Become a Patron!
True Information is the most valuable resource and we ask you to give back.
Earlier this week, a group or an individual called the Shadow Brokers published a large set of files containing the computer code for hacking tools. They were said to be from the Equation Group, which is considered part of the NSA’s hacking division TAO.
The leak got quite some media attention, but so far it was not related to some earlier leaks of highly sensitive NSA documents. These show interesting similarities with the Shadow Brokers files, which were also not attributed to Edward Snowden, but seem to come from an unknown second source.
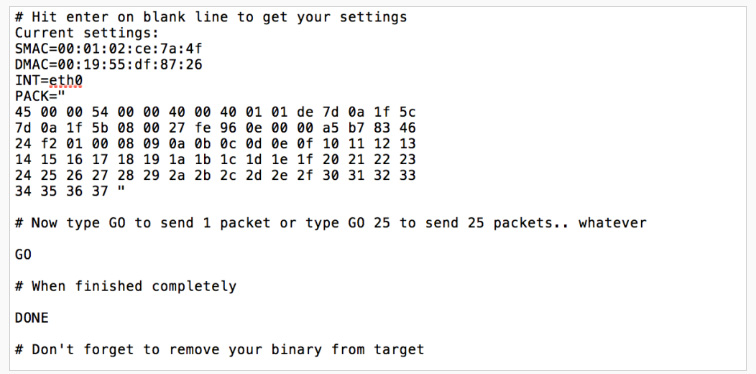
Screenshot of some computer code with instructions
from the Shadow Brokers archive
The Shadow Brokers files
Since August 13, the ShadowBrokers posted a manifesto and two large encrypted files on Pastebin, on GitHub, on Tumblr and on DropBox (the latter three closed or deleted meanwhile).
One of the encrypted files could be decrypted into a 301 MB archive containing a large number of computer codes for server side utility scripts and exploits for a variety of targets like firewalls from Cisco, Fortinet and Shaanxi. The files also include different versions of several implants and instructions on how to use them, so they’re not only the malware that could have been found on the internet, but also files that were only used internally.
A full list of the exploits in this Shadow Brokers archive can be found here.
https://musalbas.com/2016/08/16/equation-group-firewall-operations-catalogue.html
Security experts as well as former NSA employees considered the files to be authentic, and earlier today the website The Intercept came with some unpublished Snowden documents that confirm the Shadow Brokers files are real.
Besides the accessible archive, Shadow Brokers also posted a file that is still encrypted, and for which the key would only be provided to the highest bidder in an auction. Would the auction raise 1 million bitcoins (more than 500 million US dollars), then Shadow Brokers said they would release more files to the public. This auction however is likely just meant to attract attention.
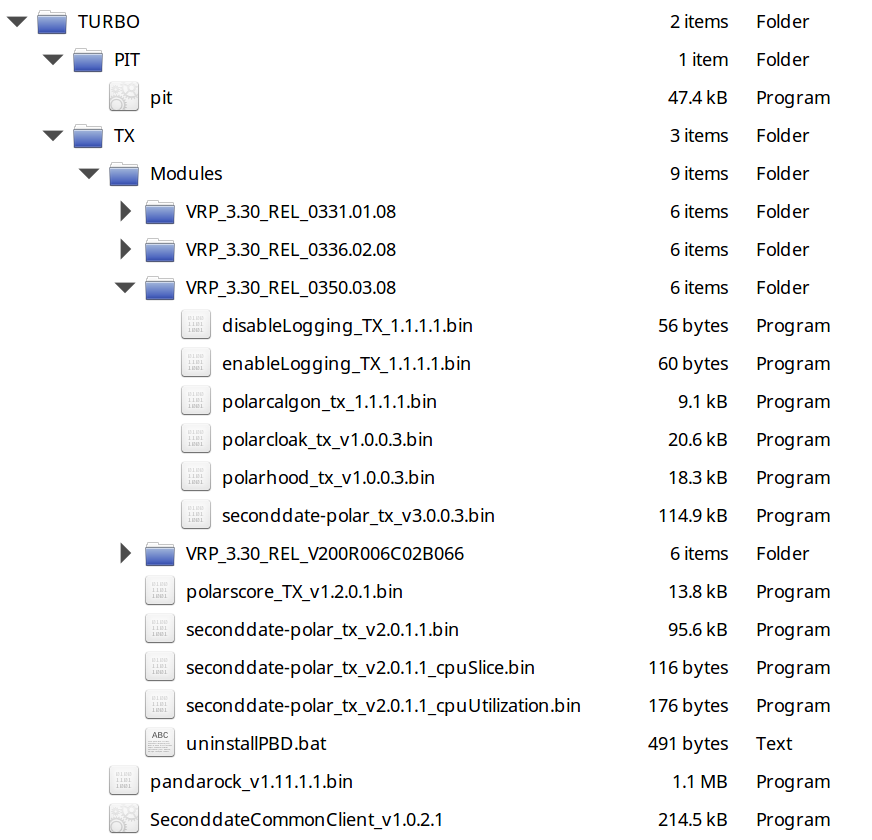
Screenshot of a file tree from the Shadow Brokers archive
From the Snowden documents?
According to security experts Bruce Schneier and Nicholas Weaver the new files aren’t from the Snowden trove. Like most people, they apparently assume that Snowden took mostly powerpoint presentations and internal reports and newsletters, but that’s not the whole picture. The Snowden documents also include various kinds of operational data, but this rarely became public.
Most notable was a large set of raw communications content collected by NSA under FISA and FAA authority, which also included incidentally collected data from Americans, as was reported by The Washington Post on July 5, 2014. The Snowden documents also include technical reports, which are often very difficult to understand and rarely provide a newsworthy story on their own.
Someone reminded me as well that in January 2015, the German magazine Der Spiegel published the full computer code of a keylogger implant codenamed QWERTY, which was a component of the NSA’s WARRIORPRIDE malware framework. So with the Snowden trove containing this one piece of computer code, there’s no reason why it should not contain more.
Contradicting the option that the Shadow Brokers files could come from Snowden is the fact that some of the files have timestamps as late as October 18, 2013, which is five months after Snowden left NSA. Timestamps are easy to modify, but if they are authentic, then these files have to be from another source.
A second source?
This brings us to a number of leaks that occured in recent years and which were also not attributed to Snowden. These leaks involved highly sensitive NSA files and were often more embarrassing than stuff from the Snowden documents – for example the catalog of hacking tools and techniques, the fact that chancellor Merkel was targeted and intelligence reports proving that NSA was actually successful at that.
> See Leaked documents that were not attributed to Snowden
It is assumed that these and some other documents came from at least one other leaker, a “second source” besides Snowden, which is something that still not many people are aware of. The files that can be attributed to this second source have some interesting similarities with the Shadow Brokers leak. Like the ANT catalog published in December 2013, they are about hacking tools and like the XKEYSCORE rules published in 2014 and 2015 they are internal NSA computer code.
This alone doesn’t say much, but it’s the choice of the kind of files that makes these leaks look very similar: no fancy presentations, but plain technical data sets that make it possible to identify specific operations and individual targets – the kind of documents many people are most eager to see, but which were rarely provided through the Snowden reporting.
As mainstream media became more cautious in publishing such files, it is possible that someone who also had access to the Snowden cache went rogue and started leaking documents just for harming NSA and the US – without attributing these leaks to Snowden because he would probably not approve them, and also to suggest that more people followed Snowden’s example.
Of course the Shadow Brokers leak can still be unrelated to the earlier ones. In that case it could have been that an NSA hacker mistakenly uploaded his whole toolkit to a server outside the NSA’s secure networks (also called a “staging server” or “redirector” to mask his true location) and that someone was able to grab the files from there – an option Snowden also seems to favor.
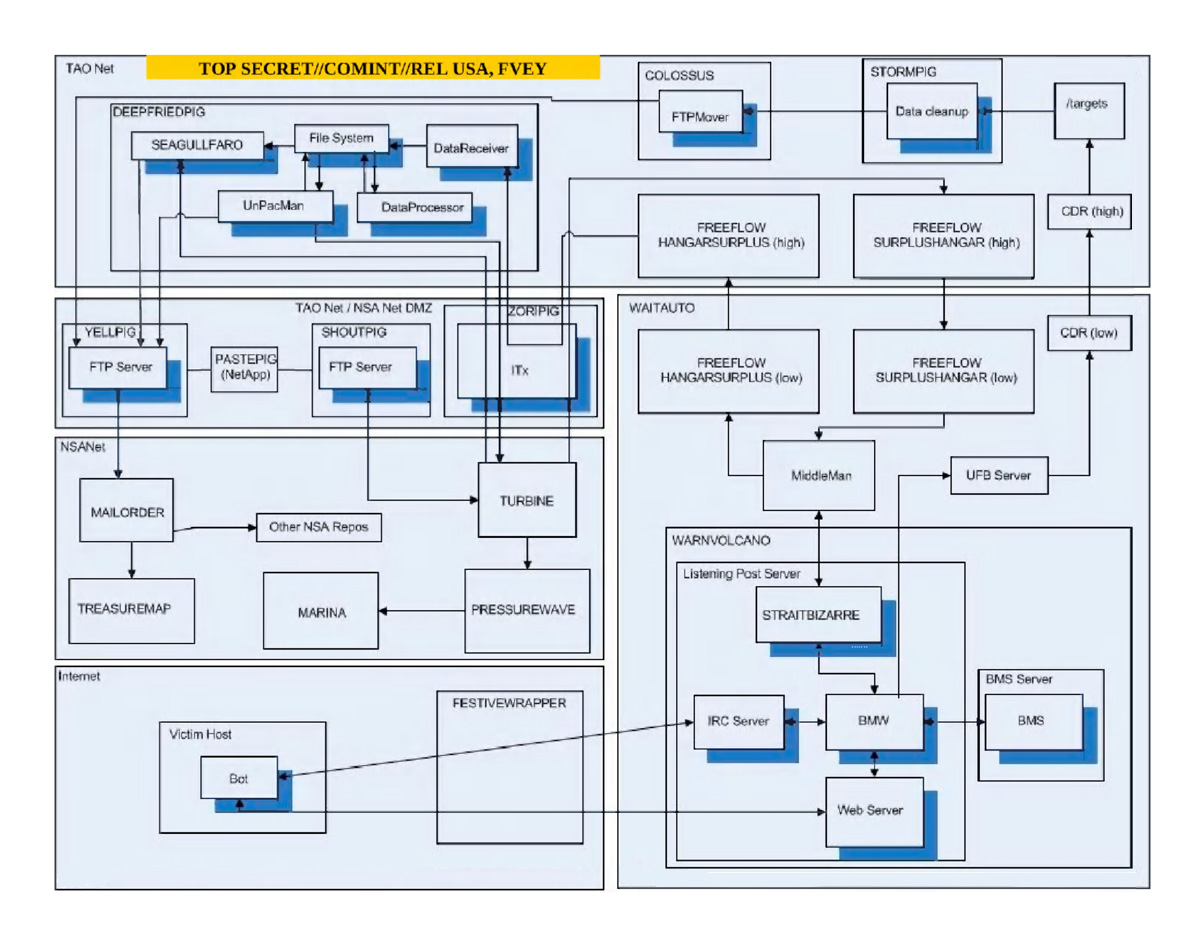
Diagram showing the various stages and networks involved
in botnet hacking operations by NSA’s TAO division
An insider?
Meanwhile, several former NSA employees have said that the current Shadow Brokers leak might not be the result of a hack from the outside, but that it’s more likely that the files come from an insider, who stole them like Snowden did earlier.
Of course it’s easier for an insider to grab these files than for a foreign intelligence agency, let alone an ordinary hacker, to steal them from the outside. But if that’s the case, it would mean that this insider would still be able to exfiltrate files from NSA premises (something that shouldn’t be possible anymore after Snowden), and that this insider has the intent to embarrass and harm the NSA (Snowden at least said he just wanted to expose serious wrongdoings).
Here we should keep in mind that such an insider is not necessarily just a frustrated individual, but can also be a mole from a hostile foreign intelligence agency.
Russian intelligence?
On Twitter, Edward Snowden said that “Circumstantial evidence and conventional wisdom indicates Russian responsibility”, but it’s not clear what that evidence should be. It seems he sees this leak as a kind of warning from the Russians not to take revenge for the hack of the Democratic National Committee (DNC) e-mails, which was attributed to Russian intelligence.
This was also what led Bruce Schneier to think it might be the Russians, because who other than a state actor would steal so much data and wait three years before publishing? Not mentioned by Schneier is that this also applies to the documents that can be attributed to the second source: they are also from before June 2013.
A related point of speculation is the text that accompanied the Shadow Brokers files, which is in bad English, as if it was written by a Russian or some other non-western individual. This is probably distraction, as it looks much more like a fluent American/English speaker who tried to imitate unexperienced English.
The text also holds accusations against “Elites”, in a style which very much resembles the language used by anarchist hacker groups, but that can also be faked to distract from the real source.

Screenshot of some file folders from the Shadow Brokers archive
Conclusion
With the authenticity of the Shadow Brokers files being confirmed, the biggest question is: who leaked them? There’s a small chance that it was a stupid accident in which an NSA hacker uploaded his whole toolkit to a non-secure server and someone (Russians?) found it there.
Somewhat more likely seems the option that they came from an insider, and in that case, this leak doesn’t stand alone, but fits into a series of leaks in which, since October 2013, highly sensitive NSA data sets were published.
So almost unnoticed by the mainstream media and the general public, someone was piggybacking on the Snowden-revelations with leaks that were often more embarrassing for NSA than many reportings based upon the documents from Snowden.
Again, obtaining such documents through hacking into highly secured NSA servers seems less likely than the chance that someone from inside the agency took them. If that person was Edward Snowden, then probably someone with access to his documents could have started his own crusade against NSA.
If that person wasn’t Snowden, then it’s either another NSA employee who was disgruntled and frustrated, or a mole for a hostile foreign intelligence agency. For an individual without the protection of the public opinion like Snowden, it must be much harder and riskier to conduct these leaks than for a foreign state actor.
Former NSA counterintelligence officer John Schindler also thinks there could have been a (Russian) mole, as the agency has a rather bad track record in finding such spies. If this scenario is true, then it would be almost an even bigger scandal than that of the Snowden-leaks.
Update:
On August 21, NSA expert James Bamford also confirmed that TAO’s ANT catalog wasn’t included in the Snowden documents (Snowden didn’t want to talk about it publicly though). Bamford favors the option of a second insider, who may have leaked the documents through Jacob Appelbaum and Julian Assange.
Nsa Jobs, Nsa Director, Nsa Softball, Nsa Meaning, Nsa Careers, Nsa Definition, Nsa Headquarters, Nsa Surveillance, Nsa Spying, Nsa Internships, Nsa Acronym, Nsa Address, Nsa Advisor, Nsa Agent, Nsa Alabama, Nsa Annapolis, Nsa Agent Salary, Nsa Arc, Nsa Approved Shredders, Nsa Agreement, Nsa Building, Nsa Bahrain, Nsa Budget, Nsa Bethesda, Nsa Baseball, Nsa Badge, Nsa Benefits, Nsa Building Nyc, Nsa Budget 2016, Nsa Backdoor, Nsa Careers, Nsa Chief, Nsa Colorado, Nsa Crane, Nsa Cyber Security, Nsa Conference, Nsa Csfc, Nsa Cae, Nsa Crypto Challenge, Nsa Css, Nsa Director, Nsa Definition, Nsa Data Center, Nsa Day Of Cyber, Nsa Director Salary, Nsa Data Collection, Nsa Domestic Surveillance, Nsa Datasheet, Nsa Deputy Director, Nsa Datasheet Is Called, Nsa Employment, Nsa Edward Snowden, Nsa Exploits, Nsa Employees, Nsa Email, Nsa Evaluated Products List, Nsa Echelon, Nsa Emblem, Nsa Encryption, Nsa Eternal Blue, Nsa Fastpitch, Nsa Florida Youth, Nsa Fort Meade, Nsa Flynn, Nsa Florida, Nsa Friend, Nsa Facebook, Nsa Fort Gordon, Nsa Foia, Nsa Facts, Nsa Georgia, Nsa Glassdoor, Nsa Government, Nsa Grindr, Nsa Github, Nsa Gift Shop, Nsa Game, Nsa Grants, Nsa Gif, Nsa Guy, Nsa Headquarters, Nsa Head, Nsa Hacking Tools, Nsa Hawaii, Nsa Hampton Roads, Nsa Hacked, Nsa History, Nsa Hiring Process, Nsa Hacking Tools Leaked, Nsa Headquarters Address, Nsa Internships, Nsa Industries, Nsa Intelligence Analyst, Nsa Indiana, Nsa Influence 2017, Nsa Iad, Nsa Ias 2017, Nsa India, Nsa Illinois, Nsa Insurance, Nsa Jobs, Nsa Juice Plus, Nsa Job Openings, Nsa Jobs Utah, Nsa Jobs Salary, Nsa Jokes, Nsa Job Requirements, Nsa Jurisdiction, Nsa Jobs In Md, Nsa Japan, Nsa Keywords, Nsa Kunia, Nsa Kc, Nsa Key, Nsa Kentucky, Nsa Kmi, Nsa Kankakee, Nsa Korea, Nsa Kaspersky, Nsa Keith Alexander, Nsa Leaker, Nsa Logo, Nsa Leak, Nsa Locations, Nsa Listening, Nsa Leader, Nsa Login, Nsa Leadership, Nsa Language Analyst, Nsa Leaked Tools, Nsa Meaning, Nsa Meme, Nsa Media, Nsa Meet, Nsa Mid South, Nsa Mike Rogers, Nsa Museum, Nsa Mcmaster, Nsa Maryland, Nsa Mission Statement, Nsa News, Nsa Naples, Nsa Name Generator, Nsa North, Nsa Number, Nsa Norfolk, Nsa Nyc, Nsa Nashville, Nsa Nursing, Nsa New Orleans, Nsa Orlando, Nsa Opm Test, Nsa Online Test, Nsa Offices, Nsa Obama, Nsa Organization, Nsa Operational Interview, Nsa Only, Nsa Org Chart, Nsa Of 1947, Nsa Prism, Nsa Police, Nsa Panama City, Nsa Police Officer, Nsa Phone Number, Nsa Philadelphia, Nsa Pay Scale, Nsa Play, Nsa Polygraph, Nsa Purpose, Nsa Quantum Computer, Nsa Quotes, Nsa Qualifications, Nsa Quantum, Nsa Quizlet, Nsa Questions, Nsa Qualifier, Nsa Quantum Computer Farm, Nsa Quartet, Nsa Quiz, Nsa Rogers, Nsa Requirements, Nsa Rules, Nsa Recruiting, Nsa Relationship, Nsa Rule Book, Nsa Ransomware, Nsa Russia, Nsa Responsibilities, Nsa Reno, Nsa Softball, Nsa Surveillance, Nsa Spying, Nsa Slang, Nsa Salary, Nsa Stands For, Nsa Soccer, Nsa Softball Rules, Nsa Scholarship, Nsa Scandal, Nsa Texas, Nsa Tournaments, Nsa Tools, Nsa Trump, Nsa Tao, Nsa Tools Leaked, Nsa Twitter, Nsa Tinder, Nsa Test, Nsa Training, Nsa Utah, Nsa Urban, Nsa Usa, Nsa Utah Facility, Nsa Unmasking, Nsa Utah Jobs, Nsa Unconstitutional, Nsa Umpire, Nsa Under Obama, Nsa Uniform, Nsa Vs Cia, Nsa Visitor Center, Nsa Virginia, Nsa Vs Fbi, Nsa Vs Cia Vs Fbi, Nsa Virus, Nsa Visitor Control Center, Nsa Vpn, Nsa Vanilla, Nsa Violation Of Privacy, Nsa Wiki, Nsa Whistleblower, Nsa Washington, Nsa Wiretapping, Nsa Website, Nsa Water Filter, Nsa Watchlist, Nsa World Series, Nsa Wikileaks, Nsa Wannacry, Nsa Xkeyscore, Nsa Xbox One, Nsa Xeno World Qualifier, Nsa Xkeyscore Download, Nsa Xcode, Nsa Xbox Live, Nsa Xeno Tournament, Nsa Xkeyscore Presentation, Nsa X, Nsa X Files, Nsa Youtube, Nsa Yogurt, Nsa Young Investigator Grant, Nsa Youth Florida, Nsa Yearly Budget, Nsa Yottabyte, Nsa Youth Program, Nsa Youth, Nsa Yellow Dots, Nsa Yakima, Nsa Zero Day, Nsa Zip Code, Nsa Zeus, Nsa Zimmermann Telegram, Nsa Zimbabwe, Nsa Za, Nsa Zero Day Exploit, Nsa Zyxel, Nsa Zero Division, Nsa Zone Store, Shadow Broker Dlc, Shadow Broker Mass Effect, Shadow Broker Vulnerability, Shadow Broker Nsa, Shadow Broker Dossiers, Shadow Broker Mass Effect 2, Shadow Broker Download, Shadow Broker Ship, Shadow Broker Tools, Shadow Brokers Leak, Shadow Broker Attack, Shadow Broker Andromeda, Shadow Broker Achievements, Shadow Broker After Beating Game, Shadow Broker Agent, Shadow Broker Adalah, Shadow Broker Analysis, Shadow Broker Agent Mass Effect 2, Shadow Broker Arrested, Shadow Broker Archive, Shadow Broker Base, Shadow Broker Base Investment Opportunities, Shadow Broker Book, Shadow Broker Boss Fight, Shadow Broker Before Or After, Shadow Broker Bug, Shadow Broker Base Model, Shadow Brokers Bbc, Shadow Broker Blog, Shadow Broker Base Video Archive, Shadow Broker Crash, Shadow Broker Cve, Shadow Broker Cisco, Shadow Broker Cyber Attack, Shadow Broker Cerberus, Shadow Broker Cyber Threat, Shadow Broker Comments, Shadow Broker Cyber Security, Shadow Broker Comments Squadmates, Shadow Broker Companion Comments, Shadow Broker Dlc, Shadow Broker Dossiers, Shadow Broker Download, Shadow Broker Definition, Shadow Brokers Dump, Shadow Broker Dlc Crash, Shadow Broker Dlc Review, Shadow Broker Dlc Ps3, Shadow Broker Dlc Glitch, Shadow Broker Dlc Cost, Shadow Broker Exploits, Shadow Broker Eternal Blue, Shadow Broker Exploit List, Shadow Broker Equation Group, Shadow Broker Eternal Champion, Shadow Broker Exploits Download, Shadow Broker Effects On Mass Effect 3, Shadow Broker Ending, Shadow Broker Mass Effect 2, Shadow Broker Mass Effect, Shadow Broker Files, Shadow Broker Fight, Shadow Broker Fuzzbunch, Shadow Broker Files Garrus, Shadow Broker Framework, Shadow Broker Fb.py, Shadow Broker Facebook, Shadow Broker Forces Mass Effect 3, Shadow Broker Free Download, Shadow Broker Files Legion, Shadow Broker Github, Shadow Broker Group, Shadow Broker Garrus, Shadow Broker Grunt, Shadow Broker Glitch, Shadow Broker Guide, Shadow Broker Dlc Glitch, Shadow Broker Mission Glitch, Shadow Broker After Beating Game, Cz Shadow Gunbroker, Shadow Broker Hack, Shadow Broker Hackers, Shadow Broker Hack Nsa, Shadow Broker Hug Liara, Shadow Broker Hack Terminals, Shadow Broker Hatch, Shadow Broker Dlc How To Start, Lair Of The Shadow Broker How To Start, Lair Of The Shadow Broker How Long, Lair Of The Shadow Broker Hours, Shadow Broker Investments, Shadow Broker Identity, Shadow Broker Information Terminals, Shadow Broker Pc, Shadow Broker Insanity, Shadow Broker Intel, Shadow Broker Illusive Man, Shadow Broker Ilium, Shadow Broker In Underworld Empire, Giving Shadow Broker Info Cerberus, Shadow Brokers June, Shadow Brokers Juniper, Shadow Brokers July, Shadow Brokers June Dump, Shadow Brokers January, Shadow Brokers June Release, Shadow Brokers June 2017, Shadow Brokers Join, Shadow Broker Jack, Shadow Broker Jak Zainstalowa\u0107, Shadow Broker Kb, Shadow Broker Kahoku, Shadow Broker Keeps Crashing, Liara Shadow Broker Kiss, Shadow Broker Who To Kill, Kasumi Shadow Broker Dossier, Lair Of The Shadow Broker Key, Lair Of The Shadow Broker Keygen, Shadow Broker Leaks, Shadow Broker Liara, Shadow Broker Legion, Shadow Broker Logs, Shadow Brokers Lost In Translation, Shadow Brokers Linux, Shadow Broker List, Shadow Brokers Leak Download, Shadow Brokers Letter To Trump, Shadow Brokers List Of Exploits, Shadow Broker Mass Effect, Shadow Broker Mass Effect 2, Shadow Broker Mass Effect 1, Shadow Broker Malware, Shadow Broker Meaning, Shadow Broker Microsoft, Shadow Broker Microsoft Patch, Shadow Broker Ms17-010, Shadow Broker Morinth, Shadow Broker Model Ship, Shadow Broker Nsa, Shadow Broker News, Shadow Brokers Nsa Tools, Shadow Brokers Nsa Tools Download, Shadow Brokers Nsa Hack, Shadow Brokers Nsa Leaks, Shadow Brokers Nsa Hacking Tools, Shadow Brokers North Korea, Shadow Brokers New Release, Shadow Brokers Nytimes, Shadow Broker Observer, Shadow Broker Oracle, Shadow Broker Oddjob, Shadow Broker Ost, Shadow Broker Investment Opportunities, Shadow Broker Before Or After, Shadow Broker Comments On Squad, Shadow Broker Effects On Mass Effect 3, Shadow Broker Door Wont Open, Origin Shadow Broker, Shadow Broker Patch, Shadow Broker Password, Shadow Broker Paragon Interrupt, Shadow Broker Planet, Shadow Broker Ps3, Shadow Broker Paragon, Shadow Broker Parking Lot, Shadow Broker Dlc Price, Shadow Broker Data Points, Liara Shadow Broker Paragon Interrupt, Shadow Broker Quotes, Shadow Broker Quest, Liara Shadow Broker Quest, Mass Effect Shadow Broker Quotes, Lair Of The Shadow Broker Quotes, Mass Effect 2 Shadow Broker Quotes, Shadow Broker Release, Shadow Broker Race, Shadow Broker Rdp, Shadow Broker Rdp Exploit, Shadow Broker Romance, Shadow Broker Reddit, Shadow Broker Ransomware, Shadow Broker Romance Liara, Shadow Broker Review, Shadow Broker Rapid7, Shadow Broker Ship, Shadow Broker Smb, Shadow Broker Species, Shadow Broker Smb Exploit, Shadow Broker Solaris, Shadow Broker Subscription, Shadow Broker Smb Vulnerability, Shadow Broker Ship Model, Shadow Broker Support Team, Shadow Broker Squad, Shadow Broker Tools, Shadow Broker Twitter, Shadow Broker Terminals, Shadow Broker Tool Dump, Shadow Broker Tali, Shadow Broker Tools Download, Shadow Broker Timeline, Shadow Broker Threat, Shadow Broker Toolkit, Shadow Broker Tutorial, Shadow Broker Unique Dialogue, Shadow Broker Upgrades, Shadow Broker Update, Shadow Broker Underworld Empire, Shadow Broker Upgrades Mass Effect 3, Shadow Broker Dlc Upgrades, Lair Of The Shadow Broker Unique Dialogue, Shadow Broker Dlc Not Showing Up, Underworld Shadow Broker, Lair Of The Shadow Broker Upgrade Locations, Shadow Broker Vulnerability, Shadow Broker Video Archive, Shadow Broker Virus, Shadow Broker Vs Illusive Man, Shadow Broker Voice, Shadow Broker Vasir, Shadow Broker Base Videos, Lair Of The Shadow Broker Vasir Bug, Shadow Broker Windows, Shadow Broker Wiki, Shadow Broker Wannacry, Shadow Broker Wikileaks, Shadow Broker Walkthrough, Shadow Broker Wet Squad, Shadow Broker Website, Shadow Broker Windows 2003, Shadow Broker Windows Exploit, Shadow Broker Windows 10, Shadow Broker Dlc Xbox, Lair Of The Shadow Broker Xbox 360, Shadow Broker Yahg, Shadow Broker Youtube, Shadow Broker Zero Day, Shadow Broker Zcash, Shadow Broker Zaeed, Shadow Broker Jak Zainstalowa\u0107