Washington, D.C., December 8, 2011 – The largest U.S. spy agency warned the incoming Bush administration in its “Transition 2001” report that the Information Age required rethinking the policies and authorities that kept the National Security Agency in compliance with the Constitution’s 4th Amendment prohibition on “unreasonable searches and seizures” without warrant and “probable cause,” according to an updated briefing book of declassified NSA documents posted today on the World Wide Web.
Wiretapping the Internet inevitably picks up mail and messages by Americans that would be “protected” under legal interpretations of the NSA’s mandate in effect since the 1970s, according to the documents that were obtained through the Freedom of Information Act by Dr. Jeffrey Richelson, senior fellow of the National Security Archive at George Washington University.
The NSA told the Bush transition team that the “analog world of point-to-point communications carried along discrete, dedicated voice channels” is being replaced by communications that are “mostly digital, carry billions of bits of data, and contain voice, data and multimedia,” and therefore, “senior leadership must understand that today’s and tomorrow’s mission will demand a powerful, permanent presence on a global telecommunications network that will host the ‘protected’ communications of Americans as well as targeted communications of adversaries.”
The documents posted today also include a striking contrast between the largely intact 1998 NSA organizational chart for the Directorate of Operations and the heavily redacted 2001 chart for the Signals Intelligence Directorate (as the operations directorate was renamed), which contains no information beyond the name of its director. “The 2001 organization charts are more informative for what they reveal about the change in NSA’s classification policy than for what they reveal about the actual structure of NSA’s two key directorates,” commented Dr. Richelson. The operations directorate organization chart was provided within three weeks of its being requested in late 1998. In contrast, the request for the Signals Intelligence Directorate organization chart was made on April 21, 2001, and NSA did not provide its substantive response until April 21, 2004 – three years instead of three weeks.
Introduction
The National Security Agency (NSA) is one of the most secret (and secretive) members of the U.S. intelligence community. The predecessor of NSA, the Armed Forces Security Agency (AFSA), was established within the Department of Defense, under the command of the Joint Chiefs of Staff, on May 20, 1949. In theory, the AFSA was to direct the communications intelligence and electronic intelligence activities of the military service signals intelligence units (at the time consisting of the Army Security Agency, Naval Security Group, and Air Force Security Service). In practice, the AFSA had little power, its functions being defined in terms of activities not performed by the service units. (Note 1)
The creation of NSA resulted from a December 10, 1951, memo sent by Walter Bedell Smith to James B. Lay, Executive Secretary of the National Security Council. The memo observed that “control over, and coordination of, the collection and processing of Communications Intelligence had proved ineffective” and recommended a survey of communications intelligence activities. The proposal was approved on December 13, 1951, and the study authorized on December 28, 1951. The report was completed by June 13, 1952. Generally known as the “Brownell Committee Report,” after committee chairman Herbert Brownell, it surveyed the history of U.S. communications intelligence activities and suggested the need for a much greater degree of coordination and direction at the national level. As the change in the security agency’s name indicated, the role of the NSA was to extend beyond the armed forces. (Note 2)
In the last several decades some of the secrecy surrounding NSA has been stripped away by Congressional hearings and investigative research. In the late 1990s NSA had been the subject of criticism for failing to adjust to the post-Cold War technological environment as well as for operating a “global surveillance network” alleged to intrude on the privacy of individuals across the world. The following documents provide insight into the creation, evolution, management and operations of NSA, including the controversial ECHELON program. Also included are newly released documents (11a – 11g) that focus on the restrictions NSA places on reporting the identities of U.S. persons – including former president Jimmy Carter and first lady Hillary Clinton, and NSA Director Michael Hayden’s unusual public statement (Document 24) before the House Intelligence Committee.
Some of the documents that appear for the first time in this update shed additional light on the history of NSA. They concern the NSA’s participation in the space reconnaissance program (Document 3), NSA’s success in deciphering Soviet communications in the 1960s (Document 4), the efficacy of NSA activities in the late mid-to-late 1960s (Document 5), and Israel’s attack on the USS Liberty during the 1967 war (Document 10). Others provide new insight on NSA’s assessment of key issues in the new century (Document 21, Document 23), on NSA’s attempts to adapt to the changing world and communications environment, (Document 22), on the agency’s regression to old policies with regard to organizational secrecy (Document 26a, Document 26b), and on NSA activities before and after the events of 9/11 (Document 25).
Several of these documents also appear in either of two National Security Archive collections on U.S. intelligence. The U.S. Intelligence Community: Organization, Operations and Management: 1947-1989 (1990) and U.S. Espionage and Intelligence: Organization, Operations, and Management, 1947-1996 (1997) publish together for the first time recently declassified documents pertaining to the organizational structure, operations and management of the U.S. Intelligence Community over the last fifty years, cross-indexed for maximum accessibility. Together, these two sets reproduce on microfiche over 2,000 organizational histories, memoranda, manuals, regulations, directives, reports, and studies, totalling more than 50,000 pages of documents from the Office of the Director of Central Intelligence, the Central Intelligence Agency, National Reconnaissance Office, National Security Agency, Defense Intelligence Agency, military service intelligence organizations, National Security Council, and other official government agencies and organizations.
Documents
Note: The following documents are in PDF format.
You will need to download and install the free Adobe Acrobat Reader to view.
Document 1: NSCID 9, “Communications Intelligence,” March 10, 1950
National Security Council Intelligence Directives have provided the highest-level policy guidance for intelligence activities since they were first issued in 1947.
This document establishes and defines the responsibilities of the United States Communications Intelligence Board. The Board, according to the directive, is to provide “authoritative coordination of [the] Communications Intelligence activities of the Government and to advise the Director of Central Intelligence in those matters in the field of Communications Intelligence for which he is responsible.”
The particularly sensitive nature of communications intelligence (COMINT) activities was highlighted by paragraph 6, which noted that such activities should be treated “in all respects as being outside the framework of other or general intelligence activities.” Thus, regulations or directives pertaining to other intelligence activities were not applicable to COMINT activities.
Document 2a: Memorandum from President Harry S. Truman to the Secretary of State, the Secretary of Defense, Subject: Communications Intelligence Activities, October 24, 1952
Document 2b: National Security Council Intelligence Directive No. 9, Communications Intelligence, December 29, 1952
President Truman’s memorandum revokes the provisions of NSCID 9 with regard to the composition, responsibilities, and procedures of the U.S. Communications Intelligence Board. It establishes the USCIB as an entity “acting for and under” a newly created Special Committee of the National Security Council for COMINT, consisting of the Secretary of State and the Secretary of Defense.
More significantly, Truman’s memo, along with a Department of Defense directive, established NSA, and transformed communications intelligence from a military activity divided among the three services to a unified national activity. (Note 3) Thus, the first sentence states that “The communications intelligence (COMINT) activities of the United States are a national responsibility.”
The memorandum instructs the Special Committee to issue a directive to the Secretary of Defense which defines the COMINT mission of NSA as being to “provide an effective, unified organization and control of the communications intelligence activities of the United States conducted against foreign governments.” Thus, “all COMINT collection and production resources of the United States are placed under his operational and technical control.”
The directive provided the NSA director with no authority regarding the collection of electronic intelligence (ELINT)—such as intelligence obtained from the interception of the emanations of radarsor of missile telemetry. Responsibility for ELINT remained with the military services.
NSCID 9 of December 1952 replaces its 1950 predecessor as mandated by Truman’s directive. Often using identical language to that in the Truman directive, it revises the responsibilities of the United States Communications Intelligence Board as well as defining the role of the newly created National Security Agency and enumerating the responsibilities of its director.
New Document 3: Memorandum of Agreement Concerning NSA Participation in the (S) National Reconnaissance Office, August 1, 1962. Top Secret
The National Reconnaissance Office was established in September 1961 to provide a central coordinating authority for the nation’s overhead reconnaissance activities, which included efforts by the Central Intelligence Agency, Air Force, and Navy. An early issue was the division of responsibilities for the development and operation of satellite systems. At a conference in May 1962, it was agreed by CIA and NRO officials that the National Security Agency, despite its responsibility for signals intelligence activities, would not be allowed to develop SIGINT satellites as part of the national reconnaissance program. Herbert Scoville, the CIA’s deputy director for research, argued that the Secretary of Defense was the government’s executive agent for SIGINT activities and since he had chosen to assign the mission to the NRO, the NSA was excluded from undertaking such development activities. (Note 4)
The Secretary’s decision did not mean, however, that NSA, was to play no role in the development and operation of signals intelligence satellites. This represents the first agreement specifying how NSA would be permitted to participate in the National Reconnaissance Program.
New Document 4: Richard Bissell, Review of Selected NSA Cryptanalytic Efforts, February 18, 1965 Top Secret Codeword
Richard Bissell joined the CIA in 1954, serving first as the special assistant to CIA Director Allen Dulles, and then as the agency’s Deputy Director (Plans). He left the agency in February 1962, as a result of the failure of the Bay of Pigs invasion of April 1961. Before and during his tenure as the CIA’s operations chief Bissell directed the development and operation of several key technical collection systems – including the U-2 and OXCART aircraft, and the CORONA reconnaissance satellite.
In his memoirs he reported that, in October 1964, “I accepted a brief assignment from John McCone at the CIA, which involved looking into very highly classified business of another agency of the government. My job was to write a report on what I had learned from visits and interviews with authorities on the problem.” (Note 5) Bissell provided no further information.
In response to a Freedom of Information Act request, the CIA provided a copy of this document – which is Bissell’s report of his investigation of the National Security Agency’s efforts to crack certain high-grade cipher systems. Although the identity of the nation whose ciphers were being attacked is deleted throughout the report, the target country is clearly the Soviet Union. The report discusses the prospects of breaking into high-level Soviet codes and concludes with three principal recommendations – which concern the extent of the overall cryptologic effort, the desirability of reallocating some cryptologic resources, and the possibility of a systematic comparison of the intelligence produced via the successful exploitation of two different components of the cryptanalytic effort.
New Document 5: Letter, Frederick M. Eaton to Richard M. Helms, Director of Central Intelligence, August 16, 1968, Top Secret Codeword w/TS Codeword attachment
This letter, along with the attachment, represents the report of the four-member group, which included Eaton, a New York lawyer and banker, General Lauris Norstad, the Defense Department’s Eugene Fubini, and ambassador Livingston T. Merchant, that was commissioned by DCI Richard Helms in September 1967 to examine the national signals intelligence effort.
The topics examined by the group included program guidance, the DCI and the National Intelligence Resources Board, central review and coordination, management of the cryptologic community, NSA staff organization, COMINT, Telemetry, and ELINT resources, and the communications and dissemination of the information. The letter from Eaton to Helms conveys the group’s nineteen recommendations and the conclusion that
“there must be no slackening in the US cryptologic effort if essential military and other national needs are to be met.”
According to James Bamford’s The Puzzle Palace, Eaton was forced to write the conclusions himself when “many of the staff turned in their pens” because Eaton “recommended no reductions and concluded that all of NSA’s programs were worthwhile,” despite “accumulated substantial evidence that much of the NSA’s intelligence collection was of little or marginal uses to the various intelligence consumers in the community.” (Note 6)
Document 6: Memo to President Johnson, September 6, 1968
This memo, from national security adviser Walt Rostow to President Johnson, provides information concerning North Vietnamese/Viet Cong military and political strategy during the last months of Johnson’s presidency. The last item in the memo notes that its conclusions were partly a function of the author’s access to relevant intercepted communications.
The memo specifically notes unusual, high-priority message traffic between Hanoi and subordinate units directing forces in South Vietnam as well as urgent messages from the Military Affairs Committee of COSVN (Central Office for South Vietnam) to subordinates. It does not reveal how extensively the U.S. was able to decrypt the messages.
Document 7: Department of Defense Directive S-5100.20, “The National Security Agency and the Central Security Service,” December 23, 1971
Originally classified Secret, this directive remains in effect today, with minor changes. Key portions of the directive specify the NSA’s role in managing the signals intelligence effort for the entire U.S. government, the role of the Secretary of Defense in appointing and supervising the work of the NSA’s director, the authorities assigned to the director of NSA, and the relationships that NSA is expected to maintain with other components of the government.
Among the specific responsibilities assigned to the director are preparation of a consolidated SIGINT program and budget for Defense Department SIGINT activities, the “exercise of SIGINT operational control over SIGINT activities of the United States,” and the production and dissemination of SIGINT “in accordance with the objectives, requirements, and priorities established by the Director of Central Intelligence.”
The directive reflects the 1958 addition of electronic intelligence to NSA’s responsibilities, making it the national authority for both components of signals intelligence.
Document 8a: NSCID 6, “Signals Intelligence,” February 17, 1972
Document 8b: Department of Justice, “Report of the Inquiry into CIA-Related Electronic Surveillance Activities,” 1976, pp. 77-9
NSCID 6 is the most recently available NSCID concerning SIGINT. It was still in effect at least as late as 1987. An earlier version of the directive was issued in 1958, when NSA was first assigned responsibility for electronics intelligence.
The version released by the NSC in 1976 contains little more than the definitions for COMINT and ELINT. However, a Justice Department report obtained by author James Bamford while researching his book, The Puzzle Palace, quoted additional portions of the directive.
The directive specifies that the Director of NSA is to produce SIGINT in response to the objectives, requirements and priorities of the Director of Central Intelligence. It also empowers the director to issue direct instructions to any organizations engaged in SIGINT operations, with the exception of certain CIA and FBI activities, and states that the instructions are mandatory.
Document 9a: NSA COMINT Report, “Capital Projects Planned in India,” August 31, 1972
Document 9b: NSA, “India’s Heavy Water Shortages,” October 1982
These two documents provide examples of NSA reporting, as well as demonstrating that NSA’s collection targets have included Indian atomic energy programs. Portions of each document that discuss or reveal the contents of the intercepts have been redacted. However, the classification of the documents indicates that high-level communications intelligence was used in preparing the report. UMBRA is the highest-level compartment of the three compartments of Special Intelligence—the euphemism for COMINT. The lower level compartments are MORAY and SPOKE.
The classification (either TSU [TOP SECRET UMBRA] or MORAY) of the 25 reports which Document 6b was derived from indicate that the report relied extensively on COMINT. The report also demonstrates how NSA, often to the annoyance of the CIA, has gone far beyond its formal collection and processing responsibilities and into the analysis of the data it has collected. (Note 7)
New Document 10: William D. Gerhard and Henry W. Millington, National Security Agency, Attack on a SIGINT Collector, the USS Liberty, 1981. Top Secret Umbra
One of the most controversial events in the history of U.S.-Israeli relations was the attack by Israeli aircraft, during the midst of the Six-Day War of June 1967, on the USS Liberty, a ship assigned to gather signals intelligence on behalf of the National Security Agency. The attack left thirty-four Americans dead and 171 wounded.
In additional to internal studies conducted by both countries there have been numerous books, portions of books, and articles that have sought to review the events and assess blame. The most controversial issue has been whether Israel knowingly attacked a ship it knew to belong to the U.S., which was cruising in international waters off the Sinai Peninsula, to prevent it from monitoring Israeli actions in the midst of the war. Authors have reached diametrically opposite conclusions on this issue. (Note 8)
This extensive report, written by a former head of the NSA element that produced studies of SIGINT crisis situations and the former head of the NSA library, examines the political-military background, consideration’s leading to the ship’s deployment, deployment to the Mediterranean, the attack, Israel’s explanation, recovery and initial assessment, reviews of the incident, and “a final look.” In their conclusion, the authors deal with the issues of possible Israeli foreknowledge of the ship’s nationality and possible Israeli motivations for an attack. They report that a CIA assessment prepared within week of the attack, drawing heavily on communications intercepts, concluded (p. 64) that Israeli forces had not deliberately attacked a ship they knew to be American.
Document 11a: United States Signals Intelligence Directive [USSID] 18, “Legal Compliance and Minimization Procedures,” July 27, 1993
While NSCIDs and DoD Directives offer general guidance on the activities of NSA and the United States SIGINT System (USSS), far more detailed guidance is provided by the director of NSA in the form of United States Signals Intelligence Directives (USSIDs). The directives fall into at least nine different categories: policy, collection, processing, analysis and reporting, standards, administration, training, data processing, and tasking.
In the aftermath of revelations in the 1970s about NSA interception of the communications of anti-war and other political activists new procedures were established governing the interception of communications involving Americans. (Note 9) The version of USSID 18 currently in force was issued in July 1993 and “prescribes policies and procedures and assigns responsibilities to ensure that the missions and functions of the United States SIGINT System (USSS) are conducted in a manner that safeguards the constitutional rights of U.S. persons.” Section 4 (“Collection,” pp.2-6) specifies the circumstances under which U.S. SIGINT activities may intercept communications of or about U.S. persons, as well as the authorities of the Foreign Intelligence Surveillance Court, the Attorney General, and the Director of NSA to approve the collection of such information.
Section 5 (“Processing,” pp.6-7) focuses on the restrictions on processing intercepted communications involving U.S. persons–including domestic communications collected during foreign communications collection operations. Section 6 (“Retention,” p.8) deals with the retention of intercepted communications about U.S. persons. Section 7 (“Dissemination,” pp.8-10) concerns restrictions on dissemination. It requires that all SIGINT reports be written “so as to focus solely on the activities of foreign entities and persons and their agents.” It also specifies some of the conditions under which U.S. persons can be identified in SIGINT reports–for example, when the communications indicate the person is an agent of a foreign power.
Document 11b: NSA, “USSID 18: Dissemination of U.S. Government Organizations and Officials (U)–INFORMATION MEMORANDUM,” February 5, 1993
This NSA memo indicates that the conditions for identification of U.S. officials by title in NSA reporting varies depending on whether or not the individual is a member of the executive branch. Senior officials of the executive branch may be identified by title, without prior approval from higher authority, when the official’s title is necessary to understand or assess foreign intelligence. In contrast, officials from the legislative and judicial branches cannot be identified by title, even if that information is necessary to understand foreign intelligence, unless approval is obtained from higher authority. The memo implies that, under the assumed conditions, the use of names is not permitted.
Document 11c: NSA, “USSID 18: Reporting Guidance on References to the First Lady,” July 8, 1993
This memo followed a U.S. Court of Appeals ruling that Hillary Clinton was a full-time government official. It notes that she could be identified in reports by title (Chairperson of the President’s Task Force on National Health Care Reform) without prior approval when that title was necessary to understand or assess foreign intelligence and when the information related to her official duties. The memo also contains guidance on reports containing information about information concerning Mrs. Clinton that is not clearly foreign intelligence.
Document 11d: National Security Agency/Central Security Service, “U.S. Identities in SIGINT,” March 1994
This 48-page document is intended to provide detailed guidance concerning on the use of U.S. identities in SIGINT reports as well as the dissemination of U.S. identities to consumers outside the United States SIGINT System. It consists of 12 sections (including ones on requests for U.S. identities, accountability, dissemination, and collection and processing), and five appendices (including those on approved generic references and USSID 18 criteria for dissemination).
Document No. 11e: NSA, USSID 18: Reporting Guidance on Former President Carter’s Involvement in the Bosnian Peace Process (U)– Information Guidance, December 15, 1994
The issue of when the identity or even title of a U.S. citizen can be included in reporting based on communications intercepts is a major focus of USSID 18. This NSA memo was prepared in response to the invitation to former President Carter to travel to Bosnia and Herzegovina to participate in efforts to end the war. It specifies that as long as Carter is acting as a private citizen he may be referred to only as a “U.S. person” in any reports.
Document 11f: NSA, “Understanding USSID 18 and Contextual Identifications,” September 30, 1997
The issue of identification by context is the subject of this memo. It notes that, in describing U.S. entities, analysts are required, in general, to substitute sufficiently generic terms for the entities–terms that do not “directly lead to the identification of a U.S. entity even though the identity has been obscured in the report.” Violation of the “contextual identification rule” requires that the report “must be cancelled, reworded and reissued to eliminate the identifying information.” The guidance clearly does not apply to those cases where inclusion of more specific information is necessary to evaluate foreign intelligence.
Document 11g: NSA, “USSID 18 Guide,” February 1998
The introduction to this document notes that it is an informal guide to the provisions of USSID 18 with respect to the issue of the COMINT collection and and dissemination of U.S. identities. One section focues on USSID 18 issues with respect to threat situations, including when an individual is held captive by a foreign power or group or when an intercept reveals a threat to a U.S. person. The section on non-threat situations contains guidance on the disposition of the inadvertent intercept of communciations between U.S. persons, on processing and reporting of incidentally intercepted communications of a U.S. person during foreign intelligence collection, and the handling of U.S. identities in reports.
Document 12: Director of Central Intelligence Directive (DCID) 6/1, “SIGINT Committee,” May 12, 1982
The SIGINT Committee, now known as the National SIGINT Committee, was first established in 1958 to oversee key aspects of U.S. SIGINT activities—the identification of collection requirements, evaluation of how well U.S. and allied SIGINT activities satisfy requirements, and the production of recommendations concerning SIGINT arrangements with foreign governments. This directive is the most recent available version of DCID 6/1. While the directive remains formally classified, the full text of the document has been published previously in scholarly works and on the world wide web. (Note 10)
The SIGINT Committee operated for many years with two permanent subcommittees—the SIGINT Requirements Validation and Evaluation Subcommittee (SIRVES) and the SIGINT Overhead Reconnaissance Subcommittee (SORS). In the mid-1990s two new groups were established: The Weapons and Space Systems Advisory Group, to “coordinate SIGINT on foreign weapons and space systems,” and the National Emitter Intelligence Subcommittee, which focuses on SIGINT production concerning foreign radars and other non-communications signals. (Note 11)
Document 13: NAVSECGRU Instruction C5450.48A, Subj: Mission, Functions and Tasks of Naval Security Group Activity (NAVSECGRUACT) Sugar Grove, West Virginia, September 3, 1991
While NSA directs and manages U.S. SIGINT activities, almost all collection activity is actually carried out by the military service SIGINT units—including the Naval Security Group Command. The role of the unit at Sugar Grove in intercepting the international leased carrier (ILC) communications passing through INTELSAT satellites was first revealed in James Bamford’s The Puzzle Palace. (Note 12)
The regulation reveals that Sugar Grove is associated with what has become a highly controversial program in Europe, North America, Australia, and New Zealand. The program, codenamed ECHELON, has been described as a global surveillance network that intercepts and processes the world’s communications and distributes it among the primary partners in the decades-old UKUSA alliance—the United States, Canada, the United Kingdom, Australia, and New Zealand. (Note 13)
In reality, ECHELON is a more limited program, allowing the UKUSA allies to specify intelligence requirements and automatically receive relevant intercepts obtained by the UKUSA facilities which intercept satellite communications (but not the U.S. facilities that receive data from SIGINT satellites). It is also limited by both technological barriers (the inability to develop word-spotting software so as to allow for the automatic processing of intercepted conversations) and the limitations imposed on collection activities by the UKUSA allies—at least as regards the citizens of those countries. (Note 14) Thus, the NAVSECGRU instruction also specifies that one of the responsibilities of the commander of the Sugar Grove site is to “ensure the privacy of U.S. citizens are properly safeguarded pursuant to the provisions of USSID 18.”
Document 14: Farewell from Vice Admiral William O. Studeman to NSA Employees, April 8, 1992
This address by the departing director of NSA, William Studeman, examines NSA’s post-Cold War mission, likely budgetary limitations, and other challenges facing the agency. Reflecting the increasing emphasis on “support to military operations,” Studeman notes that “the military account is basic to NSA as a defense agency, and the lack of utter faithfulness to this fact will court decline.” He also observes that “the demands for increased global access are growing” and that “these business areas (SMO and global access) will be the two, hopefully strong legs on which NSA must stand.” He also argues that “technical and operational innovation to deal with a changing and changed world must continue to dominate.”
Document 15: Letter, Stewart A. Baker, General Counsel, NSA to Gerald E. McDowell, Esq., September 9, 1992
In the wake of disclosures about the role of the Banca Nazionale del Lavoro (BNL), particularly its Atlanta branch, in the provision of financial assistance to the regime of Saddam Hussein, questions were raised about whether the intelligence community was providing sufficient support to law enforcement.
This letter, from NSA’s general counsel, answers a series of questions from the Justice Department pertaining to NSA’s knowledge of, or involvement in, BNL activities. The responses appear to indicate that NSA had not derived any intelligence concerning BNL activities from its intercept operations. The letter also stresses NSA’s sensitivity to the issue of the privacy of American citizens (noting that “NSA improperly targeted the communications of a number of Americans opposed to the Vietnam War”) and the restrictions on reporting information concerning U.S. citizens or corporations.
Document 16: “Activation of Echelon Units,” from History of the Air Intelligence Agency, 1 January – 31 December 1994, Volume I (San Antonio, TX: AIA, 1995)
The first extract from the Air Intelligence Agency’s 1994 annual history provides additional information on the ECHELON network. ECHELON units include components of the AIA’s 544th Intelligence Group. Detachment 2 and 3 are located at Sabana Seca, Puerto Rico and Sugar Grove, West Virginia respectively. The second reference to Detachment 3 is apparently a typo that should read Detachment 4 (located at Yakima, Washington). The deleted words appear to be “civilian communications,” “NAVSECGRU” and “NSA.”
The second extract notes that AIA’s participation in a classified activity “had been limited to LADYLOVE operations at Misawa AB [Air Base], Japan.” The Misawa LADYLOVE activity was initiated during the Cold War to intercept Soviet military communications transmitted via satellite—along with similar operations at Menwith Hill, UK; Bad Aibling, Germany; and Rosman, North Carolina. This extract suggests that both Guam and Misawa have, at the least, been considered as possible sites for ECHELON operations.
Document 17: NSA Point Paper, “SIGINT Reporting on Murders of Michael DeVine in 1990 and the Disappearance of Efraín Bamaca in 1992 in Guatemala,” March 24, 1995
On March 23, 1995, Rep. Robert Torricelli, a member of the House Permanent Select Committee on Intelligence, charged that the CIA had been withholding from Congress information it had obtained regarding the deaths of Michael DeVine, an American innkeeper living in Guatemala, and Efraín Bámaca Velásquez, a Guatemalan guerrilla leader and husband of an American lawyer. Both murders, according to Torricelli, were linked to a Guatemalan army colonel, Julio Roberto Alpírez, a paid intelligence asset of the CIA. (Note 15)
The revelations set off a firestorm of criticism and caused the Clinton administration to order a government-wide investigation over these and other cases of torture and murder attributed to Guatemalan security forces. While the CIA was the main target of such criticism, Torricelli had also reportedly received an anonymous fax from someone inside the NSA alleging that documents pertaining to the Bámaca and DeVine cases were being destroyed. (Note 16)
This Top Secret NSA position paper responds to these allegations. NSA claims that SIGINT reporting related to these cases is limited to “Guatemalan government reaction to U.S. and international human rights concerns,” and does not include specific information regarding the circumstances of death or the involvement of Colonel Alpírez. The document is one of only a handful of declassified records in which the NSA even acknowledges specific SIGINT activities or reports.
Document 18: Memorandum, Daniel C. Kurtzer, Acting Assitant Secretary, Bureau of Intelligence and Research to Vice Admiral J.M. McConnell, Director, National Security Agency, Subject: Proposed Declassification of the “Fact of” Overhead SIGINT Collection, September 6, 1995
In 1978, President Jimmy Carter acknowledged that the U.S. employed reconnaissance satellites to collect imagery of foreign targets. Early in 1995, President Clinton declassified details concerning early satellite imagery programs such as CORONA. However, even the existence of SIGINT satellites remained classified until late 1995 when Director of Central Intelligence John Deutch authorized the official acknowledgement of space-based SIGINT operations. (Note 17)
The process involved soliciting the opinions of U.S. government departments whose interests might be affected by disclosure. The State Department’s memo expressed concern about the impact in certain countries. Despite the deletions, it is clear that the department was anxious about the impact in the foreign countries where the U.S. operates ground stations for SIGINT satellites—the United Kingdom (at Menwith Hill), Germany (at Bad Aibling), and Australia (at Pine Gap). The memo also indicates that the proposal for declassification emanated from the National Reconnaissance Office.
Document 19: NSA, Recent Classification Decisions, June 2, 1998. Confidential
The increased openness at NSA in the late 1990s extended to historical as well as contemporary matters. In addition to memos announcing individual declassification decisions, summary memos were also issued on occasion. This one covers declassification decisions with regard to a number of categories, including signals intelligence targeting, NSA’s presence abroad, the use of airborne platforms for SIGINT collection, and the codenames used to indicate intelligence obtained from communications or electronic intelligence collection.
Document 20: Organization Chart, NSA Operations Directorate, November 6, 1998
The organization chart of NSA’s Directorate of Operations is notable for several reasons. Traditionally, such information was not released by NSA, which under the provisions of Public Law 86-36 is not required to release even unclassified organizational information. In recent years, however, NSA has released more information about organization and administrative matters, and acknowledged the use of a variety of aircraft for SIGINT collection.
The organization chart also shows how the operations directorate has been reorganized since the end of the Cold War. Throughout much of the Cold War, the directorate consisted of three key regional groups—A (Soviet Bloc), B (Asian Communist), and G (All Other). After the Soviet collapse the regional groups were reduced to one for European nations and one for all other. The new organizational structure reflects the increasing empahsis on transnational activities, which cut across nations and regions.
New Document 21: James R. Taylor, Deputy Director of Operations, Subject: Thoughts on Strategic Issues for the Institution, April 9, 1999. Secret
This memorandum was written early in the tenure of NSA Director Lt. Gen. Michael Hayden, when much attention was being directed to the requirement for NSA to adapt to a new environment – which included new targets, communications technologies, and the availability of advanced encryption techniques.
Taylor notes that money and technology, while among the top five issues facing NSA, are not among the first three. The first and most important issue, according to Taylor, was NSA’s need to reform the management and leadership system. His discussion foreshadowed Hayden’s reorganization of NSA to clearly establish the primacy of the two components – the directorates for signals intelligence and information assurance – responsible for carrying out NSA’s fundamental missions.
A second key issue identified in the memo is the “strengthening and leveraging of [NSA’s] strategic alliances.” This includes NSA’s relationships with foreign SIGINT services, the CIA, and the service cryptologic elements (SCE’s) that carry out much of the collection work for NSA. The discussion of NSA’s relationship with the CIA indicates the increasing importance of human intelligence support to NSA – which can come in the form of acquisition of cipher materials or the clandestine placement of eavesdropping equipment.
The third issue identified is the need to properly staff “our two missions and to spot and nurture talent and leadership for the future.”
New Document 22: Lt. Gen. Jim Clapper, NSA Scientific Advisory Board, Panel on Digital Network Intelligence (DNI), Report to the Director, June 28, 1999, Secret Comint
This study, a complement to another study on conventional collection, is another example of NSA’s attempt to address the changing communication environment. Digital network intelligence is defined as “the intelligence from intercepted digital data communications transmitted between, or resident on, networked computers.”
The study, which has been heavily redacted prior to release, notes an imperative to “re-tool: organizationally, programmatically, and technologically” and examines issues concerning the access and collection of digital network intelligence, processing and extraction of intelligence from the data collected, analysis and reporting, and dissemination.
New Document 23: SSO [Special Security Office], DIA Subject: Implementation Guidance for Elimination of Codewords, October 22, 1999. Unclassified
During the Cold War, as an extension of the system developed in World War II to protect the security of communications intelligence operations, the U.S. established the category of Special Intelligence (SI). Within SI were a number of compartments, which corresponded to the different degrees of sensitivity attached to communications intelligence activities and products. In 1960, with the launch of the first reconnaissance satellites, the U.S. also established the TALENT-KEYHOLE (TK) system, with compartments for satellite imagery (RUFF), satellite ELINT (ZARF), and aerial imagery from the U-2, and later, SR-71.
This message reflects the attempt to simplify the system by eliminating three key codenames from the SI category and one from the TK system.
Document 24: Statement for the Record of NSA Director Lt Gen Michael V. Hayden, USAF before the House Permanent Select Committee on Intelligence, April 12, 2000
In a rare public appearance by the NSA director, Lt. Gen. Michael Hayden outlines the regulatory safeguards and oversight mechanisms that are in place to ensure that the agency’s electronic surveillance mission does not infringe upon the privacy of U.S. persons, and to respond to recent allegations that NSA provides intelligence information to U.S. companies.
The agency may only target the communications of U.S. persons within the United States after obtaining a federal court order suggesting that the individual might be “an agent of a foreign power.” The number of such cases have been “very few” since the passage of the Foreign Intelligence Surveillance Act in 1978. In cases where the NSA wishes to conduct electronic surveillance on U.S. persons overseas, the agency must first obtain the approval of the Attorney General, who must have probable cause to believe that the individual “is an agent of a foreign power, or a spy, terrorist, saboteur, or someone who aides or abets them.” With regard to the unintentional collection of communications to, from, or about U.S. citizens, Hayden stresses that such information is not retained “unless the information is necessary to understand a particular piece of foreign intelligence or assess its importance.”
In response to other allegations, Hayden asserts that NSA cannot request that another country “illegally” collect intelligence on U.S. persons on their behalf, and also that the agency “is not authorized to provide signals intelligence information to private U.S. companies.”
New Document 25: National Security Agency, Transition 2001, December 2000. Secret
This document, prepared for the incoming administration of George W. Bush, was intended to provide a background on NSA’s organization and mission, as well as of the issues facing NSA in the years ahead. Its main sections include those devoted to management, external process, budget, and personnel, policy/issues.
In the discussion of major policy issues, the document notes the changing environment in which the “analog world of point-to-point communications carried along discrete, dedicated voice channels” is being replaced by communications that are “mostly digital, carry billions of bits of data, and contain voice, data and multimedia.” In addition, it states that “global networks leave US critical information infrastructure more vulnerable to foreign intelligence operations and to compromise by a host of non-state entities.” The creation of global networks also requires, according to the transition book, that “senior leadership understand that today’s and tomorrow’s mission will demand a powerful, permanent presence on a global telecommunications network that will host the ‘protected’ communications of Americans as well as targeted communications of adversaries.”
New Document 26a: Organization Chart, Signals Intelligence Directorate
New Document 26b: Organization Chart, Information Assurance Directorate
These two heavily redacted organization charts are more informative for what they reveal about the change in NSA’s classification policy than for what they reveal about the 2001 organizational structure of NSA’s two key directorates.
In contrast to Document 19, the largely intact 1998 organization chart for the Directorate of Operations, Document 26a, the chart for the Signals Intelligence Directorate (as the operations directorate was renamed) contains no information beyond the name of its director. The late 1990s was a period when NSA significantly loosened restrictions on information – not only historical information, but then current organizational information. As a result the operations directorate organization chart was provided within three weeks of its being requested in late 1998. In contrast, the request for the Signals Intelligence Directorate organization chart was made on April 21, 2001 and NSA provided its substantive response on April 21, 2004.
Similarly, in the late 1990s, NSA released detailed organizational information on its Information Security directorate, in contrast to the small amount of it detail it has released on the successor Information Assurance Directorate.
Document 27: Statement for the Record by Lieutenant General Michael V. Hayden, Director, National Security Agency/Central Security Service Before the Joint Inquiry of the Senate Select Committee on Intelligence and the House Permanent Select Committee on Intelligence, October 17, 2002, Unclassified
Hayden, in his testimony to the joint committee intelligence performance prior to the terrorist attacks on New York and Washington of September 11, 2001, addresses three major questions: what did NSA know prior to September 11, what did NSA learn in retrospect, and what had NSA done in response? In his conclusions, Hayden addresses a number of issues – including the relationship between SIGINT and law enforcement, and the line between the government’s need for counterterrorism information and the privacy interests of individuals residing in the United States.
Notes
1. Report to the Secretary of State and the Secretary of Defense by a Special Committee Appointed Pursuant to Letter of 28 December 1951 to Survey Communications Intelligence Activities of the Government, June 13, 1952, pp. 47-48, 119; RG 457, SR-123, Military Reference Branch, NARA; The National Cryptologic School, On Watch: Profiles from the National Security Agency’s Past 40 Years (Ft. Meade, Md.: NCS, 1986), p. 17.
2. Walter Bedell Smith, “Proposed Survey of Communications Intelligence Activities,” December 10, 1951; Report to the Secretary of State and the Secretary of Defense by a Special Committee, p. 118; U.S. Congress, Senate Select Committee to Study Governmental Operations with Respect to Intelligence Activities, Final Report, Book III: Foreign and Military Intelligence (Washington, D.C.: U.S. Government Printing Office, 1976), p. 736; National Security Agency/Central Security Service, NSA/CSS Manual 22-1 (Ft. Meade, MD: NSA, 1986), p. 1.
3. National Security Agency, NSA/CSS Manual 22-1 (Ft. Meade, Md.: NSA, 1986), p. 7.
4. Jeffrey T. Richelson, The Wizards of Langley: Inside the CIA’s Directorate of Science and Technology (Boulder, Co.: Westview, 2001), p. 60.
5. Richard M. Bissell Jr. with Jonathan E. Lewis and Frances T. Pudlo, Reflections of a Cold Warrior: From Yalta to the Bay of Pigs (New Haven, Ct.: Yale University Press, 1996), p. 239.
6. James Bamford, The Puzzle Palace: A Report on NSA, America’s Most Secret Agency (Boston: Houghton-Mifflin, 1982), p. 334.
7. Stansfield Turner, Secrecy and Democracy: The CIA in Transition (Boston: Houghton-Mifflin, 1985), pp. 235-236.
8. James Bamford, Body of Secrets: Anatomy of the Ultra-Secret National Security Agency (New York: Doubleday, 2001), pp. 185-239; A. Jay Cristol, The Liberty Incident: The 1967 Israeli Attack on the U.S. Navy Spy Ship (Washington, D.C.: Brassey’s 2002); James M. Ennes Jr., Assault on the Liberty: The True Story of the Israeli Attack on an American Intelligence Ship (New York: Ivy, 1979).
9. Bob Woodward, “Messages of Activists Intercepted,” Washington Post, October 13, 1975, pp. A1, A14.
10. See Jeffrey T. Richelson, The U.S. Intelligence Community (Cambridge: Ballinger, 2nd ed., 1989/Boulder: Westview Press, 3rd ed., 1995; 4th ed., 1999); See also the World Wide Web site of the Federation of American Scientists, http://fas.org/irp/offdocs/dcid16.htm
11. Lois G. Brown, “National SIGINT Committee,” NSA Newsletter, February 1997, p. 2.
12. James Bamford, The Puzzle Palace: A Report on NSA, America’s Most Secret Agency (Boston, MA: Houghton-Mifflin, 1982), p. 170.
13. Patrick S. Poole, ECHELON: America’s Secret Global Surveillance Network (Washington, D.C.: Free Congress Foundation, October 1998).
14. Duncan Campbell, Interception Capabilities 2000 (Luxembourg: European Parliament, 1999); Jeffrey T. Richelson, “Desperately Seeking Signals,” Bulletin of the Atomic Scientists, Vol. 56, No. 2, pp. 47-51.
15. Dana Priest, “Torricelli Admits Violating House Secrecy Oath,” Washington Post, April 8, 1995, p. A7.
16. Kim Masters, “Truth or Consequences; Rep. Bob Torricelli Leaked the Goods on the CIA. Was It Loyalty or Betrayal?” Washington Post, April 17, 1995, p. C1.
17. DIRNSA, “Fact of Overhead SIGINT Collection,” January 4, 1996.


![[Image]](https://i0.wp.com/cryptome.org/2012/01/0029.jpg)





































































































































































































































![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict34.jpg) Egyptian army soldiers rear arrest a woman protester wearing the Niqab during clashes near Cairo’s downtown Tahrir Square, Egypt, Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building. (Ahmed Ali)
Egyptian army soldiers rear arrest a woman protester wearing the Niqab during clashes near Cairo’s downtown Tahrir Square, Egypt, Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building. (Ahmed Ali)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict0.jpg) Egyptian army soldiers beat a protester wearing a Niqab, an Islamic veil, during clashes near Cairo’s downtown Tahrir Square, Egypt, Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building. At background graffiti depicts members of the military ruling council and Arabic reads: “Killer”. (Ahmed Ali)
Egyptian army soldiers beat a protester wearing a Niqab, an Islamic veil, during clashes near Cairo’s downtown Tahrir Square, Egypt, Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building. At background graffiti depicts members of the military ruling council and Arabic reads: “Killer”. (Ahmed Ali)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict1.jpg) Egyptian protesters threw rocks at military police during clashes near Cairo’s downtown Tahrir Square, Egypt, Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building. (Ahmed Ali)
Egyptian protesters threw rocks at military police during clashes near Cairo’s downtown Tahrir Square, Egypt, Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building. (Ahmed Ali)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict6.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict33.jpg) Egyptian army soldiers arrest a woman protester during clashes with military police near Cairo’s downtown Tahrir Square, Egypt Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building.
Egyptian army soldiers arrest a woman protester during clashes with military police near Cairo’s downtown Tahrir Square, Egypt Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict32.jpg) Egyptian army soldiers arrest a woman protester during clashes with military police near Cairo’s downtown Tahrir Square, Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building.
Egyptian army soldiers arrest a woman protester during clashes with military police near Cairo’s downtown Tahrir Square, Friday, Dec. 16, 2011. Activists say the clashes began after soldiers severely beat a young man who was part of a sit-in outside the Cabinet building.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict35.jpg) Egyptian soldiers arrested a female protester during the second day of clashes in Tahrir Square in Cairo on Saturday. Reuters
Egyptian soldiers arrested a female protester during the second day of clashes in Tahrir Square in Cairo on Saturday. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict2.jpg) A woman is taken away by the Egyptian army during clashes in central Cairo on Dec. 16, 2011. (Khaled Elfiqi)
A woman is taken away by the Egyptian army during clashes in central Cairo on Dec. 16, 2011. (Khaled Elfiqi)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict4.jpg) Egyptian anti-army protesters throw stones at pro-army protesters (not pictured) during clashes, in central Cairo, Egypt, 16 december 2011. EPA
Egyptian anti-army protesters throw stones at pro-army protesters (not pictured) during clashes, in central Cairo, Egypt, 16 december 2011. EPA![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict7.jpg) Egyptian soldiers clash with protesters near Cairo’s Tahrir Square on December 16, 2011 after demonstrators threw petrol bombs and set fire to furniture in front of the nearby parliament. AFP
Egyptian soldiers clash with protesters near Cairo’s Tahrir Square on December 16, 2011 after demonstrators threw petrol bombs and set fire to furniture in front of the nearby parliament. AFP
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict8.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict9.jpg) Anti-government protesters react to tear gas fired by riot police during clashes Saturday, Dec. 17, 2011, in Abu Saiba village west of the capital of Manama, Bahrain. It was the third straight day of clashes along a main highway where protesters have been trying to stage sit-ins against the government. (Hasan Jamali)
Anti-government protesters react to tear gas fired by riot police during clashes Saturday, Dec. 17, 2011, in Abu Saiba village west of the capital of Manama, Bahrain. It was the third straight day of clashes along a main highway where protesters have been trying to stage sit-ins against the government. (Hasan Jamali)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict19.jpg) Protestors supporting Pfc. Bradley Manning gather outside Ft. Meade, Md., Saturday, Dec. 17, 2011, where military prosecutors are presenting their case against him as the source for the WikiLeaks website’s collection of U.S. military and diplomatic secrets. Manning, 24-year-old today, is blamed for the largest leak of classified material in American history. The purpose of the hearing is to determine whether prosecutors have enough evidence to bring Manning to trial. (Jose Luis Magana)
Protestors supporting Pfc. Bradley Manning gather outside Ft. Meade, Md., Saturday, Dec. 17, 2011, where military prosecutors are presenting their case against him as the source for the WikiLeaks website’s collection of U.S. military and diplomatic secrets. Manning, 24-year-old today, is blamed for the largest leak of classified material in American history. The purpose of the hearing is to determine whether prosecutors have enough evidence to bring Manning to trial. (Jose Luis Magana)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict17.jpg) Activist of women’s movement FEMEN stand atop a fence during their protest in front of the cabinet of the Ministers building in Kiev on December 16, 2011. The young Ukrainian women climbed up a fence in front of the Cabinet of Ministers building and protested against the lack of women in the Prime Minister Mykola Azarov’s government. Getty
Activist of women’s movement FEMEN stand atop a fence during their protest in front of the cabinet of the Ministers building in Kiev on December 16, 2011. The young Ukrainian women climbed up a fence in front of the Cabinet of Ministers building and protested against the lack of women in the Prime Minister Mykola Azarov’s government. Getty
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict10.jpg) Anti-government protesters gesture toward riot police (unseen) Thursday, Dec. 15, 2011, along a northern highway by the entry to the Shiite village of Saar, Bahrain, site of an opposition sit-in that was dispersed by police with tear gas and sound bombs. (Hasan Jamali)
Anti-government protesters gesture toward riot police (unseen) Thursday, Dec. 15, 2011, along a northern highway by the entry to the Shiite village of Saar, Bahrain, site of an opposition sit-in that was dispersed by police with tear gas and sound bombs. (Hasan Jamali)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict11.jpg) Protestors hold on to a rope, forming a human chain, while marching to the finance ministry Thursday, Dec. 15 2011, in Lisbon. Civil servants’ unions organized the demonstration to protest the government’s austerity measures. Portugal needed a euro78 billion ($103 billion) bailout earlier this year as its high debt load pushed it close to bankruptcy and the government is enacting an austerity program of pay cuts and tax hikes. Banners read “Don’t rob the future”. (Armando Franca)
Protestors hold on to a rope, forming a human chain, while marching to the finance ministry Thursday, Dec. 15 2011, in Lisbon. Civil servants’ unions organized the demonstration to protest the government’s austerity measures. Portugal needed a euro78 billion ($103 billion) bailout earlier this year as its high debt load pushed it close to bankruptcy and the government is enacting an austerity program of pay cuts and tax hikes. Banners read “Don’t rob the future”. (Armando Franca)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict12.jpg) In this photo taken Tuesday, Dec. 13, 2011, villagers chant slogans as they gather for a protest in Wukan village of Lufeng, China’s Guangdong province. China’s government is trying to defuse a revolt in the small fishing village, offering to investigate the land seizures that touched off the rebellion and vowing to punish leaders of the uprising. The village of Wukan has for months been the site of simmering protests by locals who say officials sold farmland to developers without their consent.
In this photo taken Tuesday, Dec. 13, 2011, villagers chant slogans as they gather for a protest in Wukan village of Lufeng, China’s Guangdong province. China’s government is trying to defuse a revolt in the small fishing village, offering to investigate the land seizures that touched off the rebellion and vowing to punish leaders of the uprising. The village of Wukan has for months been the site of simmering protests by locals who say officials sold farmland to developers without their consent.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict13.jpg) Thousands of Lebanese private and public school teachers hold protest in front of the government building in downtown Beirut, Lebanon, Thursday, Dec. 15, 2011, to demand higher wages. The protest comes a week after the government approved a salary raise that many employees considered too low . (Bilal Hussein)
Thousands of Lebanese private and public school teachers hold protest in front of the government building in downtown Beirut, Lebanon, Thursday, Dec. 15, 2011, to demand higher wages. The protest comes a week after the government approved a salary raise that many employees considered too low . (Bilal Hussein)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict14.jpg) Indian farmers stage a sit in protest as they demand adequate compensation for their farm land acquired for different government projects in Lucknow, India, Wednesday, Dec. 14, 2011. India’s transformation from a largely agrarian nation into a global economic power hinges on a steady supply of land for new factories, call centers, power plants and homes. As cities spill over their seams with ever more people, the government is increasingly seizing the farms around them for private development.
Indian farmers stage a sit in protest as they demand adequate compensation for their farm land acquired for different government projects in Lucknow, India, Wednesday, Dec. 14, 2011. India’s transformation from a largely agrarian nation into a global economic power hinges on a steady supply of land for new factories, call centers, power plants and homes. As cities spill over their seams with ever more people, the government is increasingly seizing the farms around them for private development.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict15.jpg) Dozens of peasants and activists protest demanding the government to recognize them as victims of the country’s internal conflict, outside the Congress in Bogota, Colombia, Wednesday, Dec. 14, 2011. (William Fernando Martinez)
Dozens of peasants and activists protest demanding the government to recognize them as victims of the country’s internal conflict, outside the Congress in Bogota, Colombia, Wednesday, Dec. 14, 2011. (William Fernando Martinez)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest10/pict16.jpg) Protesters with Occupy Seattle march to the Pat the Port of Seattle, Monday afternoon, Dec. 12, 2011 as part of a national effort to disrupt West Coast port traffic. Organizers called for the protests, hoping the day of demonstrations would cut into the profits of the corporations that run the docks and send a message that their movement was not over. (Mark Harrison)
Protesters with Occupy Seattle march to the Pat the Port of Seattle, Monday afternoon, Dec. 12, 2011 as part of a national effort to disrupt West Coast port traffic. Organizers called for the protests, hoping the day of demonstrations would cut into the profits of the corporations that run the docks and send a message that their movement was not over. (Mark Harrison)


















 Political Parties in Afghanistan
Political Parties in Afghanistan










![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict71.jpg) Russian nationalists rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)
Russian nationalists rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict74.jpg) Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky)
Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict62.jpg) A woman wearing fake horns holds a banner during a demonstration against bullfighting in Mexico City December 10, 2011. More than hundred demonstrators took part in a protest against bullfighting in the country. Bullfighting has been one of the most popular sport in Mexico for the last 400 years, according to local media. The banner reads “Torture”. Reuters
A woman wearing fake horns holds a banner during a demonstration against bullfighting in Mexico City December 10, 2011. More than hundred demonstrators took part in a protest against bullfighting in the country. Bullfighting has been one of the most popular sport in Mexico for the last 400 years, according to local media. The banner reads “Torture”. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict59.jpg) French Occupy protesters participate in a rally as part of the 63rd anniversary of the Universal Declaration of the Human Rights, on December 10, 2011 in center Paris. The activists, angered by state spending cuts that hurt ordinary people and high unemployment have called for a nationwide protest. Placard reads : ‘Time for Outrage. Getty
French Occupy protesters participate in a rally as part of the 63rd anniversary of the Universal Declaration of the Human Rights, on December 10, 2011 in center Paris. The activists, angered by state spending cuts that hurt ordinary people and high unemployment have called for a nationwide protest. Placard reads : ‘Time for Outrage. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict58.jpg) Women dressed in violet clothes march from El Zocalo Square to the Revolution monument along Juarez Avenue on December 10, 2011 in Mexico City to protest against violence The activity called ‘The Rally of the One Thousand Women’ promotes to put an end to the discrimination and violence against women. Getty
Women dressed in violet clothes march from El Zocalo Square to the Revolution monument along Juarez Avenue on December 10, 2011 in Mexico City to protest against violence The activity called ‘The Rally of the One Thousand Women’ promotes to put an end to the discrimination and violence against women. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict61.jpg) Member of the Association of Parents of Disappeared Persons (APDP) hold portraits of missing relatives during a demonstration to mark International Human Rights Day in Srinagar on December 10, 2011. Demonstrations were held in Srinagar to protest against alleged human rights violations by Indian security forces on Kashmiris. Rights groups say as many as 8,000 people, mostly young men, have ‘disappeared’ by security forces in India-administered Kashmir since an armed insurgency erupted in the Muslim-majority region. Getty
Member of the Association of Parents of Disappeared Persons (APDP) hold portraits of missing relatives during a demonstration to mark International Human Rights Day in Srinagar on December 10, 2011. Demonstrations were held in Srinagar to protest against alleged human rights violations by Indian security forces on Kashmiris. Rights groups say as many as 8,000 people, mostly young men, have ‘disappeared’ by security forces in India-administered Kashmir since an armed insurgency erupted in the Muslim-majority region. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict55.jpg) In this photo taken with a fisheye lens protesters gather during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
In this photo taken with a fisheye lens protesters gather during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict52.jpg) An elderly demonstrator holds a poster showing an edited photo of Prime Minister Vladimir Putin and signed “2050. No” during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.
An elderly demonstrator holds a poster showing an edited photo of Prime Minister Vladimir Putin and signed “2050. No” during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict53.jpg) Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)
Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict54.jpg) Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)
Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict56.jpg) Protesters light flares during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin)
Protesters light flares during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict57.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict22.jpg) A supporter of Ivory Coast Prime Minister and leader of news forces the former rebel groupe looks on during a legislative election meeting in Ferkessedougou, north of Ivory Coast, on December 9, 2011. The December 11 polls are boycotted by former Ivorian President Laurent Gbagbo’s Ivorian Popular Front party (FPI) and its allies in protest against his arrest and transfer to the International Criminal Court in The Hague. Nearly 1,000 candidates are in the fray for the 255 parliamentary seats. Getty
A supporter of Ivory Coast Prime Minister and leader of news forces the former rebel groupe looks on during a legislative election meeting in Ferkessedougou, north of Ivory Coast, on December 9, 2011. The December 11 polls are boycotted by former Ivorian President Laurent Gbagbo’s Ivorian Popular Front party (FPI) and its allies in protest against his arrest and transfer to the International Criminal Court in The Hague. Nearly 1,000 candidates are in the fray for the 255 parliamentary seats. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict20.jpg) People protest in the halls of the venue of UN Climate Talks on December 9, 2011, to demand that nations not sign a “death sentence” during the UN Framework Convention on Climate Change (UNFCCC) in Durban. Standing side-by-side with delegates from some of the world’s most vulnerable countries, civil society representatives sang traditional South African freedom songs and chanted slogans like, “Listen to the People, Not the Polluters. In the last 48 hours, over 700,000 people have signed petitions calling on major emitters to stand with the nations of Africa and resist any attempts to delay climate action until 2020. UN climate talks entered their second week entangled in a thick mesh of issues with no guarantee that negotiators and their ministers will be able to sort them out. The 194-nation process is facing, for the second time in two years, the prospect of a bustup, even as scientists warn against the mounting threat of disaster-provoking storms, droughts, flood and rising seas made worse by global warming. Getty
People protest in the halls of the venue of UN Climate Talks on December 9, 2011, to demand that nations not sign a “death sentence” during the UN Framework Convention on Climate Change (UNFCCC) in Durban. Standing side-by-side with delegates from some of the world’s most vulnerable countries, civil society representatives sang traditional South African freedom songs and chanted slogans like, “Listen to the People, Not the Polluters. In the last 48 hours, over 700,000 people have signed petitions calling on major emitters to stand with the nations of Africa and resist any attempts to delay climate action until 2020. UN climate talks entered their second week entangled in a thick mesh of issues with no guarantee that negotiators and their ministers will be able to sort them out. The 194-nation process is facing, for the second time in two years, the prospect of a bustup, even as scientists warn against the mounting threat of disaster-provoking storms, droughts, flood and rising seas made worse by global warming. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict19.jpg) Journalists demonstrate during a protest against the murders of their counterparts outside the Presidential house in Tegucigalpa December 9, 2011. 17 journalists have been shot dead in Honduras since 2010, making the small Central American nation one of the world’s most dangerous places for reporters, according human rights groups. Reuters
Journalists demonstrate during a protest against the murders of their counterparts outside the Presidential house in Tegucigalpa December 9, 2011. 17 journalists have been shot dead in Honduras since 2010, making the small Central American nation one of the world’s most dangerous places for reporters, according human rights groups. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict18.jpg) Bahraini women watch as hundreds of anti-government protesters (unseen) run Friday, Dec. 9, 2011, through the Musalla area of Manama, Bahrain, toward an area that had been the hub of Bahrain’s spring uprising and is now a heavily militarized zone that protesters seek to reclaim. The protesters were forced back by riot police just short of the area. Writing on the wall reads “freedom” above pictures of political prisoners. (Hasan Jamali)
Bahraini women watch as hundreds of anti-government protesters (unseen) run Friday, Dec. 9, 2011, through the Musalla area of Manama, Bahrain, toward an area that had been the hub of Bahrain’s spring uprising and is now a heavily militarized zone that protesters seek to reclaim. The protesters were forced back by riot police just short of the area. Writing on the wall reads “freedom” above pictures of political prisoners. (Hasan Jamali)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict17.jpg) Russian opposition leader Sergei Udaltsov’s wife Anastasia, left, speaks to the media as environmental activist and leader of the Khimki forest defenders Yevgenia Chirikova looks at her during a news conference in Moscow, Russia, Friday Dec. 9, 2011. Energized activists and anxious authorities are bracing for anti-government protests planned across Russia’s sprawling expanse Saturday that promise to be the largest demonstration of public outrage since the dying days of the Soviet Union.
Russian opposition leader Sergei Udaltsov’s wife Anastasia, left, speaks to the media as environmental activist and leader of the Khimki forest defenders Yevgenia Chirikova looks at her during a news conference in Moscow, Russia, Friday Dec. 9, 2011. Energized activists and anxious authorities are bracing for anti-government protests planned across Russia’s sprawling expanse Saturday that promise to be the largest demonstration of public outrage since the dying days of the Soviet Union.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict7.jpg) Occupy Boston Protestors reacted to the announcement that their downtown encampment would not be evicted on December 9, 2011, in Boston, Massachusetts. Boston Mayor Thomas M. Menino set a midnight deadline for Occupy Boston protestors to leave their downtown encampment in Dudley Square, or face eviction. In response, many of the protestors chose to take down their tents, and by the midnight deadline much of the camp was gone. At approximately 1:15AM on December 9, 2011, the Boston police announced that they would not evict the protestors from Dudley Square. Protestors took to the street in celebration, and further protest. Getty
Occupy Boston Protestors reacted to the announcement that their downtown encampment would not be evicted on December 9, 2011, in Boston, Massachusetts. Boston Mayor Thomas M. Menino set a midnight deadline for Occupy Boston protestors to leave their downtown encampment in Dudley Square, or face eviction. In response, many of the protestors chose to take down their tents, and by the midnight deadline much of the camp was gone. At approximately 1:15AM on December 9, 2011, the Boston police announced that they would not evict the protestors from Dudley Square. Protestors took to the street in celebration, and further protest. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict9.jpg) Worker Pat Revell pickets outside Unilever’s Port Sunlight factory on the Wirral, Merseyside on December 9, 2011 in Port Sunlight, England. The workers are on strike in protest against the company’s plan to axe their final salary pension scheme. The strike is the first in the history of the consumer goods manufacturer who lists PG Tips tea and Persil washing detergent amongst its products. Getty
Worker Pat Revell pickets outside Unilever’s Port Sunlight factory on the Wirral, Merseyside on December 9, 2011 in Port Sunlight, England. The workers are on strike in protest against the company’s plan to axe their final salary pension scheme. The strike is the first in the history of the consumer goods manufacturer who lists PG Tips tea and Persil washing detergent amongst its products. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict8.jpg) Supporters of the Serbian Radical Party stand in front of policemen while holding posters with a picture of party leader Vojislav Seselj during a protest against Serbia’s efforts to become an official candidate for the European Union membership in front of Serbia’s Presidency building in Belgrade December 9, 2011. The posters read, “We don’t want in the European Union” (L), and “Tadic don’t humiliate Serbs”. Reuters
Supporters of the Serbian Radical Party stand in front of policemen while holding posters with a picture of party leader Vojislav Seselj during a protest against Serbia’s efforts to become an official candidate for the European Union membership in front of Serbia’s Presidency building in Belgrade December 9, 2011. The posters read, “We don’t want in the European Union” (L), and “Tadic don’t humiliate Serbs”. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict6.jpg) People sit as others lay on the ground as they watch a movie in the main entrance of Germans Trias i Pujol hospital during a protest against spending cuts in Catalonia’s public healthcare system, in Badalona, near Barcelona city, Spain, Friday Dec. 9, 2011. The leaders of the 17 countries that use the euro, plus six others, have tentatively agreed to a new treaty that enforces stricter budget rules seen as crucial to solving Europe’s debt crisis and holding the currency-bloc together. An agreement on fiscal discipline is considered a critical first step before the European Central Bank, the International Monetary Fund and others would commit more financial aid to help countries like Italy and Spain, which have large debts and unsustainable borrowing costs. AP
People sit as others lay on the ground as they watch a movie in the main entrance of Germans Trias i Pujol hospital during a protest against spending cuts in Catalonia’s public healthcare system, in Badalona, near Barcelona city, Spain, Friday Dec. 9, 2011. The leaders of the 17 countries that use the euro, plus six others, have tentatively agreed to a new treaty that enforces stricter budget rules seen as crucial to solving Europe’s debt crisis and holding the currency-bloc together. An agreement on fiscal discipline is considered a critical first step before the European Central Bank, the International Monetary Fund and others would commit more financial aid to help countries like Italy and Spain, which have large debts and unsustainable borrowing costs. AP![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict5.jpg) Members of the Red Shirt movement joke with a Thai police officer as they gather to protest against former Thai Prime Minister Abhisit Vejjajiva outside Metropolitan Police headquarters in Bangkok, Thailand Friday, Dec. 9, 2011. Abhisit was called in to give information to a police investigation team on the government’s crackdown on red-shirt demonstrators last year during which 91 people were killed. (Apichart Weerawong)
Members of the Red Shirt movement joke with a Thai police officer as they gather to protest against former Thai Prime Minister Abhisit Vejjajiva outside Metropolitan Police headquarters in Bangkok, Thailand Friday, Dec. 9, 2011. Abhisit was called in to give information to a police investigation team on the government’s crackdown on red-shirt demonstrators last year during which 91 people were killed. (Apichart Weerawong)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict63.jpg) Panamanian people protest against the return of former General Manuel Noriega to Panama, in Panama City on December 09,2011. Noriega returns to Panama without the trappings of political or military clout, but with something of incalculable value — detailed knowledge of the skeletons that lurk in the Central American nation’s closet. Getty
Panamanian people protest against the return of former General Manuel Noriega to Panama, in Panama City on December 09,2011. Noriega returns to Panama without the trappings of political or military clout, but with something of incalculable value — detailed knowledge of the skeletons that lurk in the Central American nation’s closet. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict4.jpg) Thousands of people gather outside the main courthouse during the first trial of 22 leftist students who were jailed after they staged a demonstration to protest a police crackdown on anti-government demonstrators in the northern town of Hopa, Black Sea, ahead of general elections in June, in Ankara, Turkey, Friday, Dec. 9, 2011. (Burhan Ozbilici)
Thousands of people gather outside the main courthouse during the first trial of 22 leftist students who were jailed after they staged a demonstration to protest a police crackdown on anti-government demonstrators in the northern town of Hopa, Black Sea, ahead of general elections in June, in Ankara, Turkey, Friday, Dec. 9, 2011. (Burhan Ozbilici)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict10.jpg) Activists of the Ukrainian women’s movement FEMEN stage a performance in front of the Christ the Saviour Cathedral in Moscow, on December 9, 2011, to protest against alleging mass fraud in the Russian December 4 parliamentary polls and demanding Russia’s Prime Minister Vladimir Putin that he stop his political activities. Putin, who became premier in 2008 after serving two Kremlin terms, filed this week his application to stand in the March elections. Getty
Activists of the Ukrainian women’s movement FEMEN stage a performance in front of the Christ the Saviour Cathedral in Moscow, on December 9, 2011, to protest against alleging mass fraud in the Russian December 4 parliamentary polls and demanding Russia’s Prime Minister Vladimir Putin that he stop his political activities. Putin, who became premier in 2008 after serving two Kremlin terms, filed this week his application to stand in the March elections. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict0.jpg) Activists of Ukraine’s protest group Femen, protest outside the Christ the Saviour cathedral in Moscow, Russia, Friday, Dec. 9, 2011. The post-election protests in Moscow drew thousands and continued for several days in the biggest ever challenge to Putin, reflecting a growing public frustration with his rule that may complicate his bid to reclaim the presidency in next March’s vote. (Ivan Sekretarev)
Activists of Ukraine’s protest group Femen, protest outside the Christ the Saviour cathedral in Moscow, Russia, Friday, Dec. 9, 2011. The post-election protests in Moscow drew thousands and continued for several days in the biggest ever challenge to Putin, reflecting a growing public frustration with his rule that may complicate his bid to reclaim the presidency in next March’s vote. (Ivan Sekretarev)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict45.jpg) Medical workers rally at the Latvian Saeima (Parliament) building to protest budget cuts in health care on December 8, 2011 in Riga. The protesters are holding black balloons and various placards, urging the government to care for medical workers and warning that many health care workers may leave Latvia. Placards read: ‘Left country. Everyone has rights to receive health care’. Getty
Medical workers rally at the Latvian Saeima (Parliament) building to protest budget cuts in health care on December 8, 2011 in Riga. The protesters are holding black balloons and various placards, urging the government to care for medical workers and warning that many health care workers may leave Latvia. Placards read: ‘Left country. Everyone has rights to receive health care’. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict44.jpg) Demonstrators protest about high inflation and low interest rates outside the Bank of England in the City of London December 8, 2011. The Bank of England voted on Thursday to stick to its four-month programme to pump an extra 75 billion pounds of quantitative easing into the rapidly slowing economy. Reuters
Demonstrators protest about high inflation and low interest rates outside the Bank of England in the City of London December 8, 2011. The Bank of England voted on Thursday to stick to its four-month programme to pump an extra 75 billion pounds of quantitative easing into the rapidly slowing economy. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict43.jpg) Pakistani protesters carry national flags as they march during a demonstration in Islamabad on December 8, 2011 against the cross-border NATO air strike on Pakistani troops. Several hundred journalists, labour leaders and traders on December 8, took to streets to condemn a recent air strike by NATO on Pakistani military checkposts that killed 24 soldiers. Pakistan shut the only supply route in Khyber tribal region for international troops in Afghanistan, boycotted the Bonn conference and announced to revisit policy towards the US in protest against the attack. Getty
Pakistani protesters carry national flags as they march during a demonstration in Islamabad on December 8, 2011 against the cross-border NATO air strike on Pakistani troops. Several hundred journalists, labour leaders and traders on December 8, took to streets to condemn a recent air strike by NATO on Pakistani military checkposts that killed 24 soldiers. Pakistan shut the only supply route in Khyber tribal region for international troops in Afghanistan, boycotted the Bonn conference and announced to revisit policy towards the US in protest against the attack. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict42.jpg) Fundamentalist Christians protest on December 8, 2011 in Paris, near the Rond-Point theatre where Argentina-born author Rodrigo Garcia’s play ‘Golgota Picnic’ is performed which they judge ‘blasphemous’. Getty
Fundamentalist Christians protest on December 8, 2011 in Paris, near the Rond-Point theatre where Argentina-born author Rodrigo Garcia’s play ‘Golgota Picnic’ is performed which they judge ‘blasphemous’. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict41.jpg) People pose with a protester wearing a mock mask depicting Russian Prime Minister Vladimir Putin during a rally in downtown St.Petersburg, Russia, Thursday, Dec. 8, 2011. More than five hundred people protested in St.Petersburg against Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
People pose with a protester wearing a mock mask depicting Russian Prime Minister Vladimir Putin during a rally in downtown St.Petersburg, Russia, Thursday, Dec. 8, 2011. More than five hundred people protested in St.Petersburg against Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict40.jpg) Occupy Boston protester Heather McCann, of Watertown, Mass., center, loads a crate of books into a truck at the Dewey Square encampment while dismantling the camps library, in Boston, Thursday, Dec. 8, 2011. Boston Mayor Thomas Menino said Thursday that Occupy Boston protesters must leave their encampment in the city’s financial district by midnight Thursday or face eviction by police. (Steven Senne)
Occupy Boston protester Heather McCann, of Watertown, Mass., center, loads a crate of books into a truck at the Dewey Square encampment while dismantling the camps library, in Boston, Thursday, Dec. 8, 2011. Boston Mayor Thomas Menino said Thursday that Occupy Boston protesters must leave their encampment in the city’s financial district by midnight Thursday or face eviction by police. (Steven Senne)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict31.jpg) A veiled Kashmiri government employee participates in a protest against the government in Srinagar, India, Thursday, Dec. 8, 2011. Dozens of government employees demanded release of arrears and regularization of jobs for daily wage workers. (Dar Yasin)
A veiled Kashmiri government employee participates in a protest against the government in Srinagar, India, Thursday, Dec. 8, 2011. Dozens of government employees demanded release of arrears and regularization of jobs for daily wage workers. (Dar Yasin)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict30.jpg) Protesters march to join fellow protesters who camped out outside a Catholic church near the Presidential Palace in Manila, Philippines Thursday Dec. 8, 2011 to await news of the scheduled execution of a Filipino man convicted in China for drug trafficking. Philippine officials said, the Filipino man, who was convicted on drug trafficking, was executed in China on Thursday despite an appeal for clemency from President Benigno Aquino III on humanitarian grounds. (Bullit Marquez)
Protesters march to join fellow protesters who camped out outside a Catholic church near the Presidential Palace in Manila, Philippines Thursday Dec. 8, 2011 to await news of the scheduled execution of a Filipino man convicted in China for drug trafficking. Philippine officials said, the Filipino man, who was convicted on drug trafficking, was executed in China on Thursday despite an appeal for clemency from President Benigno Aquino III on humanitarian grounds. (Bullit Marquez)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict29.jpg) Kashmiri government employees participate in a protest against the government in Srinagar, India, Thursday, Dec. 8, 2011. Dozens of government employees demanded release of arrears and regularization of jobs for daily wage workers. (Dar Yasin)
Kashmiri government employees participate in a protest against the government in Srinagar, India, Thursday, Dec. 8, 2011. Dozens of government employees demanded release of arrears and regularization of jobs for daily wage workers. (Dar Yasin)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict28.jpg) A small group of demonstrators screams slogans demanding UN protection for Iranian dissidents in Camp Ashraf, Iraq, as they protest outside the Dutch Foreign Ministry during U.S. Secretary of State Hillary Rodham Clinton’s visit in The Hague, Netherlands, Thursday Dec. 8, 2011. (Peter Dejong)
A small group of demonstrators screams slogans demanding UN protection for Iranian dissidents in Camp Ashraf, Iraq, as they protest outside the Dutch Foreign Ministry during U.S. Secretary of State Hillary Rodham Clinton’s visit in The Hague, Netherlands, Thursday Dec. 8, 2011. (Peter Dejong)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict27.jpg) Police officers detain an opposition activist during a rally in downtown St.Petersburg, Russia, Thursday, Dec. 8, 2011. More than five hundreds people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
Police officers detain an opposition activist during a rally in downtown St.Petersburg, Russia, Thursday, Dec. 8, 2011. More than five hundreds people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict26.jpg) French far-right leader Marine Le Pen arrives at their demonstration in Paris Thursday, Dec. 8, 2011. The demonstration was to oppose a bill on which the Senate were voting Thursday afternoon, a private members bill calling for the right for foreigners to be able to vote in French municipal elections. (Jacques Brinon)
French far-right leader Marine Le Pen arrives at their demonstration in Paris Thursday, Dec. 8, 2011. The demonstration was to oppose a bill on which the Senate were voting Thursday afternoon, a private members bill calling for the right for foreigners to be able to vote in French municipal elections. (Jacques Brinon)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict25.jpg) People living near nuclear plant sites shout slogans during an anti-nuclear protest in New Delhi, India, Thursday, Dec. 8, 2011. The protesters demanded scrapping of projects that endanger people’s safety and threaten livelihoods, according to a press release. Placard reads “Stop displacement of people in the name of development.” (Manish Swarup)
People living near nuclear plant sites shout slogans during an anti-nuclear protest in New Delhi, India, Thursday, Dec. 8, 2011. The protesters demanded scrapping of projects that endanger people’s safety and threaten livelihoods, according to a press release. Placard reads “Stop displacement of people in the name of development.” (Manish Swarup)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict23.jpg) An Israeli musician covers her face in protest, as she performs during a rally against gender segregation, in Jerusalem, Wednesday, Dec. 7, 2011. Hundreds of women and women’s rights activists gathered in central Jerusalem Wednesday night for a rally organized by the New Israel Fund, themed “women will be seen and heard”, to protest discrimination against women in Israel. (Sebastian Scheiner)
An Israeli musician covers her face in protest, as she performs during a rally against gender segregation, in Jerusalem, Wednesday, Dec. 7, 2011. Hundreds of women and women’s rights activists gathered in central Jerusalem Wednesday night for a rally organized by the New Israel Fund, themed “women will be seen and heard”, to protest discrimination against women in Israel. (Sebastian Scheiner)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict49.jpg) Nepalese Buddhist monks and nuns take out a protest in Katmandu, Nepal, Wednesday, Dec. 7, 2011. Hundreds of Buddhists demonstrated in Nepal’s capital to protest the appointment of Maoist party chief Pushpa Kamal Dahal to head a project to develop the area where Buddha was believed born in southern Nepal. The protestors demanded that there should not be any political involvement in the project to develop Lumbini, located 150 miles (240 kilometers) southwest of Katmandu. AP
Nepalese Buddhist monks and nuns take out a protest in Katmandu, Nepal, Wednesday, Dec. 7, 2011. Hundreds of Buddhists demonstrated in Nepal’s capital to protest the appointment of Maoist party chief Pushpa Kamal Dahal to head a project to develop the area where Buddha was believed born in southern Nepal. The protestors demanded that there should not be any political involvement in the project to develop Lumbini, located 150 miles (240 kilometers) southwest of Katmandu. AP![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict48.jpg) A Libyan girl holds a placard that reads in Arabic ‘Thank you our brave rebels, but now let us live in peace’ during a protest in Tripoli’s landmark Martyrs Square on December 7, 2011 against former rebels who toppled Moamer Kadhafi but are still camping out in the capital and still have their weapons. Getty
A Libyan girl holds a placard that reads in Arabic ‘Thank you our brave rebels, but now let us live in peace’ during a protest in Tripoli’s landmark Martyrs Square on December 7, 2011 against former rebels who toppled Moamer Kadhafi but are still camping out in the capital and still have their weapons. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict47.jpg) Members of the Canadian Youth Delegation stage a protest as Canada’s Minister of Environment Peter Kent addresses the United Nations Climate Change Conference (COP17) in Durban in this handout picture released by the Canada Youth Delegation, December 7, 2011. Reuters
Members of the Canadian Youth Delegation stage a protest as Canada’s Minister of Environment Peter Kent addresses the United Nations Climate Change Conference (COP17) in Durban in this handout picture released by the Canada Youth Delegation, December 7, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict46.jpg) Two protesters look at each other as they await processing after being arrested by Washington DC Metropolitan Police during an Occupy DC protest in Washington, December 7, 2011. Police arrested economic protesters in Washington on Wednesday as they blocked streets and disrupted traffic in an area famous as a center for the offices of lobbyists. Reuters
Two protesters look at each other as they await processing after being arrested by Washington DC Metropolitan Police during an Occupy DC protest in Washington, December 7, 2011. Police arrested economic protesters in Washington on Wednesday as they blocked streets and disrupted traffic in an area famous as a center for the offices of lobbyists. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict24.jpg) An Occupy DC demonstrator sits on a chair as demonstrators blocked an intersection on K St., in Washington, Wednesday, Dec. 7, 2011. (Evan Vucci)
An Occupy DC demonstrator sits on a chair as demonstrators blocked an intersection on K St., in Washington, Wednesday, Dec. 7, 2011. (Evan Vucci)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict32.jpg) Occupy Wall Street activists carry house warming gifts to a house warming party during a tour of foreclosed homes in the East New York neighborhood of the Brooklyn borough of New York, Tuesday, Dec. 6, 2011. Finding it increasingly difficult to camp in public spaces, Occupy protesters across the country are reclaiming foreclosed homes and boarded-up properties, signaling a tactical shift for the movement against wealth inequality.
Occupy Wall Street activists carry house warming gifts to a house warming party during a tour of foreclosed homes in the East New York neighborhood of the Brooklyn borough of New York, Tuesday, Dec. 6, 2011. Finding it increasingly difficult to camp in public spaces, Occupy protesters across the country are reclaiming foreclosed homes and boarded-up properties, signaling a tactical shift for the movement against wealth inequality.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict50.jpg) A Colombian woman living in Panama holds a Colombian national flag during a protest march against the Revolutionary Armed Forces of Colombia (FARC), in Panama City December 6, 2011. Outraged by the killing of four captives by FARC rebels, Colombians protested on Tuesday to demand an end to half a century of guerrilla violence and kidnapping. The words on the flag read: “Release them”. Reuters
A Colombian woman living in Panama holds a Colombian national flag during a protest march against the Revolutionary Armed Forces of Colombia (FARC), in Panama City December 6, 2011. Outraged by the killing of four captives by FARC rebels, Colombians protested on Tuesday to demand an end to half a century of guerrilla violence and kidnapping. The words on the flag read: “Release them”. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict51.jpg) Colombian demonstrators take part in a protest march against Revolutionary Armed Forces of Colombia FARC rebels in Cali December 6, 2011. Outraged by the execution of four captives by FARC rebels, tens of thousands of Colombians protested across the nation on Tuesday to demand an end to half a century of guerrilla violence and kidnapping. Reuters
Colombian demonstrators take part in a protest march against Revolutionary Armed Forces of Colombia FARC rebels in Cali December 6, 2011. Outraged by the execution of four captives by FARC rebels, tens of thousands of Colombians protested across the nation on Tuesday to demand an end to half a century of guerrilla violence and kidnapping. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict33.jpg) In this Nov. 2, 2011 file photo, occupy Oakland protesters march through the Port of Oakland in Oakland, Calif. Protesters want to shut down ports up and down the U.S. West Coast on Monday, Dec.12,2011, to gum up the engines of global commerce. But organizers who are partly billing this effort as a show of solidarity with longshoremen have not won the support of the powerful union representing thousands of dock workers. (Noah Berger)
In this Nov. 2, 2011 file photo, occupy Oakland protesters march through the Port of Oakland in Oakland, Calif. Protesters want to shut down ports up and down the U.S. West Coast on Monday, Dec.12,2011, to gum up the engines of global commerce. But organizers who are partly billing this effort as a show of solidarity with longshoremen have not won the support of the powerful union representing thousands of dock workers. (Noah Berger)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict34.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest9/pict35.jpg) An activist of a local women’s rights watchdog FEMEN, with writing “I am independent” and Ukraine’s’ national flag on her belly, seen during celebrities on the occasion of Ukraine’s 19th Independence in Kiev, Ukraine, Tuesday, Aug. 24, 2010. (Efrem Lukatsky)
An activist of a local women’s rights watchdog FEMEN, with writing “I am independent” and Ukraine’s’ national flag on her belly, seen during celebrities on the occasion of Ukraine’s 19th Independence in Kiev, Ukraine, Tuesday, Aug. 24, 2010. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict0.jpg) Kashmir Sutherland huddles with other protesters for warmth in Shemanski Park after police told them to take down tents or be kicked out Monday, Dec. 5, 2011, in Portland, Ore. The Oregonian reports the demonstrators agreed to take down a tent to stay in the park Sunday night. On Saturday night police arrested 19 demonstrators setting up structures in the South Park blocks. Police evicted demonstrators on Nov. 13 from two downtown parks.
Kashmir Sutherland huddles with other protesters for warmth in Shemanski Park after police told them to take down tents or be kicked out Monday, Dec. 5, 2011, in Portland, Ore. The Oregonian reports the demonstrators agreed to take down a tent to stay in the park Sunday night. On Saturday night police arrested 19 demonstrators setting up structures in the South Park blocks. Police evicted demonstrators on Nov. 13 from two downtown parks.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict44.jpg) A woman shouts slogans during a rally in Moscow, Monday, Dec. 5, 2011. Several thousand people have protested in Moscow against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. A group of several hundred then marched toward the Central Elections Commission near the Kremlin, but were stopped by riot police and taken away in buses. (Sergey Ponomarev)
A woman shouts slogans during a rally in Moscow, Monday, Dec. 5, 2011. Several thousand people have protested in Moscow against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. A group of several hundred then marched toward the Central Elections Commission near the Kremlin, but were stopped by riot police and taken away in buses. (Sergey Ponomarev)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict26.jpg) A blind woman rests in front of a police line during a protest by Greek blind people outside Parliament in Athens, on Monday, Dec. 5, 2011. Dozens of people took part in the demonstration, to protest against government welfare spending cuts. Greece is in the throes of an acute financial crisis and has implemented a harsh austerity programme in exchange for international rescue loans. (Petros Giannakouris)
A blind woman rests in front of a police line during a protest by Greek blind people outside Parliament in Athens, on Monday, Dec. 5, 2011. Dozens of people took part in the demonstration, to protest against government welfare spending cuts. Greece is in the throes of an acute financial crisis and has implemented a harsh austerity programme in exchange for international rescue loans. (Petros Giannakouris)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict37.jpg) Occupy DC protesters stand inside a structure set up overnight in McPherson Square, Sunday, Dec. 4, 2011 in Washington. Protesters are refusing to dismantle the unfinished wooden structure erected in the park. (Manuel Balce Ceneta)
Occupy DC protesters stand inside a structure set up overnight in McPherson Square, Sunday, Dec. 4, 2011 in Washington. Protesters are refusing to dismantle the unfinished wooden structure erected in the park. (Manuel Balce Ceneta)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict43.jpg) In this Nov. 17, 2011 file photo, students clash with police during a demonstration in Milan, Italy, as university students protest against budget cuts and a lack of jobs, hours before new Italian Premier Mario Monti reveals his anti-crisis strategy in Parliament. Europe’s sovereign-debt crisis, which has dragged on for more than two years, is entering a pivotal week, as leaders across the continent converge to prevent a collapse of the euro and a financial panic from spreading.
In this Nov. 17, 2011 file photo, students clash with police during a demonstration in Milan, Italy, as university students protest against budget cuts and a lack of jobs, hours before new Italian Premier Mario Monti reveals his anti-crisis strategy in Parliament. Europe’s sovereign-debt crisis, which has dragged on for more than two years, is entering a pivotal week, as leaders across the continent converge to prevent a collapse of the euro and a financial panic from spreading.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict35.jpg) A female activist carries a sign promoting gender equality as protesters march through downtown Rabat calling for greater democracy. Moroccan pro-democracy activists called for a day of rage on Dec. 4, 2011, a week after legislative elections but few turned out. (Paul Schemm)
A female activist carries a sign promoting gender equality as protesters march through downtown Rabat calling for greater democracy. Moroccan pro-democracy activists called for a day of rage on Dec. 4, 2011, a week after legislative elections but few turned out. (Paul Schemm)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict66.jpg) Animal rights activists of the AnimaNaturalis international organization stage a naked protest in the middle of the Plaza de Espana square in the centre of Madrid on December 4, 2011, to denounce the slaying of animals to make fur coats. The men and women, covered in red paint that resembled blood, lay down and curled up against each other under a sunny sky in the busy square which is home to several cinemas, cafes and restaurants. Placard reads ‘How many lives for a coat?’. Getty
Animal rights activists of the AnimaNaturalis international organization stage a naked protest in the middle of the Plaza de Espana square in the centre of Madrid on December 4, 2011, to denounce the slaying of animals to make fur coats. The men and women, covered in red paint that resembled blood, lay down and curled up against each other under a sunny sky in the busy square which is home to several cinemas, cafes and restaurants. Placard reads ‘How many lives for a coat?’. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict67.jpg) Participants attend the Slutwalk Singapore event held at the Speakers’ Corner on December 4, 2011. Supporters of the global SlutWalk movement against sexual violence held a rally in Singapore, attracting dozens to a rare protest in the strictly policed city-state. Getty
Participants attend the Slutwalk Singapore event held at the Speakers’ Corner on December 4, 2011. Supporters of the global SlutWalk movement against sexual violence held a rally in Singapore, attracting dozens to a rare protest in the strictly policed city-state. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict64.jpg) Russian police officers detain opposition demonstrators during an unsanctioned rally in downtown Moscow, Russia, Sunday, Dec. 4, 2011. The rally was staged by a few dozen activists of the Left Front opposition group to protest against Sunday’s elections. (Misha Japaridze)
Russian police officers detain opposition demonstrators during an unsanctioned rally in downtown Moscow, Russia, Sunday, Dec. 4, 2011. The rally was staged by a few dozen activists of the Left Front opposition group to protest against Sunday’s elections. (Misha Japaridze)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict68.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict72.jpg) Police officers try to arrest activists of the Ukrainian women’s movement FEMEN as they protest on December 3, 2011 against a meeting of opposition parties in Kiev. FEMEN activists protested against the event, saying that peeple came to the meeting because its organizers promised them money.
Police officers try to arrest activists of the Ukrainian women’s movement FEMEN as they protest on December 3, 2011 against a meeting of opposition parties in Kiev. FEMEN activists protested against the event, saying that peeple came to the meeting because its organizers promised them money.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict71.jpg) Body-painted environmental activists demonstrate outside the United Nations Climate Change conference (COP17) in Durban December 3, 2011. The protest march was part of a Global Day of Action to demand a fair climate change deal. Reuters
Body-painted environmental activists demonstrate outside the United Nations Climate Change conference (COP17) in Durban December 3, 2011. The protest march was part of a Global Day of Action to demand a fair climate change deal. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict69.jpg) An opponent of reelected Nicaraguan President Daniel Ortega holds a banner reading ‘Fraud=Poverty’, as she takes part in a protest called ”march against fraud” in Managua on December 3, 2011. About five thousand people marched in Nicaragua denouncing electoral fraud in past November 6 elections in Nicaragua and demanding a new election with foreign observers. Getty
An opponent of reelected Nicaraguan President Daniel Ortega holds a banner reading ‘Fraud=Poverty’, as she takes part in a protest called ”march against fraud” in Managua on December 3, 2011. About five thousand people marched in Nicaragua denouncing electoral fraud in past November 6 elections in Nicaragua and demanding a new election with foreign observers. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict65.jpg) Occupy LA protesters march from Pershing Square to the Los Angeles County Men’s Central Jail where protesters, who were arrested on Wednesday, were being held, in Los Angeles, on Saturday, Dec. 3, 2011. (David Zentz)
Occupy LA protesters march from Pershing Square to the Los Angeles County Men’s Central Jail where protesters, who were arrested on Wednesday, were being held, in Los Angeles, on Saturday, Dec. 3, 2011. (David Zentz)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict61.jpg) Andean people protest against Newmont Mining’s Conga gold project during a march near the Cortada lagoon at Peru’s region of Cajamarca, November 24, 2011. Peru’s prime minister on December 2, 2011, said Newmont Mining must set aside money to finance social projects and any environmental damage as a precondition for moving forward on a stalled $4.8 billion gold mine project. Opponents of Newmont Mining’s $4.8 billion Conga project refused to end their rallies on November 30, 2011, saying Peru must permanently cancel the proposed mine after temporarily halting work on it to avert violence. Protesters and farmers say the mine would cause pollution and hurt water supplies by replacing a string of alpine lakes with artificial reservoirs. Picture taken November 24, 2011.
Andean people protest against Newmont Mining’s Conga gold project during a march near the Cortada lagoon at Peru’s region of Cajamarca, November 24, 2011. Peru’s prime minister on December 2, 2011, said Newmont Mining must set aside money to finance social projects and any environmental damage as a precondition for moving forward on a stalled $4.8 billion gold mine project. Opponents of Newmont Mining’s $4.8 billion Conga project refused to end their rallies on November 30, 2011, saying Peru must permanently cancel the proposed mine after temporarily halting work on it to avert violence. Protesters and farmers say the mine would cause pollution and hurt water supplies by replacing a string of alpine lakes with artificial reservoirs. Picture taken November 24, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict56.jpg) A woman protester join others as they shout slogans during the observance of World Climate Day Saturday, Dec. 3, 2011 near the U.S. Embassy in Manila, Philippines. The protest coincided with the annual climate talks of the Conference of Parties (COP17) in Durban, South Africa. (Pat Roque)
A woman protester join others as they shout slogans during the observance of World Climate Day Saturday, Dec. 3, 2011 near the U.S. Embassy in Manila, Philippines. The protest coincided with the annual climate talks of the Conference of Parties (COP17) in Durban, South Africa. (Pat Roque)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict60.jpg) A woman holds aplacard during a protest march against the war in Afghanistan on December 3, 2011 in the western German city of Bonn where a major international conference on December 5 will discuss the country’s future beyond 2014, when NATO-led international combat troops will leave. Getty
A woman holds aplacard during a protest march against the war in Afghanistan on December 3, 2011 in the western German city of Bonn where a major international conference on December 5 will discuss the country’s future beyond 2014, when NATO-led international combat troops will leave. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict57.jpg) A survivor of the Bhopal gas tragedy lies on a railway track as others sit around to stop train movement during a protest in Bhopal, India, Saturday, Dec. 3, 2011. Thousands of survivors of the world’s worst industrial accident blocked trains through a central Indian city on Saturday to demand more compensation.
A survivor of the Bhopal gas tragedy lies on a railway track as others sit around to stop train movement during a protest in Bhopal, India, Saturday, Dec. 3, 2011. Thousands of survivors of the world’s worst industrial accident blocked trains through a central Indian city on Saturday to demand more compensation.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict58.jpg) Female Iranian demonstrators hold posters showing supreme leader Ayatollah Ali Khamenei, left in the posters, and late revolutionary founder Ayatollah Khomeini, during a demonstration to welcome Iranian diplomats expelled from London in retaliation for attacks on British compounds in Tehran, at the Mehrabad airport in Tehran, Iran, early Saturday, Dec. 3, 2011.
Female Iranian demonstrators hold posters showing supreme leader Ayatollah Ali Khamenei, left in the posters, and late revolutionary founder Ayatollah Khomeini, during a demonstration to welcome Iranian diplomats expelled from London in retaliation for attacks on British compounds in Tehran, at the Mehrabad airport in Tehran, Iran, early Saturday, Dec. 3, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict59.jpg) Students are arrested during a protest against the government to demand changes in the public state education system in Santiago, December 2, 2011. Chilean students have been protesting against what they say is profiteering in the state education system. Reuters
Students are arrested during a protest against the government to demand changes in the public state education system in Santiago, December 2, 2011. Chilean students have been protesting against what they say is profiteering in the state education system. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict41.jpg) Demonstrators walk on a protest march in central London November 30, 2011. Teachers, nurses and border guards walked out on Wednesday as up to two million state workers staged Britain’s first mass strike for more than 30 years in a growing confrontation with a deficit-cutting coalition government. Reuters
Demonstrators walk on a protest march in central London November 30, 2011. Teachers, nurses and border guards walked out on Wednesday as up to two million state workers staged Britain’s first mass strike for more than 30 years in a growing confrontation with a deficit-cutting coalition government. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict31.jpg) Thousands of Bulgarians gather in front of the Bulgarian parliament to protest against government austerity measures in Sofia, Wednesday, Nov 30, 2011. Thousands joined a mass rally on Wednesday to protest government-proposed austerity measures that include raising the retirement age by one year. (Valentina Petrova)
Thousands of Bulgarians gather in front of the Bulgarian parliament to protest against government austerity measures in Sofia, Wednesday, Nov 30, 2011. Thousands joined a mass rally on Wednesday to protest government-proposed austerity measures that include raising the retirement age by one year. (Valentina Petrova)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict36.jpg) Activists of Ukrainian women movement FEMEN hold placards reading ‘EURO-2012 without prostitution’, ‘UEFA attacked our gates’ and others during a protest in front of the Olimpisky Stadium in Kie, a few hours prior the UEFA EURO-2012 Final Draw ceremony on December 2, 2011. Getty
Activists of Ukrainian women movement FEMEN hold placards reading ‘EURO-2012 without prostitution’, ‘UEFA attacked our gates’ and others during a protest in front of the Olimpisky Stadium in Kie, a few hours prior the UEFA EURO-2012 Final Draw ceremony on December 2, 2011. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict33.jpg) Hundreds of workers on strike block the entrance gate of Hi-P International factory during a protest in a suburban area of Shanghai December 2, 2011. More than 200 workers at a Singapore-owned electronics plant in the commercial hub of Shanghai went on strike for a third day on Friday to protest against planned layoffs, the latest sign of labour unrest in the world’s second-largest economy. Reuters
Hundreds of workers on strike block the entrance gate of Hi-P International factory during a protest in a suburban area of Shanghai December 2, 2011. More than 200 workers at a Singapore-owned electronics plant in the commercial hub of Shanghai went on strike for a third day on Friday to protest against planned layoffs, the latest sign of labour unrest in the world’s second-largest economy. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict28.jpg) A police officer detains a topless woman protesting against alleged attempts to legalize prostitution during the Euro 2012 in Ukraine prior to the final draw for the Euro 2012 soccer tournament in Kiev, Ukraine, Friday, Dec. 2, 2011. Ukrainian women’s rights activists staged a topless demonstration at Kiev’s Olympic Stadium to protest what they say are attempts to legalize prostitution during the 2012 European Championship. (Ferdinand Ostrop)
A police officer detains a topless woman protesting against alleged attempts to legalize prostitution during the Euro 2012 in Ukraine prior to the final draw for the Euro 2012 soccer tournament in Kiev, Ukraine, Friday, Dec. 2, 2011. Ukrainian women’s rights activists staged a topless demonstration at Kiev’s Olympic Stadium to protest what they say are attempts to legalize prostitution during the 2012 European Championship. (Ferdinand Ostrop)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict1.jpg) Survivors of the Bhopal gas tragedy, the world’s worst industrial disaster in India, along with other supporters shout slogans during a protest against a sponsorship deal with Dow Chemicals for the 2012 Olympics, in Bhopal, India, Friday, Dec. 2, 2011. Friday’s protests come on the eve of the 27th anniversary of a lethal gas leak from a Union Carbide pesticide plant in Bhopal where an estimated 15,000 people died and tens of thousands were maimed in 1984.
Survivors of the Bhopal gas tragedy, the world’s worst industrial disaster in India, along with other supporters shout slogans during a protest against a sponsorship deal with Dow Chemicals for the 2012 Olympics, in Bhopal, India, Friday, Dec. 2, 2011. Friday’s protests come on the eve of the 27th anniversary of a lethal gas leak from a Union Carbide pesticide plant in Bhopal where an estimated 15,000 people died and tens of thousands were maimed in 1984.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict39.jpg) Iranian dissidents hold banners as they protest in Brussels, Thursday, Dec. 1, 2011. The protesters called for prevention of compulsory displacement of the Camp Ashraf residents inside Iraq and the annulment of the deadline for closure of Camp Ashraf by the end of December. Camp Ashraf, an enclave in eastern Iraq that houses more than 3,000 people, many of whom are dedicated to overthrowing the government of Iran.
Iranian dissidents hold banners as they protest in Brussels, Thursday, Dec. 1, 2011. The protesters called for prevention of compulsory displacement of the Camp Ashraf residents inside Iraq and the annulment of the deadline for closure of Camp Ashraf by the end of December. Camp Ashraf, an enclave in eastern Iraq that houses more than 3,000 people, many of whom are dedicated to overthrowing the government of Iran.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict38.jpg) Afghan girls hold placards during a demonstration in Kabul December 1, 2011. Hundreds of Afghans from the Solidarity Party of Afghanistan took to the streets of Kabul on Thursday to protest against plans for a long-term partnership deal with the United States. Reuters
Afghan girls hold placards during a demonstration in Kabul December 1, 2011. Hundreds of Afghans from the Solidarity Party of Afghanistan took to the streets of Kabul on Thursday to protest against plans for a long-term partnership deal with the United States. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict34.jpg) A woman disguised as muppet character Miss Piggy takes a mud bath in front of the House of Representatives in The Hague on December 1, 2011 during a protest with Dutch environmental organization Milieudefensie against the expansion of livestock farming. Getty
A woman disguised as muppet character Miss Piggy takes a mud bath in front of the House of Representatives in The Hague on December 1, 2011 during a protest with Dutch environmental organization Milieudefensie against the expansion of livestock farming. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict25.jpg) A protester is detained by police during a march demanding education reform in Santiago, Chile, Thursday, Dec. 1, 2011. Chilean students clashed with police on Thursday during a protest demanding more funding for public education, while students in Colombia and Argentina also took to the streets in simultaneous demonstrations.(Luis Hidalgo)
A protester is detained by police during a march demanding education reform in Santiago, Chile, Thursday, Dec. 1, 2011. Chilean students clashed with police on Thursday during a protest demanding more funding for public education, while students in Colombia and Argentina also took to the streets in simultaneous demonstrations.(Luis Hidalgo)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict27.jpg) Protesters shout anti-austerity slogans during a 24-hour general strike in Athens on Thursday, Dec. 1, 2011. Thousands of protesters bitterly opposed to government austerity measures marched through the Greek capital Thursday, as another general strike closed schools and public services, left hospitals functioning on reduced staff and confined ferries to port. (Petros Giannakouris)
Protesters shout anti-austerity slogans during a 24-hour general strike in Athens on Thursday, Dec. 1, 2011. Thousands of protesters bitterly opposed to government austerity measures marched through the Greek capital Thursday, as another general strike closed schools and public services, left hospitals functioning on reduced staff and confined ferries to port. (Petros Giannakouris)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict29.jpg) An Occupy Raleigh protester shouts during a speech by John Stumpf, the CEO and president of Wells Fargo, on Wednesday, Nov. 30, 2011, in Raleigh, N.C. Stumpf was about 30 minutes into his speech when protesters interrupted him as he talked about the importance of small business. (Chuck Liddy)
An Occupy Raleigh protester shouts during a speech by John Stumpf, the CEO and president of Wells Fargo, on Wednesday, Nov. 30, 2011, in Raleigh, N.C. Stumpf was about 30 minutes into his speech when protesters interrupted him as he talked about the importance of small business. (Chuck Liddy)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict30.jpg) A protester from Portland, Maine, warms her hand with her breath while eating a sandwich at the Occupy Boston encampment, in Boston on Wednesday, Nov. 30, 2011. In the past few weeks police broke up encampments in Portland, Ore., Oakland, Calif., and New York, where the sit-down protests against social inequality and corporate excesses began in mid-September. Protesters remain in place in Boston and Washington, which each had camps of about 100 tents Wednesday. (Steven Senne)
A protester from Portland, Maine, warms her hand with her breath while eating a sandwich at the Occupy Boston encampment, in Boston on Wednesday, Nov. 30, 2011. In the past few weeks police broke up encampments in Portland, Ore., Oakland, Calif., and New York, where the sit-down protests against social inequality and corporate excesses began in mid-September. Protesters remain in place in Boston and Washington, which each had camps of about 100 tents Wednesday. (Steven Senne)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict40.jpg) A woman is led away in handcuffs by police after being removed from Panton House in central London November 30, 2011. Demonstrators broke into an office building used by mining company Xstrata in central London on Wednesday and hung protest banners on the roof before police regained control of the building. A group of about 60 from the “Occupy” movement entered the offices in Haymarket in protest at the pay of the company’s chief executive, Occupy said in a statement. Reuters
A woman is led away in handcuffs by police after being removed from Panton House in central London November 30, 2011. Demonstrators broke into an office building used by mining company Xstrata in central London on Wednesday and hung protest banners on the roof before police regained control of the building. A group of about 60 from the “Occupy” movement entered the offices in Haymarket in protest at the pay of the company’s chief executive, Occupy said in a statement. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict24.jpg) A female protestor displays her hands with Yemen’s flag and writing Arabic that reads,”you will prosecuted,” during a demonstration demanding the prosecution of Yemen’s President Ali Abdullah Saleh in Sanaa, Yemen, Tuesday, Nov. 29, 2011. Hundreds of thousands of Yemenis are demonstrating across the country to demand President Ali Abdullah Saleh face trial for charges ranging from corruption to deadly crackdowns on protests. (Hani Mohammed)
A female protestor displays her hands with Yemen’s flag and writing Arabic that reads,”you will prosecuted,” during a demonstration demanding the prosecution of Yemen’s President Ali Abdullah Saleh in Sanaa, Yemen, Tuesday, Nov. 29, 2011. Hundreds of thousands of Yemenis are demonstrating across the country to demand President Ali Abdullah Saleh face trial for charges ranging from corruption to deadly crackdowns on protests. (Hani Mohammed)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict19.jpg) Supporters of Sri Lanka’s main opposition United National Party (UNP) protest in Colombo on November 29, 2011. They were protesting the jailing of the former army chief Darath Fonseka, a business take over bill and the government’s 2012 budget proposals. Getty
Supporters of Sri Lanka’s main opposition United National Party (UNP) protest in Colombo on November 29, 2011. They were protesting the jailing of the former army chief Darath Fonseka, a business take over bill and the government’s 2012 budget proposals. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict21.jpg) Members of India’s National Domestic Workers Movement from the southern state of Andhra Pradesh (AP) region are watched by co-ordinator Sister Mea Yaragani (2L) as they sign a sheet while participating in a protest meet and signature campaign in Hyderabad on November 29, 2011. The protesors are demanding the ratification of the 189th International Labour Organization (ILO) convention by the Indian government and their inclusion in the Sexual Harassment Bill 2010. There are between 120000-150000 domestic workers in the state. Getty
Members of India’s National Domestic Workers Movement from the southern state of Andhra Pradesh (AP) region are watched by co-ordinator Sister Mea Yaragani (2L) as they sign a sheet while participating in a protest meet and signature campaign in Hyderabad on November 29, 2011. The protesors are demanding the ratification of the 189th International Labour Organization (ILO) convention by the Indian government and their inclusion in the Sexual Harassment Bill 2010. There are between 120000-150000 domestic workers in the state. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict23.jpg) Workers protest as they shout slogans demanding higher wages in front of Indonesia’s presidential palace in Jakarta, November 29, 2011. Indonesia has been hit by a series of strikes in recent months and is expected to see more labour disputes, as workers demanded a greater share of profits in one of Asia’s fastest growing economies. Reuters
Workers protest as they shout slogans demanding higher wages in front of Indonesia’s presidential palace in Jakarta, November 29, 2011. Indonesia has been hit by a series of strikes in recent months and is expected to see more labour disputes, as workers demanded a greater share of profits in one of Asia’s fastest growing economies. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict20.jpg) Miss Water South Africa Kirsten Dukes poses in front of a banner during a protest by environmental activists outside the United Nations Framework Convention on Climate Change Conference of the Parties meeting (COP17) in Durban, November 29, 2011. The gathering runs until December 9. Reuters
Miss Water South Africa Kirsten Dukes poses in front of a banner during a protest by environmental activists outside the United Nations Framework Convention on Climate Change Conference of the Parties meeting (COP17) in Durban, November 29, 2011. The gathering runs until December 9. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict18.jpg) Student, wearing niqabs, protest on November 29, 2011 in the building housing the office of the dean of the Faculty of Arts at the University of Manuba, 25 kms west of Tunis. Several hundred people gathered at the university to demand the right for female students to wear full face veils in class and pass exams. A group of Salafists disrupted classes on November 28 at the university, demanding a stop to mixed-sex classes and for female students to wear full face veils. Getty
Student, wearing niqabs, protest on November 29, 2011 in the building housing the office of the dean of the Faculty of Arts at the University of Manuba, 25 kms west of Tunis. Several hundred people gathered at the university to demand the right for female students to wear full face veils in class and pass exams. A group of Salafists disrupted classes on November 28 at the university, demanding a stop to mixed-sex classes and for female students to wear full face veils. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict17.jpg) Workers take part in a rally during a protest against government austerity measures organized by the PAME Communist-affiliated union in central Athens Tuesday, Nov. 29, 2011. The 17 finance ministers of the countries that use the euro converged on EU headquarters Tuesday in a desperate bid to save their currency – and to protect Europe, the United States, Asia and the rest of the global economy from a debt-induced financial tsunami. AP
Workers take part in a rally during a protest against government austerity measures organized by the PAME Communist-affiliated union in central Athens Tuesday, Nov. 29, 2011. The 17 finance ministers of the countries that use the euro converged on EU headquarters Tuesday in a desperate bid to save their currency – and to protect Europe, the United States, Asia and the rest of the global economy from a debt-induced financial tsunami. AP![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict16.jpg) Supporters of Pakistan Tehreek-i-Insaf (Pakistan’s Movement for Justice) pray after a demonstration against NATO cross-border attack in Lahore November 29, 2011. Pakistan’s government confirmed it would not attend an international conference on the future of Afghanistan in Bonn next week to protest against a NATO cross-border attack that killed two dozen Pakistani soldiers. Reuters
Supporters of Pakistan Tehreek-i-Insaf (Pakistan’s Movement for Justice) pray after a demonstration against NATO cross-border attack in Lahore November 29, 2011. Pakistan’s government confirmed it would not attend an international conference on the future of Afghanistan in Bonn next week to protest against a NATO cross-border attack that killed two dozen Pakistani soldiers. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict15.jpg) Riot police detain two students inside the national congress during a protest against the government to demand changes in the public state education system in Valparaiso city, about 121 km (75 miles) northwest of Santiago, November 29, 2011. Chilean students have been protesting against what they say is the profiteering in the state education system. Reuters
Riot police detain two students inside the national congress during a protest against the government to demand changes in the public state education system in Valparaiso city, about 121 km (75 miles) northwest of Santiago, November 29, 2011. Chilean students have been protesting against what they say is the profiteering in the state education system. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict2.jpg) Pakistani protesters rally to condemn NATO strikes on Pakistani soldiers, in Lahore, Pakistan, Tuesday, Nov. 29, 2011. Pakistan pulled out of an upcoming meeting in Germany on the future of Afghanistan to protest the deadly attack by U.S.-led forces on its troops, widening the fallout on Tuesday from an incident that has sent ties between Washington and Islamabad into a tailspin. Placard at right reads “run NATO and wake Pakistan army”. (K.M. Chaudary)
Pakistani protesters rally to condemn NATO strikes on Pakistani soldiers, in Lahore, Pakistan, Tuesday, Nov. 29, 2011. Pakistan pulled out of an upcoming meeting in Germany on the future of Afghanistan to protest the deadly attack by U.S.-led forces on its troops, widening the fallout on Tuesday from an incident that has sent ties between Washington and Islamabad into a tailspin. Placard at right reads “run NATO and wake Pakistan army”. (K.M. Chaudary)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict3.jpg) A demonstrator holds a sign that reads in Portuguese: “The fight on the forest starts in the streets”, during a protest against the approval of the new Brazilian forest code in Brasilia, Brazil, Tuesday, Nov. 29, 2011. Brazil’s lower house in May approved changes to the law that would ease environmental restrictions in the Amazon and other regions in Brazil. Brazil’s Senate is expected to approve the measure this week, though President Dilma Rousseff has promised to veto some parts of the bill.
A demonstrator holds a sign that reads in Portuguese: “The fight on the forest starts in the streets”, during a protest against the approval of the new Brazilian forest code in Brasilia, Brazil, Tuesday, Nov. 29, 2011. Brazil’s lower house in May approved changes to the law that would ease environmental restrictions in the Amazon and other regions in Brazil. Brazil’s Senate is expected to approve the measure this week, though President Dilma Rousseff has promised to veto some parts of the bill.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict4.jpg) Female Iranian protesters attend a demonstration in front of the British Embassy, as one of them holds a poster of supreme leader Ayatollah Ali Khamenei, in Tehran, Iran, Tuesday, Nov. 29, 2011. Dozens of hard-line Iranian students stormed the British Embassy in Tehran on Tuesday, bringing down the Union Jack flag and throwing documents from windows in scenes reminiscent of the anger against Western powers after the 1979 Islamic Revolution.
Female Iranian protesters attend a demonstration in front of the British Embassy, as one of them holds a poster of supreme leader Ayatollah Ali Khamenei, in Tehran, Iran, Tuesday, Nov. 29, 2011. Dozens of hard-line Iranian students stormed the British Embassy in Tehran on Tuesday, bringing down the Union Jack flag and throwing documents from windows in scenes reminiscent of the anger against Western powers after the 1979 Islamic Revolution.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict5.jpg) An elderly protestor flashes the victory sign during a demonstration demanding the prosecution of Yemen’s President Ali Abdullah Saleh in Sanaa, Yemen, Tuesday, Nov. 29, 2011. Hundreds of thousands of Yemenis are demonstrating across the country to demand President Ali Abdullah Saleh face trial for charges ranging from corruption to deadly crackdowns on protests. (Hani Mohammed)
An elderly protestor flashes the victory sign during a demonstration demanding the prosecution of Yemen’s President Ali Abdullah Saleh in Sanaa, Yemen, Tuesday, Nov. 29, 2011. Hundreds of thousands of Yemenis are demonstrating across the country to demand President Ali Abdullah Saleh face trial for charges ranging from corruption to deadly crackdowns on protests. (Hani Mohammed)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict6.jpg) Mariachi musicians perform as Greenpeace activists demand Brazil’s President Dilma Rousseff protect the Amazon as they protest outside Brazil’s embassy in Mexico City, Tuesday Nov. 29, 2011. Brazil’s government has authorized the construction of one the world’s largest hydroelectric dams, the Belo Monte dam, in the state of Para, and the federal prosecutors’ office in Para has said they will go to the Supreme Court to appeal the ruling.
Mariachi musicians perform as Greenpeace activists demand Brazil’s President Dilma Rousseff protect the Amazon as they protest outside Brazil’s embassy in Mexico City, Tuesday Nov. 29, 2011. Brazil’s government has authorized the construction of one the world’s largest hydroelectric dams, the Belo Monte dam, in the state of Para, and the federal prosecutors’ office in Para has said they will go to the Supreme Court to appeal the ruling.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict7.jpg) Malaysian lawyers hold placards as they shout slogans during a protest in Kuala Lumpur, Malaysia, Tuesday, Nov. 29, 2011. Hundreds of Malaysian lawyers staged a rare protest march Tuesday demanding that the government abandon plans for a law that will forbid street rallies. (Lai Seng Sin)
Malaysian lawyers hold placards as they shout slogans during a protest in Kuala Lumpur, Malaysia, Tuesday, Nov. 29, 2011. Hundreds of Malaysian lawyers staged a rare protest march Tuesday demanding that the government abandon plans for a law that will forbid street rallies. (Lai Seng Sin)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict9.jpg) Protesters shout slogans as they hold candles with placards reading “Invalidity, FTA between South Korea and the U.S.” during a candle rally, denouncing the passing of a bill on ratification of a South Korea-U.S. free trade agreement in Seoul, South Korea, Tuesday, Nov. 29, 2011. South Korea’s president on Tuesday signed a slew of laws needed to implement the country’s free trade deal with the United States, amid growing protests denouncing the accord at home. (Lee Jin-man)
Protesters shout slogans as they hold candles with placards reading “Invalidity, FTA between South Korea and the U.S.” during a candle rally, denouncing the passing of a bill on ratification of a South Korea-U.S. free trade agreement in Seoul, South Korea, Tuesday, Nov. 29, 2011. South Korea’s president on Tuesday signed a slew of laws needed to implement the country’s free trade deal with the United States, amid growing protests denouncing the accord at home. (Lee Jin-man)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict10.jpg) UCLA students walk past a line of demonstrators lying on the Quad outside a meeting of the Board of Regents at the University of California, on the campus at UCLA in Los Angeles, Monday, Nov. 28, 2011. The regents were originally scheduled to meet in mid-November at the San Francisco-Mission Bay campus, but the session was scrapped when law enforcement warned that protests could turn violent. (Reed Saxon)
UCLA students walk past a line of demonstrators lying on the Quad outside a meeting of the Board of Regents at the University of California, on the campus at UCLA in Los Angeles, Monday, Nov. 28, 2011. The regents were originally scheduled to meet in mid-November at the San Francisco-Mission Bay campus, but the session was scrapped when law enforcement warned that protests could turn violent. (Reed Saxon)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict14.jpg) Supporters of Progressive Organization of Women raise slogans during a protest rally in New Delhi, India, Monday, Nov. 28, 2011. The protesters demanded introduction of a bill in the ongoing session of parliament for a separate statehood of Telangana region from the existing Andhra Pradesh state in southern India. (Gurinder Osan)
Supporters of Progressive Organization of Women raise slogans during a protest rally in New Delhi, India, Monday, Nov. 28, 2011. The protesters demanded introduction of a bill in the ongoing session of parliament for a separate statehood of Telangana region from the existing Andhra Pradesh state in southern India. (Gurinder Osan)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict12.jpg) Police officers stand during a demonstration by security forces in Tunis, Monday, Nov.28, 2011. Security forces are protesting against police officers sued on trial for their alleged role in the revolution. On armband reads: “Stop, break the silence”. (Hassene Dridi)
Police officers stand during a demonstration by security forces in Tunis, Monday, Nov.28, 2011. Security forces are protesting against police officers sued on trial for their alleged role in the revolution. On armband reads: “Stop, break the silence”. (Hassene Dridi)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict11.jpg) Members of Occupy Philly, from right to left, Shawn Grant, Brianne Murphy, and Diane Isser, demonstrate at Dilworth Plaza, in Philadelphia, on Sunday Nov. 27, 2011, in defiance of the city’s 5 p.m. eviction order. (Joseph Kaczmarek)
Members of Occupy Philly, from right to left, Shawn Grant, Brianne Murphy, and Diane Isser, demonstrate at Dilworth Plaza, in Philadelphia, on Sunday Nov. 27, 2011, in defiance of the city’s 5 p.m. eviction order. (Joseph Kaczmarek)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest8/pict13.jpg) A member of Occupy Philly who identified herself as Laura watches the demonstration at Dilworth Plaza, in Philadelphia, Sunday Nov. 27, 2011, held in defiance of the city’s 5 p.m. eviction order. (Joseph Kaczmarek)
A member of Occupy Philly who identified herself as Laura watches the demonstration at Dilworth Plaza, in Philadelphia, Sunday Nov. 27, 2011, held in defiance of the city’s 5 p.m. eviction order. (Joseph Kaczmarek)

![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict80.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict69.jpg) Russian nationalists hold a banner reads as “All for one and one for all” and wave old Russian imperial flags during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)
Russian nationalists hold a banner reads as “All for one and one for all” and wave old Russian imperial flags during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict70.jpg) Russian nationalists rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)
Russian nationalists rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict68.jpg) Russian nationalists shout holding old Russian imperial flags during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)
Russian nationalists shout holding old Russian imperial flags during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011.Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict78.jpg) A young masked Russian nationalist holds a banner in front of a police officer during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)
A young masked Russian nationalist holds a banner in front of a police officer during their rally at Bolotnaya Square, on an island in the Moscow River adjacent to the Kremlin in Moscow, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Alexander Zemlianichenko)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict76.jpg) Russian police troops patrol near closed Red Square, with St. Basil Cathedral at the background, in Moscow, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Misha Japaridze)
Russian police troops patrol near closed Red Square, with St. Basil Cathedral at the background, in Moscow, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in downtown Moscow, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Misha Japaridze)
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict77.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict64.jpg) In this photo taken Saturday, Dec. 10, 2011, protesters gather to protest near the Kremlin, background, against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia. Tens of thousands of people held the largest anti-government protests that post-Soviet Russia has ever seen to criticize electoral fraud and demand an end to Vladimir Putin’s rule. (Dmitriy Chistoprudov)
In this photo taken Saturday, Dec. 10, 2011, protesters gather to protest near the Kremlin, background, against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia. Tens of thousands of people held the largest anti-government protests that post-Soviet Russia has ever seen to criticize electoral fraud and demand an end to Vladimir Putin’s rule. (Dmitriy Chistoprudov)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict65.jpg) In this photo taken Saturday, Dec. 10, 2011, protesters gather to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia. Tens of thousands of people held the largest anti-government protests that post-Soviet Russia has ever seen to criticize electoral fraud and demand an end to Vladimir Putin’s rule. (Dmitriy Chistoprudov)
In this photo taken Saturday, Dec. 10, 2011, protesters gather to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia. Tens of thousands of people held the largest anti-government protests that post-Soviet Russia has ever seen to criticize electoral fraud and demand an end to Vladimir Putin’s rule. (Dmitriy Chistoprudov)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict38.jpg) Police cars and trucks block a square where demonstrators gather together during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.
Police cars and trucks block a square where demonstrators gather together during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict27.jpg) Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin)
Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict26.jpg) Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr)
Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict45.jpg) Protesters hold a red banner reads as “Rot Front” shouting anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011, with the Kremlin is the background. Russians angered by allegedly fraudulent parliamentary elections and the country’s ruling party took part in protests Saturday in cities from the freezing Pacific Coast to the southwest, eight time zones away.
Protesters hold a red banner reads as “Rot Front” shouting anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011, with the Kremlin is the background. Russians angered by allegedly fraudulent parliamentary elections and the country’s ruling party took part in protests Saturday in cities from the freezing Pacific Coast to the southwest, eight time zones away.![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict44.jpg) A protester holds an old Russian flag with the words “We are Russians, God with us” and shows a V-sing during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011, with the Kremlin is the background. Russians angered by allegedly fraudulent parliamentary elections and the country’s ruling party took part in protests Saturday in cities from the freezing Pacific Coast to the southwest, eight time zones away.
A protester holds an old Russian flag with the words “We are Russians, God with us” and shows a V-sing during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011, with the Kremlin is the background. Russians angered by allegedly fraudulent parliamentary elections and the country’s ruling party took part in protests Saturday in cities from the freezing Pacific Coast to the southwest, eight time zones away.![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict24.jpg) Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr)
Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict40.jpg) People stand on the bridge as they attend a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. The banner on the bridge reads: “Crooks Give Us the Election Back.”
People stand on the bridge as they attend a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. The banner on the bridge reads: “Crooks Give Us the Election Back.”![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict29.jpg) Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko)
Protesters gather together to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict25.jpg) Protesters shout anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr)
Protesters shout anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Alexander Zemlianichenko Jr)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict41.jpg) Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)
Demonstrators shout during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict34.jpg) Protesters light flares during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin)
Protesters light flares during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict48.jpg) Demonstrators stand in front of police line during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)
Demonstrators stand in front of police line during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict43.jpg) Opposition leader Edouard Limonov shouts anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.
Opposition leader Edouard Limonov shouts anti-Putin slogans during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict50.jpg) An elderly demonstrator holds a poster showing an edited photo of Prime Minister Vladimir Putin and signed “2050. No” during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.
An elderly demonstrator holds a poster showing an edited photo of Prime Minister Vladimir Putin and signed “2050. No” during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict47.jpg) Protesters listen to an orator during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.(Alexander Zemlianichenko Jr)
Protesters listen to an orator during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.(Alexander Zemlianichenko Jr)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict36.jpg) Protesters seen during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Sergey Ponomarev)
Protesters seen during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Sergey Ponomarev)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict35.jpg) Masked protesters seen during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin)
Masked protesters seen during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Pavel Golovkin)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict32.jpg) A protester shouts slogans in front of police line during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)
A protester shouts slogans in front of police line during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Mikhail Metzel)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict37.jpg) Protesters light flares holding an Old Russian flags during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Name)
Protesters light flares holding an Old Russian flags during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Name)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict39.jpg) Police guards the Red Square area during a mass protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Sergey Ponomarev)
Police guards the Red Square area during a mass protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power. (Sergey Ponomarev)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict28.jpg) Police vehicles seen on a Zamoskvoretsky bridge during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.(Ivan Sekret)
Police vehicles seen on a Zamoskvoretsky bridge during a mass rally to protest against alleged vote rigging in Russia’s parliamentary elections in Moscow, Russia, Saturday, Dec. 10, 2011. Many thousands of Russians angered by allegedly fraudulent parliamentary elections are protesting Saturday in cities from the freezing Pacific Coast to the southwest of Russia, eight time zones away, a striking show of indignation, challenging Prime Minister Vladimir Putin’s hold on power.(Ivan Sekret)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict75.jpg) Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. The poster reads: “One for all and all for one”. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky)
Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. The poster reads: “One for all and all for one”. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict72.jpg) Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky)
Russian nationalists shout holding old Russian imperial flags during their rally in St.Petersburg, Russia, Sunday, Dec. 11, 2011. Russian nationalists are rallying in Moscow and St.Petersburg, demanding a bigger say for ethnic Russians in the country’s politics and marking the first anniversary of a violent nationalist riot just outside the Kremlin.(Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict23.jpg) In this photo taken with a fisheye lens protesters gather during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
In this photo taken with a fisheye lens protesters gather during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict42.jpg) Protesters shout slogans during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
Protesters shout slogans during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict46.jpg) A protester walks in smoke of a smoke bomb during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign [not shown] reads “Such election is a spit at people’s face”. More than 10,000 people have protested in St. Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers say was rigged. (Dmitry Lovetsky)
A protester walks in smoke of a smoke bomb during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign [not shown] reads “Such election is a spit at people’s face”. More than 10,000 people have protested in St. Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers say was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict49.jpg) A protester holds a badminton racket as he shouts slogans during a rally in St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than 10,000 people are protesting in St. Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers say was rigged. (Dmitry Lovetsky)
A protester holds a badminton racket as he shouts slogans during a rally in St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than 10,000 people are protesting in St. Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers say was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict30.jpg) An opposition activist fights with a police officer during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousand people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
An opposition activist fights with a police officer during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousand people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict31.jpg) Riot police detain a protester during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
Riot police detain a protester during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)![[Image]](https://i0.wp.com/cryptome.org/info/russia-protest/pict33.jpg) Protesters seen during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)
Protesters seen during a rally in downtown St.Petersburg, Russia, Saturday, Dec. 10, 2011. The sign reads “No vote”. More than ten thousands people have protested in St.Petersburg against Prime Minister Vladimir Putin and his party, which won the largest share of a parliamentary election that observers said was rigged. (Dmitry Lovetsky)














 U.S. Espionage and Intelligence: Organization, Operations, and Management, 1947-1996 publishes together for the first time recent unclassified and newly declassified documents pertaining to the organizational structure, operations, and management of the U.S. intelligence community over the last fifty years, cross-indexed for maximum accessibility. This set reproduces on microfiche 1,174 organizational histories, memoranda, manuals, regulations, directives, reports, and studies, representing over 36,102 pages of documents from the Office of the Director of Central Intelligence, the Central Intelligence Agency, National Reconnaissance Office, National Security Agency, Defense Intelligence Agency, military service intelligence organizations, National Security Council and other organizations. U.S. Espionage and Intelligence presents a unique look into the internal workings of America’s intelligence community. The documents gathered here shed further light on U.S. intelligence organization and activities during the Cold War, and describe the consolidation and reevaluation of the intelligence community in the post-Cold War era. They are drawn from diverse sources, including the National Archives, manuscript collections in the Library of Congress, court files of major espionage prosecutions, presidential libraries, and most importantly, Freedom of Information Act requests. The result of this effort is an authoritative documents publication which, together with the National Security Archive’s previous collection on the structure and operations of the U.S. intelligence community,
U.S. Espionage and Intelligence: Organization, Operations, and Management, 1947-1996 publishes together for the first time recent unclassified and newly declassified documents pertaining to the organizational structure, operations, and management of the U.S. intelligence community over the last fifty years, cross-indexed for maximum accessibility. This set reproduces on microfiche 1,174 organizational histories, memoranda, manuals, regulations, directives, reports, and studies, representing over 36,102 pages of documents from the Office of the Director of Central Intelligence, the Central Intelligence Agency, National Reconnaissance Office, National Security Agency, Defense Intelligence Agency, military service intelligence organizations, National Security Council and other organizations. U.S. Espionage and Intelligence presents a unique look into the internal workings of America’s intelligence community. The documents gathered here shed further light on U.S. intelligence organization and activities during the Cold War, and describe the consolidation and reevaluation of the intelligence community in the post-Cold War era. They are drawn from diverse sources, including the National Archives, manuscript collections in the Library of Congress, court files of major espionage prosecutions, presidential libraries, and most importantly, Freedom of Information Act requests. The result of this effort is an authoritative documents publication which, together with the National Security Archive’s previous collection on the structure and operations of the U.S. intelligence community,


















![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict5.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict7.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/cia-bucharest/pict8.jpg)

![[Image]](https://i0.wp.com/cryptome.org/isp-spy/ga-tech-spy/pict2.jpg)
![[Image]](https://i0.wp.com/cryptome.org/isp-spy/ga-tech-spy/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/isp-spy/ga-tech-spy/pict1.jpg)










































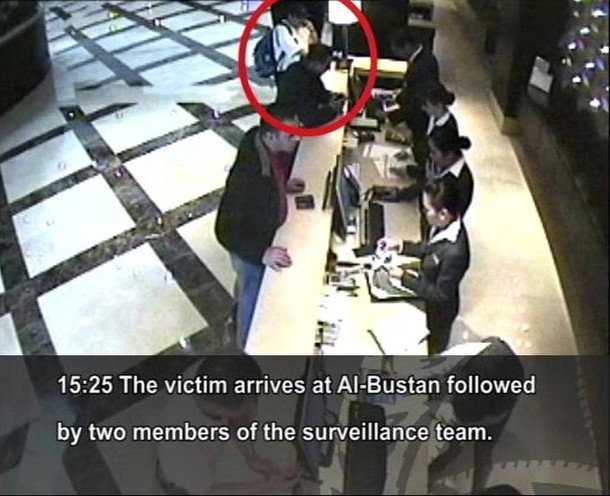































































![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict36.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict15.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict27.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict16.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict29.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict13.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict14.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict11.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict17.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict20.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict21.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict23.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict25.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict24.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict26.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict28.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict30.jpg) These gents appear leery of being photographed, and rightly so, due to persistent infiltration and photography by cops. Or could be undercover cops.
These gents appear leery of being photographed, and rightly so, due to persistent infiltration and photography by cops. Or could be undercover cops.
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict10.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict31.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict32.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict33.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-20/pict34.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict18.jpg) Supporters of Bharatiya Mazdoor Sangh, or Indian Workers Group, raise slogans at a protest rally in New Delhi, India, Wednesday, Nov. 23, 2011. The supporters demanded that the government protect workers rights in the ongoing economic reform process as well as the financial crisis. (Gurinder Osan)
Supporters of Bharatiya Mazdoor Sangh, or Indian Workers Group, raise slogans at a protest rally in New Delhi, India, Wednesday, Nov. 23, 2011. The supporters demanded that the government protect workers rights in the ongoing economic reform process as well as the financial crisis. (Gurinder Osan)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict26.jpg) Yemenis protest against President Ali Abdullah Saleh during a rally after the weekly Friday noon prayers in Sanaa on November 25, 2011. Opponents and supporters of Yemen’s embattled president held rival rallies in the capital after pre-dawn fighting between rival security forces dashed hopes an exit deal for the president would end the violence. Getty
Yemenis protest against President Ali Abdullah Saleh during a rally after the weekly Friday noon prayers in Sanaa on November 25, 2011. Opponents and supporters of Yemen’s embattled president held rival rallies in the capital after pre-dawn fighting between rival security forces dashed hopes an exit deal for the president would end the violence. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict27.jpg) Women perform prayers at the Taghyeer (Change) Square, where anti-government protesters have been camping for around ten months to call for the ouster and trial of Yemen’s President Ali Abdullah Saleh, in Sanaa November 27, 2011. Reuters
Women perform prayers at the Taghyeer (Change) Square, where anti-government protesters have been camping for around ten months to call for the ouster and trial of Yemen’s President Ali Abdullah Saleh, in Sanaa November 27, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict28.jpg) Yemeni women and anti-government protesters shout slogans during a demonstration demanding the trial of Yemeni President Ali Abdullah Saleh in Sanaa on November 26, 2011. Getty
Yemeni women and anti-government protesters shout slogans during a demonstration demanding the trial of Yemeni President Ali Abdullah Saleh in Sanaa on November 26, 2011. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict3.jpg) Demonstrators gather during protests against a nuclear waste transport in Dannenberg, northern Germany, Saturday Nov. 26, 2011. The shipment of nuclear waste reprocessed in France is on its way to a controversial storage site in Gorleben that protesters say is unsafe. It is the first such shipment from France to Germany since Berlin decided to shut all its nuclear plants by 2022, following the disaster at Japan’s Fukushima plant. The transport is due to arrive at the storage site on Sunday.
Demonstrators gather during protests against a nuclear waste transport in Dannenberg, northern Germany, Saturday Nov. 26, 2011. The shipment of nuclear waste reprocessed in France is on its way to a controversial storage site in Gorleben that protesters say is unsafe. It is the first such shipment from France to Germany since Berlin decided to shut all its nuclear plants by 2022, following the disaster at Japan’s Fukushima plant. The transport is due to arrive at the storage site on Sunday.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict31.jpg) A demonstrator dressed as a clown stands between police officers during protests against a shipment of nuclear waste to the storage facility in Gorleben, in Hitzacker, northern Germany Sunday Nov. 27, 2011. (Axel Heimken)
A demonstrator dressed as a clown stands between police officers during protests against a shipment of nuclear waste to the storage facility in Gorleben, in Hitzacker, northern Germany Sunday Nov. 27, 2011. (Axel Heimken)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict29.jpg) People demonstrate during a protest against violence in Mexico City, Sunday, Nov. 27, 2011. Demonstrators wore skull masks or painted their faces as skulls to symbolize the victims of violence in Mexico. Over 50,000 people have died since Mexican President Felipe Calderon launched his offensive against organized crime in 2006. (Marco Ugarte)
People demonstrate during a protest against violence in Mexico City, Sunday, Nov. 27, 2011. Demonstrators wore skull masks or painted their faces as skulls to symbolize the victims of violence in Mexico. Over 50,000 people have died since Mexican President Felipe Calderon launched his offensive against organized crime in 2006. (Marco Ugarte)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict21.jpg) Libyan Amazigh Berbers protest outside the prime minister’s office in Tripoli on November 27, 2011 as they step up pressure for the minority group to to be represented in the government. Getty
Libyan Amazigh Berbers protest outside the prime minister’s office in Tripoli on November 27, 2011 as they step up pressure for the minority group to to be represented in the government. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict1.jpg) Environment activists Hanna Schwarz, right, and Heiko Mueller-Ripke, have chained themselves inside a pyramid with concrete inside, they claim, on the tracks near Hitzacker, Sunday Nov. 27, 2011. Police has difficulties for hours, to unchain the protesters without injuring them. The activists protest against a nuclear waste transport from France to a storage in Gorleben. (Axel Heimken)
Environment activists Hanna Schwarz, right, and Heiko Mueller-Ripke, have chained themselves inside a pyramid with concrete inside, they claim, on the tracks near Hitzacker, Sunday Nov. 27, 2011. Police has difficulties for hours, to unchain the protesters without injuring them. The activists protest against a nuclear waste transport from France to a storage in Gorleben. (Axel Heimken)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict23.jpg) Members of the Ethiopian community block the entrance to Israel’s Ministry of Immigrant Absorption during a protest in Jerusalem November 27, 2011. About 400 Israelis of Ethiopian descent took part in the protest on Sunday calling on the government to grant permission for their relatives living in Ethiopia to immigrate. Reuters
Members of the Ethiopian community block the entrance to Israel’s Ministry of Immigrant Absorption during a protest in Jerusalem November 27, 2011. About 400 Israelis of Ethiopian descent took part in the protest on Sunday calling on the government to grant permission for their relatives living in Ethiopia to immigrate. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict32.jpg) Demonstrators drum on barrels with a nuclear sign, during protests against a nuclear waste transport in Dannenberg, northern Germany, Saturday, Nov. 26, 2011. The shipment of nuclear waste reprocessed in France is on its way to a controversial storage site in Gorleben that protesters say is unsafe. It is the first such shipment from France to Germany since Berlin decided to shut all its nuclear plants by 2022, following the disaster at Japan’s Fukushima plant.
Demonstrators drum on barrels with a nuclear sign, during protests against a nuclear waste transport in Dannenberg, northern Germany, Saturday, Nov. 26, 2011. The shipment of nuclear waste reprocessed in France is on its way to a controversial storage site in Gorleben that protesters say is unsafe. It is the first such shipment from France to Germany since Berlin decided to shut all its nuclear plants by 2022, following the disaster at Japan’s Fukushima plant.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict22.jpg) Oxfam (a confederation of 15 organizations working together to find lasting solutions to poverty and injustice) activists make a protest aimed at 17th Conference of the Parties (COP17) under the UN Framework Convention on Climate Change (UNFCCC) in Durban on November 27, 2011. Inspired by the Occupy Wall St. movement, protesters calling for ‘climate justice’ are set to gather on November 28 at the opening of UN climate talks in Durban, South Africa, organisers say. Getty
Oxfam (a confederation of 15 organizations working together to find lasting solutions to poverty and injustice) activists make a protest aimed at 17th Conference of the Parties (COP17) under the UN Framework Convention on Climate Change (UNFCCC) in Durban on November 27, 2011. Inspired by the Occupy Wall St. movement, protesters calling for ‘climate justice’ are set to gather on November 28 at the opening of UN climate talks in Durban, South Africa, organisers say. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict2.jpg) In tihis picture taken Saturday Nov. 26, 2011 police carries an environment activist away from the tracks near Harlingen, northern Germany. German police say they cleared a sit-in of about 3,500 protesters attempting to block a shipment of nuclear waste with security forces temporarily detaining 1,300 of them. (Philipp Guelland)
In tihis picture taken Saturday Nov. 26, 2011 police carries an environment activist away from the tracks near Harlingen, northern Germany. German police say they cleared a sit-in of about 3,500 protesters attempting to block a shipment of nuclear waste with security forces temporarily detaining 1,300 of them. (Philipp Guelland)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict0.jpg) South Korean police say nearly 40 officers were injured during a rally opposing the ratification of the country’s free trade deal with the United States.Hundreds of protesters have been staging near-daily demonstrations since the ruling party railroaded the U.S. trade deal last week. The protesters believe the deal favors Washington over South Korean workers. About 2,200 people rallied in Seoul on Saturday evening, November 26, 2011.
South Korean police say nearly 40 officers were injured during a rally opposing the ratification of the country’s free trade deal with the United States.Hundreds of protesters have been staging near-daily demonstrations since the ruling party railroaded the U.S. trade deal last week. The protesters believe the deal favors Washington over South Korean workers. About 2,200 people rallied in Seoul on Saturday evening, November 26, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict24.jpg) Sarah Elbaroudy, age seven, from Long Island, stands during a collaborative protest between the Occupy Wall Street movement and people supporting the 2011 Egyptian Revolution and the current social unrest throughout Egypt, near the Egyptian Embassy to the United States, at the intersection of East 44th Street and Second Avenue, in New York, November 26, 2011. Reuters
Sarah Elbaroudy, age seven, from Long Island, stands during a collaborative protest between the Occupy Wall Street movement and people supporting the 2011 Egyptian Revolution and the current social unrest throughout Egypt, near the Egyptian Embassy to the United States, at the intersection of East 44th Street and Second Avenue, in New York, November 26, 2011. Reuters![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict25.jpg) A woman dressed as the Grim Reaper attends a protest against shale gas exploration and production in Sofia on November 26, 2011. Bulgaria gave in July a licence to the United States energy major Chevron for the exploration of an area in the north-eastern part of Bulgaria. Getty
A woman dressed as the Grim Reaper attends a protest against shale gas exploration and production in Sofia on November 26, 2011. Bulgaria gave in July a licence to the United States energy major Chevron for the exploration of an area in the north-eastern part of Bulgaria. Getty![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict4.jpg) A young Romanian woman wearing make up to suggest she is a victim of domestic violence takes part in a protest in Bucharest, Romania, Friday, Nov. 25, 2011. Dozens of women gathered in protest on the International Day for the Elimination of Violence against Women demanding the introduction of the restraining order in Romanian legislation. Romania is a European Union member state but has no proper legal framework to combat domestic violence against women.
A young Romanian woman wearing make up to suggest she is a victim of domestic violence takes part in a protest in Bucharest, Romania, Friday, Nov. 25, 2011. Dozens of women gathered in protest on the International Day for the Elimination of Violence against Women demanding the introduction of the restraining order in Romanian legislation. Romania is a European Union member state but has no proper legal framework to combat domestic violence against women.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict5.jpg) Israelis covered in red color demonstrates as part of the International Anti-fur Coalition protest in Tel Aviv. Friday. Nov. 25, 2011. The demonstration was part of an international protest against fur trade.(Dan Balilty)
Israelis covered in red color demonstrates as part of the International Anti-fur Coalition protest in Tel Aviv. Friday. Nov. 25, 2011. The demonstration was part of an international protest against fur trade.(Dan Balilty)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict7.jpg) An Egyptian girl holds an anti-Israel banner during a protest at al Azhar mosque, the highest Islamic Sunni institution, after Friday prayers in Cairo, Egypt, Friday, Nov. 25, 2011. The Muslim brotherhood demonstration was to denounce Israeli control over Jerusalem’s Al Aqsa Mosque, one of the holiest sites in Islam. Arabic and Hebrew reads ” Death for Israel”. (Amr Nabil)
An Egyptian girl holds an anti-Israel banner during a protest at al Azhar mosque, the highest Islamic Sunni institution, after Friday prayers in Cairo, Egypt, Friday, Nov. 25, 2011. The Muslim brotherhood demonstration was to denounce Israeli control over Jerusalem’s Al Aqsa Mosque, one of the holiest sites in Islam. Arabic and Hebrew reads ” Death for Israel”. (Amr Nabil)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict6.jpg) An Egyptian woman holds up an infant during a rally in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011. Tens of thousands of protesters chanting, “Leave, leave!” filled Cairo’s Tahrir Square in a massive demonstration to force Egypt’s ruling military council to yield power. The Friday rally is dubbed by organizers as “The Last Chance Million-Man Protest,” and comes one day after the military offered an apology for the killing of nearly 40 protesters in clashes on side streets near Tahrir Square.
An Egyptian woman holds up an infant during a rally in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011. Tens of thousands of protesters chanting, “Leave, leave!” filled Cairo’s Tahrir Square in a massive demonstration to force Egypt’s ruling military council to yield power. The Friday rally is dubbed by organizers as “The Last Chance Million-Man Protest,” and comes one day after the military offered an apology for the killing of nearly 40 protesters in clashes on side streets near Tahrir Square.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict8.jpg) Filipino women activists stage a play to symbolize human rights violations during a demonstration to mark the International Day of Action on Violence Against Women near the Malacanang presidential palace in Manila, Philippines, Friday Nov. 25, 2011. The women’s group held the rally to raise public awareness and encourage continuing action to eliminate violence against women. (Aaron Favila)
Filipino women activists stage a play to symbolize human rights violations during a demonstration to mark the International Day of Action on Violence Against Women near the Malacanang presidential palace in Manila, Philippines, Friday Nov. 25, 2011. The women’s group held the rally to raise public awareness and encourage continuing action to eliminate violence against women. (Aaron Favila)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict9.jpg) Students march demanding an education reform in Bogota, Colombia, Thursday, Nov. 24, 2011. Protesters are demanding more funding and other changes to the public education system.(Fernando Vergara)
Students march demanding an education reform in Bogota, Colombia, Thursday, Nov. 24, 2011. Protesters are demanding more funding and other changes to the public education system.(Fernando Vergara)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict10.jpg) Protesters are hit with water from a police water canon during a march for education reform in Santiago, Chile, Thursday Nov. 24, 2011. Protesters have demanded more funding and other changes to the public education system. The annual budget is due to be approved by Nov. 30. (Luis Hidalgo)
Protesters are hit with water from a police water canon during a march for education reform in Santiago, Chile, Thursday Nov. 24, 2011. Protesters have demanded more funding and other changes to the public education system. The annual budget is due to be approved by Nov. 30. (Luis Hidalgo)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict12.jpg) Pro-Syrian regime protesters shout pro-Syrian President Bashar Assad slogans during a protest against the Arab League meeting, in Damascus, Syria, Thursday Nov. 24, 2011. An Arab League committee has given Syria 24 hours to agree to allow an observer mission into the country or it could face sanctions. (Bassem Tellawi)
Pro-Syrian regime protesters shout pro-Syrian President Bashar Assad slogans during a protest against the Arab League meeting, in Damascus, Syria, Thursday Nov. 24, 2011. An Arab League committee has given Syria 24 hours to agree to allow an observer mission into the country or it could face sanctions. (Bassem Tellawi)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict13.jpg) A woman cycles past a group of petitioners holding red scarves as they protest outside the Ministry of Civil Affairs in Beijing, China, Thursday, Nov. 24, 2011. About 30 petitioners who they said were infected with HIV from blood transfusions held up a chain of red scarves to symbolize their demands the government to provide compensation for their children’s treatment, in conjunction of the upcoming World AIDS Day, which falls on Dec. 1. (Andy Wong)
A woman cycles past a group of petitioners holding red scarves as they protest outside the Ministry of Civil Affairs in Beijing, China, Thursday, Nov. 24, 2011. About 30 petitioners who they said were infected with HIV from blood transfusions held up a chain of red scarves to symbolize their demands the government to provide compensation for their children’s treatment, in conjunction of the upcoming World AIDS Day, which falls on Dec. 1. (Andy Wong)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict15.jpg) A woman protester attempts to dismantle a barbed wire barricade, newly erected by the Egyptian army, near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)
A woman protester attempts to dismantle a barbed wire barricade, newly erected by the Egyptian army, near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict17.jpg) A protester takes a break during clashes with Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011. Egyptian police are clashing with anti-government protesters for a fifth day in Cairo. Tens of thousands of protesters in Tahrir Square have rejected a promise by Egypt’s military ruler to speed up a presidential election to the first half of next year.
A protester takes a break during clashes with Egyptian riot police, not pictured, near Tahrir Square in Cairo, Egypt, Wednesday, Nov. 23, 2011. Egyptian police are clashing with anti-government protesters for a fifth day in Cairo. Tens of thousands of protesters in Tahrir Square have rejected a promise by Egypt’s military ruler to speed up a presidential election to the first half of next year.![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict16.jpg) A woman blocks the entrance to Congress as riot police stand guard in Guatemala City, Wednesday Nov. 23, 2011. Protesters are demanding that Congress approve the Ley de Vivienda, or Housing Act, which would allow them to attain legal titles to the lands where they built their homes. (Rodrigo Abd)
A woman blocks the entrance to Congress as riot police stand guard in Guatemala City, Wednesday Nov. 23, 2011. Protesters are demanding that Congress approve the Ley de Vivienda, or Housing Act, which would allow them to attain legal titles to the lands where they built their homes. (Rodrigo Abd)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict14.jpg) A protester affiliated with the Occupy Toronto movement shouts support to fellow protesters inside a barricaded pavilion in their camp in St. James Park in Toronto on Wednesday Nov. 23, 2011, as police and city officials enforce an eviction notice. (Chris Young)
A protester affiliated with the Occupy Toronto movement shouts support to fellow protesters inside a barricaded pavilion in their camp in St. James Park in Toronto on Wednesday Nov. 23, 2011, as police and city officials enforce an eviction notice. (Chris Young)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict19.jpg) Police officers detain opposition demonstrators during an unsanctioned rally in downtown Moscow, Russia, Tuesday, Nov. 22, 2011. Several dozen people were detained in central Moscow where they were protesting against the lack of alternatives in the upcoming parliamentary and presidential elections. (Alexander Zemlianichenko)
Police officers detain opposition demonstrators during an unsanctioned rally in downtown Moscow, Russia, Tuesday, Nov. 22, 2011. Several dozen people were detained in central Moscow where they were protesting against the lack of alternatives in the upcoming parliamentary and presidential elections. (Alexander Zemlianichenko)![[Image]](https://i0.wp.com/cryptome.org/info/women-protest7/pict20.jpg) Anti-government protesters shout during a rally organized by the 20th February, the Moroccan Arab Spring movement in Casablanca, Morocco, Sunday, Nov 20, 2011, in a mass popular call to bring more democracy into this North African kingdom. Thousands of Moroccans from the pro-democracy movement braved pouring rain and high winds in Casablanca to make a final call to boycott upcoming elections. (Abdeljalil Bounhar)
Anti-government protesters shout during a rally organized by the 20th February, the Moroccan Arab Spring movement in Casablanca, Morocco, Sunday, Nov 20, 2011, in a mass popular call to bring more democracy into this North African kingdom. Thousands of Moroccans from the pro-democracy movement braved pouring rain and high winds in Casablanca to make a final call to boycott upcoming elections. (Abdeljalil Bounhar)




![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict27.jpg) Thousands of Egyptians perform Friday prayers during a rally in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011. Tens of thousands of protesters chanting, “Leave, leave!” are rapidly filling up Cairo’s Tahrir Square in what promises to be a massive demonstration to force Egypt’s ruling military council to yield power. The Friday rally is dubbed by organizers as “The Last Chance Million-Man Protest,” and comes one day after the military offered an apology for the killing of nearly 40 protesters.
Thousands of Egyptians perform Friday prayers during a rally in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011. Tens of thousands of protesters chanting, “Leave, leave!” are rapidly filling up Cairo’s Tahrir Square in what promises to be a massive demonstration to force Egypt’s ruling military council to yield power. The Friday rally is dubbed by organizers as “The Last Chance Million-Man Protest,” and comes one day after the military offered an apology for the killing of nearly 40 protesters.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict38.jpg) Egyptian protesters carry a giant Egyptian flag with Arabic writing that reads, in part, “Egypt is greater than you,” in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
Egyptian protesters carry a giant Egyptian flag with Arabic writing that reads, in part, “Egypt is greater than you,” in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict34.jpg) Protesters, including a wounded man, chant slogans and wave Egyptian national flags during a rally in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
Protesters, including a wounded man, chant slogans and wave Egyptian national flags during a rally in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict28.jpg) Egyptians, including a man perched on a lamp post, perform Friday prayers during a rally in Cairo’s Tahrir square, Egypt, Friday, Nov. 25, 2011.
Egyptians, including a man perched on a lamp post, perform Friday prayers during a rally in Cairo’s Tahrir square, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict29.jpg) Pro-reform leader and Nobel peace laureate Mohamed El-Baradei, center, is surrounded by protesters during his arrival for Friday prayers in Cairo’s Tahrir square, Egypt, Friday, Nov. 25, 2011.
Pro-reform leader and Nobel peace laureate Mohamed El-Baradei, center, is surrounded by protesters during his arrival for Friday prayers in Cairo’s Tahrir square, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict30.jpg) Egyptian women pray during Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
Egyptian women pray during Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict31.jpg) Protesters, including a man holding tear gas cannisters, chant slogans and wave national flags during a rally in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
Protesters, including a man holding tear gas cannisters, chant slogans and wave national flags during a rally in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict32.jpg) Egyptian men pray next to a t-shirt vendor during Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
Egyptian men pray next to a t-shirt vendor during Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict37.jpg) An Egyptian woman stands next to a cotton candy vendor before Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
An Egyptian woman stands next to a cotton candy vendor before Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict33.jpg) A man holds up a shoe, which is seen as a sign of disrespect, with pictures of Egyptians including Gamal Mubarak, center, during Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
A man holds up a shoe, which is seen as a sign of disrespect, with pictures of Egyptians including Gamal Mubarak, center, during Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict35.jpg) A veiled Egyptian woman waits for Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
A veiled Egyptian woman waits for Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict36.jpg) An Egyptian protester wears a safety mask around his neck as he performs Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
An Egyptian protester wears a safety mask around his neck as he performs Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict39.jpg) An Egyptian girl stands as protesters perform Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
An Egyptian girl stands as protesters perform Friday prayers in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict40.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict42.jpg) A protester displays an Egyptian flag in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
A protester displays an Egyptian flag in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict43.jpg) A protester reads a newspaper in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.
A protester reads a newspaper in Tahrir Square in Cairo, Egypt, Friday, Nov. 25, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest4/pict41.jpg) Demonstrators chant slogans as thousands spend the night in Tahrir Square, Cairo, Egypt, Thursday, Nov. 24, 2011.
Demonstrators chant slogans as thousands spend the night in Tahrir Square, Cairo, Egypt, Thursday, Nov. 24, 2011.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict29.jpg) Occupy Wall Street protesters gather to listen to speakers after being allowed back into Zuccotti Park, Tuesday, Nov. 15, 2011 in New York. State Supreme Court Justice Michael Stallman upheld the city’s eviction of the protesters after an emergency appeal by the National Lawyers Guild. If crowds of demonstrators return to the park, they will not be allowed to bring tents, sleeping bags and other equipment that turned the area into a makeshift city of dissent. (Henny Ray Abrams) [
Occupy Wall Street protesters gather to listen to speakers after being allowed back into Zuccotti Park, Tuesday, Nov. 15, 2011 in New York. State Supreme Court Justice Michael Stallman upheld the city’s eviction of the protesters after an emergency appeal by the National Lawyers Guild. If crowds of demonstrators return to the park, they will not be allowed to bring tents, sleeping bags and other equipment that turned the area into a makeshift city of dissent. (Henny Ray Abrams) [![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict41.jpg) Occupy Wall Street protesters return to Zuccotti Park on Tuesday, Nov. 15, 2011 in New York. State Supreme Court Justice Michael Stallman upheld the city’s eviction of the protesters after an emergency appeal by the National Lawyers Guild. If crowds of demonstrators return to the park, they will not be allowed to bring tents, sleeping bags and other equipment that turned the area into a makeshift city of dissent. (Bebeto Matthews)
Occupy Wall Street protesters return to Zuccotti Park on Tuesday, Nov. 15, 2011 in New York. State Supreme Court Justice Michael Stallman upheld the city’s eviction of the protesters after an emergency appeal by the National Lawyers Guild. If crowds of demonstrators return to the park, they will not be allowed to bring tents, sleeping bags and other equipment that turned the area into a makeshift city of dissent. (Bebeto Matthews)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict36.jpg) Occupy Wall Street protesters return to Zuccotti Park with strict police enforced rules on Tuesday, Nov. 15, 2011 in New York. State Supreme Court Justice Michael Stallman upheld the city’s eviction of the protesters after an emergency appeal by the National Lawyers Guild. (Bebeto Matthews)
Occupy Wall Street protesters return to Zuccotti Park with strict police enforced rules on Tuesday, Nov. 15, 2011 in New York. State Supreme Court Justice Michael Stallman upheld the city’s eviction of the protesters after an emergency appeal by the National Lawyers Guild. (Bebeto Matthews)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict38.jpg) Occupy Wall Street Encampment at Zuccotti Park seen is empty of demonstrators, Tuesday, Nov. 15, 2011 in New York. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Mary Altaffer)
Occupy Wall Street Encampment at Zuccotti Park seen is empty of demonstrators, Tuesday, Nov. 15, 2011 in New York. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict39.jpg) Occupy Wall Street protesters hold a general assembly meeting inside an enclosed site near Canal Street on Tuesday, Nov. 15, 2011. Hundreds of police officers in riot gear before dawn Tuesday raided the New York City park where the Occupy Wall Street protests began, evicting and arresting hundreds of protesters from what has become the epicenter of the worldwide movement protesting corporate greed and economic inequality. (Seth Wenig) [Photo taken and transmitted before Seth Wenig was arrested along with the protestors.]
Occupy Wall Street protesters hold a general assembly meeting inside an enclosed site near Canal Street on Tuesday, Nov. 15, 2011. Hundreds of police officers in riot gear before dawn Tuesday raided the New York City park where the Occupy Wall Street protests began, evicting and arresting hundreds of protesters from what has become the epicenter of the worldwide movement protesting corporate greed and economic inequality. (Seth Wenig) [Photo taken and transmitted before Seth Wenig was arrested along with the protestors.]![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict40.jpg) Police prepare to enter an enclosed site near Canal Street where Occupy Wall Street protesters gathered on Tuesday, Nov. 15, 2011. Hundreds of police officers in riot gear before dawn Tuesday raided the New York City park where the Occupy Wall Street protests began, evicting and arresting hundreds of protesters from what has become the epicenter of the worldwide movement protesting corporate greed and economic inequality. (Seth Wenig)
Police prepare to enter an enclosed site near Canal Street where Occupy Wall Street protesters gathered on Tuesday, Nov. 15, 2011. Hundreds of police officers in riot gear before dawn Tuesday raided the New York City park where the Occupy Wall Street protests began, evicting and arresting hundreds of protesters from what has become the epicenter of the worldwide movement protesting corporate greed and economic inequality. (Seth Wenig)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict34.jpg) Occupy Wall Street activists gain entrance in to Duarte Square to protest after police removed the protesters early in the morning from Zuccotti Park on November 15, 2011 in New York City. Getty
Occupy Wall Street activists gain entrance in to Duarte Square to protest after police removed the protesters early in the morning from Zuccotti Park on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict33.jpg) NYPD officers standoff with Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty
NYPD officers standoff with Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict27.jpg) NYPD officers clear out Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty [AP journalist Karen Matthews is at upper right in light blue jacket (and in earlier photos below). She was arrested with AP photographer Seth Wenig in following photo.]
NYPD officers clear out Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty [AP journalist Karen Matthews is at upper right in light blue jacket (and in earlier photos below). She was arrested with AP photographer Seth Wenig in following photo.]
![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict35.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict37.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict56.jpg) Seth Wenig, a photographer for The Associated Press, was arrested on Thursday near Trinity Church. (Ozier Muhammad) [Wenig handcuffed with backpack at center in following photo, back to camera.]
Seth Wenig, a photographer for The Associated Press, was arrested on Thursday near Trinity Church. (Ozier Muhammad) [Wenig handcuffed with backpack at center in following photo, back to camera.]![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict32.jpg) NYPD officers arrest Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty
NYPD officers arrest Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict31.jpg) NYPD officers arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty
NYPD officers arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict28.jpg) NYPD officers attempt to arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty
NYPD officers attempt to arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict30.jpg) NYPD officers arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty
NYPD officers arrest an Occupy Wall Street activist after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict26.jpg) NYPD officers arrest Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Police removed the protesters early in the morning from their encampment in Zuccotti Park. Hundreds of protesters, who rallied against inequality in America, have slept in tents and under tarps since September 17 in Zuccotti Park, which has since become the epicenter of the global Occupy movement. The raid in New York City follows recent similar moves in Oakland, California, and Portland, Oregon. Getty
NYPD officers arrest Occupy Wall Street activists after they gained entrance in to the private park next to Duarte Square to protest on November 15, 2011 in New York City. Police removed the protesters early in the morning from their encampment in Zuccotti Park. Hundreds of protesters, who rallied against inequality in America, have slept in tents and under tarps since September 17 in Zuccotti Park, which has since become the epicenter of the global Occupy movement. The raid in New York City follows recent similar moves in Oakland, California, and Portland, Oregon. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict20.jpg) Occupy Wall Street protesters return to Zuccotti Park on Tuesday, Nov. 15, 2011 in New York. After an early police raid removing protesters, hundreds returned to Zuccotti Park carrying photocopies of a court order they say gives them the right to return to the park. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules.
Occupy Wall Street protesters return to Zuccotti Park on Tuesday, Nov. 15, 2011 in New York. After an early police raid removing protesters, hundreds returned to Zuccotti Park carrying photocopies of a court order they say gives them the right to return to the park. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict21.jpg) Police arrest an Occupy Wall Street protester at Zuccotti Park on Tuesday, Nov. 15, 2011 in New York. After an early police raid removing protesters, hundreds returned to Zuccotti Park carrying photocopies of a court order they say gives them the right to return there.
Police arrest an Occupy Wall Street protester at Zuccotti Park on Tuesday, Nov. 15, 2011 in New York. After an early police raid removing protesters, hundreds returned to Zuccotti Park carrying photocopies of a court order they say gives them the right to return there.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict22.jpg) Occupy Wall Street protesters rally in a small park on Canal Street in New York, Tuesday, Nov. 15, 2011. Police officers evicted the protesters from their base in Zuccotti Park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)
Occupy Wall Street protesters rally in a small park on Canal Street in New York, Tuesday, Nov. 15, 2011. Police officers evicted the protesters from their base in Zuccotti Park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict23.jpg) A police officer watches from the grounds of City Hall as Occupy Wall Street protesters linked hands to block media from attending a news conference held by Mayor Michael Bloomberg in New York, Tuesday, Nov. 15, 2011. The protesters eventually dispersed peacefully.
A police officer watches from the grounds of City Hall as Occupy Wall Street protesters linked hands to block media from attending a news conference held by Mayor Michael Bloomberg in New York, Tuesday, Nov. 15, 2011. The protesters eventually dispersed peacefully.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict24.jpg) An empty and closed Zuccotti Park is seen in New York, Tuesday, Nov. 15, 2011. Police officers evicted Occupy Wall Street protesters from the park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)
An empty and closed Zuccotti Park is seen in New York, Tuesday, Nov. 15, 2011. Police officers evicted Occupy Wall Street protesters from the park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict25.jpg) A pedestrian takes a picture of an empty and closed Zuccotti Park in New York, Tuesday, Nov. 15, 2011. Police officers evicted Occupy Wall Street protesters from the park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)
A pedestrian takes a picture of an empty and closed Zuccotti Park in New York, Tuesday, Nov. 15, 2011. Police officers evicted Occupy Wall Street protesters from the park overnight. The National Lawyers Guild obtained a court order allowing the protesters to return with their tents to the park, where they have camped for two months. The guild said the injunction prevents the city from enforcing park rules on the protesters. (Seth Wenig)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict0.jpg) An Occupy Wall Street protestor draws contact from a police officer near Zuccotti Park after being ordered to leave the longtime encampment in New York, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park.
An Occupy Wall Street protestor draws contact from a police officer near Zuccotti Park after being ordered to leave the longtime encampment in New York, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park.
![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict18.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict19.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict12.jpg) Occupy Wall Street protesters clash with police at Zuccotti Park after being ordered to leave their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Craig Ruttle)
Occupy Wall Street protesters clash with police at Zuccotti Park after being ordered to leave their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Craig Ruttle)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict1.jpg) An Occupy Wall Street protestor is arrested on the ground by police near Zuccotti Park after being ordered to leave their longtime encampment in New York, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park.
An Occupy Wall Street protestor is arrested on the ground by police near Zuccotti Park after being ordered to leave their longtime encampment in New York, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict14.jpg) A demonstrator yells at police officers as they order Occupy Wall Street protesters to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)
A demonstrator yells at police officers as they order Occupy Wall Street protesters to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict13.jpg) An Occupy Wall Street protester yells out at police after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)
An Occupy Wall Street protester yells out at police after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict3.jpg) Occupy Wall Street protesters clash with police near Zuccotti Park after being ordered to leave their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)
Occupy Wall Street protesters clash with police near Zuccotti Park after being ordered to leave their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict4.jpg) Occupy Wall Street protesters are pushed by police near the encampment at Zuccotti Park in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous.
Occupy Wall Street protesters are pushed by police near the encampment at Zuccotti Park in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict2.jpg) Demonstrators clash with police after being ordered to leave the Occupy Wall Street encampment at Zuccotti Park in New York on Tuesday, Nov. 15, 2011. Police handed out notices earlier from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Craig Ruttle)
Demonstrators clash with police after being ordered to leave the Occupy Wall Street encampment at Zuccotti Park in New York on Tuesday, Nov. 15, 2011. Police handed out notices earlier from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Craig Ruttle)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict6.jpg) An Occupy Wall Street protester is arrested by police near the encampment at Zuccotti Park in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents.
An Occupy Wall Street protester is arrested by police near the encampment at Zuccotti Park in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents.![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict7.jpg) An Occupy Wall Street protestor is arrested during a march on Broadway, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)
An Occupy Wall Street protestor is arrested during a march on Broadway, Tuesday, Nov. 15, 2011, in New York, after police ordered demonstrators to leave their encampment in Zuccotti Park. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict9.jpg) An Occupy Wall Street protester is detained by police officers after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)
An Occupy Wall Street protester is detained by police officers after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict10.jpg) Occupy Wall Street protesters are detained by police officers after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)
Occupy Wall Street protesters are detained by police officers after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict11.jpg) Occupy Wall Street demonstrators are arrested after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)
Occupy Wall Street demonstrators are arrested after being ordered to leave Zuccotti Park, their longtime encampment in New York, early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (Mary Altaffer)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict17.jpg) Occupy Wall Street protesters march through the streets after they were evicted from Zuccotti Park on November 15, 2011 in New York. Hundreds of police in riot gear dismantled the Occupy Oakland camp Monday, evicting and arresting protesters in the second such US move in as many days as authorities get tough against the two-month-old protest movement. Getty
Occupy Wall Street protesters march through the streets after they were evicted from Zuccotti Park on November 15, 2011 in New York. Hundreds of police in riot gear dismantled the Occupy Oakland camp Monday, evicting and arresting protesters in the second such US move in as many days as authorities get tough against the two-month-old protest movement. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict8.jpg) A police officer carries trash through Zuccotti Park, the longtime encampment for Occupy Wall Street protesters in New York, as the cleanup effort begins early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)
A police officer carries trash through Zuccotti Park, the longtime encampment for Occupy Wall Street protesters in New York, as the cleanup effort begins early Tuesday, Nov. 15, 2011. At about 1 a.m. Tuesday, police handed out notices from the park’s owner, Brookfield Office Properties, and the city saying that the park had to be cleared because it had become unsanitary and hazardous. Protesters were told they could return, but without sleeping bags, tarps or tents. (John Minchillo)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict5.jpg) Two protesters and their dog, who said they have stayed slept with other protesters for the last 56 nights, sit along a police barricade at the edge of Zuccotti Park in New York, Tuesday, Nov. 15, 2011 after the Occupy Wall Street encampment was cleared from the park in the early morning hours after a nearly two month occupation,wa;;w and before the park reopened. (Craig Ruttle)
Two protesters and their dog, who said they have stayed slept with other protesters for the last 56 nights, sit along a police barricade at the edge of Zuccotti Park in New York, Tuesday, Nov. 15, 2011 after the Occupy Wall Street encampment was cleared from the park in the early morning hours after a nearly two month occupation,wa;;w and before the park reopened. (Craig Ruttle)![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict16.jpg) New York City sanitation crews clean Zuccotti Park after city officials evicted the ‘Occupy Wall Street’ protest from the park in the early morning hours of November 15, 2011 in New York. Occupy Wall Street protestors most feared the coming winter, but it was on the mildest of nights, when activists slept soundly in their tents, that New York police sprang a surprise operation to end the eight-week demonstration. Getty
New York City sanitation crews clean Zuccotti Park after city officials evicted the ‘Occupy Wall Street’ protest from the park in the early morning hours of November 15, 2011 in New York. Occupy Wall Street protestors most feared the coming winter, but it was on the mildest of nights, when activists slept soundly in their tents, that New York police sprang a surprise operation to end the eight-week demonstration. Getty![[Image]](https://i0.wp.com/cryptome.org/info/ows-19/pict15.jpg) People walk past New York Police Department officers guarding a closed Zuccotti Park after city officials evicted the ‘Occupy Wall Street’ protest from the park in the early morning hours of November 15, 2011 in New York. Getty
People walk past New York Police Department officers guarding a closed Zuccotti Park after city officials evicted the ‘Occupy Wall Street’ protest from the park in the early morning hours of November 15, 2011 in New York. Getty![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict47.jpg) Activists from Ukraine’s scandalous FEMEN group holds a banner reading ‘woman is not a commodity’ as they stage a topless protest on November 10, 2011 against prostitution and woman as a commodity in an official prostitution’s street in Zurich. Getty
Activists from Ukraine’s scandalous FEMEN group holds a banner reading ‘woman is not a commodity’ as they stage a topless protest on November 10, 2011 against prostitution and woman as a commodity in an official prostitution’s street in Zurich. Getty![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict12.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict48.jpg) An activist of the Ukrainian women movement Femen is being arrested by policemen in front of St Peter’s basilica after holding a placard asking for ‘Freedom for women’ following Pope Benedict XVI’s Angelus prayer on November 6, 2011 at St Peter’s square at The Vatican. Getty
An activist of the Ukrainian women movement Femen is being arrested by policemen in front of St Peter’s basilica after holding a placard asking for ‘Freedom for women’ following Pope Benedict XVI’s Angelus prayer on November 6, 2011 at St Peter’s square at The Vatican. Getty![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict49.jpg) An activist of the Ukrainian women movement Femen is taken away by Italian policemen in front of St Peter’s basilica after holding a placard asking for ‘Freedom for women’ following Pope Benedict XVI’s Angelus prayer on November 6, 2011 at St Peter’s square at The Vatican. Getty
An activist of the Ukrainian women movement Femen is taken away by Italian policemen in front of St Peter’s basilica after holding a placard asking for ‘Freedom for women’ following Pope Benedict XVI’s Angelus prayer on November 6, 2011 at St Peter’s square at The Vatican. Getty![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict56.jpg) An activist of the Ukrainian female rights organization “Femen” shows a placard demanding freedom for women, during a protest at the end of Pope Benedict XVI’s Angelus prayer in St. Peter’s Square at the Vatican, Sunday, Nov. 6, 2011. (Pier Paolo Cito)
An activist of the Ukrainian female rights organization “Femen” shows a placard demanding freedom for women, during a protest at the end of Pope Benedict XVI’s Angelus prayer in St. Peter’s Square at the Vatican, Sunday, Nov. 6, 2011. (Pier Paolo Cito)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict46.jpg) Ukrainian women’s rights group Femen, painted in colors of the Italian flag, take part in a demonstration staged by the Italian Democratic party to protest against Italian Premier Silvio Berlusconi in Rome, Saturday, Nov. 5, 2011. The International Monetary Fund will monitor Italy’s financial reform efforts, Premier Silvio Berlusconi said Friday, a humbling step for one of the world’s biggest _ but also most indebted _ economies as market confidence in its future wanes.
Ukrainian women’s rights group Femen, painted in colors of the Italian flag, take part in a demonstration staged by the Italian Democratic party to protest against Italian Premier Silvio Berlusconi in Rome, Saturday, Nov. 5, 2011. The International Monetary Fund will monitor Italy’s financial reform efforts, Premier Silvio Berlusconi said Friday, a humbling step for one of the world’s biggest _ but also most indebted _ economies as market confidence in its future wanes.![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict50.jpg) Activists from Ukraine’s scandalous FEMEN group dressed as housemaids stage a topless protest in a show of anger against French former IMF chief Dominique Strauss-Kahn’s attitude towards women in front of his residence in Paris on October 31, 2011. FEMEN has gained worldwide fame by staging a string of topless protests in Ukraine and now in Europe, in recent years to draw attention to issues from the exploitation of women to corruption. The placard read at L ‘ecstasy of power’, at R ‘your shame can’t be clean up’. Getty
Activists from Ukraine’s scandalous FEMEN group dressed as housemaids stage a topless protest in a show of anger against French former IMF chief Dominique Strauss-Kahn’s attitude towards women in front of his residence in Paris on October 31, 2011. FEMEN has gained worldwide fame by staging a string of topless protests in Ukraine and now in Europe, in recent years to draw attention to issues from the exploitation of women to corruption. The placard read at L ‘ecstasy of power’, at R ‘your shame can’t be clean up’. Getty![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict32.jpg) People walk in front of Kiev Zoo, as activists of the Ukrainian female rights organization “Femen”, take part in a topless protest in Kiev, Ukraine, Thursday, Oct. 27, 2011. Kiev zoo is a place that Femen’s activists compared to a concentration camp for those with fur and feathers. Hundreds of animals died at the zoo in recent years due to malnutrition, lack of medical care and abuse, and some suspect that corruption is at the heart of the problem.
People walk in front of Kiev Zoo, as activists of the Ukrainian female rights organization “Femen”, take part in a topless protest in Kiev, Ukraine, Thursday, Oct. 27, 2011. Kiev zoo is a place that Femen’s activists compared to a concentration camp for those with fur and feathers. Hundreds of animals died at the zoo in recent years due to malnutrition, lack of medical care and abuse, and some suspect that corruption is at the heart of the problem.![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict33.jpg) Securty guards detain an activist of the Ukrainian female rights organization “Femen”, during an action of protest in front of Kiev Zoo, Ukraine, Thursday, Oct. 27, 2011. Kiev zoo is a place that Femen’s activists compared to a concentration camp for those with fur and feathers. Hundreds of animals died at the zoo in recent years due to malnutrition, lack of medical care and abuse, and some suspect that corruption is at the heart of the problem. Femen calls for the 100-year-old zoo to be closed.
Securty guards detain an activist of the Ukrainian female rights organization “Femen”, during an action of protest in front of Kiev Zoo, Ukraine, Thursday, Oct. 27, 2011. Kiev zoo is a place that Femen’s activists compared to a concentration camp for those with fur and feathers. Hundreds of animals died at the zoo in recent years due to malnutrition, lack of medical care and abuse, and some suspect that corruption is at the heart of the problem. Femen calls for the 100-year-old zoo to be closed.![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict34.jpg) Secury guards detain an activist of the Ukrainian female rights organization “Femen”, during an action of nude protest in front of Kiev Zoo, Ukraine, Thursday, Oct. 27, 2011. Kiev zoo is a place that Femen’s activists compared to a concentration camp for those with fur and feathers. Hundreds of animals died at the zoo in recent years due to malnutrition, lack of medical care and abuse, and some suspect that corruption is at the heart of the problem.
Secury guards detain an activist of the Ukrainian female rights organization “Femen”, during an action of nude protest in front of Kiev Zoo, Ukraine, Thursday, Oct. 27, 2011. Kiev zoo is a place that Femen’s activists compared to a concentration camp for those with fur and feathers. Hundreds of animals died at the zoo in recent years due to malnutrition, lack of medical care and abuse, and some suspect that corruption is at the heart of the problem.![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict24.jpg) Police detain a member of women’s activist group FEMEN after their protest against government policy in front front of the Cabinet building in Kiev, Ukraine, Wednesday, Aug.24, 2011. The former Soviet republic marks the 20th anniversary of its independence. (Efrem Lukatsky)
Police detain a member of women’s activist group FEMEN after their protest against government policy in front front of the Cabinet building in Kiev, Ukraine, Wednesday, Aug.24, 2011. The former Soviet republic marks the 20th anniversary of its independence. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict41.jpg) Police detain a member of the women’s activist group FEMEN, after their protest against government policy in front of the Cabinet building in Kiev, Ukraine, Wednesday, Aug. 24, 2011. The former Soviet republic is marking the 20th anniversary of its independence. (Efrem Lukatsky)
Police detain a member of the women’s activist group FEMEN, after their protest against government policy in front of the Cabinet building in Kiev, Ukraine, Wednesday, Aug. 24, 2011. The former Soviet republic is marking the 20th anniversary of its independence. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict51.jpg) Ukrainian women’s rights group Femen, painted in colors of the European Union countries, protest against the regular summer switch off of public utility supply of hot water in central Kiev, Ukraine, Thursday, July 14, 2011. Women symbolically wash themselves in the city fountain to protest the need for hot water all year round, and to highlight the need for the hot water utility during the upcoming EURO 2012 soccer competition.(Efrem Lukatsky)
Ukrainian women’s rights group Femen, painted in colors of the European Union countries, protest against the regular summer switch off of public utility supply of hot water in central Kiev, Ukraine, Thursday, July 14, 2011. Women symbolically wash themselves in the city fountain to protest the need for hot water all year round, and to highlight the need for the hot water utility during the upcoming EURO 2012 soccer competition.(Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict52.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict35.jpg) Ukrainian women’s rights group Femen holding a picket in front of a court building, against the detention of a fellow activist in Kiev, Ukraine, Monday, Jan. 17, 2011. The poster reads, “Hands off, Femen”. Opposition politicians and democrats insist that President Viktor Yanukovych trampled Ukraine’s constitution in a bit to monopolize political power.(Efrem Lukatsky)
Ukrainian women’s rights group Femen holding a picket in front of a court building, against the detention of a fellow activist in Kiev, Ukraine, Monday, Jan. 17, 2011. The poster reads, “Hands off, Femen”. Opposition politicians and democrats insist that President Viktor Yanukovych trampled Ukraine’s constitution in a bit to monopolize political power.(Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict30.jpg) Ukrainian women’s rights group Femen, painted in colors of the European Union countries, protest against the regular summer switch off of public utility supply of hot water in central Kiev, Ukraine, Thursday, July 14, 2011. Women symbolically wash themselves in the city fountain to protest the need for hot water all year round, and to highlight the need for the hot water utility during the upcoming EURO 2012 soccer competition. (Efrem Lukatsky)
Ukrainian women’s rights group Femen, painted in colors of the European Union countries, protest against the regular summer switch off of public utility supply of hot water in central Kiev, Ukraine, Thursday, July 14, 2011. Women symbolically wash themselves in the city fountain to protest the need for hot water all year round, and to highlight the need for the hot water utility during the upcoming EURO 2012 soccer competition. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict26.jpg) Police detain Alexandra Shevchenko a member of women’s activist group FEMEN, in front of parliament in Kiev, Ukraine, Tuesday, July 5, 2011. Ukrainians are fiercely opposed to the pension fund reform, which parliament is set to consider this week, that is meant to raise the retirement age for women. (Efrem Lukatsky)
Police detain Alexandra Shevchenko a member of women’s activist group FEMEN, in front of parliament in Kiev, Ukraine, Tuesday, July 5, 2011. Ukrainians are fiercely opposed to the pension fund reform, which parliament is set to consider this week, that is meant to raise the retirement age for women. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict37.jpg) Semi naked activists from the Ukrainian female rights group Femen protest in front of the Saudi Arabian embassy against a ban on driving cars for women in Kiev, Ukraine, Thursday, June 16, 2011. (Sergei Chuzavkov)
Semi naked activists from the Ukrainian female rights group Femen protest in front of the Saudi Arabian embassy against a ban on driving cars for women in Kiev, Ukraine, Thursday, June 16, 2011. (Sergei Chuzavkov)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict39.jpg) An secury guard detains an activist of the Ukrainian female rights organization ‘Femen’ during an action of protest in front of the city’s State Administration at a opening ceremony of clocks counting down time that remains before the EURO 2012 soccer tournament starts, in Kiev, Ukraine, Wednesday, June 8, 2011. Writing on her back reads ‘Euro 2012 without Prostitution’. (Efrem Lukatsky)
An secury guard detains an activist of the Ukrainian female rights organization ‘Femen’ during an action of protest in front of the city’s State Administration at a opening ceremony of clocks counting down time that remains before the EURO 2012 soccer tournament starts, in Kiev, Ukraine, Wednesday, June 8, 2011. Writing on her back reads ‘Euro 2012 without Prostitution’. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict36.jpg) Activists of the Women’s Movement ‘FEMEN’ perform during a protest against the politics of Belarus President Alexander Lukashenko, during a rally to protest against what they claim is the sex-tourism and trafficking of women from Ukraine, at Independence square in Kiev, Ukraine, Wednesday, May 11, 2011. The Women’s Movement ‘FEMEN’ is an organization of the young women of the city of Kiev orientated to represent and defend the rights of women-students of the capital. (Efrem Lukatsky)
Activists of the Women’s Movement ‘FEMEN’ perform during a protest against the politics of Belarus President Alexander Lukashenko, during a rally to protest against what they claim is the sex-tourism and trafficking of women from Ukraine, at Independence square in Kiev, Ukraine, Wednesday, May 11, 2011. The Women’s Movement ‘FEMEN’ is an organization of the young women of the city of Kiev orientated to represent and defend the rights of women-students of the capital. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict40.jpg) Activists of the Women’s Movement ‘FEMEN’ performs and shout anti-Lukashenko slogans protesting against his politics in Belarus during a rally at Independence square in Kiev, Ukraine, Wednesday, May. 11, 2011. The poster reads ‘Put Lukashenko on the Rack!’. The Women’s Movement ‘FEMEN’ is an organization of the young women of the city of Kiev oriented on the women-students of the capital. The main program of the movement is the national campaign against the sex tourism and women trafficking. (Efrem Lukatsky)
Activists of the Women’s Movement ‘FEMEN’ performs and shout anti-Lukashenko slogans protesting against his politics in Belarus during a rally at Independence square in Kiev, Ukraine, Wednesday, May. 11, 2011. The poster reads ‘Put Lukashenko on the Rack!’. The Women’s Movement ‘FEMEN’ is an organization of the young women of the city of Kiev oriented on the women-students of the capital. The main program of the movement is the national campaign against the sex tourism and women trafficking. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict38.jpg) Activists of the Women’s Movement ‘FEMEN’ performs and shout anti-Lukashenko slogans protesting against his politics in Belarus during a rally at Independence square in Kiev, Ukraine, Wednesday, May. 11, 2011. The poster reading ‘Crush a cockroach’. The Women’s Movement ‘FEMEN’ is an organization of the young women of the city of Kiev oriented on the women-students A depiction of Lukashenko is seen in the background. (Efrem Lukatsky)
Activists of the Women’s Movement ‘FEMEN’ performs and shout anti-Lukashenko slogans protesting against his politics in Belarus during a rally at Independence square in Kiev, Ukraine, Wednesday, May. 11, 2011. The poster reading ‘Crush a cockroach’. The Women’s Movement ‘FEMEN’ is an organization of the young women of the city of Kiev oriented on the women-students A depiction of Lukashenko is seen in the background. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict42.jpg) Ukrainian police hold back activists from the women’s rights organization “Femen” during a protest close to the site of the international donors conference to clean up the Chernobyl nuclear disaster site in Kiev, Ukraine, Tuesday, April 19, 2011. Poster reads “Yanukovych is worse than radiation”. On April 26, Ukraine marks the 25th anniversary of the fatal explosion at the Chernobyl nuclear power plant. (Ukrafoto)
Ukrainian police hold back activists from the women’s rights organization “Femen” during a protest close to the site of the international donors conference to clean up the Chernobyl nuclear disaster site in Kiev, Ukraine, Tuesday, April 19, 2011. Poster reads “Yanukovych is worse than radiation”. On April 26, Ukraine marks the 25th anniversary of the fatal explosion at the Chernobyl nuclear power plant. (Ukrafoto)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict29.jpg) Ukrainian activists from the group Femen protest Iran’s treatment of women during the opening of Iranian Culture Days in Kiev, Ukraine, Thursday, Nov. 11, 2010. (Sergei Chuzavkov)
Ukrainian activists from the group Femen protest Iran’s treatment of women during the opening of Iranian Culture Days in Kiev, Ukraine, Thursday, Nov. 11, 2010. (Sergei Chuzavkov)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict28.jpg) Activists of the Ukrainian Women’s Movement “FEMEN” shout protests in front of the Iranian Embassy in Kiev, Ukraine, Wednesday, Nov. 3, 2010, against the death penalty given to Sakineh Mohammadi Ashtiani, a mother of two children, who was sentenced to death by stoning in Iran on charges of adultery. (Sergei Chuzavkov)
Activists of the Ukrainian Women’s Movement “FEMEN” shout protests in front of the Iranian Embassy in Kiev, Ukraine, Wednesday, Nov. 3, 2010, against the death penalty given to Sakineh Mohammadi Ashtiani, a mother of two children, who was sentenced to death by stoning in Iran on charges of adultery. (Sergei Chuzavkov)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict31.jpg) In this photo taken on Thursday, July 15, 2010, police detain activists of the local FEMEN women’s rights watchdog as they protest against the regular summer switch off of hot water in the city in downtown Kiev, Ukraine. A group of young activists is gaining popularity here for staging topless protests that involve sexually charged gestures, obscene slogans and scuffles with security guards and police. Often, the point seems to be just getting naked.
In this photo taken on Thursday, July 15, 2010, police detain activists of the local FEMEN women’s rights watchdog as they protest against the regular summer switch off of hot water in the city in downtown Kiev, Ukraine. A group of young activists is gaining popularity here for staging topless protests that involve sexually charged gestures, obscene slogans and scuffles with security guards and police. Often, the point seems to be just getting naked.![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict25.jpg) Members of the activist group Femen protest at what they see as the manipulation of the democratic system at a polling station in Kiev, Ukraine, Sunday, Feb. 7, 2010. The signs read “The War Begins Here” and “Stop Raping the Country.” (Mikhail Metzel)
Members of the activist group Femen protest at what they see as the manipulation of the democratic system at a polling station in Kiev, Ukraine, Sunday, Feb. 7, 2010. The signs read “The War Begins Here” and “Stop Raping the Country.” (Mikhail Metzel)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict43.jpg) Members of the activist group Femen protest at what they see as the manipulation of the democratic system at a polling station in Kiev, Ukraine, Sunday, Feb. 7, 2010. (Mikhail Metzel)
Members of the activist group Femen protest at what they see as the manipulation of the democratic system at a polling station in Kiev, Ukraine, Sunday, Feb. 7, 2010. (Mikhail Metzel)![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict45.jpg) Activists of the Women’s Movement “FEMEN”, dressed as prostitutes, take part in a rally outside the Central Election Commission office in Kiev, Ukraine, Thursday, Jan. 14, 2010. The event was meant to highlight what the group called political prostitution and crude populism in the election campaign. The posters with the logos of the leading candidates and signature “Choose me” in Ukraine’s presidential race are seen at top.
Activists of the Women’s Movement “FEMEN”, dressed as prostitutes, take part in a rally outside the Central Election Commission office in Kiev, Ukraine, Thursday, Jan. 14, 2010. The event was meant to highlight what the group called political prostitution and crude populism in the election campaign. The posters with the logos of the leading candidates and signature “Choose me” in Ukraine’s presidential race are seen at top.![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict27.jpg) An activist of the Women’s Movement “FEMEN”, dressed as a prostitute, holds a poster with the logo of one of the leading candidates and signature “Choose me” in Ukraine’s presidential race, during a rally outside the Central Election Commission office in Kiev, Ukraine, Thursday, Jan. 14, 2010. The event was meant to highlight what the group called political prostitution and crude populism, in the election campaign.
An activist of the Women’s Movement “FEMEN”, dressed as a prostitute, holds a poster with the logo of one of the leading candidates and signature “Choose me” in Ukraine’s presidential race, during a rally outside the Central Election Commission office in Kiev, Ukraine, Thursday, Jan. 14, 2010. The event was meant to highlight what the group called political prostitution and crude populism, in the election campaign.![[Image]](https://i0.wp.com/cryptome.org/info/femen/pict44.jpg) A security officer stops an activist of the Women’s Movement ‘FEMEN’ from climbing a barrier at Mykhailivska Square in Kiev, Ukraine, Monday, Dec. 14, 2009, prior the opening of the meeting for UEFA EURO 2012. The ‘FEMEN’ movement is campaigning against sex tourism and the trafficking of women in Ukraine. (Efrem Lukatsky)
A security officer stops an activist of the Women’s Movement ‘FEMEN’ from climbing a barrier at Mykhailivska Square in Kiev, Ukraine, Monday, Dec. 14, 2009, prior the opening of the meeting for UEFA EURO 2012. The ‘FEMEN’ movement is campaigning against sex tourism and the trafficking of women in Ukraine. (Efrem Lukatsky)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict23.jpg) Demonstrators are lit by a laser lights as thousands spend the night in Tahrir Square, Cairo, Egypt, Thursday, Nov. 24, 2011. Police and the protesters, who are demanding that Egypt’s ruling military council step down, are observing a truce after five days of deadly street battles in which dozens have died. (Bela Szandelszky)
Demonstrators are lit by a laser lights as thousands spend the night in Tahrir Square, Cairo, Egypt, Thursday, Nov. 24, 2011. Police and the protesters, who are demanding that Egypt’s ruling military council step down, are observing a truce after five days of deadly street battles in which dozens have died. (Bela Szandelszky)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict26.jpg) A wounded protester is treated at a field hospital near Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Manu Brabo)
A wounded protester is treated at a field hospital near Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Manu Brabo)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict24.jpg) Demonstrators chant slogans as thousands spend the night in Tahrir Square, Cairo, Egypt, Thursday, Nov. 24, 2011. Police and the protesters, who are demanding that Egypt’s ruling military council step down, are observing a truce after five days of deadly street battles in which dozens have died. (Bela Szandelszky)
Demonstrators chant slogans as thousands spend the night in Tahrir Square, Cairo, Egypt, Thursday, Nov. 24, 2011. Police and the protesters, who are demanding that Egypt’s ruling military council step down, are observing a truce after five days of deadly street battles in which dozens have died. (Bela Szandelszky)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict25.jpg) Protesters try to climb a concrete barricade erected by Egyptian Army soldiers in the street leading to the interior ministry from Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Manu Brabo)
Protesters try to climb a concrete barricade erected by Egyptian Army soldiers in the street leading to the interior ministry from Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Manu Brabo)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict18.jpg) Egyptian Army soldiers stand guard atop a concrete block barricade while protesters chant slogans, near Tahrir Square, in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Bernat Armangue)
Egyptian Army soldiers stand guard atop a concrete block barricade while protesters chant slogans, near Tahrir Square, in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Bernat Armangue)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict20.jpg) A protester waves an Egyptian national flag as they gather in Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Bernat Armangue)
A protester waves an Egyptian national flag as they gather in Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Bernat Armangue)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict22.jpg)
![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict5.jpg) Protesters gather as Egyptian Army soldiers build a concrete block barricade on the street between Tahrir Square and the interior ministry in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Khalil Hamra)
Protesters gather as Egyptian Army soldiers build a concrete block barricade on the street between Tahrir Square and the interior ministry in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict9.jpg) Egyptian protesters stand behind a barbed wire barricade in Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Mohammed Abu Zaid)
Egyptian protesters stand behind a barbed wire barricade in Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Mohammed Abu Zaid)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict10.jpg) An Egyptian officer, left, attempts to talk to protesters behind a newly erected barbed wire barricade by the Egyptian army near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)
An Egyptian officer, left, attempts to talk to protesters behind a newly erected barbed wire barricade by the Egyptian army near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict11.jpg) A woman protester attempts to dismantle a barbed wire barricade, newly erected by the Egyptian army, near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)
A woman protester attempts to dismantle a barbed wire barricade, newly erected by the Egyptian army, near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict14.jpg) Protesters gather behind a barbed wire barricade, newly erected by the Egyptian army, near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)
Protesters gather behind a barbed wire barricade, newly erected by the Egyptian army, near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict15.jpg) Protesters gather behind a barbed wire barricade, newly erected by the Egyptian army, near Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)
Protesters gather behind a barbed wire barricade, newly erected by the Egyptian army, near Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict13.jpg) Protesters shout through a barbed wire barricade, newly erected by the Egyptian army, near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)
Protesters shout through a barbed wire barricade, newly erected by the Egyptian army, near Tahrir square in Cairo, Egypt, Thursday, Nov. 24, 2011. International criticism of Egypt’s military rulers is mounting after five days of clashes between police and protesters demanding the generals relinquish power immediately. (Tara Todras-Whitehill)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict4.jpg) A protester watches Egyptian Army soldiers build a concrete block barricade on the street between Tahrir Square and the interior ministry in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Khalil Hamra)
A protester watches Egyptian Army soldiers build a concrete block barricade on the street between Tahrir Square and the interior ministry in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict3.jpg) Egyptian Army officers ask protesters to leave the top of a concrete block barricade on the street between Tahrir Square and the interior ministry in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Khalil Hamra)
Egyptian Army officers ask protesters to leave the top of a concrete block barricade on the street between Tahrir Square and the interior ministry in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict6.jpg) A protester looks through a concrete block barricade erected by the Egyptian Army on the street between Tahrir Square and the interior ministry in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Khalil Hamra)
A protester looks through a concrete block barricade erected by the Egyptian Army on the street between Tahrir Square and the interior ministry in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Khalil Hamra)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict8.jpg) Protesters gather around Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Mohammed Abu Zaid)
Protesters gather around Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Mohammed Abu Zaid)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict7.jpg) A protester prays moments after waking up in Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Bernat Armangue)
A protester prays moments after waking up in Tahrir Square in Cairo, Egypt, Thursday, Nov. 24, 2011. Police and protesters demanding that Egypt’s ruling military council step down are observing a truce after five days of deadly street battles in which dozens have died. (Bernat Armangue)![[Image]](https://i0.wp.com/cryptome.org/info/egypt-protest3/pict12.jpg) Egyptian protesters set a fire during clashes with security forces near Tahrir Square in Cairo, Egypt, late Wednesday, Nov. 23, 2011. Egyptian police are clashing with anti-government protesters for a fifth day in Cairo.
Egyptian protesters set a fire during clashes with security forces near Tahrir Square in Cairo, Egypt, late Wednesday, Nov. 23, 2011. Egyptian police are clashing with anti-government protesters for a fifth day in Cairo.![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111911/pict0.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111911/pict1.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111911/pict3.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111911/pict4.jpg)
![[Image]](https://i0.wp.com/cryptome.org/eyeball/daiichi-111911/pict5.jpg)
You must be logged in to post a comment.