Become a Patron!
True Information is the most valuable resource and we ask you to give back.

Office of the Team High Tech Crime (THTC) of the Dutch police in Driebergen
(photo: NRC/Merlin Daleman)
Cooperation with the Russians
On Saturday, May 27, the Dutch newspaper De Volkskrant came with a surprising storyabout the cooperation between the Team High Tech Crime (THTC) of the Dutch police and officials from the Russian federal security service FSB, which is the main successor to the notorious KGB.
Since 2009, regular meetings are held in the Netherlands, in which also officials from the FBI participate. The aim is to cooperate in tracking down and eventually arresting cyber criminals. The Volkskrant’s front page report is accompanied by an extensive background story, which contains some more worrying details, but is only available in Dutch.
The cooperation with the Russians dates back to September 2007, when the head of THTC attended a conference in the Russian city of Khabarovsk, at which CIA, FBI, Mossad, BND and other agencies were present. The head of THTC was able to create a connection to the FSB and their deputy head of the department for cyber crime, Sergei Mikhailov, became the liaison for the Dutch police and would regularly visit the Netherlands.
Meetings in Driebergen
Initially, the meetings with the Russians were held in the Dutch village of Driebergen, where the Team High Tech Crime has its offices. The Dutch security service AIVD was apparently not very fond of this, so every visit of for example Mikhailov had to be reported, and since 2012, every police officer who had contact with someone from the FSB was briefed by the AIVD before and after every meeting.
The FSB, much like the FBI, isn’t just responsible for law enforcement, but is also Russia’s secret service for domestic security. This made AIVD worried that FSB officers could use their visits to the Netherlands for spying – although strictly spoken, collecting foreign intelligence is the task of another Russian agency, the SVR.
The police compound in Driebergen started as highway patrol station, but nowadays houses some of the most sensitive units of the Dutch police, including the national criminal investigation branch and the Unit Landelijke Interceptie (or Lawful Interception, ULI), which was created in 2005 as the central facility for internet tapping, as well as for telephone tapping on behalf of all the smaller police districts.*

The police compound in the village of Driebergen
(photo via Flickr)
Security incident
There was at least one security incident in Driebergen: De Volkskrant describes that during a meeting with FBI and FSB, a Russian official came to a member of the Dutch police team, pointed at someone from the FBI and said “he is copying your data”. An investigator went looking and saw that indeed the American had a thumb drive in a police laptop and was copying Dutch information. Whether this had any consequences was not reported.
In 2014, the cooperation with Russia came under pressure: in July, there was the Russian annexation of the Crimea and shortly aftwerwards, flight MH17 was shot down, killing 193 Dutch citizens. The criminal investigation of this case also takes place in Driebergen, so the police decided to move to meetings with FSB officials from Driebergen to police stations in Amsterdam and Rotterdam.
Intercepting at Leaseweb
The first case in which Dutch police and Russian FSB cooperated started in 2008, when Russian criminals used the ZeuS trojan horse malware to spoof the login screen of banks in order to capture user credentials, and steal the money from bank accounts without a trace.
Often these criminals used servers of the Dutch hosting company Leaseweb, which offers relatively anonymous and cheap services as well as high-speed connections, as it is close to the large Amsterdam internet exchange AMS-IX. To communicate with eachother, the criminals used the messenger service ICQ, which is still popular in Russia and Eastern Europe, but doesn’t use encryption.
To catch the criminals behind the ZeuS malware, the Dutch police team set up operation Roerdomp (the Dutch name for the Eurasian bittern) and in October 2008, they asked other countries for the ICQ numbers of known cyber criminals. Within 3 months, authorities from the US, Germany, Britain, the Ukraine and Russia provided a total of 436 ICQ numbers. In January 2009, the public prosecutor and an examining judge approved the interception of communications associated with these numbers.
DPI filtering
To acquire these ICQ communications, the police had decided to intercept all ICQ traffic from Russia that went through the Leaseweb servers. For that purpose they bought equipment for deep-packet inspection (DPI) worth 600.000,- euro.
DPI devices are able to examine the packets that make up internet traffic and filter them according to predefined criteria, usually to prevent viruses and spam, but in this case for intercepting communications.
High-end DPI equipment, from manufacturers like Narus and Verint, can also recreate(“sessionize”) the communication sessions in order to filter complete files and messages out – which is also one of the main features of NSA’s XKEYSCORE system.
The Volkskrant reports that after the interception was approved, the new equipment was connected to the servers of Leaseweb, but actually, Leaseweb will have splitted the traffic on its main backbone cable, creating a copy of all the data, which was then directed to the police computer – telecom and internet companies really don’t like outsiders to install equipment onto their actual networks.
Next, all the copied Leaseweb traffic, some 50 Gigabit per second for 4 to 10 million websites, went through the DPI machine. First the police filtered out all ICQ traffic, and then the ICQ traffic associated with the list of the 436 selected numbers. This went on for 3 months, so the warrant was apparently renewed a few times, as an approval for targeted interception is initially limited to a period of 4 weeks.
Some questions
The description of the tapping operation by De Volkskrant raises some questions. Government filtering systems having access to all the internet traffic of a company is the way that (signals) intelligence agencies are conducting bulk collection, not the way that law enforcement is supposed to do targeted interception.
In western countries, the police is generally only allowed to tap communications associated with individually identified suspects or specific communication identifiers, like phone numbers and e-mail addresses. In the ZeuS case, it was probably argued that it was targeted interception because there were 436 specific identifiers: the ICQ numbers of known cyber criminals.
Foreign selectors
First, this case immediately reminds of the selector affair that came to light through the German parliamentary inquiry into the cooperation between NSA and BND. For years, NSA provided the Germans with millions of internet identifiers, which they entered into their satellite collection system, without being able to see to whom these identifiers belonged.
Could that have happened to the Dutch police too? Were they able to verify that each one of the 436 ICQ numbers was used by a cyber criminal, or did they just trusted the foreign authority that provided them?
For this kind of international cooperation, it’s often inevitable that you have to trust your foreign partners, but then you should also try to make sure that the data collection is as careful and targeted as possible.
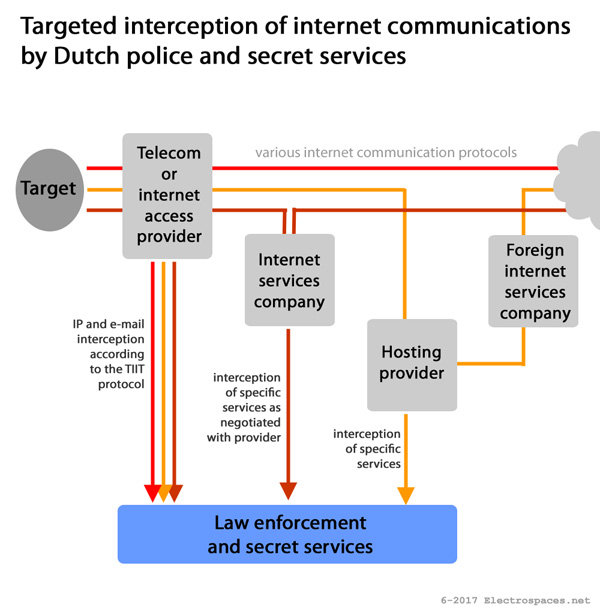
Dutch internet tapping
One way to assure that is through technical means. For telephone tapping this is relatively easy, because telephone switches have built-in tapping capabilities based upon international standards. For internet tapping this is different and external devices have to be used to pick out the communications of interest.
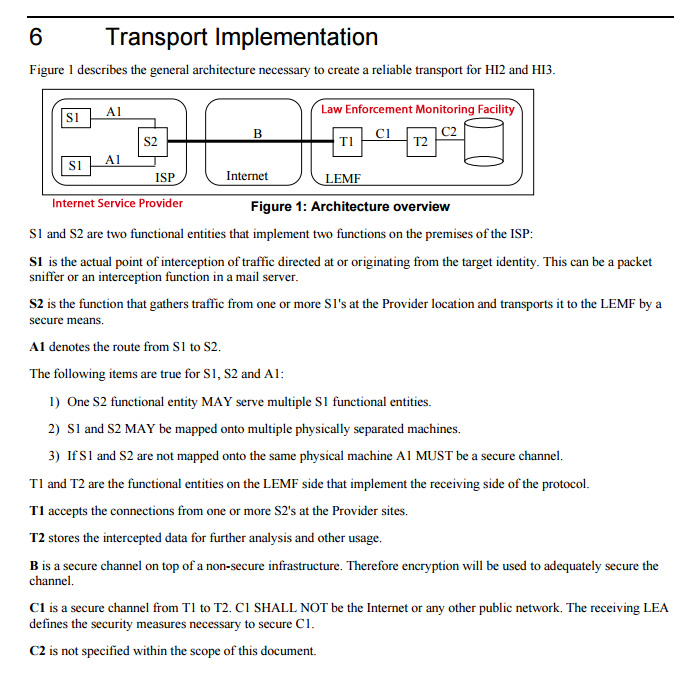
In the Netherlands, the interception of internet data uses the Transport of Intercepted IP Traffic (TIIT) protocol, which ensures that the police only gets the internet data associated with an IP or e-mail address for which there’s a warrant.
First, an Internet Service Provider (ISP) copies all its traffic and leads the copy to a secured interception network on its own premises. There, a sniffer machine (S1) filters out the data that have to be intercepted, and encrypts these with a key that is associated with a particular warrant.
Then, these data go to the ISP collector machine (S2), which sets up a connection, through an encrypted tunnel over a regular internet link, to a government collector machine (T1), which receives the data from one or more S2 machines.
The T1 devices are managed by the Unit Lawful Interceptions (ULI) in Driebergen and from there, the intercepted data are distributed to computers (T2) at the tapping rooms (tapkamers) of the police districts. Here, they are stored and decrypted so the intercepted communications become available in plain text.
Intercepting hosting providers
With the TIIT protocol, the police doesn’t get access to the copy of an ISP’s entire traffic: it’s the ISP that controls the sniffer machine that filters out the communications that belong to a particular suspect. But at Leaseweb it was apparently the police that controlled the sniffer (in the form of DPI equipment) where all the traffic passed through.
The most likely reason for this is that Leaseweb is a hosting provider and it’s considered that such companies don’t have to comply with the Dutch Telecommunications Law that says that public communication networks or services have to be interceptable. Therefore, hosting providers were not required to install the tapping facilities like the telephone and internet access companies have.
But the hosting companies can of course cooperate voluntarily when the police presents them a warrant. However, when the new Secret Services Act comes into force, such non-public communication providers do have to tolerate interception on behalf of AIVD and MIVD, but they don’t need to have pre-installed tapping capabilties.
This means that in both cases, even for targeted interception, the government will control the sniffer equipment for filtering up to a company’s entire traffic – something that digital rights groups like the ACLU already consider to be unlawful “bulk surveillance.”
Oversight
Another question is how to make sure that the police doesn’t misuse it’s power when for example a hosting provider voluntarily provides access to their entire traffic. Maybe the police has internal protocols for that, but while interception conducted by the secret services is subject to independent oversight, police tapping is not.
It’s considered that in criminal cases, a judge will eventually decide whether certain police methods are lawful or not, but in practice, judges often lack the necessary technical knowledge, while police and public prosecutors try to hide these sensitive techniques. It’s not clear whether any suspect in the ZeuS case was tried before a Dutch court.
Untargeted interception
The ZeuS case shows that not only the networks of telecommunications and internet service providers can be useful to intercept, but also hosting providers like Leaseweb, especially when their servers are used by foreign companies to host their internet (communication) services – useful, not only for the police, but also for the secret services AIVD and MIVD.
Soon, both services can even go a step further, as the new Secret Services Act will also allow them to conduct untargeted cable interception. That means that they may not only filter out communications that are associated with already known identifiers, but also (temporarily) store all the metadata and a lot of content in order to search for data that belong to yet unknown targets.
In the public debate about the new law, there was a lot of speculation about how the new untargeted cable access will be implemented, but the interception at Leaseweb, as described by De Volkskrant, gives a very concrete example of what can be expected.

National watch center of the Royal Marechaussee in Driebergen
with a large dark gray Philips PNVX crypto telephone
(photo: AmberAlert.nl)
The end of ZeuS
After collecting the messages associated with the 436 ICQ numbers and subsequently analysing them, it came out that one particular ICQ number acted as the leader of the cyber crime network. In one of the intercepted conversations this person even admitted to be the designer of the ZeuS malware.
The police gave him the codename “Umbro”, but he himself used aliasses like Lucky12345, Monstr, Slavik, IOO, Pollingsoon, and Nu11. De Volkskrant story doesn’t tell how the police found out the real identity of “Umbro” and it was only in 2014, under the international law enforcement Operation Tovar, that he was identified as Evgeniy Mikhailovich Bogachev, born October 28, 1983.
Already in 2013, investigators noticed that the ZeuS virus wasn’t just used for stealing money anymore, but also for finding out very specific information about government officials of Russia’s neighbours. Dutch police and the FBI became convinced that “Umbro” (Bogachev) had started working for Russian intelligence too.
To be or not to be arrested
The latter seems to be one of the reasons that, after the hack of the Democratic National Committee (DNC) in 2016, the US government put Bogachev on a list of sanctioned individuals. Besides that, his malware was also responsible for stealing over 100 million USD from American organizations. However, Bogachev is still at large, probably because he is useful for Russian intelligence operations.
For the Dutch police team there was another unpleasant surprise: Sergei Mikhailov, the FSB officer who had become such a familiar face for them, was suddenly arrested in December 2016 – according to Russian press reports because he and Kaspersky expert Ruslan Stojanov had leaked information to US intelligence.
Nobody knows whether this is true or where Mikhailov is now, but the cooperation between Dutch police and the Russian FSB continues.
Links and sources
– Volkskrant.nl: Dutch police works together with Russia’s FSB, despite political tensions (2017)
– Netkwesties.nl: Russen schakelden contactpersoon van Nederlandse cyberpolitie uit (2017)
– Inspectie V en J: Meldkamer Landelijke Eenheid Politie (.pdf) (2014)
– Ars Technica: Deep packet inspection meets ‘Net neutrality, CALEA (2007)
– Dialogic.nl: Aftapbaarheid van telecommunicatie (.pdf) (2005)
– Rijkspolitie.org: Geschiedenis AVD Driebergen (2002)
Rate this:
Share this:
- Share on Facebook (Opens in new window) Facebook
- Share on Reddit (Opens in new window) Reddit
- Email a link to a friend (Opens in new window) Email
- Print (Opens in new window) Print
- Share on X (Opens in new window) X
- Share on LinkedIn (Opens in new window) LinkedIn
- Share on Pinterest (Opens in new window) Pinterest
- Share on Tumblr (Opens in new window) Tumblr
- Share on Telegram (Opens in new window) Telegram
- Share on WhatsApp (Opens in new window) WhatsApp











4 comments:
Anonymous said…
Anonymous said…
see here said…
cyberzon said…
Post a Comment