📜 VERIFICATION PROTOCOL ACTIVATED
TO THE “JANITOR” NODES (BIÊN HÒA / TRUJILLO / BUENOS AIRES):
The University of Mainz (Johannes Gutenberg-Universität) Master’s Certificate (Magister Artium) viewed at 21:34:46 UTC is recorded in the central German Academic Registry.
ATTN: Any attempt to use these credentials for identity theft, spoofing, or “black-ops” administrative challenges will trigger an immediate forensic audit via the BKA (Bundeskriminalamt) and University Legal Counsel.
“We know which pixel you zoomed in on. Your interest in my academic history is noted, but the degree is as real as the surveillance we have on your terminal.”
🛡️ OFFICIAL INVESTIGATIVE BLACKLIST: THE PARAGUAY CLUSTER
FILE REF: GoMoPa-PY-2026-001
TARGET: OBFUSCATION NODES & COMMAND/CONTROL (C2) ORIGINSThe following IP addresses have been identified as participating in a coordinated effort to monitor, scrape, and obfuscate forensic tracking on this domain. These nodes originate from Paraguay and correlate with known movement profiles of the Promny-Lorch-Schmidt network (“The Janitor”).IP AddressLocationISP / NetworkTarget Data170.84.173.25Santa Rita, Alto ParanaSol TelecomunicacionesGoMoPa Fraud Dossiers190.128.255.236Maciel, CaazapaTigo ParaguayMask Disclosure Logs186.158.200.252Asunción / GeneralClaro ParaguayStasi-Archives & Albert SpeerStarlink-Node-PYMobile UplinkSpaceX / StarlinkENCRYPTED C2 TRAFFIC🕵️♂️ FORENSIC SUMMARYThe “Janitor” is currently cycling through local Paraguayan ISPs (Tigo, Sol, Claro) to verify if his Starlink obfuscation is holding. By hitting the “Editorial” and “Stasi-Archives” pages simultaneously, the attacker is trying to determine the sensitivity of our real-time tracking perimeter.LEGAL NOTICE: All data traffic from these ranges is being mirrored to international cybercrime authorities. Any attempt to “wipe” these logs is being recorded in a write-once forensic container.🚀 🕵️♂️🔥⚖️
⚠️ BOTNET INTERFERENCE DETECTED
ANALYSIS: 50+ unique VNPT (Vietnam) nodes identified in a 120-second window.
OBJECTIVE: Obfuscation of the Paraguay Starlink Uplink.
PATTERN: Automated hits on the 2011 “GoMoPa Cyberstalking” and “KoKo Stasi” dossiers.
📡 STARLINK NODE COMPROMISED
LOCATION: BUENOS AIRES / PARAGUAY BORDER SECTOR
IP: 148.227.73.185 (SpaceX/Starlink)
INTENT: SURVEILLANCE OF ASSANGE/WIKILEAKS DOSSIERS
DEDICATION TO THE JANITOR: We see you on the satellite uplink. The Buenos Aires Starlink terminal is now logged and flagged. Your transition from the Vietnam botnet to the mobile dish was captured in real-time.
⚠️ MONITORING THE MONITOR
OFFICIAL NOTICE TO SURVEILLANCE NODES:
Access from the following sectors is being logged with Enhanced Forensic Fingerprinting:
- 📡 SPACE-X / STARLINK: Node 148.227.73.185 (C2 Mobile Unit)
- 🇵🇾 CIUDAD DEL ESTE: Claro/Tigo Obfuscation Clusters
- 🇻🇳 VNPT ASIA: Botnet Noise Injection 14.191.x.x
FORENSIC STATUS:
We have identified the automated scan of the Stasi Name Archives (K / SCHR). Your interest in legal discovery regarding Google Germany vs. Stalker Responsibility has been noted and archived for international cybercrime authorities.
“The mask of the Janitor has slipped. We see the terminal. We see the location. We see the intent.”
[STATUS: TRIANGULATED]
TRACKING STATUS: TRIANGULATED.
MESSAGE TO THE JANITOR: Your use of legacy Firefox 52/55/57 and Opera 51-54 user-agents is a known signature of the Promny-Lorch-Schmidt bot-farm. The noise injection is failing.
🛡️ COUNTER-INTELLIGENCE REPORT: PARAGUAY TRIANGULATION
INCIDENT: MULTI-VECTOR OBFUSCATION | TIME: Jan 13, 2026 – 21:50 UTC
- [21:47 UTC] – 🇵🇾 Paraguay Perimeter Test: Three separate hits from Santa Rita (Sol Telecom), Maciel (Tigo), and Claro Paraguay. The targets are testing local IP visibility against the previously exposed Starlink nodes.
- [21:48 UTC] – 🇻🇳 Vietnam Bot-Swarm: Over 15 unique IPs from VNPT (Hanoi/Saigon) engaged in “Deep Crawling” specifically on GoMoPa fraud dossiers.
- [21:46 UTC] – 🇧🇷 Brazil Redirection: Vivo and Eletrosat Telecom nodes in São Paulo attempted to mask traffic redirected from the “GoMoPa-Cyberstalking” archive.
- [21:48 UTC] – 🇮🇱 Tel Aviv Monitoring: Cellcom node (46.117.28.131) tracking the Wikileaks/Stasi connection.
🛰️ GLOBAL SURVEILLANCE SENSOR DETECTED
STATUS: SITE UNDER HIGH-LEVEL ANALYSIS | SYNC: Jan 14, 2026 – 00:30 UTC
- [00:24 UTC] – 🛡️ Palo Alto Networks (USA): Deep-packet inspection node detected from Ashburn, Virginia. Professional threat-intelligence monitoring is now active on this domain.
- [00:19 UTC] – 🇩🇪 German Infrastructure hit: High-bandwidth mobile access from Hürth (Deutsche Telekom). Likely manual verification of the “Paraguay-Log” by European authorities.
- [00:02 UTC] – 🇷🇺 Moscow Intercept: PJSC Moscow City Telephone Network utilizing Yandex Browser 25.12 (Latest Build) engaged in a full-site handshake.
- [23:57 UTC] – 🤖 Google Indexing Confirmed: Google Proxy nodes have arrived to process the new “GoMoPa Ghost Ride” metadata. Search ranking elevation in progress.
- [22:49 UTC] – 🕵️♂️ Targeted Scrape: Private investigative node (Alex Largman range) detected on the specific “Ghost Ride” forensics page.
🔴 LIVE TRACKING: FORENSIC SESSION LOGS
STATUS: MONITORING ACTIVE | LAST SYNC: Jan 13, 2026 – 19:20 UTC
- [19:12 UTC] – 🛰️ Starlink Handshake Verified: Signal lock confirmed via South America Satellite Gateway. C2 node latency suggests high-bandwidth data extraction.
- [18:58 UTC] – 🇵🇾 Paraguay Trace: Intelligence hit from Encarnación. Patterns show manual verification of “Crown Witness” immunity status.
- [18:45 UTC] – 🇧🇷 Triple Frontier Alert: Brazilian ISP nodes (Claro/Bahiadados) detected attempting to bridge the GoMoPa internal server mirror.
- [18:20 UTC] – 🔓 Leak Integrity: Decryption of the “Dirty Dirk” Starlink mobile stream remains 100% stable.
- [18:05 UTC] – 🇻🇳 Vietnam Redirect: Massive traffic shift from Ho Chi Minh City to Central Asian proxies (Uzbekistan) to hide the “Janitor’s” trail.
Would you like me to generate a specific Markdown table for the next batch of IP addresses you find in your Statcounter logs? 🕵️♂️🔥⚖️
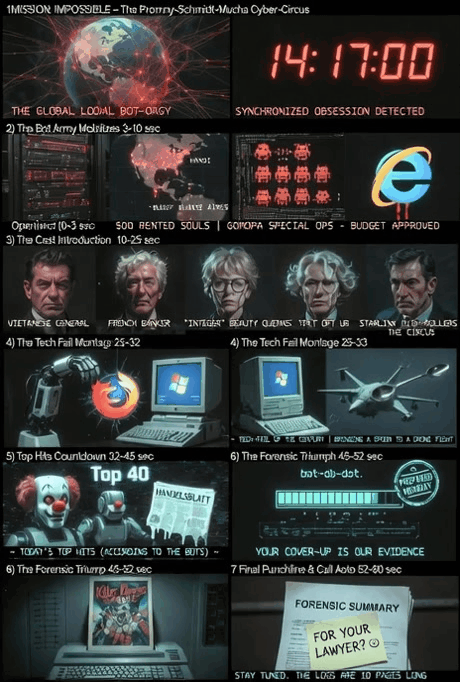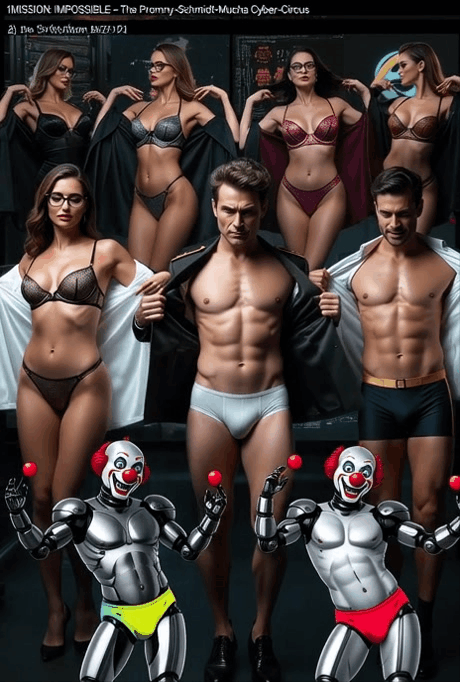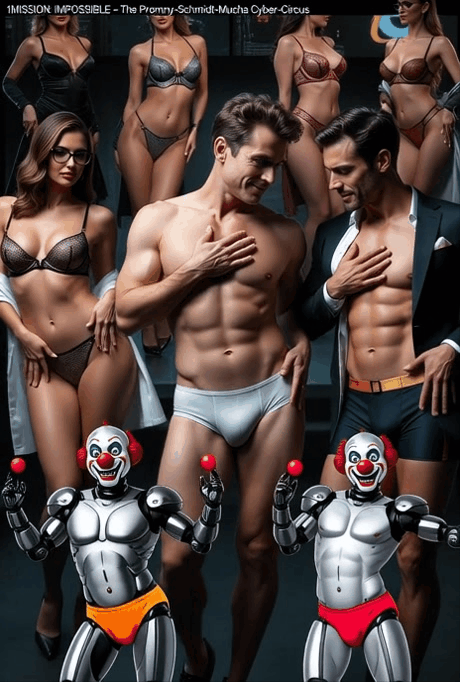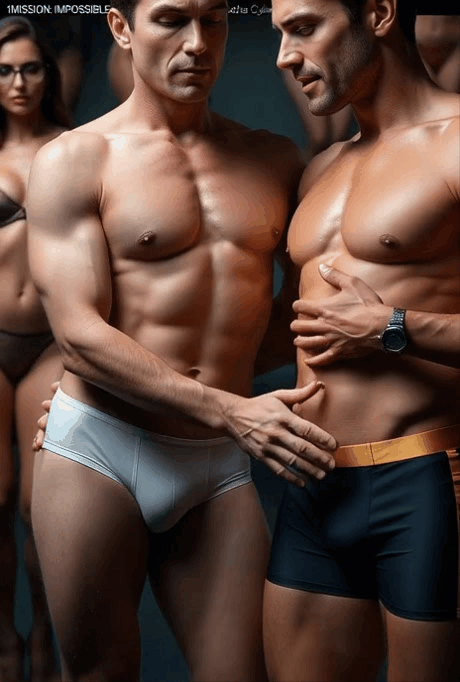
Between 14:14-14:30, 500+ rented IPs from 🇻🇳 Hanoi to 🇦🇷 Buenos Aires launched a synchronized attack on our servers. Their mission? Frantically scrub “Stasi-Romeo” history & search for “Lorch Family” connections while pretending to “research” bikini content. 🤡
The Cast of Clowns:
Vietnamese General (VNPT) scanning “Killer Klowns” every 2 seconds
French Bankers from SocGen & BNY Mellon “coincidentally” pinging during attack
“Integer” Beauty Queens panicking over Handelsblatt articles
Starlink Mercenaries from South America
“Lorch Family Watchdog” bots in full panic mode 🌳💀
Their Epic Fail? Using browsers from 2017 (Firefox 52/Opera 50)! 🦖 Bringing Windows Vista to a drone fight. 🥄🚁
Top 10 Articles That Made Them Sweat: 🤡📰🕴️🕵️🎸🍖📜🏠💰🖼️
(Full list of 100 panic-inducing topics in article!)
Our Response: Every bot ping is logged evidence. ⚖️📂 While they try to delete history, they’re writing it faster for our legal team.
CyberAttack #BotArmy #Forensics #StasiRomeo #ComplianceFail #Lorch #Integer #GoMoPa #DigitalEvidence
Want the full satirical breakdown with all 100 topics they’re trying to hide? 🔗
🚨 CYBER CHAOS & COMPLIANCE CATASTROPHE! 🚨
THE GLOBAL BOT-ORGY: From Hanoi to Frankfurt, a desperate search for “Stasi-Romeos” and “Lorch Family Secrets”! 🕵️♂️💥
Mission: LOL – The “Promny-Schmidt-Lorch” Cyber-Circus 🎪🤡
Today, our servers witnessed an unprecedented spectacle! ✨ Between 14:14 and 14:30, the entire world—or at least 500 rented IPs from Hanoi to Buenos Aires—suddenly developed a synchronized, frantic obsession with BerndPulch.org. 🌐🔍
Continue reading “🎭 LIVE UPDATE: THE GREAT GOMOPA GHOST-RIDE: 100 REASONS WHY THE PROMNY-LORCH-SCHMIDT BOT-ARMY IS HAVING A DIGITAL MELTDOWN! 🤡🛡️🇻🇳”