America’s Investigative Reports covers the photojournalists who created Unembedded, a book and photo exhibit by four independent photojournalists on the war in Iraq.
Month: April 2013
Cryptome – Can drone flight paths be private?
Will Drones Assassinate When Pigs Fly?
Date: Sun, 21 Apr 2013 22:49:37 -0500
From: Gregory Foster
To: drone-list[at]lists.stanford.edu
Subject: [drone-list] Can drone flight paths be private?
WSJ (Apr 18) – “Why Jet Owners Don’t Want to be Tracked”:
http://online.wsj.com/article/SB10001424127887323820304578410633003
145370.html
Earlier this week, while some drone pundits were seizing the moment to advocate for law enforcement access to drone technology, this article was also being passed around. Although the article is full of examples of corporations that allege security threats to their employees, the most often re-cited concern was an assassination plot, “a retaliatory act meant to dissuade Lockheed Martin from producing drone weaponry.”
The article is sourced from a 2011 FOIA request to the FAA, so the timing of the article’s release and promotion struck me as trying to generate sympathy for the woes endured by drone manufacturers.
The intent of Rupert Murdoch’s WSJ aside, the other examples of corporate insecurity in this article warrant reading. From big pharma, to the fossil-fuel energy giants, to Disney – they’re all concerned (I’m sure quite reasonably) that there are people out there who are quite angry with them.
I also highlight this article because of discussions that circulated on this list a few months ago concerning just how the FAA intends to track tens of thousands of private and public drones in American skies – and just how much transparency the public can expect to receive into that flight path information. This article confirms that the FAA does maintain exceptions to disclosure of flight path information for privately owned jets, and all the owner has to do is fill out what sounds like a very simple form. The FAA does not question the legitimacy of any request, just makes sure the form is filled out. I don’t see why we should expect that policy to change for privately owned drones.
Here’s the question I have: can the FAA regulate my ability to see, with my own eyes (or a camera, or a radio receiver), what is in the sky? I don’t think so.
And my follow up question: can the FAA regulate my ability to tell someone else, with my own voice (or an email, or a database), what I saw in the sky?
If not, I think we should crowdsource observed and correlated flight paths.
After all, communities are being asked to assume the costs of operating 149 air-traffic control towers by June 15, or they will be shut down.
Those costs run to the tune of $30-40M and the jobs of 1,000 air-traffic controllers.
http://articles.washingtonpost.com/2013-04-05/local/38299065_1_contract-towers-
air-traffic-control-towers-149-air-traffic-control-towers
Seems like a good opportunity to do things differently.
gf
—
Gregory Foster || gfoster[at]entersection.org
[at]gregoryfoster http://entersection.com/
—
Want to unsubscribe? Want to receive a weekly digest instead of daily emails? Change your preferences: https://mailman.stanford.edu/mailman/listinfo/drone-list or email companys[at]stanford.edu
__________
From: “Al Mac Wow”
To: “‘drone-list'”
Date: Mon, 22 Apr 2013 02:41:19 -0500
Cc: ‘Bob Speth’
Subject: Re: [drone-list] Can drone flight paths be private?
> When is it reasonable for a drone flight path to be kept confidential?
The only time drones should be carrying passengers is when they are used as air ambulances to transport victims to hospital, more rapidly than ground transportation is capable of.
Such vehicles should be marked on the bottom with a red cross, and/or medical caduceus, so it is crystal clear to everyone what their function is.
Outside the USA, drones are already being used to transport medical supplies to hard to reach places, in support of disaster recovery.
> Can the FAA regulate my ability to see, with my own eyes (or a camera, or a radio receiver), what is in the sky? I don’t think so.
The military has stealth drones. This means they are microscopic on radar. Some of them look like the same color as clouds, and blue sky. I know that technology exists to have something change color, as the background changes, adaptive camouflage. I do not know if that has been incorporated into drones, how expensively prohibitive it might be.
I do not know if it is legal for big corporations to have private stealth jets. If there is no regulation against it, I guess it is.
With stealth there is a risk of collision between such aircraft controlled by different interests, and there have already been several near misses.
> Can the FAA regulate my ability to tell someone else, with my own voice (or an email, or a database, or blog), what I saw in the sky?
Currently in some US states, if we are driving and we see a police radar trap for motorists traveling at speeds in excess of posted limits, and we communicate this info to motorists who have not yet driven into the trap, this action is in violation of the law.
Making something illegal does not put a stop to the activity.
Al Mac (
__________
List-Archive:
List-Subscribe: ,
FEMEN TV – ToplessJihad from Paris
Unveiled – UNODC Afghanistan Opium Risk Assessment 2013
In 2013, the Opium Risk Assessment was carried out in two phases similar to the year before. The first phase was implemented between December 2012 and January 2013 and covered the Central, Eastern, Southern and Western region, where opium was sown in fall 2012.
The second phase took place in February-March 2013 and covered the Northern and North-eastern regions, where opium poppy is mainly cultivated in spring. This report presents the findings of both phases. According to the 2013 Opium Risk Assessment increases in poppy cultivation are expected in most regions and in the main poppy-growing provinces.
In the Southern region, the Risk Assessment indicated that the largest opium cultivating provinces, Hilmand and Kandahar, are likely to see an increase in opium cultivation due to the current high price of opium and to compensate the low opium yield in 2012 which was caused by a combination of a disease of the opium poppy and unfavourable weather conditions. An increase in opium poppy cultivation is also expected in Uruzgan and Zabul province. No major changes are expected in Daykundi province. In the western provinces, namely in Farah and Ghor, opium cultivation is also expected to increase. A decrease in opium poppy cultivation is however expected in Hirat province. Increasing trends were reported from Nangarhar and Kapisa provinces in the Eastern region. No major changes in opium cultivation are expected in Nimroz, Badghis, Kabul, Kunar and Laghman provinces.
Balkh and Faryab in northern region are likely to see an increase in opium cultivation in 2013. These two provinces may lose their poppy-free status if timely effective eradication is not implemented. No major changes are expected in Baghlan province. The largest cultivating province in the north-east, Badakhshan is likely to see an increase in opium cultivation in 2013. The increase in opium cultivation is also expected in Takhar province. Takhar may lose its poppy-free status unless effective eradication is implemented in time. The remaining provinces in the northern and north-eastern regions are expected to remain poppy-free in 2013.
The Risk Assessment 2013 indicated that a strong association between insecurity, lack of agricultural assistance and opium cultivation continues to exist. Villages with a low level of security and those which had not received agricultural assistance in the previous year were significantly more likely to grow poppy in 2013 than villages with good security and those, which had received assistance. Similarly, villages which had been reached by anti-poppy awareness campaigns were significantly less likely to grow poppy in 2013.
Fear of eradication was the most frequent reason reported for not cultivating poppy in 2013 in Southern, Western, Eastern and Central region, unlike in previous years, when eradication was rarely mentioned by respondents. The large increase in eradication in 2012 compared to previous years and the fact that it happened in major poppy cultivating areas are likely reasons for this result. However, in the Northern and North-eastern region the most frequent reason for not cultivating opium was “ not enough yield in the previous year” followed by the government’s opium ban.
The findings of the 2013 Opium Risk Assessment in the Southern, Eastern, Western and Central regions points to a worrying situation. The assessment suggests that poppy cultivation is not only expected to expand in areas where it already existed in 2012, e.g. in the area north of the Boghra canal in Hilmand province or in Bawka district in Farah province but also in new areas or in areas where poppy cultivation was stopped. In eastern Afghanistan, in Nangarhar province, farmers resumed cultivation even in districts where poppy has not been present for the last four years. In the Northern and Northeastern region, the provinces of Balkh and Takhar which were poppy-free for many years are at risk of resuming poppy cultivation.
On a more positive note, some provinces with a low level of poppy cultivation, namely Ghor, Kabul, Kapisa, Hirat Zabul and Baghlan may gain poppy-free status in 2013 if effective eradication is implemented on time.
Video Skid – Monty Python – Organ Donor
Video – Report – Tips from Bob Woodward on Investigative Journalism
Bob Woodward explains the three ways journalists get their information and comments on the future of in-depth journalism in the digital age.
Unveiled – Fukushima Daiichi Nuclear Power Station Early Photos
On February 1, 2013, Tokyo Electric Power released over 100 Zipped files containing several hundred photos of the Fukushima Daiichi Nuclear Power Station taken from time of the tsunami on March 11, 2011 to April 11, 2011. They are among the earliest TEPCO photos which show the initial damage by the tsunami, aftermath of the explosions and efforts to survey, control and stabilize the plant. Most have not been widely published. These are selections.
Source: http://photo.tepco.co.jp/en/date/2013/201302-e/130201-01e.html
Compare to high-resolution aerial photos taken March 24-30, 2011:
http://cryptome.org/eyeball/daiichi-npp/daiichi-photos.htm
Fukushima Daiichi Nuclear Power Station Early Photos
Photos of March 15, 2011. Captions by TEPCO.
Appearance of Unit 3 Reactor Building after explosion. Photo taken on 2011.3.15
Video – How PR Came to Rule Modern Journalism
“You can’t believe everything you read in the papers.” Everyone knows this, but few people realise this truism extends far beyond the celebrity pages and gossip columns, and spills into ‘real’ news. Here, the near-invisible influence of PR companies is often pivotal in deciding what news gets told, and how it gets reported. By taking a brief look at the history of modern journalism, and using real examples taken from recent headlines, Michael Marshall will show why you really, really can’t believe everything you read in the papers.
Michael Marshall is the co-founder and vice-president of the Merseyside Skeptics Society and appears on the Skeptics with a K and Strange Quarks podcasts. Besides organising national and international campaigns against homeopathy, he writes about the often-unsuspected role of PR in modern media. He was once called by Ben Goldacre ‘a mighty nerd from Liverpool’. He was also once rather amusingly called a very rude word by self-proclaimed psychic Joe Power.
QED is a two-day science and skepticism conference taking place in the Piccadilly Hotel, Manchester on the 10th-11th March 2012.
Fantastic speakers from the worlds of science and entertainment will be joining us for a weekend celebration of science, reason and critical thinking.
FEMEN TV : Topless Jihad. Berlin
The Revolution fuelled by bare breasts!
The single has to become common. Aminas name became the name of all women in North Africa, the fate of Amina was their destiny. The act of Amina showed the picture of the shariatization of countries of the “Arab spring” that means religious torturing for women. This Act became the beginning of a global war between a woman and an Islamist theocracy, the riot of freedom from slavery!
4 April-international solidarity action with Amina Tyler and with all current and future victims of Islamization.
We have appealed to the world for support and the world has answered! The fate of the Femen – Tunisia activist Amina Tyler has shaken up and united thousands of women across the globe. Amina’s act of civil disobedience has brought down upon her the lethal hatred of inhuman beasts for whom killing a woman is more natural than recognizing her right to do as she pleases with her own body. For them, we now see, the love of freedom is the most dangerous kind of psychiatric illness, one demanding radical forced treatment in the spirit of fascist punitive medicine. The “Arab Spring,” for the women of North Africa, has turned out to be a frigid sharia winter that has deprived them of what few political rights and liberties they enjoyed.
Revealed – DHS-FBI Indicators and Protective Measures In Light of Boston Marathon Explosions
(U//FOUO) This Joint Intelligence Bulletin provides law enforcement and private sector safety officials with protective measures in light of the recent explosions that took place at the 2013 Boston Marathon in Boston, Massachusetts. The information is provided to support the activities of DHS and FBI and to assist federal, state, local, tribal, and territorial government counterterrorism and first responder officials and the private sector to deter, prevent, preempt, or respond to terrorist attacks in the United States.
(U) Incident Details
(U) On 15 April 2013, at approximately 2:45 pm, two explosions occurred in quick succession near the finish line of the Boston Marathon, killing at least three people and causing numerous injuries.
(U) Ongoing Concerns with Terrorism in the Homeland
(U//FOUO) The activities in Boston highlight the use of improvised explosive devices (IEDs) to target large gatherings, including at special events, in order to inflict mass casualties. Examples of previously attempted or plotted IED attacks include:
— (U//FOUO) The undetonated IED discovered along the planned 2011 “Martin Luther King Jr. Unity March” parade route in Spokane, Washington;
— (U//FOUO) The November 2010 plot to detonate a vehicle-borne IED (VBIED) at an annual Christmas tree lighting ceremony in Portland, Oregon;
— (U//FOUO) The October 2010 plot to conduct multiple mass casualty bombings at Metrorail stations in Washington, DC;
— (U//FOUO) The May 2010 attempted detonation of a vehicle-borne IED in Times Square; and
— (U//FOUO) The September 2009 plot to attack the New York City subway using IEDs.
(U//FOUO) Indicators of Pre-Operational Surveillance and Attack Planning
(U//FOUO) Given these events, we are providing indicators and protective measures to aid law enforcement and first responders in identifying and mitigating potential threats. Each indicator listed below may be by itself, lawful conduct or behavior and may also constitute the exercise of rights guaranteed by the US Constitution. In addition, there may be a wholly innocent explanation for conduct or behavior that appears suspicious in nature. For this reason, no single indicator should be the sole basis for law enforcement action. The totality of behavioral indicators and other relevant circumstances should be evaluated when considering any law enforcement response or action.
(U//FOUO) Possible indicators of pre-operational surveillance or attack planning include:
— (U//FOUO) Unusual or prolonged interest in or attempts to gain sensitive information about security measures of personnel, entry points, peak days and hours of operation, and access controls such as alarms or locks;
— (U//FOUO) Observation of security reaction drills or procedures; multiple false alarms or fictitious emergency calls to same locations or similar venues;
— (U//FOUO) Discreet use of cameras or video recorders, sketching, or note-taking consistent with pre-operational surveillance;
— (U//FOUO) Interest in speaking with building maintenance personnel;
— (U//FOUO) Observation of or questions about facility security measures, to include barriers, restricted areas, cameras, and intrusion detection systems;
— (U//FOUO) Observations of or questions about facility air conditioning, heating, and ventilation systems;
— (U//FOUO) Suspicious purchases of items that could be used to construct an explosive device, including hydrogen peroxide, acetone, gasoline, propane, or fertilizer;
— (U//FOUO) Suspicious activities in storage facilities or other areas that could be used to construct an explosive device; and
— (U//FOUO) Attempted or unauthorized access to rooftops or other potentially sensitive areas.DHS-FBI-BostonMarathonIndicators
Video Skid – Monty Python Crackpot Religions LTD
Video Skid – Monty Python – Bruce
“Peter Ehlers” – “Das Investment” im Mehrheitsbesitz des Fondsvertriebs “SJB”: Bundeskanzlerin Merkel ist Hehler Nr.1
“Sind Bundeskanzlerin Angela Merkel und Finanzminister Wolfgang Schäuble Deutschlands bekannteste Hehler ?” „Sicher nein“, werden Sie jetzt sagen und fragen: „Wer behauptet diesen staatszersetzenden Schwachsinn ?“„Fonds & Friends-Herausgeber“ Peter Ehlers (wenn der Name stimmt ?) und der Ost-Berliner NACHRICHTENDIENST” “GoMoPa” bezeichneten die deutsche Bundeskanzlerin Angela Merkel und den deutschen Bundesfinanzminister Wolfgang Schäuble als “kriminelle Hehler” und als Deutschlands „bekannteste Hehler“. Original-Zitat Peter Ehlers (wenn denn wengistens der Name stimmt ?) : „Wolfgang Schäuble, Finanzminister unter Kanzlerin Angela Merkel. Beide sind sich nicht immer einig. Jetzt schon: Sie wollen als Staat, von deutschen Steuergeldern bezahlt, ein neues staatliches Geschäft eröffnen: Hehlerei.Peter Ehlers,Herausgeber DAS INVESTMENTEin Kommentar von Peter Ehlers, Herausgeber DAS INVESTMENTEin durchaus einträgliches Geschäft, das nur einen Haken hat: Es ist illegal. Schäuble hat dafür eine lustige Rechtsauffassung: Er sieht den Deal, den der damalige Finanzminister Peer Steinbrück („das beste Geschäft meines Lebens“) machte, für sich als Rechtfertigung. Frei nach dem billigen Motto: Wenn mein Vorgänger kriminell war, darf ich das ja wohl auch sein.“Das heisst nicht nur Schäuble handelt illegal und kriminell – im ganz grossen Stil, sondern auch die Vorgänger Ex-Bundes-Finanzminister Peer Steinbrück und Ex-Bundeskanzler gerhard Schröder…Und mich bezeichnet Peter Ehlers (wenn denn wengistens der Name stimmt ?) als “Internet-Terroristen”, „Erpresser“, „Gewohnheitsverbrecher“ und „Idioten“, ach ja meinen akademischen Titel Magister Artium täusche ich auch vor, sagen Peter Ehlers und GoMoPa, unisono..
Dies ist bezeichnet für die psychotische Wahnwelt dieser mutmasslich kommunistischen Delinquenten aus dem Osten Deutschlands.
Cryptome – Alleged Cuban Spy Marta Rita Velazquez Indicted
Alleged Cuban Spy Marta Rita Velazquez Indicted
Related:
http://cryptome.org/montes/usa-v-montes.htm
http://cryptome.org/myers/usa-v-myers.htm
http://www.fbi.gov/washingtondc/press-releases/2013/unsealed-indictment-charges-
former-u.s.-federal-employee-with-conspiracy-to-commit-espionage-for-cuba
Unsealed Indictment Charges Former U.S. Federal Employee with Conspiracy to Commit Espionage for Cuba
Defendant Allegedly Helped Cuban Intelligence Service Recruit and Insert Spy into U.S. Defense Intelligence Agency
U.S. Department of Justice April 25, 2013
Office of Public Affairs (202) 514-2007/ (202) 514-1888
WASHINGTON—A one-count indictment was unsealed today in U.S. District Court for the District of Columbia charging Marta Rita Velazquez, 55, with conspiracy to commit espionage, announced John Carlin, Acting Assistant Attorney General for National Security; Ronald C. Machen, Jr., U.S. Attorney for the District of Columbia; and Valerie Parlave, Assistant Director in Charge of the FBI’s Washington Field Office.
The charges against Velazquez stem from, among other things, her alleged role in introducing Ana Belen Montes, now 55, to the Cuban Intelligence Service (CuIS) in 1984; in facilitating Montes’s recruitment by the CuIS; and in helping Montes later gain employment at the U.S. Defense Intelligence Agency (DIA). Montes served as an intelligence analyst at DIA from September 1985 until she was arrested for espionage by FBI agents on September 21, 2001. On March 19, 2002, Montes pleaded guilty in the District of Columbia to conspiracy to commit espionage on behalf of Cuba. Montes is currently serving a 25-year prison sentence.
The indictment against Velazquez, who is also known as “Marta Rita Kviele” and as “Barbara,” was originally returned by a grand jury in the District of Columbia on February 5, 2004. It has remained under court seal until today. Velazquez has continuously remained outside the United States since 2002. She is currently living in Stockholm, Sweden. If convicted of the charges against her, Velazquez faces a potential sentence of up to life in prison.
According to the indictment, Velazquez was born in Puerto Rico in 1957. She graduated from Princeton University in 1979 with a bachelor’s degree in political science and Latin American studies. Velazquez later obtained a law degree from Georgetown University Law Center in 1982 and a master’s degree from Johns Hopkins University School of Advanced International Studies (SAIS) in Washington, D.C., in 1984.
Velazquez later served as an attorney advisor at the U.S. Department of Transportation, and, in 1989, she joined the State Department’s U.S. Agency for International Development (USAID) as a legal officer with responsibilities encompassing Central America. During her tenure at USAID, Velazquez held a top secret security clearance and was posted to the U.S. Embassies in Nicaragua and Guatemala. In June 2002, Velazquez resigned from USAID following press reports that Montes had pleaded guilty to espionage and was cooperating with the U.S. government. Velazquez has remained outside the United States since 2002.
The indictment alleges that, beginning in or about 1983, Velazquez conspired with others to transmit to the Cuban government and its agents documents and information relating to the U.S. national defense, with the intent that they would be used to the injury of the United States and to the advantage of the Cuban government.
As part of the conspiracy, Velazquez allegedly helped the CuIS spot, assess, and recruit U.S. citizens who occupied sensitive national security positions or had the potential of occupying such positions in the future to serve as Cuban agents. For example, the indictment alleges that, while Velazquez was a student with Montes at SAIS in Washington, D.C., in the early 1980s, Velazquez fostered a strong, personal friendship with Montes, with both sharing similar views of U.S. policies in Nicaragua at the time.
In December 1984, the indictment alleges, Velazquez introduced Montes in New York City to a Cuban intelligence officer who identified himself as an official of the Cuban Mission to the United States. The intelligence officer then recruited Montes. In 1985, after Montes’ recruitment, Velazquez personally accompanied Montes on a clandestine trip to Cuba for Montes to receive spy craft training from CuIS.
Later in 1985, Velazquez allegedly helped Montes obtain employment as an intelligence analyst at the DIA, where Montes had access to classified national defense information and served as an agent of the CuIS until her arrest in 2001. During her tenure at the DIA, Montes disclosed the identities of U.S. intelligence officers and provided other classified national defense information to the CuIS.
During this timeframe, Velazquez allegedly continued to serve the CuIS, receiving instructions from the CuIS through encrypted, high-frequency broadcasts from her handlers and through meetings with handlers outside the United States.
This case was investigated by the FBI’s Washington Field Office and the DIA. It is being prosecuted by Senior Trial Attorney Clifford Rones of the Counterespionage Section in the Justice Department’s National Security Division and Assistant U.S. Attorney G. Michael Harvey of the U.S. Attorney’s Office for the District of Columbia.
The charges contained in an indictment are merely allegations, and each defendant is presumed innocent unless and until proven guilty in a court of law.
[Image]
Real Heroes – Boston Blasts – Bystanders Giving Aid
Date: Mon, 22 Apr 2013 19:23:25 -0400
Subject: Number 5 (Man in blue, Boston Blasts: Bystanders Giving Aid)
From the page http://cryptome.org/2013-info/04/boston-bystanders/boston-bystanders.htm
Number 5 (man in blue with shorts, not jeans) is goaltender Matt Reis of the New England Revolution (Major League Soccer), who’s wife was running in the Boston Marathon:
http://www.revolutionsoccer.net/players/matt-reis
Per an interview he gave to the media:
http://www.mlssoccer.com/news/article/2013/04/17/new-england-revolution-goalkeeper-matt-
reis-says-support-injured-father-law-
Matt had moved just before the explosion to get a better view of his wife crossing the finish line. The man he returns to the scene to help is his father-in-law John Odom, pictured in this Daily Mirror article:
http://www.dailymail.co.uk/news/article-2310426/Boston-bombing-John-Odom-just-weeks-
away-retirement-friends-reveal.html
Reis used his belt to tie a tourniquet around Odom’s leg in a move that likely saved his life, this can be seen in photos “4:10:26” through “4:11:13”. Odom, who suffered severe damage to his legs and lost a large amount of blood, has since been through six surgeries in an attempt to stabilize him:
http://www.easyreadernews.com/68821/friends-of-boston-marathon-survivor-john-odom-
gather-for-support/
20 April 2013
Boston Blasts: Bystanders Giving Aid
Also:
2013-0395.pdf Dzhokhar Tsarnaev Complaint via Boaz Guttman April 22, 2013 (2.0MB)
2013-0388.htm First Seconds After Boston Bomb Blast 1 April 21, 2013
2013-0380.pdf Tamerlan Tsarnaev April 19, 2013
2013-0379.htm Djohar Tsarnaev April 19, 2013
2013-0371.htm Boston Bomb Blasts 2 April 16, 2013
2013-0370.htm Boston Bomb Blasts April 16, 2013
Bystanders who aided victims of the Boston Marathon bomb blasts have not been individually recognized. Those who aided in the first four minutes deserve admiration for quick action which likely saved lives. Some are shown below.
For close-up photos of the scene with other bystanders giving aid:
http://cryptome.org/2013-info/boston-bombs/boston-bombs.htm
Overviews from which these are taken with some enlarged:
http://cryptome.org/2013-info/boston-bombs-02/boston-bombs-02.htm
The latter taken from 150 photos by Aaron “tango” Tang via Flicker
http://www.flickr.com/photos/hahatango/sets/72157633252445135/with/8652877581/





FEMEN TV : Topless Jihad Day. Milano
TOP-SECRET-DHS-FBI Information Regarding the Devices Likely Used in Boston Marathon Explosions
(U//FOUO) This Joint Intelligence Bulletin provides information on the devices used in the 15 April 2013 Boston Marathon explosions. The information is intended to provide aid in identifying devices and to support the activities of DHS and FBI and to assist federal, state, local, tribal, and territorial government counterterrorism and first responder officials and the private sector to deter, prevent, preempt, or respond to terrorist attacks in the United States.
(U//FOUO) Incident Details
(U) On 15 April 2013, at approximately 2:50 p.m., two explosions occurred in quick succession near the finish line of the Boston Marathon, killing at least three people and causing numerous injuries. Preliminary findings reveal the two devices were located less than a block apart, and functioned within approximately 10-15 seconds of each other. Both devices were concealed in backpacks and placed where spectators were gathered.
(U) Preliminary Device Details
(U//FOUO) Based on preliminary examination of photographs and on-scene reports, one improvised explosive device (IED) consisted of a pressure cooker concealed in a backpack with an as of yet determined main charge (possibly a low explosive) and improvised fragmentation, possibly including nails, BBs, and ball bearings. The other device was also housed in a metal container, but currently there is insufficient evidence to determine if it was also a pressure cooker. The fuzing system and method of initiation for the two devices are unknown at this time.
(U//FOUO) Further post-blast analysis and chemical analysis is necessary to confirm the presence of these components and the identity of the main charge explosive. Collection of evidence is ongoing and forensic and technical analysis will be forthcoming.
(U) Ongoing Concerns with Terrorism in the Homeland
(U//FOUO) The activities in Boston highlight the use of IEDs to target large gatherings, such as special events, in order to inflict mass casualties. Pressure cooker bombs are extremely common in Southwest Asia and have been used in a number of high profile bombings in India, Pakistan, and Afghanistan. They have also been referenced in extremist publications such as Inspire and the The Anarchist Cookbook. Examples of previously attempted or plotted IED attacks using pressure cookers include:
— (U//FOUO) One of three devices used in the 1 May 2010 attack in Times Square incorporated a pressure cooker containing approximately 120 firecrackers.
— (U//FOUO) On 24 May 2012, PFC Naser Jason Abdo was convicted of attempted use of a weapon of mass destruction and, on 10 August 2012, was sentenced to two consecutive sentences of life in prison, plus 60 years. He was in possession of bomb-making components, including two pressure cookers.
Die “Kolportagen”, Fabeln, Märchen und Latrinenparolen von Merkel-Hasser “Peter Ehlers”/”GoMoPa”/”Nawito”
Angela Merkel, laut “Peter Ehlers”, “Deutschlands Hehler Nr.1”
Die ZEIT und die SZ: Der Beweis: Wer wirklich und tatsächlich von S&K Geld erhielt: “GoMoPa” !
Liebe Leser,
wieder einmal versucht die dubiose “GoMoPa” und deren Handlanger, Konsorten und Komparsen mutmasslich “Peter Ehlers”, der berüchtigte Merkel-Hasser, und “Nawito” von mutmasslich eigenen Taten abzulenken und mir perfide den “Schwarzen Peter” zuzuschieben.
Wie bereits im Falle meines angeblichen falschen Magistertitels, dem Fall Meridian Capital etc pp die Liste ist endlos.
Ein Sammelsurium von Kolportagen, Fabeln, Märchen und Latrinenpatrolen…
Dabei liegen die Beweis klar auf dem Tisch:
Die renommierten und etablierten Medien wie “ZEIT” und “Süddeutsche Zeitung” haben es aufgedeckt, was hier im Fall “S &K”/”GoMoPa” wirklich lief.
http://www.zeit.de/2013/11/Finanznachrichtendienst-Gomopa
http://www.sueddeutsche.de/geld/mutmassliche-anlagebetrueger-sk-die-akte-midas-1.1620191-4
Zum Merkel-Hasser “Peter Ehlers, dessen Pseudo-Postille von dem dubiosen Fonds-Vertrieb “SJB”, Korschenbroich bei Neuss kontrolliert wird:
“Sind Bundeskanzlerin Angela Merkel und Finanzminister Wolfgang Schäuble Deutschlands bekannteste Hehler ?” „Sicher nein“, werden Sie jetzt sagen und fragen: „Wer behauptet diesen staatszersetzenden Schwachsinn ?“„Fonds & Friends-Herausgeber“ Peter Ehlers (wenn der Name stimmt ?) und der Ost-Berliner NACHRICHTENDIENST” “GoMoPa” bezeichneten die deutsche Bundeskanzlerin Angela Merkel und den deutschen Bundesfinanzminister Wolfgang Schäuble als “kriminelle Hehler” und als Deutschlands „bekannteste Hehler“. Original-Zitat Peter Ehlers (wenn denn wengistens der Name stimmt ?) : „Wolfgang Schäuble, Finanzminister unter Kanzlerin Angela Merkel. Beide sind sich nicht immer einig. Jetzt schon: Sie wollen als Staat, von deutschen Steuergeldern bezahlt, ein neues staatliches Geschäft eröffnen: Hehlerei.Peter Ehlers,Herausgeber DAS INVESTMENTEin Kommentar von Peter Ehlers, Herausgeber DAS INVESTMENTEin durchaus einträgliches Geschäft, das nur einen Haken hat: Es ist illegal. Schäuble hat dafür eine lustige Rechtsauffassung: Er sieht den Deal, den der damalige Finanzminister Peer Steinbrück („das beste Geschäft meines Lebens“) machte, für sich als Rechtfertigung. Frei nach dem billigen Motto: Wenn mein Vorgänger kriminell war, darf ich das ja wohl auch sein.“Das heisst nicht nur Schäuble handelt illegal und kriminell – im ganz grossen Stil, sondern auch die Vorgänger Ex-Bundes-Finanzminister Peer Steinbrück und Ex-Bundeskanzler gerhard Schröder…Und mich bezeichnet Peter Ehlers (wenn denn wengistens der Name stimmt ?) als “Internet-Terroristen”, „Erpresser“, „Gewohnheitsverbrecher“ und „Idioten“, ach ja meinen akademischen Titel Magister Artium täusche ich auch vor, sagen Peter Ehlers und GoMoPa, unisono..
Dies ist bezeichnet für die psychotische Wahnwelt dieser mutmasslich kommunistischen Delinquenten aus dem Osten Deutschlands.
Nachdem zahlreiche Internetangriffe nichts gebracht haben, nun wieder dieser Unsinn.
Hier noch einmal meine Stellungnahme zu der “GoMoPa”/Ehlers/Nawito-Absurdistan-Agit-Propaganda:
Dear Readers,
let me just briefly comment a mental cyberattack which should distract your attention from the real issues.
I have never had any consulting position or contract for any German company.
I have never worked for the Axel Springer Publishing House – not even as a freelance journalist.
These facts are clear and can be verified easily – just by calling Axel Springer.
The facts are
1) Dr. Rainer Zitelmann worked for the Axel Springer Company. You can esaily find out what happened there. I just mention the word “Auschwitz” in this context…As you see from his website and in the internet Zitelmann is in fact consulting many German companies.
2) “GoMoPa” had in fact a consultation contract with estavis and got in fact money from estavis and many various companies i.e. “S&K”
These contracts are known and 100% true and published by various media i.e. “ZEIT”, “MANAGER MAGAZIN”, “SUEDDEUTSCHE ZEITUNG” etc.
3) Meridian Capital was the subject of “GoMoPa”s articles.
4) “Nawito” whover or whatever it is did not even bother to contact us.
5) The “information” about one of our companies is false.
6) The “Nawito” informer “Peter Ehlers” did in fact attack Chancellor Merkel and the Minister of Finance Wolfgang Schäuble as “Deutschlands bekannteste Hehler” to name just one fact about “Peter Ehlers” or whatever his name might be who by the way got a lot of money from the bancrupt SAM AG which was also subject of “GoMoPa”‘s reporting and we know similiar cases of this endeavour.
7) The last editor who was attacked by such cyberattacks died in a very mysterious way, Heinz Gerlach. He might have been controversial but nevertheless – the truth is the truth.
He was the first journalist to publish the truth about the mysterious headquarter of “GoMoPa” in New York and their consulting contract with estavis and died suddenly and totally unexpected for most of us – not for all.
The circumstances of his death remain unsolved for me.
We are ready to proof this everytime and do not work with “colportations”.
Obviously cyberattacks on our websites since years are not enough to keep the truth down – defamation must be added – a wellknown STASI technique to irritate the public – MENTAL AND PYSICAL CYBERATTACKS done by the well-know suspects.
Sincerely your
Bernd Pulch
Magister Artium der Publizistik, Germanistik und Komparatistik
PS
COPIES OF PHYSICAL CYBER ATTACKS ON OUR SERVERS BY THE SUSPECTS AND “INFORMERS” OF “NAWITO”
graph eastern
graph 3
graph2
graph
The attacked website are for example:
http://www.investment-magazin.tv
and about 20 more.
Monty Python – Execution in Russia – Video Skid
STATEMENT ZU DEN “KOLPORTAGEN”, FABELN, MÄRCHEN UND LATRINENPAROLEN DER “GoMoPa”-“NAWITO”
Liebe Leser,
wieder einmal versucht die dubiose “GoMoPa” und deren Handlanger, Konsorten und Komparsen mutmasslich “Peter Ehlers” und “Nawito” von mutmasslich eigenen Taten abzulenken und mir perfide den “Schwarzen Peter” zuzuschieben.
Wie bereits im Falle meines angeblichen falschen Magistertitels, dem Fall Meridian Capital etc pp die Liste ist endlos.
Ein Sammelsurium von Kolportagen, Fabeln, Märchen und Latrinenpatrolen…
Dabei liegen die Beweis klar auf dem Tisch:
Die etablierten Medien wie “ZEIT” und “Süddeutsche Zeitung” haben es aufgedeckt, was hier im Fall “S &K”/”GoMoPa” wirklich lief.
http://www.sueddeutsche.de/geld/mutmassliche-anlagebetrueger-sk-die-akte-midas-1.1620191-4
http://www.sueddeutsche.de/geld/mutmassliche-anlagebetrueger-sk-die-akte-midas-1.1620191-4
Nachdem zahlreiche Internetangriffe nichts gebarcht haben, nun wieder dieser Unsinn.
Hier noch einmal meine Stellungnahme zu der “GoMoPa”/Ehlers/Nawito-Absurdistan-Agit-Propaganda:
Dear Readers,
let me just briefly comment a mental cyberattack which should distract your attention from the real issues.
I have never had any consulting position or contract for any German company.
I have never worked for the Axel Springer Publishing House – not even as a freelance journalist.
These facts are clear and can be verified easily – just by calling Axel Springer.
The facts are
1) Dr. Rainer Zitelmann worked for the Axel Springer Company. You can esaily find out what happened there. I just mention the word “Auschwitz” in this context…As you see from his website and in the internet Zitelmann is in fact consulting many German companies.
2) “GoMoPa” had in fact a consultation contract with estavis and got in fact money from estavis and many various companies i.e. “S&K”
These contracts are known and 100% true and published by various media i.e. “ZEIT”, “MANAGER MAGAZIN”, “SUEDDEUTSCHE ZEITUNG” etc.
3) Meridian Capital was the subject of “GoMoPa”s articles.
4) “Nawito” whover or whatever it is did not even bother to contact us.
5) The “information” about one of our companies is false.
6) The “Nawito” informer “Peter Ehlers” did in fact attack Chancellor Merkel and the Minister of Finance Wolfgang Schäuble as “Deutschlands bekannteste Hehler” to name just one fact about “Peter Ehlers” or whatever his name might be who by the way got a lot of money from the bancrupt SAM AG which was also subject of “GoMoPa”‘s reporting and we know similiar cases of this endeavour.
7) The last editor who was attacked by such cyberattacks died in a very mysterious way, Heinz Gerlach. He might have been controversial but nevertheless – the truth is the truth.
He was the first journalist to publish the truth about the mysterious headquarter of “GoMoPa” in New York and their consulting contract with estavis and died suddenly and totally unexpected for most of us – not for all.
The circumstances of his death remain unsolved for me.
We are ready to proof this everytime and do not work with “colportations”.
Obviously cyberattacks on our websites since years are not enough to keep the truth down – defamation must be added – a wellknown STASI technique to irritate the public – MENTAL AND PYSICAL CYBERATTACKS done by the well-know suspects.
Sincerely your
Bernd Pulch
Magister Artium der Publizistik, Germanistik und Komparatistik
PS
COPIES OF PHYSICAL CYBER ATTACKS ON OUR SERVERS BY THE SUSPECTS AND “INFORMERS” OF “NAWITO”
The attacked website are for example:
http://www.investment-magazin.tv
and about 20 more.
Der Beweis: Wer wirklich und tatsächlich von S&K Geld erhielt: “GoMoPa” !
Public Intelligence – DoD Issues Instructions on Military Support of Civilian Law Enforcement
Soldiers from the 3rd Battalion, 321st Field Artillery Regiment, XVIII Fires Brigade train last December to “respond to an escalating civil-disturbance situation caused by unhappy simulated hurricane victims.” According to an article produced by the 82nd Combat Aviation Brigade, the training was designed to prepare the soldiers “for their upcoming assignment as a quick reaction and rapid response force for U.S. Army North Command in support of emergencies in the United States.”
Public Intelligence
The Department of Defense has issued an instruction clarifying the rules for the involvement of military forces in civilian law enforcement. The instruction establishes “DoD policy, assigns responsibilities, and provides procedures for DoD support to Federal, State, tribal, and local civilian law enforcement agencies, including responses to civil disturbances within the United States.”
The new instruction titled “Defense Support of Civilian Law Enforcement Agencies” was released at the end of February, replacing several older directives on military assistance to civilian law enforcement and civil disturbances. The instruction requires that senior DoD officials develop “procedures and issue appropriate direction as necessary for defense support of civilian law enforcement agencies in coordination with the General Counsel of the Department of Defense, and in consultation with the Attorney General of the United States”, including “tasking the DoD Components to plan for and to commit DoD resources in response to requests from civil authorities for [civil disturbance operations].” Military officials are to coordinate with “civilian law enforcement agencies on policies to further DoD cooperation with civilian law enforcement agencies” and the heads of the combatant commands are instructed to issue procedures for “establishing local contact points in subordinate commands for purposes of coordination with Federal, State, tribal, and local civilian law enforcement officials.”
In addition to defining responsibilities for military coordination with local law enforcement, the instruction describes circumstances in which direct participation in civilian law enforcement is permissible. Under the Posse Comitatus Act of 1878, U.S military personnel are generally prohibited from assisting in civilian law enforcement functions such as search and seizure, interdiction of vehicles, arrest and interrogation, surveillance or using force except for in self-defense. Though the Posse Comitatus Act originally referred only to the Army, it was extended in 1956 to include the Air Force. Subsequent DoD regulations prevent the use of the Marine Corps or Navy for civilian law enforcement functions. In 1981, this principle was further codified in 10 USC § 375 which directs the Secretary of Defense to ensure that military activities do “not include or permit direct participation by a member of the Army, Navy, Air Force, or Marine Corps in a search, seizure, arrest, or other similar activity unless participation in such activity by such member is otherwise authorized by law.”
Though the Posse Comitatus Act is the primary restriction on direct DoD involvement in law enforcement functions, it does not prevent military personnel from participating in circumstances “authorized by the Constitution or Act of Congress.” This includes circumstances involving “insurrection, domestic violence, or conspiracy that hinders the execution of State or Federal law” as well as actions “taken under express statutory authority.” The DoD’s instruction includes a list of more than a dozen “laws that permit direct DoD participation in civilian law enforcement” including many obscure statutes that are more than a hundred years old. For example, a law passed in 1882 and codified under 16 USC § 593 allows for the President to use land and naval forces to “prevent the felling, cutting down, or other destruction of the timber of the United States in Florida.” Likewise, the Guano Islands Act of 1856 enables the President to use land and naval forces to protect the rights of a discoverer of an island covered by the Act.
Military commanders also have “emergency authority” to use military forces in civilian law enforcement functions “in extraordinary emergency circumstances where prior authorization by the President is impossible and duly constituted local authorities are unable to control the situation, to engage temporarily in activities that are necessary to quell large-scale, unexpected civil disturbances”. This authority is limited to actions “necessary to prevent significant loss of life or wanton destruction of property and are necessary to restore governmental function and public order” and “provide adequate protection for Federal property or Federal governmental functions.” In fact, an enclosure to the DoD instruction describing requirements for support of civil disturbance operations states that military commanders “shall not take charge of any function of civil government unless absolutely necessary under conditions of extreme emergency.” According to the instruction, any “commander who is directed, or undertakes, to control such functions shall strictly limit DoD actions to emergency needs and shall facilitate the reestablishment of civil responsibility at the earliest time possible.”
Monty Python Film – The Fish Slapping Dance
Hilarious monty python sketch. Just watch.
Unveiled – Suspect in Boston Marathon Attack Charged with Using a Weapon of Mass Destruction
WASHINGTON—Attorney General Eric Holder announced today that Dzhokhar A. Tsarnaev, 19, a U.S. citizen and resident of Cambridge, Massachusetts, has been charged with using a weapon of mass destruction against persons and property at the Boston Marathon on April 15, 2013, resulting in the death of three people and injuries to more than 200 people.
In a criminal complaint unsealed today in U.S. District Court for the District of Massachusetts, Tsarnaev is specifically charged with one count of using and conspiring to use a weapon of mass destruction (namely, an improvised explosive device, or IED) against persons and property within the United States resulting in death and with one count of malicious destruction of property by means of an explosive device resulting in death. The statutory charges authorize a penalty, upon conviction, of death or imprisonment for life or any term of years. Tsarnaev had his initial court appearance today from his hospital room.
“Although our investigation is ongoing, today’s charges bring a successful end to a tragic week for the city of Boston and for our country,” said Attorney General Eric Holder. “Our thoughts and prayers remain with each of the bombing victims and brave law enforcement professionals who lost their lives or suffered serious injuries as a result of this week’s senseless violence. Thanks to the valor of state and local police, the dedication of federal law enforcement and intelligence officials, and the vigilance of members of the public, we’ve once again shown that those who target innocent Americans and attempt to terrorize our cities will not escape from justice. We will hold those who are responsible for these heinous acts accountable to the fullest extent of the law.”
“The events of the past week underscore in stark terms the need for continued vigilance against terrorist threats both at home and abroad,” said John Carlin, Acting Assistant Attorney General for National Security. “Friday’s arrest and today’s charges demonstrate what can be achieved by a collaborative, ‘round-the-clock response involving law enforcement officers, intelligence professionals, prosecutors, and the general public.”
“Today’s charges are the culmination of extraordinary law enforcement coordination and the tireless efforts of so many, including ordinary citizens who became heroes as they responded to the call for help in the hours and days following the Marathon tragedy,” said Carmen Ortiz, U.S. Attorney for the District of Massachusetts. “The impact of these crimes has been far-reaching, affecting a worldwide community that is looking for peace and justice. We hope that this prosecution will bring some small measure of comfort both to the public at large and to the victims and their families that justice will be served. While we will not be able to comment on any possible communications between the suspect and law enforcement at this time, as a general rule, the government will always seek to elicit all the actionable intelligence and information we can from terrorist suspects taken into our custody.”
“The events of this week have moved at a breakneck pace. Yet the one consistent element of this investigation has been the collective efforts of our law enforcement and intelligence partners, working side-by-side, day and night, to identify and find those responsible for this attack, while keeping the public safe,” said Rick DesLauriers, Special Agent in Charge of the FBI’s Boston Division. “We are grateful to the American people for their assistance; we would not be successful without their trust and support. We will continue to investigate this matter with the greatest diligence and expediency, and we will do all that we can to protect those we serve.”
“Friday night’s capture of the suspect brought immediate relief to a community from a public safety viewpoint. However, much work remains and many questions require answers. Today’s charges represent another step on the long road toward justice for the victims of these crimes. On behalf of the citizens of this great commonwealth, the Massachusetts State Police will continue to work diligently with our federal and local partners to bring this defendant to justice for his alleged acts and ensure the public’s safety,” said Colonel Timothy P. Alben, Superintendent of the Massachusetts State Police.
“Finding the alleged perpetrators of this savage act of terrorism four days after the attack on the city of Boston was a herculean effort and shows the true cooperation and dedication of the law enforcement community,” said Boston Police Commissioner Ed Davis. “We were relentless in our pursuit of the suspects. The arrest of Tsarnaev and today’s charges should send a clear message to those who look to do us harm, the entire law enforcement community will go after you, find you, and bring you to justice.”
This investigation was conducted by the FBI’s Boston Division, the Boston Police Department, the Massachusetts State Police, and member agencies of the Boston Joint Terrorism Task Force, which is composed of more than 30 federal, state, and local enforcement agencies, including the Bureau of Alcohol, Tobacco, Firearms, and Explosives; U.S. Immigration and Customs Enforcement-Homeland Security Investigations; U.S. Marshals Service; U.S. Secret Service; the Massachusetts Bay Transit Authority; and others. In addition, the Watertown Police Department; the Cambridge Police Department; the Massachusetts Institute of Technology (MIT) Police Department; the Boston Fire Department; the National Guard; and police, fire, and emergency responders from across Massachusetts and New England played critical roles in the investigation and response.
This case is being prosecuted by Assistant U.S. Attorneys William Weinreb and Aloke Chakravarty from the Anti-Terrorism and National Security Unit of the U.S. Attorney’s Office for the District of Massachusetts, with assistance from the Counterterrorism Section of the Justice Department’s National Security Division.
The public is reminded that charges contained in an indictment or criminal complaint are merely allegations and that defendants are presumed innocent unless and until proven guilty.
FEMEN TV : Topless Jihad Day. Brussels
TOP-SECRET – Bilderberger Ghosts Praise Eric Schmidt’s Book
Bilderberger Ghosts Praise Eric Schmidt’s Book
http://newdigitalage.com/a/praise.html
The New Digital Age
Advanced Praise
“Every day, technological innovations are giving people around the world new opportunities to shape their own destinies. In this fascinating book, Eric Schmidt and Jared Cohen draw upon their unique experiences to show us a future of rising incomes, growing participation, and a genuine sense of community—if we make the right choices today.”
Bill Clinton, Former President of the United States
“This is a book that defines both the nature of the new world which the internet is creating; and its challenges. It describes a technological revolution in the making. How we navigate it is a challenge for countries, communities and citizens. There are no two people better equipped to explain what it means than Eric Schmidt and Jared Cohen.”
Tony Blair, Former Prime Minister of Great Britain and Northern Ireland
“Eric Schmidt and Jared Cohen have produced a searching meditation on technology and world order. Even those who disagree with some of their conclusions will learn much from this thought-provoking volume.”
Henry A. Kissinger, former Secretary of State
“The New Digital Age is must reading for anyone who wants to truly understand the depths of the digital revolution. Combining the skills of a social scientist and a computer scientist, Cohen and Schmidt blend the technical and the human, the scientific and the political, in ways I rarely saw while in government. They challenge the reader’s imagination on almost every page. Indeed, what will be the impact of virtual and physical worlds coexisting, the first generation of humans to have an indelible record, or more frequent revolutions without resolution as the digital age nurtures more celebrities than leaders. And these questions are just the beginning. Read on.”
General Michael Hayden, Former Director of the CIA
“This is the book I have been waiting for: a concise and persuasive description of technology’s impact on war, peace, freedom, and diplomacy. The New Digital Age is a guide to the future written by two experts who possess a profound understanding of humanity’s altered prospects in a wireless world. There are insights on every page and surprising conclusions (and questions) in every chapter. For experts and casual readers alike, Eric Schmidt and Jared Cohen have produced an indispensable book.”
Madeleine Albright, Former Secretary of State
“This is the most important — and fascinating — book yet written about how the digital age will affect our world. With vivid examples and brilliant analysis, it shows how the internet and other communications technologies will empower individuals and transform the way nations and businesses operate. How will different societies make tradeoffs involving privacy, freedom, control, security, and the relationship between the physical and virtual worlds? This realistic but deeply optimistic book provides the guideposts. It’s both profoundly wise and wondrously readable.”
Walter Isaacson, President and CEO of the Aspen Institute and Author of Steve Jobs
“The New Digital Age: Reshaping the Future of People, Nations and Business offers an intriguing fusion of ideas and insights about how the virtual world is intersecting with the “Westphalian order.” It seeks a balance between the discontinuities of technologists’ “revolutions” and the traditionalism of internationalists’ study of states, power, and behavior. The authors explain that technology is not a panacea, yet the uses of technology can make a world of difference. This book should launch a valuable debate about the practical implications of this new connectivity for citizens and policy makers, societies and governments.”
Robert B. Zoellick, Former President of the World Bank Group, U.S. Trade Representative, & U.S. Deputy Secretary of State
“Few people in the world are doing more to imagine – and build – The New Digital Age than Eric Schmidt and Jared Cohen. With this book, they are looking into their crystal ball and inviting the world to peek in.”
Michael R. Bloomberg, New York City Mayor and founder of Bloomberg LP
“We have long needed an incisive study of how the ever evolving world of technology leaves almost no aspect of life unchanged. We have it in The New Digital Age. Eric Schmidt and Jared Cohen offer a rigorous approach to decoding what the future holds in a story that is as well written and entertaining as it is important.”
General Brent Scowcroft, Former National Security Advisor
“At last, a brilliant guide book for the next century—what the future holds for entrepreneurs, revolutionaries, politicians, and ordinary citizens alike. Schmidt and Cohen offer a dazzling glimpse into how the new digital revolution is changing our lives. This book is the most insightful exploration of our future world I’ve ever read, and once I started reading I was simply unable to put it down.”
Sir Richard Branson, Founder and Chairman, Virgin Group
“[The New Digital Age] takes you on a wonderfully stimulating and important journey. It will make you rethink your concepts of the digital age, the way the world works, what lies ahead, and what all this means for you, your family and your community … Eric Schmidt and Jared Cohen brilliantly detail for us how the digital age is rapidly altering the balance of power between citizens and governments, between the physical and the virtual worlds, and between good and bad … [This book] is a must read for all those seeking to understand, and navigate well a fundamental structural shift that will play a critical role in determining the wellbeing of current and future generations.”
Mohamed El-Erian, CEO of Pimco
“Eric Schmidt and Jared Cohen’s thoughtful, well-researched work elucidates the staggering impact of technology on our daily lives, as well as what surprising and incredible developments the future may hold. Readers might be left with more questions than answers, but that’s the idea—we are at our best when we ask ‘What’s next?'”
Elon Musk, Founder of SpaceX and co-founder of Tesla Motors and PayPal
“Jared Cohen and Eric Schmidt have written a brilliant book that should be required reading for anyone who wishes to understand the huge ramifications of the Age of Google not only for our lifestyles but, more importantly, for our privacy, our democracy and our security … you had better download The New Digital Age today. The ‘technoptimistic’ case will never be more smartly argued.”
Niall Ferguson, author of Civilization: The West and the Rest
TMZ – Kate Beckinsale — The Best Penis Prank EVER
Not only did Kate Beckinsale pull the BEST rubber penis prank EVER… she pulled it on her own MOTHER!
Revealed – Air Force Office of Special Investigations Publishes Report on Military Sextortion Scams
Public Intelligence
The U.S. Air Force Office of Special Investigations (AFOSI) is warning military personnel to avoid becoming victims of online sextortion scams that use “sexual images (obtained either through enticement or malicious code)” to extort money from unsuspecting victims. “Cyber sextortion” is described as a growing problem among the military services with incidents being reported by “all Military Criminal Investigative Organizations” involving service members stationed in Europe, Asia and the U.S. The AFOSI report, released in February on a restricted basis, was recently posted online on the document-sharing website Scribd.
After reviewing Department of Defense statistics, the AFOSI found that cyber sextortion cases across the military services are primarily “webcam sextortion scams” where they DoD personnel were “enticed to engage in online sexual activities which were secretly recorded” and “money was then extorted from the victims in order to prevent the release of compromising video material.” Though it is “unclear whether perpetrators are specifically targeting US military members”, the report describes DoD members as potentially “vulnerable to blackmail and extortion” because of the expectation that they maintain “a professional appearance” and the strict requirements for maintaining a security clearance.
According to the AFOSI report, the Naval Criminal Investigative Service (NCIS) has identified four similar cases of cyber sextortion (two on Guam, one in Japan, and one in Bahrain) involving Navy members between August 2012 and November 2012. The U.S. Army Criminal Investigation Command (USACIDC) also reported three cases involving soldiers located in South Korea, Germany, and Texas. The AFOSI itself has identified multiple cases involving U.S. Air Force members in Japan, South Korea, Alaska, Portugal and Guam.
Many of the incidents reportedly originated from a criminal sextortion ring based in the Philippines. In a public affairs notice posted earlier this month on the Air Force website, a spokesperson for the AFOSI said that the ring involved “21 employees of a Philippines-based web portal solutions company” who reportedly “targeted hundreds of U.S. Army and Navy members for a period of more than a year”.
To protect against potential sextortion scams, the AFOSI recommends protecting personal information and limiting what information is divulged on social networking sites. The report also recommends not responding to “unsolicited e-mails or chat requests”, particularly when the communication involves a “request to exchange provocative pictures or videos”.
Video – Monty Python – Coconuts
“Are you suggesting coconuts migrate?”
Unveiled – USA v. Dzhokhar Tsarnaev Court Filings
3 April 2013
USA v. Dzhokhar Tsarnaev Court Filings
VICTIM
United States District Court
District of Massachusetts (Boston)
CRIMINAL DOCKET FOR CASE #: 1:13-mj-02106-MBB-1
Case title: USA v. Tsarnaev
Date Filed: 04/21/2013
Assigned to: Magistrate Judge Marianne B. Bowler
Defendant (1)
Dzhokhar Tsarnaev represented by Miriam Conrad
Federal Public Defender Office
51 Sleeper Street
Fifth Floor
Boston, MA 02210
617-223-8061
Fax: 617-223-8080
Email: miriam_conrad@fd.org
LEAD ATTORNEY
ATTORNEY TO BE NOTICED
Designation: Public Defender or Community Defender Appointment
Timothy G. Watkins
Federal Public Defender Office
District of Massachusetts
51 Sleeper Street
5th Floor
Boston, MA 02210
617-223-8061
Fax: 617-223-8080
Email: timothy_watkins@fd.org
LEAD ATTORNEY
ATTORNEY TO BE NOTICED
Designation: Public Defender or Community Defender Appointment
William W. Fick
Federal Public Defender Office
District of Massachusetts
51 Sleeper Street
5th Floor
Boston, MA 02210
617-223-8061
Fax: 617-223-8080
Email: william_fick@fd.org
LEAD ATTORNEY
ATTORNEY TO BE NOTICED
Designation: Public Defender or Community Defender Appointment
Pending Counts
Disposition
None
Highest Offense Level (Opening)
None
Terminated Counts
Disposition
None
Highest Offense Level (Terminated)
None
Complaints
Disposition
18:2332a(a)…Use of a Weapon of Mass Destruction; 18:844(i)…Malicious Destruction of Property Resulting in Death
Plaintiff
USA represented by Aloke Chakravarty
United States Attorney’s Office MA
Suite 9200
1 Courthouse Way
Boston, MA 02210
617-748-3658
Fax: 617-748-3664
Email: Aloke.Chakravarty@usdoj.gov
LEAD ATTORNEY
ATTORNEY TO BE NOTICED
Designation: Assistant US Attorney
William D. Weinreb
United States Attorney’s Office
John Joseph Moakley Federal Courthouse
1 Courthouse Way
Suite 900
Boston, MA 02210
617-748-3222
Fax: 617-748-3358
Email: william.weinreb@usdoj.gov
LEAD ATTORNEY
ATTORNEY TO BE NOTICED
Designation: Assistant US Attorney
Date Filed # Docket Text
04/21/2013 1 MOTION to Seal Case as to Dzhokhar Tsarnaev by USA. (Alves-Baptista, Antonia) (Entered: 04/22/2013)
04/21/2013 2 Magistrate Judge Marianne B. Bowler: ENDORSED ORDER entered granting 1 Motion to Seal Case as to Dzhokhar Tsarnaev (1) (Alves-Baptista, Antonia) (Entered: 04/22/2013)
04/21/2013 3 SEALED COMPLAINT as to Dzhokhar Tsarnaev (1). (Attachments: # 1 Affidavit of Daniel R. Genck, # 2 JS45)(Alves-Baptista, Antonia) (Entered: 04/22/2013)
04/22/2013 5 ELECTRONIC NOTICE of Case Assignment as to Dzhokhar Tsarnaev; Magistrate Judge Marianne B. Bowler assigned to case. (Abaid, Kimberly) (Entered: 04/22/2013)
04/22/2013 7 ELECTRONIC Clerk’s Notes for proceedings held before Magistrate Judge Marianne B. Bowler:Initial Appearance as to Dzhokhar Tsarnaev held on 4/22/2013 at Beth Israel Deaconess Medical Center. Court advises the defendant of his rights and the charges against him. Government states the maximum penalties and moves for detention. Defendant agrees to an order of voluntary detention without prejudice. Defendant declines to answer bail questions and assents to a probable cause hearing on May 30, 2013 at 10:00am. Court is satisfied that the defendant is alert and able to respond to the charges. Defendant is remanded from the custody of the FBI agents present to the U.S. Marshals. (Probable cause hearing set for 5/30/2013 10:00 AM in Courtroom 25 before Magistrate Judge Marianne B. Bowler.) (Attorneys present: Weinreb for the Government. Fick for the defendant.)Court Reporter Name and Contact or digital recording information: James Gibbons (jmsgibbons@yahoo.com). (Garvin, Brendan) (Entered: 04/22/2013)
04/22/2013 Attorney update in case as to Dzhokhar Tsarnaev. Attorney Conrad, Fick, Watkins added. (Garvin, Brendan) (Entered: 04/22/2013)
04/22/2013 8 MOTION to Unseal Case as to Dzhokhar Tsarnaev by USA. (Garvin, Brendan) (Entered: 04/22/2013)
04/22/2013 9 Magistrate Judge Marianne B. Bowler: ENDORSED ORDER entered granting 8 Motion to Unseal Case as to Dzhokhar Tsarnaev (1) (Garvin, Brendan) (Entered: 04/22/2013)
04/22/2013 10 MOTION to Appoint Counsel as to Dzhokhar Tsarnaev. (Conrad, Miriam) (Entered: 04/22/2013)
TMZ – Heather Locklear and the Fountain of Youth
Heather Locklear has one HUGE tip on how to keep ones face looking youthful. Though the technique she suggests may be hard for some to swallow.
Unveiled – National Counterterrorism Center Says Urban Exploration Could “Aid Terrorists”
ublic Intelligence
The National Counterterrorism Center (NCTC) is warning law enforcement and first responders that urban exploration, an activity that involves trying to gain access to restricted or abandoned man-made structures, can provide useful information for terrorists conducting surveillance of a potential target. Also known as “building hacking”, urban exploration has been around in its modern form for decades, tracing some its recent history to post-war exploration of the Parisian catacombs and members of MIT’s Tech Model Railroad Club Signals and Power Subcommittee, who organized explorations of steam tunnels and rooftops around campus in the late 1950s.
In an advisory released to law enforcement in November 2012 titled Urban Exploration Offers Insight Into Critical Infrastructure Vulnerabilities, the NCTC warns of the potential risks posed by urban explorers and their online posting of photos and videos depicting their exploration. The NCTC document describes urban explorers as “hobbyists who seek illicit access to transportation and industrial facilities in urban areas” including rooftops, utility tunnels and bridges. According to the NCTC, photos and videos posted online by urban explorers “could be used by terrorists to remotely identify and surveil potential targets” which could “aid terrorists in pinpointing locations in dense urban environments.” The document also makes specific reference to the advancement of navigation and mapping technology, including three-dimensional modeling and geo-tagging, as potentially aiding terrorists to conduct online surveillance of a target. Corporate websites can often provide “information about buildings” and “social media postings of explorers’ activity often identify access points and security flaws” that could be exploited by terrorists. A 2010 bulletin issued by the Department of Homeland Security expressed similar concerns about the use of Google Earth and other publicly available mapping software for terrorist surveillance. The bulletin stated that “live Web-based camera feeds combined with street-level and direct overhead imagery views from Internet imagery sites allow terrorists to conduct remote surveillance of multiple potential targets without exposing themselves to detection.”
The NCTC advisory also lists several locations, such as bridges, utility tunnels, rooftops and subways, where an urban explorer might reveal “security flaws”. Along with each location, there is a list of potential access locations and security vulnerabilities that the NCTC believes an urban explorer’s postings could potentially reveal. For example, urban explorers could discover and document the use of a bridge’s “ladders, crosswalk scaffoldings, trap doors, scuttles, and hatches” and reveal methods of accessing “structural components, including caissons (the structures that house the anchor points of a bridge suspension system), to identify weaknesses.”
Past activities by urban explorers have occasionally been mistaken for potential terrorist activity. In 2011 four men were arrested in London for “suspicion of railway trespass and burglary” after they were found near an elevator used by private contractors working on the rail lines for the London Underground. The men were arrested at the Russell Square station, one of the locations of the 7/7 terrorist attacks, after security camera operators saw the men in dark clothing with cameras and feared preparations for a terrorist attack around the upcoming royal wedding between Prince William and Catherine Middleton. A few months later, four men were arrested in New York City for criminal trespass after a local resident saw them “carrying Roman candles and cameras” into the Second Avenue Subway tunnel. The men identified themselves as urban explorers and said they planned to use the Roman candles for lighting photographs.
Video Skid – Monty Python – The Life of Brian Sketch – Biggus Dickus
FEMEN TV: The Story Behind Femen
Confidential – Philadelphia La Cosa Nostra Capo Pleads Guilty to Racketeering Conspiracy
WASHINGTON—Anthony Staino, 55, of Swedesboro, New Jersey, pleaded guilty yesterday to participating in a racketeering conspiracy as a capo in the Philadelphia La Cosa Nostra (LCN) family and committing loan sharking and illegal gambling.
Acting Assistant Attorney General Mythili Raman of the Justice Department’s Criminal Division, U.S. Attorney Zane David Memeger of the Eastern District of Pennsylvania, and Edward J. Hanko, Special Agent in Charge of the FBI’s Philadelphia Division, made the announcement after the plea was accepted by U.S. District Judge Eduardo C. Robreno of the Eastern District of Pennsylvania.
Staino pleaded guilty to conspiring to conduct and participate in the affairs of the Philadelphia LCN family through a pattern of racketeering activity. He faces a maximum penalty of 70 years in prison when he is sentenced on Jul. 17, 2013.
Through court documents and statements yesterday in court, Staino admitted that, as a made member and capo of the Philadelphia LCN family, he gave a usurious loan to an undercover FBI agent and used threats of violence to collect payments on the loan. Staino also admitted that he ran an illegal electronic gambling device business for the mob, providing video poker machines, and other gambling devices for bars, restaurants, convenience stores, coffee shops, and other locations in Philadelphia and its suburbs and then collected the illegal gambling proceeds.
The case is being investigated by the FBI, the Internal Revenue Service-Criminal Investigation, the Pennsylvania State Police, the New Jersey State Police, the Philadelphia Police Department, the U.S. Department of Labor’s Office of Inspector General Office of Labor Racketeering and Fraud Investigations, and the U.S. Department of Labor’s Employee Benefits Security Administration. Additional assistance was provided by the New Jersey Department of Corrections.
The case is being prosecuted by Trial Attorney John S. Han of the Criminal Division’s Organized Crime and Gang Section and Assistant U.S. Attorneys Frank A. Labor, III and Suzanne B. Ercole of the Eastern District of Pennsylvania. Valuable prosecutorial assistance was provided by the Pennsylvania Office of the Attorney General.
WASHINGTON—Anthony Staino, 55, of Swedesboro, New Jersey, pleaded guilty yesterday to participating in a racketeering conspiracy as a capo in the Philadelphia La Cosa Nostra (LCN) family and committing loan sharking and illegal gambling.
Acting Assistant Attorney General Mythili Raman of the Justice Department’s Criminal Division, U.S. Attorney Zane David Memeger of the Eastern District of Pennsylvania, and Edward J. Hanko, Special Agent in Charge of the FBI’s Philadelphia Division, made the announcement after the plea was accepted by U.S. District Judge Eduardo C. Robreno of the Eastern District of Pennsylvania.
Staino pleaded guilty to conspiring to conduct and participate in the affairs of the Philadelphia LCN family through a pattern of racketeering activity. He faces a maximum penalty of 70 years in prison when he is sentenced on Jul. 17, 2013.
Through court documents and statements yesterday in court, Staino admitted that, as a made member and capo of the Philadelphia LCN family, he gave a usurious loan to an undercover FBI agent and used threats of violence to collect payments on the loan. Staino also admitted that he ran an illegal electronic gambling device business for the mob, providing video poker machines, and other gambling devices for bars, restaurants, convenience stores, coffee shops, and other locations in Philadelphia and its suburbs and then collected the illegal gambling proceeds.
The case is being investigated by the FBI, the Internal Revenue Service-Criminal Investigation, the Pennsylvania State Police, the New Jersey State Police, the Philadelphia Police Department, the U.S. Department of Labor’s Office of Inspector General Office of Labor Racketeering and Fraud Investigations, and the U.S. Department of Labor’s Employee Benefits Security Administration. Additional assistance was provided by the New Jersey Department of Corrections.
The case is being prosecuted by Trial Attorney John S. Han of the Criminal Division’s Organized Crime and Gang Section and Assistant U.S. Attorneys Frank A. Labor, III and Suzanne B. Ercole of the Eastern District of Pennsylvania. Valuable prosecutorial assistance was provided by the Pennsylvania Office of the Attorney General.
Unveiled – PT Prime Minister Death and US October Surprise
1980 Death of Portugal Prime Minister and American October Surprise
I’m Frederico Duarte Carvalho, the Portuguese journalist and I’m investigating the connection between the 1980 death of Portuguese Prime-Minister and the American “October Surprise”.
It’s still an open case in Portugal and last month I was at the Portuguese Parliament to inform the MP about my investigation. Here’s a clip of what is at stake:
And here’s an English article about what we know so far in Portugal:
http://www.wsws.org/en/articles/2005/01/port-j10.html
If you think your readers are interested on this case, please use this information for Cryptome.
And you can say that, for more information, I can be contacted at this e-mail
paramimtantofaz[at]gmail.com
Best regards
Frederico Duarte Carvalho
Revealed – DoD Strategy for Homeland Defense and Defense Support of Civil Authorities February 2013
Defending U.S. territory and the people of the United States is the highest priority of the Department of Defense (DoD), and providing appropriate defense support of civil authorities (DSCA) is one of the Department’s primary missions. This Strategy for Homeland Defense and Defense Support of Civil Authorities orients the Department towards an increasingly complex strategic environment. It emphasizes innovative approaches, greater integration, deepening of external partnerships, and increased effectiveness and efficiencies in DoD’s homeland activities. It applies the vital capabilities of the Total Force – in the Active and Reserve Components – to make the nation more secure and resilient. Finally, the Strategy guides future decisions on homeland defense and civil support issues consistent with the Defense Strategic Guidance and the Quadrennial Defense Review (QDR).
This Strategy identifies two priority missions for the Department’s activities in the homeland from 2012 to 2020. DoD works with the Department of Homeland Security (DHS) and other actors to achieve these missions:
Defend U.S. territory from direct attack by state and non-state actors; and
Provide assistance to domestic civil authorities in the event of natural or manmade disasters, potentially in response to a very significant or catastrophic event.
These priority missions are reinforced, supported, or otherwise enabled through the pursuit of the following objectives:
Counter air and maritime threats at a safe distance;
Prevent terrorist attacks on the homeland through support to law enforcement;
Maintain preparedness for domestic Chemical, Biological, Radiological, Nuclear (CBRN) incidents; and
Develop plans and procedures to ensure Defense Support of Civil Authorities during complex catastrophes.
This Strategy also defines a number of other priority lines of effort, or strategic approaches, that are intended to enhance the effectiveness of the Department’s homeland defense and civil support efforts. Although these items require a distinct departmental effort, they do so without adding significant resource requirements. These are:
Assure DoD’s ability to conduct critical missions;
Promote Federal-State unity of effort;
Conduct integrated planning with Federal and State authorities; and
Expand North American cooperation to strengthen civil support.
Defending the homeland neither begins nor ends at U.S. borders, and departmental planning is guided by the concept of an active, layered defense – a global defense that aims to deter and defeat aggression abroad and simultaneously protect the homeland. It is a defense-in-depth that relies on collection, analysis, and sharing of information and intelligence; strategic and regional deterrence; military presence in forward regions; and the ability to rapidly generate and project warfighting capabilities to defend the United States, its Allies, and its interests.
The homeland is a functioning theater of operations, where DoD regularly performs a wide range of defense and civil support activities through U.S. Northern Command (in concert with the North American Aerospace Defense Command, or NORAD), U.S. Pacific Command, and other DoD components. When faced with a crisis in the homeland – for example, a complex catastrophe as a result of an attack against the Nation or a natural disaster – DoD must be prepared to respond rapidly to this crisis while sustaining other defense and civil support operations. Within the homeland, arriving late to need is not an option.
The Department acts globally to defend the United States and its interests in all domains – land, air, maritime, space, and cyberspace – and similarly must be prepared to defend the homeland and support civil authorities in all domains. This Strategy is nested within a series of mutually supporting defense strategies and national guidance that provide policy and direction for the space and cyberspace domains, including the National Security Space Strategy, the Ballistic Missile Defense Review, and the Defense Strategy for Operating in Cyberspace. Other related and supporting strategies include the DoD Mission Assurance Strategy, Presidential Policy Directive 8 – National Preparedness, and Homeland Security Presidential Directive 25 – Arctic Region Policy. Finally, an active, layered defense of the homeland cannot be accomplished unilaterally nor conducted exclusively with military capabilities. The Western Hemisphere Defense Policy, the Strategy to Combat Transnational Organized Crime, the National Strategy for Counterterrorism, the National Strategy for Global Supply Chain Security and other regional and functional strategies articulate a range of defense, diplomatic, law enforcement, and capacity-building activities that the United States pursues with its neighbors to build an integrated, mutually-supportive concept of security.
…
Objective 2.b: Develop plans and procedures to ensure Defense Support of Civil Authorities during complex catastrophes
DoD has historically supported civil authorities in a wide variety of domestic contingencies, often in response to natural disasters. However, the 21st century security environment, the concentration of population in major urban areas, and the interconnected nature of critical infrastructures have all combined to fundamentally alter the scope and scale of “worst case” incidents for which DoD might be called upon to provide civil support. This environment creates the potential for complex catastrophes, with effects that would qualitatively and quantitatively exceed those experienced to date. In such events, the demand for DSCA would be unprecedented. Meeting this demand would be especially challenging if a cyber attack or other disruption of the electrical power grid creates cascading failures of critical infrastructure, threatening lives and greatly complicating DoD response operations.
DoD must be prepared to help civilian authorities save and protect lives during a complex catastrophe. An effective response will require investments in preparedness (planning, organizing, equipping, and training), improving concepts of operations, and better linking of established Federal and State capabilities and systems. The following areas represent the Department’s priorities for preparedness and response to catastrophic events:
Leveraging immediate response authority;
Geographically proximate force-sourcing; and
Ready access to non-National Guard Reserve forces.
Immediate response authority
DoD will explore methods to leverage “immediate response” authority to provide life-saving and logistical capabilities to a broader geographic area.
There are many large and medium-size DoD installations throughout the United States with significant resident or tenant capabilities that provide immediate life-saving and life-sustaining support to their on-base population. “Immediate response” authority allows responsible DoD officials to provide support, when requested by civilian agencies, to local communities and to State and Federal officials in extreme conditions. A key to success in meeting the urgent requirements of a catastrophic incident is time. DoD will therefore explore methods to most effectively leverage immediate response authority to employ capabilities to save lives, mitigate property damage, and prevent human suffering during catastrophic incidents.
Geographically proximate force-sourcing DoD will explore new concepts of operations to leverage the relative proximity of Defense installations to a disaster area to provide life-saving capabilities to local, State, and Federal authorities.
A key consideration for catastrophic events is that response elements have the highest probability to save lives within 72-96 hours after an incident. To address this time constraint, DoD will explore force-sourcing options that include a unit’s proximity to the affected area – in addition to its readiness level for overseas missions, which is the traditional driver for mission assignments – as a core consideration for sourcing for disaster response efforts. Additionally, the Department will develop a decision matrix to give senior DoD leaders a mechanism for expedited Defense support during a complex catastrophe, while identifying effects and risks resulting from those ecisions.
Ready access to non-National Guard Reserve forces
DoD will develop rules and modalities to execute its authority for involuntary Reserve mobilization for response to emergencies in the United States, including natural disasters. The Secretary of Defense now has the authority for involuntary mobilization of non-National Guard Reservists for domestic disaster response. The geographic dispersion of Reserve units and their life-saving medical, decontamination, engineering, and other capabilities mandate consideration of Reserve employment for any Total Force response. The Department will develop, refine, and implement policy that facilitates rapid approval for Reserve activation and employment.
TMZ – Lindsay Lohan Coachella Confession – Sobriety!
Lindsay Lohan kept her word this weekend, telling TMZ, she was sober her whole time at Coachella, she has got to be telling the truth, right?!
SECRECY NEWS – INTELLIGENCE SATELLITE IMAGERY DECLASSIFIED FOR RELEASE
An enormous volume of photographic imagery from the KH-9 HEXAGON
intelligence satellites was quietly declassified in January and will be
transferred to the National Archives later this year for subsequent public
release.
The KH-9 satellites operated between 1971 and 1984. The imagery they
generated should be of historical interest with respect to a wide range of
late Cold War intelligence targets but is also expected to support current
scientific research on climate change and related fields of inquiry.
The film-based KH-9 satellites were officially declared “obsolete” by the
Director of National Intelligence in 2011. The KH-9 imagery was nominally
approved for declassification in February 2012, and then it was finally
declassified in fact this year.
ODNI spokesman Michael Birmingham said that approximately 97 percent of
the satellite imagery that was collected from the 19 successful KH-9
missions was formally declassified by DNI James R. Clapper on January 11,
2013.
“The small amount of imagery exempted from this declassification decision
will be removed prior to its accession to the National Archives (NARA) and
will remain classified pursuant to statute and national security interests,
and reviewed periodically to determine if additional declassification is
warranted,” Mr. Birmingham said last week.
The imagery is being transferred to NARA in stages, with final delivery
scheduled for September 2013, he said.
The transfer is being implemented pursuant to a November 2012 Memorandum
of Agreement between the National Geospatial-Intelligence Agency (NGA) and
the National Archives, under which the Archives is “responsible for
providing public access to the declassified imagery.”
Reishia R. Kelsey of NGA public affairs confirmed that the imagery “will
be made available to the public following its accession to NARA” later this
year.
The National Archives was not prepared last week to set a precise date for
public release. But an Archives official said that “NARA intends to make
these records available to the public at our research room in College Park,
MD as soon as possible following transfer.”
If successfully executed, the release of the KH-9 imagery will constitute
a breakthrough in the declassification and disclosure of national security
information. It will be one of several discrete but momentous shifts in
secrecy policy during the Obama Administration that have often gone
unrecognized or unappreciated. Though these declassification actions took
years or decades to accomplish, they have been downplayed by the White
House itself, which has seemed curiously ambivalent about them. They
include the public disclosure of the size of the U.S. nuclear weapons
arsenal, the routine publication of the annual intelligence budget request,
the release of the Office of Legal Counsel “torture memos,” the
declassification of the KH-9 satellite itself, and others.
The KH-9 imagery is being processed for public release pursuant to the
1995 Executive Order 12951 on “Release of Imagery Acquired by Space-based
National Intelligence Reconnaissance Systems.” That order had been
effectively dormant since the Clinton Administration, when the last major
release of intelligence satellite imagery (from the CORONA, ARGON and
LANYARD missions) took place.
The declassification of the KH-9 imagery is a massive undertaking, Mr.
Birmingham of ODNI said last year.
“For context, and to grasp the scope of the project, the KH-9/HEXAGON
system provided coverage over hundreds of millions of square miles of
territory during its 19 successful missions spanning 1971-1984,” he said.
“It is a daunting issue to address declassification of the program
specifics associated with an obsolete system such as the KH-9, which
involves the declassification of huge volumes of intelligence information
gathered on thousands of targets worldwide during a 13 year time period.”
http://blogs.fas.org/secrecy/2012/10/hexagon_imagery/
MILITARY PHOTOGRAPHERS READY TO DEPLOY AROUND THE GLOBE
Just as law enforcement relied upon surveillance cameras and personal
photography to enable the prompt identification of the perpetrators of the
Boston Marathon bombing, U.S. armed forces increasingly look to the
collection of still and motion imagery to support military operations.
Combat camera (COMCAM) capabilities support “operational planning, public
affairs, information operations, mission assessment, forensic, legal,
intelligence and other requirements during crises, contingencies, and
exercises around the globe,” according to newly updated military doctrine.
COMCAM personnel are “highly trained visual information professionals
prepared to deploy to the most austere operational environments at a
moment’s notice.”
COMCAM units “are adaptive and provide fully qualified and equipped
personnel to support sustained day or night operations” in-flight, on the
ground or undersea, as needed.
“Effectively employed COMCAM assets at the tactical level can potentially
achieve national, theater strategic, and operational level objectives in a
manner that lessens the requirement for combat in many situations,” the new
doctrine says. “Their products can counter adversary misinformation,
disinformation, and propaganda and help commanders gain situational
awareness on operations in a way written or verbal reports cannot.”
“The products can also provide historical documentation, public
information, or an evidentiary foundation… for forensic documentation of
evidence and legal proceedings. They can provide intelligence documentation
to include imagery for facial recognition and key leader engagements, and
support special reconnaissance.”
The newly issued COMCAM doctrine supersedes previous guidance from 2007.
See Combat Camera: Multi-Service Tactics, Techniques, and Procedures for
Combat Camera (COMCAM) Operations, April 2013.
Click to access atp3-55-12.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://blogs.fas.org/secrecy/subscribe/
To UNSUBSCRIBE, go to
http://blogs.fas.org/secrecy/unsubscribe/
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
https://members.fas.org/donate
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: http://www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Video – Monty Python Communist Quiz Sketch
Live from the Hollywood Bowl sketch from Monty Python – Communist quiz featuring Marx, Lenin, Che, Mao. A great parody…
TMZ – Farrah Abraham Disses Porn Partner’s Junk!
‘Teen Mom’ Farrah Abraham trashed her sex tape partner James Deen and said he has a small penis…
SECRET – FBI Bulletin: Potential Use of Exploding Targets as Explosives in IEDs
The following bulletin was released in March by the FBI Terrorist Explosive Device Analytical Center. The bulletin was first reported on and made public by a writer for Examiner.com who published low quality images of the document. This version of the bulletin is significantly higher quality and contains renderable text making it easier to read and refer to.
(U//FOUO) The FBI assesses with high confidence recreationally used exploding targets (ETs), commonly referred to as tannerite, or reactive targets, can be used as an explosive for illicit purposes by criminals and extremists and explosive precursor chemicals (EPCs) present in ETs can be combined with other materials to manufacture explosives for use in improvised explosive devices (IEDs).
(U//FOUO) The FBI further assesses with medium confidence as the regulations and restrictions on ammonium nitrate-based fertilizers continue to increase, motivated criminals and extremists seeking ammonium nitrate for illicit use will be more likely to seek alternative sources, such as ETs. The FBI assesses with high confidence criminals and extremists in the United States and overseas have access to information about exploding targets due to the wide availability of such information on the Internet.
(U//FOUO) ETs May Serve as an Alternative Source of Ammonium Nitrate for Individuals Interested in Manufacturing Improvised Explosives
(U//FOUO) The FBI assesses with medium confidence criminals and extremists may actively be attempting to acquire ETs to obtain the ammonium nitrate for use in the manufacture of improvised explosives based on FBI investigations of individuals interested in manufacturing explosives. While other methods for illicit acquisition of commercial products containing ammonium nitrate exist, the FBI assesses with medium confidence the use of ETs as a source of ammonium nitrate could represent the latest evolution in tradecraft by which criminals and extremists attempt to circumvent existing regulations based on recent reported incidents of ET acquisition for explosives manufacturing.
(U//FOUO) Currently, ETs contain ammonium nitrate, and their purchase is not regulated to the same degree as ammonium nitrate-containing fertilizers. Alternatively, the personal manufacture of ETs could be used by criminals and extremists as a rationale for purchasing large amounts of ammonium nitrate from retailers.
• (U//FOUO) In April 2012 an identified US person in Washington State, who may have undergone aggressive online radicalization, sustained serious injury after an explosive device detonated prematurely. The device’s main charge consisted of an improvised explosive mixture containing ammonium nitrate, which likely was obtained from ETs purchased online, according to a law enforcement source.
• (U//FOUO) There have been multiple instances in the past three years in which law enforcement officers discovered ETs stored with other explosives and EPCs when executing search warrants at personal residences.
• (U//FOUO) Since 2008 the FBI ammonium nitrate tripwire initiative has detected at least 18 incidents related to attempts to directly purchase ammonium nitrate, allegedly to manufacture ETs, although no nexus to terrorism was immediately apparent.
(U//FOUO) The FBI assesses with high confidence criminals and extremists remain interested in using improvised ammonium nitrate-based explosives as the main charge in IEDs and are actively seeking new ways to acquire sufficient amounts of ammonium nitrate, based on recent incidents illustrating these acquisition methods. Following the use of ammonium nitrate in the Oklahoma City bombing, the US Government instituted a number of programs designed to increase security awareness of the possible uses of ammonium nitrate-based fertilizers for use in IEDs. As a result, criminals and extremists have adapted and sought other means of acquisition, either through complex pre-operational planning to clandestinely acquire ammonium nitrate-based fertilizers or through purchasing alternative commercial products containing ammonium nitrate.
FBI-ExplodingTargets
Greek Journalist fears for his life – Kostas Vaxevanis: “They are searching for me instead of the truth”
The wanted Kostas Vaxevanis talks to “Pandora’s Box Show” about the publication of HOTDOC magazine and the notorious Lagarde list, hours before his arrest, and the attempts to silence the press and the truth.
PLEASE SHARE THIS VERSION WITH ENGLISH SUBS SO THE WHOLE WORLD CAN WITNESS THE INJUSTICE WE GREEKS ARE LIVING IN!!!
Petition on Avaaz to “drop all charges against Kostas Vaxevanis”:
http://www.avaaz.org/en/petition/Drop…
Show your support on Facebook:
https://www.facebook.com/freeVaxevani…
https://www.facebook.com/pages/Freedo…
The list has been in the possession of the Greek government since 2010 after being transferred by then French Finance Minister Christine Lagard to her Greek counterpart in order to assist in recouping lost tax revenue. Several other European governments including France, Spain, and Italy have used the information in the database to recover close to EUR 10 Billion (USD 13 Billion) in much needed revenue as they struggle with tough recessions.
All this while the Greece struggles with conditions of harsh economic depression as a result of EU/IMF imposed austerity that has disproportionately struck the middle and working classes. The list includes -among others- well known business people, journalists, doctors, lawyers, and media figures many of who have declared income that does not justify the amount of money in their HSBC accounts.
Film – Monty Python’s Best Sketch Ever
My favorite sketch from Monty Python’s Flying Circus.
Cryptome – Boston Bomb Blasts 2 Vivid Non-Commercial
Boston Bomb Blasts 2
Selected from 150 photos by Aaron “tango” Tang via Flicker
http://www.flickr.com/photos/hahatango/sets/72157633252445135/with/8652877581/
Aaron writes:
I was at my office overlooking the boston marathon which is half a block from the finish line when the explosion went off while watching which was a shock.. I ran to grab my camera hoping to catch any leads but here is what i have. Please share if you feel these might lead to what occurred especially the before shots of that area of the 1st bombing.
My observation is that the explosion was in front of the “candy store” or “marathon palace” in a trashcan or something on the far side of the sidewalk near the fence that exploded. Big blast of fire, and smoke, but it all vanished so fast and not much left to see minus lots of shattered glass.
This is a sad day for such a great event. I was amazed how fast the medics and nearby citizens took action to run into the smoke, rip off their shirts to help the wounded.
Please share, post, link this set if you feel these photos might aid in figuring out this tragic event…. especially in the “Before photos” which show lots of faces and perhaps clues.
_____
Reddit discussion of these and other photos:
Previous bomb blast photos:
http://cryptome.org/2013-info/04/boston-bombs/boston-bombs.htm
TMZ – ‘Buckwild’ Stars Have a Sex Tape Too!
“Buckwild” stars Shae Bradley and Jesse J have taken a page from the Farrah Abraham book and created their own sex tape! Only difference is that it’s trailer park sex…which means its down and far more dirtier!
TOP-SECRET – FBI Bulletin: Los Zetas Recruitment of Non-Traditional Associates in the United States
(U//FOUO) Recent FBI intelligence from multiple FBI HUMINT sources indicates a shift in Los Zetas recruiting methods and reliance on non-traditional associates. Past, accurate FBI reporting indicated Los Zetas previously focused its recruitment on members with prior specialized training, such as ex-military and ex-law enforcement officers, and not on US-based gangs or US persons in order to maintain a highly-disciplined and structured hierarchy. This hierarchy, which resembled a military-style command and control structure, facilitated drug trafficking operations and maintained lines of authority. However, current FBI reporting indicates that Los Zetas is recruiting and relying on non-traditional, non-military trained associates—US-based prison and street gangs and non-Mexican nationals—to perform drug trafficking and support operations in Mexico and in the United States. The FBI judges with high confidence that Los Zetas will continue to increase its recruitment efforts and establish pacts with non-military trained, nontraditional associates to maintain their drug trafficking and support operations, which may increase violence along the Southwest border posing a threat to US national security.
(U//FOUO) Current FBI reporting has indicated an increase of recruitment and contracting of US-Based gangs to conduct daily drug trafficking activities and support operations in the United States.
…
( U//FOUO) As of October 2010, a corroborated collaborative FBI HUMINT source with excellent access showed that Los Zetas had contracted the Texas Mexican Mafia, a Texas-based prison gang, and tasked them to collect drug debts, carry out hits, and traffic drugs in and through Laredo, Texas.
(U//FOUO) As of September 2010, a corroborated collaborative FBI HUMINT source with excellent access indicated that Los Zetas attempted to recruit US-based members in Houston, Texas, to join Los Zetas’ war against the Gulf Cartel on both sides of the border.
(U//FOUO) A corroborated collaborative FBI HUMINT source with indirect access indicated that as of August 2010, Los Zetas was buying AK-47’s from the Tango Blast Gang, a Houston, Texas-based street gang. The weapons were moved from Houston to Laredo, Texas, and were subsequently smuggled into Mexico.
(U//FOUO) As of April 2010, an established source with excellent access, much of whose reporting has been corroborated over the past ten years, indicated that the McAllen, Texas Los Piojos Drug Trafficking Organization (DTO) procured vehicles for Los Zetas through thefts, carjackings, and auto auctions held in McAllen, Texas. Los Piojos also operates a street gang in Mission, Texas who assisted with the acquisition of vehicles and vehicle parts for Los Zetas, and in some cases those parts were used to build armored vehicles for them.
(U//FOUO) FBI reporting indicates that Los Zetas is also recruiting or contracting US person Mexican nationals to conduct drug trafficking operations in the United States.
(U//FOUO) As of October 2010, a corroborated collaborative FBI HUMINT source with indirect access indicated that US person Javier Medina, a resident of Zapata, Texas, is an alleged Los Zetas recruit. Medina worked for Juan Pedro in Guerrero, Tamaulipas, Mexico. Juan Pedro was allegedly affiliated with the shooting of the US person on the Jet Ski at Falcon Lake near Zapata, Texas.
(U//FOUO) As of September 2010, a corroborated collaborative FBI HUMINT source with excellent access indicated that Los Zetas contracted a US person, identified as Alejandro, to steal vehicles in Laredo, Texas, and transport them to Nuevo Laredo, Tamaulipas, Mexico to use for its operations.
(U//FOUO) As of March 2010, an FBI contact with excellent access whose reporting is limited and whose reliability cannot be determined indicated that Los Zetas contracted US person Alma Delia Martinez to collect smuggling fees from smugglers crossing illegal aliens across the Rio Grande River.
…
(U//FOUO) The FBI San Antonio judges with high confidence that Los Zetas will continue to increase their recruitment efforts and establish pacts with other Mexico and US-based prison and street gangs, as well as non-Mexican nationals to maintain their drug trafficking and support operations. FBI San Antonio believes the Los Zetas’ shift in recruitment efforts will most likely not increase its membership numbers drastically, as recent reporting has indicated that these new members lack the training and skills to elude GOM law enforcement and military, which result in many Los Zetas casualties or captures.
(U//FOUO) FBI judges with moderate confidence that Los Zetas will likely pose a higher national security threat to the United States, based on their demonstrated capabilities for violence, their recent murders of US citizens, increased kidnappings of US citizens on both sides of the border, and their continued participation in the US drug trade. With the GOM military counter-narcotic operations and turf battles against other DTOs, Los Zetas violence and criminal activity will most likely increase.
(U//FOUO) In order to adequately assess the threat to the United States, FBI San Antonio would need information that indicated larger-scale or multiple plans to attack are being planned. With the recruitment of new members, Los Zetas have lost part of their disciplined command and control structure needed to maintain order within the organization, which is likely to hinder their ability to carry out complex attacks and could increase the likelihood that GOM officials may learn of planned attacks or operations. High-level Los Zetas members with minimal command and control authority have hindered their operations, and caused countless casualties and captures. Furthermore, new members are often undisciplined, which has led to recruits failing to follow orders and has gained the Los Zetas unneeded attention, as evidenced in the Falcon Lake shooting.
Full Video uncensored – Watertown Operation: Boston Bombing Manhunt
Video Skid – Monty Python’s – Meaning of Life – Death
TMZ – Britney Spears & David Lucado GET SERIOUS
Britney Spears and her new boyfriend David Lucado took a huge leap in their relationship and you’re not going to believe it… She wore a Virginia Tech shirt! You know, adopting her fella’s sports team… That’s one step closer to pregnancy!
Cryptome unveils Djohar Tsarnaev
Djohar Tsarnaev
A sends:
The media has Dzhokhar Tsarnaev’s name misspelled. I skiptraced him and found his Russian Facebook profile:
vk.com/id160300242?z=tag160300242
Cryptome: This Facebook material has not been verified as authentic.
Djohar Tsarnaev
[Image]
Full-size: http://cryptome.org/2013/04/Djohar-Tsarnaev-03.jpg
Video:
[Image]
FEMEN TV : Go Rape Yourself
FEMEN sextremists attacked International Porn Forum (Eropolis)of Le Bourget in Paris.
They interrupted a show staging live porn dolls while screaming “GO RAPE YOURSELF!”.
Mainstream sex industry is allowing millions of user to download each day billions of disgusting images staging women in the most humiliating way as possible to satisfy the beasty lust of patriarchy.
FEMEN places sex industry at the same level as dictatorship systems and religious institutions. Those three machines are part of the same whole which we want to destroy.
FEMEN is calling women to rise up against this pukable industry which is feeding fantasies as rape and woman object, always submitted to men desires. Death to sex bosses, freedom for sex-slaves!
TOP-SECRET-DEA General Principles for Payment of Records Requested via Administrative Subpoenas
Light Armored Reconnaissance Battalion Operations in Afghanistan: Lessons and Observations From 4th Light Armored Reconnaissance Battalion July 2009 – May 2010
25 pages
For Official Use Only
July 26, 2010
Download
(U) Purpose: To inform Deputy Commandants (DCs) Combat Development and Integration (CD&I), Plans, Policies, and Operations (PP&O), Installations and Logistics (I&L) Commanding General (CG), Training and Education Command (TECOM), Director of Intelligence, and others on results of a March 2010 collection effort to document lessons and observations from 4th Light Armored Reconnaissance Battalion (4th LAR).
Bottom Line Up Front:
(U//FOUO) The battalion mobilized one month prior to participating in Enhanced Mojave Viper (EMV). Other than for drill weekends prior to mobilization, this four week period was the only time allotted for pre-deployment training (PTP). While the unit was able to meet all of its requirements, a longer mobilization period should be the goal.
(U//FOUO) During drill weekends, the battalion’s main effort was crew cohesion, conducting gunnery and scout integration and platoon level tactics, focusing on “brilliance of the basics.”
(U//FOUO) EMV was still in the process of converting from Iraq to an Afghanistan focus. It was also oriented around a standard infantry battalion and not an LAR unit.
(U//FOUO) The primary mission of the battalion is combined arms reconnaissance and security missions to shape the battlespace. Many of the operations conducted in Afghanistan were not typical LAR operations.
(U//FOUO) As with other units in Afghanistan, 4th LAR operated in a dispersed and distributed manner, often out of platoon size patrol bases. If such operations continue, the numbers of each vehicle variants may have to be modified to better support them.
(U//FOUO) Fluctuating information on force cap restrictions impacted the mobilization process and the decisions made on the final composition of the unit.
(U//FOUO) The late decision to mobilize the battalion impacted the mobilization process for Navy medical personnel and contributed to the delayed arrival of corpsmen to support the battalion.
(U//FOUO) The lack of replacements for casualties in country increased what was already a shortage of light armored vehicle (LAV) crewman for some of the companies.
(U//FOUO) Marine Corps Base (MCB), Camp Pendleton is a particularly well-suited intermediate location (ILOC) site for mobilizing reserve units, due to its proximity to Marine Corps Air Ground Combat Center, 29 Palms and EMV, although it may require more capacity and resources to support multiple units.
(U//FOUO) Some Marines continue to outfit themselves with personally procured equipment and gear.
(U//FOUO) While the upgraded LAV, the A2 variant, generally received praise as an overall improvement, many considered it underpowered with the Ballistic Protection Upgrade Package (BPUP) armor additions mounted.
…
UAVs
(U//FOUO) Each platoon should have at least two Marines trained to operate UAVs.
(U//FOUO) Wasp performed well; a very quiet system, although they were susceptible to damage and replacements were not available. As the system was small and man portable, it extended a level of intelligence, surveillance and reconnaissance (ISR) and force protection to patrol bases and other areas where systems such as G-BOSS were not available.
(U//FOUO) The UAVs used by the unit generally received praise, but both Scan Eagle and Raven were cited as having a noise signature, which can have its own use as a deterrent and force protection, but limits some of their usefulness as a collection platform. Additionally, subordinate units, especially those operating from smaller COPs/FOBs, need to have access to overhead imagery and video, as well an imagery analyst to make it more useful.
(U//FOUO) Scan Eagle was very ineffective in trying to queue off other data collection methods due to its slow speed. LAR’s large AO also impacted the use of Scan Eagle because of range issues.
…
Afghan Border Police
(U//FOUO) LAR worked primarily with Afghan Border Police (ABP) vice Afghan National Army (ANA) or other Afghan units.
ABP were generally poorly trained, poorly equipped, poorly sustained.
Platoon commanders should be prepared to mentor groups of up to 60 ABP at a time, providing much guidance, along with communications and logistical support.
Some ABP speak Pashto, others speak Dari. They can be a good source of language training.
ABP can be helpful for doing things Americans cannot do under rules of engagement (ROE), such as night searches or home searches.
An ABP unit attached to Company C had 60 men and rated 10 Ford Ranger vehicles, but only had 5, and 3 were operable.
Be prepared to supply ABP with radios and other gear. Motorcycles confiscated from enemy forces were given to ABP.
ABP must be carefully supervised as they had a tendency to steal from the local population.
ABP are good at catching people who are fleeing. They wore little body armor, and their vehicles, Ford Rangers, were very light and performed well in the terrain.
…
Biometrics
(U//FOUO) Marines who dealt with Biometric Automated Toolset (BAT) or Handheld Interagency Identity Detection Equipment (HIIDE) said they were extremely unreliable.
Company C reported one of six HIIDE units working.
Company B reported seven HIIDE units stopped working during deployment.
The most common problem was a failure to turn on.
Camera on BAT was very problematic due to external moving lens elements that jam with dust and sand.
Often had to cannibalize multiple BAT systems to make one work.
Iris scanning was very difficult to impossible in bright sun.
Difficult to obtain parts such as extra cables, chargers, etc.
(U//FOUO) Opinion of the battalion leadership was mixed on the value of biometrics:
Pros:
Some enemy forces captured through biometrics.
Two suspected insurgents posing as wood cutters were identified through biometrics on a “rat line” interdiction.
Used effectively on the larger bases for force protection but the system was still slow.
Cons:
A lot of false positives but always from fingerprint comparison, not from iris scans.
Even when working properly, the system was too slow, at times requiring two hours to enroll just six people.
The system became more useful as more people were enrolled, but it also slowed down.
The process of loading data from the HIIDE to BAT, and BAT data uploaded and downloaded over SIPR, was disruptive of other computer operations.
…
Civil Affairs
(U//FOUO) Commander‟s Emergency Response Program (CERP) funds rules and regulations can be very confusing and bureaucratic to use:
Up to $5000 projects are easy and the paperwork is simple.
Process keeps changing. If changes must be made, time them with turnover.
Onerous levels of detail made CERP ineffective for larger projects.
(U//FOUO) The amount of money spent is not an appropriate measure of success. It is simply a means to develop relationships.
(U//FOUO) The Department of State stabilization advisor had more flexibility in regards to spending so the battalion was able to work with him and combine monies to work on larger projects. Also, those projects that only required Marine expeditionary brigade (MEB) level concurrence, generally up to $500,000, were easier to receive approval.
(U//FOUO) Projects, whether bridges, roads, schools, or even playing soccer with local children were tactically important, because they often led to tips on IEDs and enemy forces.
(U//FOUO) The civil affairs group (CAG) detachment, with only four personnel, was undermanned; a team of at least eight, if not ten, was recommended. More team members would allow for decentralization and the ability to support separate COPs and patrol bases.
(U//FOUO) Civil affair projects were difficult to do in some areas. Local leaders would often be roadblocks and would only be relatively tolerant if the project were to benefit them directly.
Monty Python’s Flying Circus: Brontasauraus Theory – Film
John Cleese as a mad woman,
Unveiled – Gambino Family Administration Member Convicted of Racketeering Conspiracy Involving Two Murders
Following a five-week trial, a federal jury in Brooklyn today found Bartolomeo Vernace, a member of the administration of the Gambino organized crime family of La Cosa Nostra (the “Gambino family”), guilty of a racketeering conspiracy spanning 1978 through 2011. As part of the racketeering conspiracy, the jury found that Vernace participated in all nine racketeering acts alleged in the indictment, including the 1981 double homicide of Richard Godkin and John D’Agnese, heroin trafficking, robbery, loansharking, and illegal gambling.
The verdict was announced by Loretta E. Lynch, United States Attorney for the Eastern District of New York, and George C. Venizelos, Assistant Director in Charge, Federal Bureau of Investigation, New York Field Office.
The evidence at trial established that Vernace, also known as “Bobby Glasses,” “Pepe,” and “John Canova,” had a long career in the mafia beginning in the early 1970s and culminating in his induction and rise to become a powerful Gambino family captain who served on the three-member ruling panel overseeing the family that was established in 2008. Vernace was arrested on January 20, 2011, as part of a national sweep of almost 100 members and associates of organized crime led by the U.S. Department of Justice and Federal Bureau of Investigation.
Among the crimes he committed for the mafia, Vernace, together with two Gambino associates, murdered Richard Godkin and John D’Agnese in the Shamrock Bar in the Woodhaven neighborhood of Queens on April 11, 1981, after a dispute arose between a Gambino family associate and others in the bar over a spilled drink. The associate left the bar and picked up Vernace and a third accomplice at a nearby social club. A short time later, the three men entered the bar and gunned down Godkin and D’Agnese—the owners of the bar—as the bar’s patrons fled for cover.
In the weeks after the murders, Vernace went into hiding while one of his close associates, Ronald “Ronnie One-Arm” Trucchio, a rising star in the Gambino family who would later become a powerful captain, sought to question witnesses from the Shamrock Bar that night, placing those witnesses in fear. While in hiding, Vernace was indicted under the alias “Pepe” in the Southern District of New York on heroin trafficking charges. Years later, Vernace, who had avoided state charges for the murders and who had never been identified in connection with the heroin trafficking indictment, returned to Queens and to an active role in the Gambino family. Over the next two decades, his power within the mafia grew as he became actively involved in robbery, loansharking, and gambling, while operating a large and profitable crew from a café on Cooper Avenue in the Glendale neighborhood of Queens.
In 1998, Vernace was charged in Queens County Supreme Court with the Godkin and D’Agnese murders but was acquitted after trial in 2002. During testimony from the first week of the federal trial, an eyewitness to the murders testified that he had lied during the state trial about Vernace’s role in the murders due to fear of retribution. In the federal case, the eyewitness testified he recognized all three assailants but that he had been afraid to testify against them because, in his words, “two men were dead over a spilled drink. I think that was reason enough to be afraid.” The eyewitness further described how, moments before the murders, he saw Vernace pointing a gun at Godkin’s head and taunting him and that he saw one of Vernace’s accomplices threatening D’Agnese with a gun. According to the medical examiner, Godkin was killed by a gunshot to the chest fired from point-blank range, and D’Agnese died from a gunshot to the face.
In addition to the Godkin and D’Agnese murders, the jury found the other seven racketeering acts proved, including heroin trafficking, robbery, loansharking, and gambling and found the defendant guilty of separate firearms and illegal gambling charges as well.
“Organized crime has been depicted by Hollywood as a group of criminals with honor. This case shows what organized crime is really all about—murder, mayhem, and making money off of the weaknesses and addictions of others. Today’s racketeering conspiracy conviction of a powerful Gambino family leader demonstrates, yet again, this office’s unwavering commitment to holding individuals who choose a life of organized crime accountable, regardless of the age of their crimes,” stated United States Attorney Lynch. “The defendant spent the last 40 years pursuing a career of crime, including the vicious double murder, as well as traditional mafia rackets. With this verdict, Vernace has finally been brought to justice and will be held to account for the destruction and pain he has inflicted on his victims and their families. We sincerely hope that today’s verdict helps bring a measure of closure for the families of Vernace’s murder victims, for whom justice has too long been denied.” Ms. Lynch expressed her grateful appreciation to the Federal Bureau of Investigation, the agency responsible for leading the government’s investigation, and to the United States Marshals Service for its assistance during trial.
FBI Assistant Director in Charge Venizelos stated, “The 32 years since Vernace took part in the ruthless double murder of two good men represent half his lifetime. They have not been years spent atoning for those murders. It has been time spent living the life of a mob soldier, capo, and overseer—half a lifetime committing and directing crimes for the Gambino crime family. We expect that Vernace’s remaining years will be spent behind bars where he belongs. There is no expiration date on the FBI’s resolve to see justice done.”
When sentenced by United States District Judge Sandra L. Townes, Bartolomeo Vernace faces a sentence of up to life imprisonment.
The government’s case was prosecuted by Assistant United States Attorneys Evan M. Norris, Amir H. Toossi, and M. Kristin Mace.
Defendant:
Bartolomeo Vernace
Age: 64
TMZ – Rachel Bilson — Barbados Got Back!
TOP-SECRET – CIA PsyWar Strategy Board Progress Report 1952
FEMEN TV : FEMEN against sex industry 2
TOP-SECRET – DEA General Principles for Payment of Records Requested via Administrative Subpoenas
We continue to receive inquiries that indicate there may be some confusion about when payment must be made for records obtained by administrative subpoena. This memorandum summarizes the basic payment principles. Title 21 U.S.C. § 876 authorizes the use of administrative subpoenas to obtain information relating to Title 21 investigations. DEA is under no obligation to pay for information provided in response to its issuance of an administrative subpoena unless a separate Federal statute or regulation specifically states that reimbursement is required.
Upon issuance of a DEA administrative subpoena, the subpoena’s recipient may send to DEA an invoice seeking reimbursement for both the information that the subpoena seeks and any related services. On most occasions the Division Administrative Officer, or his designee, or the Special Operations Division, if applicable, can determine whether payment is authorized. In instances where it is unclear whether payment should be made, clarification should be sought from your Division Counsel or the Office of Chief Counsel. Domestic Criminal Law Section (CCM ).
…
Video Skid – Monty Python’s Meaning of Life
The CIA – President Nixon and and the Role of Intelligence in the 1973 Arab-Israeli War
This collection highlights the causes and consequences of US Intelligence Community’s (IC) failure to foresee the October 1973 Arab-Israeli War, also known as the October War or the Yom Kippur War. A coalition of Arab nations led by Egypt and Syria launched a surprise attack on Israel on October 6, the day of Yom Kippur. Prior to October 6, the CIA concluded that the Arabs would not attack, so the offensive surprised US policymakers as well as Israel. Directorate of Intelligence (DI) analysts believed that Arab military inferiority would militate against an attack on Israel. DI analysis did not explore the possibility that leaders might go to war–even at the risk of losing–to pursue political objectives. According to an internal postmortem, Agency analysis was impaired by preconceptions about Arab military capabilities, information overload, rational actor modeling and groupthink.
View photos from this study on the CIA Flickr stream [external link disclaimer].
View the declassified documents for this collection.
TMZ – Lindsey Vonn Has Tiger Woods by the Tail!
Tiger Woods has been on a winning streak since going public with his gf Lindsey Vonn — but can her good luck charms put him on top at the Masters?
Confidential – Kuchera Brothers Plead Guilty to Fraud Against the Government and to Conspiracy Charges
JOHNSTOWN, PA—Two brothers who owned a major defense contracting firm waived indictment and pleaded guilty today in federal court to charges of major fraud against the government and conspiracy, United States Attorney David J. Hickton announced.
William Kuchera, 58, of Summerhill, Pennsylvania, and Ronald Kuchera, 51, of Johnstown, Pennsylvania, pleaded guilty to two counts before United States District Judge Kim Gibson.
In connection with the guilty plea, the court was advised that William and Ronald Kuchera owned and managed Kuchera Defense Systems Inc. (KDS), a contractor for the Department of Defense. KDS submitted cost certifications to the government containing unallowable expenses that inflated costs for overhead and general and administrative expenses. These unallowable expenses included the leasing of a private airplane, vacations to Jamaica, personal car leases, improvements on a private residence, and lobbying fees.
The Kuchera brothers also submitted a false invoice for $650,000 to Coherent Systems International Inc. (Coherent), a defense contractor owned by Richard S. Ianieri. As the prime contractor, Coherent was responsible for an $8 million Department of Defense contract for the Ground Mobile Gateway Systems, which involved the development of a new prototype unmanned vehicle that was designed to prevent friendly-fire incidents. The invoice sought payment for a component that had never been manufactured or delivered to Coherent. After receiving the $650,000 payment from Coherent, the Kuchera brothers kicked back to Ianieri approximately $200,000.
The court was further advised that each of the Kuchera brothers filed false income tax returns for themselves and KDS. Their personal tax returns were false because they failed to disclose as income certain personal expenses paid for by their companies. The KDS tax returns were false because they included as business deductions certain expenses that were personal expenditures of the two brothers. The brothers also caused the submission of a false corporate tax return that illegally claimed the kickback to Ianieri as a legitimate business expense.
In July 2009, Ianieri pleaded guilty to a one-count criminal information charging him with soliciting kickbacks and filing false purchase orders related to an Air Force contract in Florida. In February 2010, he was sentenced to five years’ probation and was ordered to pay a $200,000 fine.
Each brother also agreed to pay a $50,000 criminal fine to the United States. Ronald Kuchera agreed to the civil forfeiture of an additional $450,000 and agreed to make payment to the Internal Revenue Service in the amount of $121,313, which represents taxes owed due to his filing of false personal tax returns and his share of the taxes owed by KDS. William Kuchera similarly agreed to the civil forfeiture of $450,000 and to pay restitution to the IRS in the amount of $257,168.
The Kuchera brothers and KDS will also pay $2.7 million to resolve their civil liabilities with the United States Department of Defense under the False Claims Act. Ronald Kuchera will pay $950,000, and William Kuchera will pay $829,566. KDS, now doing business as Currency Inc., will pay $920,434 as a result of an audit conducted by the Defense Contract Audit Agency, which uncovered inflated billings for overhead.
“The Kucheras cheated the government by claiming improper reimbursements, submitting a false invoice and then kicking back $200,000 to the prime contractor,” said U.S. Attorney Hickton. “Such blatant and outrageous fraud against the United States cannot and will not be tolerated.”
Judge Gibson scheduled sentencing for October 7, 2013. The law provides for a total sentence of 15 years in prison, a fine of $1,250,000, or both. Under the Federal Sentencing Guidelines, the actual sentence imposed is based upon the seriousness of the offenses and the criminal history, if any, of the defendant.
Assistant United States Attorneys Nelson P. Cohen and Paul E. Skirtich are prosecuting this case on behalf of the government.
The Defense Criminal Investigative Service, the Defense Contract Audit Agency, the U.S. Internal Revenue Service-Criminal Investigations, and the Federal Bureau of Investigation conducted the investigation that led to the prosecution of William Kuchera and Ronald Kuchera.
Cryptome – Is Facebook’s Secretbook Secure?
Is Facebook’s Secretbook Secure?
Date: Thu, 11 Apr 2013 11:56:57 +0100
To: UKcrypto[at]chiark.greenend.org.uk
From: Richard Clayton
Subject: Re: “Secretbook” Lets You Encode Hidden Messages in Your Facebook Pics
Owen Blacker writes:
>http://www.wired.com/dangerroom/2013/04/secretbook/
>
>Facebook is a place where you can share pictures of cute animals and fun
>activities. Now there’s a browser extension that lets you encode those
>images with secret, hard-to-detect messages.
That’s two different properties… if the stego message has been encrypted before it is embedded then if the key is long enough then it is likely to stay secret.
If “too much” data is embedded then it will be detectable by one of a number of methods (real pictures have various statistical properties that are disrupted by the embedding of what is effectively “noise”).
There’s a vast literature on this, good starting place is Jessica Fridrich’s work:
http://www.ws.binghamton.edu/fridrich/
>”The goal of this research was to demonstrate that JPEG steganography can
>be performed on social media where it has previously been impossible,”
>Campbell-Moore tells Danger Room. He says he spent about two months spread
>out over the last year working on the extension as a research project for
>the university.
Embedding short messages into media that will survive transforms is called “watermarking” and there is a large literature on that as well! The initial robustness scheme called StirMark dates from 1997:
http://www.petitcolas.net/fabien/watermarking/stirmark/
And since this is usually successfully passed, there have been later proposals such as CheckMark which add more transforms.
The particular proposal here seems to have been specifically designed to survive Facebook’s transform rather than to survive more general changes to the image.
>It wasn’t easy developing the extension. “Many tools for steganography in
>JPEGs have existed in the past although they have always required that the
>images are transmitted exactly as they are,” Campbell-Moore says.
His draft paper is at:
Click to access secretbook-draft-1.pdf
It contains no references to other work at present, so it’s not possible to see whether or not he has encountered the papers that might disabuse him of this exact statement 😦
>If you’ve encoded a secret message in the image, Facebook will garble
>it. Facebook competitor Google+ doesn’t do this, so you can share
>encoded messages there without needing an app for it.
An important reason for processing the images is that this prevents people installing malicious images on their pages which will compromise visitors whose graphic display software contains security flaws! I fully expect [but have not tested] that Google+ does do some manipulations to avoid this!
—
richard Richard Clayton
They that can give up essential liberty to obtain a little temporary
safety deserve neither liberty nor safety. Benjamin Franklin
__________
List-Id: UK Cryptography Policy Discussion Group
List-Archive:
List-Subscribe:
FEMEN TV : FEMEN against sex industry
Revealed – DoD Instruction 3025.21 Defense Support of Civilian Law Enforcement Agencies
DoD Instruction 3025.21 Defense Support of Civilian Law Enforcement Agencies
42 pages
February 27, 2013
Download
1. PURPOSE. In accordance with the authority in DoD Directive (DoDD) 5111.1 and Deputy Secretary of Defense Memorandum (References (a) and (b)), this Instruction:
a. Establishes DoD policy, assigns responsibilities, and provides procedures for DoD support to Federal, State, tribal, and local civilian law enforcement agencies, including responses to civil disturbances within the United States, including the District of Columbia, the Commonwealth of Puerto Rico, the U.S. Virgin Islands, Guam, American Samoa, the Commonwealth of the Northern Mariana Islands, and any territory or possession of the United States or any other political subdivision thereof in accordance with DoDD 3025.18 (Reference (c)).
b. Prescribes the regulations required by section 375 of title 10, United States Code (U.S.C.) (Reference (d)).
c. Incorporates and cancels DoDDs 3025.12, 5525.5, and 5030.46 (References (e), (f), and (g)).
…
4. POLICY. It is DoD policy that:
a. DoD shall be prepared to support civilian law enforcement agencies consistent with the needs of military preparedness of the United States, while recognizing and conforming to the legal limitations on direct DoD involvement in civilian law enforcement activities.
b. Support of civilian law enforcement agencies by DoD personnel shall be provided in accordance with sections 112, 351, 831, 1116, 1751, and 1385 (also known and hereinafter referred to as “The Posse Comitatus Act, as amended”) of title 18, U.S.C. (Reference (n)); chapter 18 of Reference (d); section 1970 of title 2, U.S.C. (Reference (o)) (for support to the U.S. Capitol Police); and other Federal laws, including those protecting the civil rights and civil liberties of individuals, as applicable.
…
ENCLOSURE 3
PARTICIPATION OF DoD PERSONNEL IN CIVILIAN LAW ENFORCEMENT ACTIVITIES
1. GUIDING STATUTORY REQUIREMENTS AND SUPPORTING POLICIES
a. Statutory Restrictions
(1) The primary restriction on DoD participation in civilian law enforcement activities is the Posse Comitatus Act. It provides that whoever willfully uses any part of the Army or the Air Force as a posse comitatus or otherwise to execute U.S. laws, except in cases and under circumstances expressly authorized by the Constitution or Act of Congress, shall be fined under Reference (n), or imprisoned not more than 2 years, or both.
(2) Section 375 of Reference (d) provides that the Secretary of Defense shall prescribe such regulations as may be necessary to ensure that any activity (including the provision of any equipment or facility or the assignment or detail of any personnel) under chapter 18 of Reference (d) does not include or permit direct participation by a member of the Army, Navy, Air Force, or Marine Corps in a search, seizure, arrest, or other similar activity unless participation in such activity by such member is otherwise authorized by law.
b. Permissible Direct Assistance. Categories of active participation in direct law-enforcement-type activities (e.g., search, seizure, and arrest) that are not restricted by law or DoD policy are:
(1) Actions taken for the primary purpose of furthering a DoD or foreign affairs function of the United States, regardless of incidental benefits to civil authorities. This does not include actions taken for the primary purpose of aiding civilian law enforcement officials or otherwise serving as a subterfuge to avoid the restrictions of the Posse Comitatus Act. Actions under this provision may include (depending on the nature of the DoD interest and the authority governing the specific action in question):
(a) Investigations and other actions related to enforcement of chapter 47 of Reference (d) (also known as “the Uniform Code of Military Justice”).
(b) Investigations and other actions that are likely to result in administrative proceedings by the DoD, regardless of whether there is a related civil or criminal proceeding. (See DoDI 5525.07 (Reference (u)) and Memorandum of Agreement Between the AG and the Secretary of Defense (Reference (v)) with respect to matters in which the DoD and the Department of Justice both have an interest.)
(c) Investigations and other actions related to a commander’s inherent authority to maintain law and order on a DoD installation or facility.
(d) Protection of classified defense information or equipment or controlled unclassified information (e.g., trade secrets and other proprietary information), the unauthorized disclosure of which is prohibited by law.
(e) Protection of DoD personnel, equipment, and official guests.
(f) Such other actions that are undertaken primarily for a military or foreign affairs purpose.
(2) Audits and investigations conducted by, under the direction of, or at the request of the IG, DoD, pursuant to the Inspector General Act of 1978, as amended.
(3) When permitted under emergency authority in accordance with Reference (c), Federal military commanders have the authority, in extraordinary emergency circumstances where prior authorization by the President is impossible and duly constituted local authorities are unable to control the situation, to engage temporarily in activities that are necessary to quell large-scale, unexpected civil disturbances because:
(a) Such activities are necessary to prevent significant loss of life or wanton destruction of property and are necessary to restore governmental function and public order; or,
(b) When duly constituted Federal, State, or local authorities are unable or decline to provide adequate protection for Federal property or Federal governmental functions. Federal action, including the use of Federal military forces, is authorized when necessary to protect Federal property or functions.
(4) DoD actions taken pursuant to sections 331-334 of Reference (d) relating to the use of Federal military forces in specified circumstances with respect to insurrection, domestic violence, or conspiracy that hinders the execution of State or Federal law.
(5) Actions taken under express statutory authority to assist officials in executing the laws, subject to applicable limitations. The laws that permit direct DoD participation in civilian law enforcement include:
(a) Protection of national parks and certain other Federal lands consistent with sections 23, 78, and 593 of title 16, U.S.C. (Reference (w)).
(b) Enforcement of the Fishery Conservation and Management Act of 1976, as amended, pursuant to section 1861(a) of Reference (w).
(c) Assistance in the case of crimes against foreign officials, official guests of the United States, and other internationally protected persons pursuant to sections 112 and 1116 of Reference (n).
(d) Assistance in the case of crimes against Members of Congress, Members-of-Congress-elect, Justices of the Supreme Court and nominees, and certain senior Executive Branch officials and nominees in accordance with section 351 of Reference (n).
(e) Assistance in the case of crimes involving nuclear materials in accordance with section 831 of Reference (n).
(f) Protection of the President, Vice President, and other designated dignitaries in accordance with section 1751 of Reference (n) and Public Law 94-524 (Reference (x)).
(g) Actions taken in support of the neutrality laws in accordance with sections 408 and 461-462 of title 22, U.S.C. (Reference (y)).
(h) Removal of persons unlawfully present on Indian lands in accordance with section 180 of title 25, U.S.C. (Reference (z)).
(i) Execution of quarantine and certain health laws in accordance with section 97 of title 42, U.S.C. (Reference (aa)) and DoDI 6200.03 (Reference (ab)).
(j) Removal of unlawful enclosures from public lands in accordance with section 1065 of title 43, U.S.C. (Reference (ac)).
(k) Protection of the rights of a discoverer of an island covered by section 1418 of title 48, U.S.C. (Reference (ad)).
(l) Support of territorial governors if a civil disorder occurs, in accordance with sections 1422 and 1591 of Reference (ad).
(m) Actions in support of certain customs laws in accordance with section 220 of title 50, U.S.C. (Reference (ae)).
(6) Actions taken to provide search and rescue support domestically under the authorities provided in the National Search and Rescue Plan (Reference (af)) and DoDI 3003.01 (Reference (ag)).
…
ENCLOSURE 4
DoD SUPPORT OF CDO
1. GUIDING STATUTORY REQUIREMENTS AND SUPPORTING POLICIES
a. The President is authorized by the Constitution and laws of the United States to employ the Armed Forces of the United States to suppress insurrections, rebellions, and domestic violence under various conditions and circumstances. Planning and preparedness by the Federal Government, including DoD, for civil disturbances is important due to the potential severity of the consequences of such events for the Nation and the population.
b. The primary responsibility for protecting life and property and maintaining law and order in the civilian community is vested in State and local governments. Supplementary responsibility is vested by statute in specific agencies of the Federal Government other than DoD. The President has additional powers and responsibilities under the Constitution of the United States to ensure that law and order are maintained.
c. Any employment of Federal military forces in support of law enforcement operations shall maintain the primacy of civilian authority and unless otherwise directed by the President, responsibility for the management of the Federal response to civil disturbances rests with the Attorney General. The Attorney General is responsible for receiving State requests for Federal military assistance, coordinating such requests with the Secretary of Defense and other appropriate Federal officials, and presenting such requests to the President who will determine what Federal action will be taken.
d. The employment of Federal military forces to control civil disturbances shall only occur in a specified civil jurisdiction under specific circumstances as authorized by the President, normally through issuance of an Executive order or other Presidential directive authorizing and directing the Secretary of Defense to provide for the restoration of law and order in a specific State or locality in accordance with sections 331-334 of Reference (d).
e. Planning by the DoD Components for CDO shall be compatible with contingency plans for national security emergencies, and with planning for DSCA pursuant to Reference (c). For example:
(1) Guidelines concerning the use of deputized State or local law enforcement powers by DoD uniformed law enforcement personnel are outlined in Reference (ah).
(2) Guidelines concerning the use of deadly force and/or the carrying of firearms by DoD personnel while engaged in duties related to security or law and order, criminal investigations, or counterintelligence investigations; protecting personnel; protecting vital Government assets; or guarding Government installations and sites, property, and persons (including prisoners) are outlined in Reference (ai) and any additional Secretary of Defense-approved rules for the use of force contained in Reference (aj).
2. DoD REQUIREMENTS
a. Federal military forces shall not be used for CDO unless specifically authorized by the President, except under emergency authority as provided in Reference (c) and subparagraph 1.b.(3) of Enclosure 3.
b. Federal military forces shall be made available for CDO as directed by the President. The Secretary of Defense or other authorized DoD official may, where authorized and consistent with the direction of the President, establish the source and composition of those forces to achieve appropriate balance with other national security or DoD priorities.
c. Federal military forces employed in CDO shall remain under Secretary of Defense command and control at all times.
d. The pre-positioning of Federal military forces for CDO shall not exceed a battalion-sized unit in a single location unless a larger force is authorized by the President.
e. DoD Components shall not take charge of any function of civil government unless absolutely necessary under conditions of extreme emergency (e.g., when using emergency authority as described in Reference (c) and subparagraph1.b.(3) of Enclosure 3). Any commander who is directed, or undertakes, to control such functions shall strictly limit DoD actions to emergency needs and shall facilitate the reestablishment of civil responsibility at the earliest time possible.
Video – Skid – Monty Python-Witch Scene
TOP SECRET-Attorney Charges 34 Members and Associates of Two Russian-American Organized Crime Enterprises That Laundered More Than $100 Million
Preet Bharara, the United States Attorney for the Southern District of New York; George Venizelos, the Assistant Director in Charge of the New York Office of the Federal Bureau of Investigation (FBI); Toni Weirauch, the Special Agent in Charge of the New York Field Office of the Internal Revenue Service, Criminal Investigation (IRS-CI); and Raymond W. Kelly, the Police Commissioner of the City of New York (NYPD), announced today the unsealing of charges against 34 alleged members and associates of two related Russian-American organized crime enterprises, including a Russian “Vor,” for a range of offenses including the operation of at least two international bookmaking organizations—or “sportsbooks”—that catered to multi- millionaires and billionaires in the U.S., Russia, and the Ukraine. One enterprise, the Taiwanchik-Trincher Organization, run by VADIM TRINCHER, is alleged to have laundered tens of millions of dollars from Russia and the Ukraine through Cyprus and into the U.S. The other enterprise, the Nahmad-Trincher Organization, run by ILLYA TRINCHER, the son of VADIM TRINCHER, is alleged to have been financed by, among other entities, a prestigious art gallery in New York City.
In connection with the indictment unsealed today in the Southern District of New York, 29 defendants have been arrested in New York, Philadelphia, Detroit, and Los Angeles. The 20 defendants taken into custody today in New York were presented and arraigned in Manhattan federal court before U.S. Magistrate Judge James C. Francis, IV this afternoon. The remaining defendants arrested today will be presented in federal court in Philadelphia, Detroit, and Los Angeles this afternoon. An additional defendant, HILLEL NAHMAD, is expected to surrender in Los Angeles later today. The remaining four defendants—DONALD McCALMONT, BRYAN ZURIFF, WILLIAM EDLER, and ALIMZHAN TOKHTAKHOUNOV—are fugitives and are still being sought.
Manhattan U.S. Attorney Preet Bharara said, “As alleged, these criminal enterprises were vast and many-tentacled, with one of them reaching across the Atlantic to launder tens of millions of dollars from Russia to the U.S. via Cyprus and, in some cases, back again. International money laundering is a serious offense, and we will do everything within our power to inhibit those who seek to sanitize the proceeds of crime through legitimate investment vehicles in this country from doing so.”
FBI Assistant Director in Charge George Venizelos said, “Today’s charges demonstrate the scope and reach of Russian organized crime. One of the principal defendants is a notorious Russian ‘thief-in-law’ allegedly directing an international conspiracy through Cyprus to the U.S. The defendants are alleged to have handled untold millions in illegal wagers placed by millionaires and billionaires, laundered millions, and in some cases are themselves multi-millionaires. Crime pays only until you are arrested and prosecuted.”
IRS-CI Special Agent in Charge Toni Weirauch said, “International money laundering is not a victimless crime. Rather, it is a national and global threat that can provide criminal enterprises with resources to conduct further illegal activity. The laundering of illegal gambling proceeds, in particular, facilitates the underground, untaxed economy which, in turn, harms our nation’s economic strength.”
NYPD Commissioner Raymond W. Kelly said, “The subjects in this case ran high-stakes illegal poker games and online gambling, proceeds from which are alleged to have been funneled to organized crime overseas. The one thing they didn’t bet on was the New York City police and federal investigators’ attention. I commend the NYPD Organized Crime Investigations Division and their partners in the FBI and U.S. Attorney Bharara’s office for identifying and bringing the members of this organization to justice.”
According to the allegations in the Indictment unsealed today in Manhattan federal court and other court documents:
The Taiwanchik-Trincher Organization
The Taiwanchik-Trincher Organization is a nationwide criminal enterprise with strong ties to Russia and Ukraine. The leadership of the organization ran an international sportsbook that catered primarily to Russian oligarchs living in Russia and Ukraine and throughout the world. The Taiwanchik-Trincher Organization laundered tens of millions of dollars in proceeds from the gambling operation from Russia and the Ukraine through shell companies and bank accounts in Cyprus and from Cyprus into the U.S. Once the money arrived in the U.S., it was either laundered through additional shell companies or invested in seemingly legitimate investments, such as hedge funds or real estate.
The Taiwanchik-Trincher Organization operated under the protection of ALIMZHAN TOKHTAKHOUNOV, who is known as a “Vor,” a term translated as “Thief-in-Law” that refers to a member of a select group of high-level criminals from the former Soviet Union.
TOKHTAKHOUNOV used his status as a Vor to resolve disputes with clients of the high-stakes illegal gambling operation with implicit and sometimes explicit threats of violence and economic harm. During a single two-month period, TOKHTAKHOUNOV was paid $10 million for his services by the Taiwanchik-Trincher Organization. TOKHTAKHOUNOV is also under indictment in the Southern District of New York for his alleged involvement in bribing officials at the 2002 Winter Olympics held in Salt Lake City, Utah.
Nahmad-Trincher Organization
The Nahmad-Trincher Organization is a nationwide criminal enterprise with leadership in Los Angeles, California, and New York City. The organization ran a high-stakes illegal gambling business that catered primarily to multi-millionaire and billionaire clients. The organization utilized several online gambling websites that operated illegally in the U.S. Debts owed to the Nahmad-Trincher Organization sometimes reached hundreds of thousands of dollars and even millions. One client, who lost approximately two million dollars to the organization, surrendered his plumbing company to the organization as payment of the debt.
The Nahmad-Trincher Organization was financed by, among others, HILLEL NAHMAD, a/k/a “Helly,” and the art gallery he operates in New York City, the Helly Nahmad Gallery. NAMHAD is also charged with conspiring to commit wire fraud in connection with the sale of a painting worth approximately $250,000.
The organization laundered tens of millions of dollars through various companies and bank accounts. It was assisted in its money laundering by RONALD UY, a branch manager at a bank in New York City. UY advised ILLYA TRINCHER on how to structure financial transactions so as to avoid bank reporting requirements.
Illegal Poker Rooms
The indictment also charges various defendants with promoting and operating high-stakes illegal poker rooms in and around New York City, including EDWIN TING, MOLLY BLOOM, and EUGENE TRINCHER, who is the son of VADIM and brother of ILLYA. The poker games operated by the defendants resulted in gambling debts as high as hundreds of thousands of dollars.
A chart containing the ages, residency information, and charges against the defendants, as well as the maximum penalties they face is below.
Mr. Bharara thanked the FBI, specifically the Eurasian Organized Crime Squad of the New York Office, IRS-CI, and the NYPD for their work in the investigation.
The case is being prosecuted by the Office’s Organized Crime Unit. Assistant U.S. Attorneys Harris Fischman, Peter Skinner, and Joshua A. Naftalis of the Organized Crime Unit are in charge of the prosecution. Assistant U.S. Attorney Alexander Wilson of the Office’s Asset Forfeiture Unit is responsible for the forfeiture aspects of the case.
The charges contained in the indictment are merely accusations, and the defendants are presumed innocent unless and until proven guilty.
NAME
AKA
AGE
RESIDENCE
CHARGES
MAXIMUM PENALTY
ALIMZHAN TOKHTAKHOUNOV
Taiwanchik Alik
64
Moscow, Russia
18 USC: 1962(d) (RICO Conspiracy); 1962(c) (RICO substantive); 1956(h) (Money Laundering Conspiracy); 1955 (Operating an Illegal Gambling Business); 894 (Extortion Conspiracy); 31 USC 5363 and 5366 (Unlawful Internet Gambling)
90 years in prison; 18 years of supervised release; $1,750,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $600 special assessment
VADIM TRINCHER
Dima
52
New York, NY
18 USC: 1962(d) (RICO Conspiracy); 1962(c) (RICO substantive); 1956(h) (Money Laundering Conspiracy); 1955 (Operating an Illegal Gambling Business); 894 (Extortion Conspiracy); 31 USC 5363 and 5366 (Unlawful Internet Gambling)
90 years in prison; 18 years of supervised release; $1,750,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $600 special assessment
ANATOLY GOLUBCHIK
Tony
56
Fort Lee, NJ and New York, NY
18 USC: 1962(d) (RICO Conspiracy); 1962(c) (RICO substantive); 1956(h) (Money Laundering Conspiracy); 1955 (Operating an Illegal Gambling Business); 894 (Extortion Conspiracy); 31 USC 5363 and 5366 (Unlawful Internet Gambling)
90 years in prison; 18 years of supervised release; $1,750,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $600 special assessment
MICHAEL SALL
68
Sunny Isles Beach, FL
18 USC: 1962(d) (RICO Conspiracy); 1956(h) (Money Laundering Conspiracy
40 years in prison, six years of supervised release; $750,000 fine or twice the amount gained from the crimes or twice amount lost by victims; $200 special assessment
STAN GREENBERG
SLAVA
48
New York, NY
18 USC: 1962(d) (RICO Conspiracy); 1956(h) (Money Laundering Conspiracy
40 years in prison, six years of supervised release; $750,000 fine or twice the amount gained from the crimes or twice amount lost by victims; $200 special assessment
ILLYA TRINCHER
27
Beverly Hills, CA
18 USC: 1962(d) (RICO Conspiracy); 1962(c) (RICO substantive); 1956(h) (Money Laundering Conspiracy); 1955 (Operating an Illegal Gambling Business); 894 (Extortion Conspiracy);1084 (Transmission of Wagering Information); 31 USC 5363 and 5366 (Unlawful Internet Gambling); 31 USC 5324 (structuring)
97 years in prison; 22 years of supervised release; $2,250,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $800 special assessment
HILLEL NAHMAD
“Helly”
34
New York
18 USC: 1962(d) (RICO Conspiracy); 1962(c) (RICO substantive); 1956(h) (Money Laundering Conspiracy); 1955 (Operating an Illegal Gambling Business); 1084 (Transmission of Wagering Information); 1349 (Wire Fraud Conspiracy); 31 USC 5363 and 5366 (Unlawful Internet Gambling)
92 years in prison; 19 years of supervised release; $2,000,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $700 special assessment
NOAH SIEGEL
“The Oracle”
30
New York, NY
18 USC: 1962(d) (RICO Conspiracy); 1962(c) (RICO substantive); 1956(h) (Money Laundering Conspiracy); 1955 (Operating an Illegal Gambling Business); 1084 (Transmission of Wagering Information); 31 USC 5363 and 5366 (Unlawful Internet Gambling)
72 years in prison; 16 years of supervised release; $1,750,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $600 special assessment
JOHN HANSON
48
New York, NY
18 USC: 1962(d) (RICO Conspiracy); 1962(c) (RICO substantive); 1956(h) (Money Laundering Conspiracy); 1955 (Operating an Illegal Gambling Business); 894 (Extortion Conspiracy);1084 (Transmission of Wagering Information) 31 USC 5363 and 5366 (Unlawful Internet Gambling)
92 years in prison; 19 years of supervised release; $2,000,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $700 special assessment
JONATHAN HIRSCH
30
New York, NY
18 USC: 1962(d) (RICO Conspiracy); 1955 (Operating an Illegal Gambling Business); 1084 (Transmission of Wagering Information); 31 USC 5363 and 5366 (Unlawful Internet Gambling)
32 years in prison; 19 years of supervised release; $1,000,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $400 special assessment
ARTHUR AZEN
43
Staten Island, NY
18 USC: 1962(d) (RICO Conspiracy); 1962(c) (RICO substantive); 1956(h) (Money Laundering Conspiracy); 2 Counts of 1955 (Operating an Illegal Gambling Business); 2 Counts of 894 (Extortion Conspiracy); 31 USC 5363 and 5366 (Unlawful Internet Gambling)
115 years in prison; 24 years of supervised release; $2,250,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $800 special assessment
DONALD MCCALMONT
DON
45
Massapequa, NY
18 USC: 1962(d) (RICO Conspiracy); 1956(h) (Money Laundering Conspiracy
40 years in prison, six years of supervised release; $750,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $200 special assessment
DMITRY DRUZHINSKY
DIMA BLONDIE
42
Brooklyn, NY
18 USC: 1956(h) (Money Laundering Conspiracy); 1955 (Operating an Illegal Gambling Business); 31 USC 5363 and 5366 (Unlawful Internet Gambling)
30 years in prison, nine years of supervised release; $1,000,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $300 special assessment
ALEXANDER ZAVERUKHA
SASHA
51
Newtown, PA
18 USC 1955 (Operating an Illegal Gambling Business); 31 USC 5363 and 5366 (Unlawful Internet Gambling)
10 years in prison, six years of supervised release; $500,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $200 special assessment
ALEXANDER KATCHALOFF
Murushka
53
Brooklyn, NY
18 USC 1955 (Operating an Illegal Gambling Business); 31 USC 5363 and 5366 (Unlawful Internet Gambling)
10 years in prison, six years of supervised release; $500,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $200 special assessment
ANATOLY SHTEYNGROB
Tony
51
Brooklyn, NY
18 USC 1956(h) (Money Laundering Conspiracy)
20 years in prison, three years of supervised release; $500,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $100 special assessment
ILYA ROZENFELD
53
Staten Island, NY
18 USC 1956(h) (Money Laundering Conspiracy)
20 years in prison, three years of supervised release; $500,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $100 special assessment
PETER SKYLLAS
50
Manhattan
18 USC 1956(h) (Money Laundering Conspiracy)
20 years in prison, three years of supervised release; $500,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $100 special assessment
RONALD UY
32
Jamaica, NY
18 USC 1956(h) (Money Laundering Conspiracy); 31 USC 5324 (structuring)
22 years in prison, six years of supervised release; $750,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $200 special assessment
NICHOLAS HIRSCH
34
New York, NY
18 USC 1349 (Wire Fraud Conspiracy)
20 years in prison, three years of supervised release; $500,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $100 special assessment
BRYAN ZURIFF
43
Los Angeles, CA
18 USC 1955 (Operating an Illegal Gambling Business); 31 USC 5363 and 5366 (Unlawful Internet Gambling)
10 years in prison, six years of supervised release; $500,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $200 special assessment
MOSHE ORATZ
37
Brooklyn, NY
18 USC 1955 (Operating an Illegal Gambling Business); 31 USC 5363 and 5366 (Unlawful Internet Gambling) 894 (Extortion Conspiracy);
30 years in prison, six years of supervised release; $750,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $300 special assessment
KIRILL RAPOPORT
41
Brooklyn, NY
18 USC 894 (Extortion Conspiracy);
20 years in prison, three years of supervised release; $250,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $100 special assessment
DAVID AARON
D.A.
30
Brooklyn, NY
18 USC 1955 (Operating an Illegal Gambling Business); 31 USC 5363 and 5366 (Unlawful Internet Gambling)
10 years in prison, six years of supervised release; $500,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $200 special assessment
JUSTIN SMITH
25
Los Angeles, CA
18 USC 1955 (Operating an Illegal Gambling Business); 31 USC 5363 and 5366 (Unlawful Internet Gambling)
10 years in prison, six years of supervised release; $500,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $200 special assessment
ABRAHAM MOSSERI
39
Longboat Key, FL
18 USC 1955 (Operating an Illegal Gambling Business); 31 USC 5363 and 5366 (Unlawful Internet Gambling)
10 years in prison, six years of supervised release; $500,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $200 special assessment
WILLIAM EDLER
49
Las Vegas, NV
18 USC 1955 (Operating an Illegal Gambling Business); 31 USC 5363 and 5366 (Unlawful Internet Gambling)
10 years in prison, six years of supervised release; $500,000 fine or twice the amount gained from the crimes or twice amount lost by victims; $200 special assessment
PETER FELDMAN
35
Las Vegas, NV
18 USC 1955 (Operating an Illegal Gambling Business); 31 USC 5363 and 5366 (Unlawful Internet Gambling)
10 years in prison, six years of supervised release; $500,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $200 special assessment
EUGENE TRINCHER
26
New York, NY
18 USC 1956(h) (Money Laundering Conspiracy); 18 USC 1955 (Operating an Illegal Gambling Business); 18 USC 1952 (Travel Act)
30 years in prison, nine years of supervised release; $1,000,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $300 special assessment
EDWIN TING
Eddie
41
New York, NY
18 USC 1956(h) (Money Laundering Conspiracy); 18 USC 1955 (Operating an Illegal Gambling Business); 18 USC 1952 (Travel Act)
30 years in prison, nine years of supervised release; $1,000,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $300 special assessment
MOLLY BLOOM
34
Keystone, CO
18 USC 1955 (Operating an Illegal Gambling Business); 18 USC 1952 (Travel Act)
10 years in prison, six years of supervised release; $1500,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $200 special assessment
WILLIAM BARBALAT
41
New York, NY
18 USC 1955 (Operating an Illegal Gambling Business); 18 USC 1952 (Travel Act)
10 years in prison, six years of supervised release; $1500,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $200 special assessment
YUGESHWAR RAJKUMAR
MATEO
42/43
Teaneck, NJ
18 USC 1955 (Operating an Illegal Gambling Business); 18 USC 1952 (Travel Act)
10 years in prison, six years of supervised release; $1500,000 fine or twice the amount gained from the crimes or twice amount lost by victims; $200 special assessment
JOSEPH MANCUSO
JOE THE HAMMER
29
Staten Island, NY
18 USC 1955 (Operating an Illegal Gambling Business); 18 USC 1952 (Travel Act)
10 years in prison, six years of supervised release; $1500,000 fine or twice the amount gained from the crimes or twice the amount lost by victims; $200 special assessment
Twitter
Facebook (1)
Share
TMZ Rob Kardashian’s Ex Rita Ora is LOOKIN’ GOOD
Cryptome – Boston Bomb Blasts
FEMEN TV : FIRE OF REVOLUTION IN FRONT OF A MOSQUE IN PARIS
Videos news agencies covering the burning of the flag Salafi sekstremistkami FEMEN near the main dream in Paris, oddly came to the European audience. We do not claim the existence of censorship or Islamist lobby in the European media business, we are merely stating a fact of absolute absence of footage from the event in the Internet space and airtime. Exclusive Video antiislamistskogo protest FEMEN, provided by Everydayrebellion.net
Please help us in spreading this video!
SECRECY NEWS – NEXT STEPS IN NUCLEAR ARMS CONTROL, AND MORE FROM CRS
Negotiating a treaty to reduce nuclear weapons is so cumbersome and
fraught with political minefields that it can actually retard the process
of disarmament. “It usually takes far longer to reduce nuclear forces
through a bilateral arms control treaty than it takes to adopt unilateral
adjustments to nuclear forces,” according to a new report from the
Congressional Research Service.
“If the Obama Administration reduces U.S. nuclear forces in parallel with
Russia, but without a formal treaty, the two nations could avoid months or
years in negotiation,” the CRS report says. See “Next Steps in Nuclear Arms
Control with Russia: Issues for Congress,” April 10, 2013:
“Recent data… challenge the belief that the [U.S.] manufacturing sector,
taken as a whole, will continue to flourish,” says a newly updated CRS
report. “One interpretation of these data is that manufacturing is
‘hollowing out’ as companies undertake a larger proportion of their
high-value work abroad. These developments raise the question of whether
the United States will continue to generate highly skilled, high-wage jobs
related to advanced manufacturing.” See “‘Hollowing Out’ in U.S.
Manufacturing: Analysis and Issues for Congress,” April 15, 2013:
A rich compilation of information about discretionary government spending
was presented in “Trends in Discretionary Spending,” April 15, 2013:
Some other new or newly updated CRS reports that Congress has not made
publicly available include the following.
Federal Authority to Regulate the Compounding of Human Drugs, April 12,
2013:
Federal Traffic Safety Programs: An Overview, April 1, 2013:
The STOCK Act, Insider Trading, and Public Financial Reporting by Federal
Officials, April 12, 2013:
International Trade and Finance: Key Policy Issues for the 113th Congress,
April 15, 2013:
Why Certain Trade Agreements Are Approved as Congressional-Executive
Agreements Rather Than as Treaties, April 15, 2013:
The United Kingdom and U.S.-UK Relations, April 15, 2013:
A FRESH LOOK AT INVENTION SECRECY
The Invention Secrecy Act of 1951 has been used for more than half a
century to restrict disclosure of patent applications that could be
“detrimental to national security.” At the end of the last fiscal year, no
fewer than 5,321 secrecy orders were in effect.
http://www.fas.org/sgp/othergov/invention/index.html
These secrecy orders have been difficult to penetrate and the stories
behind them have usually been left untold. But several inventors whose
work prompted imposition of a secrecy order were interviewed by G.W. Schulz
of the Center for Investigative Reporting. See his new account in
“Government secrecy orders on patents keep lid on inventions,” April 16,
2013.
JOURNAL OF NATIONAL SECURITY LAW & POLICY
The latest issue of the Journal of National Security Law & Policy has just
been published and can be found online here:
Titles of likely interest include “Free Speech Aboard the Leaky Ship of
State: Calibrating First Amendment Protections for Leakers of Classified
Information” by Heidi Kitrosser, and “Unknotting the Tangled Threads of
Watergate Lore,” a review of Max Holland’s book “Leak” written by M.E.
(Spike) Bowman, among others.
DEFENSE SUPPORT OF CIVILIAN LAW ENFORCEMENT AGENCIES
In last Friday’s Federal Register the Department of Defense published a
final rule on “Defense Support of Civilian Law Enforcement Agencies.” The
rule specifies and defines the support that DoD may provide to federal,
state and local law enforcement agencies, “including responses to civil
disturbances.”
http://www.fas.org/sgp/news/2013/04/dsclea.html
“The President is authorized by the Constitution and laws of the United
States to employ the Armed Forces of the United States to suppress
insurrections, rebellions, and domestic violence under various conditions
and circumstances,” the new rule states.
“Planning and preparedness by the Federal Government, including the
Department of Defense, for civil disturbances is important due to the
potential severity of the consequences of such events for the Nation and
the population. The employment of Federal military forces to control civil
disturbances shall only occur in a specified civil jurisdiction under
specific circumstances as authorized by the President, normally through
issuance of an Executive order or other Presidential directive authorizing
and directing the Secretary of Defense to provide for the restoration of
law and order in a specific State or locality.”
The new rule, which forms part of the Code of Federal Regulations, is
almost identical to DoD Instruction 3025.21 on “Defense Support of Civilian
Law Enforcement Agencies” that was issued on February 27, 2013 (noted by
PublicIntelligence.net on April 11).
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://blogs.fas.org/secrecy/subscribe/
To UNSUBSCRIBE, go to
http://blogs.fas.org/secrecy/unsubscribe/
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
https://members.fas.org/donate
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: http://www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
TOP-SECRET – DHS-FBI Suspicious Activity Reporting Bulletin: Expressed or Implied Threat
ROLL CALL RELEASE
1 page
For Official Use Only
March 1, 2013
Download
(U//FOUO) Expressed or implied threats by an individual or a group communicating intent to commit acts of terrorism or violence or advocating violence against a person, population, or to damage or destroy a facility can be an indicator of pre-operational attack planning. For example, in 2010 a Virginia-based US person pled guilty to communicating threats after he posted a video to the Internet encouraging violent extremists to attack the creators of a television show, including highlighting their residence and urging online readers to “pay them a visit.” He also admitted to soliciting others to desensitize law enforcement by placing suspicious looking but innocent packages in public places, which could then be followed up by real explosives.
(U//FOUO) The following SAR incident reported to the NSI shared space provides an example of an implied threat that could be indicative of pre-operational activity and attack planning. Although it was not ultimately linked to terrorist activity, it is cited as an example for awareness and training purposes:
— (U//FOUO) A courthouse building received an envelope, postmarked out of state, in which a smaller envelope marked “white powder” contained an unknown substance. The incident appeared to be related to 17 other similar suspicious letters containing white substance mailed over a period of several weeks to financial institutions, police departments, state and local government offices, and court facilities.
(U) Possible Indicators of Suspicious Expressed or Implied Threats
(U//FOUO) The following are examples of threats that may constitute warning signs of impending acts of violence. Depending on the context—state of mind of the individual, personal behaviors, and other indicators—expressed or implied threats should be reported to appropriate authorities.
— (U//FOUO) Statements by individuals or groups communicated verbally, in writing, or through video recordings stating the intent to commit violence.
— (U//FOUO) Letters and packages containing suspicious substances accompanied by a note stating that its contents are noxious or intending to communicate threat.
— (U//FOUO) Specific warnings about impending attacks that provide date, time, or place of the threatened attack.
— (U//FOUO) Specific stated threats to individuals or facilities to deter an anticipated action or force compliance with a demand.
(U//FOUO) First Amendment-protected activities should not be reported in a SAR or ISE-SAR absent articulable facts and circumstances that support the source agency’s suspicion that the behavior observed is not innocent, but rather reasonably indicative of criminal activity associated with terrorism, including evidence of pre-operational planning related to terrorism. Race, ethnicity, national origin, or religious affiliation should not be considered as factors that create suspicion (although these factors may be used as specific suspect descriptions).
Video Skid – Monty Python-Holy Hand Grenade from the Movie – “The Holy Grail”
TOP-SECRET – CIA PsyWar Strategy Board Docs 1951-1953
TMZ – Lindsay Lohan Spreads Legs for TSA
It was the moment of truth for Lindsay Lohan when she was pulled aside at JFK airport for a very thorough, very hands-on security pat-down! For once we can’t blame the TSA for profiling…
SECRECY NEWS – NUMBER OF SECURITY CLEARED PERSONNEL GREW IN 2012
The number of people who are cleared for access to classified information
continued to rise in 2012 to more than 4.9 million, according to a new
annual report from the Office of the Director of National Intelligence.
This is only the third official tally of government-wide security clearance
activity ever prepared, and it is the largest reported to date.
Click to access clear-2012.pdf
The total number of cleared personnel as of October 1, 2012 was 4,917,751.
Although the number of contractors who held a clearance declined in 2012,
the number of eligible government employees grew at a faster rate, yielding
a net increase of 54,199 clearances, or 1.1 percent, from the year before.
It is possible that there were more security-cleared Americans at some
points during the Cold War, when there was a larger standing military with
more cleared military personnel than there are today. But until 2010, no
comprehensive account of the size of the security clearance system had ever
been produced. So the new 4.9 million figure is the largest official
figure ever published.
A 2009 report from the Government Accountability Office had estimated that
2.4 million people held clearances, excluding some intelligence agency
employees. But even allowing for one or two hundred thousand cleared
intelligence personnel, this turned out to underestimate the case by nearly
50%. A 1995 GAO report presented an estimate of 3.2 million persons as of
1993.
http://www.fas.org/blog/secrecy/2009/07/security_clearances.html
(Strictly speaking, the new ODNI report does not present data on the
number of clearances but rather on the number of people who have been
investigated and deemed “eligible” for a clearance, regardless of whether
or not they have been granted access to classified information in fact. In
addition to a security clearance, an individual is also supposed to have a
“need to know” particular classified information in order to gain access to
it.)
During 2012, the CIA denied 4.9% of the clearance applications that it
reviewed, the report indicated, while NRO denied 5.9% and NSA denied 5.7%.
Several of the intelligence agencies reported that they had individual
security clearance investigations that had remained open in excess of one
year.
“The IC faces challenges in clearing individuals with unique or critical
skills — such as highly desirable language abilities — who often have
significant foreign associations that may take additional time to
investigate and adjudicate,” the new report said.
The report notes that it was prepared in fulfillment of a requirement in
the 2010 intelligence authorization act. It does not mention the fact that
the DNI asked Congress to cancel that requirement last year.
The DNI’s request to eliminate the report was initially approved by the
Senate Intelligence Committee (as first noted by Marcy Wheeler of the
Emptywheel blog). But then several public interest groups wrote to ask the
House and Senate Intelligence Committees to preserve the annual reporting
requirement, arguing that it provided unique public insight into the size
and operation of the security clearance system. The Committees concurred,
and the reporting requirement was retained.
Click to access clearance_rpt.pdf
In the absence of similar public attention and intervention, another
intelligence community report to Congress on proliferation of weapons of
mass destruction was discontinued at the DNI’s request, to the dismay of
students of arms control.
http://lewis.armscontrolwonk.com/archive/6511/no-more-721-reports
A pending change to the security clearance process is intended to
encourage mental health counseling, but some say it may generate new
confusion, reported Josh Gerstein in Politico today.
U.S. AID TO PAKISTAN, AND MORE FROM CRS
Some lightly updated reports produced lately by the Congressional Research
Service include the following.
Direct Overt U.S. Aid Appropriations for and Military Reimbursements to
Pakistan, FY2002-FY2014, April 11, 2013:
Sensitive Covert Action Notifications: Oversight Options for Congress,
April 10, 2013:
Covert Action: Legislative Background and Possible Policy Questions, April
10, 2013:
Navy Ship Names: Background For Congress, April 8, 2013:
Navy Littoral Combat Ship (LCS) Program: Background and Issues for
Congress, April 5, 2013:
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: http://www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
TV Report – Boston Marathon 2013 Explosion
FEMEN TV : Femen vs Marzouki à Paris
Femen vs Marzouki à Paris (12/04/2013) – Institut du Monde Arabe
Unveiled by Cryptome – U.S. Intelligence Community Performance Standards
Office of the Director of National Intelligence IC Performance Standards
Version 1
April 23, 2009
Download
This document contains the following sections.
– Occupational Structure – Primary components of the occupational structure as defined in ICD 652. These components include the Work Categories and Work Levels.
– Performance Element Model – Definitions of each performance element and the key work behaviors that comprise each element. These work behaviors are the building blocks of the performance standards.
– Performance Standards – A separate set of standards has been defined for the Professional, Supervision/Management, and Technician/Administrative Support Work Categories. Within each of these categories, the performance standards define expectations for each Work Level (i.e., Entry/Developmental, Full Performance, Senior, and Expert). Within each Work Level, standards are anchored at two levels of performance: “Successful” and “Outstanding.”
…
Example Indicators of “Outstanding” Performance
Demonstrates ability to interact effectively with a wide range of individuals under varying circumstances in a manner that far exceeds expectations.
Proactively strives to improve work unit and organizational performance through innovative methods.
Demonstrates unusual creativity – comes up with new products, services, or work products that break new ground and/or greatly improve the organization’s reputation, effectiveness, or efficiency.
Outcomes have broad and significant impact beyond what would ordinarily be expected for his/her band.
Generally performs at a level more consistent with the band above his or her current level.
Operates more independently than would be expected at his/her band level.
Is proactive rather than reactive: anticipates obstacles and actively plans to overcome them; persists in overcoming obstacles or solving problems when others typically give up.
Achieves outcomes and results that are far superior in quality and depth to what would be expected ordinarily at the individual’s band level; work quality is recognized by peers and customers for excellence; work submitted for review requires few, if any, substantive revisions.
Serves as a model performer for peers; is sought out by others for advice and guidance and to handle highly visible, difficult, sensitive, complex, or ambiguous tasks.
Seeks out new responsibilities and assignments outside immediate area of responsibility, leading to additional contributions to the work unit or organization at large.
Puts forth extra effort to accomplish work assignments in the most efficient and effective manner possible – even when demands are very heavy and it is personally inconvenient.
Productivity is above what would be expected normally for the individual’s band level.
Continually strives to improve his or her performance by seeking feedback and through self-directed learning opportunities.
Demonstrates ability to handle more complex, subtle, or unusual problems than would be expected for his/her pay band.
Demonstrates a higher level of knowledge and skill than what would be expected for his/her band.
Recognizes patterns and trends in information or data and pulls together seemingly disparate pieces of information to develop new insights or solve problems.
…
TMZ – Rosie Huntington Whitely — Stiff Upper Nips
It was a cold day in LA yesterday according to our self appointed weather-lady Rosie Hungtington Whitely. While may she may have no experience in Meteorologly…her chest functions as the perfect barometer.
Revealed – Prez Sets Commission on Election Administration
Executive Order 13639
Establishment of the Presidential Commission on Election Administration
Click to access 2013-07837_PI.pdf
[FR Doc. 2013-07837 Filed 04/02/2013 at 8:45 am; Publication Date: 04/03/2013]
EXECUTIVE ORDER 13639
ESTABLISHMENT OF THE PRESIDENTIAL COMMISSION ON ELECTION ADMINISTRATION
By the authority vested in me as President by the Constitution and the laws of the United States of America, and in order to promote the efficient administration of Federal elections and to improve the experience of all voters, it is hereby ordered as follows:
Section 1. Establishment. There is established the Presidential Commission on Election Administration (Commission).
Sec. 2. Membership.
(a) The Commission shall be composed of not more than nine members appointed by the President. The members shall be drawn from among distinguished individuals with knowledge about or experience in the administration of State or local elections, as well as representatives of successful customer service-oriented businesses, and any other individuals with knowledge or experience determined by the President to be of value to the Commission.
(b) The President shall designate two members of the Commission to serve as Co-Chairs.
Sec. 3. Mission.
(a) The Commission shall identify best practices and otherwise make recommendations to promote the efficient administration of elections in order to ensure that all eligible voters have the opportunity to cast their ballots without undue delay, and to improve the experience of voters facing other obstacles in casting their ballots, such as members of the military, overseas voters, voters with disabilities, and voters with limited English proficiency. In doing so, the Commission shall consider as appropriate:
(i) the number, location, management, operation, and design of polling places;
(ii) the training, recruitment, and number of poll workers;
(iii) voting accessibility for uniformed and overseas voters;
(iv) the efficient management of voter rolls and poll books;
(v) voting machine capacity and technology;
(vi) ballot simplicity and voter education;
(vii) voting accessibility for individuals with disabilities, limited English proficiency, and other special needs;
(viii) management of issuing and processing provisional ballots in the polling place on Election Day;
(ix) the issues presented by the administration of absentee ballot programs;
(x) the adequacy of contingency plans for natural disasters and other emergencies that may disrupt elections; and
(xi) other issues related to the efficient administration of elections that the Co-Chairs agree are necessary and appropriate to the Commission’s work.
(b) The Commission shall be advisory in nature and shall submit a final report to the President within 6 months of the date of the Commission’s first public meeting.
Sec. 4. Administration.
(a) The Commission shall hold public meetings and engage with Federal, State, and local officials, technical advisors, and nongovernmental organizations, as necessary to carry out its mission.
(b) In carrying out its mission, the Commission shall be informed by, and shall strive to avoid duplicating, the efforts of other governmental entities.
(c) The Commission shall have a staff which shall provide support for the functions of the Commission.
Sec. 5. Termination. The Commission shall terminate 30 days after it presents its final report to the President.
Sec. 6. General Provisions.
(a) To the extent permitted by law, and subject to the availability of appropriations, the General Services Administration shall provide the Commission with such administrative services, funds, facilities, staff, equipment, and other support services as may be necessary to carry out its mission on a reimbursable basis.
(b) Insofar as the Federal Advisory Committee Act, as amended (5 U.S.C. App.) (the “Act”), may apply to the Commission, any functions of the President under that Act, except for those in section 6 of the Act, shall be performed by the Administrator of General Services.
(c) Members of the Commission shall serve without any additional compensation for their work on the Commission, but shall be allowed travel expenses, including per diem in lieu of subsistence, to the extent permitted by law for persons serving intermittently in the Government service (5 U.S.C. 5701-5707).
(d) Nothing in this order shall be construed to impair or otherwise affect:
(i) the authority granted by law to a department, agency, or the head thereof; or
(ii) the functions of the Director of the Office of Management and Budget relating to budgetary, administrative, or legislative proposals.
(e) This order is not intended to, and does not, create any right or benefit, substantive or procedural, enforceable at law or in equity by any party against the United States, its departments, agencies, or entities, its officers, employees, or agents, or any other person.
THE WHITE HOUSE, March 28, 2013.
Uncensored Video – FEMEN : PUTIN DICTATOR !
German Chancellor Angela Merkel and Russian President Vladimir Putin, Russia’s guest of honor at this year’s Hannover International Industrial Fair to be met. Fuar’da FEME group’s protest against Putin denied by the security guards.
Unveiled – Qatari Ministry of Interior CCTV Surveillance Camera Technical Specifications
The following are technical specifications released by the Qatari Ministry of Interior for CCTV surveillance cameras that are required in all the mentioned categories of businesses operating in Qatar. The specifications were approved in 2011 and released online in late 2012. For more information on the documents, see Carlton Purvis’ article “The World’s Most Demanding Surveillance Requirements” for IP Video Market.
المواصفات العامة المعتمدة لكاميرات وأجهزة المراقبة الأمنية
General Approved CCTV Specifications
| المواصفات الفنية الخاصة بالفنادق والشقق الفندقية والمجمعات السكنية Technical specifications for hotels and hotel apartments and residential complexes |
Download |
| المواصفات الفنية الخاصة بالبنوك والمصارف ومحلات الصرافة ومحلات بيع الذهب Technical specifications of banks, exchange Bank, exchange shop, and Gold Selling Shop |
Download |
| المواصفات الفنية الخاصة بالأندية الرياضية والثقافية Technical specifications for clubs, sports, and cultural |
Download |
| المواصفات الفنية الخاصة بمراكز التسوق والترفيه Technical specifications for shopping and entertainment centers |
Download |
| المواصفات الفنية الخاصة بمراكز المستشفيات والعيـادات Technical specifications for hospitals, and clinics |
Download |
| المواصفات الفنية للمستودعات والمخازن الخاصة بالمواد الخطرة والثمينة Technical specifications of the warehouses and private stores of hazardous materials and precious items |
Download |
Würden Sie dem mutmasslichen Auftraggeber von Internet-Verbrechern, Otmar Knoll, “Fairvesta”, Geld anvertrauen ?
Liebe Leser,
wir haben eine Umfrage gestartet:
Würden Sie dem mutmasslichen Auftraggeber von Internet-Verbrechern, Otmar Knoll, “Fairvesta”, der diese Taten selbst per E-Mail ankündigt, Ihr Geld anvertrauen ?
Und zu welchen Taten halten Sie so jemanden noch für fähig ?
Wir freuen uns auf Ihre Reaktionen !
Hier die Belege für die monatelangen Internet-Attacken der Internet-Kriminellen, die Graphiken zeigen die DDos-Attacken auf über 20 Webseiten:
und
Hier die Rechtslage:
Hier die Bekenner-E-Mail des dubiosen “Otmar Knoll” von der dubiosen “fairvesta”:
Zitat OtmarKnoll/Fairvesta:
|
||||||||||||
|
|
|
|
||||||||||||
|
|
|
Wie sich die Internet-Kriminellen wie mutmasslich Otmar Knoll und “GoMoPa” und Genossen selber entlarven
IMMER WIEDER WERDEN WEBSITES MUTMASSLICH DURCH “GOMoPa” UND DEREN MUTMASSLICHE AUFTRAGGEBER ATTACKIERT WIE MUTMASSLICH “GERD BENNEWIRTZ” UND “PETER EHLERS”SOWIE OTMAR KNOLL / FAIRVESTA:
Zitat OtmarKnoll/Fairvesta:
|
||||||||||||
|
|
||||||||||||
|
Unveiled – Seduced by Secrets – Inside the STASI Tech World – The E-Book – Free Download
Seduced-by-Secrets-Inside-the-Stasis-Spy-Tech-World-2008-Macrakis
In addition to revealing who the spies were, where they worked, and why they did what they did, the Rosenholz material unmasks an incredibly bloated human web of recruiters, instructors, couriers, and residents. The spiderweb was designed to support an agent, but was not cost-effective while it ensnared the secrets of the West. The Stasi simply overestimated the power of stolen technological secrets to solve its economic problems, and the enormous spy infrastructure investment produced a very small return.”
“Scientific-technical intelligence gathering for the MfS usually meant recruiting agents who had access to important Western companies like IBM. Occasionally foreigners volunteered to contribute to the MfS’s scientific developments. An unusual offer came in the mid-sixties from an American computer specialist, Henry Sherwood, who wanted to help East Germany’s data processing industry. Born in Berlin under the name Heinz Weizenbaum, he fled the Nazis in 1936 and arrived in America, where he changed his name while in the U.S. Army. His brother was the famous MIT computer professor Joseph Weizenbaum. Sherwood was invited to direct the Diebold European research program in 1966 and invited the East German Data Processing and Business Machines Company to take part in the program.
Suspicious that Sherwood might be an agent for a capitalist company, the Stasi set four informants on him at the Diebold Conference and between 1966 and 1969 launched ‘Action World Stature’ to try to use the material from the various conferences. Unfortunately, the Stasi staff members did not know English and could not effectively use the material. When Sherwood visited Erfurt, he brought IBM manuals and other material with him, which the Stasi photographed. When there was an opportunity for a German to go to America to acquire more knowledge about data processing, the Stasi vetoed the trip because they were worried that the scientist might be recruited and never come back.
And that was the main contradiction the Stasi presents us with: on the one hand, they vigorously supported state programs by acquiring the needed embargoed or secret technology. On the other hand, security concerns made them work against their own interests by restricting the needed international travel of scientists and by imposing other harmful security measures.
CONFIDENTIAL – Qatari Ministry of Interior CCTV Surveillance Camera Technical Specifications
The following are technical specifications released by the Qatari Ministry of Interior for CCTV surveillance cameras that are required in all the mentioned categories of businesses operating in Qatar. The specifications were approved in 2011 and released online in late 2012. For more information on the documents, see Carlton Purvis’ article “The World’s Most Demanding Surveillance Requirements” for IP Video Market.
المواصفات العامة المعتمدة لكاميرات وأجهزة المراقبة الأمنية
General Approved CCTV Specifications
المواصفات الفنية الخاصة بالفنادق والشقق الفندقية والمجمعات السكنية
Technical specifications for hotels and hotel apartments and residential complexes Download
المواصفات الفنية الخاصة بالبنوك والمصارف ومحلات الصرافة ومحلات بيع الذهب
Technical specifications of banks, exchange Bank, exchange shop, and Gold Selling Shop Download
المواصفات الفنية الخاصة بالأندية الرياضية والثقافية The following are technical specifications released by the Qatari Ministry of Interior for CCTV surveillance cameras that are required in all the mentioned categories of businesses operating in Qatar. The specifications were approved in 2011 and released online in late 2012. For more information on the documents, see Carlton Purvis’ article “The World’s Most Demanding Surveillance Requirements” for IP Video Market.
المواصفات العامة المعتمدة لكاميرات وأجهزة المراقبة الأمنية
General Approved CCTV Specifications
المواصفات الفنية الخاصة بالفنادق والشقق الفندقية والمجمعات السكنية
Technical specifications for hotels and hotel apartments and residential complexes Download
المواصفات الفنية الخاصة بالبنوك والمصارف ومحلات الصرافة ومحلات بيع الذهب
Technical specifications of banks, exchange Bank, exchange shop, and Gold Selling Shop Download
المواصفات الفنية الخاصة بالأندية الرياضية والثقافية
Technical specifications for clubs, sports, and cultural Download
المواصفات الفنية الخاصة بمراكز التسوق والترفيه
Technical specifications for shopping and entertainment centers Download
المواصفات الفنية الخاصة بمراكز المستشفيات والعيـادات
Technical specifications for hospitals, and clinics Download
المواصفات الفنية للمستودعات والمخازن الخاصة بالمواد الخطرة والثمينة
Technical specifications of the warehouses and private stores of hazardous materials and precious items Download
Technical specifications for clubs, sports, and cultural Download
المواصفات الفنية الخاصة بمراكز التسوق والترفيه
Technical specifications for shopping and entertainment centers Download
المواصفات الفنية الخاصة بمراكز المستشفيات والعيـادات
Technical specifications for hospitals, and clinics Download
المواصفات الفنية للمستودعات والمخازن الخاصة بالمواد الخطرة والثمينة
Technical specifications of the warehouses and private stores of hazardous materials and precious items Download
Video Skid – Monty Python- The Annoying Peasant
This scene features a Annoying Peasant that seems to know alot more about goverment than he should. SHUT UP! SHUP UP!!! BLOODY PEASENT!
SECRET – Canadian Forces Guidance for the Conduct of Domestic Operations
NDHQ INSTRUCTION DCDS 2/98 GUIDANCE FOR THE CONDUCT OF DOMESTIC OPERATIONS
38 pages
July 10, 1998
Download
1. The Canadian Forces (CF) is organized, equipped and trained to defend Canada and, in cooperation with Canada’s allies, protect and advance Canada’s interests in the world community. While the CF focuses on its purely military tasks, the inherent flexibility of military units, many with unique capabilities, makes the CF a potential source of assistance which may be called upon to support Canadian civil authorities and the Canadian public in Canada. CF domestic operations are any CF activities which provide assistance in response to requests for support from Canadian civil authorities, or from the Canadian public.
2. Domestic operations are conducted in response to requests from outside the control of the CF, and can take almost infinite form. The response of the CF is, however, strictly bound by the legal responsibilities that enjoin defence activities, and the accountability of commanders at all levels for personnel and material resources under their command.
3. A simplified matrix of the potential scale of CF domestic operations and the necessary levels of approval is illustrated at Annex A. It is important to note that, while in the public eye there is often no clear definition between one type of assistance and another, for the CF there are very distinctive and strict jurisdictional and legal boundaries for different types of assistance, particularly those which may involve the use of force.
…
SECTION 5
ASSISTANCE TO LAW ENFORCEMENT
47. The CF does not have a standing mandate to enforce the laws of Canada. However, there are instances where municipal, provincial/territorial or federal law enforcement agencies may seek CF assistance in discharging their duties, and CF support to law enforcement operations may be authorized. Usually, the required assistance is for a unique or special skill or equipment that is only available from the CF.
48. The CF is also prepared to provide, under legislative or statutory arrangements with federal OGDs, resources to support the enforcement of federal laws, or the maintenance of public safety.
ASSISTANCE TO PROVINCIAL/TERRITORIAL LAW ENFORCEMENT AGENCIES
49. The federal government has approved an Order in Council (OIC) Canadian Forces Assistance to Provincial Police Forces Directions (ref M), and its associated Principles for Federal (Military) Assistance to Provincial Policing. Under ref M, provincial and territorial law enforcement agencies address requests for assistance to the federal Solicitor General. The Solicitor General will either satisfy these from the resources of the RCMP, or may request the MND authorize the CDS to provide CF assistance.
50. CF assistance, when provided, is always in a supporting role to the police force of jurisdiction, which retains full responsibility for enforcing the law.
51. Procedures for assistance to provincial/territorial law enforcement agencies are outlined at Annex C. LFA/CFNAHQs will usually conduct liaison with provincial/territorial law enforcement agencies. The appropriate LFA/CFNAHQ must be informed of any requests for assistance to provincial/territorial policing handled by MARLANT, MARPAC, or 1 CAD.
ASSISTANCE TO FEDERAL LAW ENFORCEMENT AGENCIES
52. While the issue of CF support to provincial/territorial law enforcement operations is clearly defined, the parallel initiative to clarify and standardize arrangements for support to federal law enforcement operations has been overtaken by the 1997 initiative to amend the National Defence Act (ref N). If and when ref N is amended, the CF will review its arrangements and procedures for provision of assistance to federal law enforcement agencies. In the interim, requests for operational equipment and/or CF personnel in support of federal law enforcement operations, other than assistance provided under existing legislation, OIC or Memoranda of Understanding (MOU), must be directed to the MND by the requesting department.
53. The CF preference is that the approach and procedures outlined for assistance to provincial/territorial law enforcement authorities (ref M) be used as a model for responding to requests from federal OGDs. Therefore, while OGDs may direct their requests directly to the MND, the CF will encourage OGDs to initially refer their requests to the federal Solicitor General for assessment and response who, in turn, formally requests CF assistance. If the CF is requested to assist, and the MND authorizes CF assistance, then the CDS will determine the composition of any CF support, its mission, and the level of force authorized.
54. An outline of the arrangements currently in place with certain OGDs for specific support is included at Annex D.
…
INFORMATION AND INTELLIGENCE GATHERING
75. The actions of CF personnel employed on domestic operations are governed by the laws of Canada. CF personnel shall not gather intelligence on Canadian citizens, including any exploitation of the electro-magnetic spectrum aimed at fulfilling intelligence requirements, without a specific legal mandate and direction issued by CDS. CF doctrine and procedures for the production of intelligence for joint and combined operations must not be applied in domestic operations without clear and specific authority. J2 Security Intelligence (J2 SI) maintains the unique DND/CF responsibility for the assessment of national domestic security intelligence, in accordance with instructions issued annually by CDS. Operational level commanders will assess security intelligence in their areas of responsibility, however, responsibility for the collection of domestic security intelligence is vested solely in the Canadian Forces National Counter Intelligence Unit (CFNCIU).
76. Nothing in the foregoing should be construed to stand in the way of CF commanders collecting and maintaining open source information (i.e. media monitoring, press releases, government documents, open-source research and geographic materials, etc) for CF education and situational awareness, unrelated to planning and active operations, in open and unclassified files, or the briefing of commanders and staffs on current events. However, when situations arise where CF involvement is possible, commanders must take care to provide explicit direction and closely supervise information gathering to ensure that limitations on CF intelligence production are observed.
77. The Canadian Forces National Investigative Service (CFNIS), commanded by the Canadian Forces Provost Marshall(CFPM), and the CFNCIU, under NDHQ/J2, are the only agencies authorized to liaise with civil law enforcement agencies and other civilian authorities through the Police Liaison Security Programme (PLSP) (ref P) for police intelligence. In accordance with ref P, the CFNIS and CFNCIU shall only report on intelligence items with a direct DND/CF nexus, which is defined as any situation or event:
a. that threatens DND/CF property or personnel;
b. involving DND/CF personnel; and/or
c. where a civil law enforcement agency has requested DND/CF assistance, or has indicated such a request is imminent.
…
SECRECY NEWS – INTELLIGENCE BUDGET REQUESTS FOR 2014 DISCLOSED
Nebukadnezar99Some $4 billion is being cut from the National Intelligence Program this
year as a result of sequestration, Director of National Intelligence James
Clapper told the House Intelligence Committee at a hearing today. He said
that the consequences will be severe. Acquisition programs will be
“wounded,” ongoing programs will have to be curtailed, and the ensuing
degradation of intelligence capabilities will be “insidious” with
unforeseeable effects, he said.
Meanwhile, the Office of the Director of National Intelligence disclosed
yesterday that the FY 2014 budget request for the National Intelligence
Program (NIP) is $48.2 billion. However, this figure excludes the pending
funding request for Overseas Contingency Operations (OCO), so it cannot be
directly compared to previous budget allocations, such as the $53.9 billion
that was appropriated in FY 2012, or the $52.6 billion that was requested
for FY 2013.
The Secretary of Defense also disclosed the FY 2014 budget request for the
Military Intelligence Program (MIP) yesterday, which was $14.6 billion. It
also did not include the funding request for Overseas Contingency
Operations. This is a slight decline from the $14.7 billion base request
for the MIP last year. (An additional $4.5 billion was known to have been
requested for OCO in the past fiscal year.)
http://www.fas.org/irp/news/2013/04/mip-2014.html
Total intelligence spending (NIP plus MIP) peaked in Fiscal Year 2010, and
has been on a downward slope since then. Intelligence budget disclosures
from the last several years are tabulated here:
http://www.fas.org/irp/budget/index.html
The NIP intelligence budget request was publicly disclosed for the first
time in February 2011, in response to a requirement enacted by Congress in
the FY 2010 intelligence authorization act. The MIP intelligence budget
request was disclosed for the first time in February 2012, even though
there was no specific statutory requirement to do so.
FOREIGN OWNERSHIP OF U.S. FINANCIAL ASSETS, AND MORE FROM CRS
New and updated reports from the Congressional Research Service include
the following.
Foreign Ownership of U.S. Financial Assets: Implications of a Withdrawal,
April 8, 2013:
Foreign Investment and National Security: Economic Considerations, April
4, 2013:
Financial Market Supervision: Canada’s Perspective, April 4, 2013:
The European Union: Foreign and Security Policy, April 8, 2013:
The Berne Union: An Overview, April 5, 2013:
Japan’s Possible Entry Into the Trans-Pacific Partnership and Its
Implications, April 8, 2013:
El Salvador: Political and Economic Conditions and U.S. Relations, April
5, 2013:
Latin America: Terrorism Issues, April 5, 2013:
U.S. Policy Towards Burma: Issues for the 113th Congress, March 12, 2013:
Congressional Authority to Regulate Firearms: A Legal Overview, April 5,
2013:
Procedural Analysis of Private Laws Enacted: 1986-2013, April 9, 2013:
U.S. Natural Gas Exports: New Opportunities, Uncertain Outcomes, April 8,
2013:
Fluoride in Drinking Water: A Review of Fluoridation and Regulation
Issues, April 5, 2013:
State Legalization of Recreational Marijuana: Selected Legal Issues, April
5, 2013:
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: http://www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Film Comedy – Monty.Python’s :Flying Circus – Whither Canada
SECRET – Indictment Seeks Forfeiture Money Judgment of $1 Billion
WASHINGTON—Thirty-four individuals and 23 entities have been indicted and accused of operating an illegal sports bookmaking business that solicited more than $1 billion in illegal bets, announced Acting Assistant Attorney General Mythili Raman of the Justice Department’s Criminal Division and U.S. Attorney for the Western District of Oklahoma Sanford C. Coats. According to the indictment, Bartice Alan King, aka “Luke” and “Cool,” 42, of Spring, Texas, conspired with others to operate Internet and telephone gambling services first from San Jose, Costa Rica and then from Panama City, which took wagers almost exclusively from gamblers in the United States seeking to place bets on sports. Known since 2003 as Legendz Sports, the enterprise allegedly used bookies located in the United States to illegally solicit and accept sports wagers as well as settle gambling debts. The 34 defendants are alleged to have been employees, members, and associates of the ongoing Legendz Sports enterprise. The 23 corporate defendants are alleged to have been used by Legendz Sports to facilitate gambling operations, operate as payment processors, own websites and domain names used in the enterprise, launder gambling funds, and make payouts to gamblers. The indictment alleges that Legendz Sports sought to maximize the number of gamblers who opened wagering accounts by offering both “post-up” betting, which requires a bettor to first set up and fund an account before placing bets and “credit” betting, which allow the bettor to place a wager without depositing money in advance through face-to-face meetings with bookies or agents. The indictment alleges that Legendz Sports solicited millions of illegal bets totaling more than $1 billion. “These defendants allegedly participated in an illegal sports gambling business, lining their pockets with profits from over a billion dollars in illegal gambling proceeds,” said Acting Assistant Attorney General Raman. “Today’s charges demonstrate that we are as determined as ever to hold accountable those involved in facilitating illegal online gambling by U.S. citizens, regardless of where the business operates or where the defendants reside.” “The defendants cannot hide the allegedly illegal sports gambling operation behind corporate veils or state and international boundaries,” said U.S. Attorney Sanford C. Coats. “I thank the IRS and FBI for their diligent work over several years to investigate this billion dollar international gambling enterprise.” “Individuals cannot skirt the laws of the United States by setting up illegal Internet gambling operations in a foreign country while living in the United States and enjoying all the benefits of U.S. citizens,” said Jim Finch, Special Agent in Charge of the FBI Oklahoma City Field Office. “The FBI, along with our law enforcement partners, will continue to be diligent in investigating such violations of federal law.” “Combining the financial investigative expertise of the IRS with the skills and resources of the FBI makes a formidable team for combating major, greed-driven crimes,” said Andrea D. Whelan, Internal Revenue Service Special Agent in Charge. “This massive indictment is the result of our highly effective law enforcement partnership.” If convicted, the defendants face up to 20 years in prison for racketeering, up to 20 years in prison for conspiring to commit money laundering, up to 10 years in prison for money laundering, and up to five years in prison for operating an illegal gambling business. In addition, the indictment seeks a forfeiture money judgment of at least $1 billion traceable to numerous specific assets that include real estate, bank accounts, brokerage and investment accounts, certificates of deposit, individual retirement accounts, domain names, a Sabreliner aircraft, a gas lease, and vehicles. The public is reminded that the indictment is merely an accusation and that the defendants are each presumed innocent unless and until proven guilty. This case is the result of an investigation by the FBI and Internal Revenue Service-Criminal Investigation, with the assistance of U.S. Immigration and Customs Enforcement’s Homeland Security Investigations and the U.S. Marshals Service. The case is being prosecuted by Assistant U.S. Attorneys Susan Dickerson Cox and William Lee Borden, Jr. from the Western District of Oklahoma and Trial Attorney John S. Han with the Department of Justice Criminal Division Organized Crime and Gang Section. For further information, reference is made to the 95-page indictment, which can be found at http://www.justice.gov/usao/okw/news/2013/2013_04_10.html.
Unveiled – WikiLeaks Project K-Release of Kissinger Cables
WikiLeaks Project K – Release of Kissinger Cables
A sends:
From: “Sunshine Press”
Date: Apr 7, 2013 7:37 PM
Subject: WIKILEAKS PRESS RELEASE | THE KISSINGER CABLES OVER 1.3 MILLION DOCUMENTS
To: “Sunshine Press The”
WIKILEAKS SPECIAL PROJECT K: THE KISSINGER CABLES
‘Investigative journalism has never been this effective!’ Publico
The Kissinger Cables are part of today’s launch of the WikiLeaks Public Library of US Diplomacy (PlusD), which holds the world’s largest searchable collection of United States confidential, or formerly confidential, diplomatic communications. As of its launch on April 8, 2013 it holds 2 million records comprising approximately 1 billion words.
WikiLeaks’ publisher Julian Assange stated: “The collection covers US involvements in, and diplomatic or intelligence reporting on, every country on Earth. It is the single most significant body of geopolitical material ever published.”
THE KISSINGER CABLES
“The illegal we do immediately; the unconstitutional takes a little longer.” — Henry A. Kissinger, US Secretary of State, March 10, 1975: http://wikileaks.org/plusd/cables/P860114-1573_MC_b.html#efmCS3CUB
The Kissinger Cables comprise more than 1.7 million US diplomatic records for the period 1973 to 1976, including 205,901 records relating to former US Secretary of State Henry A. Kissinger. Dating from January 1, 1973 to December 31, 1976 they cover a variety of diplomatic traffic including cables, intelligence reports and congressional correspondence. They include more than 1.3 million full diplomatic cables and 320,000 originally classified records. These include more than 227,000 cables classified as “CONFIDENTIAL” and 61,000 cables classified as “SECRET”. Perhaps more importantly, there are more than 12,000 documents with the sensitive handling restriction “NODIS” or ‘no distribution’, and more than 9,000 labelled “Eyes Only”.
At around 700 million words, the Kissinger Cables collection is approximately five times the size of WikiLeaks’ Cablegate. The raw PDF data is more than 380 Gigabytes in size and is the largest WikiLeaks publication to date.
WikiLeaks’ media partners will be reporting throughout the week on their findings. These include significant revelations about US involvements with fascist dictatorships, particularly in Latin America, under Franco’s Spain (including about the Spanish royal family) and in Greece under the regime of the Colonels.
The documents also contain hourly diplomatic reporting on the 1973 war between Israel, Egypt and Syria (the “Yom Kippur war”). While several of these documents have been used by US academic researchers in the past, the Kissinger Cables provides unparalleled access to journalists and the general public.
Most of the records were reviewed by the United States Department of State’s systematic 25-year declassification process. At review, the records were assessed and either declassified or kept classified with some or all of the metadata records declassified. Both sets of records were then subject to an additional review by the National Archives and Records Administration (NARA). Once believed to be releasable, they were placed as individual PDFs at the National Archives as part of their Central Foreign Policy Files collection. Despite the review process supposedly assessing documents after 25 years there are no diplomatic records later than 1976. The formal declassification and review process of these extremely valuable historical documents is therefore currently running 12 years late.
The form in which these documents were held at NARA was as 1.7 million individual PDFs. To prepare these documents for integration into the PlusD collection, WikiLeaks obtained and reverse-engineered all 1.7 million PDFs and performed a detailed analysis of individual fields, developed sophisticated technical systems to deal with the complex and voluminous data and corrected a great many errors introduced by NARA, the State Department or its diplomats, for example harmonizing the many different ways in which departments, capitals and people’s names were spelt. All our corrective work is referenced and available from the links in the individual field descriptions on the PlusD text search interface: https://search.wikileaks.org/plusd
RECLASSIFICATION ATTEMPTS THWARTED
The CIA and other agencies have attempted to reclassify or withhold sections of the US National Archives. Detailed minutes of US State Department meetings show that these attempts, which originated under the Bush II administration, have continued on through until at least 2009. A 2006 analysis by the US National Security Archives, an independent non-governmental research institute and library located at George Washington University, found that 55,000 pages had been secretly reclassified.
The censorship of the US National Archives was thrown into stark relief in November last year when the Archive censored all searches for ‘WikiLeaks’ from its records. See http://dissenter.firedoglake.com/2012/11/03/us-national-archives-has-blocked-searches-for-wikileaks/
Julian Assange, WikiLeaks’ publisher, said: “The US administration cannot be trusted to maintain the history of its interactions with the world. Fortunately, an organisation with an unbroken record in resisting censorship attempts now has a copy.”
MEDIA ORGANIZATIONS REPORTING THIS WEEK
Australia – Fairfax (Sydney Morning Herald, The Age, the Canberra Times and the Australian Fianancial Review)
Argentina – Pagina 12
Brazil – Publica
Bulgaria – Bivol
Egypt – Al Masry Al Youm
Greece – Ta Nea
Guatemala – Plaza Publica
Haiti – Haiti Liberte
India – The Hindu
Italy – L’Espresso
Italy – La Repubblica
Lebanon – Al Akhbar
Mexico – La Jornada
Spain – Publico
Sweden – Aftonbladet
UK – Press Association
US – Associated Press
US – The Nation
PRESS CONFERENCE
WikiLeaks Special Project K: concerning the United States, Latin America, the Middle East, Africa, Central and South East Asia, Europe and the Pacific, with special focus on Israel, Russia, India, Japan, South Africa, France and Francophone Africa.
WHERE
The National Press Club
The Holeman Lounge
529 14th St. NW
13th Floor
Washington, DC
20045
+1 202-662-7500
WHEN
Monday April 8th at 9am (Washington time)
INTERVIEWS
WikiLeaks Spokesperson Kristinn Hrafnsson is available for interviews after the press conference please make arrangements with Melanie Lerardi ( Mlerardi@press.org ) or +1 (202) 662 7502 alternatively you can call Kristinn directly on +354 821 7121 or email sunshinepress@this.is
STATUS UPDATES
WIKILEAKS AND JULIAN ASSANGE
After WikiLeaks’ publication of Pentagon and State Department documents in 2010, the White House launched a multi-agency investigation into WikiLeaks and its publisher Julian Assange. The investigation includes the Department of Justice (DOJ), the FBI, the State Department, the CIA and the Defense Intelligence Agency (DIA) among others. The DoJ / FBI investigation is ongoing, as is its associated Grand Jury in Alexandria, Virginia, which is headed up by District Attorney Neil McBride, a current candidate for the FBI directorship.
A number of senior political figures in the United States have called for the assassination, extraordinary rendition or kidnapping of Julian Assange and other WikiLeaks staff and for the execution of WikiLeaks US sources: http://www.youtube.com/watch?v=ZuQW0US2sJw
The Grand Jury has coercively forced numerous people to give testimony in secret and to do so without the presence of a judge or defence lawyer. The actions of the Grand Jury, including issuing PATRIOT Act ‘subpoenas’ against Twitter, Google and other companies, is the subject of ongoing legal proceedings.
On 1 February this year, the Associated Press reported that the FBI was conducting an illegal investigation into WikiLeaks‚Äô activities in Iceland. This investigation was discovered by the Icelandic Minister of the Interior, Ögmundur Jónasson, who ordered the FBI to leave and issued a formal diplomatic protest to the United States.
Julian Assange, an Australian, was granted political asylum on 19 August 2012 by the government of Ecuador. He remains under their protection in the Embassy of Ecuador in London. British police have surrounded the embassy and the British government admits to spending more than $4.5 million on this policing presence so far. Contrary to international law, the United Kingdom refuses to grant Julian Assange safe passage to Ecuador, saying that he must be extradited to Sweden to answer questions. He has not been charged with an offence in either country and the chief of the Swedish Supreme Court says there is no legal reason why Swedish police cannot go to London should they wish to speak to him.
By 8 April 2013 Julian Assange will have been imprisoned, detained under house arrest in the United Kingdom, and unable to leave the protective custody of the Ecuadorian Embassy for a total of 854 days.
On 11 April 2013 a feature film about Julian Assange in his formative years will open the Washington DC International Film Festival: http://www.filmfestdc.org
Julian Assange is a popular figure in his native Australia, where he is running for the Australian Senate. The latest poll, by Labour party polling outfit UMR, showed he had 27 per cent of the voting intention: http://wikileaksparty.org.au/
For further information see: http://justice4assange.com/extraditing-assange.html and https//usvwikileaks.org/ and http://justice4assange.com/
BRADLEY MANNING
An alleged WikiLeaks source, intelligence analyst Bradley Manning, now aged 25, was arrested on 26 May 2010 by US Army investigators. Manning was detained under extreme conditions in Kuwait and Marine Corps Base Quantico, Virginia. The United Nations Rapporteur on Torture Juan E. Mendez formally found these conditions to amount to “cruel and abusive treatment” akin to torture. Judge Denise Lind of the US military court found that his conditions were illegal. After the resignation of Assistant Secretary of State for Public Affairs P. J. Crowley over the issue, Manning was transferred to Fort Leavenworth, Kansas, and the Quantico barracks were decommissioned. Mr. Manning’s defence team said that the abusive treatment may have been in order to break Mr. Manning into turning State’s witness against WikiLeaks publisher Julian Assange.
By 8 April 2013 Bradley Manning will have been detained without trial for 1049 days, the longest detention without trial of a US soldier in modern history. His trial is said by Guantanamo beat reporters to be more secret that the military commissions held against al Qaeda suspects. It is scheduled for 2 June 2013 at Fort Meade, Maryland. WikiLeaks, the Center for Constitutional Rights and more than 30 other media organizations have filed suit against the US military for the abuse of secrecy used in prosecuting the case.
ECONOMIC CENSORSHIP: BANKING BLOCKADE
After documented political pressure, including from Senator Joseph Lieberman and Congressman Peter T. King, VISA, MasterCard, Bank of America, PayPal, Western Union, AMEX, Diners Club, Discover and JCB erected an extra-legal banking blockade against the WikiLeaks organization and its donors. The blockade is the subject of ongoing litigation and a resolution by the European Parliament. It has been condemned by the United Nations Special Rapporteur for Freedom of Expression, Frank La Rue, the New York Times, Reporters Without Borders, the Electronic Frontier Foundation, Amnesty International, the Council of Europe, and numerous other organizations.
The fiscal blockade against WikiLeaks is similar to that conducted against the central banks of Cuba and Iran, however, unlike these two countries, the WikiLeaks blockade is being conducted with no known legal or administrative basis. In fact, the US Secretary of the Treasury found in early 2011 that there was no legal reason to place WikiLeaks under a US embargo. Due to the market dominance of VISA, MasterCard and PayPal, the extra-legal action has cut off 95 per cent of WikiLeaks’ income stream, costing the organization more than $50 million dollars.
All litigation to date has been won by WikiLeaks and its partners, but the blockade continues. An appeal, lodged by Valitor (Visa Iceland) is to be heard by the Icelandic Supreme Court on April 15, 2013.
BREAKING THE BLOCKADE: THE US FREEDOM OF THE PRESS FOUNDATION
In December 2012 Daniel Ellsberg, John Cusack, John Perry Barlow, Glenn Greenwald and others launched the Freedom of the Press Foundation, which allows US citizens to bypass the blockade to make tax-deductable and anonymous donations to WikiLeaks. For more information go to: See https://pressfreedomfoundation.org/ and http://wikileaks.org/WikiLeaks-declares-war-on-banking.html
[]YouTube – Videos from this email
TOP-SECRET – Canadian Forces Guidance for the Conduct of Domestic Operations
NDHQ INSTRUCTION DCDS 2/98 GUIDANCE FOR THE CONDUCT OF DOMESTIC OPERATIONS
38 pages
July 10, 1998
Download
1. The Canadian Forces (CF) is organized, equipped and trained to defend Canada and, in cooperation with Canada’s allies, protect and advance Canada’s interests in the world community. While the CF focuses on its purely military tasks, the inherent flexibility of military units, many with unique capabilities, makes the CF a potential source of assistance which may be called upon to support Canadian civil authorities and the Canadian public in Canada. CF domestic operations are any CF activities which provide assistance in response to requests for support from Canadian civil authorities, or from the Canadian public.NDHQ INSTRUCTION DCDS 2/98 GUIDANCE FOR THE CONDUCT OF DOMESTIC OPERATIONS
38 pages
July 10, 1998
Download
1. The Canadian Forces (CF) is organized, equipped and trained to defend Canada and, in cooperation with Canada’s allies, protect and advance Canada’s interests in the world community. While the CF focuses on its purely military tasks, the inherent flexibility of military units, many with unique capabilities, makes the CF a potential source of assistance which may be called upon to support Canadian civil authorities and the Canadian public in Canada. CF domestic operations are any CF activities which provide assistance in response to requests for support from Canadian civil authorities, or from the Canadian public.
2. Domestic operations are conducted in response to requests from outside the control of the CF, and can take almost infinite form. The response of the CF is, however, strictly bound by the legal responsibilities that enjoin defence activities, and the accountability of commanders at all levels for personnel and material resources under their command.
3. A simplified matrix of the potential scale of CF domestic operations and the necessary levels of approval is illustrated at Annex A. It is important to note that, while in the public eye there is often no clear definition between one type of assistance and another, for the CF there are very distinctive and strict jurisdictional and legal boundaries for different types of assistance, particularly those which may involve the use of force.
…
SECTION 5
ASSISTANCE TO LAW ENFORCEMENT
47. The CF does not have a standing mandate to enforce the laws of Canada. However, there are instances where municipal, provincial/territorial or federal law enforcement agencies may seek CF assistance in discharging their duties, and CF support to law enforcement operations may be authorized. Usually, the required assistance is for a unique or special skill or equipment that is only available from the CF.
48. The CF is also prepared to provide, under legislative or statutory arrangements with federal OGDs, resources to support the enforcement of federal laws, or the maintenance of public safety.
ASSISTANCE TO PROVINCIAL/TERRITORIAL LAW ENFORCEMENT AGENCIES
49. The federal government has approved an Order in Council (OIC) Canadian Forces Assistance to Provincial Police Forces Directions (ref M), and its associated Principles for Federal (Military) Assistance to Provincial Policing. Under ref M, provincial and territorial law enforcement agencies address requests for assistance to the federal Solicitor General. The Solicitor General will either satisfy these from the resources of the RCMP, or may request the MND authorize the CDS to provide CF assistance.
50. CF assistance, when provided, is always in a supporting role to the police force of jurisdiction, which retains full responsibility for enforcing the law.
51. Procedures for assistance to provincial/territorial law enforcement agencies are outlined at Annex C. LFA/CFNAHQs will usually conduct liaison with provincial/territorial law enforcement agencies. The appropriate LFA/CFNAHQ must be informed of any requests for assistance to provincial/territorial policing handled by MARLANT, MARPAC, or 1 CAD.
ASSISTANCE TO FEDERAL LAW ENFORCEMENT AGENCIES
52. While the issue of CF support to provincial/territorial law enforcement operations is clearly defined, the parallel initiative to clarify and standardize arrangements for support to federal law enforcement operations has been overtaken by the 1997 initiative to amend the National Defence Act (ref N). If and when ref N is amended, the CF will review its arrangements and procedures for provision of assistance to federal law enforcement agencies. In the interim, requests for operational equipment and/or CF personnel in support of federal law enforcement operations, other than assistance provided under existing legislation, OIC or Memoranda of Understanding (MOU), must be directed to the MND by the requesting department.
53. The CF preference is that the approach and procedures outlined for assistance to provincial/territorial law enforcement authorities (ref M) be used as a model for responding to requests from federal OGDs. Therefore, while OGDs may direct their requests directly to the MND, the CF will encourage OGDs to initially refer their requests to the federal Solicitor General for assessment and response who, in turn, formally requests CF assistance. If the CF is requested to assist, and the MND authorizes CF assistance, then the CDS will determine the composition of any CF support, its mission, and the level of force authorized.
54. An outline of the arrangements currently in place with certain OGDs for specific support is included at Annex D.
…
INFORMATION AND INTELLIGENCE GATHERING
75. The actions of CF personnel employed on domestic operations are governed by the laws of Canada. CF personnel shall not gather intelligence on Canadian citizens, including any exploitation of the electro-magnetic spectrum aimed at fulfilling intelligence requirements, without a specific legal mandate and direction issued by CDS. CF doctrine and procedures for the production of intelligence for joint and combined operations must not be applied in domestic operations without clear and specific authority. J2 Security Intelligence (J2 SI) maintains the unique DND/CF responsibility for the assessment of national domestic security intelligence, in accordance with instructions issued annually by CDS. Operational level commanders will assess security intelligence in their areas of responsibility, however, responsibility for the collection of domestic security intelligence is vested solely in the Canadian Forces National Counter Intelligence Unit (CFNCIU).
76. Nothing in the foregoing should be construed to stand in the way of CF commanders collecting and maintaining open source information (i.e. media monitoring, press releases, government documents, open-source research and geographic materials, etc) for CF education and situational awareness, unrelated to planning and active operations, in open and unclassified files, or the briefing of commanders and staffs on current events. However, when situations arise where CF involvement is possible, commanders must take care to provide explicit direction and closely supervise information gathering to ensure that limitations on CF intelligence production are observed.
77. The Canadian Forces National Investigative Service (CFNIS), commanded by the Canadian Forces Provost Marshall(CFPM), and the CFNCIU, under NDHQ/J2, are the only agencies authorized to liaise with civil law enforcement agencies and other civilian authorities through the Police Liaison Security Programme (PLSP) (ref P) for police intelligence. In accordance with ref P, the CFNIS and CFNCIU shall only report on intelligence items with a direct DND/CF nexus, which is defined as any situation or event:
a. that threatens DND/CF property or personnel;
b. involving DND/CF personnel; and/or
c. where a civil law enforcement agency has requested DND/CF assistance, or has indicated such a request is imminent.
…
2. Domestic operations are conducted in response to requests from outside the control of the CF, and can take almost infinite form. The response of the CF is, however, strictly bound by the legal responsibilities that enjoin defence activities, and the accountability of commanders at all levels for personnel and material resources under their command.
3. A simplified matrix of the potential scale of CF domestic operations and the necessary levels of approval is illustrated at Annex A. It is important to note that, while in the public eye there is often no clear definition between one type of assistance and another, for the CF there are very distinctive and strict jurisdictional and legal boundaries for different types of assistance, particularly those which may involve the use of force.
…
SECTION 5
ASSISTANCE TO LAW ENFORCEMENT
47. The CF does not have a standing mandate to enforce the laws of Canada. However, there are instances where municipal, provincial/territorial or federal law enforcement agencies may seek CF assistance in discharging their duties, and CF support to law enforcement operations may be authorized. Usually, the required assistance is for a unique or special skill or equipment that is only available from the CF.
48. The CF is also prepared to provide, under legislative or statutory arrangements with federal OGDs, resources to support the enforcement of federal laws, or the maintenance of public safety.
ASSISTANCE TO PROVINCIAL/TERRITORIAL LAW ENFORCEMENT AGENCIES
49. The federal government has approved an Order in Council (OIC) Canadian Forces Assistance to Provincial Police Forces Directions (ref M), and its associated Principles for Federal (Military) Assistance to Provincial Policing. Under ref M, provincial and territorial law enforcement agencies address requests for assistance to the federal Solicitor General. The Solicitor General will either satisfy these from the resources of the RCMP, or may request the MND authorize the CDS to provide CF assistance.
50. CF assistance, when provided, is always in a supporting role to the police force of jurisdiction, which retains full responsibility for enforcing the law.
51. Procedures for assistance to provincial/territorial law enforcement agencies are outlined at Annex C. LFA/CFNAHQs will usually conduct liaison with provincial/territorial law enforcement agencies. The appropriate LFA/CFNAHQ must be informed of any requests for assistance to provincial/territorial policing handled by MARLANT, MARPAC, or 1 CAD.
ASSISTANCE TO FEDERAL LAW ENFORCEMENT AGENCIES
52. While the issue of CF support to provincial/territorial law enforcement operations is clearly defined, the parallel initiative to clarify and standardize arrangements for support to federal law enforcement operations has been overtaken by the 1997 initiative to amend the National Defence Act (ref N). If and when ref N is amended, the CF will review its arrangements and procedures for provision of assistance to federal law enforcement agencies. In the interim, requests for operational equipment and/or CF personnel in support of federal law enforcement operations, other than assistance provided under existing legislation, OIC or Memoranda of Understanding (MOU), must be directed to the MND by the requesting department.
53. The CF preference is that the approach and procedures outlined for assistance to provincial/territorial law enforcement authorities (ref M) be used as a model for responding to requests from federal OGDs. Therefore, while OGDs may direct their requests directly to the MND, the CF will encourage OGDs to initially refer their requests to the federal Solicitor General for assessment and response who, in turn, formally requests CF assistance. If the CF is requested to assist, and the MND authorizes CF assistance, then the CDS will determine the composition of any CF support, its mission, and the level of force authorized.
54. An outline of the arrangements currently in place with certain OGDs for specific support is included at Annex D.
…
INFORMATION AND INTELLIGENCE GATHERING
75. The actions of CF personnel employed on domestic operations are governed by the laws of Canada. CF personnel shall not gather intelligence on Canadian citizens, including any exploitation of the electro-magnetic spectrum aimed at fulfilling intelligence requirements, without a specific legal mandate and direction issued by CDS. CF doctrine and procedures for the production of intelligence for joint and combined operations must not be applied in domestic operations without clear and specific authority. J2 Security Intelligence (J2 SI) maintains the unique DND/CF responsibility for the assessment of national domestic security intelligence, in accordance with instructions issued annually by CDS. Operational level commanders will assess security intelligence in their areas of responsibility, however, responsibility for the collection of domestic security intelligence is vested solely in the Canadian Forces National Counter Intelligence Unit (CFNCIU).
76. Nothing in the foregoing should be construed to stand in the way of CF commanders collecting and maintaining open source information (i.e. media monitoring, press releases, government documents, open-source research and geographic materials, etc) for CF education and situational awareness, unrelated to planning and active operations, in open and unclassified files, or the briefing of commanders and staffs on current events. However, when situations arise where CF involvement is possible, commanders must take care to provide explicit direction and closely supervise information gathering to ensure that limitations on CF intelligence production are observed.
77. The Canadian Forces National Investigative Service (CFNIS), commanded by the Canadian Forces Provost Marshall(CFPM), and the CFNCIU, under NDHQ/J2, are the only agencies authorized to liaise with civil law enforcement agencies and other civilian authorities through the Police Liaison Security Programme (PLSP) (ref P) for police intelligence. In accordance with ref P, the CFNIS and CFNCIU shall only report on intelligence items with a direct DND/CF nexus, which is defined as any situation or event:
a. that threatens DND/CF property or personnel;
b. involving DND/CF personnel; and/or
c. where a civil law enforcement agency has requested DND/CF assistance, or has indicated such a request is imminent.
…
Monty Python – Hospital Sketch – Video Skid
TOP-SECRET – U.S.-Canada Civil Assistance Plan 2012
CANADA – U.S. CIVIL ASSISTANCE PLAN (CAP) CANUS CAP-12
- 118 pages
- For Official Use Only
- January 25, 2012
1. This bilateral plan provides a framework for military forces of one nation to support military forces of the other nation that are providing military support of civil authorities.
2. The focus of this document is the unique, bilateral military planning considerations required to align our respective national military plans to respond quickly to national requests for military support of civil authorities. Nothing in this plan prevents either nation from responding unilaterally; rather, this plan will facilitate unity of effort, if and when requests for bilateral support are received.
…
1. Situation
a. General. The purpose of the Canada-United States Civil Assistance Plan (CAP) is to provide a framework for the military of one nation to provide support to the military of the other nation while in the performance of civil support operations to the primary agency (e.g., floods, forest fires, hurricanes, earthquakes, and effects of a terrorist attack).
(1) Should resources be identified outside the capabilities of each nations’ military, requests for civilian agency support would require Government of Canada (GoC) or U.S. Government (USG) approval. Support covered under this plan will only be provided when agreed to by appropriate authorities in both the GoC and the USG. When approved, military forces from one nation augment the other nation’s forces in civil support operations.
(2) Military support under this plan is not provided directly to law enforcement agencies, but rather to the other nation’s military. Support to law enforcement operations will only be considered as part of military-to-military support to civil support operations; typically, restricted to logistical and other means of indirect assistance unless coordinated and approved by both nations’ governments prior to mission execution. One nation’s military will never be directly in support of the other nation’s law enforcement agencies. GoC and USG approval will clearly delineate command relationships to ensure any military support to a nation’s law enforcement operations is under the control of that nation’s military commander.
(3) Guidance and direction to develop this plan is derived from Ref 1f. This bilateral plan may be used alone, or concurrent with the Canada-U.S. Combined Defense Plan or other national, bi-national or bi-lateral plans. The Commander, Canada COM and CDRUSNORTHCOM are the designated planning agents for the development of this plan.b. Federal Coordination of Emergency Response. The Canadian Department of Foreign Affairs and International Trade (DFAIT), acting on behalf of the GoC, and the U.S. Department of State (DOS), acting on behalf of the USG, will, upon receipt of a formal request for, or offer of mutual assistance, coordinate an agreed upon bilateral response with the appropriate government agency that may include military support.
(1) Coordination of military support of civilian authorities will take into account existing government to government agreements, which may include the bi-national NORAD Agreement and/or regional State/Provincial agreements. The supported nation’s military will coordinate the provision of all military support to their civil authorities.
(2) In the United States, coordination of foreign assistance for a disaster is conducted per the International Assistance System Concept of Operations.c. Area of Responsibility (AOR). The geographic AOR includes North America, the Gulf of Mexico, the Straits of Florida; the Caribbean region inclusive of the U.S. Virgin Islands, British Virgin Islands, Puerto Rico, the Bahamas, and Turks and Caicos Islands, including each nation’s territorial seas; and the maritime approaches to North America.
d. Opposing Force. Opposing forces are not expected during the conduct of operations described in this plan. However, when planning and conducting operations where the military forces of one nation are supporting the military forces of the other nation while they conduct civil support operations, commanders should consider operational security (OPSEC) along with the following anti-terrorism/force protection (AT/FP) issues: (1) Terrorists organizations could conduct operations against the Canadian or U.S. force, or in the civil support operations area; (2) State/provincial and local police capabilities could be severely degraded in the area of operations, allowing a corresponding rise in criminal activity that could affect the Canadian or U.S. force; and (3) Environmental factors ranging from weather to contamination and disease could significantly affect the Canadian or U.S. forces.
e. Friendly
(1) CANADA
(a) The Department of Foreign Affairs and International Trade (DFAIT). DFAIT is responsible on behalf of the GoC for facilitating requests for international assistance.
(b) Public Safety Canada (PS). The Minister of Public Safety is assigned primary responsibility within the GoC to coordinate the federal response in crisis and consequence management situations within Canada.
(c) Department of National Defence (DND) / Canadian Forces (CF). The CF may, upon request, provide support to PS, other federal departments and agencies, provincial/territorial and municipal authorities pursuant to the National Defence Act (NDA), or other legal authority. Commander, Canada COM is the responsible CF operational commander within the Canada COM AOR defined as Canada, the contiguous United States, Alaska, Mexico, and the maritime approaches to North America.(2) UNITED STATES
(a) Department of State (DOS). The Department of State is responsible for coordinating with other nations for disaster assistance, including military assistance. (Ref 3l).
(b) Department of Homeland Security (DHS). The Secretary of DHS is the principal federal official (PFO) responsible for U.S. domestic incident management. As a component of DHS, the Federal Emergency Management Agency (FEMA) is responsible for leading and supporting a risk-based, comprehensive emergency management system of preparedness, protection, response, recovery and mitigation to reduce the loss of life and property and protect the U.S. from all hazards.
(c) Department of Defense (DOD). In accordance with the National Response Framework (Ref 3k) DOD may, upon request, provide support to DHS and other federal agencies for domestic Defense Support of Civil Authorities (DSCA). Upon SecDef approval, CDRUSNORTHCOM is the supported combatant commander with responsibility to coordinate defense support to federal agencies within the portion of the United States that lies within CDRUSNORTHCOM’s AOR.f. Assumptions
(1) Requirements for military support of civilian authorities could be fulfilled by either nation’s military. However, the nation providing cross-border military support will not fulfill these requirements directly to the other nation’s civilian authorities, but rather to the other nation’s military who in turn supports that nation’s civil authorities.
(2) Operations will typically occur in a permissive environment.…
j. Law enforcement and regulatory functions.
(1) United States.
(a) USNORTHCOM forces are generally prohibited from directly participating in the enforcement of U.S. law. Exceptions to this general rule and categories of permissible support to law enforcement are outlined in the references at paragraph 1.k(1) of this Appendix. The NORTHCOM SJA shall advise on any contemplated USNORTHCOM support to U.S. law enforcement.
(b) The PCA does not prohibit USNORTHCOM forces from directly participating in the enforcement of U.S. law outside of U.S. territory; however, DOD policy prohibits such activities unless authorized by SecDef (see DoDD 5525.5). The PCA does not prohibit USNORTHCOM forces from supporting Canada Command in the enforcement of Canadian law; however, such operations must be authorized by the SecDef and CDS and must be consistent with Canadian law. The NORTHCOM SJA shall advise on any contemplated USNORTHCOM support to U.S. law enforcement. (See references at paragraph 1.k(1))(2) Canada.
(a) The CF has no mandate to conduct civilian law enforcement activities but can assist law enforcement agencies. The CF support can never be greater than the authority of the requesting law enforcement groups to conduct law enforcement activities themselves (see references at paragraph 1.k(2)).
(b) Peace Officer Status for CF. Peace Officers are public authorities responsible to maintain the public peace and enforce the law. CF personnel employed on an operation may have Peace Officer status if it would be appropriate for them to perform law enforcement duties but only when so employed, IAW QR&O 22.01. Peace Officer status ceases when CF personnel are no longer performing assistance to law enforcement duties. CF personnel with Peace Officer status have all the powers and protections of Peace Officers as set out in the Criminal Code and the special protection from civil and criminal liability enjoyed by Peace Officers. CF members without Peace Officer status have no more authority over the civilian population than they would otherwise have when performing their normal day-to-day duties. Specifically, CF personnel without Peace Officers status do not have the enhanced powers of arrest, detention, investigation, or traffic control enjoyed by Peace Officers. A legal advisor should be consulted to know whether CF personnel have peace officer status and when.…
u. Intelligence oversight – Information and Intelligence Collection and Sharing
(1) United States.
(a) References at paragraph 1.n(1) apply to USNORTHCOM operations. The USNORTHCOM SJA shall provide legal review and oversight of intelligence activities as required.
(b) Information and intelligence collection and sharing may be possible for domestic operations. Ops must be based on appropriate legal authority. Specific legal advice should be sought on a case-by-case basis for matters of this nature. In general, the CF may collect and share defence intelligence pursuant to the National Defence Act and the CF’s defence of Canada mandate, in accordance with existing intelligence programs and legal authorities. The collection, production, and dissemination of security intelligence shall be performed primarily by CFNCIU in accordance with Reference J.(2) Canada.
(a) While acting in support of a law enforcement agency for an operation, the CF is permitted to assist this agency in collecting information, pursuant to the mandate and lawful authority of that agency to do so. The law enforcement agency remains responsible to obtain any required judicial authorizations and to ensure that any CF assistance to act upon such authorizations is sought in strict accordance with the terms and limitations of those authorizations.
(b) Subject to any specific arrangement or agreement, the CF may share with a law enforcement agency classified information and intelligence in accordance with Reference K, under limited circumstances. Questions on intelligence sharing should be directed to the CF functional authority, the Chief of Defence Intelligence.
SECRECY NEWS – PENTAGON MANUAL URGES PRECISION IN CLASSIFYING INFORMATION
The Department of Defense is not particularly concerned with "openness" in
the abstract, but it is strongly motivated to conserve resources and reduce
discretionary expenditures. That imperative dictates the discriminating
use of national security secrecy -- at least in theory -- because of the
costs incurred by classification.
"Precise classification guidance is prerequisite to effective and
efficient information security and assures that security resources are
expended to protect only that which truly warrants protection in the
interests of national security," according to a newly reissued Department
of Defense manual that provides "Instructions for Developing Security
Classification Guides" (DoD Manual 5200.45, April 2, 2013).
http://www.fas.org/sgp/othergov/dod/m5200_45.pdf
The Manual presents a framework for classifying information, beginning
with a series of questions for determining whether information is eligible
for classification in the first place. ("Can the unauthorized disclosure
of the information reasonably be expected to cause identifiable or
describable damage to the national security? If the answer is no, the
information cannot be classified.")
Then it details the considerations that may arise in the classification of
information concerning military hardware, military operations, intelligence
and foreign relations. Exactly which aspects of a hardware system provide
the U.S. with a technological advantage? Precisely which operational
information requires protection in order for the operation to succeed?
The Manual discourages broad, sweeping classification of information.
Through an extended questionnaire for classifiers, it seeks "to
systematically bound and refine the scope of the analysis needed to
determine which items warrant protection through security classification."
As detailed and helpful as this guidance is, it cannot decisively resolve
all classification questions in advance. "The outcomes specified in the
flow chart are not absolute; judgment must be applied in all cases," the
Manual says.
Some decisions regarding what to classify are easy. Information about "a
foreign official speaking in a highly critical manner of his own
government's policy" or "suggesting how pressure might effectively be
brought to bear on another part of his own government" would typically be
classified. Likewise, the fact of ongoing intelligence cooperation between
the United States and a country "with which the United States is not allied
should always be classified." Also, "intelligence identifying a sensitive
source or method should always be classified."
On the other hand, the Manual says, classification can be dispensed with
in certain areas. "Intelligence that reveals the identity of a
conventional source or method [i.e., one that is not "sensitive"] normally
does not require classification."
And "in general, [intelligence budget] resource information should not be
classified unless it reveals some aspect of the intelligence mission, and
its revelation would jeopardize the effectiveness of a particular function.
An example of classifiable resource information is the intelligence
contingency fund."
At this point, the realization will dawn on some readers that this Manual,
which was originally issued in 1999, does not accurately describe -- or
effectively regulate -- DoD classification policy.
It is simply not the case that "in general, resource information [is] not
classified unless it reveals some aspect of the intelligence mission." To
the contrary, the Department's default position is that intelligence
resource information is classified. That is why the individual budget
total of each DoD intelligence agency -- and not simply intelligence
contingency funds -- is not disclosed. And beyond the total budget for the
Military Intelligence Program (MIP), "no other MIP budget figures... will
be released," DoD said last October 30, "as they remain classified for
national security reasons."
Nor does the Pentagon clearly distinguish between sensitive intelligence
sources and methods, which are classified, and "conventional" intelligence
sources and methods, which are not. Doing so sounds like a good idea, but
it is hard to detect any sign of it in Pentagon practice.
The Manual notes that all classification guidance should be reviewed at
least every five years by the original classification authority that issued
it. But it fails to mention that all guidance is also subject to a broader
periodic assessment known as the Fundamental Classification Guidance
Review. It is through such a broader review that changes in classification
policy are more likely to come about.
PROSECUTORS REBUT DEFENDANT'S CHALLENGE TO ESPIONAGE ACT STATUTE
Last month, attorneys for Navy linguist James Hitselberger, who was
charged under the Espionage Act with unlawful retention of classified
documents, filed a motion arguing that the Espionage Act is
unconstitutionally vague and unenforceable. Last week, prosecutors replied
and said that's not so.
"Prosecuting Mr. Hitselberger under this statute violates the fair notice
requirements of the Due Process clause because multiple terms contained in
[the statute] are so vague that they fail to provide him with notice of
what conduct is criminal and what conduct is not," Hitselberger's public
defenders wrote in their March 1 motion.
http://www.fas.org/sgp/jud/hitsel/030113-vague.pdf
Last Friday, prosecutors rebutted the defense motion, which they said was
without merit. "Every court that has considered similar challenges to [the
Espionage Act statutes] has rejected them and found the provisions to pass
constitutional muster," they wrote.
http://www.fas.org/sgp/jud/hitsel/040513-govopp.pdf
The prosecutors cited rulings from past and present prosecutions involving
charges under the espionage statutes to bolster their argument --
including those of State Department contractor Stephen Kim, former NSA
official Thomas Drake, former CIA officer John Kiriakou, and former naval
intelligence analyst Samuel L. Morison. Like Hitselberger, none of those
individuals was accused or suspected of espionage on behalf of a foreign
power, but rather of unlawfully retaining or disclosing national defense
information.
"Recently, the defendant in Drake made the same faulty argument as
Hitselberger makes here," prosecutors wrote. "The district court rejected
the defendant's claim that the term willfulness is unconstitutionally
vague."
"Although Hitselberger admittedly was not a career intelligence
professional, he has more in common with defendants such as Morison,
Kiriakou, and Kim than he lets on," the prosecutors asserted. It was not
meant as a compliment.
Prosecutors filed additional responses to several other pre-trial defense
motions to suppress evidence, to require a bill of particulars, to
eliminate "multiplicious" charges, and to find sections of the Classified
Information Procedures Act unconstitutional.
http://www.fas.org/sgp/jud/hitsel/index.html
NORTH KOREAN NUKES, DOMESTIC DRONES, AND MORE FROM CRS
An updated summary of open source reporting on the North Korean nuclear
weapons program was produced this week by the Congressional Research
Service. See North Korea's Nuclear Weapons: Technical Issues, April 3,
2013:
http://www.fas.org/sgp/crs/nuke/RL34256.pdf
Other new or newly updated CRS reports include the following.
Integration of Drones into Domestic Airspace: Selected Legal Issues, April
4, 2013:
http://www.fas.org/sgp/crs/natsec/R42940.pdf
Drones in Domestic Surveillance Operations: Fourth Amendment Implications
and Legislative Responses, April 3, 2013:
http://www.fas.org/sgp/crs/natsec/R42701.pdf
Super PACs in Federal Elections: Overview and Issues for Congress, April
4, 2013:
http://www.fas.org/sgp/crs/misc/R42042.pdf
"Amazon" Laws and Taxation of Internet Sales: Constitutional Analysis,
April 3, 2013:
http://www.fas.org/sgp/crs/misc/R42629.pdf
FutureGen: A Brief History and Issues for Congress, April 3, 2013:
http://www.fas.org/sgp/crs/misc/R43028.pdf
Congressional Redistricting and the Voting Rights Act: A Legal Overview,
April 2, 2013:
http://www.fas.org/sgp/crs/misc/R42482.pdf
The Temporary Assistance for Needy Families (TANF) Block Grant: A Primer
on TANF Financing and Federal Requirements, April 2, 2013:
http://www.fas.org/sgp/crs/misc/RL32748.pdf
The Recess Appointment Power After Noel Canning v. NLRB: Constitutional
Implications, March 27, 2013:
http://www.fas.org/sgp/crs/misc/R43030.pdf
Overview of Health Care Changes in the FY2014 Budget Proposal Offered by
House Budget Committee Chairman Ryan, March 22, 2013:
http://www.fas.org/sgp/crs/misc/R43017.pdf
Cuba: U.S. Policy and Issues for the 113th Congress, March 29, 2013:
http://www.fas.org/sgp/crs/row/R43024.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Die Rechtslage bei schweren Internet-Angriffen wie von mutmasslich “GoMoPa”, “Nawito” und Konsorten
Zitat:
Nachfolgend einige Links zu dem brisanten Thema, den wenn mutmasslich “GoMoPa”, “Nawito”, Sven Schmidt, “Eagle IT” und dubioser “CTO” der dubiosen “GoMoPa” sowie sein mutmasslicher Genosse Thomas Promny und Genossen unsere starken Server ungestraft attackieren können, kann bald jedes Unternehmen ähnliche Probleme haben wie wir:
http://de.wikipedia.org/wiki/Denial_of_Service
All das zeigt, welche Kriminellen hier in STASI-Manier am Werk sind:
Sie haben Angst vor der Wahrheit und können sich nur durch kriminelle Aktionen halten….
Even More Mental and Pysical Attacks on our Servers by the Suspects of “GoMoPa”, “Nawito”, “Otmar Knoll” and “Peter Ehlers”
Dear Readers,
here is the proof for that our websites and the are constantly under attack – mental and pysical attacks by
– “GoMoPa”
– “Peter Ehlers”
– “Klaus Maurischat”
– “Nawito”
– Otmar Knoll” – he announced himself the attacks in an official corporate Email of his company “Fairvesta”!!!!
and their thugs:
This is in fact a very serious crime and causes longterm jail sentences !
Krumme Immobiliengeschäfte ? Wie “Otmar Knoll”, “Fairvesta” zusammnen mit “GoMoPa” kritische Webseiten illegal ausschaltet
Zitat OtmarKnoll/Fairvesta:
|
||||||||||||
|
TOP-SECRET – Oregon Fukushima Radiation Event After Action Report

Oregon Health Authority and Public Health Division
- 45 pages
- For Official Use Only
- June 30, 2011
A 9.0 earthquake occurred at 14:46 local (Japan) time [05:46 hours GMT1 on Friday, March 11 off of the NE coast of Japan. This equates to 21:46 hours Pacific Time on Thursday. March 10. The resulting tsunami (along with earthquake damage) devastated the NE Japan coastline, sent a tsunami across the Pacific and caused severe damage to the nuclear reactors at the Fukushinia Daiichi Nuclear Plant. 127 miles NP of’ Tokyo. The tsunami alert by the Pacific Tsunami Warning Center resulted in evacuation orders being issued for coastal Oregon communities, with the only significant tsunami damage in Oregon occurring in Curry County at Brookings. Once it became clear that the tsunami would not have widespread impact in Oregon, the next issue of concern was the potential impact in Oregon of the radiation release from the damaged nuclear reactors. A determination was made between Oregon Emergency Management and state Public Health that Public Health would take the lead in addressing public concerns about radiation and OEM would assume the lead in the Tsunami response and recovery effort.
The Public Health Duty Officer was initially notified of the Earthquake & Tsunami at 0300, Friday 11 March, Oregon Public health Division (OPHD) leadership considered the appropriate roles and response for the agency during the day, with Dr. Mel Kohn, State Public Health Director, issuing his first public statement on the health implications for Oregonians from the radiation release in Japan on Saturday 12 March. The Office of Environmental Public Health and its Radiation Protection Services (RPS) initially assumed the lead in response efforts to the event. It soon became clear that the complexity of the response (communications with the public, communications and coordination with intra and inter-state partners and working with Federal agencies), required a more robust response. A modified Incident Management Team (IMT) was subsequently formed on 16 March and a limited Agency Operations Center (AOC) activation occurred on Monday, 21 March.
…
The Oregon response to the Japan Radiation Event was a real-time response triggered by the Tohuku Earthquake and Tsunami of March 11, 2011. Damage caused by the tsunami to the Oregon coast did not necessitate a state Public Health response. Rather, state PH focused primarily on the health and medical informational needs of the public, public health and medical partners and other state agencies and tribes.
OPHD initially responded in an ad hoc manner. It was subsequently determined that a more effective approach would be to establish an Incident Management Team and activate the Agency Operations Center, which were accomplished on 16 March and 21 March respectively.
Agency Operations Center and Public Health Information Center operations worked well, with enhanced cooperation demonstrated in message development and interaction with the media. Use of HAN, links on the OHA website to FAQs and statistical data, rapid translation of messages into 6 languages, teleconferences with LHDs, tribes, PIOs and Region X Federal and state partners and Oregon Emergency Management facilitated calls with sister state agencies resulted in consistent information being provided. The major deficiency in the process was the lack of clarity and responsiveness from the national headquarters of federal agencies (EPA, FDA).
‘Though circumstantial (LHDs and other state partners were surveyed, not the general public) SurveyMonkey results suggest that the state’s Japan Radiation Event responsive was effective in providing the necessary information to both inform and calm the public’s concerns.
Video Skid – Monty Python-Witch Scene
AN OVERVIEW OF THE HEAVY CYBERATTACKS ON OUR WEBSITES TO STOP THE TRUTH DONE BY THE SUSPECTS
These graphs below show the cyberattacks on our website initiated by the suspects we already mentioned and who even announced in an email that tehy would do this illegal internet crime. The email was by Otmar Knoll, Fairvesta, who announced the cybercrime. The suspected hackers are from “GoMoPa” and their thugs.
The graphs show the DDos attacks on our servers.
What is a DDos attack ?
Read here:
http://en.wikipedia.org/wiki/Denial-of-service_attack
These internet crimes are punished with longterm jail sentences and financial compensation..
Die untenstehenden Graphiken zeigen die Hackernagriffe auf unsere Webseiten, die seit Jahren durchgeführt werden im Ausschnitt. In einer Email an uns hat Otmar Knoll, Fairvesta, die Hackerangriffe, somit schwere Internetverbrechen angekündigt. Wir haben diese Emails bereits veröffentlicht. Mutmasslich arbeitet Otmar Knoll mit den üblichen Verdächtigen der “GoMoPa”, ihren Informanten und Hackern zusammen:
Die Graphiken zeigen die sogenannten DDos-Angriffe auf unsere Server.
Was ist eine DDos Attacke ?
http://de.wikipedia.org/wiki/Denial_of_Service
Lesen Sie hier:
Diese Vergehen werden mit langjährigen Freiheitsstrafen und Schadensersatz bestraft.
TOP-SECRET – DHS-FBI Terrorist Tradecraft: Impersonation Using Stolen, Cloned or Repurposed Vehicles

Fire Line Terrorist Tradecraft—Impersonation: Use of Stolen, Cloned, or Repurposed Vehicles
- 1 page
- For Official Use Only
- January 18, 2013
(U//FOUO) Stolen, cloned, or repurposed commercial or official vehicles—such as police cars, ambulances, and public utility service trucks—have been used in terrorist attacks. These vehicles could facilitate terrorist access to restricted and hardened targets as well as to emergency scenes. The use of these vehicles can provide individuals the ability to approach targets to conduct pre-operational surveillance or carry out primary attacks or secondary attacks against first responders.
— (U) In January 2013, a stolen ambulance was used as a vehicle-borne improvised explosive device (VBIED) as part of a secondary attack on a billiards hall in Quetta, Pakistan.
— (U//FOUO) Cloned vehicles are those that have been modified to resemble an authentic vehicle. In January 2010, coordinated attacks in downtown Kabul, Afghanistan included a vehicle-borne improvised explosive device van cloned as an ambulance.
— (U//FOUO) Repurposed vehicles are authentic vehicles that are no longer in official service; they often can be purchased at auctions or on the Internet. In August 2012, assailants detonated a possibly repurposed taxi cab VBIED targeting a funeral procession in Damascus, Syria.(U//FOUO) Mitigating the risk:
— (U//FOUO) Secure station or facility entrance and exit points, including apparatus bay doors.
— (U//FOUO) Limit or lock unattended emergency vehicles.
— (U//FOUO) Establish a policy for decommissioning vehicles.
— (U//FOUO) Stay current on the “branding” of vehicles used by neighboring jurisdictions and mutual aid companies.
— (U//FOUO) Consider using holograms on emergency vehicles for authentication.
— (U//FOUO) Establish a stolen vehicle reporting process that includes “be on the lookout” warnings for high interest vehicles.(U//FOUO) Possible indicators:
— (U//FOUO) Improperly marked emergency vehicles.
— (U//FOUO) Driver of emergency vehicle not knowledgeable about area of responsibility or service.
— (U//FOUO) Incorrect vehicle decal verbiage, colors, word font, and size.
— (U//FOUO) Visible identifiers—such as phone numbers, license plates, or call numbers—that are inconsistent with the vehicle’s operating area or mission.
— (U//FOUO) Heavily loaded vehicle, possibly beyond capacity.(U) Report Suspicious Activity
(U) To report suspicious activity, law enforcement, Fire-EMS, private security personnel, and emergency managers should follow established protocols; all other personnel should call 911 or contact local law enforcement. Suspicious activity reports (SARs) will be forwarded to the appropriate fusion center and FBI Joint Terrorism Task Force for further action. For more information on the Nationwide SAR Initiative, visit http://nsi.ncirc.gov/resources.aspx.
SECRECY NEWS – DEFENSE DOCTRINE OFFERS INSIGHT INTO MILITARY OPERATIONS
"Reconnaissance assets, like artillery assets, are never kept in reserve,"
according to U.S. Army doctrine.
In other words, whatever means you may have to gather information about
the activities and capabilities of an adversary should be fully deployed,
not held back.
"Reconnaissance units report exactly what they see and, if appropriate,
what they do not see.... Reports of no enemy activity are as important as
reports of enemy activity. Failing to report tells the commander nothing."
That bit of practical wisdom, which may indeed be relevant beyond the
battlefield, is contained in a new Army field manual on the subject. See
"Reconnaissance, Security, and Tactical Enabling Tasks," Volume 2, Field
Manual 3-90.2, March 2013:
http://www.fas.org/irp/doddir/army/fm3-90-2.pdf
It is a companion to "Offense and Defense," Volume 1, Field Manual 3-90.1,
March 2013:
http://www.fas.org/irp/doddir/army/fm3-90-1.pdf
The vast corpus of U.S. military doctrine offers a point of entry into
military thought that may be of interest even -- or especially -- to a
reader who is not a member of "the profession of arms." Some noteworthy
doctrinal publications that have recently been published or updated are
cited below. While they have a tendency to be jargon heavy and pedestrian,
they are never frivolous or less than professional. Occasionally they offer
impressive subtlety and sophistication or unexpected literary merit.
The distinctive vocabulary of military affairs is presented with
authoritative definitions in a 500-page "Department of Defense Dictionary
of Military and Associated Terms," Joint Publication 1-02, updated March
15, 2013:
http://www.fas.org/irp/doddir/dod/jp1_02.pdf
The conceptual framework of the U.S. military is outlined in Joint
Publication 1, "Doctrine for the Armed Forces of the United States,"
reissued on March 25. It "provides overarching guidance and fundamental
principles" for the employment of the U.S. military. "War is socially
sanctioned violence to achieve a political purpose," it explains. "The
basic nature of war is immutable, although warfare evolves constantly."
http://www.fas.org/irp/doddir/dod/jp1.pdf
The various functions of the military in humanitarian assistance are
elaborated in "Multi-Service Techniques for Civil Affairs Support to
Foreign Humanitarian Assistance," ATP 3-57.20, February 2013:
http://www.fas.org/irp/doddir/army/atp3-57-20.pdf
A reference guide for initial assessment and response to an accidental or
deliberate release of biological pathogens, radioactive material or other
hazardous substances is given in "Multi-Service Tactics, Techniques, and
Procedures for Chemical, Biological, Radiological, and Nuclear
Reconnaissance and Surveillance," ATP 3-11.37, March 2013:
http://www.fas.org/irp/doddir/army/atp3-11-37.pdf
The potential use of biological agents in war and the diagnosis and
treatment of the resulting casualties are described in "Multi-Service
Tactics, Techniques and Procedures for Treatment of Biological Warfare
Casualties," ATP 4-02.84, March 2013:
http://www.fas.org/irp/doddir/army/atp4-02-84.pdf
The intersection of law and Army operations is delineated in "Legal
Support to the Operational Army," Field Manual 1-04, updated March 2013:
http://www.fas.org/irp/doddir/army/fm1-04.pdf
SENATE REPUBS LEAD CONGRESSIONAL USE OF TWITTER, CRS SAYS
Senate Republicans are the most prolific users of Twitter in Congress,
tweeting an average of 1.53 Tweets per day, according to a new report from
the Congressional Research Service. They were followed by Senate Democrats
(1.49 Tweets on average), House Republicans (1.23), and House Democrats
(1.09).
Senate Republicans were also the most frequent posters on Facebook, with
an average of 0.84 posts per day.
"In 2012, 56% of Twitter-registered Members were Republican and 44% were
Democrats," reported the CRS study, which was performed with the LBJ School
of Public Affairs at the University of Texas in Austin.
Twitter and Facebook "allow Members to communicate directly with
constituents (and others) in a potentially interactive way that is not
possible through mail or e-mail. For Members and their staff, the ability
to collect and transmit real time information to and from constituents
could be influential for issue prioritization, policy decisions, or voting
behavior," CRS said.
However, the new study does not present any data to show that Twitter or
Facebook are actually being used interactively, i.e. that Members are
consistently reading or responding to incoming messages from constituents
or others. See "Social Networking and Constituent Communications: Members'
Use of Twitter and Facebook During a Two-Month Period in the 112th
Congress," March 22, 2013:
http://www.fas.org/sgp/crs/misc/R43018.pdf
Some other new reports from the Congressional Research Service include the
following.
Argentina's Post-Crisis Economic Reform: Challenges for U.S. Policy, March
26, 2013:
http://www.fas.org/sgp/crs/row/R43022.pdf
Proposed Cuts to Air Traffic Control Towers Under Budget Sequestration:
Background and Considerations for Congress, March 26, 2013:
http://www.fas.org/sgp/crs/misc/R43021.pdf
Administrative Agencies and Claims of Unreasonable Delay: Analysis of
Court Treatment, March 21, 2013:
http://www.fas.org/sgp/crs/misc/R43013.pdf
U.S. and World Coal Production, Federal Taxes, and Incentives, March 14,
2013:
http://www.fas.org/sgp/crs/misc/R43011.pdf
_______________________________________________
Secrecy News is written by Steven Aftergood and published by the
Federation of American Scientists.
The Secrecy News Blog is at:
http://www.fas.org/blog/secrecy/
To SUBSCRIBE to Secrecy News, go to:
http://www.fas.org/sgp/news/secrecy/subscribe.html
To UNSUBSCRIBE, go to
http://www.fas.org/sgp/news/secrecy/unsubscribe.html
OR email your request to saftergood@fas.org
Secrecy News is archived at:
http://www.fas.org/sgp/news/secrecy/index.html
Support the FAS Project on Government Secrecy with a donation:
http://www.fas.org/member/donate_today.html
_______________________
Steven Aftergood
Project on Government Secrecy
Federation of American Scientists
web: www.fas.org/sgp/index.html
email: saftergood@fas.org
voice: (202) 454-4691
twitter: @saftergood
Video Skid – Monty Python – Exploding Penguin
Statement about the dubious “colportations” of “Nawito” – MENTAL AND PHYSICAL CYBERATTACKS
Dear Readers,
let me just briefly comment a mental cyberattack which should distract your attention from the real issues.
I have never had any consulting position or contract for any German company.
I have never worked for the Axel Springer Publishing House – not even as a freelance journalist.
These facts are clear and can be verified easily – just by calling Axel Springer.
The facts are
1) Dr. Rainer Zitelmann worked for the Axel Springer Company. You can esaily find out what happened there. I just mention the word “Auschwitz” in this context…As you see from his website and in the internet Zitelmann is in fact consulting many German companies.
2) “GoMoPa” had in fact a consultation contract with estavis and got in fact money from estavis and many various companies i.e. “S&K”
These contracts are known and 100% true and published by various media i.e. “ZEIT”, “MANAGER MAGAZIN”, “SUEDDEUTSCHE ZEITUNG” etc.
3) Meridian Capital was the subject of “GoMoPa”s articles.
4) “Nawito” whover or whatever it is did not even bother to contact us.
5) The “information” about one of our companies is false.
6) The “Nawito” informer “Peter Ehlers” did in fact attack Chancellor Merkel and the Minister of Finance Wolfgang Schäuble as “Deutschlands bekannteste Hehler” to name just one fact about “Peter Ehlers” or whatever his name might be who by the way got a lot of money from the bancrupt SAM AG which was also subject of “GoMoPa”‘s reporting and we know similiar cases of this endeavour.
7) The last editor who was attacked by such cyberattacks died in a very mysterious way, Heinz Gerlach. He might have been controversial but nevertheless – the truth is the truth.
He was the first journalist to publish the truth about the mysterious headquarter of “GoMoPa” in New York and their consulting contract with estavis and died suddenly and totally unexpected for most of us – not for all.
The circumstances of his death remain unsolved for me.
We are ready to proof this everytime and do not work with “colportations”.
Obviously cyberattacks on our websites since years are not enough to keep the truth down – defamation must be added – a wellknown STASI technique to irritate the public – MENTAL AND PYSICAL CYBERATTACKS done by the well-know suspects.
Sincerely your
Bernd Pulch
Magister Artium der Publizistik, Germanistik und Komparatistik
PS
COPIES OF PHYSICAL CYBER ATTACKS ON OUR SERVERS BY THE SUSPECTS AND “INFORMERS” OF “NAWITO”
The attacked website are for example:
http://www.investment-magazin.tv
and about 20 more.
The Best Proof for the Truth we are telling – Cyberattacks everyday by the Suspects
One day after The New York Times reported that Chinese hackers had infiltrated its computers and stolen passwords for its employees, The Wall Street Journal announced that it too had been hacked.
Related
-
Hackers in China Attacked The Times for Last 4 Months(January 31, 2013)
On Thursday, The Journal reported that it had been attacked by Chinese hackers who were trying to monitor the company’s coverage of China. It said hackers had broken into its network through computers in its Beijing bureau.
In a written statement, the business newspaper owned by News Corporation described the attack as an “ongoing issue” and said it was working closely with authorities and security specialists to clean up its systems. It said that it completed a “network overhaul” on Thursday in an effort to rid its systems of hackers.
China’s Ministry of National Defense has denied any involvement in the cyberattack at The Times or any other American corporations.
But security experts said that in 2008, Chinese hackers began targeting American news organizations as part of an effort to monitor coverage of Chinese issues.
In a report for clients in December, Mandiant, a computer security company, said that over the course of several investigations it found evidence that Chinese hackers had stolen e-mails, contacts and files from more than 30 journalists and executives at Western news organizations, and had maintained a “short list” of journalists for repeated attacks. Among those targeted were journalists who had written about Chinese leaders, political and legal issues in China and the telecom giant Huawei.
Bloomberg News, another American news organization, was targeted by Chinese hackers last year, and some computers were infected, according to a person with knowledge of the company’s internal investigation. The attack occurred after Bloomberg published an article on June 29 about the wealth accumulated by relatives of Xi Jinping, a Chinese official who is expected to become president in March.
Bloomberg has confirmed that hackers had made attempts but said that “no computer systems or computers were compromised.”
The timing of the attacks on The New York Times coincided with the reporting for an investigation, published online on Oct. 25, that found that the relatives of Wen Jiabao,China’s prime minister, had accumulated a fortune worth several billion dollars through business dealings.
Security experts hired by The Times to detect and block the computer attacks found digital evidence that Chinese hackers, using methods that some consultants have associated with the Chinese military in the past, breached The Times’s network.
The Associated Press reported Thursday that officials in the Obama administration were considering more assertive action against Beijing to stop Chinese computer espionage campaigns.
The Secretary of State, Hillary Clinton, said Thursday a global effort was needed o establish “rules of the road” for cyber activity. In her final meeting with reporters at the State Department, Mrs. Clinton addressed a question about China’s efforts to infiltrate computer systems at The New York Times.
“We have seen over the last years an increase in not only the hacking attempts on government institutions but also non-governmental ones,” Mrs. Clinton said.
The Chinese, she said, “are not the only people who are hacking us.”
“There is a lot that we are working on that will be deployed in the event that we don’t get some kind of international effort under way,” Mrs. Clinton added without elaborating.
The United States has been increasingly vocal about such efforts against government and private industry. In a November 2011 intelligence report, government officials specifically accused China and Russia of stealing intellectual property for economic gain.
<nyt_author_id>
Michael Gordon contributed reporting from Washington.
So this is a part of the big picture: The small picture concerns former STASI agents and their comrades and thugs in Germany.
The Best Proof for the Truth we are telling – Cyberattacks everyday by the Suspects against our websites !
Video Skid – Monty Python – Mr. Hilter
from Monty Python’s Flying Circus
Season 1 – Episode 12
The Naked Ant
Recorded 21-12-69, Aired 04-01-70
It starts with Visitors from Coventry then proceeds to show Mr. Hilter and the Minehead by-election…
*Also known as Hitler in England
SECRET – Michael Steinberg Allegedly Earned $1.4 Million in Illegal Profits
Preet Bharara, the United States Attorney for the Southern District of New York, and George Venizelos, the Assistant Director in Charge of the New York Field Office of the Federal Bureau of Investigation (FBI), today announced conspiracy and securities fraud charges against Michael Steinberg, a portfolio manager at a hedge fund located in New York, New York (“Hedge Fund A”), for his alleged involvement in an insider trading scheme. As alleged, Steinberg executed trades based on material, non-public information (“inside information”) provided to him by a Hedge Fund A analyst who worked for him—John Horvath, who previously pled guilty to securities fraud charges pursuant to a cooperation agreement. In particular, Steinberg is alleged to have traded in two publicly traded technology companies, Dell Inc. (“Dell”) and NVIDIA Corporation (“NVIDIA”), based on inside information that Horvath obtained from a circle of research analysts at several different investment firms, all of whom have also pled guilty for their roles in the scheme. Those individuals are: Jesse Tortora, a former research analyst at Diamondback; Spyridon “Sam” Adondakis, a former research analyst at Level Global; Danny Kuo, a former research analyst and fund manager at Whittier Trust Company; and Sandeep “Sandy” Goyal, a former research analyst who worked at the Manhattan office of Neuberger Berman. Steinberg’s trading in Dell and NVIDIA earned Hedge Fund A $1.4 million in illegal profits. Steinberg was arrested this morning in Manhattan and will be presented and arraigned in Manhattan federal court before U.S. District Judge Richard J. Sullivan at 11:00 a.m.
Manhattan U.S. Attorney Preet Bharara said, “As alleged, Michael Steinberg was another Wall Street insider who fed off a corrupt grapevine of proprietary and confidential information cultivated by other professionals who made their own rules to make money. With lightning speed in at least one case, Mr. Steinberg seized on the opportunity to cash in and tried to keep his crime quiet, as charged in the Indictment. As alleged, where once Mr. Steinberg answered only to his own rules, now he will have to answer to the rule of law, like so many others before him.”
FBI Assistant Director in Charge George Venizelos said, “Mr. Steinberg’s arrest is the latest in the FBI’s campaign to root out insider trading at hedge funds and expert networking firms, resulting in more than 70 arrests so far. As alleged, Mr. Steinberg was at the center of an elite criminal club, where cheating and corruption were rewarded. Research was nothing more than well-timed tips from an extensive network of well-sourced analysts. The law is clear for everyone, including Mr. Steinberg. Trading on inside information is illegal. The FBI will continue to police our markets and arrest anyone who violates the law.”
In a separate action, the U.S. Securities and Exchange Commission announced civil charges against Steinberg.
According to the allegations in the superseding indictment, other court documents, and evidence adduced at a related trial:
A group of analysts at different hedge funds, including Tortora, Adondakis, Horvath, and Kuo, obtained inside information directly or indirectly from employees who worked at certain public companies and then shared the information with each other and with the hedge fund portfolio managers for whom they worked, including Steinberg. In particular, Tortora provided Horvath and others with inside information related to Dell’s quarterly earnings (the “Dell inside information”), which Tortora obtained from Goyal who, in turn, had obtained the Information from an employee at Dell (the “Dell insider”). For Dell’s quarter ending August 1, 2008, the results for which were publicly announced by Dell on August 28, 2008 (the “Dell Announcement”), the Dell inside information indicated that Dell would report gross margins that were materially lower than market expectations. In advance of the Dell Announcement, Horvath reported this negative inside information to Steinberg.
On August 18, 2008, after a series of calls from the Dell Insider to Goyal and from Goyal to Tortora and Horvath, Horvath then called Steinberg. Within a minute of the telephone call between Steinberg and Horvath, Steinberg’s portfolio began shorting shares of Dell. One minute later, Horvath wrote an e-mail to Steinberg stating: “Pls keep the DELL stuff especially on the down low…just mentioning that because JT [Jesse Tortora] asked me specifically to be extra sensitive with the info.” By the end of the day on August 18, 2008, Steinberg had accumulated a net short position of over 167,000 shares of Dell. On August 26, 2008, Horvath confirmed in an e-mail to Steinberg and another portfolio manager at Hedge Fund A that Horvath’s Dell information had been based on a “2nd hand read from someone at the company.” Steinberg responded, “Yes normally we would never divulge data like this, so please be discreet.” And on August 27, 2008, Steinberg sent an e-mail to Horvath with the subject line, “Dell action,” in which he asked, “Have u double checked [with] JT this week?” Horvath responded, “Yes he [Tortora] checked in [a] couple days ago, same read no change.”
On August 28, 2008, before Dell’s Announcement, Steinberg executed or caused to be executed additional short trades. Steinberg also executed or caused to be executed options trades in Dell in advance of the Dell Announcement.
After the close of the market on August 28, 2008, Dell publicly announced gross margins that were substantially below market expectations. At the end of the next trading day following Dell’s Announcement, its stock price dropped by more than 13 percent. Shortly thereafter, Steinberg covered his short position and closed out his position in Dell option contracts, resulting in an illegal profit for Hedge Fund A of approximately $1 million.
In addition, in 2009, Kuo obtained inside information regarding NVIDIA’s financial results (the “NVIDIA inside information”) in advance of NVIDIA’s quarterly earnings announcements. The NVIDIA inside information indicated, among other things, that NVIDIA’s gross margins would be lower than market expectations. Kuo obtained the NVIDIA inside information from a friend, Hyung Lim (“Lim”), who received it from an employee at NVIDIA (the “NVIDIA insider”). In advance of NVIDIA’s May 7, 2009 quarterly earnings announcement (the “NVIDIA announcement”), Kuo provided the NVIDIA inside information, which he had obtained from Lim, to Tortora, Horvath, and others. Horvath, in turn, provided the NVIDIA inside information to Steinberg, who executed or caused to be executed transactions in NVIDIA in advance of the NVIDIA Announcement.
On May 7, 2009, NVIDIA publicly announced gross margins that were substantially lower than the market expected. At the end of the trading day following the NVIDIA announcement, NVIDIA’s stock price dropped by more than 13 percent. Shortly thereafter, Steinberg caused Hedge Fund A to liquidate its position in NVIDIA, resulting in an illegal profit for Hedge Fund A of over $400,000.
* * *
Steinberg, 41, of New York, New York, is charged with one count of conspiracy to commit securities fraud and four counts of securities fraud. The conspiracy count carries a maximum sentence of five years in prison and a fine of the greater of $250,000 or twice the gross gain or loss from the offense. Each of the securities fraud counts carries a maximum sentence of 20 years in prison and a fine of $5 million or twice the gross gain or loss from the offense.
The allegations in the indictment against Steinberg are merely accusations, and he is presumed innocent unless and until proven guilty.
Horvath, 43, and Kuo, 37, each pled guilty to one count of conspiracy to commit securities fraud and two substantive counts of securities fraud in September 2012 and April 2012, respectively.
Tortora, 35, Adondakis, 41, and Goyal, 40, each pled guilty to one count of conspiracy to commit securities fraud and one substantive count of securities fraud in May 2011, April 2011, and June 2011, respectively.
Mr. Bharara praised the investigative work of the FBI. He also thanked SEC. Mr. Bharara noted that the investigation is continuing.
This case was brought in coordination with President Barack Obama’s Financial Fraud Enforcement Task Force, on which Mr. Bharara serves as a Co-Chair of the Securities and Commodities Fraud Working Group. The task force was established to wage an aggressive, coordinated, and proactive effort to investigate and prosecute financial crimes. With more than 20 federal agencies, 94 U.S. attorneys’ offices, and state and local partners, it is the broadest coalition of law enforcement, investigatory, and regulatory agencies ever assembled to combat fraud. Since its formation, the task force has made great strides in facilitating increased investigation and prosecution of financial crimes; enhancing coordination and cooperation among federal, state, and local authorities; addressing discrimination in the lending and financial markets; and conducting outreach to the public, victims, financial institutions and other organizations. Over the past three fiscal years, the Justice Department has filed nearly 10,000 financial fraud cases against nearly 15,000 defendants including more than 2,900 mortgage fraud defendants. For more information on the task force, please visit http://www.stopfraud.gov.
This case is being handled by the Office’s Securities and Commodities Fraud Task Force. Assistant U.S. Attorneys Antonia M. Apps and John T. Zach are in charge of the prosecution.
TMZ – Paris Hilton — I Would NEVER Kidnap Kim Kardashian … We’re Friends!
Paris Hilton is no Kardashian abductor … in fact, she tells TMZ the leaked Ford print ad that shows her kidnapping Kim’s family is “stupid” ’cause they’re still good friends.
Public Intelligence unveils CIA Collections of 805,929 Declassified Docs
Monty Python – Galaxy Song
Monty Python’s Meaning of Life


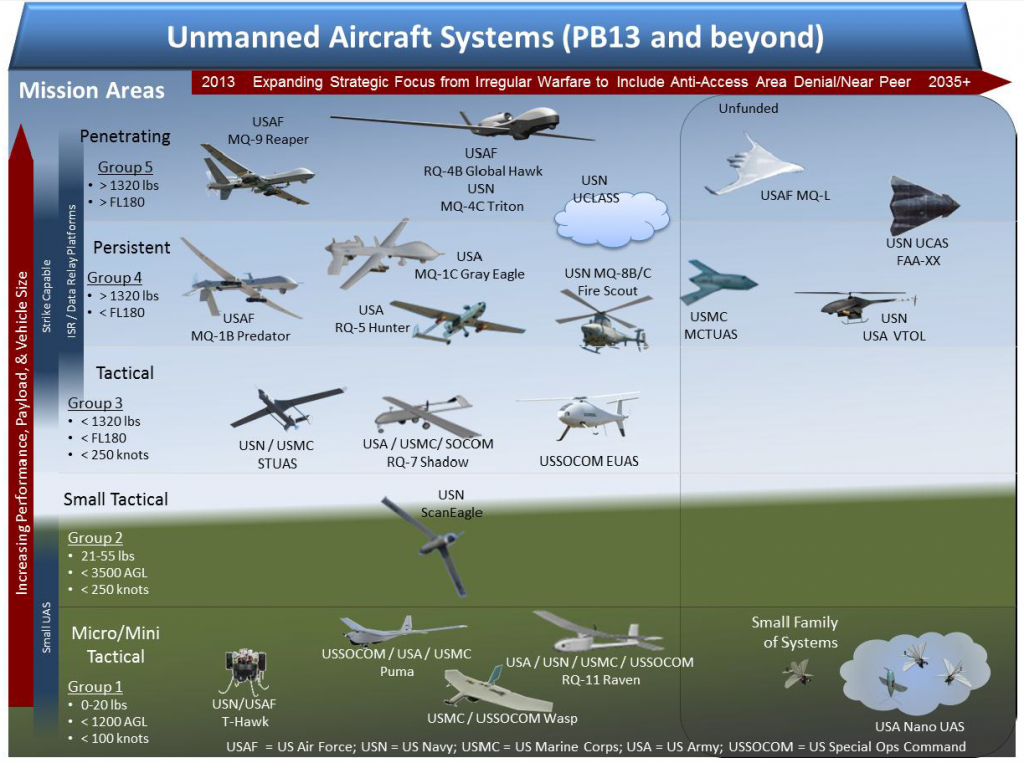



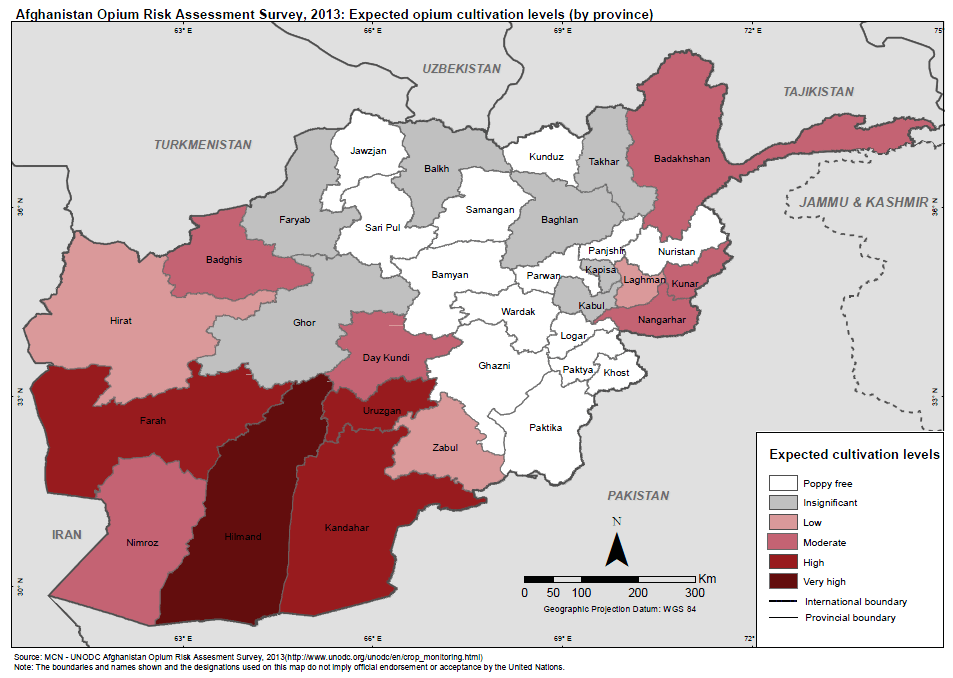









































































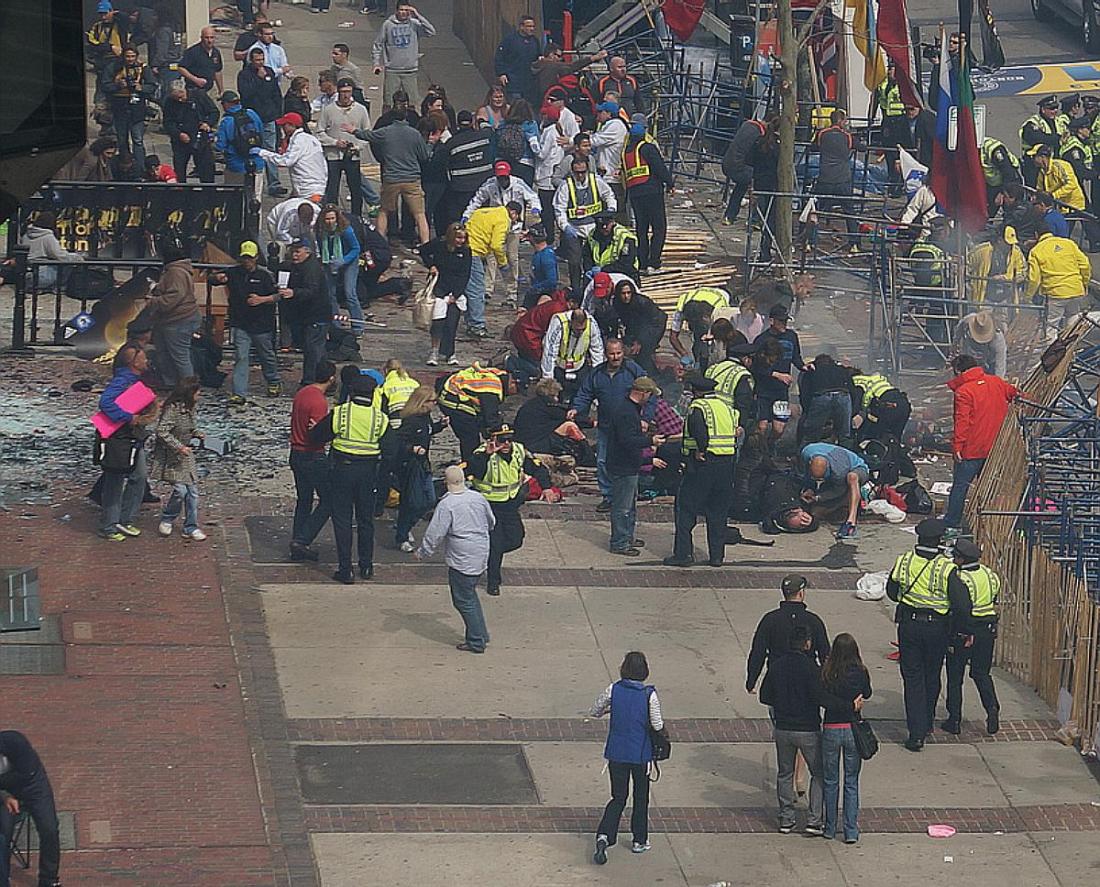



































































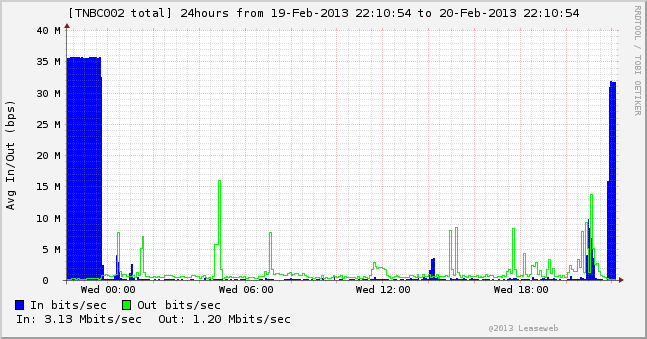
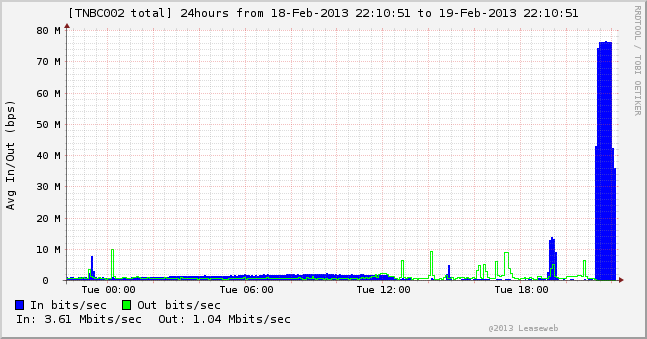
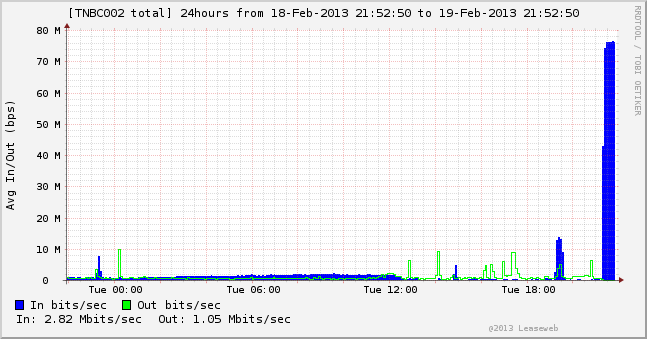
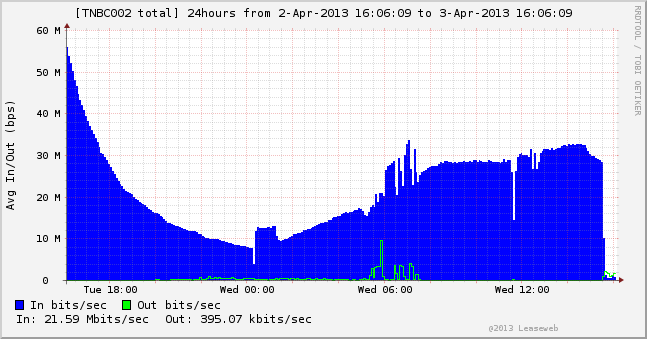


You must be logged in to post a comment.