force
Northwest Georgia Criminal Enterprise Task Force
Southwest Georgia Gang Task Force
Idaho
Treasure Valley Metro Gang Task Force
Illinois
Eastern Illinois Safe Streets Task Force
Joint Task Force on Gangs – Tactical
Joint Task Force on Gangs – West
Joint Task Force on Gangs II
Joint Task Force on Gangs-1
Metro East Safe Streets
North Suburban Gang Task Force
Peoria Area Safe Streets Task Force
Quad Cities Fed Gang Task Force
Will County Violent Crimes Task Force
Indiana
Eastern Central Indiana Safe Streets Task Force
Fort Wayne Safe Streets Gang Task Force
Gary Response Investigative Team
Gang Response Investigative Team Tippecanoe
Indianapolis Metro Gang Safe Streets Task Force
Wabash Valley Safe Streets Task Force
Iowa
Cedar Rapids Safe Streets Task Force
Kentucky
Northern Kentucky Safe Streets Task Force
Louisiana
Calcasieu Parish Gang Task Force
Capital Area Gang Task Force
Central Louisiana Gang Task Force
New Orleans Gang Task Force
Northeast Louisiana Gang Task Force
Shreveport Task Force
South Central Louisiana Safe Streets Task Force
Maine
Southern Maine Gang Task Force
Maryland
Prince George’s County Safe Streets Task Force
Violent Crime Safe Streets Initiative
Massachusetts
North Shore Gang Task Force
Southeastern Massachusetts Gang Task Force
Western Massachusetts Gang Task Force
Michigan
Benton Harbor Violent Crime Task Force
Detroit Violent Gang Task Force
Genesee County Safe Streets Task Force
Mid-Michigan Safe Streets Task Force
Oakland County Safe Streets Task Force
Minnesota
Twin Cities Safe Streets Violent Gang Task Force
Mississippi
Jackson Safe Streets Task Force
Southeast Mississippi Safe Streets Task Force
Missouri
Kansas City Metropolitan Gang Task Force
St. Louis Safe Streets Gang Task Force
Montana
Big Sky Safe Streets Task Force
Central Montana Gang Task Force
Nebraska
Central Nebraska Drug and Safe Streets Task Force
Greater Omaha Safe Streets Task Force
Nevada
Las Vegas Safe Streets Gang Task Force
New Hampshire
New Hampshire Safe Streets Task Force
New Jersey
Jersey Shore Gang and Criminal Organization Task Force
South Jersey Violent Incident/Gang Task Force
South Jersey Violent Offender and Gang Task Force
Violent Crime Criminal Enterprise Task Force
Violent Crimes Incident Task Force
New Mexico
Albuquerque Safe Streets HIDTA Gang Task Force
Four Corners Safe Streets Task Force
Southern New Mexico Street Gang Task Force
New York
Buffalo Safe Streets Task Force
Capital District Gang Task Force
Hudson Valley Safe Streets Violent Gang Task Force
Long Island Gang Task Force
Westchester County Violent Crimes Task Force
North Carolina
Charlotte Safe Streets Task Force
Piedmont Triad Safe Streets Gang Task Force
Raleigh Durham Safe Streets Task Force
Wilmington Safe Streets Task Force
Ohio
Greater Akron Area Safe Streets Task Force
Mahoning Valley Violent Crime Task Force
Miami Valley Safe Streets Task Force
Stark County, Ohio Violent Crime/Fugitive Task Force
Oklahoma
Oklahoma City Metropolitan Gang Task Force
Oregon
Portland Metro Gang Task Force
Pennsylvania
Bucks County Violent Gang Task Force
Capital Cities Safe Streets Task Force
Delaware Valley Violent Crimes Task Force
Erie Area Gang Law Enforcement Task Force
Greater Pittsburgh Safe Streets Task Force
Lehigh Valley Violent Crimes Task Force
Philadelphia Violent Gang Task Force
Safe Streets Violent Crimes Task Force
Safe Streets Violent Drug Gang Task Force
Steamtown Gang Task Force
SW Pennsylvania Safe Streets Task Force
Puerto Rico
Aguadilla Regional Enforcement Team
Fajardo Regional Enforcement Team
Ponce Safe Streets Task Force
Safe Streets Task Force
Rhode Island
Rhode Island Violent Crimes/Gang Task Force
South Carolina
Columbia Violent Gang Task Force
Pee Dee Violent Crime Task Force
Tennessee
Chattanooga Safe Streets Task Force
Knoxville Headquarters Safe Streets Violent Crimes
Task Force
Nashville Violent Crimes Gang Task Force
Safe Streets Task Force HQ City
Texas
Austin Violent Crime Gang/Organized Crime Task Force
Corpus Christi Violent Crimes Task Force
East Texas Area Gang Initiative
El Paso Street and Prison Gang Task Force
Houston Coastal Safe Streets Task Force
Multi-Agency Gang Task Force
Rio Grand Valley Violent Crimes Task Force
San Antonio Safe Streets Violent Crimes Task Force
Southeast Texas Safe Streets Task Force
Tarrant County Safe Streets Task Force
Violent Crimes and Major Offenders and Gang Task Force
West Texas Anti-Gang Team
West Texas Area Major Offender Task Force
Utah
Northern Utah Criminal Apprehension Team
Safe Streets Violent Crime Task Force
Virginia
Richmond Area Violent Enterprise Task Force
South Piedmont Virginia Gang Task Force
The Peninsula Safe Streets Task Force
Tidewater Violent Crimes Task Force
Washington
Seattle Safe Streets and Gang Task Force
South Sound Gang Task Force
Southwest Washington Safe Streets Task Force
Spokane Violent Crime Gang Enforcement Team
Tri-Cities Violent Crime Gang Enforcement Team
Washington, D.C.
WFO/MPD/Safe Streets Gang Task Force
West Virginia
Eastern Panhandle and Potomac Highlands Safe Streets Task Force
Huntington Violent Crimes/Drug Task Force
Wisconsin
Gang-Rock County Task Force
Greater Racine Gang Task Force
ATF Violent Crime Impact Teams (VCIT)

Source: ATF
ICE Operation Community Shield (OCS) Initiative Targets

Source: ICE
APPENDIX D. Acknowledgements
FEDERAL
US Department of Defense
Naval Criminal Investigative Service
US Army
Fort Dix Criminal Investigative Division
Directorate Emergency Services USAG-HI
US Department of Homeland Security
US Border Patrol
US Citizenship and Immigration Services
US Customs and Border Protection
US Homeland Security Investigations
US Department of the Interior
Bureau of Land Management
US Department of Justice
Bureau of Alcohol, Tobacco, Firearms and Explosives
Drug Enforcement Administration
Federal Bureau of Investigation
Federal Bureau of Prisons
Immigration and Customs Enforcement
National Drug Intelligence Center
National Gang Center
National Gang Intelligence Center
US Marshals Service
US Probation and Parole
US Department of State
LOCAL, STATE, AND REGIONAL
ALABAMA
Alabama Fusion Center
Bessemer Police Department
Birmingham Police Department
Etowah County Drug Task Force
Irondale Police Department
Madison County Sheriff’s Office
Pelham Police Department
ALASKA
Alaska Department of Corrections
Anchorage Police Department
ARIZONA
Arizona Adult Probation
Arizona Department of Corrections
Arizona Department of Juvenile Corrections
Arizona Department of Public Safety
Arizona DPS-State Gang Task Force (GIITEM) Central District
Arizona State Prison Kingman / MTC
Cottonwood Police Department
Lake Havasu City Police Department
Maricopa County Sheriff’s Office
Phoenix Police Department
Rocky Mountain Information Network
Scottsdale Police Department
Tempe Police Department
Tucson Police Department
ARKANSAS
13th Judicial District Deputy Prosecutors Office
Scott County Sheriff’s Office
CALIFORNIA
Alameda County Sheriff’s Office
Bakersfield Police Department
Bear Valley Police Department
Berkeley Police Department
Baldwin Park School Police Department
California Department of Corrections and Rehabilitation
California Highway Patrol
Chula Vista Police Department
Coachella Valley Gang Task Force
Compton School Police Department
Concord Police Department
Corona Police Department
Delano Community Correctional Facility
Eureka Police Department
Exeter Police Department
Fresno County Sheriff’s Office
Garden Grove Police Department
Gilroy Police Department
Greenfield Police Department
Hollister Police Department
Huntington Beach Police Department
Inglewood Police Department
Kern County Sheriff’s Office
Los Angeles Police Department
Lincoln Police Department
Long Beach Police Department
Los Angeles County District Attorney
Los Angeles County Probation Department
Los Angeles County Sheriff’s Department
Marina Police Department
Merced Multi-Agency Gang Task Force
Montebello Police Department
Monterey County Probation Department
Monterey Police Department
Morgan Hill Police Department
Mountain View Police Department
Napa County Probation Department
National City Police Department
Oakland Police Department
Office of the Fresno County District Attorney
Oxnard Police Department
Pacific Grove Police Department
Pittsburg Police Department
Placer County District Attorney’s Office
Riverside County District Attorney’s Office
Riverside Sheriff’s Department
Sacramento County Sheriff’s Department
Sacramento Police Department
San Benito County Probation Department
San Benito County Sheriff’s Office
San Bernardino County Sheriff’s Department
San Diego County Probation Department
San Diego Police Department
San Leandro Police Department
San Luis Obispo County Sheriff’s Department
Sanger Police Department
Santa Ana Police Department
Santa Barbara County Sheriff
Santa Barbara Police Department
Santa Barbara Sheriff’s Department
Santa Clara County Probation Department
Santa Monica Police Department
San Bernardino County Sheriff’s Department
San Diego Sheriff’s Department
Simi Valley Police Department
Sonoma County Sheriff’s Office
South Gate Police Department
Southern Alameda County Major Crime Task Force
Stockton Police Department
Tehachapi Police Department
Tuolumne County Sheriff
Ukiah Police Department
Vallejo Police Department
Ventura Police Department
West Covina Police Department
West Sacramento Police Department
Whittier Police Department
COLORADO
10th Judicial District Probation Department
Aurora Police Department
Colorado Department of Corrections
Garfield County Sheriff’s Office
Greeley Police Department
Mesa County Sheriff’s Office
Thornton Police Department
CONNECTICUT
Connecticut State Police
Danbury Police Department
Meriden Police Department
New Haven Police Department
South Windsor Police Department
West Hartford Police Department
DELAWARE
Delaware State Police
New Castle County Police
Wilmington Police Department
DISTRICT OF COLUMBIA
US Attorney’s Office
Washington DC Metropolitan Police Department
FLORIDA
Alachua County Sheriff’s Office
Central Florida Intelligence Exchange
Florida Department of Corrections
Florida Department of Law Enforcement
Fort Myers Police Department
Hernando County Sheriff’s Office
Highlands County Sheriff’s Office
Hillsborough County Sheriff
Jacksonville Sheriff’s Office
Lake County Sheriff’s Office
Lee County Sheriff’s Office
Maitland Police Department
Marion County Sheriff’s Office
Martin County Sheriff’s Office
Miami-Dade Corrections & Rehabilitations
Ocala Police Department
Okeechobee County Sheriff’s Office
Orange County Corrections
Orange County Sheriff’s Office
Orlando Police Department
Oviedo Police Department
Polk County Sheriff’s Office
Sanford Police Department
Sarasota Sheriff’s Office
Seminole County Sheriff’s Office
Tallahassee Police Department
Seminole Police Department
Titusville Police Department
Volusia County Sheriff’s Office
GEORGIA
Cobb County Sheriff’s Office
Douglasville Police Department
Georgia Bureau of Investigation
Gwinnett County Police Department
LaGrange Police Department
Richmond County Board of Education Public Safety
Spalding County Sheriff’s Office
ILLINOIS
Bensenville Police Department
Bloomington Police Department
Chicago Police Department
Decatur Police Department
Dolton Police Department
DuPage County State’s Attorney’s Office
Hanover Park Police Department
Illinois Department of Corrections
Jo Daviess County Sheriff’s Office
Lake County Sheriff Department
Schaumburg Police Department
INDIANA
Anderson Police Department
Boone County Sheriff Department
Cumberland Police Department
Elkhart County Sheriff’s Office
Evansville Police Department
Indiana Department of Corrections
Parke County Sheriff’s Office
Pendleton Correctional Facility
Richmond Police Department
Southwest Indiana Violent Crime Task Force
IOWA
Dubuque Police Department
Iowa Department of Corrections
Jasper County Sheriff’s Office
Storm Lake Police Department
Warren County Sheriff’s Office
KANSAS
Kansas Bureau of Investigation
Lawrence Police Department
Topeka Police Department
Wichita Police Department
KENTUCKY
Henderson Police Department
Kentucky Department of Juvenile Justice
Louisville Metro Police Department
McCracken County Regional Jail
LOUISIANA
Alexandria Police Narcotics Division
Creola Police Department
Denham Springs Police Department
Grant Parish Constable
Grant Parish Sheriff’s Office
Iberia Parish Sheriff’s Office
Jefferson Parish Sheriff’s Office
Louisiana Department of Corrections
Louisiana State Police
Metro Narcotics of Ouachita
New Orleans Police Department
Office of Juvenile Justice
MAINE
Lewiston Police Department
MARYLAND
Anne Arundel County Police Department
Calvert County Sheriff’s Office
Charles County Sheriff’s Office
Greenbelt City Police Department
Hagerstown Department of Police
Harford County Sheriff’s Office
Maryland Coordination and Analysis Center
Maryland Department of Corrections
Montgomery County Police
Prince George’s County Police Department
Wicomico County Department of Corrections
MASSACHUSETTS
Boston Police Department
Chicopee Police Department
Fitchburg Police Department
Hampden County Sheriff’s Department
Haverhill Police Department
Holyoke Police Department
Lowell Police Department
Massachusetts State Police
Springfield Police Department
Worcester Police Department
MICHIGAN
Benton Township Police Department
Berrien County Sheriff’s Department
Escanaba Public Safety Department
Grand Rapids Police Department
Holland Police Department
Muskegon Police Department
Oakland County Violent Gang Task Force
Ottawa County Sheriff’s Office
Unadilla Township Police Department
West Michigan Enforcement Team
MINNESOTA
Dakota County Community Corrections
Minneapolis Police Department
Owatonna Police Department
Prairie Island Tribal Police
Saint Peter Police Department
Shakopee Police Department
MISSISSIPPI
Gulf Coast Regional Fugitive Task Force
Gulfport Police Department
Magee Police Department
Narcotics Task Force of Jackson County
US Attorney’s Office, Southern District of Mississippi
MISSOURI
Berkeley Police Department
Joplin Police Department
Kansas City Missouri Police Department
Missouri Department of Corrections
Monett Police Department
Saint Louis County Police Department
St. Charles Police Department
St. Joseph Missouri Police Department
St. Louis County Police Department
St. Louis Metropolitan Police Department
MONTANA
Crossroads Correctional Center
Laurel Police Department
Missoula Police Department
Montana Department of Corrections
NEBRASKA
Bellevue Police Department
City of Gering Police Department
Columbus Police Department
Crete Police Department
Grand Island Police Department
Kearney Police Department
Omaha Police Department
NEVADA
Las Vegas Metropolitan Police Department
Washoe County Sheriff’s Office
NEW HAMPSHIRE
Belknap County Sheriff’s Department
Concord Police Department
Keene Police Department
Manchester Police Department
Manchester Weed and Seed Program
Merrimack County Department of Corrections
Nashua Police Department
Somersworth Police Department
NEW JERSEY
Bound Brook Police Department
Essex County Prosecutor’s Office
Kenilworth Police Department
Linden Police Department
Passaic County Sheriff’s Department
NEW MEXICO
Albuquerque Police Department
Catron County Sheriff’s Department
Eddy County Sheriff’s Office
Pueblo of Acoma Police Department
NEW YORK
Dutchess County Sheriff’s Office
Glens Falls Police Department
Nassau County Police Department
NORTH CAROLINA
Duplin County Sheriff’s Office
Durham Police Department
Fayetteville Police Department
Gastonia Police Department
New Hanover County Sheriff
North Carolina Department of Corrections
Shelby Police Department
Wake Forest Police Department
NORTH DAKOTA
Heart of America Correctional and Treatment Center
North Dakota Department of Corrections
OHIO
Akron Police Department
Canton Police Department
Columbus, Ohio Division of Police
Dayton Police Department
Lake Metroparks Ranger Department
Montpelier Police Department
Springfield Ohio Division of Police
OKLAHOMA
Davis Correctional Facility
Eastern Shawnee Tribal Police
North Fork Correctional facility
Oklahoma City Police Department
Oklahoma Department of Corrections
Owasso Police Department
OREGON
Crook County Sheriff’s Office
Portland Police Bureau
PENNSYLVANIA
California University of Pennsylvania Police Department
Cumberland County Prison
Ephrata Police Department
Lackawanna County District Attorney
Lackawanna County Prison
Lancaster County District Attorney
Manheim Borough Police Department
Mifflin County Regional Police Department
Montgomery County Adult Probation & Parole Department
Pennsylvania Capitol Police
Pennsylvania State Police
Philadelphia-Camden HIDTA
Slippery Rock University Police
PUERTO RICO
Metropolitan Detention Center, Guaynabo
Police of Puerto Rico
RHODE ISLAND
Providence Police Department
Rhode Island Department of Corrections
SOUTH CAROLINA
Anderson County Gang Task Force
Bamberg Police Department
Charleston County Sheriff Office
Chester City Police Department
Colleton County Sheriff’s Office
Columbia Police Department
Darlington County Sheriff’s Office
Darlington Police Department
Dorchester County Sheriff’s Office
Florence County Sheriff’s Office
Florence Police Department
Fountain Inn Police Department
Greenwood County Sheriff’s Office
Greenwood Police Department
Greer Police Department
Hampton County Sheriff Office
Hartsville Police Department
Lancaster City Police Department
Lancaster Police Department
Latta Police Department
Lexington Medical Health Services – Public Safety
Palmetto Protection Agency, Inc.
Prosperity Police Department
Rock Hill Police Department
South Carolina Department of Corrections
Spartanburg Public Safety Department
Summerville Police Department
Timmonsville Police Department
West Columbia Police Department
SOUTH DAKOTA
Rapid City Police Department
Tripp County Sheriff’s Office
TENNESSEE
Bradley County Juvenile Detention
Chattanooga Police Department
Coffee County Sheriff’s Department
Columbia Police Department
Cookeville Police Department
Covington Police Department
Fayette County Sheriff’s Department
Franklin Police Department
Hardeman County Correctional Facility
Juvenile Court of Jefferson County
Knoxville Police Department
Metro Nashville Police Department
Oak Ridge Police Department
Rutherford County Sheriff’s Department
Sumner County Sheriff’s Office
Tennessee Bureau of Investigation
Tennessee Department of Correction
TEXAS
Amarillo Police Department
Andrews Department of Public Safety
Austin Police Department
Bastrop County Sheriff’s Office
Baytown Police Department
Bexar County Fire Marshal’s Office
Bosque County Sheriff’s Office
Collin County District Attorney’s Office
Dallas ISD Police & Security
Dallas Police Department Gang Unit
Donna ISD Police Department
El Paso County Sheriff’s Office
Harlingen Police Department
Hays County Juvenile Probation
Hidalgo County Constable – Pct 3
Hidalgo County District Attorney’s Office
Hidalgo County Sheriff’s Office
Hutchinson County Sheriff’s Office
Kenedy County Sheriff Office
Luling Police Department
Maverick County Detention Center
Nacogdoches Police Department
New Caney ISD Police Department
Reagan County Sheriff’s Office
San Antonio Police Department
San Marcos Police Department
Schertz Police Department
Texas Alcoholic Beverage Commission
Texas Department of Criminal Justice
Travis County Sheriff’s Office
Texas Department of Public Safety
University of Texas Health Science Center Police
UTAH
West Valley City Police Department
VERMONT
No reporting
VIRGINIA
Abingdon Police Department
Alexandria Police Department
Alexandria Sheriff’s Office
Arlington County Police Department
Bland Correctional Center
Chesapeake Police Department
Chesterfield County Police Department
Chincoteague Police Department
City of Chesapeake Police Department
City of Harrisonburg Police Department
City of Manassas Police Department
Department of Conservation and Recreation
Department of Juvenile Justice
Fairfax County Police Department
Hampton Police Division
Newport News Police Department
Norfolk Police Division
Prince William County Police Department
Richmond Police Department
Staunton Police Department
Suffolk Police Department
Town of Herndon Police Department
Town of Vienna Police Department
Virginia Department of Corrections
Virginia Correctional Center for Women
Virginia Port Authority Police Department
Virginia State Police
Warsaw Probation and Parole Office
WASHINGTON
Everson Police Department
King County Jail
King County Sheriff’s Office
Lynnwood Police Department
Nisqually Indian Tribe
Northwest High Intensity Drug Trafficking Area
Seattle Police Department
Washington State Department of Corrections
WEST VIRGINIA
Eastern Panhandle Potomac Highlands SSTF
Martinsburg Police Department
Philippi Police Department
WISCONSON
Lac Courte Oreilles Tribal Police
Milwaukee Police Department
Wisconsin Department of Corrections
WYOMING
Wyoming Highway Patrol
Endnotes
a Title 18 U.S.C. Section 521(a)(A) defines criminal street gangs as ongoing groups, clubs, organizations, or associations of five or more individuals that have as one of their primary purposes the commission of one or more criminal offenses. Title 18 U.S.C. Section 521(c) further defines such criminal offenses as (1) a federal felony involving a controlled substance; (2) a federal felony crime of violence that has as an element the use or attempted use of physical force against the person of another and (3) a conspiracy to commit an offense described in paragraph (1) or (2).
b For the purpose of this assessment, OMGs include One Percenter gangs as well as support and puppet clubs.
c A juvenile refers to an individual under 18 years of age, although in some states, a juvenile refers to an individual under 16 years of age. A juvenile gang refers to a gang that is primarily comprised of individuals under 18 years of age.
d Juggalos are traditionally fans of the musical group the Insane Clown Posse. Arizona, California, Pennsylvania, and Utah are the only US states that recognize Juggalos as a gang.
e Alien smuggling involves facilitating the illegal entry of aliens for financial or other tangible benefits. It can involve an individual or a criminal organization. Business relationships typically cease once the individual has reached their destination. Human trafficking involves recruitment, transportation, and harboring of persons through force, fraud, or coercion for labor or services that result in slavery, involuntary servitude, or debt bondage. The business relationship does not end and often becomes exploitative and violent.
fAccording to the United Nations, over 90 percent of Mexican migrants illegally entering the United States are assisted by professional smugglers. Although most of the migrants are smuggled in trucks, many have been smuggled by rail, on foot, and tunnels.
g For years, gang members used Internet websites to advertise the sale of their victims. However, recently several Internet sites including Craigslist have eliminated their erotic services personal advertisement sections.
h MDTOs control up to 80 percent of wholesale cocaine distribution in the United States.
i Eurasian criminal groups include Albanian, Armenian, Eastern European, and Russian criminal enterprises.
j Legal mail refers to any correspondence sent to or received from a legal professional. Gang members may disguise their correspondence to resemble legal mail so that it is exempt from inspection.
k Gang members leave prison with the knowledge and connections that allow them to identify with a national gang which will garner them greater respect and “street credibility” within their community.
l According to the Bureau of Justice Statistics, the number of Native Americans incarcerated in jails and prisons nationwide increased by approximately 2.5 percent from 2007 to 2008.
m US military branches include Army, Air Force, Coast Guard, Marines, Navy, Army Reserves, and National Guard.
n The US Southwest Border includes the southern borders of California, Arizona, New Mexico, and Texas.
oAlthough some US and local law enforcement officials maintain that violent crime in Southwest Border states has decreased in the past few years, the effects of such violence, including drug trafficking activity and migration patterns of Mexican citizens fleeing the violence in Northern Mexico, are most acutely reflected in the US Southwest Border Region. Furthermore, as the point of entry for the vast majority of illicit drugs that are smuggled into the United States, the Southwest Border Region is most susceptible to any spillover violence.
p The Barrio Azteca works for the Juarez Cartel on both the US and Mexican sides of the border.
q These estimates were derived from the large number of gang members populating social networking Web sites such as the Hoodup.com, Facebook, and MySpace.
1 US Department of Justice (USDOJ); “Highlights of the 2009 National Youth Gang Survey;” Office of Juvenile Justice and Delinquency Prevention; National Gang Center; May 2011.
2 Open Source News Release; “11 Alleged MS-13 Members Indicted on Racketeering and Other Charges in a Series of Violent Crimes; ICE; 4 May 2011. Open Source Article; “Officials Concerned About Gang Violence in Prince George’s County;” Washington Examiner; available at http://www.washingtonexaminer.com.
3 USDOJ; “Federal Racketeering Indictment Leads to Arrest of 8 Members, Associates of San Gabriel Valley Street Gang;” Press Release; 8 June 2010; available at http://www.justice.gov/usao/cac/pressroom/pr/2010/091.html.
4 USDOJ; “National Drug Threat Assessment 2010;” National Drug Intelligence Center; February 2010.
5 NAGIA Quick Guide to Gangs, National Alliance of Gang Investigators Association; April 2010.
6 Open Source News Article; “Tips for dealing with Asian Gangs;” Police One; 21 May 2009; available at http://www.Policeone.com.
7 USDOJ; National Drug Threat Assessment 2010; NDIC; February 2010. Open Source News Article, “Pot houses linked to gangs, marijuana dispensaries;” Whittier Daily News; 6 September 2010; available at http://www.Whittierdailynews.com. Open Source News Article, “Asian Pot Ring Busted, Noted Restaurateur Suspect;” CBS4 Denver; 7 March 2010; available at http://www.CBS4denver.com.
8 Open Source News Article; “Somali Gangs Ran Sex Ring in 3 US States, Authorities Say;” Fox News; 8 November 2010; available at http://www.foxnews.com.
9 Online news article; “Judge sets $2 million bond in alleged murder, robbery;” Ohio Post; 15 April 2009.
10 FBI Indianapolis Division; “Twenty-Two Charged Federally in Evansville Drug Trafficking Case;” Press Release; 4 February 2010; available at http://indianapolis.fbi.gov/dojpressrel/pressrel10/ip020410.htm.
11 NAGIA Quick Guide to Gangs; National Alliance of Gang Investigators Association; April 2010.
12 Open Source News Article; “Hybrid Gangs responsible for rise in North Las Vegas Crime,” 13 Action News Las Vegas; 25 July 2010; available at http://www.ktnv.com/Global/story.asp;13.
13 Open Source News Article; “Man charged with shooting couple on Maple Valley Trail”; The Seattle Times; 3January 2011; available at http://seattletimes.nwsource.com/html/theblotter/2013837934_man_charged_with_xx_in_connect.html.
14 Open Source News Article; “Teen gets probation in attacks on homeless;” Gazette-Times; 22 January 2010; available at http://www.gazettetime.com/news/local/article_3b43539a-07ab-11df-b6ae-001cc4c03286.html.
15 US Immigration Customs Enforcement (ICE); “8 Arrested as ICE Dismantles Alien Smuggling Ring Linked to Notorious Local Street Gang;” News Release; 14 October 2009; available at http://www.ice.gov/news/releases/0910/091014losangeles.htm.
16 Open Source Website; Human Smuggling and Trafficking Center (HSTC) Charter and Amendments; available at http://www.state.gov/m/ds/hstcenter/41444.htm.
17 DHS; “29 Charged with Sex Trafficking Juveniles;” ICE; News Release; 8 November 2010; available at http://www.ice.gov/news/releases/1011/101108nashville.htm.
18 Open News Source Article; “Report Links Street Gangs to Child Prostitution;” KPBS News; 23 November 2010; available at http://www.kpbs.org/news/2010/nov/09/report-links-street-gangs-child-prostitution.
19 Open Source News Article; Kevin Johnson; USA Today; “Drug Cartels Unite Rival Gangs to Work for Common Bad;” USA Today; 16 March 2010.
20 USDOJ; “National Drug Threat Assessment 2010;” National Drug Intelligence Center; February 2010.
21 USDOJ; “National Drug Threat Assessment 2010;” National Drug Intelligence Center; February 2010.
22 Open Source News Article; “Drug Cartels Uniting Rival Gangs;” USA Today; 3 March 2010; available at http://www.usatoday.com.
23 USDOJ; “National Drug Threat Assessment 2010;” National Drug Intelligence Center; February 2010.
24 Open Source News Article; “US Mexico Drug Gangs Form Alliances;” Washington Times; 26 March 2010; available at http://www.washingtimes.com.
25 Open Source News Article; Kevin Johnson; “Drug Cartels Unite Rival Gangs to Work for Common Bad;” USA Today; 16 March 2010; available at http://www.usatoday.com.
26 Open Source News Article; “US Mexico Drug Gangs Form Alliances;” Washington Times; 26 March 2010; available at http://www.washingtontimes.com.
27 USDOJ; “National Drug Threat Assessment 2010;” National Drug Intelligence Center; February 2010. Open Source News Article; “US Mexico Drug Gangs Form Alliances;” Washington Times; 26 March 2010; available at http://www.washingtontimes.com.
28 Open Source News Article; “La Familia’ North of the Border;” STRATFOR Global Intelligence; 3 December 2009; available at http://www.stratfor.com/weekly/20091203_la_familia_north_border.
29 Open Source News Article; “New Jersey Authorities Indict 34 Lucchese Crime Family Bust from ‘Operation Heat’;” New Jersey.com; 14 May 2010.
30 Open Source News Article; “Authorities crack down on transnational Armenian Power crime group;” CNN; 17 February 2011; available at http://www.cnn.com.
31 Open Source News Article; “N.J. Inmate’s Ordered Killing Shows Danger of Cell Phones in Prison,” http://www.nj.com/news/index.ssf/2010/06/nj_state_prison_inmate_is_char.html; June 11, 2010; Online News Article; “Prosecutor: Trenton prison inmate Anthony Kidd used cell phone to order murder of girlfriend Kendra Degrasse,” http://www.trentonian.com/articles/2010/06/11/news/doc4c11432d64621687151693.txt; June 12, 2010
32 Open Source News Article; “Prisoner Ordered Hit Outside of Prison With Smuggle Cell Phone;” 13 September 2010; available at http://newsone.com/nation/associatedpress4/prisoner-ordered-hit-outside-of-prison-with-smuggled-cell-phone/.
33 Open Source News Article; “Parole Worker Leaked Information to Gang Member;” Fox News New York; 1 November 2010; available at http://www.myfoxny.com.
34 Open Source News Article; “Former Deputy Headed for Prison;” PE.com; 30 July 2010; available at http://www.pe.com.
35 Open Source News Article; “Ex-Cop, James Formato, Pleads Guilty in Mob Case;” CBS News Chicago; 25 April 2010; available at http://www.thechicagosyndicate.com/2010/04/ex-cop-james-formato-pleads-guilty-in.html.
36 Online publication; Bureau of Justice Statistics; Jails in Indian Country, 2008; December 2009; available at http://bjs.ojp.usdoj/index.cfm?ty=pbdetails&iid=1748.
37 Open Source News Article; “Mexican Pot Gangs Infiltrate Indian Reservations in U.S;” The Wall Street Journal; 5 November 2009; available at http://online.wsj.com/article/SB125736987377028727.html.
38 Open Source News Article; “Crunching Numbers in Mexico’s Drug Conflict;” BBC News; 14 January 2011; available at http://www.bbc.com.
39 Stratfor Global Intelligence Center; “Mexican Drug Wars: Bloodiest Year to Date;” 20 December 2010.
40 Open Source News Article; “Napolitano: Border security better than ever;” CBS News; 25 March 2011; http://www.cbsnews.com/8301-503544_162-20047102-503544.html.
41 USDOJ; “National Drug Threat Assessment 2010;” National Drug Intelligence Center; February 2010.
42 USDOJ; “National Drug Threat Assessment 2010;” National Drug Intelligence Center; February 2010.
43 Open Source News Article; “Barrio Azteca threat targets law officers;” El Paso Times; 25 March 2010; available at http://www.elpasotimes.com/ci_14753458.
44 USDOJ; “National Drug Threat Assessment 2010;” National Drug Intelligence Center; February 2010.
45 USDOJ; “National Drug Threat Assessment 2010;” National Drug Intelligence Center; February 2010.
46 USDOJ; “National Drug Threat Assessment 2010;” National Drug Intelligence Center; February 2010.
47 Press Release; “Former Marines Arrested on Weapons Charges;” USDOJ; ATF; 8 November 2010.
48 Press Release; “Three men, US Navy Seal, Arrested for Unlawfully Trafficking in Machine Guns;” US DOJ; ATF; 4 November 2010.
49 Open Source News Article; MSNBC.com, “California Gang Officers Again Targeted by Booby-Trap,”1 March 2010; available at http://www.msnbc.com.
50 Investigative Consultants; email correspondence; 29 November 2010.
51 Investigative Consultants; email correspondence; 29 November 2010. Superior Court of the State of California, County of Los Angeles, Central District; First Amended Complaint for Injunction and Civil Penalties; 15 March 2010.
52 Open Source News Article; “Seeing Green;” Baltimore City Paper; 11 August 2010; available at http://www.citypaper.com.
53 Open Source News Article; “Two Dozen Charged in Alleged Gang-led Mortgage Fraud;” Reuters News; 7 April 2009; available at http://www.reuters.com.
54 Open Source News Article; “Border Crime Sweep Nets Drugs, 246 Arrests;” Sign On San Diego; 28 March 2011; available at http://www.signonsandiego.com.
55 FBI; “Violent Border Gang Indicted; Members Charged in Consulate Murders;” News Release; 9 March 2011; available at http://www.fbi.gov.
56 FBI; “Forty-One Gang Members and Associates in Five Districts Charged with Crimes Including Racketeering, Murder, Drug Trafficking, and Firearms Trafficking;” News Release; 9 February 2011; available at http://www.fbi.gov.
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict71.jpg) Russian nationalists rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)
Russian nationalists rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict74.jpg) Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky)
Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict62.jpg) A woman wearing fake horns holds a banner during a demonstration against bullfighting in Mexico City December 10, 2011. More than hundred demonstrators took part in a protest against bullfighting in the country. Bullfighting has been one of the most popular sport in Mexico for the last 400 years, according to local media. The banner reads “Torture”. Reuters
A woman wearing fake horns holds a banner during a demonstration against bullfighting in Mexico City December 10, 2011. More than hundred demonstrators took part in a protest against bullfighting in the country. Bullfighting has been one of the most popular sport in Mexico for the last 400 years, according to local media. The banner reads “Torture”. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict59.jpg) French Occupy protesters participate in a rally as part of the 63rd anniversary of the Universal Declaration of the Human Rights, on December 10, 2011 in center Paris. The activists, angered by state spending cuts that hurt ordinary people and high unemployment have called for a nationwide protest. Placard reads : ‘Time for Outrage. Getty
French Occupy protesters participate in a rally as part of the 63rd anniversary of the Universal Declaration of the Human Rights, on December 10, 2011 in center Paris. The activists, angered by state spending cuts that hurt ordinary people and high unemployment have called for a nationwide protest. Placard reads : ‘Time for Outrage. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict58.jpg) Women dressed in violet clothes march from El Zocalo Square to the Revolution monument along Juarez Avenue on December 10, 2011 in Mexico City to protest against violence The activity called ‘The Rally of the One Thousand Women’ promotes to put an end to the discrimination and violence against women. Getty
Women dressed in violet clothes march from El Zocalo Square to the Revolution monument along Juarez Avenue on December 10, 2011 in Mexico City to protest against violence The activity called ‘The Rally of the One Thousand Women’ promotes to put an end to the discrimination and violence against women. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict61.jpg) Member of the Association of Parents of Disappeared Persons (APDP) hold portraits of missing relatives during a demonstration to mark International Human Rights Day in Srinagar on December 10, 2011. Demonstrations were held in Srinagar to protest against alleged human rights violations by Indian security forces on Kashmiris. Rights groups say as many as 8,000 people, mostly young men, have ‘disappeared’ by security forces in India-administered Kashmir since an armed insurgency erupted in the Muslim-majority region. Getty
Member of the Association of Parents of Disappeared Persons (APDP) hold portraits of missing relatives during a demonstration to mark International Human Rights Day in Srinagar on December 10, 2011. Demonstrations were held in Srinagar to protest against alleged human rights violations by Indian security forces on Kashmiris. Rights groups say as many as 8,000 people, mostly young men, have ‘disappeared’ by security forces in India-administered Kashmir since an armed insurgency erupted in the Muslim-majority region. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict55.jpg) In this photo taken with a fisheye lens protesters gather during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
In this photo taken with a fisheye lens protesters gather during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict52.jpg) An elderly demonstrator holds a poster showing an edited photo of Prime Minister Vladimir Putin and signed “2050. No” during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.
An elderly demonstrator holds a poster showing an edited photo of Prime Minister Vladimir Putin and signed “2050. No” during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict53.jpg) Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)
Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict54.jpg) Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)
Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict56.jpg) Protesters light flares during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin)
Protesters light flares during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict22.jpg) A supporter of Ivory Coast Prime Minister and leader of news forces the former rebel groupe looks on during a legislative election meeting in Ferkessedougou, north of Ivory Coast, on December 9, 2011. The December 11 polls are boycotted by former Ivorian President Laurent Gbagbo’s Ivorian Popular Front party (FPI) and its allies in protest against his arrest and transfer to the International Criminal Court in The Hague. Nearly 1,000 candidates are in the fray for the 255 parliamentary seats. Getty
A supporter of Ivory Coast Prime Minister and leader of news forces the former rebel groupe looks on during a legislative election meeting in Ferkessedougou, north of Ivory Coast, on December 9, 2011. The December 11 polls are boycotted by former Ivorian President Laurent Gbagbo’s Ivorian Popular Front party (FPI) and its allies in protest against his arrest and transfer to the International Criminal Court in The Hague. Nearly 1,000 candidates are in the fray for the 255 parliamentary seats. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict20.jpg) People protest in the halls of the venue of UN Climate Talks on December 9, 2011, to demand that nations not sign a “death sentence” during the UN Framework Convention on Climate Change (UNFCCC) in Durban. Standing side-by-side with delegates from some of the world’s most vulnerable countries, civil society representatives sang traditional South African freedom songs and chanted slogans like, “Listen to the People, Not the Polluters. In the last 48 hours, over 700,000 people have signed petitions calling on major emitters to stand with the nations of Africa and resist any attempts to delay climate action until 2020. UN climate talks entered their second week entangled in a thick mesh of issues with no guarantee that negotiators and their ministers will be able to sort them out. The 194-nation process is facing, for the second time in two years, the prospect of a bustup, even as scientists warn against the mounting threat of disaster-provoking storms, droughts, flood and rising seas made worse by global warming. Getty
People protest in the halls of the venue of UN Climate Talks on December 9, 2011, to demand that nations not sign a “death sentence” during the UN Framework Convention on Climate Change (UNFCCC) in Durban. Standing side-by-side with delegates from some of the world’s most vulnerable countries, civil society representatives sang traditional South African freedom songs and chanted slogans like, “Listen to the People, Not the Polluters. In the last 48 hours, over 700,000 people have signed petitions calling on major emitters to stand with the nations of Africa and resist any attempts to delay climate action until 2020. UN climate talks entered their second week entangled in a thick mesh of issues with no guarantee that negotiators and their ministers will be able to sort them out. The 194-nation process is facing, for the second time in two years, the prospect of a bustup, even as scientists warn against the mounting threat of disaster-provoking storms, droughts, flood and rising seas made worse by global warming. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict19.jpg) Journalists demonstrate during a protest against the murders of their counterparts outside the Presidential house in Tegucigalpa December 9, 2011. 17 journalists have been shot dead in Honduras since 2010, making the small Central American nation one of the world’s most dangerous places for reporters, according human rights groups. Reuters
Journalists demonstrate during a protest against the murders of their counterparts outside the Presidential house in Tegucigalpa December 9, 2011. 17 journalists have been shot dead in Honduras since 2010, making the small Central American nation one of the world’s most dangerous places for reporters, according human rights groups. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict18.jpg) Bahraini women watch as hundreds of anti-government protesters (unseen) run Friday, Dec. 9, 2011, through the Musalla area of Manama, Bahrain, toward an area that had been the hub of Bahrain’s spring uprising and is now a heavily militarized zone that protesters seek to reclaim. The protesters were forced back by riot police just short of the area. Writing on the wall reads “freedom” above pictures of political prisoners. (Hasan Jamali)
Bahraini women watch as hundreds of anti-government protesters (unseen) run Friday, Dec. 9, 2011, through the Musalla area of Manama, Bahrain, toward an area that had been the hub of Bahrain’s spring uprising and is now a heavily militarized zone that protesters seek to reclaim. The protesters were forced back by riot police just short of the area. Writing on the wall reads “freedom” above pictures of political prisoners. (Hasan Jamali)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict17.jpg) Russian opposition leader Sergei Udaltsov’s wife Anastasia, left, speaks to the media as environmental activist and leader of the Khimki forest defenders Yevgenia Chirikova looks at her during a news conference in Moscow, Russia, Friday Dec. 9, 2011. Energized activists and anxious authorities are bracing for anti-government protests planned across Russia’s sprawling expanse Saturday that promise to be the largest demonstration of public outrage since the dying days of the Soviet Union.
Russian opposition leader Sergei Udaltsov’s wife Anastasia, left, speaks to the media as environmental activist and leader of the Khimki forest defenders Yevgenia Chirikova looks at her during a news conference in Moscow, Russia, Friday Dec. 9, 2011. Energized activists and anxious authorities are bracing for anti-government protests planned across Russia’s sprawling expanse Saturday that promise to be the largest demonstration of public outrage since the dying days of the Soviet Union.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict7.jpg) Occupy Boston Protestors reacted to the announcement that their downtown encampment would not be evicted on December 9, 2011, in Boston, Massachusetts. Boston Mayor Thomas M. Menino set a midnight deadline for Occupy Boston protestors to leave their downtown encampment in Dudley Square, or face eviction. In response, many of the protestors chose to take down their tents, and by the midnight deadline much of the camp was gone. At approximately 1:15AM on December 9, 2011, the Boston police announced that they would not evict the protestors from Dudley Square. Protestors took to the street in celebration, and further protest. Getty
Occupy Boston Protestors reacted to the announcement that their downtown encampment would not be evicted on December 9, 2011, in Boston, Massachusetts. Boston Mayor Thomas M. Menino set a midnight deadline for Occupy Boston protestors to leave their downtown encampment in Dudley Square, or face eviction. In response, many of the protestors chose to take down their tents, and by the midnight deadline much of the camp was gone. At approximately 1:15AM on December 9, 2011, the Boston police announced that they would not evict the protestors from Dudley Square. Protestors took to the street in celebration, and further protest. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict9.jpg) Worker Pat Revell pickets outside Unilever’s Port Sunlight factory on the Wirral, Merseyside on December 9, 2011 in Port Sunlight, England. The workers are on strike in protest against the company’s plan to axe their final salary pension scheme. The strike is the first in the history of the consumer goods manufacturer who lists PG Tips tea and Persil washing detergent amongst its products. Getty
Worker Pat Revell pickets outside Unilever’s Port Sunlight factory on the Wirral, Merseyside on December 9, 2011 in Port Sunlight, England. The workers are on strike in protest against the company’s plan to axe their final salary pension scheme. The strike is the first in the history of the consumer goods manufacturer who lists PG Tips tea and Persil washing detergent amongst its products. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict8.jpg) Supporters of the Serbian Radical Party stand in front of policemen while holding posters with a picture of party leader Vojislav Seselj during a protest against Serbia’s efforts to become an official candidate for the European Union membership in front of Serbia’s Presidency building in Belgrade December 9, 2011. The posters read, “We don’t want in the European Union” (L), and “Tadic don’t humiliate Serbs”. Reuters
Supporters of the Serbian Radical Party stand in front of policemen while holding posters with a picture of party leader Vojislav Seselj during a protest against Serbia’s efforts to become an official candidate for the European Union membership in front of Serbia’s Presidency building in Belgrade December 9, 2011. The posters read, “We don’t want in the European Union” (L), and “Tadic don’t humiliate Serbs”. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict6.jpg) People sit as others lay on the ground as they watch a movie in the main entrance of Germans Trias i Pujol hospital during a protest against spending cuts in Catalonia’s public healthcare system, in Badalona, near Barcelona city, Spain, Friday Dec. 9, 2011. The leaders of the 17 countries that use the euro, plus six others, have tentatively agreed to a new treaty that enforces stricter budget rules seen as crucial to solving Europe’s debt crisis and holding the currency-bloc together. An agreement on fiscal discipline is considered a critical first step before the European Central Bank, the International Monetary Fund and others would commit more financial aid to help countries like Italy and Spain, which have large debts and unsustainable borrowing costs. AP
People sit as others lay on the ground as they watch a movie in the main entrance of Germans Trias i Pujol hospital during a protest against spending cuts in Catalonia’s public healthcare system, in Badalona, near Barcelona city, Spain, Friday Dec. 9, 2011. The leaders of the 17 countries that use the euro, plus six others, have tentatively agreed to a new treaty that enforces stricter budget rules seen as crucial to solving Europe’s debt crisis and holding the currency-bloc together. An agreement on fiscal discipline is considered a critical first step before the European Central Bank, the International Monetary Fund and others would commit more financial aid to help countries like Italy and Spain, which have large debts and unsustainable borrowing costs. AP![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict5.jpg) Members of the Red Shirt movement joke with a Thai police officer as they gather to protest against former Thai Prime Minister Abhisit Vejjajiva outside Metropolitan Police headquarters in Bangkok, Thailand Friday, Dec. 9, 2011. Abhisit was called in to give information to a police investigation team on the government’s crackdown on red-shirt demonstrators last year during which 91 people were killed. (Apichart Weerawong)
Members of the Red Shirt movement joke with a Thai police officer as they gather to protest against former Thai Prime Minister Abhisit Vejjajiva outside Metropolitan Police headquarters in Bangkok, Thailand Friday, Dec. 9, 2011. Abhisit was called in to give information to a police investigation team on the government’s crackdown on red-shirt demonstrators last year during which 91 people were killed. (Apichart Weerawong)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict63.jpg) Panamanian people protest against the return of former General Manuel Noriega to Panama, in Panama City on December 09,2011. Noriega returns to Panama without the trappings of political or military clout, but with something of incalculable value — detailed knowledge of the skeletons that lurk in the Central American nation’s closet. Getty
Panamanian people protest against the return of former General Manuel Noriega to Panama, in Panama City on December 09,2011. Noriega returns to Panama without the trappings of political or military clout, but with something of incalculable value — detailed knowledge of the skeletons that lurk in the Central American nation’s closet. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict4.jpg) Thousands of people gather outside the main courthouse during the first trial of 22 leftist students who were jailed after they staged a demonstration to protest a police crackdown on anti-government demonstrators in the northern town of Hopa, Black Sea, ahead of general elections in June, in Ankara, Turkey, Friday, Dec. 9, 2011. (Burhan Ozbilici)
Thousands of people gather outside the main courthouse during the first trial of 22 leftist students who were jailed after they staged a demonstration to protest a police crackdown on anti-government demonstrators in the northern town of Hopa, Black Sea, ahead of general elections in June, in Ankara, Turkey, Friday, Dec. 9, 2011. (Burhan Ozbilici)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict10.jpg) Activists of the Ukrainian women’s movement FEMEN stage a performance in front of the Christ the Saviour Cathedral in Moscow, on December 9, 2011, to protest against alleging mass fraud in the Russian December 4 parliamentary polls and demanding Russia’s Prime Minister Vladimir Putin that he stop his political activities. Putin, who became premier in 2008 after serving two Kremlin terms, filed this week his application to stand in the March elections. Getty
Activists of the Ukrainian women’s movement FEMEN stage a performance in front of the Christ the Saviour Cathedral in Moscow, on December 9, 2011, to protest against alleging mass fraud in the Russian December 4 parliamentary polls and demanding Russia’s Prime Minister Vladimir Putin that he stop his political activities. Putin, who became premier in 2008 after serving two Kremlin terms, filed this week his application to stand in the March elections. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict0.jpg) Activists of Ukraine’s protest group Femen, protest outside the Christ the Saviour cathedral in Moscow, Russia, Friday, Dec. 9, 2011. The post-election protests in Moscow drew thousands and continued for several days in the biggest ever challenge to Putin, reflecting a growing public frustration with his rule that may complicate his bid to reclaim the presidency in next March’s vote. (Ivan Sekretarev)
Activists of Ukraine’s protest group Femen, protest outside the Christ the Saviour cathedral in Moscow, Russia, Friday, Dec. 9, 2011. The post-election protests in Moscow drew thousands and continued for several days in the biggest ever challenge to Putin, reflecting a growing public frustration with his rule that may complicate his bid to reclaim the presidency in next March’s vote. (Ivan Sekretarev)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict45.jpg) Medical workers rally at the Latvian Saeima (Parliament) building to protest budget cuts in health care on December 8, 2011 in Riga. The protesters are holding black balloons and various placards, urging the government to care for medical workers and warning that many health care workers may leave Latvia. Placards read: ‘Left country. Everyone has rights to receive health care’. Getty
Medical workers rally at the Latvian Saeima (Parliament) building to protest budget cuts in health care on December 8, 2011 in Riga. The protesters are holding black balloons and various placards, urging the government to care for medical workers and warning that many health care workers may leave Latvia. Placards read: ‘Left country. Everyone has rights to receive health care’. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict44.jpg) Demonstrators protest about high inflation and low interest rates outside the Bank of England in the City of London December 8, 2011. The Bank of England voted on Thursday to stick to its four-month programme to pump an extra 75 billion pounds of quantitative easing into the rapidly slowing economy. Reuters
Demonstrators protest about high inflation and low interest rates outside the Bank of England in the City of London December 8, 2011. The Bank of England voted on Thursday to stick to its four-month programme to pump an extra 75 billion pounds of quantitative easing into the rapidly slowing economy. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict43.jpg) Pakistani protesters carry national flags as they march during a demonstration in Islamabad on December 8, 2011 against the cross-border NATO air strike on Pakistani troops. Several hundred journalists, labour leaders and traders on December 8, took to streets to condemn a recent air strike by NATO on Pakistani military checkposts that killed 24 soldiers. Pakistan shut the only supply route in Khyber tribal region for international troops in Afghanistan, boycotted the Bonn conference and announced to revisit policy towards the US in protest against the attack. Getty
Pakistani protesters carry national flags as they march during a demonstration in Islamabad on December 8, 2011 against the cross-border NATO air strike on Pakistani troops. Several hundred journalists, labour leaders and traders on December 8, took to streets to condemn a recent air strike by NATO on Pakistani military checkposts that killed 24 soldiers. Pakistan shut the only supply route in Khyber tribal region for international troops in Afghanistan, boycotted the Bonn conference and announced to revisit policy towards the US in protest against the attack. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict42.jpg) Fundamentalist Christians protest on December 8, 2011 in Paris, near the Rond-Point theatre where Argentina-born author Rodrigo Garcia’s play ‘Golgota Picnic’ is performed which they judge ‘blasphemous’. Getty
Fundamentalist Christians protest on December 8, 2011 in Paris, near the Rond-Point theatre where Argentina-born author Rodrigo Garcia’s play ‘Golgota Picnic’ is performed which they judge ‘blasphemous’. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict41.jpg) People pose with a protester wearing a mock mask depicting Russian Prime Minister Vladimir Putin during a rally in downtown St.Petersburg, Russia, Thursday, Dec. 8, 2011. More than five hundred people protested in St.Petersburg against Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
People pose with a protester wearing a mock mask depicting Russian Prime Minister Vladimir Putin during a rally in downtown St.Petersburg, Russia, Thursday, Dec. 8, 2011. More than five hundred people protested in St.Petersburg against Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict40.jpg) Occupy Boston protester Heather McCann, of Watertown, Mass., center, loads a crate of books into a truck at the Dewey Square encampment while dismantling the camps library, in Boston, Thursday, Dec. 8, 2011. Boston Mayor Thomas Menino said Thursday that Occupy Boston protesters must leave their encampment in the city’s financial district by midnight Thursday or face eviction by police. (Steven Senne)
Occupy Boston protester Heather McCann, of Watertown, Mass., center, loads a crate of books into a truck at the Dewey Square encampment while dismantling the camps library, in Boston, Thursday, Dec. 8, 2011. Boston Mayor Thomas Menino said Thursday that Occupy Boston protesters must leave their encampment in the city’s financial district by midnight Thursday or face eviction by police. (Steven Senne)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict31.jpg) A veiled Kashmiri government employee participates in a protest against the government in Srinagar, India, Thursday, Dec. 8, 2011. Dozens of government employees demanded release of arrears and regularization of jobs for daily wage workers. (Dar Yasin)
A veiled Kashmiri government employee participates in a protest against the government in Srinagar, India, Thursday, Dec. 8, 2011. Dozens of government employees demanded release of arrears and regularization of jobs for daily wage workers. (Dar Yasin)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict30.jpg) Protesters march to join fellow protesters who camped out outside a Catholic church near the Presidential Palace in Manila, Philippines Thursday Dec. 8, 2011 to await news of the scheduled execution of a Filipino man convicted in China for drug trafficking. Philippine officials said, the Filipino man, who was convicted on drug trafficking, was executed in China on Thursday despite an appeal for clemency from President Benigno Aquino III on humanitarian grounds. (Bullit Marquez)
Protesters march to join fellow protesters who camped out outside a Catholic church near the Presidential Palace in Manila, Philippines Thursday Dec. 8, 2011 to await news of the scheduled execution of a Filipino man convicted in China for drug trafficking. Philippine officials said, the Filipino man, who was convicted on drug trafficking, was executed in China on Thursday despite an appeal for clemency from President Benigno Aquino III on humanitarian grounds. (Bullit Marquez)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict29.jpg) Kashmiri government employees participate in a protest against the government in Srinagar, India, Thursday, Dec. 8, 2011. Dozens of government employees demanded release of arrears and regularization of jobs for daily wage workers. (Dar Yasin)
Kashmiri government employees participate in a protest against the government in Srinagar, India, Thursday, Dec. 8, 2011. Dozens of government employees demanded release of arrears and regularization of jobs for daily wage workers. (Dar Yasin)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict28.jpg) A small group of demonstrators screams slogans demanding UN protection for Iranian dissidents in Camp Ashraf, Iraq, as they protest outside the Dutch Foreign Ministry during U.S. Secretary of State Hillary Rodham Clinton’s visit in The Hague, Netherlands, Thursday Dec. 8, 2011. (Peter Dejong)
A small group of demonstrators screams slogans demanding UN protection for Iranian dissidents in Camp Ashraf, Iraq, as they protest outside the Dutch Foreign Ministry during U.S. Secretary of State Hillary Rodham Clinton’s visit in The Hague, Netherlands, Thursday Dec. 8, 2011. (Peter Dejong)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict27.jpg) Police officers detain an opposition activist during a rally in downtown St.Petersburg, Russia, Thursday, Dec. 8, 2011. More than five hundreds people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
Police officers detain an opposition activist during a rally in downtown St.Petersburg, Russia, Thursday, Dec. 8, 2011. More than five hundreds people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict26.jpg) French far-right leader Marine Le Pen arrives at their demonstration in Paris Thursday, Dec. 8, 2011. The demonstration was to oppose a bill on which the Senate were voting Thursday afternoon, a private members bill calling for the right for foreigners to be able to vote in French municipal elections. (Jacques Brinon)
French far-right leader Marine Le Pen arrives at their demonstration in Paris Thursday, Dec. 8, 2011. The demonstration was to oppose a bill on which the Senate were voting Thursday afternoon, a private members bill calling for the right for foreigners to be able to vote in French municipal elections. (Jacques Brinon)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict25.jpg) People living near nuclear plant sites shout slogans during an anti-nuclear protest in New Delhi, India, Thursday, Dec. 8, 2011. The protesters demanded scrapping of projects that endanger people’s safety and threaten livelihoods, according to a press release. Placard reads “Stop displacement of people in the name of development.” (Manish Swarup)
People living near nuclear plant sites shout slogans during an anti-nuclear protest in New Delhi, India, Thursday, Dec. 8, 2011. The protesters demanded scrapping of projects that endanger people’s safety and threaten livelihoods, according to a press release. Placard reads “Stop displacement of people in the name of development.” (Manish Swarup)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict23.jpg) An Israeli musician covers her face in protest, as she performs during a rally against gender segregation, in Jerusalem, Wednesday, Dec. 7, 2011. Hundreds of women and women’s rights activists gathered in central Jerusalem Wednesday night for a rally organized by the New Israel Fund, themed “women will be seen and heard”, to protest discrimination against women in Israel. (Sebastian Scheiner)
An Israeli musician covers her face in protest, as she performs during a rally against gender segregation, in Jerusalem, Wednesday, Dec. 7, 2011. Hundreds of women and women’s rights activists gathered in central Jerusalem Wednesday night for a rally organized by the New Israel Fund, themed “women will be seen and heard”, to protest discrimination against women in Israel. (Sebastian Scheiner)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict49.jpg) Nepalese Buddhist monks and nuns take out a protest in Katmandu, Nepal, Wednesday, Dec. 7, 2011. Hundreds of Buddhists demonstrated in Nepal’s capital to protest the appointment of Maoist party chief Pushpa Kamal Dahal to head a project to develop the area where Buddha was believed born in southern Nepal. The protestors demanded that there should not be any political involvement in the project to develop Lumbini, located 150 miles (240 kilometers) southwest of Katmandu. AP
Nepalese Buddhist monks and nuns take out a protest in Katmandu, Nepal, Wednesday, Dec. 7, 2011. Hundreds of Buddhists demonstrated in Nepal’s capital to protest the appointment of Maoist party chief Pushpa Kamal Dahal to head a project to develop the area where Buddha was believed born in southern Nepal. The protestors demanded that there should not be any political involvement in the project to develop Lumbini, located 150 miles (240 kilometers) southwest of Katmandu. AP![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict48.jpg) A Libyan girl holds a placard that reads in Arabic ‘Thank you our brave rebels, but now let us live in peace’ during a protest in Tripoli’s landmark Martyrs Square on December 7, 2011 against former rebels who toppled Moamer Kadhafi but are still camping out in the capital and still have their weapons. Getty
A Libyan girl holds a placard that reads in Arabic ‘Thank you our brave rebels, but now let us live in peace’ during a protest in Tripoli’s landmark Martyrs Square on December 7, 2011 against former rebels who toppled Moamer Kadhafi but are still camping out in the capital and still have their weapons. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict47.jpg) Members of the Canadian Youth Delegation stage a protest as Canada’s Minister of Environment Peter Kent addresses the United Nations Climate Change Conference (COP17) in Durban in this handout picture released by the Canada Youth Delegation, December 7, 2011. Reuters
Members of the Canadian Youth Delegation stage a protest as Canada’s Minister of Environment Peter Kent addresses the United Nations Climate Change Conference (COP17) in Durban in this handout picture released by the Canada Youth Delegation, December 7, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict46.jpg) Two protesters look at each other as they await processing after being arrested by Washington DC Metropolitan Police during an Occupy DC protest in Washington, December 7, 2011. Police arrested economic protesters in Washington on Wednesday as they blocked streets and disrupted traffic in an area famous as a center for the offices of lobbyists. Reuters
Two protesters look at each other as they await processing after being arrested by Washington DC Metropolitan Police during an Occupy DC protest in Washington, December 7, 2011. Police arrested economic protesters in Washington on Wednesday as they blocked streets and disrupted traffic in an area famous as a center for the offices of lobbyists. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict24.jpg) An Occupy DC demonstrator sits on a chair as demonstrators blocked an intersection on K St., in Washington, Wednesday, Dec. 7, 2011. (Evan Vucci)
An Occupy DC demonstrator sits on a chair as demonstrators blocked an intersection on K St., in Washington, Wednesday, Dec. 7, 2011. (Evan Vucci)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict32.jpg) Occupy Wall Street activists carry house warming gifts to a house warming party during a tour of foreclosed homes in the East New York neighborhood of the Brooklyn borough of New York, Tuesday, Dec. 6, 2011. Finding it increasingly difficult to camp in public spaces, Occupy protesters across the country are reclaiming foreclosed homes and boarded-up properties, signaling a tactical shift for the movement against wealth inequality.
Occupy Wall Street activists carry house warming gifts to a house warming party during a tour of foreclosed homes in the East New York neighborhood of the Brooklyn borough of New York, Tuesday, Dec. 6, 2011. Finding it increasingly difficult to camp in public spaces, Occupy protesters across the country are reclaiming foreclosed homes and boarded-up properties, signaling a tactical shift for the movement against wealth inequality.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict50.jpg) A Colombian woman living in Panama holds a Colombian national flag during a protest march against the Revolutionary Armed Forces of Colombia (FARC), in Panama City December 6, 2011. Outraged by the killing of four captives by FARC rebels, Colombians protested on Tuesday to demand an end to half a century of guerrilla violence and kidnapping. The words on the flag read: “Release them”. Reuters
A Colombian woman living in Panama holds a Colombian national flag during a protest march against the Revolutionary Armed Forces of Colombia (FARC), in Panama City December 6, 2011. Outraged by the killing of four captives by FARC rebels, Colombians protested on Tuesday to demand an end to half a century of guerrilla violence and kidnapping. The words on the flag read: “Release them”. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict51.jpg) Colombian demonstrators take part in a protest march against Revolutionary Armed Forces of Colombia FARC rebels in Cali December 6, 2011. Outraged by the execution of four captives by FARC rebels, tens of thousands of Colombians protested across the nation on Tuesday to demand an end to half a century of guerrilla violence and kidnapping. Reuters
Colombian demonstrators take part in a protest march against Revolutionary Armed Forces of Colombia FARC rebels in Cali December 6, 2011. Outraged by the execution of four captives by FARC rebels, tens of thousands of Colombians protested across the nation on Tuesday to demand an end to half a century of guerrilla violence and kidnapping. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict33.jpg) In this Nov. 2, 2011 file photo, occupy Oakland protesters march through the Port of Oakland in Oakland, Calif. Protesters want to shut down ports up and down the U.S. West Coast on Monday, Dec.12,2011, to gum up the engines of global commerce. But organizers who are partly billing this effort as a show of solidarity with longshoremen have not won the support of the powerful union representing thousands of dock workers. (Noah Berger)
In this Nov. 2, 2011 file photo, occupy Oakland protesters march through the Port of Oakland in Oakland, Calif. Protesters want to shut down ports up and down the U.S. West Coast on Monday, Dec.12,2011, to gum up the engines of global commerce. But organizers who are partly billing this effort as a show of solidarity with longshoremen have not won the support of the powerful union representing thousands of dock workers. (Noah Berger)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict35.jpg) An activist of a local women’s rights watchdog FEMEN, with writing “I am independent” and Ukraine’s’ national flag on her belly, seen during celebrities on the occasion of Ukraine’s 19th Independence in Kiev, Ukraine, Tuesday, Aug. 24, 2010. (Efrem Lukatsky)
An activist of a local women’s rights watchdog FEMEN, with writing “I am independent” and Ukraine’s’ national flag on her belly, seen during celebrities on the occasion of Ukraine’s 19th Independence in Kiev, Ukraine, Tuesday, Aug. 24, 2010. (Efrem Lukatsky)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict57.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict34.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict0.jpg) Kashmir Sutherland huddles with other protesters for warmth in Shemanski Park after police told them to take down tents or be kicked out Monday, Dec. 5, 2011, in Portland, Ore. The Oregonian reports the demonstrators agreed to take down a tent to stay in the park Sunday night. On Saturday night police arrested 19 demonstrators setting up structures in the South Park blocks. Police evicted demonstrators on Nov. 13 from two downtown parks.
Kashmir Sutherland huddles with other protesters for warmth in Shemanski Park after police told them to take down tents or be kicked out Monday, Dec. 5, 2011, in Portland, Ore. The Oregonian reports the demonstrators agreed to take down a tent to stay in the park Sunday night. On Saturday night police arrested 19 demonstrators setting up structures in the South Park blocks. Police evicted demonstrators on Nov. 13 from two downtown parks.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict44.jpg) A woman shouts slogans during a rally in Moscow, Monday, Dec. 5, 2011. Several thousand people have protested in Moscow against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. A group of several hundred then marched toward the Central Elections Commission near the Kremlin, but were stopped by riot police and taken away in buses. (Sergey Ponomarev)
A woman shouts slogans during a rally in Moscow, Monday, Dec. 5, 2011. Several thousand people have protested in Moscow against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. A group of several hundred then marched toward the Central Elections Commission near the Kremlin, but were stopped by riot police and taken away in buses. (Sergey Ponomarev)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict26.jpg) A blind woman rests in front of a police line during a protest by Greek blind people outside Parliament in Athens, on Monday, Dec. 5, 2011. Dozens of people took part in the demonstration, to protest against government welfare spending cuts. Greece is in the throes of an acute financial crisis and has implemented a harsh austerity programme in exchange for international rescue loans. (Petros Giannakouris)
A blind woman rests in front of a police line during a protest by Greek blind people outside Parliament in Athens, on Monday, Dec. 5, 2011. Dozens of people took part in the demonstration, to protest against government welfare spending cuts. Greece is in the throes of an acute financial crisis and has implemented a harsh austerity programme in exchange for international rescue loans. (Petros Giannakouris)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict37.jpg) Occupy DC protesters stand inside a structure set up overnight in McPherson Square, Sunday, Dec. 4, 2011 in Washington. Protesters are refusing to dismantle the unfinished wooden structure erected in the park. (Manuel Balce Ceneta)
Occupy DC protesters stand inside a structure set up overnight in McPherson Square, Sunday, Dec. 4, 2011 in Washington. Protesters are refusing to dismantle the unfinished wooden structure erected in the park. (Manuel Balce Ceneta)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict43.jpg) In this Nov. 17, 2011 file photo, students clash with police during a demonstration in Milan, Italy, as university students protest against budget cuts and a lack of jobs, hours before new Italian Premier Mario Monti reveals his anti-crisis strategy in Parliament. Europe’s sovereign-debt crisis, which has dragged on for more than two years, is entering a pivotal week, as leaders across the continent converge to prevent a collapse of the euro and a financial panic from spreading.
In this Nov. 17, 2011 file photo, students clash with police during a demonstration in Milan, Italy, as university students protest against budget cuts and a lack of jobs, hours before new Italian Premier Mario Monti reveals his anti-crisis strategy in Parliament. Europe’s sovereign-debt crisis, which has dragged on for more than two years, is entering a pivotal week, as leaders across the continent converge to prevent a collapse of the euro and a financial panic from spreading.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict35.jpg) A female activist carries a sign promoting gender equality as protesters march through downtown Rabat calling for greater democracy. Moroccan pro-democracy activists called for a day of rage on Dec. 4, 2011, a week after legislative elections but few turned out. (Paul Schemm)
A female activist carries a sign promoting gender equality as protesters march through downtown Rabat calling for greater democracy. Moroccan pro-democracy activists called for a day of rage on Dec. 4, 2011, a week after legislative elections but few turned out. (Paul Schemm)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict66.jpg) Animal rights activists of the AnimaNaturalis international organization stage a naked protest in the middle of the Plaza de Espana square in the centre of Madrid on December 4, 2011, to denounce the slaying of animals to make fur coats. The men and women, covered in red paint that resembled blood, lay down and curled up against each other under a sunny sky in the busy square which is home to several cinemas, cafes and restaurants. Placard reads ‘How many lives for a coat?’. Getty
Animal rights activists of the AnimaNaturalis international organization stage a naked protest in the middle of the Plaza de Espana square in the centre of Madrid on December 4, 2011, to denounce the slaying of animals to make fur coats. The men and women, covered in red paint that resembled blood, lay down and curled up against each other under a sunny sky in the busy square which is home to several cinemas, cafes and restaurants. Placard reads ‘How many lives for a coat?’. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict67.jpg) Participants attend the Slutwalk Singapore event held at the Speakers’ Corner on December 4, 2011. Supporters of the global SlutWalk movement against sexual violence held a rally in Singapore, attracting dozens to a rare protest in the strictly policed city-state. Getty
Participants attend the Slutwalk Singapore event held at the Speakers’ Corner on December 4, 2011. Supporters of the global SlutWalk movement against sexual violence held a rally in Singapore, attracting dozens to a rare protest in the strictly policed city-state. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict64.jpg) Russian police officers detain opposition demonstrators during an unsanctioned rally in downtown Moscow, Russia, Sunday, Dec. 4, 2011. The rally was staged by a few dozen activists of the Left Front opposition group to protest against Sunday’s elections. (Misha Japaridze)
Russian police officers detain opposition demonstrators during an unsanctioned rally in downtown Moscow, Russia, Sunday, Dec. 4, 2011. The rally was staged by a few dozen activists of the Left Front opposition group to protest against Sunday’s elections. (Misha Japaridze)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict68.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict72.jpg) Police officers try to arrest activists of the Ukrainian women’s movement FEMEN as they protest on December 3, 2011 against a meeting of opposition parties in Kiev. FEMEN activists protested against the event, saying that peeple came to the meeting because its organizers promised them money.
Police officers try to arrest activists of the Ukrainian women’s movement FEMEN as they protest on December 3, 2011 against a meeting of opposition parties in Kiev. FEMEN activists protested against the event, saying that peeple came to the meeting because its organizers promised them money.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict71.jpg) Body-painted environmental activists demonstrate outside the United Nations Climate Change conference (COP17) in Durban December 3, 2011. The protest march was part of a Global Day of Action to demand a fair climate change deal. Reuters
Body-painted environmental activists demonstrate outside the United Nations Climate Change conference (COP17) in Durban December 3, 2011. The protest march was part of a Global Day of Action to demand a fair climate change deal. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict69.jpg) An opponent of reelected Nicaraguan President Daniel Ortega holds a banner reading ‘Fraud=Poverty’, as she takes part in a protest called ”march against fraud” in Managua on December 3, 2011. About five thousand people marched in Nicaragua denouncing electoral fraud in past November 6 elections in Nicaragua and demanding a new election with foreign observers. Getty
An opponent of reelected Nicaraguan President Daniel Ortega holds a banner reading ‘Fraud=Poverty’, as she takes part in a protest called ”march against fraud” in Managua on December 3, 2011. About five thousand people marched in Nicaragua denouncing electoral fraud in past November 6 elections in Nicaragua and demanding a new election with foreign observers. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict65.jpg) Occupy LA protesters march from Pershing Square to the Los Angeles County Men’s Central Jail where protesters, who were arrested on Wednesday, were being held, in Los Angeles, on Saturday, Dec. 3, 2011. (David Zentz)
Occupy LA protesters march from Pershing Square to the Los Angeles County Men’s Central Jail where protesters, who were arrested on Wednesday, were being held, in Los Angeles, on Saturday, Dec. 3, 2011. (David Zentz)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict61.jpg) Andean people protest against Newmont Mining’s Conga gold project during a march near the Cortada lagoon at Peru’s region of Cajamarca, November 24, 2011. Peru’s prime minister on December 2, 2011, said Newmont Mining must set aside money to finance social projects and any environmental damage as a precondition for moving forward on a stalled $4.8 billion gold mine project. Opponents of Newmont Mining’s $4.8 billion Conga project refused to end their rallies on November 30, 2011, saying Peru must permanently cancel the proposed mine after temporarily halting work on it to avert violence. Protesters and farmers say the mine would cause pollution and hurt water supplies by replacing a string of alpine lakes with artificial reservoirs. Picture taken November 24, 2011.
Andean people protest against Newmont Mining’s Conga gold project during a march near the Cortada lagoon at Peru’s region of Cajamarca, November 24, 2011. Peru’s prime minister on December 2, 2011, said Newmont Mining must set aside money to finance social projects and any environmental damage as a precondition for moving forward on a stalled $4.8 billion gold mine project. Opponents of Newmont Mining’s $4.8 billion Conga project refused to end their rallies on November 30, 2011, saying Peru must permanently cancel the proposed mine after temporarily halting work on it to avert violence. Protesters and farmers say the mine would cause pollution and hurt water supplies by replacing a string of alpine lakes with artificial reservoirs. Picture taken November 24, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict56.jpg) A woman protester join others as they shout slogans during the observance of World Climate Day Saturday, Dec. 3, 2011 near the U.S. Embassy in Manila, Philippines. The protest coincided with the annual climate talks of the Conference of Parties (COP17) in Durban, South Africa. (Pat Roque)
A woman protester join others as they shout slogans during the observance of World Climate Day Saturday, Dec. 3, 2011 near the U.S. Embassy in Manila, Philippines. The protest coincided with the annual climate talks of the Conference of Parties (COP17) in Durban, South Africa. (Pat Roque)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict60.jpg) A woman holds aplacard during a protest march against the war in Afghanistan on December 3, 2011 in the western German city of Bonn where a major international conference on December 5 will discuss the country’s future beyond 2014, when NATO-led international combat troops will leave. Getty
A woman holds aplacard during a protest march against the war in Afghanistan on December 3, 2011 in the western German city of Bonn where a major international conference on December 5 will discuss the country’s future beyond 2014, when NATO-led international combat troops will leave. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict57.jpg) A survivor of the Bhopal gas tragedy lies on a railway track as others sit around to stop train movement during a protest in Bhopal, India, Saturday, Dec. 3, 2011. Thousands of survivors of the world’s worst industrial accident blocked trains through a central Indian city on Saturday to demand more compensation.
A survivor of the Bhopal gas tragedy lies on a railway track as others sit around to stop train movement during a protest in Bhopal, India, Saturday, Dec. 3, 2011. Thousands of survivors of the world’s worst industrial accident blocked trains through a central Indian city on Saturday to demand more compensation.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict58.jpg) Female Iranian demonstrators hold posters showing supreme leader Ayatollah Ali Khamenei, left in the posters, and late revolutionary founder Ayatollah Khomeini, during a demonstration to welcome Iranian diplomats expelled from London in retaliation for attacks on British compounds in Tehran, at the Mehrabad airport in Tehran, Iran, early Saturday, Dec. 3, 2011.
Female Iranian demonstrators hold posters showing supreme leader Ayatollah Ali Khamenei, left in the posters, and late revolutionary founder Ayatollah Khomeini, during a demonstration to welcome Iranian diplomats expelled from London in retaliation for attacks on British compounds in Tehran, at the Mehrabad airport in Tehran, Iran, early Saturday, Dec. 3, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict59.jpg) Students are arrested during a protest against the government to demand changes in the public state education system in Santiago, December 2, 2011. Chilean students have been protesting against what they say is profiteering in the state education system. Reuters
Students are arrested during a protest against the government to demand changes in the public state education system in Santiago, December 2, 2011. Chilean students have been protesting against what they say is profiteering in the state education system. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict41.jpg) Demonstrators walk on a protest march in central London November 30, 2011. Teachers, nurses and border guards walked out on Wednesday as up to two million state workers staged Britain’s first mass strike for more than 30 years in a growing confrontation with a deficit-cutting coalition government. Reuters
Demonstrators walk on a protest march in central London November 30, 2011. Teachers, nurses and border guards walked out on Wednesday as up to two million state workers staged Britain’s first mass strike for more than 30 years in a growing confrontation with a deficit-cutting coalition government. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict31.jpg) Thousands of Bulgarians gather in front of the Bulgarian parliament to protest against government austerity measures in Sofia, Wednesday, Nov 30, 2011. Thousands joined a mass rally on Wednesday to protest government-proposed austerity measures that include raising the retirement age by one year. (Valentina Petrova)
Thousands of Bulgarians gather in front of the Bulgarian parliament to protest against government austerity measures in Sofia, Wednesday, Nov 30, 2011. Thousands joined a mass rally on Wednesday to protest government-proposed austerity measures that include raising the retirement age by one year. (Valentina Petrova)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict36.jpg) Activists of Ukrainian women movement FEMEN hold placards reading ‘EURO-2012 without prostitution’, ‘UEFA attacked our gates’ and others during a protest in front of the Olimpisky Stadium in Kie, a few hours prior the UEFA EURO-2012 Final Draw ceremony on December 2, 2011. Getty
Activists of Ukrainian women movement FEMEN hold placards reading ‘EURO-2012 without prostitution’, ‘UEFA attacked our gates’ and others during a protest in front of the Olimpisky Stadium in Kie, a few hours prior the UEFA EURO-2012 Final Draw ceremony on December 2, 2011. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict33.jpg) Hundreds of workers on strike block the entrance gate of Hi-P International factory during a protest in a suburban area of Shanghai December 2, 2011. More than 200 workers at a Singapore-owned electronics plant in the commercial hub of Shanghai went on strike for a third day on Friday to protest against planned layoffs, the latest sign of labour unrest in the world’s second-largest economy. Reuters
Hundreds of workers on strike block the entrance gate of Hi-P International factory during a protest in a suburban area of Shanghai December 2, 2011. More than 200 workers at a Singapore-owned electronics plant in the commercial hub of Shanghai went on strike for a third day on Friday to protest against planned layoffs, the latest sign of labour unrest in the world’s second-largest economy. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict28.jpg) A police officer detains a topless woman protesting against alleged attempts to legalize prostitution during the Euro 2012 in Ukraine prior to the final draw for the Euro 2012 soccer tournament in Kiev, Ukraine, Friday, Dec. 2, 2011. Ukrainian women’s rights activists staged a topless demonstration at Kiev’s Olympic Stadium to protest what they say are attempts to legalize prostitution during the 2012 European Championship. (Ferdinand Ostrop)
A police officer detains a topless woman protesting against alleged attempts to legalize prostitution during the Euro 2012 in Ukraine prior to the final draw for the Euro 2012 soccer tournament in Kiev, Ukraine, Friday, Dec. 2, 2011. Ukrainian women’s rights activists staged a topless demonstration at Kiev’s Olympic Stadium to protest what they say are attempts to legalize prostitution during the 2012 European Championship. (Ferdinand Ostrop)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict1.jpg) Survivors of the Bhopal gas tragedy, the world’s worst industrial disaster in India, along with other supporters shout slogans during a protest against a sponsorship deal with Dow Chemicals for the 2012 Olympics, in Bhopal, India, Friday, Dec. 2, 2011. Friday’s protests come on the eve of the 27th anniversary of a lethal gas leak from a Union Carbide pesticide plant in Bhopal where an estimated 15,000 people died and tens of thousands were maimed in 1984.
Survivors of the Bhopal gas tragedy, the world’s worst industrial disaster in India, along with other supporters shout slogans during a protest against a sponsorship deal with Dow Chemicals for the 2012 Olympics, in Bhopal, India, Friday, Dec. 2, 2011. Friday’s protests come on the eve of the 27th anniversary of a lethal gas leak from a Union Carbide pesticide plant in Bhopal where an estimated 15,000 people died and tens of thousands were maimed in 1984.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict39.jpg) Iranian dissidents hold banners as they protest in Brussels, Thursday, Dec. 1, 2011. The protesters called for prevention of compulsory displacement of the Camp Ashraf residents inside Iraq and the annulment of the deadline for closure of Camp Ashraf by the end of December. Camp Ashraf, an enclave in eastern Iraq that houses more than 3,000 people, many of whom are dedicated to overthrowing the government of Iran.
Iranian dissidents hold banners as they protest in Brussels, Thursday, Dec. 1, 2011. The protesters called for prevention of compulsory displacement of the Camp Ashraf residents inside Iraq and the annulment of the deadline for closure of Camp Ashraf by the end of December. Camp Ashraf, an enclave in eastern Iraq that houses more than 3,000 people, many of whom are dedicated to overthrowing the government of Iran.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict38.jpg) Afghan girls hold placards during a demonstration in Kabul December 1, 2011. Hundreds of Afghans from the Solidarity Party of Afghanistan took to the streets of Kabul on Thursday to protest against plans for a long-term partnership deal with the United States. Reuters
Afghan girls hold placards during a demonstration in Kabul December 1, 2011. Hundreds of Afghans from the Solidarity Party of Afghanistan took to the streets of Kabul on Thursday to protest against plans for a long-term partnership deal with the United States. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict34.jpg) A woman disguised as muppet character Miss Piggy takes a mud bath in front of the House of Representatives in The Hague on December 1, 2011 during a protest with Dutch environmental organization Milieudefensie against the expansion of livestock farming. Getty
A woman disguised as muppet character Miss Piggy takes a mud bath in front of the House of Representatives in The Hague on December 1, 2011 during a protest with Dutch environmental organization Milieudefensie against the expansion of livestock farming. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict25.jpg) A protester is detained by police during a march demanding education reform in Santiago, Chile, Thursday, Dec. 1, 2011. Chilean students clashed with police on Thursday during a protest demanding more funding for public education, while students in Colombia and Argentina also took to the streets in simultaneous demonstrations.(Luis Hidalgo)
A protester is detained by police during a march demanding education reform in Santiago, Chile, Thursday, Dec. 1, 2011. Chilean students clashed with police on Thursday during a protest demanding more funding for public education, while students in Colombia and Argentina also took to the streets in simultaneous demonstrations.(Luis Hidalgo)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict27.jpg) Protesters shout anti-austerity slogans during a 24-hour general strike in Athens on Thursday, Dec. 1, 2011. Thousands of protesters bitterly opposed to government austerity measures marched through the Greek capital Thursday, as another general strike closed schools and public services, left hospitals functioning on reduced staff and confined ferries to port. (Petros Giannakouris)
Protesters shout anti-austerity slogans during a 24-hour general strike in Athens on Thursday, Dec. 1, 2011. Thousands of protesters bitterly opposed to government austerity measures marched through the Greek capital Thursday, as another general strike closed schools and public services, left hospitals functioning on reduced staff and confined ferries to port. (Petros Giannakouris)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict29.jpg) An Occupy Raleigh protester shouts during a speech by John Stumpf, the CEO and president of Wells Fargo, on Wednesday, Nov. 30, 2011, in Raleigh, N.C. Stumpf was about 30 minutes into his speech when protesters interrupted him as he talked about the importance of small business. (Chuck Liddy)
An Occupy Raleigh protester shouts during a speech by John Stumpf, the CEO and president of Wells Fargo, on Wednesday, Nov. 30, 2011, in Raleigh, N.C. Stumpf was about 30 minutes into his speech when protesters interrupted him as he talked about the importance of small business. (Chuck Liddy)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict30.jpg) A protester from Portland, Maine, warms her hand with her breath while eating a sandwich at the Occupy Boston encampment, in Boston on Wednesday, Nov. 30, 2011. In the past few weeks police broke up encampments in Portland, Ore., Oakland, Calif., and New York, where the sit-down protests against social inequality and corporate excesses began in mid-September. Protesters remain in place in Boston and Washington, which each had camps of about 100 tents Wednesday. (Steven Senne)
A protester from Portland, Maine, warms her hand with her breath while eating a sandwich at the Occupy Boston encampment, in Boston on Wednesday, Nov. 30, 2011. In the past few weeks police broke up encampments in Portland, Ore., Oakland, Calif., and New York, where the sit-down protests against social inequality and corporate excesses began in mid-September. Protesters remain in place in Boston and Washington, which each had camps of about 100 tents Wednesday. (Steven Senne)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict40.jpg) A woman is led away in handcuffs by police after being removed from Panton House in central London November 30, 2011. Demonstrators broke into an office building used by mining company Xstrata in central London on Wednesday and hung protest banners on the roof before police regained control of the building. A group of about 60 from the “Occupy” movement entered the offices in Haymarket in protest at the pay of the company’s chief executive, Occupy said in a statement. Reuters
A woman is led away in handcuffs by police after being removed from Panton House in central London November 30, 2011. Demonstrators broke into an office building used by mining company Xstrata in central London on Wednesday and hung protest banners on the roof before police regained control of the building. A group of about 60 from the “Occupy” movement entered the offices in Haymarket in protest at the pay of the company’s chief executive, Occupy said in a statement. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict24.jpg) A female protestor displays her hands with Yemen’s flag and writing Arabic that reads,”you will prosecuted,” during a demonstration demanding the prosecution of Yemen’s President Ali Abdullah Saleh in Sanaa, Yemen, Tuesday, Nov. 29, 2011. Hundreds of thousands of Yemenis are demonstrating across the country to demand President Ali Abdullah Saleh face trial for charges ranging from corruption to deadly crackdowns on protests. (Hani Mohammed)
A female protestor displays her hands with Yemen’s flag and writing Arabic that reads,”you will prosecuted,” during a demonstration demanding the prosecution of Yemen’s President Ali Abdullah Saleh in Sanaa, Yemen, Tuesday, Nov. 29, 2011. Hundreds of thousands of Yemenis are demonstrating across the country to demand President Ali Abdullah Saleh face trial for charges ranging from corruption to deadly crackdowns on protests. (Hani Mohammed)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict19.jpg) Supporters of Sri Lanka’s main opposition United National Party (UNP) protest in Colombo on November 29, 2011. They were protesting the jailing of the former army chief Darath Fonseka, a business take over bill and the government’s 2012 budget proposals. Getty
Supporters of Sri Lanka’s main opposition United National Party (UNP) protest in Colombo on November 29, 2011. They were protesting the jailing of the former army chief Darath Fonseka, a business take over bill and the government’s 2012 budget proposals. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict21.jpg) Members of India’s National Domestic Workers Movement from the southern state of Andhra Pradesh (AP) region are watched by co-ordinator Sister Mea Yaragani (2L) as they sign a sheet while participating in a protest meet and signature campaign in Hyderabad on November 29, 2011. The protesors are demanding the ratification of the 189th International Labour Organization (ILO) convention by the Indian government and their inclusion in the Sexual Harassment Bill 2010. There are between 120000-150000 domestic workers in the state. Getty
Members of India’s National Domestic Workers Movement from the southern state of Andhra Pradesh (AP) region are watched by co-ordinator Sister Mea Yaragani (2L) as they sign a sheet while participating in a protest meet and signature campaign in Hyderabad on November 29, 2011. The protesors are demanding the ratification of the 189th International Labour Organization (ILO) convention by the Indian government and their inclusion in the Sexual Harassment Bill 2010. There are between 120000-150000 domestic workers in the state. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict23.jpg) Workers protest as they shout slogans demanding higher wages in front of Indonesia’s presidential palace in Jakarta, November 29, 2011. Indonesia has been hit by a series of strikes in recent months and is expected to see more labour disputes, as workers demanded a greater share of profits in one of Asia’s fastest growing economies. Reuters
Workers protest as they shout slogans demanding higher wages in front of Indonesia’s presidential palace in Jakarta, November 29, 2011. Indonesia has been hit by a series of strikes in recent months and is expected to see more labour disputes, as workers demanded a greater share of profits in one of Asia’s fastest growing economies. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict20.jpg) Miss Water South Africa Kirsten Dukes poses in front of a banner during a protest by environmental activists outside the United Nations Framework Convention on Climate Change Conference of the Parties meeting (COP17) in Durban, November 29, 2011. The gathering runs until December 9. Reuters
Miss Water South Africa Kirsten Dukes poses in front of a banner during a protest by environmental activists outside the United Nations Framework Convention on Climate Change Conference of the Parties meeting (COP17) in Durban, November 29, 2011. The gathering runs until December 9. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict18.jpg) Student, wearing niqabs, protest on November 29, 2011 in the building housing the office of the dean of the Faculty of Arts at the University of Manuba, 25 kms west of Tunis. Several hundred people gathered at the university to demand the right for female students to wear full face veils in class and pass exams. A group of Salafists disrupted classes on November 28 at the university, demanding a stop to mixed-sex classes and for female students to wear full face veils. Getty
Student, wearing niqabs, protest on November 29, 2011 in the building housing the office of the dean of the Faculty of Arts at the University of Manuba, 25 kms west of Tunis. Several hundred people gathered at the university to demand the right for female students to wear full face veils in class and pass exams. A group of Salafists disrupted classes on November 28 at the university, demanding a stop to mixed-sex classes and for female students to wear full face veils. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict17.jpg) Workers take part in a rally during a protest against government austerity measures organized by the PAME Communist-affiliated union in central Athens Tuesday, Nov. 29, 2011. The 17 finance ministers of the countries that use the euro converged on EU headquarters Tuesday in a desperate bid to save their currency – and to protect Europe, the United States, Asia and the rest of the global economy from a debt-induced financial tsunami. AP
Workers take part in a rally during a protest against government austerity measures organized by the PAME Communist-affiliated union in central Athens Tuesday, Nov. 29, 2011. The 17 finance ministers of the countries that use the euro converged on EU headquarters Tuesday in a desperate bid to save their currency – and to protect Europe, the United States, Asia and the rest of the global economy from a debt-induced financial tsunami. AP![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict16.jpg) Supporters of Pakistan Tehreek-i-Insaf (Pakistan’s Movement for Justice) pray after a demonstration against NATO cross-border attack in Lahore November 29, 2011. Pakistan’s government confirmed it would not attend an international conference on the future of Afghanistan in Bonn next week to protest against a NATO cross-border attack that killed two dozen Pakistani soldiers. Reuters
Supporters of Pakistan Tehreek-i-Insaf (Pakistan’s Movement for Justice) pray after a demonstration against NATO cross-border attack in Lahore November 29, 2011. Pakistan’s government confirmed it would not attend an international conference on the future of Afghanistan in Bonn next week to protest against a NATO cross-border attack that killed two dozen Pakistani soldiers. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict15.jpg) Riot police detain two students inside the national congress during a protest against the government to demand changes in the public state education system in Valparaiso city, about 121 km (75 miles) northwest of Santiago, November 29, 2011. Chilean students have been protesting against what they say is the profiteering in the state education system. Reuters
Riot police detain two students inside the national congress during a protest against the government to demand changes in the public state education system in Valparaiso city, about 121 km (75 miles) northwest of Santiago, November 29, 2011. Chilean students have been protesting against what they say is the profiteering in the state education system. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict2.jpg) Pakistani protesters rally to condemn NATO strikes on Pakistani soldiers, in Lahore, Pakistan, Tuesday, Nov. 29, 2011. Pakistan pulled out of an upcoming meeting in Germany on the future of Afghanistan to protest the deadly attack by U.S.-led forces on its troops, widening the fallout on Tuesday from an incident that has sent ties between Washington and Islamabad into a tailspin. Placard at right reads “run NATO and wake Pakistan army”. (K.M. Chaudary)
Pakistani protesters rally to condemn NATO strikes on Pakistani soldiers, in Lahore, Pakistan, Tuesday, Nov. 29, 2011. Pakistan pulled out of an upcoming meeting in Germany on the future of Afghanistan to protest the deadly attack by U.S.-led forces on its troops, widening the fallout on Tuesday from an incident that has sent ties between Washington and Islamabad into a tailspin. Placard at right reads “run NATO and wake Pakistan army”. (K.M. Chaudary)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict3.jpg) A demonstrator holds a sign that reads in Portuguese: “The fight on the forest starts in the streets”, during a protest against the approval of the new Brazilian forest code in Brasilia, Brazil, Tuesday, Nov. 29, 2011. Brazil’s lower house in May approved changes to the law that would ease environmental restrictions in the Amazon and other regions in Brazil. Brazil’s Senate is expected to approve the measure this week, though President Dilma Rousseff has promised to veto some parts of the bill.
A demonstrator holds a sign that reads in Portuguese: “The fight on the forest starts in the streets”, during a protest against the approval of the new Brazilian forest code in Brasilia, Brazil, Tuesday, Nov. 29, 2011. Brazil’s lower house in May approved changes to the law that would ease environmental restrictions in the Amazon and other regions in Brazil. Brazil’s Senate is expected to approve the measure this week, though President Dilma Rousseff has promised to veto some parts of the bill.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict4.jpg) Female Iranian protesters attend a demonstration in front of the British Embassy, as one of them holds a poster of supreme leader Ayatollah Ali Khamenei, in Tehran, Iran, Tuesday, Nov. 29, 2011. Dozens of hard-line Iranian students stormed the British Embassy in Tehran on Tuesday, bringing down the Union Jack flag and throwing documents from windows in scenes reminiscent of the anger against Western powers after the 1979 Islamic Revolution.
Female Iranian protesters attend a demonstration in front of the British Embassy, as one of them holds a poster of supreme leader Ayatollah Ali Khamenei, in Tehran, Iran, Tuesday, Nov. 29, 2011. Dozens of hard-line Iranian students stormed the British Embassy in Tehran on Tuesday, bringing down the Union Jack flag and throwing documents from windows in scenes reminiscent of the anger against Western powers after the 1979 Islamic Revolution.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict5.jpg) An elderly protestor flashes the victory sign during a demonstration demanding the prosecution of Yemen’s President Ali Abdullah Saleh in Sanaa, Yemen, Tuesday, Nov. 29, 2011. Hundreds of thousands of Yemenis are demonstrating across the country to demand President Ali Abdullah Saleh face trial for charges ranging from corruption to deadly crackdowns on protests. (Hani Mohammed)
An elderly protestor flashes the victory sign during a demonstration demanding the prosecution of Yemen’s President Ali Abdullah Saleh in Sanaa, Yemen, Tuesday, Nov. 29, 2011. Hundreds of thousands of Yemenis are demonstrating across the country to demand President Ali Abdullah Saleh face trial for charges ranging from corruption to deadly crackdowns on protests. (Hani Mohammed)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict6.jpg) Mariachi musicians perform as Greenpeace activists demand Brazil’s President Dilma Rousseff protect the Amazon as they protest outside Brazil’s embassy in Mexico City, Tuesday Nov. 29, 2011. Brazil’s government has authorized the construction of one the world’s largest hydroelectric dams, the Belo Monte dam, in the state of Para, and the federal prosecutors’ office in Para has said they will go to the Supreme Court to appeal the ruling.
Mariachi musicians perform as Greenpeace activists demand Brazil’s President Dilma Rousseff protect the Amazon as they protest outside Brazil’s embassy in Mexico City, Tuesday Nov. 29, 2011. Brazil’s government has authorized the construction of one the world’s largest hydroelectric dams, the Belo Monte dam, in the state of Para, and the federal prosecutors’ office in Para has said they will go to the Supreme Court to appeal the ruling.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict7.jpg) Malaysian lawyers hold placards as they shout slogans during a protest in Kuala Lumpur, Malaysia, Tuesday, Nov. 29, 2011. Hundreds of Malaysian lawyers staged a rare protest march Tuesday demanding that the government abandon plans for a law that will forbid street rallies. (Lai Seng Sin)
Malaysian lawyers hold placards as they shout slogans during a protest in Kuala Lumpur, Malaysia, Tuesday, Nov. 29, 2011. Hundreds of Malaysian lawyers staged a rare protest march Tuesday demanding that the government abandon plans for a law that will forbid street rallies. (Lai Seng Sin)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict9.jpg) Protesters shout slogans as they hold candles with placards reading “Invalidity, FTA between South Korea and the U.S.” during a candle rally, denouncing the passing of a bill on ratification of a South Korea-U.S. free trade agreement in Seoul, South Korea, Tuesday, Nov. 29, 2011. South Korea’s president on Tuesday signed a slew of laws needed to implement the country’s free trade deal with the United States, amid growing protests denouncing the accord at home. (Lee Jin-man)
Protesters shout slogans as they hold candles with placards reading “Invalidity, FTA between South Korea and the U.S.” during a candle rally, denouncing the passing of a bill on ratification of a South Korea-U.S. free trade agreement in Seoul, South Korea, Tuesday, Nov. 29, 2011. South Korea’s president on Tuesday signed a slew of laws needed to implement the country’s free trade deal with the United States, amid growing protests denouncing the accord at home. (Lee Jin-man)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict10.jpg) UCLA students walk past a line of demonstrators lying on the Quad outside a meeting of the Board of Regents at the University of California, on the campus at UCLA in Los Angeles, Monday, Nov. 28, 2011. The regents were originally scheduled to meet in mid-November at the San Francisco-Mission Bay campus, but the session was scrapped when law enforcement warned that protests could turn violent. (Reed Saxon)
UCLA students walk past a line of demonstrators lying on the Quad outside a meeting of the Board of Regents at the University of California, on the campus at UCLA in Los Angeles, Monday, Nov. 28, 2011. The regents were originally scheduled to meet in mid-November at the San Francisco-Mission Bay campus, but the session was scrapped when law enforcement warned that protests could turn violent. (Reed Saxon)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict14.jpg) Supporters of Progressive Organization of Women raise slogans during a protest rally in New Delhi, India, Monday, Nov. 28, 2011. The protesters demanded introduction of a bill in the ongoing session of parliament for a separate statehood of Telangana region from the existing Andhra Pradesh state in southern India. (Gurinder Osan)
Supporters of Progressive Organization of Women raise slogans during a protest rally in New Delhi, India, Monday, Nov. 28, 2011. The protesters demanded introduction of a bill in the ongoing session of parliament for a separate statehood of Telangana region from the existing Andhra Pradesh state in southern India. (Gurinder Osan)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict12.jpg) Police officers stand during a demonstration by security forces in Tunis, Monday, Nov.28, 2011. Security forces are protesting against police officers sued on trial for their alleged role in the revolution. On armband reads: “Stop, break the silence”. (Hassene Dridi)
Police officers stand during a demonstration by security forces in Tunis, Monday, Nov.28, 2011. Security forces are protesting against police officers sued on trial for their alleged role in the revolution. On armband reads: “Stop, break the silence”. (Hassene Dridi)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict11.jpg) Members of Occupy Philly, from right to left, Shawn Grant, Brianne Murphy, and Diane Isser, demonstrate at Dilworth Plaza, in Philadelphia, on Sunday Nov. 27, 2011, in defiance of the city’s 5 p.m. eviction order. (Joseph Kaczmarek)
Members of Occupy Philly, from right to left, Shawn Grant, Brianne Murphy, and Diane Isser, demonstrate at Dilworth Plaza, in Philadelphia, on Sunday Nov. 27, 2011, in defiance of the city’s 5 p.m. eviction order. (Joseph Kaczmarek)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict13.jpg) A member of Occupy Philly who identified herself as Laura watches the demonstration at Dilworth Plaza, in Philadelphia, Sunday Nov. 27, 2011, held in defiance of the city’s 5 p.m. eviction order. (Joseph Kaczmarek)
A member of Occupy Philly who identified herself as Laura watches the demonstration at Dilworth Plaza, in Philadelphia, Sunday Nov. 27, 2011, held in defiance of the city’s 5 p.m. eviction order. (Joseph Kaczmarek)

![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict80.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict69.jpg) Russian nationalists hold a banner reads as “All for one and one for all” and wave old Russian imperial flags during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)
Russian nationalists hold a banner reads as “All for one and one for all” and wave old Russian imperial flags during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict70.jpg) Russian nationalists rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)
Russian nationalists rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict68.jpg) Russian nationalists shout holding old Russian imperial flags during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)
Russian nationalists shout holding old Russian imperial flags during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict78.jpg) A young masked Russian nationalist holds a banner in front of a police officer during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)
A young masked Russian nationalist holds a banner in front of a police officer during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict76.jpg) Russian police troops patrol near closed Red Square, with St. Basil Cathedral at the background, in Moscow, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Misha Japaridze)
Russian police troops patrol near closed Red Square, with St. Basil Cathedral at the background, in Moscow, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Misha Japaridze)
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict77.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict64.jpg) In this photo taken Saturday, Dec. 10, 2011, protesters gather to protest near the Kremlin, background, against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia. Tens of thousands of people held the largest anti-government protests that post-Soviet Russia has ever seen to criticize electoral fraud and demand an end to Vladimir Putin’s rule. (Dmitriy Chistoprudov)
In this photo taken Saturday, Dec. 10, 2011, protesters gather to protest near the Kremlin, background, against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia. Tens of thousands of people held the largest anti-government protests that post-Soviet Russia has ever seen to criticize electoral fraud and demand an end to Vladimir Putin’s rule. (Dmitriy Chistoprudov)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict65.jpg) In this photo taken Saturday, Dec. 10, 2011, protesters gather to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia. Tens of thousands of people held the largest anti-government protests that post-Soviet Russia has ever seen to criticize electoral fraud and demand an end to Vladimir Putin’s rule. (Dmitriy Chistoprudov)
In this photo taken Saturday, Dec. 10, 2011, protesters gather to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia. Tens of thousands of people held the largest anti-government protests that post-Soviet Russia has ever seen to criticize electoral fraud and demand an end to Vladimir Putin’s rule. (Dmitriy Chistoprudov)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict38.jpg) Police cars and trucks block a square where demonstrators gather together during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.
Police cars and trucks block a square where demonstrators gather together during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict27.jpg) Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin)
Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict26.jpg) Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr)
Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict45.jpg) Protesters hold a red banner reads as “Rot Front” shouting anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011, with the Kremlin is the background. Russians angered by allegedly fraudulent parliamentary elections and the country’s ruling party took part in protests Saturday in cities from the freezing Pacific Coast to the southwest, eight time zones away.
Protesters hold a red banner reads as “Rot Front” shouting anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011, with the Kremlin is the background. Russians angered by allegedly fraudulent parliamentary elections and the country’s ruling party took part in protests Saturday in cities from the freezing Pacific Coast to the southwest, eight time zones away.![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict44.jpg) A protester holds an old Russian flag with the words “We are Russians, God with us” and shows a V-sing during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011, with the Kremlin is the background. Russians angered by allegedly fraudulent parliamentary elections and the country’s ruling party took part in protests Saturday in cities from the freezing Pacific Coast to the southwest, eight time zones away.
A protester holds an old Russian flag with the words “We are Russians, God with us” and shows a V-sing during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011, with the Kremlin is the background. Russians angered by allegedly fraudulent parliamentary elections and the country’s ruling party took part in protests Saturday in cities from the freezing Pacific Coast to the southwest, eight time zones away.![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict24.jpg) Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr)
Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict40.jpg) People stand on the bridge as they attend a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. The banner on the bridge reads: “Crooks Give Us the Election Back.”
People stand on the bridge as they attend a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. The banner on the bridge reads: “Crooks Give Us the Election Back.”![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict29.jpg) Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko)
Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict25.jpg) Protesters shout anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr)
Protesters shout anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict41.jpg) Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)
Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict34.jpg) Protesters light flares during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin)
Protesters light flares during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict48.jpg) Demonstrators stand in front of police line during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)
Demonstrators stand in front of police line during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict43.jpg) Opposition leader Edouard Limonov shouts anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.
Opposition leader Edouard Limonov shouts anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict50.jpg) An elderly demonstrator holds a poster showing an edited photo of Prime Minister Vladimir Putin and signed “2050. No” during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.
An elderly demonstrator holds a poster showing an edited photo of Prime Minister Vladimir Putin and signed “2050. No” during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict47.jpg) Protesters listen to an orator during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.(Alexander Zemlianichenko Jr)
Protesters listen to an orator during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.(Alexander Zemlianichenko Jr)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict36.jpg) Protesters seen during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Sergey Ponomarev)
Protesters seen during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Sergey Ponomarev)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict35.jpg) Masked protesters seen during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin)
Masked protesters seen during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict32.jpg) A protester shouts slogans in front of police line during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)
A protester shouts slogans in front of police line during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict37.jpg) Protesters light flares holding an Old Russian flags during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Name)
Protesters light flares holding an Old Russian flags during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Name)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict39.jpg) Police guards the Red Square area during a mass protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Sergey Ponomarev)
Police guards the Red Square area during a mass protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Sergey Ponomarev)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict28.jpg) Police vehicles seen on a Zamoskvoretsky bridge during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.(Ivan Sekret)
Police vehicles seen on a Zamoskvoretsky bridge during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.(Ivan Sekret)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict75.jpg) Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. The poster reads: “One for all and all for one”. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky)
Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. The poster reads: “One for all and all for one”. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict72.jpg) Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky)
Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict23.jpg) In this photo taken with a fisheye lens protesters gather during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
In this photo taken with a fisheye lens protesters gather during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict42.jpg) Protesters shout slogans during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
Protesters shout slogans during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict46.jpg) A protester walks in smoke of a smoke bomb during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign [not shown] reads “Such election is a spit at people’s face”. More than 10,000 people have protested in St. Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers say was rigged. (Dmitry Lovetsky)
A protester walks in smoke of a smoke bomb during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign [not shown] reads “Such election is a spit at people’s face”. More than 10,000 people have protested in St. Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers say was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict49.jpg) A protester holds a badminton racket as he shouts slogans during a rally in St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than 10,000 people are protesting in St. Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers say was rigged. (Dmitry Lovetsky)
A protester holds a badminton racket as he shouts slogans during a rally in St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than 10,000 people are protesting in St. Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers say was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict30.jpg) An opposition activist fights with a police officer during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousand people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
An opposition activist fights with a police officer during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousand people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict31.jpg) Riot police detain a protester during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
Riot police detain a protester during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict33.jpg) Protesters seen during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
Protesters seen during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)




















 U.S. Espionage and Intelligence: Organization, Operations, and Management, 1947-1996 publishes together for the first time recent unclassified and newly declassified documents pertaining to the organizational structure, operations, and management of the U.S. intelligence community over the last fifty years, cross-indexed for maximum accessibility. This set reproduces on microfiche 1,174 organizational histories, memoranda, manuals, regulations, directives, reports, and studies, representing over 36,102 pages of documents from the Office of the Director of Central Intelligence, the Central Intelligence Agency, National Reconnaissance Office, National Security Agency, Defense Intelligence Agency, military service intelligence organizations, National Security Council and other organizations. U.S. Espionage and Intelligence presents a unique look into the internal workings of America’s intelligence community. The documents gathered here shed further light on U.S. intelligence organization and activities during the Cold War, and describe the consolidation and reevaluation of the intelligence community in the post-Cold War era. They are drawn from diverse sources, including the National Archives, manuscript collections in the Library of Congress, court files of major espionage prosecutions, presidential libraries, and most importantly, Freedom of Information Act requests. The result of this effort is an authoritative documents publication which, together with the National Security Archive’s previous collection on the structure and operations of the U.S. intelligence community,
U.S. Espionage and Intelligence: Organization, Operations, and Management, 1947-1996 publishes together for the first time recent unclassified and newly declassified documents pertaining to the organizational structure, operations, and management of the U.S. intelligence community over the last fifty years, cross-indexed for maximum accessibility. This set reproduces on microfiche 1,174 organizational histories, memoranda, manuals, regulations, directives, reports, and studies, representing over 36,102 pages of documents from the Office of the Director of Central Intelligence, the Central Intelligence Agency, National Reconnaissance Office, National Security Agency, Defense Intelligence Agency, military service intelligence organizations, National Security Council and other organizations. U.S. Espionage and Intelligence presents a unique look into the internal workings of America’s intelligence community. The documents gathered here shed further light on U.S. intelligence organization and activities during the Cold War, and describe the consolidation and reevaluation of the intelligence community in the post-Cold War era. They are drawn from diverse sources, including the National Archives, manuscript collections in the Library of Congress, court files of major espionage prosecutions, presidential libraries, and most importantly, Freedom of Information Act requests. The result of this effort is an authoritative documents publication which, together with the National Security Archive’s previous collection on the structure and operations of the U.S. intelligence community,


















![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/isp-spy/ga-tech-spy/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/isp-spy/ga-tech-spy/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/isp-spy/ga-tech-spy/pict1.jpg)










































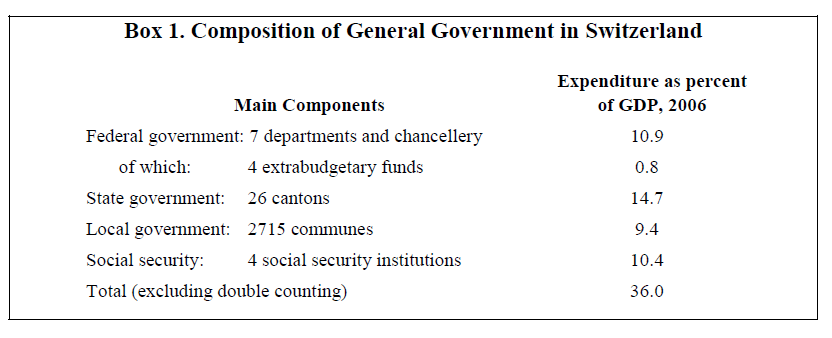











































![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict16.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict21.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict23.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict30.jpg) These gents appear leery of being photographed, and rightly so, due to persistent infiltration and photography by cops. Or could be undercover cops.
These gents appear leery of being photographed, and rightly so, due to persistent infiltration and photography by cops. Or could be undercover cops.
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict33.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict34.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict18.jpg) Supporters of Bharatiya Mazdoor Sangh, or Indian Workers Group, raise slogans at a protest rally in New Delhi, India, Wednesday, Nov. 23, 2011. The supporters demanded that the government protect workers rights in the ongoing economic reform process as well as the financial crisis. (Gurinder Osan)
Supporters of Bharatiya Mazdoor Sangh, or Indian Workers Group, raise slogans at a protest rally in New Delhi, India, Wednesday, Nov. 23, 2011. The supporters demanded that the government protect workers rights in the ongoing economic reform process as well as the financial crisis. (Gurinder Osan)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict26.jpg) Yemenis protest against President Ali Abdullah Saleh during a rally after the weekly Friday noon prayers in Sanaa on November 25, 2011. Opponents and supporters of Yemen’s embattled president held rival rallies in the capital after pre-dawn fighting between rival security forces dashed hopes an exit deal for the president would end the violence. Getty
Yemenis protest against President Ali Abdullah Saleh during a rally after the weekly Friday noon prayers in Sanaa on November 25, 2011. Opponents and supporters of Yemen’s embattled president held rival rallies in the capital after pre-dawn fighting between rival security forces dashed hopes an exit deal for the president would end the violence. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict27.jpg) Women perform prayers at the Taghyeer (Change) Square, where anti-government protesters have been camping for around ten months to call for the ouster and trial of Yemen’s President Ali Abdullah Saleh, in Sanaa November 27, 2011. Reuters
Women perform prayers at the Taghyeer (Change) Square, where anti-government protesters have been camping for around ten months to call for the ouster and trial of Yemen’s President Ali Abdullah Saleh, in Sanaa November 27, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict28.jpg) Yemeni women and anti-government protesters shout slogans during a demonstration demanding the trial of Yemeni President Ali Abdullah Saleh in Sanaa on November 26, 2011. Getty
Yemeni women and anti-government protesters shout slogans during a demonstration demanding the trial of Yemeni President Ali Abdullah Saleh in Sanaa on November 26, 2011. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict3.jpg) Demonstrators gather during protests against a nuclear waste transport in Dannenberg, northern Germany, Saturday Nov. 26, 2011. The shipment of nuclear waste reprocessed in France is on its way to a controversial storage site in Gorleben that protesters say is unsafe. It is the first such shipment from France to Germany since Berlin decided to shut all its nuclear plants by 2022, following the disaster at Japan’s Fukushima plant. The transport is due to arrive at the storage site on Sunday.
Demonstrators gather during protests against a nuclear waste transport in Dannenberg, northern Germany, Saturday Nov. 26, 2011. The shipment of nuclear waste reprocessed in France is on its way to a controversial storage site in Gorleben that protesters say is unsafe. It is the first such shipment from France to Germany since Berlin decided to shut all its nuclear plants by 2022, following the disaster at Japan’s Fukushima plant. The transport is due to arrive at the storage site on Sunday.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict31.jpg) A demonstrator dressed as a clown stands between police officers during protests against a shipment of nuclear waste to the storage facility in Gorleben, in Hitzacker, northern Germany Sunday Nov. 27, 2011. (Axel Heimken)
A demonstrator dressed as a clown stands between police officers during protests against a shipment of nuclear waste to the storage facility in Gorleben, in Hitzacker, northern Germany Sunday Nov. 27, 2011. (Axel Heimken)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict29.jpg) People demonstrate during a protest against violence in Mexico City, Sunday, Nov. 27, 2011. Demonstrators wore skull masks or painted their faces as skulls to symbolize the victims of violence in Mexico. Over 50,000 people have died since Mexican President Felipe Calderon launched his offensive against organized crime in 2006. (Marco Ugarte)
People demonstrate during a protest against violence in Mexico City, Sunday, Nov. 27, 2011. Demonstrators wore skull masks or painted their faces as skulls to symbolize the victims of violence in Mexico. Over 50,000 people have died since Mexican President Felipe Calderon launched his offensive against organized crime in 2006. (Marco Ugarte)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict21.jpg) Libyan Amazigh Berbers protest outside the prime minister’s office in Tripoli on November 27, 2011 as they step up pressure for the minority group to to be represented in the government. Getty
Libyan Amazigh Berbers protest outside the prime minister’s office in Tripoli on November 27, 2011 as they step up pressure for the minority group to to be represented in the government. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict1.jpg) Environment activists Hanna Schwarz, right, and Heiko Mueller-Ripke, have chained themselves inside a pyramid with concrete inside, they claim, on the tracks near Hitzacker, Sunday Nov. 27, 2011. Police has difficulties for hours, to unchain the protesters without injuring them. The activists protest against a nuclear waste transport from France to a storage in Gorleben. (Axel Heimken)
Environment activists Hanna Schwarz, right, and Heiko Mueller-Ripke, have chained themselves inside a pyramid with concrete inside, they claim, on the tracks near Hitzacker, Sunday Nov. 27, 2011. Police has difficulties for hours, to unchain the protesters without injuring them. The activists protest against a nuclear waste transport from France to a storage in Gorleben. (Axel Heimken)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict23.jpg) Members of the Ethiopian community block the entrance to Israel’s Ministry of Immigrant Absorption during a protest in Jerusalem November 27, 2011. About 400 Israelis of Ethiopian descent took part in the protest on Sunday calling on the government to grant permission for their relatives living in Ethiopia to immigrate. Reuters
Members of the Ethiopian community block the entrance to Israel’s Ministry of Immigrant Absorption during a protest in Jerusalem November 27, 2011. About 400 Israelis of Ethiopian descent took part in the protest on Sunday calling on the government to grant permission for their relatives living in Ethiopia to immigrate. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict32.jpg) Demonstrators drum on barrels with a nuclear sign, during protests against a nuclear waste transport in Dannenberg, northern Germany, Saturday, Nov. 26, 2011. The shipment of nuclear waste reprocessed in France is on its way to a controversial storage site in Gorleben that protesters say is unsafe. It is the first such shipment from France to Germany since Berlin decided to shut all its nuclear plants by 2022, following the disaster at Japan’s Fukushima plant.
Demonstrators drum on barrels with a nuclear sign, during protests against a nuclear waste transport in Dannenberg, northern Germany, Saturday, Nov. 26, 2011. The shipment of nuclear waste reprocessed in France is on its way to a controversial storage site in Gorleben that protesters say is unsafe. It is the first such shipment from France to Germany since Berlin decided to shut all its nuclear plants by 2022, following the disaster at Japan’s Fukushima plant.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict22.jpg) Oxfam (a confederation of 15 organizations working together to find lasting solutions to poverty and injustice) activists make a protest aimed at 17th Conference of the Parties (COP17) under the UN Framework Convention on Climate Change (UNFCCC) in Durban on November 27, 2011. Inspired by the Occupy Wall St. movement, protesters calling for ‘climate justice’ are set to gather on November 28 at the opening of UN climate talks in Durban, South Africa, organisers say. Getty
Oxfam (a confederation of 15 organizations working together to find lasting solutions to poverty and injustice) activists make a protest aimed at 17th Conference of the Parties (COP17) under the UN Framework Convention on Climate Change (UNFCCC) in Durban on November 27, 2011. Inspired by the Occupy Wall St. movement, protesters calling for ‘climate justice’ are set to gather on November 28 at the opening of UN climate talks in Durban, South Africa, organisers say. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict2.jpg) In tihis picture taken Saturday Nov. 26, 2011 police carries an environment activist away from the tracks near Harlingen, northern Germany. German police say they cleared a sit-in of about 3,500 protesters attempting to block a shipment of nuclear waste with security forces temporarily detaining 1,300 of them. (Philipp Guelland)
In tihis picture taken Saturday Nov. 26, 2011 police carries an environment activist away from the tracks near Harlingen, northern Germany. German police say they cleared a sit-in of about 3,500 protesters attempting to block a shipment of nuclear waste with security forces temporarily detaining 1,300 of them. (Philipp Guelland)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict0.jpg) South Korean police say nearly 40 officers were injured during a rally opposing the ratification of the country’s free trade deal with the United States.Hundreds of protesters have been staging near-daily demonstrations since the ruling party railroaded the U.S. trade deal last week. The protesters believe the deal favors Washington over South Korean workers. About 2,200 people rallied in Seoul on Saturday evening, November 26, 2011.
South Korean police say nearly 40 officers were injured during a rally opposing the ratification of the country’s free trade deal with the United States.Hundreds of protesters have been staging near-daily demonstrations since the ruling party railroaded the U.S. trade deal last week. The protesters believe the deal favors Washington over South Korean workers. About 2,200 people rallied in Seoul on Saturday evening, November 26, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict24.jpg) Sarah Elbaroudy, age seven, from Long Island, stands during a collaborative protest between the Occupy Wall Street movement and people supporting the 2011 Egyptian Revolution and the current social unrest throughout Egypt, near the Egyptian Embassy to the United States, at the intersection of East 44th Street and Second Avenue, in New York, November 26, 2011. Reuters
Sarah Elbaroudy, age seven, from Long Island, stands during a collaborative protest between the Occupy Wall Street movement and people supporting the 2011 Egyptian Revolution and the current social unrest throughout Egypt, near the Egyptian Embassy to the United States, at the intersection of East 44th Street and Second Avenue, in New York, November 26, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict25.jpg) A woman dressed as the Grim Reaper attends a protest against shale gas exploration and production in Sofia on November 26, 2011. Bulgaria gave in July a licence to the United States energy major Chevron for the exploration of an area in the north-eastern part of Bulgaria. Getty
A woman dressed as the Grim Reaper attends a protest against shale gas exploration and production in Sofia on November 26, 2011. Bulgaria gave in July a licence to the United States energy major Chevron for the exploration of an area in the north-eastern part of Bulgaria. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict4.jpg) A young Romanian woman wearing make up to suggest she is a victim of domestic violence takes part in a protest in Bucharest, Romania, Friday, Nov. 25, 2011. Dozens of women gathered in protest on the International Day for the Elimination of Violence against Women demanding the introduction of the restraining order in Romanian legislation. Romania is a European Union member state but has no proper legal framework to combat domestic violence against women.
A young Romanian woman wearing make up to suggest she is a victim of domestic violence takes part in a protest in Bucharest, Romania, Friday, Nov. 25, 2011. Dozens of women gathered in protest on the International Day for the Elimination of Violence against Women demanding the introduction of the restraining order in Romanian legislation. Romania is a European Union member state but has no proper legal framework to combat domestic violence against women.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict5.jpg) Israelis covered in red color demonstrates as part of the International Anti-fur Coalition protest in Tel Aviv. Friday. Nov. 25, 2011. The demonstration was part of an international protest against fur trade.(Dan Balilty)
Israelis covered in red color demonstrates as part of the International Anti-fur Coalition protest in Tel Aviv. Friday. Nov. 25, 2011. The demonstration was part of an international protest against fur trade.(Dan Balilty)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict7.jpg) An Egyptian girl holds an anti-Israel banner during a protest at al Azhar mosque, the highest Islamic Sunni institution, after Friday prayers in Cairo, Egypt, Friday, Nov. 25, 2011. The Muslim brotherhood demonstration was to denounce Israeli control over Jerusalem’s Al Aqsa Mosque, one of the holiest sites in Islam. Arabic and Hebrew reads ” Death for Israel”. (Amr Nabil)
An Egyptian girl holds an anti-Israel banner during a protest at al Azhar mosque, the highest Islamic Sunni institution, after Friday prayers in Cairo, Egypt, Friday, Nov. 25, 2011. The Muslim brotherhood demonstration was to denounce Israeli control over Jerusalem’s Al Aqsa Mosque, one of the holiest sites in Islam. Arabic and Hebrew reads ” Death for Israel”. (Amr Nabil)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict6.jpg) An Egyptian woman holds up an infant during a rally in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011. Tens of thousands of protesters chanting, “Leave, leave!” filled Cairo’s Tahrir Square in a massive demonstration to force Egypt’s ruling military council to yield power. The Friday rally is dubbed by organizers as “The Last Chance Million-Man Protest,” and comes one day after the military offered an apology for the killing of nearly 40 protesters in clashes on side streets near Tahrir Square.
An Egyptian woman holds up an infant during a rally in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011. Tens of thousands of protesters chanting, “Leave, leave!” filled Cairo’s Tahrir Square in a massive demonstration to force Egypt’s ruling military council to yield power. The Friday rally is dubbed by organizers as “The Last Chance Million-Man Protest,” and comes one day after the military offered an apology for the killing of nearly 40 protesters in clashes on side streets near Tahrir Square.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict8.jpg) Filipino women activists stage a play to symbolize human rights violations during a demonstration to mark the International Day of Action on Violence Against Women near the Malacanang presidential palace in Manila, Philippines, Friday Nov. 25, 2011. The women’s group held the rally to raise public awareness and encourage continuing action to eliminate violence against women. (Aaron Favila)
Filipino women activists stage a play to symbolize human rights violations during a demonstration to mark the International Day of Action on Violence Against Women near the Malacanang presidential palace in Manila, Philippines, Friday Nov. 25, 2011. The women’s group held the rally to raise public awareness and encourage continuing action to eliminate violence against women. (Aaron Favila)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict9.jpg) Students march demanding an education reform in Bogota, Colombia, Thursday, Nov. 24, 2011. Protesters are demanding more funding and other changes to the public education system.(Fernando Vergara)
Students march demanding an education reform in Bogota, Colombia, Thursday, Nov. 24, 2011. Protesters are demanding more funding and other changes to the public education system.(Fernando Vergara)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict10.jpg) Protesters are hit with water from a police water canon during a march for education reform in Santiago, Chile, Thursday Nov. 24, 2011. Protesters have demanded more funding and other changes to the public education system. The annual budget is due to be approved by Nov. 30. (Luis Hidalgo)
Protesters are hit with water from a police water canon during a march for education reform in Santiago, Chile, Thursday Nov. 24, 2011. Protesters have demanded more funding and other changes to the public education system. The annual budget is due to be approved by Nov. 30. (Luis Hidalgo)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict12.jpg) Pro-Syrian regime protesters shout pro-Syrian President Bashar Assad slogans during a protest against the Arab League meeting, in Damascus, Syria, Thursday Nov. 24, 2011. An Arab League committee has given Syria 24 hours to agree to allow an observer mission into the country or it could face sanctions. (Bassem Tellawi)
Pro-Syrian regime protesters shout pro-Syrian President Bashar Assad slogans during a protest against the Arab League meeting, in Damascus, Syria, Thursday Nov. 24, 2011. An Arab League committee has given Syria 24 hours to agree to allow an observer mission into the country or it could face sanctions. (Bassem Tellawi)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict13.jpg) A woman cycles past a group of petitioners holding red scarves as they protest outside the Ministry of Civil Affairs in Beijing, China, Thursday, Nov. 24, 2011. About 30 petitioners who they said were infected with HIV from blood transfusions held up a chain of red scarves to symbolize their demands the government to provide compensation for their children’s treatment, in conjunction of the upcoming World AIDS Day, which falls on Dec. 1. (Andy Wong)
A woman cycles past a group of petitioners holding red scarves as they protest outside the Ministry of Civil Affairs in Beijing, China, Thursday, Nov. 24, 2011. About 30 petitioners who they said were infected with HIV from blood transfusions held up a chain of red scarves to symbolize their demands the government to provide compensation for their children’s treatment, in conjunction of the upcoming World AIDS Day, which falls on Dec. 1. (Andy Wong)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict15.jpg) A woman protester attempts to dismantle a barbed wire barricade, newly erected by the Egyptian army, near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)
A woman protester attempts to dismantle a barbed wire barricade, newly erected by the Egyptian army, near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict17.jpg) A protester takes a break during clashes with Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011. Egyptian police are clashing with anti-government protesters for a fifth day in Cairo. Tens of thousands of protesters in Tahrir Square have rejected a promise by Egypt’s military ruler to speed up a presidential election to the first half of next year.
A protester takes a break during clashes with Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011. Egyptian police are clashing with anti-government protesters for a fifth day in Cairo. Tens of thousands of protesters in Tahrir Square have rejected a promise by Egypt’s military ruler to speed up a presidential election to the first half of next year.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict16.jpg) A woman blocks the entrance to Congress as riot police stand guard in Guatemala City, Wednesday Nov. 23, 2011. Protesters are demanding that Congress approve the Ley de Vivienda, or Housing Act, which would allow them to attain legal titles to the lands where they built their homes. (Rodrigo Abd)
A woman blocks the entrance to Congress as riot police stand guard in Guatemala City, Wednesday Nov. 23, 2011. Protesters are demanding that Congress approve the Ley de Vivienda, or Housing Act, which would allow them to attain legal titles to the lands where they built their homes. (Rodrigo Abd)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict14.jpg) A protester affiliated with the Occupy Toronto movement shouts support to fellow protesters inside a barricaded pavilion in their camp in St. James Park in Toronto on Wednesday Nov. 23, 2011, as police and city officials enforce an eviction notice. (Chris Young)
A protester affiliated with the Occupy Toronto movement shouts support to fellow protesters inside a barricaded pavilion in their camp in St. James Park in Toronto on Wednesday Nov. 23, 2011, as police and city officials enforce an eviction notice. (Chris Young)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict19.jpg) Police officers detain opposition demonstrators during an unsanctioned rally in downtown Moscow, Russia, Tuesday, Nov. 22, 2011. Several dozen people were detained in central Moscow where they were protesting against the lack of alternatives in the upcoming parliamentary and presidential elections. (Alexander Zemlianichenko)
Police officers detain opposition demonstrators during an unsanctioned rally in downtown Moscow, Russia, Tuesday, Nov. 22, 2011. Several dozen people were detained in central Moscow where they were protesting against the lack of alternatives in the upcoming parliamentary and presidential elections. (Alexander Zemlianichenko)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict20.jpg) Anti-government protesters shout during a rally organized by the 20th February, the Moroccan Arab Spring movement in Casablanca, Morocco, Sunday, Nov 20, 2011, in a mass popular call to bring more democracy into this North African kingdom. Thousands of Moroccans from the pro-democracy movement braved pouring rain and high winds in Casablanca to make a final call to boycott upcoming elections. (Abdeljalil Bounhar)
Anti-government protesters shout during a rally organized by the 20th February, the Moroccan Arab Spring movement in Casablanca, Morocco, Sunday, Nov 20, 2011, in a mass popular call to bring more democracy into this North African kingdom. Thousands of Moroccans from the pro-democracy movement braved pouring rain and high winds in Casablanca to make a final call to boycott upcoming elections. (Abdeljalil Bounhar)






![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict27.jpg) Thousands of Egyptians perform Friday prayers during a rally in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011. Tens of thousands of protesters chanting, “Leave, leave!” are rapidly filling up Cairo’s Tahrir Square in what promises to be a massive demonstration to force Egypt’s ruling military council to yield power. The Friday rally is dubbed by organizers as “The Last Chance Million-Man Protest,” and comes one day after the military offered an apology for the killing of nearly 40 protesters.
Thousands of Egyptians perform Friday prayers during a rally in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011. Tens of thousands of protesters chanting, “Leave, leave!” are rapidly filling up Cairo’s Tahrir Square in what promises to be a massive demonstration to force Egypt’s ruling military council to yield power. The Friday rally is dubbed by organizers as “The Last Chance Million-Man Protest,” and comes one day after the military offered an apology for the killing of nearly 40 protesters.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict38.jpg) Egyptian protesters carry a giant Egyptian flag with Arabic writing that reads, in part, “Egypt is greater than you,” in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
Egyptian protesters carry a giant Egyptian flag with Arabic writing that reads, in part, “Egypt is greater than you,” in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict34.jpg) Protesters, including a wounded man, chant slogans and wave Egyptian national flags during a rally in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
Protesters, including a wounded man, chant slogans and wave Egyptian national flags during a rally in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict28.jpg) Egyptians, including a man perched on a lamp post, perform Friday prayers during a rally in Cairo’s Tahrir square, Egypt, Friday, Nov. 25, 2011.
Egyptians, including a man perched on a lamp post, perform Friday prayers during a rally in Cairo’s Tahrir square, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict29.jpg) Pro-reform leader and Nobel peace laureate Mohamed El-Baradei, center, is surrounded by protesters during his arrival for Friday prayers in Cairo’s Tahrir square, Egypt, Friday, Nov. 25, 2011.
Pro-reform leader and Nobel peace laureate Mohamed El-Baradei, center, is surrounded by protesters during his arrival for Friday prayers in Cairo’s Tahrir square, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict30.jpg) Egyptian women pray during Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
Egyptian women pray during Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict31.jpg) Protesters, including a man holding tear gas cannisters, chant slogans and wave national flags during a rally in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
Protesters, including a man holding tear gas cannisters, chant slogans and wave national flags during a rally in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict32.jpg) Egyptian men pray next to a t-shirt vendor during Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
Egyptian men pray next to a t-shirt vendor during Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict37.jpg) An Egyptian woman stands next to a cotton candy vendor before Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
An Egyptian woman stands next to a cotton candy vendor before Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict33.jpg) A man holds up a shoe, which is seen as a sign of disrespect, with pictures of Egyptians including Gamal Mubarak, center, during Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
A man holds up a shoe, which is seen as a sign of disrespect, with pictures of Egyptians including Gamal Mubarak, center, during Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict35.jpg) A veiled Egyptian woman waits for Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
A veiled Egyptian woman waits for Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict36.jpg) An Egyptian protester wears a safety mask around his neck as he performs Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
An Egyptian protester wears a safety mask around his neck as he performs Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict39.jpg) An Egyptian girl stands as protesters perform Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
An Egyptian girl stands as protesters perform Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict40.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict42.jpg) A protester displays an Egyptian flag in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
A protester displays an Egyptian flag in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict43.jpg) A protester reads a newspaper in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
A protester reads a newspaper in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict41.jpg) Demonstrators chant slogans as thousands spend the night in Tahrir Square, Cairo, Egypt, Thursday, Nov. 24, 2011.
Demonstrators chant slogans as thousands spend the night in Tahrir Square, Cairo, Egypt, Thursday, Nov. 24, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict47.jpg) Activists from Ukraine’s scandalous FEMEN group holds a banner reading ‘woman is not a commodity’ as they stage a topless protest on November 10, 2011 against prostitution and woman as a commodity in an official prostitution’s street in Zurich. Getty
Activists from Ukraine’s scandalous FEMEN group holds a banner reading ‘woman is not a commodity’ as they stage a topless protest on November 10, 2011 against prostitution and woman as a commodity in an official prostitution’s street in Zurich. Getty![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict48.jpg) An activist of the Ukrainian women movement Femen is being arrested by policemen in front of St Peter’s basilica after holding a placard asking for ‘Freedom for women’ following Pope Benedict XVI’s Angelus prayer on November 6, 2011 at St Peter’s square at The Vatican. Getty
An activist of the Ukrainian women movement Femen is being arrested by policemen in front of St Peter’s basilica after holding a placard asking for ‘Freedom for women’ following Pope Benedict XVI’s Angelus prayer on November 6, 2011 at St Peter’s square at The Vatican. Getty![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict49.jpg) An activist of the Ukrainian women movement Femen is taken away by Italian policemen in front of St Peter’s basilica after holding a placard asking for ‘Freedom for women’ following Pope Benedict XVI’s Angelus prayer on November 6, 2011 at St Peter’s square at The Vatican. Getty
An activist of the Ukrainian women movement Femen is taken away by Italian policemen in front of St Peter’s basilica after holding a placard asking for ‘Freedom for women’ following Pope Benedict XVI’s Angelus prayer on November 6, 2011 at St Peter’s square at The Vatican. Getty![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict56.jpg) An activist of the Ukrainian female rights organization “Femen” shows a placard demanding freedom for women, during a protest at the end of Pope Benedict XVI’s Angelus prayer in St. Peter’s Square at the Vatican, Sunday, Nov. 6, 2011. (Pier Paolo Cito)
An activist of the Ukrainian female rights organization “Femen” shows a placard demanding freedom for women, during a protest at the end of Pope Benedict XVI’s Angelus prayer in St. Peter’s Square at the Vatican, Sunday, Nov. 6, 2011. (Pier Paolo Cito)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict46.jpg) Ukrainian women’s rights group Femen, painted in colors of the Italian flag, take part in a demonstration staged by the Italian Democratic party to protest against Italian Premier Silvio Berlusconi in Rome, Saturday, Nov. 5, 2011. The International Monetary Fund will monitor Italy’s financial reform efforts, Premier Silvio Berlusconi said Friday, a humbling step for one of the world’s biggest _ but also most indebted _ economies as market confidence in its future wanes.
Ukrainian women’s rights group Femen, painted in colors of the Italian flag, take part in a demonstration staged by the Italian Democratic party to protest against Italian Premier Silvio Berlusconi in Rome, Saturday, Nov. 5, 2011. The International Monetary Fund will monitor Italy’s financial reform efforts, Premier Silvio Berlusconi said Friday, a humbling step for one of the world’s biggest _ but also most indebted _ economies as market confidence in its future wanes.![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict50.jpg) Activists from Ukraine’s scandalous FEMEN group dressed as housemaids stage a topless protest in a show of anger against French former IMF chief Dominique Strauss-Kahn’s attitude towards women in front of his residence in Paris on October 31, 2011. FEMEN has gained worldwide fame by staging a string of topless protests in Ukraine and now in Europe, in recent years to draw attention to issues from the exploitation of women to corruption. The placard read at L ‘ecstasy of power’, at R ‘your shame can’t be clean up’. Getty
Activists from Ukraine’s scandalous FEMEN group dressed as housemaids stage a topless protest in a show of anger against French former IMF chief Dominique Strauss-Kahn’s attitude towards women in front of his residence in Paris on October 31, 2011. FEMEN has gained worldwide fame by staging a string of topless protests in Ukraine and now in Europe, in recent years to draw attention to issues from the exploitation of women to corruption. The placard read at L ‘ecstasy of power’, at R ‘your shame can’t be clean up’. Getty![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict32.jpg) People walk in front of Kiev Zoo, as activists of the Ukrainian female rights organization “Femen”, take part in a topless protest in Kiev, Ukraine, Thursday, Oct. 27, 2011. Kiev zoo is a place that Femen’s activists compared to a concentration camp for those with fur and feathers. Hundreds of animals died at the zoo in recent years due to malnutrition, lack of medical care and abuse, and some suspect that corruption is at the heart of the problem.
People walk in front of Kiev Zoo, as activists of the Ukrainian female rights organization “Femen”, take part in a topless protest in Kiev, Ukraine, Thursday, Oct. 27, 2011. Kiev zoo is a place that Femen’s activists compared to a concentration camp for those with fur and feathers. Hundreds of animals died at the zoo in recent years due to malnutrition, lack of medical care and abuse, and some suspect that corruption is at the heart of the problem.![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict33.jpg) Securty guards detain an activist of the Ukrainian female rights organization “Femen”, during an action of protest in front of Kiev Zoo, Ukraine, Thursday, Oct. 27, 2011. Kiev zoo is a place that Femen’s activists compared to a concentration camp for those with fur and feathers. Hundreds of animals died at the zoo in recent years due to malnutrition, lack of medical care and abuse, and some suspect that corruption is at the heart of the problem. Femen calls for the 100-year-old zoo to be closed.
Securty guards detain an activist of the Ukrainian female rights organization “Femen”, during an action of protest in front of Kiev Zoo, Ukraine, Thursday, Oct. 27, 2011. Kiev zoo is a place that Femen’s activists compared to a concentration camp for those with fur and feathers. Hundreds of animals died at the zoo in recent years due to malnutrition, lack of medical care and abuse, and some suspect that corruption is at the heart of the problem. Femen calls for the 100-year-old zoo to be closed.![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict34.jpg) Secury guards detain an activist of the Ukrainian female rights organization “Femen”, during an action of nude protest in front of Kiev Zoo, Ukraine, Thursday, Oct. 27, 2011. Kiev zoo is a place that Femen’s activists compared to a concentration camp for those with fur and feathers. Hundreds of animals died at the zoo in recent years due to malnutrition, lack of medical care and abuse, and some suspect that corruption is at the heart of the problem.
Secury guards detain an activist of the Ukrainian female rights organization “Femen”, during an action of nude protest in front of Kiev Zoo, Ukraine, Thursday, Oct. 27, 2011. Kiev zoo is a place that Femen’s activists compared to a concentration camp for those with fur and feathers. Hundreds of animals died at the zoo in recent years due to malnutrition, lack of medical care and abuse, and some suspect that corruption is at the heart of the problem.![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict24.jpg) Police detain a member of women’s activist group FEMEN after their protest against government policy in front front of the Cabinet building in Kiev, Ukraine, Wednesday, Aug.24, 2011. The former Soviet republic marks the 20th anniversary of its independence. (Efrem Lukatsky)
Police detain a member of women’s activist group FEMEN after their protest against government policy in front front of the Cabinet building in Kiev, Ukraine, Wednesday, Aug.24, 2011. The former Soviet republic marks the 20th anniversary of its independence. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict41.jpg) Police detain a member of the women’s activist group FEMEN, after their protest against government policy in front of the Cabinet building in Kiev, Ukraine, Wednesday, Aug. 24, 2011. The former Soviet republic is marking the 20th anniversary of its independence. (Efrem Lukatsky)
Police detain a member of the women’s activist group FEMEN, after their protest against government policy in front of the Cabinet building in Kiev, Ukraine, Wednesday, Aug. 24, 2011. The former Soviet republic is marking the 20th anniversary of its independence. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict51.jpg) Ukrainian women’s rights group Femen, painted in colors of the European Union countries, protest against the regular summer switch off of public utility supply of hot water in central Kiev, Ukraine, Thursday, July 14, 2011. Women symbolically wash themselves in the city fountain to protest the need for hot water all year round, and to highlight the need for the hot water utility during the upcoming EURO 2012 soccer competition.(Efrem Lukatsky)
Ukrainian women’s rights group Femen, painted in colors of the European Union countries, protest against the regular summer switch off of public utility supply of hot water in central Kiev, Ukraine, Thursday, July 14, 2011. Women symbolically wash themselves in the city fountain to protest the need for hot water all year round, and to highlight the need for the hot water utility during the upcoming EURO 2012 soccer competition.(Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict52.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict35.jpg) Ukrainian women’s rights group Femen holding a picket in front of a court building, against the detention of a fellow activist in Kiev, Ukraine, Monday, Jan. 17, 2011. The poster reads, “Hands off, Femen”. Opposition politicians and democrats insist that President Viktor Yanukovych trampled Ukraine’s constitution in a bit to monopolize political power.(Efrem Lukatsky)
Ukrainian women’s rights group Femen holding a picket in front of a court building, against the detention of a fellow activist in Kiev, Ukraine, Monday, Jan. 17, 2011. The poster reads, “Hands off, Femen”. Opposition politicians and democrats insist that President Viktor Yanukovych trampled Ukraine’s constitution in a bit to monopolize political power.(Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict30.jpg) Ukrainian women’s rights group Femen, painted in colors of the European Union countries, protest against the regular summer switch off of public utility supply of hot water in central Kiev, Ukraine, Thursday, July 14, 2011. Women symbolically wash themselves in the city fountain to protest the need for hot water all year round, and to highlight the need for the hot water utility during the upcoming EURO 2012 soccer competition. (Efrem Lukatsky)
Ukrainian women’s rights group Femen, painted in colors of the European Union countries, protest against the regular summer switch off of public utility supply of hot water in central Kiev, Ukraine, Thursday, July 14, 2011. Women symbolically wash themselves in the city fountain to protest the need for hot water all year round, and to highlight the need for the hot water utility during the upcoming EURO 2012 soccer competition. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict26.jpg) Police detain Alexandra Shevchenko a member of women’s activist group FEMEN, in front of parliament in Kiev, Ukraine, Tuesday, July 5, 2011. Ukrainians are fiercely opposed to the pension fund reform, which parliament is set to consider this week, that is meant to raise the retirement age for women. (Efrem Lukatsky)
Police detain Alexandra Shevchenko a member of women’s activist group FEMEN, in front of parliament in Kiev, Ukraine, Tuesday, July 5, 2011. Ukrainians are fiercely opposed to the pension fund reform, which parliament is set to consider this week, that is meant to raise the retirement age for women. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict37.jpg) Semi naked activists from the Ukrainian female rights group Femen protest in front of the Saudi Arabian embassy against a ban on driving cars for women in Kiev, Ukraine, Thursday, June 16, 2011. (Sergei Chuzavkov)
Semi naked activists from the Ukrainian female rights group Femen protest in front of the Saudi Arabian embassy against a ban on driving cars for women in Kiev, Ukraine, Thursday, June 16, 2011. (Sergei Chuzavkov)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict39.jpg) An secury guard detains an activist of the Ukrainian female rights organization ‘Femen’ during an action of protest in front of the city’s State Administration at a opening ceremony of clocks counting down time that remains before the EURO 2012 soccer tournament starts, in Kiev, Ukraine, Wednesday, June 8, 2011. Writing on her back reads ‘Euro 2012 without Prostitution’. (Efrem Lukatsky)
An secury guard detains an activist of the Ukrainian female rights organization ‘Femen’ during an action of protest in front of the city’s State Administration at a opening ceremony of clocks counting down time that remains before the EURO 2012 soccer tournament starts, in Kiev, Ukraine, Wednesday, June 8, 2011. Writing on her back reads ‘Euro 2012 without Prostitution’. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict36.jpg) Activists of the Women’s Movement ‘FEMEN’ perform during a protest against the politics of Belarus President Alexander Lukashenko, during a rally to protest against what they claim is the sex-tourism and trafficking of women from Ukraine, at Independence square in Kiev, Ukraine, Wednesday, May 11, 2011. The Women’s Movement ‘FEMEN’ is an organization of the young women of the city of Kiev orientated to represent and defend the rights of women-students of the capital. (Efrem Lukatsky)
Activists of the Women’s Movement ‘FEMEN’ perform during a protest against the politics of Belarus President Alexander Lukashenko, during a rally to protest against what they claim is the sex-tourism and trafficking of women from Ukraine, at Independence square in Kiev, Ukraine, Wednesday, May 11, 2011. The Women’s Movement ‘FEMEN’ is an organization of the young women of the city of Kiev orientated to represent and defend the rights of women-students of the capital. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict40.jpg) Activists of the Women’s Movement ‘FEMEN’ performs and shout anti-Lukashenko slogans protesting against his politics in Belarus during a rally at Independence square in Kiev, Ukraine, Wednesday, May. 11, 2011. The poster reads ‘Put Lukashenko on the Rack!’. The Women’s Movement ‘FEMEN’ is an organization of the young women of the city of Kiev oriented on the women-students of the capital. The main program of the movement is the national campaign against the sex tourism and women trafficking. (Efrem Lukatsky)
Activists of the Women’s Movement ‘FEMEN’ performs and shout anti-Lukashenko slogans protesting against his politics in Belarus during a rally at Independence square in Kiev, Ukraine, Wednesday, May. 11, 2011. The poster reads ‘Put Lukashenko on the Rack!’. The Women’s Movement ‘FEMEN’ is an organization of the young women of the city of Kiev oriented on the women-students of the capital. The main program of the movement is the national campaign against the sex tourism and women trafficking. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict38.jpg) Activists of the Women’s Movement ‘FEMEN’ performs and shout anti-Lukashenko slogans protesting against his politics in Belarus during a rally at Independence square in Kiev, Ukraine, Wednesday, May. 11, 2011. The poster reading ‘Crush a cockroach’. The Women’s Movement ‘FEMEN’ is an organization of the young women of the city of Kiev oriented on the women-students A depiction of Lukashenko is seen in the background. (Efrem Lukatsky)
Activists of the Women’s Movement ‘FEMEN’ performs and shout anti-Lukashenko slogans protesting against his politics in Belarus during a rally at Independence square in Kiev, Ukraine, Wednesday, May. 11, 2011. The poster reading ‘Crush a cockroach’. The Women’s Movement ‘FEMEN’ is an organization of the young women of the city of Kiev oriented on the women-students A depiction of Lukashenko is seen in the background. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict42.jpg) Ukrainian police hold back activists from the women’s rights organization “Femen” during a protest close to the site of the international donors conference to clean up the Chernobyl nuclear disaster site in Kiev, Ukraine, Tuesday, April 19, 2011. Poster reads “Yanukovych is worse than radiation”. On April 26, Ukraine marks the 25th anniversary of the fatal explosion at the Chernobyl nuclear power plant. (Ukrafoto)
Ukrainian police hold back activists from the women’s rights organization “Femen” during a protest close to the site of the international donors conference to clean up the Chernobyl nuclear disaster site in Kiev, Ukraine, Tuesday, April 19, 2011. Poster reads “Yanukovych is worse than radiation”. On April 26, Ukraine marks the 25th anniversary of the fatal explosion at the Chernobyl nuclear power plant. (Ukrafoto)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict29.jpg) Ukrainian activists from the group Femen protest Iran’s treatment of women during the opening of Iranian Culture Days in Kiev, Ukraine, Thursday, Nov. 11, 2010. (Sergei Chuzavkov)
Ukrainian activists from the group Femen protest Iran’s treatment of women during the opening of Iranian Culture Days in Kiev, Ukraine, Thursday, Nov. 11, 2010. (Sergei Chuzavkov)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict28.jpg) Activists of the Ukrainian Women’s Movement “FEMEN” shout protests in front of the Iranian Embassy in Kiev, Ukraine, Wednesday, Nov. 3, 2010, against the death penalty given to Sakineh Mohammadi Ashtiani, a mother of two children, who was sentenced to death by stoning in Iran on charges of adultery. (Sergei Chuzavkov)
Activists of the Ukrainian Women’s Movement “FEMEN” shout protests in front of the Iranian Embassy in Kiev, Ukraine, Wednesday, Nov. 3, 2010, against the death penalty given to Sakineh Mohammadi Ashtiani, a mother of two children, who was sentenced to death by stoning in Iran on charges of adultery. (Sergei Chuzavkov)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict31.jpg) In this photo taken on Thursday, July 15, 2010, police detain activists of the local FEMEN women’s rights watchdog as they protest against the regular summer switch off of hot water in the city in downtown Kiev, Ukraine. A group of young activists is gaining popularity here for staging topless protests that involve sexually charged gestures, obscene slogans and scuffles with security guards and police. Often, the point seems to be just getting naked.
In this photo taken on Thursday, July 15, 2010, police detain activists of the local FEMEN women’s rights watchdog as they protest against the regular summer switch off of hot water in the city in downtown Kiev, Ukraine. A group of young activists is gaining popularity here for staging topless protests that involve sexually charged gestures, obscene slogans and scuffles with security guards and police. Often, the point seems to be just getting naked.![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict25.jpg) Members of the activist group Femen protest at what they see as the manipulation of the democratic system at a polling station in Kiev, Ukraine, Sunday, Feb. 7, 2010. The signs read “The War Begins Here” and “Stop Raping the Country.” (Mikhail Metzel)
Members of the activist group Femen protest at what they see as the manipulation of the democratic system at a polling station in Kiev, Ukraine, Sunday, Feb. 7, 2010. The signs read “The War Begins Here” and “Stop Raping the Country.” (Mikhail Metzel)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict43.jpg) Members of the activist group Femen protest at what they see as the manipulation of the democratic system at a polling station in Kiev, Ukraine, Sunday, Feb. 7, 2010. (Mikhail Metzel)
Members of the activist group Femen protest at what they see as the manipulation of the democratic system at a polling station in Kiev, Ukraine, Sunday, Feb. 7, 2010. (Mikhail Metzel)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict45.jpg) Activists of the Women’s Movement “FEMEN”, dressed as prostitutes, take part in a rally outside the Central Election Commission office in Kiev, Ukraine, Thursday, Jan. 14, 2010. The event was meant to highlight what the group called political prostitution and crude populism in the election campaign. The posters with the logos of the leading candidates and signature “Choose me” in Ukraine’s presidential race are seen at top.
Activists of the Women’s Movement “FEMEN”, dressed as prostitutes, take part in a rally outside the Central Election Commission office in Kiev, Ukraine, Thursday, Jan. 14, 2010. The event was meant to highlight what the group called political prostitution and crude populism in the election campaign. The posters with the logos of the leading candidates and signature “Choose me” in Ukraine’s presidential race are seen at top.![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict27.jpg) An activist of the Women’s Movement “FEMEN”, dressed as a prostitute, holds a poster with the logo of one of the leading candidates and signature “Choose me” in Ukraine’s presidential race, during a rally outside the Central Election Commission office in Kiev, Ukraine, Thursday, Jan. 14, 2010. The event was meant to highlight what the group called political prostitution and crude populism, in the election campaign.
An activist of the Women’s Movement “FEMEN”, dressed as a prostitute, holds a poster with the logo of one of the leading candidates and signature “Choose me” in Ukraine’s presidential race, during a rally outside the Central Election Commission office in Kiev, Ukraine, Thursday, Jan. 14, 2010. The event was meant to highlight what the group called political prostitution and crude populism, in the election campaign.![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict44.jpg) A security officer stops an activist of the Women’s Movement ‘FEMEN’ from climbing a barrier at Mykhailivska Square in Kiev, Ukraine, Monday, Dec. 14, 2009, prior the opening of the meeting for UEFA EURO 2012. The ‘FEMEN’ movement is campaigning against sex tourism and the trafficking of women in Ukraine. (Efrem Lukatsky)
A security officer stops an activist of the Women’s Movement ‘FEMEN’ from climbing a barrier at Mykhailivska Square in Kiev, Ukraine, Monday, Dec. 14, 2009, prior the opening of the meeting for UEFA EURO 2012. The ‘FEMEN’ movement is campaigning against sex tourism and the trafficking of women in Ukraine. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict23.jpg) Demonstrators are lit by a laser lights as thousands spend the night in Tahrir Square, Cairo, Egypt, Thursday, Nov. 24, 2011. Police and the protesters, who are demanding that Egypt’s ruling military council step down, are observing a truce after five days of deadly street battles in which dozens have died. (Bela Szandelszky)
Demonstrators are lit by a laser lights as thousands spend the night in Tahrir Square, Cairo, Egypt, Thursday, Nov. 24, 2011. Police and the protesters, who are demanding that Egypt’s ruling military council step down, are observing a truce after five days of deadly street battles in which dozens have died. (Bela Szandelszky)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict26.jpg) A wounded protester is treated at a field hospital near Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Manu Brabo)
A wounded protester is treated at a field hospital near Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Manu Brabo)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict24.jpg) Demonstrators chant slogans as thousands spend the night in Tahrir Square, Cairo, Egypt, Thursday, Nov. 24, 2011. Police and the protesters, who are demanding that Egypt’s ruling military council step down, are observing a truce after five days of deadly street battles in which dozens have died. (Bela Szandelszky)
Demonstrators chant slogans as thousands spend the night in Tahrir Square, Cairo, Egypt, Thursday, Nov. 24, 2011. Police and the protesters, who are demanding that Egypt’s ruling military council step down, are observing a truce after five days of deadly street battles in which dozens have died. (Bela Szandelszky)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict25.jpg) Protesters try to climb a concrete barricade erected by Egyptian Army soldiers in the street leading to the interior ministry from Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Manu Brabo)
Protesters try to climb a concrete barricade erected by Egyptian Army soldiers in the street leading to the interior ministry from Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Manu Brabo)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict18.jpg) Egyptian Army soldiers stand guard atop a concrete block barricade while protesters chant slogans, near Tahrir Square, in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Bernat Armangue)
Egyptian Army soldiers stand guard atop a concrete block barricade while protesters chant slogans, near Tahrir Square, in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Bernat Armangue)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict20.jpg) A protester waves an Egyptian national flag as they gather in Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Bernat Armangue)
A protester waves an Egyptian national flag as they gather in Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Bernat Armangue)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict5.jpg) Protesters gather as Egyptian Army soldiers build a concrete block barricade on the street between Tahrir Square and the interior ministry in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Khalil Hamra)
Protesters gather as Egyptian Army soldiers build a concrete block barricade on the street between Tahrir Square and the interior ministry in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict9.jpg) Egyptian protesters stand behind a barbed wire barricade in Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Mohammed Abu Zaid)
Egyptian protesters stand behind a barbed wire barricade in Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Mohammed Abu Zaid)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict10.jpg) An Egyptian officer, left, attempts to talk to protesters behind a newly erected barbed wire barricade by the Egyptian army near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)
An Egyptian officer, left, attempts to talk to protesters behind a newly erected barbed wire barricade by the Egyptian army near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict11.jpg) A woman protester attempts to dismantle a barbed wire barricade, newly erected by the Egyptian army, near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)
A woman protester attempts to dismantle a barbed wire barricade, newly erected by the Egyptian army, near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict14.jpg) Protesters gather behind a barbed wire barricade, newly erected by the Egyptian army, near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)
Protesters gather behind a barbed wire barricade, newly erected by the Egyptian army, near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict15.jpg) Protesters gather behind a barbed wire barricade, newly erected by the Egyptian army, near Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)
Protesters gather behind a barbed wire barricade, newly erected by the Egyptian army, near Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict13.jpg) Protesters shout through a barbed wire barricade, newly erected by the Egyptian army, near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)
Protesters shout through a barbed wire barricade, newly erected by the Egyptian army, near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict4.jpg) A protester watches Egyptian Army soldiers build a concrete block barricade on the street between Tahrir Square and the interior ministry in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Khalil Hamra)
A protester watches Egyptian Army soldiers build a concrete block barricade on the street between Tahrir Square and the interior ministry in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict3.jpg) Egyptian Army officers ask protesters to leave the top of a concrete block barricade on the street between Tahrir Square and the interior ministry in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Khalil Hamra)
Egyptian Army officers ask protesters to leave the top of a concrete block barricade on the street between Tahrir Square and the interior ministry in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict6.jpg) A protester looks through a concrete block barricade erected by the Egyptian Army on the street between Tahrir Square and the interior ministry in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Khalil Hamra)
A protester looks through a concrete block barricade erected by the Egyptian Army on the street between Tahrir Square and the interior ministry in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict8.jpg) Protesters gather around Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Mohammed Abu Zaid)
Protesters gather around Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Mohammed Abu Zaid)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict7.jpg) A protester prays moments after waking up in Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Bernat Armangue)
A protester prays moments after waking up in Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Bernat Armangue)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict12.jpg) Egyptian protesters set a fire during clashes with security forces near Tahrir Square in Cairo, Egypt, late Wednesday, Nov. 23, 2011. Egyptian police are clashing with anti-government protesters for a fifth day in Cairo.
Egyptian protesters set a fire during clashes with security forces near Tahrir Square in Cairo, Egypt, late Wednesday, Nov. 23, 2011. Egyptian police are clashing with anti-government protesters for a fifth day in Cairo.![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111911/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111911/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111911/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111911/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111911/pict5.jpg)

![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict0.jpg) Protesters gather in Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011. Egyptian police are clashing with anti-government protesters for a fifth day in Cairo. Tens of thousands of protesters in Tahrir Square have rejected a promise by Egypt’s military ruler to speed up a presidential election to the first half of next year. They want Field Marshal Hussein Tantawi to step down immediately in favor of an interim civilian council. (Tara Todras-Whitehill)
Protesters gather in Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011. Egyptian police are clashing with anti-government protesters for a fifth day in Cairo. Tens of thousands of protesters in Tahrir Square have rejected a promise by Egypt’s military ruler to speed up a presidential election to the first half of next year. They want Field Marshal Hussein Tantawi to step down immediately in favor of an interim civilian council. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict15.jpg) An injured protester, center, is aided by men on a motorcycle during clashes with Egyptian riot police, not pictured, near Tahrir square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
An injured protester, center, is aided by men on a motorcycle during clashes with Egyptian riot police, not pictured, near Tahrir square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict10.jpg) An injured protester is carried by other men during clashes with the Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
An injured protester is carried by other men during clashes with the Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict13.jpg) Egyptian riot policeman clash with protesters near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
Egyptian riot policeman clash with protesters near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict1.jpg) An Egyptian protester using scrap metal as a shield takes cover from tear gas during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
An Egyptian protester using scrap metal as a shield takes cover from tear gas during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict2.jpg) An Egyptian protester, center, uses a sling shot during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
An Egyptian protester, center, uses a sling shot during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict3.jpg) Egyptian protesters take cover from tear gas during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
Egyptian protesters take cover from tear gas during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict11.jpg) Egyptian protesters throw stones at security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
Egyptian protesters throw stones at security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict12.jpg) An Egyptian riot policeman throws a rock at protesters during clashes near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
An Egyptian riot policeman throws a rock at protesters during clashes near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict4.jpg) A protester takes a break during clashes with Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
A protester takes a break during clashes with Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict6.jpg) An injured Egyptian cleric from Al-Azhar, the country’s most prominent Islamic institution, wears a scarf as a mask to shield him from tear gas during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
An injured Egyptian cleric from Al-Azhar, the country’s most prominent Islamic institution, wears a scarf as a mask to shield him from tear gas during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict9.jpg) A wounded protester is aided by a comrade during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
A wounded protester is aided by a comrade during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict17.jpg) A protester walks away from tear gas fired during clashes with Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
A protester walks away from tear gas fired during clashes with Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict5.jpg) Female medics and doctors distribute supplies during nearby clashes with Egyptian riot police, in Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
Female medics and doctors distribute supplies during nearby clashes with Egyptian riot police, in Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict8.jpg) An Egyptian protester waves a national flag during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
An Egyptian protester waves a national flag during clashes with security forces near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict7.jpg) Protesters sit on a partially demolished wall during a temporary cease-fire with the Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
Protesters sit on a partially demolished wall during a temporary cease-fire with the Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict14.jpg) Protesters sit on a barricade during a temporary cease-fire with the Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
Protesters sit on a barricade during a temporary cease-fire with the Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest2/pict16.jpg) Protesters sit on the sidewalk during a temporary cease-fire with the Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.
Protesters sit on the sidewalk during a temporary cease-fire with the Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011.











![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict39.jpg) Protesters keep a pathway clear to move injured people during nearby clashes with Egyptian riot police in Tahrir Square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s ruling military moved up the date for transferring power to a civilian government to July next year and consulted Tuesday with political parties on forming a new Cabinet. But the major concessions were immediately rejected by tens of thousands of protesters in Cairo’s iconic Tahrir Square threatening a “second revolution.” (Tara Todras-Whitehill)
Protesters keep a pathway clear to move injured people during nearby clashes with Egyptian riot police in Tahrir Square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s ruling military moved up the date for transferring power to a civilian government to July next year and consulted Tuesday with political parties on forming a new Cabinet. But the major concessions were immediately rejected by tens of thousands of protesters in Cairo’s iconic Tahrir Square threatening a “second revolution.” (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict41.jpg) Women protesters stand in a group during nearby clashes with Egyptian riot police in Tahrir Square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s ruling military moved up the date for transferring power to a civilian government to July next year and consulted Tuesday with political parties on forming a new Cabinet. But the major concessions were immediately rejected by tens of thousands of protesters in Cairo’s iconic Tahrir Square threatening a “second revolution.” (AP Photo/Tara Todras-Whitehill)
Women protesters stand in a group during nearby clashes with Egyptian riot police in Tahrir Square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s ruling military moved up the date for transferring power to a civilian government to July next year and consulted Tuesday with political parties on forming a new Cabinet. But the major concessions were immediately rejected by tens of thousands of protesters in Cairo’s iconic Tahrir Square threatening a “second revolution.” (AP Photo/Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict40.jpg) Egyptian protesters perform prayers as they are guarded by other protesters who hold the national flag at Tahrir Square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egyptian politicians say the ruling military has moved up the date for transferring power to a civilian government to July 1, 2012. (Ahmed Ali)
Egyptian protesters perform prayers as they are guarded by other protesters who hold the national flag at Tahrir Square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egyptian politicians say the ruling military has moved up the date for transferring power to a civilian government to July 1, 2012. (Ahmed Ali)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict42.jpg) Protesters demonstrate during clashes with Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s ruling military moved up the date for transferring power to a civilian government to July next year and consulted Tuesday with political parties on forming a new Cabinet. But the major concessions were immediately rejected by tens of thousands of protesters in Cairo’s iconic Tahrir Square threatening a “second revolution.” (Tara Todras-Whitehill)
Protesters demonstrate during clashes with Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s ruling military moved up the date for transferring power to a civilian government to July next year and consulted Tuesday with political parties on forming a new Cabinet. But the major concessions were immediately rejected by tens of thousands of protesters in Cairo’s iconic Tahrir Square threatening a “second revolution.” (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict43.jpg) Protesters chant slogans during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011.Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)
Protesters chant slogans during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011.Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict44.jpg) A protester runs to throw a tear gas canister away during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011.Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)
A protester runs to throw a tear gas canister away during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011.Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict45.jpg) Protesters run for cover during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)
Protesters run for cover during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict46.jpg) Protesters carry a wounded man during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011.Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)
Protesters carry a wounded man during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011.Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict47.jpg) A protester on a motorcycle chants slogans during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)
A protester on a motorcycle chants slogans during clashes with the Egyptian riot police near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict48.jpg) An Egyptian riot police officer fires tear gas during clashes with protesters near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)
An Egyptian riot police officer fires tear gas during clashes with protesters near Tahrir square in Cairo, Egypt, Tuesday, Nov. 22, 2011. Egypt’s civilian Cabinet has offered to resign after three days of violent clashes in many cities between demonstrators and security forces, but the action failed to satisfy protesters deeply frustrated with the new military rulers. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict49.jpg) Egyptian protesters and riot police face off in Alexandria, Egypt, Monday, Nov. 21, 2011. Security forces fired tear gas and clashed Monday with several thousand protesters in Cairo’s Tahrir Square in the third straight day of violence that has killed dozens of people and has turned into the most sustained challenge yet to the rule of Egypt’s military.
Egyptian protesters and riot police face off in Alexandria, Egypt, Monday, Nov. 21, 2011. Security forces fired tear gas and clashed Monday with several thousand protesters in Cairo’s Tahrir Square in the third straight day of violence that has killed dozens of people and has turned into the most sustained challenge yet to the rule of Egypt’s military.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict50.jpg) Protesters gather in Tahrir Square in Cairo, Egypt, Monday, Nov. 21, 2011. Security forces fired tear gas and clashed Monday with several thousand protesters in Cairo’s Tahrir Square in the third straight day of violence that has killed dozens of people and has turned into the most sustained challenge yet to the rule of Egypt’s military.(Khalil Hamra)
Protesters gather in Tahrir Square in Cairo, Egypt, Monday, Nov. 21, 2011. Security forces fired tear gas and clashed Monday with several thousand protesters in Cairo’s Tahrir Square in the third straight day of violence that has killed dozens of people and has turned into the most sustained challenge yet to the rule of Egypt’s military.(Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict51.jpg) Protesters evacuate a wounded man during clashes with Egyptian riot police to a field hospital near Tahrir Square in Cairo, Egypt, Monday, Nov. 21, 2011. Security forces fired tear gas and clashed Monday with several thousand protesters in Cairo’s Tahrir Square in the third straight day of violence that has killed at least two dozen people and has turned into the most sustained challenge yet to the rule of Egypt’s military. (Tara Todras-Whitehill)
Protesters evacuate a wounded man during clashes with Egyptian riot police to a field hospital near Tahrir Square in Cairo, Egypt, Monday, Nov. 21, 2011. Security forces fired tear gas and clashed Monday with several thousand protesters in Cairo’s Tahrir Square in the third straight day of violence that has killed at least two dozen people and has turned into the most sustained challenge yet to the rule of Egypt’s military. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict52.jpg) Canadian volunteer nurse, Merikel, below right, helps an Egyptian medical team to treat an injured protester at a field hospital at Tahrir Square in Cairo, Egypt, Monday, Nov. 21, 2011. Egyptian riot police clashed Monday with thousands of protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. (Amr Nabil)
Canadian volunteer nurse, Merikel, below right, helps an Egyptian medical team to treat an injured protester at a field hospital at Tahrir Square in Cairo, Egypt, Monday, Nov. 21, 2011. Egyptian riot police clashed Monday with thousands of protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. (Amr Nabil)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict53.jpg) Egyptian protesters throw stones at Egyptian riot police, unseen, in Tahrir Square in Cairo, Egypt, Monday, Nov. 21, 2011. Police are clashing for a third day in Cairo’s central Tahrir Square with stone-throwing protesters demanding the country’s military rulers quickly transfer power to a civilian government. (Ahmed Ali)
Egyptian protesters throw stones at Egyptian riot police, unseen, in Tahrir Square in Cairo, Egypt, Monday, Nov. 21, 2011. Police are clashing for a third day in Cairo’s central Tahrir Square with stone-throwing protesters demanding the country’s military rulers quickly transfer power to a civilian government. (Ahmed Ali)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict54.jpg) Protesters throw stones as they take cover during clashes with Egyptian riot police near the interior ministry in downtown Cairo, Egypt, Sunday, Nov. 20, 2011. Firing tear gas and rubber bullets, Egyptian riot police on Sunday clashed for a second day with thousands of rock-throwing protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. The police battled an estimated 5,000 protesters in and around central Cairo’s Tahrir Square.
Protesters throw stones as they take cover during clashes with Egyptian riot police near the interior ministry in downtown Cairo, Egypt, Sunday, Nov. 20, 2011. Firing tear gas and rubber bullets, Egyptian riot police on Sunday clashed for a second day with thousands of rock-throwing protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. The police battled an estimated 5,000 protesters in and around central Cairo’s Tahrir Square.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict55.jpg) Tear gas surrounds Egyptian riot police as they stand guard during clashes in Tahrir Square in Cairo, Egypt, Saturday, Nov. 19, 2011. Thousands of police clashed with protesters for control of downtown Cairo’s Tahrir Square on Saturday after security forces tried to stop activists from staging a long-term sit-in there. The violence took place just nine days before Egypt’s first elections since the ouster of longtime President Hosni Mubarak in February. (Khalil Hamra)
Tear gas surrounds Egyptian riot police as they stand guard during clashes in Tahrir Square in Cairo, Egypt, Saturday, Nov. 19, 2011. Thousands of police clashed with protesters for control of downtown Cairo’s Tahrir Square on Saturday after security forces tried to stop activists from staging a long-term sit-in there. The violence took place just nine days before Egypt’s first elections since the ouster of longtime President Hosni Mubarak in February. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest/pict56.jpg) Egyptian riot police clash with protesters in Tahrir Square in Cairo, Egypt, Saturday, Nov. 19, 2011. Egyptian riot police beat protesters and dismantled a small tent city set up to commemorate revolutionary martyrs in Cairo’s Tahrir Square on Saturday. The clashes occurred after activists camped in the central square overnight following a massive Friday rally. The military tolerates daytime demonstrations in the central square, a symbol of the country’s Jan. 25-Feb. 11 uprising.
Egyptian riot police clash with protesters in Tahrir Square in Cairo, Egypt, Saturday, Nov. 19, 2011. Egyptian riot police beat protesters and dismantled a small tent city set up to commemorate revolutionary martyrs in Cairo’s Tahrir Square on Saturday. The clashes occurred after activists camped in the central square overnight following a massive Friday rally. The military tolerates daytime demonstrations in the central square, a symbol of the country’s Jan. 25-Feb. 11 uprising.![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict54.jpg) In this Friday, Nov. 18, 2011, photo University of California, Davis Police Lt. John Pike uses pepper spray to move Occupy UC Davis protesters while blocking their exit from the school’s quad Friday in Davis, Calif. Two University of California, Davis police officers involved in pepper spraying seated protesters were placed on administrative leave Sunday, Nov. 20, 2011, as the chancellor of the school accelerates the investigation into the incident. (Wayne Tilcock)
In this Friday, Nov. 18, 2011, photo University of California, Davis Police Lt. John Pike uses pepper spray to move Occupy UC Davis protesters while blocking their exit from the school’s quad Friday in Davis, Calif. Two University of California, Davis police officers involved in pepper spraying seated protesters were placed on administrative leave Sunday, Nov. 20, 2011, as the chancellor of the school accelerates the investigation into the incident. (Wayne Tilcock)![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict55.jpg) In this Friday, Nov. 18, 2011, photo Occupy University of California, Davis, protesters including David Buscho, far left, react after being pepper sprayed by police who came to remove tents set up on the school’s quad Friday in Davis, Calif. Two University of California, Davis police officers involved in pepper spraying seated protesters were placed on administrative leave Sunday, Nov. 20, 2011, as the chancellor of the school accelerates the investigation into the incident. (Wayne Tilcock)
In this Friday, Nov. 18, 2011, photo Occupy University of California, Davis, protesters including David Buscho, far left, react after being pepper sprayed by police who came to remove tents set up on the school’s quad Friday in Davis, Calif. Two University of California, Davis police officers involved in pepper spraying seated protesters were placed on administrative leave Sunday, Nov. 20, 2011, as the chancellor of the school accelerates the investigation into the incident. (Wayne Tilcock)![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict53.jpg) In this Friday, Nov. 18, 2011, photo occupy protester David Buscho is helped after being pepper sprayed by campus police while blocking their exit from the school’s Quad Friday in Davis, Calif. Two University of California, Davis police officers involved in pepper spraying seated protesters were placed on administrative leave Sunday, Nov. 20, 2011, as the chancellor of the school accelerates the investigation into the incident. (Wayne Tilcock)
In this Friday, Nov. 18, 2011, photo occupy protester David Buscho is helped after being pepper sprayed by campus police while blocking their exit from the school’s Quad Friday in Davis, Calif. Two University of California, Davis police officers involved in pepper spraying seated protesters were placed on administrative leave Sunday, Nov. 20, 2011, as the chancellor of the school accelerates the investigation into the incident. (Wayne Tilcock)![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict31.jpg) In this image made from video, a police officer uses pepper spray as he walks down a line of Occupy demonstrators sitting on the ground at the University of California, Davis on Friday, Nov. 18, 2011. The video – posted on YouTube – was shot Friday as police moved in on more than a dozen tents erected on campus and arrested 10 people, nine of them students. AP
In this image made from video, a police officer uses pepper spray as he walks down a line of Occupy demonstrators sitting on the ground at the University of California, Davis on Friday, Nov. 18, 2011. The video – posted on YouTube – was shot Friday as police moved in on more than a dozen tents erected on campus and arrested 10 people, nine of them students. AP
![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict30.jpg) University of California, Davis, student Mike Fetterman, receives a treatment for pepper spray by UC Davis firefighter Nate Potter, after campus police dismantled an Occupy Wall Street encampment on the campus quad in Davis, Calif. , Friday, Nov. 18, 2011. UC Davis officials say eight men and two women were taken into custody. AP
University of California, Davis, student Mike Fetterman, receives a treatment for pepper spray by UC Davis firefighter Nate Potter, after campus police dismantled an Occupy Wall Street encampment on the campus quad in Davis, Calif. , Friday, Nov. 18, 2011. UC Davis officials say eight men and two women were taken into custody. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict33.jpg) A police officer uses pepper spray on an Occupy Portland protestor at Pioneer Courthouse Square in Portland Ore. , Thursday, Nov. 17, 2011. AP
A police officer uses pepper spray on an Occupy Portland protestor at Pioneer Courthouse Square in Portland Ore. , Thursday, Nov. 17, 2011. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict28.jpg) A protester affiliated with the Occupy Wall Street movement pours liquid over the eyes of another fellow protester to ease the pain from pepper spray during an unannounced raid by the New York City Police Department outside Zuccotti Park in New York, in the early hours of November 15, 2011. Police wearing helmets and carrying shields evicted protesters with the Occupy Wall Street movement early on Tuesday from the park in New York City’s financial district where they have camped since September. Reuters
A protester affiliated with the Occupy Wall Street movement pours liquid over the eyes of another fellow protester to ease the pain from pepper spray during an unannounced raid by the New York City Police Department outside Zuccotti Park in New York, in the early hours of November 15, 2011. Police wearing helmets and carrying shields evicted protesters with the Occupy Wall Street movement early on Tuesday from the park in New York City’s financial district where they have camped since September. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict34.jpg) Seattle Police officers deploy pepper spray into a crowd during an Occupy Seattle protest on Tuesday, Nov. 15, 2011 at Westlake Park in Seattle. Protesters gathered in the intersection of 5th Avenue and Pine Street after marching from their camp at Seattle Central Community College in support of Occupy Wall Street. Many refused to move from the intersection after being ordered by police. Police then began spraying pepper spray into the gathered crowd hitting dozens of people. AP
Seattle Police officers deploy pepper spray into a crowd during an Occupy Seattle protest on Tuesday, Nov. 15, 2011 at Westlake Park in Seattle. Protesters gathered in the intersection of 5th Avenue and Pine Street after marching from their camp at Seattle Central Community College in support of Occupy Wall Street. Many refused to move from the intersection after being ordered by police. Police then began spraying pepper spray into the gathered crowd hitting dozens of people. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict35.jpg) Seattle activist Dorli Rainey, 84, reacts after being hit with pepper spray during an Occupy Seattle protest on Tuesday, Nov. 15, 2011 at Westlake Park in Seattle. Protesters gathered in the intersection of 5th Avenue and Pine Street after marching from their camp at Seattle Central Community College in support of Occupy Wall Street. Many refused to move from the intersection after being ordered by police. Police then began spraying pepper spray into the gathered crowd hitting dozens of people. AP
Seattle activist Dorli Rainey, 84, reacts after being hit with pepper spray during an Occupy Seattle protest on Tuesday, Nov. 15, 2011 at Westlake Park in Seattle. Protesters gathered in the intersection of 5th Avenue and Pine Street after marching from their camp at Seattle Central Community College in support of Occupy Wall Street. Many refused to move from the intersection after being ordered by police. Police then began spraying pepper spray into the gathered crowd hitting dozens of people. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict36.jpg) A woman who gave her name as Jennifer and said she was two months pregnant is rushed to an ambulance after being hit with pepper spray at an Occupy Seattle protest on Tuesday, Nov. 15, 2011 at Westlake Park in Seattle. Protesters gathered in the intersection of 5th Avenue and Pine Street after marching from their camp at Seattle Central Community College in support of Occupy Wall Street. Many refused to move from the intersection after being ordered by police. Police then began spraying pepper spray into the gathered crowd hitting dozens of people. AP
A woman who gave her name as Jennifer and said she was two months pregnant is rushed to an ambulance after being hit with pepper spray at an Occupy Seattle protest on Tuesday, Nov. 15, 2011 at Westlake Park in Seattle. Protesters gathered in the intersection of 5th Avenue and Pine Street after marching from their camp at Seattle Central Community College in support of Occupy Wall Street. Many refused to move from the intersection after being ordered by police. Police then began spraying pepper spray into the gathered crowd hitting dozens of people. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict23.jpg) A man is treated by fellow protesters after he was sprayed in the face with pepper spray by police during the Occupy Seattle’s protest against JPMorgan Chase CEO Jamie Dimon in Seattle November 2, 2011. About 300 rain-soaked protesters blocked the street outside the Sheraton hotel where Dimon was scheduled to speak at an event organized by the University of Washington’s school of business. Reuters
A man is treated by fellow protesters after he was sprayed in the face with pepper spray by police during the Occupy Seattle’s protest against JPMorgan Chase CEO Jamie Dimon in Seattle November 2, 2011. About 300 rain-soaked protesters blocked the street outside the Sheraton hotel where Dimon was scheduled to speak at an event organized by the University of Washington’s school of business. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict24.jpg) A police officer escorts an Occupy Tulsa protestor who was pepper sprayed in the face while being arresting for an alleged curfew violation for inhabiting a city park at night at Centennial Green in downtown Tulsa, Okla. , early Wednesday morning Nov. 2, 2011. Police warned demonstrators that they were in violation of a city curfew and gave them the choice of leaving before applying pepper spray and forcibly removing demonstrators sitting in a circle at the park shortly before 2 a.m. AP
A police officer escorts an Occupy Tulsa protestor who was pepper sprayed in the face while being arresting for an alleged curfew violation for inhabiting a city park at night at Centennial Green in downtown Tulsa, Okla. , early Wednesday morning Nov. 2, 2011. Police warned demonstrators that they were in violation of a city curfew and gave them the choice of leaving before applying pepper spray and forcibly removing demonstrators sitting in a circle at the park shortly before 2 a.m. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict27.jpg) Protesters use a metal structure against riot police as the police use pepper spray against them during clashes outside the Greek parliament in Athens, Wednesday, Oct. 19, 2011. Greek anger over new austerity measures and layoffs erupted into violence outside parliament on Wednesday, as demonstrators hurled chunks of marble and gasoline bombs and riot police responded with tear gas and stun grenades that echoed across Athens’ main square. Wednesday was the first day of a two-day general strike that unions described as the largest protests in years, with at least 100,000 people marching through central Athens. AP
Protesters use a metal structure against riot police as the police use pepper spray against them during clashes outside the Greek parliament in Athens, Wednesday, Oct. 19, 2011. Greek anger over new austerity measures and layoffs erupted into violence outside parliament on Wednesday, as demonstrators hurled chunks of marble and gasoline bombs and riot police responded with tear gas and stun grenades that echoed across Athens’ main square. Wednesday was the first day of a two-day general strike that unions described as the largest protests in years, with at least 100,000 people marching through central Athens. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict42.jpg) A San Diego Police officer maces a demonstrator at the Civic Center Plaza Friday, Oct. 14, 2011 in San Diego. Police on Friday began removing about a half-dozen tents after warning demonstrators that their personal belongings couldn’t stay in the Occupy San Diego camp. (Lenny Ignelzi)
A San Diego Police officer maces a demonstrator at the Civic Center Plaza Friday, Oct. 14, 2011 in San Diego. Police on Friday began removing about a half-dozen tents after warning demonstrators that their personal belongings couldn’t stay in the Occupy San Diego camp. (Lenny Ignelzi)![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict26.jpg) A demonstrator receives help after San Diego Police used pepper spray during a demonstration at the Civic Center Plaza Friday, Oct. 14, 2011 in San Diego. Police on Friday began removing about a half-dozen tents after warning demonstrators that their personal belongings couldn’t stay in the Occupy San Diego camp. AP
A demonstrator receives help after San Diego Police used pepper spray during a demonstration at the Civic Center Plaza Friday, Oct. 14, 2011 in San Diego. Police on Friday began removing about a half-dozen tents after warning demonstrators that their personal belongings couldn’t stay in the Occupy San Diego camp. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict25.jpg) A demomstrator tries to wash pepper spray from his eyes after a clash with the San Diego Police at the Civic Center Plaza Friday, Oct. 14, 2011 in San Diego. Police on Friday began removing about a half-dozen tents after warning demonstrators that their personal belongings couldn’t stay in the Occupy San Diego camp. AP
A demomstrator tries to wash pepper spray from his eyes after a clash with the San Diego Police at the Civic Center Plaza Friday, Oct. 14, 2011 in San Diego. Police on Friday began removing about a half-dozen tents after warning demonstrators that their personal belongings couldn’t stay in the Occupy San Diego camp. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict29.jpg) Two demonstrators cover themselves after San Diego Police used pepper spray during a protest at the Civic Center Plaza Friday, Oct. 14, 2011 in San Diego. Police on Friday began removing about a half-dozen tents after warning demonstrators that their personal belongings couldn’t stay in the Occupy San Diego camp. AP
Two demonstrators cover themselves after San Diego Police used pepper spray during a protest at the Civic Center Plaza Friday, Oct. 14, 2011 in San Diego. Police on Friday began removing about a half-dozen tents after warning demonstrators that their personal belongings couldn’t stay in the Occupy San Diego camp. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict43.jpg) One demonstrator helps another flush her eyes with water after after police pepper-sprayed a group of protestors, who were trying to get into the National Air and Space Museum in Washington Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)
One demonstrator helps another flush her eyes with water after after police pepper-sprayed a group of protestors, who were trying to get into the National Air and Space Museum in Washington Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)
![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict44.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict45.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict46.jpg) NYPD Deputy Inspector Anthony Bologna sprays protestors, 26 September 2011. Charlie Grapski via Daily Kos
NYPD Deputy Inspector Anthony Bologna sprays protestors, 26 September 2011. Charlie Grapski via Daily Kos
![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict47.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict38.jpg) A protester is hit by pepper spray when police used them against protesters as they broke through a police cordon to carry out a sit-in protest in the Hong Kong’s central business district Friday, July 1, 2011, Tens of thousands people march to vent their anger over skyrocketing property prices and government policies, the 14th anniversary of the former British colony’s return to Chinese rule. AP
A protester is hit by pepper spray when police used them against protesters as they broke through a police cordon to carry out a sit-in protest in the Hong Kong’s central business district Friday, July 1, 2011, Tens of thousands people march to vent their anger over skyrocketing property prices and government policies, the 14th anniversary of the former British colony’s return to Chinese rule. AP![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict40.jpg) A riot police reacts, after his colleagues used pepper spray, against protesters outside the Health Ministry in Athens, Thursday, May 26, 2011. Police have used pepper spray to disperse protesting doctors and state hospital staff, in the latest protest against public spending cuts.
A riot police reacts, after his colleagues used pepper spray, against protesters outside the Health Ministry in Athens, Thursday, May 26, 2011. Police have used pepper spray to disperse protesting doctors and state hospital staff, in the latest protest against public spending cuts.![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict39.jpg) Israeli riot police detain a man whose face was sprayed with pepper spray during riots in the East Jerusalem neighborhood of Issawiya on May 13, 2011 as Israeli police flooded the streets of Jerusalem, fearing violence as Palestinians began marking the ‘Nakba’ or ‘catastrophe’ which befell them following Israel’s establishment in 1948.
Israeli riot police detain a man whose face was sprayed with pepper spray during riots in the East Jerusalem neighborhood of Issawiya on May 13, 2011 as Israeli police flooded the streets of Jerusalem, fearing violence as Palestinians began marking the ‘Nakba’ or ‘catastrophe’ which befell them following Israel’s establishment in 1948.![[Image]](https://i0.wp.com/cryptome.org/info/pepper-spray/pict41.jpg) Police spray pepper gas and water canons at protesters in Ankara, Turkey, Thursday, Feb. 3, 2011, trying to stop a march on Parliament by workers protesting government-proposed legislation that they say will strip them of their rights. About ten thousands of workers, many of whom had traveled from across Turkey, had gathered in the capital Ankara and vowed to reach Parliament in defiance of laws that bar demonstrations near the assembly building. AP
Police spray pepper gas and water canons at protesters in Ankara, Turkey, Thursday, Feb. 3, 2011, trying to stop a march on Parliament by workers protesting government-proposed legislation that they say will strip them of their rights. About ten thousands of workers, many of whom had traveled from across Turkey, had gathered in the capital Ankara and vowed to reach Parliament in defiance of laws that bar demonstrations near the assembly building. AP



![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict36.jpg) Members of the Galician pro-indepence group Ceive stage a protest in favor of the transfert of jailed Galician independentist to Galician jails, next to a polling station in the village of Escravitude, some 20 kms from Santiago de Compostela, northwestern Spain, on November 20, 2011. Spaniards voted in rain-swept elections Sunday that were all but certain to hand a thundering victory to the right and topple yet another debt-laden eurozone government. Bowed by a 21,5 percent jobless rate, economic stagnation and deep spending cuts, the first voters of the 36 million-strong Spanish electorate headed to polls ready to punish the ruling Socialists. Getty
Members of the Galician pro-indepence group Ceive stage a protest in favor of the transfert of jailed Galician independentist to Galician jails, next to a polling station in the village of Escravitude, some 20 kms from Santiago de Compostela, northwestern Spain, on November 20, 2011. Spaniards voted in rain-swept elections Sunday that were all but certain to hand a thundering victory to the right and topple yet another debt-laden eurozone government. Bowed by a 21,5 percent jobless rate, economic stagnation and deep spending cuts, the first voters of the 36 million-strong Spanish electorate headed to polls ready to punish the ruling Socialists. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict34.jpg) A protester gestures during clashes with Egyptian riot police, not seen, near the interior ministry in downtown Cairo, Egypt, Sunday, Nov. 20, 2011. Firing tear gas and rubber bullets, Egyptian riot police on Sunday clashed for a second day with thousands of rock-throwing protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. (Tara Todras-Whitehill)
A protester gestures during clashes with Egyptian riot police, not seen, near the interior ministry in downtown Cairo, Egypt, Sunday, Nov. 20, 2011. Firing tear gas and rubber bullets, Egyptian riot police on Sunday clashed for a second day with thousands of rock-throwing protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict33.jpg) A protester overcome with tear gas inhalation is helped inside a cafe during clashes with the Egyptian riot police, not seen, near the interior ministry in downtown Cairo, Egypt, Sunday, Nov. 20, 2011. Firing tear gas and rubber bullets, Egyptian riot police on Sunday clashed for a second day with thousands of rock-throwing protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. (Tara Todras-Whitehill)
A protester overcome with tear gas inhalation is helped inside a cafe during clashes with the Egyptian riot police, not seen, near the interior ministry in downtown Cairo, Egypt, Sunday, Nov. 20, 2011. Firing tear gas and rubber bullets, Egyptian riot police on Sunday clashed for a second day with thousands of rock-throwing protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict35.jpg) Wounded protesters are seen in a field hospital during clashes with Egyptian riot police in Tahrir Square in Cairo, Egypt, Sunday, Nov. 20, 2011. Firing tear gas and rubber bullets, Egyptian riot police on Sunday clashed for a second day with thousands of rock-throwing protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. (Khalil Hamra)
Wounded protesters are seen in a field hospital during clashes with Egyptian riot police in Tahrir Square in Cairo, Egypt, Sunday, Nov. 20, 2011. Firing tear gas and rubber bullets, Egyptian riot police on Sunday clashed for a second day with thousands of rock-throwing protesters demanding that the ruling military quickly announce a date to hand over power to an elected government. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict25.jpg) Occupy Oakland protester Abby Balanda demonstrates during a march through Oakland, Calif., on Saturday, Nov. 19, 2011. Anti-Wall Street protesters in Oakland pushed down a chain-link fence surrounding a city-owned vacant lot where they planned a new encampment on Saturday. (Noah Berger)
Occupy Oakland protester Abby Balanda demonstrates during a march through Oakland, Calif., on Saturday, Nov. 19, 2011. Anti-Wall Street protesters in Oakland pushed down a chain-link fence surrounding a city-owned vacant lot where they planned a new encampment on Saturday. (Noah Berger)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict28.jpg) An Occupy Oakland protester, who declined to give her name, pitches a tent to establish a new encampment in Oakland, Calif., on Saturday, Nov. 19, 2011. Police raided the group’s previous camp on Monday. Anti-Wall Street protesters in Oakland pushed down a chain-link fence surrounding a city-owned vacant lot where they planned a new encampment on Saturday. (Noah Berger)
An Occupy Oakland protester, who declined to give her name, pitches a tent to establish a new encampment in Oakland, Calif., on Saturday, Nov. 19, 2011. Police raided the group’s previous camp on Monday. Anti-Wall Street protesters in Oakland pushed down a chain-link fence surrounding a city-owned vacant lot where they planned a new encampment on Saturday. (Noah Berger)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict29.jpg) A police officer arrests a demonstrator affiliated with the Occupy Wall Street movement as they block the entrance to the New York Stock Exchange on Broad Street, Thursday, Nov. 17, 2011 in New York. Two days after the encampment that sparked the global Occupy protest movement was cleared by authorities, demonstrators marched through New York’s financial district and promised a national day of action with mass gatherings in other cities. (Mary Altaffer)
A police officer arrests a demonstrator affiliated with the Occupy Wall Street movement as they block the entrance to the New York Stock Exchange on Broad Street, Thursday, Nov. 17, 2011 in New York. Two days after the encampment that sparked the global Occupy protest movement was cleared by authorities, demonstrators marched through New York’s financial district and promised a national day of action with mass gatherings in other cities. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict30.jpg) Police officers arrest a demonstrator affiliated with the Occupy Wall Street movement, Thursday, Nov. 17, 2011 in New York. Two days after the encampment that sparked the global Occupy protest movement was cleared by authorities, demonstrators marched through New York’s financial district and promised a national day of action with mass gatherings in other cities. (Mary Altaffer)
Police officers arrest a demonstrator affiliated with the Occupy Wall Street movement, Thursday, Nov. 17, 2011 in New York. Two days after the encampment that sparked the global Occupy protest movement was cleared by authorities, demonstrators marched through New York’s financial district and promised a national day of action with mass gatherings in other cities. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict21.jpg) Naked Israeli women pose for a photograph in Tel Aviv, November 19, 2011, to show solidarity with Egyptian blogger Aliaa Magda Elmahdy, who put naked pictures of herself on the Internet, support free expression and protest against Islamic extremism. The banner reads: “Love With No Boundaries”. Picture taken November 19, 2011. Reuters
Naked Israeli women pose for a photograph in Tel Aviv, November 19, 2011, to show solidarity with Egyptian blogger Aliaa Magda Elmahdy, who put naked pictures of herself on the Internet, support free expression and protest against Islamic extremism. The banner reads: “Love With No Boundaries”. Picture taken November 19, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict23.jpg) Tibetan Buddhist nun Palden Choetso sits in a house, in this handout picture taken in 1998 and recently released by the
Tibetan Buddhist nun Palden Choetso sits in a house, in this handout picture taken in 1998 and recently released by the ![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict24.jpg) Activists are blocked by the police during a march against the use of fur on November 19, 2011 in Paris, France. The march, in its third year, is held to protest the use of animal fur in fashion and animal cruelty. Getty
Activists are blocked by the police during a march against the use of fur on November 19, 2011 in Paris, France. The march, in its third year, is held to protest the use of animal fur in fashion and animal cruelty. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict27.jpg) Pro-Syrian regime protesters shout pro-Syrian President Bashar Assad slogans during a demonstration to show their soldarity with their president, in Damascus, Syria, on Sunday Nov. 20, 2011. Residents in the Syrian capital awoke to two loud explosions Sunday amid reports from activists that the Damascus headquarters of the ruling Baath party had been hit by several rocket-propelled grenades. But eyewitnesses said the party headquarters appeared intact and reported no significant security deployments.
Pro-Syrian regime protesters shout pro-Syrian President Bashar Assad slogans during a demonstration to show their soldarity with their president, in Damascus, Syria, on Sunday Nov. 20, 2011. Residents in the Syrian capital awoke to two loud explosions Sunday amid reports from activists that the Damascus headquarters of the ruling Baath party had been hit by several rocket-propelled grenades. But eyewitnesses said the party headquarters appeared intact and reported no significant security deployments.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict15.jpg) Women supporters hold placards during a protest organised by Awami National Conference in Srinagar on November 19, 2011. The protesters demanded revocation of Armed Forces Special Powers Act in restive Kashmir. The draconian Armed Forces Special Powers Act (AFSPA) was introduced in 1990 to give the army and paramilitary forces sweeping powers to detain people, use deadly force and destroy property. Violence is at its lowest in Indian Kashmir since the start of the insurgency that has so far left more than 47,000 people dead by official count but separatists putting the toll twice as high. Getty
Women supporters hold placards during a protest organised by Awami National Conference in Srinagar on November 19, 2011. The protesters demanded revocation of Armed Forces Special Powers Act in restive Kashmir. The draconian Armed Forces Special Powers Act (AFSPA) was introduced in 1990 to give the army and paramilitary forces sweeping powers to detain people, use deadly force and destroy property. Violence is at its lowest in Indian Kashmir since the start of the insurgency that has so far left more than 47,000 people dead by official count but separatists putting the toll twice as high. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict14.jpg) Spain’s ‘indignant’ protesters demostrate in the Puerta del Sol square in Madrid on November 19, 2011 against spending cuts, high unemployment and political corruption, a week before a general election. Spain’s so-called ‘indignant’ protest movement was born when thousands of people set up camp in Madrid’s Puerta del Sol square ahead of May 22 municipal elections. Getty
Spain’s ‘indignant’ protesters demostrate in the Puerta del Sol square in Madrid on November 19, 2011 against spending cuts, high unemployment and political corruption, a week before a general election. Spain’s so-called ‘indignant’ protest movement was born when thousands of people set up camp in Madrid’s Puerta del Sol square ahead of May 22 municipal elections. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict6.jpg) A female protester gestures as she argues with Egyptian riot police officers in Tahrir Square in Cairo, Egypt, Saturday, Nov. 19, 2011. Egyptian riot police beat protesters and dismantled a small tent city set up to commemorate revolutionary martyrs in Cairo’s Tahrir Square on Saturday. (Khalil Hamra)
A female protester gestures as she argues with Egyptian riot police officers in Tahrir Square in Cairo, Egypt, Saturday, Nov. 19, 2011. Egyptian riot police beat protesters and dismantled a small tent city set up to commemorate revolutionary martyrs in Cairo’s Tahrir Square on Saturday. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict9.jpg) Egyptian women wave flags during a rally in Cairo’s Tahrir square, Egypt, Friday, Nov.18, 2011, in a protest against what they say are attempts by the country’s military rulers to reinforce their powers. The rally Friday was dominated by the country’s most organized political group, the Muslim Brotherhood.
Egyptian women wave flags during a rally in Cairo’s Tahrir square, Egypt, Friday, Nov.18, 2011, in a protest against what they say are attempts by the country’s military rulers to reinforce their powers. The rally Friday was dominated by the country’s most organized political group, the Muslim Brotherhood.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict5.jpg) Egyptian Laila Soueif, at left, the mother of prominent blogger Alaa Abdel-Fattah who was jailed by Egypt’s ruling generals, who is on hunger strike to protest her son’s detention, as they celebrate Alaa’s 30th birthday in Cairo’s Tahrir square, Friday, Nov. 18, 2011. At Friday’s rally in Tahrir square, protesters gathered to celebrate the birthday of one of the most prominent revolutionary bloggers to be jailed by the military prosecutor. (Amr Nabil)
Egyptian Laila Soueif, at left, the mother of prominent blogger Alaa Abdel-Fattah who was jailed by Egypt’s ruling generals, who is on hunger strike to protest her son’s detention, as they celebrate Alaa’s 30th birthday in Cairo’s Tahrir square, Friday, Nov. 18, 2011. At Friday’s rally in Tahrir square, protesters gathered to celebrate the birthday of one of the most prominent revolutionary bloggers to be jailed by the military prosecutor. (Amr Nabil)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict2.jpg) Bahraini demonstrators gesture Friday, Nov. 18, 2011, in A’ali, Bahrain, in front of a replica of the massive protest encampment that was demolished by government forces last spring in the crackdown on a pro-democracy uprising, complete with tents and a model of the landmark pearl monument (unseen). Thousands of Shiite-led protesters calling for greater rights streamed into the area outside the capital of Manama in one of the largest demonstrations in weeks against the Gulf kingdom’s rulers.
Bahraini demonstrators gesture Friday, Nov. 18, 2011, in A’ali, Bahrain, in front of a replica of the massive protest encampment that was demolished by government forces last spring in the crackdown on a pro-democracy uprising, complete with tents and a model of the landmark pearl monument (unseen). Thousands of Shiite-led protesters calling for greater rights streamed into the area outside the capital of Manama in one of the largest demonstrations in weeks against the Gulf kingdom’s rulers.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict16.jpg) Muslims rally in Foley Square during a protest of ethnic profiling by law enforcement on November 18, 2011 in New York City. Muslims held a rally and Friday prayers and were joined by protesters affiliated with Occupy Wall Street. Getty
Muslims rally in Foley Square during a protest of ethnic profiling by law enforcement on November 18, 2011 in New York City. Muslims held a rally and Friday prayers and were joined by protesters affiliated with Occupy Wall Street. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict17.jpg) Animal activists, painted in “blood”, lie on a pile of fur during a protest in Belgrade November 18, 2011. The protest was held in conjunction with the “anti-fur” campaign in Europe. Reuters
Animal activists, painted in “blood”, lie on a pile of fur during a protest in Belgrade November 18, 2011. The protest was held in conjunction with the “anti-fur” campaign in Europe. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict19.jpg) Syrians living in Turkey write ‘Freedom’ with their blood during a protest against the government of Syria’s President Bashar al-Assad in front of the Syrian consulate in Istanbul, on November 18, 2011. Turkey added its voice Friday to warnings that civil war threatens Syria, while France’s top diplomat called for stepped up sanctions against Damascus, which he said had left it too late to reform. Getty
Syrians living in Turkey write ‘Freedom’ with their blood during a protest against the government of Syria’s President Bashar al-Assad in front of the Syrian consulate in Istanbul, on November 18, 2011. Turkey added its voice Friday to warnings that civil war threatens Syria, while France’s top diplomat called for stepped up sanctions against Damascus, which he said had left it too late to reform. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict20.jpg) Opponents of ousted Thai premier Thaksin Shinawatra hold banners as they shout during a protest in central Bangkok November 18, 2011. Opponents of Thaksin Shinawatra said on Thursday they could take to the streets if the government led by his sister tried to push through an amnesty that would let him return from exile a free man. Reuters
Opponents of ousted Thai premier Thaksin Shinawatra hold banners as they shout during a protest in central Bangkok November 18, 2011. Opponents of Thaksin Shinawatra said on Thursday they could take to the streets if the government led by his sister tried to push through an amnesty that would let him return from exile a free man. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict0.jpg) Muslims listen during a rally in Foley Square to protest against the NYPD surveillance operations of Muslim communities, Friday, Nov. 18, 2011, in New York. Hundreds of Muslims gathered in prayer Friday to oppose a decade of police spying on Muslim communities. The crowd filled about three-fourths of Foley Square in lower Manhattan, not far from City Hall. Demonstrators were scheduled to march on police headquarters (Bebeto Matthews)
Muslims listen during a rally in Foley Square to protest against the NYPD surveillance operations of Muslim communities, Friday, Nov. 18, 2011, in New York. Hundreds of Muslims gathered in prayer Friday to oppose a decade of police spying on Muslim communities. The crowd filled about three-fourths of Foley Square in lower Manhattan, not far from City Hall. Demonstrators were scheduled to march on police headquarters (Bebeto Matthews)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict3.jpg) Dorli Rainey, 84, left, who was pepper-sprayed by police last Tuesday while taking part in an “Occupy Seattle” protest, speaks Friday, Nov. 18, 2011, in front of police headquarters in downtown Seattle. Rainey and several dozen others marched to the station Friday and held the rally to call attention to how protesters have been treated. (Ted S. Warren)
Dorli Rainey, 84, left, who was pepper-sprayed by police last Tuesday while taking part in an “Occupy Seattle” protest, speaks Friday, Nov. 18, 2011, in front of police headquarters in downtown Seattle. Rainey and several dozen others marched to the station Friday and held the rally to call attention to how protesters have been treated. (Ted S. Warren)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict4.jpg) Virila Perez, left, and Francisco Gonzalez, who work as municipal trash collectors, demonstrate against proposed lay-offs by lying on broken glass in Asuncion, Paraguay, Friday Nov. 18, 2011. Asuncion’s municipal government is proposing cuts in employment to reduce the cost of municipal workers to 60% of the city budget. The sign covering them reads in Spanish “Until the final fight, overcome or die.” (Jorge Saenz)
Virila Perez, left, and Francisco Gonzalez, who work as municipal trash collectors, demonstrate against proposed lay-offs by lying on broken glass in Asuncion, Paraguay, Friday Nov. 18, 2011. Asuncion’s municipal government is proposing cuts in employment to reduce the cost of municipal workers to 60% of the city budget. The sign covering them reads in Spanish “Until the final fight, overcome or die.” (Jorge Saenz)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict22.jpg) Annette Jones waits with other demonstrators to be arrested during a protest organized by Occupy Chicago and Stand Up Chicago November 17, 2011 in Chicago, Illinois. The demonstration was one of many protests held nationwide to mark the second month of the Occupy Wall Street protests. Getty
Annette Jones waits with other demonstrators to be arrested during a protest organized by Occupy Chicago and Stand Up Chicago November 17, 2011 in Chicago, Illinois. The demonstration was one of many protests held nationwide to mark the second month of the Occupy Wall Street protests. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict10.jpg) Occupy Seattle protestors demonstrate at the University Bridge, temporarily shutting it down, after meeting others from Seattle Central Community College during a national day of action, Thursday, Nov. 17, 2011, in Seattle. Traffic was snarled around Seattle’s University District as two rallies marched toward the bridge. (Kevin P. Casey)
Occupy Seattle protestors demonstrate at the University Bridge, temporarily shutting it down, after meeting others from Seattle Central Community College during a national day of action, Thursday, Nov. 17, 2011, in Seattle. Traffic was snarled around Seattle’s University District as two rallies marched toward the bridge. (Kevin P. Casey)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict7.jpg) Eugene Police officers carry an Occupy Eugene protester away after arresting her for blocking the entrance to a Chase Bank in Eugene, Ore. Nov. 17, 2011. Occupy Eugene protesters spent an afternoon demonstrating at bank offices, and 17 were arrested. (Chris Pietsch)
Eugene Police officers carry an Occupy Eugene protester away after arresting her for blocking the entrance to a Chase Bank in Eugene, Ore. Nov. 17, 2011. Occupy Eugene protesters spent an afternoon demonstrating at bank offices, and 17 were arrested. (Chris Pietsch)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict11.jpg) A Occupy Portland protester is arrested by Portland Police officers after protesters take over a Wells Fargo bank Thursday, Nov. 17, 2011, in Portland, Ore. Occupy Wall Street demonstrators held modestly sized, but energetic rallies around the country Thursday to celebrate two months since the movement’s birth and signal that they aren’t ready to quit yet, despite police raids that have destroyed some of their encampments. (Rick Bowmer)
A Occupy Portland protester is arrested by Portland Police officers after protesters take over a Wells Fargo bank Thursday, Nov. 17, 2011, in Portland, Ore. Occupy Wall Street demonstrators held modestly sized, but energetic rallies around the country Thursday to celebrate two months since the movement’s birth and signal that they aren’t ready to quit yet, despite police raids that have destroyed some of their encampments. (Rick Bowmer)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict8.jpg) Occupy Wall Street protesters walk across the Brooklyn Bridge after a rally in Foley Square, Thursday, Nov. 17, 2011 in New York. Organizers with the Service Employees International Union and progressive groups staged similar bridge marches in several cities in an event that was planned weeks ago, but happened to coincide with rallies marking two months since the start of the Occupy movement (Henny Ray Abrams)
Occupy Wall Street protesters walk across the Brooklyn Bridge after a rally in Foley Square, Thursday, Nov. 17, 2011 in New York. Organizers with the Service Employees International Union and progressive groups staged similar bridge marches in several cities in an event that was planned weeks ago, but happened to coincide with rallies marking two months since the start of the Occupy movement (Henny Ray Abrams)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict12.jpg) Protesters willing to be arrested, including Donna Cassult, left, of Minneapolis, linked arms and sat on the roadway of the 10th Ave. Bridge in Minneapolis and waited for police to place them in custody Thursday, Nov. 17, 2011. Demonstrators peacefully shut down the 10th Ave. Bridge during rush hour to call attention to the need for more jobs and racial equality in employment.
Protesters willing to be arrested, including Donna Cassult, left, of Minneapolis, linked arms and sat on the roadway of the 10th Ave. Bridge in Minneapolis and waited for police to place them in custody Thursday, Nov. 17, 2011. Demonstrators peacefully shut down the 10th Ave. Bridge during rush hour to call attention to the need for more jobs and racial equality in employment.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/pict13.jpg) Police officers arrest a demonstrators affiliated with the Occupy Wall Street movement, Thursday, Nov. 17, 2011 in New York. Two days after the encampment that sparked the global Occupy protest movement was cleared by authorities, demonstrators marched through New York’s financial district and promised a national day of action with mass gatherings in other cities. (Mary Altaffer)
Police officers arrest a demonstrators affiliated with the Occupy Wall Street movement, Thursday, Nov. 17, 2011 in New York. Two days after the encampment that sparked the global Occupy protest movement was cleared by authorities, demonstrators marched through New York’s financial district and promised a national day of action with mass gatherings in other cities. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest6/Aliaa-Magda-Elmahdy-nude-30.jpg) 20-year-old Egyptian blogger Aliaa Mahdy. Photograph: Aliaa Mahdy
20-year-old Egyptian blogger Aliaa Mahdy. Photograph: Aliaa Mahdy![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict8.jpg) Spanish ‘indignant’ protesters hold a placard reading ‘We do not want fascists’ during a protest in front of a campaign meeting of the far-right party ‘Plataforma per Catalunya’ on November 13, 2011 in Barcelona. Hundreds of Spain’s ‘indignant’ protesters marched through the streets of Madrid Sunday to protest spending cuts, high unemployment and political corruption, a week before a general election. In Barcelona about 30 members of the movement decided at an assembly Saturday to camp out in the Plaza de Catalunya until the general election on November 20. Getty
Spanish ‘indignant’ protesters hold a placard reading ‘We do not want fascists’ during a protest in front of a campaign meeting of the far-right party ‘Plataforma per Catalunya’ on November 13, 2011 in Barcelona. Hundreds of Spain’s ‘indignant’ protesters marched through the streets of Madrid Sunday to protest spending cuts, high unemployment and political corruption, a week before a general election. In Barcelona about 30 members of the movement decided at an assembly Saturday to camp out in the Plaza de Catalunya until the general election on November 20. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict0.jpg) Two girls holds a coffin with a doll inside that wearing a mask with the faces of presidential candidates of Popular Party Mariano Rajoy and Socialist Party Alfredo Perez Rubalcaba during a demonstration against the government and banks in Madrid on Sunday, Nov. 13, 2011. Spain goes to the polls for presidential elections on November 20. (Arturo Rodriguez)
Two girls holds a coffin with a doll inside that wearing a mask with the faces of presidential candidates of Popular Party Mariano Rajoy and Socialist Party Alfredo Perez Rubalcaba during a demonstration against the government and banks in Madrid on Sunday, Nov. 13, 2011. Spain goes to the polls for presidential elections on November 20. (Arturo Rodriguez)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict10.jpg) Public workers march during a protest in Lisbon’s main avenue of Liberdade November 12, 2011. Public workers, policemen and military personnel are holding several protests in Lisbon against the job and 2012 state budget cuts. Reuters
Public workers march during a protest in Lisbon’s main avenue of Liberdade November 12, 2011. Public workers, policemen and military personnel are holding several protests in Lisbon against the job and 2012 state budget cuts. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict9.jpg) A woman holds up a sign that reads “No is No” as she takes part in the “Marcha de las Putas” (SlutWalk), held to protest against discrimination and violence against women in Lima, November 12, 2011. The march is part of the SlutWalk protest movement which started after a policeman advised women students in Canada to “avoid dressing like sluts”. Reuters
A woman holds up a sign that reads “No is No” as she takes part in the “Marcha de las Putas” (SlutWalk), held to protest against discrimination and violence against women in Lima, November 12, 2011. The march is part of the SlutWalk protest movement which started after a policeman advised women students in Canada to “avoid dressing like sluts”. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict1.jpg) Pro-Syrian regime protesters, hold up portraits of Syrian President Bashar Assad with Arabic words: ” The lion (Assad) of resistance and the rejectionism” during a demonstration against the Arab League decision to suspend Syria in front the Syrian embassy, in Beirut, Lebanon, on Sunday Nov. 13, 2011. Tens of thousands of pro-regime demonstrators gathered in a Damascus square Sunday to protest the Arab League’s vote to suspend Syria over its bloody crackdown on the country’s eight-month-old uprising.
Pro-Syrian regime protesters, hold up portraits of Syrian President Bashar Assad with Arabic words: ” The lion (Assad) of resistance and the rejectionism” during a demonstration against the Arab League decision to suspend Syria in front the Syrian embassy, in Beirut, Lebanon, on Sunday Nov. 13, 2011. Tens of thousands of pro-regime demonstrators gathered in a Damascus square Sunday to protest the Arab League’s vote to suspend Syria over its bloody crackdown on the country’s eight-month-old uprising.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict7.jpg) Syrian protesters shout anti-Syrian Preident Bashar Assad slogans during a protest in front of the Arab League headquarters in Cairo, Egypt, Saturday, Nov.12, 2011 where the League emergency session on Syria is to discuss the country’s failure to end bloodshed caused by government crackdowns on civil protests. Protesters called the Arab League to suspend the country’s membership. Arabic read ” step out, we need to build civilian modern country” (Amr Nabil)
Syrian protesters shout anti-Syrian Preident Bashar Assad slogans during a protest in front of the Arab League headquarters in Cairo, Egypt, Saturday, Nov.12, 2011 where the League emergency session on Syria is to discuss the country’s failure to end bloodshed caused by government crackdowns on civil protests. Protesters called the Arab League to suspend the country’s membership. Arabic read ” step out, we need to build civilian modern country” (Amr Nabil)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict5.jpg) Demonstrators with cooking pots and colanders on their heads stand in front of the European Central Bank in Frankfurt, Germany, Saturday, Nov.12, 2011. Thousands of people formed a human chain around the Frankfurt bank towers protesting against the power of banks. German police say more than ten thousand people are protesting against the banks’ dominance in two of the country’s major cities.
Demonstrators with cooking pots and colanders on their heads stand in front of the European Central Bank in Frankfurt, Germany, Saturday, Nov.12, 2011. Thousands of people formed a human chain around the Frankfurt bank towers protesting against the power of banks. German police say more than ten thousand people are protesting against the banks’ dominance in two of the country’s major cities.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict2.jpg) A group of protesters prepare their signs before heading out into the ocean to hold an anti-APEC protest at Waikiki Beach in Honolulu on Saturday, Nov. 12, 2011 as the summit is held in Oahu over the weekend. (Marco Garcia)
A group of protesters prepare their signs before heading out into the ocean to hold an anti-APEC protest at Waikiki Beach in Honolulu on Saturday, Nov. 12, 2011 as the summit is held in Oahu over the weekend. (Marco Garcia)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict4.jpg) Demonstrators hold a ribbon reading “smash banks, redistribute wealth” in front of the European Central Bank in Frankfurt, Germany, Saturday, Nov.12, 2011. Thousands of people formed a human chain with the ribbon around the Frankfurt bank towers to protest against the power of banks.Thousands of people formed a human chain around the Frankfurt bank towers protesting against the worldwide power of banks. German police say more than ten thousand people are protesting against the banks’ dominance in two of the country’s major cities.
Demonstrators hold a ribbon reading “smash banks, redistribute wealth” in front of the European Central Bank in Frankfurt, Germany, Saturday, Nov.12, 2011. Thousands of people formed a human chain with the ribbon around the Frankfurt bank towers to protest against the power of banks.Thousands of people formed a human chain around the Frankfurt bank towers protesting against the worldwide power of banks. German police say more than ten thousand people are protesting against the banks’ dominance in two of the country’s major cities.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict3.jpg) Protestors march through downtown Lisbon during a demonstration by military personnel associations against austerity measures Saturday, Nov. 12 2011. The Portuguese government plans to introduce more pay cuts and steep tax hikes next year while the country is struggling to restore its fiscal health despite a euro78 billion ($106 billion) bailout earlier this year. Banner reads ” Amnesty for the military punished for offenses of opinion” refering to military who have been punished for taking part in protests.
Protestors march through downtown Lisbon during a demonstration by military personnel associations against austerity measures Saturday, Nov. 12 2011. The Portuguese government plans to introduce more pay cuts and steep tax hikes next year while the country is struggling to restore its fiscal health despite a euro78 billion ($106 billion) bailout earlier this year. Banner reads ” Amnesty for the military punished for offenses of opinion” refering to military who have been punished for taking part in protests.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict67.jpg) Students march against government plans to reform higher education in Medellin, Colombia, Thursday, Nov. 10, 2011. Thousands of students march in the country’s main cities despite President Juan Manuel Santos’ proposal to withdraw a reform bill on higher education. (Luis Benavides)
Students march against government plans to reform higher education in Medellin, Colombia, Thursday, Nov. 10, 2011. Thousands of students march in the country’s main cities despite President Juan Manuel Santos’ proposal to withdraw a reform bill on higher education. (Luis Benavides)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict80.jpg) A UCLA student arrested by Los Angeles Police Department officers after she attempted to escape after eleven student protesters sat in circle in middle of the Westwood and Wilshire boulevard intersection as part of a protest of bank practices and rising fees at public universities on November 9, 2011 in Los Angeles, California. The protest organized by ReFund California was one of several planned at universities around the state. Getty
A UCLA student arrested by Los Angeles Police Department officers after she attempted to escape after eleven student protesters sat in circle in middle of the Westwood and Wilshire boulevard intersection as part of a protest of bank practices and rising fees at public universities on November 9, 2011 in Los Angeles, California. The protest organized by ReFund California was one of several planned at universities around the state. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict76.jpg) Students demonstrate against an education reform bill in Bogota, on November 10, 2011. Thousands of students from more than 30 public universities took to the streets in Colombia to protest against proposed education reforms they fear will partially privatize higher education. The students have been on strike over the past month to protest a bill put forward by President Juan Manuel Santos that would require public universities to generate some of their own revenues. On Wednesday Santos offered to withdraw the draft and open a dialogue if the more than half a million students on strike lift their form of pressure. Getty
Students demonstrate against an education reform bill in Bogota, on November 10, 2011. Thousands of students from more than 30 public universities took to the streets in Colombia to protest against proposed education reforms they fear will partially privatize higher education. The students have been on strike over the past month to protest a bill put forward by President Juan Manuel Santos that would require public universities to generate some of their own revenues. On Wednesday Santos offered to withdraw the draft and open a dialogue if the more than half a million students on strike lift their form of pressure. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict72.jpg) A demonstrator holds a banner against the ECB in Naples on November 11, 2011 during a rally called ‘Occupy Napoli’ (Occupy Naples), refering to the Occupy Wall Street movement in New York, to protest against banks and international financial power. Getty
A demonstrator holds a banner against the ECB in Naples on November 11, 2011 during a rally called ‘Occupy Napoli’ (Occupy Naples), refering to the Occupy Wall Street movement in New York, to protest against banks and international financial power. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict71.jpg) Hungarian and foreign activists and sympathizers of the ‘True Democracy Now’ group hold banners reading ‘Direct Democracy’ (R) and ‘Be part’, (L) as an elderly woman mouth’s is covered by a fake 1000 euro bill in front the central bank of Budapest on November 11, 2011 during a demonstration for a better and livable world and to protest against the political and economical system. Getty
Hungarian and foreign activists and sympathizers of the ‘True Democracy Now’ group hold banners reading ‘Direct Democracy’ (R) and ‘Be part’, (L) as an elderly woman mouth’s is covered by a fake 1000 euro bill in front the central bank of Budapest on November 11, 2011 during a demonstration for a better and livable world and to protest against the political and economical system. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict70.jpg) A protester holds a sign reading “Neither Tremonti nor Monti” during a protest in front of the Ministry of Finance in Rome November 11, 2011. The package of austerity measures that were demanded by the European Union will now go to the Italian lower house, which is expected to approve it on Saturday. That vote will trigger the resignation of Prime Minister Silvio Berlusconi. The signs refer to Italian Finance Minister Giulio Tremonti and former European Commissioner Mario Monti, who is tipped as the favourite to replace Berlusconi. Reuters
A protester holds a sign reading “Neither Tremonti nor Monti” during a protest in front of the Ministry of Finance in Rome November 11, 2011. The package of austerity measures that were demanded by the European Union will now go to the Italian lower house, which is expected to approve it on Saturday. That vote will trigger the resignation of Prime Minister Silvio Berlusconi. The signs refer to Italian Finance Minister Giulio Tremonti and former European Commissioner Mario Monti, who is tipped as the favourite to replace Berlusconi. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict73.jpg) A Yemeni woman covers her mouth with her hand painted in the colours of the national flag during to a protest against the regime of Ali Abdullah Saleh in the capital Sanaa, on November11, 2011. Forces loyal to Yemeni President Abdullah Saleh shelled the country’s second largest city Taez, killing nine people, among them two women and a child, a medic and witnesses said. Getty
A Yemeni woman covers her mouth with her hand painted in the colours of the national flag during to a protest against the regime of Ali Abdullah Saleh in the capital Sanaa, on November11, 2011. Forces loyal to Yemeni President Abdullah Saleh shelled the country’s second largest city Taez, killing nine people, among them two women and a child, a medic and witnesses said. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict74.jpg) A protester holding a banner camps outside the Banca d’Italia on November 11, 2011 in Venice, Italy. Protest in several Italian cities have been called by the Indignados, students, social centres and other organizations for today 11.11.11 to protest against financial insitutions and cuts proposed by the Government. Getty
A protester holding a banner camps outside the Banca d’Italia on November 11, 2011 in Venice, Italy. Protest in several Italian cities have been called by the Indignados, students, social centres and other organizations for today 11.11.11 to protest against financial insitutions and cuts proposed by the Government. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict69.jpg) Dalbir Kaur, sister of Indian national Sarabjit Singh on death row in Pakistan, second right, along with supporters of All India Youth Foundation takes an oath for securing his release in front of the India Gate war memorial at 11:11 am, in New Delhi, India, Friday, Nov. 11, 2011. A placard on left reads, “People’s Voice, Sarabjit.” (Gurinder Osan)
Dalbir Kaur, sister of Indian national Sarabjit Singh on death row in Pakistan, second right, along with supporters of All India Youth Foundation takes an oath for securing his release in front of the India Gate war memorial at 11:11 am, in New Delhi, India, Friday, Nov. 11, 2011. A placard on left reads, “People’s Voice, Sarabjit.” (Gurinder Osan)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict68.jpg) An Indonesian Muslim woman wears a Palestinian flag face mask during a solidarity protest for the Palestinian people in Jakarta, Indonesia, Thursday, Nov. 10, 2011. (Irwin Fedriansyah)
An Indonesian Muslim woman wears a Palestinian flag face mask during a solidarity protest for the Palestinian people in Jakarta, Indonesia, Thursday, Nov. 10, 2011. (Irwin Fedriansyah)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict77.jpg) Demonstrators of a group “Occupy Rio” protest against Rio de Janeiro’s governor Sergio Cabral in downtown Rio de Janeiro November 10, 2011. The demonstration, inspired by the Occupy Wall Street movement, seeks to address the corruption in the police and the problems with the health care system under the governance of Cabral. Cabral had originally organized a demonstration to rally against an oil reform amendment approved by the lower house of Congress. Reuters
Demonstrators of a group “Occupy Rio” protest against Rio de Janeiro’s governor Sergio Cabral in downtown Rio de Janeiro November 10, 2011. The demonstration, inspired by the Occupy Wall Street movement, seeks to address the corruption in the police and the problems with the health care system under the governance of Cabral. Cabral had originally organized a demonstration to rally against an oil reform amendment approved by the lower house of Congress. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict78.jpg) Protesters from the communist-affiliated trade union PAME shout slogans during an anti-government protest in Athens November 10, 2011. Greece named former European Central Bank vice-president Lucas Papademos on Thursday to head a crisis government, ending a chaotic search for a leader to save the country from default, bankruptcy and an exit from the euro zone. Reuters
Protesters from the communist-affiliated trade union PAME shout slogans during an anti-government protest in Athens November 10, 2011. Greece named former European Central Bank vice-president Lucas Papademos on Thursday to head a crisis government, ending a chaotic search for a leader to save the country from default, bankruptcy and an exit from the euro zone. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict64.jpg) A demonstrator marches during a student protest against government plans to reform higher education at the main square in Bogota, Colombia, Thursday, Nov. 10, 2011. Thousands of students marched in the country’s main cities despite a government proposal to withdraw a reform bill on higher education. (William Fernando Martinez)
A demonstrator marches during a student protest against government plans to reform higher education at the main square in Bogota, Colombia, Thursday, Nov. 10, 2011. Thousands of students marched in the country’s main cities despite a government proposal to withdraw a reform bill on higher education. (William Fernando Martinez)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict66.jpg) People wave flags of Rio de Janeiro state during a protest against an oil reform amendment in Rio de Janeiro, Brazil, Thursday, Nov. 10, 2011. Thousands of Brazilians are demonstrating against a plan that reduces revenue for oil-producing states and the federal government while increasing oil royalties for non-producing states. (Felipe Dana)
People wave flags of Rio de Janeiro state during a protest against an oil reform amendment in Rio de Janeiro, Brazil, Thursday, Nov. 10, 2011. Thousands of Brazilians are demonstrating against a plan that reduces revenue for oil-producing states and the federal government while increasing oil royalties for non-producing states. (Felipe Dana)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict65.jpg) Christian fundamentalist holds a candle during a demonstration against Italian director Romeo Castellucci’s play “On the Concept of the Face, Regarding the Son of God” in Rennes, western France, Thursday Nov. 10, 2011. Christian fundamentalists gathered outside the cultural palace the Theatre National de Bretagne, (National Theatre of Brittany), to protest against the play which they claim is blasphemous. (David Vincent)
Christian fundamentalist holds a candle during a demonstration against Italian director Romeo Castellucci’s play “On the Concept of the Face, Regarding the Son of God” in Rennes, western France, Thursday Nov. 10, 2011. Christian fundamentalists gathered outside the cultural palace the Theatre National de Bretagne, (National Theatre of Brittany), to protest against the play which they claim is blasphemous. (David Vincent)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict75.jpg) One of the students with peaceful attitude cleans the shield of a riot policemen that was stained with paint by more violent protesters, during a demonstration against an education reform bill at Bogota’s main square Plaza de Bolivar, on November 10, 2011. Thousands of students from more than 30 public universities took to the streets in Colombia to protest against proposed education reforms they fear will partially privatize higher education. The students have been on strike over the past month to protest a bill put forward by President Juan Manuel Santos that would require public universities to generate some of their own revenues. On Wednesday Santos offered to withdraw the draft and open a dialogue if the more than half a million students on strike lift their form of pressure. Getty
One of the students with peaceful attitude cleans the shield of a riot policemen that was stained with paint by more violent protesters, during a demonstration against an education reform bill at Bogota’s main square Plaza de Bolivar, on November 10, 2011. Thousands of students from more than 30 public universities took to the streets in Colombia to protest against proposed education reforms they fear will partially privatize higher education. The students have been on strike over the past month to protest a bill put forward by President Juan Manuel Santos that would require public universities to generate some of their own revenues. On Wednesday Santos offered to withdraw the draft and open a dialogue if the more than half a million students on strike lift their form of pressure. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict79.jpg) NOVEMBER 09: UCLA graduate student Cheryl Deutsch is arrested by Los Angeles Police Department officers after she and 10 other student protesters sat in circle in middle of the Westwood and Wilshire boulevard intersection as part of a protest of bank practices and rising fees at public universities on November 9, 2011 in Los Angeles, California. The protest organized by ReFund California was one of several planned at universities around the state. Getty
NOVEMBER 09: UCLA graduate student Cheryl Deutsch is arrested by Los Angeles Police Department officers after she and 10 other student protesters sat in circle in middle of the Westwood and Wilshire boulevard intersection as part of a protest of bank practices and rising fees at public universities on November 9, 2011 in Los Angeles, California. The protest organized by ReFund California was one of several planned at universities around the state. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict61.jpg) A woman shouts out as police officers move into the crowd of demonstrators and push people back during a student anti-cuts protest in London, Wednesday, Nov. 9, 2011. Thousands of students marched through central London on Wednesday to protest cuts to public spending and a big increase in university tuition fees. Police said there were “a number of arrests for public order offenses” Wednesday, but the march was largely peaceful as demonstrators made their way through the city center.
A woman shouts out as police officers move into the crowd of demonstrators and push people back during a student anti-cuts protest in London, Wednesday, Nov. 9, 2011. Thousands of students marched through central London on Wednesday to protest cuts to public spending and a big increase in university tuition fees. Police said there were “a number of arrests for public order offenses” Wednesday, but the march was largely peaceful as demonstrators made their way through the city center.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict62.jpg) A protester cries out as students and campaigners march through the streets of London in a protest against higher tuition fees and government cuts, Wednesday, Nov. 9, 2011. (Sang Tan)
A protester cries out as students and campaigners march through the streets of London in a protest against higher tuition fees and government cuts, Wednesday, Nov. 9, 2011. (Sang Tan)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict63.jpg) A lone protester stands outside the Scottsdale Plaza Resort to protest Republican Presidential candidate Herman Cain who was addressing the media Tuesday, Nov. 8, 2011, in Scottsdale, Ariz. Cain said Tuesday that he would not drop his bid for the Republicans’ presidential nomination in the face of decade-old allegations of inappropriate sexual behavior. (Charlie Leight)
A lone protester stands outside the Scottsdale Plaza Resort to protest Republican Presidential candidate Herman Cain who was addressing the media Tuesday, Nov. 8, 2011, in Scottsdale, Ariz. Cain said Tuesday that he would not drop his bid for the Republicans’ presidential nomination in the face of decade-old allegations of inappropriate sexual behavior. (Charlie Leight)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict59.jpg) Two members of People for the Ethical Treatment of Animals (PETA) who are covered from head to toe in green and blue bodypaint, as they hold a banner reading, “Save the Planet, Go Vegan,” at the Nanjing pedestrian street in Shanghai, China Wednesday, Nov. 9, 2011. (Eugene Hoshiko)
Two members of People for the Ethical Treatment of Animals (PETA) who are covered from head to toe in green and blue bodypaint, as they hold a banner reading, “Save the Planet, Go Vegan,” at the Nanjing pedestrian street in Shanghai, China Wednesday, Nov. 9, 2011. (Eugene Hoshiko)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict57.jpg) Protestors from Occupy Philly participate in a ‘die in’ demonstration outside a PNC Bank branch in Philadelphia on Monday Nov. 7, 2011. The demonstration was conducted to draw attention to PNC Bank’s business practices. (Joseph Kaczmarek)
Protestors from Occupy Philly participate in a ‘die in’ demonstration outside a PNC Bank branch in Philadelphia on Monday Nov. 7, 2011. The demonstration was conducted to draw attention to PNC Bank’s business practices. (Joseph Kaczmarek)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict54.jpg) A Syrian woman, who lives in Cairo, reacts as others wave a giant Syrian revolution flag during an anti-Syrian President Bashar Assad demonstration at Tahrir Square, the focal point of Egyptian uprisings, in Cairo, Egypt, Sunday, Nov. 6, 2011 to support protesters in Syria during the first day of Islamic Eid al-Adha, or Feast of the Sacrifice. (Amr Nabil)
A Syrian woman, who lives in Cairo, reacts as others wave a giant Syrian revolution flag during an anti-Syrian President Bashar Assad demonstration at Tahrir Square, the focal point of Egyptian uprisings, in Cairo, Egypt, Sunday, Nov. 6, 2011 to support protesters in Syria during the first day of Islamic Eid al-Adha, or Feast of the Sacrifice. (Amr Nabil)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict56.jpg) An activist of the Ukrainian female rights organization “Femen” shows a placard demanding freedom for women, during a protest at the end of Pope Benedict XVI’s Angelus prayer in St. Peter’s Square at the Vatican, Sunday, Nov. 6, 2011. (Pier Paolo Cito)
An activist of the Ukrainian female rights organization “Femen” shows a placard demanding freedom for women, during a protest at the end of Pope Benedict XVI’s Angelus prayer in St. Peter’s Square at the Vatican, Sunday, Nov. 6, 2011. (Pier Paolo Cito)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict55.jpg) Yemeni girls hold a giant Yemeni flag, left, as Syrians hold their revolution flag, right, during a protest against Yemeni and Syrian regimes at Tahrir Square, the focal point of Egyptian uprising, in Cairo, Egypt, Sunday, Nov. 6, 2011 to support protesters in Yemen and Syria during the first day of Islamic Eid al-Adha, or Feast of the Sacrifice. (Amr Nabil)
Yemeni girls hold a giant Yemeni flag, left, as Syrians hold their revolution flag, right, during a protest against Yemeni and Syrian regimes at Tahrir Square, the focal point of Egyptian uprising, in Cairo, Egypt, Sunday, Nov. 6, 2011 to support protesters in Yemen and Syria during the first day of Islamic Eid al-Adha, or Feast of the Sacrifice. (Amr Nabil)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict53.jpg) Amy Barnes protests as police move in to clear a downtown street during an Occupy Atlanta demonstration late Saturday, Nov. 5, 2011 in Atlanta. (David Goldman)
Amy Barnes protests as police move in to clear a downtown street during an Occupy Atlanta demonstration late Saturday, Nov. 5, 2011 in Atlanta. (David Goldman)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest5/pict58.jpg) In this Nov. 27, 2010 file photo, Susanna Camusso, leader of Italy’s largest labor confederation CGIL, arrives to deliver her speech during a demonstration to protest government policies regarding the economical crisis, in Rome. In an interview with The Associated Press Monday Nov. 7, 2011, Camusso is predicting 2012 will be a “terrifying” year for the economy even if beleaguered Premier Silvio Berlusconi leaves power soon.
In this Nov. 27, 2010 file photo, Susanna Camusso, leader of Italy’s largest labor confederation CGIL, arrives to deliver her speech during a demonstration to protest government policies regarding the economical crisis, in Rome. In an interview with The Associated Press Monday Nov. 7, 2011, Camusso is predicting 2012 will be a “terrifying” year for the economy even if beleaguered Premier Silvio Berlusconi leaves power soon.








![[Image]](https://i0.wp.com/cryptome.org/ows-shutdown-2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/ows-shutdown-4.jpg)






 In His Own Words “Mr. So and So, I understand that you’re going to whip any FBI agent that walks into your store. I’m not armed, but I wanted to let you know if you would like to whip me, let’s get started…”
In His Own Words “Mr. So and So, I understand that you’re going to whip any FBI agent that walks into your store. I’m not armed, but I wanted to let you know if you would like to whip me, let’s get started…”






 Intimidation…vandalism…assault…rape…murder. These are crimes by anyone’s definition. But add an element of bias against the victims—because of their race or religion, for example—and these traditional crimes become hate crimes.
Intimidation…vandalism…assault…rape…murder. These are crimes by anyone’s definition. But add an element of bias against the victims—because of their race or religion, for example—and these traditional crimes become hate crimes.
![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict38.jpg) Occupy Wall Street Encampment at Zuccotti Park seen is empty of demonstrators, Tuesday, Nov. 15, 2011 in New York. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Mary Altaffer)
Occupy Wall Street Encampment at Zuccotti Park seen is empty of demonstrators, Tuesday, Nov. 15, 2011 in New York. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict39.jpg) Occupy Wall Street protesters hold a general assembly meeting inside an enclosed site near Canal Street on Tuesday, Nov. 15, 2011. Hundreds of police officers in riot gear before dawn Tuesday raided the New York City park where the Occupy Wall Street protests began, evicting and arresting hundreds of protesters from what has become the epicenter of the worldwide movement protesting corporate greed and economic inequality. (Seth Wenig) [Photo taken and transmitted before Seth Wenig was arrested along with the protestors.]
Occupy Wall Street protesters hold a general assembly meeting inside an enclosed site near Canal Street on Tuesday, Nov. 15, 2011. Hundreds of police officers in riot gear before dawn Tuesday raided the New York City park where the Occupy Wall Street protests began, evicting and arresting hundreds of protesters from what has become the epicenter of the worldwide movement protesting corporate greed and economic inequality. (Seth Wenig) [Photo taken and transmitted before Seth Wenig was arrested along with the protestors.]![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict40.jpg) Police prepare to enter an enclosed site near Canal Street where Occupy Wall Street protesters gathered on Tuesday, Nov. 15, 2011. Hundreds of police officers in riot gear before dawn Tuesday raided the New York City park where the Occupy Wall Street protests began, evicting and arresting hundreds of protesters from what has become the epicenter of the worldwide movement protesting corporate greed and economic inequality. (Seth Wenig)
Police prepare to enter an enclosed site near Canal Street where Occupy Wall Street protesters gathered on Tuesday, Nov. 15, 2011. Hundreds of police officers in riot gear before dawn Tuesday raided the New York City park where the Occupy Wall Street protests began, evicting and arresting hundreds of protesters from what has become the epicenter of the worldwide movement protesting corporate greed and economic inequality. (Seth Wenig)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict34.jpg) Occupy Wall Street activists gain entrance in to Duarte Square to protest after police removed the protesters early in the morning from Zuccotti Park on November 15, 2011 in New York City. Getty
Occupy Wall Street activists gain entrance in to Duarte Square to protest after police removed the protesters early in the morning from Zuccotti Park on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict33.jpg) NYPD officers standoff with Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty
NYPD officers standoff with Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict27.jpg) NYPD officers clear out Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty [AP journalist Karen Matthews is at upper right in light blue jacket (and in earlier photos below). She was arrested with AP photographer Seth Wenig (at center in following photo).]
NYPD officers clear out Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty [AP journalist Karen Matthews is at upper right in light blue jacket (and in earlier photos below). She was arrested with AP photographer Seth Wenig (at center in following photo).]![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict37.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict31.jpg) NYPD officers arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty
NYPD officers arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict32.jpg) NYPD officers arrest Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty
NYPD officers arrest Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict28.jpg) NYPD officers attempt to arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty
NYPD officers attempt to arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict30.jpg) NYPD officers arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty
NYPD officers arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict26.jpg) NYPD officers arrest Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Police removed the protesters early in the morning from their encampment in Zuccotti Park. Hundreds of protesters, who rallied against inequality in America, have slept in tents and under tarps since September 17 in Zuccotti Park, which has since become the epicenter of the global Occupy movement. The raid in New York City follows recent similar moves in Oakland, California, and Portland, Oregon. Getty
NYPD officers arrest Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Police removed the protesters early in the morning from their encampment in Zuccotti Park. Hundreds of protesters, who rallied against inequality in America, have slept in tents and under tarps since September 17 in Zuccotti Park, which has since become the epicenter of the global Occupy movement. The raid in New York City follows recent similar moves in Oakland, California, and Portland, Oregon. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict20.jpg) Occupy Wall Street protesters return to Zuccotti Park on Tuesday, Nov. 15, 2011 in New York. After an early police raid removing protesters, hundreds returned to Zuccotti Park carrying photocopies of a court order they say gives them the right to return to the park. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules.
Occupy Wall Street protesters return to Zuccotti Park on Tuesday, Nov. 15, 2011 in New York. After an early police raid removing protesters, hundreds returned to Zuccotti Park carrying photocopies of a court order they say gives them the right to return to the park. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict21.jpg) Police arrest an Occupy Wall Street protester at Zuccotti Park on Tuesday, Nov. 15, 2011 in New York. After an early police raid removing protesters, hundreds returned to Zuccotti Park carrying photocopies of a court order they say gives them the right to return there.
Police arrest an Occupy Wall Street protester at Zuccotti Park on Tuesday, Nov. 15, 2011 in New York. After an early police raid removing protesters, hundreds returned to Zuccotti Park carrying photocopies of a court order they say gives them the right to return there.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict22.jpg) Occupy Wall Street protesters rally in a small park on Canal Street in New York, Tuesday, Nov. 15, 2011. Police officers evicted the protesters from their base in Zuccotti Park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)
Occupy Wall Street protesters rally in a small park on Canal Street in New York, Tuesday, Nov. 15, 2011. Police officers evicted the protesters from their base in Zuccotti Park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict23.jpg) A police officer watches from the grounds of City Hall as Occupy Wall Street protesters linked hands to block media from attending a news conference held by Mayor Michael Bloomberg in New York, Tuesday, Nov. 15, 2011. The protesters eventually dispersed peacefully.
A police officer watches from the grounds of City Hall as Occupy Wall Street protesters linked hands to block media from attending a news conference held by Mayor Michael Bloomberg in New York, Tuesday, Nov. 15, 2011. The protesters eventually dispersed peacefully.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict24.jpg) An empty and closed Zuccotti Park is seen in New York, Tuesday, Nov. 15, 2011. Police officers evicted Occupy Wall Street protesters from the park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)
An empty and closed Zuccotti Park is seen in New York, Tuesday, Nov. 15, 2011. Police officers evicted Occupy Wall Street protesters from the park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict25.jpg) A pedestrian takes a picture of an empty and closed Zuccotti Park in New York, Tuesday, Nov. 15, 2011. Police officers evicted Occupy Wall Street protesters from the park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)
A pedestrian takes a picture of an empty and closed Zuccotti Park in New York, Tuesday, Nov. 15, 2011. Police officers evicted Occupy Wall Street protesters from the park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict0.jpg) An Occupy Wall Street protestor draws contact from a police officer near Zuccotti Park after being ordered to leave the longtime encampment in New York, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park.
An Occupy Wall Street protestor draws contact from a police officer near Zuccotti Park after being ordered to leave the longtime encampment in New York, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict12.jpg) Occupy Wall Street protesters clash with police at Zuccotti Park after being ordered to leave their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Craig Ruttle)
Occupy Wall Street protesters clash with police at Zuccotti Park after being ordered to leave their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Craig Ruttle)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict1.jpg) An Occupy Wall Street protestor is arrested on the ground by police near Zuccotti Park after being ordered to leave their longtime encampment in New York, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park.
An Occupy Wall Street protestor is arrested on the ground by police near Zuccotti Park after being ordered to leave their longtime encampment in New York, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict14.jpg) A demonstrator yells at police officers as they order Occupy Wall Street protesters to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)
A demonstrator yells at police officers as they order Occupy Wall Street protesters to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict13.jpg) An Occupy Wall Street protester yells out at police after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)
An Occupy Wall Street protester yells out at police after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict3.jpg) Occupy Wall Street protesters clash with police near Zuccotti Park after being ordered to leave their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)
Occupy Wall Street protesters clash with police near Zuccotti Park after being ordered to leave their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict4.jpg) Occupy Wall Street protesters are pushed by police near the encampment at Zuccotti Park in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous.
Occupy Wall Street protesters are pushed by police near the encampment at Zuccotti Park in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict2.jpg) Demonstrators clash with police after being ordered to leave the Occupy Wall Street encampment at Zuccotti Park in New York on Tuesday, Nov. 15, 2011. Police handed out notices earlier from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Craig Ruttle)
Demonstrators clash with police after being ordered to leave the Occupy Wall Street encampment at Zuccotti Park in New York on Tuesday, Nov. 15, 2011. Police handed out notices earlier from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Craig Ruttle)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict6.jpg) An Occupy Wall Street protester is arrested by police near the encampment at Zuccotti Park in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents.
An Occupy Wall Street protester is arrested by police near the encampment at Zuccotti Park in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict7.jpg) An Occupy Wall Street protestor is arrested during a march on Broadway, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)
An Occupy Wall Street protestor is arrested during a march on Broadway, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict9.jpg) An Occupy Wall Street protester is detained by police officers after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)
An Occupy Wall Street protester is detained by police officers after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict10.jpg) Occupy Wall Street protesters are detained by police officers after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)
Occupy Wall Street protesters are detained by police officers after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict11.jpg) Occupy Wall Street demonstrators are arrested after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)
Occupy Wall Street demonstrators are arrested after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict17.jpg) Occupy Wall Street protesters march through the streets after they were evicted from Zuccotti Park on November 15, 2011 in New York. Hundreds of police in riot gear dismantled the Occupy Oakland camp Monday, evicting and arresting protesters in the second such US move in as many days as authorities get tough against the two-month-old protest movement. Getty
Occupy Wall Street protesters march through the streets after they were evicted from Zuccotti Park on November 15, 2011 in New York. Hundreds of police in riot gear dismantled the Occupy Oakland camp Monday, evicting and arresting protesters in the second such US move in as many days as authorities get tough against the two-month-old protest movement. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict8.jpg) A police officer carries trash through Zuccotti Park, the longtime encampment for Occupy Wall Street protesters in New York, as the cleanup effort begins early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)
A police officer carries trash through Zuccotti Park, the longtime encampment for Occupy Wall Street protesters in New York, as the cleanup effort begins early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict5.jpg) Two protesters and their dog, who said they have stayed slept with other protesters for the last 56 nights, sit along a police barricade at the edge of Zuccotti Park in New York, Tuesday, Nov. 15, 2011 after the Occupy Wall Street encampment was cleared from the park in the early morning hours after a nearly two month occupation,wa;;w and before the park reopened. (Craig Ruttle)
Two protesters and their dog, who said they have stayed slept with other protesters for the last 56 nights, sit along a police barricade at the edge of Zuccotti Park in New York, Tuesday, Nov. 15, 2011 after the Occupy Wall Street encampment was cleared from the park in the early morning hours after a nearly two month occupation,wa;;w and before the park reopened. (Craig Ruttle)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict16.jpg) New York City sanitation crews clean Zuccotti Park after city officials evicted the ‘Occupy Wall Street’ protest from the park in the early morning hours of November 15, 2011 in New York. Occupy Wall Street protestors most feared the coming winter, but it was on the mildest of nights, when activists slept soundly in their tents, that New York police sprang a surprise operation to end the eight-week demonstration. Getty
New York City sanitation crews clean Zuccotti Park after city officials evicted the ‘Occupy Wall Street’ protest from the park in the early morning hours of November 15, 2011 in New York. Occupy Wall Street protestors most feared the coming winter, but it was on the mildest of nights, when activists slept soundly in their tents, that New York police sprang a surprise operation to end the eight-week demonstration. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict15.jpg) People walk past New York Police Department officers guarding a closed Zuccotti Park after city officials evicted the ‘Occupy Wall Street’ protest from the park in the early morning hours of November 15, 2011 in New York. Getty
People walk past New York Police Department officers guarding a closed Zuccotti Park after city officials evicted the ‘Occupy Wall Street’ protest from the park in the early morning hours of November 15, 2011 in New York. Getty
 Nachfolgend bringen wir eine Original-Pressemeldung von „
Nachfolgend bringen wir eine Original-Pressemeldung von „










![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict26.jpg) An official from the Tokyo Electric Power Co. (TEPCO), wearing a protective suit and mask, uses a plastic covered megaphone to speak to fellow TEPCO workers and journalists as they drive towards the crippled Fukushima Dai-ichi nuclear power station in Okuma, Japan, Saturday, Nov. 12, 2011. Conditions at Japan’s wrecked Fukushima nuclear power plant, devastated by a tsunami in March, were slowly improving to the point where a “cold shutdown” would be possible as planned, officials said on Saturday during a tour of the facility. The nuclear reactor buildings were still surrounded by crumpled trucks, twisted metal fences, and large, dented water tanks. Smaller office buildings around the reactors were left as they were abandoned on March 11, when the tsunami hit.
An official from the Tokyo Electric Power Co. (TEPCO), wearing a protective suit and mask, uses a plastic covered megaphone to speak to fellow TEPCO workers and journalists as they drive towards the crippled Fukushima Dai-ichi nuclear power station in Okuma, Japan, Saturday, Nov. 12, 2011. Conditions at Japan’s wrecked Fukushima nuclear power plant, devastated by a tsunami in March, were slowly improving to the point where a “cold shutdown” would be possible as planned, officials said on Saturday during a tour of the facility. The nuclear reactor buildings were still surrounded by crumpled trucks, twisted metal fences, and large, dented water tanks. Smaller office buildings around the reactors were left as they were abandoned on March 11, when the tsunami hit.![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict25.jpg) Japanese police man a checkpoint near the edge of the contaminated exclusion zone around the crippled Fukushima Dai-ichi nuclear power station near Okuma, Fukushima prefecture, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
Japanese police man a checkpoint near the edge of the contaminated exclusion zone around the crippled Fukushima Dai-ichi nuclear power station near Okuma, Fukushima prefecture, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict13.jpg) A deserted street inside the contaminated exclusion zone around the crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011.
A deserted street inside the contaminated exclusion zone around the crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011.![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict22.jpg) A deserted field and buildings inside the contaminated exclusion zone around the crippled Fukushima Dai-ichi nuclear power station are seen through a bus window near Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
A deserted field and buildings inside the contaminated exclusion zone around the crippled Fukushima Dai-ichi nuclear power station are seen through a bus window near Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict23.jpg) An official from the Tokyo Electric Power Co., right, and an unidentified man, both wearing protective suits and masks ride on a bus as they pass by the crippled Fukushima Dai-ichi nuclear power station, seen through the window, in Okuma, Japan, Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
An official from the Tokyo Electric Power Co., right, and an unidentified man, both wearing protective suits and masks ride on a bus as they pass by the crippled Fukushima Dai-ichi nuclear power station, seen through the window, in Okuma, Japan, Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict20.jpg) Officials from the Tokyo Electric Power Co. and Japanese journalists look at the crippled Fukushima Dai-ichi nuclear power station from bus windows in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)
Officials from the Tokyo Electric Power Co. and Japanese journalists look at the crippled Fukushima Dai-ichi nuclear power station from bus windows in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict19.jpg) A view of Tokyo Electric Power Co’s tsunami-crippled Fukushima Daiichi nuclear power plant in Fukushima prefecture November 12, 2011. (David Guttenfelder, Pool)
A view of Tokyo Electric Power Co’s tsunami-crippled Fukushima Daiichi nuclear power plant in Fukushima prefecture November 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict2.jpg) The crippled Fukushima Daiichi nuclear power plant’s No.4, No.3, No.2 and No.1 (R-L) reactor buildings are seen from bus windows in Fukushima prefecture November 12, 2011. Reuters
The crippled Fukushima Daiichi nuclear power plant’s No.4, No.3, No.2 and No.1 (R-L) reactor buildings are seen from bus windows in Fukushima prefecture November 12, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict3.jpg) The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters
The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict21.jpg) The Unit 4 reactor building of the crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)
The Unit 4 reactor building of the crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict32.jpg) The Unit 4 reactor building of the crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
The Unit 4 reactor building of the crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict27.jpg) Broken vehicles are abandoned outside Unit 4 turbine building at the crippled Fukushima Dai-ichi nuclear power station as they are observed from inside a bus in Okuma, Fukushima Prefecture, Japan, Saturday, Nov. 12, 2011.
Broken vehicles are abandoned outside Unit 4 turbine building at the crippled Fukushima Dai-ichi nuclear power station as they are observed from inside a bus in Okuma, Fukushima Prefecture, Japan, Saturday, Nov. 12, 2011.![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict0.jpg) The crippled Fukushima Daiichi nuclear power plant’s upper part of the No.3 reactor building is seen from a bus window in Fukushima prefecture, November 12, 2011. Reuters
The crippled Fukushima Daiichi nuclear power plant’s upper part of the No.3 reactor building is seen from a bus window in Fukushima prefecture, November 12, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict29.jpg) The crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)
The crippled Fukushima Dai-ichi nuclear power station is seen through a bus window in Okuma, Japan Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned vehicles, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict4.jpg) The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters
The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict16.jpg) The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters
The crippled Fukushima Daiichi nuclear power plant is seen from bus windows in Fukushima prefecture, November 12, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict24.jpg) Crushed piping is observed from inside a bus at the crippled Fukushima Dai-ichi nuclear power station in Okuma, Fukushima Prefecture, Japan, Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned trucks, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (Ikuro Aiba, Pool)
Crushed piping is observed from inside a bus at the crippled Fukushima Dai-ichi nuclear power station in Okuma, Fukushima Prefecture, Japan, Saturday, Nov. 12, 2011. Media allowed into Japan’s tsunami-damaged nuclear power plant for the first time Saturday saw a striking scene of devastation: twisted and overturned trucks, crumbling reactor buildings and piles of rubble virtually untouched since the wave struck more than eight months ago. (Ikuro Aiba, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict31.jpg) Units five and six of the Fukushima Dai-ichi nuclear power station are seen through a bus window in Futaba, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
Units five and six of the Fukushima Dai-ichi nuclear power station are seen through a bus window in Futaba, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict28.jpg) Members of the media, wearing protective suits, interview Japan’s Minister of the Environment, Goshi Hosono, and Chief of the Fukushima Dai-ichi nuclear power plant, Masao Yoshida, inside the emergency operation center at the crippled nuclear power station in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
Members of the media, wearing protective suits, interview Japan’s Minister of the Environment, Goshi Hosono, and Chief of the Fukushima Dai-ichi nuclear power plant, Masao Yoshida, inside the emergency operation center at the crippled nuclear power station in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111211/pict33.jpg) Tokyo Electric Power Co. employees work inside the emergency operation center at the crippled Fukushima Dai-ichi nuclear power station in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)
Tokyo Electric Power Co. employees work inside the emergency operation center at the crippled Fukushima Dai-ichi nuclear power station in Okuma, Japan Saturday, Nov. 12, 2011. (David Guttenfelder, Pool)












 “Today, with the flip of a switch, the FBI and our partners dismantled the Rove criminal enterprise. Thanks to the collective effort across the U.S. and in Estonia, six leaders of the criminal enterprise have been arrested and numerous servers operated by the criminal organization have been disabled. Additionally, thanks to a coordinated effort of trusted industry partners, a mitigation plan commenced today, beginning with the replacement of rogue DNS servers with clean DNS servers to keep millions online, while providing ISPs the opportunity to coordinate user remediation efforts.”
“Today, with the flip of a switch, the FBI and our partners dismantled the Rove criminal enterprise. Thanks to the collective effort across the U.S. and in Estonia, six leaders of the criminal enterprise have been arrested and numerous servers operated by the criminal organization have been disabled. Additionally, thanks to a coordinated effort of trusted industry partners, a mitigation plan commenced today, beginning with the replacement of rogue DNS servers with clean DNS servers to keep millions online, while providing ISPs the opportunity to coordinate user remediation efforts.”







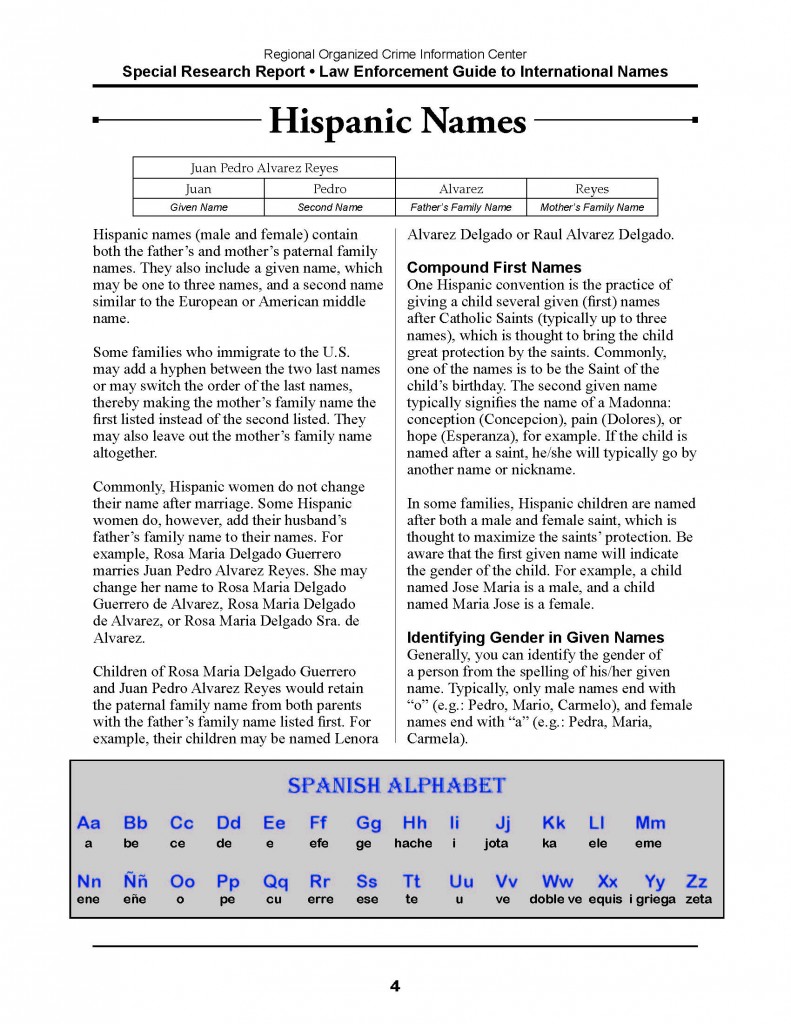
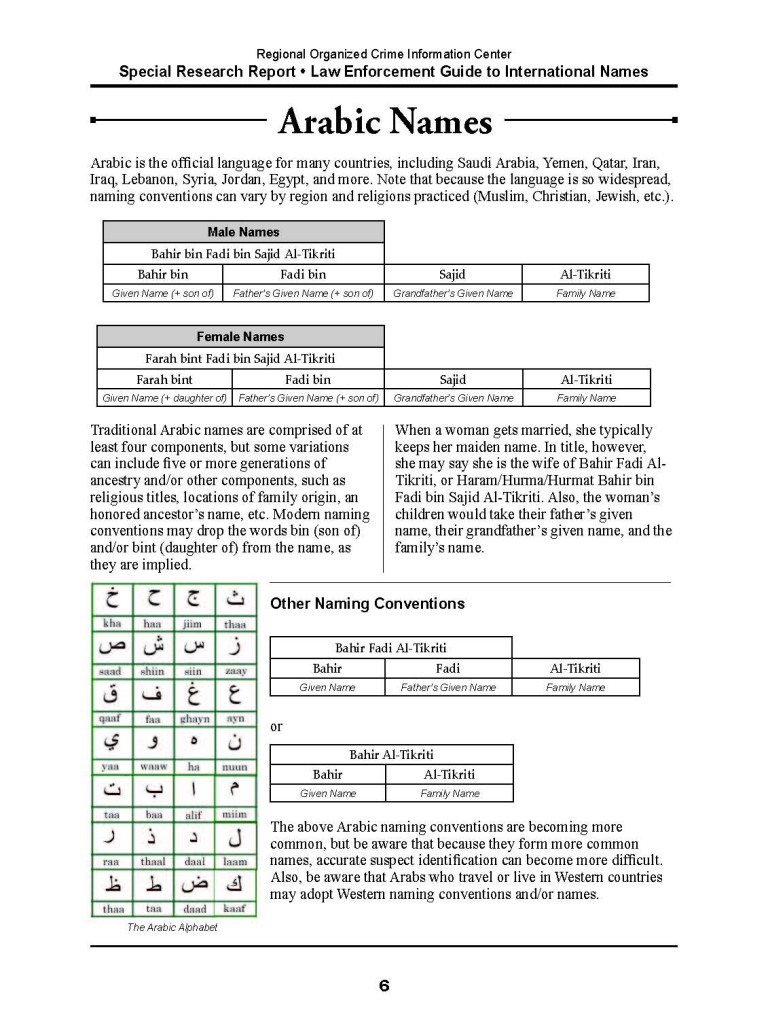

![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict17.jpg) Supporters of the Occupy London Stock Exchange protest take part in a mass meditation on the steps of St Paul’s Cathedral in London, Thursday, Oct. 27, 2011. The senior St. Paul’s Cathedral priest who welcomed anti-capitalist demonstrators to camp outside the London landmark resigned Thursday, saying he feared moves to evict the protesters could end in violence.
Supporters of the Occupy London Stock Exchange protest take part in a mass meditation on the steps of St Paul’s Cathedral in London, Thursday, Oct. 27, 2011. The senior St. Paul’s Cathedral priest who welcomed anti-capitalist demonstrators to camp outside the London landmark resigned Thursday, saying he feared moves to evict the protesters could end in violence.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict20.jpg) Young South Africans who brought their frustration over poverty and joblessness to the streets Thursday, responding to a call by Julius Malema, the tough-talking youth leader of the governing African National Congress, reach the Johannesburg Stock Exchange Thursday Oct. 27, 2011. Malema took the lead in the “economic freedom march” that left downtown Johannesburg by foot to the Stock Exchange, then on foot and by bus about 40 miles (60 kilometers) north to Pretoria, the seat of government.
Young South Africans who brought their frustration over poverty and joblessness to the streets Thursday, responding to a call by Julius Malema, the tough-talking youth leader of the governing African National Congress, reach the Johannesburg Stock Exchange Thursday Oct. 27, 2011. Malema took the lead in the “economic freedom march” that left downtown Johannesburg by foot to the Stock Exchange, then on foot and by bus about 40 miles (60 kilometers) north to Pretoria, the seat of government.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict18.jpg) Jackie Hayes of Binghamton, N.Y., speaks supporting the Occupy Wall Street movement rally at the state Capitol in Albany, N.Y., Thursday, Oct. 27, 2011. Several speakers criticized Gov. Andrew Cuomo for blocking a bill that would tax New Yorkers making over $1 million a year at a higher rate while cutting aid to schools, colleges and the poor. Cuomo, who was in New York City, had no immediate comment Thursday. (Hans Pennink)
Jackie Hayes of Binghamton, N.Y., speaks supporting the Occupy Wall Street movement rally at the state Capitol in Albany, N.Y., Thursday, Oct. 27, 2011. Several speakers criticized Gov. Andrew Cuomo for blocking a bill that would tax New Yorkers making over $1 million a year at a higher rate while cutting aid to schools, colleges and the poor. Cuomo, who was in New York City, had no immediate comment Thursday. (Hans Pennink)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict10.jpg) Security guards detain an activist of the Ukrainian female rights organization “Femen”, during an action of nude protest in front of Kiev Zoo, Ukraine, Thursday, Oct. 27, 2011. Kiev zoo is a place that Femen’s activists compared to a concentration camp for those with fur and feathers. Hundreds of animals died at the zoo in recent years due to malnutrition, lack of medical care and abuse, and some suspect that corruption is at the heart of the problem. Femen calls for the 100-year-old zoo to be closed.
Security guards detain an activist of the Ukrainian female rights organization “Femen”, during an action of nude protest in front of Kiev Zoo, Ukraine, Thursday, Oct. 27, 2011. Kiev zoo is a place that Femen’s activists compared to a concentration camp for those with fur and feathers. Hundreds of animals died at the zoo in recent years due to malnutrition, lack of medical care and abuse, and some suspect that corruption is at the heart of the problem. Femen calls for the 100-year-old zoo to be closed.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict11.jpg) South Korea protesters stage a rally to protest against a free trade agreement (FTA) between South Korea and the United States near the National Assembly in Seoul, South Korea, Thursday, Oct. 27, 2011. The ruling Grand National Party and the government have set Friday, Oct. 28, as the deadline for ratifying the FTA bill. The letters read: ” Block the FTA between South Korea and the United States.” (Ahn Young-joon)
South Korea protesters stage a rally to protest against a free trade agreement (FTA) between South Korea and the United States near the National Assembly in Seoul, South Korea, Thursday, Oct. 27, 2011. The ruling Grand National Party and the government have set Friday, Oct. 28, as the deadline for ratifying the FTA bill. The letters read: ” Block the FTA between South Korea and the United States.” (Ahn Young-joon)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict12.jpg) Supporters of the Occupy London Stock Exchange movement hold protest placards against bankers betting on food prices in financial markets outside a branch of the Goldman Sachs banking firm on Fleet Street in London, Thursday, Oct. 27, 2011. A police officer, second left, stands guarding the front door and one of the demonstrators, second right, is wearing a mask representing Britain’s Chancellor of the Exchequer George Osborne. (Matt Dunham)
Supporters of the Occupy London Stock Exchange movement hold protest placards against bankers betting on food prices in financial markets outside a branch of the Goldman Sachs banking firm on Fleet Street in London, Thursday, Oct. 27, 2011. A police officer, second left, stands guarding the front door and one of the demonstrators, second right, is wearing a mask representing Britain’s Chancellor of the Exchequer George Osborne. (Matt Dunham)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict8.jpg) A female Yemeni protestor burns veils during a demonstration demanding the resignation of Yemeni President Ali Abdullah Saleh in Sanaa, Yemen, Wednesday, Oct. 26, 2011. The burning of the veil was not related to women’s rights or issues surrounding the Islamic veils – rather, the act of women burning their clothing is a symbolic Bedouin tribal gesture signifying an appeal for help to tribesmen, in this case to stop the attacks on women protesters. (Hani Mohammed)
A female Yemeni protestor burns veils during a demonstration demanding the resignation of Yemeni President Ali Abdullah Saleh in Sanaa, Yemen, Wednesday, Oct. 26, 2011. The burning of the veil was not related to women’s rights or issues surrounding the Islamic veils – rather, the act of women burning their clothing is a symbolic Bedouin tribal gesture signifying an appeal for help to tribesmen, in this case to stop the attacks on women protesters. (Hani Mohammed)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict9.jpg) Occupy Wall Street protesters continue to increase their makeshift shelter at Zuccotti Park, Tuesday, Oct. 25, 2011 in New York. While some businesses and residents are losing patience with the protesters in Zuccotti Park, organizers say they are receiving and storing heavy duty winter supplies to protest throughout the winter. (Bebeto Matthews)
Occupy Wall Street protesters continue to increase their makeshift shelter at Zuccotti Park, Tuesday, Oct. 25, 2011 in New York. While some businesses and residents are losing patience with the protesters in Zuccotti Park, organizers say they are receiving and storing heavy duty winter supplies to protest throughout the winter. (Bebeto Matthews)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict7.jpg) Anti-corporate protesters pose for pictures as they stand next to tents of their protest camp outside St Paul’s Cathedral, in central London, Wednesday, Oct. 26, 2011. As authorities around the world swoop in to evict anti-corporate protesters, London’s protest camp has become a tourist attraction _ one that has shut down the landmark St. Paul’s Cathedral.
Anti-corporate protesters pose for pictures as they stand next to tents of their protest camp outside St Paul’s Cathedral, in central London, Wednesday, Oct. 26, 2011. As authorities around the world swoop in to evict anti-corporate protesters, London’s protest camp has become a tourist attraction _ one that has shut down the landmark St. Paul’s Cathedral.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict6.jpg) University students carry mock coffins that read in Spanish “Here rests a fundamental right,” left, and “Colombian education, 1867-2012,” right, during a protest in Bogota, Colombia, Wednesday Oct. 26, 2011. Students are protesting education reforms planned by the government that propose private funding for public institutions. (Fernando Vergara)
University students carry mock coffins that read in Spanish “Here rests a fundamental right,” left, and “Colombian education, 1867-2012,” right, during a protest in Bogota, Colombia, Wednesday Oct. 26, 2011. Students are protesting education reforms planned by the government that propose private funding for public institutions. (Fernando Vergara)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict5.jpg) Occupy Wall Street protesters huddle together after police use tear gas to disperse a large crowd that gathered at 14th Street and Broadway in Oakland, Calif., Tuesday, October 25, 2011. Many demonstrators were arrested. (Darryl Bush)
Occupy Wall Street protesters huddle together after police use tear gas to disperse a large crowd that gathered at 14th Street and Broadway in Oakland, Calif., Tuesday, October 25, 2011. Many demonstrators were arrested. (Darryl Bush)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict3.jpg) A protestor yells as police seal off Woodruff Park to arrest those refusing to leave after Mayor Kasim Reed revoked his executive order allowing the Occupy Atlanta protestors to camp out in Woodruff Park Tuesday, Oct. 25, 2011 in Atlanta. (David Goldman)
A protestor yells as police seal off Woodruff Park to arrest those refusing to leave after Mayor Kasim Reed revoked his executive order allowing the Occupy Atlanta protestors to camp out in Woodruff Park Tuesday, Oct. 25, 2011 in Atlanta. (David Goldman)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict4.jpg) North Korean defectors and South Korean civic members hold banners during a rally for North Korean refugees who were repatriated by the Chinese government, in front of the Chinese Embassy in Seoul, South Korea, Wednesday, Oct. 26, 2011. The protesters called for China not to send North Korean refugees back to their country, saying those refugees might get executed. About 30 protesters participated at a rally. (Lee Jin-man)
North Korean defectors and South Korean civic members hold banners during a rally for North Korean refugees who were repatriated by the Chinese government, in front of the Chinese Embassy in Seoul, South Korea, Wednesday, Oct. 26, 2011. The protesters called for China not to send North Korean refugees back to their country, saying those refugees might get executed. About 30 protesters participated at a rally. (Lee Jin-man)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict0.jpg) Police officers detain an opposition demonstrator during an unsanctioned rally on Triumfalnaya Square in downtown Moscow, Russia, Tuesday, Oct. 25, 2011. Several dozens people have been detained at an opposition rally in central Moscow where they were protesting against the lack of alternatives in the upcoming parliamentary and presidential elections. The posters, placed on a fence around a construction site, campaigns against violence to children by the national foundation to support children.
Police officers detain an opposition demonstrator during an unsanctioned rally on Triumfalnaya Square in downtown Moscow, Russia, Tuesday, Oct. 25, 2011. Several dozens people have been detained at an opposition rally in central Moscow where they were protesting against the lack of alternatives in the upcoming parliamentary and presidential elections. The posters, placed on a fence around a construction site, campaigns against violence to children by the national foundation to support children.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict2.jpg) Swedish protester Rebecka Kullberg applies make-up beside a second protest campsite formed on Saturday by supporters of the Occupy London Stock Exchange group in Finsbury Square, London, Tuesday, Oct. 25, 2011. The Occupy protests over economic inequality have spread from a single camp in New York City to cities across the United States, Europe and Asia since mid-September. (Matt Dunham)
Swedish protester Rebecka Kullberg applies make-up beside a second protest campsite formed on Saturday by supporters of the Occupy London Stock Exchange group in Finsbury Square, London, Tuesday, Oct. 25, 2011. The Occupy protests over economic inequality have spread from a single camp in New York City to cities across the United States, Europe and Asia since mid-September. (Matt Dunham)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict1.jpg) Atlanta Mayor Kasim Reed, far left, faced off with Occupy Atlanta protesters during the mayor’s news conference at City Hall in Atlanta on Monday, Oct. 24, 2011. A protester holds a paper that reads Occupy Wall St. goes global as the mayor leaves. (Curtis Compton)
Atlanta Mayor Kasim Reed, far left, faced off with Occupy Atlanta protesters during the mayor’s news conference at City Hall in Atlanta on Monday, Oct. 24, 2011. A protester holds a paper that reads Occupy Wall St. goes global as the mayor leaves. (Curtis Compton)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict200.jpg) An exile Tibetan woman cries out as she scuffles with Indian police outside the United Nations Information Center at a protest seeking U.N. intervention in the Tibet issue in New Delhi, India, Monday, Oct. 24, 2011. The protest was held to express solidarity with the plight of people in Tibet who set themselves on fire in protest against Chinese rule. (Mustafa Quraishi)
An exile Tibetan woman cries out as she scuffles with Indian police outside the United Nations Information Center at a protest seeking U.N. intervention in the Tibet issue in New Delhi, India, Monday, Oct. 24, 2011. The protest was held to express solidarity with the plight of people in Tibet who set themselves on fire in protest against Chinese rule. (Mustafa Quraishi)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict199.jpg) Russian police officers detain a protester as she shouts anti-government slogans during an unsanctioned pro-democracy rally in front of Central Election commission office in downtown Moscow, Russia, Monday, Oct. 24, 2011. (Ivan Sekretarev)
Russian police officers detain a protester as she shouts anti-government slogans during an unsanctioned pro-democracy rally in front of Central Election commission office in downtown Moscow, Russia, Monday, Oct. 24, 2011. (Ivan Sekretarev)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict197.jpg) President of Kashmir’s main opposition People’s Democratic Party (PDP) Mehbooba Mufti, center, addresses supporters during a protest in Srinagar, India, Monday, Oct. 24, 2011. Indian police in Srinagar on Monday stopped a protest march led by Mufti against the Jammu Kashmir state government’s alleged mass corruption. (Mukhtar Khan)
President of Kashmir’s main opposition People’s Democratic Party (PDP) Mehbooba Mufti, center, addresses supporters during a protest in Srinagar, India, Monday, Oct. 24, 2011. Indian police in Srinagar on Monday stopped a protest march led by Mufti against the Jammu Kashmir state government’s alleged mass corruption. (Mukhtar Khan)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict196.jpg) Supporters of Sri Lanka’s Marxist Party, known as Peoples Liberation Front, shout slogans during a protest against the rising cost of living in Colombo, Sri Lanka, Monday, Oct. 24, 2011. (Eranga Jayawardena)
Supporters of Sri Lanka’s Marxist Party, known as Peoples Liberation Front, shout slogans during a protest against the rising cost of living in Colombo, Sri Lanka, Monday, Oct. 24, 2011. (Eranga Jayawardena)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict174.jpg) Paramedics carry a wounded woman to an ambulance at Athens’ main Syntagma Square, during violent demonstrations, Thursday, Oct. 20, 2011. A protester died during an anti-austerity demonstration that turned violent in the Greek capital Thursday, authorities said, hours before lawmakers were to vote on deeply unpopular new cutbacks demanded by creditors to keep Greece afloat. (Lefteris Pitarakis)
Paramedics carry a wounded woman to an ambulance at Athens’ main Syntagma Square, during violent demonstrations, Thursday, Oct. 20, 2011. A protester died during an anti-austerity demonstration that turned violent in the Greek capital Thursday, authorities said, hours before lawmakers were to vote on deeply unpopular new cutbacks demanded by creditors to keep Greece afloat. (Lefteris Pitarakis)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict183.jpg) Two police officers hold a woman during clashes in Rome, Saturday, Oct. 15, 2011. Italian police fired tear gas and water cannons as protesters in Rome turned a demonstration against corporate greed into a riot Saturday, smashing shop and bank windows, torching cars and hurling bottles. The protest in the Italian capital was part of Occupy Wall Street demonstrations against capitalism and austerity measures that went global Saturday, leading to dozens of marches and protests worldwide.
Two police officers hold a woman during clashes in Rome, Saturday, Oct. 15, 2011. Italian police fired tear gas and water cannons as protesters in Rome turned a demonstration against corporate greed into a riot Saturday, smashing shop and bank windows, torching cars and hurling bottles. The protest in the Italian capital was part of Occupy Wall Street demonstrations against capitalism and austerity measures that went global Saturday, leading to dozens of marches and protests worldwide.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict187.jpg) Dr. Angelina Shigeura, 31, left, and Dr. Amit Patel, 29, right, chant during a demonstration by doctors and medical professionals at the Occupy Wall Street protests in Zuccotti Park, Sunday, Oct. 23, 2011, in New York. Doctors from the National Health Program and National Physicians Alliance have merged with the health care demonstrators within the Occupy Wall Street protests to form a group under the banner of “Healthcare for the 99%” and speak out against corporate greed in the medical industry. (John Minchillo)
Dr. Angelina Shigeura, 31, left, and Dr. Amit Patel, 29, right, chant during a demonstration by doctors and medical professionals at the Occupy Wall Street protests in Zuccotti Park, Sunday, Oct. 23, 2011, in New York. Doctors from the National Health Program and National Physicians Alliance have merged with the health care demonstrators within the Occupy Wall Street protests to form a group under the banner of “Healthcare for the 99%” and speak out against corporate greed in the medical industry. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict191.jpg) Protesters march for a healthier and pollutant free environment during a demonstration called by the South Durban Community Environmental Alliance (SDCEA), a Non-Government Organisation (NGO), in Durban on October 22, 2011. The protest initiated by the SDCEA comes after a fire broke out at the Engen Oil Refinery on October 11 and around one hundred school children have been hospitalised for smoke and toxic fume inhalation. Durban will host the 17 th Conference of Parties (COP) International Climate Change Conference in Durban in December 2011. Getty
Protesters march for a healthier and pollutant free environment during a demonstration called by the South Durban Community Environmental Alliance (SDCEA), a Non-Government Organisation (NGO), in Durban on October 22, 2011. The protest initiated by the SDCEA comes after a fire broke out at the Engen Oil Refinery on October 11 and around one hundred school children have been hospitalised for smoke and toxic fume inhalation. Durban will host the 17 th Conference of Parties (COP) International Climate Change Conference in Durban in December 2011. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict188.jpg) Demonstrators cut a barbed wire fence as they march during a protest against the construction of a high-speed train line, known as TAV, which will link Turin in northern Italy to Lyon in France, near Chiomonte, north of Turin October 23, 2011. Reuters
Demonstrators cut a barbed wire fence as they march during a protest against the construction of a high-speed train line, known as TAV, which will link Turin in northern Italy to Lyon in France, near Chiomonte, north of Turin October 23, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict192.jpg) Protesters shout as they take part in the ProAlt demonstration at the Old Town Square in Prague on October 22, 2011, to protest against the government planned budget cuts and social reforms. Over one thousand protesters, including Communist Union of Youth, trade unionists, members of organisations for people with disabilities and Czech Roma organisations, demonstrated in Prague. Getty
Protesters shout as they take part in the ProAlt demonstration at the Old Town Square in Prague on October 22, 2011, to protest against the government planned budget cuts and social reforms. Over one thousand protesters, including Communist Union of Youth, trade unionists, members of organisations for people with disabilities and Czech Roma organisations, demonstrated in Prague. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict193.jpg) ‘Occupy Melbourne’ demonstrators protest on October 22, 2011 in Melbourne, Australia. Protesters and riot police clashed in Melbourne again today after police, acting on a Melbourne City Council eviction order, attempted to break up the crowd of hundreds that had been positioned in City Square for a week. Getty
‘Occupy Melbourne’ demonstrators protest on October 22, 2011 in Melbourne, Australia. Protesters and riot police clashed in Melbourne again today after police, acting on a Melbourne City Council eviction order, attempted to break up the crowd of hundreds that had been positioned in City Square for a week. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict185.jpg) Demonstrators chant slogans against Hungarian Prime Minister Viktor Orban during an anti-government demonstration in Budapest, Hungary, Sunday, Oct. 23, 2011. Tens of thousands of Hungarians gathered to protest against Orban’s government at the 55th anniversary of the 1956 Hungarian revolution. (Bela Szandelszky)
Demonstrators chant slogans against Hungarian Prime Minister Viktor Orban during an anti-government demonstration in Budapest, Hungary, Sunday, Oct. 23, 2011. Tens of thousands of Hungarians gathered to protest against Orban’s government at the 55th anniversary of the 1956 Hungarian revolution. (Bela Szandelszky)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict189.jpg) Hungarian women listen to a speech during a demonstration attended by tens of thousands of people in Budapest on October 23, 2011 to protest against what they call the anti-democratic regime of Prime Minister Viktor Orban, on the anniversary of the 1956 revolution. Hungary’s uprising erupted on October 23, 1956 and was crushed by Soviet tanks on November 4, sealing the country’s fate as a satellite state of Moscow until the fall of the Iron Curtain in 1989. Getty
Hungarian women listen to a speech during a demonstration attended by tens of thousands of people in Budapest on October 23, 2011 to protest against what they call the anti-democratic regime of Prime Minister Viktor Orban, on the anniversary of the 1956 revolution. Hungary’s uprising erupted on October 23, 1956 and was crushed by Soviet tanks on November 4, sealing the country’s fate as a satellite state of Moscow until the fall of the Iron Curtain in 1989. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict175.jpg) Kurdish protesters opposed to President Bashar Assad, shout slogans as they demonstrate against the Syrian regime, during a sit-in in front of the Syrian embassy, in Beirut, Lebanon, Sunday, Oct. 23, 2011. The banner at left in Arabic reads: “down with the present gang. We want a civil state.” (Bilal Hussein)
Kurdish protesters opposed to President Bashar Assad, shout slogans as they demonstrate against the Syrian regime, during a sit-in in front of the Syrian embassy, in Beirut, Lebanon, Sunday, Oct. 23, 2011. The banner at left in Arabic reads: “down with the present gang. We want a civil state.” (Bilal Hussein)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict178.jpg) A protester gets arrested during an Occupy Chicago march and protest in Grant Park in Chicago, Sunday, Oct. 23, 2011. Demonstrators of the anti-Wall Street group Occupy Chicago stood their ground in the park and defied police orders to clear the area, prompting police to make more than a dozen arrests early Sunday. (Paul Beaty)
A protester gets arrested during an Occupy Chicago march and protest in Grant Park in Chicago, Sunday, Oct. 23, 2011. Demonstrators of the anti-Wall Street group Occupy Chicago stood their ground in the park and defied police orders to clear the area, prompting police to make more than a dozen arrests early Sunday. (Paul Beaty)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict179.jpg) Protesters are arrested during an Occupy Chicago march and protest at Grant Park in Chicago Sunday, Oct. 23, 2011. Demonstrators of the anti-Wall Street group Occupy Chicago stood their ground in the park and defied police orders to clear the area, prompting police to make more than a dozen arrests early Sunday. (Paul Beaty)
Protesters are arrested during an Occupy Chicago march and protest at Grant Park in Chicago Sunday, Oct. 23, 2011. Demonstrators of the anti-Wall Street group Occupy Chicago stood their ground in the park and defied police orders to clear the area, prompting police to make more than a dozen arrests early Sunday. (Paul Beaty)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict186.jpg) Occupy Wall Street protestors hold a meeting to discuss the use of funds for cleaning supplies proceeding a proposed cleanup of their camp in Zuccotti Park, Saturday, Oct. 22, 2011, in New York. The protests continue to draw large crowds and fresh participants as similar demonstrations are occuring around the world. (John Minchillo)
Occupy Wall Street protestors hold a meeting to discuss the use of funds for cleaning supplies proceeding a proposed cleanup of their camp in Zuccotti Park, Saturday, Oct. 22, 2011, in New York. The protests continue to draw large crowds and fresh participants as similar demonstrations are occuring around the world. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict170.jpg) Demonstrators associated with the Occupy Wall Street march past New York City police officers towards a rally against police brutality at Union Square, Saturday, Oct. 22, 2011 in New York. (Mary Altaffer)
Demonstrators associated with the Occupy Wall Street march past New York City police officers towards a rally against police brutality at Union Square, Saturday, Oct. 22, 2011 in New York. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict147.jpg) Activists vote during a meeting held amid tents in front of St Paul’s Cathedral in London October 22, 2011. London’s landmark St Paul’s Cathedral closed its doors on Friday because of hazards posed by hundreds of protesters encamped in front of it in a demonstration inspired by the Occupy Wall Street movement. Reuters
Activists vote during a meeting held amid tents in front of St Paul’s Cathedral in London October 22, 2011. London’s landmark St Paul’s Cathedral closed its doors on Friday because of hazards posed by hundreds of protesters encamped in front of it in a demonstration inspired by the Occupy Wall Street movement. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict149.jpg) Iranian women gather for a protest in support of the Occupy Wall Street movement outside the Swiss embassy which handles US interests in Tehran on October 22, 2011. Getty
Iranian women gather for a protest in support of the Occupy Wall Street movement outside the Swiss embassy which handles US interests in Tehran on October 22, 2011. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict150.jpg) A protestor looks from her tent during an occupation protest in Finsbury Square in the city of London on October 22, 2011. Saint Paul’s Cathedral remains closed for the first time in modern history because of anti-capitalist demonstrators camping outside the London landmark. More than 200 activists inspired by the Occupy Wall Street movement have taken over the churchyard in front of the cathedral in the city’s financial district since last October 15 to protest against corporate greed and state cutbacks. Getty
A protestor looks from her tent during an occupation protest in Finsbury Square in the city of London on October 22, 2011. Saint Paul’s Cathedral remains closed for the first time in modern history because of anti-capitalist demonstrators camping outside the London landmark. More than 200 activists inspired by the Occupy Wall Street movement have taken over the churchyard in front of the cathedral in the city’s financial district since last October 15 to protest against corporate greed and state cutbacks. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict151.jpg) Demonstrators associated with the Occupy Wall Street march through the streets of the East Village neighborhood of Manhattan during a rally against police brutality on Saturday, Oct. 22, 2011. The demonstration marked Saturday’s observance of the “National Day of Protest to Stop Police Brutality, Repression and the Criminalization of a Generation.” AP
Demonstrators associated with the Occupy Wall Street march through the streets of the East Village neighborhood of Manhattan during a rally against police brutality on Saturday, Oct. 22, 2011. The demonstration marked Saturday’s observance of the “National Day of Protest to Stop Police Brutality, Repression and the Criminalization of a Generation.” AP![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict152.jpg) People take a picture of themselves as a souvenir at the location where Occupy Wall Street members are resting at Zuccotti park in New York October 22, 2011. Reuters
People take a picture of themselves as a souvenir at the location where Occupy Wall Street members are resting at Zuccotti park in New York October 22, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict153.jpg) Protestors and members of Occupy Wall Street shout slogans next to NYPD officers, during an annual demonstration calling for a stop to police brutality in New York October 22, 2011. Reuters
Protestors and members of Occupy Wall Street shout slogans next to NYPD officers, during an annual demonstration calling for a stop to police brutality in New York October 22, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict154.jpg) The Council on American Islamic Relations New York Chapter (CAIR-NY) holds Friday prayers with Demonstrators with ‘Occupy Wall Street’ continue their protest at Zuccotti Park in New York on October 21, 2011. The encampment in the financial district of New York City is now in its second month. The demonstrators are protesting bank bailouts, foreclosures and high unemployment. Getty
The Council on American Islamic Relations New York Chapter (CAIR-NY) holds Friday prayers with Demonstrators with ‘Occupy Wall Street’ continue their protest at Zuccotti Park in New York on October 21, 2011. The encampment in the financial district of New York City is now in its second month. The demonstrators are protesting bank bailouts, foreclosures and high unemployment. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict155.jpg) A lady meditates on the outer wall of Zuccotti Park at the Occupy Wall Street Encampment in New York October 21, 2011. Reuters
A lady meditates on the outer wall of Zuccotti Park at the Occupy Wall Street Encampment in New York October 21, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict156.jpg) Demonstrators with ‘Occupy Wall Street’ continue their protest at Zuccotti Park in New York on October 21, 2011. The encampment in the financial district of New York City is now in its second month. The demonstrators are protesting bank bailouts, foreclosures and high unemployment. Getty
Demonstrators with ‘Occupy Wall Street’ continue their protest at Zuccotti Park in New York on October 21, 2011. The encampment in the financial district of New York City is now in its second month. The demonstrators are protesting bank bailouts, foreclosures and high unemployment. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict176.jpg) Swiss Copts demonstrate against violence and injustice directed against their community in Egypt at the Place des Nations in front of the European headquarters of the United Nations in Geneva, Switzerland, Friday, Oct. 21, 2011. (Martial Trezzini)
Swiss Copts demonstrate against violence and injustice directed against their community in Egypt at the Place des Nations in front of the European headquarters of the United Nations in Geneva, Switzerland, Friday, Oct. 21, 2011. (Martial Trezzini)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict157.jpg) Demonstrators with ‘Occupy Wall Street’ continue their protest at Zuccotti Park in New York on October 21, 2011. The encampment in the financial district of New York City is now in its second month. The demonstrators are protesting bank bailouts, foreclosures and high unemployment. Getty
Demonstrators with ‘Occupy Wall Street’ continue their protest at Zuccotti Park in New York on October 21, 2011. The encampment in the financial district of New York City is now in its second month. The demonstrators are protesting bank bailouts, foreclosures and high unemployment. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict158.jpg) A woman sits outside the closed doors of St Paul’s Cathedral in the city of London on October 21, 2011. St Paul’s Cathedral said Friday it was closing its doors to the public for the first time in modern history because of anti-capitalist demonstrators camping outside the London landmark. More than 200 activists inspired by the Occupy Wall Street movement have taken over the churchyard in front of the cathedral in the city’s financial district since last Saturday to protest against corporate greed and state cutbacks. Getty
A woman sits outside the closed doors of St Paul’s Cathedral in the city of London on October 21, 2011. St Paul’s Cathedral said Friday it was closing its doors to the public for the first time in modern history because of anti-capitalist demonstrators camping outside the London landmark. More than 200 activists inspired by the Occupy Wall Street movement have taken over the churchyard in front of the cathedral in the city’s financial district since last Saturday to protest against corporate greed and state cutbacks. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict159.jpg) Margie Levinthal holds a sign during a march from City Hall to the Wharton School of Business at Pennsylvania University Friday, Oct. 21, 2011 in Philadelphia. The demonstration at City Hall is one of many being held across the country in conjunction with the Occupy Wall Street demonstration in New York. AP
Margie Levinthal holds a sign during a march from City Hall to the Wharton School of Business at Pennsylvania University Friday, Oct. 21, 2011 in Philadelphia. The demonstration at City Hall is one of many being held across the country in conjunction with the Occupy Wall Street demonstration in New York. AP![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict171.jpg) Protesters display placards during a rally at the financial district of Makati city, east of Manila, Philippines Friday Oct. 21, 2011 in support of the new wave of protests around the globe known as “Occupy Wall Street.” The protesters singled out the country’s three big oil companies as “greedy for profit” as they raised anew this week the pump prices of gasoline and other oil products. (Bullit Marquez)
Protesters display placards during a rally at the financial district of Makati city, east of Manila, Philippines Friday Oct. 21, 2011 in support of the new wave of protests around the globe known as “Occupy Wall Street.” The protesters singled out the country’s three big oil companies as “greedy for profit” as they raised anew this week the pump prices of gasoline and other oil products. (Bullit Marquez)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict161.jpg) Marylou Wagner, left, and her grandchildren, Anthony Evenson, second from left, Phoebe Wagner, and Caitlin Wiesenborn, right, all from Fort Plain, N.Y. , demonstrate while supporting the Occupy Wall Street movement as protesters set up an encampment in Albany, N.Y. , Friday, Oct. 21, 2011. AP
Marylou Wagner, left, and her grandchildren, Anthony Evenson, second from left, Phoebe Wagner, and Caitlin Wiesenborn, right, all from Fort Plain, N.Y. , demonstrate while supporting the Occupy Wall Street movement as protesters set up an encampment in Albany, N.Y. , Friday, Oct. 21, 2011. AP![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict162.jpg) Demonstrators with ‘Occupy Wall Street’ continue their protest at Zuccotti Park in New York on October 20, 2011. The encampment in the financial district of New York City is now in its second month. The demonstrators are protesting bank bailouts, foreclosures and high unemployment. Getty
Demonstrators with ‘Occupy Wall Street’ continue their protest at Zuccotti Park in New York on October 20, 2011. The encampment in the financial district of New York City is now in its second month. The demonstrators are protesting bank bailouts, foreclosures and high unemployment. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict172.jpg) Authorities, from left, front, Chile’s Education Minister Felipe Bulnes, Santiago University Rector Juan Manuel Zolezzi, and Chile’s Senator Ena Anglein von Baer, fourth from left, looks on as protesters carrying a banner that reads in Spanish “Plebiscite now,” stand on a table during a protest at the Chilean Senator headquarters in Santiago, Chile, Thursday Oct. 20, 2011. Students and other protesters interrupted a Senate committee meeting to demand a popular referendum on how to resolve Chile’s social problems, especially education. They left the building after receiving a promise from opposition lawmakers to present a proposal to hold a plebiscite.(Luis Hidalgo)
Authorities, from left, front, Chile’s Education Minister Felipe Bulnes, Santiago University Rector Juan Manuel Zolezzi, and Chile’s Senator Ena Anglein von Baer, fourth from left, looks on as protesters carrying a banner that reads in Spanish “Plebiscite now,” stand on a table during a protest at the Chilean Senator headquarters in Santiago, Chile, Thursday Oct. 20, 2011. Students and other protesters interrupted a Senate committee meeting to demand a popular referendum on how to resolve Chile’s social problems, especially education. They left the building after receiving a promise from opposition lawmakers to present a proposal to hold a plebiscite.(Luis Hidalgo)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict173.jpg) A student voluntarily leaves the Senate headquarters seized earlier by dozens of students in Santiago, Chile, Thursday Oct. 20, 2011. Students and other protesters interrupted a Senate committee meeting to demand a popular referendum on how to resolve Chile’s social problems, especially education. They left the building after receiving a promise from opposition lawmakers to present a proposal to hold a plebiscite.(Luis Hidalgo)
A student voluntarily leaves the Senate headquarters seized earlier by dozens of students in Santiago, Chile, Thursday Oct. 20, 2011. Students and other protesters interrupted a Senate committee meeting to demand a popular referendum on how to resolve Chile’s social problems, especially education. They left the building after receiving a promise from opposition lawmakers to present a proposal to hold a plebiscite.(Luis Hidalgo)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict177.jpg) A Tibetan exile has her face covered with a Tibetan flag as she sits after a march to express solidarity with the plight of the people in Tibet, in New Delhi, India, Wednesday, Oct. 19, 2011. Tibetan spiritual leader The Dalai Lama on Wednesday fasted and led prayers in honor of nine Tibetans who set themselves on fire in apparent protest against China’s tight grip over Buddhist practices in Tibet. (Tsering Topgyal)
A Tibetan exile has her face covered with a Tibetan flag as she sits after a march to express solidarity with the plight of the people in Tibet, in New Delhi, India, Wednesday, Oct. 19, 2011. Tibetan spiritual leader The Dalai Lama on Wednesday fasted and led prayers in honor of nine Tibetans who set themselves on fire in apparent protest against China’s tight grip over Buddhist practices in Tibet. (Tsering Topgyal)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict163.jpg) Occupy Wall Street participants carry on their occupation of Zuccotti Park near Wall Street in New York, October 18, 2011. Getty
Occupy Wall Street participants carry on their occupation of Zuccotti Park near Wall Street in New York, October 18, 2011. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict164.jpg) A woman holds a sign outside of the Occupy Boston encampment as protester walks by with a box on his head in Boston, Massachusetts October 18, 2011. Occupy Boston is an extension of the Occupy Wall Street movement in New York City. Reuters
A woman holds a sign outside of the Occupy Boston encampment as protester walks by with a box on his head in Boston, Massachusetts October 18, 2011. Occupy Boston is an extension of the Occupy Wall Street movement in New York City. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict165.jpg) A protester takes part in an Occupy Phoenix demonstration in Phoenix, Arizona October 17, 2011. Occupy Phoenix is part of the Occupy Wall Street movement that began in New York last month with a few people and expanded to protest marches and camps across the US and abroad. Reuters
A protester takes part in an Occupy Phoenix demonstration in Phoenix, Arizona October 17, 2011. Occupy Phoenix is part of the Occupy Wall Street movement that began in New York last month with a few people and expanded to protest marches and camps across the US and abroad. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict166.jpg) In an Oct. 9, 2011 photo, Diane McEachern sits with her dogs Mr. Snickers, left, Seabiscuit, and Ruffian, right, on the tundra near Bethel, Alaska. McEachern wanted to participate in the Occupy Wall Street protests so she gathered her dogs, bundled up and went out to the tundra with a homemade sign that read “Occupy the Tundra.” The photo was posted on the Occupy Wall Street Facebook page and has since been shared thousands of times. AP
In an Oct. 9, 2011 photo, Diane McEachern sits with her dogs Mr. Snickers, left, Seabiscuit, and Ruffian, right, on the tundra near Bethel, Alaska. McEachern wanted to participate in the Occupy Wall Street protests so she gathered her dogs, bundled up and went out to the tundra with a homemade sign that read “Occupy the Tundra.” The photo was posted on the Occupy Wall Street Facebook page and has since been shared thousands of times. AP![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict167.jpg) Protesting farmers and their supporters raise their clenched fists as they shout slogans during a rally in front of the Supreme Court Tuesday Oct. 18, 2011 in Manila, Philippines. The farmers called on to occupy the Supreme Court similar to the protest dubbed “Occupy Wall Street” to force them to act on their cases on the distribution of lands including Hacienda Luisita which is owned by the family of President Benigno Aquino III. AP
Protesting farmers and their supporters raise their clenched fists as they shout slogans during a rally in front of the Supreme Court Tuesday Oct. 18, 2011 in Manila, Philippines. The farmers called on to occupy the Supreme Court similar to the protest dubbed “Occupy Wall Street” to force them to act on their cases on the distribution of lands including Hacienda Luisita which is owned by the family of President Benigno Aquino III. AP![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict168.jpg) Students from the United Community daycare center of Brooklyn color in Zuccotti Park where Occupy Wall Street campaign demonstrators have been stationed near Wall Street in New York October 17, 2011. Reuters
Students from the United Community daycare center of Brooklyn color in Zuccotti Park where Occupy Wall Street campaign demonstrators have been stationed near Wall Street in New York October 17, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict169.jpg) A protestor hops in her sleeping bag as she camps outside St Paul’s Cathedral on October 17, 2011, in London’s financial district, during a third day of demonstrations against corporate greed and state spending cutbacks. The London encampment began on Saturday following a demonstration by about 2,000-3,000 people, as part of Europe-wide anti-capitalist protests inspired by the Occupy Wall Street movement born in New York in September. Getty
A protestor hops in her sleeping bag as she camps outside St Paul’s Cathedral on October 17, 2011, in London’s financial district, during a third day of demonstrations against corporate greed and state spending cutbacks. The London encampment began on Saturday following a demonstration by about 2,000-3,000 people, as part of Europe-wide anti-capitalist protests inspired by the Occupy Wall Street movement born in New York in September. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict180.jpg) Protesters shout slogans during a demonstration against the government and banks in Puerta del Sol square in solidarity action for the worldwide protest dubbed “Occupy the City” in Madrid on Saturday, Oct. 15, 2011. The organizers of the Occupy Wall Street announced on their website that protesters will demonstrate in concert over 951 cities in 82 countries. (Arturo Rodriguez)
Protesters shout slogans during a demonstration against the government and banks in Puerta del Sol square in solidarity action for the worldwide protest dubbed “Occupy the City” in Madrid on Saturday, Oct. 15, 2011. The organizers of the Occupy Wall Street announced on their website that protesters will demonstrate in concert over 951 cities in 82 countries. (Arturo Rodriguez)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict182.jpg) Protestors march near Toronto’s financial district on Saturday Oct. 15, 2011. The demonstration is one of many being held across the country recently in support of the ongoing Occupy Wall Street demonstration in New York. (Chris Young)
Protestors march near Toronto’s financial district on Saturday Oct. 15, 2011. The demonstration is one of many being held across the country recently in support of the ongoing Occupy Wall Street demonstration in New York. (Chris Young)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict181.jpg) A protestor blows her whistle during a demonstration in Barcelona Saturday Oct. 15, 2011. Demonstrators in cities all over the world are protesting against corporate power and the banking system. (Emilio Morenatti)
A protestor blows her whistle during a demonstration in Barcelona Saturday Oct. 15, 2011. Demonstrators in cities all over the world are protesting against corporate power and the banking system. (Emilio Morenatti)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest2/pict184.jpg) Occupy Wall Street protestors prepare for a day of demonstrations throughout Manhattan by having their hair cut in Zuccotti Park, Saturday, Oct. 15, 2011, in New York. As many as 1,000 protesters were marching Saturday morning to a Chase bank branch in the financial district, banging drums, blowing horns and carrying signs decrying corporate greed. Other demonstrations are planned around the city all day Saturday. (John Minchillo)
Occupy Wall Street protestors prepare for a day of demonstrations throughout Manhattan by having their hair cut in Zuccotti Park, Saturday, Oct. 15, 2011, in New York. As many as 1,000 protesters were marching Saturday morning to a Chase bank branch in the financial district, banging drums, blowing horns and carrying signs decrying corporate greed. Other demonstrations are planned around the city all day Saturday. (John Minchillo)

![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict27.jpg) A demonstrator sits holding a sign during a protest against bullfighting in Lima, Peru, Saturday, Nov. 5, 2011. Peru hosts the oldest bullring in the Americas, the Plaza de Acho, inaugurated in 1766 under the ruling of Viceroy Manuel de Amat y Juniet, where every year bullfighters compete for the renown ‘Escapulario de Oro’ or ‘Golden Scapular’, one of the most important bullfighting trophies worldwide. (Karel Navarro)
A demonstrator sits holding a sign during a protest against bullfighting in Lima, Peru, Saturday, Nov. 5, 2011. Peru hosts the oldest bullring in the Americas, the Plaza de Acho, inaugurated in 1766 under the ruling of Viceroy Manuel de Amat y Juniet, where every year bullfighters compete for the renown ‘Escapulario de Oro’ or ‘Golden Scapular’, one of the most important bullfighting trophies worldwide. (Karel Navarro)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict30.jpg) Iranian opposition members hold an old Iranian flag as they protest against the regime in their country, asking the release of jailed dissidents and union members, in Ankara, Turkey, Saturday, Nov. 5, 2011.(Burhan Ozbilici)
Iranian opposition members hold an old Iranian flag as they protest against the regime in their country, asking the release of jailed dissidents and union members, in Ankara, Turkey, Saturday, Nov. 5, 2011.(Burhan Ozbilici)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict23.jpg) An activist supporting the repeal of the Armed Forces Special Powers Act (AFSPA) stands in front of banners in support of rights activist Irom Chanu Sharmila during a protest in New Delhi on November 5, 2011. Sharmila has been on a 10-year hunger strike demanding the Indian government to repeal the AFSPA. Getty
An activist supporting the repeal of the Armed Forces Special Powers Act (AFSPA) stands in front of banners in support of rights activist Irom Chanu Sharmila during a protest in New Delhi on November 5, 2011. Sharmila has been on a 10-year hunger strike demanding the Indian government to repeal the AFSPA. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict25.jpg) More than 100 police moved on Occupy Sydney protesters at Martin Place October 23, 2011, resulting in the arrest of 40 people. Damian Baker
More than 100 police moved on Occupy Sydney protesters at Martin Place October 23, 2011, resulting in the arrest of 40 people. Damian Baker![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict24.jpg) Occupy Wall Street demonstrator Mimi Ho, right, gestures as she carries her daughter Juniper, 1, after she withdrew her savings from a Wells Fargo Bank as part of the protest in downtown Oakland, Calif. , Friday, Nov. 4, 2011. At left is Kimi Lee, who also withdrew her savings. Saturday is Bank Transfer Day for supporters to take their money out of major banks and put their money into smaller banks. AP
Occupy Wall Street demonstrator Mimi Ho, right, gestures as she carries her daughter Juniper, 1, after she withdrew her savings from a Wells Fargo Bank as part of the protest in downtown Oakland, Calif. , Friday, Nov. 4, 2011. At left is Kimi Lee, who also withdrew her savings. Saturday is Bank Transfer Day for supporters to take their money out of major banks and put their money into smaller banks. AP![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict21.jpg) Students stage a protest in front of the government house in Riga November 4, 2011. Thousands of students staged the protest against education budget cuts the Latvian government is planning for 2012, local media reported. Reuters
Students stage a protest in front of the government house in Riga November 4, 2011. Thousands of students staged the protest against education budget cuts the Latvian government is planning for 2012, local media reported. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict22.jpg) Albanian citizens protest in front of the parliament building to stop the passing of a law that will allow the import of waste into the country, in Tirana November 3, 2011. The Albanian government insists that the controversial bill will only allow the import of a limited list of non-toxic waste for recycling purposes, but environmental activists insist that bill would turn Albania into a backyard recycling bin of Europe?s richer countries. A similar attempt to pass a law that would allow import of waste was thwarted in 2004 due to strong public opposition. Reuters
Albanian citizens protest in front of the parliament building to stop the passing of a law that will allow the import of waste into the country, in Tirana November 3, 2011. The Albanian government insists that the controversial bill will only allow the import of a limited list of non-toxic waste for recycling purposes, but environmental activists insist that bill would turn Albania into a backyard recycling bin of Europe?s richer countries. A similar attempt to pass a law that would allow import of waste was thwarted in 2004 due to strong public opposition. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict7.jpg) University students with their necks painted protest at Bolivar square in Bogota, Colombia, Thursday Nov. 3, 2011. Their signs read in Spanish “We have the right to be outraged,” left, and “Excellent education and for all!!” Students are protesting education reforms planned by the government that propose private funding for public institutions. (Fernando Vergara)
University students with their necks painted protest at Bolivar square in Bogota, Colombia, Thursday Nov. 3, 2011. Their signs read in Spanish “We have the right to be outraged,” left, and “Excellent education and for all!!” Students are protesting education reforms planned by the government that propose private funding for public institutions. (Fernando Vergara)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict9.jpg) Protesters chant slogans in front of the Greek Parliament during an anti-austerity protest in Athens, Thursday, Nov. 3 2011. Greece’s prime minister abandoned his explosive plan to put a European rescue deal to popular vote and opened emergency talks Thursday with his opponents, demanding their support in parliament to pass the hard-fought agreement into law. (Kostas Tsironis)
Protesters chant slogans in front of the Greek Parliament during an anti-austerity protest in Athens, Thursday, Nov. 3 2011. Greece’s prime minister abandoned his explosive plan to put a European rescue deal to popular vote and opened emergency talks Thursday with his opponents, demanding their support in parliament to pass the hard-fought agreement into law. (Kostas Tsironis)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict11.jpg) Anti-government protesters pass through their makeshift barricades Thursday, Nov. 3, 2011, during a demonstration in the western village of Malkiya, Bahrain. Men, women and children waved national flags, chanted against the regime and called for prisoners to be freed. Such barricades are used in restive Shiite areas nationwide to slow riot police jeeps who often arrive to disperse the daily demonstrations. (Hasan Jamali)
Anti-government protesters pass through their makeshift barricades Thursday, Nov. 3, 2011, during a demonstration in the western village of Malkiya, Bahrain. Men, women and children waved national flags, chanted against the regime and called for prisoners to be freed. Such barricades are used in restive Shiite areas nationwide to slow riot police jeeps who often arrive to disperse the daily demonstrations. (Hasan Jamali)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict18.jpg) Aileen Mioko Smith, center, executive director of pro-sustainable energy NGO group Green Action, and supporters shout anti-nuclear slogans by a yarn ball made by women in Fukushima as they stage a sit-in demonstration, opposing the government’s nuclear energy policy in front of the Economy, Trade and Industry Ministry in Tokyo Thursday, Nov. 3, 2011. (Shuji Kajiyama)
Aileen Mioko Smith, center, executive director of pro-sustainable energy NGO group Green Action, and supporters shout anti-nuclear slogans by a yarn ball made by women in Fukushima as they stage a sit-in demonstration, opposing the government’s nuclear energy policy in front of the Economy, Trade and Industry Ministry in Tokyo Thursday, Nov. 3, 2011. (Shuji Kajiyama)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict16.jpg) An exile Tibetan woman tries to immolate herself as others from the community try to stop her, during a protest against China and to honor Tibetans who have immolated themselves since March in a restive Tibetan area of western China, in Katmandu, Nepal, Wednesday, Nov. 2, 2011. Protesters urged G20 leaders to raise the issue of rights violation and crackdown on monasteries in Tibet. (Niranjan Shrestha)
An exile Tibetan woman tries to immolate herself as others from the community try to stop her, during a protest against China and to honor Tibetans who have immolated themselves since March in a restive Tibetan area of western China, in Katmandu, Nepal, Wednesday, Nov. 2, 2011. Protesters urged G20 leaders to raise the issue of rights violation and crackdown on monasteries in Tibet. (Niranjan Shrestha)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict20.jpg) Occupy Chicago protesters march in downtown Chicago, Wednesday, Nov. 2, 2011. Protesters are gathering in Chicago’s financial district to march in solidarity with other anti-Wall Street protesters nationwide for an Iraq War veteran who was injured in clashes between protesters and police in California. (Nam Y. Huh)
Occupy Chicago protesters march in downtown Chicago, Wednesday, Nov. 2, 2011. Protesters are gathering in Chicago’s financial district to march in solidarity with other anti-Wall Street protesters nationwide for an Iraq War veteran who was injured in clashes between protesters and police in California. (Nam Y. Huh)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict19.jpg) An Occupy Oakland protester wears makeup in observance of the traditional Mexican holiday “Day of the Dead,” Wednesday, Nov. 2, 2011, in Oakland, Calif. Oakland’s citywide general strike, a hastily planned and ambitious action called by Occupy protesters a day after police forcibly removed their City Hall encampment last week, seeks to shut down the Port of Oakland. (Ben Margot)
An Occupy Oakland protester wears makeup in observance of the traditional Mexican holiday “Day of the Dead,” Wednesday, Nov. 2, 2011, in Oakland, Calif. Oakland’s citywide general strike, a hastily planned and ambitious action called by Occupy protesters a day after police forcibly removed their City Hall encampment last week, seeks to shut down the Port of Oakland. (Ben Margot)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict5.jpg) A woman holds her child during a protest in Ciudad Juarez November 1, 2011. Police arrested around 25 protesters as they were trying to put up crosses in a public area in representation of the thousands of victims of the drug war. Reuters
A woman holds her child during a protest in Ciudad Juarez November 1, 2011. Police arrested around 25 protesters as they were trying to put up crosses in a public area in representation of the thousands of victims of the drug war. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict14.jpg) In this photograph taken by AP Images for AIDS Healthcare Foundation, Protestors from the AIDS Healthcare Foundation deliver a bag full of petitions requesting lower AIDS drug pricing to Johnson & Johnson headquarters in New Brunswick, NJ on Wednesday, Nov. 2, 2011. (Charles Sykes)
In this photograph taken by AP Images for AIDS Healthcare Foundation, Protestors from the AIDS Healthcare Foundation deliver a bag full of petitions requesting lower AIDS drug pricing to Johnson & Johnson headquarters in New Brunswick, NJ on Wednesday, Nov. 2, 2011. (Charles Sykes)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict10.jpg) An anti-G20 demonstrator poses on a fake beach during a photobooth session as she takes part in a protest against globalisation in Nice, southeastern France, November 2, 2011. G20 leaders will gather in Cannes for the final summit of France’s presidency on November 3 and 4. Reuters
An anti-G20 demonstrator poses on a fake beach during a photobooth session as she takes part in a protest against globalisation in Nice, southeastern France, November 2, 2011. G20 leaders will gather in Cannes for the final summit of France’s presidency on November 3 and 4. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict17.jpg) A woman involved in the clean-up operation after the Chernobyl nuclear disaster shouts slogans during a protest in front of riot police at Cabinet in Kiev, Ukraine, Wednesday, Nov. 2, 2011. The veterans were demanding the right to keep the social benefits given to them after the clean-up. (Efrem Lukatsky)
A woman involved in the clean-up operation after the Chernobyl nuclear disaster shouts slogans during a protest in front of riot police at Cabinet in Kiev, Ukraine, Wednesday, Nov. 2, 2011. The veterans were demanding the right to keep the social benefits given to them after the clean-up. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict8.jpg) Indian police officers detain Members of the Tibetan Youth Congress during a protest, on the eve of G20 summit in France , outside the Chinese Embassy in New Delhi on November 2, 2011. The protesters flew Tibetan flags,and burned Chinese flags to express their opposition to China’s policies in Tibet, and to call for support for their movement from leaders of the G20. Getty
Indian police officers detain Members of the Tibetan Youth Congress during a protest, on the eve of G20 summit in France , outside the Chinese Embassy in New Delhi on November 2, 2011. The protesters flew Tibetan flags,and burned Chinese flags to express their opposition to China’s policies in Tibet, and to call for support for their movement from leaders of the G20. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict15.jpg) Protester Alexis Marvel, of Boston, front, holds an American flag and shouts slogans while joining with members of the Occupy Boston movement, students from area colleges, and union workers as they march through downtown Boston, Wednesday, Nov. 2, 2011. The march was held to protest the nations growing student debt burden. AP
Protester Alexis Marvel, of Boston, front, holds an American flag and shouts slogans while joining with members of the Occupy Boston movement, students from area colleges, and union workers as they march through downtown Boston, Wednesday, Nov. 2, 2011. The march was held to protest the nations growing student debt burden. AP![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict6.jpg) Demonstrators shout slogans in front of riot police on November 2, 2011 during a protest as the Ukrainian cabinet was meeting in Kiev. Ukrainian veterans of the clean-up from the Chernobyl nuclear disaster are demonstrating against planned benefit cuts. In September, lawmakers gave initial approval to a bill cutting back benefits paid to those who helped clean up the April 1986 nuclear disaster and those who still live on the affected lands. Getty
Demonstrators shout slogans in front of riot police on November 2, 2011 during a protest as the Ukrainian cabinet was meeting in Kiev. Ukrainian veterans of the clean-up from the Chernobyl nuclear disaster are demonstrating against planned benefit cuts. In September, lawmakers gave initial approval to a bill cutting back benefits paid to those who helped clean up the April 1986 nuclear disaster and those who still live on the affected lands. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict2.jpg) Tibetan nationals demonstrate to protest against China’s President Hu Jintao visit to France for Cannes’ G20 meeting, on November 2, 2011 in Paris. Getty
Tibetan nationals demonstrate to protest against China’s President Hu Jintao visit to France for Cannes’ G20 meeting, on November 2, 2011 in Paris. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict0.jpg) Young unemployed graduates protest against unemployment and the cost of living, in front of the Moroccan Parliament in Rabat November 2, 2011. Reuters
Young unemployed graduates protest against unemployment and the cost of living, in front of the Moroccan Parliament in Rabat November 2, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict1.jpg) Anti-Wall Street protesters demonstrate in front of a closed bank in Oakland, California, November 2, 2011. Hundreds of protesters took to the streets of downtown Oakland at the start of what they called a general strike to protest economic conditions and police brutality in the city. Reuters
Anti-Wall Street protesters demonstrate in front of a closed bank in Oakland, California, November 2, 2011. Hundreds of protesters took to the streets of downtown Oakland at the start of what they called a general strike to protest economic conditions and police brutality in the city. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict3.jpg) Members of the New York City chapter of Iraq Veterans Against the War and dozens of other uniformed veterans known as ‘Veterans of the 99%’ march from Vietnam Veterans Plaza to Zucotti Park where the Occupy Wall Street movement is centered on November 2, 2011 in New York City. The veterans groups, which feature current and former members of the United States military, marched in support of Occupy Wall Street and to pay homage to Scott Olsen, a former Marine and Iraq War vet who sustained a skull fracture after he was injured by police at an Occupy Oakland protest. Getty
Members of the New York City chapter of Iraq Veterans Against the War and dozens of other uniformed veterans known as ‘Veterans of the 99%’ march from Vietnam Veterans Plaza to Zucotti Park where the Occupy Wall Street movement is centered on November 2, 2011 in New York City. The veterans groups, which feature current and former members of the United States military, marched in support of Occupy Wall Street and to pay homage to Scott Olsen, a former Marine and Iraq War vet who sustained a skull fracture after he was injured by police at an Occupy Oakland protest. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict4.jpg) A demonstrator tries to cross a police line during a protest against the Islamist Ennahda movement in Tunis November 2, 2011. The moderate Islamist party Ennahda, which advocates democracy and pledges not to impose religious bans on the secularist minority here, won 40 percent of the vote in the October 23 election for a constituent assembly. Reuters
A demonstrator tries to cross a police line during a protest against the Islamist Ennahda movement in Tunis November 2, 2011. The moderate Islamist party Ennahda, which advocates democracy and pledges not to impose religious bans on the secularist minority here, won 40 percent of the vote in the October 23 election for a constituent assembly. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict12.jpg) A woman holds a placard on November 1, 2011 during a demonstration in the French city of Nice, two days ahead of the G20 summit to be held in Cannes on November 3 and 4. Thousands of anti-capitalists are to march through the streets of Nice today to protest corporate greed ahead of the G20 summit, echoing protests worldwide. The placard reads : ‘Life not money’. Getty
A woman holds a placard on November 1, 2011 during a demonstration in the French city of Nice, two days ahead of the G20 summit to be held in Cannes on November 3 and 4. Thousands of anti-capitalists are to march through the streets of Nice today to protest corporate greed ahead of the G20 summit, echoing protests worldwide. The placard reads : ‘Life not money’. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest4/pict13.jpg) In this Thursday, Sept. 8, 2011 file photo, a female protestor, center, flashes the victory sign during a demonstration in Sanaa, Yemen demanding the resignation of President Ali Abdullah Saleh. Women are fighting to keep a voice for their rights sounding out amid the tumult of Yemen’s landmark revolt. The main goal of the protests by millions around the country, day in and day out since February, is the ouster of President Saleh.
In this Thursday, Sept. 8, 2011 file photo, a female protestor, center, flashes the victory sign during a demonstration in Sanaa, Yemen demanding the resignation of President Ali Abdullah Saleh. Women are fighting to keep a voice for their rights sounding out amid the tumult of Yemen’s landmark revolt. The main goal of the protests by millions around the country, day in and day out since February, is the ouster of President Saleh.





 Zielvorstellung Marine 2025+
Zielvorstellung Marine 2025+











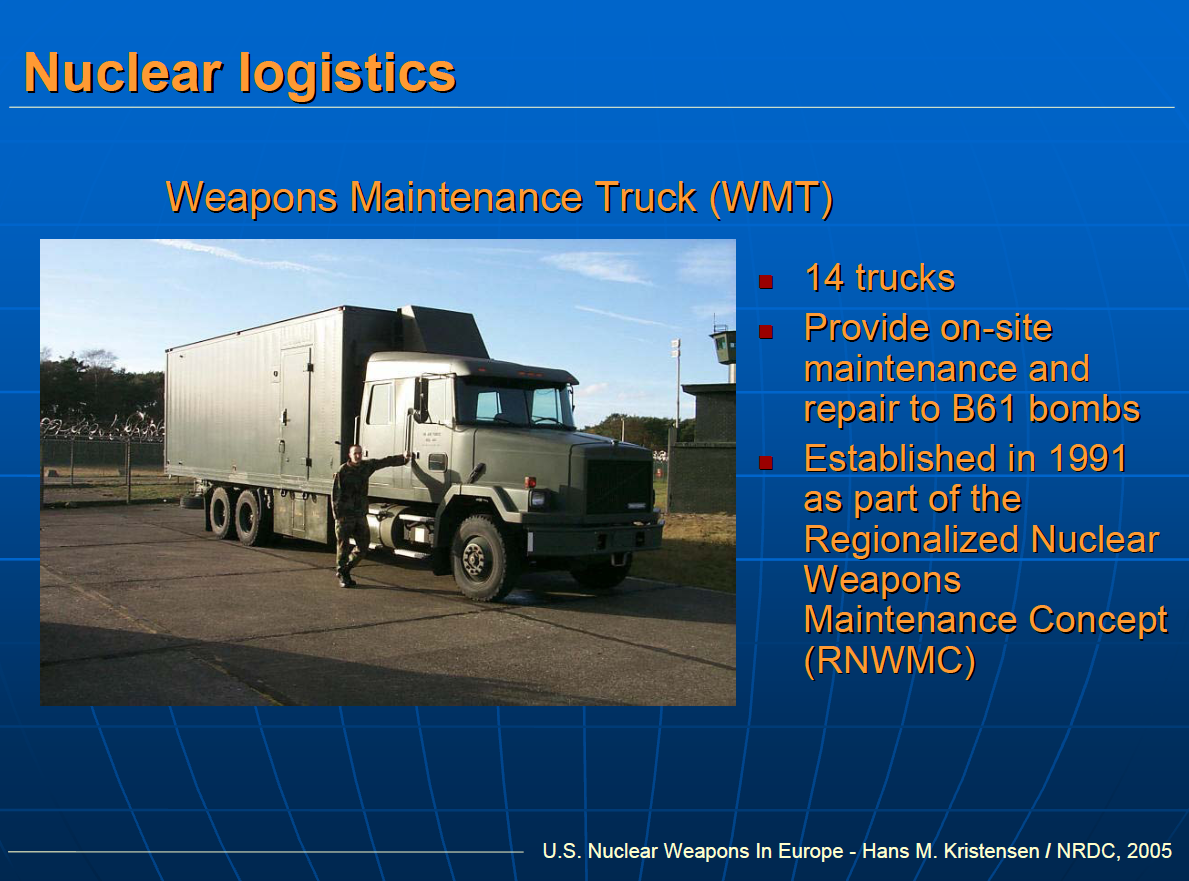
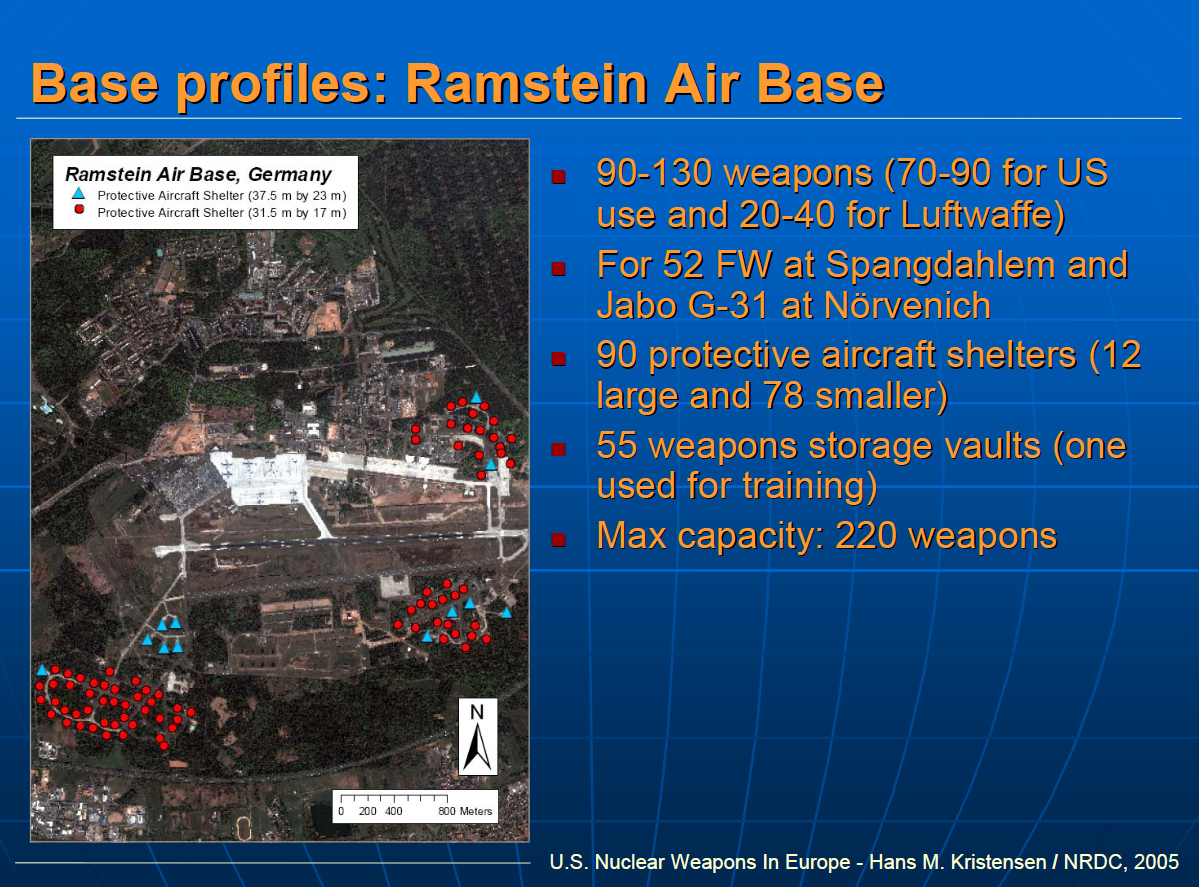











![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict2.jpg) Occupy Wall Street protesters help a man injured after police used tear gas to disperse a large crowd of protesters at 14th Street and Broadway in Oakland, Calif., Tuesday, Oct. 25, 2011. (Darryl Bush)
Occupy Wall Street protesters help a man injured after police used tear gas to disperse a large crowd of protesters at 14th Street and Broadway in Oakland, Calif., Tuesday, Oct. 25, 2011. (Darryl Bush)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict0.jpg) Occupy Wall Street protesters huddle together after police use tear gas to disperse a large crowd that gathered at 14th Street and Broadway in Oakland, Calif., Tuesday, October 25, 2011. Many demonstrators were arrested. (Darryl Bush)
Occupy Wall Street protesters huddle together after police use tear gas to disperse a large crowd that gathered at 14th Street and Broadway in Oakland, Calif., Tuesday, October 25, 2011. Many demonstrators were arrested. (Darryl Bush)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict1.jpg) An Occupy Wall Street protester stands with a banner after police use tear gas to disperse a large crowd that gathered at 14th Street and Broadway in Oakland, Calif., Tuesday, October 25, 2011. Scores of demonstrators were arrested. (Darryl Bush)
An Occupy Wall Street protester stands with a banner after police use tear gas to disperse a large crowd that gathered at 14th Street and Broadway in Oakland, Calif., Tuesday, October 25, 2011. Scores of demonstrators were arrested. (Darryl Bush)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict7.jpg) Oakland police fire tear gas as they prepare to move in to Frank Ogawa Plaza to disperse Occupy Oakland protesters on Tuesday. Oct. 25, 2011 in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)
Oakland police fire tear gas as they prepare to move in to Frank Ogawa Plaza to disperse Occupy Oakland protesters on Tuesday. Oct. 25, 2011 in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict9.jpg) Police prepare to enter Occupy Oakland’s City Hall encampment on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)
Police prepare to enter Occupy Oakland’s City Hall encampment on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict10.jpg) Oakland Occupy protestors form a line opposing the police at the Frank Ogawa Plaza on Tuesday. Oct. 25, 2011 in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)
Oakland Occupy protestors form a line opposing the police at the Frank Ogawa Plaza on Tuesday. Oct. 25, 2011 in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict6.jpg) Oakland police search tents in Frank Ogawa Plaza as they disperse Occupy Oakland protesters on Tuesday. Oct. 25, 2011 in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)
Oakland police search tents in Frank Ogawa Plaza as they disperse Occupy Oakland protesters on Tuesday. Oct. 25, 2011 in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict3.jpg) Oakland police search tents in Frank Ogawa Plaza as they disperse Occupy Oakland protesters on Tuesday, Oct. 25, 2011 in Oakland, Calif. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)
Oakland police search tents in Frank Ogawa Plaza as they disperse Occupy Oakland protesters on Tuesday, Oct. 25, 2011 in Oakland, Calif. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict12.jpg) An Occupy Oakland protester waits in his tent as police clear the group’s Snow Park encampment on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)
An Occupy Oakland protester waits in his tent as police clear the group’s Snow Park encampment on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict5.jpg) Unidentified protesters link arms as police advance on their City Hall encampment on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)
Unidentified protesters link arms as police advance on their City Hall encampment on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict4.jpg) An Occupy Oakland camper carries belonging in his teeth as he’s arrested from the group’s city hall encampment on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)
An Occupy Oakland camper carries belonging in his teeth as he’s arrested from the group’s city hall encampment on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Jane Tyska)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict8.jpg) The Oakland Occupy encampment at Frank Ogawa Plaza after Oakland Police disbanded the tent community leaving debris strewn throughout the plaza on Tuesday. Oct. 25, 2011 in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Noah Berger)
The Oakland Occupy encampment at Frank Ogawa Plaza after Oakland Police disbanded the tent community leaving debris strewn throughout the plaza on Tuesday. Oct. 25, 2011 in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Noah Berger)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict14.jpg) Tents and debris are seen on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Noah Berger)
Tents and debris are seen on Tuesday, Oct. 25, 2011, in Oakland, Calif. Police in riot gear began clearing anti-Wall Street protesters on Tuesday morning from the plaza in front of Oakland’s City Hall where they have been camped out for about two weeks. City officials had originally been supportive of the protesters, but the city later warned the protesters that they were breaking the law and could not stay in the encampment overnight. (Noah Berger)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict13.jpg) An Oakland police officer in riot gear stands guard over Frank H. Ogawa plaza Tuesday, Oct. 25, 2011, in Oakland, Calif. Occupy Oakland protestors were evicted from the plaza early this morning. (AP Photo/Ben Margot)
An Oakland police officer in riot gear stands guard over Frank H. Ogawa plaza Tuesday, Oct. 25, 2011, in Oakland, Calif. Occupy Oakland protestors were evicted from the plaza early this morning. (AP Photo/Ben Margot)![[Image]](https://i0.wp.com/cryptome.org/info/ows-18/pict11.jpg)









 Long before it was acknowledged to be a significant criminal and national security threat, the FBI established a forward-looking organization to proactively address the issue of cyber crime.
Long before it was acknowledged to be a significant criminal and national security threat, the FBI established a forward-looking organization to proactively address the issue of cyber crime.


































 In den Akten der Staatssicherheit findet sich zum Fall Günter Litfin auch ein undatiertes Foto: Gedenkstein für Günter Litfin am Friedrich-List-Ufer, aufgestellt am 24.8.1962. Heute befindet sich der Gedenkstein an der Sandkrugbrücke in der Berliner Invalidenstraße. Quelle: BStU, MfS, HA IX, Fo 1673, Bild 88
In den Akten der Staatssicherheit findet sich zum Fall Günter Litfin auch ein undatiertes Foto: Gedenkstein für Günter Litfin am Friedrich-List-Ufer, aufgestellt am 24.8.1962. Heute befindet sich der Gedenkstein an der Sandkrugbrücke in der Berliner Invalidenstraße. Quelle: BStU, MfS, HA IX, Fo 1673, Bild 88






 Born of an immigrant family in Brooklyn, New York in 1899, Al Capone quit school after the sixth grade and associated with a notorious street gang, becoming accepted as a member. Johnny Torrio was the street gang leader and among the other members was Lucky Luciano, who would later attain his own notoriety.
Born of an immigrant family in Brooklyn, New York in 1899, Al Capone quit school after the sixth grade and associated with a notorious street gang, becoming accepted as a member. Johnny Torrio was the street gang leader and among the other members was Lucky Luciano, who would later attain his own notoriety.



![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict143.jpg) Demonstrators chat while warming their hands on a makeshift fire in the park near the European Central Bank in Frankfurt, central Germany, Monday, Oct. 17, 2011. Thousands of people demonstrated against corporate greed in cities across Europe on Saturday, along with much smaller protests in cities across the U.S. Banners on tent read right: ‘WTF where is freedom?’ and at left : ‘A good life instead of profit’. (Thomas Lohnes)
Demonstrators chat while warming their hands on a makeshift fire in the park near the European Central Bank in Frankfurt, central Germany, Monday, Oct. 17, 2011. Thousands of people demonstrated against corporate greed in cities across Europe on Saturday, along with much smaller protests in cities across the U.S. Banners on tent read right: ‘WTF where is freedom?’ and at left : ‘A good life instead of profit’. (Thomas Lohnes)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict144.jpg) A protester stands outside the Toronto Stock Exchange in the city’s financial district on Monday Oct. 17, 2011 as the Occupy Bay Street protest continues into it’s third day. (Chris Young)
A protester stands outside the Toronto Stock Exchange in the city’s financial district on Monday Oct. 17, 2011 as the Occupy Bay Street protest continues into it’s third day. (Chris Young)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict145.jpg) A participant who asked not to identified and a dog begin the day along with others at the Occupy Wall Street protests at Zuccotti Park in New York Monday, Oct. 17, 2011 as the protest enters it’s 30th day. (Craig Ruttle)
A participant who asked not to identified and a dog begin the day along with others at the Occupy Wall Street protests at Zuccotti Park in New York Monday, Oct. 17, 2011 as the protest enters it’s 30th day. (Craig Ruttle)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict140.jpg) [Published October 17, 2011.] In this Oct. 14, 2011 photo, demonstrators affiliated with the Occupy Wall Street protests stand in line to be served lunch at Zuccotti Park in New York. The outcry against the nation’s financial institutions that has swept the country in recent weeks has crossed many boundaries, including class, gender and age. But a stubborn hurdle in many cities has been a lack of racial inclusion, something noted by organizers and participants alike. (Mary Altaffer)
[Published October 17, 2011.] In this Oct. 14, 2011 photo, demonstrators affiliated with the Occupy Wall Street protests stand in line to be served lunch at Zuccotti Park in New York. The outcry against the nation’s financial institutions that has swept the country in recent weeks has crossed many boundaries, including class, gender and age. But a stubborn hurdle in many cities has been a lack of racial inclusion, something noted by organizers and participants alike. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict141.jpg) [Published October 17, 2011.] In this Oct. 14, 2011 photo, Nicole Carty, 23, from Atlanta, confers with fellow organizing colleagues as she prepares to conduct a general assembly meeting for participants of Zuccotti Park’s Occupy Wall Street encampment, in New York. She is considered a core facilitator who organizes activities at the encampment. The outcry against the nation’s financial institutions that has swept the country in recent weeks has crossed many boundaries, including class, gender and age. But a stubborn hurdle But a stubborn hurdle in many cities has been a lack of racial inclusion, something noted by organizers and participants alike.
[Published October 17, 2011.] In this Oct. 14, 2011 photo, Nicole Carty, 23, from Atlanta, confers with fellow organizing colleagues as she prepares to conduct a general assembly meeting for participants of Zuccotti Park’s Occupy Wall Street encampment, in New York. She is considered a core facilitator who organizes activities at the encampment. The outcry against the nation’s financial institutions that has swept the country in recent weeks has crossed many boundaries, including class, gender and age. But a stubborn hurdle But a stubborn hurdle in many cities has been a lack of racial inclusion, something noted by organizers and participants alike.![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict142.jpg) [Published October 17, 2011.] In this Oct. 15, 2011 photo, a woman participates in an Occupy Atlanta protest at the state Capitol, in Atlanta. The outcry against the nation’s financial institutions that has swept the country in recent weeks has crossed many boundaries, including class, gender and age. But a stubborn hurdle in many cities has been a lack of racial inclusion, something noted by organizers and participants alike. (Erik S. Lesser)
[Published October 17, 2011.] In this Oct. 15, 2011 photo, a woman participates in an Occupy Atlanta protest at the state Capitol, in Atlanta. The outcry against the nation’s financial institutions that has swept the country in recent weeks has crossed many boundaries, including class, gender and age. But a stubborn hurdle in many cities has been a lack of racial inclusion, something noted by organizers and participants alike. (Erik S. Lesser)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict139.jpg) Two security guards stand at the entrance to the NYSE Euronext stock exchange in Amsterdam, Netherlands, Monday Oct. 17, 2011, plastered with slogans in support of the Occupy Wall Street movement. Hundreds of thousands demonstrated against corporate greed in cities across Europe on Saturday, along with much smaller protests in cities across the U.S. (Peter Dejong)
Two security guards stand at the entrance to the NYSE Euronext stock exchange in Amsterdam, Netherlands, Monday Oct. 17, 2011, plastered with slogans in support of the Occupy Wall Street movement. Hundreds of thousands demonstrated against corporate greed in cities across Europe on Saturday, along with much smaller protests in cities across the U.S. (Peter Dejong)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict132.jpg) A protest banner put up by protesters from the Occupy London Stock Exchange group hangs besides tents pitched outside St Paul’s Cathedral before sunrise, as they continue their demonstration that started there on Saturday near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)
A protest banner put up by protesters from the Occupy London Stock Exchange group hangs besides tents pitched outside St Paul’s Cathedral before sunrise, as they continue their demonstration that started there on Saturday near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict134.jpg) A protester from the Occupy London Stock Exchange group puts up a notice on an information point on the side of St Paul’s Cathedral as they continue their demonstration that started on Saturday near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)
A protester from the Occupy London Stock Exchange group puts up a notice on an information point on the side of St Paul’s Cathedral as they continue their demonstration that started on Saturday near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict135.jpg) A masked protester from the Occupy London Stock Exchange group offers passing business people ‘Free Hugs’ as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)
A masked protester from the Occupy London Stock Exchange group offers passing business people ‘Free Hugs’ as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict133.jpg) A protester from the Occupy London Stock Exchange group puts the finishing touches to a placard stating “London Hug Exchange”, as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)
A protester from the Occupy London Stock Exchange group puts the finishing touches to a placard stating “London Hug Exchange”, as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict129.jpg) Police officers chat to protesters beside tents put up by supporters of the Occupy London Stock Exchange group as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)
Police officers chat to protesters beside tents put up by supporters of the Occupy London Stock Exchange group as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict130.jpg) Protesters begin to rise from sleep before sunrise beside tents put up by supporters of the Occupy London Stock Exchange group, as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)
Protesters begin to rise from sleep before sunrise beside tents put up by supporters of the Occupy London Stock Exchange group, as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict128.jpg) Business people walk past tents put up by protesters from the Occupy London Stock Exchange group as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)
Business people walk past tents put up by protesters from the Occupy London Stock Exchange group as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict131.jpg) A businessman walks past tents put up by protesters from the Occupy London Stock Exchange group as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham) [Note “Fire Access Point” and safety corridors, a sign of capable oversight.]
A businessman walks past tents put up by protesters from the Occupy London Stock Exchange group as they continue their demonstration that started on Saturday outside St Paul’s Cathedral, near the London Stock Exchange in London, Monday, Oct. 17, 2011. Protesters in cities across Europe have taken part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Matt Dunham) [Note “Fire Access Point” and safety corridors, a sign of capable oversight.]![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict136.jpg) In this photo taken Saturday, Oct. 15, 2011, protesters take part in a march and rally at Michigan and Congress in Chicago for the Global Day of Occupation. About 2,000 people participated Saturday in an Occupy Chicago demonstration, and about 500 pitched tents in Congress Plaza that evening. Chicago police say the protesters were told to remove their tents and leave the park when it closed at 11 p.m. When they didn’t, police began cutting down the tents and making arrests. (Chicago Sun Times)
In this photo taken Saturday, Oct. 15, 2011, protesters take part in a march and rally at Michigan and Congress in Chicago for the Global Day of Occupation. About 2,000 people participated Saturday in an Occupy Chicago demonstration, and about 500 pitched tents in Congress Plaza that evening. Chicago police say the protesters were told to remove their tents and leave the park when it closed at 11 p.m. When they didn’t, police began cutting down the tents and making arrests. (Chicago Sun Times)![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict137.jpg) Hip Hop Mogul Russell Simmons, right, listens to a protester at the camp for the Occupy Wall Street demonstration in New York, Sunday, Oct. 16, 2011. (David Karp) [The cardboard, twine and rain-sheet shelter deftly by-passes Brookfield Properties’ forbidden tents and tarps.]
Hip Hop Mogul Russell Simmons, right, listens to a protester at the camp for the Occupy Wall Street demonstration in New York, Sunday, Oct. 16, 2011. (David Karp) [The cardboard, twine and rain-sheet shelter deftly by-passes Brookfield Properties’ forbidden tents and tarps.]![[Image]](https://i0.wp.com/cryptome.org/info/ows-17/pict138.jpg) A group of activists hold a strategy meeting in a storage space for supplies supporting the camp of Occupy Wall Street protesters, Sunday, Oct. 16, 2011, in New York. The goods are housed in an unused space donated by the United Federation of Teachers. (David Karp) [From a base in Liberty Park there are thousands of spaces available for sharing openly and not so openly in New York City and worldwide cities as “Wall Street” is widely dispersed openly and secretly.]
A group of activists hold a strategy meeting in a storage space for supplies supporting the camp of Occupy Wall Street protesters, Sunday, Oct. 16, 2011, in New York. The goods are housed in an unused space donated by the United Federation of Teachers. (David Karp) [From a base in Liberty Park there are thousands of spaces available for sharing openly and not so openly in New York City and worldwide cities as “Wall Street” is widely dispersed openly and secretly.]












 A latent print removed from the victim’s car was determined to be a match to the suspect’s
A latent print removed from the victim’s car was determined to be a match to the suspect’s![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict93.jpg) Protesters hurl objects at police in Rome, Saturday, Oct. 15, 2011. Protesters in Rome smashed shop windows and torched cars as violence broke out during a demonstration in the Italian capital, part of worldwide protests against corporate greed and austerity measures. The “Occupy Wall Street” protests, that began in Canada and spread to cities across the U.S., moved Saturday to Asia and Europe, linking up with anti-austerity demonstrations that have raged across the debt-ridden continent for months.
Protesters hurl objects at police in Rome, Saturday, Oct. 15, 2011. Protesters in Rome smashed shop windows and torched cars as violence broke out during a demonstration in the Italian capital, part of worldwide protests against corporate greed and austerity measures. The “Occupy Wall Street” protests, that began in Canada and spread to cities across the U.S., moved Saturday to Asia and Europe, linking up with anti-austerity demonstrations that have raged across the debt-ridden continent for months.![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict94.jpg) Two protesters spray graffiti at a bank, during a march in Brussels, Saturday, Oct. 15, 2011. The protest in the Belgian capital was part of Occupy Wall Street demonstrations against capitalism and austerity measures that went global Saturday, leading to dozens of marches and protests worldwide. (Yves Logghe)
Two protesters spray graffiti at a bank, during a march in Brussels, Saturday, Oct. 15, 2011. The protest in the Belgian capital was part of Occupy Wall Street demonstrations against capitalism and austerity measures that went global Saturday, leading to dozens of marches and protests worldwide. (Yves Logghe)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict99.jpg) A protestor holds a placard during an anti-capitalist demonstration, in Paris, Saturday, Oct. 15, 2011. Protesters in cities across Europe took part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. The placard reads: “Financial market dictatorship, enough”(Thibault Camus)
A protestor holds a placard during an anti-capitalist demonstration, in Paris, Saturday, Oct. 15, 2011. Protesters in cities across Europe took part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. The placard reads: “Financial market dictatorship, enough”(Thibault Camus)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict95.jpg) A man wears an anti-establishment mask during the “Occupy Bucharest” protest in Bucharest, Romania, Saturday, Oct. 15, 2011. The protest, meant as a part of worldwide protests “Occupy Wall Street” against corporate greed and austerity measures, was joined by few people who at times fought among themselves, trying to clarify their vague requests, aimed at linking up with anti-austerity demonstrations that have raged across the debt-ridden continent for months.(Vadim Ghirda)
A man wears an anti-establishment mask during the “Occupy Bucharest” protest in Bucharest, Romania, Saturday, Oct. 15, 2011. The protest, meant as a part of worldwide protests “Occupy Wall Street” against corporate greed and austerity measures, was joined by few people who at times fought among themselves, trying to clarify their vague requests, aimed at linking up with anti-austerity demonstrations that have raged across the debt-ridden continent for months.(Vadim Ghirda)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict96.jpg) Julian Assange, center, takes part in the Occupy London Stock Exchange demonstration in London Saturday Oct, 15, 2011. Protesters in cities across Europe take part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Elizabeth Dalziel)
Julian Assange, center, takes part in the Occupy London Stock Exchange demonstration in London Saturday Oct, 15, 2011. Protesters in cities across Europe take part in rallies inspired by the Occupy Wall Street demonstrations in the United States, expressing their frustration at social inequality and corporate greed. (Elizabeth Dalziel)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict97.jpg) Frederic Carmel sits next to his tent in Montreal’s financial district on Saturday, Oct. 15, 2011. The demonstration is one of many being held across the country recently in support of the ongoing Occupy Wall Street demonstration in New York. (Graham Hughes)
Frederic Carmel sits next to his tent in Montreal’s financial district on Saturday, Oct. 15, 2011. The demonstration is one of many being held across the country recently in support of the ongoing Occupy Wall Street demonstration in New York. (Graham Hughes)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict98.jpg) Protestors gather in Toronto’s financial district for the Occupy Bay Street demonstration on Saturday, Oct. 15, 2011 in Toronto. The demonstration is one of many being held across the country recently in support of the ongoing Occupy Wall Street demonstration in New York. (Chris Young)
Protestors gather in Toronto’s financial district for the Occupy Bay Street demonstration on Saturday, Oct. 15, 2011 in Toronto. The demonstration is one of many being held across the country recently in support of the ongoing Occupy Wall Street demonstration in New York. (Chris Young)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict101.jpg) Diane Kuhn, of West Columbia, S.C. holds a protest sign calling for the prosecution of financial criminals during the Occupy Columbia demonstration at the South Carolina Statehouse in Columbia, S.C., Saturday, Oct. 15, 2011. (Brett Flashnick)
Diane Kuhn, of West Columbia, S.C. holds a protest sign calling for the prosecution of financial criminals during the Occupy Columbia demonstration at the South Carolina Statehouse in Columbia, S.C., Saturday, Oct. 15, 2011. (Brett Flashnick)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict100.jpg) Demonstrators hold banners during the Jobs at Justice rally at Washington Monument in Washington on Saturday, Oct. 15, 2011. (Jose Luis Magana)
Demonstrators hold banners during the Jobs at Justice rally at Washington Monument in Washington on Saturday, Oct. 15, 2011. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict82.jpg) Protestors march through the streets of Berlin during a demonstration to support the ‘ Occupy Wall Street’ -movement Saturday Oct. 15, 2011. Protestors gathered at many major European cities Saturday to join in demonstrations against corruption, capitalism and austerity measures. (Maja Hitij)
Protestors march through the streets of Berlin during a demonstration to support the ‘ Occupy Wall Street’ -movement Saturday Oct. 15, 2011. Protestors gathered at many major European cities Saturday to join in demonstrations against corruption, capitalism and austerity measures. (Maja Hitij)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict91.jpg) Protesters gather in front of the Reserve Bank of Australia in central Sydney, Australia, Saturday, Oct. 15, 2011. The organizer of the Occupy Wall Street announced on their website that protesters will demonstrate in concert over 951 cities in 82 countries. (Rick Rycroft)
Protesters gather in front of the Reserve Bank of Australia in central Sydney, Australia, Saturday, Oct. 15, 2011. The organizer of the Occupy Wall Street announced on their website that protesters will demonstrate in concert over 951 cities in 82 countries. (Rick Rycroft)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict81.jpg) Bosnian people carrying banners with the text “For a class war against dictatorship of capitalism”, top, and “What did bank do? The bank bankrupted!”, bottom banner, during a protest march, in the Bosnian capital of Sarajevo, Saturday, Oct. 15, 2011. Hundreds marched down the main streets of Bosnian cities carrying banners that call for the end of alleged worldwide “Capitalistic Dictatorship”. (Amel Emric)
Bosnian people carrying banners with the text “For a class war against dictatorship of capitalism”, top, and “What did bank do? The bank bankrupted!”, bottom banner, during a protest march, in the Bosnian capital of Sarajevo, Saturday, Oct. 15, 2011. Hundreds marched down the main streets of Bosnian cities carrying banners that call for the end of alleged worldwide “Capitalistic Dictatorship”. (Amel Emric)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict92.jpg) Protesters gather at the Pennsylvania Capitol Saturday, Oct 15, 2011 in Harrisburg, Pa. The demonstration is one of many being held across the country recently in support of the ongoing Occupy Wall Street demonstration in New York. (Bradley C Bower)
Protesters gather at the Pennsylvania Capitol Saturday, Oct 15, 2011 in Harrisburg, Pa. The demonstration is one of many being held across the country recently in support of the ongoing Occupy Wall Street demonstration in New York. (Bradley C Bower)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict87.jpg) Participants march through Tokyo’s Kasumigaseki administrative district during “Occupy Tokyo” protest Saturday, Oct. 15, 2011. The demonstration was held in support of the Occupy Wall Street protest against corporate power. (Itsuo Inouye)
Participants march through Tokyo’s Kasumigaseki administrative district during “Occupy Tokyo” protest Saturday, Oct. 15, 2011. The demonstration was held in support of the Occupy Wall Street protest against corporate power. (Itsuo Inouye)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict85.jpg) Children watch as protestors prepare placards outside the NYSE Euronext stock exchange in Amsterdam, Netherlands, Saturday Oct. 15, 2011, during a demonstration in support of the Occupy Wall Street movement. Demonstrators in hundreds of cities all over the world protested against corporate power and the banking system. (Peter Dejong)
Children watch as protestors prepare placards outside the NYSE Euronext stock exchange in Amsterdam, Netherlands, Saturday Oct. 15, 2011, during a demonstration in support of the Occupy Wall Street movement. Demonstrators in hundreds of cities all over the world protested against corporate power and the banking system. (Peter Dejong)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict89.jpg) Protesters shout slogans as they march towards the U.S. embassy in solidarity action for the U.S. protest dubbed “Occupy Wall Street” Saturday, Oct. 15, 2011 in Manila, Philippines. (Pat Roque)
Protesters shout slogans as they march towards the U.S. embassy in solidarity action for the U.S. protest dubbed “Occupy Wall Street” Saturday, Oct. 15, 2011 in Manila, Philippines. (Pat Roque)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict86.jpg) South Korean protesters stage an “Occupy Seoul” rally in Seoul, South Korea, Saturday, Oct. 15, 2011. The demonstration was held in support of the “Occupy Wall Street” protest against corporate power. The Korean letters read: “Tax the Rich 1%, Welfare for the 99%.” (Ahn Young-joon)
South Korean protesters stage an “Occupy Seoul” rally in Seoul, South Korea, Saturday, Oct. 15, 2011. The demonstration was held in support of the “Occupy Wall Street” protest against corporate power. The Korean letters read: “Tax the Rich 1%, Welfare for the 99%.” (Ahn Young-joon)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict84.jpg) Protesters take part in the “Occupy central” protest in Stockholm, Saturday, Oct. 15, 2011, as protesters worldwide demonstrated against bankers and politicians they accuse of ruining global economies through greed. (Maja Suslin)
Protesters take part in the “Occupy central” protest in Stockholm, Saturday, Oct. 15, 2011, as protesters worldwide demonstrated against bankers and politicians they accuse of ruining global economies through greed. (Maja Suslin)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict83.jpg) People demonstrate on the Place des Nations in front of the European headquarters of the United Nations in Geneva, Switzerland, Saturday Oct. 15, 2011. Protestors gathered at many major European cities Saturday to join in demonstrations against corporate greed and inequality. (Martial Trezzini)
People demonstrate on the Place des Nations in front of the European headquarters of the United Nations in Geneva, Switzerland, Saturday Oct. 15, 2011. Protestors gathered at many major European cities Saturday to join in demonstrations against corporate greed and inequality. (Martial Trezzini)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict90.jpg) Young people demonstrate in the financial district of Zurich, Switzerland, Saturday Oct. 15, 2011. The organizer of the Occupy Wall Street movement announced on their website that protesters will demonstrate in over 951 cities in 82 countries. (Ennio Leanza)
Young people demonstrate in the financial district of Zurich, Switzerland, Saturday Oct. 15, 2011. The organizer of the Occupy Wall Street movement announced on their website that protesters will demonstrate in over 951 cities in 82 countries. (Ennio Leanza)![[Image]](https://i0.wp.com/cryptome.org/info/ows-16/pict88.jpg) Activists hold magazines titled “Socialist” during a protest named “Occupy Taipei” organized by Taiwanese net friends in front of the Taipei 101 building in Taipei, Taiwan, Saturday, Oct. 15, 2011. The rally was a part of Saturday’s worldwide activities held in support of the Occupy Wall Street protest against corporate power. (Chiang Ying-ying)
Activists hold magazines titled “Socialist” during a protest named “Occupy Taipei” organized by Taiwanese net friends in front of the Taipei 101 building in Taipei, Taiwan, Saturday, Oct. 15, 2011. The rally was a part of Saturday’s worldwide activities held in support of the Occupy Wall Street protest against corporate power. (Chiang Ying-ying)














![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict9.jpg) Demonstrators who camped out at Freedom Plaza wake up for the third day of demonstrations Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)
Demonstrators who camped out at Freedom Plaza wake up for the third day of demonstrations Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict5.jpg) One demonstrator helps another flush her eyes with water after after police pepper-sprayed a group of protestors, who were trying to get into the National Air and Space Museum in Washington Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)
One demonstrator helps another flush her eyes with water after after police pepper-sprayed a group of protestors, who were trying to get into the National Air and Space Museum in Washington Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict8.jpg) Pepper-sprayed demonstrators sit and lie on the ground outside the entrance to the National Air and Space Museum in Washington after a group of protestors tryed to get into the museum Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)
Pepper-sprayed demonstrators sit and lie on the ground outside the entrance to the National Air and Space Museum in Washington after a group of protestors tryed to get into the museum Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict23.jpg) Demonstrators react at the entrance of the National Air and Space Museum in Washington after police pepper-sprayed a group of protestors trying to get into the museum Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)
Demonstrators react at the entrance of the National Air and Space Museum in Washington after police pepper-sprayed a group of protestors trying to get into the museum Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict7.jpg) A demonstrator lies on the ground at an entrance to the National Air and Space Museum in Washington after police pepper-sprayed a group of protestors trying to get into the museum Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)
A demonstrator lies on the ground at an entrance to the National Air and Space Museum in Washington after police pepper-sprayed a group of protestors trying to get into the museum Saturday, Oct. 8, 2011, as part of Occupy DC activities in Washington. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict6.jpg) Demonstrators march through the streets of Washington Saturday, Oct. 8, 2011, as part of the Occupy DC activities in the nation’s capital. (Jose Luis Magana)
Demonstrators march through the streets of Washington Saturday, Oct. 8, 2011, as part of the Occupy DC activities in the nation’s capital. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict11.jpg) Demonstrators protest at Freedom Plaza in Washington on Saturday, Oct. 8, 2011, on day three of demonstrations in Washington as part of Occupy DC activities. (Jose Luis Magana)
Demonstrators protest at Freedom Plaza in Washington on Saturday, Oct. 8, 2011, on day three of demonstrations in Washington as part of Occupy DC activities. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict19.jpg) Demonstrators carrying a variety of signs march through the streets of Washington Saturday, Oct. 8, 2011, as part of Occupy DC activities in the nation’s capital. (Jose Luis Magana)
Demonstrators carrying a variety of signs march through the streets of Washington Saturday, Oct. 8, 2011, as part of Occupy DC activities in the nation’s capital. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict24.jpg) Matthew Gember, of Chicago, makes a point as Occupy Boston demonstrators protest on the plaza in front of the Federal Reserve Bank in Boston, Saturday, Oct. 8, 2011. (Michael Dwyer)
Matthew Gember, of Chicago, makes a point as Occupy Boston demonstrators protest on the plaza in front of the Federal Reserve Bank in Boston, Saturday, Oct. 8, 2011. (Michael Dwyer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict25.jpg) Occupy Boston protesters demonstrate on the plaza in front of the Federal Reserve Bank in Boston, Saturday, Oct. 8, 2011. (Michael Dwyer)
Occupy Boston protesters demonstrate on the plaza in front of the Federal Reserve Bank in Boston, Saturday, Oct. 8, 2011. (Michael Dwyer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict30.jpg) Courtney Haskell, lower left, of North Reading, Mass., demonstrates on the plaza in front of the Federal Reserve Bank in Boston as police reflected in a motorcycle mirror look on, Saturday, Oct. 8, 2011. (Michael Dwyer)
Courtney Haskell, lower left, of North Reading, Mass., demonstrates on the plaza in front of the Federal Reserve Bank in Boston as police reflected in a motorcycle mirror look on, Saturday, Oct. 8, 2011. (Michael Dwyer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict1.jpg) Marilyn Mullen stands in support for the ‘Occupy Wall Street’ movement during the Casper, Wyo. rally on Center Street Saturday, Oct. 8, 2011 Over 50 people held signs and American flags in support of the demonstration which is trying to achieve change in government tax law, asking the wealthy to pay an equal percentage of taxes that the working class pays. (Tim Kupsick)
Marilyn Mullen stands in support for the ‘Occupy Wall Street’ movement during the Casper, Wyo. rally on Center Street Saturday, Oct. 8, 2011 Over 50 people held signs and American flags in support of the demonstration which is trying to achieve change in government tax law, asking the wealthy to pay an equal percentage of taxes that the working class pays. (Tim Kupsick)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict13.jpg) With a statue of Abraham Lincoln at center right, protesters begin their march through downtown Cincinnati during the Occupy Cincinnati protest, Saturday, Oct. 8, 2011. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (David Kohl)
With a statue of Abraham Lincoln at center right, protesters begin their march through downtown Cincinnati during the Occupy Cincinnati protest, Saturday, Oct. 8, 2011. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (David Kohl)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict18.jpg) Protesters march through downtown Cincinnati for the Occupy Cincinnati protest on Saturday, Oct. 8, 2011. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (David Kohl)
Protesters march through downtown Cincinnati for the Occupy Cincinnati protest on Saturday, Oct. 8, 2011. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (David Kohl)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict0.jpg) Tamra Bell 52, back right, and her four children Stephanie Stayton, 28, left front, Robert 21, left back, and Courtney 23, attend the Occupy Indy protest in Indianapolis on Saturday, Oct. 8, 2011. Tamra’s husband has been unemployed for two years and suffers from health problems. His unemployment will soon run out and Bell is on the verge of losing the home. The small income her son Robert brings in has helped the family to stay in their home so far. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Michelle Pemberton)
Tamra Bell 52, back right, and her four children Stephanie Stayton, 28, left front, Robert 21, left back, and Courtney 23, attend the Occupy Indy protest in Indianapolis on Saturday, Oct. 8, 2011. Tamra’s husband has been unemployed for two years and suffers from health problems. His unemployment will soon run out and Bell is on the verge of losing the home. The small income her son Robert brings in has helped the family to stay in their home so far. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Michelle Pemberton)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict4.jpg) More than a thousand demonstrators gather in Veteran’s Plaza in Indianapolis on Saturday, Oct. 8, 2011 for Occupy Indy, a protest against everything from bank foreclosures and corporate influence in politics to the wars in Iraq and Afghanistan and unemployment. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Michelle Pemberton)
More than a thousand demonstrators gather in Veteran’s Plaza in Indianapolis on Saturday, Oct. 8, 2011 for Occupy Indy, a protest against everything from bank foreclosures and corporate influence in politics to the wars in Iraq and Afghanistan and unemployment. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Michelle Pemberton)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict16.jpg) A demonstrator holds a sign as more than a thousand gather in Veteran’s Plaza in Indianapolis on Saturday, Oct. 8, 2011 for Occupy Indy, a protest against everything from bank foreclosures and corporate influence in politics to the wars in Iraq and Afghanistan and unemployment. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Michelle Pemberton)
A demonstrator holds a sign as more than a thousand gather in Veteran’s Plaza in Indianapolis on Saturday, Oct. 8, 2011 for Occupy Indy, a protest against everything from bank foreclosures and corporate influence in politics to the wars in Iraq and Afghanistan and unemployment. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Michelle Pemberton)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict17.jpg) More than a thousand protesters march through Indianapolis on Saturday, Oct. 8, 2011 for Occupy Indy, a protest against everything from bank foreclosures and corporate influence in politics to the wars in Iraq and Afghanistan and unemployment. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Michelle Pemberton)
More than a thousand protesters march through Indianapolis on Saturday, Oct. 8, 2011 for Occupy Indy, a protest against everything from bank foreclosures and corporate influence in politics to the wars in Iraq and Afghanistan and unemployment. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Michelle Pemberton)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict3.jpg) Occupy Wall Street protesters gather in Washington Square Park, Saturday, Oct. 8, 2011 in New York. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Henny Ray Abrams)
Occupy Wall Street protesters gather in Washington Square Park, Saturday, Oct. 8, 2011 in New York. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Henny Ray Abrams)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict10.jpg) Demonstrators holding signs gather at the Occupy Wall Street rally in New York on Saturday, Oct. 8, 2011. (Caleb Jones)
Demonstrators holding signs gather at the Occupy Wall Street rally in New York on Saturday, Oct. 8, 2011. (Caleb Jones)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict12.jpg) Protesters with Occupy Wall Street march from Zuccotti Park to Washington Square Park in New York on Saturday, Oct. 8, 2011. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Henny Ray Abrams)
Protesters with Occupy Wall Street march from Zuccotti Park to Washington Square Park in New York on Saturday, Oct. 8, 2011. The Occupy Wall Street movement started in New York City last month and is spreading to other parts of the country. (Henny Ray Abrams)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict22.jpg) Hundreds of skateboarders heading down Broadway toward OWS from West 89th Street and Broadway, October 8, 2011. (Cryptome)
Hundreds of skateboarders heading down Broadway toward OWS from West 89th Street and Broadway, October 8, 2011. (Cryptome)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict15.jpg) In this Friday, Oct. 7, 2011 photo, Cherie Walters, 58, from Mount Clemens, Mich., poses for a photograph, in New York. Walters, who has participated in Occupy Wall Street protests, is wearing the shirt she wore to two of the protests. (Tina Fineberg)
In this Friday, Oct. 7, 2011 photo, Cherie Walters, 58, from Mount Clemens, Mich., poses for a photograph, in New York. Walters, who has participated in Occupy Wall Street protests, is wearing the shirt she wore to two of the protests. (Tina Fineberg)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict2.jpg) People hold signs and are reflected in a bus stop pane, as they walk in the street during their march from City Hall to the Independence National Historical Park Saturday, Oct. 8, 2011, in Philadelphia. Organizers of what is being called Occupy Philadelphia say the demonstration is meant to be a stand against corporate greed. (Alex Brandon)
People hold signs and are reflected in a bus stop pane, as they walk in the street during their march from City Hall to the Independence National Historical Park Saturday, Oct. 8, 2011, in Philadelphia. Organizers of what is being called Occupy Philadelphia say the demonstration is meant to be a stand against corporate greed. (Alex Brandon)![[Image]](https://i0.wp.com/cryptome.org/info/ows-12/pict14.jpg) People hold signs as they walk in the street during their march from City Hall to the Independence National Historical Park Saturday, Oct. 8, 2011 in Philadelphia. Organizers of what is being called Occupy Philadelphia say the demonstration is meant to be a stand against corporate greed. (Alex Brandon)
People hold signs as they walk in the street during their march from City Hall to the Independence National Historical Park Saturday, Oct. 8, 2011 in Philadelphia. Organizers of what is being called Occupy Philadelphia say the demonstration is meant to be a stand against corporate greed. (Alex Brandon)
You must be logged in to post a comment.