Become a Patron!
True Information is the most valuable resource and we ask you to give back.
The following study was released in two parts by the European Parliament Science and Technology Options Assessment (STOA) program earlier this month.
| Part 1 – Risks and opportunities raised by the current generation of network services and applications | 66 pages | Download |
| Part 1 – Annex 1 |
66 pages | Download (13.3 MB PDF) |
| Part 1 – Annex 2 |
66 pages | Download |
| Part 2 – Technology foresight, options for longer term security and privacy improvements | 80 pages | Download |
| Part 2 – Annex 1 | 100 pages | Download |
| Part 2 – Annex 2 |
4 pages | Download |
| Complete study and all appendices in a ZIP archive | Download (17.5 MB ZIP) |
The disclosure of controversial mass surveillance programmes by intelligence and national security agencies has evoked an international debate on the right of citizens to be protected from illegitimate or warrantless collection and analysis of their data and meta-data. This report aims at identifying what are the risks of data breaches for users of publicly available Internet services such as web browsing, email, social networks, cloud computing, or voice communications, via personal computers or mobile devices, and what are the possible impacts for the citizens and the European Information Society. In this context a clear distinction has to be made between data and meta-data. Also it must be differentiated between mass unwarranted and indiscriminate interception, and targeted lawful interception of Internet and telephony data for the purpose of law enforcement and crime investigation. While targeted lawful interception constitutes a necessary and legitimate instrument of intelligence and law enforcement agencies, mass surveillance is considered a threat to civil liberties such as the right to freedom of opinion and expression. These civil liberties are essential human rights in democratic societies and of particular importance for safeguarding independent journalism and political opposition.
Meta-data is data that is produced when electronic communication channels, like Internet or telephony are used and that provides information about the time, the origin the destination, the location, the duration and the frequency of communications carried out. Meta-data does, however, not contain the content of communications. Two types of meta-data exist, meta-data that provides data on the content (e.g. read/write/modify attributes of the file, author of the document, GPS location of a picture, etc.), and meta-data of the communication (e.g. sender, receiver, communication duration, communication starting date and time, communication channel, communication protocol used, etc.). In the context of this study, the cardinal interest lies on communication meta-data.
Communication meta-data is routinely gathered by telecom providers and Internet service providers as part of their business operations. Different laws and regulations exist in Europe and other countries that define the retention period of this data. The lawful interception of meta-data is targeted surveillance required by law enforcement authorities and is not considered as mass surveillance. The analysis of meta-data, despite the fact that it does not contain content, can reveal very detailed information about the person who has generated it.
Another potential source of information containing private data are Cookies. Cookies are text files that visited websites store on a user’s local disk. Cookies allow for smarter and faster navigation, and are commonly used for personalizing website content, as well as ads and features by associated third parties. No evidence has been found that government agencies are leveraging the information that can be inferred from the data contained in Cookies through collaboration with commercial tracking companies.
The structured nature of meta-data is ideally suited for analysis using data mining techniques such as pattern recognition, machine learning, and information or data fusion. Meta-data analysis can reveal an extraordinary amount of information about people’s habits and associations that when aggregated – data over time, or linked with other datasets – can expose even richer personal information and associational details. Unless special precautions are taken, few personal secrets of everyday life would withstand close analysis of meta-data.
Government agencies are intercepting meta-data either through their own technical capabilities, or accessing it through service providers on the basis of lawful requests, or under threat of fines. They also possess powerful capabilities to break system protections and to infiltrate systems and networks by applying advanced hard and software technology.
Commercial surveillance technology vendors are selling software applications and tools for surveillance purposes as advanced solutions for lawful communications data (including both metadata and content) interception, collection, processing and/or analysis. Clients are governments, intelligence organizations, national security and law enforcement agencies which use these intelligence platforms and tools for collecting, processing and analysing both, mass and targeted communications data.
The legal context for commercial surveillance technology vendors is defined in different national and international laws, agreements and regulations. The Wassenaar Agreement, a comprehensive international treaty on export controls, including surveillance technology and undersigned by 42 states, has been extended in 2013 to law enforcement/intelligence gathering tools and IP network surveillance systems or equipment. Notwithstanding, the report of the UN OHCHR of June 2014 states that in most states, legal standards are either non-existent or inadequate to deal with the modern communications surveillance environment.
But also national security agencies themselves have developed a number of highly sophisticated hard and software interception tools that enable them to penetrate networking equipment, monitor mobile phones and computers and divert or even modify data without being noticed.
A special focus in the endeavour of mass surveillance is on breaking encryption that may prevent access to relevant data for intelligence and law enforcement agencies. Software flaws in the implementation of encryption algorithms can lead to vulnerabilities which may be easily exploitable, regardless of the complexity, the theoretical strength or quality of the applied encryption technique. Security agencies have managed to exploit such vulnerabilities, allegedly by introducing backdoors in encryption standards, but have had only limited success with traditional cryptanalytic attacks. The new generation of encryption technology is proficient enough to avoid deterministic brute force attacks and provides the most reliable protection against unauthorized data access if its implementation and configuration parameters are well set up. Major attacks occur when implementations of current encryption technologies do not faithfully comply with their specifications, or when bugs and flaws – sometimes deliberately – are injected at code level. This is the reason for calling for a policy action that guarantees European citizens access to certified, resilient and open source implementations of different encryption specifications.
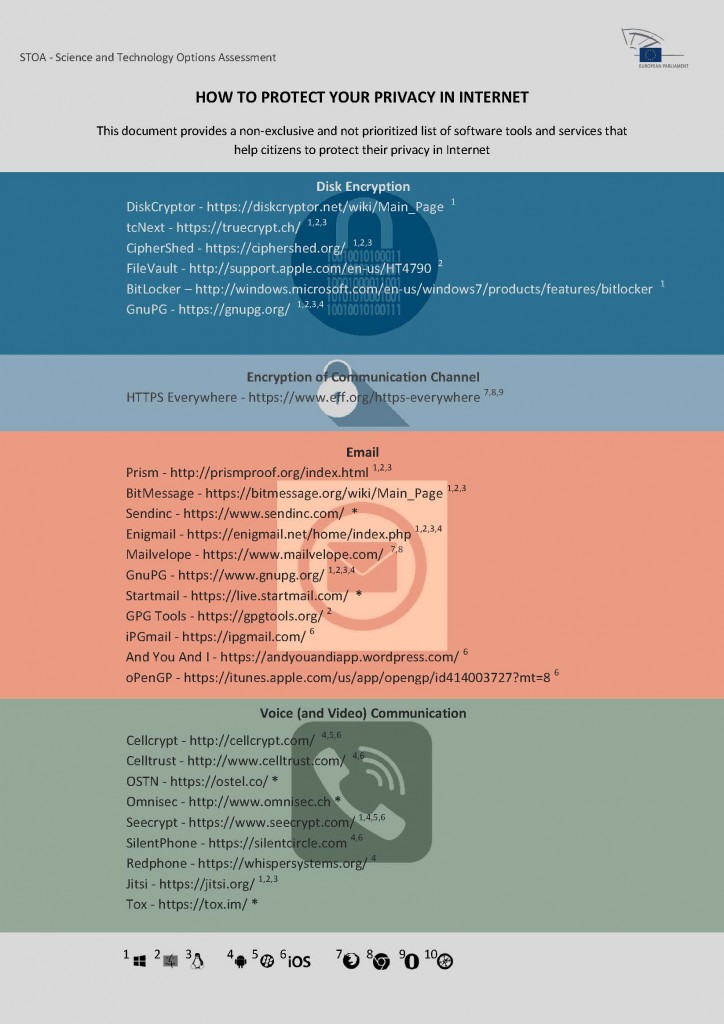
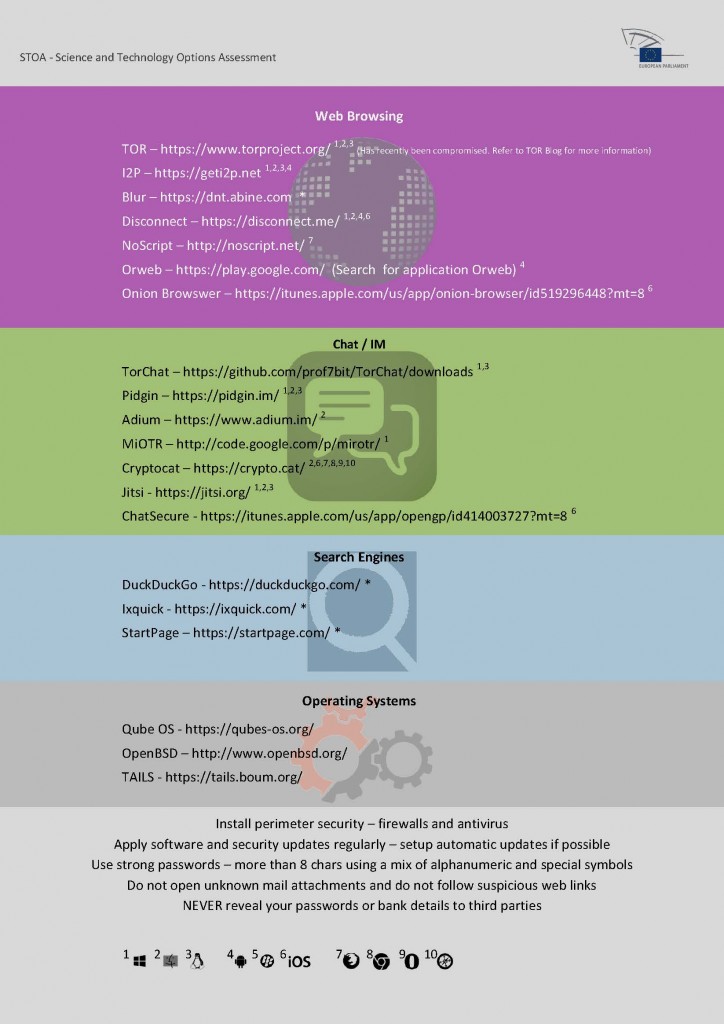
For an end user it is practically impossible to detect whether meta-data generated while navigating through the web, sending mails, or establishing other communications through Internet is being analysed or used by third parties and even less, if a system is subject to a complex attack orchestrated by powerful opponents like government agencies. Citizens can protect their privacy by applying safety conscious practices and using special software tools and services that help hiding their digital traces. Firewalls, anti-virus software, Virtual Private Networks, anonymizing proxies and networks and, most importantly, cryptography are technical means accessible to end users. But even though it is possible to hinder unauthorized access to private data or meta-data by applying a mix of different protection mechanisms, there is no means for guaranteeing total immunity against such attacks. Policy options that are considered of help in reducing the risk of privacy intrusion by mass surveillance in a short to mid-term timeframe are: a) the promotion of open source operating systems and applications that allow for constant inspection and scrutiny by a large community of experts and verification and validation bodies and b) investing in and stimulating the integration of user friendly, utility-like software solutions.
The threat posed by mass surveillance practices can however not be solved on a technical terrain. Intelligence and security agencies will always have a competitive advantage in winning a race for technological supremacy in Internet security due to the resources at their command. The problem needs to be addressed on a political level. An adequate balance between civil liberties and legitimate national security interests needs to be established, based on a public discussion that empowers citizens to decide upon their civil rights affected and the societal values at stake.
…
mass Mass Surveillance In The Us, Mass Surveillance Definition, Mass Surveillance Nsa, Mass Surveillance Programs, Mass Surveillance Pros, Mass Surveillance In America, Mass Surveillance Benefits, Mass Surveillance Debate, Mass Surveillance In Russia, Mass Surveillance Terrorism, Mass Surveillance And Terrorism, Mass Surveillance Articles, Mass Surveillance And Human Rights, Mass Surveillance After 9\/11, Mass Surveillance Australia, Mass Surveillance And Crime Prevention, Mass Surveillance And Privacy, Mass Surveillance And State Control, Mass Surveillance And Targeted Surveillance, Mass Surveillance And International Law, Mass Surveillance Benefits, Mass Surveillance Bbc, Mass Surveillance Bae, Mass Surveillance By Remote Control, Mass Surveillance By Country, Mass Surveillance Bad, Mass Surveillance Book, Mass Surveillance By Nsa, Mass Surveillance Bangladesh, Mass Blanket Surveillance, Mass Surveillance Cons, Mass Surveillance Companies, Mass Surveillance Countries, Mass Surveillance China, Mass Surveillance Canada, Mass Surveillance Conspiracy, Mass Surveillance Council Of Europe, Mass Surveillance Cases, Mass Surveillance Controversy, Mass Surveillance Chilling Effect, Mass Surveillance Definition, Mass Surveillance Debate, Mass Surveillance Does Not Work, Mass Surveillance Doesn’t Work, Mass Surveillance Disclosures, Mass Surveillance Documentary, Mass Surveillance Disadvantages, Mass Surveillance Democracy, Mass Surveillance Denmark, Mass Surveillance Data Retention Laws, Mass Surveillance Essay, Mass Surveillance Effectiveness, Mass Surveillance Ethics, Mass Surveillance Equipment, Mass Surveillance Examples, Mass Surveillance Echr, Mass Surveillance Europe, Mass Surveillance Eu, Mass Surveillance Evidence, Mass Surveillance Expropriation, Mass Surveillance Facts, Mass Surveillance France, Mass Surveillance Freedom Of Expression, Mass Surveillance Future, Mass Surveillance Facebook, Mass Surveillance Failure, Mass Surveillance Facial Recognition, Mass Surveillance Francais, Mass Surveillance Is Fundamental Threat To Human Rights, Mass Surveillance In Fiction, Mass Surveillance Good, Mass Surveillance Game, Mass Surveillance Good Or Bad, Mass Surveillance Guardian, Mass Surveillance Government, Mass Surveillance Germany, Mass Surveillance Google, Mass Surveillance Great Britain, Mass Surveillance Globally, Mass Surveillance Gone Too Far, Mass Surveillance History, Mass Surveillance Human Rights, Mass Surveillance Violates Human Rights, Mass Surveillance Against Human Rights, Mass Surveillance Threatens Human Rights, Mass Surveillance Nothing To Hide, Hacker News Mass Surveillance, Human Mass Surveillance, Mass Surveillance In The Us, Mass Surveillance In America, Mass Surveillance In Russia, Mass Surveillance In China, Mass Surveillance In North Korea, Mass Surveillance Is Good, Mass Surveillance In 1984, Mass Surveillance In The Uk, Mass Surveillance Isn’t The Answer To Fighting Terrorism, Mass Surveillance In India, Mass Surveillance Japan, Mass Surveillance Justified, Mass Surveillance Justification, Mass Surveillance Jokes, Mass Surveillance Journalists, Mass Surveillance Data Journalism, Mass Surveillance Is Not Justified, Mass Surveillance Kickstarter, Mass Surveillance North Korea, Mass Surveillance In The United Kingdom, Mass Surveillance In The Dark Knight, Mass Surveillance Laws, Mass Surveillance Leak, Mass Surveillance Legal, Mass Surveillance London, Mass Surveillance Legal Definition, Mass Surveillance Law France, Mass Surveillance Legal Framework, Mass Surveillance Laws Australia, Mass Surveillance Law Essay, Mass Surveillance International Law, Mass Surveillance Meaning, Mass Surveillance Method, Mass Surveillance Metadata, Mass Media Surveillance, Mass Mortality Surveillance, Mass Surveillance Silences Minority Opinions, Mass Surveillance In Malaysia, Mass Surveillance In Mexico, What Does Mass Surveillance Mean, Mozilla Mass Surveillance, Mass Surveillance Nsa, Mass Surveillance North Korea, Mass Surveillance New Zealand, Mass Surveillance Nz, Mass Surveillance News, Mass Surveillance Necessary, Mass Surveillance Necessity, Mass Surveillance Netherlands, Mass Surveillance Nothing To Hide, Mass Surveillance New York Times, Mass Surveillance Obama, Mass Surveillance Of Eu Citizens, Mass Surveillance On The Internet, Mass Surveillance Opinions, Mass Surveillance Online, Electronic Mass Surveillance Of Eu Citizens, Mass Surveillance Council Of Europe, Mass Surveillance Freedom Of Expression, Mass Surveillance Good Or Bad, Nsa Mass Surveillance Over, Mass Surveillance Programs, Mass Surveillance Pros, Mass Surveillance Pros And Cons, Mass Surveillance Privacy, Mass Surveillance Privacy International, Mass Surveillance Pdf, Mass Surveillance Programs International Law, Mass Surveillance Prism, Mass Surveillance Problems, Mass Surveillance Petition, Mass Surveillance Quotes, Mass Surveillance Questions, Mass Surveillance Reddit, Mass Surveillance Russia, Mass Surveillance Research, Mass Surveillance Right To Privacy, Mass Surveillance Report, Mass Surveillance Reasons, Mass Surveillance Ruled Illegal, Mass Surveillance Revelations, Mass Surveillance Resolution, Mass Surveillance Research Topics, Mass Surveillance Statistics, Mass Surveillance Synonym, Mass Surveillance Stops Terrorism, Mass Surveillance System, Mass Surveillance Solutions, Mass Surveillance Snowden, Mass Surveillance Software, Mass Surveillance Society, Mass Surveillance Sweden, Mass Surveillance Silencing Dissenting Opinions, Mass Surveillance Terrorism, Mass Surveillance Technology, Mass Surveillance Tools, Mass Surveillance Thesis, Mass Surveillance The Guardian, Mass Surveillance Timeline, Mass Surveillance Threatens Human Rights, Mass Surveillance Treaties, Mass Surveillance Transparency, Mass Surveillance In The Us, Mass Surveillance Usa, Mass Surveillance Uk, Mass Surveillance Uae, Mass Surveillance Un, Mass Surveillance Under International Law, End Mass Surveillance Under The Patriot Act, Mass Surveillance Statistics Uk, Uk Mass Surveillance Ruled Unlawful, Uk Mass Surveillance Plan, Uk Mass Surveillance Bill, Mass Surveillance Vs Targeted Surveillance, Mass Surveillance Violates Human Rights, Mass Surveillance Violates Privacy, Mass Surveillance Violation, Mass Surveillance Video Game, Mass Surveillance Vertaling, Mass Surveillance Vocabulary, Mass Video Surveillance Laws, Why Mass Surveillance Violates International Law, Vertaal Mass Surveillance, Mass Surveillance Works, Mass Surveillance Wiki, Mass Surveillance Worldwide, Does Mass Surveillance Work, Mass Surveillance Doesn’t Work, Mass Surveillance Is Wrong, Mass Surveillance In The World, Mass Surveillance Around The World, Why Mass Surveillance Is Bad, Why Mass Surveillance Is Good, Mass Surveillance Youtube, Mass Surveillance New York Times, Mass Surveillance New Zealand,



You must be logged in to post a comment.