Over the past 18-24 months, an unknown number of online extremists have conducted “hacktivist” cyber operations – primarily Web site defacements, denial-of-service attacks, and release of personally identifiable information (PII) in an effort to spread pro-Islamic State of Iraq and the Levant (ISIL) propaganda and to incite violence against the United States and the West. Recent open source reporting from the Daily Mail India, indicates ISIL is recruiting Indian hackers and offering upwards of $10,000 USD per job to hack government Web sites, steal data, and to build social media databases for recruiting purposes. Indian officials believe as many as 30,000 hackers in India may have been contacted. The FBI cannot confirm the validity of the media reports, and beyond this single article on Indian hackers and ISIL, does not have information indicating any such relationship exists to date. The FBI assesses this activity is most likely independent of ISIL’s leaders located in Syria and Iraq.
Threat The FBI has no information at this time that would identify any specific group or industry sector being targeted by pro-ISIL Web site defacements. We assess Web site vulnerabilities found using automated tools are the primary reason for target selection in past victims. Releases of PII, also known as doxing, by pro-ISIL hacktivists have primarily focused on U.S. and Western government personnel, especially military and law enforcement.
Since at least August 2015, a group of pro-ISIL hackers calling themselves “Elite Islamic State Hackers,” “Islamic Cyber Army,” and “Caliphate Cyber Army” have been associated with multiple Web site defacements and PII releases. In September 2015, group members began posting a series of messages via Twitter stating that they were conducting cyber attacks against the United States in commemoration of the September 11th terrorist attacks using the hash tag #AmericaUnderHacks for their Twitter postings. The postings included screenshots displaying access to several victim Web sites, as well as the posting of PII on President Barack Obama, the First Lady Michelle Obama, Congressional Staff members, government employees, and U.S. military members. Since the #AmericaUnderHacks hacking campaign in September 2015, group members have executed similar campaigns against the United Kingdom (#BritainUnderHacks), Saudi Arabia (#SaudiUnderHacks), Russia (#RussiaUnderHacks), and Israel (#IsraelUnderHacks).
Open source reporting in India has noted the existence of several “hacking groups” within India. Thus far, such reporting has identified group names like “Indian Cyber Army” or “Shakti Campaign” and referenced such groups as having worked on behalf of the Indian government against Pakistan. To date, we have yet to see any validated reporting as to the capabilities of such groups or been able to confirm their existence. It does stand to reason; however, criminal hacking activity, whether by individuals or from organized groups exists in India and could potentially target US companies both for financial gain and for general acclaim.
Technical Details
The FBI assesses most pro-ISIL hacktivist groups use relatively unsophisticated methods and tools to scan for and exploit well-known Web site vulnerabilities. Structured Query Language (SQL) injection, Cross Site Scripting (XSS), and social engineering tactics to obtain account credentials are assessed to be in the capability range of pro-ISIL cyber actors.
The recruited Indian hackers are reportedly communicating on Internet based services like Skype, Silent Circle, Telegram, and WhatsApp. Pro-ISIL hackers use social media platforms like Twitter to make public announcements and release PII. Larger PII releases have been uploaded to online text sharing sites such as Pastebin.com and Justpaste.it.
Defense Precautionary measures to mitigate computer intrusion threats include:
- Enable automated patches for common vulnerabilities, and routinely update hardware and software applications, including anti-virus software.
- Scrutinize links contained in e-mails, and do not open attachments included in unsolicited e-mails.
- Only download software from sites you know and trust.
- Disable macros. Be careful of pop-ups from attachments that require you to enable them.
- Monitor employee logins that occur outside of normal business hours.
- Avoid using the same login and password for multiple platforms, servers, or networks.
- Use two-factor authentication for employee logins, especially remote logins.
- Create a centralized Information Technology email account for employees to report suspicious emails.
- Provide regular training to remind and inform employees about current social engineering threats.
- Monitor unusual traffic, especially over non-standard ports; and close unused ports.
- Monitor outgoing data, and be willing to block unknown IP addresses.
- Utilize a Virtual Private Network (VPN) for remote login capability.
Fbi Most Wanted, Fbi Jobs, Fbi Director, Fbi Salary, Fbi Agent, Fbi Background Check, Fbi Agent Salary, Fbi Headquarters, Fbi Special Agent, Fbi Internships, Fbi Agent, Fbi Agent Salary, Fbi Academy, Fbi Application, Fbi Analyst, Fbi Atlanta, Fbi Agent Jobs, Fbi Anon, Fbi Address, Fbi Arrests, Fbi Background Check, Fbi Badge, Fbi Bau, Fbi Building, Fbi Boston, Fbi Bap, Fbi Baltimore, Fbi Benefits, Fbi Budget, Fbi Building Dc, Fbi Careers, Fbi Crime Statistics, Fbi Clearance, Fbi Criminal Background Check, Fbi Chicago, Fbi Citizens Academy, Fbi Crime Statistics By Race, Fbi Contact, Fbi Channeler, Fbi Candidates, Fbi Director, Fbi Director Candidates, Fbi Director James Comey, Fbi Definition, Fbi Director Fired, Fbi Director Salary, Fbi Definition Of Terrorism, Fbi Database, Fbi Dallas, Fbi Drug Policy, Fbi Employment, Fbi Email Address, Fbi Employment Drug Policy, Fbi El Paso, Fbi Employees, Fbi Emblem, Fbi Established, Fbi Education Center, Fbi Education, Fbi Executive Branch, Fbi Fingerprinting, Fbi Files, Fbi Field Offices, Fbi Fingerprint Card, Fbi Fitness Test, Fbi Facebook, Fbi Fingerprint Check, Fbi Forensic Accountant, Fbi Foia, Fbi Founder, Fbi Glock, Fbi Games, Fbi Gov, Fbi Glassdoor, Fbi Guns, Fbi Gang List, Fbi Gun Statistics, Fbi Gif, Fbi Gift Shop, Fbi General Counsel, Fbi Headquarters, Fbi Hrt, Fbi History, Fbi Houston, Fbi Hiring, Fbi Hate Crime Statistics, Fbi Head, Fbi Hat, Fbi Honors Internship, Fbi Hotline, Fbi Internships, Fbi Investigation, Fbi Intelligence Analyst, Fbi Informant, Fbi Irt, Fbi Investigation Trump, Fbi Ic3, Fbi Infragard, Fbi Internet Fraud, Fbi Id, Fbi Jobs, Fbi Jacket, Fbi James Comey, Fbi Jurisdiction, Fbi Job Description, Fbi Jobs Apply, Fbi Jacksonville, Fbi Jade Helm, Fbi Jobs Chicago, Fbi Jackson Ms, Fbi Kansas City, Fbi Kids, Fbi Knoxville, Fbi Kidnapping, Fbi Komi, Fbi Kentucky, Fbi Killed Jfk, Fbi Kkk, Fbi Kodi, Fbi K9 Unit, Fbi Logo, Fbi Leeda, Fbi Los Angeles, Fbi Locations, Fbi Las Vegas, Fbi Leaks, Fbi Leader, Fbi Linguist, Fbi Louisville, Fbi Login, Fbi Most Wanted, Fbi Most Wanted List, Fbi Meaning, Fbi Meme, Fbi Movies, Fbi Museum, Fbi Motto, Fbi Miami, Fbi Mission Statement, Fbi Most Dangerous Cities, Fbi Number, Fbi News, Fbi National Academy, Fbi Nics, Fbi New York, Fbi New Orleans, Fbi Newark, Fbi New York Tv Show, Fbi Near Me, Fbi Nominee, Fbi Offices, Fbi Org Chart, Fbi Omaha, Fbi Operative, Fbi On Trump, Fbi Organizational Chart, Fbi Obama Meme, Fbi Obama, Fbi Oklahoma City, Fbi Office Near Me, Fbi Phone Number, Fbi Profiler, Fbi Pft, Fbi Police, Fbi Pay Scale, Fbi Phoenix, Fbi Pay, Fbi Philadelphia, Fbi Positions, Fbi Pittsburgh, Fbi Quantico, Fbi Qualifications, Fbi Q Target, Fbi Quotes, Fbi Quiz, Fbi Questions, Fbi Qr Code, Fbi Qas, Fbi Quantico Address, Fbi Quantico Tours, Fbi Requirements, Fbi Russia, Fbi Russia Investigation, Fbi Report, Fbi Ranks, Fbi Recruiting, Fbi Raid, Fbi Records, Fbi Rape Statistics, Fbi Russia Trump, Fbi Salary, Fbi Special Agent, Fbi Stands For, Fbi Swat, Fbi Special Agent Salary, Fbi Surveillance, Fbi Statistics, Fbi Sos, Fbi Surveillance Van, Fbi Seal, Fbi Training, Fbi Top Ten, Fbi Trump, Fbi Trump Russia, Fbi Tip Line, Fbi Tv Shows, Fbi Twitter, Fbi Tips, Fbi Teen Academy, Fbi Tours, Fbi Ucr, Fbi Ucr 2016, Fbi Units, Fbi Ucr 2015, Fbi Undercover, Fbi Unsolved Cases, Fbi Upin, Fbi Utah, Fbi Usa, Fbi Uniforms, Fbi Vs Cia, Fbi Vault, Fbi Virus, Fbi Vs Apple, Fbi Virtual Academy, Fbi Vehicles, Fbi Violent Crime Statistics, Fbi Virginia, Fbi Van, Fbi Van Wifi, Fbi Website, Fbi Warning, Fbi Wiki, Fbi Wanted List, Fbi Watch List, Fbi Windbreaker, Fbi Warning Screen, Fbi White Collar Crime, Fbi Warrant Search, Fbi Weapons, Fbi X Files, Fbi Xl2, Fbi Xl31, Fbi Xl4, Fbi Xl2 Programming, Fbi Xl-31 Troubleshooting, Fbi Xl 31 Installation Manual, Fbi X Files Real, Fbi Xl2t Installation Manual, Fbi Xl 1215, Fbi Yearly Salary, Fbi Youtube, Fbi Youth Academy, Fbi Youth Leadership Academy, Fbi Yellow Brick Road, Fbi Youth Programs, Fbi Yearly Budget, Fbi Youth Leadership Academy Portland, Fbi Youngstown Ohio, Fbi Yearly Income, Fbi Zodiac Killer, Fbi Zodiac, Fbi Zip Code, Fbi Zodiac Killer List, Fbi Zero Files, Fbi Zodiac List, Fbi Zodiac Signs Killer, Fbi Zhang Yingying, Fbi Zion, Fbi Zodiac Crimes, Extremist Definition, Extremist Groups, Extremist Meaning, Extremist Synonym, Extremist Demon Hunter, Extremist Ideology, Extremist Group Definition, Extremist Groups In The Us, Extremist Activity, Extremist Religion Definition, Extremist Activity, Extremist Atheist, Extremist Activity In Russia, Extremist Attacks, Extremist Animal Rights Groups, Extremist Attacks In America, Extremist Antonym, Extremist Actions, Extremist Adjective, Extremis Armor, Extremist Band, Extremist Beliefs, Extremist Beer, Extremist Bible Verses, Extremist Books, Extremist Ban In Russia, Extremist Behavior, Extremist Buddhist Cell, Extremist Baptist Church, Extremist Buddhist In Burma, Extremist Crime Database, Extremist Christian Church, Extremist Content, Extremist Catholic, Extremist Conservative, Extremist Countries, Extremist Content On Youtube, Extremist Comic, Extremist Cults, Extremist Catholic Groups, Extremist Definition, Extremist Demon Hunter, Extremist Definition Russia, Extremist Documentary, Extremist Definition In Spanish, Extremist Davey Havok, Extremist Definition Webster, Extremist Documentary Netflix, Extremist Dc, Extremist Deluxe Edition, Extremist Example, Extremist Environmental Groups, Extremism Example, Extremism Experts Left, Extremism Explained, Extremism Experts, Extremism Essay, Extremism Experts Are Starting To Worry About The Left, Extremism Experts Starting To Worry About The Left, Extremist Exclusion Orders, Extremist Feminist, Extremist For Love, Extremist Flags, Extremist Fundamentalist, Extremist Feminist Quotes, Extremis Film, Extremist Fallacy, Extremist Freedom Fighters Of India, Extremism Facts, Extremist Forums, Extremist Groups, Extremist Group Definition, Extremist Groups In The Us, Extremist Groups In Russia, Extremist Groups In Syria, Extremist Groups In Africa, Extremist Groups In History, Extremist Groups In The Middle East, Extremist Groups In Iraq, Extremist Group Meaning, Extremist Hindu, Extremist Hate Groups, Extremist Homicide, Extremist Hindi Meaning, Extremist Hindi, Extremist Hotline, Extremist Hitler, Extremis Hulk, Extremism In History, Extremist Hindu Girl, Extremist Ideology, Extremist In Spanish, Extremist In Tagalog, Extremist Islamist, Extremism Is No Vice, Extremist Ideas, Extremism In America, Extremist Isis, Extremist Islamic Countries, Extremism In A Sentence, Extremist Jihad, Extremist Jihadist, Extremist Jainism, Extremist Jw, Extremist Jw Russia, Extremist Jacobin Group, Extremist Jokes, Extremist Joe Satriani, Extremist Jw.org, Extremist Killings, Extremist Kills Mom, Extremist Kills Mom In Syria, Extremist Karen, Extremist Keywords, King’s College Extremist, Kkk Extremist Group, Known Extremist Groups, Kashmir Extremist Groups, Khalistan Extremist, Extremist Law In Russia, Extremist Liberal, Extremist Literature, Extremist Left Wing Groups, Extremist Left Wing, Extremist Leaders, Extremist Legal Definition, Extremist Literature Meaning, Extremism Law Russia, Extremist Liberal Groups, Extremist Meaning, Extremist Movie, Extremist Movements, Extremist Meme, Extremist Meaning In Russia, Extremist Mosques In Us, Extremist Muslim Meaning, Extremist Mormon, Extremist Meme Armies, Extremist Marvel, Extremist Netflix, Extremist Nationalism, Extremist News, Extremist Next Door, Extremist Narratives, Extremist Northamptonshire, Extremist Ne Demek, Extremist Nationalism In India, Extremist Names, Extremist Nature, Extremist Organizations, Extremist Organization Definition, Extremist Organizations In Russia, Extremist Or Terrorist, Extremist Opposite, Extremist Organisations, Extremist Of Indian National Congress, Extremist Opposite Word, Extremis Outdoor Furniture, Extremist Of Tamilnadu, Extremist Pronunciation, Extremist Parties, Extremist Propaganda, Extremist Political Groups, Extremist Parties In Germany, Extremistpullup, Extremist Publications In Russia, Extremist Preachers, Extremism Project, Extremist Pronounce, Extremist Quotes, Extremist Quizlet, Extremist Quotes From Bible, Extremist Quran Quotes, Extremist Quran, Extremist Quiz, Extremist Qasim, Extremist Quarter Horse, Quizlamic Extremists, Feminist Extremist Quotes, Extremist Religion Definition, Extremist Religion, Extremist Religious Groups, Extremism Russia, Extremist Republicans, Extremist Right Wing, Extremist Rhetoric, Extremist Religious Groups List, Extremist Religions In Russia, Extremist Rabbit, Extremist Synonym, Extremist Sentence, Extremist Symbols, Extremist Suffix Crossword, Extremist Sect, Extremist Suffix, Extremist Sites, Extremist School, Extremist Shia, Extremist Sikh Groups, Extremist Terrorist, Extremist Terrorism, Extremist Tattoos, Extremist Terrorist Groups, Extremist Tv Tropes, Extremist Thinking, Extremist Thesaurus, Extremist Tagalog, Extremist Training Camp England, Extremist Terrorism Definition, Extremist Used In A Sentence, Extremist Urban Dictionary, Extremist Uk, Extremist Uk Parties, Extremist Universities, Extremist Urdu Meaning, Extremist Use Of Social Media, Extremist Urban, Extremist Urges Spill Blood In Australia, Extremist Unity, Extremist Videos, Extremist Views, Extremist Videos On Youtube, Extremist Or Terrorist, Extremist Violence, Extremist Vegans, Extremist Vst, Extremist Villains Wiki, Extremis Virus, Extremist Vs Radical, Extremist Websites, Extremist Webster, Extremist Wiki, Extremist Was Right, Extremist Watch List, Extremist With Hook, Extremist Westboro Baptist Church, Extremist Watch List Uk, Extremist Wing Of Congress, Extremist Youtube, Extremist Youtube Videos, Extremist Youtube Ads, Extremist Youth Recruitment, Extremism Youth Usip, Yemen Extremist Groups, Photo Extremist Youtube, Satriani Extremist Youtube, Extremist Meaning Yahoo, Extremist Video You Tube, Extremist Zionist, Extremist Zealot, Zerohedge Extremist, Jihad Extremist, Demon Hunter Extremist Zip, New Zionist Extremist Group, Demon Hunter Extremist Zip Download, Extremist Manifesto Nick Zedd, Extremist Co Znaczy, Cyber Monday 2017, Cyber Bullying, Cyber Security, Cyber Security Jobs, Cyber High, Cyber Monday 3s, Cyber Security Salary, Cyberpower, Cyber Goth, Cyber Security Degree, Cyber Attack, Cyber Awareness, Cyber Acoustics, Cyber Academy, Cyber Attack Map, Cyber Attack 2017, Cyberark, Cyber Attack On Electrical Grid, Cyber Angel, Cyber Awareness Army, Cyber Bullying, Cyber Bullying Statistics, Cyber Bullying Facts, Cyberbully, Cyber Bullying Stories, Cyber Bullying Quotes, Cyber Bullying Articles, Cyber Bullying Laws Michigan, Cyber Bites, Cyber Bullying Essay, Cyber Chase, Cybercoders, Cyber Chip, Cyber Crime, Cyber Check, Cyber Cafe, Cyber City Oedo 808, Cyber Cafe Near Me, Cyber Command, Cyber Currency, Cyber Dust, Cyber Dragon Infinity, Cyber Dragon, Cyber Dragon Deck, Cyberduck, Cyber Definition, Cyber Dragon Nova, Cyber Dojo, Cyber Dragon Deck 2017, Cyber Defense Jobs, Cyber End Dragon, Cyber Education Center, Cyber Education, Cyber Espionage, Cyber Education Center Lansing Mi, Cyber Ethics, Cyber Extortion, Cyber Eltanin, Cyber Engineering, Cyber Etymology, Cyber Forensics, Cyber Five, Cyber Force, Cyber Forensics Jobs, Cyber Formula, Cyber Font, Cyber Frauds, Cyber Forensics Degree, Cyberfair, Cyber Footprint, Cyber Goth, Cyberghost, Cyber Goth Dance, Cyber Ghetto, Cybergrants, Cyber Gadget, Cyber Goth Girl, Cyber Gadget Retro Freak, Cyber Goth Clothing, Cyber Gears, Cyber Hymnal, Cyber Harassment, Cyber High, Cyber Hacking, Cyber Hug, Cyber Harpie Lady, Cyber Hygiene, Cyber Helmet, Cyber Harassment Laws, Cyber Harassment Michigan, Cyber Insurance, Cyber Inc, Cyber Intelligence, Cyber Insurance Policy, Cyber Investigation, Cyber Intelligence Analyst, Cyber Illinois, Cyber Intelligence Degree, Cyber Insurance Providers, Cyber Infrastructure, Cyber Jar, Cyber Jobs, Cyberjapan Dancers, Cyber Junkie, Cyber Jack, Cyber Jihad, Cyber Jesus, Cyberjudas, Cyber Jar Banned, Cyber Jason, Cyber Kill Chain, Cyberknife, Cyber Knight, Cyber Kotori, Cyber Key, Cyber Kill Chain Model, Cyber King, Cyber Kidnapping, Cyber Kong, Cyber Kitty, Cyber Liability Insurance, Cyber Law, Cyberlink, Cyber Liquids, Cyber Love Live, Cyber Laser Dragon, Cyberlock, Cyber Liability Insurance Cost, Cyber Lawyer, Cyberlink Powerdirector, Cyber Monday 2017, Cyber Monday 3s, Cyber Monday, Cyber Monday 1s, Cyber Monday 2016, Cyber Meaning, Cyber Michigan, Cyber Marvel, Cyberman, Cybermen, Cyber News, Cyber Nico, Cyber Ninja, Cyber Nations, Cyber Ninja Hanzo, Cyber Nuke, Cyber Network, Cyber Nozomi, Cyber Net, Cyber Nanny, Cyber Operations, Cyber Optics Detroit, Cyber Operations Officer, Cyber Optics, Cyber Ops, Cyber Operations Specialist, Cyber Outlet, Cyber Ogre, Cyber Operations Specialist Salary, Cyber Officer Air Force, Cyberpower, Cyberpunk, Cyber Police, Cyber Physical Systems, Cyberpatriot, Cyber Pegasus, Cyberpunk 2077, Cyber Playground, Cyberpower Ups, Cyber Pink, Cyber Quest, Cyberq, Cyber Quest Soaring Eagle, Cyber Quotes, Cyber Queen, Cyberquery, Cybex Q Cloud, Cyber Questions, Cyber Quest Fort Gordon, Cyberq Manual, Cyber Research, Cyber Risk, Cyber Resilience, Cyber Range, Cyber Risk Management, Cyber Rain, Cyber Recruiter, Cyber Risk Insurance, Cyber Repair Plant, Cyber Rider Turbo, Cyber Security, Cyber Security Jobs, Cyber Security Salary, Cyber Security Degree, Cyber Security Training, Cyber Security News, Cyber Stalking, Cyber Security Certifications, Cyber Security Companies, Cyber Safety, Cyber Terrorism, Cyber Tech, Cyber Threat, Cyber Transport Systems, Cyber Terrorism Definition, Cyber Terminators, Cyber Threat Intelligence, Cyber Technology, Cyber Theft, Cyber Threat Alliance, Cyber Umi, Cyber University, Cyber U, Cyber Ups, Cyber Bullying, Cyber Umi Cosplay, Cyber Underground, Cyber Unit, Cyber Usa, Cyber Underwriter Salary, Cyber Valley, Cyber Vandalism, Cyber Violence, Cyber Vpn, Cyber Vulnerability, Cyber Victimization, Cyber Village Academy, Cyber Virus, Cyber Vision, Cyber Vulnerability Assessment, Cyber Warfare, Cyberweld, Cyber Woman With Corn, Cyber World, Cyber Warfare Definition, Cyber World Institute, Cyber Warrior, Cyber Weapons, Cyber Wars, Cyber Wallpaper, Cyber X, Cyber Xmen, Cyber X Games, Cyber X Link, Cyber X Designs, Cyber X 3d, Cyborg X Trailer, Cyber X Internet Cafe, Cyber X Games 2017, Cyber Xl, Cyber Yugioh, Cyber Yellow, Cyber Yog, Cyber Yugioh Cards, Cyber Yankee, Cyber Yankee 2017, Cyber Yellow Vans, Cyber Youtube, Cyber Youcam, Cyber You, Cyber Zilla, Cyber Zone, Cyber Zarya, Cyber Zombie, Cyber Z, Cyber Zoom, Cyberzone Internet Cafe, Cyber Zone Hours, Cyber Zilla Toy, Cyber Zone Opelika, Isil Meaning, Isil Definition, Isil News, Isil Vs Isis, Isil Isis, Isis Map, Isil Akbulut, Isil Leader, Isil Stock, Isis Flag, Isil Akbulut, Isil Acronym, Isil Attacks, Isil Abbreviation, Isil Aktan, Isil Alev, Isil Afghanistan, \U0131\u015f\u0131l Alben, Isis Apush, Isil Aksoy, Isil Bagdadi, Isis Band, Isis Bombing, Isil Bs Isis, Isil Blackboard, Isil Berkun, Isis Build, Isis Beliefs, Isis Button, Isis Beauty, Isil Certification, Isil Chemical Weapons, Isis Coney Island, Isis Cartoon, Isil Conflict, Isis Capital, Isil Capabilities, Isis Control Map, Isis Caliphate, Isis Chan, Isil Definition, Isil Dillig, Isis Definition, Isil Daesh, Isil Define, Isil Dipietro, Isis Dearborn, Isis Damil, Isil Dilek, Isis Drones, Isil Erel, Isil Egypt, \U0131\u015f\u0131l E\u011frikavuk, Isis Egypt, Isis Explained, Isis Exchange, Isis Excussion, Isis Europe, Isis Edc, Isis Events, Isis Flag, Isil Fighters, Isil Funding, Isil Finances, Isil Full Form, Isis Facts, Isil Founder, Isis Fighters, Isis Fails, Isis Founder, Isis Goddess, Isil Group, Isis Goals, Isil Guney, Isis Gallardo, Isis Genocide, Isis Goat Meme, Isis Getting Shot, Isis Getting Bombed, Isis Goat, Isil Halac Md, Isis Harambe, Isis History, Lsil Hpv, Isis Hair, Isis Hit List, Isis Hunting Permit, Isis Heavy, Isil Hamdemir, Isis Hostages, Isil Isis, Isil In Yemen, Isil In Syria, Isil In Afghanistan, Isil In Iraq, Isil In Libya, Isil Ideology, Isil In Mosul, Isil Insurgency In Tunisia, Isil In Egypt, Isil Jordan, Isil Job, Isil Journal, Isil Jesus Maria, Isil Je, Isis Jokes, Isil Japan, Isil Japanese, Isis Jordan Pilot, Isis Japanese Hostage, Isis K, Isis King, Isil Karaca, Isis Kurds, Isis Kids, Isis Kidnapping, Isis Knot, Isis Keyshia, Isis Kneading, Isis King Net Worth, Isil Leader, Isil Libya, Isil Leader Killed, Isil Latest News, Isil Lima Peru, Isil Lima, Isil Lu, Isil Leader Dead, Isis Leader Killed, Isis Logo, Isil Meaning, Isis Memes, Isis Meaning, Isis Map, Isis Mosul, Isil Meaning In English, Isil Meaning Levant, Isis Music, Isis Members, Isis Magazine, Isil News, Isil Name, Isil Numbers, Isil Nal, Isil Not Isis, Isis Names, Isil Name Meaning, Isis Net Worth, Isis Navy, Isil News Now, Isil Origin, Isil Or Isis, Isle Of Man, Isil Or Isis What Is The Difference, Isil Oz, Isis Origin, Isis Osiris, Isis Oceanic, Isis Oil, Isis Oracle, Isil Peru, Isis Propaganda, Isis Papers, Lsil Pap, Isil Photos, Isil Pakistan, Isil Palmyra, Isis Persona 5, Isis Pharmaceuticals, Isis Pictures, Isis Quotes, Isis Queen, Isis Quizlet, Isis Quran, Isis Questions, Isis Quartz, Isis Qaraqosh, Isis Quick Facts, Isis Qatar, Isis Queen Of Heaven, Isil Recber, Isil Russia, Isis Religion, Isis Recruitment, Isis Recruitment Video, Isis Raqqa, Isis Rea Boykin, Isil Stands For, Isil Stock, Isil Stock Price, Isil Sinai Province, Isis Sunni, Isil Saudi Arabia, Isil Symbol, Isis Shia, Isil Size, Isis Social Media, Isis Territory, Isil Terrorism, Isil Target Russia, Isis Tv Show, Isis Twitter, Isil Territorial Claims, Isil Turkish Name, Isil Today, Isis Theme Song, Isil Tunisia, Isil Uzum, Isil Uk, Isis Uf, Isis Unveiled, Isis Update, Isis Using Drones, Isis Uniforms, Isis Uk, Isis Us, Isis Uiowa, Isil Vs Isis, Isil Videos, Isil Vs Isis Wiki, Isil Vs Isis Snopes, Isil Vs Isis Reddit, Isis Violence, Isil Vs Iran, Isil Vs Isis Israel, Isil Videos Of Executions, Isil Vs Isis Meaning, Isil Wiki, Isil War, Isis Website, Isil What Does It Stand For, Isil Waxman, Isis Wigs, Isis War, Isis Wings, Isis Waswas, Isis Women, Isil Xmas, Isil Xi Lu, Isil Xinjiang, Xidigaha Isil, Isil And Isis, Isil X\u30c7\u30fc, Isil Yemen, Isil Yucesoy, Isil Yildiz Yale, Isil Yucesoy Biography, Isil Yucesoy Funeral, Isil Yildiz, Isil Youtube, Isil Yavuz, Isis Yilmaz, Isil Zastava, Isil Zaprijetio Balkanu, Isil Znacenje, Entil’zha, Isil Zorlu, Isil Zionist, Isil Zakat, Isil Zapalio Zarobljenika














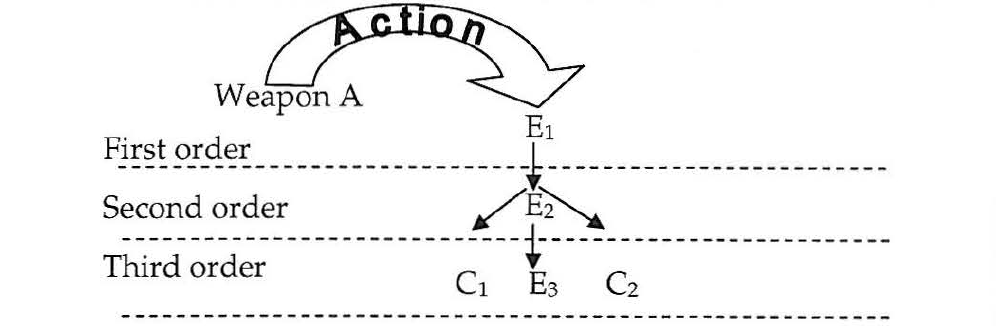
 A restricted document from U.S. Strategic Command provides insight into the underlying philosophy of military efforts to wage cyber warfare.
A restricted document from U.S. Strategic Command provides insight into the underlying philosophy of military efforts to wage cyber warfare.









You must be logged in to post a comment.