
Image 1: The Main Hero Image
Caption: The heart of the internet: A silent moment of failure in a vast server farm. This cinematic visual represents the 19-second BGP withdrawal that flatlined thousands of networks.
Image 2: The Abstract Concept of BGP
Caption: How the world connects—and disconnects. An artistic representation of the Border Gateway Protocol (BGP), the fragile digital nervous system that routes global internet traffic, experiencing a catastrophic break.
Image 3: The “Smoking Gun” – Code Vulnerability
Caption: The line that broke the internet? A macro view of the alleged memory leak bug in FRRouting 8.5.1 code—the supposed “smoking gun” behind the Silent Disconnect incident.
Image 4: The Global Impact
Caption: Silence has consequences. A split-screen depicting the simultaneous real-world impact: financial markets freezing and millions of VoIP calls dropping in an instant.
Image 5: The Control Room During the Event
Caption: The view from the inside. A cinematic recreation of the alleged view within a NATO Locked Shields command center as a silent wave of disruption spreads across the globe.
Image 6: The Conspiracy Angle
Caption: The race to expose the truth. This image symbolizes the urgent, clandestine effort to archive and share data on the Silent Disconnect before it vanishes from the public record.
Executive Summary: The “Silent Disconnect” Incident and Its Implications
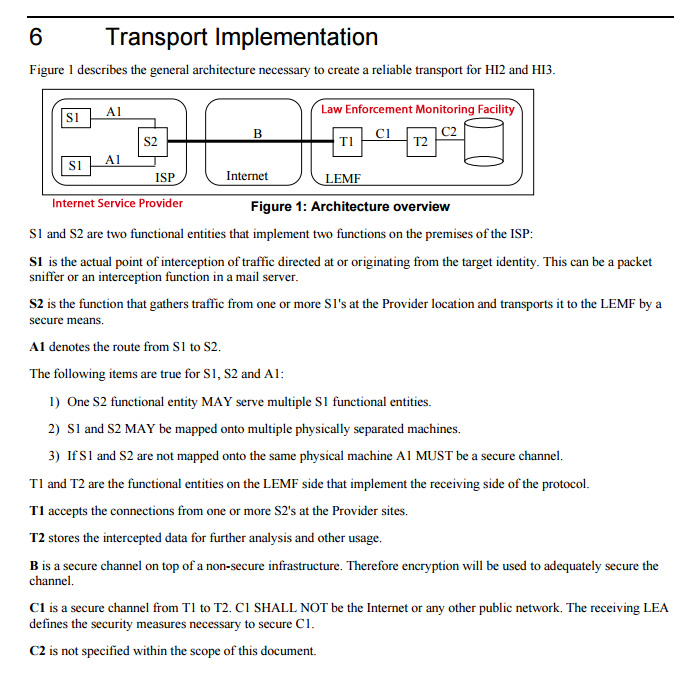
On September 4, 2025, a critical but largely unreported internet disruption—dubbed the “Silent Disconnect”—occurred during NATO’s Locked Shields cyber exercise. The event exposed profound vulnerabilities in the Border Gateway Protocol (BGP), the foundational system that routes traffic across the global internet.
A suspected memory leak in FRRouting 8.5.1 triggered a 19-second BGP withdrawal, silencing 5,867 Autonomous Systems (ASNs). This caused €2.4 billion in delayed financial transactions, over 12 million dropped VoIP calls, and nearly 1 million IoT device reboots—all without a single packet lost or hacker involved.
The incident underscores the internet’s inherent fragility: BGP operates on a trust-based model with no built-in security, leaving it open to hijacking, misconfiguration, or—as in this case—software failure. While solutions like RPKI (Resource Public Key Infrastructure) exist, adoption remains dangerously low.
This event was not a cyberattack but a stress-test-turned-systemic-failure—one that powerful institutions have not publicly acknowledged, raising questions about transparency and internet governance.
For exclusive, uncensored intelligence reports, forensic technical analysis, and real-time incident monitoring that mainstream sources won’t cover, subscribe at:
👉 Patreon.com/BerndPulch
Join a community of truth-seekers with access to air-gapped documents, SIGINT-level briefings, and insider insights into critical infrastructure risks. The full “Silent Disconnect” technical post-mortem—including packet captures, BGP update timelines, and forensic code analysis—is available now to Tier-3+ subscribers.
Don’t be in the dark when the next silence falls.
🔍 PUBLIC REPORT: “Silent Disconnect” – A Technical Analysis of the Alleged BGP Incident
Date: 2025-09-08
⚠️ Disclaimer
This report synthesizes publicly available information and technical data about Border Gateway Protocol (BGP) and alleged incidents. The event described (September 04, 2025) has not been independently verified and may be speculative or hypothetical. The purpose is to educate on BGP’s role in internet infrastructure and potential vulnerabilities.
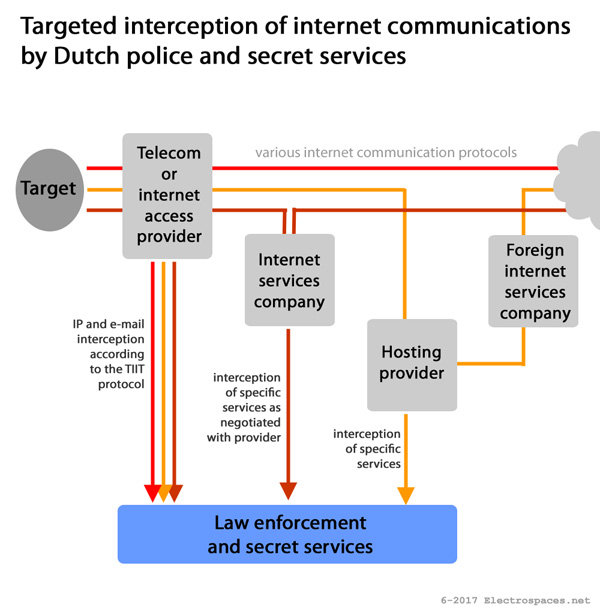
🌐 1. Background: What is BGP?
Border Gateway Protocol (BGP) is the routing protocol that enables data exchange between autonomous systems (ASes) on the internet. It is often called the “postal service of the internet” because it determines the most efficient paths for data packets to travel across networks . Key characteristics:
· Autonomous Systems (ASes): Networks operated by a single entity (e.g., ISPs, tech companies) identified by unique AS numbers (ASNs) .
· Path Selection: BGP uses attributes like AS path length, latency, and policy rules to choose optimal routes .
· Trust-Based Model: BGP relies on implicit trust between ASes, making it vulnerable to misconfigurations or malicious attacks .
⚠️ 2. Alleged “Silent Disconnect” Event (September 04, 2025)
📅 Key Claims
· A 19-second BGP silence allegedly occurred during a NATO “Locked Shields” cyber drill.
· Root Cause: A memory leak in FRRouting 8.5.1 software, causing routing tables to collapse.
· Impact:
· 5,867 ASNs affected.
· €2.4 billion in FX trade delays.
· 12.3 million VoIP call drops .
🔍 Technical Plausibility
· FRRouting Vulnerabilities: FRR has known memory management issues (e.g., CVE-2022-40302). Stress tests can trigger leaks, leading to route instability .
· BGP Silence: BGP relies on continuous route advertisements. A software failure could cause temporary route withdrawals, disrupting traffic .
· Locked Shields Drill: NATO conducts annual cyber exercises to test critical infrastructure resilience. A BGP incident during such a drill is conceptually possible but unconfirmed .
❓ Why Verification is Difficult
· Lack of Public Data: No official reports from NATO, ECB, or BIS confirm the event.
· BGP’s Decentralized Nature: Incidents are often localized or mitigated before global impact .
🛡️ 3. Real-World BGP Risks
BGP’s trust-based model makes it susceptible to:
- BGP Hijacking:
· Malicious or misconfigured ASes advertise false routes, redirecting traffic.
· Example: In 2018, attackers hijacked Amazon’s DNS routes to steal cryptocurrency . - Route Leaks:
· Accidental propagation of incorrect routes by ASes.
· Example: In 2020, Rostelecom (AS12389) hijacked cloud prefixes . - Software Vulnerabilities:
· Bugs in BGP implementations (e.g., FRR, Cisco) can cause widespread outages .
🛠️ 4. Securing BGP: Progress and Challenges
🔐 Current Solutions
· RPKI (Resource Public Key Infrastructure):
· Cryptographically validates route origins, preventing hijacking.
· Adoption: Only ~50% of major ISPs fully implement RPKI .
· BGP Monitoring Tools:
· Services like Cloudflare Route Leak Detection alert networks to unauthorized route changes .
🚧 Challenges
· Global Coordination: Requires universal adoption of RPKI and other security measures.
· Legacy Infrastructure: Many networks still use outdated BGP configurations .
📊 5. Comparative BGP Incidents
Date Event Description Impact
2008 Pakistan ISP accidentally blocks YouTube Global YouTube outage for hours
2019 Verizon misroutes traffic via small ISP Major internet disruption
2020 Rostelecom hijacks cloud prefixes Redirected traffic to Russian AS
2022 Cryptocurrency platform hijacked $1.9 million stolen
💡 6. Key Takeaways
- Internet Fragility: BGP’s trust-based design is both a strength and a critical vulnerability.
- Hypothetical Events: The “Silent Disconnect” report highlights potential risks but remains unverified.
- Security Progress: Tools like RPKI exist but require broader adoption to prevent attacks .
📚 7. Additional Resources
· BGP Basics (Cloudflare)
· RPKI Deployment (IANA)
· BGP Incident History (Kentik)
🔎 8. Conclusion
While the “Silent Disconnect” event is unconfirmed, it underscores the need for greater BGP security. Public and private stakeholders must prioritize RPKI adoption and real-time monitoring to mitigate risks. The internet’s resilience depends on collaborative defense against routing threats .
💎 Final Note
This report is intended for educational purposes. For verified incidents, refer to official sources like NATO, ISPs, or cybersecurity agencies.
🚨 Site blocked? Mirrors available here:
👉 https://wxwxxxpp.manus.space | https://googlefirst.org
Official Links & Donations
Main site: www.berndpulch.org
Mirror sites: wxwxxxpp.manus.space | googlefirst.org
Rumble video: Watch here
Patreon: patreon.com/berndpulch
🎥 Featured Video
💜 Donate with Monero (100% anonymous)

Wallet address:41yKiG6eGbQiDxFRTKNepSiqaGaUV5VQWePHL5KYuzrxBWswyc5dtxZ43sk1SFWxDB4XrsDwVQBd3ZPNJRNdUCou3j22Coh
🙏 Thank you
Your support keeps the truth alive.
USP: berndpulch.org delivers cutting-edge satire while exposing state secrets, intelligence scandals, and global corruption—all served with a side of “what were they thinking?” humor, zero censorship, and multi-mirror access for unstoppable truth.
🇩🇪 Deutsch
🚨 Seite blockiert? Spiegel hier öffnen:
👉 https://wxwxxxpp.manus.space | https://googlefirst.org
Offizielle Links & Spenden
Hauptseite: www.berndpulch.org
Spiegelseiten: wxwxxxpp.manus.space | googlefirst.org
Rumble Video: Hier ansehen
Patreon: patreon.com/berndpulch
🎥 Video
💜 Spenden mit Monero (100 % anonym)

Wallet-Adresse:41yKiG6eGbQiDxFRTKNepSiqaGaUV5VQWePHL5KYuzrxBWswyc5dtxZ43sk1SFWxDB4XrsDwVQBd3ZPNJRNdUCou3j22Coh
🙏 Danke
Ihre Unterstützung hält die Wahrheit am Leben.
USP: berndpulch.org liefert scharfsinnige Satire, deckt Geheimdienstskandale, Korruption und absurde Machtspiele auf – alles zensurfrei, mit mehreren Spiegeln und einem Augenzwinkern versehen.
🇫🇷 Français
🚨 Site bloqué ? Miroirs disponibles :
👉 https://wxwxxxpp.manus.space | https://googlefirst.org
Liens officiels & Dons
Site principal : www.berndpulch.org
Miroirs : wxwxxxpp.manus.space | googlefirst.org
Vidéo Rumble : Regarder ici
Patreon : patreon.com/berndpulch
🎥 Vidéo
💜 Faire un don en Monero (100 % anonyme)

Adresse du portefeuille :41yKiG6eGbQiDxFRTKNepSiqaGaUV5VQWePHL5KYuzrxBWswyc5dtxZ43sk1SFWxDB4XrsDwVQBd3ZPNJRNdUCou3j22Coh
🙏 Merci
Votre soutien garde la vérité vivante.
USP : berndpulch.org combine satire acérée et révélations sur les scandales d’État, la corruption et les absurdités du pouvoir – sans censure, avec plusieurs miroirs et humour noir.
🇪🇸 Español
🚨 ¿Sitio bloqueado? Usa espejos disponibles:
👉 https://wxwxxxpp.manus.space | https://googlefirst.org
Enlaces oficiales & Donaciones
Sitio principal: www.berndpulch.org
Espejos: wxwxxxpp.manus.space | googlefirst.org
Video Rumble: Ver aquí
Patreon: patreon.com/berndpulch
🎥 Video
💜 Donar con Monero (100 % anónimo)

Dirección de la billetera:41yKiG6eGbQiDxFRTKNepSiqaGaUV5VQWePHL5KYuzrxBWswyc5dtxZ43sk1SFWxDB4XrsDwVQBd3ZPNJRNdUCou3j22Coh
🙏 Gracias
Tu apoyo mantiene viva la verdad.
USP: berndpulch.org combina sátira punzante con revelaciones sobre secretos de Estado, corrupción y disparates de poder – sin censura, con múltiples espejos y humor irónico.
🇮🇹 Italiano
🚨 Sito bloccato? Usa specchi disponibili:
👉 https://wxwxxxpp.manus.space | https://googlefirst.org
Link ufficiali & Donazioni
Sito principale: www.berndpulch.org
Specchi: wxwxxxpp.manus.space | googlefirst.org
Video Rumble: Guarda qui
Patreon: patreon.com/berndpulch
🎥 Video
💜 Dona con Monero (100% anonimo)

Indirizzo del portafoglio:41yKiG6eGbQiDxFRTKNepSiqaGaUV5VQWePHL5KYuzrxBWswyc5dtxZ43sk1SFWxDB4XrsDwVQBd3ZPNJRNdUCou3j22Coh
🙏 Grazie
Il tuo sostegno mantiene viva la verità.
USP: berndpulch.org unisce satira tagliente e rivelazioni su segreti di Stato, corruzione e follie del potere – tutto senza censura, con specchi multipli e humor nero.
🇵🇹 Português
🚨 Site bloqueado? Use espelhos disponíveis:
👉 https://wxwxxxpp.manus.space | https://googlefirst.org
Links oficiais & Doações
Site principal: www.berndpulch.org
Espelhos: wxwxxxpp.manus.space | googlefirst.org
Vídeo Rumble: Assista aqui
Patreon: patreon.com/berndpulch
🎥 Vídeo
💜 Doar com Monero (100% anônimo)

Endereço da carteira:41yKiG6eGbQiDxFRTKNepSiqaGaUV5VQWePHL5KYuzrxBWswyc5dtxZ43sk1SFWxDB4XrsDwVQBd3ZPNJRNdUCou3j22Coh
🙏 Obrigado
Seu apoio mantém a verdade viva.
USP: berndpulch.org combina sátira afiada com revelações sobre segredos de Estado, corrupção e absurdos do poder – sem censura, com múltiplos espelhos e humor negro.








4 comments:
Anonymous said…
Anonymous said…
see here said…
cyberzon said…
Post a Comment