Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Growing Trend of Ransomware Attacks Targeting Hospitals and Healthcare Facilities
Page Count: 5 pages
Date: July 21, 2016
Restriction: For Official Use Only
Originating Organization: Department of Homeland Security, Office of Intelligence and Analysis, Oregon Terrorist Information and Threat Analysis Network, Kentucky Intelligence Fusion Center
File Type: pdf
File Size: 700,582 bytes
File Hash (SHA-256):7C06327003FC391E7C97CE2B86E7E07EAF9B04768EB4C793D3409A81F61192C0
(U) Key Judgments: An uptick in ransomware attacks directed against the healthcare community in the first four months of 2016 underscores the potential vulnerability of all hospital and healthcare provider computer systems.
(U//FOUO) TITAN, KIFC, and I&A have not identified any specific impending or future threats to hospitals or healthcare providers in Oregon or Kentucky.
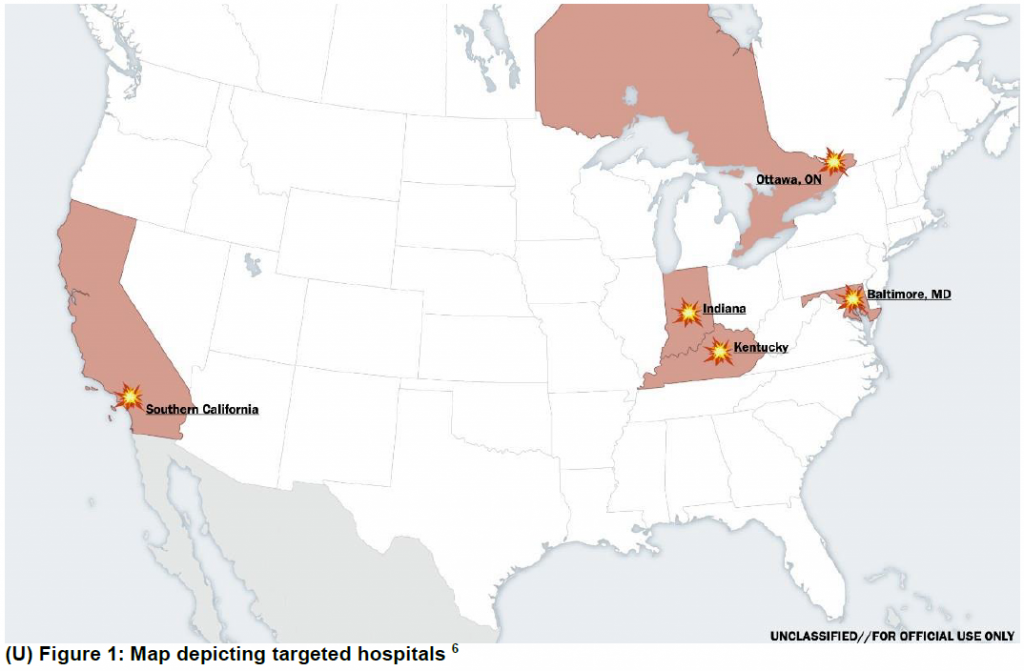
(U//FOUO) Recent incidents in the United States, Canada, and New Zealand, however, indicate that hospitals and healthcare providers could become victims. There have been six reported ransomware attacks on healthcare organizations in the United States, affecting at least 16 hospitals during the first four months of 2016.
(U) End-user training and education about cybersecurity, threats such as ransomware, and systems vulnerabilities could mitigate such attacks in the future.
…
(U//FOUO) The healthcare sector has been a desirable target for hackers due to the sensitive nature of patient information contained in their systems. The stakes are very high in the healthcare industry because any disruption in operations and care can have significant repercussions for patients. As such, this industry offers an ideal victim for ransomware, and these attacks are likely to continue—disrupting employee access to important documents and patient data and hampering the ability to provide critical services—creating a public safety concern.
(U//FOUO) Locky will likely decline in the coming months as a new ransomware strain known as SamSam begins to emerge. According to researchers, SamSam, which exploits server vulnerabilities to spread across and infect enterprise networks, may be a precursor to a new generation of ransomware known as “cryptoworms.” Cryptoworms are predicted to penetrate networks through previously known vulnerabilities, blending modern network intrusion tactics based off SamSam with past computer worms that targeted unpatched server vulnerabilities, such as the Conficker and SQL Slammer worms. Organizations that operate on typically less-secure networks should remain especially diligent in prevention efforts.
…
Department Of Home Security Immigration, Department Of Home Security Jobs, Department Of Home Security Usa, Department Of Home Security German Shepherd, Department Of Home Security Form I-9, Department Of Home Security Uscis, Department Of Home Security Uk, Department Of Home Affairs Security Guards Jobs, Us Department Of Home Security Esta, Indiana Department Of Home Security, Department Of Home And Security, Department Of Home Affairs Security Guards Jobs, Department Of Homeland Security Address, Ministry Of Home Affairs Internal Security Department, Un Department Of Safety And Security Home, Department Of Economic Security Bethany Home Road, Department Of Economic Security Bethany Home, When Was The Department Of Homeland Security Created, Department Of Home Security Jobs, Department Of Homeland Security Definition, What Does The Department Of Homeland Security Do, Us Department Of Home Security Esta, Department Of Economic Security Bethany Home Road, Department Of Economic Security Bethany Home, Department Of Home Security Form I-9, Department Of Home Security Formula, Department Of Homeland Security Formular, Department Of Home Security German Shepherd, Department Of Home Affairs Security Guards Jobs, Department Of Home Land Security.gov, Department Of Homeland Security Home Page, Microsoft Home Use Program Department Of Homeland Security, Department Of Home Security Immigration, Department Of Home Security Form I-9, Indiana Department Of Home Security, Ministry Of Home Affairs Internal Security Department, Texas Department Of Insurance Home Security Inspection, Security Jobs In Department Of Home Affairs, Department Of Homeland Security, Department Of Home Security Jobs, Department Of Home Affairs Security Jobs, Department Of Homeland Security, Department Of Homeland Security Jobs, Department Of Homeland Security Address, Department Of Homeland Security Definition, Homeland Security Department Of Immigration, Department Of Homeland Security Mission, Department Of Homeland Security Shutdown, Department Of Home Lance Security, Indiana Department Of Homeland Security, What Does The Department Of Homeland Security Do, Department Of Homeland Security Mission, Ministry Of Home Affairs Internal Security Department, Department Of Economic Security On Bethany Home, Ministry Of Home Affairs Department Of Internal Security, Department Of Homeland Security Home Page, Department Of Economic Security Bethany Home Road, Department Of Home Security German Shepherd, Department Of Homeland Security Shutdown, U.s Department Of Home Security, Un Department Of Safety And Security Home, The Department Of Home Security, Texas Department Of Insurance Home Security Inspection, What Does The Department Of Homeland Security Do, When Was The Department Of Homeland Security Created, Department Of Home Security Us Citizenship And Immigration Services, Department Of Home Security Usa, Department Of Home Security Uscis, Department Of Home Security Uk, Us Department Of Home Security Esta, Us Department Of Home Security Website, Un Department Of Safety And Security Home, Department Of Home Affairs Security Vacancies, Us Department Of Home Security Website, Department Of Homeland Security, What Does The Department Of Homeland Security Do, When Was The Department Of Homeland Security Created, Ransomware Protection, Ransomware Virus, Ransomware Attack, Ransomware News, Ransomware Removal, Ransomware 2017, Ransomware As A Service, Ransomware Mac, Ransomware Patch, Ransomware Statistics 2017, Ransomware Attack, Ransomware As A Service, Ransomware Attacks 2016, Ransomware Attack 2017, Ransomware Android, Ransomware Attacks In Usa, Ransomware Articles, Ransomware Attacks 2017 Wiki, Ransomware Apple, Ransomware And Healthcare, Ransomware Bitcoin, Ransomware Blocker, Ransomware Builder, Ransomware Best Practices, Ransomware Business, Ransomware Blog, Ransomware Background, Ransomware Backup, Ransomware Breach, Ransomware Bbc, Ransomware Cost, Ransomware Cases, Ransomware Cry, Ransomware Checker, Ransomware Customer Service, Ransomware Cerber, Ransomware Cisco, Ransomware Code, Ransomware Case Study, Ransomware Cnn, Ransomware Decryptor, Ransomware Download, Ransomware Definition, Ransomware Detection, Ransomware Decrypt Tool, Ransomware Definition Computer, Ransomware Defense, Ransomware Defender, Ransomware Dropbox, Ransomware Data Recovery, Ransomware Extensions, Ransomware Example, Ransomware Epidemic, Ransomware Email, Ransomware Encryption, Ransomware Encrypted Files, Ransomware Explained, Ransomware Ecmc, Ransomware Email Example, Ransomware Education, Ransomware Fix, Ransomware Fbi, Ransomware Facts, Ransomware File Decryptor, Ransomware Free, Ransomware For Dummies, Ransomware Families, Ransomware For Mac, Ransomware Facts 2017, Ransomware File Extensions List, Ransomware Hospital, Ransomware Healthcare, Ransomware History, Ransomware Hack, Ransomware Hackers, Ransomware Help, Ransomware Hero, Ransomware Hospital 2017, Ransomware Hacker Caught, Ransomware Hipaa, Ransomware Insurance, Ransomware Iphone, Ransomware Images, Ransomware Infographic, Ransomware In Healthcare, Ransomware Icon, Ransomware Identifier, Ransomware Is An Anonymous Digital Encrypted Currency, Ransomware In The News, Ransomware Incident Response Plan, Ransomware Jaff, Ransomware Jigsaw, Ransomware Javascript, Ransomware Jokes, Ransomware June 2017, Ransomware Java, Ransomware Jail, Ransomware Japan, Ransomware Juniper, Ransomware Jpg, Ransomware Kaspersky, Ransomware Kill Switch, Ransomware Keys, Ransomware Kill Chain, Ransomware Kb, Ransomware Kit, Ransomware Keys Released, Ransomware Kaiser, Ransomware Killer, Ransomware Korea, Ransomware List, Ransomware Linux, Ransomware Locky, Ransomware Law Firm, Ransomware Logo, Ransomware Losses 2016, Ransomware Laws, Ransomware Latest News, Ransomware Latest, Ransomware League Of Legends, Ransomware Mac, Ransomware Meaning, Ransomware Microsoft Patch, Ransomware Microsoft, Ransomware Meme, Ransomware Message, Ransomware Mcafee, Ransomware May 2017, Ransomware Map, Ransomware Mitigation, Ransomware News, Ransomware Names, Ransomware Nsa, Ransomware Nhs, Ransomware Netflix, Ransomware Norton, Ransomware Note, Ransomware Npr, Ransomware Numbers, Ransomware Negotiation, Ransomware On Mac, Ransomware On Iphone, Ransomware On The Rise, Ransomware Outbreak, Ransomware On Ipad, Ransomware Onedrive, Ransomware On Linux, Ransomware On Android, Ransomware Origin, Ransomware Onion, Ransomware Protection, Ransomware Patch, Ransomware Patch Microsoft, Ransomware Prevention, Ransomware Popup, Ransomware Playbook, Ransomware Policy, Ransomware Payment, Ransomware Pdf, Ransomware Phishing, Ransomware Removal, Ransomware Recovery, Ransomware Removal Windows 10, Ransomware Reddit, Ransomware Response Plan, Ransomware Removal Tools, Ransomware Report, Ransomware Rdp, Ransomware Research Paper, Ransomware Research, Ransomware Statistics 2017, Ransomware Statistics, Ransomware Scanner, Ransomware Statistics 2016, Ransomware Screenshot, Ransomware Source Code, Ransomware Solutions, Ransomware Simulator, Ransomware Samples, Ransomware Symptoms, Ransomware Tracker, Ransomware Types, Ransomware Trends, Ransomware Tabletop Exercise, Ransomware Timeline, Ransomware Training, Ransomware Test, Ransomware Tools, Ransomware Threat, Ransomware Trend Micro, Ransomware Update, Ransomware Uk, Ransomware United States, Ransomware User Education, Ransomware Usa, Ransomware Ups, Ransomware Unlocker, Ransomware University, Ransomware Usa Today, Ransomware Update For Xp, Ransomware Virus, Ransomware Virus Removal, Ransomware Variants, Ransomware Virus 2017, Ransomware Victims, Ransomware And Malware, Ransomware Video, Ransomware Variants List, Ransomware Vectors, Ransomware Vaccine, Ransomware Wanna Cry, Ransomware Wiki, Ransomware Windows Update, Ransomware What To Do, Ransomware Windows 10, Ransomware Windows 7, Ransomware Worm, Ransomware Windows, Ransomware Windows Patch, Ransomware Windows Xp, Ransomware Xp Patch, Ransomware Xp, Ransomware Xp Patch Download, Ransomware Xbox, Ransomware Xdata, Ransomware X3m, Ransomware Xp Only, Ransomware Xp Patch Microsoft, Ransomware Xp Patch Link, Ransomware Xp Download, Ransomware Youngstown







You must be logged in to post a comment.